Page 1

Release
Published
2021-03-04
Notes
Junos®OS 20.4R1 Release Notes
SUPPORTED ON
ACX Series, cRPD, cSRX, EX Series, JRR Series, Juniper Secure Connect, Junos Fusion
•
Enterprise, Junos Fusion Provider Edge, MX Series, NFX Series, PTX Series, QFX Series,
SRX Series, vMX, vRR, and vSRX
SOFTWARE HIGHLIGHTS
Support for mobility on Junos Multi-Access User Plane (MX204, MX240, MX480, MX960,
•
MX10003)
Static VXLAN at VLAN or bridge domain level (MX5, MX10, MX40, MX80, MX150, MX240,
•
MX480, MX960, MX2008, MX2010, MX2020, MX10003, MX10008, MX10016 routers
and QFX5120-32C, QFX5120-48T, and QFX5120-48Y switches)
Support for cRPD in SONiC (PTX10008)
•
Phone-home client (EX4300-48MP Virtual Chassis)
•
RADIUS attributes for dynamic VLAN assignment on colorless ports (EX2300, EX2300-MP,
•
EX3400, EX4300, and EX4300-MP)
ZTP with DHCPv6 client support (EX3400, EX4300, PTX1000, PTX5000, PTX10002-60C,
•
PTX10008, QFX5100, QFX5200, QFX10002, and QFX10002-60C)
Support for express segments to establish end-to-end segment routing path (MX Series
•
and PTX Series)
MAC VRF with EVPN-VXLAN (MX Series and vMX routers; QFX5100, QFX5110, QFX5120,
•
QFX5200, QFX10002, QFX10008, and QFX10016 switches)
Support for tunneling applications in unified policies (NFX Series and SRX Series)
•
Support for unidirectional session refreshing (SRX Series)
•
Page 2

Support for captive portal on Wi-Fi Mini-Physical Interface Module (SRX320, SRX340,
•
SRX345, SRX380, and SRX550HM)
Support for Annex J and G.Fast with specialized SFP (SRX380, SRX300, SRX320, SRX340,
•
and SRX345)
Security policy support for security inspection on VXLAN tunnels (SRX4100, SRX4200,
•
SRX4600, and vSRX)
AWS Key Management Service (KMS) Integration support (vSRX 3.0)
•
IN FOCUS GUIDE
Use this new guide to quickly learn about the most important Junos OS features and how
•
you can deploy them in your network.
Day One+
Use this new setup tool to get your Junos OS up and running in three quick steps.
•
Page 3

Release Notes: Junos®OS Release 20.4R1 for
the ACX Series, cRPD, cSRX, EX Series, JRR
Series, Juniper Secure Connect, Junos Fusion,
MX Series, NFX Series, PTX Series, QFX Series,
SRX Series, vMX, vRR, and vSRX
1
4 March 2021
Contents
Introduction | 15
Junos OS Release Notes for ACX Series | 15
What's New | 16
Hardware | 17
High Availability (HA) and Resiliency | 20
Junos Telemetry Interface | 20
Routing Protocols | 21
Timing and Synchronization | 21
What's Changed | 22
General Routing | 22
MPLS | 23
Network Management and Monitoring | 23
Routing Protocols | 23
User Interface and Configuration | 23
Known Limitations | 24
General Routing | 24
Timing and Synchronization | 24
Page 4

Open Issues | 26
Class of Service (CoS) | 26
General Routing | 26
Platform and Infrastructure | 27
VPNs | 27
Resolved Issues | 28
Forwarding and Sampling | 28
General Routing | 28
Interfaces and Chassis | 31
Layer 2 Features | 31
Routing Protocols | 31
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 32
Upgrade and Downgrade Support Policy for Junos OS Releases | 32
2
Junos OS Release Notes for cRPD | 33
What’s New | 33
Platform and Infrastructure | 34
What's Changed | 34
Junos Telemetry Interface | 35
Known Limitations | 35
Open Issues | 35
Resolved Issues | 35
Routing Policy and Firewall Filters | 36
Junos OS Release Notes for cSRX | 36
What’s New | 36
What's Changed | 36
Platform and Infrastructure | 37
Known Limitations | 37
Open Issues | 38
Resolved Issues | 38
Junos OS Release Notes for EX Series | 38
What's New | 39
Authentication, Authrorization, and Accounting | 39
EVPN | 39
Page 5
Interfaces and Chassis | 42
Junos OS XML, API, and Scripting | 42
Network Management and Monitoring | 43
Routing Protocols | 43
Software Installation and Upgrade | 44
Subscriber Management and Services | 45
What's Changed | 45
MPLS | 47
Network Management and Monitoring | 47
Platform and Infrastructure | 47
User Interface and Configuration | 47
Known Limitations | 48
EVPN | 48
Platform and Infrastructure | 48
3
Open Issues | 49
Infrastructure | 50
Juniper Extension Toolkit (JET) | 50
Platform and Infrastructure | 50
Routing Policy and Firewall Filters | 51
Routing Protocols | 51
User Interface and Configuration | 52
Resolved Issues | 52
Authentication and Access Control | 53
EVPN | 53
Infrastructure | 53
Layer 2 Features | 53
Network Management and Monitoring | 53
Platform and Infrastructure | 53
Routing Protocols | 54
User Interface and Configuration | 55
Virtual Chassis | 55
Documentation Updates | 55
Migration, Upgrade, and Downgrade Instructions | 56
Upgrade and Downgrade Support Policy for Junos OS Releases | 56
Page 6

Junos OS Release Notes for JRR Series | 57
What's New | 57
Routing Protocols | 58
What's Changed | 58
Known Limitations | 59
Routing Protocols | 59
Open Issues | 60
Resolved Issues | 60
Resolved Issues: 20.4R1 Release | 60
Documentation Updates | 61
Migration, Upgrade, and Downgrade Instructions | 61
Upgrade and Downgrade Support Policy for Junos OS Releases | 62
Junos OS Release Notes for Juniper Secure Connect | 63
What’s New | 63
4
What's Changed | 63
Known Limitations | 63
Open Issues | 64
Juniper Secure Connect Client | 64
Resolved Issues | 64
Junos OS Release Notes for Junos Fusion for Enterprise | 64
What’s New | 65
What's Changed | 65
Known Limitations | 66
Open Issues | 66
Resolved Issues | 67
Resolved Issues: Release 20.4R1 | 67
Documentation Updates | 68
Migration, Upgrade, and Downgrade Instructions | 68
Basic Procedure for Upgrading Junos OS on an Aggregation Device | 68
Upgrading an Aggregation Device with Redundant Routing Engines | 70
Preparing the Switch for Satellite Device Conversion | 71
Converting a Satellite Device to a Standalone Switch | 72
Upgrade and Downgrade Support Policy for Junos OS Releases | 72
Downgrading Junos OS | 73
Page 7

Junos OS Release Notes for Junos Fusion for Provider Edge | 74
What's New | 74
Hardware | 75
What's Changed | 75
Known Limitations | 76
Open Issues | 76
Resolved Issues | 77
Documentation Updates | 77
Migration, Upgrade, and Downgrade Instructions | 78
Basic Procedure for Upgrading an Aggregation Device | 78
Upgrading an Aggregation Device with Redundant Routing Engines | 81
Preparing the Switch for Satellite Device Conversion | 81
Converting a Satellite Device to a Standalone Device | 83
Upgrading an Aggregation Device | 85
5
Upgrade and Downgrade Support Policy for Junos OS Releases | 85
Downgrading from Junos OS Release 20.1 | 86
Junos OS Release Notes for MX Series | 86
What's New | 87
Hardware | 88
EVPN | 90
High Availability (HA) and Resiliency | 91
Interfaces and Chassis | 92
Juniper Extension Toolkit (JET) | 92
Junos OS, XML, API, and Scripting | 93
Junos Telemetry Interface | 93
MPLS | 95
Network Management and Monitoring | 96
Routing Policy and Firewall Filters | 97
Routing Protocols | 97
Services Applications | 99
Software Defined Networking | 99
Software Installation and Upgrade | 101
Software Licensing | 101
Subscriber Management and Services | 101
Page 8
System Management | 102
System Logging | 103
What's Changed | 103
Class of Service (CoS) | 105
EVPN | 105
General Routing | 105
Interfaces and Chassis | 106
Infrastructure | 107
J-Web | 107
MPLS | 108
Network Management and Monitoring | 108
User Interface and Configuration | 108
Known Limitations | 109
General Routing | 109
6
Interfaces and Chassis | 109
MPLS | 110
Network Management and Monitoring | 110
Open Issues | 110
Class of Service (CoS) | 111
EVPN | 111
Forwarding and Sampling | 111
General Routing | 111
Infrastructure | 114
Interfaces and Chassis | 114
Juniper Extension Toolkit (JET) | 114
Layer 2 Ethernet Services | 114
MPLS | 114
Platform and Infrastructure | 115
Routing Policy and Firewall Filters | 115
Routing Protocols | 115
User Interface and Configuration | 116
VPNs | 116
Page 9

Resolved Issues | 117
EVPN | 118
Forwarding and Sampling | 118
General Routing | 119
Infrastructure | 125
Interfaces and Chassis | 125
Intrusion Detection and Prevention (IDP) | 126
Juniper Extension Toolkit (JET) | 126
J-Web | 126
Layer 2 Ethernet Services | 126
Layer 2 Features | 127
MPLS | 127
Network Address Translation (NAT) | 128
Network Management and Monitoring | 128
7
Platform and Infrastructure | 128
Routing Policy and Firewall Filters | 129
Routing Protocols | 129
Services Applications | 131
Subscriber Access Management | 131
User Interface and Configuration | 131
VPNs | 131
Documentation Updates | 132
Migration, Upgrade, and Downgrade Instructions | 132
Basic Procedure for Upgrading to Release 20.4R1 | 133
Procedure to Upgrade to FreeBSD 11.x-Based Junos OS | 133
Procedure to Upgrade to FreeBSD 6.x-Based Junos OS | 136
Upgrade and Downgrade Support Policy for Junos OS Releases | 138
Upgrading a Router with Redundant Routing Engines | 138
Downgrading from Release 20.4R1 | 139
Junos OS Release Notes for NFX Series | 139
What’s New | 140
Application Security | 140
High Availability | 142
Flow-Based and Packet-Based Processing | 142
Page 10
Logical Systems and Tenant Systems | 142
Routing Protocols | 142
Security | 143
What's Changed | 143
Junos OS XML API and Scripting | 144
Known Limitations | 144
Interfaces | 145
Open Issues | 145
Interfaces | 146
Platform and Infrastructure | 146
Virtual Network Functions (VNFs) | 146
Resolved Issues | 146
High Availability | 147
Interfaces | 147
8
Platform and Infrastructure | 147
Documentation Updates | 147
Migration, Upgrade, and Downgrade Instructions | 148
Upgrade and Downgrade Support Policy for Junos OS Releases | 148
Basic Procedure for Upgrading to Release 20.4 | 149
Junos OS Release Notes for PTX Series | 150
What's New | 151
Junos OS XML, API, and Scripting | 151
Junos Telemetry Interface | 152
MPLS | 154
Network Management and Monitoring | 155
Routing Policy and Firewall Filters | 155
Routing Protocols | 156
Software Installation and Upgrade | 158
System Logging | 158
What's Changed | 159
Class of Service (CoS) | 159
General Routing | 159
MPLS | 160
Network Management and Monitoring | 160
Page 11
User Interface and Configuration | 160
Known Limitations | 161
General Routing | 161
Routing Protocols | 161
Open Issues | 162
General Routing | 162
Layer 2 Ethernet Services | 164
MPLS | 164
Platform and Infrastructure | 164
Routing Protocols | 164
Resolved Issues | 165
General Routing | 165
Infrastructure | 166
Interfaces and Chassis | 166
9
MPLS | 166
Network Management and Monitoring | 166
Routing Protocols | 167
Documentation Updates | 167
Migration, Upgrade, and Downgrade Instructions | 168
Basic Procedure for Upgrading to Release 20.4 | 168
Upgrade and Downgrade Support Policy for Junos OS Releases | 171
Upgrading a Router with Redundant Routing Engines | 171
Junos OS Release Notes for the QFX Series | 172
What's New | 172
Hardware | 173
Class of Service (CoS) | 187
EVPN | 188
Flow-Based and Packet-Based Processing | 191
High Availability (HA) and Resiliency | 194
Interfaces and Chassis | 194
IP Tunneling | 194
Juniper Extension Toolkit | 194
Junos OS XML, API, and Scripting | 195
Junos Telemetry Interface | 195
Page 12
Network Management and Monitoring | 195
Platform and Infrastructure | 197
Routing Policy and Firewall Filters | 197
Routing Protocols | 198
Software Defined Networking (SDN) | 199
Software Installation and Upgrade | 200
System Management | 201
System Logging | 201
What's Changed | 202
Class of Service (CoS) | 202
General Routing | 202
MPLS | 203
Network Management and Monitoring | 203
User Interface and Configuration | 203
10
Known Limitations | 204
General Routing | 204
Layer 2 Features | 206
Routing Protocols | 206
Open Issues | 207
EVPN | 208
General Routing | 208
High Availability (HA) and Resiliency | 210
Layer 2 Ethernet Services | 210
Layer 2 Features | 210
Platform and Infrastructure | 210
Routing Policy and Firewall Filters | 211
Routing Protocols | 211
Virtual Chassis | 211
Resolved Issues | 212
Resolved Issues: 20.4R1 Release | 212
Documentation Updates | 216
Migration, Upgrade, and Downgrade Instructions | 217
Upgrading Software on QFX Series Switches | 217
Installing the Software on QFX10002-60C Switches | 220
Page 13
Installing the Software on QFX10002 Switches | 220
Upgrading Software from Junos OS Release 15.1X53-D3X to Junos OS Release
15.1X53-D60, 15.1X53-D61.7, 15.1X53-D62, and 15.1X53-D63 on QFX10008 and
QFX10016 Switches | 221
Installing the Software on QFX10008 and QFX10016 Switches | 223
Performing a Unified ISSU | 227
Preparing the Switch for Software Installation | 228
Upgrading the Software Using Unified ISSU | 228
Upgrade and Downgrade Support Policy for Junos OS Releases | 230
Junos OS Release Notes for SRX Series | 231
What’s New | 232
Application Layer Gateways (ALGs) | 233
Application Security | 233
ATP Cloud | 234
11
Authentication and Access Control | 235
Chassis Clustering | 235
Flow-Based and Packet-Based Processing | 237
Interfaces and Chassis | 238
Intrusion Detection and Prevention | 239
Juniper Extension Toolkit (JET) | 240
Junos OS XML and API Scripting | 241
J-Web | 241
Layer 2 Features | 243
Logical Systems and Tenant Systems | 243
Multinode High Availability | 243
Network Management and Monitoring | 244
Securing GTP and SCTP Traffic | 245
Security | 246
Unified Threat Management (UTM) | 247
VPNs | 247
What's Changed | 248
Class of Service (CoS) | 249
Flow-Based and Packet-Based Processing | 249
Intrusion Detection and Prevention (IDP) | 250
Interfaces and Chassis | 250
Page 14
J-Web | 250
Network Address Translation (NAT) | 251
Network Management and Monitoring | 251
Platform and Infrastructure | 251
Securing GTP and SCTP Traffic | 251
User Interface and Configuration | 252
VPNs | 252
Known Limitations | 253
Class of Service (CoS) | 254
Flow-Based and Packet-Based Processing | 254
J-Web | 254
VPNs | 255
Open Issues | 255
Flow-Based Packet-Based Processing | 256
12
Interfaces and Chassis | 256
J-Web | 256
Protocols | 256
Routing Policy and Firewall Filters | 256
VPNs | 257
Resolved Issues | 257
Application Layer Gateways (ALGs) | 258
Flow-Based and Packet-Based Processing | 258
Interfaces and Chassis | 259
Intrusion Detection and Prevention (IDP) | 259
J-Web | 259
Layer 2 Ethernet Services | 260
Network Address Translation (NAT) | 260
Platform and Infrastructure | 260
Routing Policy and Firewall Filters | 260
Routing Protocols | 261
Subscriber Access Management | 261
Unified Threat Management (UTM) | 261
VPNs | 261
Documentation Updates | 261
Page 15

Migration, Upgrade, and Downgrade Instructions | 262
Upgrade and Downgrade Support Policy for Junos OS Releases and Extended End-Of-Life
Releases | 262
Junos OS Release Notes for vMX | 263
What’s New | 264
EVPN | 264
Juniper Extension Toolkit (JET) | 264
Junos OS XML ,API, and Scripting | 265
Network Management and Monitoring | 265
Routing Protocols | 266
What's Changed | 266
Licensing | 267
Known Limitations | 267
Open Issues | 267
13
Resolved Issues | 267
Interfaces and Chassis | 267
Network Management and Monitoring | 268
Licensing | 268
Upgrade Instructions | 268
Junos OS Release Notes for vRR | 269
What’s New | 269
Routing Protocols | 270
What's Changed | 270
Known Limitations | 270
Open Issues | 270
Resolved Issues | 271
Junos OS Release Notes for vSRX | 271
What’s New | 271
ATP Cloud | 272
Flow-Based Packet-Based Processing | 272
High Availability | 273
Juniper Extension Toolkit (JET) | 273
Junos OS XML ,API, and Scripting | 274
Network Management and Monitoring | 274
Page 16

Platform and Infrastructure | 275
Routing Protocols | 275
VPNs | 275
What's Changed | 275
Platform and Infrastructure | 276
Known Limitations | 276
Open Issues | 276
J-Web | 277
Platform and Infrastructure | 277
Resolved Issues | 277
Application Security | 277
Chassis Clustering | 278
CLI | 278
Flow-Based and Packet-Based Processing | 278
14
Install and Upgrade | 278
Interfaces and Chassis | 278
Intrusion Detection and Prevention (IDP) | 278
Platform and Infrastructure | 279
Routing Policy and Firewall Filters | 279
User Access and Authentication | 279
VPNs | 279
Migration, Upgrade, and Downgrade Instructions | 279
Upgrading Software Packages | 281
Validating the OVA Image | 286
Upgrading Using ISSU | 286
Licensing | 287
Compliance Advisor | 287
Finding More Information | 287
Documentation Feedback | 288
Requesting Technical Support | 288
Self-Help Online Tools and Resources | 289
Creating a Service Request with JTAC | 289
Revision History | 290
Page 17
Introduction
Junos OS runs on the following Juniper Networks®products: ACX Series, cRPD, cSRX, EX Series, JRR
Series, Juniper Secure Connect, Junos Fusion Enterprise, Junos Fusion Provider Edge, MX Series, NFX
Series, PTX Series, QFX Series, SRX Series, vMX, vRR, and vSRX.
These release notes accompany Junos OS Release 20.4R1 for the ACX Series, Containerized Routing
Protocol Process (cRPD), cSRX Container Firewall (cSRX), EX Series, JRR Series, Juniper Secure Connect,
Junos Fusion Enterprise, Junos Fusion Provider Edge, MX Series, NFX Series, PTX Series, QFX Series, SRX
Series, virtual MX Series router (vMX), Virtual Route Reflector (vRR), and vSRX Virtual Firewall (vSRX).
They describe new and changed features, limitations, and known and resolved problems in the hardware
and software.
In Focus guide—We have a document called In Focus that provides details on the most important features
•
for the release in one place. We hope this document will quickly get you to the latest information about
Junos OS features. Let us know if you find this information useful by sending an e-mail to
techpubs-comments@juniper.net.
15
Important Information:
•
Upgrading Using ISSU on page 286
•
Licensing on page 287
•
Compliance Advisor on page 287
•
Finding More Information on page 287
•
Documentation Feedback on page 288
•
Requesting Technical Support on page 288
•
Junos OS Release Notes for ACX Series
IN THIS SECTION
What's New | 16
What's Changed | 22
Known Limitations | 24
Open Issues | 26
Resolved Issues | 28
Page 18
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 32
These release notes accompany Junos OS Release 20.4R1 for the ACX Series. They describe new and
changed features, limitations, and known and resolved problems in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What's New
16
IN THIS SECTION
Hardware | 17
High Availability (HA) and Resiliency | 20
Junos Telemetry Interface | 20
Routing Protocols | 21
Timing and Synchronization | 21
This section describes the new features or enhancements to existing features in Junos OS Release 20.4R1
for the ACX Series.
Page 19

Hardware
17
Page 20

We've added the following features to the ACX5448 in Junos OS Release 20.4R1.
•
Table 1: Features Supported by the ACX5448 Routers
DescriptionFeature
18
Authentication, Authorization and
Accounting
Automation
Class of service (CoS)
Ethernet OAM
Support for 802.1X authentication on Layer 3 interfaces. 802.1X is an
•
IEEE standard for port-based network access control that authenticates
users connected to a LAN port. [See 802.1X Authentication.]
Support for either WAN interfaces or management interfaces to
•
automatically download and install the appropriate software and the
configuration file on your device during the ZTP bootstrap process.
[See Zero Touch Provisioning.]
Support for up to three levels of hierarchical scheduling (physical
•
interfaces, logical interfaces, and queues). Configurable buffer support
is also added. By default, all interfaces on the ACX5448 use port-based
scheduling (eight queues per physical port). To enable hierarchical
scheduling, set the hierarchical-scheduler statement at the [edit
interfaces interface-name] hierarchy level. [See Hierarchical Class of
Service in ACX Series Routers.]
Support for Ethernet OAM CFM. You can now synchronize
•
local-interface status between two connected devices with remote
interface up/down trigger with OAM CFM. CFM provides end-to-end
signals even if the two devices are not directly connected. [See
Introduction to OAM Connectivity Fault Management (CFM).]
EVPN
Layer 2 features
Layer 3 features
Support for EVPNs and Interfaces. In EVPN-MPLS and MC-LAG
•
environments, the configuration of anycast gateways on ACX5448
routers that are multihomed in all-active mode is supported. [See
Anycast Gateways.]
Support for pseudowire redundancy in MC-LAG. ACX5448 routers
•
support pseudowire redundant Layer 2 circuits in MC-LAG routers.
VPLS is not supported. [See Understanding Pseudowire Redundancy
Mobile Backhaul Scenarios.]
Support for Layer 3 VPN in MC-LAG chassis. ACX5448 routers support
•
Layer 3 VPN in VRRP over IRB interfaces in MC-LAG routers. Layer
3 routing and Layer 3 VPN are not directly supported on the MC-LAG
interfaces. [See Understanding VRRP and Understanding Layer 3
VPNs.]
Page 21
Table 1: Features Supported by the ACX5448 Routers (continued)
DescriptionFeature
19
Network Security
Software installation and upgrade
Timing and synchronization
Support for control plane DDoS protection, which is enabled by default
•
on ACX5448 routers for many Layer 2 and Layer 3 protocols. Control
Plane DDoS protection uses firewall filters and policers to discard or
rate-limit control plane traffic at the Routing Engine level, which
prevents malicious traffic from interfering with device operations. You
can disable this feature or change the default policer parameters for
supported protocol groups. [See Control Plane Distributed
Denial-of-Service (DDoS) Protection Overview]
Support for the ACX5448-M-LT, a top-of-rack router that supports
•
only Junos Limited image. The Junos Limited image does not have
data-plane encryption and is intended only for countries in the Eurasian
Customs Union because these countries have import restrictions on
software containing data-plane encryption. Unlike the JunosWorldwide
image, the Junos Limited image supports control plane encryption
through Secure Shell (SSH) and Secure Sockets Layer (SSL), thus
allowing secure management of the system. [See ACX5448 System
Overview.]
Support for Precision Time Protocol (PTP) G.8275.2 enhanced profile
•
with PTP over IPv4 and IPv6 unicast traffic. [See Understanding the
PTP G.8275.2 Enhanced Profile (Telecom Profile).]
Support for SFP-1GE-LH-ET transceivers (ACX1100 and ACX2100)—Starting in Junos OS Release
•
20.4R1, the ACX1100 and ACX2100 Universal Metro Routers support the SFP-1GE-LH-ET transceivers.
[See the Hardware Compatibility Tool (HCT) for details.]
Support for SFP-GE80KT14R15 and SFP-GE80KT15R14 transceivers (ACX5448, ACX5448-D, and
•
ACX5448-M)—Starting in Junos OS Release 20.4R1, the ACX5448, ACX5448-D, and ACX5448-M
Universal Metro Routers support the SFP-GE80KT14R15 and SFP-GE80KT15R14 transceivers.
[See the Hardware Compatibility Tool (HCT) for details.]
Support for SFPP-10GE-DWDM-IT transceivers (ACX5448, ACX5448-D, and ACX5448-M)—Starting
•
in Junos OS Release 20.4R1, the ACX5448, ACX5448-D, and ACX5448-M Universal Metro Routers
support the SFPP-10GE-DWDM-IT transceivers.
[See the Hardware Compatibility Tool (HCT) for details.]
Page 22

High Availability (HA) and Resiliency
NSR support for IS-IS with SR (ACX Series, MX Series)—Starting in Junos OS Release 20.4R1, ACX Series
•
devices support NSR for IS-IS with segment routing (SR). To use NSR, you must first enable GRES on
your device.
[See Nonstop Active Routing Concepts]
Junos Telemetry Interface
•
JTI support for persistent active gRPC sessions between collector and server during an SSL certificate
update (ACX Series, MX Series, and PTX Series)—Junos OS Release 20.4R1 supports persistent active
remote procedure call (gRPC) sessions between the collector (client) and server during an SSL certificate
update.
For secure channel authentication, the TLS protocol is used to maintain a secure channel between the
collector and the server. TLS uses the server certificate and the client certificate to authenticate each
other and send encrypted messages over the network. When an SSL certificate is updated, existing gRPC
sessions are abruptly terminated, forcing the collector to initiate a new gRPC connection and subscribe
to sensors again.
20
To avoid this problem, you can enable persistent active gRPC sessions by configuring hot-reloading at
the [edit system services extension-service request-response grpc ssl] hierarchy level. After you enable
this feature, gRPC sessions will remain active even when authentication certificates are updated.
After the certificate is updated, any new gRPC session will use the updated certificate.
[See gRPC Services for Junos Telemetry Interface and ssl.]
•
Juniper Resiliency Interface for exception reporting and null route detection (ACX Series, PTX Series,
and MX Series)—Starting in Junos OS Release 20.4R1, you can use Juniper Resiliency Interface to detect
and reduce Mean Time to Repair (MTTR) first-order network issues. Juniper Resiliency Interface uses a
push model for data reporting from the entities in the system which encounter packet drops. This
automates the workflow for detecting, reporting, and mitigating adverse exceptions.
To collect kernel routing table and routing protocol process exceptions, configure the set system resiliency
exceptions statement at the [edit] hierarchy level to specify exception reporting based on kernel
exceptions, and routing exceptions.
You can display exceptions from a remote collector by means of remote procedure call (gRPC) services
or gRPC network management interface (gNMI) services. Display on-box exceptions by accessing the
/var/log file or the database at /var/db/ResiliencyExceptions.db. No Junos operational mode commands
display these exceptions.
Page 23

Routing Protocols
Support for multiple single-hop EBGP sessions on different links using the same IPv6 link-local address
•
(ACX Series, EX Series, MX Series, PTX Series, QFX Series, SRX Series, vMX, and vSRX)—Starting in
Junos OS Release 20.4R1, you are no longer required to have unique peer addresses for Juniper devices
for every EBGP session. You can now enable single-hop EBGP sessions on different links over multiple
directly connected peers that use the same IPv6 link-local address.
In earlier Junos OS Releases, BGP peers could be configured with link-local addresses, but multiple BGP
peers could not be configured to use the same link-local address on different interfaces.
[See Configure Multiple Single-Hop EBGP Sessions on Different Links Using the Same Link-Local Address
(IPv6).]
Timing and Synchronization
Support for PTP G.8275.2 profile (ACX710)—Starting in Junos OS Release 20.4R1, we support the
•
Precision Time Protocol (PTP) G.8275.2 profile with node type T-BC-P (BC).
21
You can use the [edit protocols ptp profile-type g.8275.2 ] hierarchy level to configure the G.8275.2
profile.
[See Understanding the Time Management Administration Guide and profile-type.]
SEE ALSO
What's Changed | 22
Known Limitations | 24
Open Issues | 26
Resolved Issues | 28
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 32
Page 24
What's Changed
IN THIS SECTION
General Routing | 22
MPLS | 23
Network Management and Monitoring | 23
Routing Protocols | 23
User Interface and Configuration | 23
This section lists the changes in behavior of Junos OS features and changes in the syntax of Junos OS
statements and commands in Junos OS Release 20.4R1 for the ACX Series routers.
22
General Routing
Support for unicast ARP request on table entry expiration—You can configure the device to send a
•
unicast ARP request instead of the default broadcast request when an ARP table entry is about to expire.
The retry requests are unicast at intervals of 5 seconds. Without this option, the retry requests are
broadcast at intervals of 800 milliseconds. This behavior reduces ARP overall broadcast traffic. It also
supports the use case where access nodes are configured not to forward broadcast ARP requests toward
customer CPEs for security reasons and instead translate ARP broadcasts to unicast requests. To confirm
whether this is configured, you can issue the following command: show configuration system arp | grep
unicast-mode-on-expire.
[See arp.]
Support for gigether-options statement (ACX5048, ACX5096)—Junos OS supports the gigether-options
•
statement at the edit interfaces interface-name hierarchy on the ACX5048 and ACX5096 routers.
Previously, support for the gigether-statement was deprecated. See gigether-options and
Page 25

MPLS
The show mpls lsp extensivel and show mpls lsp detail commands display next-hop gateway LSPid —
•
When you use the show mpls lsp extensivel and show mpls lsp detail commands, you'll see next-hop
gateway LSPid in the output.
Network Management and Monitoring
Warning changed for configuration statements that correspond to "deviate not-supported" nodes in
•
YANG data models (ACX Series, EX Series, MX Series, PTX Series, QFX Series, and SRX Series)—If you
configure a statement corresponding to a YANG data model node that defines the deviate not-supported
statement, the Junos OS configuration annotates that statement with the comment Warning: statement
ignored: unsupported platform. In earlier releases, the warning is Warning: 'statement' is deprecated.
Routing Protocols
23
Inet6 is disabled in VT interface (ACX5448)—Starting in this release, the inet6 statement at the edit
•
interfaces vt-interface-number unit unit-number family hierarchy level is disabled.
User Interface and Configuration
Verbose format option to export JSON configuration data (ACX Series, EX Series, MX Series, PTX
•
Series, QFX Series, and SRX Series)—The Junos OS CLI exposes the verbose statement at the edit system
export-format json hierarchy level. The default format to export configuration data in JSON changed
from verbose format to ietf format starting in Junos OS Release 16.1R1. You can explicitly specify the
default export format for JSON configuration data by configuring the appropriate statement at the edit
system export-format json hierarchy level. Although the verbose statement is exposed in the Junos OS
CLI as of the current release, you can configure this statement starting in Junos OS Release 16.1R1.
[See export-format.]
SEE ALSO
What's New | 16
Known Limitations | 24
Open Issues | 26
Resolved Issues | 28
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 32
Page 26
Known Limitations
IN THIS SECTION
General Routing | 24
Timing and Synchronization | 24
Learn about known limitations in this release for the ACX Series.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
General Routing
24
On the ACX710 router, Servo moves to the Holdover-in/Holdover-out/Acq state from the Phase-aligned
•
state with impairment. PR1550367
On the ACX710 router, PTP with Vlan-id-range does not work for specific VLANs. PR1550482
•
On the ACX710 router, the holdover error HOLDOVER OUT OF SPEC does not reset during the Servo
•
state change. PR1556798
Timing and Synchronization
On the ACX5448 router, the two-way time error and CTE for 1 PPS does not meet the class A metrics.
•
PR1535434
On the ACX5448-M router, the 1 PPS CTE does not meet the class A performance in 1-Gigabits interface.
•
PR1542744
On the ACX5448 router, due to BRCM KBP issue route lookup might fail. PR1533557
•
On the ACX5448 router, ping stops working even though the ARP entry is present during continuous
•
script executions. PR1533513
On the ACX710 router, T1 or T4 cTE should be tuned closer to two-way CTE. PR1527347
•
On the ACX710 router, huge offset is observed initially with ACQ and holdover inspec and outspec
•
conditions. PR1534470
On the ACX710 router, the incremental PTP FPGA upgrades do not bundle along with the regular image
•
upgrades. PR1540799
Page 27

On the ACX710 router, changing the PTP profile type from g.8275.1 to g.8275.2 requires the Packet
•
Forwarding Engine to reboot and the clksyncd process to restart. As a workaround, you must reboot
the Packet Forwarding Engine and restart the clocking process before you change the profile. PR1546614
On the ACX710 router, the Servo transition is incorrect after chassis restart. PR1550270
•
On the ACX710 router, the delay-asymmetry compensation update does not work at CLI with the
•
G.8275.2 profile. PR1550441
On the ACX710 router, the PTP Servo status shows holdover during transition between virtual port and
•
PTP. PR1510880
On the ACX710 router, if the client clock candidate is configured with a virtual port, the clock class is
•
on T-BC. PR1520204
On the ACX710 router, the SyncE to 1PPS transient test results do not meet G.8273.2 SyncE to 1PPS
•
transient metric. PR1522796
On the ACX710 router, the clock parameters are incorrect in certain scenarios when the Servo is in the
•
FREERUN state. PR1548192
25
On the ACX710 router, the PTP Servo takes longer time to lock after the clksyncd process restarts.
•
PR1549952
On the ACX710 router, the show ptp global-information command does not display correct Clock Class
•
or ESMC QL details when the Servo goes to the Holdover-in state. PR1553213
On the ACX710 router, the Servo transition is incorrect during the T-GM switchover scenario. PR1553439
•
SEE ALSO
What's New | 16
What's Changed | 22
Open Issues | 26
Resolved Issues | 28
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 32
Page 28
Open Issues
IN THIS SECTION
Class of Service (CoS) | 26
General Routing | 26
Platform and Infrastructure | 27
VPNs | 27
Learn about open issues in this release for the ACX Series.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
26
Class of Service (CoS)
Unexpected behavior of Class of Service is observed with the wildcard classifier. PR1559516
•
General Routing
On the ACX5448 router, latency is observed for the host-generated ICMP traffic. PR1380145
•
Tx power cannot be configured using the + sign. PR1383980
•
On the ACX710 router, alarm is not raised when booting the system with recovery snapshot. PR1517221
•
On the ACX5448 router, the BGPV6LU traffic drop is observed when the node is deployed in ingress.
•
PR1538819
On the ACX500-I router, the show services session count does not work as expected. PR1520305
•
The ARP packets from the CE device are added with VLAN tag if the VLAN-ID is configured in the EVPN
•
routing instance. PR1555679
On the ACX710 router, the global configuration of IPv4-dscp naming convention must be corrected as
•
per the stream level dscp, which is more meaningful for both the the IPv6 and IPv4 services. PR1557262
On the ACX5448 router, the unicast packets from the CE devices might be forwarded by the PE devices
•
with additional VLAN tag if IRB is used. PR1559084
On the ACX5048 router, the fxpc process generates core file on the analyzer configuration. PR1559690
•
Page 29

On the ACX5448 router, the following syslog message is reported every 30 seconds;
•
ACX_DFW_CFG_FAILED: ACX Error (dfw):dnx_dfw_dyn_entry_counter_get : Entry is invalid. PR1562323
On the ACX5448 router, the transit DHCPv4 and DHCPv6 packets drop in a Layer 2 domain. PR1517420
•
On the ACX5448 router, the ISSU upgrade fails due to the Packet Forwarding Engine restart issue.
•
PR1554915
On the ACX5048 router, all the OAM sessions are not established. PR1561751
•
Even though enhanced-ip is active, the following alarm is observed during ISSU: RE0 network-service
•
mode mismatch between configuration and kernel setting. PR1546002
The ACX5448 device as TWAMP server delays the start session acknowledgment by 10 seconds.
•
PR1556829
On the ACX2100 device, laser-output-power is seen after the interface is disabled and rebooted.
•
PR1560501
Inline BFD stays down with IS-IS or Static clients. PR1561590
•
27
Platform and Infrastructure
The CFM REMOTE MEP does not come up after configuration or if the MEP remains in the Start state.
•
PR1460555
VPNs
On the ACX5448 router, the MC-AE Layer 2 circuit states are not updated instantly and for some time
•
after disabling the core interface on the MC-LAG active node, double hit in traffic is observed. PR1543408
SEE ALSO
What's New | 16
What's Changed | 22
Known Limitations | 24
Resolved Issues | 28
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 32
Page 30
Resolved Issues
IN THIS SECTION
Forwarding and Sampling | 28
General Routing | 28
Interfaces and Chassis | 31
Layer 2 Features | 31
Routing Protocols | 31
This section lists the issues fixed in Junos OS Release 20.4R1 for the ACX Series.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
28
Forwarding and Sampling
VLAN-ID based firewall match conditions might not work for the VPLS service. PR1542092
•
General Routing
The gigether-options command is enabled again under the interface hierarchy. PR1430009
•
Repeated powering-off or powering-on of the device, the SMBUS transactions timeout occurs. PR1463745
•
On the ACX5048 router, the egress queue statistics do not work for the aggregated Ethernet interfaces.
•
PR1472467
On the ACX5048 router, traffic loss is observed during the unified ISSU upgrade. PR1483959
•
The following syslog error message is observed: ACX_DFW_CFG_FAILED. PR1490940
•
On the ACX5048 and ACX5096 routers, the LACP control packets might be dropped due to high CPU
•
utilization. PR1493518
On the ACX710 router, high convergence is observed with the EVPN-ELAN service in a scaled scenario
•
during FRR switchover. PR1497251
On the ACX5448 router, the EXP rewrite for the Layer 3 VPN sends all traffic with incorrect EXP.
•
PR1500928
The following error message is observed during MPLS route add, change, and delete operation: mpls_extra
•
NULL. PR1502385
Page 31

The ACX1100, ACX2100, ACX2200, ACX2000, and ACX4000 routers might stop forwarding transit
•
and control traffic. PR1508534
On the ACX710 router, the Packet Forwarding Engine might crash and the fpc process might remain
•
down. PR1509402
The loopback filter cannot take more than 2 TCAM slices. PR1513998
•
On the ACX710 router, the following error message is observed in the Packet Forwarding Engine while
•
the EVPN core link flaps: dnx_l2alm_add_mac_table_entry_in_hw. PR1515516
The VM process generates a core file while running stability test in a multidimensional scenario.
•
PR1515835
The l2ald process crashes during stability test with traffic on a scaled setup. PR1517074
•
On the ACX710 router, whenever a copper optic interface is disabled and enabled, the speed shows 10
•
Gbps rather than 1 Gbps. This issue is not seen with the fiber interface. PR1518111
Tagged traffic matching the vlan-list configuration in the vlan-circuit cross-connect logical interface gets
•
dropped in the ingress interface. PR1519568
29
The Incompatible Media alarm is not raised when the Synchronous Ethernet source is configured over
•
the copper SFP. PR1519615
On the ACX710 router, the alarm port configuration is not cleared after deleting the alarm-port.
•
PR1520326
PTP to 1PPS noise transfer test fails for frequency 1.985 Hz. PR1522666
•
The show class-of-service interface command does not show the classifier information. PR1522941
•
Interface does not come up with the auto-negotiation setting between the ACX1100 router and the
•
other ACX Series routers, MX Series routers and QFX Series switches as the other end. PR1523418
With the ACX5448 router with 1000 CFM, the CCM state does not go in the Ok state after loading the
•
configuration or restarting the Packet Forwarding Engine. PR1526626
On the ACX5448 and ACX710 routers, the vlan-id-list statement might not work as expected. PR1527085
•
The FEC field is not displayed when the interface is down. PR1530755
•
The show class-of-service routing-instance does not show the configured classifier. PR1531413
•
Memory leak in Local OutLif in VPLS/CCC topology is observed. PR1532995
•
The clksyncd process generates core file on Junos OS Release 20.3R1.3 image. PR1537107
•
The rpd process generates core file at l2ckt_vc_adv_recv, l2ckt_adv_rt_flash (taskptr=0x4363b80,
•
rtt=0x4418100, rtl=< optimized out>, data=< optimized out>, opcode=< optimized out>) at
../../../../../../../../../src/junos/usr.sbin/rpd/l2vpn/l2ckt.c:7982. PR1537546
The Management Ethernet link down alarm is observed while verifying the system alarms in the Virtual
•
Chassis setup. PR1538674
Page 32

On the ACX5448 router, unexpected behavior of the show chassis network-services command is
•
observed. PR1538869
The following error message is observed while deleting the remote stream 0 0 0 0 0 0 along with feb
•
core file at 0x00ae6484 in bcmdnx_queue_assert (queue=0xc599b60) at
../../../../../src/pfe/common/drivers/bcmdnx/bcmdnx_sdk_ukern_layer.c: Err]
clksync_mimic_delete_clock_entry Unexpected error. PR1539953
The announcement or synchronization interval rate range is not as expected. PR1542516
•
Synchronization Ethernet goes in the Holdover state and comes back to the Locked state when the PTP
•
configuration is deleted. PR1546681
The ACX5448 router as transit for the BGP labeled unicast drops traffic. PR1547713
•
Multicast traffic is stopped when HQoS with multicast configurations are applied. PR1551248
•
With the no-local-switching command, traffic between the local and remote CE devices are affected.
•
PR1527231
On the ACX710 router, the T-BC-P switch-over performance fails beyond the standard mask and servo
•
moving to multiple Holdover-in state, Acquiring state, Holdover-in state, Holdover-out state, and
Acquiring state. PR1556087
30
Running SNMP MIB walk and executing the show interfaces command might cause the picd process to
•
crash. PR1533766
On the ACX5448 router, you cannot downgrade to Junos OS Release 18.4 code-base. PR1556377
•
BIND does not sufficiently limit the number of fetches while processing referrals. PR1512212
•
The clksyncd process generates core file during the stability test with traffic and scale. PR1518253
•
The fxpc process generates core file during EEPROM read when SFP is removed. PR1518480
•
On the ACX5448 routers, multicast traffic loop over ICL might be observed. PR1521113
•
On the ACX710 router, PIR/CIR HQoS behavior is inconsistent. PR1525789
•
Error messages are displayed while attaching tcp on physical interfaces. PR1527541
•
The l2cpd memory leak might be observed with the aggregated Ethernet interface flap. PR1527853
•
Upon classifying the Layer 3 packets, DSCP is not preserved and is lost at the egress due to the limitations
•
of a chipset. PR1535876
Other than IPv4 and IPV6, other IPs should not be forwarded. Only IP header with version 4 and 6 can
•
pass through. PR1550748
Profile switch between G.8275.1 and G.8275.2 works as expected. PR1533263
•
Page 33

Interfaces and Chassis
The fpc process might crash in the inline mode with CFM configured. PR1500048
•
Layer 2 Features
On the ACX5448 routers, the VPLS traffic statistics are not displayed when the show vpls statistics
•
command is executed. PR1506981
The rpd might crash on the new primary Routing Engine after GRES in the VPLS or Layer 2 circuit scenario.
•
PR1507772
Routing Protocols
The rpd process might report 100 percent CPU usage with the BGP route damping enabled. PR1514635
•
On the ACX5448 routers, the family inet6 configuration under the vt- interface is disabled. PR1514595
•
31
SEE ALSO
What's New | 16
What's Changed | 22
Known Limitations | 24
Open Issues | 26
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 32
Documentation Updates
There are no errata or changes in Junos OS Release 20.4R1 documentation for ACX Series routers.
SEE ALSO
What's New | 16
What's Changed | 22
Open Issues | 26
Page 34

Known Limitations | 24
Resolved Issues | 28
Migration, Upgrade, and Downgrade Instructions | 32
Migration, Upgrade, and Downgrade Instructions
IN THIS SECTION
Upgrade and Downgrade Support Policy for Junos OS Releases | 32
This section contains the upgrade and downgrade support policy for Junos OS for ACX Series routers.
Upgrading or downgrading Junos OS might take several minutes, depending on the size and configuration
of the network.
32
For information about software installation and upgrade, see the Installation and Upgrade Guide.
Upgrade and Downgrade Support Policy for Junos OS Releases
Support for upgrades and downgrades that span more than three Junos OS releases at a time is not
provided, except for releases that are designated as Extended End-of-Life (EEOL) releases. EEOL releases
provide direct upgrade and downgrade paths—you can upgrade directly from one EEOL release to the
next EEOL release even though EEOL releases generally occur in increments beyond three releases.
You can upgrade or downgrade to the EEOL release that occurs directly before or after the currently
installed EEOL release, or to two EEOL releases before or after. For example, Junos OS Releases 19.3,
19.4, and 20.1 are EEOL releases. You can upgrade from Junos OS Release 19.3 to Release 19.4 or from
Junos OS Release 19.3 to Release 20.1.
You cannot upgrade directly from a non-EEOL release to a release that is more than three releases ahead
or behind. To upgrade or downgrade from a non-EEOL release to a release more than three releases before
or after, first upgrade to the next EEOL release and then upgrade or downgrade from that EEOL release
to your target release.
For more information about EEOL releases and to review a list of EEOL releases, see
https://www.juniper.net/support/eol/junos.html.
For information about software installation and upgrade, see the Installation and Upgrade Guide.
Page 35
SEE ALSO
What's New | 16
What's Changed | 22
Known Limitations | 24
Open Issues | 26
Resolved Issues | 28
Documentation Updates | 31
Junos OS Release Notes for cRPD
IN THIS SECTION
33
What’s New | 33
What's Changed | 34
Known Limitations | 35
Open Issues | 35
Resolved Issues | 35
These release notes accompany Junos OS Release 20.4R1 for the containerized routing protocol process
(cRPD) container. They describe new and changed features, limitations, and known and resolved problems
in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What’s New
IN THIS SECTION
Platform and Infrastructure | 34
Page 36

Learn about new features introduced in the Junos OS main and maintenance releases for cRPD.
Platform and Infrastructure
Support for eventd (cRPD)—Starting in Junos OS Release 20.4R1, we support only external event policies.
•
You can enable these policies in container RPD. In cRPD, eventd and rsyslogd run as two independent
processes. The eventd process provides event interface to processes such as rpd/auditd/mgd and
supports automated event policy execution.
Use the set event-options policy policy name events [events] then command to enable an event policy
and restart event-processing to restart event processing.
By default, Python 3.x support is enabled along with existing on-box Python/SLAX functions in cRPD
environment.
Use the [edit system scripts language python3] command to enable and to support python event
automation.
[See event-options, events and event-policy.]
34
Support for Configuring cRPD through SONiC (PTX10008)—Juniper Networks’ PTX10008 router
•
supports configuring cRPD in SONiC through the config_db.json configuration utility. The config_db.json
utility is a local redis database (redis-db). You need to do a config save and config load for the
configurations to take effect in cRPD.
Support for cRPD in SONiC (PTX10008)—cRPD routing stack is supported on PTX10008 router running
•
SONiC.
What's Changed
IN THIS SECTION
Junos Telemetry Interface | 35
Learn about what changed in the Junos OS main and maintenance releases for cRPD.
Page 37

Junos Telemetry Interface
cRPD supports the Junos Telemetry Interface (JTI) over TLS similar to Junos OS (cRPD)—cRPD supports
•
local (server-side) certificate validation for gRPC and JTI similar to Junos OS. cRPD doesn't support
bidirectional authentication for gRPC and JTI. See Configuring gRPC for the Junos Telemetry Interface
and Importing SSL Certificates for Junos XML Protocol Support.
Known Limitations
There are no known behavior for cRPD in Junos OS Release 20.4R1.
Open Issues
35
There are no open issues for cRPD in Junos OS Release 20.4R1.
Resolved Issues
Learn which issues were resolved in the Junos OS main and maintenance releases for cRPD.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
Page 38

Routing Policy and Firewall Filters
The show route forwarding-table or show route instance operational commands output is incomplete.
•
PR1545415
Junos OS Release Notes for cSRX
IN THIS SECTION
What’s New | 36
What's Changed | 36
Known Limitations | 37
36
Open Issues | 38
Resolved Issues | 38
These release notes accompany Junos OS Release 20.4R1 for the cSRX Container Firewall, a containerized
version of the SRX Series Services Gateway. They describe new and changed features, limitations, and
known and resolved problems in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What’s New
There are no new features in Junos OS Release 20.4R1 for cSRX.
What's Changed
IN THIS SECTION
Platform and Infrastructure | 37
Page 39

Learn about what changed in the Junos OS main and maintenance releases for cSRX.
Platform and Infrastructure
Downloading of Signature Pack You can download the signature pack from the Signature Pack directly
•
when the cSRX doesn’t have pre-installed signature pack.
Configure proxy server so that IP address of proxy server is reachable from cSRX.
•
Run the following command to enter the configurational mode from CLI.
•
root@host> configure [edit]
root@host#
Configure proxy server profile on cSRX using IP address and port of proxy server.
•
root@host#set services proxy profile appid_sigpack_proxy protocol http host 4.0.0.1
root@host#set services proxy profile appid_sigpack_proxy protocol http port 3128
Attach the profile to AppID and IDP.
•
root@host#set services application-identification download proxy-profile appid_sigpack_proxy
root@host#set security idp security-package proxy-profile appid_sigpack_proxy
37
Commit the configuration.
•
root@host#commit and-quit
commit complete
Download IDP and APPID sigpack through proxy server.
•
root@host>request services application-identification download
root@host>request security idp security-package download
To verify if download is going through proxy server:
•
Verify the logs in proxy server.
[root@srxdpi-lnx39 squid]# cat /var/log/squid/access.log 1593697174.470 1168 4.0.0.254
TCP_TUNNEL/200 5994 CONNECT signatures.juniper.net:443 - HIER_DIRECT/66.129.242.156 -
1593697175.704 1225 4.0.0.254 TCP_TUNNEL/200 11125 CONNECT signatures.juniper.net:443 HIER_DIRECT/66.129.242.156 - 1593697176.950 1232 4.0.0.254 TCP_TUNNEL/200 5978 CONNECT
signatures.juniper.net:443 - HIER_DIRECT/66.129.242.156 - 1593697178.195 1236 4.0.0.254
TCP_TUNNEL/200 11188 CONNECT signatures.juniper.net:443 - HIER_DIRECT/66.129.242.156 -
1593697198.337 1243 4.0.0.254 TCP_TUNNEL/200 6125 CONNECT signatures.juniper.net:443 HIER_DIRECT/66.129.242.156 In cSRX, TLS protocol is used and traffic through proxy is encrypted.
Known Limitations
There are no known behavior for cSRX in Junos OS Release 20.4R1.
Page 40

Open Issues
There are no open issues for cSRX in Junos OS Release 20.4R1.
Resolved Issues
There are no resolved issues for cSRX in Junos OS Release 20.4R1.
Junos OS Release Notes for EX Series
38
IN THIS SECTION
What's New | 39
What's Changed | 45
Known Limitations | 48
Open Issues | 49
Resolved Issues | 52
Documentation Updates | 55
Migration, Upgrade, and Downgrade Instructions | 56
These release notes accompany Junos OS Release 20.4R1 for the EX Series. They describe new and
changed features, limitations, and known and resolved problems in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
Page 41

What's New
IN THIS SECTION
Authentication, Authrorization, and Accounting | 39
EVPN | 39
Interfaces and Chassis | 42
Junos OS XML, API, and Scripting | 42
Network Management and Monitoring | 43
Routing Protocols | 43
Software Installation and Upgrade | 44
Subscriber Management and Services | 45
39
Learn about new features introduced in this release for EX Series Switches.
NOTE: The following EX Series switches are supported in Release 20.4R1: EX2300, EX3400,
EX4300, EX4600, EX4650, EX9200, EX9204, EX9208, EX9214, EX9251, and EX9253.
Authentication, Authrorization, and Accounting
RADIUS attributes for dynamic VLAN assignment on colorless ports (EX2300, EX2300-MP, EX3400,
•
EX4300, and EX4300-MP)—We now support IETF-defined RADIUS attributes that provide VLAN
assignments and also indicate whether frames on the VLAN are in tagged or untagged format. This
enables the network access control server to dynamically assign VLANs on colorless ports. The VLAN
assignments, which are based on device profiling, can be made on either access ports or trunk ports.
[See Dynamic VLAN Assignment on Colorless Ports.]
EVPN
MAC limit, MAC move limit, and persistent MAC learning with EVPN-VXLAN (EX4300-48MP)—We
•
support the following Layer 2 port security features in an EVPN-VXLAN overlay network:
MAC limit—You can limit the number of MAC addresses learned by network (local) interfaces.
•
Page 42

NOTE: We don’t support MAC limits on virtual tunnel endpoint (VTEP) interfaces.
MAC move limit—You can limit the number of times a MAC address is moved to a different interface
•
within 1 second. To configure this feature, you apply a limit to a VLAN. In an EVPN-VXLAN network,
a VLAN’s members can include network (local) and VTEP interfaces. We support the following MAC
move use cases and actions:
MAC moves between network interfaces—By default, the configured action is applied on the interface
•
to which the MAC address is last moved. If you configured action priority on the interfaces, the
action is applied on the interface with the lesser priority.
MAC moves between network and VTEP interfaces and vice-versa—The action is applied on the
•
network interface.
NOTE: We don’t support MAC moves between the following:
40
VTEP interfaces.
•
A VTEP interface and a network interface on which persistent MAC learning and static
•
MAC addresses are configured.
Persistent MAC learning (sticky MAC)—You can enable network interfaces to retain dynamically learned
•
MAC addresses when the switch is restarted or when an interface goes down and comes back up
again.
NOTE: We don’t support persistent MAC learning on VTEP interfaces.
[See Understanding MAC Limiting and MAC Move Limiting and Understanding and Using Persistent
MAC Learning.]
MC-LAG emulation in an EVPN deployment (EX Series, MX Series, and vMX)—Starting in Junos OS
•
Release 20.4R1, you can emulate the function of an MC-LAG in active-standby mode in an EVPN
configuration without having to configure an ICCP or ICL interface. In a standard EVPN configuration,
logical interfaces configured on an aggregated Ethernet interface can have different designated forwarder
election roles. To emulate an MC-LAG configuration, the designated forwarder (DF) takes on the role
of the aggregated Ethernet interface. The provider edge (PE) that is the non-DF will send LACP out-of-sync
packets to the CE. This causes LACP to go down on the CE device, and the CE device does not use the
links connected to the non-DF for sending traffic. If the connection between a CE and a DF PE fails, the
PE is re-elected as a DF. If the connection between a CE and a non-DF PE fails, the current DF PE is not
changed.
Page 43

To enable this functionality, configure the lacp-oos-on-ndf statement at the [edit interfaces interface
name esi df-election-granularity per-esi] hierarchy.
Support for IGMP snooping and selective multicast forwarding (EX4300-MP)—Starting in Junos OS
•
Release 20.4R1, the EX4300-MP switch supports IGMP snooping and selective multicast forwarding in
an EVPN-VXLAN centrally-routed bridging overlay network with all-active multihoming. Selective
multicast Ethernet (SMET) forwarding is part of IGMP snooping. IGMP snooping and SMET forwarding
reduce the volume of multicast traffic in a broadcast domain by forwarding multicast traffic only to
interfaces that have IGMP listeners. SMET forwarding sends multicast packets to the leaf devices in the
core that have expressed an interest in that multicast group. SMET forwarding is supported only in
intra-VLAN replication. This feature supports EVPN Type 7 (IGMP Join Synch Route) and EVPN Type
8 (IGMP Leave Synch Routes). To configure IGMP snooping, include the igmp-snooping proxy
configuration statement at the [edit routing-instances routing-instance-name protocols] hierarchy level.
[See Overview of Multicast Forwarding with IGMP Snooping in an EVPN-VXLAN Environment and
Overview of Selective Multicast Forwarding.]
Support for assisted replication (EX4300MP)—Starting in Junos OS Release 20.4R1, the EX4300-MP
•
switch supports assisted replication in an EVPN-VXLAN centrally-routed bridging overlay network with
all-active multihoming. Assisted replication (AR) optimizes multicast traffic flow by offloading traffic
replication to devices that can more efficiently handle replication and forwarding. You can configure the
EX4300-MP only as an AR-leaf device. You can further optimize multicast traffic by configuring AR with
IGMP snooping. To configure the EX4300-MP as an AR leaf, include the assisted-replication leaf
statement at the [edit routing-instances routing-instance-name protocols evpn] or [edit protocols evpn]
hierarchy level.
41
[See Assisted Replication Multicast Optimization in EVPN Networks
Support for sFlow in an EVPN-VXLAN network (EX4300-MP)—Starting in Junos OS Release 20.4R1,
•
sFlow monitoring is supported on EX4300-MP switches in an EVPN-VXLAN network. sFlow monitoring
provides visibility into your EVPN VXLAN network by sampling VXLAN-encapsulated traffic at the
ingress and egress interfaces. You can configure sFlow technology on a device to monitor traffic
continuously at wire speed on all interfaces simultaneously. You must enable sFlow monitoring on each
interface individually. Configure sFlow monitoring at the [edit protocols sflow] hierarchy level. Use the
show sflow collector command to display the collector statistics and the clear sflow collector command
to delete the collector statistics.
[See Overview of sFlow Technology.]
Layer 3 gateway in an EVPN-MPLS environment (EX9200 with EX9200-SF3 switch fabric module and
•
EX9200-15C line card)—Starting in Junos OS Release 20.4R1, an EX9200 switch with an EX9200-SF3
switch fabric module and an EX9200-15C line card can act as a default Layer 3 gateway for an EVPN
instance (EVI) that can span a set of devices. In this role, the EX9200 switch can perform inter-subnet
forwarding. With inter-subnet forwarding, each subnet represents a distinct broadcast domain.
Page 44

The Layer 3 gateway supports the following features:
IRB interfaces through which the default gateway routes IPv4 and IPv6 traffic from one VLAN to
•
another [See Example: Configuring EVPN with IRB Solution.]
Dynamic list next hop [See Configuring Dynamic List Next Hop.]
•
EVPN proxy ARP and ARP suppression, and proxy NDP and NDP suppression on IRB interfaces [See
•
EVPN Proxy ARP and ARP Suppression, and Proxy NDP and NDP Suppression.]
Substitution of a source MAC address with a proxy MAC address in an ARP or NDP reply [See ARP
•
and NDP Request with a Proxy MAC Address.]
Data center interconnectivity using EVPN Type 5 routes [See EVPN Type-5 Route with MPLS
•
encapsulation for EVPN-MPLS.]
Interfaces and Chassis
10GBASE-T SFP+ transceiver for EX4600-40F—Starting in Junos OS Release 20.4R1, EX4600-40F
•
switches support the 10GBASE-T SFP+ transceiver (JNP-SFPP-10GE-T), capable of working at speeds
of 10 Gbps, 1Gbps, and 100Mbps, and also auto-negotiation. You can use the existing show commands
such as the show interfaces media command to view the details of the transceivers.
42
[See speed(Ethernet).]
Junos OS XML, API, and Scripting
Support for Certificate Authority Chain Profile (EX2300, EX3400, EX4300, MX240, MX480, MX960,
•
PTX-5000, VMX, vSRX and QFX5200)—Starting in Junos OS Release 20.4R1, you can configure
intermediate Certificate Authority (CA) chain profile certificate and perform https REST API request
using mutual and server authentications.
To configure intermediate ca-chain certificate, configure ca-chain ca-chain statement at the [edit system
services rest https] hierarchy level.
Start time option for interval-based internal events that trigger event policies (EX Series, MX Series,
•
PTX Series, QFX Series, and SRX Series)—Starting in Junos OS Release 20.4R1, when you create an
interval-based internal event for triggering event policies, you can specify the start date and time for
the initial event. To specify a start time, configure the start-time option along with the time-interval
option at the [edit event-options generate-event] hierarchy level.
[See Generating Internal Events to Trigger Event Policies.]
Page 45

Network Management and Monitoring
Configuration retrieval using the configuration revision identifier (EX3400, EX4300, MX204, MX240,
•
MX480, MX960, MX2020, PTX3000, PTX10008, QFX5100, QFX10002-60C, SRX5800, vMX, and
vSRX)—Starting in Junos OS Release 20.4R1, you can use the configuration revision identifier feature
to view the configuration for a specific revision. This configuration database revision can be viewed with
the CLI command show system configuration revision.
[See show system configuration revision.]
Junos XML protocol operations support loading and comparing configurations using the configuration
•
revision identifier (EX3400, EX4300, MX204, MX240, MX480, MX960, MX2020, PTX3000, PTX10008,
QFX5100, QFX10002-60C, SRX5800, vMX, and vSRX)—Starting in Junos OS Release 20.4R1, the Junos
XML management protocol operations support loading and comparing configurations by referencing
the configuration revision identifier of a committed configuration. You can execute the
<load-configuration> operation with the configuration-revision attribute to load the configuration with
the given revision identifier into the candidate configuration. Additionally, you can compare the candidate
or active configuration to a previously committed configuration by referencing the configuration revision
identifier for the comparison configuration. The <get-configuration> operation supports the
compare="configuration-revision" and configuration-revision attributes to perform the comparison.
43
[See <get-configuration> and <load-configuration>.]
Routing Protocols
BGP Prefix-Independent Convergence (PIC) Edge for MPLS VPNs (EX9200)—You can now install a
•
Layer 3 VPN route in the forwarding table as an alternate path, enabling fast failover when a provider
edge (PE) router fails or you lose connectivity to a PE router. This already installed path is used until
global convergence through the IGP is resolved.
To enable BGP PIC Edge in an MPLS VPN, include the protect-core statement at the [edit
routing-instances routing-instance-name routing-options] hierarchy level. Both IS-IS LDP and OSPF LDP
are supported. When BGP PIC Edge is enabled, the show route extensive command now displays the
weight assigned to the indirect hop.
[See Configuring BGP PIC Edge for MPLS Layer 3 VPNs.]
Support for multiple single-hop EBGP sessions on different links using the same IPv6 link-local address
•
(ACX Series, EX Series, MX Series, PTX Series, QFX Series, SRX Series, vMX, and vSRX)—Starting in
Junos OS Release 20.4R1, you are no longer required to have unique peer addresses for Juniper devices
for every EBGP session. You can now enable single-hop EBGP sessions on different links over multiple
directly connected peers that use the same IPv6 link-local address.
In earlier Junos OS Releases, BGP peers could be configured with link-local addresses, but multiple BGP
peers could not be configured to use the same link-local address on different interfaces.
Page 46

[See Configure Multiple Single-Hop EBGP Sessions on Different Links Using the Same Link-Local Address
(IPv6).]
Software Installation and Upgrade
Phone-home client (EX4600, EX4650, EX9200, QFX5110, QFX5200, QFX5210, QFX5120-32C, and
•
QFX5120-48Y)—Starting with Junos OS Release 20.4R1, you can use either the legacy
DHCP-options-based ZTP or the phone-home client (PHC) to provision software for the switch. When
the switch boots up, if there are DHCP options that have been received from the DHCP server for ZTP,
ZTP resumes. If DHCP options are not present, PHC is attempted. PHC enables the switch to securely
obtain bootstrapping data, such as a configuration or software image, with no user intervention other
than having to physically connect the switch to the network. When the switch first boots up, PHC
connects to a redirect server, which redirects to a phone home server to obtain the configuration or
software image.
To initiate either DHCP-options-based ZTP or PHC, the switch must be in a factory-default state, or
you can issue the request system zeroize command.
44
[See Understanding the Phone-Home Client
ZTP with DHCPv6 client support (EX3400, EX4300, PTX1000, PTX5000, PTX10002-60C, PTX10008,
•
QFX5100, QFX5200, QFX10002, and QFX10002-60C)—Starting in Junos OS Release 20.4R1, zero
touch supports the DHCPv6 client. During the bootstrap process, the device first uses the DHCPv4
client to request for information regarding image and configuration file from the DHCP server. The
device checks the DHCPv4 bindings sequentially. If one of the DHCPv4 bindings fails, the device continues
to check for bindings until provisioning is successful. However, if there are no DHCPv4 bindings, the
device checks for DHCPv6 bindings and follows the same process as for DHCPv4 until the device can
be provisioned successfully. Both DHCPv4 and DHCPv6 clients are included as part of the default
configuration on the device.
The DHCP server uses DHCPv6 options 59 and 17 and applicable suboptions to exchange ZTP-related
information between itself and the DHCP client.
NOTE: ZTP supports only HTTP and HTTPS transport protocols.
[See Zero Touch Provisioning.]
Phone-home client (EX4300-48MP Virtual Chassis)—Starting in Junos OS Release 20.4R1, the
•
phone-home client (PHC) can securely provision a Virtual Chassis consisting of all EX4300-48MP member
switches without requiring user interaction. If the switches all have the factory-default configuration,
you just need to:
Connect the switches using the Virtual Chassis ports.
•
Connect any network port or the management port to the network.
•
Page 47

Power on the Virtual Chassis.
•
The PHC automatically starts up and connects to the phone-home server (PHS), which responds with
bootstrapping information. The PHC then upgrades each member with the new image and applies the
configuration, and the Virtual Chassis is ready to go.
[See Provision a Virtual Chassis Using the Phone-Home Client.]
Subscriber Management and Services
Control plane DDoS protection against DDoS attacks (EX9200 with MPC10E)—Starting in Junos OS
•
Release 20.4R1, control plane distributed denial of service (DDoS) protection is enabled by default on
EX9200 switches with MPC10E line cards. To prevent malicious traffic from interfering with device
operations, this feature uses firewall filters and policers to discard or rate-limit control plane traffic. You
can disable this feature at different levels or change the default policer parameters for many protocol
groups and individual packet types in the supported protocol groups.
[See Control Plane Distributed Denial-of-Service (DDoS) Protection Overview.]
45
SEE ALSO
What's Changed | 45
Known Limitations | 48
Open Issues | 49
Resolved Issues | 52
Documentation Updates | 55
Migration, Upgrade, and Downgrade Instructions | 56
What's Changed
IN THIS SECTION
MPLS | 47
Network Management and Monitoring | 47
Platform and Infrastructure | 47
User Interface and Configuration | 47
Page 48

Learn about what changed in this release for EX Series Switches in Junos OS Release 20.4R1.
46
Page 49

MPLS
The show mpls lsp extensivel and show mpls lsp detail commands display next hop gateway LSPid—When
•
you use the show mpls lsp extensivel and show mpls lsp detail commands, you'll see next hop gateway
LSPid in the output as well.
Network Management and Monitoring
Warning changed for configuration statements that correspond to deviate not-supported nodes in
•
YANG data models (ACX Series, EX Series, MX Series, PTX Series, QFX Series, and SRX Series)—If you
configure a statement corresponding to a YANG data model node that defines the deviate not-supported
statement, the Junos OS configuration annotates that statement with the comment Warning: statement
ignored: unsupported platform. In earlier releases, the warning is Warning: 'statement' is deprecated.
Platform and Infrastructure
47
Support for unicast ARP request on table entry expiration—You can configure the device to send a
•
unicast ARP request instead of the default broadcast request when an ARP table entry is about to expire.
The retry requests are unicast at intervals of 5 seconds. Without this option, the retry requests are
broadcast at intervals of 800 milliseconds. This behavior reduces ARP overall broadcast traffic. It also
supports the use case where access nodes are configured not to forward broadcast ARP requests toward
customer CPEs for security reasons and instead translate ARP broadcasts to unicast requests. To confirm
whether this is configured, you can issue the following command: show configuration system arp | grep
unicast-mode-on-expire.
[See arp.]
User Interface and Configuration
Verbose format option for exporting JSON configuration data (ACX Series, EX Series, MX Series, PTX
•
Series, QFX Series, and SRX Series)—The Junos OS CLI exposes the verbose statement at the edit system
export-format json hierarchy level. The default format for exporting configuration data in JSON changed
from verbose format to ietf format starting in Junos OS Release 16.1R1. You can explicitly specify the
default export format for JSON configuration data by configuring the appropriate statement at the edit
system export-format json hierarchy level. Although the verbose statement is exposed in the Junos OS
CLI as of the current release, you can configure this statement starting in Junos OS Release 16.1R1.
[See export-format.]
SEE ALSO
Page 50

What's New | 39
Known Limitations | 48
Open Issues | 49
Resolved Issues | 52
Documentation Updates | 55
Migration, Upgrade, and Downgrade Instructions | 56
Known Limitations
IN THIS SECTION
EVPN | 48
Platform and Infrastructure | 48
48
Learn about known limitations in this release for EX Series. For the most complete and latest information
about known Junos OS defects, use the Juniper Networks online Junos Problem Report Search application.
EVPN
After a reboot during recovery process, the ESI LAGs come up before the BGP sessions and routes/ARP
•
entries are not synced. PR1487112
Platform and Infrastructure
Junos OS can hang trying to acquire the SMP IPI lock while rebooting when it is running as a VM on
•
Linux and QEMU hypervisor. Device can be recovered using power-cycle of the device. PR1385970
10G Channels shows false up even when peer end is configured with different speed. The LED on the
•
box also shows green. PR1530061
In a qinq configuration, xSTP should not be enabled on interface having ifls with vlan-id-list configured.
•
If xSTP is enabled on such interface, it will only run on ifl whose vlan-id range includes native-vlan-id
configured, and all other ifls of this interface will in discarding state. So, user should not enable xSTP on
these kind of interfaces. Sample configuration which is not allowed: set interfaces ge-0/0/1
flexible-vlan-tagging set interfaces ge-0/0/1 native-vlan-id 3000 set interfaces ge-0/0/1 encapsulation
extended-vlan-bridge set interfaces ge-0/0/1 unit 2000 vlan-id-list 1-200 set interfaces ge-0/0/1 unit
Page 51

2000 input-vlan-map push set interfaces ge-0/0/1 unit 2000 output-vlan-map pop set vlans csvlan1
interface ge-0/0/1.2000 set protocols mstp interface ge-0/0/1. PR1532992
SEE ALSO
What's New | 39
What's Changed | 45
Open Issues | 49
Resolved Issues | 52
Documentation Updates | 55
Migration, Upgrade, and Downgrade Instructions | 56
Open Issues
49
IN THIS SECTION
Infrastructure | 50
Juniper Extension Toolkit (JET) | 50
Platform and Infrastructure | 50
Routing Policy and Firewall Filters | 51
Routing Protocols | 51
User Interface and Configuration | 52
Learn about open issues in Junos OS Release 20.4R1 for EX Series switches. For the most complete and
latest information about known Junos OS defects, use the Juniper Networks online Junos Problem Report
Search application.
Page 52

Infrastructure
On EX Series legacy Switches, fsck is run with '-C' option, which skips the file system corruption check
•
if the partition has been marked clean during the boot 'nand-media' check. Due to this, there have been
multiple instances where the partition has had file system issues even when cleanly shut down. This
change is to enforce fsck during the boot cycle to strengthen the file system check during boot time.
Fixed in releases: 12.3R12-S7, 14.1X53-D46, 15.1R6 HOW TO RECOVER:* The switch will repair the
corruption during the boot cycle when the file system check (fsck) is run.* In the rare instance that the
file system check (fsck) is completed, and there are continued file system corruptions, then the next step
is to do an 'install -format'. This will format the file system and all file system corruptions will be removed,
along with the previous logs and configuration. PR1191072
On EX Series switches except EX4300/EX4600/EX9200, an interface is configured for single VLAN or
•
multiple VLANs, if all these VLANs of this interface have IGMP snooping enabled, then this interface
will drop HSRPv2 (Hot Standby Router Protocol for IPv6) packets. But if some VLANs do not have IGMP
snooping enabled, then this interface works fine. PR1232403
On EX Series switches, If you are configuring a large number of firewall filters on some interfaces, the
•
FPC might crash and generate core files. PR1434927
50
PROTOCOLS:SWITCHING: AI: Unable to Verify jais-7.0R3-THIN.0.tgz in EX4600 box due to space
•
issue. PR1548668
On EX3400 Virtual Chassis, traffic destined to IRB interface would be dropped after mac-persistence-timer
•
was expired. PR1557229
Juniper Extension Toolkit (JET)
gRPC stack uses IPV4 mapped IPV6 address internally, so that gRPC server can work with pure/mapped
•
IPV4/IPV6 addresses. However, a recent change in kernel IPv4/v6 handling causes a problem when a
management IP is configured. Workaround: Changing address to 0.0.0.0 solves the issue set system
services extension-service request-response grpc clear-text address 0.0.0.0. PR1559064
Platform and Infrastructure
On EX, OCX or QFX based platforms using Broadcom chipset, with SFP+ implemented, interface on the
•
platforms might be in active status when TX or RX connector is removed. When this issue happens,
traffic could be dropped. PR1495564
Do not renumber the Virtual Chassis in non consecutive fashion , for SNMP POE MIB walk to work
•
correctly. PR1503985
35 seconds delay is added in reboot time from Junos OS Release 20.2R1 release compared to Release
•
19.4R2. PR1514364
Page 53

The request chassis fpc slot <slot_num> restart command is unsupported in EX series platforms, so
•
avoid using that command. PR1536997
OSPF and OSPF3 adjacency uptime is more than expected after NSSU upgrade and Outage is higher
•
than the expected. PR1551925
Traffic drop is seen after l2 gres switchover with Layer 2 forwarding database. PR1561344
•
Limited images are not supported for EX92XX on this release. PR1561741
•
Client authentication is failing after performing graceful switchover. PR1563431
•
On certain Junos platforms with Dual-REs (platforms capable of installing Junos packages with name
•
format as "junos*install"), BGP replication may fail to start under GRES/NSR setup after a crash on backup
Routing Engine. NSR starts un-replicating the socket since backup Routing Engine is no longer present.
Massive unreplicated request leads to memory buffer getting full with multiple BGP sessions (e.g., 20
BGP peers). Hence BGP unreplicated request returned with an error. Besides, the kernel is left with stale
data. It does not allow the JSR (Juniper Socket Replication, BGP in this case) when backup RE comes up
due to the stale data. BGP-NSR (Nonstop Routing) is broke under the conditions. Traffic outage will be
observed after performing GRES. PR1552603
51
Routing Policy and Firewall Filters
On all Junos OS platforms with "set policy-options rtf-prefix-list" configured, if you upgrade to a specific
•
version, the device might fail to validate its configuration, which eventually causes rpd to crash
unexpectedly due to a software fault. PR1538172
Routing Protocols
When l2 and l3 ifls are configured on the same ifd and vport scale is enabled on QFX 5110 and QFX
•
5120 and the l2 ifl is part of a vxlan, then SVP is derived from source_trunk_map table. In this case, the
packet will not match with the SOURCE_FIELDS in my_station_tcam table due to which the entry is not
getting hit. OSPF unicast pkts will be dropped due to this and it will be stuck in ExStart State. PR1519244
On Trio based Virtual Chassis (VC) platform, when there are multicast tunneled packets being received,
•
which come into the Virtual Chassis Ports (VCP) and then pop out of the tunnel, if the VCP ports and
the interfaces where multicast packets enter/leave the router are located on the same Packet Forwarding
Engine (PFE), it might fail in sending multicast traffic to downstream receiver due to this issue. PR1555518
Page 54

User Interface and Configuration
In Junos OS 20.4R1 release, if your switch is not connected to the Internet, then J-Web UI cannot
•
download and install the J-Web application package automatically. PR1563588
SEE ALSO
What's New | 39
What's Changed | 45
Known Limitations | 48
Resolved Issues | 52
Documentation Updates | 55
Migration, Upgrade, and Downgrade Instructions | 56
52
Resolved Issues
IN THIS SECTION
Authentication and Access Control | 53
EVPN | 53
Infrastructure | 53
Layer 2 Features | 53
Network Management and Monitoring | 53
Platform and Infrastructure | 53
Routing Protocols | 54
User Interface and Configuration | 55
Virtual Chassis | 55
This section lists the issues fixed in Junos OS Release 20.4R1 for EX Series switches.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
Page 55

Authentication and Access Control
The dot1x client won't be moved to held state when the authenticated PVLAN is deleted. PR1516341
•
EVPN
Unable to create a new VTEP interface. PR1520078
•
Infrastructure
qmon-sw sensor is not supported in EX3400. PR1506710
•
The IP communication between directly connected interfaces on EX4600 would fail. PR1515689
•
The VC system might get hanged after committing the VSTP configurations. PR1520351
•
OID ifOutDiscards reports zero and sometimes shows valid value. PR1522561
•
53
Firewall policer with discard action might fail on EX4300. PR1532670
•
Errors might be seen when dumping vmcore on EX2300 and EX3400 switches. PR1537696
•
The LLDP neighborship with the VoIP phones can't be established. PR1538482
•
Layer 2 Features
The dcpfe/FPC might crash due to the memory leak during the vlan add/delete operation. PR1505239
•
On the QFX5000 line of switches, traffic imbalance might be observed if hash-params is not configured.
•
PR1514793
The MAC address in the hardware table might become out of synchronization between the primary and
•
member in Virtual Chassis after the MAC flaps. PR1521324
Network Management and Monitoring
EX4300: SNMP OID 1.3.6.1.2.1.25.3.3.1.2.0 (hrProcessorLoad ) always returns 0 irrespective of the real
•
CPU utilization. PR1508364
Platform and Infrastructure
IPv6 neighbor solicitation packets might be dropped in a transit device. PR1493212
•
DHCP Binding is not happening after Graceful switchover. PR1515234
•
LLDP adjacency might fail for non-AE interfaces on EX4300 platform. PR1538401
•
Page 56

uRPF in the Strict mode does not work. PR1417546
•
Virtual Chassis split after network topology changed. PR1427075
•
IRB MAC will not be programmed in hardware when MAC persistence timer expires. PR1484440
•
Authentication session might be terminated if PEAP request is retransmitted by authenticator. PR1494712
•
In some cases, if we have an OSPF session on the IRB over LAG interface with 40-Gigabit Ethernet port
•
as member, the session gets stuck in restart. PR1498903
On the EX4300, EX3400, and EX2300 Virtual Chassis with NSB and xSTP enabled, continuous traffic
•
loss might be observed while performing GRES. PR1500783
The mge interface might still stay up while the far end of its link goes down. PR1502467
•
LLDP is not acquired when native-VLAN-ID and tagged VLAN-ID are the same on a port. PR1504354
•
The output VLAN push might not work. PR1510629
•
Traffic might not flow as per configured policer parameters. PR1512433
•
LACP goes down after performing Routing Engine switchover if MACsec is enabled on the LAG members
•
on EX4300. PR1513319
54
Last commit line in configuration is updated after the configuration backup has been done. PR1513499
•
The 100M SFP-FX is not supported on satellite device in a Junos Fusion setup. PR1514146
•
ARP learning issue might be seen on EX4300-MP platform when configuring Layer 3 gateway interfaces.
•
PR1514729
"dot1x" memory leak is seen. PR1515972
•
The dcpfe (PFE) process might crash due to memory leak. PR1517030
•
MPPE-Send/Recv-key attribute is not extracted correctly by dot1xd. PR1522469
•
"Drops" and "Dropped packets" counters in the output by "show interface extensive" are double counting.
•
PR1525373
EX4300-48MP device might go out of service during a software upgrade operation. PR1526493
•
PoE messages "poe_get_dev_class: Failed to get PD class info" seen on EX2300. PR1536408
•
EX3400, EX2300 : Upgrade failure do to lack of available storage. PR1539293
•
Slaac-Snoopd child process core is observed upon multiple switchovers on Routing Engine. PR1543181
•
EX9200 SF3 Fabric OIR Issues with Junos 23.1R1.8. PR1555727
•
Routing Protocols
The rpd process might report 100 percent CPU usage with the BGP route damping enabled. PR1514635
•
Page 57

Packet loss might be observed while verifying traffic from access to core network for IPv4 and IPv6
•
interfaces. PR1520059
OSPFv3 adjacency should not be established when IPsec authentication is enabled. PR1525870
•
User Interface and Configuration
J-Web does not display the correct Flow-control status on EX Series devices. PR1520246
•
Virtual Chassis
On the EX4650 device, the following error message is observed during booting: kldload: an error occurred
•
while loading the module. PR1527170
SEE ALSO
55
What's New | 39
What's Changed | 45
Known Limitations | 48
Open Issues | 49
Documentation Updates | 55
Migration, Upgrade, and Downgrade Instructions | 56
Documentation Updates
There are no errata or changes in Junos OS Release 20.4R1 documentation for EX Series switches.
SEE ALSO
What's New | 39
What's Changed | 45
Known Limitations | 48
Open Issues | 49
Resolved Issues | 52
Migration, Upgrade, and Downgrade Instructions | 56
Page 58

Migration, Upgrade, and Downgrade Instructions
IN THIS SECTION
Upgrade and Downgrade Support Policy for Junos OS Releases | 56
This section contains the upgrade and downgrade support policy for Junos OS for EX Series switches.
Upgrading or downgrading Junos OS can take several hours, depending on the size and configuration of
the network. For information about software installation and upgrade, see the Installation and Upgrade
Guide.
Upgrade and Downgrade Support Policy for Junos OS Releases
56
Support for upgrades and downgrades that span more than three Junos OS releases at a time is not
provided, except for releases that are designated as Extended End-of-Life (EEOL) releases. EEOL releases
provide direct upgrade and downgrade paths—you can upgrade directly from one EEOL release to the
next EEOL release even though EEOL releases generally occur in increments beyond three releases.
You can upgrade or downgrade to the EEOL release that occurs directly before or after the currently
installed EEOL release, or to two EEOL releases before or after. For example, Junos OS Releases 19.3,
19.4, and 20.1 are EEOL releases. You can upgrade from Junos OS Release 19.3 to Release 19.4 or from
Junos OS Release 19.3 to Release 20.1.
You cannot upgrade directly from a non-EEOL release to a release that is more than three releases ahead
or behind. To upgrade or downgrade from a non-EEOL release to a release more than three releases before
or after, first upgrade to the next EEOL release and then upgrade or downgrade from that EEOL release
to your target release.
For more information about EEOL releases and to review a list of EEOL releases, see
https://support.juniper.net/support/eol/software/junos/.
SEE ALSO
What's New | 39
What's Changed | 45
Known Limitations | 48
Open Issues | 49
Resolved Issues | 52
Page 59

Documentation Updates | 55
Junos OS Release Notes for JRR Series
IN THIS SECTION
What's New | 57
What's Changed | 58
Known Limitations | 59
Open Issues | 60
Resolved Issues | 60
Documentation Updates | 61
57
Migration, Upgrade, and Downgrade Instructions | 61
These release notes accompany Junos OS Release 20.4R1 for the JRR Series. They describe new and
changed features, limitations, and known and resolved problems in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What's New
IN THIS SECTION
Routing Protocols | 58
Learn about new features introduced in Junos OS Release 20.4R1 for JRR Series Route Reflectors.
Page 60

Routing Protocols
Support for BGP Sharding (JRR200)—Starting in Junos OS Release 20.4R1, we support BGP sharding.
•
BGP sharding splits a BGP RIB into several sub RIBs and each sub RIB handles a subset of BGP routes.
Each sub RIB is served by a separate RPD thread to achieve parallel processing. This results in reduced
convergence time and faster performance. BGP sharding is disabled by default.
To enable BGP sharding, configure rib-sharding at the [edit system processes routing bgp] hierarchy
level. Sharding is dependent on the update I/O thread feature. Therefore, you need to enable update
I/O thread when you configure sharding. To enable update I/O, configure update-threading at the [edit
system processes routing bgp] hierarchy level for rib-sharding configuration to pass commit check.
If you configure rib-sharding on a routing engine, RPD will create sharding threads. By default the number
of sharding and update threads created is same as the number of CPU cores on the routing engine.
Optionally, you can specify the number-of-shards and number-of-threads you want to create.
NOTE: BGP sharding is supported for IPv4, IPv6, L3VPN and BGP-LU. All the other RIBs are
processed without sharding.
58
[See rib-sharding and update-threading.]
SEE ALSO
What's Changed | 58
Known Limitations | 59
Open Issues | 60
Resolved Issues | 60
Documentation Updates | 61
Migration, Upgrade, and Downgrade Instructions | 61
What's Changed
There are no changes in behavior and syntax in Junos OS Release 20.4R1 for JRR Series Route Reflectors.
SEE ALSO
Page 61

What's New | 57
Known Limitations | 59
Open Issues | 60
Resolved Issues | 60
Documentation Updates | 61
Migration, Upgrade, and Downgrade Instructions | 61
Known Limitations
IN THIS SECTION
Routing Protocols | 59
59
Learn about known limitations in this release for JRR200 Route Reflectors.
Routing Protocols
These features are not supported in Junos OS 20.4R1 release for BGP Sharding:
•
routing-options validations with rib sharding
•
inet4/6 unicast rib-group along with rib sharding
•
outbound route-filter with bgp sharding.
•
SEE ALSO
What's New | 57
What's Changed | 58
Open Issues | 60
Resolved Issues | 60
Documentation Updates | 61
Migration, Upgrade, and Downgrade Instructions | 61
Page 62

Open Issues
There are no open issues in Junos OS 20.4R1 Release for JRR Series Route Reflectors.
SEE ALSO
What's New | 57
What's Changed | 58
Known Limitations | 59
Resolved Issues | 60
Documentation Updates | 61
Migration, Upgrade, and Downgrade Instructions | 61
60
Resolved Issues
IN THIS SECTION
Resolved Issues: 20.4R1 Release | 60
This section lists the issues fixed in Junos OS Release 20.4R1 for JRR Series routers.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
Resolved Issues: 20.4R1 Release
General Routing
On the JRR200 routers, the firewall filter with non-zero TTL value might cause a commit error. PR1531034
•
tcp_timer_keep logs flood on JRR200. PR1533168
•
Optics info of physical interfaces is not available for JRR200 on Junos OS. PR1537261
•
The CLI "request system power-off" and "request system halt" commands do not work as expected on
•
JRR200. PR1534795
Page 63

SEE ALSO
What's New | 57
What's Changed | 58
Known Limitations | 59
Open Issues | 60
Documentation Updates | 61
Migration, Upgrade, and Downgrade Instructions | 61
Documentation Updates
There are no errata or changes in Junos OS Release 20.4R1 documentation for JRR200 Route Reflectors.
61
SEE ALSO
What's New | 57
What's Changed | 58
Known Limitations | 59
Open Issues | 60
Resolved Issues | 60
Migration, Upgrade, and Downgrade Instructions | 61
Migration, Upgrade, and Downgrade Instructions
IN THIS SECTION
Upgrade and Downgrade Support Policy for Junos OS Releases | 62
This section contains the upgrade and downgrade support policy for Junos OS for the JRR Series Route
Reflector. Upgrading or downgrading Junos OS might take several minutes, depending on the size and
configuration of the network.
Page 64

For information about software installation and upgrade, see the JRR200 Route Reflector Quick Start and
the Installation and Upgrade Guide.
Upgrade and Downgrade Support Policy for Junos OS Releases
Support for upgrades and downgrades that span more than three Junos OS releases at a time is not
provided, except for releases that are designated as Extended End-of-Life (EEOL) releases. EEOL releases
provide direct upgrade and downgrade paths—you can upgrade directly from one EEOL release to the
next EEOL release even though EEOL releases generally occur in increments beyond three releases.
You can upgrade or downgrade to the EEOL release that occurs directly before or after the currently
installed EEOL release, or to two EEOL releases before or after. For example, Junos OS Releases 19.3,
19.4, and 20.1 are EEOL releases. You can upgrade from Junos OS Release 19.3 to Release 19.4 or from
Junos OS Release 19.3 to Release 20.1.
You cannot upgrade directly from a non-EEOL release to a release that is more than three releases ahead
or behind. To upgrade or downgrade from a non-EEOL release to a release more than three releases before
or after, first upgrade to the next EEOL release and then upgrade or downgrade from that EEOL release
to your target release.
62
For more information about EEOL releases and to review a list of EEOL releases, see
https://www.juniper.net/support/eol/junos.html.
SEE ALSO
What's New | 57
What's Changed | 58
Known Limitations | 59
Open Issues | 60
Resolved Issues | 60
Documentation Updates | 61
Page 65

Junos OS Release Notes for Juniper Secure Connect
IN THIS SECTION
What’s New | 63
What's Changed | 63
Known Limitations | 63
Open Issues | 64
Resolved Issues | 64
These release notes accompany Junos OS Release 20.4R1 for Juniper Secure Connect. They describe new
and changed features, limitations, and known and resolved problems in the hardware and software.
63
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What’s New
There are no new features in Junos OS Release 20.4R1 for Juniper Secure Connect.
What's Changed
There are no changes in behavior or syntax for Juniper Secure Connect in Junos OS Release 20.4R1.
Known Limitations
There are no known behavior or limitation for Juniper Secure Connect in Junos OS Release 20.4R1.
Page 66

Open Issues
IN THIS SECTION
Juniper Secure Connect Client | 64
Learn about open issues in this release for Juniper Secure Connect.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
Juniper Secure Connect Client
64
IKE configure mode payload is not pushing secondary DNS and secondary WINS attributes to Xauth
•
module with IKEv1. Hence client is not getting assigned with secondary DNS and secondary WINS with
IKEv1. PR1558831
Resolved Issues
There are no resolved issues for Juniper Secure Connect in Junos OS Release 20.4R1.
Junos OS Release Notes for Junos Fusion for Enterprise
IN THIS SECTION
What’s New | 65
What's Changed | 65
Known Limitations | 66
Open Issues | 66
Resolved Issues | 67
Page 67

Documentation Updates | 68
Migration, Upgrade, and Downgrade Instructions | 68
These release notes accompany Junos OS Release 20.4R1 for the Junos fusion for enterprise. They describe
new and changed features, limitations, and known and resolved problems in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What’s New
There are no new features or enhancements to existing features in Junos OS Release 20.4R1 for Junos
fusion for enterprise.
65
NOTE: For more information about Junos fusion for enterprise, see the Junos Fusion for
Enterprise User Guide.
SEE ALSO
What's Changed | 65
Known Limitations | 66
Open Issues | 66
Resolved Issues | 67
Documentation Updates | 68
Migration, Upgrade, and Downgrade Instructions | 68
What's Changed
There are no changes in behavior of Junos OS features and changes in the syntax of Junos OS statements
and commands in Junos OS Release 20.4R1 for Junos fusion for enterprise.
Page 68

SEE ALSO
What's New | 65
Known Limitations | 66
Open Issues | 66
Resolved Issues | 67
Documentation Updates | 68
Migration, Upgrade, and Downgrade Instructions | 68
Known Limitations
There are no known behaviors, system maximums, and limitations in hardware and software in Junos OS
Release 20.4R1 for Junos fusion for enterprise.
For the most complete and latest information about known Junos OS problems, use the Juniper Networks
online Junos Problem Report Search application.
66
SEE ALSO
What's New | 65
What's Changed | 65
Open Issues | 66
Resolved Issues | 67
Documentation Updates | 68
Migration, Upgrade, and Downgrade Instructions | 68
Open Issues
There are no known issues in hardware and software in Junos OS Release for 20.4R1 Junos fusion for
enterprise.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
SEE ALSO
Page 69

What's New | 65
What's Changed | 65
Known Limitations | 66
Resolved Issues | 67
Documentation Updates | 68
Migration, Upgrade, and Downgrade Instructions | 68
Resolved Issues
IN THIS SECTION
Resolved Issues: Release 20.4R1 | 67
67
Learn which issues were resolved in the Junos OS main and maintenance releases for Junos fusion for
enterprise.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
Resolved Issues: Release 20.4R1
The 100M SFP-FX is not supported on satellite devices in a Junos fusion setup. PR1514146
•
SEE ALSO
What's New | 65
What's Changed | 65
Known Limitations | 66
Open Issues | 66
Documentation Updates | 68
Migration, Upgrade, and Downgrade Instructions | 68
Page 70

Documentation Updates
There are no errata or changes in Junos OS Release 20.4R1 for documentation for Junos fusion for
enterprise.
SEE ALSO
What's New | 65
What's Changed | 65
Known Limitations | 66
Open Issues | 66
Resolved Issues | 67
Migration, Upgrade, and Downgrade Instructions | 68
68
Migration, Upgrade, and Downgrade Instructions
IN THIS SECTION
Basic Procedure for Upgrading Junos OS on an Aggregation Device | 68
Upgrading an Aggregation Device with Redundant Routing Engines | 70
Preparing the Switch for Satellite Device Conversion | 71
Converting a Satellite Device to a Standalone Switch | 72
Upgrade and Downgrade Support Policy for Junos OS Releases | 72
Downgrading Junos OS | 73
This section contains the procedure to upgrade or downgrade Junos OS and satellite software for a Junos
fusion for enterprise. Upgrading or downgrading Junos OS and satellite software might take several hours,
depending on the size and configuration of the Junos fusion for enterprise topology.
Basic Procedure for Upgrading Junos OS on an Aggregation Device
When upgrading or downgrading Junos OS for an aggregation device, always use the junos-install package.
Use other packages (such as the jbundle package) only when so instructed by a Juniper Networks support
Page 71

representative. For information about the contents of the junos-install package and details of the installation
process, see the Installation and Upgrade Guide.
NOTE: Before upgrading, back up the file system and the currently active Junos OS configuration
so that you can recover to a known, stable environment in case the upgrade is unsuccessful.
Issue the following command:
user@host> request system snapshot
The installation process rebuilds the file system and completely reinstalls Junos OS. Configuration
information from the previous software installation is retained, but the contents of log files might
be erased. Stored files on the routing platform, such as configuration templates and shell scripts
(the only exceptions are the juniper.conf and ssh files), might be removed. To preserve the stored
files, copy them to another system before upgrading or downgrading the routing platform. See
the Junos OS Administration Library.
69
To download and install Junos OS:
1. Using a Web browser, navigate to the Download Software URL on the Juniper Networks webpage:
https://www.juniper.net/support/downloads/
2. Log in to the Juniper Networks authentication system using the username (generally your e-mail address)
and password supplied by Juniper Networks representatives.
3. Select By Technology > Junos Platform > Junos fusion to find the software that you want to download.
4. Select the release number (the number of the software version that you want to download) from the
Version drop-down list on the right of the page.
5. Select the Software tab.
6. Select the software package for the release.
7. Review and accept the End User License Agreement.
8. Download the software to a local host.
9. Copy the software to the routing platform or to your internal software distribution site.
10. Install the new junos-install package on the aggregation device.
Page 72

NOTE: We recommend that you upgrade all software packages out of band using the console
because in-band connections are lost during the upgrade process.
Customers in the United States and Canada, use the following commands, where n is the spin number.
user@host> request system software add validate reboot source/package-name.n.tgz
All other customers, use the following commands, where n is the spin number.
user@host> request system software add validate reboot source/package-name.n-limited.tgz
Replace source with one of the following values:
/pathname—For a software package that is installed from a local directory on the router.
•
For software packages that are downloaded and installed from a remote location:
•
70
ftp://hostname/pathname
•
http://hostname/pathname
•
scp://hostname/pathname (available only for Canada and U.S. version)
•
The validate option validates the software package against the current configuration as a prerequisite
to adding the software package to ensure that the router reboots successfully. This is the default
behavior when the software package being added is a different release.
Adding the reboot command reboots the router after the upgrade is validated and installed. When the
reboot is complete, the router displays the login prompt. The loading process might take 5 to 10 minutes.
Rebooting occurs only if the upgrade is successful.
Upgrading an Aggregation Device with Redundant Routing Engines
If the aggregation device has two Routing Engines, perform a Junos OS installation on each Routing Engine
separately to minimize disrupting network operations as follows:
1. Disable graceful Routing Engine switchover (GRES) on the master Routing Engine and save the
configuration change to both Routing Engines.
2. Install the new Junos OS release on the backup Routing Engine while keeping the currently running
software version on the master Routing Engine.
Page 73

3. After making sure that the new software version is running correctly on the backup Routing Engine,
switch over to the backup Routing Engine to activate the new software.
4. Install the new software on the original master Routing Engine that is now active as the backup Routing
Engine.
For the detailed procedure, see the Installation and Upgrade Guide.
Preparing the Switch for Satellite Device Conversion
There are multiple methods to upgrade or downgrade satellite software in your Junos fusion for enterprise.
See Configuring or Expanding a Junos fusion for enterprise.
For satellite device hardware and software requirements, see Understanding Junos fusion for enterprise
Software and Hardware Requirements.
Use the following command to install Junos OS on a switch before converting it into a satellite device:
user@host> request system software add validate reboot source/package-name
71
NOTE: The following conditions must be met before a Junos switch that is running Junos OS
Release 14.1X53-D43 can be converted to a satellite device when the action is initiated from
the aggregation device:
The switch running Junos OS can be converted only to SNOS 3.1 and later.
•
Either the switch must be set to factory-default configuration by using the request system
•
zeroize command, or the following command must be included in the configuration: set chassis
auto-satellite-conversion.
When the interim installation has completed and the switch is running a version of Junos OS that is
compatible with satellite device conversion, perform the following steps:
1. Log in to the device using the console port.
2. Clear the device:
[edit]
user@satellite-device# request system zeroize
NOTE: The device reboots to complete the procedure for resetting the device.
Page 74

If you are not logged in to the device using the console port connection, your connection to the device
is lost after you enter the request system zeroize command.
If you lose connection to the device, log in using the console port.
3. (EX4300 switches only) After the reboot is complete, convert the built-in 40-Gbps QSFP+ interfaces
from Virtual Chassis ports (VCPs) into network ports:
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port port-number
For example, to convert all four built-in 40-Gbps QSFP+ interfaces on an EX4300-24P switch into
network ports:
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 0
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 1
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 2
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 3
72
This step is required for the 40-Gbps QSFP+ interfaces that will be used as uplink interfaces in a Junos
fusion topology. Built-in 40-Gbps QSFP+ interfaces on EX4300 switches are configured into VCPs by
default, and the default settings are restored after the device is reset.
After this initial preparation, you can use one of three methods to convert your switches into satellite
devices—autoconversion, manual conversion, or preconfiguration. See Configuring or Expanding a Junos
fusion for enterprise for detailed configuration steps for each method.
Converting a Satellite Device to a Standalone Switch
If you need to convert a satellite device to a standalone device, you must install a new Junos OS software
package on the satellite device and remove it from the Junos fusion topology. For more information, see
Converting a Satellite Device to a Standalone Device.
Upgrade and Downgrade Support Policy for Junos OS Releases
Support for upgrades and downgrades that span more than three Junos OS releases at a time is not
provided, except for releases that are designated as Extended End-of-Life (EEOL) releases. EEOL releases
provide direct upgrade and downgrade paths—you can upgrade directly from one EEOL release to the
next EEOL release even though EEOL releases generally occur in increments beyond three releases.
You can upgrade or downgrade to the EEOL release that occurs directly before or after the currently
installed EEOL release, or to two EEOL releases before or after. For example, Junos OS Releases 19.3,
19.4, and 20.1 are EEOL releases. You can upgrade from Junos OS Release 19.3 to Release 19.4 or from
Junos OS Release 19.3 to Release 20.1.
Page 75

You cannot upgrade directly from a non-EEOL release to a release that is more than three releases ahead
or behind. To upgrade or downgrade from a non-EEOL release to a release more than three releases before
or after, first upgrade to the next EEOL release and then upgrade or downgrade from that EEOL release
to your target release.
For more information about EEOL releases and to review a list of EEOL releases, see
https://www.juniper.net/support/eol/junos.html
Downgrading Junos OS
Junos fusion for enterprise is first supported in Junos OS Release 16.1, although you can downgrade a
standalone EX9200 switch to earlier Junos OS releases.
NOTE: You cannot downgrade more than three releases.
For more information, see the Installation and Upgrade Guide.
73
To downgrade a Junos fusion for enterprise, follow the procedure for upgrading, but replace the junos-install
package with one that corresponds to the appropriate release.
SEE ALSO
What's New | 65
What's Changed | 65
Known Limitations | 66
Open Issues | 66
Resolved Issues | 67
Documentation Updates | 68
Page 76

Junos OS Release Notes for Junos Fusion for Provider Edge
IN THIS SECTION
What's New | 74
What's Changed | 75
Known Limitations | 76
Open Issues | 76
Resolved Issues | 77
Documentation Updates | 77
Migration, Upgrade, and Downgrade Instructions | 78
74
These release notes accompany Junos OS Release 20.4R1 for Junos fusion for provider edge. They describe
new and changed features, limitations, and known and resolved problems in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What's New
IN THIS SECTION
Hardware | 75
Learn about new features introduced in this release for Junos fusion for provider edge.
Page 77

Hardware
Support for QFX5110 as a satellite device in a Junos fusion for provider edge environment on a GNF
•
(MX480, MX960, MX2010, and MX2020)—With Junos node slicing, you can create guest network
functions (GNFs), which are partitions where an aggregation device can be configured. The aggregation
device on a GNF supports a maximum of 10 satellite devices. Starting in Junos OS Release 20.4R1, you
can configure QFX5110 switches as satellite devices in a Junos fusion for provider edge environment
on a GNF.
[See Understanding Junos Fusion Provider Edge Software and Hardware Requirements and Junos Node
Slicing Overview.]
SEE ALSO
What's Changed | 75
Known Limitations | 76
75
Open Issues | 76
Resolved Issues | 77
Documentation Updates | 77
Migration, Upgrade, and Downgrade Instructions | 78
What's Changed
There are no changes in the behavior of Junos OS features or in the syntax of Junos OS statements and
commands in this release for Junos fusion for provider edge.
SEE ALSO
What's New | 74
Known Limitations | 76
Open Issues | 76
Resolved Issues | 77
Documentation Updates | 77
Migration, Upgrade, and Downgrade Instructions | 78
Page 78

Known Limitations
There are no known behaviors, system maximums, and limitations in hardware and software in Junos OS
Release 20.4R1 for Junos fusion for provider edge.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
SEE ALSO
What's New | 74
What's Changed | 75
Open Issues | 76
Resolved Issues | 77
Documentation Updates | 77
76
Migration, Upgrade, and Downgrade Instructions | 78
Open Issues
There are no open issues in the Junos OS Release 20.4R1 for Junos fusion for provider edge.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
SEE ALSO
What's New | 74
What's Changed | 75
Known Limitations | 76
Resolved Issues | 77
Documentation Updates | 77
Migration, Upgrade, and Downgrade Instructions | 78
Page 79

Resolved Issues
There are no fixed issues in the Junos OS Release 20.4R1 for Junos fusion for provider edge.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
SEE ALSO
What's New | 74
What's Changed | 75
Known Limitations | 76
Open Issues | 76
Documentation Updates | 77
Migration, Upgrade, and Downgrade Instructions | 78
77
Documentation Updates
There are no errata or changes in Junos OS Release 20.4R1 documentation for Junos fusion for provider
edge.
SEE ALSO
What's New | 74
What's Changed | 75
Known Limitations | 76
Open Issues | 76
Resolved Issues | 77
Migration, Upgrade, and Downgrade Instructions | 78
Page 80

Migration, Upgrade, and Downgrade Instructions
IN THIS SECTION
Basic Procedure for Upgrading an Aggregation Device | 78
Upgrading an Aggregation Device with Redundant Routing Engines | 81
Preparing the Switch for Satellite Device Conversion | 81
Converting a Satellite Device to a Standalone Device | 83
Upgrading an Aggregation Device | 85
Upgrade and Downgrade Support Policy for Junos OS Releases | 85
Downgrading from Junos OS Release 20.1 | 86
78
This section contains the procedure to upgrade Junos OS, and the upgrade and downgrade policies for
Junos OS for Junos fusion for provider edge. Upgrading or downgrading Junos OS might take several
hours, depending on the size and configuration of the network.
Basic Procedure for Upgrading an Aggregation Device
When upgrading or downgrading Junos OS, always use the jinstall package. Use other packages (such as
the jbundle package) only when so instructed by a Juniper Networks support representative. For information
about the contents of the jinstall package and details of the installation process, see the Installation and
Upgrade Guide.
NOTE: Before upgrading, back up the file system and the currently active Junos OS configuration
so that you can recover to a known, stable environment in case the upgrade is unsuccessful.
Issue the following command:
user@host> request system snapshot
The installation process rebuilds the file system and completely reinstalls Junos OS. Configuration
information from the previous software installation is retained, but the contents of log files might
be erased. Stored files on the routing platform, such as configuration templates and shell scripts
(the only exceptions are the juniper.conf and ssh files), might be removed. To preserve the stored
files, copy them to another system before upgrading or downgrading the routing platform. See
the Installation and Upgrade Guide.
Page 81
The download and installation process for Junos OS Release 20.4R1 is different from that for earlier Junos
OS releases.
1. Using a Web browser, navigate to the Download Software URL on the Juniper Networks webpage:
https://www.juniper.net/support/downloads/
2. Log in to the Juniper Networks authentication system by using the username (generally your e-mail
address) and password supplied by Juniper Networks representatives.
3. Select By Technology > Junos Platform > Junos fusion to find the software that you want to download.
4. Select the release number (the number of the software version that you want to download) from the
Version drop-down list to the right of the page.
5. Select the Software tab.
79
6. Select the software package for the release.
7. Review and accept the End User License Agreement.
8. Download the software to a local host.
9. Copy the software to the routing platform or to your internal software distribution site.
10. Install the new jinstall package on the aggregation device.
NOTE: We recommend that you upgrade all software packages out-of-band using the console,
because in-band connections are lost during the upgrade process.
Customers in the United States and Canada, use the following commands.
For 64-bit software:
•
NOTE: We recommend that you use 64-bit Junos OS software when implementing Junos
fusion for provider edge.
user@host> request system software add validate reboot
source/jinstall64-20.4R1.SPIN-domestic-signed.tgz
Page 82

For 32-bit software:
•
user@host> request system software add validate reboot
source/jinstall-20.4R1.SPIN-domestic-signed.tgz
All other customers, use the following commands.
For 64-bit software:
•
NOTE: We recommend that you use 64-bit Junos OS software when implementing Junos
fusion for provider edge.
user@host> request system software add validate reboot
source/jinstall64-20.4R1.SPIN-export-signed.tgz
For 32-bit software:
•
80
user@host> request system software add validate reboot
source/jinstall-20.4R1.SPIN-export-signed.tgz
Replace source with one of the following values:
/pathname—For a software package that is installed from a local directory on the router.
•
For software packages that are downloaded and installed from a remote location:
•
ftp://hostname/pathname
•
http://hostname/pathname
•
scp://hostname/pathname (available only for the Canada and U.S. version)
•
The validate option validates the software package against the current configuration as a prerequisite
for adding the software package to ensure that the router reboots successfully. This is the default
behavior when the software package being added is for a different release.
Adding the reboot command reboots the router after the upgrade is validated and installed. When the
reboot is complete, the router displays the login prompt. The loading process might take 5 to 10 minutes.
Rebooting occurs only if the upgrade is successful.
Page 83

NOTE: After you install a Junos OS Release 20.4R1 jinstall package, you cannot return to the
previously installed software by issuing the request system software rollback command. Instead,
you must issue the request system software add validate command and specify the jinstall
package that corresponds to the previously installed software.
Upgrading an Aggregation Device with Redundant Routing Engines
If the aggregation device has two Routing Engines, perform a Junos OS installation on each Routing Engine
separately as follows to minimize disrupting network operations:
1. Disable graceful Routing Engine switchover (GRES) on the master Routing Engine and save the
configuration change to both Routing Engines.
2. Install the new Junos OS release on the backup Routing Engine while keeping the currently running
software version on the master Routing Engine.
81
3. After making sure that the new software version is running correctly on the backup Routing Engine,
switch over to the backup Routing Engine to activate the new software.
4. Install the new software on the original master Routing Engine that is now active as the backup Routing
Engine.
For the detailed procedure, see the Installation and Upgrade Guide.
Preparing the Switch for Satellite Device Conversion
Satellite devices in a Junos fusion topology use a satellite software package that is different from the
standard Junos OS software package. Before you can install the satellite software package on a satellite
device, you first need to upgrade the target satellite device to an interim Junos OS software version that
can be converted to satellite software. For satellite device hardware and software requirements, see
Understanding Junos fusion Software and Hardware Requirements
NOTE: The following conditions must be met before a standalone switch that is running Junos
OS Release 14.1X53-D43 can be converted to a satellite device when the action is initiated from
the aggregation device:
The switch can be converted to only SNOS 3.1 and later.
•
Either the switch must be set to factory-default configuration by using the request system
•
zeroize command, or the following command must be included in the configuration: set chassis
auto-satellite-conversion.
Page 84

Customers with EX4300 switches, use the following command:
user@host> request system software add validate reboot
source/jinstall-ex-4300-14.1X53-D43.3-domestic-signed.tgz
Customers with QFX5100 switches, use the following command:
user@host> request system software add reboot
source/jinstall-qfx-5-14.1X53-D43.3-domestic-signed.tgz
When the interim installation has completed and the switch is running a version of Junos and OS on one
line that is compatible with satellite device conversion, perform the following steps:
1. Log in to the device by using the console port.
2. Clear the device:
82
[edit]
user@satellite-device# request system zeroize
NOTE: The device reboots to complete the procedure for resetting the device.
If you are not logged in to the device by using the console port connection, your connection to the
device is lost after you enter the request system zeroize command.
If you lose your connection to the device, log in using the console port.
3. (EX4300 switches only) After the reboot is complete, convert the built-in 40-Gbps QSFP+ interfaces
from Virtual Chassis ports (VCPs) into network ports:
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port port-number
For example, to convert all four built-in 40-Gbps QSFP+ interfaces on an EX4300-24P switch into
network ports:
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 0
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 1
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 2
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 3
Page 85

This step is required for the 40-Gbps QSFP+ interfaces that will be used as uplink interfaces in a Junos
fusion topology. Built-in 40-Gbps QSFP+ interfaces on EX4300 switches are configured into VCPs by
default, and the default settings are restored after the device is reset.
After this initial preparation, you can use one of three methods to convert your switches into satellite
devices—autoconversion, manual conversion, and preconfiguration. See Configuring Junos fusion for
provider edge for detailed configuration steps for each method.
Converting a Satellite Device to a Standalone Device
If you need to convert a satellite device to a standalone device, you must install a new Junos OS software
package on the satellite device and remove the satellite device from the Junos fusion topology.
NOTE: If the satellite device is a QFX5100 switch, you need to install a PXE version of Junos
OS. The PXE version of Junos OS is software that includes pxe in the Junos OS package name
when it is downloaded from the Software Center—for example, the PXE image for Junos OS
Release 14.1X53-D43 is named install-media-pxe-qfx-5-14.1X53-D43.3-signed.tgz . If the
satellite device is an EX4300 switch, you install a standard jinstall-ex-4300 version of Junos OS.
83
The following steps explain how to download software, remove the satellite device from Junos fusion, and
install the Junos OS software image on the satellite device so that the device can operate as a standalone
device.
1. Using a Web browser, navigate to the Junos OS software download URL on the Juniper Networks
webpage:
https://www.juniper.net/support/downloads
2. Log in to the Juniper Networks authentication system by using the username (generally your e-mail
address) and password supplied by Juniper Networks representatives.
3. Select By Technology > Junos Platform > Junos fusion from the drop-down list and select the switch
platform series and model for your satellite device.
4. Select the Junos OS Release 14.1X53-D30 software image for your platform.
5. Review and accept the End User License Agreement.
6. Download the software to a local host.
7. Copy the software to the routing platform or to your internal software distribution site.
Page 86

8. Remove the satellite device from the automatic satellite conversion configuration.
If automatic satellite conversion is enabled for the satellite device’s member number, remove the
member number from the automatic satellite conversion configuration. The satellite device’s member
number is the same as the FPC slot ID.
[edit]
user@aggregation-device# delete chassis satellite-management auto-satellite-conversion
satellite member-number
For example, to remove member number 101 from Junos fusion:
[edit]
user@aggregation-device# delete chassis satellite-management auto-satellite-conversion
satellite 101
You can check the automatic satellite conversion configuration by entering the show command at the
[edit chassis satellite-management auto-satellite-conversion] hierarchy level.
84
9. Commit the configuration.
To commit the configuration to both Routing Engines:
[edit]
user@aggregation-device# commit synchronize
Otherwise, commit the configuration to a single Routing Engine:
[edit]
user@aggregation-device# commit
10. Install the Junos OS software on the satellite device to convert the device to a standalone device.
[edit]
user@aggregation-device> request chassis satellite install URL-to-software-package fpc-slot
member-number
For example, to install a PXE software package stored in the /var/tmp directory on the aggregation
device onto a QFX5100 switch acting as the satellite device using FPC slot 101:
[edit]
user@aggregation-device> request chassis satellite install
/var/tmp/install-media-pxe-qfx-5-14.1X53-D43.3-signed.tgz fpc-slot 101
For example, to install a software package stored in the var/tmp directory on the aggregation device
onto an EX4300 switch acting as the satellite device using FPC slot 101:
Page 87

[edit]
user@aggregation-device> request chassis satellite install
/var/tmp/jinstall-ex-4300-14.1X53-D30.3-domestic-signed.tgz fpc-slot 101
The satellite device stops participating in the Junos fusion topology after the software installation starts.
The software upgrade starts after this command is entered.
11. Wait for the reboot that accompanies the software installation to complete.
12. When you are prompted to log back into your device, uncable the device from the Junos fusion topology.
See Removing a Transceiver from a QFX Series Device or Remove a Transceiver, as needed. Your device
has been removed from Junos fusion.
NOTE: The device uses a factory-default configuration after the Junos OS installation is
complete.
85
Upgrading an Aggregation Device
When you upgrade an aggregation device to Junos OS Release 20.4R1, you must also upgrade your satellite
device to Satellite Device Software version 3.1R1.
Upgrade and Downgrade Support Policy for Junos OS Releases
Support for upgrades and downgrades that span more than three Junos OS releases at a time is not
provided, except for releases that are designated as Extended End-of-Life (EEOL) releases. EEOL releases
provide direct upgrade and downgrade paths—you can upgrade directly from one EEOL release to the
next EEOL release even though EEOL releases generally occur in increments beyond three releases.
You can upgrade or downgrade to the EEOL release that occurs directly before or after the currently
installed EEOL release, or to two EEOL releases before or after. For example, Junos OS Releases 19.3,
19.4, and 20.1 are EEOL releases. You can upgrade from Junos OS Release 19.3 to Release 19.4 or from
Junos OS Release 19.3 to Release 20.1.
You cannot upgrade directly from a non-EEOL release to a release that is more than three releases ahead
or behind. To upgrade or downgrade from a non-EEOL release to a release more than three releases before
or after, first upgrade to the next EEOL release and then upgrade or downgrade from that EEOL release
to your target release.
For more information about EEOL releases and to review a list of EEOL releases, see
https://www.juniper.net/support/eol/junos.html.
Page 88

Downgrading from Junos OS Release 20.1
To downgrade from Release 20.1 to another supported release, follow the procedure for upgrading, but
replace the 20.1 jinstall package with one that corresponds to the appropriate release.
NOTE: You cannot downgrade more than three releases.
For more information, see the Installation and Upgrade Guide.
SEE ALSO
What's New | 74
What's Changed | 75
Known Limitations | 76
86
Open Issues | 76
Resolved Issues | 77
Documentation Updates | 77
Junos OS Release Notes for MX Series
IN THIS SECTION
What's New | 87
What's Changed | 103
Known Limitations | 109
Open Issues | 110
Resolved Issues | 117
Documentation Updates | 132
Migration, Upgrade, and Downgrade Instructions | 132
Page 89

These release notes accompany Junos OS Release 20.4R1 for the MX Series 5G Universal Routing Platforms.
They describe new and changed features, limitations, and known and resolved problems in the hardware
and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What's New
IN THIS SECTION
Hardware | 88
EVPN | 90
High Availability (HA) and Resiliency | 91
87
Interfaces and Chassis | 92
Juniper Extension Toolkit (JET) | 92
Junos OS, XML, API, and Scripting | 93
Junos Telemetry Interface | 93
MPLS | 95
Network Management and Monitoring | 96
Routing Policy and Firewall Filters | 97
Routing Protocols | 97
Services Applications | 99
Software Defined Networking | 99
Software Installation and Upgrade | 101
Software Licensing | 101
Subscriber Management and Services | 101
System Management | 102
System Logging | 103
This section describes the new features and enhancements to existing features in Junos OS Release 20.4R1
for the MX Series routers.
Page 90
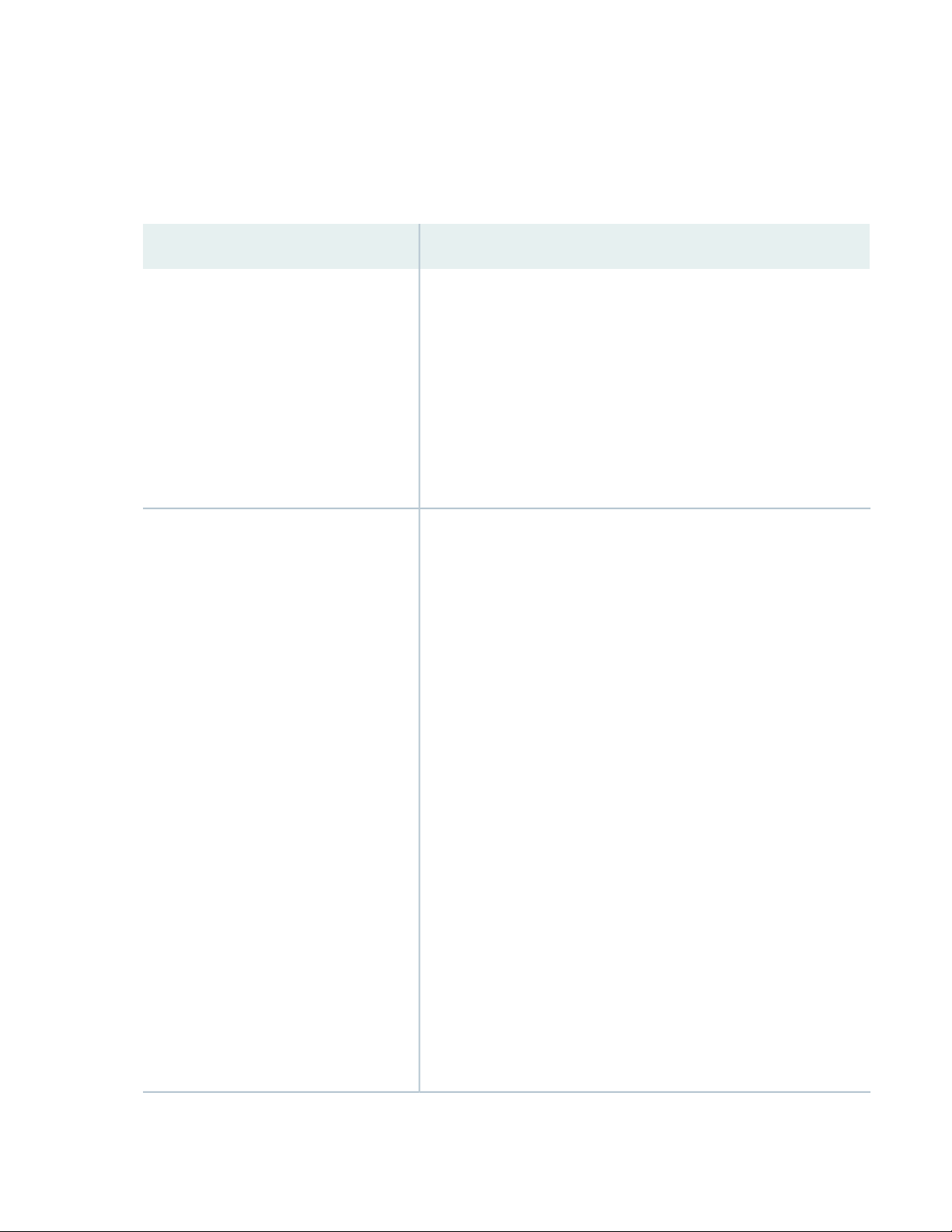
Hardware
•
We've added the following features to the MX Series routers in Junos OS Release 20.4R1.
Table 2: Features Supported by MPC10E and MPC11E Line Cards on MX Series Routers
DescriptionFeature
88
EVPN
Interfaces and chassis
Support for configuring an Ethernet VPN Ethernet Tree (E-Tree) service
•
on MX240, MX480, and MX960 routers using MPC10E-15C-MRATE
line cards. [See EVPN-ETREE Overview.]
Support for configuring an EVPN point-to multipoint (P2MP) label
•
switch path (LSP) as a provider tunnel on a bud router. The bud router
functions both as an egress router and a transit router. [See Configuring
Bud Node Support.]
Support for configuring and signalling a P2MP LSP for the EVPN
•
Inclusive Provider Tunnel for BUM traffic. [See Understanding P2MPs
LSP for the EVPN Inclusive Provider Tunnel.]
Support for configuring VLAN rewrite operations on CCC interfaces.
•
[See Stacking and Rewriting Gigabit Ethernet VLAN Tags Overview
and Stacking and Rewriting Gigabit Ethernet VLAN Tags.]
Support for 100GE AOC optics on MPC10E-15C-MRATE and
•
MPC10E-10C-MRATE (with SCBE3-MX) in the MX240, MX480, and
MX960 routers. [See Hardware Compatibility Tool.]
Support for 4X100G FR transceivers and the channelization option
•
on the 400G-DR4 transceiver on MPC10E-15C-MRATE and
MPC10E-10C-MRATE (with SCBE3) in the MX240, MX480, and
MX960 routers. [See Hardware Compatibility Tool.]
Support for configuring dynamic learning of the source and destination
•
MAC addresses on aggregated Ethernet interfaces on the
MPC10E-15C-MRATE, MPC10E-10C-MRATE, and MX2K-MPC11E
line cards. [See MAC Address Accounting for Dynamically Learned
Addresses.]
Support for monitoring link degradation of the 25GbE interfaces and
•
400GbE interfaces on the MPC10E (MPC10E-15C-MRATE and
MPC10E-10C-MRATE) line cards. [See Link Degrade Monitoring
Overview.]
Support for Layer 2 address learning process (ALD). [See Understanding
•
Layer 2 Learning and Forwarding.]
Support for a bandwidth of 500 Gbps per Packet Forwarding Engine
•
with four fabric planes on MPC10E-10C-MRATE and
MPC10E-15C-MRATE (with the Packet Forwarding Engine 2 powered
off) line cards. [See MPC10E-10C-MRATE and MPC10E-15C-MRATE.]
Page 91

Table 2: Features Supported by MPC10E and MPC11E Line Cards on MX Series Routers (continued)
DescriptionFeature
89
General routing
Layer 2 features
Support for configuring the TCP maximum segment size (MSS). [See
•
Configure TCP Options.]
Support for configuring the GRE key to identify the traffic flows in a
•
GRE tunnel on the MPC10E-10C-MRATE, MPC10E-15C-MRATE, and
MX2K-MPC11E line cards. [See dynamic-tunnel-gre-key.]
Support for packet mirroring with Layer 2 headers for Layer 3
•
forwarded traffic. [See Firewall Filter Nonterminating Actions.]
Support for Layer2 Ethernet services over GRE tunnel interfaces. [See
•
Configuring Layer 2 Ethernet Services over GRE Tunnel Interfaces.]
Support for Spanning-Tree Protocol (STP), Rapid Spanning-Tree
•
Protocol (RSTP), Multiple Spanning-Tree Protocol (MSTP), and VLAN
Spanning-Tree Protocol (VSTP). [See Configuring STP Protocol.]
Support for the base bridging feature commands.
•
NOTE: You can configure propagate option under the mac-flush
command.
[See clear bridge mac-table, global-mac-move, global-no-mac-learning,
mac-flush, global-no-control-mac-aging, and global-no-hw-mac-learning
.]
Multicast
Network management and monitoring
Support for redundant virtual tunnels (RVTs) and fast re-route (FRR)
•
for both active/backup and active/active redundancy models (MX240,
MX480, MX960, MX2010, and MX2020). RVT interfaces are used in
Multicast Layer 3 VPNs (MVPN) to facilitate virtual routing and
forwarding (VRF) table lookup based on MPLS labels and to provide
resiliency. [See Resiliency in Multicast L3 VPNs with Redundant Virtual
Tunnels.]
Support for verifying the global table multicast (GTM) with IPv6 and
•
Type-7 on MPC10 and MPC11 line cards. [See Multicast Overview.]
Support for configuring ITU-T Y.1731 standard-compliant Ethernet
•
synthetic loss measurement (ETH-SLM) and Ethernet delay
measurement (ETH- DM) capabilities on MPC10E-10C-MRATE,
MPC10E-15C-MRATE, and MX2K-MPC11E line cards. [See ITU-T
Y.1731 Ethernet Service OAM Overview.]
Page 92

Table 2: Features Supported by MPC10E and MPC11E Line Cards on MX Series Routers (continued)
DescriptionFeature
90
Services Applications
Support for QSFP-100G-FR, QSFP-100G-DR, and QSFP-100G-LR transceivers (MX2010 and MX2020
•
Support for inline monitoring services to provide the flexibility to
•
monitor different streams of traffic at different sampling rates on the
same interface. [See Inline Monitoring Services Configuration.]
Support for Aggregated Multiservices Interfaces (AMS) on the
•
MPC10E-10C-MRATE, MPC10E-15C-MRATE, and MX2K-MPC11E
line cards to provide load balancing (LB) and high availability (HA)
features for stateful firewall and NAT services. You can configure AMS
with next-hop style service-sets and with MS-MPC or MS-MIC only.
[See Understanding Aggregated Multiservices Interfaces.]
with MX2K-MPC11E)—Starting in Junos OS Release 20.4R1, the MX2K-MPC11E MPCs in the MX2010
and MX2020 routers support the QSFP-100G-FR, QSFP-100G-DR, and QSFP-100G-LR transceivers.
[See the Hardware Compatibility Tool (HCT) for details.]
EVPN
MAC VRF with EVPN-VXLAN (MX Series and vMX routers; QFX5100, QFX5110, QFX5120, QFX5200,
•
QFX10002, QFX10008, and QFX10016 switches)—Data center service providers must support multiple
customers with their own routing and bridging policies in the same physical network. To accommodate
this requirement, you can now configure multiple customer-specific EVPN instances (EVIs) of type
mac-vrf, each of which can support a different EVPN service type. This configuration results in
customer-specific virtual routing and forwarding (VRF) tables with MAC addresses on each Juniper
Networks device that serves as a virtual tunnel endpoint (VTEP) in the EVPN-VXLAN network.
NOTE: We support MAC VRF routing instances for EVPN unicast routes only.
To support this feature, we introduce a uniform routing instance configuration, which complies with
RFC 7432, BGP MPLS-Based Ethernet VPN. The uniform configuration eliminates hardware restrictions
that limit the number of EVIs and combinations of EVIs with their respective policies that can
simultaneously exist. The common configuration includes the following new CLI elements:
The mac-vrf keyword at the [edit routing-instances name instance-type] hierarchy level.
•
The service-type configuration statement at the [edit routing-instances name] hierarchy level. We
•
support VLAN-based, VLAN-aware, and VLAN-bundle service types.
(QFX10000 line of switches only) The forwarding-instance configuration statement at the [edit
•
routing-instances name] hierarchy level. With this optional configuration statement, you can map
Page 93

multiple routing instances to a single forwarding instance. If you don’t include this configuration
statement, the default forwarding instance is used.
We continue to support the existing method of routing instance configuration along with the new uniform
routing instance configuration.
[See EVPN User Guide.]
MC-LAG emulation in an EVPN deployment (EX-Series, MX-Series, and vMX)—Starting in Junos OS
•
Release 20.4R1, you can emulate the function of an MC-LAG in active-standby mode in an EVPN
configuration without having to configure an ICCP or ICL interface. In a standard EVPN configuration,
logical interfaces configured on an aggregated Ethernet interface can have different designated forwarder
election roles. To emulate an MC-LAG configuration, the designated forwarder (DF) takes on the role
of the aggregated Ethernet interface. The provider edge (PE) that is the non-DF will send LACP out-of-sync
packets to the CE. This will cause LACP to go down on the CE device, and the CE device will not use
the links connected to the non-DF for sending traffic. If the connection between a CE and a DF PE fails,
the PE is re-elected as a DF. If the connection between a CE and a non-DF PE fails, the current DF PE
is not changed.
91
To achieve this functionality, configure the lacp-oos-on-ndf statement at the [edit interfaces interface
name esi df-election-granularity per-esi] hierarchy.
Support for EVPN E-Tree service (MX240, MX480, and MX960)—Starting in Junos OS 20.4R1, on
•
MX240, MX480, and MX960 routers using MPC10E-15C-MRATE line cards you can configure an
Ethernet VPN Ethernet-Tree (E-Tree) service.
[See EVPN-ETREE Overview.]
High Availability (HA) and Resiliency
Support for pause and resume options with unified ISSU (MX Series)—Starting in Junos OS Release
•
20.4R1, MX Series routers support pausing and resuming unified ISSU operations. Use the pause and
resume options with the request system software in-service-upgrade command to control when to
pause and resume unified ISSU.
[See request system software in-service-upgrade]
NSR support for IS-IS with SR (ACX Series, MX Series)—Starting in Junos OS Release 20.4R1, MX Series
•
routers support NSR for IS-IS with segment routing (SR). To use NSR, you must first enable GRES on
your device.
[See Nonstop Active Routing Concepts]
Page 94

Interfaces and Chassis
464XLAT support for mobility on MS-MPC (MX Series)—Starting in Junos OS Release 20.4R1, you can
•
specify the IPv6 prefix length for the CLAT source address using the new command
clat-ipv6-prefix-length. When you configure this command, NAT rules apply 464XLAT based on
destination-address of the traffic, and source-address and source-prefix are no longer required. The
clat-ipv6-prefix-length command is available at the [edit services nat rule rule-name term term-name
then translated] hierarchy level.
[See translated and clat-ipv6-prefix-length.]
Juniper Extension Toolkit (JET)
Juniper Extension Toolkit (JET) support for 64-bit applications (MX5, MX10, MX40, MX80, MX104,
•
MX150, MX204, MX240, MX480, MX960, MX2008, MX2010, MX2020, MX10003, MX10008, MX
ELM, JunosV Firefly, cSRX, SRX100, SRX110, SRX210, SRX220, SRX240, SRX300, SRX320, SRX340,
SRX345, SRX550, SRX550HM, SRX650, SRX720E, SRX750E, SRX1400, SRX1500,SRX3400, SRX3600,
SRX4100, SRX4200, SRX4400, SRX4600, SRX4800, SRX5400, SRX5600, SRX5800, SRX7X0E, SRX-ES7,
SRX-ES8, VMX, and VSRX)—Starting in Junos OS Release 20.4R1, JET supports 64-bit applications. Use
the following commands to compile 64-bit applications for use with the AMD64 or ARM64 64-bit
processor architecture.
92
mk-amd64: Compiles the application for use with AMD64 and Junos OS with FreeBSD.
•
mk-amd64,bsdx: Compiles the application for use with AMD64 and Junos OS with upgraded FreeBSD.
•
mk-arm64,bsdx: Compiles the application for use with ARM64 and Junos OS with upgraded FreeBSD.
•
[See Develop On-Device JET Applications.]
Configure inner source MAC address for flexible VXLAN tunnels (MX Series and vMX with MPC1-MPC9E
•
or LC2101)—Starting in Junos OS Release 20.4R1, you can use the Juniper Extension Toolkit (JET) RIB
Service API to configure the source MAC address used in IPv4 and IPv6 flexible VXLAN tunnel
encapsulation profiles. The source MAC addresses is stored in the inner Ethernet header of VXLAN
encapsulation. If you don’t specify a source MAC address, the default source MAC address
00:00:5e:00:52:01 is used to encapsulate IPv4 and IPv6 flexible VXLAN tunnels.
Use the show route detail, show route extensive, and show flexible-tunnels profiles CLI commands or
the get-route-information and get-flexible-tunnels-profiles RPC/NETCONF commands to view the
source MAC address that is specified in the flexible tunnel profile.
[See Understanding Programmable Flexible VXLAN Tunnels and JET APIs on Juniper EngNet.]
Page 95

Junos OS, XML, API, and Scripting
Support for Certificate Authority Chain Profile (EX2300, EX3400, EX4300, MX240, MX480, MX960,
•
PTX-5000, VMX, vSRX and QFX5200)—Starting in Junos OS Release 20.4R1, you can configure
intermediate Certificate Authority (CA) chain profile certificate and perform https REST API request
using mutual and server authentications.
To configure intermediate ca-chain certificate, configure ca-chain ca-chain statement at the [edit system
services rest https] hierarchy level.
Start time option for interval-based internal events that trigger event policies (EX Series, MX Series,
•
PTX Series, QFX Series, and SRX Series)—Starting in Junos OS Release 20.4R1, when you create an
interval-based internal event for triggering event policies, you can specify the start date and time for
the initial event. To specify a start time, configure the start-time option along with the time-interval
option at the [edit event-options generate-event] hierarchy level.
[See Generating Internal Events to Trigger Event Policies.]
93
Junos Telemetry Interface
•
JTI support for inline Junos Traffic Vision sensors with gRPC services (MX Series and PTX Series)—Junos
OS Release 20.4R1 supports inline Jflow sensors for FPC3 and MPC 1 through 9. This feature enables
you to monitor inline Junos Traffic Vision (previously known as Jflow) service statistics on a router and
to export statistics to an outside collector at configurable intervals using remote procedure call (gRPC)
services.
Use the resource path /junos/system/linecard/services/inline-jflow/ in a subscription to export statistics.
You can view statistics in the collector output under /components/. The collector component ID in the
statistics output will include the FPC slot number for which inline Junos Traffic Vision statistics are
exported. For example, inline Jflow statistics for FPC 0 will be under component id 0, and inline Jflow
statistics for FPC 1 will be under component id 1.
Inline Junos Traffic Vision statistics are slightly different, depending on the routing platform.
[See Guidelines for gRPC and gNMI Sensors (Junos Telemetry Interface).]
•
JTI support for persistent active gRPC sessions between collector and server during an SSL certificate
update (ACX Series, MX Series, and PTX Series)—Junos OS Release 20.4R1 supports persistent active
remote procedure call (gRPC) sessions between the collector (client) and server during an SSL certificate
update.
For secure channel authentication, the TLS protocol is used to maintain a secure channel between the
collector and the server. TLS uses the server certificate and the client certificate to authenticate each
other and send encrypted messages over the network. When an SSL certificate is updated, existing gRPC
sessions are abruptly terminated, forcing the collector to initiate a new gRPC connection and subscribe
to sensors again.
Page 96

To avoid this problem, you can enable persistent active gRPC sessions by configuring hot-reloading at
the [edit system services extension-service request-response grpc ssl] hierarchy level. After you enable
this feature, gRPC sessions will remain active even when authentication certificates are updated.
After the certificate is updated, any new gRPC session will use the updated certificate.
[See gRPC Services for Junos Telemetry Interface and ssl.]
•
BGP neighbor telemetry with sharding (MX Series, PTX Series, and QFX Series)—Starting in Junos OS
Release 20.4R1, BGP neighbor telemetry with sharding (multi-threading) is supported.
[See Guidelines for gRPC and gNMI Sensors (Junos Telemetry Interface).]
•
LACP sensors for actor partner states on JTI (MX Series and PTX Series)—Starting in Junos OS Release
20.4R1, you can use Junos telemetry interface (JTI) and gRPC Network Management Interface (gNMI)
services to export LACP actor partner states (also known as LACP port states). When a subscription is
configured, ON_CHANGE or periodic streaming statistics are sent from devices to an outside collector.
You can subscribe to /lacpd/ to collect all statistics or include the following resource paths individually
in a subscription:
94
/lacpd/ae/member/partner_collecting
•
/lacpd/ae/member/partner_synchronization
•
/lacpd/ae/member/partner_timeout
•
/lacpd/ae/member/partner_aggregatable
•
/lacpd/ae/member/partner_distributing
•
/junos/system/linecard/interface/traffic/
•
[See Guidelines for gRPC and gNMI Sensors (Junos Telemetry Interface).]
•
Juniper Resiliency Interface for exception reporting and null route detection (ACX Series, PTX Series
and MX Series)—Starting in Junos OS Release 20.4R1, you can use Juniper Resiliency Interface to detect
and reduce Mean Time to Repair (MTTR) first-order network issues. Juniper Resiliency Interface uses a
push model for data reporting from the entities in the system which encounter packet drops. This
automates the workflow for detecting, reporting, and mitigating adverse exceptions.
To collect kernel routing table and routing protocol process exceptions, configure the set system resiliency
exceptions statement at the [edit] hierarchy level to specify exception reporting based on kernel
exceptions, and routing exceptions.
You can display exceptions from a remote collector by means of remote procedure call (gRPC) services
or gRPC network management interface (gNMI) services. Display on-box exceptions by accessing the
/var/log file or the database at /var/db/ResiliencyExceptions.db. No Junos operational mode commands
display these exceptions.
Page 97

MPLS
Re-engineering of SR-TE (MX Series, PTX Series)—Starting with Junos OS Release 20.4R1, you can
•
incorporate the following features to enhance the debugging capability of segment routing
traffic-engineering (SR-TE):
rib-group import functionality.
•
Display of SR-TE routes installed from various tunnel sources using the show spring-traffic-engineering
•
command.
Template map for BGP SR-TE tunnels.
•
Compute profile in template with distributed Constrained Shortest Path First (CSPF) for dynamic SR-TE
•
tunnels.
6PE (IPv6 over IPv4 SR-TE tunnel)
•
no-chained-composite-next-hop option
•
[See source-packet-routing and show spring-traffic-engineering.]
95
Support for optimizing auto-bandwidth adjustments for MPLS LSPs (MX Series and PTX Series)—Starting
•
in Junos OS Release 20.4R1, you can configure faster auto-bandwidth adjustment for MPLS LSPs under
overflow or underflow conditions. This feature decreases the minimum allowed
adjust-threshold-overflow-limit and adjust-interval to 150 seconds when adjust-threshold-overflow-limit
and adjust-threshold-underflow-limit cross the configured threshold values. In releases earlier than
Junos OS Evolved Release 20.4R1, the adjust-interval is 300 seconds under overflow or underflow
conditions.
You can configure faster in-place LSP bandwidth update that avoids signaling of a new LSP instance as
part of make-before-break. To configure faster in-place LSP bandwidth update, include the
in-place-lsp-bandwidth-update configuration statement at the [edit protocols mpls label-switched-path
lsp-name] hierarchy level.
You can also configure RSVP interfaces to support subscription percentage per priority. To configure
subscription percentage per priority, include the subscription priority priority percent value configuration
statement at the [edit protocols rsvp interface interface-name] hierarchy level.
[See Configuring Optimized Auto-bandwidth Adjustments for MPLS LSPs.]
Support for express segments to establish end-to-end segment routing path (MX Series and PTX
•
Series)—Starting in Junos OS Release 20.4R1, express segments can be used to establish end-to-end TE
paths between interconnected TE networks. Express segments (also known as virtual TE links) are
generated dynamically through policies matching the underlay LSPs. Express segments and the
corresponding abstracted topology (required by RFC7926) is generated with policies.
To apply a policy, include the policy policy-name statement at the [edit protocols express-segment
traffic-engineering] hierarchy level.
Page 98

To configure express segment, include the express-segment statement under the [edit protocols]
hierarchy level.
[See How to Establish End-to-End Segment Routing Paths Using Express Segments.]
Network Management and Monitoring
Configuration support to prevent drifting of accounting records (MX Series routers, vMX) —You can
•
configure accounting records to record data in accounting files and archive the accounting files to analyze
the information collected. Drifting of the accounting records happens if the time at which the records
are written to the accounting file spills beyond the transfer window of the file. Starting in Junos OS
Release 20.4R1, to prevent drifting of accounting records:
Use the start-time statement with the accounting profiles (class-usage-profile, filter-profile,
•
flat-file-profile, interface-profile, mib-profile, and routing-engine-profile) to have a predictable start
time of the profiles.
Use the timestamp statement with the request accounting add records command to record the
•
timestamp externally instead of epoch timestamp when the command is executed.
96
[See routing-engine-profile, class-usage-profile, interface-profile, filter-profile, mib-profile, flat-file-profile.]
Configuration retrieval using the configuration revision identifier (EX3400, EX4300, MX204, MX240,
•
MX480, MX960, MX2020, PTX3000, PTX10008, QFX5100, QFX10002-60C, SRX5800, vMX, and
vSRX)—Starting in Junos OS Release 20.4R1, you can use the configuration revision identifier feature
to view the configuration for a specific revision. This configuration database revision can be viewed with
the CLI command show system configuration revision.
[See show system configuration revision.]
Junos XML protocol operations support loading and comparing configurations using the configuration
•
revision identifier (EX3400, EX4300, MX204, MX240, MX480, MX960, MX2020, PTX3000, PTX10008,
QFX5100, QFX10002-60C, SRX5800, vMX, and vSRX)—Starting in Junos OS Release 20.4R1, the Junos
XML management protocol operations support loading and comparing configurations by referencing
the configuration revision identifier of a committed configuration. You can execute the
<load-configuration> operation with the configuration-revision attribute to load the configuration with
the given revision identifier into the candidate configuration. Additionally, you can compare the candidate
or active configuration to a previously committed configuration by referencing the configuration revision
identifier for the comparison configuration. The <get-configuration> operation supports the
compare="configuration-revision" and configuration-revision attributes to perform the comparison.
[See <get-configuration> and <load-configuration>.]
Support for an extension to the rpm-tracked static routes (MX Series, PTX Series, and vMX)—Starting
•
in Junos OS Release 20.4R1, you can configure route preference and tag values for each destination-prefix.
This feature supports both IPv4 and IPv6 rpm-tracked static routes.
[See show route rpm-tracking.]
Page 99

Limitations
Qualified next hop is not supported with rpm-tracked static routes. Hence, the setting of preference,
metric, and tags applies only to the rpm-tracking static route and not to the related next hops.
Routing Policy and Firewall Filters
Support for route’s next-hop weight in policy match condition (MX Series, PTX Series, and QFX
•
Series)—Starting in Junos OS Release 20.4R1, a route with multiple next-hop paths can use the weight
associated with a path to identify primary and backup paths. The path with the lowest weight is used
as the primary path, and any paths with higher weights are treated as backup paths. You can use the
next-hop weight as a match condition in export policies to redistribute IGP and BGP routes based on
whether the primary or backup paths are active.
Configure this match condition using the [edit policy-options policy-statement policy-name term
term-name from] statement.
[See policy-statement and show policy.]
97
Routing Protocols
Support for relaxing BGP router ID format from /32 to a nonzero ID per RFC 6286 ( MX204, NFX
•
Series, PTX5000, QFX Series, and vRR)—Starting in Junos OS Release 20.4R1, you can establish a BGP
connection using a BGP identifier that is a 4-octet, unsigned, nonzero integer and it needs to be unique
only within the autonomous system (AS) per RFC 6286. In earlier releases, the BGP ID of a BGP speaker
was required to be a valid IPv4 host address assigned to the BGP speaker.
To enable this feature, use the bgp-identifier identifier group bgp group name bgp-identifier identifier
neighbor peer address bgp-identifier identifier configuration statement at the [edit protocols bgp]
hierarchy level.
[See router-id]
Support for multiple single-hop EBGP sessions on different links using the same IPv6 link-local address
•
(ACX Series, EX Series, MX Series, PTX Series, QFX Series, SRX Series, vMX, and vSRX)—Starting in
Junos OS Release 20.4R1, you are no longer required to have unique peer addresses for Juniper devices
for every EBGP session. You can now enable single-hop EBGP sessions on different links over multiple
directly-connected peers that use the same IPv6 link-local address.
In earlier Junos OS Releases, BGP peers could be configured with link-local addresses, but multiple BGP
peers could not be configured to use the same link-local address on different interfaces.
[See Configure Multiple Single-Hop EBGP Sessions on Different Links Using the Same Link-Local Address
(IPv6).]
Support for IPv6 L3VPN over IPv6 SR-TE and IPv6 Underlay (MX Series)—Starting in Junos OS Release
•
20.4R1, You can configure an IPv6 Layer3 VPN connection with an IPv6 local address and an IPv6
Page 100

neighbor address. We have extended BGP support for IPv6 Layer 3 VPN over BGP IPv6 SR-TE in IS-IS
networks. You can connect an IPv6 provider edge device with a colored or non-colored IPv6 penultimate
nexthop (PNH) address mapped to IPv6 SR-TE tunnels.
To configure an IPv6 address for Layer 3 VPN connection, include the family inet6-vpn configuration
statement at the [edit protocols bgp group name] hierarchy level.
[See Understanding Static Segment Routing LSP in MPLS Networks.]
Support for BGP Labeled Unicast prefix SID (MX Series and PTX Series)—Starting in Junos OS 20.4R1,
•
BGP labeled unicast can carry segment routing global block label range and index information through
the prefix segment attribute. With this feature we support segment routing using the BGP labeled unicast
prefix segments and the MPLS data plane in medium to large scaled data centers. The controller directs
the server to assign a stack- of labels to an incoming packet based on the available network state
information. The assigned label stack avoids congested paths and steers the packet through a best
available path.
To configure and advertise the SRGB label range specifically for BGP include the source-packet-routing
srgb start-label start-label index-range index-rante and advertise-srgb configuration statements at the
[edit protocols bgp] hierarchy level.
98
To advertise prefix SIDs to external BGP peers, include the advertise-prefix-sid configuration statement
at the [edit protocols bgp] hierarchy level. You can configure this statement globally or for specific BGP
groups or BGP neighbors.
[See srgb.]
Support for SRv6 network programming and Layer 3 Services over SRv6 in BGP (MX Series)—Starting
•
in Junos OS Release 20.4R1, you can configure BGP based Layer 3 service over SRv6 core. You can
enable Layer 3 overlay services with BGP as control plane and SRv6 as dataplane. SRv6 network
programming provides flexibility to leverage segment routing without deploying MPLS. Such networks
depend only on the IPv6 headers and header extensions for transmitting data.
To configure IPv4 and IPv6 transport over SRv6 core, include the end-dt4-sid sid and the end-dt6-sid
sid statements at the [edit protocols bgp source-packet-routing srv6 locator name] hierarchy level.
To configure IPv4 VPN and IPv6 VPN service over SRv6 core, include the end-dt4-sid sid and the
end-dt6-sid sid statements at the [edit routing-instances routing-instance name protocols bgp
source-packet-routing srv6 locator name] hierarchy level.
[See Understanding SRv6 Network Programming and Layer 3 Services over SRv6 in BGP.]
Support for unicast ARP request on table entry expiration (MX Series)—Starting in Junos OS Release
•
20.4R1, you can configure the device to send a unicast ARP request instead of the default broadcast
request when an ARP table entry is about to expire. The retry requests are unicast at intervals of 5
seconds. Without this option, the retry requests are broadcast at intervals of 800 milliseconds. This
behavior reduces overall ARP broadcast traffic. It also supports the use case where access nodes are
configured not to forward broadcast ARP requests toward customer CPEs for security reasons and to
 Loading...
Loading...