Page 1

Release
Published
2021-04-22
Notes
Junos®OS 19.3R1 Release Notes
SUPPORTED ON
ACX Series, EX Series, Junos Fusion Enterprise, Junos Fusion Provider Edge, MX Series,
•
NFX Series, PTX Series, QFX Series, and SRX Series
HARDWARE HIGHLIGHTS
Support for two 100-Gigabit Ethernet QSFP28 transceivers on the 2-port QSFP+/QSFP28
•
uplink module
(EX4300-48MP, EX4300-48MP-S switches)
SOFTWARE HIGHLIGHTS
Adding custom YANG data models to the Junos OS schema (ACX5448-D and ACX5448-M)
•
Match condition for IPv6 firewall filters (ACX6360)
•
IGMP snooping for EVPN-VXLAN (EX9200 switches, MX Series, vMX)
•
Power over Ethernet IEEE 802.3bt (EX4300-48MP switches)
•
Configuring Q-in-Q tagging behavior for the native VLAN (EX4300 and EX4300-MP
•
switches and Virtual Chassis)
IPv6 filter-based forwarding (EX4650 and QFX5120 switches)
•
Input traffic control profile assignment to dynamic logical interface sets (MX Series)
•
Multiple routing instance for ping overlay and traceroute overlay on VXLAN (MX Series
•
routers and vMX virtual routers)
Seamless BFD inline mode for static segment routing LSPs (MX Series)
•
Page 2

Program management interface in a nondefault routing instance in op scripts and JET
•
applications (MX Series)
IPv6 support in Python automation scripts (MX Series, PTX Series, and QFX Series)
•
Juniper AAA Model streaming telemetry support for subscriber services for JTI (MX Series)
•
OSPF TI-LFA back paths for Segment Routing (MX Series)
•
Dual virtual function (NFX150)
•
UDP tunnels using FTI interfaces (PTX Series)
•
VLAN tag manipulation: pop, push, and swap (PTX Series)
•
DSCP in APBR rule (SRX Series and vSRX)
•
Express Path (SRX4600)
•
Application quality of services for logical systems and tenant systems (SRX Series)
•
New SCB, IOC, and Routing Engine improve performance and scalability (SRX5400,
•
SRX5600, and SRX5800)
Diameter S6a authentication (SRX Series)
•
Page 3

Release Notes: Junos®OS Release 19.3R1 for
the ACX Series, EX Series, MX Series, NFX
Series, PTX Series, QFX Series, SRX Series, and
Junos Fusion
1
22 April 2021
Contents
Introduction | 13
Junos OS Release Notes for ACX Series | 13
What's New | 14
What’s New in 19.3R1-S1 | 14
What’s New in 19.3R1 | 15
What's Changed | 21
General Routing | 22
Junos OS XML API and Scripting | 22
Interfaces and Chassis | 22
System Logging | 23
Operation, Administration, and Maintenance (OAM) | 23
Known Limitations | 23
General Routing | 24
Open Issues | 25
General Routing | 26
Resolved Issues | 28
Resolved Issues: 19.3R1 | 28
Documentation Updates | 31
Page 4

Migration, Upgrade, and Downgrade Instructions | 31
Upgrade and Downgrade Support Policy for Junos OS Releases | 32
Junos OS Release Notes for EX Series Switches | 33
What's New | 33
Hardware | 35
Authentication, Authorization and Accounting (AAA) (RADIUS) | 35
EVPN | 35
Forwarding and Sampling | 36
Interfaces and Chassis | 37
Junos Telemetry Interface | 37
Layer 2 Features | 39
Management | 39
Multicast | 40
Routing Policy and Firewall Filters | 40
2
Routing Protocols | 40
Services Applications | 40
Software Installation and Upgrade | 41
Virtual Chassis | 42
What's Changed | 44
General Routing | 44
Interfaces and Chassis | 45
Junos OS XML API and Scripting | 45
Layer 2 Features | 45
System Logging | 45
Known Limitations | 46
EVPN | 47
Infrastructure | 47
Platform and Infrastructure | 47
Open Issues | 48
Authentication and Access Control | 48
Infrastructure | 48
Interfaces and Chassis | 49
J-Web | 49
Network Management and Monitoring | 49
Page 5

Platform and Infrastructure | 49
Routing Protocols | 50
Resolved Issues | 51
EVPN | 51
Forwarding and Sampling | 52
Infrastructure | 52
Interfaces and Chassis | 52
Layer 2 Ethernet Services | 52
Network Management and Monitoring | 52
Platform and Infrastructure | 52
Routing Protocols | 56
Subscriber Access Management | 56
User Interface and Configuration | 56
Virtual Chassis | 56
3
VPNs | 56
Documentation Updates | 57
Migration, Upgrade, and Downgrade Instructions | 57
Upgrade and Downgrade Support Policy for Junos OS Releases | 58
Junos OS Release Notes for Junos Fusion Enterprise | 58
What’s New | 59
What’s Changed | 60
Known Limitations | 60
Open Issues | 61
Junos Fusion for Enterprise | 61
Resolved Issues | 62
Resolved Issues: 19.3R1 | 62
Documentation Updates | 62
Migration, Upgrade, and Downgrade Instructions | 63
Basic Procedure for Upgrading Junos OS on an Aggregation Device | 63
Upgrading an Aggregation Device with Redundant Routing Engines | 65
Preparing the Switch for Satellite Device Conversion | 66
Converting a Satellite Device to a Standalone Switch | 67
Upgrade and Downgrade Support Policy for Junos OS Releases | 67
Downgrading from Junos OS | 68
Page 6

Junos OS Release Notes for Junos Fusion Provider Edge | 69
What's New | 69
What's Changed | 70
Known Limitations | 70
Open Issues | 71
Junos Fusion Provider Edge | 71
Resolved Issues | 72
Junos Fusion for Provider Edge | 72
Documentation Updates | 73
Migration, Upgrade, and Downgrade Instructions | 73
Basic Procedure for Upgrading an Aggregation Device | 74
Upgrading an Aggregation Device with Redundant Routing Engines | 76
Preparing the Switch for Satellite Device Conversion | 77
Converting a Satellite Device to a Standalone Device | 78
4
Upgrading an Aggregation Device | 80
Upgrade and Downgrade Support Policy for Junos OS Releases | 81
Downgrading from Junos OS Release 19.3 | 81
Junos OS Release Notes for MX Series 5G Universal Routing Platform | 82
What's New | 82
Hardware | 83
Authentication and Access Control | 83
Class of Service (CoS) | 84
EVPN | 85
General Routing | 86
Interfaces and Chassis | 87
Junos OS XML API and Scripting | 88
Junos Telemetry Interface | 88
Layer 2 Features | 92
Management | 93
MPLS | 93
Operation, Administration, and Maintenance (OAM) | 94
Port Security | 94
Routing Protocols | 95
Services Applications | 96
Page 7

Software-Defined Networking (SDN) | 98
Software Installation and Upgrade | 98
Subscriber Management and Services | 100
What's Changed | 102
EVPN | 102
General Routing | 102
Interfaces and Chassis | 103
Junos OS XML API and Scripting | 103
MPLS | 103
Operation, Administration, and Maintenance (OAM) | 104
Routing Protocols | 104
Services Applications | 104
Software Defined Networking (SDN) | 105
Subscriber Management and Services | 105
5
System Logging | 105
Known Limitations | 106
General Routing | 106
Infrastructure | 107
Interfaces and Chassis | 107
MPLS | 108
Platform and Infrastructure | 108
Routing Protocols | 108
Open Issues | 109
EVPN | 109
Forwarding and Sampling | 110
General Routing | 110
Infrastructure | 116
Interfaces and Chassis | 117
J-Web | 118
Layer 2 Ethernet Services | 118
MPLS | 118
Platform and Infrastructure | 118
Routing Policy and Firewall Filters | 120
Routing Protocols | 120
Page 8
Services Applications | 121
User Interface and Configuration | 121
VPN | 121
Resolved Issues | 122
Class of Service (CoS) | 123
EVPN | 123
Forwarding and Sampling | 124
General Routing | 124
Infrastructure | 133
Interfaces and Chassis | 134
Layer 2 Features | 135
Layer 2 Ethernet Services | 135
MPLS | 136
Network Address Translation (NAT) | 137
6
Network Management and Monitoring | 137
Platform and Infrastructure | 137
Routing Policy and Firewall Filters | 138
Routing Protocols | 138
Services Applications | 140
Software Installation and Upgrade | 141
Subscriber Access Management | 141
User Interface and Configuration | 141
VPNs | 141
Documentation Updates | 142
Migration, Upgrade, and Downgrade Instructions | 143
Basic Procedure for Upgrading to Release 19.3 | 144
Procedure to Upgrade to FreeBSD 11.x based Junos OS | 144
Procedure to Upgrade to FreeBSD 6.x based Junos OS | 147
Upgrade and Downgrade Support Policy for Junos OS Releases | 148
Upgrading a Router with Redundant Routing Engines | 149
Downgrading from Release 19.3 | 149
Page 9
Junos OS Release Notes for NFX Series | 150
What’s New | 150
Application Security | 151
Interfaces | 151
What's Changed | 151
Factory-Default Configuration | 152
Known Limitations | 152
Interfaces | 153
Platform and Infrastructure | 153
Open Issues | 153
High Availability | 154
Interfaces | 154
Platform and Infrastructure | 154
Virtual Network Functions (VNFs) | 155
7
Resolved Issues | 155
Class-of-Service (CoS) | 156
Interfaces | 156
Platform and Infrastructure | 157
Protocols | 157
Virtual Network Functions (VNFs) | 157
Documentation Updates | 158
Migration, Upgrade, and Downgrade Instructions | 158
Upgrade and Downgrade Support Policy for Junos OS Releases | 159
Basic Procedure for Upgrading to Release 19.3 | 159
Junos OS Release Notes for PTX Series Packet Transport Routers | 160
What's New | 161
Class of Service | 162
Interfaces and Chassis | 162
Junos OS XML, API, and Scripting | 162
Junos Telemetry Interface | 163
Management | 165
MPLS | 165
Network Management and Monitoring | 165
Routing Policy and Firewall filters | 166
Page 10
Routing Protocols | 166
Security | 167
Software Installation and Upgrade | 167
What's Changed | 169
General Routing | 170
Interfaces and Chassis | 170
Junos OS XML, API, and Scripting | 171
Software Defined Networking | 171
System Logging | 171
Known Limitations | 172
General Routing | 172
Interfaces and Chassis | 173
Open Issues | 174
General Routing | 174
8
Infrastructure | 176
Interfaces and Chassis | 176
Routing Protocols | 176
Resolved Issues | 176
General Routing | 177
Infrastructure | 178
Interfaces and Chassis | 179
Layer 2 Ethernet Services | 179
MPLS | 179
Routing Protocols | 179
VPNs | 179
Documentation Updates | 180
Migration, Upgrade, and Downgrade Instructions | 180
Basic Procedure for Upgrading to Release 19.3 | 181
Upgrade and Downgrade Support Policy for Junos OS Releases | 183
Upgrading a Router with Redundant Routing Engines | 184
Junos OS Release Notes for the QFX Series | 185
What's New | 185
Hardware | 186
EVPN | 186
Page 11
Forwarding and Sampling | 187
Interfaces and Chassis | 188
Junos OS XML, API, and Scripting | 189
Junos Telemetry Interface | 190
Management | 190
Multicast | 191
Routing Protocols | 191
Routing Protocols and Firewall Filters | 192
Services Applications | 192
Software Installation and Upgrade | 192
Virtual Chassis | 194
What's Changed | 195
Interfaces and Chassis | 195
Junos OS XML, API, and Scripting | 197
9
Layer 2 Features | 197
Software Defined Networking | 197
System Logging | 197
Known Limitations | 198
Class of Service (CoS) | 199
EVPN | 199
General Routing | 199
Infrastructure | 200
Layer 2 Features | 200
Routing Protocols | 200
Open Issues | 201
General Routing | 201
High Availability (HA) and Resiliency | 204
Infrastructure | 204
Interfaces and Chassis | 204
Layer 2 Features | 204
MPLS | 205
Platform and Infrastructure | 205
Routing Protocols | 205
Page 12
Resolved Issues | 206
Class of Service (CoS) | 206
EVPN | 206
General Routing | 207
Interfaces and Chassis | 212
Layer 2 Ethernet Services | 212
Layer 2 Features | 212
MPLS | 212
Routing Protocols | 213
User Interface and Configuration | 214
Documentation Updates | 214
Migration, Upgrade, and Downgrade Instructions | 214
Upgrading Software on QFX Series Switches | 215
Installing the Software on QFX10002-60C Switches | 217
10
Installing the Software on QFX10002 Switches | 217
Upgrading Software from Junos OS Release 15.1X53-D3X to Junos OS Release
15.1X53-D60, 15.1X53-D61.7, 15.1X53-D62, and 15.1X53-D63 on QFX10008 and
QFX10016 Switches | 218
Installing the Software on QFX10008 and QFX10016 Switches | 220
Performing a Unified ISSU | 224
Preparing the Switch for Software Installation | 225
Upgrading the Software Using Unified ISSU | 225
Upgrade and Downgrade Support Policy for Junos OS Releases | 227
Junos OS Release Notes for SRX Series | 228
What’s New | 229
Application Security | 229
Chassis Clustering | 231
Flow-Based and Packet-Based Processing | 231
General Packet Radio Switching (GPRS) | 231
Hardware | 231
J-Web | 232
Logical Systems and Tenant Systems | 233
Network Address Translation (NAT) | 234
Network Management and Monitoring | 234
Platform and Infrastructure | 234
Page 13
Routing Protocols | 235
Security | 235
Juniper Sky ATP | 236
Subscriber Management and Services | 237
Virtual Routing | 237
What's Changed | 238
Application Security | 238
Authentication and Access Control | 239
Junos OS XML API and Scripting | 239
J-Web | 239
Licensing | 239
Network Management and Monitoring | 239
System Logging | 240
Unified Threat Management (UTM) | 240
11
VPN | 240
Known Limitations | 241
J-Web | 241
Logical Systems and Tenant Systems | 241
VPNs | 241
Open Issues | 242
Application Security | 242
J-Web | 242
Platform and Infrastructure | 243
Routing Policy and Firewall Filters | 243
VPNs | 243
Resolved Issues | 244
Application Layer Gateways (ALGs) | 244
Application Security | 244
Authentication and Access Control | 245
Chassis Clustering | 245
Class of Service (CoS) | 245
Flow-Based and Packet-Based Processing | 245
Infrastructure | 247
Interfaces and Routing | 247
Page 14

Installation and Upgrade | 247
Interfaces and Chassis | 247
Intrusion Detection and Prevention (IDP) | 248
J-Web | 248
Network Address Translation (NAT) | 248
Network Management and Monitoring | 248
Platform and Infrastructure | 249
Routing Policy and Firewall Filters | 250
Unified Threat Management (UTM) | 250
User Interface and Configuration | 251
VPNs | 251
Documentation Updates | 252
Migration, Upgrade, and Downgrade Instructions | 253
Upgrade and DowngradeSupport Policy for Junos OS Releases and Extended End-Of-Life
Releases | 253
12
Upgrading Using ISSU | 254
Licensing | 254
Finding More Information | 255
Documentation Feedback | 255
Requesting Technical Support | 256
Self-Help Online Tools and Resources | 256
Opening a Case with JTAC | 257
Revision History | 257
Page 15

Introduction
Junos OS runs on the following Juniper Networks®hardware: ACX Series, EX Series, M Series, MX Series,
NFX Series, PTX Series, QFabric systems, QFX Series, SRX Series, T Series, and Junos Fusion.
These release notes accompany Junos OS Release 19.3R1 for the ACX Series, EX Series, MX Series, NFX
Series, PTX Series, QFX Series, SRX Series, and Junos Fusion. They describe new and changed features,
limitations, and known and resolved problems in the hardware and software.
Junos OS Release Notes for ACX Series
IN THIS SECTION
13
What's New | 14
What's Changed | 21
Known Limitations | 23
Open Issues | 25
Resolved Issues | 28
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 31
These release notes accompany Junos OS Release 19.3R1 for the ACX Series. They describe new and
changed features, limitations, and known and resolved problems in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
Page 16
What's New
IN THIS SECTION
What’s New in 19.3R1-S1 | 14
What’s New in 19.3R1 | 15
Learn about new features introduced in this release for ACX Series routers.
What’s New in 19.3R1-S1
Hardware
New ACX5448-M Universal Metro Routers—In Junos OS Release 19.3R1-S1, we introduce the
•
ACX5448-M, a top-of-rack router with support for advanced security capabilities such as Media Access
Control Security (MACsec). A compact 1 U model, the ACX5448-M provides a system throughput of up
to 800 Gbps through the following port configuration:
14
Forty-four 10-Gigabit Ethernet SFP+ or 1-Gigabit Ethernet SFP ports (0 through 43). The ACX5448-M
•
supports MACsec only on these ports.
Six 100-Gigabit Ethernet QSFP28 or 40-Gigabit Ethernet QSFP+ ports (44 through 49). You can
•
channelize each QSFP28 port into four 25-Gbps interfaces and each QSFP+ port into 10-Gbps interfaces
using breakout cables (and the channelization configuration).
The ACX5448-M routers have redundant fan modules and redundant AC or DC power supply modules.
New ACX5448-D Universal Metro Routers—In Junos OS Release 19.3R1-S1, we introduce the
•
ACX5448-D, a top-of-rack router for aggregation environments. Designed for packet-optical convergence,
this compact 1 U router provides wire-speed packet performance, very low latency, and a rich set of
Layer 2 and Layer 3 features.
The ACX5448-D provides a system throughput of up to 800 Gbps through the following port
configuration:
Thirty-six 10-Gigabit Ethernet SFP+ or 1-Gigabit Ethernet SFP ports (0 through 35).
•
Two 100-Gigabit Ethernet QSFP28 or 40-Gigabit Ethernet QSFP+ ports (36 and 37). You can channelize
•
each QSFP28 port into four 25-Gbps interfaces and each QSFP+ port into four 10-Gbps interfaces
using breakout cables (and the channelization configuration).
Two 200-Gigabit Ethernet CFP2-DCO ports (38 and 39).
•
The ACX5448-D routers have redundant fan modules and redundant AC or DC power supply modules.
Page 17

What’s New in 19.3R1
Class of Service
Class of Service (CoS) parity support for ACX5000 routers—Starting in Junos OS 19.3R1, the
•
Class-of-Service feature set is supported on ACX5000 devices to enable users to configure classification,
rewrite, shaping, queueing, and scheduling parameters for traffic flow.
For more information regarding CoS, see Understanding Class of Service.
Support for Class-of-Service (CoS) for ACX5448 devices—Starting in Junos OS 19.3R1, support is
•
provided for Class-of-Service (COS) on ACX5448 devices to include firewall filter families (ANY, VPLS,
ethernet-switching, CCC, IPv6, IPv4, Lo0-IPv6, Lo0-IPv4, and MPLS), and CoS (classification, policing,
forwarding policy, forwarding class to queue map, WRED and Tail drop profiles, fabric queue and
scheduling configuration, scheduler, deep buffers, and remarking).
For more information regarding CoS, see Understanding Class of Service.
High Availability (HA) and Resiliency
VRRP support (ACX5448)—Starting in Junos OS Release 19.3R1, the ACX5448 router supports the
•
Virtual Router Redundancy Protocol (VRRP) over aggregated Ethernet and integrated routing and bridging
(IRB) interfaces. The VRRP queue size is limited, so it doesn’t disturb other protocols such as Bidirectional
Forwarding Detection (BFD) and connectivity fault management (CFM). The ACX5448 supports 16
VRRP groups.
15
[See Understanding VRRP. ]
•
Software Support (ACX5448-D and ACX5448-M)—Starting in Junos OS Release 19.3R1, ACX5448-D
and ACX5448-M routers support:
Chassis management software—Manages the onboard FRUs
•
Upgradable common BIOS software—Initializes all the devices on the hardware
•
FPC and PIC management
•
Interfaces and Chassis
Hardware resiliency support (ACX5448-D and ACX5448-M)—Starting in Junos OS Release 19.3R1,
•
ACX5448-D and ACX5448-M routers support the resiliency feature, which includes handling of hardware
failure and faults. Resiliency on an ACX5448-D enhances its debugging capability in the case of hardware
failure of its components such as Routing Engine, solid-state drive (SSD), and PCI Express. For example,
the resiliency feature enables the router to recover from inter-integrated circuit (I2C) failure, and improves
its voltage monitoring, temperature monitoring, and PCI Express error handling and reporting. The
resiliency feature also provides DRAM single-bit and multibit error checking and correction (ECC)
capabilities.
[See show chassis fpc errors.]
Page 18

Interface speed, channelization, and MACsec support (ACX5448-M)—In Junos OS Release 19.3R1, we
•
introduce the ACX5448-M Universal Metro Router with support for advanced security capabilities such
as Media Access Control Security (MACsec). The ACX5448-M has the following port types:
Forty-four 10-Gigabit Ethernet or 1-Gigabit Ethernet SFP+ ports (0 through 43). Based on the optics
•
plugged in, the ports come up either as 1-Gbps or 10-Gbps.
Six 100-Gigabit Ethernet QSFP28 ports (44 through 49). These ports support 100-Gbps (the default)
•
and 40-Gbps speeds. You can channelize these ports into four 25-Gbps or four 10-Gbps interfaces.
The 44 SFP+ ports on the ACX5448-M support MACsec; however, the six QSFP28 ports do not support
MACsec.
[See Channelize Interfaces on ACX5448-D and ACX5448-M Routers.]
Layer 2 Features
Support for Layer 2 Features (ACX5448-D and ACX5448-M)—Starting in Junos OS Release 19.3R1,
•
Junos OS supports Layer 2 bridging, Q-in-Q tunneling, no-local switching, Layer 2 protocol tunneling,
Spanning Tree Protocols (RSTP,MSTP), Bridge Protocol Data Unit (guard, root and loop protect), Ethernet
OAM, VPLS, BGP, LDP, pseudowire ping, and Bidirectional Forwarding Detection (BFD) support for
virtual circuit connectivity verification (VCCV) on ACX5448-D and ACX5448-M routers.
16
Support for Layer 2 switching cross-connects (ACX5440)—Starting in Junos OS Release 19.3R1, you
•
can leverage the hardware support available for cross-connects on the ACX5448 device with the Layer
2 local switching functionality using certain models. With this support, you can provide the EVP and
Ethernet Virtual Private Line (EVPL) services.
[See Configuring Layer 2 Switching Cross-Connects Using CCC.]
Layer 3 Features
Support for Layer 3 features (ACX5448-D and ACX5448-M)—Starting in Junos OS Release 19.3R1,
•
Junos OS supports Layer 3 protocols, multicast, and MPLS as the transport mechanism on ACX5448-D
and ACX5448-M routers.
Management
OpenConfig AAA data model support (ACX1100, ACX2100, ACX5448, ACX6360, EX4300, MX240,
•
MX480, MX960, MX10003, PTX10008, PTX10016, QFX5110, and QFX10002)—Junos OS Release
19.3R1 supports the configuration leaves specified in the OpenConfig AAA data model. Mapping the
OpenConfig AAA configuration to the Junos AAA configuration using the following YANG files in the
data model makes this support possible:
openconfig-aaa.yang
•
openconfig-aaa-types.yang
•
openconfig-aaa-tacacs.yang
•
openconfig-aaa-radius.yang
•
Page 19

The configuration model supporting the OpenConfig data model includes:
A translation script (.py / .slax) that maps each configuration leaf in the OpenConfig schema to one
•
or more configuration leafs in the JUNOS OS schema.
A deviation file (.yang) that specifies how much the implementation deviates from the vendor-neutral
•
model.
[See Mapping OpenConfig AAA Commands to Junos Configuration.]
Network Management and Monitoring
Support for adding custom YANG data models to the Junos OS schema (ACX5448-D and
•
ACX5448-M)—Starting in Junos OS Release 19.3R1, ACX5448-D and ACX5448-M routers support
loading custom YANG data models on the device, which enables you to add RPCs or configuration
hierarchies that are customized for your operations. The ability to add data models to a device is beneficial
when you want to create device-agnostic RPCs and configuration models that can be used on different
devices from one or more vendors.
[See Understanding the Management of Non-Native YANG Modules on Devices Running Junos OS.]
17
Port Security
Media Access Control Security (MACsec) support (ACX5448)—Starting with Junos OS Release 19.3R1,
•
ACX5448 routers support MACsec on 1-Gigabit Ethernet SFP and 10-Gigabit Ethernet SFP+ ports.
MACsec is an industry-standard security technology that provides secure communication for all traffic
on point-to-point Ethernet links. MACsec is standardized in IEEE 802.1AE.
[See Understanding Media Access Control Security (MACsec).]
Routing Policy and Firewall Filters
Match condition support for IPv6 firewall filters (ACX6360)—Starting in Junos OS Release 19.3R1, the
•
ACX6360 router supports the following firewall filter match conditions for IPv6 traffic: address,
destination-address, destination-port, destination-port-except, destination-prefix-list, port, port-except,
icmp-code, icmp-code-except, icmp-type, icmp-type-except, next-header, next-header-except, prefix-list,
source-address, source-port, source-port-except, and source-prefix-list.
[See Firewall Filter Match Conditions for IPv6 Traffic on ACX Series Routers and ACX6360
Documentation. ]
Routing Protocols
Clocking and Synchronous Ethernet support (ACX5448)—Starting in Junos OS Release 19.3R1, ACX5448
•
routers support frequency synchronization using the Synchronous Ethernet and Ethernet Synchronization
Message Channel (ESMC) protocols. The routers also support phase and time synchronization through
Precision Time Protocol (PTP).
[See Synchronous Ethernet Overview.]
Page 20

Transparent clock over IPv6 support (ACX5448)—Starting with Junos OS Release 19.3R1, ACX5448
•
routers support transparent clock functionality for PTP over IPv6. To configure the transparent clock
functionality, you must include the e2e-transparent statement at the [edit protocol ptp] hierarchy level.
Use the show ptp global-information command to check the status of the transparent clock functionality
configured on the router.
[See Understanding Transparent Clocks in Precision Time Protocol.]
Support for RIPv2 (ACX5448)—Starting in Junos OS Release 19.3R1, Junos OS supports RIP version 2
•
(RIPv2) for both IPv4 and IPv6 packets.
Services Applications
•
Support for Two-Way Active Measurement Protocol or TWAMP (ACX5448-D and ACX5448-M)—Starting
in Junos OS Release 19.3R1, you can configure TWAMP on your ACX5448-D and ACX5448-M routers.
TWAMP enables you measure the IP performance between two devices in a network. The ACX5448-D
and ACX5448-M routers support only the reflector side of TWAMP.
[See Two-Way Active Measurement Protocol on ACX Series.]
18
•
Support for virtualization (ACX5448-D and ACX5448-M)—Starting in Junos OS Release 19.3R1, the
Routing Engines on the ACX5448-D routers and ACX5448-M routers support virtualization.
On Routing Engines of ACX5448-D routers and ACX5448-M routers, one instance of Junos OS, which
runs as a guest operating system, is launched by default. The user needs to log in to this instance for
operations and management.
With virtualization of the Routing Engine, Junos OS supports new request and show commands associated
with host and hypervisor processes. The commands are related to:
Reboot, halt, and power management for the host
•
Software upgrade for the host
•
Disk snapshot for the host
•
[See What Are VM Hosts?.]
Port mirroring support for the IPv6 address family (ACX6360)—Starting in Release 19.3R1, you can
•
configure port mirroring on the ACX6360 router for the inet6 family. Port mirroring copies packets
entering or exiting a port and sends the copies to a local interface for local monitoring. You can use port
mirroring to send traffic to applications that analyze traffic for purposes such as monitoring compliance,
enforcing policies, detecting intrusions, monitoring and predicting traffic patterns, and correlating events.
[See Configuring Port Mirroring.]
Page 21
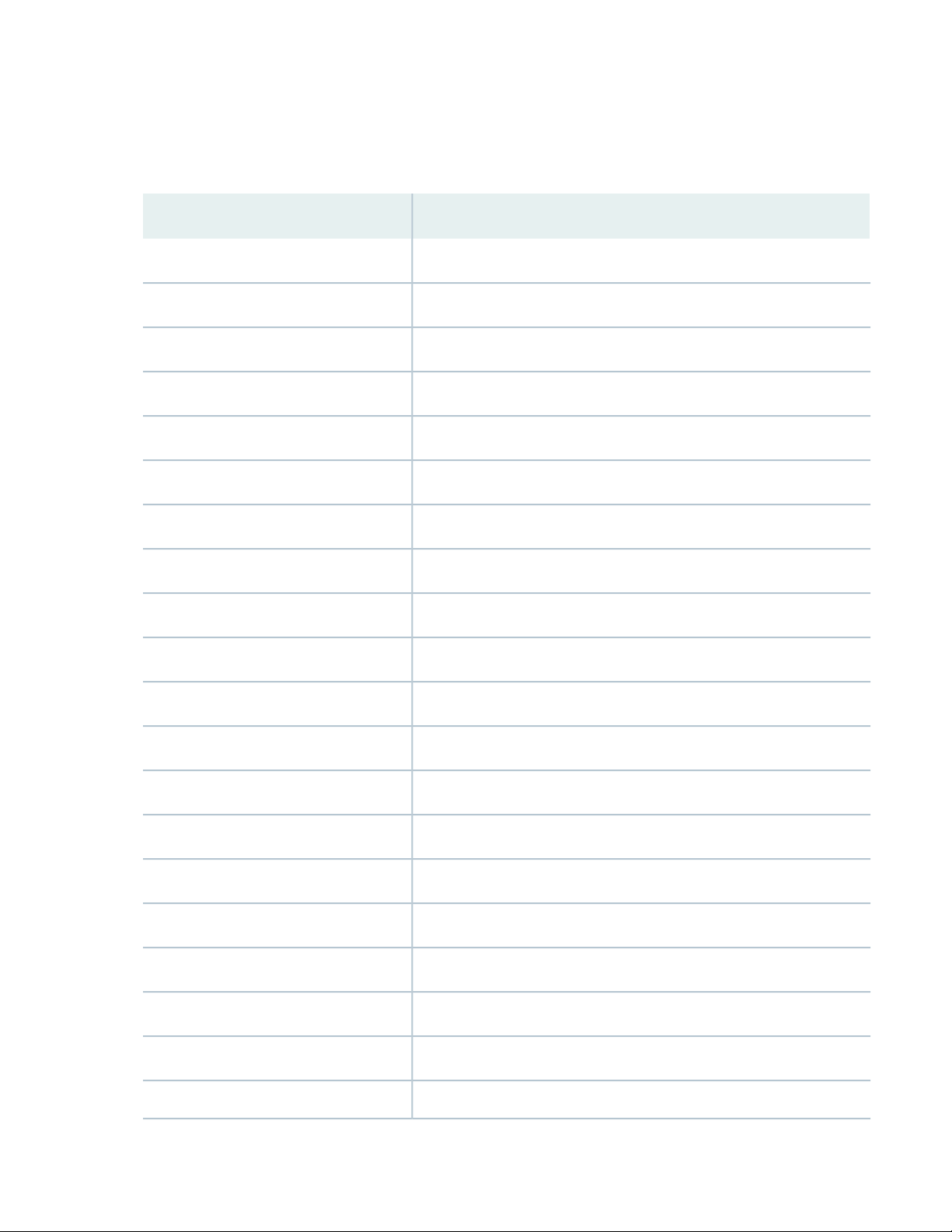
Software Installation and Upgrade
Migration of Linux kernel version—Starting in Junos OS Release 19.3R1, the following devices support
•
the Wind River Linux 9 (WRL9) kernel version:
Routing Engine SupportedPlatforms
RE-ACX-5448ACX5448-D
RE-S-X6-64GMX240, MX480, and MX960
REMX2K-X8-64GMX2020 and MX2010
RE-S-1600x8MX204
RE-S-1600x8MX10003
RE-MX2008-X8-64GMX2008
19
RE X10MX10016
RE X10MX10008
RE-PTX-X8-64GPTX5000
RCBPTXPTX3000
RE-PTX-2X00x4/RE X10PTX10016
RE-PTX-2X00x4/RE X10PTX10008
RE-PTX1000PTX1000
RE-PTX10002-60CPTX10002-XX
RE-S-EX9200-2X00x6EX9208
EX9251-REEX9251
EX9253-REEX9253
RE-S-EX9200-2X00x6EX9204
RE-S-EX9200-2X00x6EX9214
RE-QFX10002-60CQFX10002
Page 22
Routing Engine SupportedPlatforms
RE-QFX10008QFX10008
RE-QFX10016QFX10016
Starting in Junos OS Release 19.3R1, in order to install a VM host image based on Wind River Linux 9,
you must upgrade the i40e NVM firmware on the following routers:
MX Series—MX240, MX480, MX960, MX2010, MX2020, MX2008, MX10016, and MX10008
•
PTX Series—PTX3000, PTX5000, PTX10016, PTX10008, and PTX10002-XX
•
If you perform a software upgrade on a router with i40e NVM version earlier than 6.01, the upgrade
fails and the following error message is displayed:
ERROR: i40e NVM firmware is not compatible ,please upgrade i40e NVM beforeinstalling this package
ERROR: Aborting the installation
20
ERROR: Upgrade failed
[See https://kb.juniper.net/TSB17603.]
System Management
Transparent clock functionality support on (ACX5448)—Starting in Junos OS Release 19.3R1, transparent
•
clock functionality and a global configuration for enabling it are supported on the ACX5448 router.
Transparent clock functionality works for PTP over both IPv4 and Ethernet packets. To check the status
of transparent clock, use the show ptp global-information command.
[See Understanding Transparent Clocks in Precision Time Protocol. ]
Synchronous Ethernet and PTP support (ACX 5448)—Starting in Junos OS Release 19.3R1, the ACX5448
•
router supports the following features:
Frequency synchronization using Synchronous Ethernet
•
Ethernet Synchronization Message Channel (ESMC)
•
Phase and time synchronization using Precision Timing Protocol (PTP)
•
[See Synchronous Ethernet Overview. ]
SEE ALSO
What's Changed | 21
Known Limitations | 23
Open Issues | 25
Page 23
Resolved Issues | 28
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 31
What's Changed
IN THIS SECTION
General Routing | 22
Junos OS XML API and Scripting | 22
Interfaces and Chassis | 22
System Logging | 23
Operation, Administration, and Maintenance (OAM) | 23
21
See what changed in this release for ACX Series routers.
Page 24

General Routing
Support for gigether-options statement (ACX5048, ACX5096)—Junos OS supports the gigether-options
•
statement at the edit interfaces interface-name hierarchy on the ACX5048 and ACX5096 routers.
Previously, support for the gigether-statement was deprecated.
[See gigether-options.]
Junos OS XML API and Scripting
Range defined for confirm-timeout value in NETCONF and Junos XML protocol sessions (ACX Series,
•
EX Series, MX Series, PTX Series, QFX Series, and SRX Series)—Starting in Junos OS Release 19.3R1,
the value for the <confirm-timeout> element in the Junos XML protocol <commit-configuration>
operation must be in the range 1 through 65,535 minutes, and the value for the <confirm-timeout>
element in the NETCONF <commit> operation must be in the range 1 through 4,294,967,295 seconds.
In earlier releases, the range is determined by the minimum and maximum value of its unsigned integer
data type.
22
Interfaces and Chassis
Support for creating Layer 2 logical interfaces independently (ACXSeries)—In Junos OS Release 19.3R1
•
and later, ACX Series switches support creating Layer 2 logical interfaces independent of the Layer 2
routing instance type. That is, you can configure and commit the Layer 2 logical interfaces separately
and add the interfaces to the bridge domain or EVPN routing instance separately. Note that the Layer
2 logical interfaces work fine when they are added to the bridge domain or EVPN routing instance.
In the earlier Junos OS releases, when a Layer 2 logical interface configuration (units with encapsulation
vlan-bridge configuration) is used, then you must add the logical interface as part of a bridge domain or
EVPN routing instance for the commit to succeed.
Monitoring information available only in trace log (ACX Series)—In Junos OS Release 19.3R1 and later,
•
the Ethernet link fault management daemon (lfmd process) in the peer router stops monitoring the locally
occurred errors until unified ISSU completes. You can view the monitoring-related details only through
the trace log file.
Page 25

System Logging
Preventing system instability during core file generation (ACX Series)—Starting with Release 19.3R1
•
onward, Junos OS checks for available storage space on the Routing Engine before generating core files
either on request or because of an assertion condition. This check ensures that your device does not
become unstable because of shortage of storage space on the Routing Engine. If the available space is
not sufficient, core files are not generated. Instead, Junos OS either displays the Insufficient Disk space
!!! Core generation skipped message as an output or issues the syslog message core generation is skipped
due to disk full.
Operation, Administration, and Maintenance (OAM)
Performance monitoring history data is lost when change in number of supported history records is
•
detected (ACX Series)—In Junos OS Release 19.3R1, when Ethernet Connectivity Fault Management
(ECFM) starts, it detects the number of history records supported by the existing Performance Monitoring
history database and if there is any change from the number of history records supported (that is, 12)
in 19.3R1, then the existing Performance Monitoring history database is cleared and all performance
monitoring sessions are restarted with mi-index 1.
23
SEE ALSO
What's New | 14
Known Limitations | 23
Open Issues | 25
Resolved Issues | 28
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 31
Known Limitations
IN THIS SECTION
General Routing | 24
Page 26

Learn about known limitations in this release for ACX Series routers. For the most complete and latest
information about known Junos OS defects, use the Juniper Networks online Junos Problem Report Search
application.
General Routing
For an et-interface, only PRE_FEC_SD defect is raised, and no OTN alarm is raised. PR1371997
•
clock-class to QL level mapping needs to be changed via CLI in Arb GM with network option-1 PR1384968
•
When a timing configuration and the corresponding interface configuration are flapped for multiple
•
times in iteration, PTP is stuck in "INITIALIZE" state where the ARP for the neighbor is not resolved. In
issue state, BCM hardware block gets into inconsistency state, where the lookup is failing. PR1410746
Hardware-based fragmentation or reassembly is not supported. Software-based fragmentation rates
•
are going to be extremely slow depending on CPU load. PR1419371
This is the expected behaviour across all ACX Series platforms. The input packets account for all the
•
frames that are coming in, including the oversized frames, whereas the oversized frame counter only
accounts for oversized frames. PR1425748
24
These error messages can be seen sometimes if the optics is being unplugged during the EEPROM read.
•
This is expected and does not impact any functionality. PR1429016
Packet rates are not seen for aggregated Ethernet logical interface. PR1429590
•
Multicast packets are flooded in a BD if snooping is not enabled. If interfaces x and y belongs to a BD,
•
then all multicast packets will be flooded to both x and y interfaces. If packets are received from interface
x, packets will be flooded to x and y at ingress but discarded in the egress path for interface x because
packet is received from the same interface. But these packets are also counted in the VOQ and hence
we are seeing more queue statistics. It is a known Hardware limitation. monitor interface xe-0/0/30
Input packets: 177958 (64 pps) [0] Output packets: 357306 (128 pps) [0] monitor interface xe-0/0/12
Input packets: 361161 (128 pps) [642] Output packets: 179878 (63 pps) [320] user@router> show
interfaces queue xe-0/0/30 Queue: 0, Forwarding classes: best-effort Queued: Packets : 544032 192
pps . => Sum of 64 + 128pps user@router> show interfaces queue xe-0/0/12 Queue: 0, Forwarding
classes: best-effort Queued: Packets : 550929 192 pps . => Sum of 64 + 128pps. PR1429628
Any packet with size greater than the MTU size are accounted for as oversized packets. Packets exceeding
•
MTU sizes are not considered for Jabber check. PR1429923
The statistics are accessed through Broadcom API, which is the same for both tagged and untagged
•
packets. This cannot be changed in accordance with MX since it is direct access from Broadcom without
any statistics changes specific to tagging from ACX5448 side. It will impact other statistics if the change
is made. PR1430108
The port LEDs glowing during system/vmhost halt state is the expected behaviour across all ACX Series
•
platforms. Even the system LED glows during halt state. PR1430129
Page 27

Packets dropped due to MTU checks in the output interface are not accounted for as MTU errors. All
•
packets with sizes greater than the MTU size are accounted for as Oversized-packets in the input
interface. PR1430446
If Layer 2 VPN sessions have OAM control-channel option set to router-alert-label, the no-control-word
•
option in Layer 2 VPN shouldn't be used for BFD sessions to come up. PR1432854
With an asymmetric network connection, EX: a 10-Gbps MACsec port connected to a 10-Gbps
•
channelized port, high and asymmetric T1 and T4 time errors are seen. This situation introduces a high
two-way time error and also different CF updates in forward and reverse paths. PR1440140
By default, the management interface speed is always displayed as 1000 Mbps in Junos OS command
•
output. PR1440675
With the MACsec feature enabled and introduction of traffic, the peak-to-peak value varies with the
•
percentage of traffic introduced. Please find the max and mean values of the Time errors with different
traffic rates(two router scenario). Can have max value jumps as high as 1054ns with 95% traffic, 640ns
for 90% traffic and 137ns with no traffic. PR1441388
Synchronous Ethernet jitter tolerance test fails for MACsec ports. For Synchronous Ethernet and MACsec,
•
there seems to be additional framing header and footer that would get added by the MACsec protocol.
The impact on the jitter test is not obvious and appears undefined in the standards and not qualifiable
with a single DUT and Calnex. PR1447296
25
SEE ALSO
What's New | 14
What's Changed | 21
Open Issues | 25
Resolved Issues | 28
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 31
Open Issues
IN THIS SECTION
General Routing | 26
Page 28

Learn about open issues in this release for ACX Series routers. For the most complete and latest information
about known Junos OS defects, use the Juniper Networks online Junos Problem Report Search application.
General Routing
The switchover time observed was more than 50ms under certain soak test conditions with an increased
•
scale with a multi-protocol multi-router topology. PR1387858
The optic comes with Tx enabled by default. As the port is administratively disabled, the port is stopped
•
but as the port has not been started, it does not disable Tx. PR1411015
FEC NONE should be configured through cli in case of speed 40G with SR optics combination for
•
ACX5448 to interop with other platforms. PR1414649
Clock Class value is wrong in Default Data (show ptp clock) when the slave interface is down in PTP-OC
•
device. PR1416421
With ACX5448 platform devices, the ztp process will proceed with image upgrade even in situations
•
when there is a mismatch in platform name of the software image stored on ftp/ztp servers and actual
platform where the ztp process is being run. PR1418313
26
On ethernet bridge, L2 filters may not work as expected when trying to match vlan based fields for
•
untagged packets. PR1423214
DHCP clients are not able to scale to 96K PR1432849
•
With scaled interface config, delete/add or deactivate/activate interface take time. This is due to the
•
reason that we need to clear mac-entries associated with L2 ifl's and the BCM api's for that are time
consuming. PR1433426
This is a day 1 design issue which needs to be redesigned. The impact is more, But definitely this needs
•
some soaking time in DCB before it gets ported in previous versions. So it will be fixed in DCB first. Our
target is to fix this in 19.4DCB. PR1435648
On ACX5448 box, after issuing deactivate/activate "class-of-service", traffic drop might be seen.
•
PR1436494
Timing on 1G, performance is not in par compared with 10G, compensation is done to bring the mean
•
value under class-A but the peak to peak variations are high and can go beyond 100ns. It has a latency
variation with peak to peak variations of around 125ns-250ns(i.e 5-10% of the mean latency introduced
by the each phy which is of around 2.5us) without any traffic. PR1437175
These errors can be seen if CFP2 optics not plugged in. PR1438039
•
Memory leaks are expected in this release. PR1438358
•
When the interface is flapped between channelized configurations (25G to 100 G), the parent AE interface
•
configuration is not cleaned up properly. It leads to fail the traffic in that interface. The issue is happening
with channelized interfaces with ae and the issue dependent on delete sequence. Only channelized
Page 29
interface deletion doesn't reproduce the issue, both the interface and chassis deletion is creating the
issue. PR1441374
In ACX, auto exported route between VRFs might not reply for icmp echo requests. PR1446043
•
Recovery of JUNOS volume isn't possible from OAM menu. PR1446512
•
Drop profile max threshold may not be reached to its limit when the packet size is other than 1000
•
bytes. PR1448418
When a XE interface working in 1G mode in ACX5448-D, is added to a member link of an AE interface,
•
the speed of AE is wrongly shown as 10G. There is no functional impact. This is a display issue.PR1449887
If the client et- interface is up and transportd state is in init state, restart transportd process to get the
•
state updated to normal. This scenario isn't seen in normal operation but seen when interfaces are
deleted and re-created and configs are applied. PR1449937
Red Drops seen on the 25G Channelized AE Interfaces after some events (Deactivate, activate etc) on
•
the PEER box. PR1450674
Fan numbering is not the same in the two outputs: show chassis fan and show snmp mib walk
•
jnxContentsDescr. PR1456589
27
Route resolve resolution is not happening when the packet size is 10000. PR1458744
•
ACX5448 Macsec SKU Problem : On Enabling local Loopback on 10G interface, the link doesn't come
•
up. On 1G and 100G, link comes UP fine after local loopback is enabled. WorkAround : Disable/Enable
of the interface makes the link UP when local loopback is enabled. PR1460715
Arp issue is seen with aggregated Ethernet when one member of aggregated Ethernet is removed and
•
also when device is rebooted with aggregated Ethernet configuration. PR1461485
SEE ALSO
What's New | 14
What's Changed | 21
Known Limitations | 23
Resolved Issues | 28
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 31
Page 30
Resolved Issues
IN THIS SECTION
Resolved Issues: 19.3R1 | 28
Learn which issues were resolved in this release for ACX Series routers. For the most complete and latest
information about known Junos OS defects, use the Juniper Networks online Junos Problem Report Search
application.
Resolved Issues: 19.3R1
Class of Service
28
When the forwarding-class is configured under firewall policer, the dfwd might crash. PR1436894
•
General Routing
On QFX10k Series platforms (QFX10002, QFX10008, QFX10016), the 1G copper module interface on
•
10G line card (QFX10000-60S-6Q) incorrectly displays with 'Link-mode: Half-duplex'. PR1286709
Upon classifying the L3 packets, DSCP will not be preserved or lost at the egress due to the limittations
•
of broadcom chipset. PR1322142
START_BY_START_ERR interrupt handler was not available with the previous version of bcm sdk code.
•
This lead to the status checking of this flag continously by bcmDPC process leading to high CPU utilization.
This has been fixed in this release by adding a handler for this interrupt. PR1329656
On ACX5000 platforms with Junos 16.2 onwards, if the ECC Errors occur, the FPC/fxpc process might
•
use high CPU. This issue can be hit after the upgrade in some cases. PR1360452
As part of the pic_periodic, before setting the port to master/slave mode, AN bit is checked if AN is
•
complete and this would return if AN is still in progress. Since An was disabled, this port wasn't set to
either mode and this was going on in a loop causing the CPU to go high. PR1360844
On ACX1x00/ACX2x00/ACX4x00 running in 15-releases previous to 15.1R8, when configuring
•
"mac-table-size" under bridge-domain, a wrong commit error appear not allowing the commit to pass.
PR1364811
ACX led on GE interface goes down when speed 10M is added. PR1385855
•
Link Fault Signaling (LFS) feature is not supported on ACX5448 10/40/100GbE interfaces. PR1401718
•
If user configures invalid speed config on TIC ports (PIC slot 1) on ACX6360-OR/OX, TIC interfaces are
•
not created. regress@tron# show chassis fpc 0 { pic 1 { port 0 { speed 40g; } } } PR1403546
Page 31

On ACX 1000/2000/4000/5048/5096 platforms, after a new child IFL with VLAN and filter is added
•
on an AE IFD or changing the VLAN ID of a child IFL with filter, traffic over the AE IFD might get filtered
with that filter on the child IFL. Example: ae-0/0/0 is an IFD and ae-0/0/0.100 is an IFL. PR1407855
"show services inline stateful-firewall flow" or "show services inline stateful-firewall flow extensive"
•
command may cause the memory leak. which may cause that inline Nat issue. PR1408982
When using PCEP (Path ComputationElement Protocol), if a PCE (Path Computation Element) generates
•
a PCUpdate or PCCreate message which contains a metric type other than type 2, the Junos device
acting as PCC (Path Computation Client) may fail to process the message and reject the PCUpdate or
PCCreate message from the PCE. When the issue occurs the LSPs' (Label-Switched Path) characteristics
cannot be updated hence it may cause traffic impact. PR1412659
ACX-5448: BFD Timer value are not as per the configured 900ms with multiplier 3, its showing 6.000
•
with multiplier 3 instead for most of the sessions. PR1418680
On ACX5K platform, the fxpc process high CPU usage might be seen under rare condition if parity errors
•
are detected in devices. It has no direct service/traffic impact. However since CPU utilization is high
during this issue, there are some side-effects. Eg, it could impact time-sensitive features like BFD.
PR1419761
29
copy images from WAN interface to RE of ACX5448 takes long time PR1422544
•
On ACX5448 box, traffic with VLAN tag which doesn't match any of the configured interfaces will be
•
dropped. While after changing interface encapsulation from ethernet-bridge to vlan-bridge, the unmatched
traffic can enter an erroneous bridge-domain which the bridge index (VSI) is the same as the vlan-id of
the unmatched traffic. PR1423610
On ACX5448 platforms, the JUNIPER_SOURCE LR4T2 optics may not work properly due to the fact
•
that an internal defect causes it to not output power, as a result, the interface may not become up.
PR1424814
Due to BCM sdk design, EEDB hardware entry is not freed for unicast next-hop creation. This leads to
•
resource leakage and is not allowing to higher scale. PR1426734
In a rare condition, due to a timing issue, the FPC/fxpc may crash if the AE interface flaps, such as
•
deactivating/activating the AE interface. PR1427362
Multiple HW i2c failure observed because of intermittent I2C access failure on main board switches.
•
PR1429047
Chassisd can crash with unsupported hcos configuration when mx104 is used as fusion aggregation
•
device PR1430076
The tx laser was enabled by default in CPLD. Therefore, the link is shown up on the peer as soon as the
•
pfe starts. PR1430910
L4 Hashing will work for both IPv4 & IPv6 packets, if any one of the two CLIs is enabled. To disable L4
•
hashing for any one of IPV4 or IPV6, both CLIs needs to be in disabled state. CLIs for reference, set
forwarding-options hash-key family inet layer-4 set forwarding-options hash-key family inet6 layer-4
PR1431206
Page 32

On ACX5448, if egress link is 40G/100G, small size packets are encapsulated improperly and causing
•
remote interface drops the packets as runts. PR1434900
No-vrf-propagate-ttl may not work after activate or deactivate of COS configuration in acx PR1435791
•
maximum theoritical that can go for shaping rates on a queue will be upto 10%. PR1436297
•
1PPS performance metrics (class A) of G.8273.2 are not met for 1G interfaces because of the variable
•
latency added by the Vittesse PHY. PR1439231
Transit DHCP packets are not punted to CPU and are transparently passthrough. PR1439518
•
In an ACX5448 platforms, when the PFE failed to allocate packet buffer, portion of packet memories
•
may not be freed. PR1442901
On an ACX5448 box, link flaps or CoS configuration changes (specific to temporal value changes) might
•
result in traffic drop on all interfaces and recorded as RED drops. PR1443466
ACX5448/18.3R1-S4.1 not performing proper dot1p CoS rewrite on interfaces configured with
•
l2circuit/local-switching/family ccc PR1445979
ACX5448 FPC crashed due to segmentation fault, due to timing issue. There is very low chance of this
•
core occurring. PR1453766
30
Interfaces and Chassis
On ACX series, in CFM ethernet OAM scenario, after the upgrade from 17.4 onwards, the cfmd coredump
•
might be seen after committing configuration on CFM (connectivity-fault-management). PR1425804
Layer 2 Ethernet Services
In DHCP relay scenario, if the device (DHCP relay) receives a request packet with option 50 where the
•
requested IP address matches the IP address of an existing subscriber session, such request packet would
be dropped. In such a case the subscriber may need more time to get IP address assigned. The subscriber
may remain in this state until it's lease expires if it had previously bound with the address in the option
50. PR1435039
MPLS
Dynamically configured RSVP LSPs for LDP link protection may not come up after disabling/enabling
•
protocol mpls. PR1432138
Routing Protocols
On ACX platforms, the loopback address exported into other VRF instance might not work. PR1449410
•
On ACX platforms, when there is MAC change for LDP neighbor and IP remains the same, ARP update
•
is proper but MPLS LDP may still use the stale MAC of the neighbor. If there is any application/service
such as MP-BGP using LDP as next-hop, all transit traffic pointing to the stale MAC will be dropped.
PR1451217
Page 33

SEE ALSO
What's New | 14
What's Changed | 21
Known Limitations | 23
Open Issues | 25
Documentation Updates | 31
Migration, Upgrade, and Downgrade Instructions | 31
Documentation Updates
There are no errata or changes in Junos OS Release 19.3R1 documentation for the ACX Series.
31
SEE ALSO
What's New | 14
What's Changed | 21
Known Limitations | 23
Open Issues | 25
Resolved Issues | 28
Migration, Upgrade, and Downgrade Instructions | 31
Migration, Upgrade, and Downgrade Instructions
IN THIS SECTION
Upgrade and Downgrade Support Policy for Junos OS Releases | 32
This section contains the upgrade and downgrade support policy for Junos OS for the ACX Series Router.
Upgrading or downgrading Junos OS might take several minutes, depending on the size and configuration
of the network.
Page 34

For information about software installation and upgrade, see the Installation and Upgrade Guide.
Upgrade and Downgrade Support Policy for Junos OS Releases
Support for upgrades and downgrades that span more than three Junos OS releases at a time is not
provided, except for releases that are designated as Extended End-of-Life (EEOL) releases. EEOL releases
provide direct upgrade and downgrade paths—you can upgrade directly from one EEOL release to the
next EEOL release even though EEOL releases generally occur in increments beyond three releases.
You can upgrade or downgrade to the EEOL release that occurs directly before or after the currently
installed EEOL release, or to two EEOL releases before or after. For example, Junos OS Releases 17.1,
17.2, and 17.3 are EEOL releases. You can upgrade from Junos OS Release 17.1 to Release 17.2 or from
Junos OS Release 17.1 to Release 17.3.
You cannot upgrade directly from a non-EEOL release to a release that is more than three releases ahead
or behind. To upgrade or downgrade from a non-EEOL release to a release more than three releases before
or after, first upgrade to the next EEOL release and then upgrade or downgrade from that EEOL release
to your target release.
32
For more information about EEOL releases and to review a list of EEOL releases, see
https://www.juniper.net/support/eol/junos.html.
For information about software installation and upgrade, see the Installation and Upgrade Guide.
SEE ALSO
What's New | 14
What's Changed | 21
Known Limitations | 23
Open Issues | 25
Resolved Issues | 28
Documentation Updates | 31
Page 35

Junos OS Release Notes for EX Series Switches
IN THIS SECTION
What's New | 33
What's Changed | 44
Known Limitations | 46
Open Issues | 48
Resolved Issues | 51
Documentation Updates | 57
Migration, Upgrade, and Downgrade Instructions | 57
33
These release notes accompany Junos OS Release 19.3R1 for the EX Series. They describe new and
changed features, limitations, and known and resolved problems in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What's New
IN THIS SECTION
Hardware | 35
Authentication, Authorization and Accounting (AAA) (RADIUS) | 35
EVPN | 35
Forwarding and Sampling | 36
Interfaces and Chassis | 37
Junos Telemetry Interface | 37
Layer 2 Features | 39
Management | 39
Multicast | 40
Routing Policy and Firewall Filters | 40
Page 36

Routing Protocols | 40
Services Applications | 40
Software Installation and Upgrade | 41
Virtual Chassis | 42
Learn about new features introduced in this release for EX Series switches.
NOTE: The following EX Series switches are supported in Release 19.3R1: EX2300, EX2300-C,
EX3400, EX4300, EX4600-40F, EX4650, EX9200, EX9204, EX9208, EX9214, EX9251, and
EX9253.
34
Page 37

Hardware
Support for two 100-Gigabit Ethernet QSFP28 transceivers on the 2-port QSFP+/QSFP28 uplink
•
module (EX4300-48MP and EX4300-48MP-S switches)—Starting in Junos OS Release 19.3R1, you can
install two 100-Gigabit Ethernet QSFP28 transceivers in the 2-port QSFP+/QSFP28 uplink module
(model number: EX-UM-2QSFP-MR) for EX4300-48MP and EX4300-48MP-S switches. You can install
two QSFP+ transceivers, two QSFP28 transceivers, or a combination of one QSFP+ transceiver and one
QSFP28 transceiver in the uplink module.
If you configure both the ports on the uplink module to operate at 100-Gbps speed, the four QSFP+
ports on the switch are disabled.
[See EX4300 Switch Hardware Guide.]
Authentication, Authorization and Accounting (AAA) (RADIUS)
802.1X trunk port and multidomain authentication (EX4300-48MP switches)—Starting with Junos OS
•
Release 19.3R1, 802.1X trunk port and multidomain authentication is supported on EX4300-MP switches.
Authentication on the trunk port supports only single supplicant and single-secure supplicant modes.
35
Multidomain authentication is an extension of 802.1X authentication for multiple supplicants, which
authenticates multiple clients individually on one authenticator port. Multidomain authentication allows
one VoIP client and multiple data clients to authenticate to different VLANs while on the same port.
The VoIP client is authenticated to the voice VLAN while the data clients are authenticated to the data
VLAN.
[See Understanding 802.1X and VoIP on EX Series Switches.]
EVPN
Support for DHCP relay in an EVPN-MPLS network (EX9200 switches, MX Series, and vMX)—Starting
•
in Junos OS Release 19.3R1, EX9200 switches, MX Series routers, and vMX virtual routers support
DHCPv4 and DHCPv6 relay in an EVPN-MPLS network. We support this feature in a data center
architecture that includes a layer of spine devices that perform EVPN Layer 2 and Layer 3 functions.
These devices are connected to a layer of leaf devices that perform EVPN Layer 2 functions. In this
architecture, DHCP clients are connected to leaf devices, and DHCP servers are connected to spine
devices. The DHCP relay functions are centralized at the spine layer. As a result, this architecture is
known as the centrally routed bridging architecture.
[See DHCP Relay Agent in EVPN-MPLS Network.]
IGMP snooping support for EVPN-VXLAN (EX9200 switches, MX Series, vMX)—Starting in Junos OS
•
Release 19.3R1, you can configure IGMP snooping on EX9200 switches, MX Series routers, and vMX
virtual routers in an EVPN-VXLAN network. Enabling IGMP snooping helps to constrain multicast traffic
to interested receivers in a broadcast domain.
Page 38

The listed devices support these IGMP snooping use cases in a centrally routed bridging overlay (an
EVPN-VXLAN network with a two-layer IP fabric):
Forwarding multicast traffic within a VLAN (intra-VLAN)
•
Routing multicast traffic between VLANs (inter-VLAN) using one of the following methods:
•
IRB interfaces configured with Physical Interface Module (PIM) on an elected designated router (DR)
•
device
A PIM gateway with Layer 2 or Layer 3 connectivity
•
An external multicast router
•
The listed devices support these IGMP versions and membership report modes:
IGMPv2 with Any-Source Multicast (ASM) (*,G) mode only.
•
IGMPv3 in either of the following modes:
•
ASM (*,G)—the default behavior.
•
36
Single-Source Multicast (SSM) (S,G)—you must explicitly configure by including the
•
evpn-ssm-reports-only configuration statement at the [edit protocols igmp-snooping] hierarchy
level.
[See Overview of IGMP Snooping in an EVPN-VXLAN Environment.]
Forwarding and Sampling
Customizing hashing parameters and shared-buffer alpha values for better load balancing (EX4650 and
•
QFX5120 switches)—Theseswitches achieve load balancing through use of a hashing algorithm, which
determines how to forward traffic over LAG bundles or to next-hop devices when ECMP is enabled.
The hashing algorithm makes hashing decisions based on values in various packet fields. Starting with
Junos OS Release 19.3R1, you can explicitly configure some hashing parameters to make hashing more
efficient. The shared-buffer pool is a global memory space that all ports on the switch share dynamically
as they need buffers. The switch uses the shared-buffer pool to absorb traffic bursts after the
dedicated-buffer pool is exhausted. The shared-buffer pool threshold is dynamically calculated based
on a factor called alpha.Also starting with Junos OS Release 19.3R1, you can specify the alpha, or
dynamic threshold, value to determine the change threshold of shared buffer pools for both ingress and
egress buffer partitions.
To specify hashing parameters:
user@switch# set forwarding-options enhanced-hash-key hash-parameters (ecmp | lag)
To specify a threshold value for a particular queue:
Page 39

user@switch# set class-of-service shared-buffer (ingress|egress) buffer-partition buffer
dynamic-threshold value
[See hash-parameters and buffer-partition.]
Interfaces and Chassis
Power over Ethernet IEEE 802.3bt (EX4300-48MP switches)—The IEEE 802.3bt standard for Power
•
over Ethernet (PoE) is supported on EX4300-48MP switches. The IEEE 802.3bt standard enables delivery
of up to 90 W over all four pairs of wire in a standard RJ-45 Ethernet cable.
[See Understanding PoE on EX Series Switches.]
Junos Telemetry Interface
JTI support extended for Junos kernelGRES and RTSOCK(EX9200, EX9251, EX9253, MX240, MX480,
•
MX960, MX2010, MX2020, vMX, PTX1000, PTX10008, PTX10016, PTX3000 with RE-PTX-X8-64G,
and PTX5000 with RE-PTX-X8-64G)—Starting in Junos OS Release 19.3R1, Junos telemetry interface
(JTI) extends support for streaming Junos kernel graceful Routing Engine switchover (GRES) and routing
socket (RTSOCK) information using remote procedure call (gRPC) services. Junos kernel sensors can be
used by device monitoring and network analytics applications to provide insight into the health status
of the Junos kernel.
37
You can use the following base resource paths for exporting kernel GRES and routing socket information:
/junos/chassis/gres/
•
/junos/kernel/rtsock/
•
[See Understanding OpenConfig and gRPC on Junos Telemetry Interface and Guidelines for gRPC Sensors
(Junos Telemetry Interface).]
JTI support extended for Junos kernel LAG, NSR, and TCP (EX9200, EX9251, EX9253, MX240, MX480,
•
MX960, MX2010, MX2020, vMX, PTX1000, PTX10008, PTX10016, PTX3000 with RE-PTX-X8-64G,
PTX5000 with RE-PTX-X8-64G)—Starting in Junos OS Release 19.3R1, Junos Telemetry Interface (JTI)
extends support for streaming Junos kernel Link Aggregation Group (LAG), nonstop Routing (NSR) Junos
socket replication (JSR), and Transport Control Protocol (TCP) information using remote procedure call
(gRPC) services. Device monitoring and network analytics applications can use Junos kernel sensors to
provide insight into the health status of the Junos kernel.
You can use the following base resource paths for exporting kernel LAG, NSR, and TCP information:
/junos/chassis/aggregated-devices/
•
/junos/routing-options/nonstop-routing/
•
/junos/kernel/tcpip/tcp/
•
Page 40

[See Understanding OpenConfig and gRPC on Junos Telemetry Interface and Guidelines for gRPC Sensors
(Junos Telemetry Interface).]
JTI support extended for Junos kernel IPv4 and IPv6 (EX9200, EX9251, EX9253, MX240, MX480,
•
MX960, MX2010, MX2020, vMX, PTX1000, PTX10008, PTX10016, PTX3000 with RE-PTX-X8-64G,
and PTX5000 with RE-PTX-X8-64G)—Starting in Junos OS Release 19.3R1, Junos telemetry interface
(JTI) extends support for streaming Junos kernel IPv4 and IPv6 information using remote procedure call
(gRPC) services. Device monitoring and network analytics applications can use Junos kernel sensors to
provide insight into the health status of the Junos kernel.
You can use the following base resource paths for exporting kernel IPv4 and IPv6 information:
/junos/kernel/tcpip/arp/ — Address Resolution Protocol cache
•
/junos/kernel/tcpip/ndp/ — Neighbor Discovery Protocol cache
•
/junos/kernel/tcpip/netisr/ — NETISR network queues
•
/junos/kernel/tcpip/nhdix/ — Next-hop index space exhaustion
•
/junos/kernel/tcpip/rtb/ — Route tables
•
38
[See Understanding OpenConfig and gRPC on Junos Telemetry Interface and Guidelines for gRPC Sensors
(Junos Telemetry Interface).]
JTI support extended for Junos kernel IP multicast, tunnels, TNP, and VPLS (EX9200, EX9251, EX9253,
•
MX240, MX480, MX960, MX2010, MX2020, vMX, PTX1000, PTX10008, PTX10016, PTX3000 with
RE-PTX-X8-64G, PTX5000 with RE-PTX-X8-64G)—Starting in Junos OS Release 19.3R1, Junos telemetry
interface (JTI) extends support for streaming Junos kernel IP multicast, tunnels, Trivial Network Protocol
(TNP), and virtual private LAN service (VPLS) information using remote procedure call (gRPC) services.
Device monitoring and network analytics applications can use Junos kernel sensors to provide insight
into the health status of the Junos kernel.
You can use the following base resource paths for exporting kernel IP multicast, tunnels, TNP, and VPLS
information:
/junos/kernel/multicast/
•
/junos/kernel/tunnel/
•
/junos/kernel/tnp/
•
/junos/kernel/vpls/
•
[See Understanding OpenConfig and gRPC on Junos Telemetry Interface and Guidelines for gRPC Sensors
(Junos Telemetry Interface).]
Page 41

Layer 2 Features
Configuring Q-in-Q tagging behavior for the native VLAN (EX4300 and EX4300-MP switches and
•
Virtual Chassis)—Starting in Junos OS Release 19.3R1, when Q-in-Q tunneling is configured and an
untagged packet is received on a C-VLAN interface, you can configure these switches to add either one
or two tags before sending the packet out of the S-VLAN interface. To send two tags, set the configuration
statement input-native-vlan-push to “enable” and ensure that the input-vlan-map configuration is set to
“push”.
[See Configuring Q-in-Q Tunneling and VLAN Q-in-Q Tunneling and VLAN Translations.]
Management
OpenConfig AAA data model support (ACX1100, ACX2100, ACX5448, ACX6360, EX4300, MX240,
•
MX480, MX960, MX10003, PTX10008, PTX10016, QFX5110, and QFX10002)—Junos OS Release
19.3R1 supports the configuration leafs specified in the OpenConfig AAA data model. Mapping the
OpenConfig AAA configuration to the Junos AAA configuration using the following YANG files in the
data model makes this support possible:
39
openconfig-aaa.yang
•
openconfig-aaa-types.yang
•
openconfig-aaa-tacacs.yang
•
openconfig-aaa-radius.yang
•
The configuration model supporting the OpenConfig data model includes:
A translation script (.py / .slax) that maps each config leaf in the OpenConfig Schema to one or more
•
config leafs in the JUNOS Schema.
A deviation file (.yang) that specifies how much the implementation deviates from the vendor-neutral
•
model.
Page 42

[See Mapping OpenConfig AAA Commands to Junos Configuration.]
Multicast
MLDv1, MLDv2, and MLD snooping (EX4650 and QFX5120-48Y switches and Virtual Chassis)—Starting
•
in Junos OS Release 19.3R1, you can configure Multicast Listener Discovery (MLD) version 1 (MLDv1),
MLD version 2 (MLDv2), and MLD snooping on EX4650 and QFX5120-48Y switches and Virtual Chassis.
With MLD snooping enabled, these switches or Virtual Chassis replicate and forward IPv6 traffic for a
multicast group only to the interfaces in a VLAN with listeners who joined the group, rather than flooding
to all interfaces in the VLAN.
[See Examples: Configuring MLD and Understanding MLD Snooping.]
Routing Policy and Firewall Filters
Support for IPv6 filter-based forwarding (EX4650 and QFX5120 switches)—Startingwith Junos OS
•
Release 19.3R1, you can use stateless firewall filters in conjunction with filters and routing instances to
control how IPv6 traffic travels in a network on EX4650 and QFX5120 switches. This is called IPv6
filter-based forwarding. To set up this feature, you define a filtering term that matches incoming packets
based on the source or destination address and then specify the routing instance to send packets to.
You can use filter-based forwarding to route specific types of traffic through a firewall or security device
before the traffic continues on its path. You can also use it to give certain types of traffic preferential
treatment or to improve load balancing of switch traffic.
40
[See Firewall Filter Match Conditions for IPv6 Traffic and Filter-Based Forwarding Overview.]
Routing Protocols
RIPng routing protocol supported (EX4650 and QFX5120 switches)—Starting with Junos OS Release
•
19.3R1, EX4650 and QFX5120 switches support the RIPng routing protocol.
[See Basic RIPng Configuration.]
Services Applications
Support for real-time performance monitoring or RPM (EX4650)—Starting in Junos OS Release 19.3R1,
•
you can configure active probes to track and monitor traffic across the network and to investigate
network problems on EX4650 switches.
You can use RPM in the following ways:
Monitor time delays between devices.
•
Monitor time delays at the protocol level.
•
Page 43

Set thresholds to trigger SNMP traps when values are exceeded.
•
You can configure thresholds for round-trip time, ingress or egress delay, standard deviation, jitter,
successive lost probes, and total lost probes per test.
Determine automatically whether a path exists between a host router or switch and its configured
•
BGP neighbors. You can view the results of the discovery using an SNMP client.
Use the history of the most recent 50 probes to analyze trends in your network and predict future
•
needs.
[See Understanding Real-Time Performance Monitoring on Switches.]
Software Installation and Upgrade
Migration of Linux kernel version—Starting in Junos OS Release 19.3R1, the following devices support
•
the Wind River Linux 9 (WRL9) kernel version:
Routing Engine SupportedPlatforms
41
RE-ACX-5448ACX5448-D
RE-S-X6-64GMX240, MX480, and MX960
REMX2K-X8-64GMX2020 and MX2010
RE-S-1600x8MX204
RE-S-1600x8MX10003
RE-MX2008-X8-64GMX2008
RE X10MX10016
RE X10MX10008
RE-PTX-X8-64GPTX5000
RCBPTXPTX3000
RE-PTX-2X00x4/RE X10PTX10016
RE-PTX-2X00x4/RE X10PTX10008
RE-PTX1000PTX1000
Page 44

42
Routing Engine SupportedPlatforms
RE-PTX10002-60CPTX10002-XX
RE-S-EX9200-2X00x6EX9208
EX9251-REEX9251
EX9253-REEX9253
RE-S-EX9200-2X00x6EX9204
RE-S-EX9200-2X00x6EX9214
RE-QFX10002-60CQFX10002
RE-QFX10008QFX10008
RE-QFX10016QFX10016
Starting in Junos OS Release 19.3R1, in order to install a VM host image based on Wind River Linux 9,
you must upgrade the i40e NVM firmware on the following routers:
MX Series—MX240, MX480, MX960, MX2010, MX2020, MX2008, MX10016, and MX10008
•
PTX Series—PTX3000, PTX5000, PTX10016, PTX10008, and PTX10002-XX
•
If you perform a software upgrade on a router with i40e NVM version earlier than 6.01, the upgrade
fails and the following error message is displayed:
ERROR: i40e NVM firmware is not compatible ,please upgrade i40e NVM beforeinstalling this package
ERROR: Aborting the installation
ERROR: Upgrade failed
See [https://kb.juniper.net/TSB17603.]
Virtual Chassis
Virtual Chassis support (EX4650 and QFX5120-48Y switches)—Starting in Junos OS Release 19.3R1,
•
you can interconnect two EX4650 or two QFX5120-48Y switches into a Virtual Chassis, which operates
as one logical device managed as a single chassis.
Member switches must be two EX4650 or two QFX5120 switches (no mixed mode).
•
Both member switches take the Routing Engine role with one as master and one as backup.
•
Page 45

You can use any of the 100-Gbps QSFP28 or 40-Gbps QSFP+ ports on the front panel (ports 48
•
through 55) as Virtual Chassis ports (VCPs) to connect the member switches.
You can run nonstop software upgrade (NSSU) to update the Junos OS release on both member
•
switches with minimal traffic disruption during the upgrade.
EX4650 and QFX5120 Virtual Chassis support the same protocols and features as the standalone
•
switches in Junos OS Release 19.3R1 except for the following:
IEEE 802.1X authentication
•
EVPN-VXLAN (QFX5120)
•
Layer 2 port security features, DHCP, and DHCP snooping
•
Junos telemetry interface (JTI)
•
MPLS
•
Multichassis link aggregation (MC-LAG)
•
Redundant trunk groups (RTG)
•
43
Priority-based flow control (PFC)
•
Configuration parameters and operation are the same as for other non-mixed EX Series and QFX Series
Virtual Chassis.
[See Virtual Chassis Overview for Switches.]
SEE ALSO
What's Changed | 44
Known Limitations | 46
Open Issues | 48
Resolved Issues | 51
Documentation Updates | 57
Migration, Upgrade, and Downgrade Instructions | 57
Page 46

What's Changed
IN THIS SECTION
General Routing | 44
Interfaces and Chassis | 45
Junos OS XML API and Scripting | 45
Layer 2 Features | 45
System Logging | 45
See what changed in this release for EX Series.
44
General Routing
Enhancement to the show interfaces mc-ae extensive command—You can now view additional LACP
•
information about the LACP partner system ID when you run the show interfaces mc-ae extensive
command. The output now displays the following two additional fields:
Local Partner System ID?LACP partner system ID as seen by the local node.
•
Peer Partner System ID?LACP partner system ID as seen by the MC-AE peer node.
•
Previously, the show interfaces mc-ae extensive command did not display these additional fields.
Page 47

See [show interfaces mc-ae.].
Interfaces and Chassis
Support for creating Layer 2 logical interfaces independently (EX Series)—In Junos OS Release 19.3R1
•
and later, EX Series switches support creating Layer 2 logical interfaces independent of the Layer 2
routing instance type. That is, you can configure and commit the Layer 2 logical interfaces separately
and add the interfaces to the bridge domain or EVPN routing instance separately. Note that the Layer
2 logical interfaces work fine when they are added to the bridge domain or EVPN routing instance.
In the earlier Junos OS releases, when a Layer 2 logical interface configuration (units with encapsulation
vlan-bridge configuration) is used, then the logical interface must be added as part of a bridge domain
or EVPN routing instance for the commit to succeed.
Junos OS XML API and Scripting
Range defined for confirm-timeout value in NETCONF and Junos XML protocol sessions (ACX Series,
•
EX Series, MX Series, PTX Series, QFX Series, and SRX Series)—Starting in Junos OS Release 19.3R1,
the value for the <confirm-timeout> element in the Junos XML protocol <commit-configuration>
operation must be in the range 1 through 65,535 minutes, and the value for the <confirm-timeout>
element in the NETCONF <commit> operation must be in the range 1 through 4,294,967,295 seconds.
In earlier releases, the range is determined by the minimum and maximum value of its unsigned integer
data type.
45
Layer 2 Features
input-native-vlan-push (EX2300, EX3400, EX4600, EX4650, and the QFX5000 line of switches)—From
•
Junos OS Release 19.3R1, the configuration statement input-native-vlan-push at the [edit interfaces
interface-name] hierarchy level is introduced. You can use this statement in a Q-in-Q tunneling
configuration to enable or disable whether the switch inserts a native VLAN identifier in untagged frames
received on the C-VLAN interface, when the configuration statement input-vlan-map with a push
operation is configured.
[See input-native-vlan-push.]
System Logging
Page 48

Preventing system instability during core file generation (EX Series)—Starting with Release 19.3R1
•
onward, Junos OS checks for available storage space on the Routing Engine before generating core files
either on request or because of an assertion condition. This check ensures that your device does not
become unstable because of shortage of storage space on the Routing Engine. If the available space is
not sufficient, core files are not generated. Instead, Junos OS either displays the Insufficient Disk space
!!! Core generation skipped message as an output or issues the syslog message core generation is skipped
due to disk full.
SEE ALSO
What's New | 33
Known Limitations | 46
Open Issues | 48
Resolved Issues | 51
Documentation Updates | 57
46
Migration, Upgrade, and Downgrade Instructions | 57
Known Limitations
IN THIS SECTION
EVPN | 47
Infrastructure | 47
Platform and Infrastructure | 47
Learn about known limitations in this release for EX Series. For the most complete and latest information
about known Junos OS defects, use the Juniper Networks online Junos Problem Report Search application.
Page 49

EVPN
When a VLAN uses an IRB interface as the routing interface, the vlan-id parameter must be set to none
•
to ensure proper traffic routing. This issue is platform-independent. PR1287557
Infrastructure
The Data Carrier Detect (DCD) modem control signal is not implemented in the UART driver for EX3400
•
and EX2300 platforms. Hence, the log-out-on-disconnect feature is not functional on these platforms.
PR1351906
Platform and Infrastructure
During sw upgrade to a more recent 19.3 images system hung right after the command "request system
•
software add /var/tmp/ <image.gz> was issued.Device could be recovered by power cycling the device.
PR1405629
47
When the box is loaded and unloaded with the macsec configuration multiple times with operations
•
made continuously, Layer 3 connectivity is lost and hence halts the system followed by a reboot to
resume operation. PR1416499
On deactivating and activating poe, the poe interfaces draws more power (as per display) for quite some
•
time. PR1431647
Filters are installed only during route add if there is enough space. If it fails due to nonavailability of
•
TCAM space, those routes will not be processed for filter add later when space becomes available.
PR1419926
The set class-of-service shared-buffer ingress buffer-partition lossless-headroom percent 0 is not
•
supported when in a Virtual Chassis (VC), as the VCP ports should have some headroom to support PFC.
Configuration will be rejected at the HW layer with a log message. PR1448377
SEE ALSO
What's New | 33
What's Changed | 44
Open Issues | 48
Resolved Issues | 51
Documentation Updates | 57
Migration, Upgrade, and Downgrade Instructions | 57
Page 50

Open Issues
IN THIS SECTION
Authentication and Access Control | 48
Infrastructure | 48
Interfaces and Chassis | 49
J-Web | 49
Network Management and Monitoring | 49
Platform and Infrastructure | 49
Routing Protocols | 50
48
Learn about open issues in this release for EX Series. For the most complete and latest information about
known Junos OS defects, use the Juniper Networks online Junos Problem Report Search application.
Authentication and Access Control
On EX Series switches except EX4300, EX4600, and EX9200, the Link Layer Discovery Protocol (LLDP)
•
core files might be seen when the LLDP neighbor gets expired. The impact is that all the information
gathered through LLDP will be affected. (For example, MAC address and physical layer information,
power information, and so on.) PR1408707
Infrastructure
On EX3400 and EX2300 during ZTP with configuration and image upgrade with FTP as file transfer,
•
image upgrade is successful but sometimes VM core files are observed. PR1377721
On EX Series platforms, if configuring large-scale number of firewall filters on some interfaces, an FPC
•
crash with core files might be seen. PR1434927
On EX2300 and EX3400 platforms, the recovery snapshot might not be created after a system zeroize.
•
This is due to certain hardware space limitation over time where there is not enough space to save the
full snapshot. PR1439189
EX3400 may go a reset with vmcore by panic. This is extremely a rare case. root@ex3400> show system
•
core-dumps no-forwarding -rw-r--r-- 1 root wheel 283194368 Jan 1 1970 /var/crash/vmcore.direct.
PR1456668
Page 51

Interfaces and Chassis
After GRES, the VSTP port cost on aggregated Ethernet interfaces might get changed, leading to a
•
topology change. PR1174213
VRRP-V6 state is flapping with init and idle states after configuring vlan-tagging. PR1445370
•
J-Web
When J-Web is used, if log into J-Web and navigate to multiple pages frequently, some error messages
•
would be seen. It has no impact to service or traffic. This affects only J-Web UI. PR1446081
Network Management and Monitoring
On EX Series switches except EX4300, EX4600, EX9200, when RTG (redundant trunk group) switchovers
•
are done, then the /var/log/shadow.log or /var/log/shadow_debug.log is rotated. It might also cause
Packet Forwarding Engine process to crash. PR1233050
49
Platform and Infrastructure
ARP queue limit has been changed from 100 pps to 3000 pps. PR1165757
•
A few XE interfaces are going down with error if_msg_ifd_cmd_tlv_decode ifd xe-0/0/0 #190 down
•
with ASIC Error. PR1377840
There are multiple failures when a events such as node reboots, ICL flaps and ICCP flaps occur even
•
with enhanced convergence configured. There is no guarantee that subsecond convergence will be
achieved. PR1371493
Traffic loss is observed if ingress and egress ports are in different FPCs. PR1429714
•
There is a possibility of seeing multiple reconnect logs, JTASK_IO_CONNECT_FAILED during the device
•
initialization. There is no functionality impact due to these messages. These messages can be ignored.
PR1408995
Unicast RPF check in strict mode does not work properly. PR1417546
•
There is a IPC sequence issue when VC member rebooted in aggregated interface. After reboot VC
•
member, RE kernel inject mac entry to fpc. Because of IPC sequence issue, RE added mac entry, originally
source mac entry, is added to fpc as remote mac entry. And entry is never be aged out because it is
remote entry. PR1440574
The time it takes to install/delete IPv4/Pv6 routes into the FIB is slowed down in Junos OS Release
•
19.3. Analysis shows that rpd learning rates are not degraded but RIB to FIB download rate is degraded.
PR1441737
Page 52

BUM traffic rate limiting done after removing Ethernet headers. L1 TX rate on ingress interface: 1G Tx
•
rate with headers: 865Mbps Rx rate on the egress interface:800M L1 RX rate on egress interface:
925Mbps Storm control functionalities in MX-L card is achieved by poilcer and hence the below mentioned
policer inaccuracy is applicable for storm control feature as well. The below is mentioned in the FS clearly.
Policer inaccuracy ?Since XM sprays packets to 4 different LUs, each LU will be processing packets of
varying sizes. XM does not do strict round-robin, so even if all the incoming packets were to be of exact
same sizes (which is not a practical scenario), each LU will still be loaded differently, hence there will be
some periods where some LUs policing limit may reach sooner than the others (either due to processing
more packets or due to processing larger packets). Hence, it is possible that, some LUs, who see the
policing limit reached sooner may drop the packet or color them differently that might result into eventual
drop while the other LUs could queue the packets for transmission; We could see this behavior within
a single flow as well. Hence the policier functionality can be unpredictable at times. In an extreme case,
a packet flow may be sent to a single LU and the policer result is 1/4th of what it is expected. Since the
policer functionality, in general, may not work correctly, we will see the impact on all the policing features
e.g. input-policer, three-color-policer (srTCM, trTCM), output-policer. PR1442842
EX9208: : 33% degradation with Mac learning rate in Junos OS Release 19.3R1 while comparing with
•
Junos OS Release 18.4R1. PR1450729
50
EX9208 - L2ald and eventd are overusing 100% after issuing clear ethernet-switching and also observed
•
the continuous syslog errors: l2ald[18605]: L2ALD_IPC_MESSAGE_INVALID: Invalid message received
(message type 0, subtype 0): null message. PR1452738
The VLAN specific parameters might not be used if configuring VLAN all option and VLAN specific
•
configuration. PR1453505
Syslog "timeout connecting to peer database-replication" is generated when command "show version
•
detail" issued. PR1457284
Routing Protocols
QFX5100 : BGP v4/v6 convergence & RIB install/delete time degraded in Junos OS Releases 19.1R1,
•
19.2R1, 19.3R1, and 19.4R1. PR1414121
In the scenario where BFD session authentication is configured, after a certain period of time, BFD
•
sessions flaps may be seen, this will cause the neighbor to be down. PR1448649
SEE ALSO
What's New | 33
What's Changed | 44
Known Limitations | 46
Page 53

Resolved Issues | 51
Documentation Updates | 57
Migration, Upgrade, and Downgrade Instructions | 57
Resolved Issues
IN THIS SECTION
EVPN | 51
Forwarding and Sampling | 52
Infrastructure | 52
Interfaces and Chassis | 52
Layer 2 Ethernet Services | 52
51
Network Management and Monitoring | 52
Platform and Infrastructure | 52
Routing Protocols | 56
Subscriber Access Management | 56
User Interface and Configuration | 56
Virtual Chassis | 56
VPNs | 56
This section lists the issues fixed in Junos OS Release 19.3R1 for the EX Series.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
EVPN
The device may proxy the ARP probe packets in an EVPN environment. PR1427109
•
Configuring ESI on a single-homed 25-Gbps port might not work. PR1438227
•
Page 54

Forwarding and Sampling
Enable interface with input/output vlan-maps to be added to a routing-instance configured with a VLAN
•
ID or VLAN tags (instance type virtual-switch/vpls). PR1433542
Infrastructure
The traffic to the NLB server may not be forwarded if the NLB cluster works in multicast mode.
•
PR1411549
The operations on the console might not work if the system ports console log-out-on-disconnect
•
statement is configured. PR1433224
Interfaces and Chassis
Missing mandatory ICCP configuration statement redundancy-group-id-list produces misleading error
•
message. PR1402606
52
The IFLs in EVPN routing instances might flap after committing configurations. PR1425339
•
EX9214 unexpected duplicate VLAN-ID commit error. PR1430966
•
Layer 2 Ethernet Services
DHCP request may get dropped in DHCP relay scenario. PR1435039
•
On EX9200 switches, DHCP Relay is stripping the 'GIADDR' field in messages toward the DHCP clients.
•
PR1443516
Network Management and Monitoring
Overtemperature trap does not sent out even though there is the Temperature Hot alarm. PR1412161
•
Platform and Infrastructure
[SIRT]Certain QFX and EX Series devices are vulnerable to 'Etherleak' memory disclosure in Ethernet
•
padding data (CVE-2017-2304). PR1063645
Transit OSPF traffic over Q-in-Q tunneling might be dropped if a firewall filter is applied to Lo0 interface.
•
PR1355111
The l2ald process might crash and generate a core file on EX2300 Virtual Chassis when a trunk port is
•
converted to dot1x access port with tagged traffic flowing. PR1362587
Page 55

QFX5120 and EX4650 : Convergence delay between PE1 and P router link is more than expected delay
•
value. PR1364244
IPv6 router advertisement (RA) messages might increase internal kernel memory usage. PR1369638
•
The DHCP discover packets are forwarded out of an interface incorrectly if DHCP snooping is configured
•
on that interface. PR1403528
MAC address movement might not happen in Flexible Ethernet Services mode when family inet/inet6
•
and vlan-bridge are configured on the same IFD. PR1408230
EX9251, EX9253, and EX9208: DDoS violation for LLDP, MVRP, provider MVRP and dot1x is incorrectly
•
reported as LACP DDoS violation. PR1409626
EX2300-24P, error message: dc-pfe: BRCM_NH-,brcm_nh_resolve_get_nexthop(),346:Failed to find if
•
family. PR1410717
EX4300-48MP : Chassis Status LED glow yellow instead of amber. PR1413194
•
The upgrade of the PoE firmware might fail on EX3400. PR1413802
•
EX3400 : show chassis environment repeats "OK" and "Failed" at short intervals. PR1417839
•
53
The EX3400 Virtual Chassis status might be unstable during the bootup of the Virtual Chassis or after
•
the Virtual Chassis port flaps. PR1418490
EX4300-48MP-18.3R1.9 //Over Temperature SNMP trap generated wrongky for LC (EX4300-48P)
•
based on the master Routing Engine (EX4300-48MP) temperature threshold value. PR1419300
EX4300: Runt counter never incremented. PR1419724
•
The pfex process might crash and generates core files when you reinsert SFP. PR1421257
•
Commit of configurations involving interface-range defined over wildcard range such as ge-*/*/* not
•
supported. PR1421446
Virtual Chassis may become unstable and FXPC core files may be generated when there are a lot of
•
configured filter entries. PR1422132
Traffic loss when one of the logical interfaces on the LAG is deactivated or deleted. PR1422920
•
Ensure phone-home works in factory-default configuration. PR1423015
•
Adding the second IRB interface to an aggregated Ethernet interface and rolling it back might cause the
•
first IRB interface to stop working. PR1423106
IPv6 multicast traffic received on one Virtual Chassis member might be dropped when egressing on
•
other Virtual Chassis member if MLD snooping is enabled. PR1423310
EX3400 : Auto negotiation status shows incomplete on ge-0/2/0 using SFP-SX. PR1423469
•
Multicast traffic might be silently dropped on ingress port with igmp-snooping enabled. PR1423556
•
MACsec connection on EX4600 platforms might not come back up after interface disconnect/reconnect.
•
PR1423597
Page 56

On MX204 optics "SFP-1GE-FE-E-T" I2C read errors are seen when an SFP-T is inserted into a disabled
•
state port. PR1423858
The auditd crashed when Accounting RADIUS server was not reachable. PR1424030
•
The native VLAN ID of packets might fail to be removed when leaving out. PR1424174
•
MAC overlapping between different switches. PR1425123
•
SNMP (ifHighSpeed) value is not getting displayed appear properly only for VCP interfaces, it is getting
•
displayed as zero. PR1425167
The jdhcpd might consume 100% CPU and crash if dhcp-security is configured. PR1425206
•
Interface flapping scenario might lead to ECMP next-hop installation failure on EX4300s. PR1426760
•
Virtual Chassis split after network topology changed. PR1427075
•
The fxpc/Packet Forwarding Engine might crash on EX2300 or EX3400 platforms. PR1427391
•
Rebooting or halting a Virtual Chassis member might cause 30 seconds down on RTG link. PR1427500
•
IPv6 traffic might be dropped when static /64 IPv6 routes are configured. PR1427866
•
54
VIP might not forward the traffic if VRRP is configured on an aggregated Ethernet interface. PR1428124
•
EX2300-24P : l2ald core files observed after removal and re-addition of multiple supplicant mode with
•
PVLAN on interface. PR1428469
Data port LEDs are off even while interfaces are up. PR1428703
•
CI-PR: Verification of ND inspection with a dynamically bound client, moved to a different VLAN on the
•
same port is failing. PR1428769
The delay in transmission of BPDUs after GRES might result in loss of traffic on EX2300/3400 Virtual
•
Chassis. PR1428935
When forward-only is set within dhcp-reply, dhcp declines are not forwarded to server. PR1429456
•
EX4300 does not drop FCS frames with CRC error on xe- interfaces. PR1429865
•
Unicast ARP requests are not replied to with the no-arp-trap option. PR1429964
•
EX4300 without soft error recovery(parity check, correction and memscan) enable. PR1430079
•
The jdhcpd_era log files constantly consume 121M of space out of 170M, resulting into file system full
•
and traffic impact. PR1431201
EX4300-48MP switch cannot learn MAC address through some access ports that are directly connected
•
to a host when auto-negotiation is used. PR1430109
Disabling DAC QSFP port may not work on MX204, MX10003, or EX9251. PR1430921
•
Incorrect model Information while polling through SNMP from Virtual-Chassis. PR1431135
•
The ERPS failover does not work as expected on an EX4300 device. PR1432397
•
Page 57

Native VLAN might not take into effect when it is enabled with flexible VLAN tagging on a Layer 3
•
subinterface. PR1434646
The device might not be accessible after the upgrade. PR1435173
•
The mc-ae interface may get stuck in waiting state in a dual mc-ae scenario. PR1435874
•
i40e NVM upgrade support for EX9200 platform. PR1436223
•
The FPC/pfex crash may be observed due to DMA buffer leaking. PR1436642
•
The /var/db/scripts directory might be deleted after executing request system zeroize. PR1436773
•
Commit check error for VSTP on EX9200s: xSTP:Trying to configure too many interfaces for given
•
protocol. PR1438195
The DHCP Snooping table might be cleared for VLAN ID 1 after adding a new VLAN ID to it. PR1438351
•
The dot1x might not work when captive-port is also configured on the interface on backup/non-master
•
FPC. PR1439200
DHCPv6 relay binding is not up while verifying the DHCP snooping along with DHCPv6 relay. PR1439844
•
55
The ports of the EX device might stay in up state even if the EX46XX/QFX51XX series device is rebooted.
•
PR1441035
Clients in an isolated VLAN might not get IP addresses after completing authentication when both
•
dhcp-security and dot1x are configured. PR1442078
EX3400 fan alarm (Fan X not spinning) appears and disappears repeatedly after the fan tray is removed
•
(absent). PR1442134
DHCPv6 client might fail to get an IP address. PR1442867
•
Non-designated port is not moving to backup port role. PR1443489
•
/var/host/motd does not exist message is flooded every 5 seconds in chassisd logs. PR1444903
•
On EX4300-MP, log generated continuously: rpd[6550]: task_connect: task AGENTD I/O.128.0.0.1+9500
•
addr 128.0.0.1+9500: Connection refused. PR1445618
CI-PR: On EX3400 - dot1xd core files found @ macsec_update_intf macsec_destroy_ca. PR1445764
•
Major alarm log messages for temperature conditions for EX4600 at 56 degrees Celsius. PR1446363
•
The traffic might be dropped when a firewall filter rule uses 'then vlan' as the action in a Virtual Chassis
•
scenario. PR1446844
The PoE might not work after upgrading the PoE firmware on EX4300 platforms. PR1446915
•
The firewall filters might not be created with error logs after reboot. PR1447012
•
Phone home on macallan fails because sysctl cannot read the device serial number. PR1447291
•
Added CLI configuration on-disk-failure on EX3400. PR1447853
•
Unicast ARP requests are not replied with the no-arp-trap option. PR1448071
•
Page 58

On EX3400, IPv6 routes received through BGP do not show the correct age time. PR1449305
•
Incoming Layer3-encapsulated packets are dropped on Layer 3VPN MPLS PE-CE interface. PR1451032
•
Routing Protocols
Host-destined packets with filter log action might not reach the Routing Engine if log/syslog is enabled.
•
PR1379718
Sometimes, IGMP snooping may not work. PR1420921
•
The multicast traffic might be dropped when proxy mode is used for igmp-snooping. PR1425621
•
The error message RPD_DYN_CFG_GET_PROF_NAME_FAILED: Get profile name for session XXX
•
failed: -7, may be seen in syslog after restarting routing daemon. PR1439514
The bandwidth value of the DDoS-protection might cause the packets loss after the device reboot.
•
PR1440847
IPv6 connectivity between MC-LAG peers might fail when multiple IRB interfaces are present. PR1443507
•
56
Loopback address exported into other VRF instance might not work on EX Series, QFX Series, or ACX
•
Series platforms. PR1449410
MPLS LDP may still use stale MAC of the neighbor even the LDP neighbor's MAC changes. PR1451217
•
Subscriber Access Management
EX4300 /var showing full /var/log/dfcd_enc file grows in size PR1425000
•
User Interface and Configuration
EX4600 and QFX5100 were unable to commit baseline configuration after zeroization. PR1426341
•
Virtual Chassis
Current MAC address might change when deleting one of the multiple Layer 3 interfaces. PR1449206
•
VPNs
MVPN using PIM dense mode does not prune the OIF when PIM prune is received. PR1425876
•
SEE ALSO
Page 59

What's New | 33
What's Changed | 44
Known Limitations | 46
Open Issues | 48
Documentation Updates | 57
Migration, Upgrade, and Downgrade Instructions | 57
Documentation Updates
There are no errata or changes in Junos OS Release 19.3R1 documentation for the EX Series switches.
SEE ALSO
57
What's New | 33
What's Changed | 44
Known Limitations | 46
Open Issues | 48
Resolved Issues | 51
Migration, Upgrade, and Downgrade Instructions | 57
Migration, Upgrade, and Downgrade Instructions
IN THIS SECTION
Upgrade and Downgrade Support Policy for Junos OS Releases | 58
This section contains the upgrade and downgrade support policy for Junos OS for the EX Series. Upgrading
or downgrading Junos OS can take several hours, depending on the size and configuration of the network.
For information about software installation and upgrade, see the Installation and Upgrade Guide.
Page 60

Upgrade and Downgrade Support Policy for Junos OS Releases
Support for upgrades and downgrades that span more than three Junos OS releases at a time is not
provided, except for releases that are designated as Extended End-of-Life (EEOL) releases. EEOL releases
provide direct upgrade and downgrade paths—you can upgrade directly from one EEOL release to the
next EEOL release even though EEOL releases generally occur in increments beyond three releases.
You can upgrade or downgrade to the EEOL release that occurs directly before or after the currently
installed EEOL release, or to two EEOL releases before or after. For example, Junos OS Releases 17.1,
17.2, and 17.3 are EEOL releases. You can upgrade from Junos OS Release 17.1 to Release 17.2 or from
Junos OS Release 17.1 to Release 17.3.
You cannot upgrade directly from a non-EEOL release to a release that is more than three releases ahead
or behind. To upgrade or downgrade from a non-EEOL release to a release more than three releases before
or after, first upgrade to the next EEOL release and then upgrade or downgrade from that EEOL release
to your target release.
For more information about EEOL releases and to review a list of EEOL releases, see
https://support.juniper.net/support/eol/software/junos/.
58
SEE ALSO
What's New | 33
What's Changed | 44
Known Limitations | 46
Open Issues | 48
Resolved Issues | 51
Documentation Updates | 57
Junos OS Release Notes for Junos Fusion Enterprise
IN THIS SECTION
What’s New | 59
What’s Changed | 60
Known Limitations | 60
Open Issues | 61
Page 61

Resolved Issues | 62
Documentation Updates | 62
Migration, Upgrade, and Downgrade Instructions | 63
These release notes accompany Junos OS Release 19.3R1 for Junos Fusion Enterprise. Junos Fusion
Enterprise is a Junos Fusion that uses EX9200 switches in the aggregation device role. These release notes
describe new and changed features, limitations, and known problems in the hardware and software.
NOTE: For a complete list of all hardware and software requirements for a Junos Fusion
Enterprise, including which Juniper Networks devices can function as satellite devices, see
Understanding Junos Fusion Enterprise Software and Hardware Requirements .
59
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What’s New
There are no new features or enhancements to existing features in Junos OS Release 19.3R1 for Junos
fusion for enterprise.
NOTE: For more information about the Junos Fusion Enterprise features, see the Junos Fusion
Enterprise User Guide.
SEE ALSO
What’s Changed | 60
Known Limitations | 60
Known Issues | 61
Resolved Issues | 62
Documentation Updates | 62
Page 62

Migration, Upgrade, and Downgrade Instructions | 63
What’s Changed
There are no changes in behavior of Junos OS features and changes in the syntax of Junos OS statements
and commands in Junos OS Release 19.3R1 for Junos fusion for enterprise.
SEE ALSO
What’s New | 59
Known Limitations | 60
Known Issues | 61
Resolved Issues | 62
60
Documentation Updates | 62
Migration, Upgrade, and Downgrade Instructions | 63
Known Limitations
There are no known behaviors, system maximums, and limitations in hardware and software in Junos OS
Release 19.3R1 for Junos fusion for enterprise.
For the most complete and latest information about known Junos OS problems, use the Juniper Networks
online Junos Problem Report Search application.
SEE ALSO
What’s New | 59
What’s Changed | 60
Known Issues | 61
Resolved Issues | 62
Documentation Updates | 62
Migration, Upgrade, and Downgrade Instructions | 63
Page 63

Open Issues
IN THIS SECTION
Junos Fusion for Enterprise | 61
Learn about open issues in this release for Junos fusion for enterprise. For the most complete and latest
information about known Junos OS defects, use the Juniper Networks online Junos Problem Report Search
application.
Junos Fusion for Enterprise
On EX4300 when 10G fiber port is using 1G Ethernet SFP optics, auto-negotiation is enabled by default.
•
To bring up the satellite device, BCM recommends to disable the auto-negotiation for PHY84756 ports.
PR1420343
61
In a Junos fusion for enterprise environment with EX2300-48P or EX2300-48T acting as satellite devices,
•
loop-detect feature does not work for ports 0-23, since the loop detect filter is not properly applied.
PR1426757
In a Junos fusion for enterprise environment, when traffic originates from a peer device connected to
•
the aggregation device and the ICL is a LAG, there might be a reachability issue if the cascade port is
disabled and traffic has to flow through the ICL LAG to reach the satellite device. As a workaround, use
single interface as the ICL instead of a LAG. PR1447873
SEE ALSO
What’s New | 59
What’s Changed | 60
Known Limitations | 60
Resolved Issues | 62
Documentation Updates | 62
Migration, Upgrade, and Downgrade Instructions | 63
Page 64

Resolved Issues
IN THIS SECTION
Resolved Issues: 19.3R1 | 62
This section lists the issues fixed in Junos OS Release 19.3R1.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
Resolved Issues: 19.3R1
62
Traffic might be dropped in Junos Fusion Enterprise scenario with dual aggregation devices. PR1417139
•
The 1G SFP in 10G upstream port on EX3400 and EX4300 satellite devices might not come up.
•
PR1420343
The loop-detect feature does not work in Junos Fusion Enterprise. PR1426757
•
SEE ALSO
What’s New | 59
What’s Changed | 60
Known Limitations | 60
Known Issues | 61
Documentation Updates | 62
Migration, Upgrade, and Downgrade Instructions | 63
Documentation Updates
There are no errata or changes in Junos OS Release 19.3R1 for documentation for Junos fusion for
enterprise.
Page 65

SEE ALSO
What’s New | 59
What’s Changed | 60
Known Limitations | 60
Known Issues | 61
Resolved Issues | 62
Migration, Upgrade, and Downgrade Instructions | 63
Migration, Upgrade, and Downgrade Instructions
IN THIS SECTION
63
Basic Procedure for Upgrading Junos OS on an Aggregation Device | 63
Upgrading an Aggregation Device with Redundant Routing Engines | 65
Preparing the Switch for Satellite Device Conversion | 66
Converting a Satellite Device to a Standalone Switch | 67
Upgrade and Downgrade Support Policy for Junos OS Releases | 67
Downgrading from Junos OS | 68
This section contains the procedure to upgrade or downgrade Junos OS and satellite software for a Junos
Fusion Enterprise. Upgrading or downgrading Junos OS and satellite software might take several hours,
depending on the size and configuration of the Junos Fusion Enterprise topology.
Basic Procedure for Upgrading Junos OS on an Aggregation Device
When upgrading or downgrading Junos OS for an aggregation device, always use the junos-install package.
Use other packages (such as the jbundle package) only when so instructed by a Juniper Networks support
representative. For information about the contents of the junos-install package and details of the installation
process, see the Installation and Upgrade Guide.
Page 66

NOTE: Before upgrading, back up the file system and the currently active Junos OS configuration
so that you can recover to a known, stable environment in case the upgrade is unsuccessful.
Issue the following command:
user@host> request system snapshot
The installation process rebuilds the file system and completely reinstalls Junos OS. Configuration
information from the previous software installation is retained, but the contents of log files might
be erased. Stored files on the routing platform, such as configuration templates and shell scripts
(the only exceptions are the juniper.conf and ssh files), might be removed. To preserve the stored
files, copy them to another system before upgrading or downgrading the routing platform. See
the Junos OS Administration Library.
To download and install Junos OS:
64
1. Using a Web browser, navigate to the Download Software URL on the Juniper Networks webpage:
https://www.juniper.net/support/downloads/
2. Log in to the Juniper Networks authentication system using the username (generally your e-mail address)
and password supplied by Juniper Networks representatives.
3. Select By Technology > Junos Platform > Junos Fusion to find the software that you want to download.
4. Select the release number (the number of the software version that you want to download) from the
Version drop-down list on the right of the page.
5. Select the Software tab.
6. Select the software package for the release.
7. Review and accept the End User License Agreement.
8. Download the software to a local host.
9. Copy the software to the routing platform or to your internal software distribution site.
10. Install the new junos-install package on the aggregation device.
Page 67

NOTE: We recommend that you upgrade all software packages out of band using the console
because in-band connections are lost during the upgrade process.
Customers in the United States and Canada, use the following commands:
user@host> request system software add validate reboot source/package.tgz
All other customers, use the following commands, where n is the spin number.
user@host> request system software add validate reboot source/package-limited.tgz
Replace source with one of the following values:
/pathname—For a software package that is installed from a local directory on the router.
•
For software packages that are downloaded and installed from a remote location:
•
65
ftp://hostname/pathname
•
http://hostname/pathname
•
scp://hostname/pathname (available only for Canada and U.S. version)
•
The validate option validates the software package against the current configuration as a prerequisite
to adding the software package to ensure that the router reboots successfully. This is the default
behavior when the software package being added is a different release.
Adding the reboot command reboots the router after the upgrade is validated and installed. When the
reboot is complete, the router displays the login prompt. The loading process might take 5 to 10 minutes.
Rebooting occurs only if the upgrade is successful.
Upgrading an Aggregation Device with Redundant Routing Engines
If the aggregation device has two Routing Engines, perform a Junos OS installation on each Routing Engine
separately to minimize disrupting network operations as follows:
1. Disable graceful Routing Engine switchover (GRES) on the master Routing Engine and save the
configuration change to both Routing Engines.
2. Install the new Junos OS release on the backup Routing Engine while keeping the currently running
software version on the master Routing Engine.
Page 68

3. After making sure that the new software version is running correctly on the backup Routing Engine,
switch over to the backup Routing Engine to activate the new software.
4. Install the new software on the original master Routing Engine that is now active as the backup Routing
Engine.
For the detailed procedure, see the Installation and Upgrade Guide.
Preparing the Switch for Satellite Device Conversion
There are multiple methods to upgrade or downgrade satellite software in your Junos Fusion Enterprise.
See Configuring or Expanding a Junos Fusion Enterprise.
For satellite device hardware and software requirements, see Understanding Junos Fusion Enterprise
Software and Hardware Requirements.
Use the following command to install Junos OS on a switch before converting it into a satellite device:
user@host> request system software add validate reboot source/package-name
66
NOTE: The following conditions must be met before a Junos switch that is running Junos OS
Release 14.1X53-D43 can be converted to a satellite device when the action is initiated from
the aggregation device:
The switch running Junos OS can be converted only to SNOS 3.1 and later.
•
Either the switch must be set to factory-default configuration by using the request system
•
zeroize command, or the following command must be included in the configuration: set chassis
auto-satellite-conversion.
When the interim installation has completed and the switch is running a version of Junos OS that is
compatible with satellite device conversion, perform the following steps:
1. Log in to the device using the console port.
2. Clear the device:
[edit]
user@satellite-device# request system zeroize
NOTE: The device reboots to complete the procedure for resetting the device.
Page 69

If you are not logged in to the device using the console port connection, your connection to the device
is lost after you enter the request system zeroize command.
If you lose connection to the device, log in using the console port.
3. (EX4300 switches only) After the reboot is complete, convert the built-in 40-Gbps QSFP+ interfaces
from Virtual Chassis ports (VCPs) into network ports:
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port port-number
For example, to convert all four built-in 40-Gbps QSFP+ interfaces on an EX4300-24P switch into
network ports:
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 0
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 1
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 2
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 3
67
This step is required for the 40-Gbps QSFP+ interfaces that will be used as uplink interfaces in a Junos
Fusion topology. Built-in 40-Gbps QSFP+ interfaces on EX4300 switches are configured into VCPs by
default, and the default settings are restored after the device is reset.
After this initial preparation, you can use one of three methods to convert your switches into satellite
devices—autoconversion, manual conversion, or preconfiguration. See Configuring or Expanding a Junos
Fusion Enterprise for detailed configuration steps for each method.
Converting a Satellite Device to a Standalone Switch
If you need to convert a satellite device to a standalone device, you must install a new Junos OS software
package on the satellite device and remove it from the Junos Fusion topology. For more information, see
Converting a Satellite Device to a Standalone Device.
Upgrade and Downgrade Support Policy for Junos OS Releases
Support for upgrades and downgrades that span more than three Junos OS releases at a time is not
provided, except for releases that are designated as Extended End-of-Life (EEOL) releases. EEOL releases
provide direct upgrade and downgrade paths—you can upgrade directly from one EEOL release to the
next EEOL release even though EEOL releases generally occur in increments beyond three releases.
You can upgrade or downgrade to the EEOL release that occurs directly before or after the currently
installed EEOL release, or to two EEOL releases before or after. For example, Junos OS Releases 17.1,
17.2, and 17.3 are EEOL releases. You can upgrade from Junos OS Release 17.1 to Release 17.2 or from
Junos OS Release 17.1 to Release 17.3.
Page 70

You cannot upgrade directly from a non-EEOL release to a release that is more than three releases ahead
or behind. To upgrade or downgrade from a non-EEOL release to a release more than three releases before
or after, first upgrade to the next EEOL release and then upgrade or downgrade from that EEOL release
to your target release.
For more information about EEOL releases and to review a list of EEOL releases, see
https://www.juniper.net/support/eol/junos.html
Downgrading from Junos OS
Junos Fusion Enterprise is first supported in Junos OS Release 16.1, although you can downgrade a
standalone EX9200 switch to earlier Junos OS releases.
NOTE: You cannot downgrade more than three releases.
For more information, see the Installation and Upgrade Guide.
68
To downgrade a Junos Fusion Enterprise from Junos OS Release 19.2R1, follow the procedure for upgrading,
but replace the 19.2 junos-install package with one that corresponds to the appropriate release.
SEE ALSO
What’s New | 59
What’s Changed | 60
Known Limitations | 60
Known Issues | 61
Resolved Issues | 62
Documentation Updates | 62
Page 71

Junos OS Release Notes for Junos Fusion Provider Edge
IN THIS SECTION
What's New | 69
What's Changed | 70
Known Limitations | 70
Open Issues | 71
Resolved Issues | 72
Documentation Updates | 73
Migration, Upgrade, and Downgrade Instructions | 73
69
These release notes accompany Junos OS Release 19.3R1 for the Junos Fusion Provider Edge. They
describe new and changed features, limitations, and known and resolved problems in the hardware and
software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What's New
There are no new features or enhancements to existing features for Junos Fusion Provider Edge in Junos
OS Release 19.3R1.
SEE ALSO
What's Changed | 70
Known Limitations | 70
Open Issues | 71
Resolved Issues | 72
Documentation Updates | 73
Page 72

Migration, Upgrade, and Downgrade Instructions | 73
What's Changed
There are no changes in the behavior of Junos OS features or in the syntax of Junos OS statements and
commands in Junos OS Release 19.3R1 for Junos fusion for provider edge.
SEE ALSO
What's New | 69
Known Limitations | 70
Open Issues | 71
Resolved Issues | 72
70
Documentation Updates | 73
Migration, Upgrade, and Downgrade Instructions | 73
Known Limitations
There are no known behaviors, system maximums, or limitations in hardware and software in Junos OS
Release 19.3R1 for Junos Fusion Provider Edge.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
SEE ALSO
What's New | 69
What's Changed | 70
Open Issues | 71
Resolved Issues | 72
Documentation Updates | 73
Migration, Upgrade, and Downgrade Instructions | 73
Page 73

Open Issues
IN THIS SECTION
Junos Fusion Provider Edge | 71
This section lists the Open Issues in hardware and software in Junos OS Release 19.3R1 for Junos Fusion
for provider edge.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
Junos Fusion Provider Edge
71
When the igmp queries are sent out, the igmp membership is not learnt completely by the AD. PR1419265
•
When a few packets transmitted from the egress of AD1 is short of FCS (4 bytes) + 2 bytes of data,
•
traffic drops from SD to AD. This loss is not observed regularly. It is seen that the normal data packets
are of size 128 bytes (4 bytes FCS + 14 bytes Ethernet header + 20 bytes IP header + 90 bytes data)
while the corrupted packet is 122 byte (14 bytes Ethernet header + 20 byte IP HEADER + 88 bytes
data). PR1450373
SEE ALSO
What's New | 69
What's Changed | 70
Known Limitations | 70
Resolved Issues | 72
Documentation Updates | 73
Migration, Upgrade, and Downgrade Instructions | 73
Page 74

Resolved Issues
IN THIS SECTION
Junos Fusion for Provider Edge | 72
This section lists the issues fixed in Junos OS Release 19.3R1 for Junos fusion for provider edge.
For the most complete and latest information about known Junos OS defects, use the Juniper Networks
online Junos Problem Report Search application.
Junos Fusion for Provider Edge
72
Auto-negotiation is not disabled in hardware after setting no-auto-negotiation option in the CLI.
•
PR1411852
Junos fusion: Incorrect power values for extended optical ports. PR1412781
•
The sdpd process may continuously crash if there are more than 12 cascade ports configured to a satellite
•
device. PR1437387
The aggregated Ethernet interface might flap whenever a new logical interface is added to it. PR1441869
•
Deprecate Junos fusion support on QFX10000. PR1448245
•
SEE ALSO
What's New | 69
What's Changed | 70
Known Limitations | 70
Open Issues | 71
Documentation Updates | 73
Migration, Upgrade, and Downgrade Instructions | 73
Page 75

Documentation Updates
There are no errata or changes in Junos OS Release 19.3R1 documentation for Junos fusion for provider
edge.
SEE ALSO
What's New | 69
What's Changed | 70
Known Limitations | 70
Open Issues | 71
Resolved Issues | 72
Migration, Upgrade, and Downgrade Instructions | 73
73
Migration, Upgrade, and Downgrade Instructions
IN THIS SECTION
Basic Procedure for Upgrading an Aggregation Device | 74
Upgrading an Aggregation Device with Redundant Routing Engines | 76
Preparing the Switch for Satellite Device Conversion | 77
Converting a Satellite Device to a Standalone Device | 78
Upgrading an Aggregation Device | 80
Upgrade and Downgrade Support Policy for Junos OS Releases | 81
Downgrading from Junos OS Release 19.3 | 81
This section contains the procedure to upgrade Junos OS, and the upgrade and downgrade policies for
Junos OS for Junos fusion for provider edge. Upgrading or downgrading Junos OS might take several
hours, depending on the size and configuration of the network.
Page 76

Basic Procedure for Upgrading an Aggregation Device
When upgrading or downgrading Junos OS, always use the jinstall package. Use other packages (such as
the jbundle package) only when so instructed by a Juniper Networks support representative. For information
about the contents of the jinstall package and details of the installation process, see the Installation and
Upgrade Guide.
NOTE: Before upgrading, back up the file system and the currently active Junos OS configuration
so that you can recover to a known, stable environment in case the upgrade is unsuccessful.
Issue the following command:
user@host> request system snapshot
The installation process rebuilds the file system and completely reinstalls Junos OS. Configuration
information from the previous software installation is retained, but the contents of log files might
be erased. Stored files on the routing platform, such as configuration templates and shell scripts
(the only exceptions are the juniper.conf and ssh files), might be removed. To preserve the stored
files, copy them to another system before upgrading or downgrading the routing platform. See
the Installation and Upgrade Guide.
74
The download and installation process for Junos OS Release 19.3R1 is different from that for earlier Junos
OS releases.
1. Using a Web browser, navigate to the Download Software URL on the Juniper Networks webpage:
https://www.juniper.net/support/downloads/
2. Log in to the Juniper Networks authentication system by using the username (generally your e-mail
address) and password supplied by Juniper Networks representatives.
3. Select By Technology > Junos Platform > Junos Fusion to find the software that you want to download.
4. Select the release number (the number of the software version that you want to download) from the
Version drop-down list to the right of the page.
5. Select the Software tab.
6. Select the software package for the release.
7. Review and accept the End User License Agreement.
Page 77

8. Download the software to a local host.
9. Copy the software to the routing platform or to your internal software distribution site.
10. Install the new jinstall package on the aggregation device.
NOTE: We recommend that you upgrade all software packages out-of-band using the console,
because in-band connections are lost during the upgrade process.
Customers in the United States and Canada, use the following commands.
For 64-bit software:
•
NOTE: We recommend that you use 64-bit Junos OS software when implementing Junos
Fusion Provider Edge.
75
user@host> request system software add validate reboot
source/jinstall64-19.3R1.SPIN-domestic-signed.tgz
For 32-bit software:
•
user@host> request system software add validate reboot
source/jinstall-19.3R1.SPIN-domestic-signed.tgz
All other customers, use the following commands.
For 64-bit software:
•
NOTE: We recommend that you use 64-bit Junos OS software when implementing Junos
Fusion Provider Edge.
user@host> request system software add validate reboot
source/jinstall64-19.3R1.SPIN-export-signed.tgz
For 32-bit software:
•
user@host> request system software add validate reboot
source/jinstall-19.3R1.SPIN-export-signed.tgz
Page 78

Replace source with one of the following values:
/pathname—For a software package that is installed from a local directory on the router.
•
For software packages that are downloaded and installed from a remote location:
•
ftp://hostname/pathname
•
http://hostname/pathname
•
scp://hostname/pathname (available only for the Canada and U.S. version)
•
The validate option validates the software package against the current configuration as a prerequisite
for adding the software package to ensure that the router reboots successfully. This is the default
behavior when the software package being added is for a different release.
Adding the reboot command reboots the router after the upgrade is validated and installed. When the
reboot is complete, the router displays the login prompt. The loading process might take 5 to 10 minutes.
Rebooting occurs only if the upgrade is successful.
76
NOTE: After you install a Junos OS Release 19.3R1 jinstall package, you cannot return to the
previously installed software by issuing the request system software rollback command. Instead,
you must issue the request system software add validate command and specify the jinstall
package that corresponds to the previously installed software.
Upgrading an Aggregation Device with Redundant Routing Engines
If the aggregation device has two Routing Engines, perform a Junos OS installation on each Routing Engine
separately as follows to minimize disrupting network operations:
1. Disable graceful Routing Engine switchover (GRES) on the master Routing Engine and save the
configuration change to both Routing Engines.
2. Install the new Junos OS release on the backup Routing Engine while keeping the currently running
software version on the master Routing Engine.
3. After making sure that the new software version is running correctly on the backup Routing Engine,
switch over to the backup Routing Engine to activate the new software.
4. Install the new software on the original master Routing Engine that is now active as the backup Routing
Engine.
For the detailed procedure, see the Installation and Upgrade Guide.
Page 79

Preparing the Switch for Satellite Device Conversion
Satellite devices in a Junos fusion topology use a satellite software package that is different from the
standard Junos OS software package. Before you can install the satellite software package on a satellite
device, you first need to upgrade the target satellite device to an interim Junos OS software version that
can be converted to satellite software. For satellite device hardware and software requirements, see
Understanding Junos Fusion Software and Hardware Requirements
NOTE: The following conditions must be met before a standalone switch that is running Junos
OS Release 14.1X53-D43 can be converted to a satellite device when the action is initiated from
the aggregation device:
The switch can be converted to only SNOS 3.1 and later.
•
Either the switch must be set to factory-default configuration by using the request system
•
zeroize command, or the following command must be included in the configuration: set chassis
auto-satellite-conversion.
77
Customers with EX4300 switches, use the following command:
user@host> request system software add validate reboot
source/jinstall-ex-4300-14.1X53-D43.3-domestic-signed.tgz
Customers with QFX5100 switches, use the following command:
user@host> request system software add reboot
source/jinstall-qfx-5-14.1X53-D43.3-domestic-signed.tgz
When the interim installation has completed and the switch is running a version of Junos OS on one line
that is compatible with satellite device conversion, perform the following steps:
1. Log in to the device by using the console port.
2. Clear the device:
[edit]
user@satellite-device# request system zeroize
NOTE: The device reboots to complete the procedure for resetting the device.
Page 80

If you are not logged in to the device by using the console port connection, your connection to the
device is lost after you enter the request system zeroize command.
If you lose your connection to the device, log in using the console port.
3. (EX4300 switches only) After the reboot is complete, convert the built-in 40-Gbps QSFP+ interfaces
from Virtual Chassis ports (VCPs) into network ports:
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port port-number
For example, to convert all four built-in 40-Gbps QSFP+ interfaces on an EX4300-24P switch into
network ports:
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 0
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 1
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 2
user@satellite-device> request virtual-chassis vc-port delete pic-slot 1 port 3
78
This step is required for the 40-Gbps QSFP+ interfaces that will be used as uplink interfaces in a Junos
Fusion topology. Built-in 40-Gbps QSFP+ interfaces on EX4300 switches are configured into VCPs by
default, and the default settings are restored after the device is reset.
After this initial preparation, you can use one of three methods to convert your switches into satellite
devices—autoconversion, manual conversion, and preconfiguration. See Configuring Junos Fusion Provider
Edge for detailed configuration steps for each method.
Converting a Satellite Device to a Standalone Device
If you need to convert a satellite device to a standalone device, you must install a new Junos OS software
package on the satellite device and remove the satellite device from the Junos Fusion topology.
NOTE: If the satellite device is a QFX5100 switch, you need to install a PXE version of Junos
OS. The PXE version of Junos OS is software that includes pxe in the Junos OS package name
when it is downloaded from the Software Center—for example, the PXE image for Junos OS
Release 14.1X53-D43 is named install-media-pxe-qfx-5-14.1X53-D43.3-signed.tgz . If the
satellite device is an EX4300 switch, you install a standard jinstall-ex-4300 version of Junos OS.
The following steps explain how to download software, remove the satellite device from Junos fusion, and
install the Junos OS software image on the satellite device so that the device can operate as a standalone
device.
Page 81

1. Using a Web browser, navigate to the Junos OS software download URL on the Juniper Networks
webpage:
https://www.juniper.net/support/downloads
2. Log in to the Juniper Networks authentication system by using the username (generally your e-mail
address) and password supplied by Juniper Networks representatives.
3. Select By Technology > Junos Platform > Junos Fusion from the drop-down list and select the switch
platform series and model for your satellite device.
4. Select the Junos OS Release 14.1X53-D30 software image for your platform.
5. Review and accept the End User License Agreement.
6. Download the software to a local host.
79
7. Copy the software to the routing platform or to your internal software distribution site.
8. Remove the satellite device from the automatic satellite conversion configuration.
If automatic satellite conversion is enabled for the satellite device’s member number, remove the
member number from the automatic satellite conversion configuration. The satellite device’s member
number is the same as the FPC slot ID.
[edit]
user@aggregation-device# delete chassis satellite-management auto-satellite-conversion
satellite member-number
For example, to remove member number 101 from Junos Fusion:
[edit]
user@aggregation-device# delete chassis satellite-management auto-satellite-conversion
satellite 101
You can check the automatic satellite conversion configuration by entering the show command at the
[edit chassis satellite-management auto-satellite-conversion] hierarchy level.
9. Commit the configuration.
To commit the configuration to both Routing Engines:
[edit]
user@aggregation-device# commit synchronize
Page 82

Otherwise, commit the configuration to a single Routing Engine:
[edit]
user@aggregation-device# commit
10. Install the Junos OS software on the satellite device to convert the device to a standalone device.
[edit]
user@aggregation-device> request chassis satellite install URL-to-software-package fpc-slot
member-number
For example, to install a PXE software package stored in the /var/tmp directory on the aggregation
device onto a QFX5100 switch acting as the satellite device using FPC slot 101:
[edit]
user@aggregation-device> request chassis satellite install
/var/tmp/install-media-pxe-qfx-5-14.1X53-D43.3-signed.tgz fpc-slot 101
80
For example, to install a software package stored in the var/tmp directory on the aggregation device
onto an EX4300 switch acting as the satellite device using FPC slot 101:
[edit]
user@aggregation-device> request chassis satellite install
/var/tmp/jinstall-ex-4300-14.1X53-D30.3-domestic-signed.tgz fpc-slot 101
The satellite device stops participating in the Junos Fusion topology after the software installation
starts. The software upgrade starts after this command is entered.
11. Wait for the reboot that accompanies the software installation to complete.
12. When you are prompted to log back into your device, uncable the device from the Junos Fusion topology.
See Removing a Transceiver from a QFX Series Device or Remove a Transceiver, as needed. Your device
has been removed from Junos Fusion.
NOTE: The device uses a factory-default configuration after the Junos OS installation is
complete.
Upgrading an Aggregation Device
When you upgrade an aggregation device to Junos OS Release 19.3R1, you must also upgrade your satellite
device to Satellite Device Software version 3.1R1.
Page 83

Upgrade and Downgrade Support Policy for Junos OS Releases
Support for upgrades and downgrades that span more than three Junos OS releases at a time is not
provided, except for releases that are designated as Extended End-of-Life (EEOL) releases. EEOL releases
provide direct upgrade and downgrade paths—you can upgrade directly from one EEOL release to the
next EEOL release even though EEOL releases generally occur in increments beyond three releases.
You can upgrade or downgrade to the EEOL release that occurs directly before or after the currently
installed EEOL release, or to two EEOL releases before or after. For example, Junos OS Releases 17.1,
17.2, and 17.3 are EEOL releases. You can upgrade from Junos OS Release 17.1 to Release 17.2 or from
Junos OS Release 17.1 to Release 17.3.
You cannot upgrade directly from a non-EEOL release to a release that is more than three releases ahead
or behind. To upgrade or downgrade from a non-EEOL release to a release more than three releases before
or after, first upgrade to the next EEOL release and then upgrade or downgrade from that EEOL release
to your target release.
For more information about EEOL releases and to review a list of EEOL releases, see
https://www.juniper.net/support/eol/junos.html.
81
Downgrading from Junos OS Release 19.3
To downgrade from Release 19.3 to another supported release, follow the procedure for upgrading, but
replace the 19.3 jinstall package with one that corresponds to the appropriate release.
NOTE: You cannot downgrade more than three releases.
For more information, see the Installation and Upgrade Guide.
SEE ALSO
What's New | 69
What's Changed | 70
Known Limitations | 70
Open Issues | 71
Resolved Issues | 72
Documentation Updates | 73
Page 84

Junos OS Release Notes for MX Series 5G Universal Routing Platform
IN THIS SECTION
What's New | 82
What's Changed | 102
Known Limitations | 106
Open Issues | 109
Resolved Issues | 122
Documentation Updates | 142
Migration, Upgrade, and Downgrade Instructions | 143
82
These release notes accompany Junos OS Release 19.3R1 for the MX Series. They describe new and
changed features, limitations, and known and resolved problems in the hardware and software.
You can also find these release notes on the Juniper Networks Junos OS Documentation webpage, located
at https://www.juniper.net/documentation/product/en_US/junos-os.
What's New
IN THIS SECTION
Hardware | 83
Authentication and Access Control | 83
Class of Service (CoS) | 84
EVPN | 85
General Routing | 86
Interfaces and Chassis | 87
Junos OS XML API and Scripting | 88
Junos Telemetry Interface | 88
Layer 2 Features | 92
Page 85

Management | 93
MPLS | 93
Operation, Administration, and Maintenance (OAM) | 94
Port Security | 94
Routing Protocols | 95
Services Applications | 96
Software-Defined Networking (SDN) | 98
Software Installation and Upgrade | 98
Subscriber Management and Services | 100
Learn about new features introduced in this release for MX Series routers.
83
Hardware
Next Gen Services with the MX-SPC3 card is referenced in the documentation but not supported on
•
the MX platform in Junos OS Release 19.3R1.
Authentication and Access Control
Support for DYCE randomizer (MX Series)—Starting in Junos OS Release 19.3R1, Junos OS supports
•
the Dyce randomizer on MX960 routers. Dyce is a cryptographically secure pseudo-random number
generator (CSPRNG) in the Junos OS kernel. To enable the Dyce randomizer, use the dyce statement
at the [edit system rng] hierarchy level and reboot the Routing Engine when prompted.
set system rng dyce
NOTE: This configuration is available only at the administrator privilege level.
[See rng].
Support for remote authorization on tacplus for locally authenticated users (MX Series)—Starting in
•
Junos OS Release 19.3R1, Junos OS supports remote authorization on TACPLUS server for the locally
authenticated users by using their locally configured parameters. You can use this feature through
password-options, a new configuration statement, to configure options for local authentication; and its
option tacplus-authorization, to choose the remote authorization for locally authenticated users.
Page 86

NOTE: You must configure the password under authentication-order when password-options
is configured.
The feature does not work in a local fallback scenario because password is not configured
under authentication-order for a local fallback scenario.
To configure remote authorization, include the tacplus-authorization option under the password-options
configuration statement at the [edit system] hierarchy level.
[See password-options].
Class of Service (CoS)
Support for default interface set traffic control profiles (MX Series)— Starting with Junos OS Release
•
19.3R1, you can set a single traffic control profile (TCP) to be the system-wide default input TCP for a
dynamic interface-set and either the same or a different TCP to be the system-wide default output TCP
for a dynamic interface set. When a dynamic interface-set is not explicitly assigned an output TCP, a
static TCP configured as the default output TCP for a dynamic interface-set is automatically assigned
to this interface-set. Likewise, when a dynamic interface-set is not explicitly assigned an input TCP, a
static TCP configured as the default input TCP for a dynamic interface-set is automatically assigned to
this interface-set. To set the default input TCP and output TCP, add interface-set-input profile-name
and interface-set-output profile-name options at the [edit class-of-service system-defaults
traffic-control-profiles] hierarchy level.
84
[See system-defaults.]
Support for input traffic control profile assignment to dynamic logical interface sets (MX Series)—To
•
support assigning both static and dynamic logical interfaces to the same interface set (either static or
dynamic), starting with Junos 19.3R1, you can apply an input traffic control profile (TCP) to a dynamic
logical interface set in 4-level hierarchical scheduling or to two dynamic logical interface sets in 5-level
hierarchical scheduling. Thus, Junos CoS enables you to dynamically assign a static input TCP with
shaping-rate to a dynamic interface-set to enforce a customer’s SLA. If no such SLA enforcement is
needed, you can configure a static TCP that is designated as the default input TCP assigned to any
dynamic interface-set that does not already have an explicitly assigned input TCP.
[See Understanding Hierarchical CoS for Subscriber Interfaces.]
Class of Service (CoS) parity support for forwarding-class (FC) counters on MX-series routers
•
(MPC10/MPC11)—Starting in Junos OS 19.3R1, class of service (CoS) parity support is provided for
forwarding-class (FC) counters on MX-series routers with MPC10 and MPC11 line cards. Feature was
originally introduced in Junos OS 14.1.
[For more information regarding CoS, see Understanding Class of Service.]
Page 87

EVPN
Support for DHCP relay in an EVPN-MPLS network (EX9200 switches, MX Series, vMX)—Starting in
•
Junos OS Release 19.3R1, EX9200 switches, MX Series routers, and vMX virtual routers support DHCPv4
and DHCPv6 relay in an EVPN-MPLS network. We support this feature in a data center architecture
that includes a layer of spine devices that perform EVPN Layer 2 and Layer 3 functions. These devices
are connected to a layer of leaf devices that perform EVPN Layer 2 functions. In this architecture, DHCP
clients are connected to leaf devices, and DHCP servers are connected to spine devices. The DHCP
relay functions are centralized at the spine layer. As a result, this architecture in known as the centrally
routed bridging architecture.
[See DHCP Relay Agent in EVPN-MPLS Network.]
IGMP snooping support for EVPN-VXLAN (EX9200 switches, MX Series, and vMX)—Starting in Junos
•
OS Release 19.3R1, you can configure IGMP snooping on EX9200 switches, MX Series routers, and
vMX virtual routers in an EVPN-VXLAN network. Enabling IGMP snooping helps to constrain multicast
traffic to interested receivers in a broadcast domain.
The listed devices support these IGMP snooping use cases in a centrally-routed bridging overlay (an
EVPN-VXLAN network with a two-layer IP fabric):
85
Forwarding multicast traffic within a VLAN (intra-VLAN)
•
Routing multicast traffic between VLANs (inter-VLAN) using one of the following methods:
•
IRB interfaces configured with Physical Interface Module (PIM) on an elected designated router (DR)
•
device
A PIM gateway with Layer 2 or Layer 3 connectivity
•
An external multicast router
•
The listed devices support these IGMP versions and membership report modes:
IGMPv2 with Any-Source Multicast (ASM) (*,G) mode only.
•
IGMPv3 in either of the following modes:
•
ASM (*,G)—the default behavior.
•
Single-Source Multicast (SSM) (S,G)—you must explicitly configure by including the
•
evpn-ssm-reports-only configuration statement at the [edit protocols igmp-snooping] hierarchy
level.
[See Overview of IGMP Snooping in an EVPN-VXLAN Environment .]
Multiple routing instance support for ping overlay and traceroute overlay on VXLAN (MX Series routers
•
and vMX virtual routers)—Starting in Junos OS Release 19.3R1, Junos OS supports using ping overlay
and traceroute overlay commands on a static VXLAN tunnel with multiple routing instances. The OAM
packets created for the ping overlay and traceroute overlay commands follow the same underlay network
Page 88

path as the data packets. This allows you to verify the connectivity and to detect fault in the underlay
network for an overlay segment between two VTEPs.
[See Understanding Overlay ping and traceroute Packet Support.]
General Routing
Seamless BFD inline mode support for static segment routing LSPs (MX Series)—Starting in Junos OS
•
Release 19.3R1, MX Series routers support inline mode for seamless BFD on static segment routing
LSPs. Inline mode helps increase the number of supported sessions.
[See Routing Engine-Based S-BFD for Segment Routing.]
BFD support (MX2008,MX2010, and MX2020)—Starting in Junos OS Release 19.3R1, MX2008, MX2010,
•
and MX2020 routers with the MPC10E-15C-MRATE line card support the following BFD features:
Inline BFD with the ps-over-lt interface
•
Inline BFD with the ps-over-rlt interface
•
86
Inline BFD over GR tunnels
•
Inline BFD sessions over IRB interface
•
BGP Prefix-Independent Convergence (PIC) Edge
•
[See Understanding BFD for Static Routes for Faster Network Failure Detection.]
Distributed BFD support (MX240, MX480, MX960, MX2010, and MX2020)—Starting in Junos OS
•
Release 19.3R1, MX240, MX480, MX960, MX2010, and MX2020 routers with the MPC10E-15C-MRATE
line card support the following distributed BFD features:
Micro-BFD
•
VCCV BFD
•
BFD sessions that are supported in inline mode can also run in distributed mode.
•
Micro-BFD at the Packet Forwarding Engine level behaves slightly differently on MPC10E-15C-MRATE
line cards. If micro-BFD is enabled an aggregated Ethernet (ae-) interface, the micro BFD packets are
not subjected to firewall filters, for both tagged and untagged ae interfaces.
[See Understanding BFD for Static Routes for Faster Network Failure Detection.]
Page 89

Interfaces and Chassis
10-Gigabit Ethernet WAN PHY mode implementation (MX240, MX480, MX960, MX2010, and
•
MX2020)—Starting in Release 19.3R1, Junos OS follows the RFC 3635 specification while implementing
WAN PHY (physical layer) mode of framing speed reporting. In earlier releases, the 10-Gigabit Ethernet
WAN PHY mode implementation does not consider the payload data rate over the WAN interface
sublayer. As specified in RFC 3635, for Ethernet-like interfaces on WAN interfaces operating at speeds
greater than 1000 Mbps, IfHighSpeed now represents the current operational speed of the
interface—9.294 Gbps— for WAN implementations.
[See 10-Gigabit Ethernet Framing Overview.]
New bidirectional SFP transceivers for MX240, MX80, MX104, MX480, and MX960—Starting in Release
•
19.3R1, Junos OS supports the new bidirectional SFP transceivers (part numbers: 740-088382:
1GE-BX80-T15R14-D and 740-088384: 1GE-BX80-T14R15-U), which provide a speed of 1 Gbps and
a reach of up to 80 km. You can use the existing show commands such as show chassis pic and show
chassis hardware to view the inventory details of the transceivers.
[See show chassis pic and show chassis hardware.]
87
Support for 25-Gbps port speed on MPC10E (MX240, MX480, and MX960)—In Junos OS Release 19.3R1,
•
you can configure port speed of 25 Gbps on MPC10E-10C-MRATE and MPC10E-15C-MRATE on
MX240, MX480, and MX960 routers. Use QSFPP-4x25GE breakout cables to configure 25-Gbps port
speed on:
MPC10E-10C-MRATE: Any of the ten ports.
•
MPC10E-15C-MRATE: Any of the fifteen ports.
•
NOTE: The MPC10E-10C-MRATE and MPC10E-15C-MRATE line cards support the following
4x25 Gigabit Ethernet transceivers:
QSFP-100GBASE-SR4 (with optical breakout)
•
QSFP-100GBASE-PSM4 (with optical breakout)
•
[See MPC10E-15C-MRATE Rate Selectability Overview, MPC10E-10C-MRATE Rate Selectability
Overview].
High-voltage second-generation universal PSM for MX960—Starting in Junos OS Release 19.3R1,
•
MX960 routers support the new high-voltage second-generation universal power supply module (PSM).
This single feed PSM provides a maximum output power of 5100 W, and supports either AC or DC input.
The PSM supports a 1+1 redundancy.
[See MX960 Power System Overview.]
Page 90

Junos OS XML API and Scripting
Program management interface in a nondefault routing instance in op scripts and JET applications (MX
•
Series)—Junos OS Release 19.3R1 supports, on 32-bit architecture, Junos operating scripts and on-box
JET applications can use the function set_routing_instance() to program the protocol software (TCP/UDP)
to use a nondefault routing instance instead of the default management routing interface.
[See set_routing_instance() Function (Python).]
IPv6 support in Python automation scripts (MX Series, PTX Series, and QFX Series)—Starting in Junos
•
OS Release 19.3R1, devices running Junos OS with upgraded FreeBSD support using IPv6 in:
Python automation scripts, including commit, event, op, and SNMP scripts
•
Juniper Extension Toolkit (JET) scripts
•
YANG action scripts
•
IPv6 support enables Python scripts to establish connections and perform operations using IPv6 addresses.
[See IPv6 Support in Python Automation Scripts.]
88
Junos Telemetry Interface
•
Juniper AAA Model streaming telemetry support for subscriber services for JTI (MX5, MX10, MX40,
MX150, MX204, MX240, MX480, MX960, MX2008, MX2010, MX2020, MX10003, MX10008, and
MX100016)—Junos OS Release 19.3R1 supports streaming statistics for subscribers for the diameter
application protocols Network Access Server Application (NASREQ), policy and charging rules function
(PCRF), and Online Charging System (OCS). There are also new diameter peer sensors that provide
response time measurements for messages exchanged between an MX router and the peer for each of
the diameter applications. Statistics are exported using Junos telemetry interface (JTI) and the Juniper
AAA Model, which covers telemetry export using remote procedure calls (gRPC), gRPC Management
Interface (gNMI), or Juniper proprietary RPC or UDP.
To stream diameter application statistics, include the resource paths in a subscription or using the sensor
configuration statement:
For NASREQ statistics, /junos/system/subscriber-management/aaa/diameter/clients/nasreq
•
For PCRF statistics, /junos/system/subscriber-management/aaa/diameter/clients/gx
•
For OCS statistics, /junos/system/subscriber-management/aaa/diameter/clients/gy
•
To stream response time measurements for the diameter applications, include the resource paths in a
subscription or using the sensor configuration statement:
For NASREQ measurements, /junos/system/subscriber-management/aaa/diameter/peers/
•
peer[peer_address=’peer-address’]/nasreq/response-time
Page 91

For PCRF measurements, /junos/system/subscriber-management/aaa/diameter/peers/
•
peer[peer_address=’peer-address’]/gx/response-time
For OCS measurements, /junos/system/subscriber-management/aaa/diameter/peers/
•
peer[peer_address=’peer-address’]/gy/response-time
To enable these statistics for an MX Series router for native (UDP) export, include the sensors statement
at the [edit services analytics] hierarchy level.
To provision the sensor to export data through gNMI, use the Subscribe RPC defined in the gnmi.proto
to specify request parameters.
To provision the sensor to export data through gRPC, use the telemetrySubscribe RPC to specify
telemetry parameters. Streaming telemetry data through gRPC also requires the OpenConfig for Junos
OS module.
[See Guidelines for gRPC Sensors (Junos Telemetry Interface), Understanding OpenConfig and gRPC
on Junos Telemetry Interface, and sensor (Junos Telemetry Interface).]
JTI support extended for Junos kernelGRES and RTSOCK(EX9200, EX9251, EX9253, MX240, MX480,
•
MX960, MX2010, MX2020, vMX, PTX1000, PTX10008, PTX10016, PTX3000 with RE-PTX-X8-64G,
PTX5000 with RE-PTX-X8-64G)—Starting in Junos OS Release 19.3R1, Junos Telemetry Interface (JTI)
extends support for streaming Junos kernel Graceful Routing Engine Switchover (GRES) and Routing
Socket (RTSOCK) information using remote procedure call (gRPC) services. Junos kernel sensors can be
used by device monitoring and network analytics applications to provide insight into the health status
of the Junos kernel.
89
You can use the following base resource paths for exporting kernel GRES and RTSOCK information:
/junos/chassis/gres/
•
/junos/kernel/rtsock/
•
[See Understanding OpenConfig and gRPC on Junos Telemetry Interface and Guidelines for gRPC Sensors
(Junos Telemetry Interface)]
Physical interface operational status sensor (int-exp) support on JTI (MX960, MX2010, and
•
MX2020)—Starting with Junos OS Release 19.3R1, Junos telemetry interface (JTI) uses the sensor int-exp
(interface express) to export interface operational UP and DOWN status at a user-configurable rate.
This sensor leverages statistics out of the physical interface sensor, providing faster and more frequent
operational status statistics. Only the physical interfaces’ operational status from the Flexible PIC
Concentrator (FPC) is collected and reported. Statistics from the Routing Engine interface are not
reported.
You can apply the intf-exp sensor using the following path for either native (UDP) export using the
sensor configuration statement or through OpenConfig using remote procedure calls (gRPC) services:
/junos/system/linecard/intf-exp/
•
To provision a sensor to export data through gRPC, use the telemetrySubscribe RPC to specify telemetry
parameters. Streaming telemetry data through gRPC also requires the OpenConfig for Junos OS module.
Page 92

[See Guidelines for gRPC Sensors (Junos Telemetry Interface) and sensor (Junos Telemetry Interface)]
•
gNMI support for Routing Engine statistics for JTI (MX960, MX2010, MX2020, PTX5000, PTX1000,
and PTX10000)—Junos OS Release 19.3R1 supports the Junos telemetry interface (JTI) export of Routing
Engine sensors using gRPC Management Interface (gNMI). gNMI is a protocol for configuration and
retrieval of state information. Both streaming and ON_CHANGE export is supported using gNMI.
JTI exports the following statistics using gNMI:
Network discovery, ARP table state (resource path /arp-information/)
•
Network discovery, NDP table state (resource paths /nd6-information/ and /ipv6-ra/)
•
To provision the sensor to export data through gNMI, use the Subscribe RPC defined in the gnmi.proto
to specify request parameters. Streaming telemetry data through gNMI also requires the OpenConfig
for Junos OS module. Starting in Junos OS Release 18.3R1, OpenConfig and Network Agent packages
are bundled into the Junos OS image by default. Both packages support the JTI.
[See Guidelines for gRPC Sensors (Junos Telemetry Interface).]
•
CPU/NPU sensors support using JTI (MPC10E-10C-MRATE and MPC10E-15C-MRATE line cards)—Junos
OS Release 19.3R1 supports Junos telemetry interface (JTI) CPU and network processing unit (NPU)
sensors on MX Series routers with on MPC10E-10C-MRATE and MPC10E-15C-MRATE line cards. JTI
enables the export of statistics from these sensors to outside collectors at configurable intervals using
remote procedure call (gRPC) services.
90
Unlike the previous Junos kernel implementation for these sensors in earlier Junos OS releases, this
feature uses the OpenConfig AFT model. Because of this, there is a difference in the resource path and
key-value (kv) pair output compared to the Junos kernel output.
Use the following resource path to export statistics:
/junos/system/linecard/cpu/memory/
/junos/system/linecard/npu/memory/
/junos/system/linecard/npu/utilization/
To provision the sensor to export data through gRPC services, use the telemetrySubscribe RPC to specify
telemetry parameters. Streaming telemetry data through gRPC also requires the OpenConfig for Junos
OS module. Starting in Junos OS Release 18.3R1, OpenConfig and Network Agent packages are bundled
into the Junos OS image by default. Both packages support JTI.
[See Guidelines for gRPC Sensors (Junos Telemetry Interface) and Understanding OpenConfig and gRPC
on Junos Telemetry Interface.]
•
gNMI-based streaming telemetry support for Packet Forwarding Engine sensors (MX240, MX480, and
MX960)—Starting in Junos OS Release 19.3R1, gRPC Network Management Interface (gNMI) service
support is available to export Packet Forwarding Engine statistics for telemetry monitoring and
management using Junos telemetry interface (JTI). Using gNMI and JTI, data is exported from devices
to outside collectors at configurable intervals. This feature includes support (SensorD daemon) to export
Page 93

telemetry data for integration with AFTTelemetry and LibTelemetry libraries in the OpenConfig model
called AFT platform.
Use the following resource paths to export sensor data for interface information and traffic, logical
interface traffic, firewall filter counters, and policer counters:
/junos/system/linecard/interface/
•
/junos/system/linecard/interface/traffic/
•
/junos/system/linecard/interface/queue/
•
/junos/system/linecard/interface/logical/usage/
•
/junos/system/linecard/firewall/
•
/junos/system/linecard/services/inline-jflow/
•
To provision the sensor to export data through gNMI services, use the Subscribe RPC. The Subscribe
RPC and subscription parameters are defined in the gnmi.proto file. Streaming telemetry data through
gRPC or gNMI also requires the OpenConfig for Junos OS module.
91
[See Guidelines for gRPC and gNMI Sensors (Junos Telemetry Interface) and Understanding OpenConfig
and gRPC on Junos Telemetry Interface.]
JTI support extended for Junos kernel LAG, NSR, and TCP (EX9200, EX9251, EX9253, MX240, MX480,
•
MX960, MX2010, MX2020, vMX, PTX1000, PTX10008, PTX10016, PTX3000 with RE-PTX-X8-64G,
and PTX5000 with RE-PTX-X8-64G)—Starting in Junos OS Release 19.3R1, Junos telemetry interface
(JTI) extends support for streaming Junos kernel Link Aggregation Group (LAG), nonstop routing (NSR)
Junos socket replication (JSR), and Transport Control Protocol (TCP) information using remote procedure
call (gRPC) services. Device monitoring and network analytics applications can use Junos kernel sensors
to provide insight into the health status of the Junos kernel.
You can use the following base resource paths for exporting kernel LAG, NSR, and TCP information:
/junos/chassis/aggregated-devices/
•
/junos/routing-options/nonstop-routing/
•
/junos/kernel/tcpip/tcp/
•
[See Understanding OpenConfig and gRPC on Junos Telemetry Interface and Guidelines for gRPC Sensors
(Junos Telemetry Interface)]
JTI support extended for Junos kernel IPv4 and IPv6 (EX9200, EX9251, EX9253, MX240, MX480,
•
MX960, MX2010, MX2020, vMX, PTX1000, PTX10008, PTX10016, PTX3000 with RE-PTX-X8-64G,
and PTX5000 with RE-PTX-X8-64G)—Starting in Junos OS Release 19.3R1, Junos telemetry interface
(JTI) extends support for streaming Junos kernel IPv4 and IPv6 information using remote procedure call
(gRPC) services. Device monitoring and network analytics applications can use Junos kernel sensors
provide insight into the health status of the Junos kernel.
You can use the following base resource paths for exporting kernel IPv4 and IPv6 information:
Page 94

/junos/kernel/tcpip/arp/ — Address Resolution Protocol cache
•
/junos/kernel/tcpip/ndp/ — Neighbor Discovery Protocol cache
•
/junos/kernel/tcpip/netisr/ — NETISR network queues
•
/junos/kernel/tcpip/nhdix/ — Next-hop index space exhaustion
•
/junos/kernel/tcpip/rtb/ — Route tables
•
[See Understanding OpenConfig and gRPC on Junos Telemetry Interface and Guidelines for gRPC Sensors
(Junos Telemetry Interface)]
JTI support extended for Junos kernel IP multicast, tunnels, TNP, and VPLS (EX9200, EX9251, EX9253,
•
MX240, MX480, MX960, MX2010, MX2020, vMX, PTX1000, PTX10008, PTX10016, PTX3000 with
RE-PTX-X8-64G, PTX5000 with RE-PTX-X8-64G)—Starting in Junos OS Release 19.3R1, Junos telemetry
interface (JTI) extends support for streaming Junos kernel IP multicast, tunnels, Trivial Network Protocol
(TNP), and virtual private LAN service (VPLS) information using remote procedure call (gRPC) services.
Device monitoring and network analytics applications can use Junos kernel sensors provide insight into
the health status of the Junos kernel.
92
You can use the following base resource paths for exporting kernel IP multicast, tunnels, TNP, and VPLS
information:
/junos/kernel/multicast/
•
/junos/kernel/tunnel/
•
/junos/kernel/tnp/
•
/junos/kernel/vpls/
•
[See Understanding OpenConfig and gRPC on Junos Telemetry Interface and Guidelines for gRPC Sensors
(Junos Telemetry Interface)]
Layer 2 Features
Supported features on MPC10E-15C-MRATE line cards (MX Series)—Starting in Junos OS Release
•
19.3R1, the MPC10E-15C-MRATE line card supports the following advanced Layer 2 features::
Forwarding CoS (Q-depth monitoring)—You can configure a Junos telemetry interface sensor that
•
exports queue depth statistics for ingress and egress queue traffic. Telemetry data is exported directly
from the line card. You can also apply one or more regular expressions to filter data. Only UDP streaming
of data is supported. gRPC streaming of queue depth statistics is not currently supported. [See sensor
(Junos Telemetry Interface).]
Layer 2 firewall forwarding support. [See Layer 2 Port Mirroring Firewall Filters.]
•
Layer 2 forwarding—IRB, VLAN handling, and Q-in-Q tunneling. [See Configuring Q-in-Q Tunneling
•
and VLAN Q-in-Q Tunneling and VLAN Translation.] Firewall filters for Layer 2 and MAC filters. [See
Layer 2 Forwarding Tables.]
Page 95

Load balancing—Enhanced hash key options, consistent flow hashing, symmetrical load balancing over
•
802.3ad LAGs, source IP only hashing, and destination IP only hashing. [See Configuring Per-Flow
Load Balancing Based on Hash Values.]
Multicast features—P2MP (RSVP-TE P2MP & mLDP inband) and P2MP interface support for PIM,
•
Rosen multicast VPNs, and multicast-only fast reroute (MoFRR)(mLPD inband and PIM signaling). [See
Multicast Overview.]
Management
OpenConfig AAA data model support (ACX1100, ACX2100, ACX5448, ACX6360, EX4300, MX240,
•
MX480, MX960, MX10003, PTX10008, PTX10016, QFX5110, and QFX10002)—Junos OS Release
19.3R1 supports the configuration leafs specified in the OpenConfig AAA data model. Mapping the
OpenConfig AAA configuration to the Junos AAA configuration using the following YANG files in the
data model makes this support possible:
openconfig-aaa.yang
•
93
openconfig-aaa-types.yang
•
openconfig-aaa-tacacs.yang
•
openconfig-aaa-radius.yang
•
The configuration model supporting the OpenConfig data model includes:
A translation script (.py / .slax) that maps each configuration leaf in the OpenConfig schema to one
•
or more configuration leafs in the Junos schema.
A deviation file (.yang) that specifies how much the implementation deviates from the vendor-neutral
•
model.
[See Mapping OpenConfig AAA Commands to Junos Configuration.]
MPLS
Support for Entropy Label and FAT PW Label in Advanced Forwarding Toolkit (MX Series)—Starting in
•
Junos OS Release 19.3R1, the Junos OS supports entropy labels and Flow Aware Transport for
Psuedowires (FAT) labels. Entropy label and FAT label when configured on the label-switching routers
(LSRs) and label edge routers (LEs) perform load-balancing of MPLS packets across equal-cost multipath
(ECMP) paths or link aggregation groups (LAG) without the need for deep packet inspection of the
payload.
[See Configuring the Entropy Label for LSPs and FAT Flow Labels Overview].
Support for Seamless MPLS Layer 3 features (MX Series with MPC10E)—Starting in Junos OS Release
•
19.3R1, the following MPLS Layer 3 features are supported on MX series routers with MPC10E line
cards:
Page 96

Redundant logical tunnel interfaces.
•
Pseudowire subscriber interfaces using either logical tunnel or redundant logical tunnel interfaces as
•
anchor point.
[See Redundant Logical Tunnels Overview, and MPLS Pseudowire Subscriber Logical Interfaces.]
Operation, Administration, and Maintenance (OAM)
Support for LFM (MPC10E)—Starting in Junos OS Release 19.3R1, you can configure IEEE 802.3ah link
•
fault management (LFM) for MPC10E-10C-MRATE and MPC10E-15C-MRATE on MX240, MX480, and
MX960 routers. You can also configure the following supported LFM features:
Discovery and link monitoring
•
Distributed LFM
•
Remote fault detection and remote loopback
•
94
NOTE: You cannot configure inline LFM for MPC10E on MX240, MX480, and MX960 routers.
[See IEEE 802.3ah OAM Link-Fault Management Overview.]
Port Security
MACsec on logical interfaces (MX Series)—Starting with Junos OS Release 19.3R1, you can configure
•
Media Access Control Security (MACsec) at the logical interface level on the MIC-MACSEC-20GE in an
MX Series router. This feature allows multiple MACSec Key Agreement (MKA) sessions on a single
physical port.
[See Understanding Media Access Control Security (MACsec).]
PSK hitless rollover and fail-open mode for MACsec(MX Series)—Starting with Junos OS Release 19.3R1,
•
MX Series routers with the MPC10E-15C or MPC10E-10C line card support preshared key (PSK) hitless
rollover and fail-open mode for Media Access Control Security (MACsec).
[See Understanding Media Access Control Security (MACsec).]
Support for configuring unicast MAC DA for MACsec (MX Series)—Starting with Junos OS Release
•
19.3R1, you can configure the destination EAPoL address for MACsec as a unicast address. When
MACsec Key Agreement PDUs (MKA PDUs) are exchanged over a provider network, they might be
dropped or consumed if the default multicast address is used. You can configure the unicast MAC address
to ensure that the MKA PDUs reach their destination.
[See mka (MX Series).]
Page 97

Routing Protocols
Support for nondefault routing instance for outbound SSH (MX Series and SRX Series)—Starting in
•
Junos OS Release 19.3R1, you can specify the name of the routing instance on which the outbound SSH
connectivity needs to be established using the routing-instance statement at the [edit system services
outbound-ssh] hierarchy level. If you do not specify a routing instance, your device will establish the
outbound SSH connection using the default routing table.
[See outbound-ssh, Configuring Outbound SSH Service.]
Support for color mode in segment routing traffic engineering using BGP (MX Series, PTX Series, and
•
QFX Series)—Starting in Junos OS Release 19.3R1, Junos OS supports color-only mode corresponding
to color bits 01 and supports the steering fallback mechanism (in a limited manner) when color bits as
set to 01 as described in IETF DRAFT-SPRING-SRTE. Use the extended-nexthop-color CLI configuration
option to set color bits to 01 to enable color-only mode. Fall back to color-only SRTE policies is also
supported and can be configured independently by configuring an import policy at the headend.
[See Understanding Ingress Peer Traffic Engineering for BGP SPRING.]
Support for segment routing (SR) and segment routing traffic engineering (SRTE) statistics in Advanced
•
Forwarding Toolkit (MX960, MX2010, and MX2020)—Starting in Junos OS Release 19.3R1, the traffic
statistics in a segment routing (SR) network can be recorded in an OpenConfig compliant format for
Layer 3 interfaces. The statistics is recorded for the Source Packet Routing in Networking (SPRING)
traffic only, excluding RSVP and LDP-signaled traffic, and the family MPLS statistics per interface is
accounted for separately. The SR statistics also includes SPRING traffic statistics per link aggregation
group (LAG) member, and per segment identifier (SID).
95
Junos OS also supports SRTE telemetry statistics and BINDING-SID routes for uncolored SRTE policies.
Uncolored SRTE LSP is characterized by the absence of color statement in its configuration. Junos OS
now allows collection of traffic statistics for both ingress IP traffic and transit MPLS traffic that take
uncolored SRTE paths. Also, you can install BINDING-SID labels even if the first hop of the segment list
is a label. By default, traffic sensors and statistic collection are disabled for static SRTE routes. To enable
provisioning of JVISION traffic sensors in Junos OS data plane to stream out traffic statistics on SR
policies and their Binding-SID routes, use the existing statistics statement at the [edit
source-packet-routing telemetry] hierarchy level.
[See Understanding Source Packet Routing in Networking (SPRING).]
Support for OSPF TI-LFA back paths for Segment Routing (MX Series)—Starting in Junos OS Release
•
19.3R1, Junos OS supports creation of OSPF topology-independent TI-LFA backup paths where the
prefix SID is learned from a segment routing mapping server advertisement when the PLR and mapping
server are both in the same OSPF area.
[See Configuring Topology-Independent Loop-Free Alternate with Segment Routing for OSPF.]
Page 98

Services Applications
Regulate and add frame and byte count for carrier-grade NAT syslog messages—Starting in Junos OS
•
Release 19.3R1, you can enable or disable the display of the carrier-grade NAT syslog message in certain
deployment scenarios. When you configure the disable-session-open-syslog statement at the [edit
services service-set service-set-name service-set-options] hierarchy level:
The JSERVICES_SESSION_OPEN logs are disabled and are no longer generated for the incoming
•
sessions.
The JSERVICES_SESSION_CLOSE logs, which are generated after the incoming sessions are closed,
•
are printed with byte and packet count for the packets received and sent as part of the same session.
[See service-set (Services).]
Configure next-hop-based dynamic tunnels on MPC10E (MX240, MX480, and MX960 routers)—Starting
•
in Junos OS Release 19.3R1, on MX240, MX480, and MX960 routers with an MPC10E line card, you
can configure next-hop-based dynamic tunnels for the following configurations:
MPLS-over-UDP—You can configure a dynamic MPLS-over-UDP tunnel that includes atunnel composite
•
next hop.
96
MPLS-over-GRE—You can configure MPLS LSPs to use generic routing encapsulation (GRE) tunnels
•
to cross routing areas, autonomous systems, and ISPs.
[See dynamic-tunnels.]
Inline active flow monitoring on MPC10E (MX240, MX480, and MX960 routers)—Starting in Junos OS
•
Release 19.3R1, you can configure inline active flow monitoring on the MPC10E line card to support:
MPLS, MPLS-IPv4, and MPLS-IPv6 traffic
•
IPv4 or IPv6 traffic on next-hop-based GRE tunnels and PS interfaces
•
The flow records support both IPFIX and version 9 formats.
[See Understanding Inline Active Flow Monitoring.]
L2TP silent failover on peer interface for L2TP subscriber services on MPC10E (MX Series)—Starting
•
in Junos OS Release 19.3R1, you can configure L2TP silent failover on peer interface for L2TP subscriber
services on MPC10E line card.
L2TP failover enables a failed L2TP endpoint to resynchronize with its nonfailed peer during recovery
and restart of the L2TP protocol on the failed endpoint. L2TP failover is enabled by default.
[See Peer Resynchronization After an L2TP Failover.]
FlowTapLite suppport on MPC10E (MX240, MX480, and MX960 routers)—Starting in Junos OS Release
•
19.3R1, you can configure FlowTapLite on an MPC10E line card. FlowTapLite enables interception of
IPv6 packets on MX Series, M120, and M320 routers.
[See Configuring FlowTapLite on MX Series Routers and M320 Routers with FPCs.]
Page 99

Support for TWAMP (ACX5448-M)—Starting in Junos OS Release 19.3R1, you can configure Two-Way
•
Active Measurement Protocol (TWAMP) on your ACX5448 routers. TWAMP enables you to measure
the IP performance between two devices in a network. The ACX5448-M router supports only the
reflector side of TWAMP.
[See Two-Way Active Measurement Protocol on ACX Series.]
Support for multiple features on tunnel interfaces on the MPC10E line card (MX Series)—Starting in
•
Release 19.3R1, Junos OS supports the multiple features on tunnel interfaces.
On logical tunnels, you can now configure the CCC/MPLS family configuration.
On GRE tunnel interfaces, you can:
Copy the ToS bits of the inner IP header to the outer IP packet header for traffic transiting the router.
•
Configure an IPv6 GRE tunnel interface.
•
Configure the flow-label field in the IPv6 header of the delivery protocol for an IPv6 GRE tunnel
•
interface.
Enable or disable fragmentation of GRE-encapsulated packets for an IPv4 GRE tunnel interface.
•
97
Enable a GRE tunnel for keepalive messages for an IPv4 GRE tunnel interface.
•
Enable or disable path MTU discovery for an IPv4 GRE tunnel interface.
•
[See GRE Keepalive Time Overview.]
[SeeEnabling Fragmentation on GRE Tunnels.]
Support for ECMP routing with MAP-E (MX Series)—Starting in Junos OS Release 19.3R1, you can
•
configure ECMP routing with MAP-E. By configuring the disable-auto-route statement at the [edit
services softwire softwire-concentrator map-e <domain-name>] hierarchy level, you can disable auto
routes and configure static routes that point to an ECMP load balancer. As a result, the packets are
distributed among different inline service interfaces.
[See Understanding Mapping of Address and Port with Encapsulation (MAP-E).]
Enhance Juniper SkyATP URL filtering logging through sampling (MX240, MX480, and MX960
•
routers)—Starting in Junos OS Release 19.3R1, the URL filtering daemon (url-filterd) supports inline
sampling as a threat action. You can configure the following threat-level actions in the web filtering
profile at the [edit services web-filter- profile p1 security-intelligence-policy threat-level threat-level
threat-action] hierarchy level.
drop-and-sample
•
drop-log-and-sample
•
log-and-sample
•
sample
•
Page 100

The inline J-Flow samples the packets and sends it to a collector in IPFIX format. You can derive the
threat level for the sampled packets received at the external collector by matching the received IP from
the sampled packets with the corresponding IP entry in /var/db/url-filterd/urlf_si_cc_db.txt.
[See web-filter.]
Software-Defined Networking (SDN)
Upgrade JDM to support WRL 9-based VM host for in-chassis Junos node slicing (MX2010, MX2020,
•
MX2008, MX960, and MX480)—Starting in Junos OS Release 19.3R1, you can upgrade the Juniper
Device Manager (JDM) to support the Wind River Linux 9 (WRL 9)-based VM host for in-chassis Junos
node slicing. For the upgrade, you don't need to change the configuration of the existing guest network
functions (GNFs) in JDM, although you must stop the GNFs and JDM before you upgrade JDM. The
JDM software version 19.3R1 supports both WRL 6-based and WRL 9-based VM host software versions.
[See Junos Node Slicing Upgrade.]
98
Software Installation and Upgrade
Migration of Linux kernel version—Starting in Junos OS Release 19.3R1, the following devices support
•
the Wind River Linux 9 (WRL9) kernel version:
Routing Engine SupportedPlatforms
RE-ACX-5448ACX5448-D
RE-S-X6-64GMX240, MX480, and MX960
REMX2K-X8-64GMX2020 and MX2010
RE-S-1600x8MX204
RE-S-1600x8MX10003
RE-MX2008-X8-64GMX2008
RE X10MX10016
RE X10MX10008
RE-PTX-X8-64GPTX5000
RCBPTXPTX3000
 Loading...
Loading...