Page 1

VGW VIRTUAL GATEWAY
DATASHEET
Product Overview
The vGW Virtual Gateway combines
best-in-class virtual firewall to meet
the unique security challenges of virtual
data centers and clouds. IT teams can
now secure their virtual environment
by enforcing a rule-based firewall
for each VM. Because the vGW has
been purpose-built with virtualization
features in mind, it synchronizes
automatically with VMware vCenter,
secures VMotion, and uses VMsafe to
provide breakthrough levels of security
and performance.
The vGW delivers superior protection,
throughput, scalability, automated
deployment and operations, and value
for virtualized environments. Enterprises
can now achieve the full ROI of
virtualization by maximizing the number
of secure VMs on each physical host
and virtualizing mission-critical systems.
And for the first time, they can maintain
equal security and regulatory compliance
across physical and virtual networks.
Product Description
Juniper Networks® vGW Virtual Gateway rounds out a virtualization security solution that
includes a high-performance hypervisor-based stateful firewall complete virtual network
visibility, monitoring, and reporting. The vGW brings forward powerful new features that
automate security and compliance enforcement within virtual networks and clouds. By
leveraging virtual machine introspection (VMI) data and intelligence, and coupling it with
Juniper ’s wide-ranging knowledge of the security and virtual network environment, vGW
creates an extensive database of control points by which security policies and compliance
rules can be defined.
The vGW makes this rich data available in intuitive UIs that let administrators build
the entire range of policies from corporate rules on global protocol handling (e.g.,
block Kazaa) to discrete regulatory compliance policies for how virtual machines
should be configured (e.g., must have antivirus installed). Compliance assessment and
security enforcement happen automatically and in lockstep with changes in the virtual
environment. New VMs, for example, will be scanned and quarantined if out of compliance
with policies. The same applies to VMs whose “state” changes such that the security
posture is weakened. The vGW VMware VMsafe-certified security operates from deep
within the virtualization fabric as part of the hypervisor. Consequently, the software
delivers unprecedented levels of security, far beyond what is possible with traditional
physical network security products.
Security and compliance concerns are top of mind in virtualization and cloud
deployments. Juniper’s experience and innovative research in virtualization security has
resulted in a powerful software suite capable of monitoring and protecting virtualized
environments without negatively impacting performance. A hypervisor-based, VMsafe-
certified, virtualization security approach, in combination with “X-ray” level knowledge of
each virtual machine through VMI, gives the vGW a unique vantage point in the virtualized
fabric. Here, virtualization security can be applied efficiently and with context about the
virtual environment and its state at any given moment.
1
Page 2
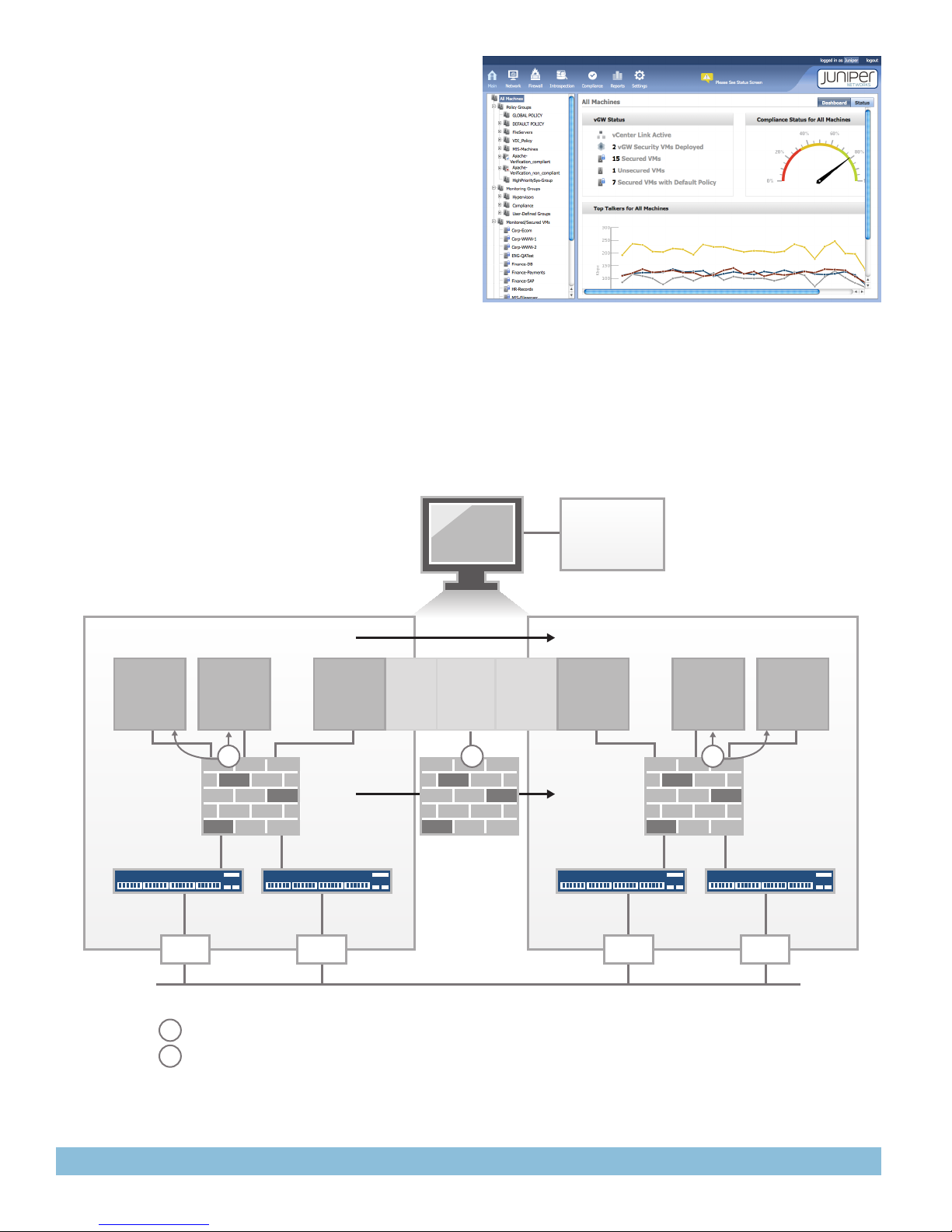
vGW delivers total virtual data center protection and cloud
security through visibility, compliance, and control:
• Visibility—full view to all applications flowing between VMs
and how they are used. Complete VM and VM group inventory,
including virtual network settings. Deep knowledge of VM state,
including installed applications, operating systems, and patch
level, through VMI.
• Compliance—enforcement of corporate and regulatory policies
for the presence of required or banned applications via VMI.
Some practical applications of compliance enforcement such
as assurance of segregation of duties to ensure that VMs are
assigned to the right trust zones inside the virtual environment.
Pre-built compliance assessment based on common industry
best practices and leading regulatory standards.
• Control—a VMsafe-certified, stateful firewall provides access
control over all traffic via policies that define which ports,
protocols, destination VMs, etc. should be blocked. Further
inspection of allowed traffic can be conducted by protocol or
application in order to identify intrusion attempts, malformed
packets, or the presence of malware.
Architecture and Key Components
Figure 1: A dashboard view of virtual network security and
compliance states
Database
VM
Virtual
Switch
Physical Server #1
Intranet Application
SAP
VM
1
Virtual
Firewall
NIC
NIC
WWW
VM
Virtual
Switch
Live
Migration
WWWVMWWWVMWWW
VM
2
Physical Network
WWW
VM
Virtual
Switch
Virtual
Center
Physical Server #2
Desktop
Virtual
Firewall
NIC
VM
Desktop
VM
1
Virtual
Switch
NIC
Virtual Firewall
1
secure inter-VM communication, stopping infections.
Secure VMotion by “attaching” an enforceable policy to the migrating VM.
2
Figure 2: The vGW secures highly dynamic VMs through change and motion
2
Page 3

Features and Benefits
Virtualization has brought both economic benefits and new
security concerns to enterprises. IT managers often hesitate to
virtualize systems with sensitive data or take full advantage of VM
live migration due to security worries. Among their concerns are:
• Undetected and uncontained malware outbreaks or insider
attacks in the virtual environment
• Lack of visibility into, or control of, traffic between VMs that
never touches the physical network
• Inability to enforce policies that isolate VMs, prevent VM sprawl,
or secure features like VMotion
• Virtualization compliance gaps and audit data holes
• Increasing network complexity and administrative burden
caused by applying legacy VLAN or firewall technology to the
virtual environment
infrastructure (VI) and VM information. The dynamic policy groups
can then be associated with one or more VMs. When additional
VMs are created, they can be automatically associated with known
groups and policies by matching predefined criteria. Administration
overhead is reduced by allowing a “build once, apply continuously”
model to security policy definition and enforcement.
Cloud Security API
Juniper provides an XML-RPC programming interface that lets
service providers and large enterprises customize and automate
firewall provisioning. Users of the API can efficiently secure
virtualization services for internal or external customers, while
ensuring strict isolation of customer VMs.
Compliance
The vGW lets administrators, security managers, and compliance
auditors define and report on the specific conditions (corporate
and regulatory) that constitute compliant operation in their
environments. The vGW user interface allows for the building
of custom “whitelists” (desired configurations) and “ blacklists”
(unwanted conditions). vGW continuously monitors all VMs,
including newly created ones, to report on the overall compliance
posture of the virtual environment. Virtual data center and cloud
administrators can see their aggregate compliance posture at a
glance and drill down on each VM to identify the exact condition
that has triggered a noncompliance alert (e.g., VM in wrong VLAN,
or trust zone has been quarantined).
Figure 3: VM Introspection technology gives the vGW an
X-ray view of VMs
Without the means to mitigate risks in a cost-effective manner,
many enterprises are not currently realizing the full potential that
virtualization technology offers.
Architected for Multiple Platforms
Juniper Networks multi-platform architecture is designed to secure
all leading virtualization platforms (e.g., Microso Hyper-V, Xen) and
support their newest technologies, such as VMsafe from VMware.
Enterprises retain the freedom to choose whatever virtualization
technologies meet their needs, today and into the future.
Automated Deployment and Integration
The vGW virtual appliance automatically installs itself and
discovers all guest VMs through integration with vCenter. Unlike
using VLANs to isolate VMs, Juniper’s solution is easy to maintain
and readily scales as virtualization use grows and new virtual
machines are added to the environment.
Automated VM Security
The vGW automates the application and enforcement of security
rules. This is accomplished in two ways. First, it allows for the
creation of highly detailed security policies that “dynamically”
combine desired conditions from a rich database of virtual
High Availability
Using redundant system components, the vGW provides mission-
critical reliability. An easily deployed shadow management server
immediately takes over if the primary system fails, ensuring
uninterrupted policy enforcement and management control.
High-Performance, Hypervisor-Resident Firewall
By processing inspections in the VMware hypervisor kernel,
vGW provides 10 times the throughput of older, bridge-mode
firewalls running in virtual environments. This optimized VMsafe
innovation can increase VMs per host while eliminating network
reconfigurations. Firewall protection is continuous as VMs move
from host to host using VMotion. Unlike traditional firewalls,
the vGW keeps the “live” in live migration by maintaining open
connections and security throughout the event.
Intuitive Central Management
The Web-based central management console displays real-time
views of each virtual machine’s operating and security status at
a glance. And a simple, familiar interface for defining rules and
managing policies supports role-based administration, enabling
separation of duties.
Logging, Reporting, and Alerts
System logging output gives security event management systems
insight into virtual network activity. Administrators can print
reports of historical VM traffic data and configure SNMP traps to
alert them to selected events.
3
Page 4

Smart Default Policy for New Virtual Machines
When a new VM is created, the vGW assigns it an administrator-
defined default policy. Allowing only admin and Domain Name
System (DNS) protocols, for example, mitigates the risks of
misconfigured or “rogue” VMs with vulnerable or infected workloads.
VMware Hypervisor Protection
By monitoring and storing all network connections to the
hypervisor using VMsafe APIs, the vGW creates a new defensive
layer that protects hypervisors against unauthorized connection
attempts from VMs.
vGW provides a hypervisor-based stateful firewall that inspects
all packets to and from VMs, blocking all unapproved connections
and subjecting allowed packets to deeper inspection (e.g., port 80
for Web applications). Administrators can enforce stateful firewall
policies for individual VMs, logical groups of VMs, or all VMs.
VM Introspection
Virtual Machine Introspection (VMI) is a groundbreaking approach,
analogous to an “X-ray” of VMs and the virtual environment from
the hypervisor. VMI enables information gathering about VMs, the
security of the virtual network, and virtual environment settings—
without the use of agents. The ability of malware to disable or
hide from security agents is a classic unresolved security problem
that has plagued the security industry for decades. VMI offers
an innovative new approach to leveraging the hypervisor for
an uncompromised “X-ray” inspection of VMs, where malware
literally has nowhere to hide. vGW incorporates VMI as part of its
security policy definition and enforcement mechanism.
By amassing information about the kinds of applications and
services running on VMs, vGW sustains deep knowledge about
the internal security state of each virtual device. This information
is then made available through vGW’s point-and-click dynamic
policy editor, so that rules can be easily built to enforce a desired
VM security posture. For example, a security rule could require
the presence of antivirus software to be present inside a VM, or
alternatively discover unapproved applications, forcing automated
quarantine and alerts for noncompliant machines. vGW’s unique
vantage point in the hypervisor delivers unprecedented visibility
and control over the virtual environment to achieve compliance
with corporate standards.
Figure 4: Granular virtual firewall policies enforce all
access to and from VMs
System Requirements
vGW Firewall
• Operating System Virtual Appliance
• Memory: 512 MB
• Disk space: 1 GB
• Virtual Infrastructure VMware
• vSphere 4
• VMware ESX or ESXi 4.0, with vCenter 4
Security Design for vGW
• Operating System Virtual Appliance
• Memory: 1 GB
• Disk space: 10 GB
• Virtual Infrastructure Infrastructure 3
• VMware ESX
• Server 3.x.x
• VirtualCenter 2.x.x
Juniper Networks Services and Support
Juniper Networks is the leader in performance-enabling services
and support, which are designed to accelerate, extend, and
optimize your high-performance network. Our services allow
you to bring revenue-generating capabilities online faster so
you can realize bigger productivity gains and faster rollouts of
new business models and ventures. At the same time, Juniper
Networks ensures operational excellence by optimizing your
network to maintain required levels of performance, reliability, and
availability. For more details, please visit www.juniper.net/us/en/
products-services.
4
Page 5

Ordering Information
For more information about Juniper Networks vGW Virtual
Gateway, please contact www.juniper.net.
MODEL NUMBER DESCRIPTION
ALTOR-CENTER-1 Central management center
ALTOR-SVM-ADD-2 Security VM license for 2 CPU sockets
ALTOR-SVM-ADD-10 Security VM license for 10 CPU sockets
ALTOR-SVM-ADD-20 Security VM license for 20 CPU sockets
ALTOR-SVM-ADD-50 Security VM license for 50 CPU sockets
ALTOR-SVM-ADD-100 Security VM license for 100 CPU sockets
ALTOR-SVM-UNL Security VM license for unlimited CPU
sockets
ALTOR-HA-ADD-2 High availability license for 2 CPU sockets
ALTOR-HA-ADD-10 High availability license for 10 CPU sockets
ALTOR-HA-ADD-20 High availability license for 20 CPU sockets
ALTOR-HA-ADD-50 High availability license for 50 CPU sockets
ALTOR-HA-ADD-100 High availability license for 100 CPU sockets
About Juniper Networks
Juniper Networks is in the business of network innovation. From
devices to data centers, from consumers to cloud providers,
Juniper Networks delivers the software, silicon and systems that
transform the experience and economics of networking. The
company serves customers and partners worldwide. Additional
information can be found at www.juniper.net.
5
Page 6

Corporate and Sales Headquarters
Juniper Networks, Inc.
1194 North Mathilda Avenue
Sunnyvale, CA 94089 USA
Phone: 888.JUNIPER (888.586.4737)
or 408.745.2000
Fax: 408.745.2100
APAC Headquar ters
Juniper Networks (Hong Kong)
26/F, Citypla za One
1111 King’s Road
Taikoo Shing, Hong Kong
Phone: 852. 2332.3636
Fax: 852.2574.7803
www.juniper.net
Copyri ght 2011 Juniper Net works, Inc. All r ights reser ved. Junipe r Networks, t he Juniper Net works logo, Jun os,
NetScr een, and Screen OS are registere d trademarks o f Juniper Netw orks, Inc. in th e United States and oth er
countri es. All other trad emarks, se rvice marks , registered m arks, or regis tered serv ice marks are th e property o f
their re spective own ers. Junipe r Networks a ssumes no res ponsibilit y for any inaccurac ies in this docum ent. Juniper
Netwo rks reser ves the right to cha nge, modify, tran sfer, or otherw ise revise thi s publication w ithout notice.
1000363-001-EN Feb 2011
Printed o n recycled pape r
6
EMEA Headquarters
Juniper Networks Ireland
Airside Business Park
Swords, County D ublin, Ireland
Phone: 35.31.8903.600
EMEA Sales: 00800.4586.4737
Fax: 35.31.8903.601
To purchase Juniper Networks solutions,
please contact your Juniper Networks
representative at 1-866-298-6428 or
authorized reseller.
 Loading...
Loading...