Juniper SECURITY THREAT RESPONSE MANAGER 2008.2 R2 - MANAGING SENSOR DEVICES REV 1, Security Threat Response Manager User Manual
Security Threat Response Manager
Managing Sensor Devices
Release 2008.2 R2
Juniper Networks, Inc.
1194 North Mathilda Avenue
Sunnyvale, CA 94089
USA
408-745-2000
www.juniper.net
Part Number: 530-027301-01, Revision 1

Copyright Notice
Copyright © 2008 Juniper Networks, Inc. All rights reserved. Juniper Networks and the Juniper Networks logo are registered trademarks of Juniper
Networks Inc. in the United States and other countries. All other trademarks, service marks, registered trademarks, or registered service marks in this
document are the property of Juniper Networks or their respective owners. All specifications are subject to change without notice. Juniper Networks
assumes no responsibility for any inaccuracies in this document or for any obligation to update information in this document. Juniper Networks reserves
the right to change, modify, transfer, or otherwise revise this publication without notice.
FCC Statement
The following information is for FCC compliance of Class A devices: This equipment has been tested and found to comply with the limits for a Class A
digital device, pursuant to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the
equipment is operated in a commercial environment. The equipment generates, uses, and can radiate radio-frequency energy and, if not installed and
used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential
area is likely to cause harmful interference, in which case users will be required to correct the interference at their own expense. The following
information is for FCC compliance of Class B devices: The equipment described in this manual generates and may radiate radio-frequency energy. If it
is not installed in accordance with NetScreen’s installation instructions, it may cause interference with radio and television reception. This equipment has
been tested and found to comply with the limits for a Class B digital device in accordance with the specifications in part 15 of the FCC rules. These
specifications are designed to provide reasonable protection against such interference in a residential installation. However, there is no guarantee that
interference will not occur in a particular installation. If this equipment does cause harmful interference to radio or television reception, which can be
determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the following measures:
Reorient or relocate the receiving antenna. Increase the separation between the equipment and receiver. Consult the dealer or an experienced radio/TV
technician for help. Connect the equipment to an outlet on a circuit different from that to which the receiver is connected.
Caution: Changes or modifications to this product could void the user's warranty and authority to operate this device.
Disclaimer
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET
THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE
SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR JUNIPER NETWORKS REPRESENTATIVE FOR A COPY.
Managing Sensor Devices
Release 2008.2 R2
Copyright © 2008, Juniper Networks, Inc.
All rights reserved. Printed in USA.
Revision History
September 2008—Revision 1
The information in this document is current as of the date listed in the revision history.
2
CONTENTS
ABOUT THIS GUIDE
Conventions 1
Audience 1
Technical Documentation 1
Contacting Customer Support 2
1 MANAGING SENSOR DEVICES
Configuring STRM Log Management to Receive Events 3
Managing Sensor Devices 4
Adding a Sensor Device 4
Editing Sensor Devices 6
Enabling/Disabling Sensor Devices 9
Deleting a Sensor Device 9
Configuring Protocols 10
Adding a Protocol 10
Editing a Protocol 17
Deleting a Protocol 17
Grouping Sensor Devices 18
Viewing Sensor Devices Using Groups 18
Creating a Group 18
Editing a Group 19
Copying a Sensor Device to Another Group 20
Removing a Sensor Device From a Group 20
2 CREATING A DEVICE EXTENSION
About Device Extensions 23
Creating a Device Extension Document 24
Viewing Device Extensions 24
Adding a Device Extension 25
Editing a Device Extension 27
Copying a Device Extension 28
Deleting a Device Extension 29
Enabling/Disabling a Device Extension 30
Reporting a Device Extension 30


ABOUT THIS GUIDE
The Managing Sensor Devices Guide provides you with information for configuring
sensor devices (DSMs) in the STRM Log Management interface and integrating
the DSMs with STRM Log Management.
Conventions Table 1 lists conventions that are used throughout this guide.
Table 1 Icons
Icon Type Description
Information note Information that describes important features or
instructions.
Caution Information that alerts you to potential loss of data
or potential damage to an application, system,
device, or network.
Warning Information that alerts you to potential personal
injury.
Audience This guide is intended for the system administrator responsible for setting up
STRM Log Management in your network. This guide assumes that you have
STRM Log Management administrative access and a knowledge of your corporate
network and networking technologies.
Technical
Documentation
You can access technical documentation, technical notes, and release notes
directly from the Juniper Networks support web site at https://juniper.net/support.
Once you access the Juniper Networks support web site, locate the product and
software release for which you require documentation.
Your comments are important to us. Please send your e-mail comments about this
guide or any of the Juniper Networks documentation to:
documentation@juniper.net
Managing Sensor Devices Guide
2 ABOUT THIS GUIDE
Include the following information with your comments:
• Document title
• Page number
Contacting
Customer Support
To help you resolve any issues that you may encounter when installing or
maintaining STRM Log Management, you can contact Customer Support as
follows:
• Log a support request 24/7: https://juniper.net/support/
For access to the Juniper Networks support web site, please contact Customer
Support.
• Access Juniper Networks support and Self-Service support using e-mail:
support@juniper.net
• Telephone assistance: 1-800-638-8296
Managing Sensor Devices Guide
1
MANAGING SENSOR DEVICES
You can configure STRM Log Management to log and correlate events received
from external sources such as security equipment (for example, firewalls and
IDSs) and network equipment (for example, switches and routers). Sensor devices
allow you to integrate STRM Log Management with these external devices. This
chapter provides information on configuring sensor devices to the system
including:
• Configuring STRM Log Management to Receive Events
• Managing Sensor Devices
• Configuring Protocols
• Grouping Sensor Devices
Configuring STRM
Log Management to
Receive Events
Step 1 Configure the device to send events to STRM Log Management.
Step 2 Configure STRM Log Management to receive events from specific devices. See
Step 3 Configure the necessary protocols. See Configuring Protocols.
STRM Log Management allows you to automatically discover sensor devices in
your deployment that are sending syslog messages. Any sensor devices that are
automatically discovered by STRM Log Management appear in the Sensor
Devices window. Automatic discovery of sensor devices can be configured on a
per Event Collector basis using the Auto Detection Enabled parameter in the Event
Collector configuration. For more information, see the STRM Log Management
Administration Guide, Using the Deployment Editor.
To configure STRM Log Management to receive events from devices, you must:
For information on configuring DSMs, see the Configuring DSMs Guide and your
vendor documentation.
Managing Sensor Devices.
Note: You must have administrative privileges to configure sensor devices in
STRM Log Management. For more information on accessing the Administration
Console, see the STRM Log Management Administration Guide.
Managing Sensor Devices Guide

4 MANAGING SENSOR DEVICES
Managing Sensor
Devices
Adding a Sensor
Device
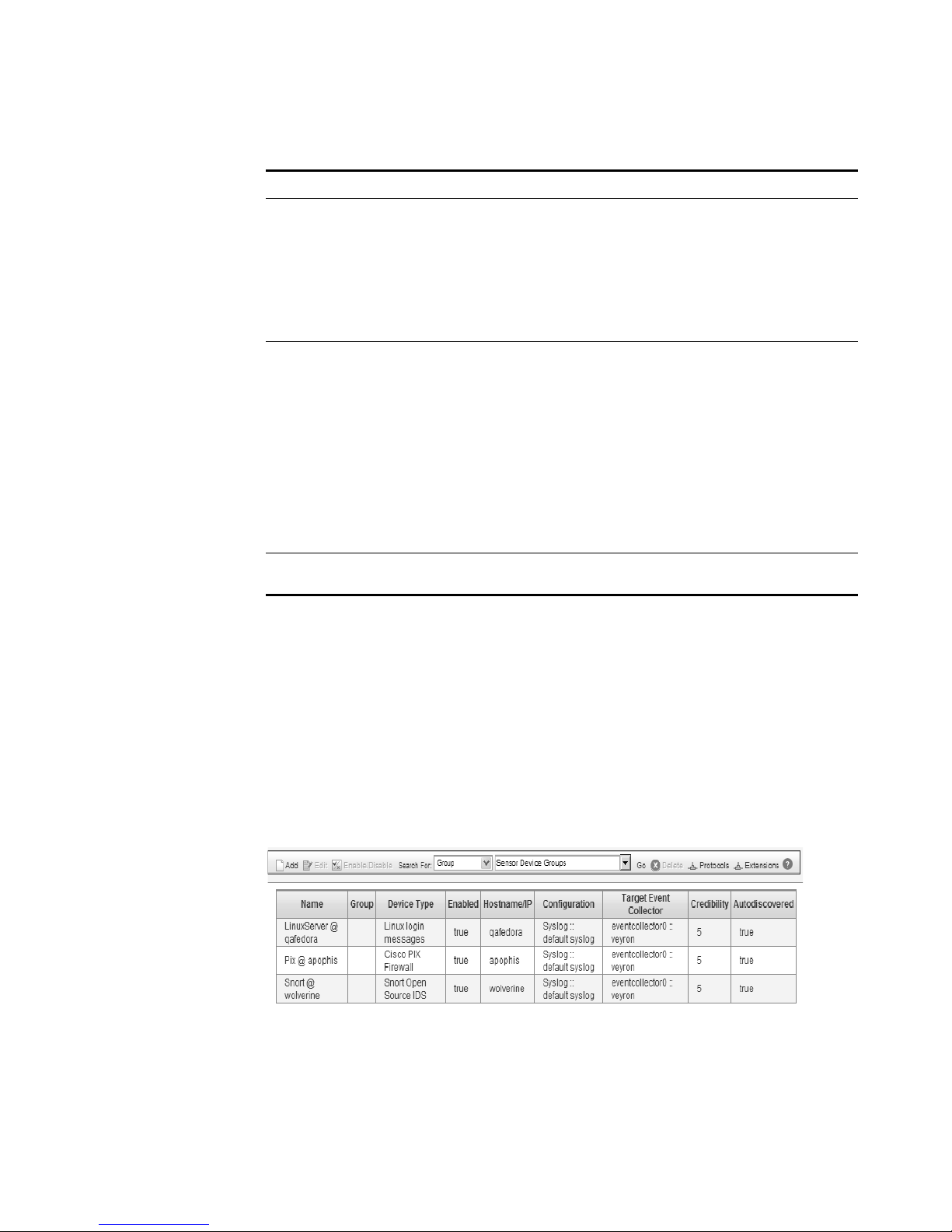
Step 1 In the Administration Console, click the SIM Configuration tab.
Step 2 Click the Sensor Devices icon.
A sensor device provides events to your deployment through DSMs. Using the
Administration Console, you can:
• Add a sensor device. See Adding a Sensor Device.
• Edit an existing sensor device. See Editing Sensor Devices.
• Enable or disable a sensor device. See Enabling/Disabling Sensor Devices.
• Delete a sensor device. See Deleting a Sensor Device.
To add a sensor device to your deployment:
The SIM Configuration panel appears.
The Sensor Devices window appears.
Step 3 Click Add.
The Add a sensor device window appears.
Step 4 Enter values for the parameters:
Managing Sensor Devices Guide

Managing Sensor Devices 5
Table 1- 1 Add a Sensor Device Parameters
Parameter Description
Device Name Specify the desired name of the device.
Sensor Device Type Using the drop-down list, select the type of sensor
device you wish to add.
Protocol Configuration Using the drop-down list box, select the protocol you
wish to use for this sensor device. If the device uses
syslog, a default syslog configuration is automatically
applied. For more information on configuring protocols,
see
Adding a Protocol.
Device Description Specify a description for the sensor device (optional).
Device Hostname/IP Specify the hostname or IP address for the device. If
you wish to add the device using the hostname, please
note that you must enter the hostname as it exactly
appears in the logs sent to STRM Log Management.
Otherwise, STRM Log Management will not process
the events.
Credibility Specify the credibility of the device. The range is from 0
to 10. The credibility indicates the integrity of an event
or offense as determined by the credibility rating from
source devices. Credibility increases if multiple sources
report the same event. The default is 5.
Target Event Collector Using the drop-down list box, select the Event Collector
you wish to use as the target for this device.
Coalescing Events Enables or disables the ability of a sensor device to
coalesce (bundle) events. The default is Yes.
By default, all auto detected sensor devices use the
value configured in the Coalescing Events parameter in
the STRM Settings window. However, when you create
a new sensor device or update the configuration for an
auto detected sensor device, the value configured in
the individual sensor device is the value used by the
sensor device. For more information, see the STRM
Log Management Administration Guide.
Store Event Payload Enables or disables the ability for a sensor device to
store event payload information. The default is Yes.
By default, all auto detected sensor devices use the
value configured in the Store Event Payload parameter
in the STRM Settings window. However, when you
create a new sensor device or update the configuration
for an auto detected sensor device, the value
configured in the individual sensor device is the value
used by the sensor device. For more information, see
the STRM Log Management Administration Guide.
Managing Sensor Devices Guide
6 MANAGING SENSOR DEVICES
Table 1-1 Add a Sensor Device Parameters
Parameter Description
Device Extension Using the drop-down list box, select the device
Extension Use Condition Using the drop-down list box, select the extension use
Groups Select any groups of which you wish this sensor device
extension you wish to use for this sensor device.
Device extensions allow you to immediately extend the
parsing routines of specific devices, which ensures
DSMs send valid data to STRM.
For more information on device extensions, see
Creating a Device Extension.
condition that you wish to use for this sensor device:
• Parsing Enhancement - When the DSM is unable
to parse correctly or is unable to retrieve specific
information from the DSM, the selected device
extension overrides the failed parsing by the DSM.
This is the default setting.
• Parsing Override - When the DSM parses correctly
for most fields, but needs either one or two fields
corrected, the incorrectly parsed field values are
enhanced.
to be a member.
Step 5 Click Save.
Editing Sensor
Devices
Step 1 In the Administration Console, click the SIM Configuration tab.
Step 2 Click the Sensor Devices icon.
Step 3 Select the sensor device you wish to edit.
Step 4 Click Edit.
The Sensor Devices window appears.
To edit a sensor device:
The SIM Configuration panel appears.
The Sensor Devices window appears.
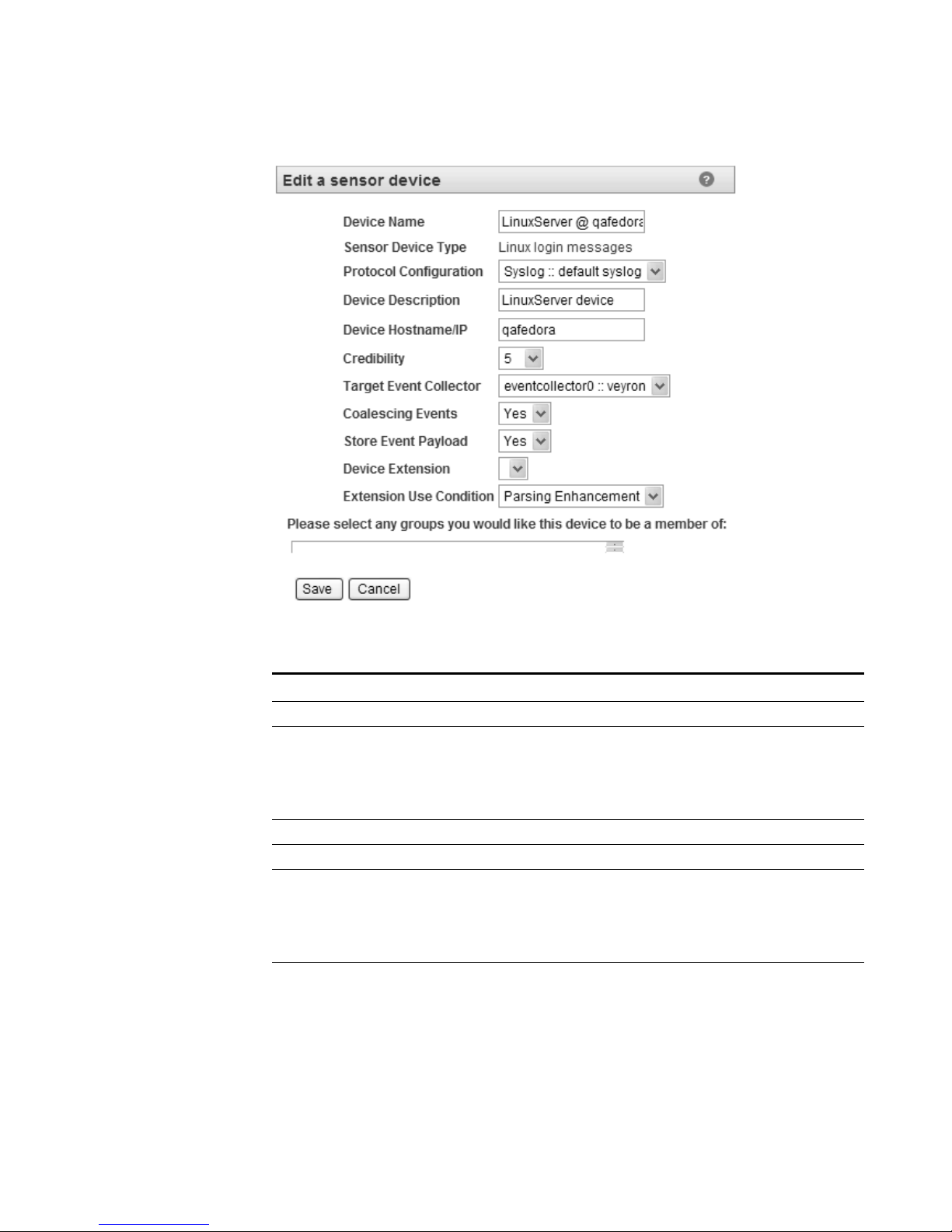
The Edit a sensor device window appears.
Managing Sensor Devices Guide
Managing Sensor Devices 7
Step 5
Edit values for the parameters, as necessary:
Table 1- 2 Edit a Sensor Device Parameters
Parameter Description
Device Name Specify the desired name of the device.
Protocol Configuration Using the drop-down list box, select the protocol you
wish to use for this sensor device. If the device uses
syslog, a default syslog configuration is automatically
applied. For more information on configuring protocols,
see
Adding a Protocol.
Device Description Specify a description for the sensor device (optional).
Device Hostname/IP Specify the hostname or IP address for the device.
Credibility Specify the credibility of the device. The range is from 0
to 10. The credibility indicates the integrity of an event
or offense as determined by the credibility rating from
source devices. Credibility increases as the multiple
sources report the same event. The default is 5.
Target Event Collector Using the drop-down list box, select the Event Collector
you wish to use as the target for this device.
Managing Sensor Devices Guide
 Loading...
Loading...