Juniper SECURITY THREAT RESPONSE MANAGER 2008.2 - MANAGING VULNERABILITY ASSESSMENT V1, Security Threat Response Manager User Manual
Security Threat Response Manager
Managing Vulnerability Assessment
Release 2008.2
Juniper Networks, Inc.
1194 North Mathilda Avenue
Sunnyvale, CA 94089
USA
408-745-2000
www.juniper.net
Part Number: 530-025614-01, Revision 1

Copyright Notice
Copyright © 2008 Juniper Networks, Inc. All rights reserved. Juniper Networks and the Juniper Networks logo are registered trademarks of Juniper
Networks Inc. in the United States and other countries. All other trademarks, service marks, registered trademarks, or registered service marks in this
document are the property of Juniper Networks or their respective owners. All specifications are subject to change without notice. Juniper Networks
assumes no responsibility for any inaccuracies in this document or for any obligation to update information in this document. Juniper Networks reserves
the right to change, modify, transfer, or otherwise revise this publicati on without notice.
FCC Statement
The following information is for FCC compliance of Class A devices: This equipment has been tested and found to comply with the limits for a Class A
digital device, pursuant to part 15 of the FCC rules. These limits are designed to provide reasonable protection against harmful interference when the
equipment is operated in a commercial environment. The equipment generates, uses, and can radiate radio-frequency energy and, if not installed and
used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential
area is likely to cause harmful interference, in which case users will be required to correct the interference at their own expense. The following
information is for FCC compliance of Class B devices: The equipment described in this manual generates and may radiate radio-frequency energy. If it
is not installed in accordance with NetScreen’s installation instructions, i t may cause interference wi th radio and tele vision reception. This equip ment has
been tested and found to comply with the limits for a Class B digital device in accordance with the specifications in part 15 of the FCC rules. These
specifications are designed to provide reasonable protection against such interference in a residential installation. However, there is no guarantee that
interference will not occur in a particular installation. If this equipmen t does cause harmful interference to radio or television reception, which can be
determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the following measures:
Reorient or relocate the receiving antenna. Increase the separation between the equipme nt and receive r. Consult t he dealer o r an experienced ra dio/TV
technician for help. Connect the equipment to an outlet on a circuit different from that to which the receiver is connected.
Caution: Changes or modifications to this product could void the user's warrant y and authority to operate this device.
Disclaimer
THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET
THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE
SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR JUNIPER NETWORKS REPRESENTATIVE FOR A COPY.
Managing Vulnerability Assessment
Release 2008.2
Copyright © 2008, Juniper Networks, Inc.
All rights reserved. Printed in USA.
Revision History
June 2008—Revision 1
The information in this document is current as of the date listed in the revision history.
2
CONTENTS
ABOUT THIS GUIDE
Conventions 3
Technical Documentation 3
Documentation Feedback 3
Requesting Support 4
1 OVERVIEW
Configuring Vulnerability Assessment 5
Viewing Scanners 6
2 MANAGING IP360 SCANNERS
Adding an ip360 Scanner 9
Editing an ip360 Scanner 11
Deleting an ip360 Scanner 11
Exporting Reports 12
3 MANAGING NESSUS SCANNERS
Adding a Nessus Scanner 13
Editing an Nessus Scanner 16
Deleting a Nessus Scanner 16
4 MANAGING NESSUS SCAN RESULT IMPORTERS
Adding a Nessus Scan Result Importer 17
Editing a Nessus Scan Result Importer 19
Deleting a Nessus Scan Result Importer 20
5 MANAGING NMAP SCANNERS
Adding a Nmap Scanner 21
Editing an Nmap Scanner 23
Deleting an Nmap Scanner 24
6 MANAGING QUALYS SCANNERS
Adding a Qualys Scanner 25
Editing a Qualys Scanner 27
Deleting a Qualys Scanner 27
7 MANAGING FOUNDSCAN SCANNERS
Adding a FoundScan Scanner 29
Editing a FoundScan Scanner 32
Deleting a FoundScan Scanner 32
Importing Custom Certificates 32
Example Of TrustedCA.pem File 34
Example of Portal.pem File 34
8 MANAGING JUNIPER NSM PROFILER SCANNERS
Adding a Juniper NSM Profiler Scanner 39
Editing a Profiler Scanner 41
Deleting a Profiler Scanner 41
9 MANAGING RAPID7 NEXPOSE SCANNERS
Adding a Rapid7 NeXpose Scanner 43
Editing a Rapid7 NeXpose Scanner 45
Deleting a Rapid7 NeXpose Scanner 45
10 MANAGING SCAN SCHEDULES
Scheduling a Scan 47
Editing a Scan Schedule 49
Deleting a Scheduled Scan 50
11 VIEWING ASSET PROFILE INFORMATION
INDEX
ABOUT THIS GUIDE
The Managing Vulnerability Assessment Guide provides you with information for
managing vulnerability scanners and scan schedules using STRM.
Conventions Table 1 lists conventions that are used throughout this guide.
Table 1 Icons
Icon Type Description
Information note Information that describes important features or
instructions.
Caution Information that alerts you to potential loss of
data or potential damage to an application,
system, device, or network.
Warning Information that alerts you to potential personal
injury.
Technical
Documentation
Documentation
Feedback
You can access technical documentation, technical notes, and release notes
directly from the Juniper networks Support Web site at
www.juniper.net/support/.
http://
We encourage you to provide feedback, comments, and suggestions so that we
can improve the documentation. Send your comments to
techpubs-comments@juniper.net, or fill out the documentation feedback form at
http://www.juniper.net/techpubs/docbug/docbugreport.html. If you are using e-mail, be
sure to include the following information with your comments:
• Document name
• Document part number
• Page number
• Software release version
Managing Vulnerability Assessment

4 ABOUT THIS GUIDE
Requesting
Support
• Open a support case using the Case Management link at
http://www.juniper.net/support/ or call 1-888-314-JTAC (from the United States,
Canada, or Mexico) or 1-408-745-9500 (from elsewher e).
Managing Vulnerability Assessment
1
OVERVIEW
Vulnerability assessment integration enables vulnerability assessment data to
build profiles of attackers and targets. Vulnerability assessment data uses
correlated event data, network activity, and behavioral changes to remove false
positives to determine the threat level for ea ch critical business asset.
STRM's integration with vulnerability assessment tools allows you to schedule
scans to keep your vulnerability assessment data up-to-date.
Note: You must have permissions to all CIDRs you wish to scan. Also, do not
include CIDRs in your vulnerability assessment that are configured in your global
exclusions list. For more information on global exclusions, see the Offense
Resolutions Users Guide.
This chapter provides an overview of configuring vulnerability assessment ,
including:
• Configuring Vulnerability Assessment
Configuring
Vulnerability
Assessment
• Viewing Scanners
To configure vulnerability assessment, you must:
Step 1 Configure your scanner using one of the following supported scanners:
• Chapter 2 Managing ip360 Scanners
• Chapter 3 Managing Nessus Scanners
• Chapter 4 Managing Nessus Scan Result Importers
• Chapter 5 Managing Nmap Scanners
• Chapter 6 Managing Qualys Scanners
• Chapter 7 Managing FoundScan Scanners
• Chapter 8 Managing Juniper NSM Profiler Scanners
• Chapter 9 Managing Rapid7 NeXpose Scanners
Managing Vulnerability Assessment
6 OVERVIEW
The scanner determines the tests performed during the scanning of a host. The
selected scanner populates your asset profile data including the host information,
ports, and potential vulnerabilities.
Y ou must configure scanners using the Administration Console. For information on
accessing the Administration Console, see the STRM Administration Guide.
Step 2 Schedule vulnerability assessment. See Chapter 10 Managing Scan Schedules.
Step 3 View the results of the asset profile. See Chapter 11 Viewing Asset Profile
Information.
Note: If you add, edit, or delete a scanner or if you add, edit, or delete a scheduled
vulnerability assessment scan, you must select Configurations > Deploy
Configuration Changes from the Administration Console menu for the changes to
take effect.
The results of the scan provides the operating system and version on each CIDR,
server, and version of each port. Also, the scan provides the known vulnerabilities
on discovered ports and services.
Viewing Scanners To view currently co nfigured scanners:
Step 1 In the Administration Console, click the SIM Configuration tab.
The SIM Configuration panel appears.
Step 2 Click the VA Scanners icon.
The VA Scanners window appears.
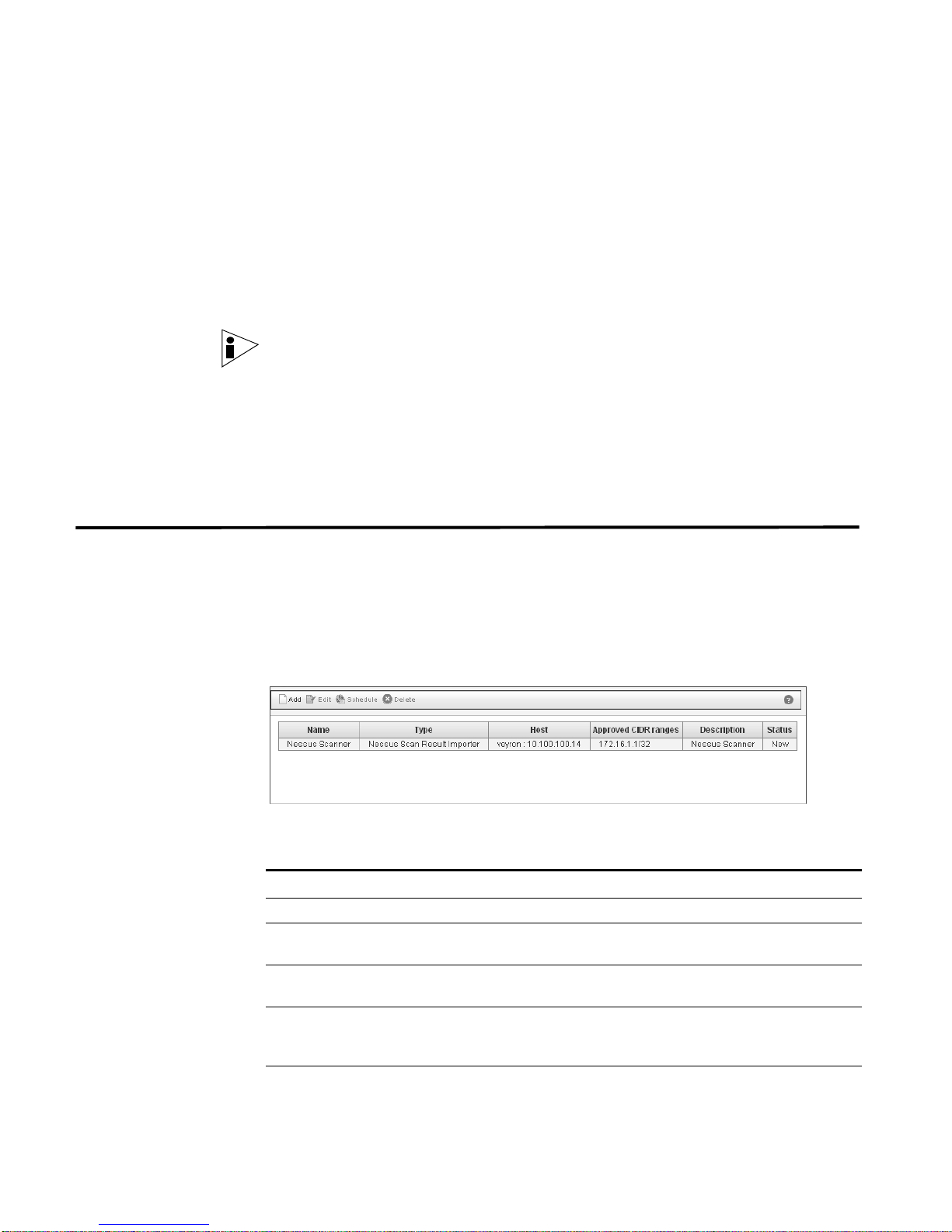
The VA Scanners window provides the following details for each scanner:
Table 1-1 Scanner Parameters
Parameter Description
Name Specifies the name of the scanner.
Type Specifies the type of scanner, for example, Nessus Scan Results
Importer.
Host Specifies the IP address or host name of the host on which the
scanner operates.
Approved CIDR
Ranges
Description Specifies a description for this scanner.
Specifies the CIDR range(s) you wish this scanner to consider.
Multiple CIDR ranges are displayed using a comma separated
list.
Managing Vulnerability Assessment

Viewing Scanners 7
Table 1-1 Scanner Parameters (continued)
Parameter Description
Status Specifies the status of the scanner schedule.
Managing Vulnerability Assessment

2
MANAGING ip360 SCANNERS
STRM uses SSH to access the remote server (SS H ex port server) then retrieves
and interprets the scanned data. STRM supports VnE Manager version
IP360-6.5.2 - 6.7.1.
This chapter includes information on configuring an ip360 scanner including:
• Adding an ip360 Scanner
• Editing an ip360 Scanner
• Deleting an ip360 Scanner
• Adding an ip360 Scanner
Adding an ip360
Scanner
To add an ip360 scanner:
Step 1 In the Administration Console, click the SIM Configuration tab.
The SIM Configuration panel appears.
Step 2 Click the VA Scanners icon.
The VA Scanners window appears.
Step 3 Click Add.
The Add Scanner window appears.
Step 4 Enter values for the following parameters:
Table 2-1 Scanner Parameters
Parameter Description
Scanner Name Specify the name you wish to assign to this scanner. The name
may be up to 255 characters in length.
Description Specify a description for this scanner. The description may be up
to 255 characters in length.
Managed Host Using the drop-down list box, select the managed host you wish
to configure this scanner.
Type Using the drop-down list box, select nCircle IP360 Scanner.
The list of parameters for the selected scanner type appears.
Managing Vulnerability Assessment

10 MANAGING IP360 SCANNERS
Step 5 Enter values for the parameters:
Table 2-2 ip360 Parameters
Parameter Description
Path Specify the location on the remote server where the scan results
are stored. The default is /var/ncircle/.
SSH Server Host
Specify the IP address or host name to the remote server.
Name
SSH Username Specify the SSH remote server username.
Password Specify the password to the remote server.
Private Key
Authorization
Enable (Yes) or disable (No) private key authorization for the
server. The default value is No.
Private Key Path Specify the private key path. The default is
/opt/qradar/conf/vis.ssh.key. This parameter is not used if the
Private Key Authorization parameter is set to false.
File Pattern The Vulnerability Assessment Integration Server (VIS) retrieves
reports, at the configured polling interval, from the nCircle device.
Specify the file pattern you wish to retrieve. The filename pattern
used should select only the ip360 exported XML files. It is
important to ensure that only ip360 XML files are included in the
listing. Typical values for this parameter are:
XML2_ip360.d_([0-9]*).a_([0-9]*).xml
We recommend that you use the above pattern, however, you
can also use the below pattern:
XML2_ip360.d_1.a_([0-9]*).xml
Managing Vulnerability Assessment
Editing an ip360 Scanner 11
Table 2-2 ip360 Parameters (continued)
Parameter Description
Polling Interval Specify the frequency that you wish the VIS to retrieve reports
from the nCircle device. The default value is 900 seconds.
Note: If the scanner is configured to use a password, the SSH scanner server to
which STRM connects must support password authentication. If it does not, SSH
authentication for the scanner may fail. Make sure the following line appears
exactly as shown in your sshd_config file, which is typically found in the /etc/ssh
directory on the SSH server:
PasswordAuthentication yes. If your scanner
server does not use OpenSSH, the configuration may be slightly different.
Step 6 To configure the CIDR ranges you wish this scanner to consider:
a In the text field, enter the CIDR range you wish this scanner to consider or click
Browse to select the CIDR range from the network list.
b Click Add.
Step 7 Click Save.
Step 8 From the STRM Administration Console menu, select Configurations > Deploy
Configuration Changes.
Editing an ip360
Scanner
Step 1 In the Administration Console, click the SIM Configuration tab.
Step 2 Click the VA Scanners icon.
Step 3 Select the scanner you wish to edit.
Step 4 Click Edit.
Step 5 Update parameters, as necessary. See Table 2-2.
Step 6 Click Save. From the STRM Administration Console menu, select Configurations
Deleting an ip360
Scanner
Step 1 In the Administration Console, click the SIM Configuration tab.
Step 2 Click the VA Scanners icon.
To edit a scanner:
The SIM Configuration panel appears.
The V A Scanners window appears.
The Edit Scanner window appears.
> Deploy Configuration Changes.
To delete a scanner:
The SIM Configuration panel appears.
The V A Scanners window appears.
Managing Vulnerability Assessment

12 MANAGING IP360 SCANNERS
Step 3 Select the scanner you wish to delete.
Step 4 Click Delete.
A confirmation window appears.
Step 5 Click Ok.
Step 6 From the STRM Administration Console menu, select Configurations > Deploy
Configuration Changes.
Exporting Reports For the VIS to retrieve reports that are exported from the ip360 device, you must
configure the automated export of reports on the ip360 device.
To co nfigure automated export of reports:
Step 1 Log in to the IP360 VNE Manager UI.
Step 2 Select Administer -> System -> VNE Manager -> Automated Export from the
left-hand navigation area.
The Automated Export menu appears.
Step 3 From the Automated Export menu, click the Export to File tab.
Step 4 Click the Help link at the top right-hand corner of the menu.
The help that appears provides a link to instructions for configuring automated
exports of reports using ssh. To integrate with STRM, the export must be
configured to use the XML2 format.
Managing Vulnerability Assessment
3
MANAGING NESSUS SCANNERS
Nessus software includes separate client and server components. You can install
the client on the same system as the server. However, for performance reasons,
you can provide a dedicated Nessus server with distributed clients, which means a
separate client and server. The Nessus client may consume significant system
resources during large or detailed scans.
Note: Since Nessus may require high CPU usage, we recommend that you do not
install your Nessus software on a network critical system.
STRM supports Nessus version 2.2.x to 3.0.4. For more information on installing
and configuring Nessus, see your Nessus documentation.
This chapter provides information on managing your Nessus scanner including:
• Adding a Nessus Scanner
• Editing an Nessus Scanner
Adding a Nessus
Scanner
Step 1 In the Administration Console, click the SIM Configuration tab.
Step 2 Click the VA Scanners icon.
Step 3 Click Add.
Step 4 Enter values for the following parameters:
• Deleting a Nessus Scanner
To add a Nessus scanner:
The SIM Configuration panel appears.
The VA Scanners window appears.
The Add Scanner window appears.
Table 3-1 Scanner Parameters
Parameter Description
Scanner Name Specify the name you wish to assign to this scanner. The name
may be up to 255 characters in length.
Managing Vulnerability Assessment

14 MANAGING NESSUS SCANNERS
Table 3-1 Scanner Parameters (continued)
Parameter Description
Description Specify a description for this scanner. The description may be up
Managed Host Using the drop-down list box, select the managed host you wish
Type Using the drop-down list box, select Nessus Scanner.
The list of parameters for the selected scanner type appears.
to 255 characters in length.
to configure this scanner.
Step 5 Enter values for the parameters:
Table 3-2 Nessus Parameters
Parameter Description
Path Specify the location of the Nessus client executable file on the
Server Host Name Specify the IP address or DNS name of the Nessus server as
Server Port Specify the port for the nessus server. The default is port 1241.
Username Specify the Nessus username that the Nessus client uses to
Password Specify the Nessus password.
Nessus client host. The default is /usr/bin/nessus.
seen by the Nessus client. The default is localhost.
authenticate with the Nessus server.
Managing Vulnerability Assessment
Adding a Nessus Scanner 15
Table 3-2 Nessus Parameters (continued)
Parameter Description
Disable Pixmaps Enables (Yes) or Disables (No) pixmaps. If the Nessus
installation includes a graphical client, set this parameter to Yes.
The default is No.
To determine if the Nessus client has graphical interf ace support,
you must log in to the system that is hosting the Nessus client
and execute the client with no parameters. An error message
appears if no graphical client is installed.
Remote
Hostname
Specify the DNS name or IP address of the system hosting the
Nessus client.
Login Username Specifies the username used by STRM to authenticate the SSH
connection.
Enable Key
Authentication
Enables (Yes) or disables (No) public/private key authentication.
If enabled, STRM attempts to authenticate the SSH connection
using the provided private key. The default is Yes. For more
information, see your SSH documentation for configuring public
key authentication.
Login Password If Enable Key Authentication is disabled, specify the password
that STRM uses to authenticate the SSH connection.
If key authentication is disabled, you must set a login password.
Private Key File Specify the directory path to the file that contains the private key
information. STRM uses the private key to auth e ntic at e the S SH
connection, if you are using SSH key based authentication. The
default is /opt/qradar/conf/vis.ssh.key.
This parameter is mandatory if key authentication is enabled.
Remote Temp Dir Specify the directory on the Nessus client that STRM may use to
store temporary files used during the execution of the Nessus
client. These files are removed once the client has successfully
executed. Default setting is /tmp.
Note: If the scanner is configured to use a password, the SSH scanner server to
which STRM connects must support password authentication. If it does not, SSH
authentication for the scanner will fail. Make sure the following line appears exactly
as shown in your sshd_config file, which is typically found in the /etc/ssh directory
on the SSH server:
does not use OpenSSH, the configuration may be slightly different.
Step 6 To configure the CIDR ranges you wish this scanner to consider:
a In the text field, enter the CIDR range you wish this scanner to consider or click
Browse to select the CIDR range from the network list.
b Click Add.
Step 7 Click Save.
Step 8 From the STRM Administration Console menu, select Configurations > Deploy
Configuration Changes.
PasswordAuthentication yes. If your scanner server
Managing Vulnerability Assessment
16 MANAGING NESSUS SCANNERS
Editing an Nessus
Scanner
Step 1 In the Administration Console, click the SIM Configuration tab.
Step 2 Click the VA Scanners icon.
Step 3 Select the scanner you wish to edit.
Step 4 Click Edit.
Step 5 Update parameters, as necessary. See Table 3-2.
Step 6 Click Save.
Step 7 From the STRM Administration Console menu, select Configurations > Deploy
Deleting a Nessus
Scanner
Step 1 In the Administration Console, click the SIM Configuration tab.
To edit a scanner:
The SIM Configuration panel appears.
The VA Scanners window appears.
The Edit Scanner window appears.
Configuration Changes.
To delete a scanner:
The SIM Configuration panel appears.
Step 2 Click the VA Scanners icon.
The VA Scanners window appears.
Step 3 Select the scanner you wish to delete.
Step 4 Click Delete.
A confirmation window appears.
Step 5 Click Ok.
Step 6 From the STRM Administration Console menu, select Configurations > Deploy
Configuration Changes.
Managing Vulnerability Assessment
 Loading...
Loading...