Page 1

JUNOS SPACE SECURITY DESIGN
DATASHEET
Product Overview
In properly designed networks, security is
an integral attribute of the system. When
security is treated as an aerthought, or
developed independent of the overall
design requirements, it is oen costly,
inflexible, and risky.
Enterprises are mostly driven by
time-to-market pressures and oen
deploy systems before achieving
appropriate levels of quality and
security. Consequences can impact
overall deployment schedules, increase
complexity, and even delay profitability.
Junos Space Security Design helps
integrate a secure network design
workflow into your branch deployment
solution. The result is faster time
to market, reduced security risk,
centralized, consistent configuration of
the network, and overall lower cost of
maintenance.
Product Description
Juniper Networks® Junos® Space Security Design is a state-of-the-art, scalable enterprise
solution designed to automate the visualization, configuration, and deployment of the
security architecture of a multi-domain network.
Large-scale network security implementations often increase operational complexity
and cause configuration errors leading to heightened security risk. Considering the critical
elements of a network security deployment as topology visualization, business policy
management, VPN implementation, as well as provisioning, distribution and application
of required configurations require a holistic, smart, and automated design approach.
Grappling with compliance requirements and the need to reduce administrative costs,
IT departments can translate business policies easily and quickly into the network
infrastructure with minimal manual intervention using Security Design. Benefiting from
a platform-wide consistent visual interface, Security Design features a sophisticated yet
simple web based design environment.
allowed
HTTPS
MS-SQL
RADIUS
San Francisco
denied
HTTP
TELNET
SSH
SRX240
Internet
London
SRX240
Branch
allowed
SNMP
SSH
SRX3400
Security Design
running on
Junos Space
Figure 1: Typical topology for headquarters to branch security
HQ
1
Page 2
Security Design provides an innovative method to model
network security between network domains by providing security
architects with a solution that is easy to use and easy to deploy.
The application automates security design through a familiar
web-based interface with design and deployment workflows, and
facilitates rapid deployment of thousands of security devices to
branch locations securely and efficiently.
Unlike solutions that require highly skilled onsite network
security architects at each branch location, multi-domain
security architecture can be designed once in the corporate
office, then distributed and applied to each branch network via
several convenient and secure methods. Using Security Design,
IT departments can automate the translation of business policy
requirements into the network infrastructure, reducing the
complexity while increasing consistency and reliability.
Junos Space
Security Design is a software application that is built on the Junos
Space network application platform, and it leverages all Junos
Space platform capabilities. The premise of Security Design is
to provide the security architect with an environment in which
it is easy to design, configure and deploy required security rules.
It provides sophisticated, end-to-end visibility to the network
topology, drag-and-drop policy associations between network
resources, wizards to configure and provision VPN and device
configurations, and convenient and secure deployment options.
Junos Space is underpinned by a programmable application
environment, a powerful runtime environment, and a Web 2.0 GUI.
Figure 2: Security Design is an application on Junos Space platform
Architecture and Key Components
Security Design represents several innovations including topology
based policy definition to model security devices once and have
the configuration ready to push to thousands of devices, policy
abstraction to create a logical security topology, and patent
pending security domains to allow common security restrictions to
be applied to a grouping of distributed network resources. These
innovations are embodied in the following components:
• Object builder, to create applications, domains, and addresses.
• Security whiteboard, to design the network security topology,
establish policies, and create VPN configurations.
• Rapid deployment, to specify branch settings, and create and
distribute the configuration profiles.
Features and Benefits
Security whiteboard and object builder are the two workspaces
included to facilitate the architecture design and the device
configurations. Functionality to trace and control the progress is
provided by the job management feature of Security Design.
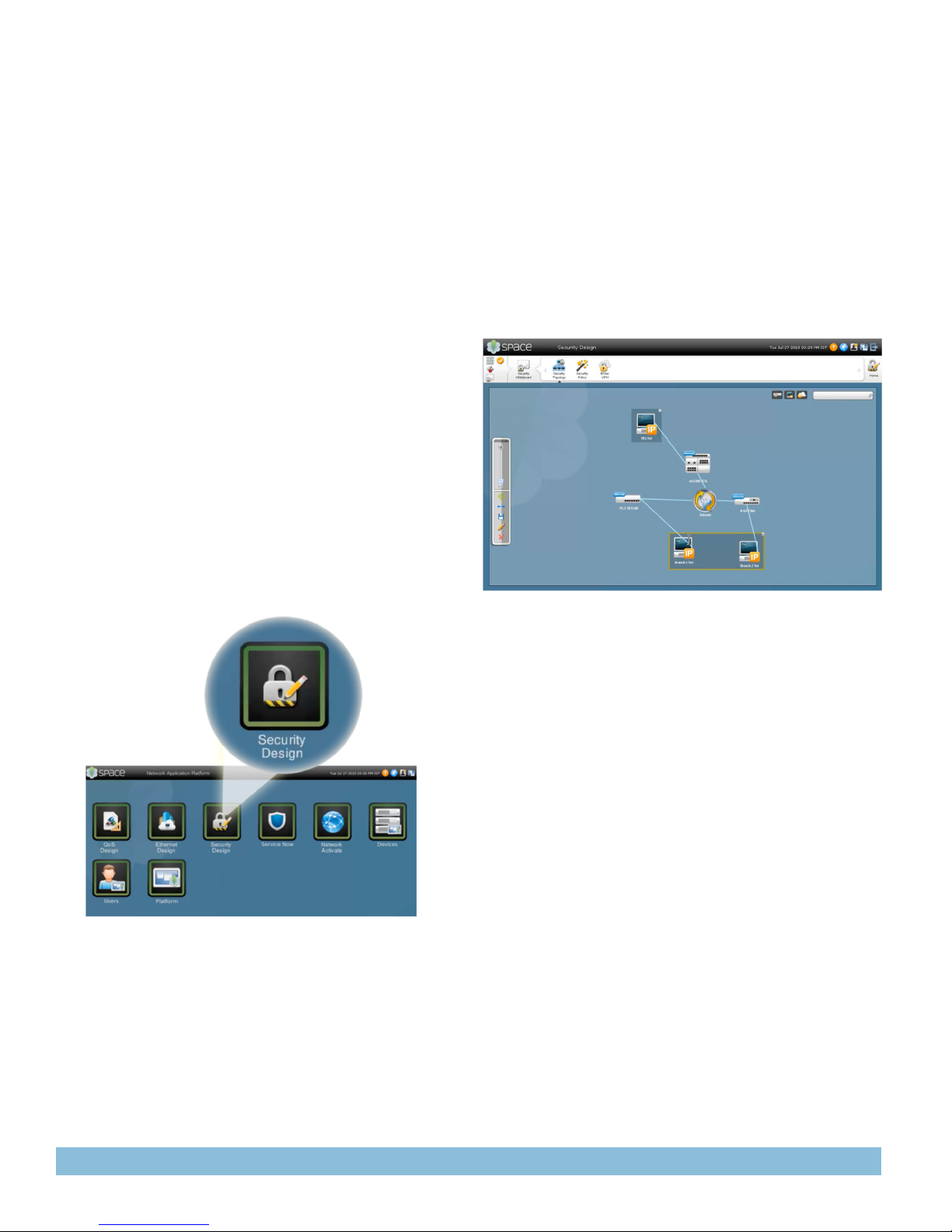
Figure 3: Security whiteboard and network topology
Security Whiteboard
Security whiteboard consists of three sub-functions—security
topology, security policy, and IPsec VPN configurations. Using
topology view of the whiteboard the user can create and manage
network objects of a targeted network domain. Each object allows
the user to view its specific properties and thus make further
adjustments. When specific topology information is not available,
the architect can simply import the new topology from a comma-
separated values (CSV) file that can be created using other design
tools. The objects within the security whiteboard workspace include
applications, security domains, and addresses that can be created
and managed using the object builder feature of Security Design.
Security policies that control the traffic between security domains
are applied to the topology using GUI tools provided in the
workspace. For example, the user can simply establish a policy
association between two security domains by dragging a line
from the toolset. Then, the details of the policy and the traffic
rules are created graphically in a dialog box related to this policy
association. In the next step, the architect decides whether to
provision the security policy immediately or schedule it for a later
date to finally complete policy implementation between the
required security domains.
2
Page 3

Figure 4: Creating a policy using security whiteboard
IPsec VPN is the last of the Security Whiteboard functions
enabling configuration of thousands of VPNs in hub spoke, full
mesh, or site-site, and the monitoring and troubleshooting of
these tunnels:
A sophisticated VPN configuration wizard simplifies an otherwise
complex VPN setup, reducing it to a few simple steps.
1. Define VPN properties as name, VPN type, profile, and the
tunnel IP subnet.
2. Specify the endpoints of the tunnel on the topology diagram.
3. Provision the VPN configuration to the network resources.
Object Builder
Object builder is a multi-tenant workspace that contains standard
network objects and enables the addition of new devices. Similar
to the security whiteboard workspace, network resources as
applications, security domains, and addresses are displayed
graphically. A set of predefined, common applications such as
FTP, telnet, SSH, SMTP, netbios-session, and many others are
shipped with Security Design. If a new application is needed, the
user can conveniently provide the details using object builder, and
it will simply add the application to the Junos Space database.
Figure 5: Adding devices using object builder
Rapid Deployment
Junos Space provides a rapid deployment workflow that is common
to all Junos Space applications. Similar to the other workspaces
in Security Design, rapid deployment follows a familiar convention
to present an overview of the devices that are maintained in Junos
Space, available to deploy, and can be added to the topology as
required. Introduction of new devices to the network infrastructure,
including the required security policy configuration, is as simple as
creating a configuration file, known as configlet, and applying it to the
network device in the branch location.
Central management and simple provisioning capabilities of rapid
deployment enable network operators to deploy and provision
new devices with minimal manual intervention.
Features and Benefits
Table 1: Junos Space Security Design features and benefits
FEATURE BENEFIT
Web-based Interface • Junos Space applications are web-based and provide a simple to use but sophisticated browser interface with
Application within the Junos
Space family
Granular device configuration • Anywhere in the workflow, each object provides a rich set of property information that is either gathered from the
Policy life cycle management • Provides orchestration of policy design, configuration, and granular visibility of policies.
IPsec VPN configuration wizard • IPsec VPN wizard as a component of whiteboard helps the user design and provision, otherwise complex VPN
familiar design tools.
• Users can focus on their task, better apply their knowledge, interact within a familiar environment, and challenge
their creativity as they design. The consistent interface among applications, whether it is a Juniper or a third-party
application, lets users accomplish tasks with greater productivity.
• As a member of the Junos Space family, Security Design provides the user with a common Web interface
thataccesses an expanded Junos Space feature set.
• Rapid deployment is an example of a feature shared among all Junos Space applications.
Junos Platform or created as a part of the design process.
• In-depth property information helps the architect make accurate design decisions.
• Benefiting from the policy abstraction layer handling thousands of devices provides the operator with ecient ways
to optimize policies, clean up unused rules, and design and enforce policy compliance mandates.
• Eliminates rule-by-rule policy definitions benefiting from the abstraction layer and promotes accuracy, simpicity and
faster time to deployment.
configurations easily.
• Enables configuration of thousands of VPNs in hub spoke, full mesh, or site-site topologies.
• Provides monitoring and troubleshooting of these VPN tunnels.
3
Page 4

Table 1: Junos Space Security Design Features and Benefits (continued)
FEATURE BENEFIT
Network topology visualization • Calculates the path between endpoints and determine which policy enforcement point will be impacted.
• Allows the user to design the security policy and let the system intelligently establish which device gets aected.
Job management • Tasks such as VPN deployment or policy application can be provisioned either immediately or at a scheduled date
Rapid deployment wizard • Facilitates network device management, e.g. when a new device is introduced to the network, it must be configured
and time.
• Provides the flexibility of deciding when to deploy a particular function and monitoring its progress.
• Facilitates additional control over the readiness and deployment schedule.
and required security policies applied.
• Using this wizard accessed from within the Security Design workspace, the required configuration file can be created
and distributed to the branch location conveniently.
• Application of configuration does not require an onsite security architect and, when applied, the device is simply
commissioned to the network with a preset configuration.
• Accelerates the deployment of a network device with controlled configuration settings.
• Greatly reduces or eliminates the risk of security configuration errors.
Specifications
Client Browser Support
Supported browsers include Firefox 3.0, Internet Explorer 7.0, and
above.
VMware Version
Junos Space works with VMware vSphere 4.0 and above.
Juniper Platforms
Security Design runs on Juniper Networks devices running
Junos OS 9.0 and later releases.
Junos Space Appliance
Security Design runs on the Junos Space appliance.
Juniper Networks Services and Support
Juniper Networks is the leader in performance-enabling services
and support, which are designed to accelerate, extend, and
optimize your high-performance network. Our services allow
you to bring revenue-generating capabilities online faster so
you can realize bigger productivity gains and faster rollouts of
new business models and ventures. At the same time, Juniper
Networks ensures operational excellence by optimizing your
network to maintain required levels of performance, reliability, and
availability. For more details, please visit www.juniper.net/us/en/
products-services.
Ordering Information
When ordering Junos Space Security Design two items are
required: the Junos Space plaform—physical or a virtual appliance
for VMWare environment—and a Junos Space Security Design
application license. The SKUs are as follows:
MODEL NUMBER DESCRIPTION
SPC1500-A-BSE Junos Space JA1500 Appliance
SPC-VA-BSE Junos Space Virtual Appliance for VMWare
environment
SPC-SECDGN-FWVPN Add Junos Space Security Design application
- soware license
For further information on Junos Space Platform please refer to:
www.juniper.net/us/en/products-services/software/junos-
platform/junos-space/platform.
About Juniper Networks
Juniper Networks, Inc. is the leader in high-performance
networking. Juniper offers a high-performance network
infrastructure that creates a responsive and trusted environment
for accelerating the deployment of services and applications
over a single network. This fuels high-performance businesses.
Additional information can be found at www.juniper.net.
Corporate and Sales Headquarters
Juniper Networks, Inc.
1194 North Mathilda Avenue
Sunnyvale, CA 94089 USA
Phone: 888.JUNIPER (888.586.4737)
or 408.745.2000
Fax: 408.745.2100
www.juniper.net
Copyri ght 2010 Juniper Netw orks, Inc. All r ights reser ved. Juniper N etworks, t he Juniper Net works logo, Jun os,
NetScr een, and Screen OS are registere d trademarks o f Juniper Netw orks, Inc. in th e United States and ot her
countri es. All other trad emarks, se rvice marks , registered m arks, or regis tered serv ice marks are th e property o f
their re spective own ers. Junipe r Networks a ssumes no res ponsibilit y for any inaccurac ies in this docum ent. Juniper
Netwo rks reser ves the right to cha nge, modify, tran sfer, or otherw ise revise thi s publication w ithout notice.
1000332-001-EN Sept 2010
4
APAC Headquar ters
Juniper Networks (Hong Kong)
26/F, Citypla za One
1111 King’s Road
Taikoo Shing, Hong Kong
Phone: 852. 2332.3636
Fax: 852.2574.7803
Printed o n recycled pape r
EMEA Headquarters
Juniper Networks Ireland
Airside Business Park
Swords, County D ublin, Ireland
Phone: 35.31.8903.600
EMEA Sales: 00800.4586.4737
Fax: 35.31.8903.601
To purchase Juniper Networks solutions,
please contact your Juniper Networks
representative at 1-866-298-6428 or
authorized reseller.
 Loading...
Loading...