Page 1

J SERIES SERVICES
J SERIES SERVICES
J2320, J2350, J4350, and J6350
ROUTERS
J2320, J2350, J4350, and J6350
DATASHEET
Product Overview
Juniper Networks J Series
Services Routers extend enterprise
applications and deliver reliable
connectivity to remote offi ces
with a powerful blend of highperformance network protection and
advanced services. J Series Services
Routers leverage the modular
JUNOS Software and Juniper’s rich
product and partner portfolio to
consolidate market leading security,
application optimization, and voice
capabilities onto a single, easy to
manage platform. Our innovative
security approach inseparably
integrates routing and fi rewalls for
exceptional performance. Available
options, including integrated
Juniper Networks WX application
acceleration and integrated voice
gateway technology from Avaya,
make the J Series the ideal choice
for closing the distance between
central resources and remote
locations.
Product Description
Enterprises are faced with a number of challenges and opportunities by converging
voice, video and data to one network. This consolidation of network elements reduces
cost by easing deployment of SIP enabled VoIP, real-time high-defi nition Telepresence
and standardizing on a consistent infrastructure network operating system like Juniper
Networks
interactions with suppliers, and employee productivity. This mission-critical multimedia network must be always on and always available. To accomplish this, fully
integrated stateful security is a key requirement, not merely forwarding packets without
regard to the intended application or individual user session. JUNOS Software provides
the high-performance networking infrastructure that helps enterprises implement key
initiatives that:
• Integrates routing, fi rewalling and vpn into one best in class secure router. By
• Minimizes the cost of installing and operating a network by deploying J Series. With
Whether you have an enterprise network or a service provider looking for customer
premise equipment for an MPLS or IP network, the J Series offers a mix of features that
excel at both. By leveraging JUNOS, the J Series can be deployed at medium to large
sites and the wide range of interfaces scales the bandwidth as necessary for today’s real
time communications
®
JUNOS® Software. These new technologies improve; customer relations,
securing an enterprise’s mission critical information and protecting the network from
vulnerabilities and attack, the J Series offers a combination of features that increases
productivity and reduces costs. With JUNOS release 9.6, the J Series enhances these
features with Unifi ed Threat Management, consisting of antivirus, antispam, Web
fi ltering and intrusion prevention system. These advanced security features can
eliminate a standalone appliance and be applied with a software key.
the modular, protected mode design of JUNOS Software and the rigorous JUNOS
development and testing process, there are fewer system process failures. The single
code source of JUNOS makes the qualifi cation of new releases across the network
much simpler. In addition, superior confi guration management reduces human errors
that could lead to network downtime.
1
Page 2

Table 1: Key Hardware Features of the J Series Services Routers
PRODUCT DESCRIPTION
J2320 • Support for T1, E1, Synchronous Serial, ISDN Basic Rate Interface, ADSL2/ADSL2+, G.SHDSL, and Gigabit
J2350 • Support for T1, E1, Synchronous Serial, ISDN BRI, ADSL/2/2+, G.SHDSL, and Gigabit Ethernet interfaces
Ethernet interfaces
• Support for integrated IP telephony using the Avaya IG550 Integrated Gateway
• Support for application acceleration using the Juniper Networks ISM200 Integrated Services Module
• 4 xed Gigabit Ethernet LAN ports, and 3 PIM slots
• 512 MB DRAM default, expandable to 1 GB DRAM
• 512 MB compact ash default, upgradeable to 1 GB
• Hardware encryption acceleration (optional)
• Full UTM; antivirus, antispam, Web ltering, intrusion prevention system (with high memory version)
• Unied Access Control (UAC) and content ltering
• Support for integrated IP telephony using the Avaya IG550 Integrated Gateway
• Support for application acceleration using the Juniper Networks ISM200 Integrated Services Module
• 4 xed Gigabit Ethernet LAN ports, and 5 PIM slots
• 512 MB DRAM default, expandable to 1 GB DRAM
• 512 MB compact ash default, upgradeable to 1 GB
• Hardware encryption acceleration (optional)
• DC version available
• NEBS-compliant models available
• Full UTM; antivirus, antispam, Web ltering, intrusion prevention system (with high memory version)
• Unied Access Control (UAC) and content ltering
J4350 • Support for T1, E1, Fast Ethernet, Synchronous Serial, ISDN BRI, ADSL2/ADSL2+, G.SHDSL, DS3, E3, Gigabit
J6350 • Support for T1, E1, Fast Ethernet, Synchronous Serial, ISDN BRI, ADSL2/ADSL2+, G.SHDSL, DS3, E3, Gigabit
Ethernet interfaces
• Support for integrated IP telephony using the Avaya IG550 Integrated Gateway
• Support for application acceleration using the Juniper Networks ISM200 Integrated Services Module
• 4 xed Gigabit Ethernet LAN ports, 4 PIM slots, and 2 EPIM/PIM slots
• DC version available
• 512 MB or 1 GB DRAM default, expandable to 2 GB DRAM
• 512 MB compact ash default, upgradeable to 1 GB
• Hardware encryption acceleration (optional)
• NEBS-compliant models available
• Full UTM; antivirus, antispam, Web ltering, intrusion prevention system (with high memory version)
• Unied Access Control (UAC) and content ltering
Ethernet interfaces
• Support for integrated IP telephony using the Avaya IG550 Integrated Gateway
• Support for application acceleration using the Juniper Networks ISM200 Integrated Services Module
• 4 xed Gigabit Ethernet LAN ports, 2 PIM slots, and 4 EPIM/PIM slots
• DC version available
• 1 GB DRAM default, expandable to 2 GB DRAM
• 512 MB compact ash default, upgradeable to 1 GB
• Hardware encryption acceleration standard
• NEBS-compliant models available
• Redundant AC or DC power supplies
• Full UTM; antivirus, antispam, Web ltering, intrusion prevention system (with high memory version)
• Unied Access Control (UAC) and content ltering
2
Page 3
Features and Benefits
Secure Routing
Should you use a router and a firewall to secure your network?
By building the branch J Series Services Routers with best-inclass routing and firewall capabilities in one product, enterprises
don’t have to make that choice. Why forward traffic if it’s not
legitimate?
J Series for the branch checks the traffic to see if it is legitimate,
and only forwards it on when it is. This reduces the load on
the network, allocates bandwidth for all other mission-critical
applications, and secures the network from hacking.
The main purpose of a secure router is to provide firewall
protection and apply policies. The rewall (zone) functionality
inspects trafc ows and state to ensure that originating and
returning information in a session is expected and permitted for
a particular zone. The security policy determines if the session
can originate in one zone and traverse to another zone. This
architectural choice receives packets from a wide variety of
clients and servers and keeps track of every session, of every
application, and of every user. It allows the enterprise to make
sure that only legitimate traffic is on its network and that traffic
is owing in the expected direction.
“Untrust” Zone
INTERNET
High Availability
Active/StandbyActive/Standby
INTERNETINTERNET
Active
J Series
EX Series EX Series
Active
EX Series
By using the Web interface or CLI, enterprises can create a
series of security policies that will control the traffic from within
and in between zones by defining policies. At the broadest
level, all types of traffic can be allowed from any source in
security zones to any destination in all other zones without any
scheduling restrictions. At the narrowest level, policies can be
created that allow only one kind of traffic between a specified
host in one zone and another specified host in another zone
during a scheduled time period.
Standby
J Series
Active
J SeriesJ Series
EX Series
Figure 2: High availability
Failure
Failure
EX Series
EX Series
Active
J SeriesJ Series
EX Series
Active/ActiveActive/Active
INTERNETINTERNET
Active
J SeriesJ Series
EX Series
“Trust” Zone
Intranet
“Guest” Zone
“DMZ” Zone
Figure 1: Firewalls, zones and policies
To ease the configuration of a firewall, J Series for the branch
uses two features—“zones” and “policies.” While these can be
user defined, the default shipping configuration contains, at a
minimum, a trust and an untrust zone. The trust zone is used
for configuration and attaching the LAN to the branch J Series
routers. The untrust zone is used for the WAN or Internet
interface. To simplify installation and make configuration easier,
a default policy is in place that allows traffic originating from the
trust zone to ow to the untrust zone. This policy blocks all trafc
originating from the untrust zone to the trust zone. A traditional
router forwards all trafc without regard to a rewall (session
awareness) or policy (origination and destination of a session).
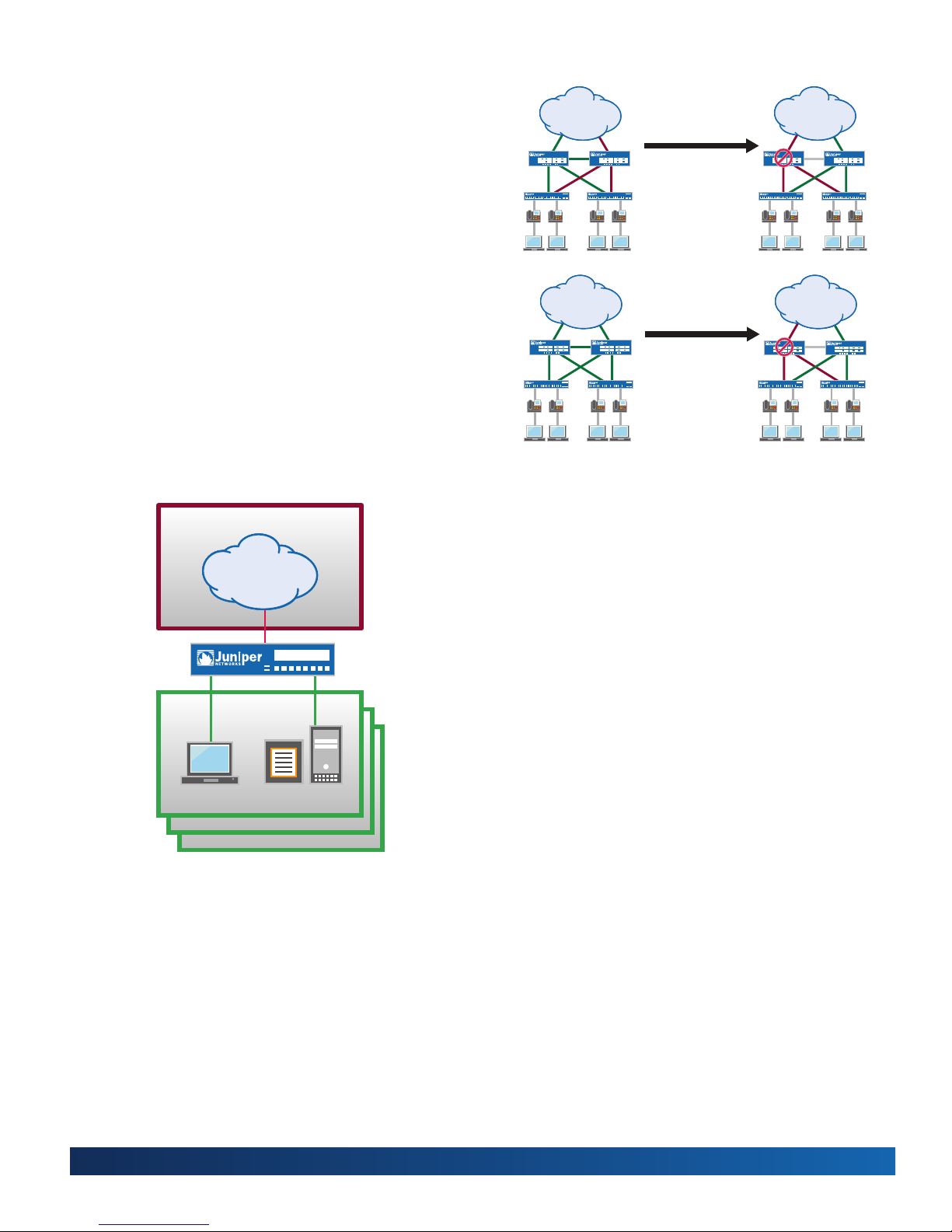
High Availability
JUNOS Services Redundancy Protocol (JSRP) is a core feature
of the J Series for the branch. JSRP enables a pair of security
systems to be easily integrated into a high availability network
architecture, with redundant physical connections between
the systems and the adjacent network switches. With link
redundancy, Juniper Networks can address many common
causes of system failures, such as a physical port going bad
or a cable getting disconnected, to ensure that a connection
is available, without having to fail over the entire system. This
is consistent with a typical active/standby nature of routing
resiliency protocols.
When J Series routers for the branch are configured as an
active/active pair, trafc and conguration will be mirrored
automatically to provide active firewall and VPN session
maintenance in case of a failure. The J Series will now
synchronize both configuration and runtime information.
As a result, during failover, synchronization of the following
information is shared: connection/session state and ow
information, IPsec security associations, Network Address
Translation (NAT) trafc, address book information, conguration
changes, and more. In contrast to the typical router active/
standby resiliency protocols such as Virtual Router Redundancy
3
Page 4
Protocol (VRRP), all dynamic ow and session information is
lost and must be reestablished in the event of a failover. Some
or all applications sessions will have to restart depending on the
convergence time of the links or nodes. By maintaining state,
not only is the session preserved, but security is intact. In an
unstable network, this active/active conguration also mitigates
link apping affecting session performance.
Session-Based Forwarding Without the Performance Hit
In order to optimize the throughput and latency of the combined
router and firewall, JUNOS implements session-based
forwarding, an innovation that combines the session state
information of a traditional firewall and the next-hop forwarding
of a classic router into a single operation. With JUNOS, a
session that is permitted by the forwarding policy is added to
the forwarding table along with a pointer to the next-hop route.
Established sessions have a single table lookup to verify that
the session has been permitted and to find the next hop. This
efficient algorithm improves throughput and lowers latency
for session traffic when compared with a classic router that
performs multiple table lookups to verify session information and
then to find a next-hop route.
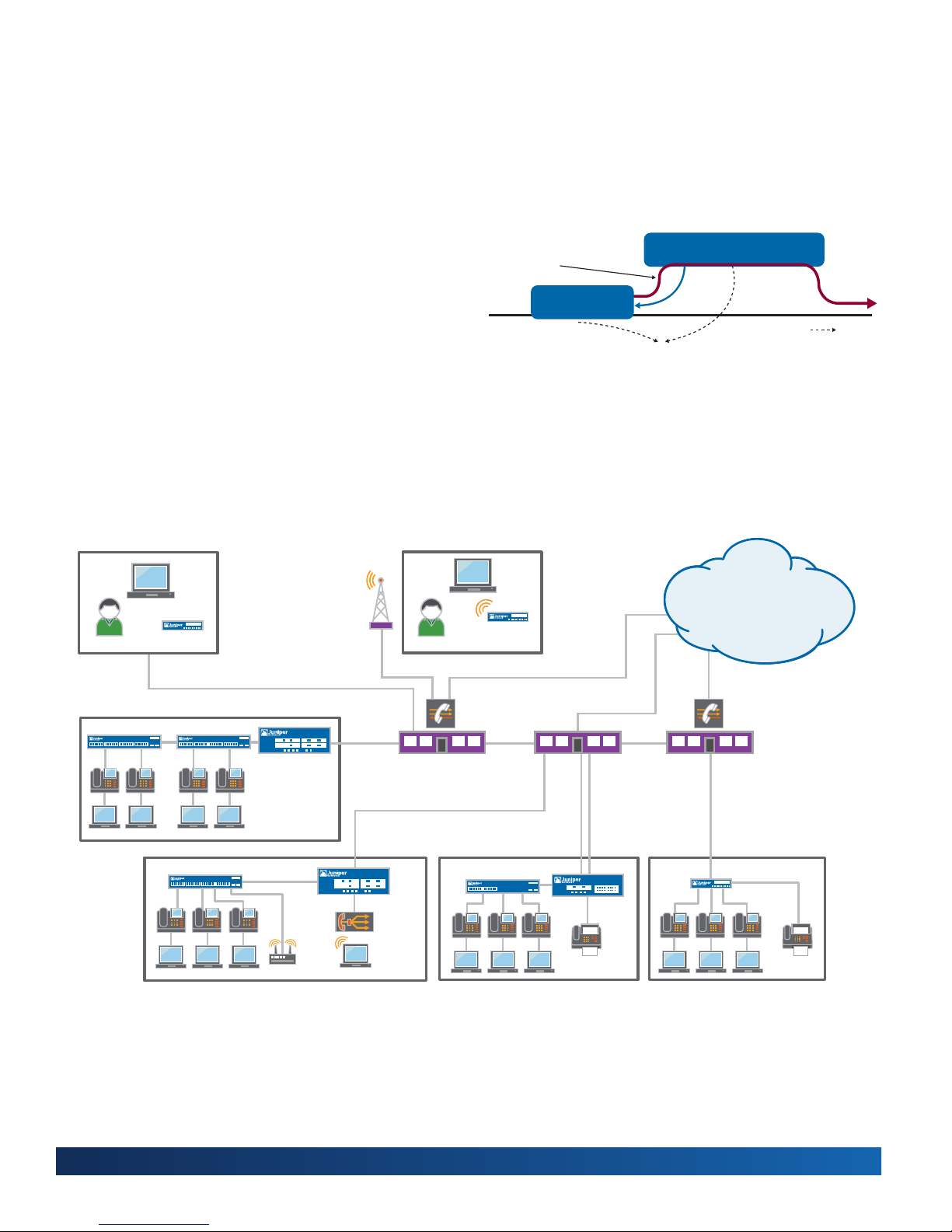
Figure 3 shows the session-based forwarding algorithm. When
a new session is established, the session-based architecture
within JUNOS verifies that the session is allowed by the
forwarding policies. If the session is allowed, JUNOS will look
up the next-hop route in the routing table. It then inserts the
session and the next-hop route into the session and forwarding
table and forwards the packet. Subsequent packets for the
established session require a single table lookup in the session
and forwarding table, and are forwarded to the egress interface.
Session Initial
Packet Processing
Forwarding Table
Ingress
Interface
Session and
Figure 3: Session-based forwarding algorithm
Security Policy Evaluation
and Next-Hop Lookup
Table
Update
Disallowed by
Policy: Dropped
Forwarding for
Permitted Traffic
Egress
Interface
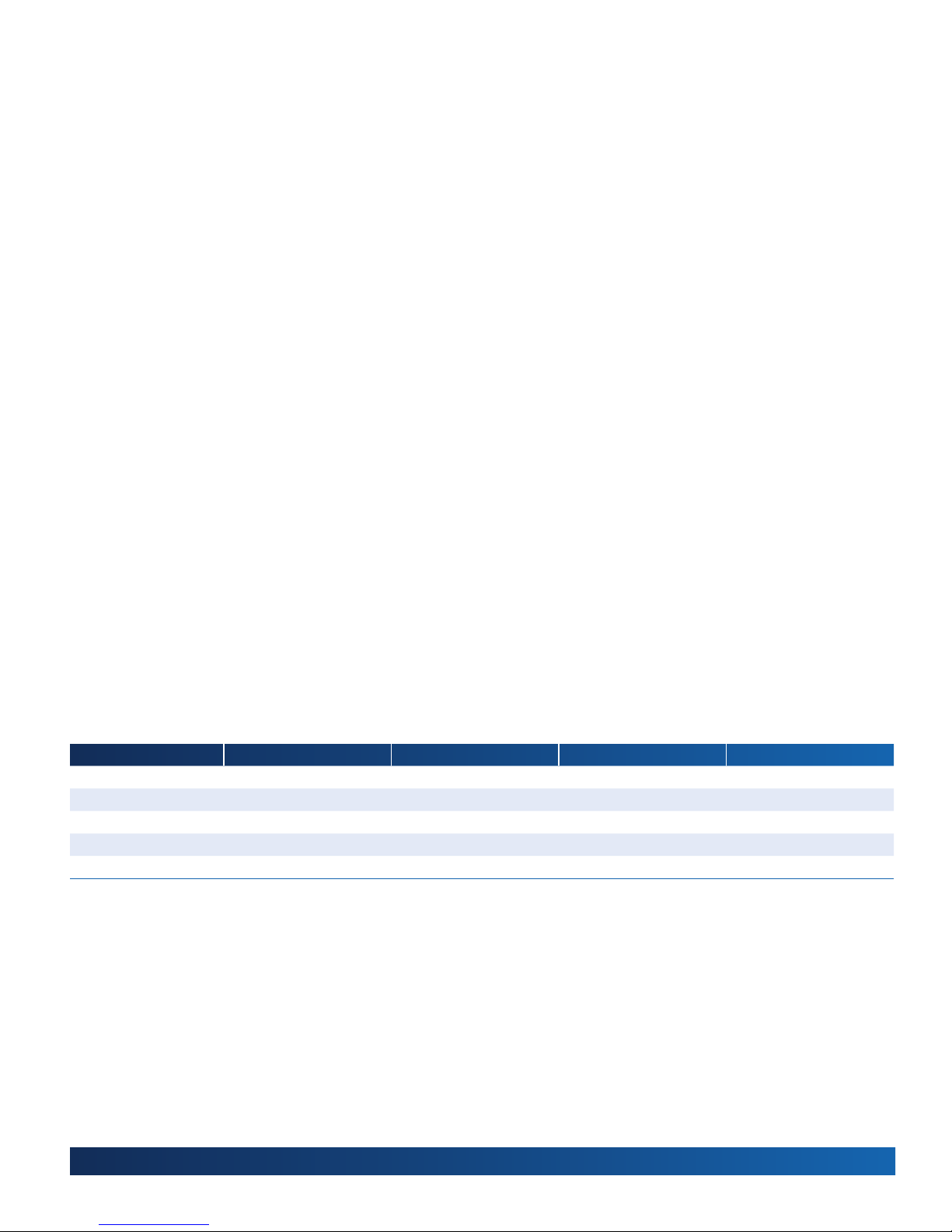
SMALL OFFICE
Mobile
SRX210
DSL
LARGE OFFICE
EX4200 EX3200
EX4200-24T
J4350
Cellular
J6350
FIXED MOBILE SITE
(Mobile – 3G)
POP
PBX
SRX210
Wireless
Service Provider
SIP Softswitch
PSTN
EX3200-24P
POP
Voice (AMI)
Data (B8ZS)
Channelized T-1
Clear channel T-1
J2350
Fax
INTERNET
Service Provider
SIP Softswitch
PSTN
POP
SRX210
Fax
HQ BRANCH
4
BRANCH
Figure 4: The distributed enterprise
Page 5
Product Options
Juniper Networks J2320, J2350, J4350, and J6350 Services
Routers offer a number of options in terms of LAN and WAN
ports, hardware encryption acceleration, power supplies, DRAM,
compact ash, and feature licenses.
LAN Ports
All J2320, J2350, J4350, and J6350 Services Routers ship with
four xed 10/100/1000 Ethernet ports. You can add more modular
LAN interfaces by ordering the appropriate PIMs, Enhanced PIMs
(EPIMs), or Universal PIMs (UPIMs). For more information, see
the J Series WAN and LAN modules Ordering Information section
on page 14.
WAN Ports
All J2320, J2350, J4350, and J6350 Services Routers ship without
fixed WAN ports. The customer can add modular WAN interfaces
by ordering the appropriate PIMs. For more information, see the
J Series WAN and LAN Modules Part Numbers in the Ordering
Information section on page 14.
Hardware Encryption Acceleration
The J2320, J2350, and J4350 are available with optional hardware
encryption acceleration. All J6350 models include hardware
encryption acceleration by default. If you purchase a J2320,
J2350, or J4350 without hardware encryption, you can add it later
by ordering the appropriate encryption card.
Power Supply
All J2350, J4350, and J6350 Services Routers ship with either a
DC power supply or an AC power supply and include a regionspecic power cord. (The J2320 is available with AC power only.)
The J6350 supports a second redundant AC or DC power supply,
which can be added by ordering SSG-PS-DC or SSG-PS-AC. The
region-specic AC power cable for SSG-PS-AC must be ordered
separately.
DRAM
The J2320 and J2350 are upgradeable to a maximum of 1
GB DRAM. The J2320 and J2350 models without hardware
encryption acceleration (J2320-JB-SC and J2350-JB-SC) come
with 512 MB DRAM. All other models come with 1 GB of DRAM.
All J4350 models are upgradeable to a maximum of 2 GB
DRAM. The J4350 model that ships without hardware encryption
acceleration (J-4350-JB-SC) ships with 512 MB of DRAM. All
other J4350 models ship with 1 GB of DRAM.
All J6350 Services Routers ship with 1 GB of DRAM and are
upgradeable to 2 GB of DRAM. Order and install two additional
JXX50-MEM-512M-S DIMMs.
Note that when upgrading DRAM, DIMMs should always be
installed in pairs; for example, to upgrade to 1 GB DRAM, order
two JXX50-MEM-512M-S DIMMs. To upgrade to 2 GB DRAM,
order four JXX50-MEM-512M-S DIMMs.
With JUNOS Release 9.1 and later, all J Series Services Routers
(J2320, J2350, J4350, J6350) must run at least 512 MB of DRAM.
Compact Flash
All J2320, J2350, J4350, and J6350 Services Routers ship with
512 MB of primary compact ash. You can replace that with a
larger compact ash by ordering one either JX-CF-512M-S (for
512 MB) or JX-CF-1G-S (for 1 GB).
Table 2: J4350 and J6350 Supported Memory Configurations
TOTAL MEMORY DIMM 0 DIMM 1 DIMM 2 DIMM 3
512 MB 512 MB
512 MB 256 MB – 256 MB –
1 GB 256 MB 256 MB 256 MB 256 MB
1 GB 512 MB – 512 MB –
2 GB 512 MB 512 MB 512 MB 512 MB
5
Page 6

Specifications
Protocols
• IPv4, IPv6, ISO Connectionless Network Service (CLNS)
Routing and Multicast
• Static routes
• RIPv2
• OSPF
• BGP
• BGP Router Reector
• IS-IS
• Multicast ((Internet Group Management Protocol (IGMPv3),
PIM, Session Description Protocol (SDP), Distance Vector
Multicast Routing Protocol (DVMRP), source-specic))
• MPLS
IP Address Management
• Static
• Dynamic Host Conguration Protocol (DHCP) (client
and server)
• DHCP relay
Encapsulations
• Ethernet (MAC and tagged)
• Point-to-Point Protocol (PPP) (synchronous)
– Multilink Point-to-Point Protocol (MLPPP)
• Frame Relay
– Multilink Frame Relay (MLFR) (FRF.15, FRF.16)
• High-Level Data Link Control (HDLC)
• Serial (RS-232, RS-449, X.21, V.35, EIA-530)
• 802.1q VLAN support
• Point-to-Point Protocol over Ethernet (PPPoE)
Traffic Management
• Marking, policing, and shaping
• Class-based queuing with prioritization
• Weighted random early detection (WRED)
• Queuing based on VLAN, data-link connection identier (DLCI),
interface, bundles, or filters
Security
• Firewall, zones, screens, policies
• Stateful rewall, ACL lters
• Denial of service (DoS) and distributed denial of service (DDoS)
protections (anomaly-based)
• Prevent replay attack; Anti-Replay
• Unied Access Control Dynamic Remote
• Unied Threat Management - Licensed on high memory
products only
2
– Antivirus, antispam, Web filtering, IPS
Voice Transport
• FRF.12
• Link fragmentation and interleaving (LFI)
• Compressed Real-Time Transport Protocol (CRTP)
1
High Availability
• VRRP
• Stateful failover and dual box clustering via JSRP
– Redundant power (optional)
IPv6
• OSPFv3
• IPv6 Multicast Listener Discovery (MLD)
• BGP
• Quality of service (QoS)
SLA and Measurement
• Real-time performance monitoring (RPM)
• Top talkers (sessions, packets, bandwidth usage)
• J-Flow ow monitoring and accounting services
Logging and Monitoring
• Syslog
• Traceroute
Administration
• Juniper Networks Network and Security Manager support
• Juniper Networks STRM Series Security Threat Response
Managers support
• Juniper Networks Advanced Insight Solutions support
• External administrator database (RADIUS, LDAP, SecureID)
• Auto conguration
• Conguration rollback
• Rescue conguration with button
• Commit conrm for changes
• Auto record for diagnostics
• Software upgrades
• J-Web
Operating System
All J Series Services Routers ship with the worldwide version
of JUNOS Software, which has standard encryption, as opposed
to the US and Canada version, which has strong encryption. You
can download the strong encryption version at no charge so
long as you can certify eligibility. The download is available from
Juniper’s Customer Support Center Web site: www.juniper.net/
customers/csc/software/.
Feature Licenses
Licenses are required for advanced functionality on the J Series
Services Routers. To run the Advanced BGP features, order
Advanced BGP (JX-BGP-ADV-LTU). Each license is good for one
chassis.
On the high memory versions of the J Series, you can run Unified
Threat Management consisting of antivirus, antispam, Web
filtering and IPS. These licenses are good for one chassis and
available as single features, bundles, single year and multi year
ordering options.
1
BGP Route Reflector see ordering information.
2
Unified Threat Management is only supported on high memory versions of J Series and requires a license. See ordering information.
6
Page 7

J2320
J2350
J4350
J6350
Product Comparison
SPECIFICATION J2320 J2350 J4350 J6350
Maximum Performance and Capacity
JUNOS Software version tested JUNOS 9.6 JUNOS 9.6 JUNOS 9.6 JUNOS 9.6
Firewall performance (large packets) 600 Mbps 750 Mbps 2 Gbps 3.5 Gbps
Firewall performance (IMIX) 400 Mbps 500 Mbps 600 Mbps 1 Gbps
Firewall + routing PPS (64 Byte) 150 Kpps 175 Kpps 225 Kpps 400 Kpps
AES256+SHA-1/3DES+SHA-1 VPN
performance
IPsec VPN Tunnels 512 MB / GB DRAM
IPS (intrusion prevention system) 115 Mbps 130 Mbps 250 Mbps 500 Mbps
Antivirus 25 Mbps 30 Mbps 65 Mbps 130 Mbps
Connections per second 5,000 5,000 10,000 20,000
Maximum concurrent sessions
DRAM options
Maximum security policies 2048 (1 GB DRAM) 2048 (1 GB DRAM) 5192 (1 GB DRAM) 10384 (2 GB DRAM)
Maximum users supported Unrestricted Unrestricted Unrestricted Unrestricted
Network Connectivity
Fixed I/O 24 x 10/100/1000BASE-T 4 x 10/100/1000BASE-T 4 x 10/100/1000BASE-T 4 x 10/100/1000BASE-T
I/O slots 3 x PIM 5 x PIM 4 x PIM +
Services and Routing Engine slots N/A N/A N/A N/A
ExpressCard slot (3G WAN) N/A N/A N/A N/A
WAN/LAN interface options See ordering
Optional maximum number of PoE ports N/A N/A N/A N/A
USB 2 2 2 2
Routing
BGP instances 32 32 32 64
BGP peers 512 MB / 1 GB DRAM
BGP routes 512 MB / 1 GB DRAM
OSPF instances 512 MB / 1 GB DRAM
OSPF routes 512 MB / 1 GB DRAM
RIP v1/v2 instances 512 MB / 1 GB DRAM
125 Mbps 150 Mbps 400 Mbps 900 Mbps
256 / 512
64 K / 128K
512 MB / 1 GB DRAM
information
64 / 64
64 K / 400 K
32 / 32
5 K / 10 K
32 / 32
512 MB / GB DRAM
256 / 512
64 K / 128K
512 MB / 1 GB DRAM
See ordering
information
512 MB / 1 GB DRAM
64 / 64
512 MB / 1 GB DRAM
64 K / 400 K
512 MB / 1 GB DRAM
32 / 32
512 MB / 1 GB DRAM
5 K / 10 K
512 MB / 1 GB DRAM
32 / 32
512 MB / GB DRAM
256 / 512
64 K / 128 K
512 MB / 1 GB DRAM
2 x EPIM/PIM
See ordering
information
512 MB / 1 GB DRAM
64 / 64
512 MB / 1 GB DRAM
64 K / 400 K
512 MB / 1 GB DRAM
32 / 32
512 MB / 1 GB DRAM
5 K / 10 K
512 MB / 1 GB DRAM
32 / 32
1 GB / 2 GB DRAM
512 MB / 1 GB DRAM
1 GB / 2 GB DRAM
1 GB / 2 GB DRAM
1 GB / 2 GB DRAM
1 GB / 2 GB DRAM
1 GB / 2 GB DRAM
512 / 1024
256 K / 256 K
2 x PIM +
4 x EPIM/PIM
See ordering
information
64 / 64
400 K / 1000 K
64 / 64
10 K / 20 K
64 / 64
7
Page 8

Product Comparison (continued)
SPECIFICATION J2320 J2350 J4350 J6350
Routing (continued)
RIP v2 routes 512 MB / 1 GB DRAM
Static routes 512 MB / 1 GB DRAM
Source-based routing Yes Yes Yes Yes
Policy-based routing Yes Yes Yes Yes
Equal-cost multipath (ECMP) Yes Yes Yes Yes
Reverse path forwarding (RPF) Yes Yes Yes Yes
5 K / 10 K
5 K / 10 K
MPLS
Layer 2 VPN (VPLS) Yes Yes Yes Yes
Layer 3 VPN Yes Yes Yes Yes
LDP Yes Yes Yes Yes
RSVP Yes Yes Yes Yes
Circuit Cross-connect (CCC) Yes Yes Yes Yes
Translational Cross-connect (TCC) Yes Yes Yes Yes
Multicast
IGMP (v1, v2, v3) Yes Yes Yes Yes
PIM SM Yes Yes Yes Yes
PIM source-specific multicast (SSM) Yes Yes Yes Yes
Multicast inside IPsec tunnel Yes Yes Yes Yes
IPsec VPN
Concurrent VPN tunnels 256 / 512
Tunnel interfaces 256 / 512
DES (56-bit), 3DES (168-bit) and
AES (256-bit)
MD-5 and SHA-1 authentication Yes Yes Yes Yes
Manual key, Internet Key Exchange (IKE),
public key infrastructure (PKI) (X.509)
Perfect forward secrecy (DH Groups) 1,2,5 1,2,5 1,2,5 1,2,5
Prevent replay attack Yes Yes Yes Yes
Dynamic remote access VPN Yes Yes Yes No
IPsec NAT traversal Yes Yes Yes Yes
Redundant VPN gateways Yes Yes Yes Yes
(512 MB / 1 GB DRAM)
(512 MB / 1 GB DRAM)
Yes Yes Yes Yes
Yes Yes Yes Yes
User Authentication and Access Control
Third-party user authentication RADIUS, RSA SecureID,
RADIUS accounting Yes Yes Yes Yes
XAUTH VPN, Web-based, 802.X
authentication
PKI certificate requests (PKCS 7 and
PKCS 10)
Certificate Authorities supported VeriSign, Entrust,
LDAP
Yes Yes Yes Yes
Yes Yes Yes Yes
Microsoft, RSA Keon,
iPLanet, (Netscape),
Baltimore,
DoD PKI
Virtualization
Maximum number of security zones 40 40 50 60
Maximum number of virtual routers 25 25 30 60
Maximum number of VLANs 256 256 512 1024
512 MB / 1 GB DRAM
5 K / 10 K
512 MB / 1 GB DRAM
5 K / 10 K
256 / 512
(512 MB / 1 GB DRAM)
256 / 512
(512 MB / 1 GB DRAM)
RADIUS, RSA SecureID,
LDAP
VeriSign, Entrust,
Microsoft, RSA Keon,
iPLanet, (Netscape),
Baltimore,
DoD PKI
512 MB / 1 GB DRAM
5 K / 10 K
512 MB / 1 GB DRAM
5 K / 10 K
256 / 512
(512 MB / 1 GB DRAM)
256 / 512
(512 MB / 1 GB DRAM)
RADIUS, RSA SecureID,
LDAP
VeriSign, Entrust,
Microsoft, RSA Keon,
iPLanet, (Netscape),
Baltimore,
DoD PKI
1 GB / 2 GB DRAM
10 K / 20 K
1 GB / 2 GB DRAM
10 K / 20 K
512 / 1024
(1 GB / 2 GB DRAM)
512 / 1024
(1 GB / 2 GB DRAM)
RADIUS, RSA SecureID,
LDAP
VeriSign, Entrust,
Microsoft, RSA Keon,
iPLanet, (Netscape),
Baltimore,
DoD PKI
8
Page 9

Product Comparison (continued)
SPECIFICATION J2320 J2350 J4350 J6350
Encapsulations
PPP/MLPPP Yes Yes Yes Yes
MLPPP maximum physical interfaces 6 10 12 12
Frame Relay Yes Yes Yes Yes
MLFR (FRF .15, FRF .16) Yes Yes Yes Yes
MLFR maximum physical interfaces 6 10 12 12
HDLC Yes Yes Yes Yes
Address Translation
Source NAT with Port Address Translation
(PAT)
Static NAT Yes Yes Yes Yes
Destination NAT with PAT Yes Yes Yes Yes
IP Address Assignment
Static Yes Yes Yes Yes
DHCP, PPPoE client Yes Yes Yes Yes
Internal DHCP server Yes Yes Yes Yes
DHCP relay Yes Yes Yes Yes
L2 Switching
VLAN 802.1Q Yes Yes Yes Yes
Link Aggregation 802.3ad/LACP Yes Yes Yes Yes
Jumbo Frame (9216 Byte) Yes Yes Yes Yes
Spanning Tree Protocol (STP) 802.1D, RSTP
802.1w, MSTP 802.1s
Authentication 802.1x Port based and
multiple supplicant
Traffic Management Quality of Service (QoS)
Guaranteed bandwidth Yes Yes Yes Yes
Maximum bandwidth Yes Yes Yes Yes
Ingress traffic policing Yes Yes Yes Yes
Priority-bandwidth utilization Yes Yes Yes Yes
DiffServ marking Yes Yes Yes Yes
High Availability
Active/active—L3 mode Yes Yes Yes Yes
Active/passive—L3 mode Yes Yes Yes Yes
Configuration synchronization Yes Yes Yes Yes
VRRP Yes Yes Yes Yes
Session synchronization for firewall and VPN Yes Yes Yes Yes
Session failover for routing change Yes Yes Yes Yes
Device failure detection Yes Yes Yes Yes
Link failure detection Yes Yes Yes Yes
Firewall
Network attack detection Yes Yes Yes Yes
DoS and DDos protection Yes Yes Yes Yes
TCP reassembly for fragmented packet
protection
Brute force attack mitigation Yes Yes Yes Yes
SYN cookie protection Yes Yes Yes Yes
Zone-based IP spoofing Yes Yes Yes Yes
Malformed packet protection Yes Yes Yes Yes
Yes Yes Yes Yes
Yes Yes Yes Yes
Yes Yes Yes Yes
Yes Yes Yes Yes
9
Page 10

Product Comparison (continued)
SPECIFICATION J2320 J2350 J4350 J6350
Unified Threat Management
Intrusion Prevention System (IPS) Yes Yes Yes Yes
Protocol anomaly detection Yes Yes Yes Yes
Stateful protocol signatures Yes Yes Yes Yes
Intrusion prevention system (IPS) attack
pattern obfuscation
Customer signatures creation Yes Yes Yes Yes
Frequency of updates Daily and emergency Daily and emergency Daily and emergency Daily and emergency
Antivirus
Express AV (packet-based AV) No Yes Yes Yes
File-based antivirus Yes Yes Yes Yes
Signature database Yes Yes Yes Yes
Protocols scanned POP3, HTTP, SMTP,
Antispyware Yes Yes Yes Yes
Antiadware Yes Yes Yes Yes
Antikeylogger Yes Yes Yes Yes
Antispam Yes Yes Yes Yes
Integrated Web filtering Yes Yes Yes Yes
Redirect Web filtering Yes Yes Yes Yes
Content filtering Yes Yes Yes Yes
Based on MIME type, file extension, and
protocol commands
System Management
Web UI Yes Yes Yes Yes
Command-line interface Yes Yes Yes Yes
Network and Security Manager Yes Yes Yes Yes
STRM Series Yes Yes Yes Yes
Flash and Memory
Memory minimum and maximum (DRAM) 512 MB, 1 GB 512 MB, 1 GB 512 MB, 2 GB 1 GB, 2 GB
Memory slots 4 DIMM 4 DIMM 4 DIMM 4 DIMM
Standard and Maximum Flash memory 512MB / 1GB 512MB / 1GB 512MB / 1GB 512MB / 1GB
USB port for external storage Yes Yes Yes Yes
Dimensions and Power
Dimensions (W x H x D) 17.5 x 1.75 x 15.1 in
Weight 15 lb (6.8 kg)
No interface modules,
Rack mountable Yes, 1 RU Yes, 1.5 RU Yes, 2 RU Yes, 2 RU
Power supply (AC) 100–240 VAC, 275 W 100–240 VAC, 300 W 100–240 VAC, 350 W 100–240 VAC, 420 W
Average power consumption 80 W 80 W 143 W 166 W
Input frequency 47-63 Hz 47-63 Hz 47-63 Hz 47-63 Hz
Maximum current consumption 3.2 A @ 100 VAC 3.5 A @ 100 VAC 5.7 A @ 100 VAC 5.7 A @ 100 VAC
Maximum inrush current 30 A 32 A 32 A 42 A
Yes Yes Yes Yes
IMAP, FTP
Yes Yes Yes Yes
(445 x 44 x 383 mm)
16.6 lb (7.6 kg)
3 interface modules
POP3, HTTP, SMTP,
IMAP, FTP
17.5 x 1.75 x 15.1 in
(445 x 44 x 383 mm)
16 lb (7.3 kg)
No interface modules,
19 lb (8.6 kg)
5 interface modules
POP3, HTTP, SMTP,
IMAP, FTP
17.5 x 3.5 x 21.5 in
(445 x 89 x 546 mm)
23 lb (10.4 kg)
No interface modules,
25.3 lb (11.5 kg)
6 interface modules
POP3, HTTP, SMTP,
IMAP, FTP
17.5 x 3.5 x 21.5 in
(445 x 89 x 546 mm)
25 lb (11.3 kg)
No interface modules,
1 power supply
30.7 lb (13.9 kg)
6 interface modules,
2 power supplies
10
Page 11

Product Comparison (continued)
SPECIFICATION J2320 J2350 J4350 J6350
Dimensions and Power (continued)
Average heat dissipation 273 BTU/hour 273 BTU/hour 488 BTU/hour 566 BTU/hour
Maximum heat dissipation 1091 BTU/hour 1195 BTU/hour 1070 BTU/hour 1145 BTU/hour
Power supply (DC) NA -48 to -60 VDC, 300 W -48 to -60 VDC, 420 W -48 to -60 VDC, 420 W
Redundant power supply (hot swappable) No No No Yes
Acoustic noise level
(Note: Per ISO 7779 Standard)
Environment
Operational temperature 32° to 122° F
Nonoperational temperature 4° to 158° F
Humidity 10–90% noncondensing 10–90% noncondensing 10–90% noncondensing 10–90% noncondensing
Mean time between failures
(Telcordia model)
Certifications and Network Homologation
USA
Safety certifications UL 60950-1 UL 60950-1 UL 60950-1 UL 60950-1
EMC certifications FCC Class B FCC Class B
Network homologation TIA-968 TIA-968 TIA-968 TIA-966
Canada
Safety certifications CSA 60950-1 CSA 60950-1 CSA 60950-1 CSA 60950-1
EMC certifications ICES class B ICES class B
Network homologation CS-03 CS-03 CS-03 CS-03
Australia
Safety certifications AS / NZS 60950-1 AS / NZS 60950-1 AS / NZS 60950-1 AS / NZS 60950-1
EMC certifications AS / NZS CISPR22
Network homologation AS / ACIF S 002, S 016, S
New Zealand
Safety certifications AS / NZS 60950-1 AS / NZS 60950-1 AS / NZS 60950-1 AS / NZS 60950-1
EMC certifications AS / NZS CISPR22
Network homologation PTC 217, PTC 273 PTC 217, PTC 273 PTC 217, PTC 273 PTC 217, PTC 273
Japan
Safety certifications CB Scheme CB Scheme CB Scheme CB Scheme
EMC certifications VCCI Class B VCCI Class B
Network homologation Certicate for Technical
European Union
Safety certifications EN 60950-1 EN 60950-1 EN 60950-1 EN 60950-1
EMC certifications EN 55022 Class B, EN
Network homologation CTR 12 / 13, CTR 21,
40.0 dB 59.2 dB 59.3 dB 61.2 dB
(0° to 50° C)
(-20° to 70° C)
7.2 years 6.8 years 7.6 years 12 years with redundant
Class B
043.1, S043.2
Class B
Conditions
300386
DoC
32° to 122° F
(0° to 50° C)
4° to 158° F
(-20° to 70° C)
10
10
AS / NZS CISPR22 Class
AS / ACIF S 002, S 016, S
AS / NZS CISPR22 Class
Certicate for Technical
EN 55022 Class B10, EN
CTR 12 / 13, CTR 21,
10
B
043.1, S043.2
10
B
Conditions
300386
DoC
10
32° to 122° F
(0° to 50° C)
4° to 158° F
(-20° to 70° C)
FCC Class A FCC Class A
ICES class A ICES class A
AS / NZS CISPR22
Class A
AS / ACIF S 002, S 016, S
043.1, S043.2
AS / NZS CISPR22
Class A
VCCI Class A VCCI Class A
Certicate for Technical
Conditions
EN 55022 Class A, EN
300386
CTR 12 / 13, CTR 21,
DoC
AS / NZS CISPR22
AS / ACIF S 002, S 016, S
AS / NZS CISPR22
Certicate for Technical
EN 55022 Class A, EN
CTR 12 / 13, CTR 21,
32° to 122° F
(0° to 50° C)
4° to 158° F
(-20° to 70° C)
power
Class A
043.1, S043.2
Class A
Conditions
300386
DoC
Performance-Enabling Services and Support
Juniper Networks is the leader in performance-enabling services and support, which are designed to accelerate, extend, and optimize
your high-performance network. Our services allow you to bring revenue-generating capabilities online faster so you can realize bigger
productivity gains, faster rollouts of new business models and ventures, and greater market reach, while generating higher levels of
customer satisfaction. At the same time, Juniper Networks ensures operational excellence by optimizing your network to maintain
required levels of performance, reliability, and availability. For more details, please visit www.juniper.net/products-services.
11
Page 12

Ordering Information
The following tables outline part numbers for J6350, J4350, J2350, and J2320 base systems and options; associated WAN and LAN
modules; and additional accessories.
J6350 Base Systems and Options
MODEL NUMBER DESCRIPTION
J6350 Base System
J-6350-JB J6350, Hw-encryption, high memory (1 GB DRAM,
512 MB Flash), 0 PIM cards, 1 AC PSU, w/JUNOS
J-6350-JB-DC J6350, 512 MB CF, 1 GB RAM, Hw-encryption,
0 PIM cards, 1 DC PSU
J-6350-JB-DC-N-TAA J6350, 512 MB CF, 1 GB RAM, Hw-encryption,
0 PIM cards, 1 DC PSU, w/JUNOS - NEBS and TAA
compliant
J-6350-JB-N-TAA J6350, 512 MB CF, 1 GB RAM, Hw-encryption,
0 PIM cards, 1 AC PSU, w/JUNOS - NEBS and TAA
compliant
J6350 Options
Redundant Power Supply
SSG-PS-DC DC power supply
SSG-PS-AC AC power supply
Region-Specific AC Power Cables for SSG-PS-AC
CBL-JX-PWR-AU Australia
CBL-JX-PWR-CH China
CBL-JX-PWR-EU Europe
CBL-JX-PWR-IT Italy
CBL-JX-PWR-JP Japan
CBL-JX-PWR-UK United Kingdom
CBL-JX-PWR-US USA
Additional DRAM
JXX50-MEM-512M-S 2 GB (2 x JXX50-MEM-512M-S, added to default)
Primary Compact Flash (Replaces default)
JX-CF-512M-S 512 MB
JX-CF-1G-S 1 GB
Additional Software Feature Licenses
JX-BGP-ADV-LTU Advanced BGP
JX-JFlow-LTU J-Flow Accounting
J6350-K-AV One year subscription for Juniper-Kaspersky AV
updates
J6350-K-AV-3 Three year subscription for Juniper-Kaspersky AV
updates
J6350-S2-AS One year subscription for Juniper-Sophos
Antispam
J6350-S2-AS-3 Three year subscription for Juniper-Sophos
Antispam
J6350-W-WF One year subscription for Juniper-Websense
Integrated Web Filtering
J6350-W-WF-3 Three year subscription for Juniper-Websense
Integrated Web Filtering
J6350-IDP One year subscription for IDP updates
J6350-IDP-3 Three year subscription for IDP updates
J6350-SMB2-CS One year security subscription for Enterprise -
includes Kaspersky AV, WF, Sophos AS,
and IDP
J6350-SMB2-CS-3 Three year security subscription for Enterprise -
includes Kaspersky AV, WF, Sophos AS,
and IDP
Interface Modules (Various choices; see page 14)
J4350 Base Systems and Options
MODEL NUMBER DESCRIPTION
J4350 Base System
J-4350-JB J4350, Hw-encryption, high-memory (1 GB DRAM,
512 MB Flash), 0 PIM cards, AC PSU, w/JUNOS
J-4350-JB-DC J4350, 512 MB CF, 1 GB RAM, Hw-encryption,
0 PIM cards, DC PSU
J-4350-JB-SC J4350, software encryption, low memory, (512 MB
DRAM, 512 MB Flash) 0 PIM cards, AC PSU, w/
JUNOS, Software Crypto
J-4350-JB-SC-DC J4350, software encryption, low memory, (512 MB
DRAM, 512 MB Flash) 0 PIM cards, DC PSU, w/
JUNOS, Software Crypto
J-4350-JB-DC-N-TAA J4350, 256 MB CF, 1GB RAM, Hw-encryption,
0 PIM cards, DC PSU, NEBS, w/JUNOS - NEBS and
TAA compliant
J-4350-JB-N-TAA J4350, 256 MB CF, 1GB RAM, Hw-encryption,
0 PIM cards, AC PSU, w/JUNOS - NEBS and TAA
compliant
J4350 Options
Additional DRAM for J4350 without encryption acceleration (DRAM
upgrades must be installed in matching pairs)
JXX50-MEM-256M-S 512 MB (JXX50-MEM-256M-S, added
to default)
JXX50-MEM-512M-S • 1 GB (2 x JXX50-MEM-512M-S, replaces default)
• 2 GB (4 x JXX50-MEM-512M-S, replaces default)
Additional DRAM for J4350 with encryption acceleration (DRAM upgrades
must be installed in matching pairs)
JXX50-MEM-512M-S 2 GB (4 x JXX50-MEM-512M-S, replaces default)
Primary Compact Flash (Replaces default)
JX-CF-512M-S 512 MB
JX-CF-1G-S 1 GB
Additional Software Feature Licenses
JX-BGP-ADV-LTU Advanced BGP
JX-JFlow-LTU J-Flow Accounting
J4350-K-AV One year subscription for Juniper-Kaspersky AV
updates
J4350-K-AV-3 Three year subscription for Juniper-Kaspersky AV
updates
J4350-S2-AS One year subscription for Juniper Antispam
J4350-S2-AS-3 Three year subscription for Juniper Antispam
J4350-W-WF One year subscription for Juniper-Websense
Integrated Web Filtering
J4350-W-WF-3 Three year subscription for Juniper-Websense
Integrated Web Filtering
J4350-IDP One year subscription for IDP updates
J4350-IDP-3 Three year subscription for IDP updates
J4350-SMB2-CS One year security subscription for Enterprise -
includes Kaspersky AV, WF, Sophos AS
and IDP
J4350-SMB2-CS-3 Three year security subscription for Enterprise -
includes Kaspersky AV, WF, Sophos AS
and IDP
Interface Modules (Various choices; see page 14)
JXH-HC2-S Cryptographic Acceleration Module, to be used
with J2350-JB-SC only
12
Page 13

J2350 Base Systems and Options
MODEL NUMBER DESCRIPTION
J2350 Base System
J2350-JB-SC J2350, JUNOS, base memory (512 MB), 5 PIM slots,
J2350-JB-SC-DC J2350, JUNOS, base memory (512 MB DRAM,
J2350-JH J2350, JUNOS, high memory (1 GB DRAM,
J2350-JH-DC J2350, JUNOS, high memory (1 GB), 5 PIM slots,
J2350-JB-SC-DCN-TAA
J2350-JB-SC-TAA J2350, JUNOS, base memory (512 MB), 5 PIM
J2350-JH-DC-N-TAA J2350, JUNOS, high memory (1 GB), 5 PIM slots,
J2350-JH-TAA J2350, JUNOS, high memory (1 GB), 5 PIM slots,
J2350 Options
Additional DRAM for J2350 without encryption acceleration (DRAM
upgrades must be installed in matching pairs)
JXX50-MEM-512M-S 1 GB (2 x JXX50-MEM-512M-S, replaces default)
Primary Compact Flash (Replaces default)
JX-CF-512M-S 512 MB
JX-CF-1G-S 1 GB
Additional Software Feature Licenses
JX-BGP-ADV-LTU Advanced BGP
JX-JFlow-LTU J-Flow Accounting
J2350-K-AV One year subscription for Juniper-Kaspersky AV
J2350-K-AV-3 Three year subscription for Juniper-Kaspersky AV
J2350-S2-AS One year subscription for Juniper-Sophos
J2350-S2-AS-3 Three year subscription for Juniper-Sophos
J2350-W-WF One year subscription for Juniper-Websense
J2350-W-WF-3 Three year subscription for Juniper-Websense
J2350-IDP One year subscription for IDP updates
J2350-IDP-3 Three year subscription for IDP updates
J2350-SMB2-CS One year security subscription for Enterprise -
J2350-SMB2-CS-3 Three year security subscription for Enterprise -
Interface Modules (Various choices; see page 14)
JXH-HC2-S Cryptographic Acceleration Module, to be used
SW security, AC power supply, 19” rack mount
512 MB Flash), 5 PIM slots, SW encryption, DC
power supply, 19” rack mount
512 MB Flash), 3 PIM slots, HW encryption, AC
power supply, 19” rack mount
HW Crypto, DC power supply, fan lter, 19” rack
mount
J2350, JUNOS, base memory (512 MB), 5 PIM slots,
SW Crypto, DC power supply, fan lter, NEBS, TAA,
19” rack mount
slots, SW Crypto, AC power supply, TAA, 19” rack
mount
HW Crypto, DC power supply, fan lter, NEBS, TAA,
19” rack mount
HW Crypto, AC power supply, TAA, 19” rack mount
updates
updates
Antispam
Antispam
Integrated Web Filtering
Integrated Web Filtering
includes Kaspersky AV, WF, Sophos AS
and IDP
includes Kaspersky AV, WF, Sophos AS
and IDP
with J2350-JB-SC only
J2320 Base Systems and Options
MODEL NUMBER DESCRIPTION
J2320 Base System
J2320-JB-SC J2320, JUNOS, base memory (512 MB DRAM,
512 MB Flash), 3 PIM slots, SW security, AC power
supply, 19” rack mount
J2320-JB-SC-TAA J2320, JUNOS, base memory (512 MB DRAM,
512 MB Flash), 3 PIM slots, SW security, AC power
supply, TAA 19” rack mount
J2320-JH J2320, JUNOS, high memory (1 GB DRAM,
512 MB Flash), 3 PIM slots, Hw-encryption,
AC power supply, 19” rack mount
J2320 Options
Additional DRAM for J2320 without encryption acceleration (DRAM
upgrades must be installed in matching pairs)
J-MEM-512M-S 1 GB (2 x J-MEM-512M-S replaces default)
Primary Compact Flash (Replaces default)
JX-CF-512M-S 512 MB
JX-CF-1G-S 1 GB
Additional Software Feature Licenses
JX-BGP-ADV-LTU Advanced BGP
JX-JFlow-LTU J-Flow Accounting
J2320-K-AV One year subscription for Juniper-Kaspersky
AV updates
J2320-K-AV-3 Three year subscription for Juniper-Kaspersky
AV updates
J2320-S2-AS One year subscription for Juniper -Sophos
Antispam
J2320-S2-AS-3 Three year subscription for Juniper -Sophos
Antispam
J2320-W-WF One year subscription for Juniper-Websense
Integrated Web Filtering
J2320-W-WF-3 Three year subscription for Juniper-Websense
Integrated Web Filtering
J2320-IDP One year subscription for IDP updates
J2320-IDP-3 Three year subscription for IDP updates
J2320-SMB2-CS One year security subscription for Enterprise -
includes Kaspersky AV, WF, Sophos AS
and IDP
J2320-SMB2-CS-3 Three year security subscription for Enterprise -
includes Kaspersky AV, WF, Sophos AS
and IDP
Interface Modules (Various choices; see page 14)
JXH-HC2-S Cryptographic Acceleration Module, to be used
with J2320-JB-SC only
13
Page 14

WAN and LAN Module Part Numbers
PART NUMBER DESCRIPTION SUPPORTED ON J2320, J2350 SUPPORTED ON J4350, J6350
Physical Interface Module (PIM)
JX-1DS3-S 1-Port DS3 PIM No Yes
JX-1E3-S 1-Port E3 PIM No Yes
JX-2T1-RJ48-S 2-Port T1 PIM Yes Yes
JX-2E1-RJ48-S 2-Port E1 PIM Yes Yes
JX-2CT1E1-RJ45-S 2-Port Channelized T1/E1 PIM Yes Yes
JX-2Serial-1SL-S 2-Port Synchronous Serial PIM Yes Yes
JX-2FE-TX-S 2-Port FE PIM No Yes
JX-4BRI-S-S 4-Port ISDN BRI – S Interface Yes Yes
JX-4BRI-U-S 4-Port ISDN BRI – U Interface Yes Yes
JX-1ADSL-A-S 1-Port ADSL Annex A PIM Yes Yes
JX-1ADSL-B-S 1-Port ADSL Annex B PIM Yes Yes
JX-2SHDSL-S 2-Port 2-wire or 1-Port 4-wire
G.SHDSL Interface
JX-1DS3-S 1-Port DS3 PIM No Yes
Enhanced Physical Interface Module (EPIM)
JXE-1GE-TX-S 1-Port Gigabit Copper EPIM No Yes
JXE-1GE-SFP-S 1-Port Gigabit SFP EPIM No Yes
JXE-4FE-TX-S 4-Port FE EPIM No Yes
Universal Physical Interface Module (UPIM)
JXU-6GE-SFP-S 6-Port SFP Gigabit Ethernet
Universal PIM, SFPs sold separately
JXU-8GE-TX-S 8-Port Gigabit Ethernet 10/100/1000
Copper Universal PIM
JXU-16GE-TX-S 16-Port Gigabit Ethernet 10/100/1000
Copper Universal PIM
JXU-1SFP-S 1-Port SFP 100 Mbps or Gigabit
Ethernet Universal PIM (SFP sold
separately)
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Yes Yes
Integrated Services Modules PIM
INTEGRATED SERVICES
MODULE PIM
JX-ISM-200-WXC ISM200 Integrated Services Module JUNOS 9.1 JUNOS 9.1
DESCRIPTION
J2320/J2350 J4350/J6350
MINIMUM JUNOS SOFTWARE
Avaya Telephony Gateway Modules and Telephony Interface Modules
AVAYA
PART NUMBER
700406978 TGM550 - Media Gateway Module JUNOS 9.1 JUNOS 9.1
700396138 TIM510 T1/E1 Media Module JUNOS 9.1 JUNOS 9.1
700396146 TIM514 Analog 4+4 Media Module JUNOS 9.1 JUNOS 9.1
700396153 TIM 521 BRI Media Module JUNOS 9.1 JUNOS 9.1
700436645 TGM550-20 Media Gateway Module JUNOS 9.1 JUNOS 9.1
700436652 TGM550-10 Media Gateway Module JUNOS 9.1 JUNOS 9.1
700426786 TIM508 Analog 8FXS Media Module JUNOS 9.1 JUNOS 9.1
700426794 TIM516 Analog 16FXS Media Module JUNOS 9.1 JUNOS 9.1
700426786 TIM518 Analog 8FXS+8FXO Media Module JUNOS 9.1 JUNOS 9.1
*Avaya Telephony Gateway Modules and Telephony Interface Modules are available through Avaya resellers and partners.
DESCRIPTION
J2320/J2350 J4350/J6350
14
MINIMUM JUNOS SOFTWARE
Page 15

Small Form Pluggable (SFP) Modules
The one-port 100 Mbps or Gigabit Ethernet Universal PIM and the six-port SFP Gigabit Ethernet Universal PIM require an SPF module
to provide the physical interface. The SFP must be ordered separately from the UPIM.
PART NUMBER DESCRIPTION
JX-SFP-1GE-LX SFP 1000BASE-LX Gigabit Optical Transceiver SFP Module
JX-SFP-1GE-SX SFP 1000BASE-SX Gigabit Optical Transceiver SFP Module
JX-SFP-1GE-T SFP 1000BASE-T Gigabit Copper Transceiver SFP Module
JX-SFP-1FE-FX SFP 100BASE-FX Optical Transceiver Module (JXU-1SFP-S only)
Serial Interface Cables
The two-port Serial PIM requires separate purchase of serial cables.
PART NUMBER CABLE TYPE LENGTH CONNECTOR TYPE
JX-CBL-EIA530-DCE EIA530 cable (DCE) 10 ft (3 m) Female
JX-CBL-EIA530-DTE EIA530 cable (DTE) 10 ft (3 m) Male
JX-CBL-RS232-DCE RS232 cable (DCE) 10 ft (3 m) Female
JX-CBL-RS232-DTE RS232 cable (DTE) 10 ft (3 m) Male
JX-CBL-RS449-DCE RS449 cable (DTE) 10 ft (3 m) Female
JX-CBL-RS449-DTE RS449 cable (DTE) 10 ft (3 m) Male
JX-CBL-V35-DCE V.35 cable (DTE) 10 ft (3 m) Female
JX-CBL-V35-DTE V.35 cable (DTE) 10 ft (3 m) Male
JX-CBL-X21-DCE X.21 cable (DCE) 10 ft (3 m) Female
JX-CBL-X21-DTE X.21 cable (DTE) 10 ft (3 m) Male
15
Page 16

About Juniper Networks
Juniper Networks, Inc. is the leader in high-performance networking. Juniper offers a high-performance network infrastructure
that creates a responsive and trusted environment for accelerating the deployment of services and applications over a single network.
This fuels high-performance businesses. Additional information can be found at www.juniper.net.
Corporate and Sales Headquarters
Juniper Networks, Inc.
1194 North Mathilda Avenue
Sunny vale, CA 94089 USA
Phone: 888.JUNIPER (888.586.4737)
or 408.745.20 00
Fax: 408.745.2100
APAC Headquarters
Juniper Networks (Hong Kong)
26/F, Cityplaza One
1111 King’s Road
Taikoo Shing, Hong Kong
Phone: 852.2332.3636
Fax: 852.2574.7803
To purchase Juniper Networks solutions, please
contact your Juniper Networks representative
at 1-866-298-6428 or authorized reseller.
1000 206-003-E N Sept 20 09 Printed on recycled paper.
16
EMEA Headquarters
Juniper Networks Irel and
Airside Business Park
Swords, County Dublin, Ireland
Phone: 35.31.8903.600
Fax: 35.31.890 3.601
Copy right 2009 Juniper Netw orks, Inc. All rights
reserved. Juniper Networks, the Juniper Networks
logo, JUNOS, NetScreen, and ScreenOS are
registered tr ademar ks of Juniper Networks, Inc.
in the United State s and other countries. JUNOSe
is a trademark of Juniper Networks, Inc. All other
trademarks, serv ice marks, registered marks, or
registered service marks are the property of their
respective owners . Juniper Networ ks assumes
no responsibility for any inaccuracies in this
document. Juniper Netw orks re serves the right to
change, modif y, transfer, or other wise revise this
publication without notice.
 Loading...
Loading...