Page 1

Page 2
Page 3
Page 4

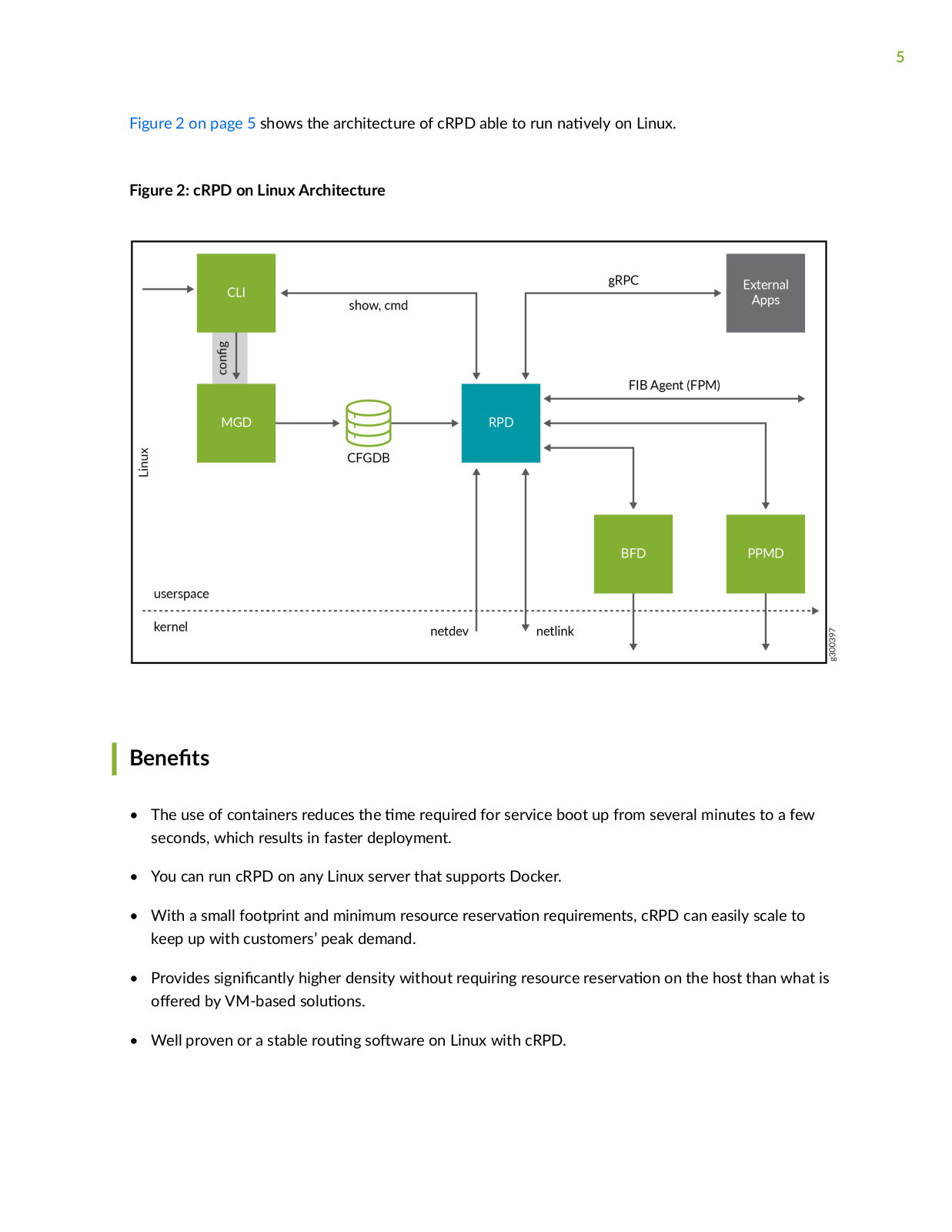
Page 5

Page 6

Page 7

Page 8
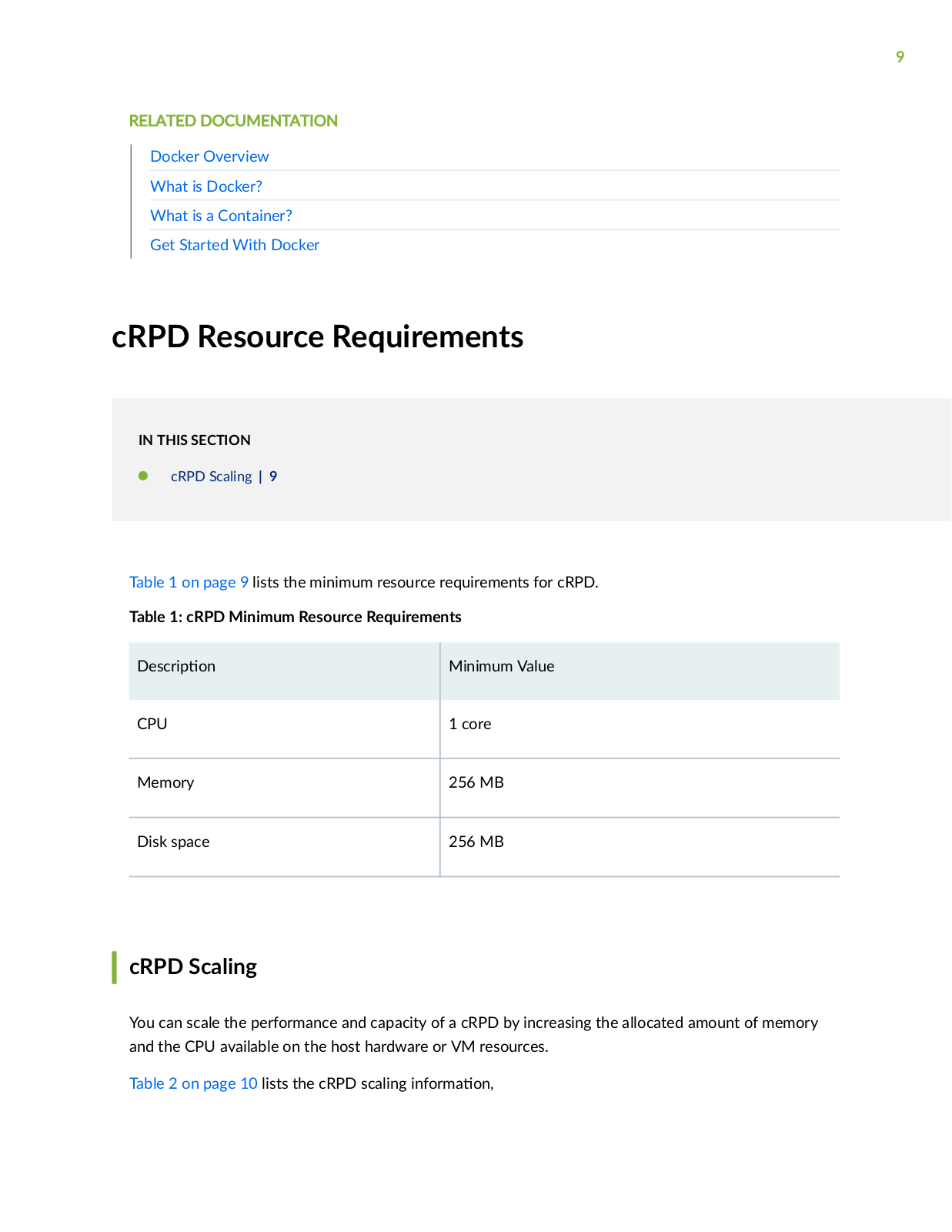
Page 9
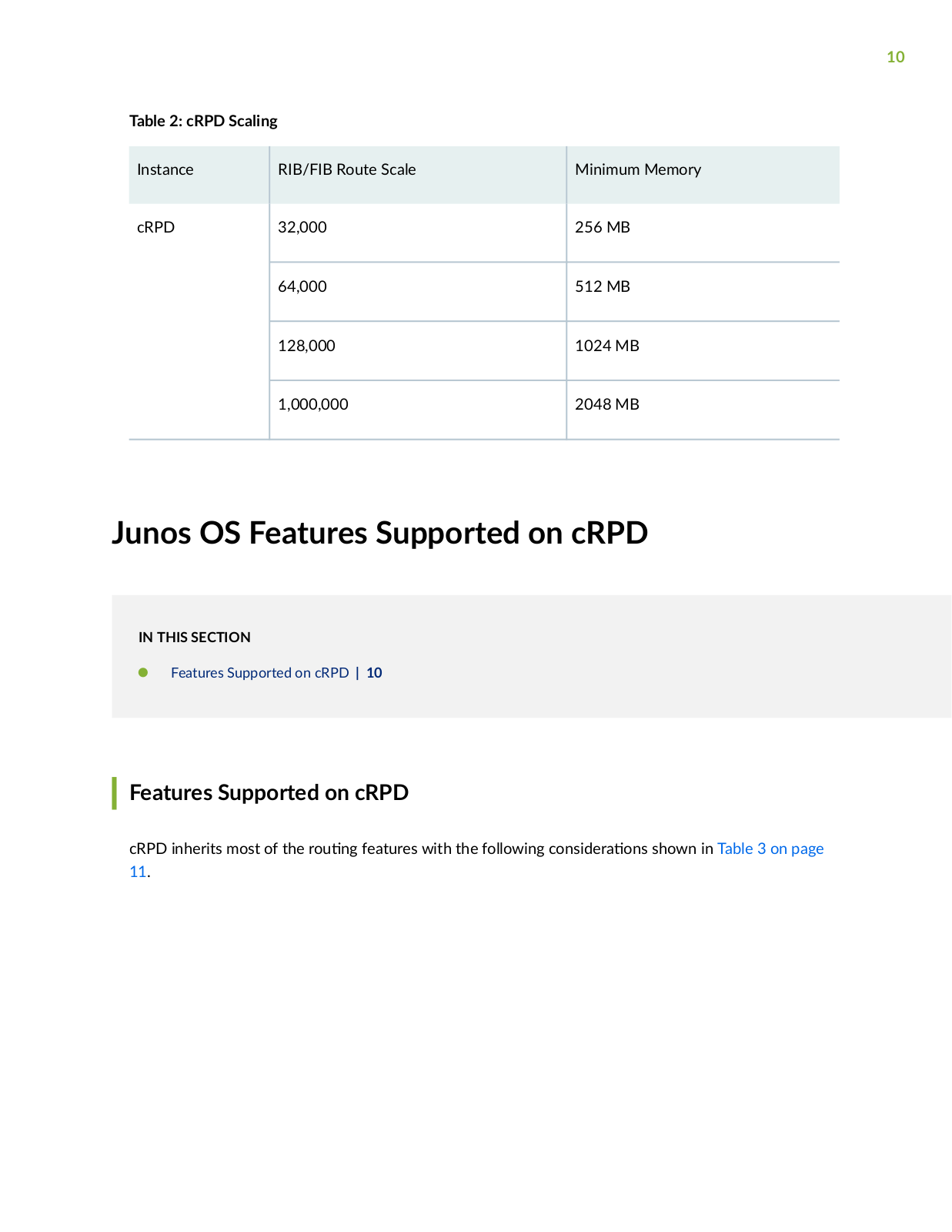
Page 10

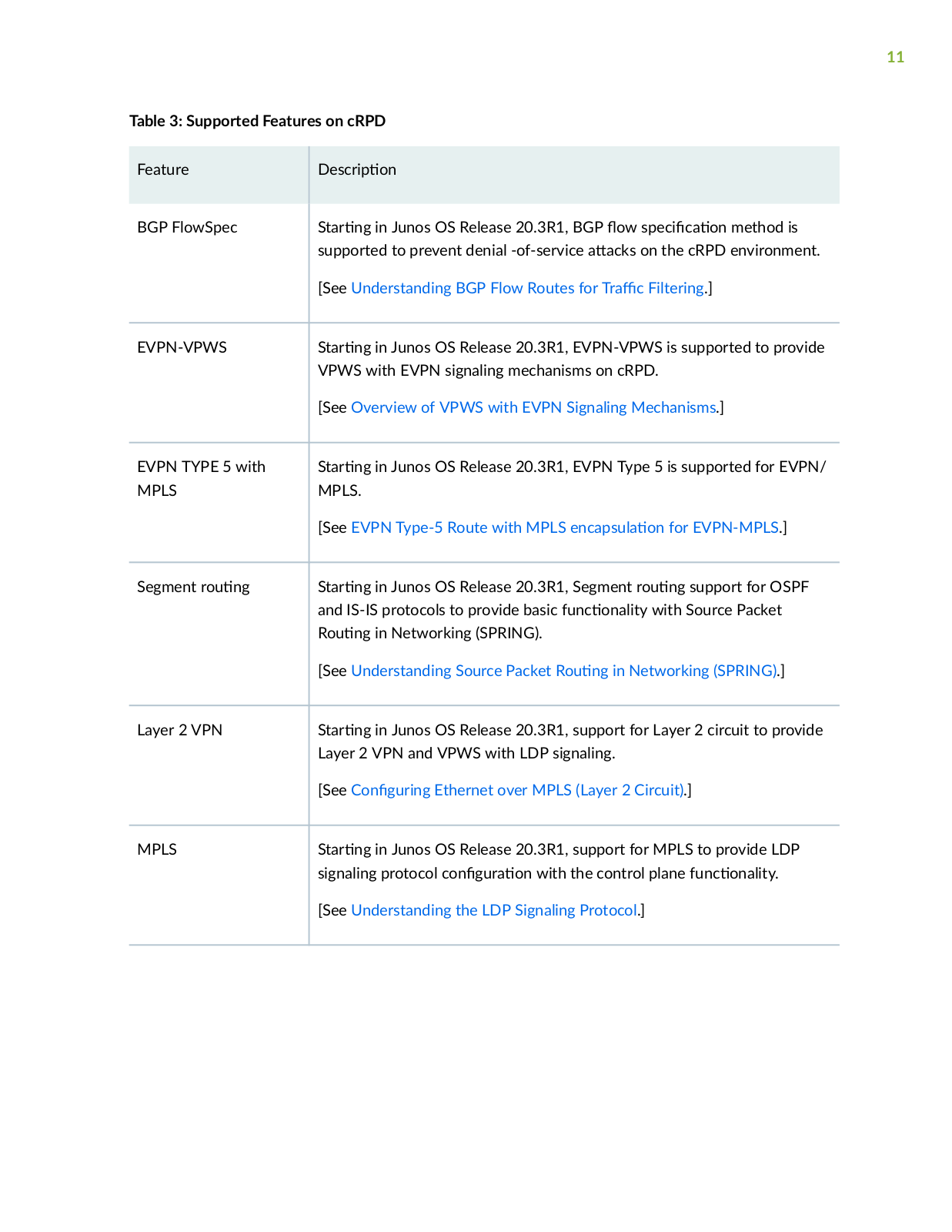
Page 11

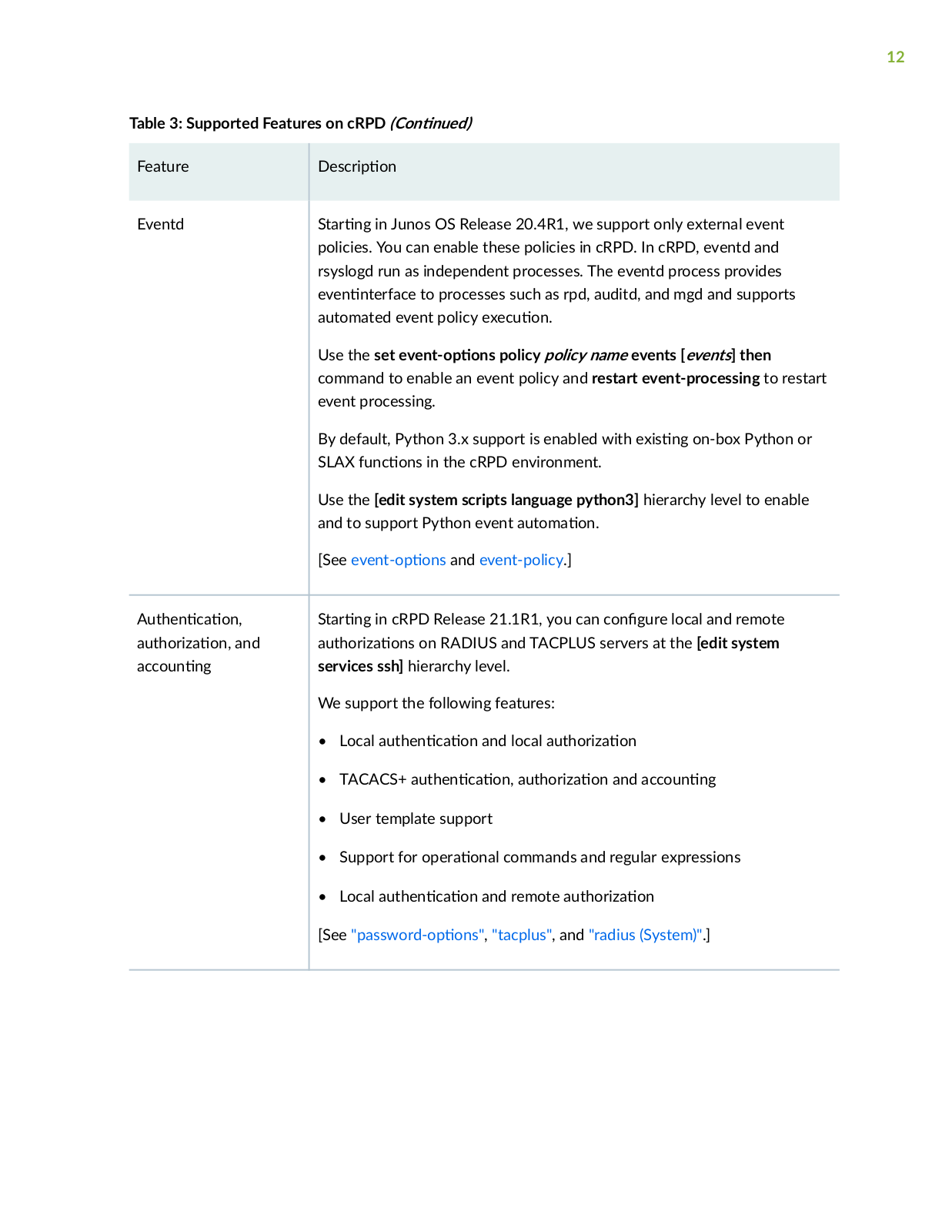
Page 12
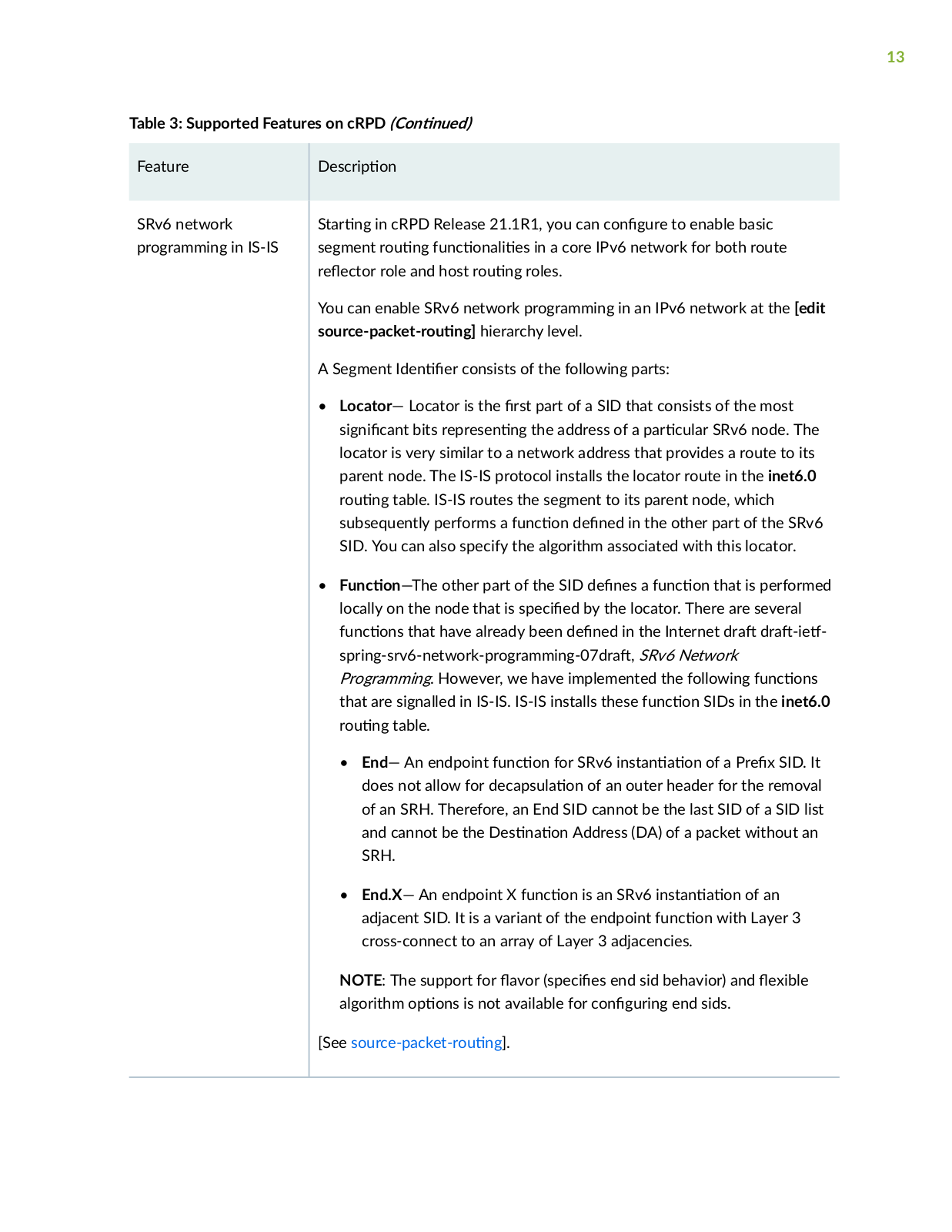
Page 13

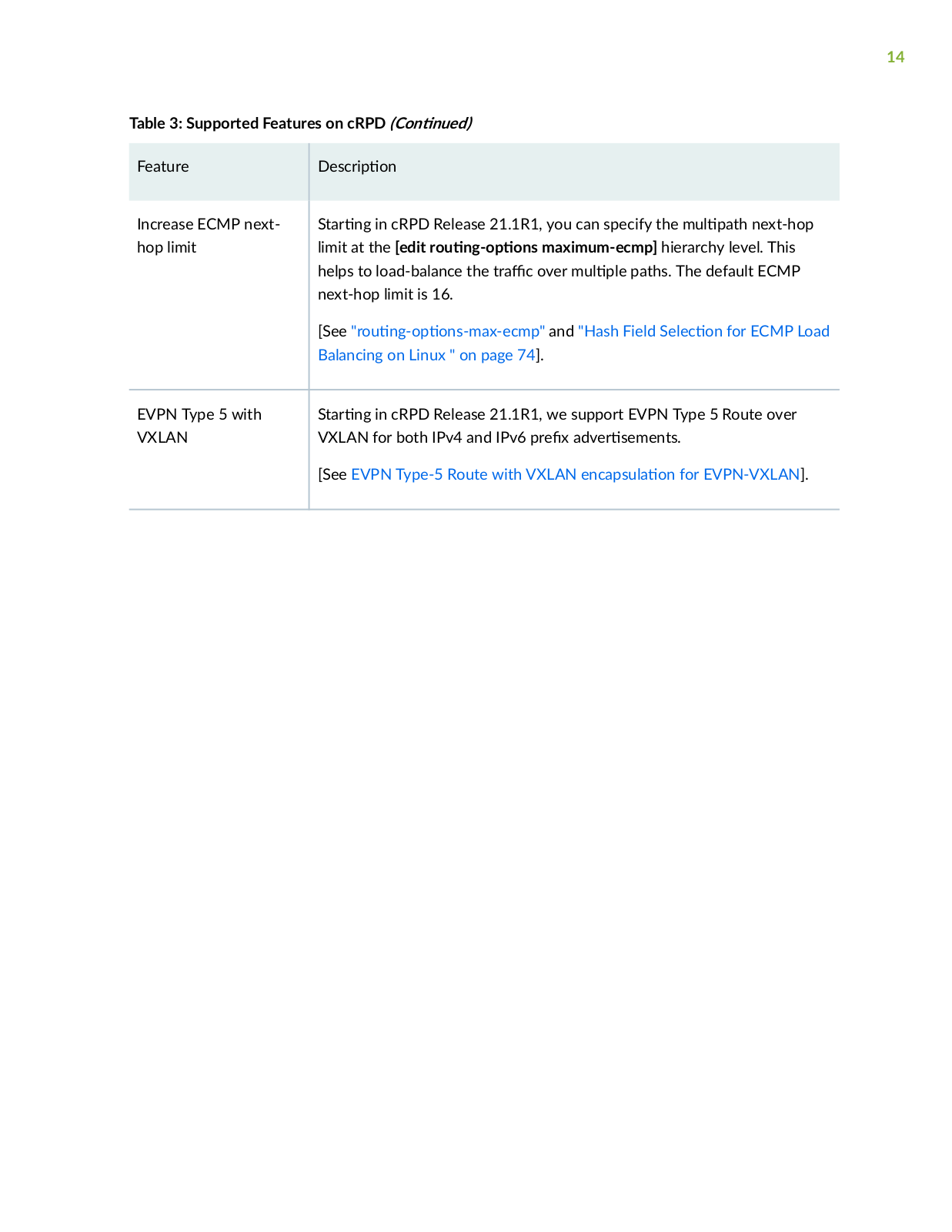
Page 14
Page 15

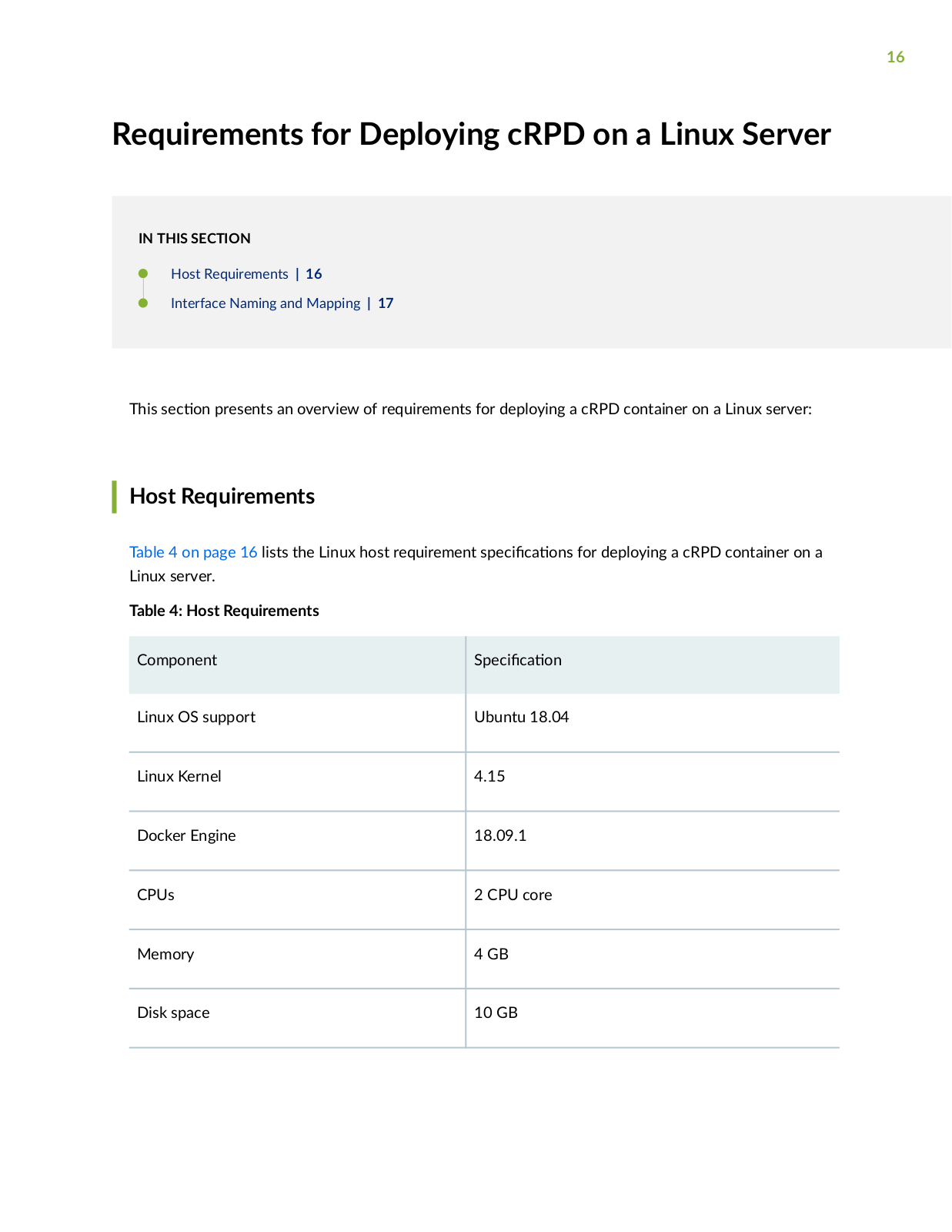
Page 16
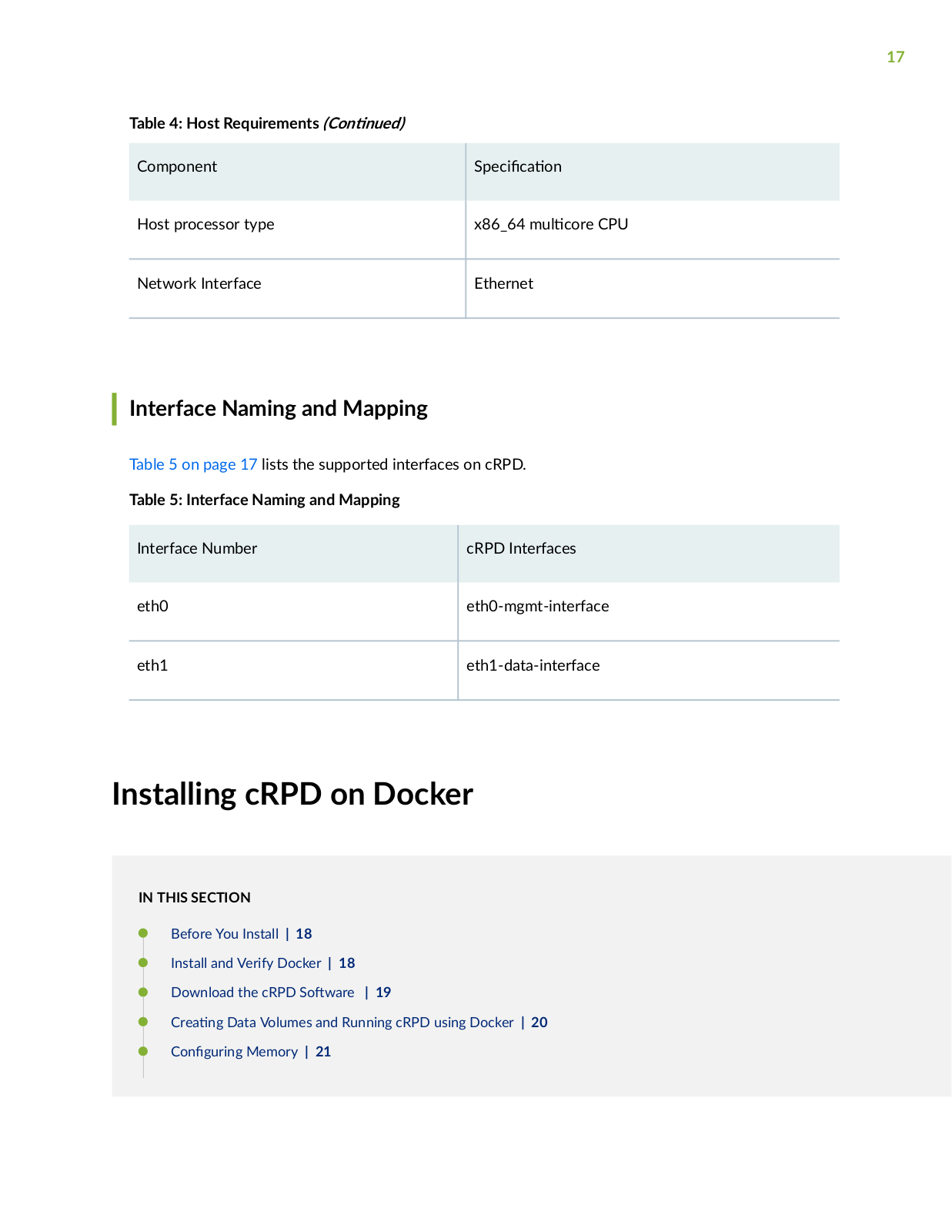
Page 17
Page 18
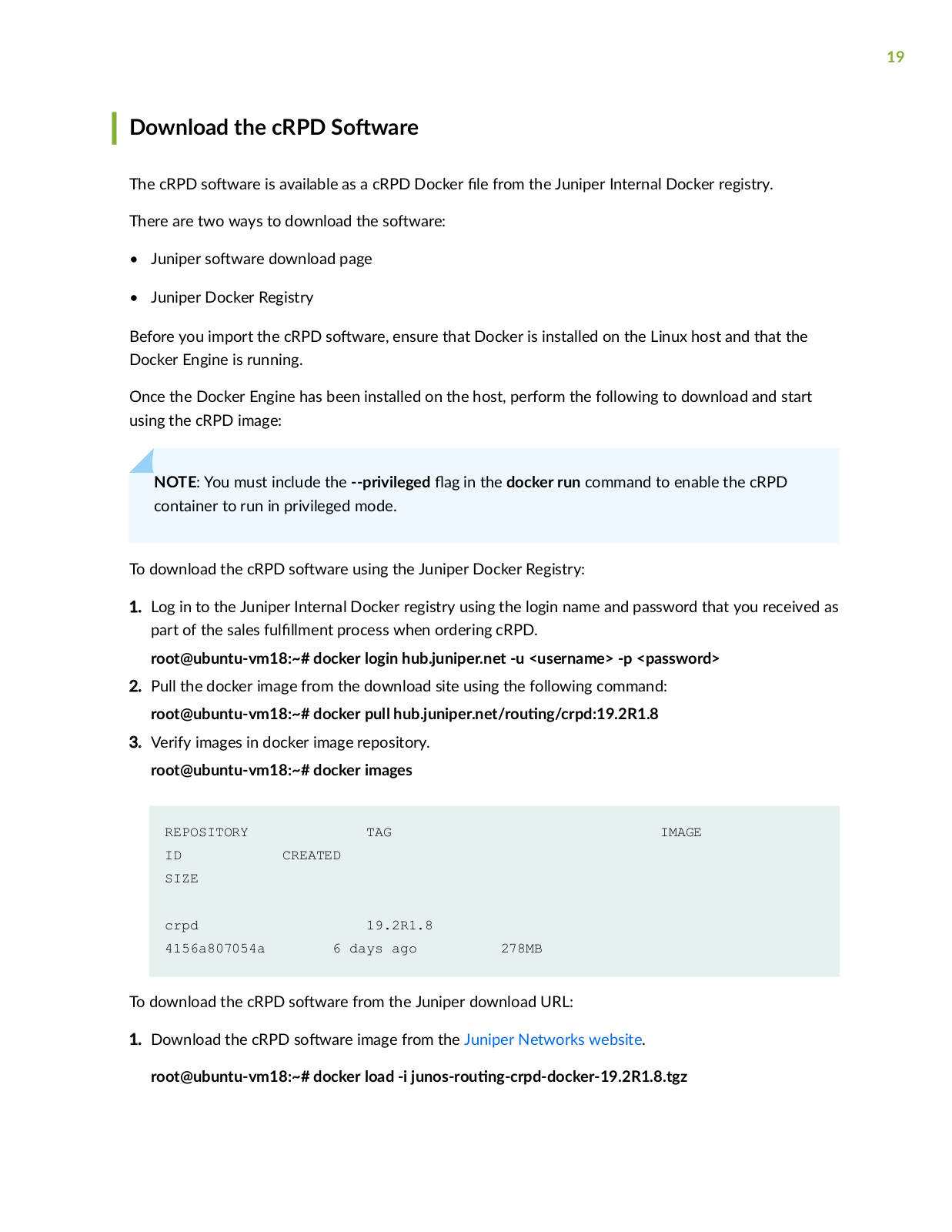
Page 19
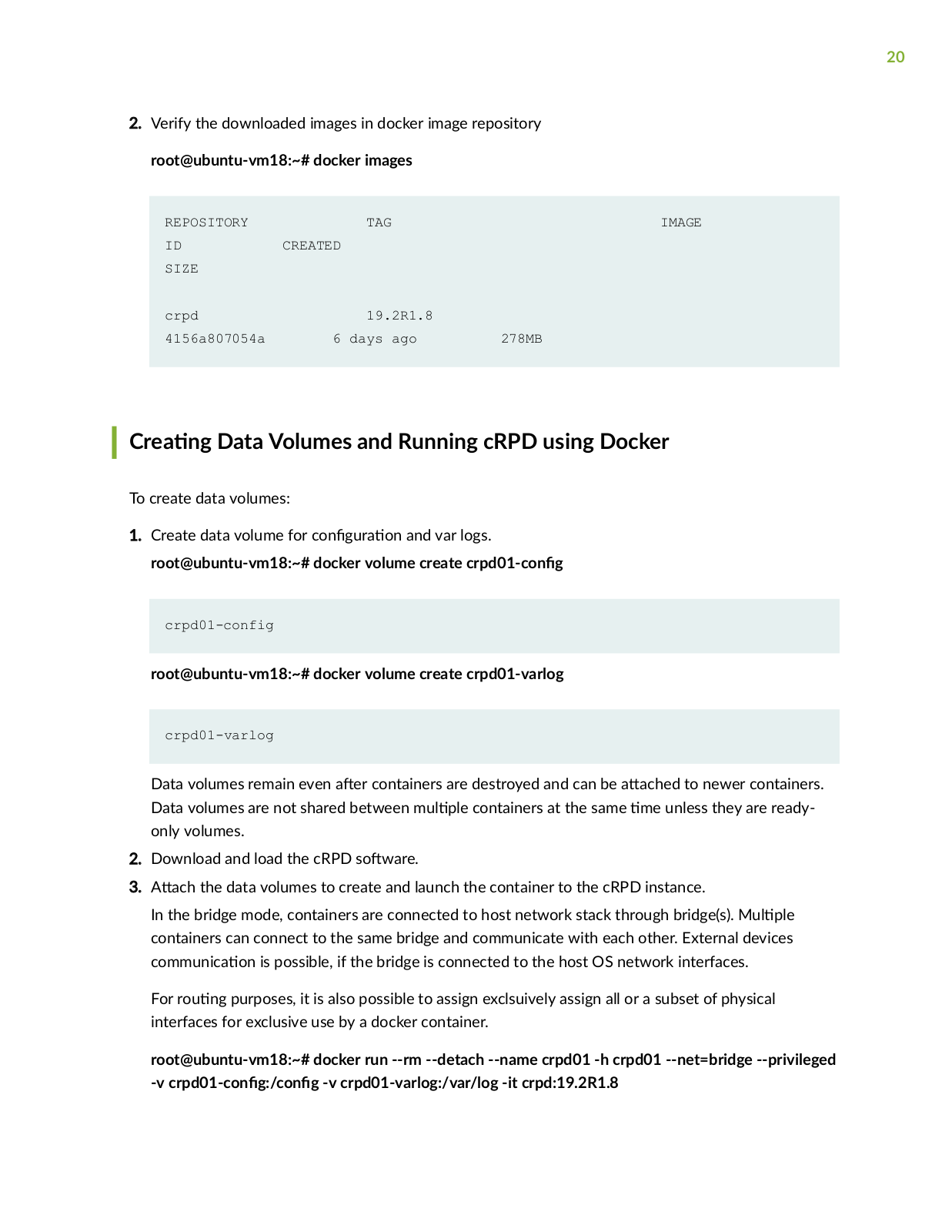
Page 20
Page 21
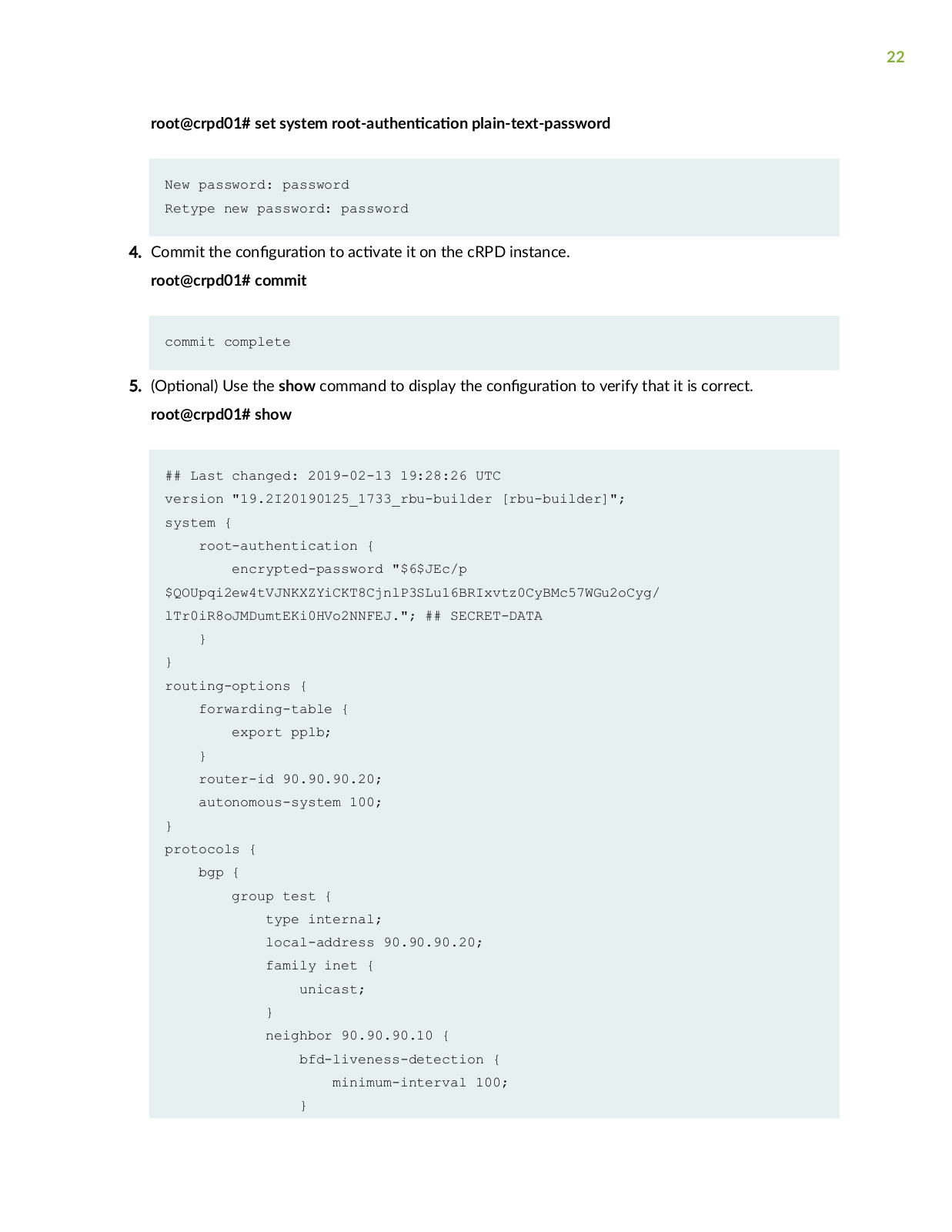
Page 22

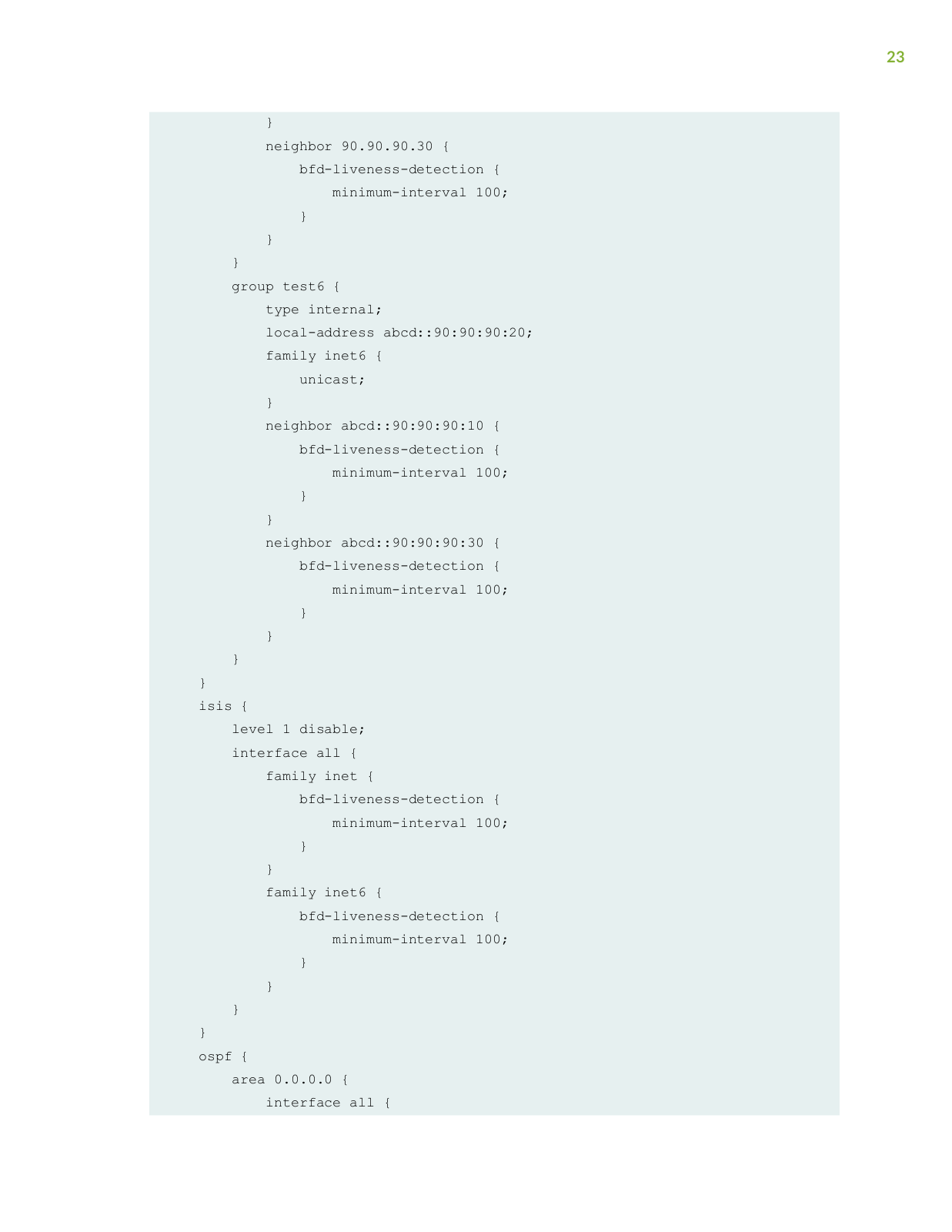
Page 23
Page 24
Page 25
Page 26
Page 27
Page 28

Page 29
Page 30
Page 31

Page 32

Page 33

Page 34

Page 35

Page 36

Page 37

Page 38

Page 39

Page 40

Page 41

Page 42

Page 43

Page 44

Page 45

Page 46

Page 47

Page 48

Page 49

Page 50

Page 51

Page 52

Page 53

Page 54

Page 55

Page 56

Page 57

Page 58

Page 59

Page 60

Page 61

Page 62

Page 63

Page 64

Page 65

Page 66

Page 67

Page 68

Page 69

Page 70

Page 71

Page 72

Page 73

Page 74

Page 75

Page 76

Page 77

Page 78

Page 79

Page 80

Page 81

Page 82

Page 83

Page 84

Page 85

Page 86

Page 87

Page 88

Page 89

Page 90

Page 91

Page 92

Page 93

Page 94

Page 95

Page 96

Page 97

Page 98

Page 99

Page 100

 Loading...
Loading...