Page 1

User Guide
IronKey Personal
Secure Flash Drive
PAGE 1IRONKEY USER GUIDE
Page 2
Thank you for your interest in IronKey.
IronKey is committed to creating and developing
the best security technologies and making them
simple-to-use, affordable, and available to everyone. Years of research and millions of dollars of
development have gone into bringing this technology to you in the IronKey.
For a quick product overview, you can also view
our online demos at https://www.ironkey.com/demo.
We are very open to user feedback and would
greatly appreciate hearing about your comments,
suggestions, and experiences with the IronKey.
Standard Feedback:
feedback@ironkey.com
Anonymous Feedback:
https://www.ironkey.com/feedback
User Forum:
https://forum.ironkey.com
PAGE 1IRONKEY USER GUIDE
Page 3

CONTENTS
What is it?
Meet the IronKey
Core Features
Device Diagrams
Technical & Security Notes
IronKey Device Security
IronKey Services Security
How Does it Work?
Product Walkthrough
Initializing and Activating Your IronKey on Windows
Using the IronKey Unlocker on Windows
Initializing Your IronKey on a Mac
Using the IronKey Unlocker on a Mac
Initializing Your IronKey on Linux
Using the IronKey Unlocker on Linux
Using the IronKey Control Panel
Using the IronKey Virtual Keyboard
Using the Onboard Firefox & Secure Sessions Service
Using the IronKey Password Manager
Using the Secure Backup Software
ImportingaDigitalCerticateintotheIronKey
Using my.ironkey.com
Using Your IronKey in Read-Only Mode
Product Specications
3
3
3
5
6
6
7
9
9
9
11
12
13
13
14
16
18
19
21
23
24
26
28
29
What’s Next?
Where can I go for more Information?
Who is the IronKey Team?
Contact Information
30
30
30
31
PAGE 2IRONKEY USER GUIDE
Page 4

What is it?
Meet the IronKey
The IronKey Personal Secure Flash Drive, designed to be the world’s
most secure USB ash drive, protects your data, passwords, and Internet
privacy with some of today’s most advanced security technologies. Even
if your IronKey is lost or stolen, your data remains protected and can
even be restored to a new IronKey from an encrypted backup. While the
underlying security technologies are complex, the IronKey is simple to use
and you only need to remember a password to unlock it.
Core Features
Hardware-Encrypted Flash Drive
Your IronKey can safely store 1, 2, 4 or 8 gigabytes of documents, applica-
tions, les and other data. The IronKey Cryptochip inside the IronKey
protects your data to the same level as highly classied government infor-
mation, and it cannot be disabled or accidently turned off.
Self-Destruct Sequence
If the IronKey Cryptochip detects any physical tampering by a thief or a
hacker, it will self-destruct. Similarly, after 10 consecutive invalid password
attempts
Anti-Malware Autorun Protection
Your IronKey helps protect you from many of the latest malware threats
targeting USB ash drives. It will detect and prevent autorun execution of
unapproved programs, and it can be unlocked in a Read-Only Mode.
your IronKey will self-destruct using ash-trash technology.
PAGE 3IRONKEY USER GUIDE
Page 5

Portable Cross-Platform Data Access
The IronKey Unlocker allows you to access your encrypted les on Windows 2000, XP, Vista, Mac OS X and numerous distributions of Linux.
Simple Device Management
Your IronKey includes the IronKey Control Panel, a central launchpad for
launching your applications, editing your preferences, and safely locking
your IronKey.
Secure Data Recovery
Securely back up the data on your IronKey using IronKey’s Secure Backup
software. It allows you to recover your data to a new IronKey in case
your IronKey is ever lost, and even synchronize data between IronKeys.
Stealth Browsing Technology
Surf the Web safely and privately through almost any network, even across
unsecured wireless hotspots, with IronKey’s Secure Sessions Service. It
can be easily toggled through the onboard Mozilla Firefox web browser.
Self-Learning Password Management
Securely store and back up all your online passwords as you go with the
IronKey Password Manager. It allows you to automatically log into your
online accounts to avoid keylogging spyware and phishing attacks.
Online my.ironkey.com Account
You can manage all of your IronKeys online at https://my.ironkey.com, a
secure website that requires two-factor authentication to access it. Here
you can recover forgotten passwords, disable device services, and more.
Online Security Vault
If your IronKey is ever lost or stolen, you can easily restore your online
passwords from an encrypted online backup.
Waterproof & Tamper-Resistent
The IronKey was designed to survive the extremes. The
IronKey’s rugged metal casing is injected with an epoxy
compound that makes it not only tamper-resistent, but
waterproof to military specications (MIL-STD-810F).
PAGE 4IRONKEY USER GUIDE
Page 6

Up to 8 gigabytes
of secure storage
INCLUDES
“Flash-Trash” technology
for complete data erasure
SMART
Stores data up to 10 times
longer than ordinary flash drives
RELIABLE
Waterproof & tamperproof metal casing
RUGGED
IronKey Cryptochip with
military-grade cryptography
SAFE
Transfers data up to 8 times
faster than ordinary flash drives
FAST
The World’s Most Secure Flash Drive
TM
Rugged metal case
lled solid with epoxy
Multi-color LED
Drilled hole for
keyring/lanyard
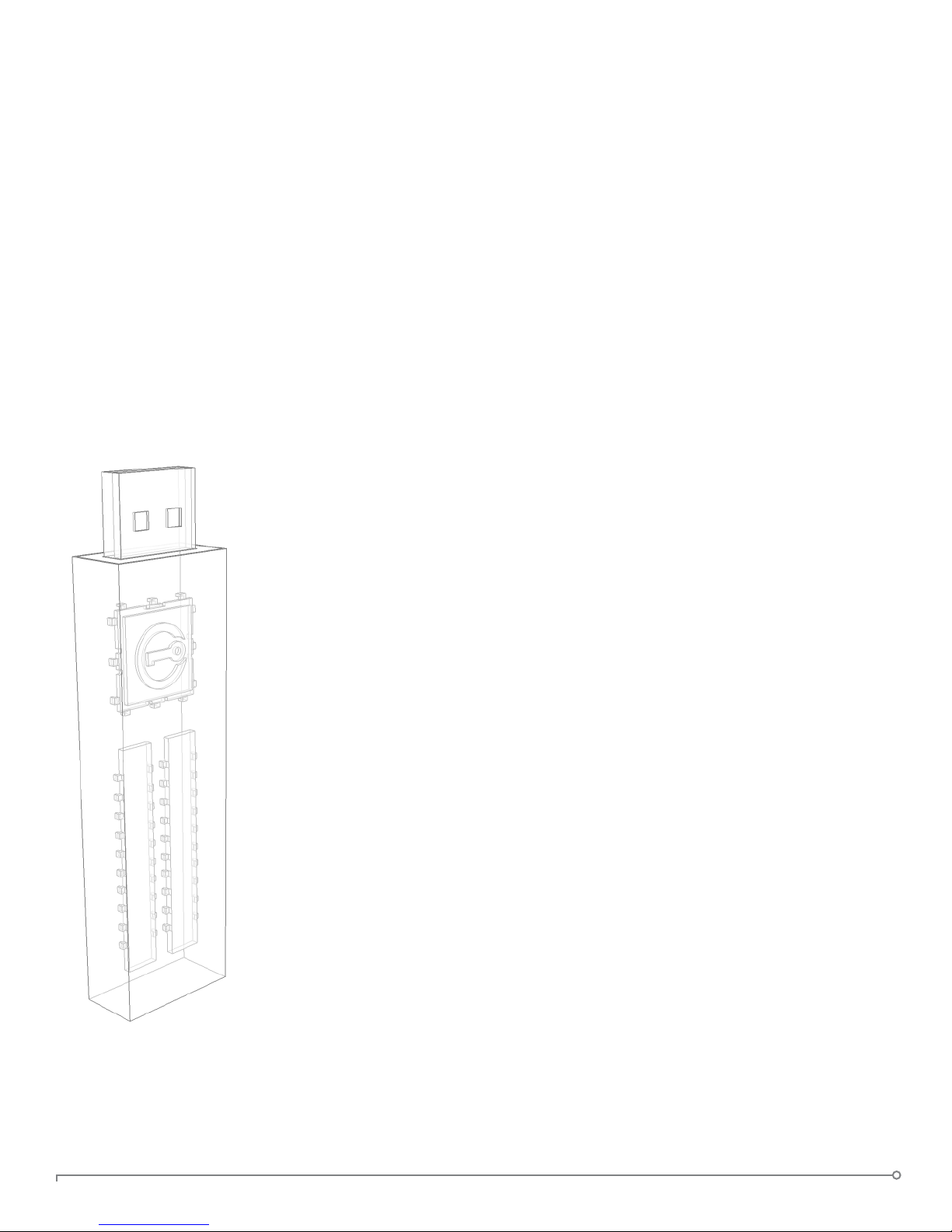
Device Diagrams
The IronKey has been designed from the ground up with security in mind.
A combination of advanced security technologies are used to ensure
maximum protection of your data. Additionally, the IronKey has been
designed to be physically secure, to prevent hardware-level attacks and
tampering, as well as to make the device rugged and long-lasting. You can
rest assured that your data is secured when you carry an IronKey.
Metal Cap
Area to engrave
your name/code
Stamped unique
serial number
This IronKey Cryptochip is hardened against physical attacks such as pow-
er attacks and bus snifng. It is physically impossible to tamper with its
protected data or reset the password counter. If the Cryptochip detects
a physical attack from a hacker, it will destroy the encryption keys, making
the stored encrypted les inaccessible.
USB 2.0
Connector
PAGE 5IRONKEY USER GUIDE
Page 7

Technical & Security Notes
We are endeavoring to be very open about the security architecture and
technology that we use in designing and building the IronKey devices and
online services. There is no hocus-pocus or handwaving here. We use
established cryptographic algorithms, we develop threat models, and we
perform security analyses (internal and third party) of our systems all the
way through design, development and deployment. Your IronKey is FIPS
IRONKEY DEVICE SECURITY
Data Encryption Keys
» AES keys generated by onboard Random Number Generator
» AES keys generated by user at initialization time and encrypted
» AES keys never leave the hardware and are not stored in NAND ash
Self-Destruct Data Protection
» Secure volume does not mount until password is veried in hardware
» Password try-counter implemented in tamper-resistent hardware
» Once password try-count is exceeded, all data is erased by hardware
(FIPS 186-2)
Additional Security Features
» USB command channel encryption to protect device communications
» Firmware and software securely updateable over the Internet
» Updates veried by digital signatures in hardware
Physically Secure
» Solid, rugged metal case
» Encryption keys stored in the tamper-resistent IronKey Cryptochip
» All chips are protected by epoxy-based potting compound
» Exceeds military waterproof standards (MIL-STD-810F)
Device Password Protection
The device password is hashed using salted SHA-256 before being transmitted to the IronKey Secure Flash Drive over a secure and unique USB
channel. It is stored in an extremely inaccessible location in the protected
hardware. The hashed password is validated in hardware (there is no “getPassword” function that can retrieve the hashed password), and only after
the password is validated is the AES encryption key unlocked. The password try-counter is also implemented in hardware to prevent memory
rewind attacks. Typing your password incorrectly too many times initi-
ates a patent-pending “ash-trash” self-destruct sequence, which is run in
hardware rather than using software, ensuring the ultimate protection for
your data.
PAGE 6IRONKEY USER GUIDE
Page 8

Password Manager Protection
The IronKey Password Manager and my.ironkey.com work together, giving
you the ability to back up your online passwords to your Online Security
Vault at my.ironkey.com. First, you must unlock your IronKey device, which
requires two-factor authentication. Your passwords are securely stored in
a hidden hardware-encrypted area inside the device (not in the le system), being rst locally encrypted with 256-bit AES, using randomly gener-
ated keys encrypted with a SHA-256 hash of your device password. All
of this data is then doubly encrypted with 128-bit AES hardware encryption. This is the strongest password protection we have ever seen in the
industry.
When you back up your passwords online, IronKey performs a complicated public key cryptography handshake with IronKey’s services using RSA
2048-bit keys. After successful authentication, your encrypted block of
password data is securely transmitted over SSL to your encrypted Online
Security Vault within one of our highly-secure data facilities.
IRONKEY SERVICES SECURITY
Secure Facilities
IronKey hosts its online services at state-of-the-art third-party data center facilities. Physical access to the IronKey systems requires multiple levels of authentication, including but not limited to hand geometry biomet-
ric readers, “man trap” entry, government-issued photo ID verications
and individual access credentials. Each data center facility is equipped with
numerous surveillance cameras, motion detectors, and a sophisticated
alarm system. The IronKey infrastructure resides in a secured cage. The
entire facility is monitored by dedicated on-site security personnel on a
24x7 basis.
Secure Environments & Policies
Logical access to the IronKey environments is controlled by multiple layers of network technologies such as rewalls, routers, intrusion prevention systems and application security appliances. For additional protection,
IronKey partitions its online services and backend applications into different network segments with independent security rules and policies.
Secure Communications & Data at Rest
When users access IronKey web sites and services, all information is exchanged over an encrypted channel. This is accomplished through Secure
Socket Layer (SSL) and by utilizing VeriSign Secure Site and VeriSign Secure
Site Pro certicates. To ensure additional security for its services, IronKey
qualied for and is using Extended Validation SSL. The IronKey applica-
tions encrypt all sensitive data prior to transmitting it within the IronKey
network and storing in databases.
PAGE 7IRONKEY USER GUIDE
Page 9
Secure Sessions: Making Tor Faster and More Secure
IronKey maintains a secure, private Tor network with its own, high-perfor-
mance servers (separate from the public Tor network). This improves the
overall security in at least two ways:
Since IronKey controls the “exit-node” in your encrypted Tor
circuit, we can ensure that no one is injecting unwanted or
malicious content into your online communications, such as
advertisements or spyware. You are not assured this level of
security with other publicly-run exit-nodes.
IronKey can also make sure that no exit-node is redirecting
your web trafc by providing addition DNS protections. This
anti-pharming measure can also help mitigate phishing attacks
and other online threats.
Find lots more technical information at https://learn.ironkey.com.
PAGE 8IRONKEY USER GUIDE
Page 10

How does it work?
Product Walkthrough
Your IronKey Personal Secure Flash Drive consists of the following components:
» IronKey Unlocker (Windows, Mac and Linux)
» IronKey Control Panel (Windows only)
» IronKey Virtual Keyboard (Windows only)
» Mozilla Firefox & IronKey’s Secure Sessions Service (Windows only)
» IronKey Password Manager (Windows XP & Vista only)
» IronKey Secure Backup (Windows only)
» my.ironkey.com (Windows only)
Standard Usage Requires:
» Windows 2000 (SP4), XP (SP2), Vista, Mac OS X (10.4+) or Linux (2.6+) computer
» A USB 2.0 port for high-speed data transfer
» An email address and Internet connection for the online services
INITIALIZING & ACTIVATING YOUR IRONKEY ON WINDOWS
When you open the package, you will nd one IronKey Secure Flash Drive, one lanyard, and a
Quick Start Guide. Below is a brief description of the standard way of setting up an IronKey:
Step Description
1 Plug the IronKey into your
Windows computer’s USB port.
2 The “Initialize Your IronKey”
screen will appear.
Your IronKey can be initialized on a Windows 2000, XP
or Vista computer (see Mac and Linux instructions below). To use the full speed of the IronKey, plug it into a
USB 2.0 port.
The IronKey autoruns as a virtual CD-ROM.
This screen may not appear if your computer does not
allow devices to auto-run. You can start it manually by
double-clicking on the IronKey icon in “My Computer”
and running “IronKey.exe”.
PAGE 9IRONKEY USER GUIDE
Page 11

3 Create
a device
password
Since you can have multiple IronKeys associated with
one IronKey account, the nickname helps you distin-
guish between different IronKey devices.
and a
nickname
for your
IronKey.
Your password is case-sensitive and must be at least 4
characters in length. The threat of brute-force pass-
word attacks is removed by the IronKey’s self-destruct
feature.
4 Back up your password to your
online IronKey account
You have the option to back up your password online
to your my.ironkey.com account. That way, if you ever
forget your password, you can safely log into https://
my.ironkey.com and recover it.
5 Agree to the License Agreements A screen with IronKey’s End-User License Agreement
will appear. This can also be found online at:
https://www.ironkey.com/terms
6 The IronKey will initialize. During this process, it will generate the AES encryption
keys, create the le system for the secure volume, and
copy over secure applications and les to the secure
volume.
7 Activate your my.ironkey.com
account.
my.ironkey.com is a secure site where you can man-
age your IronKey account and devices. Accessing
my.ironkey.com requires two-factor authentication (your
IronKey and your password).
8 Follow the onscreen directions to
setup your my.ironkey.com account.
You will create a unique username and password, con-
rm your email address for out-of-band authentication,
and answer Secret Questions for supplemental authen-
tication.
You will also select a Secret Image that you will see
whenever you log in, as well as a Secret Phrase that is
used as an anti-phishing measure when communicating
with you via email.
9 Respond to the conrmation
email by entering in the activation
code on the website.
IronKey must verify your email address because it uses
it to help you reset your account password, unlock
your my.ironkey.com account, and to notify you about
account security alerts.
At this point, your IronKey is ready to protect your data, identity, and online privacy.
PAGE 10IRONKEY USER GUIDE
Page 12

USING THE IRONKEY UNLOCKER ON WINDOWS
The IronKey Unlocker allows you to securely access your les on multiple operating systems.
It prompts you for your password, securely validates it, and then mounts your secure volume
where all of your les are stored on the IronKey.
Here is how to unlock your IronKey on Windows 2000 (SP4), XP (SP2), and Vista:
Step Description
1 Plug in your IronKey and unlock
it with your password.
When you plug your IronKey in, the “Unlock Your IronKey” window appears (if it does not, you can go to “My
Computer” and double-click on the IronKey drive).
Entering your password correctly (which is veried in
hardware) will mount your secure volume with all your
secure applications and les.
Entering the wrong password 10 consecutive times will
permanently erase all of your data. After every three
attempts, you must unplug and reinsert the IronKey.
2 Choose which action to take
when you unlock it.
By selecting the corresponding checkboxes before
unlocking your IronKey, you can view your secure les,
launch the IronKey Control Panel, unlock the IronKey
in a Read-Only Mode where les cannot be edited,
and/or securely log into your my.ironkey.com account.
Your selection of these checkboxes will be stored as
the default for the next time you plug your device in.
PAGE 11IRONKEY USER GUIDE
Page 13

INITIALIZING YOUR IRONKEY ON A MAC
If you prefer to use a Mac, you can choose to initialize your IronKey on a Mac OS X computer:
Step Description
1 Plug the IronKey into your
computer’s USB port.
Your IronKey will run on Mac OS X (10.4 or 10.5),
PowerPC or Intel computers. It can also be setup and
used on Windows and Linux.
To use the full speed of the IronKey, plug it into a USB
2.0 port.
2 Launch the IronKey Unlocker.
The IronKey has a virtual CD-ROM.
The “Initialize Your IronKey”
screen will appear.
You must start the IronKey Unlocker manually by going
to “IronKey:Mac:IronKey Unlocker” and double-click-
ing on the IronKey icon.
3 Create your device password and
a nickname for your IronKey.
Your password is case-sensitive and must be 4 or more
characters long. The threat of brute-force password
attacks is removed by IronKey’s self-destruct feature.
4 Agree to the License Agreement A screen with IronKey’s End-User License Agreement
will appear. This can also be found online at:
https://www.ironkey.com/terms
5 The IronKey will initialize. During this process, it will generate the AES encryption
key, and create the le system for the secure volume.
Your IronKey is now ready for use.
This process may take a minute.
PAGE 12IRONKEY USER GUIDE
Page 14

USING THE IRONKEY UNLOCKER ON A MAC
The IronKey Unlocker for Mac will allow you to access your les and change your device password on a Mac. You can use the other IronKey applications and services on a Windows computer.
Step Description
1 Plug in your IronKey and unlock
it with your password.
When you plug in your IronKey, go to “IronKey:Mac:
IronKey Unlocker” and double-click on the IronKey
icon.
Entering your password correctly (which is veried
in hardware) will mount your secure volume with all
your secure les.
Entering the wrong password too many times will
permanently erase all of your data. After every three
attempts, you must unplug and reinsert the IronKey.
2 Choose which action to take
when you unlock it.
By selecting the corresponding checkbox before un-
locking your IronKey, you can view your secure les.
3 Locking & unplugging the IronKey Clicking “Lock Drive” will exit open IronKey applica-
tions and lock the device. It is then safe to unplug it
from your computer.
INITIALIZING YOUR IRONKEY ON LINUX
If you prefer to use a Linux computer, you can choose to initialize your IronKey on Linux:
Step Description
1 Plug it into your computer’s USB
port
2 Run the ironkey program from
the IronKey’s linux folder
Your IronKey can be initialized on Linux 2.6+ (x86 sys-
tems only). It can also be setup and used on Windows
and a Mac.
To use the full speed of the IronKey, plug it into a USB
2.0 port.
The IronKey has a virtual CD-ROM.
You must start the IronKey Unlocker manually by going
to linux folder and running ironkey
PAGE 13IRONKEY USER GUIDE
Page 15

3 Create a device password and a
nickname for your IronKey.
Since you can have multiple IronKeys, the nickname
helps you distinguish between different IronKey de-
vices.
Your password is case-sensitive and must be at least 4
characters long . The threat of brute-force password
attacks is removed by the IronKey’s self-destruct fea-
ture.
4 Agree to the license agreement IronKey’s End-User License Agreement will appear.
This can also be found online at:
https://www.ironkey.com/terms
5 The IronKey will initialize. During this process, it will generate the AES encryption
key, and create the le system for the secure volume.
This process may take a minute.
Your IronKey is now ready for use.
USING THE IRONKEY UNLOCKER ON LINUX
The IronKey Unlocker for Linux will allow you to access your les and change your device
password on Linux, allowing you to securely transfer les from and between Windows, Mac,
and Linux computers. You can use the other IronKey applications and services on a Windows
computer.
Depending on your Linux distribution, you may need root privileges to use the program ‘iron-
key’ found in the Linux folder of the mounted virtual CD-ROM. If you have only one IronKey
attached to the system, simply run the program from a command shell with no arguments (e.g.
ironkey). If you have multiple IronKeys, you will have to specify the device name of the one
you wish to unlock.
Note that ‘ironkey’ only unlocks the secure volume; it must then be mounted. Many modern
Linux distributions will do this automatically; if not, run the mount program from the command
line, using the device name printed by ironkey.
ironkey may also be used to change the password or to lock the device. Use:
ironkey --changepwd [devicename]
to change the password of the IronKey named “devicename”. Similarly, use:
ironkey --lock [devicename]
to lock the IronKey named “devicename”, and:
ironkey --read-only
to unlock the IronKey in Read-Only Mode.
PAGE 14IRONKEY USER GUIDE
Page 16

Note that simply unmounting the device will not automatically lock the secure volume. To lock
the device you will have to either unmount and physically remove (unplug) it, or else run:
ironkey --lock
Please note the following important details for using your IronKey on Linux:
1. Kernel Version must be 2.6 or higher
If you compile your own kernel, you must include the following in it:
» DeviceDrivers->SCSIDeviceSupport-><*>SCSICDROMSupport
» DeviceDrivers-><*> Support for Host-side USB
» DeviceDrivers-><*> USB device lesystem
» DeviceDrivers-><*> EHCI HCD (USB 2.0) support
» DeviceDrivers-><*> UHCI HCD (most Intel and VIA) support
» DeviceDrivers-><*> USB Mass Storage Support
The kernels that are included by default in most major distributions already have these features,
so if you are using the default kernel that comes with a supported distribution you do not need
to take any other action.
Also, on 64-bit linux systems the 32-bit libraries will have to be installed in order to run the
ironkey program.
2. Mounting problems
Make sure you have permissions to mount external SCSI & USB devices
» Some distributions do not mount automatically and require the following command to
be run:
mount /dev/<name of the device> /media/<name of the mounted
device>
» The name of the mounted device varies depending on the distribution. The names of
the IronKey devices can be discovered by running:
ironkey --show
You must have permissions to mount external/usb/ash devices
» You must have permissions to run executables off the IronKey CD-ROM in order to
launch the IronKey Unlocker
» You may need root user permissions
4. Supported distributions
Not all distributions of Linux are supported. Please visit https://support.ironkey.com/linux for the
latest list of supported distributions.
See https://support.ironkey.com/linux for more information.
PAGE 15IRONKEY USER GUIDE
Page 17

USING THE IRONKEY CONTROL PANEL
The IronKey Control Panel is a central
location for:
» Launching secure applications
» Securely logging into my.ironkey.com
» Conguring your IronKey settings
» Updating your device
» Changing your IronKey password
» Editing Password Manager data
» Safely locking your device
» Getting online help
Most of the Control Panel’s options
are located in the “Settings” menu.
Step Description
1 Creating, editing, deleting secure
les
2 Updating device rmware/soft-
ware
When you click on “Secure Files” in the IronKey
Control Panel, Windows Explorer will open directly to
your secure volume.
All les on your IronKey are strongly encrypted with
military-grade AES encryption. Encrypting les is
as simple as moving them into the secure volume.
Dragging les onto your desktop will decrypt them
on-the-y in hardware. The IronKey gives you the
convenience of working as you normally would with
a regular ash drive, while at the same time providing
strong and “always-on” security.
The IronKey can securely update its software and
rmware through signed updates that are veried in
hardware. This allows users to keep their devices upto-date and protect themselves from future malware
and online threats.
To check for available updates, click the “Check for Updates” button. If an update is available, you can choose
to download and install it by clicking the “Download
Update” button.
PAGE 16IRONKEY USER GUIDE
Page 18

3 Conguring device settings The Settings menu allows you to congure preferences
to your liking, such as:
»
Enabling/Disabling the Password Manager
»
Enabling/Disabling the Secure Sessions
»
Conguring Password Manager options
»
Select which web browser your IronKey should use
»
Enabling an automatic check for device updates
on a weekly basis
As well as some important drive maintenance features:
»
Reformatting your secure volume
»
Restoring your IronKey applications if they are ever
erased or corrupted
4 Congure your IronKey’s
network and proxy settings
Click on Network Settings to congure how your
IronKey connects to the Internet:
»
Direct Connection: Does not use a proxy
»
Use System Settings: import the proxy settings from
Windows’ Internet Options
»
Use WPAD: Enter the URL to where your Web
Proxy Auto-Detect le is located
»
Manual Proxy: Enter the URL and port number for
your proxy server
If proxy authentication is required, you can enter your
username and password in the appropriate elds.
5 Creating a Lost & Found Message This feature allows you to create a message that will
appear on the IronKey Unlocker window. In the event
that you lose your IronKey, someone can return it to
you if you provide your contact information.
6 Changing your device password You can change your device password and option-
ally back it up online to your Online Security Vault at
my.ironkey.com.
Changing your password on a regular basis is a good
security practice. However, be especially careful to
remember your IronKey password.
PAGE 17IRONKEY USER GUIDE
Page 19

7 Adding, renaming, and removing
applications to the Applications
List
8 Locking & unplugging the IronKey Clicking “Lock Drive” will exit open IronKey applica-
To manage the items in the Application List of the
IronKey Control Panel, simply right-click anywhere in
Application List. A menu will appear allowing you to:
1. Browse to a new application to add it to the list
2. Rename existing applications in the list
3. Delete an application from the list
4. Modify the way the list is presented
Please note that:
»
Items in the list are shortcuts to actual les. Manag-
ing the items in the list will not alter the actual le.
»
Items are automatically sorted alphabetically
»
Any le can be added to the list, including docu-
ments, images, and batch les
»
For items that are not applications, Windows will
open the item with the default program associated
with that letype
tions and lock the device. It is then safe to unplug it
from your computer.
Do not unplug your IronKey while applications are still
running. This could result in data corruption.
USING THE IRONKEY VIRTUAL KEYBOARD
If you are using your IronKey on an unfamiliar computer and are concerned about keylogging
and screenlogging spyware, use the IronKey Virtual Keyboard, which helps protects your passwords by letting you click out letters and numbers. The underlying techniques in the IronKey
Virtual Keyboard will bypass many trojans, keyloggers, and screenloggers.
The IronKey Virtual Keyboard can be launched in a couple of ways:
»
In places where you enter a password into the IronKey (e.g. the IronKey Unlocker, changing
your device password, initializing your device), click on the Virtual Keyboard icon
»
Use the keyboard shortcut of CTRL + ALT + V
The IronKey Virtual Keyboard can be used in a number of other applications when you need
extra security typing out information (e.g. email, documents, etc.).
PAGE 18IRONKEY USER GUIDE
Page 20

Step Description
1 Click the IronKey Virtual Key-
board icon.
The IronKey Virtual Keyboard will
appear. Alternatively, you can press
CTRL + ALT + V
2 Click on the keys to type out
your password. Click on ‘Enter’
when you are nished.
3 You can optionally click the
“Randomize” button to randomize where the keys are. This helps
protect against screenloggers.
Note that you can use the IronKey Virtual Keyboard
in conjunction with the actual keyboard if you wish, so
that some characters are typed and some are clicked.
Notice that when you click on a key in the Virtual Key-
board, all of the keys will go blank. This is a protection
that prevents screenloggers from capturing what you
clicked on.
If you do not wish to use this protection, simple dis-
able it in the options menu next to the close button.
You can also have the Virtual Keyboard automatically
launch when it encounters password elds. This too is
congured in the options menu.
USING THE ONBOARD FIREFOX & SECURE SESSIONS SERVICE
Since your IronKey comes with a Firefox web browser already onboard, none of your cookies,
history les, bookmarks, add-ons or online passwords are stored on the local computer. Now
you can carry your personalized web experience with you to other computers without worry.
Step Description
1 Launch the onboard Firefox web
browser for portable surng
Clicking on the Mozilla Firefox icon in the Applica-
tions list of the IronKey Control Panel will launch the
onboard Firefox. You cannot have a local version of
Firefox running at the same time; if you do, you will be
prompted to close it.
PAGE 19IRONKEY USER GUIDE
Page 21

2 Toggle Secure Sessions for secure
and private surng
3 Using the Secure Sessions Tools:
Network Map, Bandwidth Meter,
and Changing Identities
Clicking the IronKey button on the bottom right of
the onboard Firefox will silently turn IronKey’s Secure
Sessions Service on/off. This will create an encrypted
tunnel directly from your IronKey, out to a secured
IronKey web server, where it is then decrypted and
sent out to the destination site.
This security gives you anti-phishing and anti-pharm-
ing protection (for example, we do our own DNS
checking), as well as enhanced privacy protection (for
example your IP address will not be available to other
websites and ISPs). You can check this out by going to
a site such as whatismyip.com or ipchicken.com.
At any point while using Secure Sessions, you can
launch additional tools form the IronKey System Tray
Menu that show you more information regarding your
web trafc and current session.
The Network Map will show all of your available
“circuits” and where in the world your trafc will be
coming from.
The Bandwidth Meter will show you your current
bandwidth metrics.
You can easily change your apparent online “identity”,
which creates a new random circuit and changes the
path of your encrypted web trafc. As you will be
coming from a different IP address, it will likely appear
to websites that you are a different person.
PAGE 20IRONKEY USER GUIDE
Page 22

USING THE IRONKEY PASSWORD MANAGER
The IronKey Password Manager connects to the onboard Firefox browser, or to Internet Ex-
plorer (versions 6 or 7) on your computer, automatically lling in your saved passwords so you
can log directly into your online
accounts. The IronKey Password
Manager can securely store your
sensitive online identity information, including usernames, passwords, credit card numbers and
addresses. It can even generate
strong passwords for you, so that
you can really lock down your
online accounts. Not having to
type out your passwords provides
added protection from keyloggers
and other crimeware.
IronKey’s Password Manager also allows you to back up your encrypted Password Manger data
to your Online Security Vault, synchronize password data between IronKeys, or, if your IronKey
is ever lost or stolen, securely restore all your passwords to a new IronKey. Only you can access
and decrypt your passwords.
The IronKey Password Manager does not store your passwords in a le on the le system of
the ash drive, so malware will not be able to simple copy off your password database.
Step Description
1 Adding Portable Bookmarks To make a bookmark work in both the onboard
Firefox and the local PC’s Internet Explorer, simply
click the ‘Add Website” button on the IronKey Toolbar.
This will add it to your Portable Bookmarks list, which
you can access by clicking “Portable Bookmarks”.
2 Adding online accounts The IronKey Password Manager uses a self-learning
approach to capturing your logins to your online ac-
counts. To store a login, simply log into a site as you
normally would. The IronKey Password Manager will
prompt you to ask if you want to store this password
securely on your IronKey.
The next time you return to that website, you will be
asked if you want to log in with that username, or, if
you added it to your Portable Bookmark list when you
created the login, you can select the website from your
Portable Bookmarks in the IronKey Toolbar and the
IronKey Password Manager will automatically log you
into that website.
PAGE 21IRONKEY USER GUIDE
Page 23

3 Editing/deleting logins and Por-
table Bookmarks
You can manage your Password Manager accounts
from within the IronKey Control Panel. Each website
will have a set-able name, a URL, a username (logins
only), and a password (logins only).
Your passwords are not shown unless you click the
“Show” checkbox.
4 Backing Up and Restoring Pass-
word Manager Data
You can securely back up your encrypted Password
Manager data to your Online Security Vault. Simply
click the corresponding buttons from within the Iron-
Key Control Panel. This procedure will back up your
Portable Bookmarks, logins, and Form Filler data.
Synchronizing IronKeys (or setting up Master-Slave
relationships) is easy since you can restore password
backups to your other IronKeys.
5 Using the Form Filler You can have the IronKey Password Manager automati-
cally ll in your webform data, such as names, phone
numbers, addresses, credit card data and email ad-
dresses.
First, set up this information by clicking on the “Set-
tings” button in the IronKey Toolbar. Then, to ll a
webform, simply click the “Form Filler” button.
6 Generating strong and random
passwords
You can use the Password Generator (located within
the IronKey Control Panel) to create long, random
passwords. Then, you can have the IronKey Password
Manager remember then for you. Simply copy and
paste them into a webform when logging into an online
account.
7 Automatically logging into online
accounts
When you add a login to your Portable Bookmarks,
that login will appear not only in your Portable Book-
marks list, but also in the IronKey System Tray Menu.
Simply right-click on the IronKey icon in the System
Tray, and then click on the Secure Login. The onboard
Firefox web browser will launch and automatically log
you into the account.
Safely logging into your online accounts has never been
easier.
PAGE 22IRONKEY USER GUIDE
Page 24

USING THE SECURE BACKUP SOFTWARE
If your IronKey is lost or stolen, you
have peace of mind knowing that your
condential information cannot be seen
by anyone but you. And getting your
data back is simple with IronKey’s Secure
Backup software, which securely restores your data to a new IronKey.
Back up your data on a regular basis and
always before an update.
Step Description
1 Backing up your IronKey You can create an encrypted backup of a single
le or your entire IronKey to your local computer. Click on the “Secure Backup” button in the
IronKey Control Panel, select a destination folder,
and select which les to back up. It’s that simple.
2 Restoring encrypted backups If you ever lose your IronKey, you can restore
your data from an encrypted backup. Open the
Secure Backup client, select the location on your
local computer where the backup is located, and
select which les/folders to restore. If the data is
coming from a different IronKey, you will have to
supply the device password for that IronKey.
PAGE 23IRONKEY USER GUIDE
Page 25

IMPORTING A DIGITAL CERTIFICATE INTO THE IRONKEY
The IronKey Cryptochip includes a limited amount of extremely secure hardware storage space,
which can be used for storing the private key associated with a digital certicate. This provides
you with additional strong authentication capabilities. For example, you could store a self-signed
certicate used for internal systems that will allow you to automatically log in when using the
IronKey’s onboard Firefox web browser.
The import process uses IronKey’s PKCS#11 interface and requires Mozilla Firefox. Note that
there is only space for one additional private key in the IronKey Cryptochip, though that key
will receive the security benets of the Cryptochip’s tamperproof hardware and self-destruct
mechanisms.
Step Description
1 Open the onboard Firefox Click on the icon in the IronKey Control Panel’s applica-
tion list on your user’s device.
2 Open Firefox’s Options menu
to the Encryption tab.
3 Click the ‘ViewCerticates’
button.
This will open the Firefox
Certicate Manager
1. Click the ‘Tools’ in the menu bar
2. Click on ‘Options...’
3. Click the ‘Advanced’ icon
4. Click on the ‘Encryption’ tab
PAGE 24IRONKEY USER GUIDE
Page 26

4 Note that IronKey’s certicate
is available here. Now you can
add your own.
Click the ‘Import’ button.
5 Browse to the PKCS#12-for-
mat certicate le and open it.
6 A window will appear ask-
ing you to conrm where to
store the certicate.
Choose “IronKey PKCS#11”
7 Enter the password that was
used to protect the certicate.
If no password was used, sim-
ply leave the text eld blank.
8 Your certicate is now stored
securely in the IronKey
Cryptochip and is available
for use in the onboard Mozilla
Firefox.
You will be prompted for the location of the PKCS#12-
format certicate le (le extension will be .p12 in UNIX/
Linux, .pfx in Windows).
PAGE 25IRONKEY USER GUIDE
Page 27

USING MY.IRONKEY.COM
Your IronKey supports advanced cryptographic authentication using strong PKI key pairs generated in the IronKey Cryptochip. When you log into my.ironkey.com from your device, it uses these
unique keys as your digital identity credentials. This locks down your account so that you must
have both your IronKey and your password in order to gain access. In other words, only you can
access your online IronKey account, even if someone stole your IronKey or your password.
In the event that you
ever lose your IronKey,
you can still access the
site in Safe Mode: a
restricted mode with
limited functionality. This
is useful for marking
your IronKey as lost, or
recovering a forgotten
password.
Step Description
1 Securely logging into your account You can securely log into your my.ironkey.com by
clicking the “my.ironkey.com” button in the IronKey
Control Panel. This will initiate a complex PKI
handshake, thus logging you in with strong, multifactor authentication.
If you ever lose your IronKey, you can log into
Safe Mode by going to https://my.ironkey.com, log-
ging in the account credentials you created when
you activated your account. This will allow you
to mark an IronKey as lost or recover a forgotten
device password.
2 Marking IronKeys as lost If you ever lose your IronKey, you can rest as-
sured that no one will ever get your data. As an
additional precaution, you can mark an IronKey as
lost from within my.ironkey.com, which will prevent
that device from ever accessing your account. If
you nd your IronKey later, you can also mark it
as found again.
3 Recovering device passwords People sometimes forget passwords. IronKey
gives you the option to back up your device password to your Online Security Vault at my.ironkey.
com. That way, you can log into Safe Mode or with
another IronKey and recover the password.
PAGE 26IRONKEY USER GUIDE
Page 28

4 Monitoring account activities The Account Dashboard shows you the recent
activities on your account, such as logins, failed
password attempts, and when your device password has been recovered.
5 Enabling Account Alerts for real-time
account monitoring
6 Changing account credentials You can change your password, Secret Questions,
You can enable a number of Account Alerts for
additional insight into what activities are occurring on your my.ironkey.com account. An email will
be sent to you with details on the security event,
such as the time and IP address of the event.
All emails regarding your account will have part of
your Secret Phrase in the subject line for additional anti-phishing protection.
Secret Image and Phrase, as well as your email addresses from within my.ironkey.com as often as you
wish to ensure that no one else may access your
account.
Creating a secondary email address gives you a
fail-safe in case your primary email address is no
longer available.
In the event that you ever lose your IronKey or forget your IronKey device password, you can
still access the site in Safe Mode: a restricted mode with limited functionality. This is useful for
marking your IronKey as lost, or recovering a forgotten password.
Step Description
1 Go to https://my.ironkey.com Here you will log into Safe Mode without your
IronKey.
2 Enter your email address (or user-
name) and your online account pass-
word. Click “Submit”
3 An email will be sent to you with a
Login Code.
4 You are now logged into Safe Mode. If you had forgotten your device password and
Your Secret Image will be displayed so that you
know you are at the correct site.
Do not enter your device password in this screen.
If you have forgotten your online account pass-
word, click the “Reset Password” link.
Copy and paste that login code into the page that
asks for it.
Depending on the conguration of your account,
you may need to answer your Secret Questions.
have backed it up to your Online Security Vault,
you can recover it now.
PAGE 27IRONKEY USER GUIDE
Page 29

USING YOUR IRONKEY IN READ-ONLY MODE
You can unlock your IronKey in a read-only state such that les on your IronKey cannot be edited. An example of when this is useful is when you want to access a le on your IronKey while
using an untrusted or unknown computer. If you unlock your IronKey in Read-Only Mode, you
need not fear that malware on that machine will infect your IronKey or modify your les.
When you unlock your IronKey in Read-Only Mode, you will remain in Read-Only Mode until
you lock your IronKey.
Note that some features are not available in Read-Only Mode because they require modifying
les on your IronKey. Examples of unavailable features include the onboard Firefox, reformatting, updating and restoring applications and les to your IronKey, and using the Applications List.
On Windows and Mac OS X Computers:
Step Description
1 When unlocking your IronKey, select
the “Unlock IronKey in Read-Only
Mode” checkbox
2 You will see a message in the IronKey
Control Panel that conrms you are in
Read-Only Mode.
On Linux Computers:
Step Description
1 To unlock your IronKey in Read-Only
ironkey --read-only
Mode on Linux, use:
2 To return to a normal state where you
ironkey --lock
can edit les again, lock your IronKey
PAGE 28IRONKEY USER GUIDE
Page 30

Product Specications
CAPACITY*
1GB, 2GB, 4GB, 8GB
SPEED*
Up to 30 MB per second read speed
Up to 20 MB per second write speed
DIMENSIONS
75mm X 19mm X 9mm
WEIGHT
0.8 oz
WATERPROOF
MIL-STD-810F
OPERATING TEMPERATURE
-40 C, +85 C
OPERATING SHOCK
16G rms
ENCRYPTION
Hardware: 128-bit AES (CBC-Mode)
Hashing: 256-bit SHA
PKI: 2048-bit RSA
FIPS CERTIFICATIONS
FIPS 140-2 Level 2 (Certicate Number 938)
FIPS 186-2 (Certicate Numbers 305 and 380)
FIPS 197 (Certicate Numbers 655 and 689)
HARDWARE
USB 2.0 High-Speed & USB 1.1
OS COMPATIBILITY
Windows 2000 (SP4), XP (SP2), Vista
IronKey Unlocker for Linux (2.6+, x86)
IronKey Unlocker for Mac (10.4+, PPC and Intel)
Designed and Assembled in the U.S.A.
IronKey devices do not require any
software or drivers to be installed.
* Speeds tested with 4GB device in a laboratory environment with Iometer software. Actual speeds may vary.
Advertised capacity is approximate and not all of it will be available for storage. Some space is required for onboard software.
PAGE 29IRONKEY USER GUIDE
Page 31

What’s next?
In many ways, that’s up to you. We are focused on building not only the
world’s most secure ash drive, but also enabling technologies that are
simple and enjoyable to use. Your feedback really matters to us, and we
carefully review all feature requests and customer feedback for prioritization of our next great features and products.
Have a cool idea or suggestion? Please let us know. You can open a
thread on the IronKey Forum (forum.ironkey.com) or submit feedback to
feedback@ironkey.com. Let us know if you would like to be a beta tester
of new functionality.
Where can I go for more info?
We are endeavoring to be very open about the security architecture and
technology that we use in designing and building the IronKey devices and
online services. A great deal of information can be found online on our
websites:
forum.ironkey.com User forum with thousands of “IronKeyologists”
www.ironkey.com General Information
learn.ironkey.com Technical Information, such as whitepapers & FAQs
support.ironkey.com Customer support information
Who is the IronKey Team?
The IronKey Team consists of security, fraud, and industry experts with
many years of background at companies such as Visa, RSA Security, PayPal,
Authenex, Nokia, Cisco, Lexar, Netscape, Tumbleweed, Valicert, Apple, and
the Department of Homeland Security. IronKey CEO Dave Jevans is also
the chairman of the Anti-Phishing Working Group (www.antiphishing.org).
We have spent years and millions of dollars of research and development
to create the IronKey. Simple, accessible, and of great value, now you can
carry the world’s most secure ash drive to protect your digital life online
and on-the-go.
PAGE 30IRONKEY USER GUIDE
Page 32

Contact Information
Product Feedback Feature Requests
feedback@ironkey.com featurerequest@ironkey.com
IronKey Online IronKey Support
https://my.ironkey.com https://support.ironkey.com
https://learn.ironkey.com support@ironkey.com
https://support.ironkey.com 5150 El Camino Real, Suite C31
https://forum.ironkey.com Los Altos, CA 94022 USA
https://store.ironkey.com Monday - Friday, 8am - 5pm PST
Note: IronKey is not liable for technical or editorial errors and/or omissions contained herein; nor for incidental or consequential damages resulting from the furnishing or use of this material. The information provided
herein is subject to change without notice.
The information contained in this document represents the current view of IronKey on the issue discussed as of the date of publication. IronKey cannot guarantee the accuracy of any information presented after the date of publication. This document is for information purposes only. IronKey makes
no warranties, expressed or implied, in this document. IronKey and the IronKey logo are trademarks of IronKey, Inc. in the United States and other
countries. All other trademarks are the properties of their respective owners. © 2008 IronKey, Inc. All rights reserved. IK0010883
PAGE 31IRONKEY USER GUIDE
 Loading...
Loading...