Page 1

ioSafe® R4 : Disaster-proof NAS/RAID
User’s Guide, ioSafe R4
/N: 900-10004-00 REV 02
Page 2

CONGRATULATIONS!
This product represents the latest in disaster proof computer equipment. This system has the
following disaster proof specifications:
1. Fire proof data storage to 1700 F, 1 hr duration per UL72
2. Waterproof data storage to 30’ depth, 30 days in fresh water or salt water.
IMPORTANT NOTE: DISASTER RECOVERY
Please refer to the website for the latest disaster recovery procedures and product warranties. While
no device can protect against every disaster, this ioSafe R4 system has been tested to protect data
against fires, floods and building collapse. More information is available and updated online at our
website www.iosafe.com. Please see the website or details in this manual for the terms and
conditions of our Disaster Recovery Service.
If you have a disaster please contact the ioSafe Disaster Response Team at 1.888.984.6723 x430 for
assistance in recovery of your ioSafe unit. Due to the unique nature of individual disasters, different
recovery strategies may have to be employed depending on your particular circumstances. Let the
experts at ioSafe assist with recovery.
Some general rules regarding recovery are as follows:
1. Don’t attempt to recover the ioSafe R4 unit by yourself. The lack of our expert support
might lead to irretrievable data loss. Let our disaster support engineers help recover your
critical data.
2. Turn off the power.
3. Do not restart the ioSafe R4 after a disaster without first consulting with an ioSafe disaster
support person first.
Do not try to reconfigure or re-initialize the RAID array.
4.
Copyright © 2008,
ioSafe Inc
. All rights reserved.
http://www.iosafe.com
ioSafe is a trademark or registered trademark of ioSafe Inc.. ReadyNAS, X-RAID,
FrontView, RAIDar, RAIDiator, Network Storage Processor, and NSP are trademarks
or registered trademarks of Infrant Technologies Inc. All other product names are the
property of their respective owner.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
2
Page 3

Limited Warranty Statement
Appendix A
Warranty Services
End User Limited Product Warranty
ioSafe Incorporated, ("ioSafe") values your business and always attempts to provide you the ver y best data
protection and recovery services.
No limited warranty is provided by ioSafe unless you are the original customer of the product. ioSafe’s warranty is
non-transferable. No limited warrant is provided unless your ioSafe product ("Product") was purchased from an
authorized distributor or authorized reseller. Distributors may sell Products to resell ers who then sell Products to end
users. Please see below for warranty information or obtaining service. No warranty service is provided unless the
Product is returned ioSafe.
Warranty Policy
ioSafe warrants to the end user customer, subject to limitations list below, that the warranted hardware components,
listed below, shall be free from defects in material or workmanship and will conform to ioSafe's specification for the
particular Product for the applicable warranty period. ioSafe further warrants that for the applicable warrant period
shown below and starting from the date of purchase, the media on which any software included in the hardware
components is furnished will be free from defects in materials and workmanship under normal use. Except for the
foregoing, such software is provided AS IS. During the applicable warranty period ioSafe will repair or replace (at
ioSafe’s option) any warranted hardware part which does not comply with this warranty with a new or functionally
equivalent replacement part, provided the defective part is returned to ioSafe as described in the “Returned Materials
Authorization (RMA
)” section detailed below.
Warranted Product Warranty Period
ioSafe S2 3 Years – Optional 5 Years
ioSafe R4 3 Years – Optional 5 Years
Note:
The limited warranty extends only for the period of time set forth above. The period comm ences from the date of
purchase of the original Product. To verify the warranty of your Product, please maintain the receipt of the original
Purchase. In the United States, some states do not allow limitations on how long implied warranties last, so the above
limitation may not apply to you.
THERE ARE NO WARRANTIES WHICH EXTEND BEYOND THE FACE OF THE IOSAFE LIMITED WARRANTY.
IOSAFE DISCLAIMS ALL OTHER WARRANTIES, EXPRESS OR IMPLIED, REGARDING THE PRODUCTS,
INCLUDING ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE
OR NONINFRINGEMENT. IN THE UNITED STATES, SOME STATES DO NOT ALLOW THE EXCLUSION OF THE
IMPLIED WARRANTIES, SO THE ABOVE EXCLUSION MAY NOT APPLY TO YOU.
Return Material Authorization (RMA)
No Product may be returned directly to ioSafe without first contacting ioSafe for a Return Material Authorization
("RMA") number. If it is determined that the Product may be defective, you will be given an RMA number and
instructions for Product return. An unauthorized return, i.e. one for which an RMA number has not been issued, will
be returned to you at your expense. Authorized returns are to be shipped prepaid and insured to the address on the
RMA in an approved shipping container. To request an RMA, please refer to the ioSafe web site at www.iosafe.com.
Extended Warranty
Customers can purchase an extended warranty on eligible ioSafe products with less than a 5-year warranty. The
maximum warranty period for these products, including any warranty extension, cannot be longer than 5 years from
the date of purchase. Extended warranty is currently available for purchase online.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
3
Page 4

LIMITATION OF REMEDIES
YOUR EXCLUSIVE REMEDY FOR ANY DEFECTIVE PRODUCT IS LIMITED TO THE REPAIR OR
REPLACEMENT OF THE DEFECTIVE PRODUCT.
ioSafe may elect which remedy or combination of remedies to provide in its sole discretion. ioSafe shall have a
reasonable time after determining that a defective Product exists to repair or replace a defective Product. ioSafe's
replacement Product under its limited warranty will be manufactured from new and serviceable used parts. ioSafe's
warranty applies to repaired or replaced Products for the balance of the a pplicable period of the original warranty or
ninety days from the date of shipment of a repaired or replaced Product, whichever is longer.
LIMITATION OF DAMAGES
IOSAFE'S ENTIRE LIABILITY FOR ANY DEFECTIVE PRODUCT SHALL IN NO EVENT EXCEED THE PURCHASE
PRICE FOR THE DEFECTIVE PRODUCT. THIS LIMITATION APPLIES EVEN IF IOSAFE CANNOT OR DOES NOT
REPAIR OR REPLACE ANY DEFECTIVE PRODUCT AND YOUR EXCLUSIVE REMEDY FAILS OF ITS
ESSENTIAL PURPOSE.
NO CONSEQUENTIAL OR OTHER DAMAGES
NOTWITHSTANDING ANYTHING ELSE IN THIS POLICY OR OTHERWISE, IOSAFE WILL NOT BE LIABLE WITH
RESPECT TO THE PRODUCTS UNDER ANY CONTRACT, NEGLIGENCE, STRICT LIABILITY OR OTHER LEGAL
OR EQUITABLE THEORY (I) FOR ANY AMOUNT IN EXCESS OF THE PURCHASE PRICE FOR THE DEFECTIVE
PRODUCT OR (II) FOR ANY GENERAL, CONSEQUENTIAL, PUNITIVE, INCIDENTAL OR SPECIAL DAMAGES.
THESE INCLUDE LOSS OF RECORDED DATA, INTERRUPTION OF USE, THE COST OF RECOVERY OF LOST
DATA, LOST PROFITS AND THE COST OF THE INSTALLATION OR REMOVAL OF ANY PRODUCTS, THE
INSTALLATION OF REPLACEMENT PRODUCTS, AND ANY INSPECTION, TESTING, OR REDESIGN CAUSED
BY ANY DEFECT OR BY THE REPAIR OR REPLACEMENT OF PRODUCTS ARISING FROM A DEFECT IN ANY
PRODUCT. THIS SECTION DOES NOT LIMIT LIABILITY FOR BODILY INJURY OF A PERSON.
IN THE UNITED STATES, SOME STATES DO NOT ALLOW EXCLUSION OR LIMITATION OF INCIDENTAL OR
CONSEQUENTIAL DAMAGES, SO THE LIMITATIONS ABOVE MAY NOT APPLY TO YOU. THIS WARRANTY
GIVES YOU SPECIFIC LEGAL RIGHTS, AND YOU MAY ALSO HAVE OTHER RIGHTS WHICH VARY FROM
STATE TO STATE.
Your Use of the Product
ioSafe will have no liability for any Product returned if ioSafe determines that:
• The product was stolen from ioSafe.
• The asserted defect:
A. is not present,
B. cannot reasonably be fixed because of damage occurring when the Product is in the possession of
someone other than ioSafe, or
C. is attributable to misuse, improper installation, alteration (including removing or obliterating labels
and opening or removing external covers (unless authorized to do so by ioSafe or an authorized
Service Center)), accident or mishandling while in the possession of someone other than ioSafe.
• The Product was not sold to you as new.
Additional Limitations on Warranty
ioSafe’s limited warranty does not cover Products which have been received improperly packaged, altered, or
physically damaged. Products will be inspected upon receipt. You can view additional examples of the warranty
limitations below by clicking on the available links.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
4
Page 5
ioSafe Disaster Recovery Service Terms and Conditions
As applicable during the warranty period and proper registering of an ioSafe product, ioSafe will assist the original purchaser
who has experienced a “qualified disaster” to restore the data that was stored on their ioSafe product by the following ways:
1. ioSafe will provide phone or email based support to assist in recovering the data, or
2. ioSafe will pay for the disaster exposed product to be shipped back to ioSafe headquarters for data recovery. If data
recovery is successful, a replacement product will be loaded with the original data and shipped back to the original user, or
3. if the data recovery by ioSafe is not successful, ioSafe will pay up to the amount shown in the table below for the specific
ioSafe product to a third party disk recovery service of ioSafe's choice to extract the data. Any data extracted will be loaded on
a replacement product and shipped back to the original user. ioSafe has the right to use a factory refurbished product as the
replacement product.
Product Line U.S. Dollars per disk
ioSafe S2, ioSafe R4 $5,000
ioSafe's good faith attempts to restore and recover the data in accordance with these terms and conditions shall b e the
purchaser's sole and exclusive remedy and ioSafe shall not be liable for any damages whatsoever. ioSafe cannot guarantee
that any data will be recoverable nor can it guarantee which data files are on the ioSafe product. Data restoration or recovery
shall be strictly limited to whatever files are restorable or recoverable and not what the purchaser believ es to exist on the
ioSafe product. Only one instance of data extraction per ioSafe product is covered by this program. Other exclusions may
apply. See web site for details: www.iosafe.com.
A “qualified disaster” is defined as a disaster by which a police or fire incident report is written to describe the disaster event.
The disaster event would include, but is not limited to: fire, flood, theft and acts of God.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
5
Page 6

Contents
About This Guide 10
1 FrontView Advanced Control 11
Network 14
Ethernet 14
► Speed/Duplex Mode 15
► MTU 15
► VLAN Setting 15
► Performance Setting 16
Global Network Settings 17
► Hostname 17
► Default Gateway 17
► DNS 17
WINS 18
DHCP 19
Route 20
Security 21
Admin Password 21
Security Mode Selection 22
Share Security Mode 23
► Specify a Workgroup 23
► Share Accounts 23
User Security Mode 23
► Specify a Workgroup 24
► Setting up Accounts 24
► Managing Groups 25
► Managing Users 28
► Setting Accounts Preferences 30
Domain Security Mode 31
► Domain/ADS Authentication 31
► Setting up Accounts 32
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
6
Page 7

Services 33
Standard File Protocols 33
Streaming Services 34
Discovery Services 36
Volumes 37
Volume Management 37
► Advantages of Flex-RAID 37
► Advantages of X-RAID 37
Volume Management for Flex-RAID 37
► Deleting a Volume 38
► Adding a Volume 39
► RAID Settings 40
Volume Management for X-RAID 41
► X-RAID Redundancy Overhead 41
► X-RAID Has one data volume 42
► Adding a 2nd DISK for Redundancy 42
► Adding a 3rd and 4th DISK for MORE Capacity 42
► Replacing All Your Disks for Even MORE Capacity 42
Changing Between X-RAID and Flex-RAID Modes 43
Snapshot 43
► Taking and Scheduling Snapshot 43
► Resizing Snapshot Space 46
USB Storage 47
Shares 50
Adding Shares 50
Managing Shares 51
► Setting Share Access in Share Mode 53
► Setting Share Access in User and Domain Modes 55
► Advanced Options 58
USB Shares 59
Printers 60
Print Shares over CIFS/SMB 60
IPP Printing 61
Managing Print Queues 61
Backup 62
Adding a New Backup Job 62
► Step 1 – Select Backup Source 63
► Step 2 – Select Backup Destination 65
► Step 3 – Choose Backup Schedule 65
► Step 4 – Choose Backup Options 65
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
7
Page 8

Viewing the Backup Schedule 67
Programming the Backup Button 68
Viewing the Backup Log 68
Editing a Backup Job 68
System 69
Clock 69
► System Time 69
► NTP Option 69
Alerts 70
► Alerts Contacts 70
► Alerts Settings 71
► SNMP 72
► SMTP 73
Performance 74
► Adding a UPS for performance 75
Language 76
Unicode for User, Group, and Share Names 77
Enable Character encoding conversion for FTP clients 77
Updating ioSafe R4 77
► Remote Update 77
► Local Update 79
► Settings 80
► Factory Default 80
Power Management 82
► Disk Spin-down Option 82
► Power Timer 83
► UPS Configuration 83
Shutdown 84
Status 85
Health 85
Logs 86
2 Accessing Shares 87
Windows 88
MAC OS X 89
AFP over Bonjour 89
AFP over AppleTalk 91
MAC OS 9 93
Linux/Unix 95
Web Browser 96
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
8
Page 9

FTP / FTPS 98
Rsync 99
Networked DVE Players and UPnP AV Media Adapters 100
3 Replacing a Failed Disk 101
Locate the Failed Disk 101
Ordering Replacement Disk 101
Replace the Failed Disk 101
Re-synchronize the Volume 102
Disaster Recovery Procedure 102
4 System Reset Switch 105
5 Changing User Passwords 107
A RAID Levels Simplified 108
RAID Level 0 108
RAID Level 1 108
RAID Level 5 108
RAID Level “X” (X-RAID) 109
B Input Field Format 110
Domain/Workgroup Name 110
Host 110
Host Name 110
ioSafe R4 Host Name 110
Host Expression 111
Share Name 111
Share Password 111
SNMP Community 111
User/Group Name 111
User Password 111
C Glossary 112
D If You Need Help… 113
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
9
Page 10

About This Guide
Congratulations and thank you for purchasing an ioSafe disaster proof backup and storage system
from ioSafe Inc. This ioSafe system represents the latest technology in disaster-proof computer
hardware.
Chapter 1
, “FrontView Advanced Control”, describes all the menus and tabs available in the
Advanced Control mode.
If you have already configured the ioSafe R4 and you need help in accessing the shares on the ioSafe
R4, skip to
In the event of a disk failure, the proper procedure for replacing the failed disk is in
Chapter 2
, “Accessing Shares”.
Chapter 3
“Replacing a Failed Disk”.
Sometimes it may be necessary to re-install the firmware or reset the system back to the factory
default configuration.
Chapter 5
, “Changing User Passwords”, covers how non-admin users can access FrontView to
Chapter 4
, “System Reset Switch”, explains the process for doing both.
change their password.
For an explanation of the RAID levels that the ioSafe R4 supports, please refer to
Appendix A
“RAID Levels Simplified”.
If you have questions on what constitutes a valid input for host name, workgroup, or password,
Appendix B
Appendix C
, “Input Field Format”, describes these and more.
, “Glossary”, provides definitions for some of the technical terminologies used in this
document.
,
,
If you need help during setup, refer to
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
Appendix D
, “If You Need Help…”.
10
Page 11
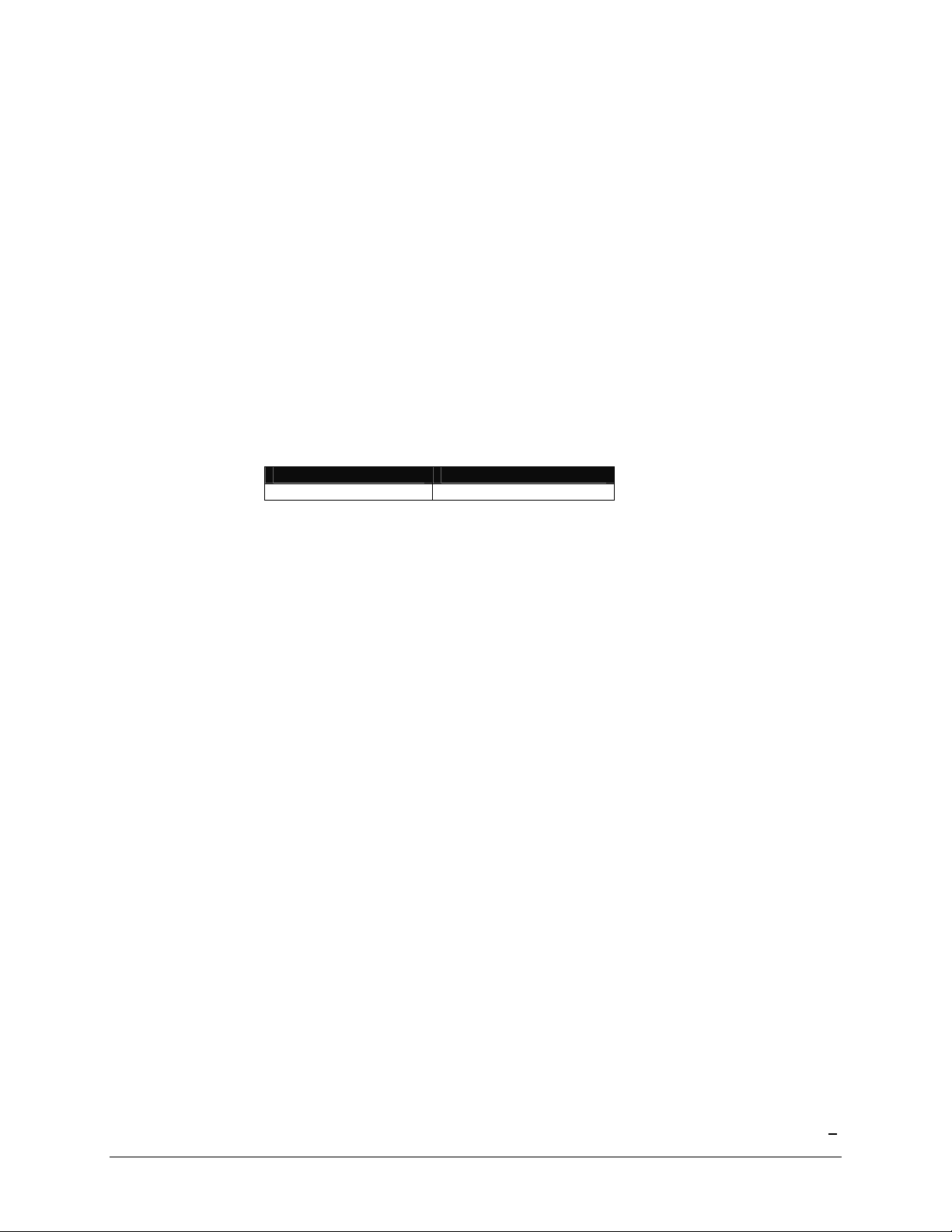
Chapter
1
FrontView Advanced Control
The Advanced Control mode offers the all settings available in the Setup Wizard plus more.
When you first switch to this mode, you’ll see the menus on the left that allow you to quickly jump
to the desired menu page. Towards the bottom left, you’ll notice buttons that allow you to switch
back and forth between the Setup Wizard mode and the Advanced Control mode.
As you click on the menu buttons, you’ll notice a similar theme across all menu pages. At the top
right corner is the command bar which typically provides options to return to the home page,
refresh the browser window, display help where available, or to log out of the session. Due to
security reasons, the
which is necessary to securely log out.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
Logout
button only acts as a reminder to close the current browser session
11
Page 12

At the furthest bottom is the status bar with the date button which doubles its duty as a clock and a
link to the Clock page. The status LEDs to the right gives a quick glimpse of the system device
status.
The statuses represent:
Not present
Normal
– No disk or device attached.
– Device in normal operating mode. If the LED is blinking, this disk is currently
re-syncing. During the re-sync process, the performance is temporarily in a “degraded”
mode and another disk failure in the volume will render it dead.
Warning or Dead
Inactive spare
– The device has failed or requires attention.
– This disk is a “hot spare” on standby. When a disk fails, this disk will
take over automatically.
Awaiting re-sync
Life support mode
– This disk is waiting to re-sync to the RAID volume.
– The volume has encountered multiple disk failures and is in the state
of being marked dead. However, the ioSafe R4 has blocked it from being marked dead in
the event that someone may have accidentally pulled out the wrong disk during runtime. If
the wrong disk was pulled out, shutdown the ioSafe R4 immediately, reconnect the disk,
and power-on the ioSafe R4. If you reconnect the disk during runtime, the ioSafe R4 will
mark it as a newly added disk and you will no longer be able to access the data on it.
Background task active
– A lengthy background task such as a system update is in
progress.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
12
Page 13

Move the mouse cursor over the LED to display more information on the device, or click on it to
display the status in more detail.
Right above the status bar is the action bar. To the left are the Advanced Control and Setup Wizard
buttons. To the right is the Apply button. Use this to save any changes in the current menu page.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
13
Page 14
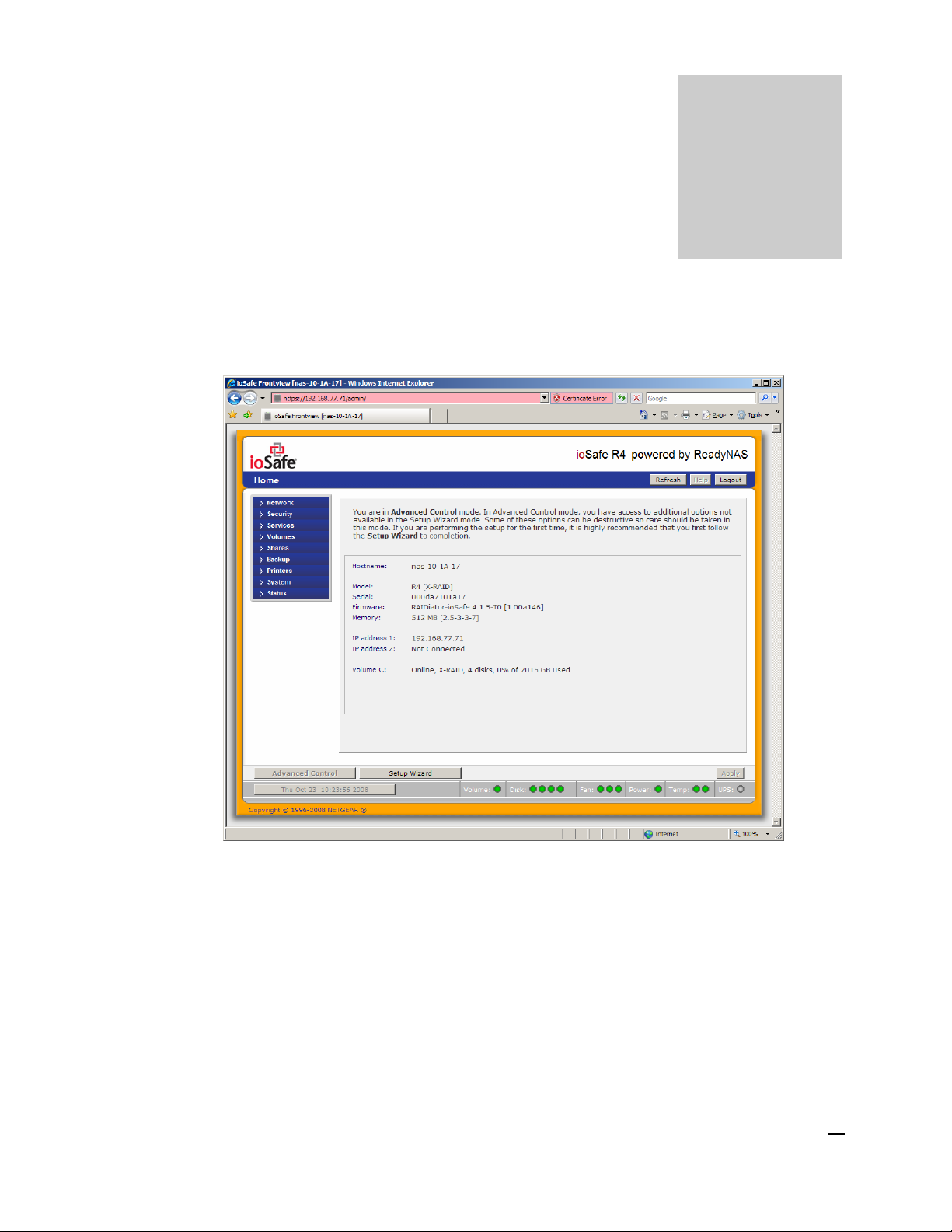
Network
Ethernet
The Ethernet tab allows you to specify network interface-specific settings.
In the
Standard Setting
and MTU settings. In most networks where a DHCP server is enabled, you can simply specify the
“Use values from a DHCP server” option to automatically set the IP address and network mask.
box, you can specify the IP address, network mask, speed/duplex mode,
If you assign a static IP address, be aware that the browser will lose connection to the ioSafe R4
device after the IP address has been changed. You can click Rescan in RAIDar to locate the device
and reconnect from there.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
14
Page 15
Note
If you elect to assign the IP address using DHCP, it is advisable to set the
lease time on the DHCP server/router to a value of at least a day.
Otherwise, you may notice that the ioSafe R4 IP address may change even
when it has been powered down for only a few minutes. Most DHCP
servers allow you to assign a static IP address for specified MAC addresses.
If you have this option, this would be a good way to ensure your ioSafe R4
maintains the same IP address even in DHCP mode.
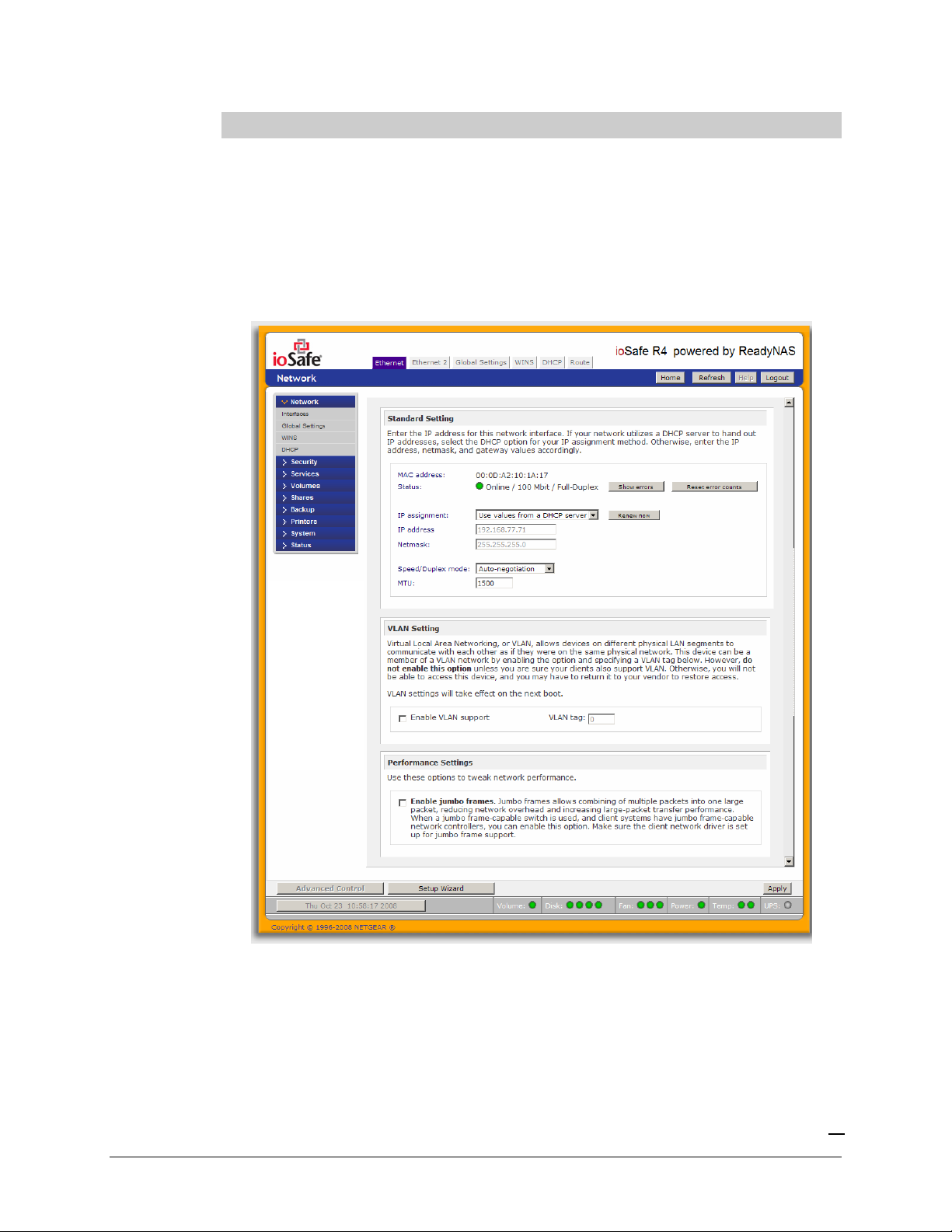
►
SPEED/DUPLEX MODE
If you have a managed switch that works best if the devices are forced to a particular speed or
duplex mode, you can select the desired setting. It’s advisable to keep the setting in auto-negotiation
mode otherwise.
►
MTU
In some network environments, changing the default MTU value may fix throughput problems. It’s
advisable to leave the default setting otherwise.
►
VLAN SETTING
Virtual Local Area Network, or VLAN, allows devices residing on different segments of a LAN to
appear in the same segment, or conversely allows devices on the same switch to behave as though
they belong to a different LAN.
If you wish to use the ioSafe R4 in a VLAN environment, select the
Enable VLAN support
checkbox and input a numeric VLAN tag. You will need to reboot the ioSafe R4 for the VLAN
function to take effect.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
15
Page 16
Warning
Do not enable VLAN support unless you are sure your clients also support
VLAN. Otherwise, you can lose network access to the ioSafe R4 and you
may need to perform a firmware re-installation to disable the VLAN setting.
►
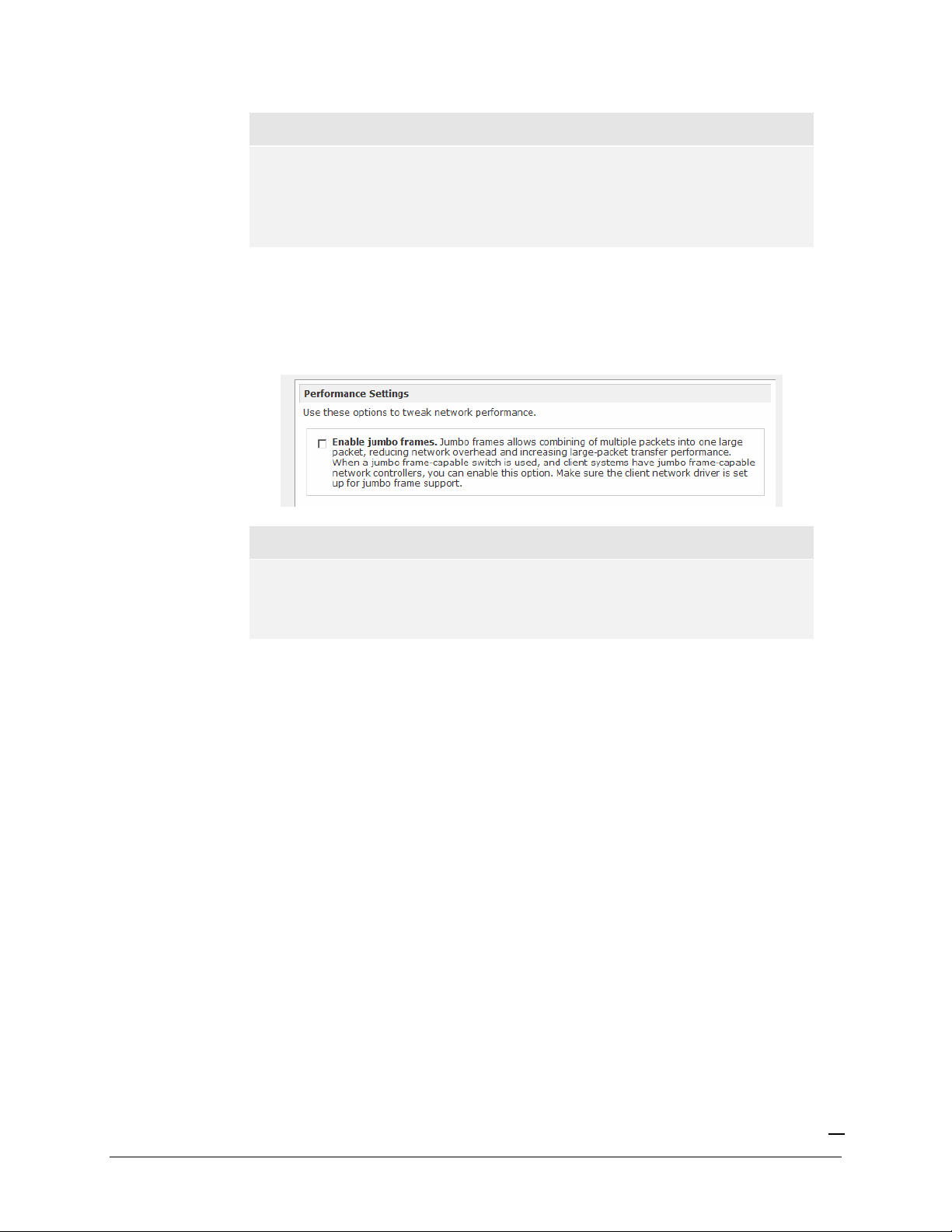
PERFORMANCE SETTING
The
Enable jumbo frames
option allows you to optimize the ioSafe R4 for large data transfers
such as multiple streams of video playback. Select this option if your NIC and your gigabit switch
support jumbo frames.
Note
The ioSafe R4 supports a 7936 byte frame size, so for optimal performance,
a switch capable of this frame size or larger should also be used.
Your ioSafe R4 device comes with multiple Ethernet interfaces, you will see a separate configuration
tab for each interface.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
16
Page 17
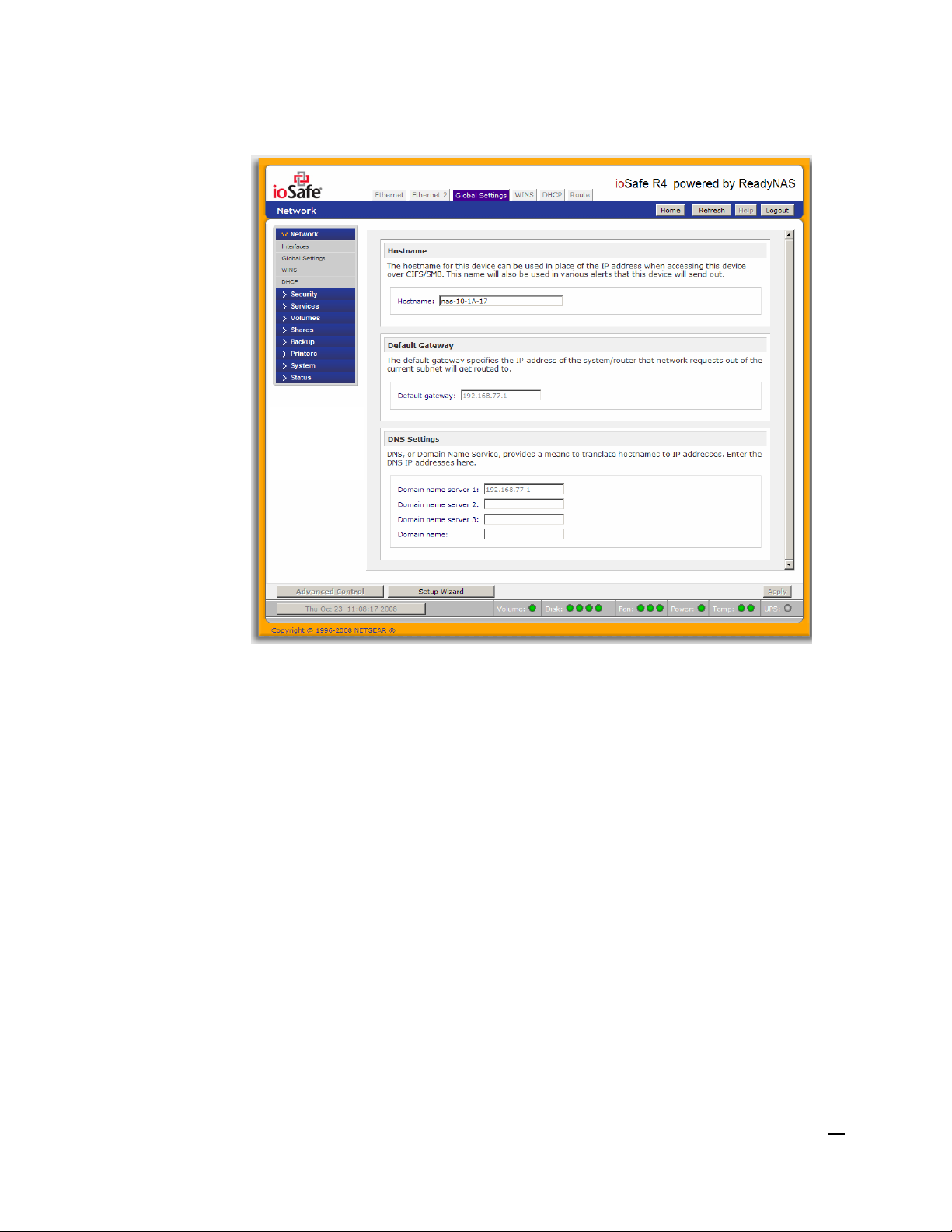
Global Network Settings
►
HOSTNAME
The Hostname you specify is used to advertise the ioSafe R4 on your network. You can use the
hostname to address the ioSafe R4 in place of the IP address when accessing the ioSafe R4 from
Windows, or over OS X using SMB. This is also the name that will appear in the RAIDar scan list.
The default hostname is
►
DEFAULT GATEWAY
nas-
followed by the last three bytes of your primary MAC address.
The Default Gateway specifies the IP address of the system where your network traffic is routed to
if the destination is outside of your subnet. In most homes and smaller offices, this is the IP address
of the router connected to the cable modem or your DSL service.
If you had selected the DHCP option in the Ethernet tab, the Default Gateway field will be
automatically populated with the setting from your DHCP server. If you had selected the Static
option, you can manually specify the IP addresses of the default gateway server here.
►
DNS
The DNS box allows you to specify up to three Domain Name Service servers for host name
resolution. If you are unfamiliar with DNS, the service translates host names into IP addresses.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
17
Page 18
If you had selected the DHCP option in the Ethernet tab, the domain name server fields will be
automatically populated with the DNS settings from your DHCP server. If you had selected the
Static option, you can manually specify the IP addresses of the DNS servers and the domain name
here.
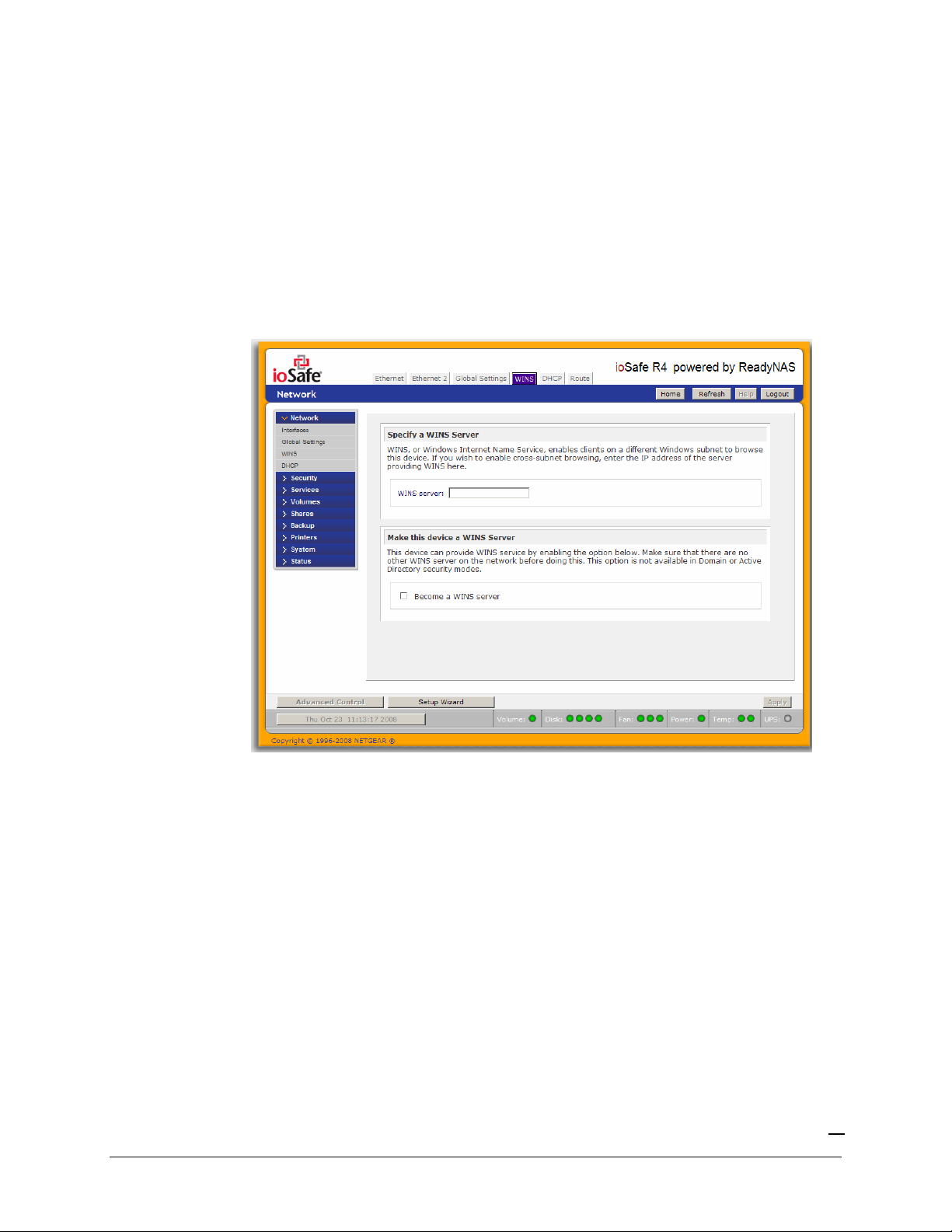
WINS
The WINS option allows you to specify the IP address of the WINS (Windows Internet Naming
Service) server. A WINS server is typically a Windows server on the network that will allow the
ioSafe R4 or other devices on the network to be (Windows) browsed from other subnets.
If you do not have an existing WINS server, you can designate the ioSafe R4 to be one. Simply
select the
Become a WINS server
checkbox and configure your Windows PC to specify the ioSafe
R4 IP address as the WINS server. This can be useful if you wish to browse by hostname across
multiple subnets, i.e. over VPN.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
18
Page 19
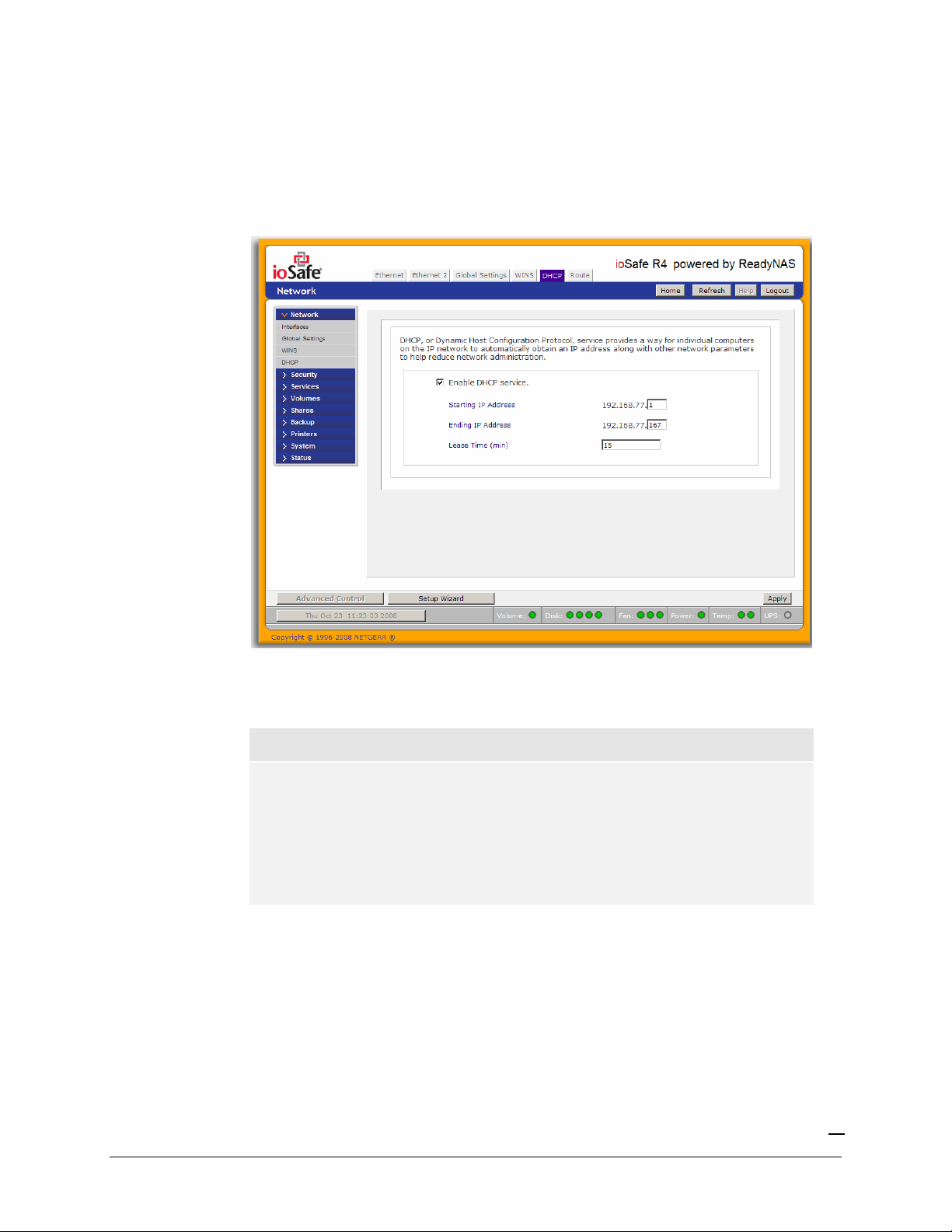
DHCP
The DHCP tab allows this device to act as a DHCP (Dynamic Host Configuration Protocol) server.
DHCP service simplifies management of a network by dynamically assigning IP addresses to new
clients on the network.
Click on the
Enable DHCP service
checkbox if you want the ioSafe R4 device to act as a DHCP
server. This is convenient in networks where DHCP service is not already available.
Note
These options are available only if this device is not already using a DHCP
address. Enabling DHCP service on a network already utilizing another
DHCP server will result in conflicts. If you wish to use this device as a
DHCP server, make sure to specify static addresses in the Ethernet and
DNS tabs.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
19
Page 20
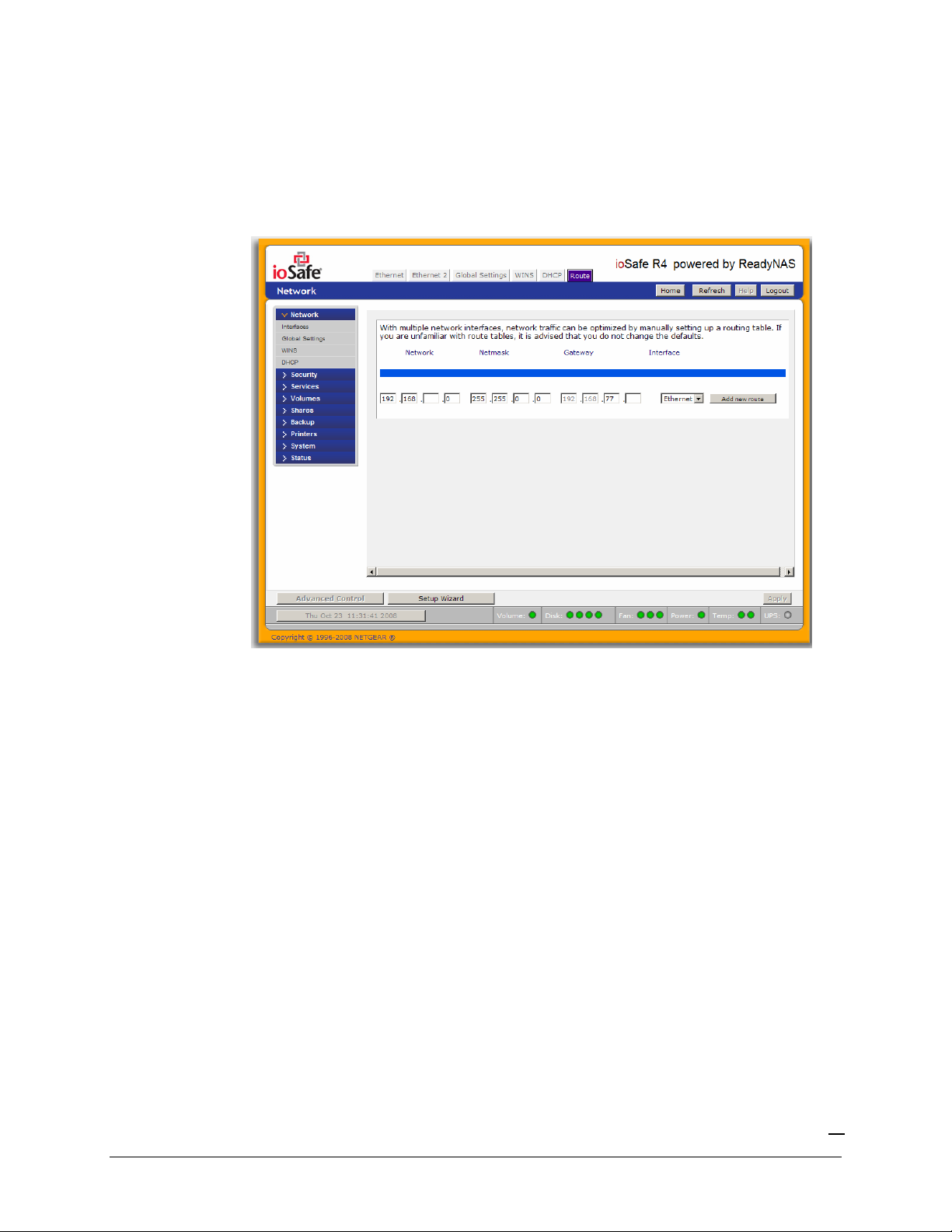
Route
The
Route
tab is available if you have two or more network interfaces (Ethernet or Wireless
combined) on your ioSafe R4. In some environments, you can optimize your network traffic by
manually setting up a routing table.
Route table management is beyond the scope of this manual, and this option is provided only for
advanced users who understand routing and wish to deviate from the default routes.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
20
Page 21
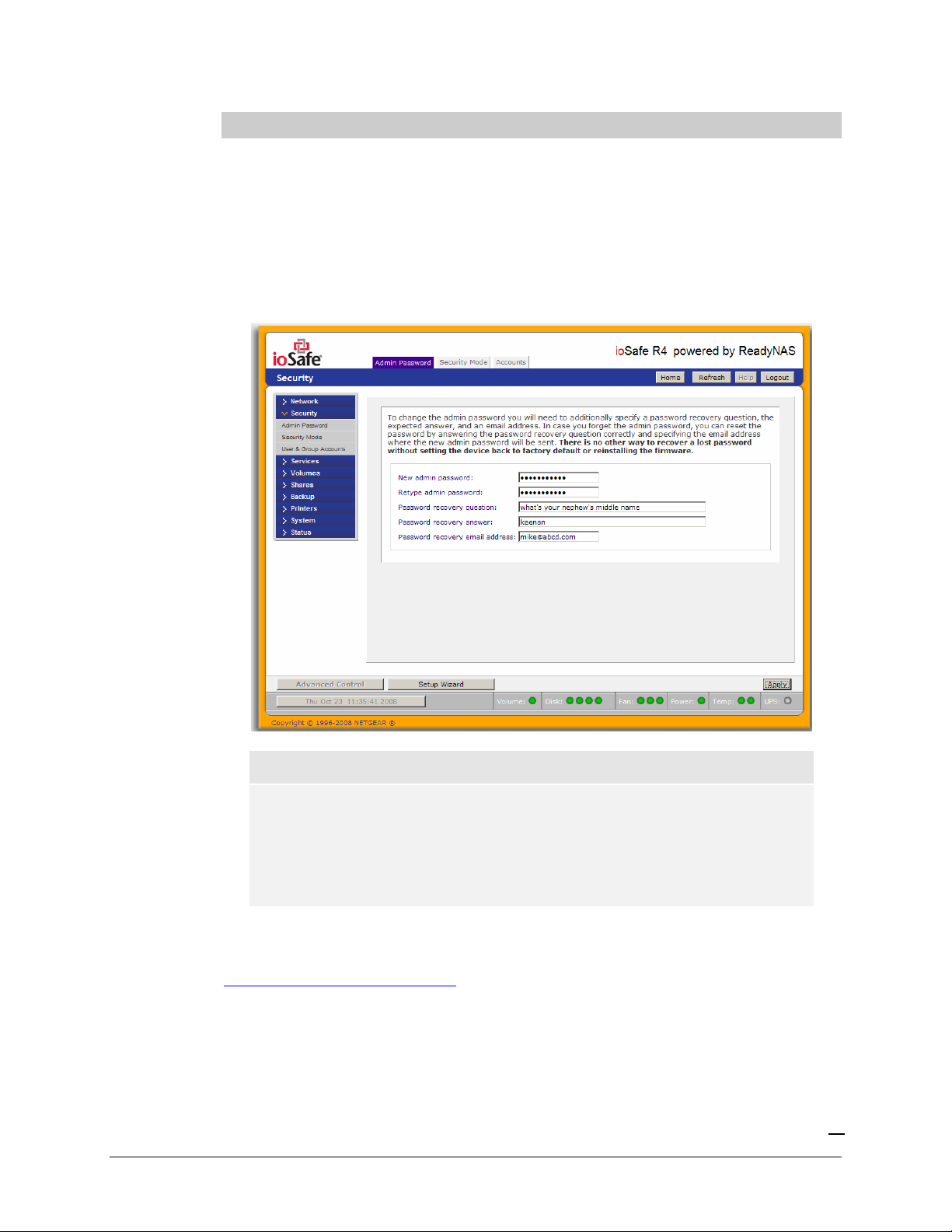
Security
Admin Password
The
Admin Password
only user that can access FrontView and this user has administrative privileges when accessing
shares. Be sure to set a password different from the default password and make sure this password is
kept in a safe place. Anyone who obtains this password can effectively change or erase the data on
the ioSafe R4. The default
tab allows you to change the
admin
user password is “iosafe1” .
admin
user password. The
admin
user is the
Note
In User or Domain security mode, you can use the admin account to login
to a Windows share, and perform maintenance on any file or folder in that
share. The admin user also has permission to access all user private home
shares to perform backups.
As a safeguard, you will be requested to enter a password recovery question, the expected answer,
and an email address. If, in the future, you forget the password, you can go to
https://
ip_address
/password_recovery. Successfully answering the questions there will reset the
admin password, and that new password will be sent to the email address you enter in this tab.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
21
Page 22
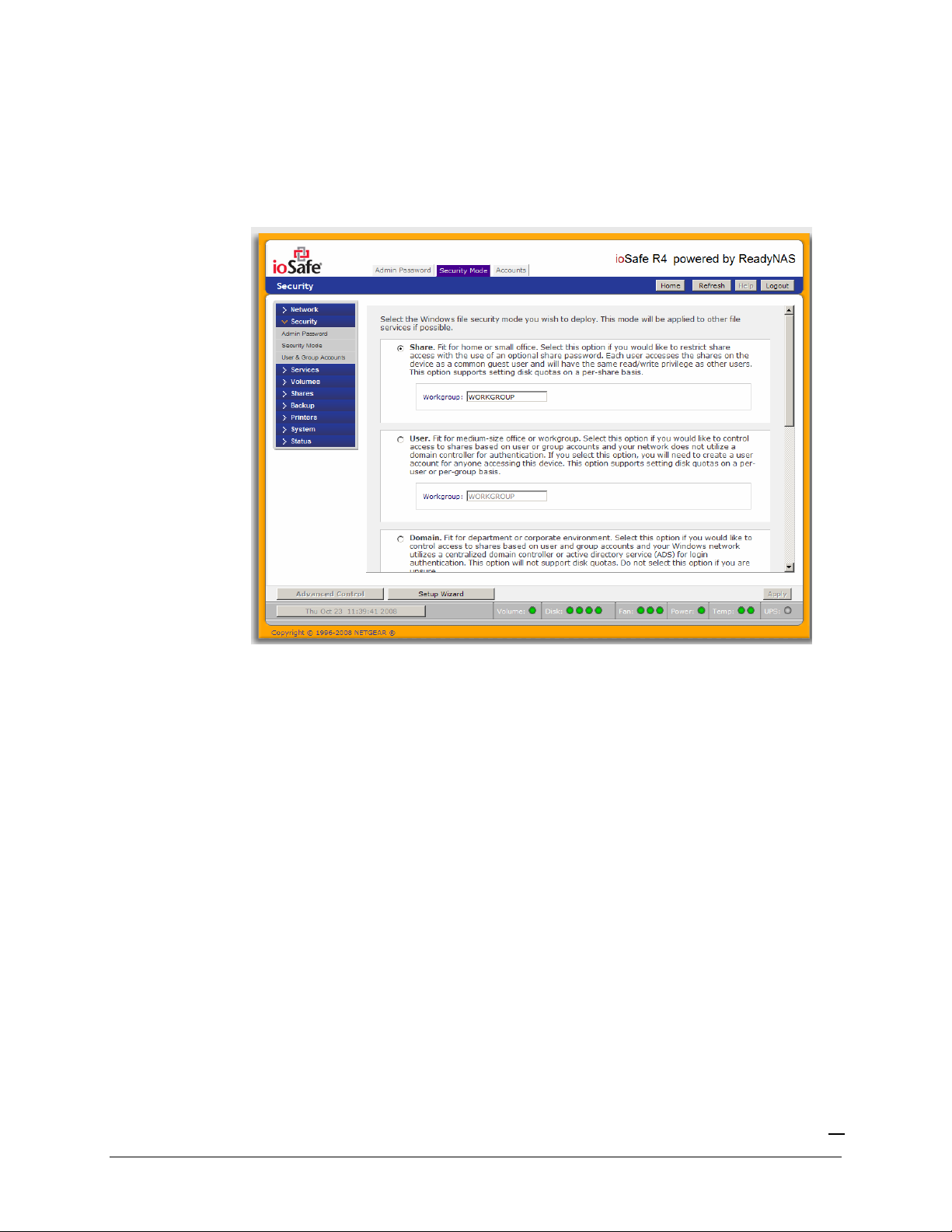
Security Mode Selection
The ioSafe R4 device offers three security options for your network environment. Read the quick
overview below to help select the most appropriate option based on the required level of security
and your current network authentication scheme.
The Share security mode is suitable for most home and small office environments, providing a
simple way for people in a trusted environment to share files without the necessity of setting up
separate user and group accounts. Shares that you create in this environment can be passwordprotected if desired.
A more appropriate selection for the medium-size office or workgroup environment is the User
security mode. This mode allows you to set up user and group accounts to allow for more specific
share access restrictions. Access to shares requires proper login authentication, and you can specify
which users and/or groups you wish to offer access. As an example, you may want to restrict
company financial data to just users belonging to one particular group. In this security mode, the
administrator will need to set up and maintain user and group accounts on the ioSafe R4 device
itself. In addition, each user account will be automatically set up with a private home share on the
ioSafe R4.
The Domain security mode is most appropriate for larger department or corporate environments,
where a centralized Windows-based domain controller or active directory server is present. The
ioSafe R4 device integrates in this environment by creating a trusted relationship with the
domain/ADS authentication server and allowing all user authentications to occur there, eliminating
the need for separate account administration on the device itself. Also, in this security mode, each
domain/ADS user will be automatically set up with a private home share on the ioSafe R4.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
22
Page 23
Note
The FrontView management system will slow down in proportion to the
number of users in the domain. It is not advisable to use the ioSafe R4 in a
domain environment with more than 1000 users.
Share Security Mode
The
Share security mode
►
SPECIFY A WORKGROUP
You only need to specify a workgroup if you wish to change it from the default.
A valid workgroup name must conform to the following restrictions:
is the easiest security option to set up.
Name must consist of characters a-z, A-Z, 0-9, and the symbols _ (underscore), – (dash),
and . (period).
Name must start with a letter.
Name length must be 15 characters or less.
►
SHARE ACCOUNTS
You will notice the Accounts tab which consists of share accounts which match the current share
names on the ioSafe R4. These share accounts are listed to allow you the option of changing the
UID and quota assigned to the share. The share quota can be changed from the Share Listing in the
Share menu as well. The UID does not need to be changed unless you wish to avoid a UID conflict
with an existing NFS user.
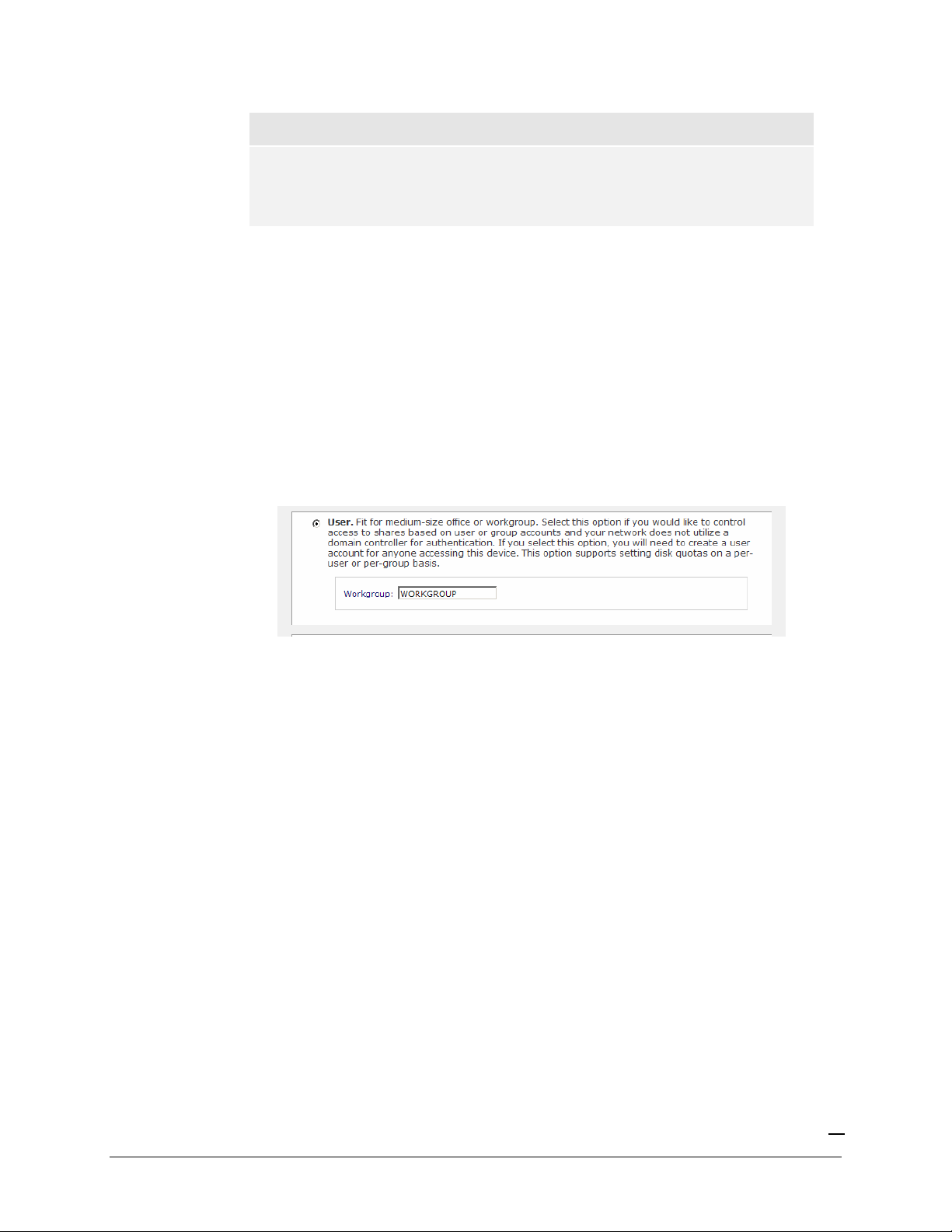
User Security Mode
In User security mode, you specify a workgroup name just as you would in the previous security
option, and create user and group accounts. You will have control over how much disk space is
allocated for each user or group.
In this security mode, each user will be given a home share on the ioSafe R4 device that the user can
use to keep private data such as backups of the user’s PC. This home share is accessible only by that
user and the administrator who needs the privilege to perform backups of these private shares. The
option to automatically generate the private home share is controlled in the Accounts/Preferences
tab, and you can disable it if you wish.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
23
Page 24
Note
Private user shares are only accessible by users using CIFS (Windows) or
AppleTalk file protocols.
To set up the ioSafe R4 for this security mode, you will need the following information:
Workgroup name
Group names you wish to create (i.e. Marketing, Sales, Engineering)
User names you wish to create (plus email addresses if you will be setting disk quotas)
Amount of disk space you would like to allocate to users and groups (optional)
►
SPECIFY A WORKGROUP
To change or set a workgroup name, enter the desired name in the Workgroup field in the User
option box. The name can be the workgroup name that is already used on your Windows network.
►
SETTING UP ACCOUNTS
In this security mode, the Accounts tab allows you to manage user and group accounts on the ioSafe
R4. A good starting point would be to select the
Manage groups
option from the drop-down box
in the upper right corner.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
24
Page 25
►
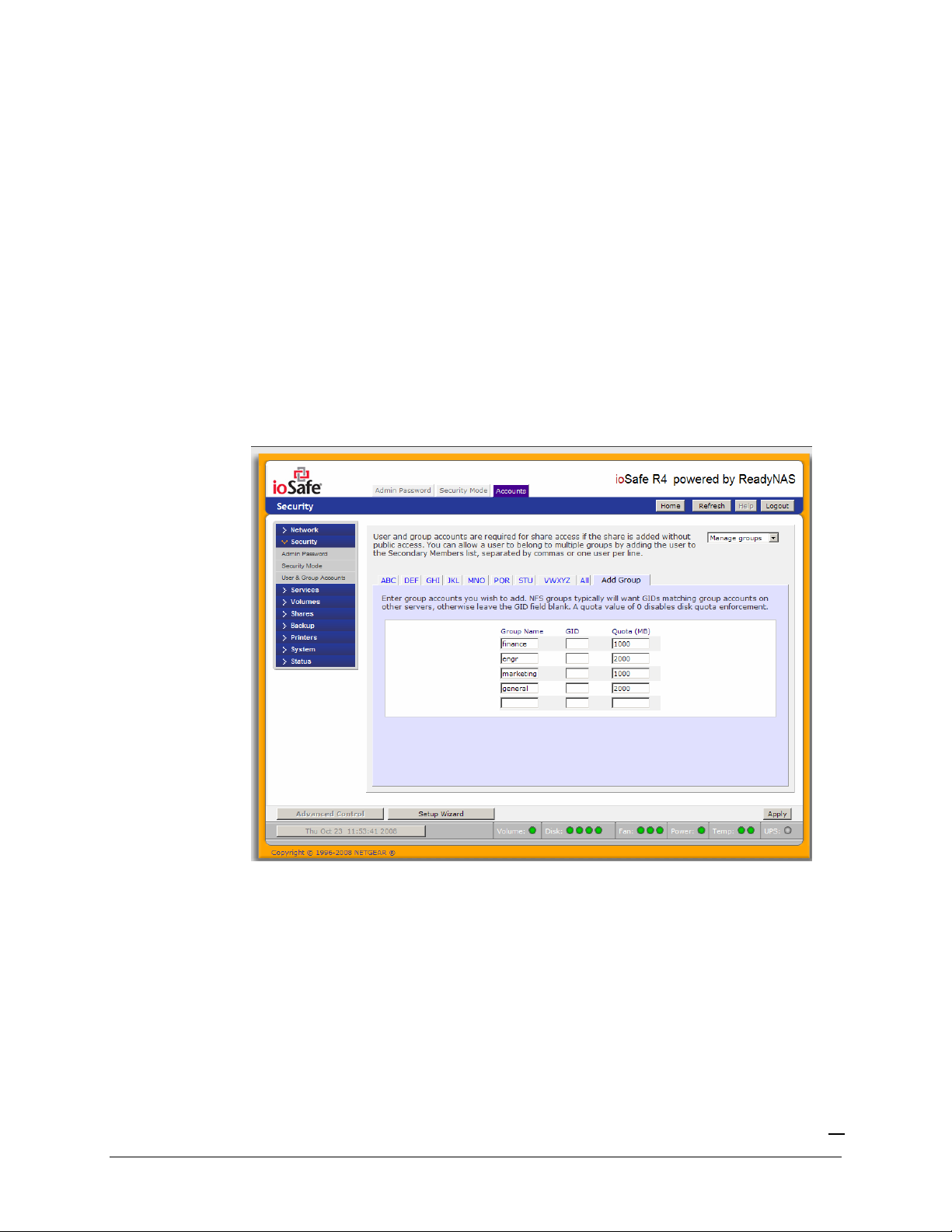
MANAGING GROUPS
To add a new group, click on the Add Group tab if it is not already selected. You can add up to five
groups at a time. If you expect to have just one big set of users for one group, you can forego
adding a new group and accept the default
users
group.
If desired, a user can belong to multiple groups. Once you have created user accounts, you can
specify secondary groups that the user can belong to. This allows for finer-grain settings for share
access. For instance, you can have user
can access shares restricted to only
joe
in group
marketing
and
marketing
sales
groups.
also belong to group
sales
so
joe
While adding a new group, you can specify the amount of disk space you wish to allocate that group
by setting a disk quota. A value of 0 denotes no limit. You can set or change the quota at a later
time. You can also set the Group ID, or GID, of the group that you are adding. You can leave this
field blank and let the system automatically assign this value unless you wish to match your GID to
your NFS clients.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
25
Page 26
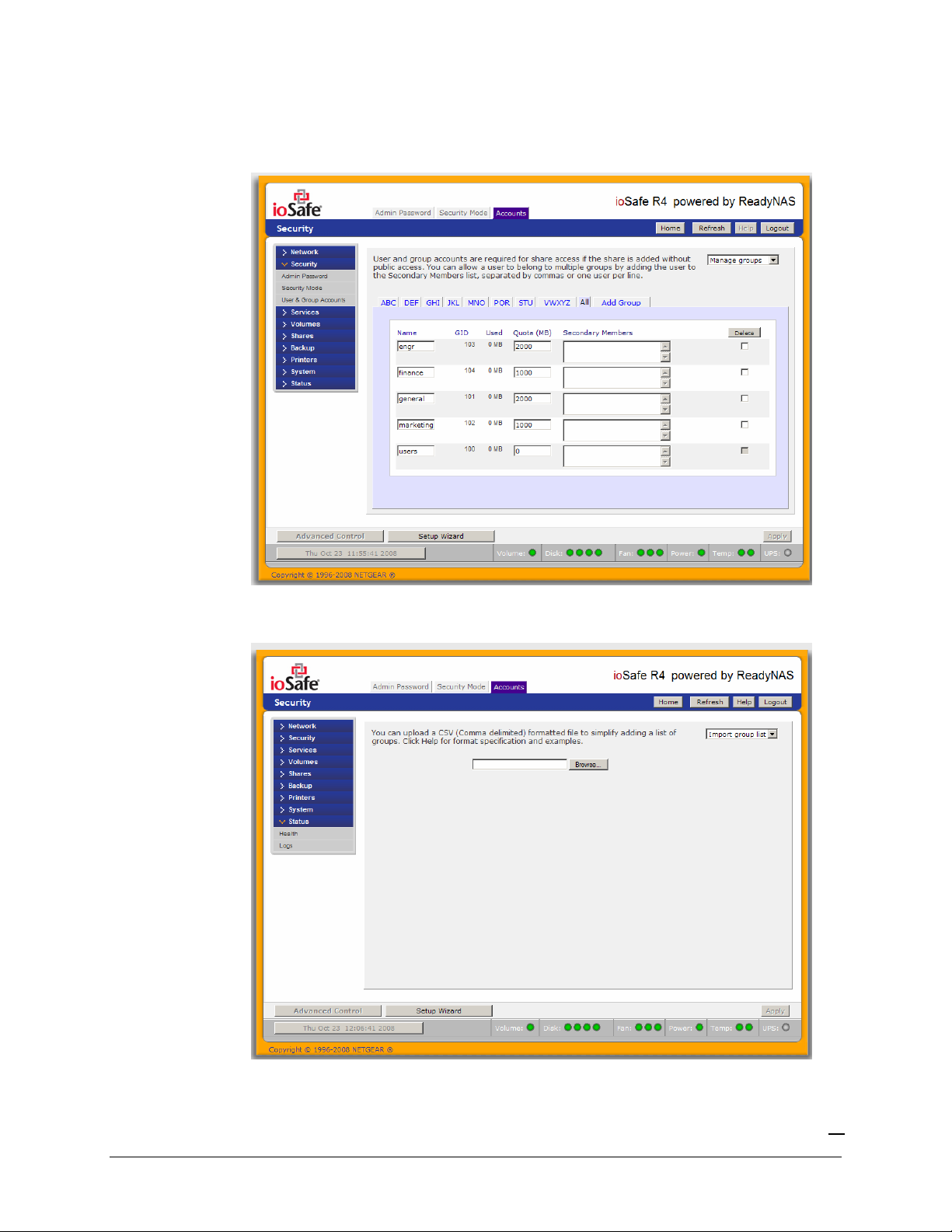
After adding your groups, you can view or change your groups by clicking on the alphabetical index
tab, or
All
to list all groups.
If you wish to add a large number of groups, select
Import group list
from the selection box.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
26
Page 27

Here, you can upload a CSV (Comma Separated Value) formatted file containing the group account
information. The format of the file is:
name1,gid1,quota1,member11:member12:member13
name2,gid2,quota2,member21:member22:member23
name3,gid3,quota3,member31:member32:member33
Please note the following:
Spaces around commas are ignored.
The name fields are required.
Quota will be set to default if not specified.
GID will be automatically generated if not specified.
Empty fields are replaced with accounts defaults.
Group members are optional.
Examples of acceptable formats are as follows (note that you can omit follow-on commas and fields
if you wish to accept the system defaults for those fields, or you can leave the fields empty):
flintstones
In this example, group
flintstones
will be created with an automatically assigned GID, and default
quota.
rubble,1007,5000,barney:betty
In this example, group
betty
.
rubble
will have GID 1007, quota of 5000 MB, with members
barney
and
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
27
Page 28

►
MANAGING USERS
To manage user accounts, select the Manage users option in the drop-down box.
To add a user, click on the Add User tab. You can add up to five users at a time.
You can enter a user name, email address, user ID, select a group, password, and disk quota for the
user. Only the user name and password fields are required, however, you should specify the user
email address if you intend to set up disk quotas. Without an email address, the user will not be
warned when disk usage approaches the specified disk quota limit. If you do not wish to assign a
disk quota, enter 0.
If you wish to add a large number of users, select
Import user list
from the selection box.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
28
Page 29
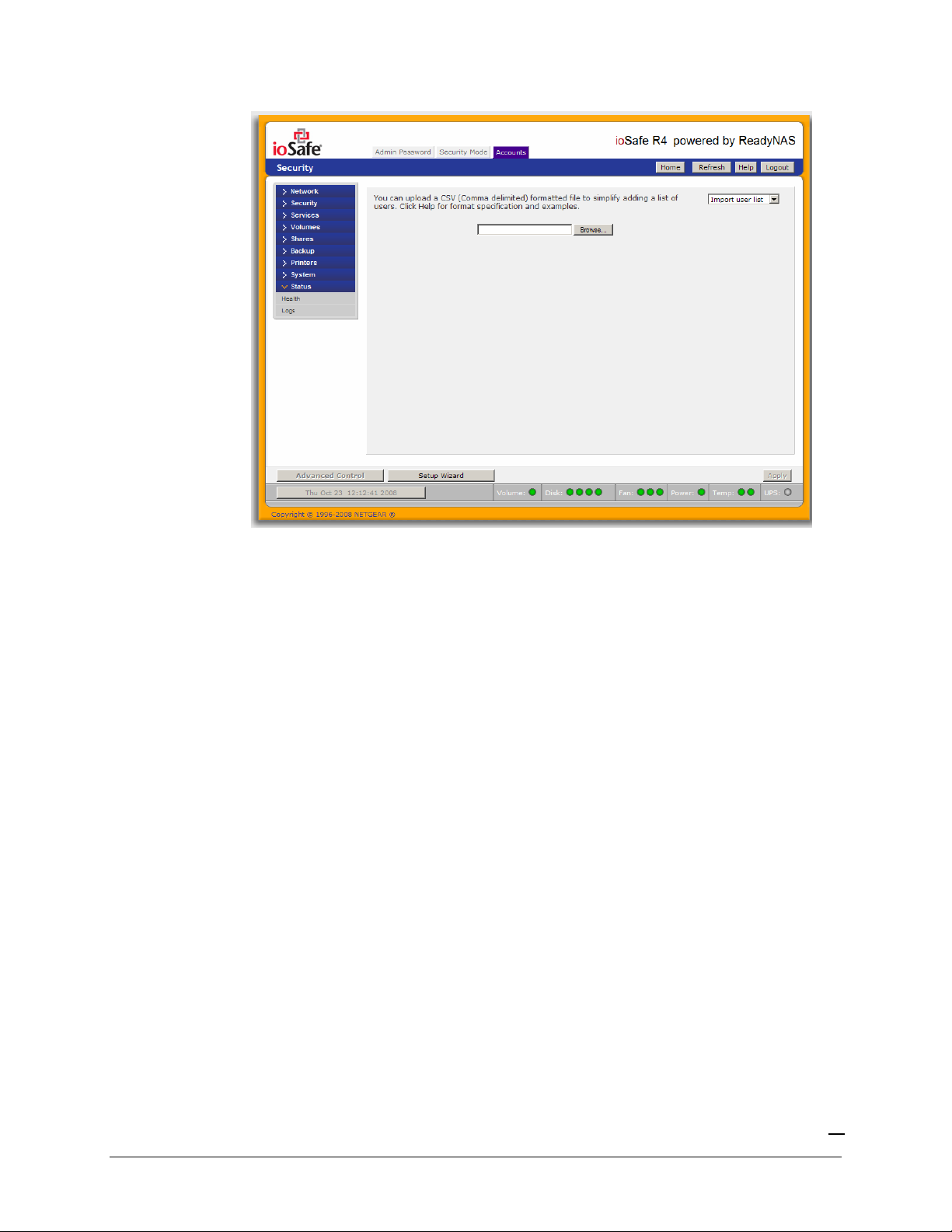
Here, you can upload a CSV (Comma Separated Value) formatted file containing the user account
information. The format of the file is:
name1,password1,group1,email1,uid1,quota1
name2,password2,group2,email2,uid2,quota2
name3,password3,group3,email3,uid3,quota3
Please note the following:
Spaces around commas are ignored.
The name and password fields are required.
If a listed group account does not exist, it will be automatically created.
Group and quota will be set to the defaults if not specified.
Email notification will not be sent to the user if the field is ommitted or left blank.
UID will be automatically generated if not specified.
Empty fields are replaced with accounts defaults.
Examples of acceptable formats are as follows (note that you can ommit follow-on commas and
fields if you wish to accept the system defaults for those fields, or you can leave the fields empty):
fred,hello123
In this example, user
fred
will have password set to
hello123
notification, automatic UID assigned, and default quota.
barney,23stone,,barney@bedrock.com
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
, belongs to the default group, no email
29
Page 30
In this example, user
sent email notification to
wilma,imhiswif,ourgroup,wilma@bedrock.com,225,50
barney
will have password set to
barney@bedrock.com
23stone
, automatic UID assigned, and default quota.
, belongs to the default group, will be
In this example, user
sent to
wilma@bedrock.com
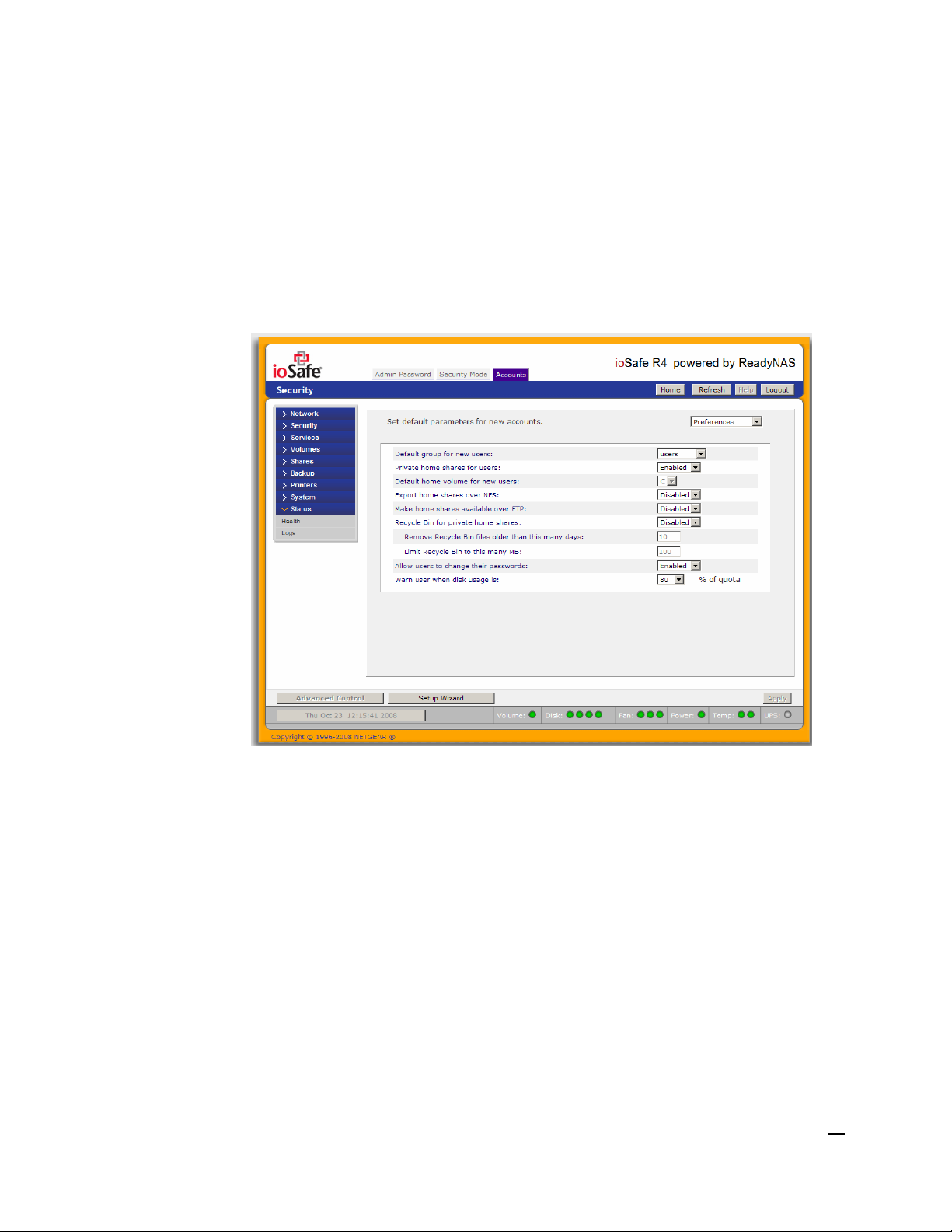
►
SETTING ACCOUNTS PREFERENCES
wilma
will have password
, UID set to
imhiswif
225
, and quota set to
, belongs to group
50MB
.
ourgroup
, email notification
You can set various account defaults by selecting the Preferences option in the drop-down box.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
30
Page 31

Domain Security Mode
►
DOMAIN/ADS AUTHENTICATION
If you choose the Domain security mode option, you will need to create a trusted relationship with
the domain controller or the active directory server (ADS) that will act as the authentication server
for the ioSafe R4 device. You will need the following information:
Domain name
Domain administrator login
Domain administrator password
If using ADS:
- DNS name of the ADS realm
- OU (Organization Unit). You can specify nested OU's by separating OU entries with
commas. The lowest level OU must be specified first.
You can elect to have the ioSafe R4 automatically auto-detect the domain controller, or you can
specify the IP address. Sometimes auto-detect will fail, and you will need to supply the IP address of
the domain controller to join the domain.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
31
Page 32

If you have a large number of users in your domain, you may need to deselect the
from trusted domains
… checkbox. Otherwise, FrontView management system may slow down
Display users
to an unusable state.
Note
Use of the ioSafe R4 in a domain environment with more than 1000 users is
not recommended at this time.
Click Apply to join the domain. If successful, users and groups from the domain will have login
access to the shares on this device.
►
SETTING UP ACCOUNTS
Accounts are managed on the domain controller. The ioSafe R4 simply pulls the account
information from the controller and displays them in the Accounts tab if you have the
users from trusted domains…
option enabled.
Display
If you wish, you can assign a disk quota to the domain users and groups. If email addresses are
specified, users will be automatically notified when approaching and reaching their quotas.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
32
Page 33

Services
The Services menu allows you to manage various services for share access. This in effect controls
the type of clients you wish to allow access to the ioSafe R4.
You will notice three tabs at the top:
Discovery Services
. These different services are explained below.
Standard File Protocols, Streaming Services
, and
Standard File Protocols
The standard file protocols are common file sharing services that allow your workstation clients file
transfer to and from the ioSafe R4 using built-in file manager over network file protocols on the
client operating system. The available services are:
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
33
Page 34

CIFS
(Common Internet File Service). Sometimes referred to as SMB. This protocol is
used mainly by Microsoft Windows clients, and sometimes used by Mac OS X clients.
Under Windows, when you click on My Network Places or Network Neighborhood,
you’re going across CIFS. This service is enabled by default and cannot be disabled.
NFS
(Network File Service.) NFS is used by Linux and Unix clients. Mac OS 9/X users
can access NFS shares as well through console shell access. The ioSafe R4 supports NFS
v3 over UDP and TCP.
AFP
(Apple File Protocol). Mac OS 9 and OS X works best using this protocol as it
handles an extensive character set. The ioSafe R4 supports AFP 3.1.
FTP
(File Transfer Protocol). Widely used in public file upload and download sites. The
ioSafe R4 supports anonymous or user access for FTP clients, regardless of the security
mode selected. If you wish, you can elect to set up port-forwarding to non-standard ports
for better security when accessing files over the Internet.
HTTP
(Hypertext Transfer Protocol). Used by web browsers. The ioSafe R4 supports
HTTP file manager, allowing web browsers to read and write to shares using the web
browser. This service can be disabled in lieu of HTTPS to allow for a more secure
transmission of passwords and data. With the option to redirect default web access to a
specified share, you can transparently force access to http://
http://
iosafe_ip/share
. This is useful if you do not want to expose your share listing to
iosafe_ip
outsiders as well as allowing you to redirect all default web access to a share dedicated to be
your website. All you need in the target share is an index file such as
index.html
. You have the option of enabling or disabling login authentication to this
index.htm
share.
HTTPS
(HTTP with SSL encryption). This service is enabled by default and cannot be
disabled. Access to FrontView is strictly through HTTPS for this reason. If you want
remote web access to FrontView or your HTTPS shares, you have the option of specifying
a non-standard port that you can forward on your router for better security. You can also
regenerate the SSL key based on the hostname or IP address that users will address the
ioSafe R4. This allows you to bypass the default dummy certificate warnings whenever you
access the ioSafe R4 over HTTPS.
to
or
Rsync
. An extremely popular and efficient form of incremental backup made popular in
the Linux platform but is now available for various other Unix systems as well as Windows
and Mac. Enabling rsync service on the ioSafe R4 will allow clients to use rsync to initiate
backups to and from the ioSafe R4.
Streaming Services
The built-in streaming services on the ioSafe R4 allow you to stream multi-media content directly
from the ioSafe R4, without the need to have your PC or Mac powered on.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
34
Page 35

SquezeCenter
(SlimServer) provides music streaming to the popular Squeezebox music
players from Slim Devices.
iTunes Streaming Server
enables iTunes clients to stream media files straight from the
ioSafe R4.
UPnP AV
provides media streaming service to stand-alone networked home media
adapters and networked DVD players that support the UPnP AV protocol or are Digital
Living Network Alliance (DLNA) standard compliant. The ioSafe R4 comes with a
reserved
media
share that is advertised and recognized by the players. Simply copy your
media files to the Videos, Music, and Pictures folders in that share to display them on your
player. If you wish, you can specify a different media path where your files reside.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
35
Page 36

Home Media Streaming Server
provides streaming of videos, music, and pictures to
popular networked DVD players. The streaming players often utilize the streaming client
developed by Syabas. Similar to UPnP AV, this service is used to stream videos, music,
and pictures from the reserved
media
share to these adapters. If you wish to change the
location where the media files are stored, you can specify a different share and folder path.
Note that this path is shared between the UPnP AV and this service.
Discovery Services
Bonjour Service
provides a simple way of discovering various services on the ioSafe R4.
Bonjour currently provides an easy way to connect to FrontView, IPP Printing, and AFP
services. OS X has built-in Bonjour support and you can download Bonjour for Windows
from Apple’s website.
UPnP
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
provides a means for UPnP-enabled clients to discover the ioSafe R4 on your LAN.
36
Page 37

Volumes
Volume Management
The ioSafe R4 consists of two RAID volume technologies –
standard RAID levels 0, 1, and 5, and
technology. Your system defaults to
through a factory default reset process described in
X-RAID
X-RAID
, NETGEAR-patented expandable RAID
, however, you can switch between the two modes
Chapter 4 – System Reset Switch
Flex-RAID
, utilizing the industry-
There are advantages to both technologies.
►
ADVANTAGES OF FLEX-RAID
1. The default volume can be deleted and recreated, with or without the snapshot
reserved space.
2.
Hot spare disk is supported.
3. Full volume management is available – you can create a volume utilizing RAID level 0,
1, or 5, specify the size of the volume, delete a disk from a volume, assign a hot spare,
etc.
4. Multiple volumes are supported, each with a different RAID level, snapshot schedule
and disk quota definition.
5. Each disk can be replaced, one by one, then rebuilt; after the last disk is replaced,
another data volume utilizing the newly added capacity can be configured.
.
►
ADVANTAGES OF X-RAID
1. One volume technology, but supports volume expansion, either by adding more disks
or by replacing existing disk with larger capacity disks.
2. You can start out with one disk, and add up to 3 more disks when you need them or
can afford them.
Volume management is automatic. Add a 2nd disk; it becomes a mirror to the 1st. Add
3.
a 3rd, your capacity doubles; add a 4th, and your capacity triples – the expansion
occurring while maintaining redundancy.
4.
At a future point in time, each disk can be replaced one by one, have it finish
rebuilding, and after the last disk is replaced, your volume automatically expands
utilizing the new capacity.
Volume Management for Flex-RAID
If you wish to reconfigure the default volume C, wish to split it into multiple volumes, or specify a
different RAID level, you will need to reconfigure your volume. The first step is to delete the
existing volume you wish to replace.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
37
Page 38

►
DELETING A VOLUME
To delete a volume, click on the volume tab of the volume you wish to delete or Volume C if only
one volume is configured. Make sure if you have data in that volume that you back up the files you
wish to keep first. All shares, files, and snapshots residing on that volume
WILL BE DELETED
AND ARE NON-RECOVERABLE!
Click
Delete Volume
You will be asked to confirm your intention by typing:
in the Volume C tab.
DELETE VOLUME
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
38
Page 39

►
ADDING A VOLUME
You will then be presented with the
Add Volume
tab listing the available configurable space on the
hard disks. All the disks will be selected by default. You can elect to specify a hot spare disk if you
wish. A hot spare remains in standby mode and will automatically regenerate the data from a failed
disk from the volume. A hot spare disk is only available for RAID level 1 and RAID level 5 if there
are enough disks to fulfill the required minimum plus one.
Select Hard Disks
In our example here, we’ll select the first three disks and elect not to specify any of them as a hot
spare.
Select RAID level
RAID level determines how the redundancy, capacity utilization, and performance is implemented
for the volume. See Appendix A, “RAID Levels Simplified”, for more information. Typically in a
three or more disk configuration, RAID level 5 is recommended.
In our example above, we selected RAID level 5 for the three selected disks.
Specify reserve space for snapshot
Next, select the amount of the volume you wish to allocate for snapshots. You can elect to specify 0
if you wish to disable snapshot capability, or you can specify a 5GB increment from 5 to 100GB.
This represents the amount of data you feel would be changing while the snapshot is active. This
typically depends on how often you schedule your snapshot (see following section on snapshot), and
the maximum amount of data (plus padding) you feel will change during that time. Make sure to
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
39
Page 40

allocate enough space for worse case as the snapshot becomes unusable when its reserved space
runs out.
In our example above, we selected 50GB of the volume to be reserved for snapshots.
Specify desired volume size
After you’ve specified the above volume parameters, enter the desired volume size if you wish to
configure a smaller volume size than the maximum displayed. The resulting volume will be
approximately the size that is specified.
In our example above, we kept the maximum size that was calculated.
Click
Apply
and wait for the instruction to reboot the system. It typically takes about 1 minute
before you are notified to reboot.
After rebooting, you will then be notified by email when the volume has been added. Use RAIDar
to reconnect to the NAS device.
►
RAID SETTINGS
After you have added a volume, you can revisit the Volume tab and click on the
RAID Settings
tab
to display the current RAID information and configuration options for the volume.
Notice the disk on channel 4 that we did not configure is listed in the Available Disks section. We
can add this disk as a hot spare by clicking on the
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
Make hot spare
button.
40
Page 41

We can also remove a disk from the volume by clicking on the
Remove
button. The volume will
still be available but in a non-redundant state. An additional disk failure would render this volume
unusable.
Warning
The Remove operation is a maintenance feature and is not recommended in
a live environment. Its function is equivalent to hot-removing the disk or
simulating a disk failure.
The
Locate
Clicking on
option is a way to verify that a disk is correctly situated in the expected disk slot.
Locate
will blink the LED of the disk for 15 seconds.
Volume Management for X-RAID
The X-RAID technology offers a simplified approach to volume management. X-RAID works on
the premise that what most people want to do with their data volume over time is either adding
redundancy or expanding it without the headaches usually associated with doing that. By using
simple rules, X-RAID is able to hide all the complexities yet provide volume management features
only previously available in enterprise-level storage solutions.
►
X-RAID REDUNDANCY OVERHEAD
To maintain redundancy from disk failure, X-RAID requires a one-disk overhead. In a two-disk XRAID volume, the usable capacity is one disk. In a three-disk X-RAID volume, the usable capacity
is two disks. In a four-disk X-RAID volume, the usable capacity is three disks.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
41
Page 42

►
X-RAID HAS ONE DATA VOLUME
X-RAID devices only have one data volume. This volume encompasses one to four disks, utilizing
the capacity of the smallest disk from each disk. For instance, if you had one 80GB disk and two
250GB disks, only 80GB from each disk will be used in the volume. (The leftover space on the
250GB disks will be reclaimed only when the 80GB disk is replaced with a 250GB or greater
capacity disk. See “Replacing All Your Disks for Even More Capacity” below.)
►
ADDING A 2ND DISK FOR REDUNDANCY
A one-disk X-RAID device has no redundancy and provides no protection from a disk failure.
However, if and when you feel the need for redundancy, simply power down the device, add a new
disk with at least the capacity of the first disk, and power on. Depending on the size of the disk,
within a few hours, your data volume will be fully redundant. The process occurs in the
background, so access to the ioSafe R4 is not interrupted.
►
ADDING A 3RD AND 4TH DISK FOR MORE CAPACITY
At a certain point, you will want more capacity. With typical RAID volumes, you will have to
backup your data to another system (with enough space), add a new disk, reformat your RAID
volume, and restore your data back to the new RAID volume.
Not so with X-RAID. Simply power down the device, add the 3rd and perhaps 4th disk and power
on. The X-RAID device will initialize and scan the newly added disk(s) for bad sectors in the
background. You can continue working normally with the device during this process without any
lag in performance. When the process finishes, you will be alerted by email to reboot the device.
During the boot process, your data volume is expanded. This process typically takes about 15-30
minutes per disk, perhaps more, depending on the size of your disks. A 250GB disk takes
approximately 30 minutes. Access to the ioSafe R4 is not permitted during this time. You will be
notified by email when the process is complete.
After you receive your email, the ioSafe R4 will have been expanded with the capacity from your
new disk(s).
►
REPLACING ALL YOUR DISKS FOR EVEN MORE CAPACITY
A couple years down the line, you find the need more disk space, and 1 TB disks are available at an
attractive price. Again, you can expand your volume capacity quite easily, although you will need to
power down several times to replace your old disks.
First, power down the ioSafe R4, replace the first disk with the larger capacity disk, and boot. The
ioSafe R4 will detect that a new disk was put in place and will resync the disk with data from the
removed disk. This process will take several hours, depending on disk capacity. The disk will be
initialized and scanned for bad sectors first before the resync is started. The total time from the start
of initialization to the end of resync can be around 5 hours or more, depending on disk capacity.
You will be notified when this resync process is complete.
Upon completion, power down, replace the 2nd disk with another larger capacity disk, and boot. The
process will be the same as the 1st disk. You will do this also for the 3rd and 4th disk.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
42
Page 43

Once you get the completion notification for the 4th disk, reboot the ioSafe R4. During boot,
volume capacity is expanded with the additional capacity from each disk. For instance, if you had
replaced four 250GB disks with four 600GB disks, the capacity of the volume will increase by
approximately 350GB x 3 (the fourth disk is reserved for parity). The expansion process will take
several hours depending on the capacity expanded, and you will be notified by email when the
process is complete. There is no access to the ioSafe R4 during this time.
Changing Between X-RAID and Flex-RAID Modes
You can switch between X-RAID and Flex-X-RAID modes. The process involves setting the
ioSafe R4 to factory default and using RAIDar to configure the volume during a 10-minute delay
window during boot. Please see
Chapter 4 – System Reset Switch
for more information.
Snapshot
The Volume page offers the ability to schedule and take snapshots. You can visualize a snapshot as
a frozen image of a volume at the time you take the snapshot. Snapshots are typically used for
backups during which time the original volume can continue to operate normally. As primary
storage becomes larger, offline backups tend to become increasingly difficult as backup time
increases beyond offline hours. Snapshots allow backups to occur without taking systems offline.
Snapshots also can be used as temporary backups as well, perhaps as a means to backup data against
viruses. As an example, if a file becomes infected with a virus on the NAS device, the uninfected file
can be restored from a prior snapshot taken before the attack.
►
TAKING AND SCHEDULING SNAPSHOT
To take or schedule a snapshot, click on the
Note
Snapshot
tab.
The ioSafe R4 ships with a snapshot reserved space of 0 GB.
In the tab, you can specify how often a snapshot should be taken. Snapshots can be scheduled in
intervals from once every 4 hours to once a week.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
43
Page 44

Specify the frequency and the days that you wish to schedule a snapshot. A start and end-time of
00:00 will take one snapshot at midnight. A start time of 00:00 and end-time of 23:00 will take
snapshots between midnight and 11pm the next day at the interval you specify. Once you save the
snapshot schedule, the time of the next snapshot will be displayed. When the next snapshot is
taken, the previous one is replaced.
If you prefer, you can manually take a snapshot – just click on
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
Take snapshot now
.
44
Page 45

You can also specify how long a snapshot should last. If you will be using snapshots for backups,
you can schedule the snapshot to last slightly longer than the expected duration of the backup.
Having an active snapshot can affect the write performance to the ioSafe R4, so deactivating it when
not needed may be advantageous in write-intensive environments.
When a snapshot is taken, snapshots of shares appear in your browse list alongside the original
shares, except the snapshot share names have
example, a snapshot taken of share
backup
–snap
appended to the original share names. For
will be available as
backup-snap
.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
45
Page 46

You can traverse a snapshot share just as you would a normal share except that the snapshot share is
read-only. If you wish, you can select a detailed listing to show the snapshot time in the description
field.
Snapshots can expire when the snapshot reserved space is filled. The snapshot mechanism keeps
track of data that has been changed from the original volume starting at the point when the snapshot
is taken. All these changes are kept in the snapshot reserved space on the volume. If you look at the
Disk space
utilization information just below the
Volume
tab, you will see how much space has
been reserved for snapshots.
After snapshot is taken, if changes on the volume exceed this reserved space, the snapshot is
invalidated and can no longer be used.
Note
Changes that occupy space in the snapshot reserved space include new file
creation, modifications, and deletions; for instance, any time you delete a
1MB file, the change caused by the deletion will use up 1MB of reserved
space.
When the snapshot does become invalidated, an email alert will be sent and the status will be
reflected in the Snapshot tab. The snapshot is no longer usable at this stage.
►
RESIZING SNAPSHOT SPACE
If you are constantly getting snapshot invalidation alerts, you may want to either increase the
frequency of the snapshot, or consider increasing the snapshot reserved space. To do this, or to
eliminate your existing snapshot space (thus increasing your usable volume space), you can specify
the desired snapshot space in the Snapshot Space box. Simply select a value from the selection box
Save
and click
. Your snapshot space will be limited to approximately 100GB.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
46
Page 47

The process of resizing the snapshot space can take awhile depending on your data volume size and
the number of files in your volume. Expanding the snapshot space will reduce your data volume
size, and reducing the snapshot space will expand it.
Note
Due to the nature of how snapshots work, you will encounter a drop in
write performance when a snapshot is active. If your environment requires
the highest throughput in performance, the active snapshot should be
deleted, or you should set a limit on how long the snapshot should last.
USB Storage
The USB tab displays the USB disk and flash devices connected to the ioSafe R4, and offers various
options for these devices. A flash device will appear as USB_FLASH_1 and a disk device will
appear as USB_HDD_1. If you have multiple devices, they will appear appended by an increasing
device number, i.e. USB_HDD_2. If the device contains multiple partitions, the partitions will be
listed beneath the main device entry.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
47
Page 48

Partitions on the storage devices must be one of the following file system formats:
FAT32
NTFS
Ext2
Ext3
To the right of the access icons are command options for the device. The following commands are
available:
Disconnect
: This option prepares the USB partition for disconnection by properly
unmounting the file system. In most cases, you can safely disconnect the device
without first unmounting; however, the Disconnect command ensures that any
data still in the write-cache is written out to the disks and the file system is
properly closed. The Disconnect option unmounts all partitions on the device.
Once disconnected, physically remove and re-connect to the ioSafe R4 to regain
access to the USB device.
Locate
: In cases where you attach multiple storage devices and wish to determine which
device corresponds to the device listing, the
device LED, if present.
Format FAT32
: This option formats the device as a FAT32 file system. FAT32 format is easily
recognizable by most newer Windows, Linux and Unix operating systems.
Format EXT3
: This option formats the device as an EXT3 file system. Select this option if you
will be accessing the USB device mainly from Linux systems or ioSafe R4 devices.
The advantage of EXT3 over FAT32 is that file ownership and mode information
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
Locate
command will blink the
48
Page 49

can be retained using this format whereas this capability is not there with FAT32.
Although not natively present in the base operating system, Ext3 support for
Windows and OS X can be added. The installation images can be downloaded
from the web.
When the USB device is unmounted, you have the option of renaming it. The next time the same
device is connected, it will use the new name rather than the default USB_FLASH_n or
USB_HDD_n naming scheme.
The USB storage shares are listed in the Share menu, and access restrictions can be specified there.
The share names will reflect the USB device names.
USB Flash Device Option
Towards the lower portion of the USB Storage tab, you’ll notice the USB Flash Device Option.
There, you can elect to copy the content of a USB flash device automatically on connect to a
specified share. Files are copied into a unique timestamp folder to prevent overwriting previous
contents. This is useful for uploading pictures from digital cameras and music from MP3 players
without needing to power-on a PC.
In User security mode, an additional option to set the ownership of the copied files is available.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
49
Page 50

Shares
The Shares menu provides all the options pertaining to share services for the ioSafe R4 device. This
entails share management (including data and print shares), volume management, and share service
management.
We’ll first look at how we can control the services.
Adding Shares
To add a share, click on the
Volume
tab. If more than one volume is configured, click on the
volume you wish to add the share.
The
Add Share
tab has two looks, depending on the security mode. In the
Share
mode, you will
enter the share name, description, and optional password and disk quota. The share password and
share disk quota is available only in this security mode.
In the User or Domain security modes, the Add Share tab consists only of fields for the share name
and description. Password and disk quotas are account-specific.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
50
Page 51

In either case, you can add up to five shares at a time. Once you finish adding the shares, you can
refer to Chapter 2 for instructions on how to access them from different client interfaces.
Managing Shares
Once you have added shares, you may want to manually fine-tune share access in the
tab. This tab has two looks, one for
Share
security mode and one for
User and Domain
Share List
mode.
They’re both similar except for the password and disk quota prompts which only appear in Share
mode.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
51
Page 52

If you want to delete a share, click on the checkbox to the far right of the share listing and click
Delete
. You have the option of deleting up to five shares at a time.
The columns to the left of the Delete checkbox represent the services that are currently enabled, and
the access icons in those columns summarize the access rights to the share for each of the services.
You can move the mouse pointer over the access icons to get a quick glimpse of the access settings.
The settings represent:
Disabled
Read-only Access
Read/Write Access
Read Access with exceptions
– Access to this share is disabled.
– Access to this share is read-only.
– Access to this share is read/write.
– Either (1) access to this share is read-only and only
allowed for specified hosts, (2) access is read-only except for one or more users or groups
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
52
Page 53

that are granted read/write permission, or (3) access is disabled except for one or more
users or groups that are granted read-only privilege.
Write Access with exceptions
– Either (1) access to this share is read/write and only
allowed for specified hosts, (2) access is read/write except for one or more users or groups
that are restricted to read-only access, or (3) access is disabled except for one or more users
or groups that are granted read/write privilege.
You can click on the access icons to bring up the Share Options tab where you can set the access
rules for each file protocol. Keep in mind that access options will differ between protocols.
►
SETTING SHARE ACCESS IN SHARE MODE
In Share mode, the CIFS/Windows share options tab will look as follows:
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
53
Page 54

In this tab, you can select the default access at the top and optionally specify the host(s) that you
wish to allow restrict access to in the Share Access Restriction box.
Share Access Restriction
For instance, select
Access from all other hosts will be denied. For example, to allow only host
read-only
for default access and list the hosts you wish to allow access to.
192.168.2.101
read-only
access to the share, specify the following:
Default: Read-only
Hosts allowed access: 192.168.2.101
Multiple hosts can be separated with commas (see
Appendix B
for more description of valid host
formats.) For example, if you wish to limit access to the share to particular hosts, you can enter host
IP addresses or valid DNS hostnames in the
Host allowed
access field. In addition, you can enter a
range of hosts using common IP range expressions such as:
192.168.2., 192.168.2.0/255.255.255.0, 192.168.2.0/24
The above designations all allow hosts with IP addresses
192.168.2.1
through
192.168.2.254.
Towards the bottom of the
and
Opportunistic Locking
Windows [CIFS]
tab, you’ll notice the
options.
Share Display, Recycle Bin
,
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
54
Page 55

►
SETTING SHARE ACCESS IN USER AND DOMAIN MODES
In User or Domain modes, the same tab would look as follows (note the addition of read-only and
write-enabled user and group fields):
Page 56

Share Access Restriction
If you wish to limit share access to particular users and/or groups, you can enter their names in the
Read-only users, Read-only groups, Write-enabled users
, and
Write-enabled group
fields.
The names must be valid accounts, either on the ioSafe R4 or on the domain controller.
For instance, if you wish to allow read-only access to all and read/write access only user
group
engr
, you would set the following:
Default: Read-only
Write-enabled users: fred
Write-enabled groups: engr
If you wish to limit the above access only to hosts
192.168.2.101
and
192.168.2.102
fred
and
, set the
following:
Default: Read-only
Hosts allowed access: 192.168.2.101, 192.168.2.102
Write-enabled users: fred
Write-enabled groups: engr
If you wish to specify some users and groups for read-only access and some for read/write access,
and disallow all other users and groups, enter the following:
Default: Disabled
Hosts allowed access: 192.168.2.101, 192.168.2.102
Read-only users: mary, joe
Read-only groups: marketing, finance
Write-enabled users: fred
Write-enabled groups: engr
Note that access control will differ slightly from service to service.
Share Display Option
Restricting access to a share will not prevent users from seeing the share in the browse list. In
certain instances, this might not be desirable, such as for backup shares that you may want to
prevent users from seeing. To hide a share, select the
Hide this share…
option. Users who have
access to this share must specify the path explicitly. For example, to access a hidden share, enter
\\host\share in the Windows Explorer.
Recycle Bin
The ioSafe R4 can have a Recycle Bin for each share for Windows users. You will see the
Recycle Bin
option at the bottom of the
Windows [CIFS]
access tab.
Enable
When enabled, whenever you delete a file, the file gets inserted into the Recycle Bin folder in the
Share rather than being permanently deleted. This allows for a grace period where users can restore
deleted files.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
56
Page 57

You can specify how long to keep the files in the Recycle Bin and how large the Recycle Bin can get
before files get permanently erased.
Advanced CIFS Permission
The Advanced CIFS Permission box offers options for setting the default permission of new files
and folders created via CIFS. The default permission of newly created files is read/write for the
owner and owner’s group and read-only for others (i.e. everyone). Permission for newly created
folders is read/write for everyone. If the default doesn’t satisfy your security requirement, you can
change it here.
Opportunistic locking (often referred to as oplocks) enhances CIFS performance by allowing files
residing on the NAS to be cached locally on the Windows client, thus eliminating network latency
when the files are constantly accessed.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
57
Page 58

►
ADVANCED OPTIONS
The Advanced Options tab offers advanced low-level file manipulation options that can affect
remote file access through all file protocol interfaces. Care should be taken before using these
options as anything that changes ownership and permissions may not be easily reversible.
Advanced Share Permission
The Advanced Share Permission section offers the options to override the default ownership and
permission of the share folder on the embedded file system and to permeate these settings to all files
and folders residing on the selected share. The
and folders…
option will perform a one-time change. Depending on the size of the share, this can
Set ownership and permission for existing files
take awhile to finish.
You can also
grant rename and delete privilege to non-owners of the files
option. In a
collaborative environment, it may be desirable to enable this option. In a more security-conscious
environment, it may be desirable to disable this option.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
58
Page 59

USB Shares
USB storage devices are shared using the name of the device appended by the partition number.
The base device name can be changed in the Volumes/USB tab if desired. The ioSafe R4 attempts
to remember the name as long as there’s a unique ID associated with the USB device so that the
next time the device is connected, the same share name(s) will be available. Share access restrictions
are not saved across disconnects, however.
Note
Although access authorization is based on user login in non-Share mode,
files saved on the USB device, regardless of the user account, are with UID
0. This is to allow easy sharing of the USB device with other ioSafe R4 and
PC systems.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
59
Page 60

Printers
The ioSafe R4 device supports automatic recognition of USB printers. If you have not already done
so, you can connect a printer now, wait a few seconds, and click
Refresh
to display detected
printers. The print share name will automatically reflect the manufacturer and model of your printer
and will list in the USB Printers tab.
Print Shares over CIFS/SMB
The ioSafe R4 can act as a print server for up to two USB printers for your Windows or Mac clients.
For example, to setup a printer under Windows, click Browse in RAIDar or simply enter
\\
hostname
R4.
in the Windows Explorer address bar to list all data and printer shares on the ioSafe
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
60
Page 61

Double-click the printer icon to assign a Windows driver.
IPP Printing
The ioSafe R4 also supports the IETF standard Internet Printing Protocol (IPP) over HTTP. Any
client supporting IPP Printing (IPP is available natively on the latest Windows Versions and OS X)
can now use this protocol to utilize printers connected to the ioSafe R4. The simplest way to utilize
IPP Printing is to use
Bonjour
to discover and setup the print queue. Bonjour is built into OS X
and can be installed on Windows (Bonjour for Windows is available for download from Apple’s
website at http://www.apple.com/macosx/features/bonjour/ ).
Managing Print Queues
From time to time, printers may run out of ink, paper, or simply jam up, forcing you to deal with the
print jobs stuck in a queue. The ioSafe R4 has a built-in print queue management to handle this.
Simply go to the
for any “stuck” printers.
USB Printers
tab or click
Refresh
to display the printers and the jobs queued up
Click on the checkbox next to the print jobs and click
Delete Print Job
print queue.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
to remove them from the
61
Page 62

Backup
The
Backup
manager integrated with the ioSafe R4 allows the ioSafe R4 to act as a backup
appliance. Backup tasks can be controlled directly from the ioSafe R4 without the need for a clientbased backup application.
With the flexibility to support full and incremental backups across FTP, HTTP, CIFS/SMB, and
NFS protocols, the ioSafe R4 can act as a simple central repository for both home and office
environments. And with multiple ioSafe R4 systems, you can set up one ioSafe R4 to backup
another directly.
Adding a New Backup Job
To create a new backup job, click on the
procedure on creating a job.
Add a New Backup Job
tab. You will notice a 4-step
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
62
Page 63

►
STEP 1 – SELECT BACKUP SOURCE
The backup source can be located remotely or it can be a public, a private home share, or all home
shares on the ioSafe R4.
A USB device will appear as a share, so if you want to backup a USB device, select on a share name
starting with USB. If you want to backup data from a remote source, you will need to select from
one of the following:
Windows/NAS (Timestamp)
– select this if you wish to backup a share from a
Windows PC or another ioSafe R4 device. Incremental backups use timestamps to
determine whether files should be backed up.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
63
Page 64

Windows/NAS (Archive Bit)
– select this if you wish to backup a share from a Windows
PC. Incremental backups use the archive bit of files, similar to Windows, to determine
whether they should be backed up.
Website
– select thi if you wish to back up a website or a website directory. The backed
up files include files in the default index file and all associated files, as well as all index file
links to web page image files.
FTP site
NFS server
– select this if you wish to back up an FTP site or a path from that site.
– select this option if you wish to back up from a Linux/Unix server across
NFS. Mac OS X users can also use this option by setting up a NFS share from the console
terminal.
Rsync server
– select this if you wish to perform backups from a rsync server. Rsync was
originally available for Linux and other flavors of Unix, but has lately become popular
under Windows and Mac for its efficient use of incremental file transfers. This is the
preferred backup method between two ioSafe R4 systems.
Once you have selected a backup source, you can enter the path from that source. If you selected a
ioSafe R4 share, you can either leave the path blank to backup the entire share, or enter a folder
path. Note that you should use forward slashes, ‘/’, in place of backslashes (\).
If you selected a remote source, each remote protocol uses a slightly different notation for the path.
If the path field is empty, selecting the remote source in the pull-down menu shows an example
format of the path. Following are some examples:
Examples of a FTP path
ftp://myserver/mypath/mydir
ftp://myserver/mypath/mydir/myfile
Examples of a Website path
http://www.mywebsite.com
http://192.168.0.101/mypath/mydir
Examples of a Windows or remote NAS path
//myserver/myshare
//myserver/myshare/myfolder
//192.168.0.101/myshare/myfolder
Examples of NFS path
myserver:/mypath
192.168.0.101:/mypath/myfolder
Examples of Rsync path
myserver::mymodule/mypath
192.168.0.101::mymodule/mypath
Examples of local path
myfolder
media/Videos
My Folder
My Documents/My Pictures
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
64
Page 65

With a remote source, you may need to enter a login and password to access the share. If you are
accessing a password-protected share on a remote ioSafe R4 server configured for Share security
mode, enter the name of the share name for login.
You should click on the
Test Connection
button to make sure you have proper access to the
remote backup source before continuing.
►
STEP 2 – SELECT BACKUP DESTINATION
The
Step 2
process is almost identical to Step 1 except that you are now specifying the backup
destination. If you had selected a remote backup source, you will need to select a public or a private
home share on the ioSafe R4 (either the source or destination must be local to the ioSafe R4). If you
selected an ioSafe R4 share for the source, you can either enter another local ioSafe R4 share for the
destination, or you can specify a remote backup destination.
The remote backup destination can be a Windows PC/ioSafe R4 system, NFS server, or a Rsync
server. Note that you can select Rsync for a remote ioSafe R4 if it is configured to serve data over
Rsync.
►
STEP 3 – CHOOSE BACKUP SCHEDULE
You can select a backup schedule as frequently as once every four hours every day to just once a
week. The backup schedule is offset by 5 minutes from the hour to allow you to schedule snapshots
on the hour (snapshots are almost instantaneous) and perform backups on those snapshots.
If you wish, you can elect not to schedule the backup job so that you can invoke it manually instead
by not selecting the
Perform backup every…
check box. You may want to do this if you will be
starting the backup from the Backup Button on ioSafe R4 system.
►
STEP 4 – CHOOSE BACKUP OPTIONS
In this last step, select how you would like backups to be performed.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
65
Page 66

Schedule full backup
First, select when you want full backups to be performed. You can elect to do this just at the first
time, every week, every two weeks, every three weeks, every four weeks, or every time this backup
job is invoked. The first full backup is performed at the next scheduled occurrence of the backup
depending on the schedule you specify, and the next full backup is performed at the weekly interval
you choose calculated from this first backup. Incremental backup is performed between the full
backup cycles.
Backups of Web or FTP site only have the option to do full backup every time.
Send backup log
Backup logs can be sent to the users on the Alert contact list when the backup is complete. It is a
good idea to select this option to make sure files are backed up as expected. You can elect to send
only errors encountered during backup, full backup logs consisting of file listing (can be large), or
status and errors (
Note
status
refers to completion status).
Backup log e-mails are restricted to approximately 10K lines. To view the
full backup log (regardless of length), select Status > Logs and click the
Download All Logs link.
Remove files from destination first
Select if you want to erase the destination path contents before the backup is performed. Be careful
not to reverse your backup source and destination as doing so can delete your source files for good.
It is safer to not select this option unless your device is running low on space. Do experiment with a
test share to make sure you understand this option.
Remove deleted files on backup target for Rsync
By default, files deleted in the backup source will not get deleted in the backup destination. With
Rsync, you have the option of simulating
mirror
mode by removing files in the backup destination
deleted from the backup source since the last backup. Select this option if you wish to do this. Do
experiment with a test share to make sure you understand this option.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
66
Page 67

Change ownership of backup files
The Backup Manager attempts to maintain original file ownership whenever possible; however, this
may cause problems in Share security mode when backup files are accessed. To work around this,
you have the option of automatically changing the ownership of the backed up files to match the
ownership of the share. This allows anyone who can access the backup share to have full access to
the backed up files.
Before trusting that your backup job to a schedule, it is always a good idea to manually perform the
backup to make sure access to the remote backup source or destination is granted, and the backup
job can be done within the backup frequency you selected. You can do this after clicking
Apply
to
save the backup job.
Viewing the Backup Schedule
After saving the backup job, a new job appears in the Backup Schedule section of the Backup Jobs
screen.
Here, you will see a summary of the backup jobs that have been scheduled. Jobs are numbered
starting from 001. You can modify the backup job by clicking the Job number button.
If you wish, you can enable or disable the job scheduling by clicking on the
Enable
checkbox.
Disabling the job will not delete the job, but rather take it out of the automatic scheduling. If you
wish to delete the job, click the
Delete
button.
You can manually start the backup job by clicking Go. You will see the status change as the backup
is started, encounters an error, or is finished.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
67
Page 68

Click
Click
View Logs
Clear Logs
to check a detailed status of the backup.
to clear the current log detail.
Programming the Backup Button
On ioSafe R4 systems you can program the backup button to execute one or more pre-defined
backup jobs. Simply select the backup jobs in the order that you want them run and click
Apply
Pressing the Backup Button once will start the job(s).
Viewing the Backup Log
.
You can view the backup log while the job is in progress or after it has finished.
The log format might differ depending on the backup source and destination that was selected, but
you can see when the job was started and finished, and whether it was completed successfully or
with errors.
Editing a Backup Job
To edit a backup job, you can either click on the 3-digit
job number
screen. You can make appropriate changes or adjustments to the job.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
button in the Backup Jobs
68
Page 69

System
To set up and manage your ioSafe R4 system effectively, review the settings in the following sections
and make any necessary changes.
Clock
An accurate time setting on the Clock screen is required to ensure proper file timestamps. You can
access the Clock screen by selecting System > Clock from the main menu.
►
SYSTEM TIME
The System Time tab in the Clock page allows you to set the date, time, and time zone. Set
appropriately to ensure files maintain proper timestamp.
►
NTP OPTION
You can elect to synchronize the system time on the device with a remote NTP (Network Time
Protocol) server. You can elect to keep the default servers or enter up to two NTP servers closer to
your locale. Available public NTP servers can be found by searching the web.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
69
Page 70

Alerts
►
ALERTS CONTACTS
The
Contacts
The ioSafe R4 device has a robust system monitoring feature and sends email alerts if something
appears to be wrong or when a device has failed. Make sure to enter a primary email address and a
backup one if possible.
tab allows you to specify up to three email addresses where system alerts will be sent.
Some email addresses can be tied to a mobile phone. This is a great way to monitor the device when
you are away from your desk.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
70
Page 71

►
ALERTS SETTINGS
This ioSafe R4 device has been pre-configured with mandatory and optional alerts for various
system device warnings and failures. The
Settings
tab allows you to control the settings for the
optional alerts.
It is highly recommended that all alerts are kept enabled; however, you may choose to disable an
alert if you are aware of a problem and wish to temporarily disable it.
At bottom of the tab, under the
options. Selecting the
Power-off NAS when a disk fails or no longer responds
Other Alert Settings
heading, you’ll notice a couple additional
option will
gracefully power off the ioSafe R4 in the event that a disk failure or a disk remove event is detected.
Selecting the
Power-off NAS when disk temperature exceeds safe level
will gracefully power off
the ioSafe R4 when the disk temperature exceeds nominal range.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
71
Page 72

►
SNMP
If you utilize a SNMP management system such as HP OpenView or CA UniCenter to monitor
devices on your network, you can set up the ioSafe R4 device to work within this infrastructure.
To set up SNMP service, check the
leave the
Community name
Enable SNMP service
as
public
, or specify a private name if you have opted for a more
checkbox in the
SNMP
tab. You can
segregated monitoring scheme.
Next, enter a host name or an IP address for
Trap destination
. This is where all trap messages will
be sent. The following system events will generate a trap:
Abnormal power voltage
Abnormal board enclosure temperature
Fan failure
UPS connected
UPS detected power failure
RAID disk sync started and finished
RAID disk added, removed, and failure
Snapshot invalidated
If you wish to limit SNMP access to only a secure list of hosts, specify the hosts in the
allowed access
field.
Hosts
Click
Apply
to save your settings.
When you have saved the SNMP settings on the ioSafe R4, you can import the ioSafe SNMP MIB
to your SNMP client application. The ioSafe MIB can be from the ioSafe Support site at
http://www.iosafe.com.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
72
Page 73

►
SMTP
The ioSafe R4 system has a built-in email message transfer agent (MTA) that is set up to send alert
email messages from the device. Some corporate environments, however, may have a firewall that
blocks untrusted MTA’s from sending out messages.
If you were unable to receive the test message from the
Alerts Settings
tab, it may have been
blocked by the firewall. In that case, specify an appropriate SMTP server in this tab.
Internet Service Providers (ISP) for home may also block untrusted MTA’s. Furthermore, they may
allow you to specify their SMTP server but require you to enter a user login and password to send
out email – this is common with most DSL services. If this is the case, simply enter the user name
and password in the fields provided.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
73
Page 74

Performance
If you wish to tweak the system performance, select the
Performance
tab in the
System
menu.
Note that some of the settings suggest that you utilize an Uninterruptible Power Supply (UPS)
before enabling that option.
Select
Disable full data journaling
to substantially improve disk write performance. During an
unexpected power down without battery backup, there is a small chance that parity written to a disk
in a RAID set may become out of sync with the data disks, possibly causing incorrect data to be
recovered if one disk fails.
Disable journaling
Select
if you understand the consequences of this action, and you do not mind
a long file system check (only after unexpected power failures). File system journaling allows disk
checks of only a few seconds verses possibly an hour or longer without journaling. Disabling
journaling will improve disk write performance slightly.
Note
You can buy a UPS with USB monitoring at a very reasonable cost. By
safely allowing the performance options to be checked, you can effectively
double your write performance and provide uninterrupted service of your
ioSafe R4 for a very low price.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
74
Page 75

The
Optimize for OS X
option provides the best performance in Mac OS X environments when
connected to the ioSafe R4 through the SMB/CIFS protocol. This option however introduces
compatibility issues with Windows NT 4.0; do not enable this option if this device will be accessed
by Windows NT 4.0 clients.
The
Enable fast CIFS writes
option allows for fast write performance by enabling aggressive
write-back caching over CIFS. Do not enable this option in multi-user application environments
such as Quickbooks where synchronized writes are necessary to keep files in sync.
The
Enable fast USB disk writes
option speeds up USB write access by accessing the USB device
in asynchronous mode. If you enable this option, do not remove the USB device without properly
unmounting it. Failure to do so can compromise data integrity on the device.
►
ADDING A UPS FOR PERFORMANCE
Adding a UPS to the NAS is an easy way to protect against power failures, but as mentioned in the
System Performance
section, a UPS can also safely allow for a more aggressive performance
setting. Simply connect the NAS power cable to the UPS and connect the UPS USB monitoring
cable between the UPS and the NAS. The UPS will be detected automatically and will show up in
the Status bar. You can move the mouse pointer over the UPS LED icon to display the current
UPS information and battery life.
Note
Alert notification and automatic system optimization is available only with a
UPS that utilizes a USB monitoring interface.
You are notified by email whenever the status of the UPS changes; for example, when a power
failure forces the UPS to be in battery mode or when the battery is low. When the battery is low, the
NAS device automatically shuts down safely.
Make sure to adjust the optimization settings in the Performance tab if you wish to take advantage
of the available options.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
75
Page 76

Language
The
Language
for file names.
tab offers the option of setting the ioSafe R4 device to the appropriate character set
For example, selecting Japanese allows sharing of files with Japanese names in Windows Explorer.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
76
Page 77

It is best to select the appropriate language based on the region that this device will operate in.
Note
This option does not set the web browser language display – browser
settings must be done using the browser language option.
Unicode for User, Group, and Share Names
If desired, you can elect to enable use of Unicode for user, group, and share names, allowing for
greater flexibility in non-English speaking regions. This option, once selected, cannot be reversed.
Note
HTTP and WebDAV access will not work with Unicode user names.
Other restrictions may exist.
Enable Character encoding conversion for FTP clients
If your FTP client uses different character encoding from the NAS character encoding specified in
Unicode, the NAS FTP server will convert to it if this option is selected.
Updating ioSafe R4
The ioSafe R4 device offers the option of upgrading the operating firmware either automatically
using the Remote Update option or manually loading an update image downloaded from the ioSafe
Support website.
►
REMOTE UPDATE
The preferred and quicker method if the ioSafe R4 has Internet access is the
Remote
update option.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
77
Page 78

Simply click Check for Update to check for updates on the ioSafe update server.
If you wish to continue, click
Perform System Update
. After the update image has been
downloaded, you will be asked to reboot the system. The update process only updates the firmware
image and does not modify your data volume. However, it is always a good idea to backup your
important data whenever you perform an update.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
78
Page 79

►
LOCAL UPDATE
When the ioSafe R4 device is not connected to the Internet, or Internet access is blocked, you can
download an update file from the Support site and upload that file to the ioSafe R4 in the
Local
update tab.
Click on the Browse button to select the update file and click the
The process will take several minutes at which time can click the
Upload and verify image
Perform System Update
You will be requested to reboot the system to proceed with the upgrade.
browser Refresh button
during the update process.
button.
button.
DO NOT click on the
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
79
Page 80

►
SETTINGS
If you do have reliable Internet connection, you can enable the automatic update check and
download options in the Settings tab.
If you enable the
Automatically check for updates
option, the ioSafe R4 will not download the
actual firmware update, but will notify you when an update is available. If you enable the
Download updates automatically
option, the update image will be downloaded, and you will be
notified by email to reboot to the device to perform the update.
►
FACTORY DEFAULT
The
Factory Default
option carefully as
tab allows you to set the ioSafe R4 device back to factory default. Choose this
ALL DATA WILL BE LOST
, and remember to back up any data that you
wish to keep.
You will be asked to confirm the command by typing:
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
FACTORY
80
Page 81

Warning
Resetting to Factory Default will erase everything, including data shares,
volume(s), user and group accounts, and configuration information. There
is no way to recover after you confirm this command.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
81
Page 82

Power Management
The ioSafe R4 offers a couple of power management options to reduce the system’s power
consumption while it is in use and when it is expected to not be in use.
►
DISK SPIN-DOWN OPTION
You can elect to spin-down your ioSafe R4 disks after a specified time of inactivity. The disks will
spin-up as needed.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
82
Page 83

Note
Enabling disk spin-down will disable journal mode. Once enabled, if you
decide to disable disk spin-down, you will need to manually re-enable
journal mode if desired. A UPS is recommended if you utilize this option.
►
POWER TIMER
The ioSafe R4 can be scheduled to power off and power back on automatically. Select the
power timer
checkbox and enter the desired action and time.
Note
When the ioSafe R4 is powered off, any file transfers and backup jobs will
be interrupted, and backup jobs scheduled during the power off state will
not be run.
Enable
►
UPS CONFIGURATION
If this device is sharing a UPS with another ioSafe R4 system, but not directly monitoring the battery
status through a USB connection, you may elect to
attached to a remote ReadyNAS
the
Remote IP address
field of the ioSafe R4 system that is monitoring the UPS battery status.
. To use this feature, check the box and enter the IP Address in
Enable monitoring of UPS physically
As an option, the ioSafe R4 can remotely monitor the UPS when connected to a PC running
Network UPS Tools (NUT). For more information about NUT, see
http://www.networkupstools.org/.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
83
Page 84

Shutdown
The Shutdown tab offers the option to power-off or reboot the ioSafe R4 device.
You have the option of performing a full file system check or quota check on the next boot. Both
these options can take several minutes to several hours depending on the size of your volume and
the number of files in the volume. You do not need to select these options unless you suspect there
might be data or quota integrity problems.
When you reboot or shutdown the ioSafe R4, you will need to close the browser window and use
RAIDar to reconnect to FrontView.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
84
Page 85

Status
The Status page consists of the
Health
and
Logs
Health
The
Health
available, normal expected values are provided.
page displays the disk, fan, power, temperature, and UPS status in detail. When
tabs providing system status information.
For disks, you can click on the
SMART+
(Self-Monitoring, Analysis and Reporting Technology)
button to display the content of the internal disk log.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
85
Page 86

Logs
The Logs tab provides status information of management tasks along with a timestamp.
The
Download All Logs
link is available in case of problems where technical support personnel
may be of assistance in analyzing low-level log information. A zip file of all logs is downloaded and
can be attached to an email for further technical support.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
86
Page 87

Chapter
2
Accessing Shares
This chapter presents examples of how shares on the ioSafe R4 device can be accessed by the
various operating systems. If you have problems accessing your shares, make sure to enable the
corresponding service in the
set to
Read-only
or
Read/write
Shares Services
.
tab. Also make sure the default access of the share is
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
87
Page 88

Windows
To see a share listing under Windows, either click
\\ip_address
tab. The default hostname is set to
in the Explorer address bar.
nas-
Hostname
followed by the last three hex bytes of the device MAC
Browse
in
RAIDar
or enter
\\hostname
is the NAS hostname assigned in the Network
address.
To access the share under Windows, specify the hostname followed by the share name in the
Explorer address bar, i.e. \\
hostname
\backup, as follows:
or
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
88
Page 89

MAC OS X
To access the same share over AFP with OS X, select
Network
from the Finder Go menu.
At this point, there are two ways in which you can access your AFP share, depending on how you
have chosen to advertise your AFP share.
AFP over Bonjour
To access the AFP share advertised over
Go
menu to see a listing of available networks.
Bonjour
on Mac OS X, select
Network
from the Finder
Open the
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
My Network
folder to display the ioSafe R4 hostname.
89
Page 90

Double-click on the hostname icon to display the share listing.
In
Share
security mode, simply select
“Guest”
to access the shares. In
User
or
mode, enter the user name and password you wish to connect to the ioSafe R4 as.
Domain
security
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
90
Page 91

Select the Share you would like to view.
AFP over AppleTalk
If you had chosen to advertise your AFP service over AppleTalk, you will see a listing of available
networks.
Open the
My Network
folder to display the ioSafe R4 hostname. Select the one that has the
hostname only.
You’ll be prompted with a connection box.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
91
Page 92

Select
Guest
and then the share you wish to connect to, and click OK.
In
Share
security mode, you will need to only specify user name and password if you have set up a
password for your share. Enter the share name in place of the user name. In
User
or
security mode, enter the user name and password you wish to connect to the ioSafe R4 as.
You should see the same file listing as you would in Windows Explorer.
Domain
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
92
Page 93

MAC OS 9
To access the same share under Mac OS 9, select Connect to Server from the Finder menu, choose
the NAS device entry from the AppleTalk selection, and click
Connect
.
When you are prompted to login, enter the
configured for
click
Commect.
Share
security mode, or enter a valid
share name
user account
and
password
and
password
if the ioSafe R4 is
otherwise, and
If no share password is set in Share mode, you can select Guest user and leave the password field
blank. If your login is successful, you will be given a listing of one or more shares. Select the share
you wish to connect to and click
OK
.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
93
Page 94

You should see the same files in the share that you do under Windows Explorer.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
94
Page 95

Linux/Unix
To access this share from a Linux or Unix client, you will need to mount the share over NFS, i.e.
type:
mount ipaddr:/backup /backup
where
backup
is the share name. Running the ls command in the mounted path displays the share
content.
Note
The ioSafe R4 does not support NIS as it is unable to correlate NIS
information with CIFS logins. In mixed environments where CIFS and
NFS integration is desired, you can set the security to User mode and
manually specify the UID and GID of the user and group accounts to
match your NIS or other Linux/Unix server settings. The ioSafe R4
provides the ability to import a comma-delimited file containing the user
and group information to coordinate Linux/Unix login settings. Please see
the Managing Users section for more information.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
95
Page 96

Web Browser
To access the same share using a web browser, enter http://
can use
https
if you want a secure encrypted connection. You will be prompted to login.
ipaddr
Enter the share name and share password if the ioSafe R4 is in
login with a valid user and password if the ioSafe R4 is in
User
or
in the browser address bar. You
Share
security mode. Otherwise,
Domain
mode.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
96
Page 97

If the share access is read-only, the file manager will only display:
If the share is also writable, the file manager will have options for creating, modifying, and deleting
files, as follows:
One useful application for a web share is for setting up an internal company website. You can copy
HTML files to the web share using Windows, Mac, NFS, or HTTP. When you set HTTP access to
read-only, html files, including index.htm and index.html, can be viewed using any web browser.
Note
Files created under the Web file manager can only be deleted under this file
manager. The only exception is the admin user, who can change or delete
any files created through the web.
Files not created from this file manager can be modified within the file
manager but cannot be deleted here.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
97
Page 98

FTP / FTPS
To access the share via FTP in Share security mode, use “anonymous” as the login and your email
address as the password.
Note
Enabling FTP access in Share mode opens up the share to anyone who has
an FTP client on your network. It is best to enable FTP access only to
shares you are comfortable making public on your network.
Warning
Disk usage using FTP in Share mode does not count towards the share
disk quota, so carefully choose how you advertise a FTP Share.
To access the share in User or Domain security mode, use the appropriate user login and password
used to access the ioSafe R4. For better security, you can use a FTPS (FTP-SSL) client to connect to
the ioSafe R4 FTP service. With FTPS, password and data is encrypted.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
98
Page 99

Rsync
Access to the share via rsync is identical regardless of the security mode. If you had specified a user
or password in the rsync share access tab, you will need to specify this when accessing the rsync
share. Unlike other protocols, rsync uses arbitrary user name and password that is specific only for
rsync access. The user account you specify does not need to exist on the ioSafe R4 or a domain
controller.
Hers is an example of a way for a Linux client to list the content of an ioSafe R4 rsync share with no
user name and password defined:
# rsync ipaddr::backup
To recursively copy the content of a share to /tmp:
# rsync –a ipaddr::backup /tmp
To do the same except with a login
# rsync –a user@ipaddr::backup /tmp
Passowrd: *****
Note
user
and password
hello
:
The ioSafe R4 does not support rsync over SSH.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
99
Page 100

Networked DVE Players and UPnP AV Media Adapters
Networked DVD players and UPnP AV Media adapters will detect the ioSafe R4 if the Home
Media Streaming Server or the UPnP AV services are enabled. The content of the Streaming
Services
media
share on the ioSafe R4 is available to these players for playback. Please consult the
player manual for information on the file formats that it supports. Multiple players can be
connected to the ioSafe R4 and can play the media files concurrently.
Make sure that you enable the appropriate service in the Services tab before invoking this service.
Consult the Device Compatibility list for information on which DVD players and media adapters
will work with Netgear's ReadyNAS technology.
P/N: 900-10004-00 REV 02 USER GUIDE, IOSAFE R4
100
 Loading...
Loading...