Page 1

Intego NetBarrier X5 User’s Manual Page 1
Intego NetBarrier X5
User’s Manual
Page 2

Intego NetBarrier X5 User’s Manual Page 2
Intego NetBarrier X5 for Macintosh
© 2007 Intego. All Rights Reserved
Intego
www.intego.com
This manual was written for use with Intego NetBarrier X5 software for Macintosh. This manual
and the Intego NetBarrier X5 software described in it are copyrighted, with all rights reserved. This
manual and the Intego NetBarrier X5 software may not be copied, except as otherwise provided in
your software license or as expressly permitted in writing by Intego.
The Software is owned by Intego and its suppliers, and its structure, organization and code are the
valuable trade secrets of Intego and its suppliers. The Software is protected by United States
Copyright Law and International Treaty provisions.
Page 3

Intego NetBarrier X5 User’s Manual Page 3
Contents
1- About Intego NetBarrier X5 .......................................................................................6
What is Intego NetBarrier X5? .......................................................................................................7
Personal Firewall........................................................................................................................................... 7
Antivandal...................................................................................................................................................... 7
Privacy Protection......................................................................................................................................... 8
Monitoring......................................................................................................................................................9
Erasing Your Tracks With Washing Machine.........................................................................................9
Using this User’s Manual .............................................................................................................10
2—Introduction to Computer Security........................................................................11
Why You Need to be Protected ...................................................................................................12
How Can a Computer be Totally Safe? .................................................................................................. 13
What Is a Firewall? .....................................................................................................................................13
Friend or Foe? ..............................................................................................................................................13
What You Risk.................................................................................................................................14
Why People Break into Computers......................................................................................................... 14
The Different Types of Attacks and Intrusions Possible ....................................................................15
Privacy Protection ...........................................................................................................................15
3—Installation...............................................................................................................17
System Requirements ....................................................................................................................18
Installing Intego NetBarrier X5...................................................................................................18
4—Quick Start ...............................................................................................................19
Using Intego NetBarrier X5 ..........................................................................................................20
Using the NetBarrier X5 Overview Screen...............................................................................20
Status Indicators on the Overview Screen ...............................................................................24
Using the Setup Assistant ............................................................................................................25
Using the Intego Menu..................................................................................................................29
NetBarrier X5 Password Protection............................................................................................30
Getting Help.....................................................................................................................................30
5—The Four Lines of Defense: Firewall .......................................................................31
Firewall Rules ..................................................................................................................................32
Simple Mode ................................................................................................................................................32
Advanced Mode..........................................................................................................................................35
Creating Rules with the Assistant..............................................................................................37
Name and Behavior.................................................................................................................................... 39
Communication Direction ........................................................................................................................40
Service ...........................................................................................................................................................42
Options..........................................................................................................................................................43
Conclusion....................................................................................................................................................44
Creating Service-Specific Rules Quickly .................................................................................46
Page 4

Intego NetBarrier X5 User’s Manual Page 4
Creating Rules Manually..............................................................................................................48
Rule Naming, Logging, Evaluation and Schedules.............................................................................49
Rule Sources and Destinations................................................................................................................. 52
Rule Services ................................................................................................................................................55
Rule Interfaces .............................................................................................................................................60
Rule Actions................................................................................................................................................. 61
Multi-Part Sources, Destinations, Services and Interfaces.................................................................61
Deleting Sources, Destinations, Services and Interfaces .................................................................... 62
Working with Rules .......................................................................................................................63
Rule Order....................................................................................................................................................63
Editing and Deleting Rules.......................................................................................................................63
Using the Rule Contextual Menu ............................................................................................................64
Trojan Horse Protection ................................................................................................................66
6—The Four Lines of Defense: Privacy ........................................................................68
Data Filter .........................................................................................................................................69
How the Data Filter Works.......................................................................................................................70
What to Protect............................................................................................................................................ 71
Adding Data to the Filter ..........................................................................................................................72
Activating, Deactivating and Deleting Data Items..............................................................................75
Data Filter Options .....................................................................................................................................76
Surf Filters ........................................................................................................................................77
Banners Filter ............................................................................................................................................... 78
Cookies Filter ...............................................................................................................................................82
Information Hiding ....................................................................................................................................85
7—The Four Lines of Defense: Antivandal..................................................................86
Antivandal ........................................................................................................................................87
Policy .............................................................................................................................................................88
Options..........................................................................................................................................................91
Unifying Policy Options............................................................................................................................ 92
Anti-Spyware ...................................................................................................................................93
Options..........................................................................................................................................................96
Applications: Adding, Removing and Changing Settings.................................................................97
The Stop List and Trusted Group...............................................................................................99
Stop List/Trusted Group Information .................................................................................................101
A Note About DNS Lookups .................................................................................................................103
Adding Addresses ....................................................................................................................................104
Using Wildcards........................................................................................................................................105
Removing Addresses ...............................................................................................................................105
Moving Addresses Between the Stop List and Trusted Group ......................................................106
Editing an Address ...................................................................................................................................107
The Contextual Menu ..............................................................................................................................108
8—The Four Lines of Defense: Monitoring................................................................109
The Log ............................................................................................................................................110
Log View Options .....................................................................................................................................111
Log Window Contextual Menu .............................................................................................................115
Pausing the Log.........................................................................................................................................117
Clearing the Log........................................................................................................................................117
Exporting the Log .....................................................................................................................................118
Filtering Data in the Log Window ........................................................................................................120
Page 5

Intego NetBarrier X5 User’s Manual Page 5
Traffic...............................................................................................................................................122
Traffic View Modes ..................................................................................................................................122
Selecting Activity Data Types ................................................................................................................126
NetBarrier Monitor ...................................................................................................................................127
NetBarrier Monitor Preferences.............................................................................................................129
The NetBarrier Monitor Widget ............................................................................................................130
The NetBarrier X5 Monitor Screen Saver.............................................................................................131
Services ............................................................................................................................................133
Network...........................................................................................................................................135
Whois ...............................................................................................................................................139
Traceroute .......................................................................................................................................140
NetUpdate .......................................................................................................................................144
9—Understanding Alerts ............................................................................................145
Alert Settings .................................................................................................................................146
Examples of Alerts........................................................................................................................149
Attack Counter...............................................................................................................................152
10—Preferences and Configurations..........................................................................153
Modem Preferences......................................................................................................................154
Log Preferences .............................................................................................................................155
Traffic Preferences........................................................................................................................157
Whois Preferences ........................................................................................................................159
Advanced Preferences .................................................................................................................160
About NetBarrier X5.....................................................................................................................161
Configurations...............................................................................................................................162
Creating, Editing and Deleting Configurations .................................................................................162
Exporting and Importing Settings............................................................................................165
Locking and Unlocking the Interface......................................................................................166
11—Technical Support ................................................................................................167
12—Glossary................................................................................................................170
Page 6

Intego NetBarrier X5 User’s Manual Page 6
1- About Intego
NetBarrier X5
Page 7

Intego NetBarrier X5 User’s Manual Page 7
What is Intego NetBarrier X5?
Intego NetBarrier X5 is the Internet security solution for Macintosh computers running Mac OS X.
It offers thorough protection against intrusions coming across the Internet or a local network.
NetBarrier X5 protects your computer from intrusions by constantly filtering all the activity that
enters and leaves through the Internet or a network. NetBarrier X5 protects you from thieves,
hackers and intruders, and warns you automatically if any suspicious activity occurs.
NetBarrier X5 has four lines of defense to protect your Mac and your data from intrusions and
attacks.
Personal Firewall
NetBarrier X5 contains a personal firewall that filters data as it enters and leaves your computer. A
full set of basic filtering rules is used by default, and its Customized protection mode allows you to
create your own rules, if you need to.
Antivandal
NetBarrier X5’s Antivandal is a powerful guardian for your computer. It watches over your Mac’s
network activity, looking for signs of intrusion. If it detects any suspicious activity, NetBarrier X5
stops the intruder in their tracks and displays an alert. The Antivandal has another powerful
function, the Stop List, that records the addresses of intruders who attempt to get into your Mac,
ensuring that they will always be blocked. Several options allow you to choose the type of
protection you have on your computer.
Policy
NetBarrier X5 can stop incoming data that is considered hostile. It can display an alert
dialogue, showing why the data was stopped, and asking you to allow or deny it. You can
also select other alert options, such as having NetBarrier X5 play a sound, put the host
automatically in the Stop List, or send an e-mail message to the address(es) of your choice.
Page 8

Intego NetBarrier X5 User’s Manual Page 8
Stop List
When an intruder is detected trying to break into your Mac, NetBarrier X5 allows you to
put them on the Stop List, which records their network address. If a computer with the same
address tries to enter your computer again it will be automatically blocked.
Trusted Group
In some cases, computers you know—friends, not foes—will be blocked by NetBarrier X5.
These may be computers on your local network, blocked because they are sending pings to
your computer, for example. NetBarrier X5 allows you to put them in the Trusted Group,
where they will be considered friends for as long as you want, ensuring that they can always
access your Mac. It is important to note that the Trusted Group only applies to NetBarrier
X5’s Antivandal functions and data filter, and Firewall rules are still applied to computers
in the Trusted Group.
Anti-Spyware
NetBarrier X5 lets you control Internet and network access by individual applications.
Whenever an untrusted application tries to connect to a network, NetBarrier X5 can display
an alert, informing you which application is making the connection. If you want to allow
that application to access the network—if it truly is an application you know should be
using the network—then you can do so. But if an application tries to connect in secret, you
can block it permanently.
Privacy Protection
NetBarrier X5 helps protect your privacy. It filters data to ensure that no sensitive information
leaves your computer, blocks ad banners, and lets you surf anonymously. And it has a unique
feature that hides information about your computer: its platform, which browser you are using, and
the last web page you visited.
Page 9

Intego NetBarrier X5 User’s Manual Page 9
Monitoring
NetBarrier X5 contains powerful tools for monitoring your network activity and usage. Its activity
gauges show your network traffic in real time, and its additional monitoring functions give you
essential information on your computer, its network and the services and connections that are
active.
NetBarrier X5 even offers a separate program, NetBarrier Monitor, that you can keep open all the
time, as well as a monitoring screen saver, so you can always keep an eye on your network traffic.
Erasing Your Tracks With Washing Machine
NetBarrier X5 includes a separate program named Washing Machine that further protects your
privacy by helping you delete information about your Internet habits. It provides an easy way to
remove bookmarks, cookies, caches, download histories and browsing histories for more than two
dozen programs that regularly store such information, and can be set to periodically “clean” those
items for effortless protection.
Washing Machine includes functions that were in previous versions of NetBarrier; you can launch
the program from the Intego Menu in the NetBarrier X5 submenu. For detailed information about
using Washing Machine, see the Intego Washing Machine User Manual you received with
NetBarrier X5.
Page 10

Intego NetBarrier X5 User’s Manual Page 10
Using this User’s Manual
If you are a:
Read:
Home user, connected to the
Internet
• Chapter 2, Introduction to Computer Security
• Chapter 3, Installation
• Chapter 4, Quick Start
• Optional: chapters 5-9, The Four Lines of Defense.
NetBarrier X5 is configured to automatically protect your
computer from intruders.
Business or Academic user,
connected to a local network
and the Internet
• Chapter 2, Introduction to Computer Security
• Chapter 3, Installation
• Chapter 4, Quick Start.
NetBarrier X5’s basic protection modes will probably be
sufficient for you; however, you might also want to read chapters
5-8, The Four Lines of Defense.
Advanced user, using your
computer as a server, or
administering a network
The entire manual concerns your situation, but you will want to
read chapters 5-8, The Four Lines of Defense, and especially
chapter 5, which explains how to create your own rules.
There is a glossary at the end of the manual that defines specific terms used.
Page 11

Intego NetBarrier X5 User’s Manual Page 11
2—Introduction to
Computer Security
Page 12

Intego NetBarrier X5 User’s Manual Page 12
Why You Need to be Protected
Whether you use your Mac for work or just for surfing the Internet, whether you are online all day
long, or just occasionally, whether you are on a local network in a home office, or part of a large
corporation or educational institution, your computer contains sensitive information. This may be
anything from your credit card numbers to your bank account information, contracts with customers
or employees, confidential projects or e-mail messages and passwords. No matter what you have on
your Mac that is for your eyes only, there is somebody out there who would certainly find it
interesting.
The more you use your Mac for daily activities, whether personal or professional, the more you
should protect the information it contains.
Think of your computer as a house. You certainly lock your doors and windows when you go out,
but do you protect your Mac in the same way? As long as you are connected to a network, there is a
way for wily hackers or computer criminals to get into it—unless you protect it with NetBarrier X5.
When your Mac is connected to a network, whether it be a private, local network, or the Internet, it
is like a house on a street, with doors and windows. NetBarrier X5 works like a set of locks to
protect those doors and windows. You never know who is watching when you are connected to a
web site. Maybe that gaming site with the cheats you were looking for has a cracker behind it who
wants to snoop on your Mac and see if he can find anything interesting. Or perhaps that stock
market information site, where you went to get company results, has a curious hacker watching who
enjoys messing up people’s computers just for fun.
A computer is only as secure as the people who have access to it. NetBarrier X5 protects your
computer by preventing unauthorized network access to your Mac, and by protecting against
unauthorized export of private information.
Without Intego NetBarrier X5, you may never know
if anyone is trying to get into your Mac.
Page 13

Intego NetBarrier X5 User’s Manual Page 13
How Can a Computer be Totally Safe?
It has been said that the only truly secure computer is one that is switched off and unplugged,
locked in a titanium-lined safe, buried in a concrete bunker, and surrounded by nerve gas and very
highly-paid armed guards. Obviously, this is not practical—if you have a computer, you want to be
able to use it.
But NetBarrier X5 provides a level of protection that goes far beyond what most users need, and its
customizable rules make it a powerful tool for system and network administrators, allowing them to
adapt the protection to their specific needs.
What Is a Firewall?
A firewall is, as its name suggests, like a wall. It protects your computer or network by separating
users into two groups—those inside the wall, and those outside. It is configured to determine what
access outsiders have to computers inside the wall, and what access insiders have to computers and
networks on the other side of the wall.
A firewall is a kind of filter that acts between your computer, or network, and a wide area network
such as the Internet. It functions by filtering packets of data, and examining where they come from
and where they are going.
NetBarrier X5 offers powerful firewall protection for your Mac, and its customized protection
allows advanced users to configure specific rules to protect against foes who wish to infiltrate your
computer.
Friend or Foe?
Every wall has to have a gate so people can get in and out. NetBarrier X5’s Antivandal acts as a
filter, or a guard standing at the gate in the wall, checking all incoming and outgoing data for signs
of hackers, crackers, vandals, spies, intruders and thieves. This can be done because there are many
“standard” ways to enter an unprotected computer, and NetBarrier X5 knows these methods.
Page 14

Intego NetBarrier X5 User’s Manual Page 14
What You Risk
Why People Break into Computers
People break into computers for many reasons. Sometimes this is done just to get into more
systems; by hopping between many computers before breaking into a new one, crackers hope to
confuse any possible pursuers and put them off the scent. There is an advantage to be gained in
breaking into as many different sites as possible, in order to “launder” connections.
Another reason is that some people simply love to play with computers and stretch them to the
limits of their capabilities. This is a bit like people who write graffiti on walls—they just want to do
it because it’s there.
But the more serious invaders are real criminals. These may be competitors, looking for information
on your company’s activities, projects or customers; thieves, looking for passwords and credit card
numbers; or simply spies. While most companies have computer security policies, few of them
think of protecting data on their employees’ home computers—but these computers often have
sensitive documents that employees have brought home from work.
Unfortunately, we live in a world where anything of value is a target for thieves. Since today’s
economy is built around information, it is obvious that information has become the latest target.
Here’s a simple example: last year, on Mother’s Day, you sent your mother some flowers. You
ordered by fax, because you don’t trust sending your credit card number over the web. But the
document that you typed, containing your credit card number, is still on your hard disk. If someone
found it, they would have your credit card number, and you might become a victim of fraud.
Page 15

Intego NetBarrier X5 User’s Manual Page 15
The Different Types of Attacks and Intrusions Possible
There are many reasons why people attempt to obtain entry into other people’s computers, and
many ways to do so. Here are some of them:
• To steal confidential documents or information.
• To execute commands on your computer that modify the system, erase your hard disk, or
disable your computer.
• To hack web sites, replacing pages with different text and graphics.
• To launch denial-of-service attacks that can render your computer temporarily unusable.
• To get information about your computer that will allow someone to break into your network, or
your computer, at a later time.
Privacy Protection
One thing you don’t notice when you surf the Internet is how much personal information different
web sites try to get from you. You can clearly see the ones that openly ask you to register to use
them; you enter a user name and a password, and sometimes your name, address, and other
information as well. This information is often used to trace your behavior, to find what your
interests are, and to market products and services to you.
More and more Internet users refuse to give web sites this kind of information. Sometimes you
learn the hard way: you register at a web site, and end up getting spam or e-mail about things you
never requested. By then, it’s usually too late.
But web sites have other ways of getting information about you and your behavior. Did you know
that your browser sends information to web sites telling which operating system you are using,
which browser you are surfing with, and even the last web page you visited?
Then there are cookies. A cookie is a file on your hard disk that contains information sent by a web
server to a web browser and then sent back by the browser each time it accesses that server.
Typically, this is used to authenticate or identify a registered user of a web site without requiring
them to sign in again every time they access that site. Other uses of cookies are to maintain a
Page 16

Intego NetBarrier X5 User’s Manual Page 16
“shopping basket” of goods you have selected to purchase during a session at a site, site
personalization (presenting different pages to different users), or to track a particular user’s access
to a site.
While cookies can have legitimate uses, as we have seen above, unscrupulous web sites use them to
collect data on your surfing habits. They sell this data to companies that will then target you
specifically for products and services that correspond to these habits, or even ensure that when you
surf on certain sites, you see ad banners that match these habits.
NetBarrier X5’s approach to privacy is simple: it provides you with the means to prevent certain
types of information from being recorded without your knowledge.
Page 17

Intego NetBarrier X5 User’s Manual Page 17
3—Installation
Page 18

Intego NetBarrier X5 User’s Manual Page 18
System Requirements
• Any officially-supported Mac OS X compatible computer
• Mac OS X 10.4 or higher, or Mac OS X Server 10.4 or higher
• 40 MB free hard disk space
Installing Intego NetBarrier X5
For information on installing and serializing Intego NetBarrier X5, see the Intego Getting Started
manual, included with your copy of the program. If you purchased the Intego NetBarrier X5 by
download from the Intego web site, this manual will be in the disk image you downloaded that
contains the software. If you purchased NetBarrier X5 on a CD or a DVD, you’ll find this manual
on the disc.
Page 19

Intego NetBarrier X5 User’s Manual Page 19
4—Quick Start
Page 20

Intego NetBarrier X5 User’s Manual Page 20
Using Intego NetBarrier X5
When you first open NetBarrier X5, the Overview screen displays. If you’ve used an earlier version
of NetBarrier, you’ll notice that this screen has been simplified and streamlined. But don’t worry:
all the old functions are there.
Using the NetBarrier X5 Overview Screen
The Overview screen gives quick access to:
• NetBarrier X5’s functions, settings and logs,
• Several helpful network utilities, such as Whois and Traceroute,
• Visual indicators of what sorts of protection are enabled,
• Information about the program itself, such as when it was last updated,
• A way of managing multiple configurations, so you can quickly change protection settings.
Page 21

Intego NetBarrier X5 User’s Manual Page 21
Central to the Overview screen are sections that control NetBarrier X5’s four lines of defense.
Controls for Firewall, Antivandal and Privacy appear as large buttons in the center of the Overview
screen; controls for Monitoring are the smaller buttons in the bottom-right corner.
The Firewall section gives you access to Rules that define
what programs can send and receive information to and
from your Mac, and Trojan settings to protect your Mac
from malicious Trojan horses.
The Privacy section gives you access to settings that
prevent specific data from being sent over the Internet and
local networks, and blocks certain types of information that
are sent and received when you surf the internet.
The Antivandal section gives you ways to see and control your Policy of stopping certain sorts of
attacks; how you’re protected against programs that secretly connect to remote computers (Anti-
Spyware); your Stop List, that keeps track of the bad guys; and your Trusted Group of friends who
are explicitly allowed to access your Mac.
Page 22

Intego NetBarrier X5 User’s Manual Page 22
You can access Monitoring functions through buttons in the bottom-right corner of the Overview
screen. They’re also available through selections under the View menu, and by using keyboard
shortcuts. They are:
Log
Option-Command-L
Shows a record of NetBarrier’s activities, and
traffic to and from your Mac to the Internet
or local networks
Traffic
Option-Command-1
Shows network traffic entering and leaving
your Mac
Services
Option-Command-2
Shows a list of ways that your Mac is
prepared to provide information to the
outside world
Networks
Option-Command-3
Shows outside networks that are currently
available to your Mac
Whois
Option-Command-4
Shows information about the owners and
managers of Internet domains
Traceroute
Option-Command-5
Shows the network path that a signal takes to
get from your Mac to another computer
Each of these features is described in chapter 8, The Four Lines of Defense: Monitoring.
At the left of the Overview window is a list of Configurations. Each configuration is a collection of
settings for NetBarrier’s Firewall, Privacy and Antivandal protection. At first there is only one
configuration, named “default”. The radio button shows which configuration is currently active.
Page 23

Intego NetBarrier X5 User’s Manual Page 23
At the bottom of the Configurations list are four buttons that let you duplicate, edit, remove and
hide configurations. (You can also toggle between showing and hiding the Configurations list by
pressing Command-K or choosing View > Hide/Show Configurations List.) For more information,
see chapter 10, Preferences and Configurations.
At the very top of the screen is the NetUpdate Status Bar, which shows the dates of the latest
NetBarrier filters installed on your Mac, and the date of the latest filters available through Intego
NetUpdate. NetUpdate periodically checks for updates, or you can have it check immediately by
clicking the “Check Now…” button in the upper-left corner. To hide the NetUpdate Status Bar,
choose View > Hide NetUpdate Status Bar. For more information, see the Intego Getting Started
Manual.
Finally, a small button near the top-left corner of the Overview screen tells you which section of the
NetBarrier X5 interface you’re currently viewing. When you first launch the program, it simply
says “Overview”.
But when you look at the control screen for Trojans, for example, you see a segmented button that
makes clear that it’s a part of the Firewall section, along with Rules.
Clicking on Rules takes you there; clicking on Firewall or Overview takes you back to the
Overview screen. The Privacy and Antivandal sections work the same way.
Page 24

Intego NetBarrier X5 User’s Manual Page 24
Status Indicators on the Overview Screen
The status of various NetBarrier X5 features appears as part of the icons on the Overview Screen.
When the Trojans, Data and Anti-Spyware sections are on, you’ll see a small check mark in the
bottom-right corner of their icons.
Off
On
Similarly, the Stop List and Trusted Group icons show how many entries are in their lists.
None
Two
Page 25

Intego NetBarrier X5 User’s Manual Page 25
Using the Setup Assistant
When you install NetBarrier X5 and restart your Macintosh, it automatically begins protecting your
Mac. The firewall is enabled in “Client, local server” mode and activity is written to the log. In this
mode, your Mac can access the Internet as a client computer, and your Mac can function as both a
client and server on a local network. For more information about NetBarrier X5’s Firewall Modes,
see below.
NetBarrier X5 includes a Setup Assistant to help you quickly and easily adjust NetBarrier X5’s
basic settings so they are appropriate to your network usage. The first time you open NetBarrier X5,
the Setup Assistant launches automatically. If you have upgraded from a previous version of
NetBarrier, you will need to launch the Setup Assistant manually. To do this, choose NetBarrier X5
> Preferences and click the Advanced icon. Click Show Assistant… at the bottom of the window.
You will need an administrator’s password to run the Setup Assistant.
Page 26

Intego NetBarrier X5 User’s Manual Page 26
Click the right arrow to begin configuring NetBarrier X5. You can click the left arrow at any time
to return to previous screens. The NetBarrier X5 Setup Assistant briefly presents informational
screens about the program’s different functions:
• Firewall (Rules and Trojans)
• Privacy (Data and Surf protection)
• Antivandal (Policy, Anti-Spyware, Stop List, and Trusted Group)
• Monitoring (the Log and five Monitor tools)
• One more thing (miscellaneous tools)
When done, the Configuration screen allows you to choose which NetBarrier X5 configuration you
want to use.
Page 27

Intego NetBarrier X5 User’s Manual Page 27
The configurations are:
Name
Best if…
Firewall setting
Other settings
Default
…you need to allow
access to your Mac from
the local network, but
want to be protected from
invasions from outside
your local network.
“Client, local server”
mode: your Mac can
access the Internet as a
client computer, and can
function as both a client
and server on a local
network.
All Antivandal and Privacy
filters are disabled.
Normal
…you do not use your
computer as a network
server or for local file
sharing.
Client only mode: your
Mac can function only as
a client on a local
network or the Internet.
The server functions of
your computer are
blocked.
Antivandal filters are enabled
against Buffer Overflow
Attacks, Intrusion Attempts,
Ping Attacks, Port Scans and
SYN Flooding, but disabled
against Ping Broadcasts. All
Privacy filters are disabled.
Page 28

Intego NetBarrier X5 User’s Manual Page 28
Strong
…you want maximal
protection, and can accept
that this configuration
might block some traffic.
Client only mode.
All Antivandal filters are
enabled, as are those that
protect against Trojans.
Click the Configure button to activate the configuration you have selected.
Page 29

Intego NetBarrier X5 User’s Manual Page 29
Using the Intego Menu
NetBarrier X5, like all other Intego programs, installs a menu in the menubar, called the Intego
menu. Its icon is a small tower, as in the Intego logo.
Click the Intego menu icon to display a menu that shows all your Intego software:
You can change many of NetBarrier X5’s settings from the Intego menu. Choose the Intego Menu >
NetBarrier X5. You can change configurations, and you can turn on or off settings, such as filtering
or privacy settings. You can open Intego Washing Machine from the Intego menu, by choosing the
Intego menu, then NetBarrier X5 > Open Washing Machine.... And you can open NetBarrier
Monitor by choosing NetBarrier X5 > Open NetBarrier Monitor.
Page 30

Intego NetBarrier X5 User’s Manual Page 30
NetBarrier X5 Password Protection
NetBarrier X5 uses built-in Mac OS X password protection. In order to install and configure the
program, the user must have administrator’s rights, and log in with an administrator’s name and
password. Users who do not have administrator’s rights cannot change any of NetBarrier X5’s
settings or preferences. These users can view Monitoring functions such things as logs and traffic
gauges, but are not authorized to make changes to the program’s operation.
Getting Help
You can get help on some of NetBarrier X5’s functions by holding your cursor over certain texts
and zones:
A Tool Tip displays explaining the various functions and features.
For complete help, this manual is available by choosing Help > NetBarrier X5 User Guide.
Page 31

Intego NetBarrier X5 User’s Manual Page 31
5—The Four Lines of
Defense: Firewall
Page 32

Intego NetBarrier X5 User’s Manual Page 32
NetBarrier X5 is a powerful, easy-to-use program that protects your Mac when connected to a
network through four lines of defense. The first of these is a personal firewall, a powerful program
that filters all data packets entering or leaving your Mac through the Internet or a local TCP/IP
network. It also protects you from Trojan horses by blocking the ports they use.
The Overview screen shows the Firewall section, which contains two buttons: Rules and Trojans.
Firewall Rules
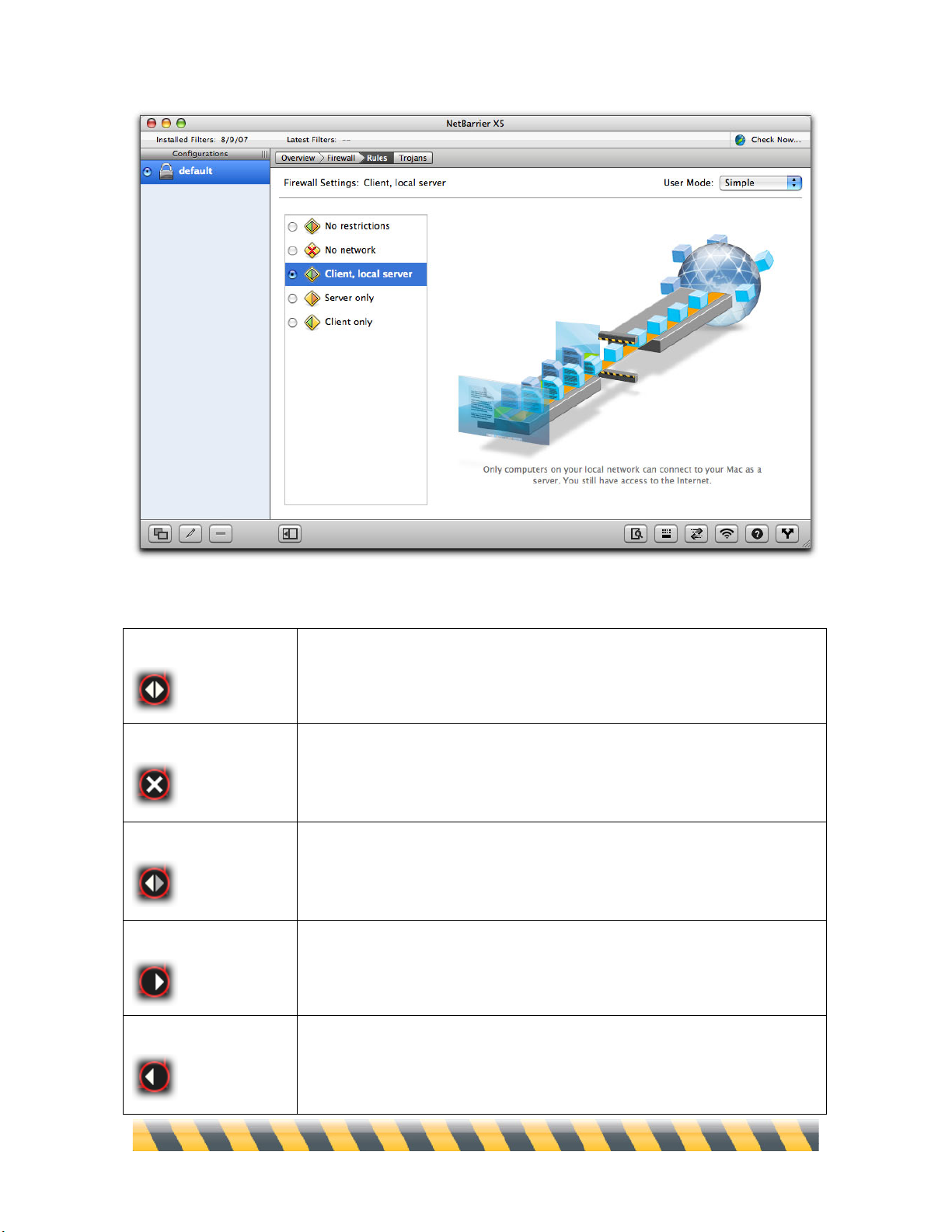
Simple Mode
When you click the Rules button, NetBarrier X5 presents the simple mode for controlling Firewall
settings. There are five preset firewall settings that cover all the situations that you will encounter in
normal use, each accompanied by an animation that graphically shows the effect of applying the
setting. The screen closest to you represents your Mac; the globe represents the Internet; the screen
halfway between the two represents the limit of your local network. Here the default setting,
“Client, local server”, shows how your computer can receive information from beyond the local
network, but that computers beyond your local network cannot access your Mac.
Page 33
Intego NetBarrier X5 User’s Manual Page 33
The following are the five firewall settings, and how they display on the Overview screen:
No restrictions
NetBarrier X5’s firewall allows all incoming and outgoing network data
to be sent and received,.
No network
NetBarrier X5’s firewall prevents all data from entering or leaving your
computer to or from the Internet or a local TCP/IP network. This is useful
if you are away from your computer and wish to protect it totally.
Client, local server
NetBarrier X5’s firewall allows your Mac to function as a client and local
network server. Your Mac can access the Internet as a client computer,
and as both a client and server on a local network.
Server only
NetBarrier X5’s firewall allows your Mac to function only as a server: All
client functions, including your ability to surf the Internet, are blocked.
Client only
NetBarrier X5’s firewall allows your Mac to function only as a client on a
local network or the Internet. The server and file-sharing functions of your
Mac are blocked.
Page 34

Intego NetBarrier X5 User’s Manual Page 34
These five settings are sufficient for most people. But if you want more control over access to your
computer—if, for example, you’re running a gaming party and want to forbid all traffic except for
communications that are part of the game—then you need to switch to NetBarrier X5’s Advanced
mode.
Page 35
Intego NetBarrier X5 User’s Manual Page 35
Advanced Mode
Each of the five settings described above is actually a collection of rules, each of which in turn is
defined by naming permitted or forbidden sources, destinations, services and interfaces. Simple
mode doesn’t permit you to change the rules or any of their parts. To do that, you need to enter the
Firewall screen’s advanced mode.
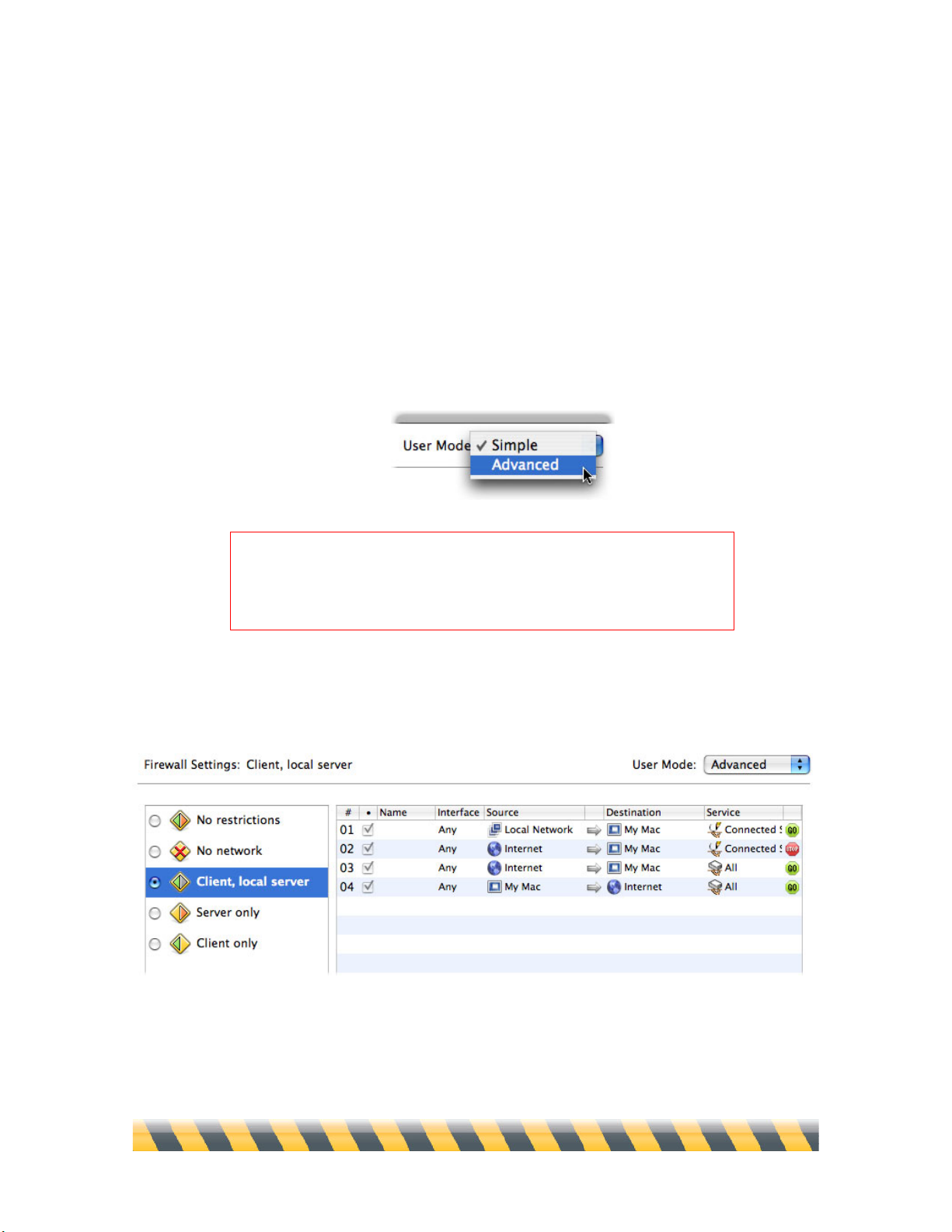
To access NetBarrier X5’s complete set of firewall rules, change the User Mode popup menu in the
upper-right corner from Simple to Advanced.
In simple mode, clicking any of the five preset firewall settings displays an animation; in advanced
mode, you see the details of each setting’s rules.
WARNING: Changing these settings could dramatically affect your
computer’s ability to access local networks and the Internet. You
should only use advanced mode if you fully understand its effects and
how it functions.
Page 36
Intego NetBarrier X5 User’s Manual Page 36
In this example, the “Client, local server” setting shown has four rules. The first allows the local
network to access your Mac through all Connected Services—that is, TCP connections that involve
back-and-forth communications, such as serving files from your Mac. The second rule, however,
forbids such connections from the Internet at large, preventing your Mac from acting as a server to
an unknown computer outside your local network. The third rule allows all other communications
from the Internet to your Mac, while the fourth allows all communications from your Mac to the
Internet.
The five preset firewall settings are “frozen” for convenience and stability: you can’t change their
rules, or the order in which they appear. But NetBarrier X5 gives you two ways to create additional,
customized settings: through the Assistant, and manually.
In either case, the first step is to click the + button below the list of settings. You’ll see a new
setting appear, named “untitled setting”. Click it and type any name you prefer, then press Enter or
Return to make the change permanent.
Note that you have only created this setting, but have not enabled it yet. It’s a good idea to not
enable firewall settings until you have finished adding all your rules. To make it the active setting,
click the radio button to its left.
Page 37
Intego NetBarrier X5 User’s Manual Page 37
Creating Rules with the Assistant
NetBarrier X5 contains an assistant to help you create your own custom firewall rules. With this
assistant, you can create your own rules with just a few mouse clicks. While not all of NetBarrier
X5’s rule features are available when you create rules with the assistant, it can cover most of your
needs for firewall rules. If you need more customization, you can create rules using the assistant
then edit them manually.
The NetBarrier X5 Assistant walks you through a series of steps to create your rule:
• Name and Behavior
• Direction
• Service
• Options
• Conclusion
To create a new rule using the assistant, click the Assistant button.
Page 38
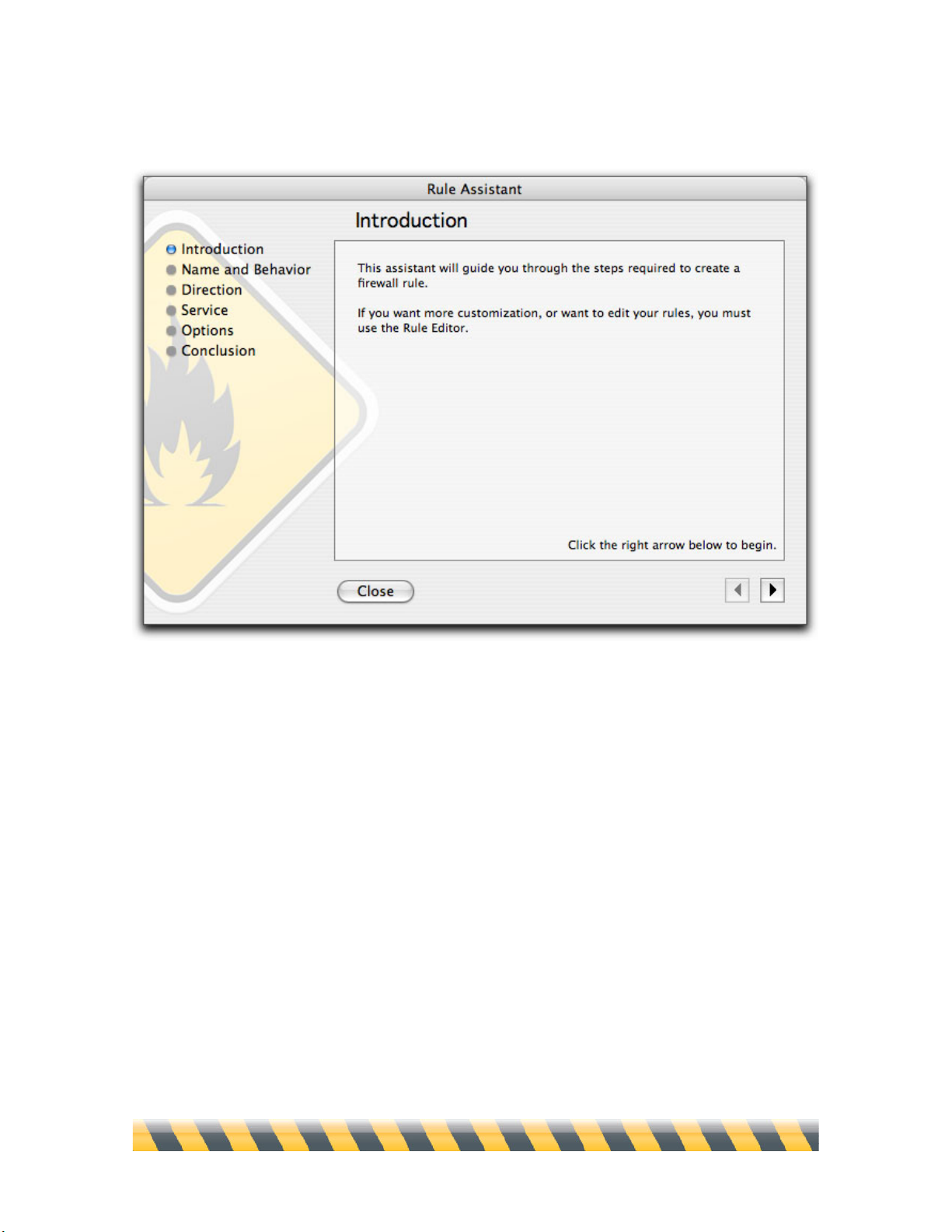
Intego NetBarrier X5 User’s Manual Page 38
The first assistant screen displays.
Click the right arrow to begin creating a new rule. You can click the left arrow at any time to return
to previous screens.
Or click Close to exit the Assistant.
Page 39

Intego NetBarrier X5 User’s Manual Page 39
Name and Behavior
This screen lets you choose a name for your rule and its behavior.
Enter a name for your rule in the name field, then select the behavior for the rule: Allow data or
Deny data. If you select Allow data, the rule will allow data matching its direction and service to
pass. If you select Deny data, the rule will block data matching its direction and service.
Click the right arrow to go to the next screen.
Page 40
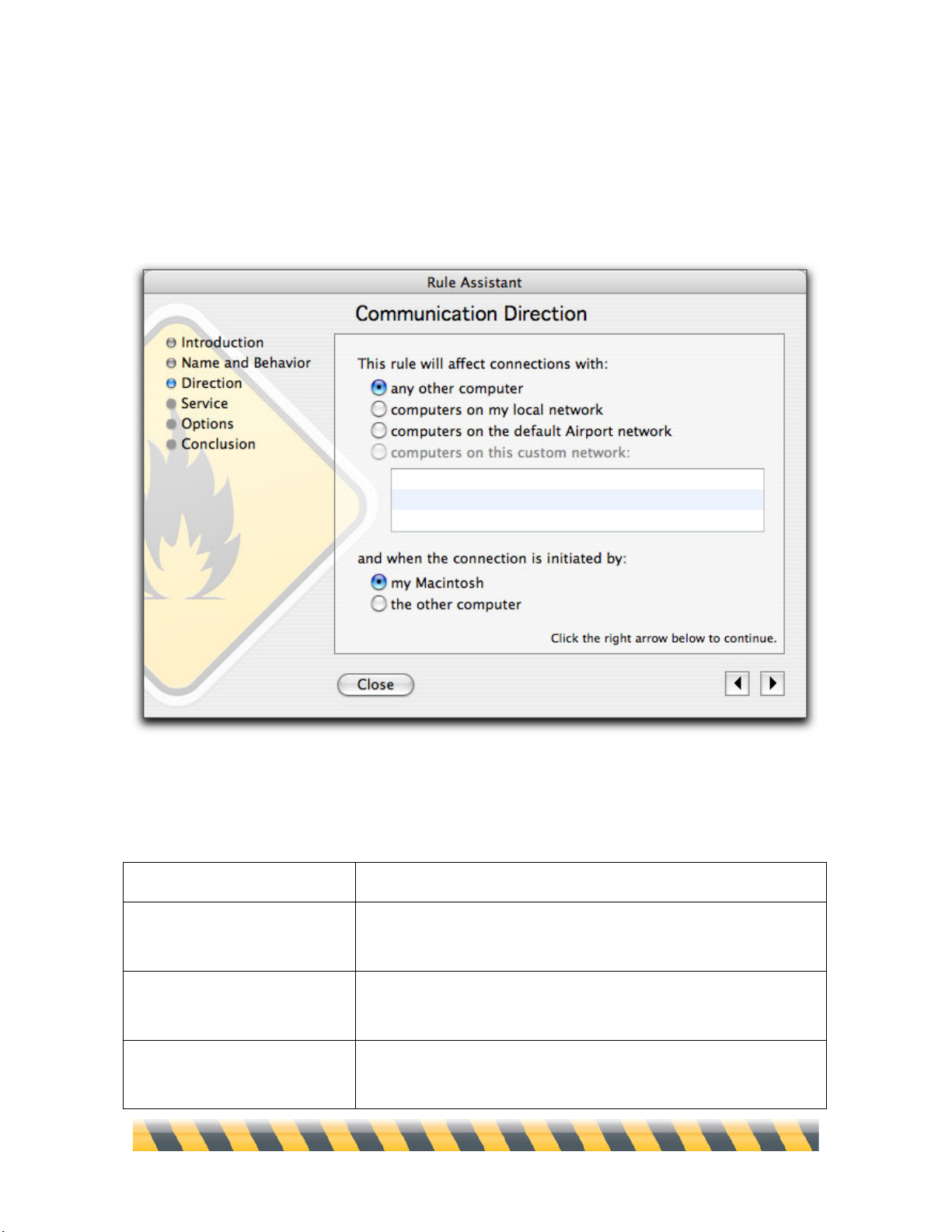
Intego NetBarrier X5 User’s Manual Page 40
Communication Direction
This screen lets you choose the communication direction and which host initiates the
communication.
First, in the This rule will affect connections with: section, select a remote host. You have four
choices for the remote host:
Any other computer
Any computer other than your Macintosh.
Computers on my local
network
Any computer on the same local network as your Macintosh.
Computers on the default
AirPort network
Any computer on your default AirPort network, if you have one.
Computers on this custom
network
If you have created any custom networks using the standard rule
editor, you can select one of them here.
Page 41

Intego NetBarrier X5 User’s Manual Page 41
Next, select the computer that initiates the connection:
My Macintosh
Your Macintosh, the computer using this rule.
The other computer
The remote host, as was defined in the first part of this screen.
When you have finished, click the right arrow to go to the next screen.
Page 42

Intego NetBarrier X5 User’s Manual Page 42
Service
This screen lets you choose the service that the rule affects.
You can choose from three types of services:
All services
All network services.
TCP services (connected
services)
Services that require that a connection be open and maintained
between two computers, such as HTTP, FTP, TELNET, SSH,
POP3, AppleShare, etc. This covers all TCP connections.
This service
You can choose from a list of services that correspond to popular
applications and protocols. Select the service you want to use by
clicking its name in the list.
When you have finished, click the right arrow to go to the next screen.
Page 43

Intego NetBarrier X5 User’s Manual Page 43
Options
This screen lets you choose additional options for your rule.
Two options are available on this screen:
Log rule usage
The firewall records each time this rule is used in its log.
Disable the rule
NetBarrier X5 creates the rule but disables it. You can enable it manually
later.
When you have finished, click the right arrow to go to the next screen.
Page 44

Intego NetBarrier X5 User’s Manual Page 44
Conclusion
This screen creates the rule according to the settings you have selected in the assistant.
This screen offers one final option: if you check Create a rule in the opposite direction, the
assistant creates a matching rule with the source and destination switched.
Click Create to create your rule and exit the assistant.
Page 45

Intego NetBarrier X5 User’s Manual Page 45
When you have finished, you will see that your rule (or rules, if you checked Create a rule in the
opposite direction) displays in the NetBarrier X5 list of firewall rules.
If you wish to further customize the rule, or edit it, see below, Editing Rules.
Page 46

Intego NetBarrier X5 User’s Manual Page 46
Creating Service-Specific Rules Quickly
There are two ways to quickly create rules to control information to and from common services and
programs. The first is by clicking the + button at the bottom of the Rule list and holding your mouse
button down for a second. You’ll be able to choose from a popup list of the most common services.
A rule governing your selection then appears in the Rules list.
The second way to quickly create service-specific Rules is through the Services Library. To display
the Services Library, choose Window > Services Library, or press Option-Command-S.
Page 47

Intego NetBarrier X5 User’s Manual Page 47
The Services Library window opens and displays a list of the most common services.
To create a new rule, select the desired service and drag it to the rule list. By default, rules added in
this way allow all traffic from your Mac to the Internet, on all interfaces. In other words, the rule
doesn’t prohibit any activity until you edit its settings, as is described below.
Page 48

Intego NetBarrier X5 User’s Manual Page 48
Creating Rules Manually
You can also create individual rules using the Rule Editor. Click the + button at the bottom of the
list of rules and the Rule Editor displays.
NetBarrier X5’s Rule Editor allows network administrators to quickly and easily define and
implement a comprehensive security policy. It is extremely flexible, and allows you to define an
unlimited number of rules in seconds. To create a rule, you need to specify details in six areas:
• Rule Name, Logging and Schedule
• Rule Source
• Rule Destination
• Rule Service
• Rule Interface
• Rule Action
Page 49
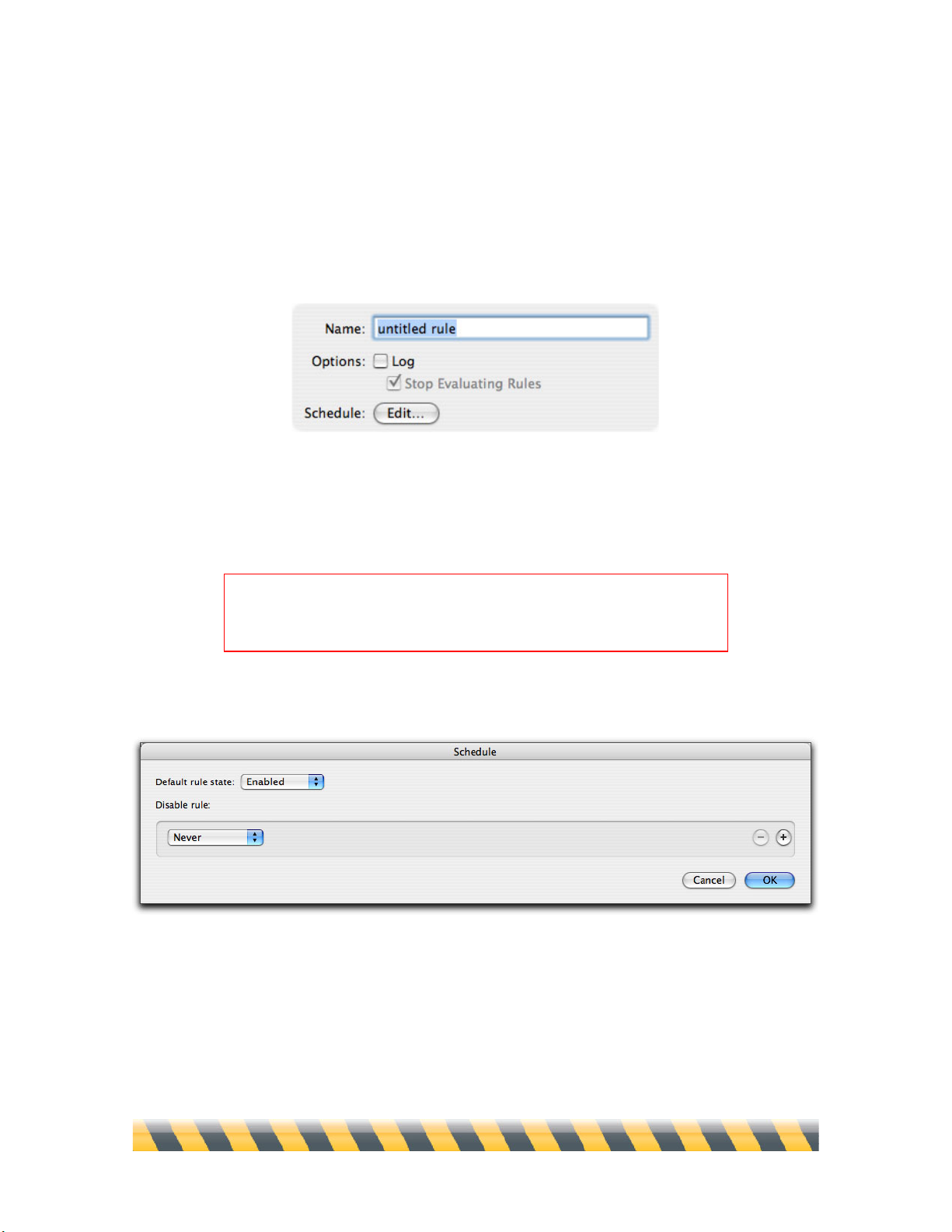
Intego NetBarrier X5 User’s Manual Page 49
Rule Naming, Logging, Evaluation and Schedules
At the top of the Rule Editor is a field where you can name this rule. Just below it is the Log
checkbox. If you check the Log box, an entry is added to the NetBarrier X5 log any time this rule
acts; a small red dot to the right of the rule’s name in the Rules list indicates that the rule is logged.
If it is not checked, this rule is not logged.
If the Log checkbox is checked, the Stop Evaluating Rules checkbox will be available, and is
checked by default. These two settings, in tandem, are a powerful way to troubleshoot a network
without hampering its traffic.
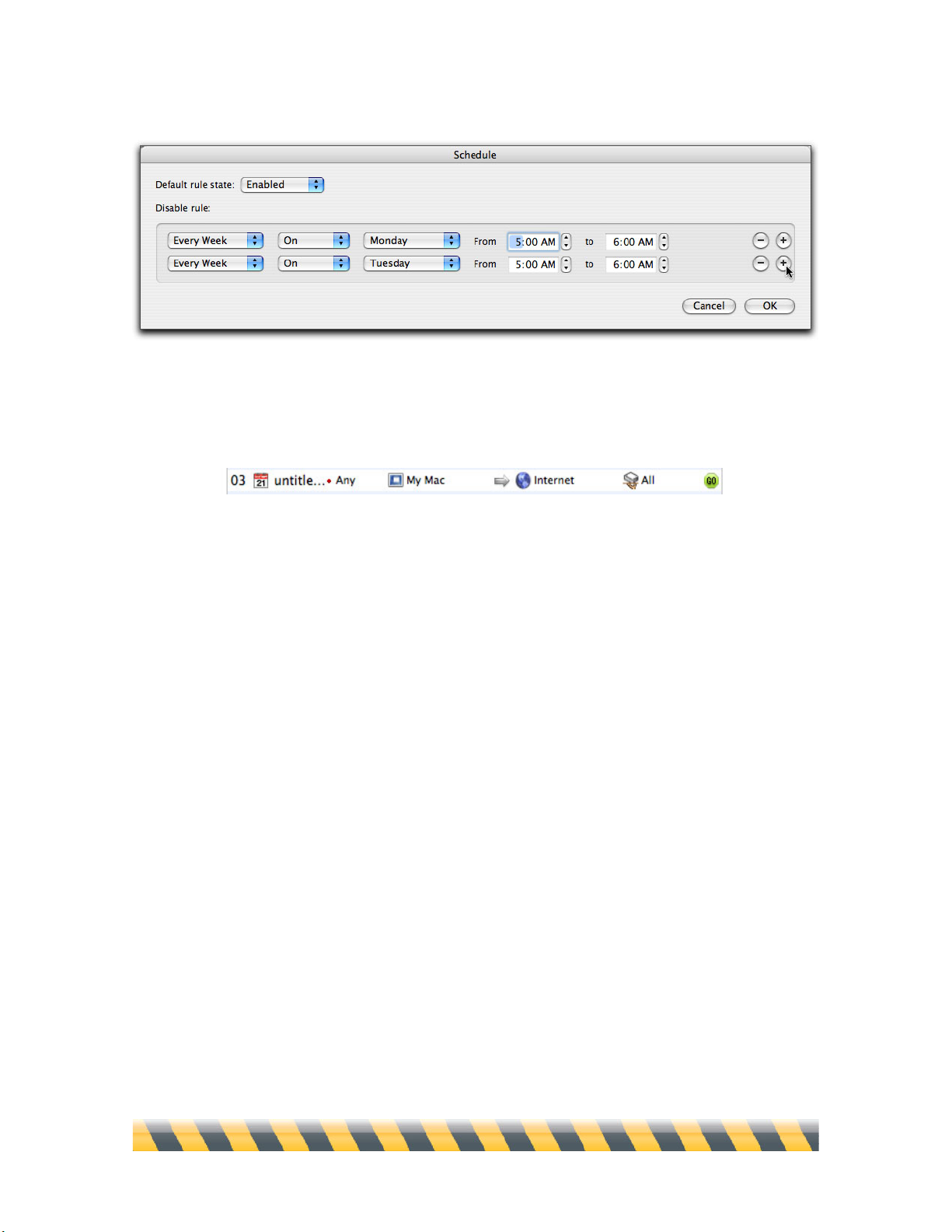
To edit the Schedule, click the Edit… button. The Schedule window displays.
The Default rule state is set to Enabled, which means that your rule is activated. If you set it to
Disabled, NetBarrier X5 does not use this rule. You may want to have certain rules active in one
configuration, and not another. For more on using configuration sets, see chapter 10, Preferences
and Configurations.
WARNING: If you can’t figure out why some of your rules aren’t
taking effect, look at the rules above it and ensure that the “Stop
Evaluating Rules” checkbox is off for each of them.
Page 50
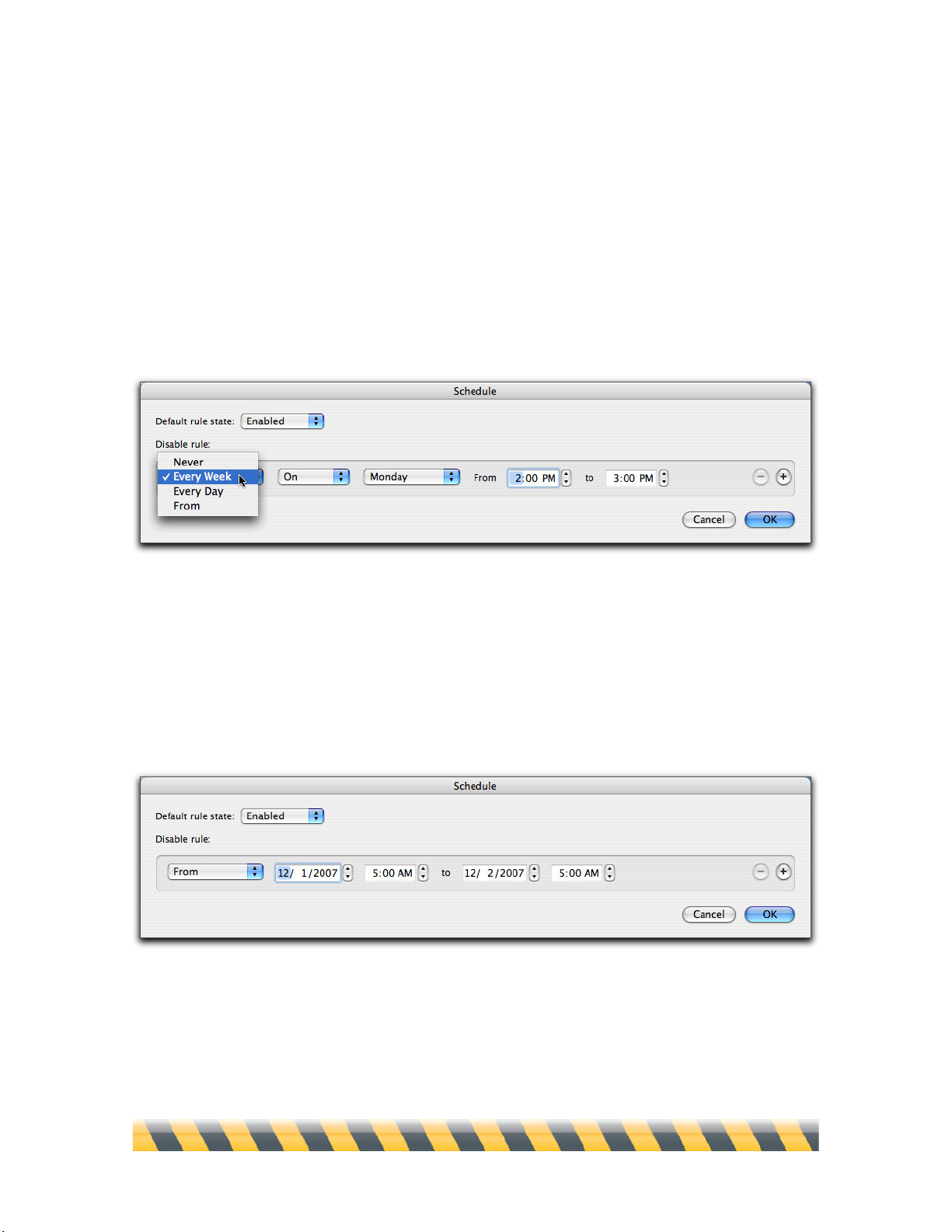
Intego NetBarrier X5 User’s Manual Page 50
If your default rule state is enabled, you can set specific times for the rule to be disabled. If your
default rule state is disabled, you can set specific times for the rule to be enabled.
When you first create a rule, the Default rule state is set to Enabled and the Disable rule menu is set
to Never. In other words, if you make no other changes, the rule will always be active. If you wish
to have the rule enabled or disabled at certain times, click the popup menu for either Enable rule or
Disable rule, depending on which Default rule state you have chosen, and select one of the time
intervals in the list.
Three options are available in addition to Never. Every Week and Every Day allow you to disable
or enable the rule on a recurring basis at fixed times every week or every day, or on specific days of
the week. The third option, From, allows you to disable or enable the rule for a specific period of
time. In this case you must set the date and time at which you want the rule to start being active in
the From field. Set the date and time that you want the rule to expire in the to field.
You can schedule additional times for rules to be enabled or disabled using the + button. For
example, if you need a rule to be disabled only on Mondays and Tuesdays, you can set these two
days in the Schedule window. To remove a scheduled time from the list, click the – button next to
the time line.
Page 51
Intego NetBarrier X5 User’s Manual Page 51
Scheduled rules are displayed with a calendar icon in the rule list. This particular rule also has
logging turned on, as is indicated by the small red dot next to its name.
Page 52
Intego NetBarrier X5 User’s Manual Page 52
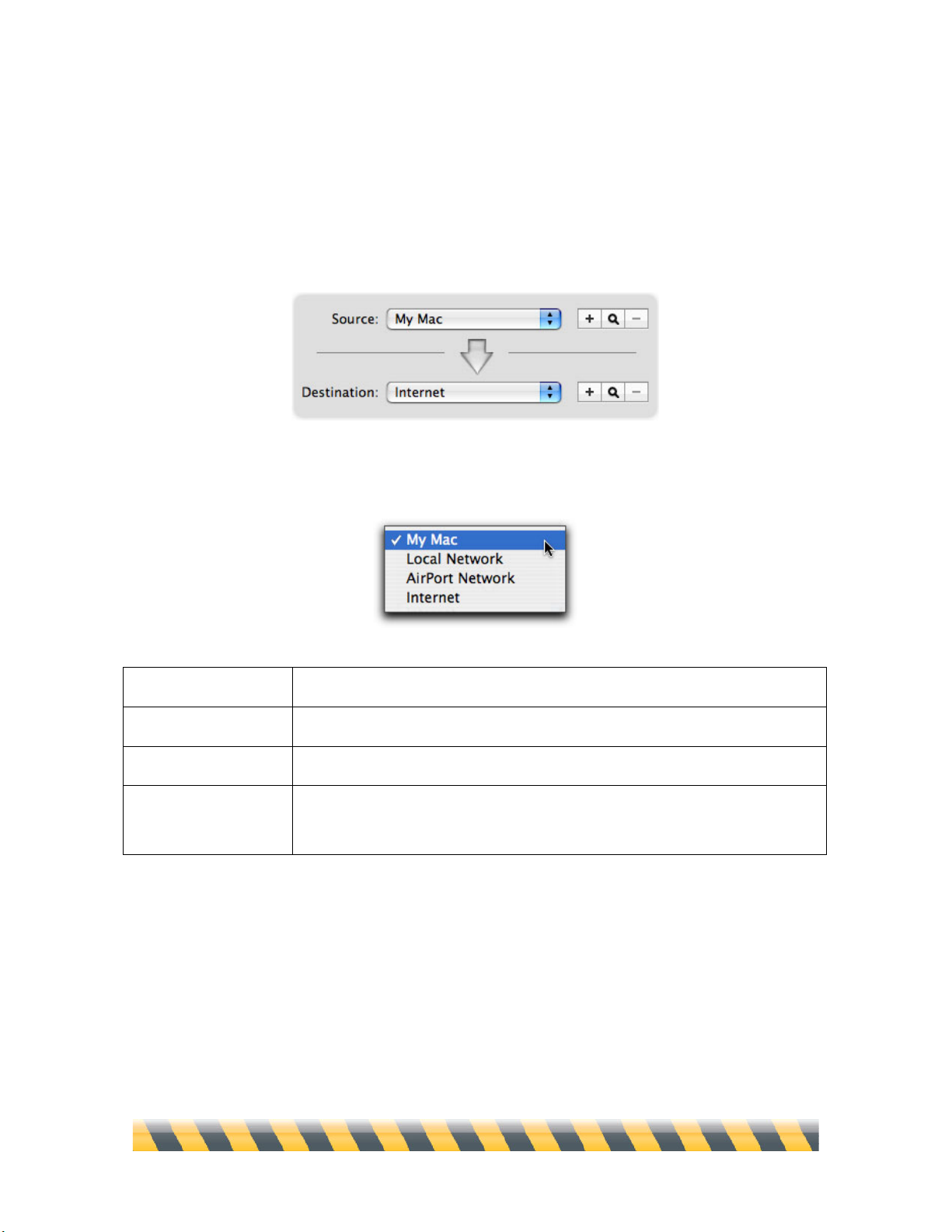
Rule Sources and Destinations
When defining rules, the Source is the entity that sends data; the Destination is where the data goes.
You can choose from a list of four sources and destinations for any rule. However, NetBarrier X5
will not allow you to choose the same source and destination for a given rule.
These four Sources and Destinations are available by default:
My Mac
Your computer.
Local Network
A local network that your computer is connected to.
AirPort Network
A wireless AirPort network that your computer is connected to.
Internet
The Internet, in addition to any local network you may be connected to;
effectively, all networks.
Page 53
Intego NetBarrier X5 User’s Manual Page 53
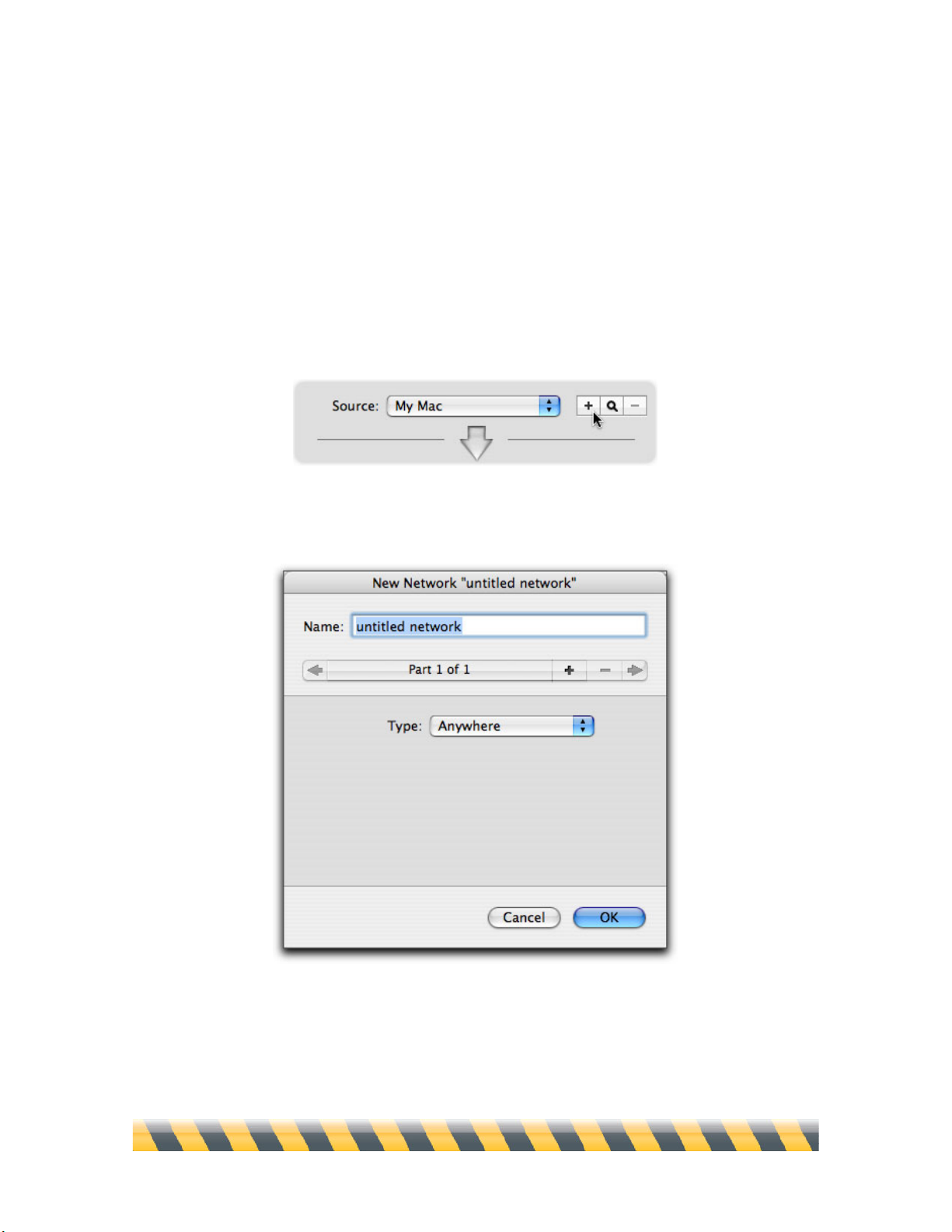
Creating New Sources and Destinations
You can create new sources and destinations to use in your rules. This allows you to specify exactly
which computers you wish to have your Mac communicate with.
To create a new source, click the + button to the right of the Source or Destination popup menu. In
our example, we’ll create a new Source; however, once it’s created, it will also show up in the list
of possible Destinations.
The New Network editor displays.
Enter a name that will help you remember the network. If, for example, you’re blocking IP
addresses whose last octet is in the range of 100-155, you might name the Source/Destination “IPs
from 100-155”.
Page 54

Intego NetBarrier X5 User’s Manual Page 54
The pop-up menu offers a selection from seven types of network.
Name
Definition
Address Type
Anywhere
Any network.
None, as this source covers all networks.
My Mac
Your computer.
The IP address(es) of your Mac displays in the
Address field, and cannot be changed.
My local network
The local network
your computer is
connected to.
The IP address(es) of your Mac and subnet mask
of your local network display in the Address field,
and cannot be changed.
Machine
A specific IP address.
Any IP address. If you enter a domain name,
NetBarrier X5 will resolve it to a single IP
address.
Network
A specific network.
Any Subnet IP address and Subnet mask. As
above, NetBarrier X5 will resolve domain names
to a single IP address.
Address Range
A group of IP
addresses.
Beginning and ending addresses. NetBarrier X5
will resolve domain names to a single IP address.
Ethernet ID
A single device
connected to the
network by Ethernet.
An Ethernet ID, as six two-character hexadecimal
numbers.
Page 55

Intego NetBarrier X5 User’s Manual Page 55
Rule Services
“Service” refers to a combination of protocol type, port (or ports) used, and protocol-specific
criteria. These items, taken together, typically describe a program or class of program that sends and
receives information. For example, information sent by the TCP protocol over port 80 using HTTP
would be a Web service.
NetBarrier X5 comes with over 50 common services preprogrammed so you can easily stop (or
allow) traffic that appears to be of a specific type.
While most preprogrammed Services clearly map to a specific program, some selections in this list.
such as “Web” pertain to a class of communications instead. Here are some of those non-specific
Services:
Page 56
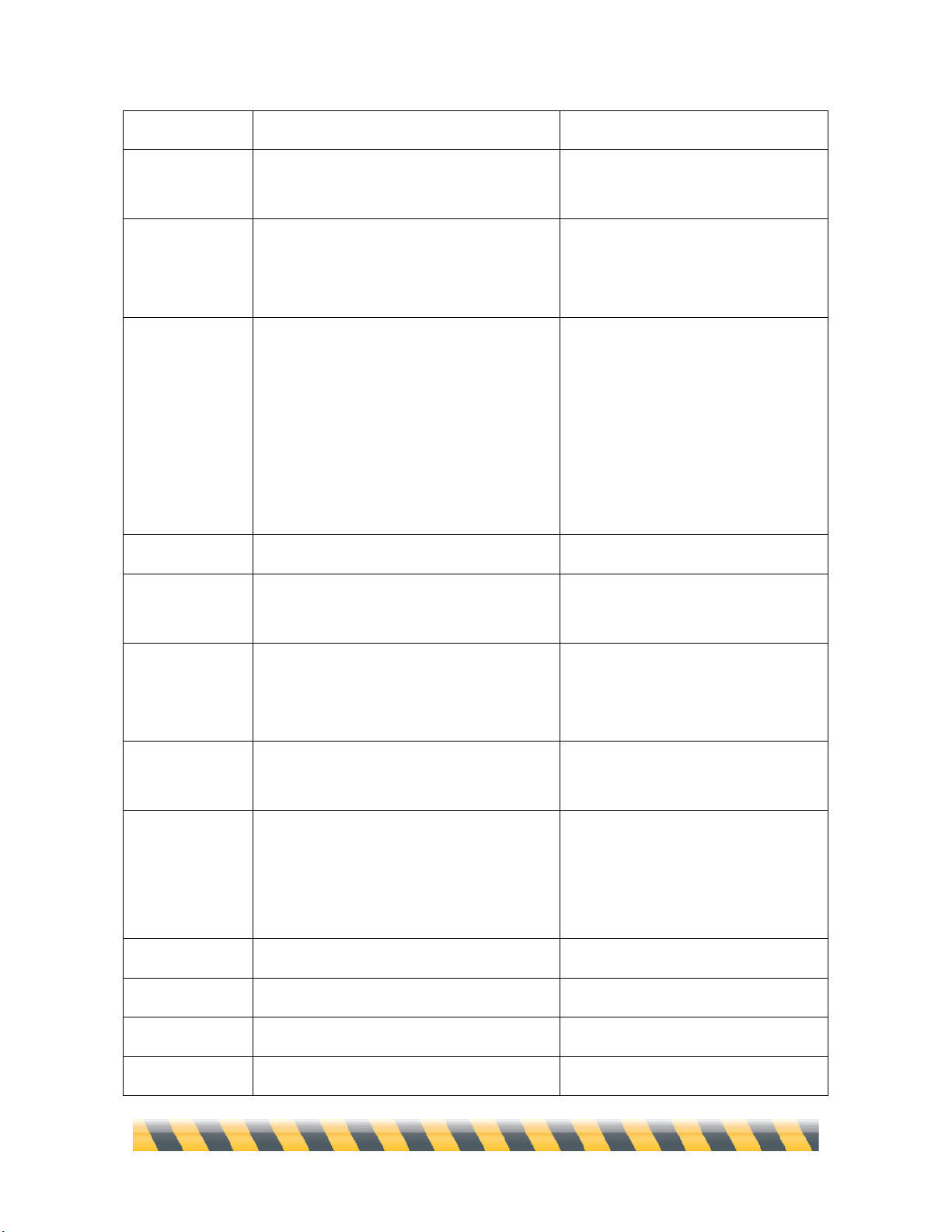
Intego NetBarrier X5 User’s Manual Page 56
Name
Description
Settings
All
All communications, regardless of
protocol or port.
All protocols, on all ports.
Apple Remote
Desktop
A program that allows an administrator
Mac to control another Mac over a
network connection.
Port 3283 over UDP.
Connected
Services
All TCP communications. A TCP session
maintains a connection between
computers, so it’s always clear that it was
initiated by the Mac and can therefore be
trusted. By comparison, a UDP session is
a series of communications without a
“memory” of who initiated it.
All TCP communications, on any
port.
FTP
File Transfer Protocol.
TCP, ports 20 or 21.
iChat AV
An instant messaging program with video
and sound.
Port 5060 over UDP.
IRC
Internet Relay Chat.
TCP on port 194 for IRC, and all
TCP traffic between ports 6665 and
6669, inclusive.
iTunes Music
Sharing
A way to share your iTunes music library
over your local network.
Port 3689 over TCP.
Mail
E-mail communications.
TCP port 25 for SMTP, port 110 for
POP3, port 143 for IMAP4, port
220 for IMAP3 port 389 for LDAP,
and ort 587 for message submission.
NTP
Network Time Protocol.
UDP on port 123.
SSH
Secure Shell.
TCP on port 22 using SSH.
Telnet
Remote login.
TCP on port 23 using telnet.
VNC
Virtual Network Computing, a graphical
TCP on ports 5900-5999.
Page 57
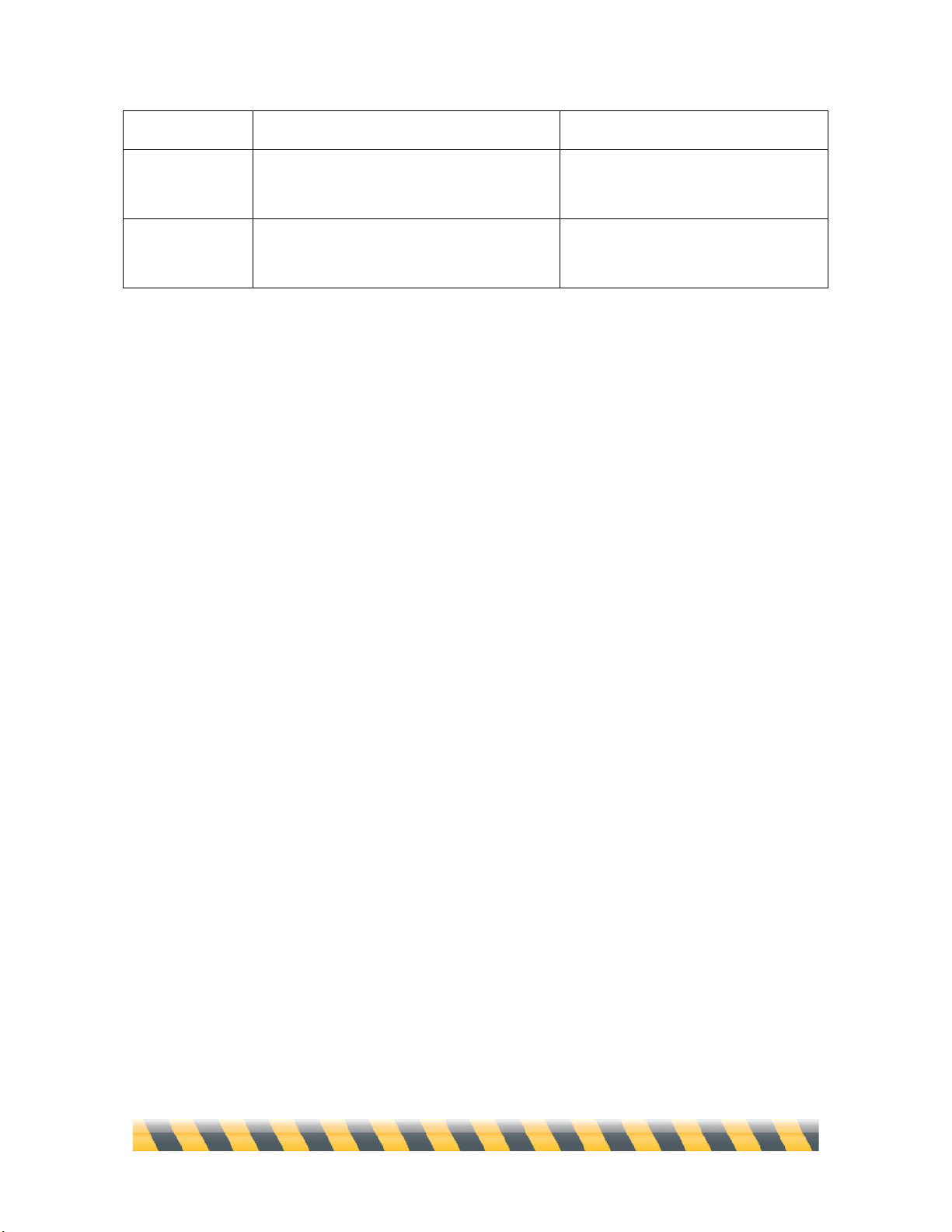
Intego NetBarrier X5 User’s Manual Page 57
remote-control system.
Web
Web browsing, for example through a
browser such as Firefox.
TCP on ports 80 and 8080 through
HTTP, and on port 443 on HTTPS.
Well-Known
Ports
A large range of ports with long usage
traditions in network communications.
TCP and UDP on all ports from 0 to
1023.
The remaining services are for specific programs or protocols.
Be careful when creating rules for specific services. When you select a service for a specific
program, it is possible that this program uses the same port as another program or service. Blocking
or authorizing a specific service may conflict with other, more general rules. For example, if you
wish to block ICQ traffic, selecting ICQ as a service will also block AOL Instant Messenger traffic
since both programs use the same port. Other programs may also use the same ports. If you find that
you cannot connect to a given service, or send or receive traffic, try deactivating your rules one by
one to see if there is a conflict.
Page 58

Intego NetBarrier X5 User’s Manual Page 58
Creating New Services
Four different protocol suites are available from the pop-up menu: TCP, UDP, ICMP and IGMP.
You can also select Any, which covers all protocols.
When you select one of these protocol suites, additional options display in the bottom section of the
panel, with a list of services that you can select from. The options depend on the protocol you have
selected. For more information on these protocols and services, see chapter 12, Glossary.
Protocol
Port selections
Options
Any Port
No additional options
Single Port
(Popup menu has over 100 options.)
TCP or UDP
Range of Ports
Any
No additional options
ICMP or IGMP
Specific Type
(Popup menu has over 20 options.)
For each of these, an option is available to Allow Broadcast Packets. If checked, packets sent to all
computers on a local network are included in this service.
Page 59

Intego NetBarrier X5 User’s Manual Page 59
Destination Port is a final option, available only for services utilizing the UDP protocol. If it is
checked, packets are filtered according to the function of the Destination Port. If left unchecked,
packets are filtered according to the function of the source Port.
Page 60

Intego NetBarrier X5 User’s Manual Page 60
Rule Interfaces
The Interface is the network adapter that the data passes through. This can be an Ethernet card, a
wireless AirPort card, a PPP connection or any other type of network interface. You can choose
from a list of preprogrammed interfaces that exist on your computer, or you can create your own
interfaces.
The Type pop-up menu has two options. The first, Any, uses all available network interfaces. The
second, Specific, lists those interfaces that are available to you, depending on your computer’s
hardware and software. Typical interfaces are:
Airport
Wireless networking
Built-in Ethernet
Wired interface commonly used
for networking
Built-in FireWire
Wired interface commonly used
for peripherals
The BSD Name and Index number are the identifiers used by the Unix layer of Mac OS X. You
can set these manually, if you need to. If other interfaces are present in your Mac, an Other option
will also be available.
Page 61

Intego NetBarrier X5 User’s Manual Page 61
Rule Actions
Two actions are possible for any rule: Allow or Deny. Select the action you wish to use for your
rule by checking the appropriate radio button, at the bottom of the Rule Editor window.
Finally, click OK to add this rule to your NetBarrier X5 firewall rules.
Multi-Part Sources, Destinations, Services and Interfaces
Rule sources, destinations, services and interfaces can have several parts. You can, for example,
dictate that traffic from several specific IP addresses be banned, listing each one separately in a
given Source.
When you create or edit a source, destination, service or interface, you see a bar at the top of the
window that looks like this:
Create a new part
Click the + button.
Move among parts
Click the arrow icons. Note that the text in the middle will tell you
where you are, and how many parts exist in total. When you reach
the last part, clicking the right arrow takes you back to the first one.
Delete a part
To delete a part, it must be visible. Click one of the arrow icons until
the part you wish to delete is displayed. Click the – button, then
confirm the deletion in the dialog box that follows.
Page 62

Intego NetBarrier X5 User’s Manual Page 62
Deleting Sources, Destinations, Services and Interfaces
You can delete any sources that you have created. To do so, select the source, and then click the –
button.
A dialog box displays, asking if you really want to remove that network. Click Remove to delete the
source network, or Cancel if not.
Page 63

Intego NetBarrier X5 User’s Manual Page 63
Working with Rules
Rule Order
Rules you add to NetBarrier X5’s firewall are enacted from first to last, so you need to make sure
that your rules are in the correct order to function properly.
In this example, the first rule blocks data coming from the Internet (which includes all networks,
even a local network). Rule 3, however, allows traffic from a local network, but since it is in 3rd
position, it is not applied; the 1st rule takes precedence. For rule 3 to be applied, it needs to be
moved to the top of the rule list. To do this, select the rule and drag it to the appropriate position.
Editing and Deleting Rules
To edit a rule, select the rule by clicking it, then click the button with the pencil icon at the bottom
of the list. The Rule Editor will open, and you can make any changes you want to this rule. When
you have finished making changes, click OK to save your changes. If you decide you do not want to
save the changes, click Cancel.
To delete a rule, click the rule in the list of rules, then click the – button at the bottom of the list.
Page 64

Intego NetBarrier X5 User’s Manual Page 64
Using the Rule Contextual Menu
NetBarrier X5 lets you make changes to Firewall Rules quickly through a contextual menu. You
can use this contextual menu to add new rules, to edit existing rules, or to change rule
characteristics on the fly.
To see this contextual menu, hold down the Control key and click on a rule. (If you have a two-
button mouse, you can just click the right button of your mouse.)
The menu offers the following options:
Copy to Clipboard
Copies the contents of a Rule to the Mac’s Clipboard in plain-text
format. You can then paste the rule into a document, where it will
look something like this: “#02/ON/Input/Any/Internet -> My
Mac/All/Deny” (where slashes are tabs).
Insert Standard Set / Add
Standard Set
Insert or add a standard set of rules, from the same selection as is
found in simple mode: No restrictions, No network, Client, Local
Server, Server only, or Client only.
Status
You can toggle the state of a rule, turning it On or Off. If the rule is
scheduled to run at certain times, a check mark is displayed next to
Scheduled in the submenu.
Behavior
Toggle the behavior of a rule between Allow or Deny traffic.
Log
Toggle whether the rule records traffic information in the log.
Page 65
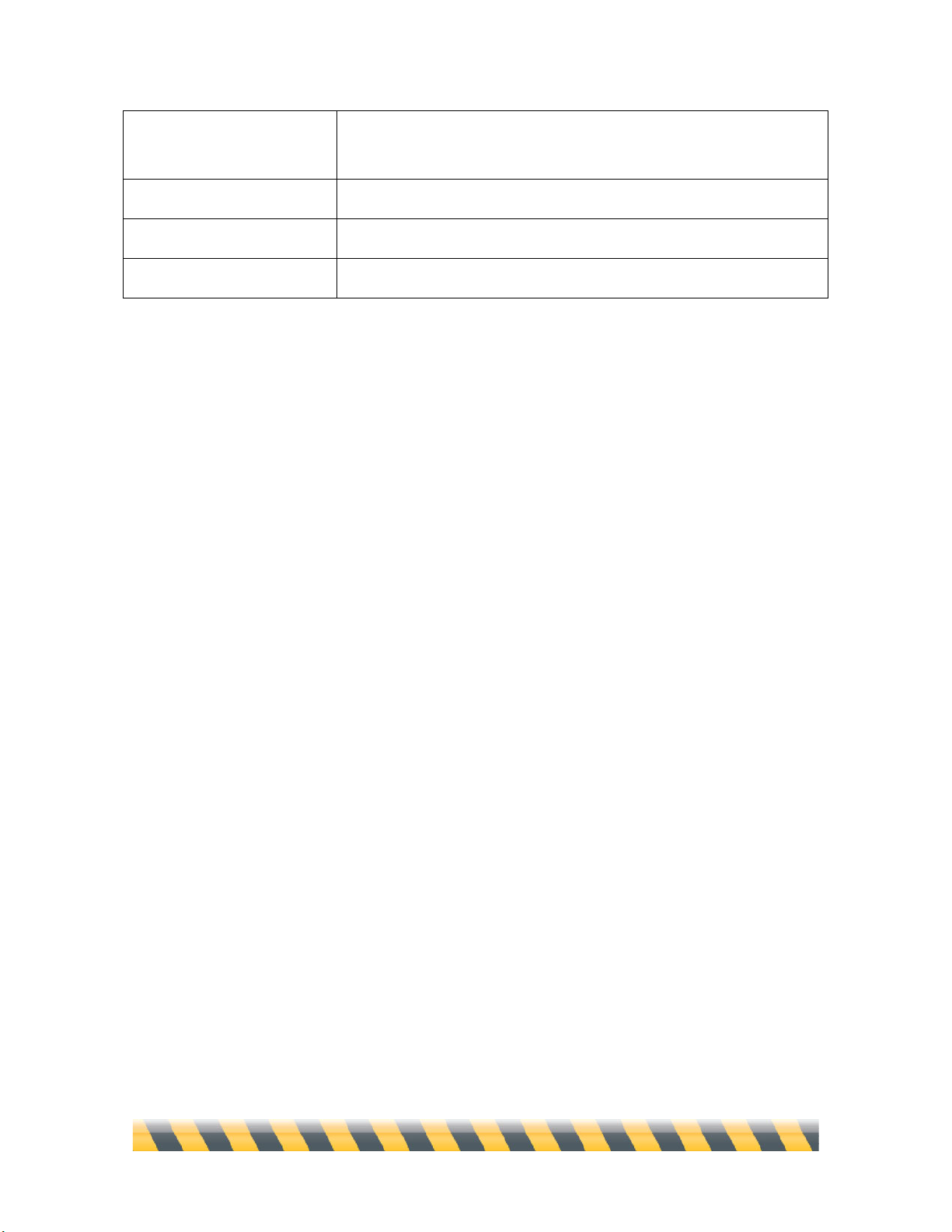
Intego NetBarrier X5 User’s Manual Page 65
Switch Source &
Destination
“Reverses” a Rule, exchanging the source and destination.
Duplicate
Makes a new copy of the Rule.
Edit...
Opens the Rule Editor for the indicated Rule.
Remove...
Deletes the Rule.
Page 66

Intego NetBarrier X5 User’s Manual Page 66
Trojan Horse Protection
Trojan horses are applications that are surreptitiously installed on your computer, either by virus-
laden attachments you receive with e-mail messages, or by programs you download or buy on disc.
In some cases, programs install a specific type of Trojan horse, known as spyware, which sends
personal information to a server. Since the connection is made from your computer, it is generally
trusted. But NetBarrier X5 knows how to spot the actions of the most common Trojan horses and
stop them in their tracks. There have been cases where such programs have sent information about
users’ browsing habits to a central server; other Trojan horses open “back doors” in your computer
that allow hackers to take control of it or delete files.
To turn on Trojan horse protection, click the Protect against Trojan Horses checkbox, then click the
checkboxes of individual Trojans to select them. The Enable All and Disable All buttons at the
bottom are handy shortcuts that select or deselect all checkboxes at once.
Page 67
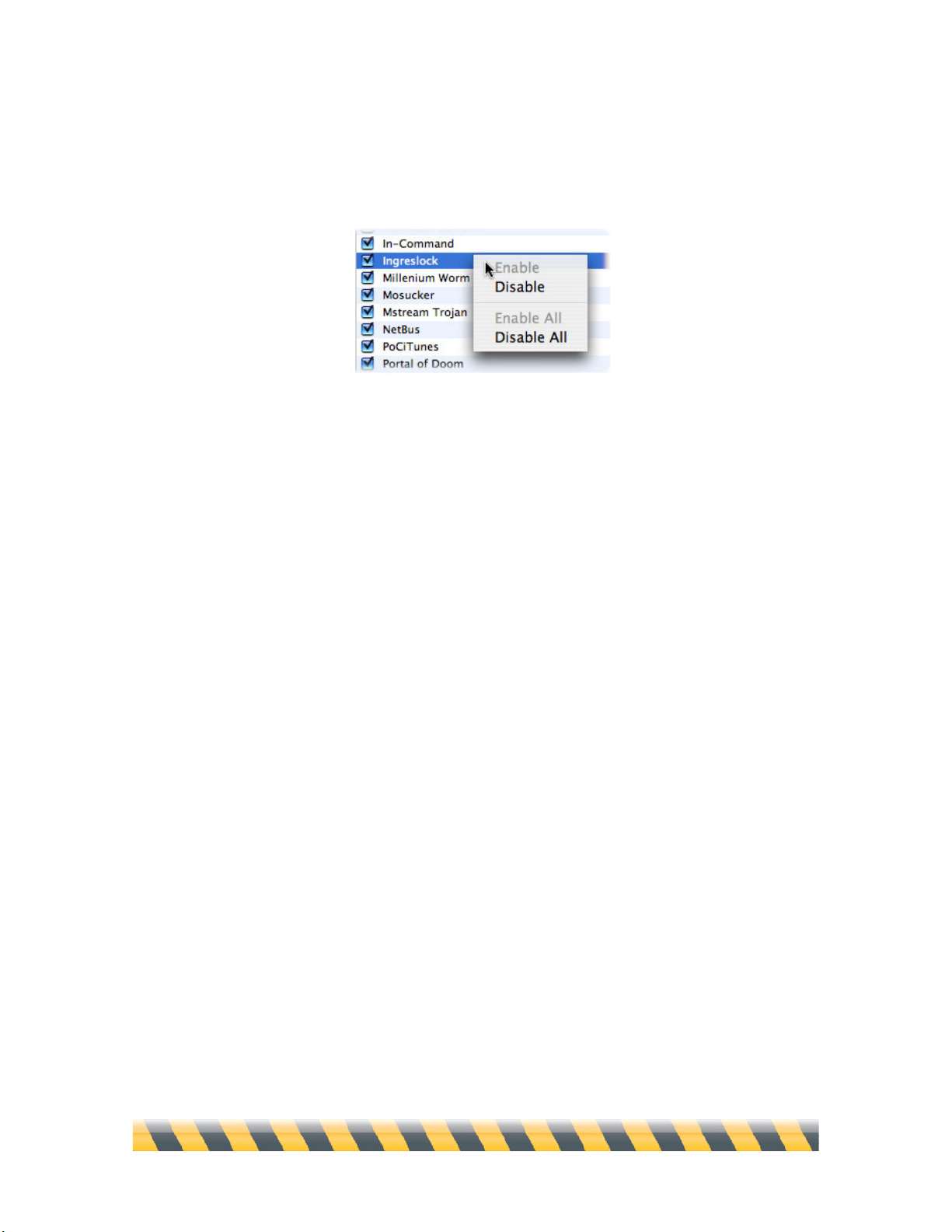
Intego NetBarrier X5 User’s Manual Page 67
You can also enable Trojan blocking for an individual Trojan horse, or for all Trojan horses, by
holding down the Control key on your keyboard and clicking on the name of a Trojan. A contextual
menu displays.
Page 68

Intego NetBarrier X5 User’s Manual Page 68
6—The Four Lines of
Defense: Privacy
Page 69
Intego NetBarrier X5 User’s Manual Page 69
NetBarrier X5’s privacy filters examine both incoming and outgoing packets, looking for specific
types of data. There are several filters, separated into two sections: Data, and Surf.
Data Filter
The data filter ensures that any sensitive information you choose to protect cannot leave your Mac
and go onto a network. You decide what to protect—your credit card number, passwords, or key
words that appear in sensitive documents—and NetBarrier X5’s data filter checks each outgoing
packet to make sure that no documents containing this information are sent. Not only does this
protect you from accidentally sending documents containing this information, but it also protects
against anyone who has network access to your Mac from taking copies of them.
Remember that, if your computer is accessible across a network and other users have file-sharing
privileges, they may be able to copy your files.
Page 70
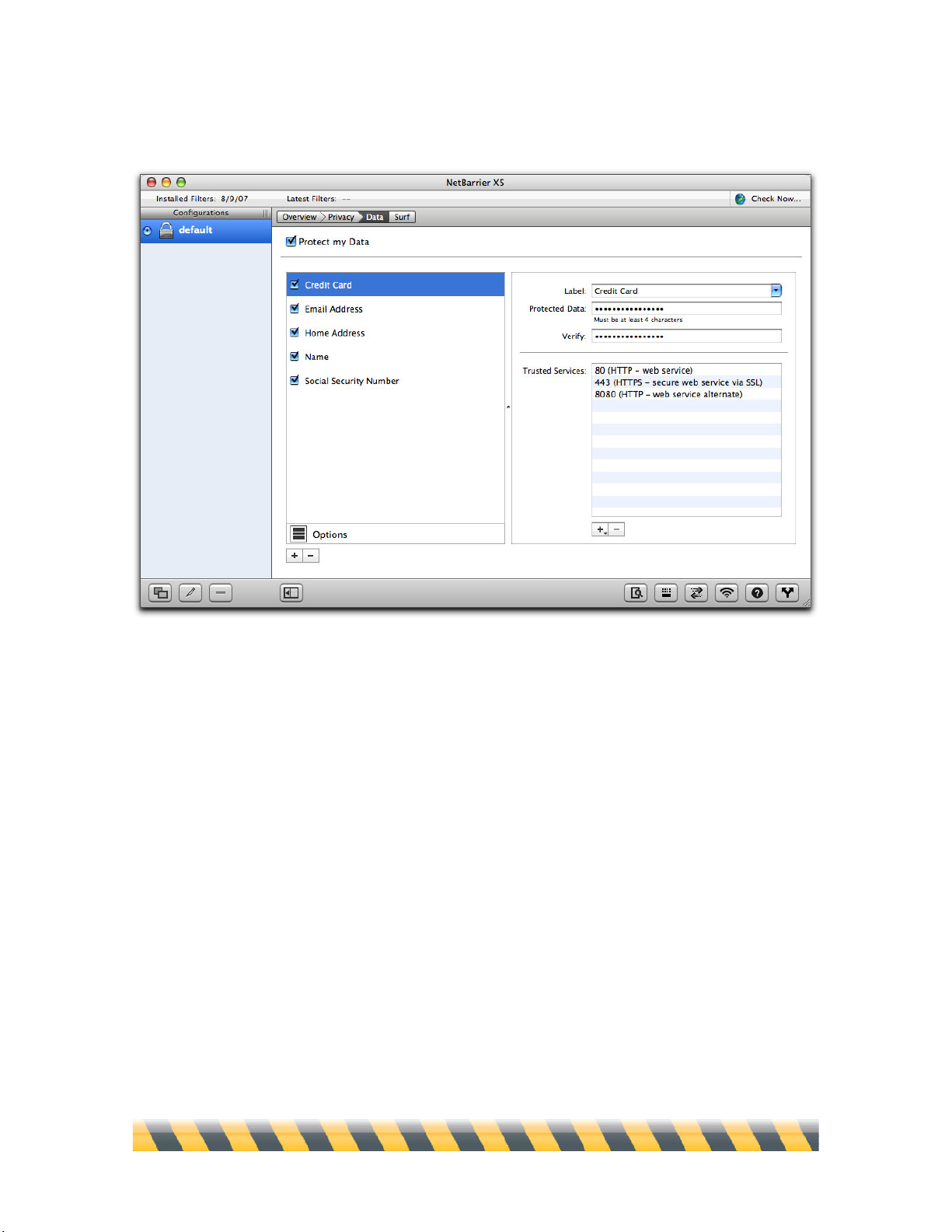
Intego NetBarrier X5 User’s Manual Page 70
Here is the data filter window with some sample data in place:
How the Data Filter Works
NetBarrier X5 examines all data packets that are sent from your computer to the Internet or a local
network. If any of the data you indicated in the filter is found, the packet is blocked.
The data filter only blocks data that corresponds exactly to the text you indicated, including
punctuation and case. For example, if you entered your credit card number as protected data,
NetBarrier X5 prevents it from leaving your computer and can warn you in several ways if you
choose. But if you enter the same number in a secure web page, your browser encrypts this number.
The data therefore no longer corresponds to the protected data, and is sent. The same is true for data
that is encoded in other manners, or compressed.
In extremely rare instances, the data filter stops data that matches your criteria but not your
intention. For example, graphic files (such as images on web sites) are essentially just strings of
data thousands of characters long. It’s possible that a graphic file could coincidentally contain a
Page 71

Intego NetBarrier X5 User’s Manual Page 71
piece of data you want protected, and would therefore be blocked by the data filter. (If you decided
to block the name “Jodie”, for example, a graphic file containing the string
“Cg34gb$sEbOJodie8%” would be stopped.) If you find yourself unable to send or receive a
specific piece of information, try turning off the data filter momentarily, then turn it on after the
information has been transferred.
Click the “Protect my Data” checkbox in the upper-left corner to enable the data filter. You can turn
it off at any time, for example to temporarily allow your protected data to be sent.
What to Protect
The data filter includes labels for the five most common types of sensitive information:
• Credit Cards
• E-mail Addresses
• Home Addresses
• Name
• Social Security Number
However, these labels are merely for convenience. NetBarrier itself doesn’t treat these types
differently from one another, or differently from any additional types you might decide to enter
later—for example, “Phone Number”, “Children’s Names” or “Passwords”.
Page 72
Intego NetBarrier X5 User’s Manual Page 72
Adding Data to the Filter
To add data to the filter, click the + button below the Options icon. A new entry named “untitled
data” appears in the filter list.
Enter a description for your protected data in the Label field, or choose it from the popup menu:
you’ll notice that it is echoed in the filter list. Then enter the actual data you wish to protect in the
Protected Data field. This text is hidden so nobody watching over your shoulder or with later access
to your Mac can see it. You must enter the data a second time in the Verify field. If the Protected
Data and Verify fields do not match, a window displays, giving you the choice of either resetting
the protected data, in which case you will have to retype both data fields, or clicking OK. If you
click OK, you will have to retype the verified protected data.
You must enter your text exactly as it will be found in your documents for the filter to protect it. For
example, a credit card number may be found as ####-####-####-#### or as #### #### #### ####.
If you protect only the first example, the filter does not look for the second one. Also, this data is
case sensitive. If you need to protect a key word, such as a project name, you must enter it in all
possible cases: i.e., Marketing Study, marketing study, MARKETING STUDY.
Page 73
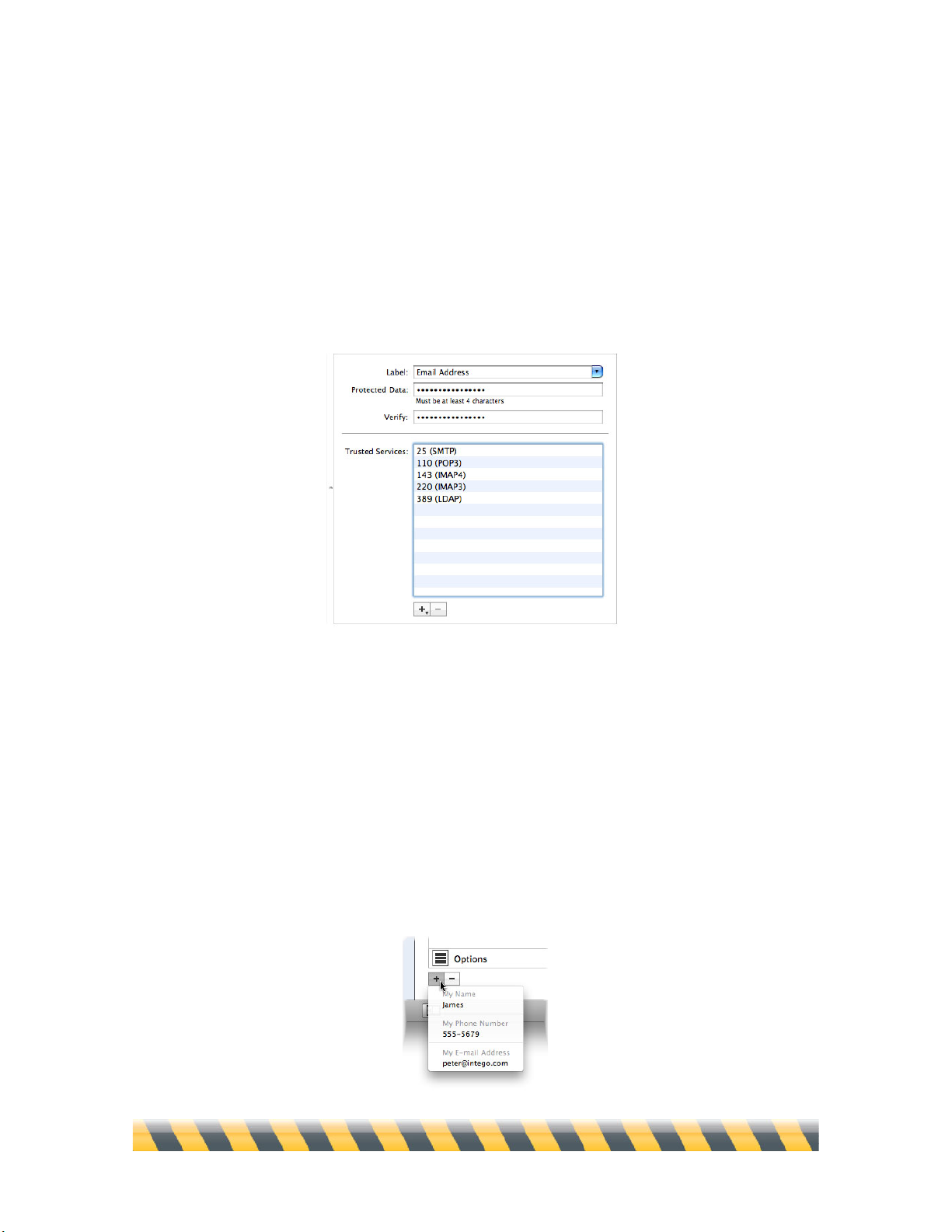
Intego NetBarrier X5 User’s Manual Page 73
The Trusted Services section allows you to choose to block data for all but the selected services. To
do this, click the + button. Then, type the port number of the service. Alternately, click the + sign
and hold the mouse button down for a few seconds: you’ll be able to choose from a popup list of
common services. (Some of them, such as Mail in the example below, add several ports in one go.)
You can add a single port number, or a range of port numbers, for example 110-123. Data to this
port (or these ports) will not be blocked. To add another service, repeat the above operation. You
can add as many services as you wish.
You can also drag and drop services from the Services Library. This is particularly helpful if you do
not know the specific port numbers you wish to add to the list. To display the Services Library,
choose Window > Services Library, or press Option-Command-S. Select the desired service, then
drag it onto the Trusted Services list.
You can also add certain personal information from your card in Apple’s Address Book, if you have
filled one out. To do this, click and hold the + button, and you’ll see three items: My Name, My
Phone Number and My E-mail Address. Select one of these to add it as protected data.
Page 74

Intego NetBarrier X5 User’s Manual Page 74
Once you have finished entering this information, your data is protected. You can go back at any
time to edit the data item by clicking on it in the Data Filter list and changing information in its
pane to the right.
Page 75

Intego NetBarrier X5 User’s Manual Page 75
Activating, Deactivating and Deleting Data Items
Each item of protected data appears on a line in the data filter window. A checkbox at the left of
each line allows you to activate or deactivate the filter for each data item. When you add a new data
item, the box is checked, indicating that the filter is active for this item. If you wish to send that data
over the Internet or a local network, you must uncheck the checkbox for the item in question, or
deactivate all the data filters by unchecking “Protect my Data” as was mentioned earlier.
You can also activate or deactivate Data Filters for individual protected data items, or for all
protected data items, by holding down the Control key on your keyboard and clicking the name of a
data item, or by clicking with your right mouse button. A contextual menu displays.
Select Disable to disable protection for the selected data item, or select Disable All to disable
protection for all data items. (If the selected item in the above example had been disabled already,
the choices for Enable and Enable All would be available.)
If you’d like to permanently remove the item from the Data Filter list, either Control-click as
described above and choose Remove..., or select the data item and click the – button. In either case,
a dialog box asks you to confirm that you really want to remove the data item.
Page 76

Intego NetBarrier X5 User’s Manual Page 76
Data Filter Options
When protected data attempts to enter or leave your Mac, you have several options on how you’re
notified, and what to do about future attempts. To see these options, click the Options button in the
lower-left of the data screen. Changes to data filter options affect all data filters.
To understand these options, see chapter 9, Understanding Alerts.
Page 77

Intego NetBarrier X5 User’s Manual Page 77
Surf Filters
NetBarrier X5 includes three kinds of filters that help you control the information your Mac sends
and receives while surfing the Internet:
• The Banners Filter hides ad banners on web sites that you visit;
• The Cookies Filter prevents your Mac from sending certain information to web sites that
tracks your movements;
• The Information Hiding filter cloaks certain facts about your Mac, web browser, last web site
visited and iTunes account.
Surf filters affect all computer programs that communicate using HTTP (see chapter 12, Glossary).
Web browsers are the most common programs using HTTP, but it’s also part of iTunes, RSS
newsreaders, and a lot of other software that has Internet browsing capabilities. If you have
unexpected difficulties with such programs—downloading music through iTunes, for example—try
disabling the surf filters temporarily.
Page 78

Intego NetBarrier X5 User’s Manual Page 78
Banners Filter
The Banners Filter is a list of rules that NetBarrier X5 uses to filter unwanted web material such as
graphic ads known as “ad banners”, helping you surf much faster and with less distraction.
NetBarrier X5 blocks these ads, and replaces them with tiny, transparent graphics. NetBarrier X5
contains an internal list of ad banner strings to filter, but you can also add custom strings to filter
more ads you encounter when surfing. Here is the banners filter window, populated with sample
data:
To enable the banners filter, click the “Filter banners:” checkbox.
Page 79

Intego NetBarrier X5 User’s Manual Page 79
Adding Rules to the Banners Filter
The Banners filter already contains a set of rules, which is kept up-to-date when you update your
NetBarrier X5 Filters using NetUpdate X5, but you can easily add your own. To add rules to the
banners filter, click the + button. A new line is added to the banner list for you to edit.
The list contains four columns: a checkbox, URL Component, Comparator and Pattern. The pattern,
obviously, is how you define what you want blocked.
The URL Component popup menu has three options. NetBarrier X5 searches each banner filter in
the selected element:
Host Name
The Internet domain—that is, anything in a Web address between the http:// and
the first “/”. The default value is www.example.com. Note that such an entry
wouldn’t block (for example) http://forums.example.com; to block both, you
should simply enter example.com.
Path
Any part of the URL following the host name, such as /ads/ in
http://www.example.com/home/graphics/ads/6542.html.
URL
The entire URL, such as http://www.example.com/home/graphics/ads/6542.html.
Page 80
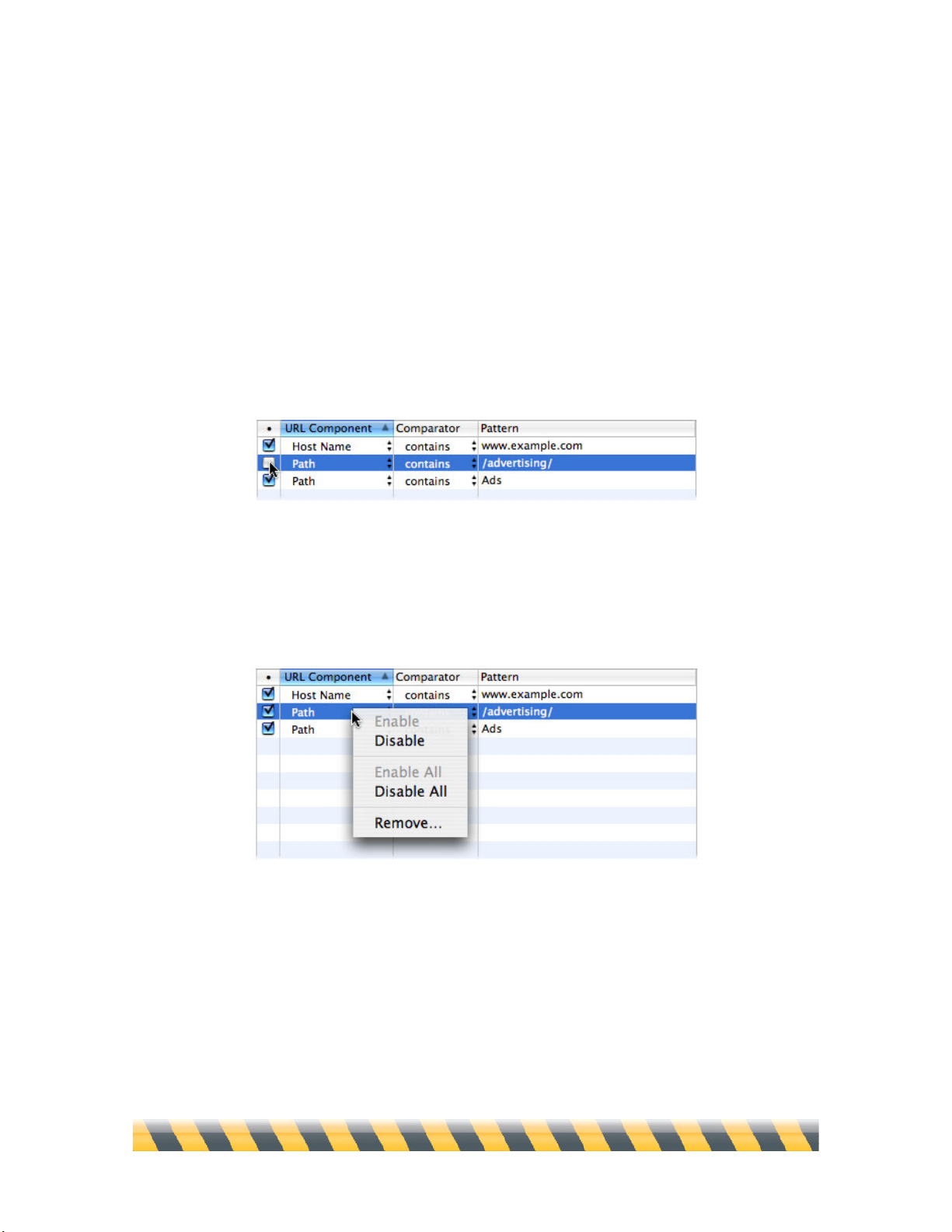
Intego NetBarrier X5 User’s Manual Page 80
The Comparator popup menu lets you choose whether content should be blocked based on an
exact match (“is”) or when your text matches at least a portion of the URL (“contains”).
Activating or Deactivating Banner Rules
Each banner rule appears on a line in the banner window. A checkbox at the left of each line allows
you to activate or deactivate the filter for each banner rule. When you add a new banner rule, the
box is checked, indicating that the filter is active for this rule. To stop blocking certain banners,
uncheck the checkboxes for the banners in question.
You can also enable ad banner blocking for an individual ad banner rule, or for all ad banner rules,
by holding down the Control key on your keyboard and clicking on the name of an ad banner rule.
A contextual menu displays.
Select Disable to disable protection for the selected ad banner rule, or select Disable All to disable
protection for all ad banner rules. (If the Rule was already disabled, the “Enable” and “Enable All”
choices would be available.)
To remove banner rules, either choose the Remove option in the contextual menu or click the –
button below the list of banner rules.
Page 81

Intego NetBarrier X5 User’s Manual Page 81
Note that the banners filter doesn’t know what content it’s filtering, only that the URL matches the
criteria you specified. Therefore, you might occasionally have difficulty seeing information on Web
pages that coincidentally matches your criteria, but isn’t actually an ad banner. If this is the case, try
turning off the banners filter temporarily. You can do this from the NetBarrier X5 application, or
from the Intego menu in your menubar.
Page 82
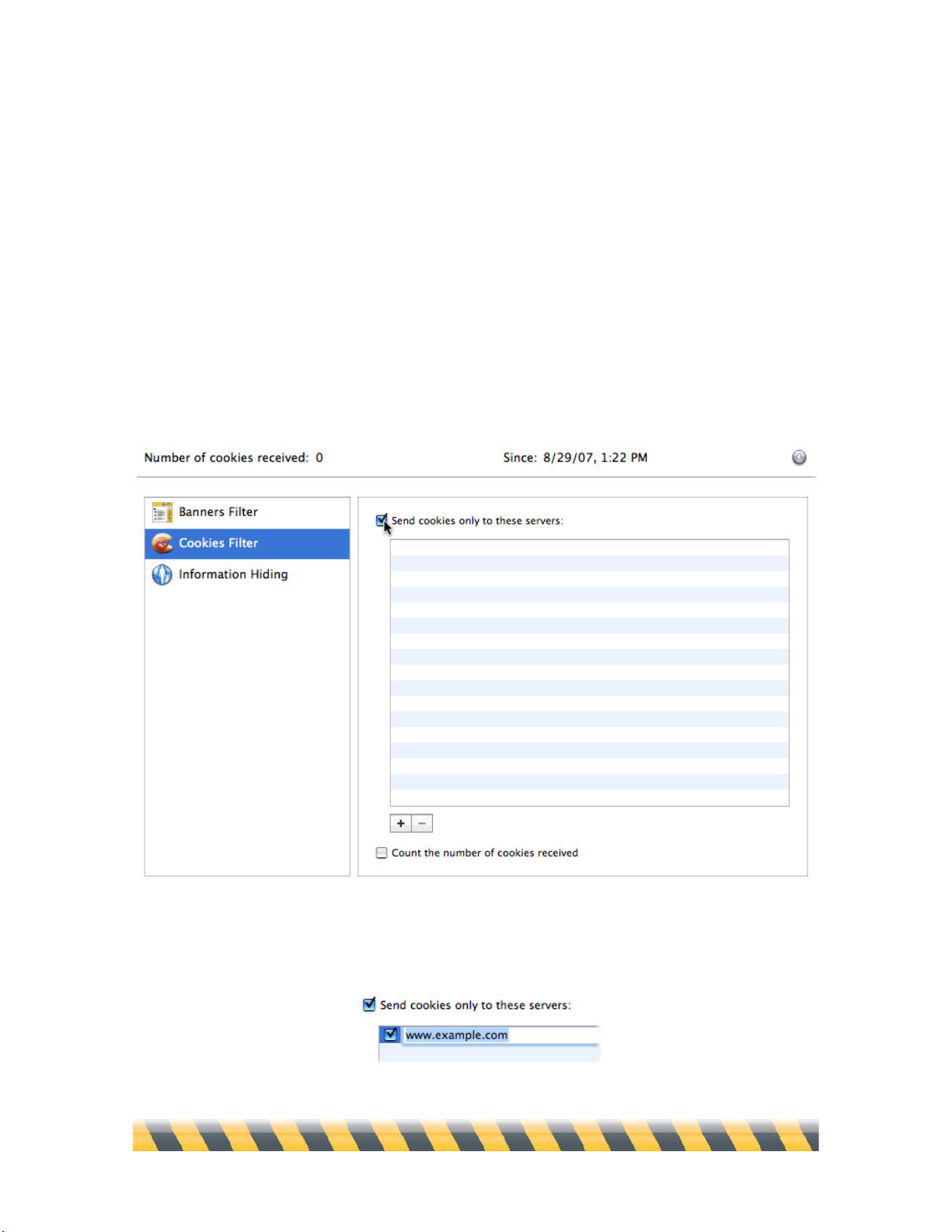
Intego NetBarrier X5 User’s Manual Page 82
Cookies Filter
NetBarrier X5 includes a cookies filter, which prevents your Mac from sending tracking
information, called “cookies”, to all Internet sites except for those you specify.
The cookies filter is useful when you want to surf in extreme privacy, only telling a few, trusted
sites about your actions. However, many Web sites—particularly those that require a password—
won’t work correctly unless you specifically include them in the list of trusted sites.
To turn on the cookies filter, click the “Send cookies only to these servers:” checkbox.
To add a server to the Cookies Filter list, click the + button at the bottom of the list. A dummy
server address (www.example.com) displays: change it to the site of your choice.
Page 83

Intego NetBarrier X5 User’s Manual Page 83
Erase the dummy server address and enter the name of the server you want to allow cookies to be
sent to. You can also drag a URL from a browser, or even a URL in text format, to this field to add
it to the list.
As with the banners filter, you can enable or disable individual cookies filters by clicking the
checkboxes next to them, or by holding down the Control key while clicking on them and using the
contextual menu, or clicking with your right mouse button.
To remove cookies that are already on your Mac, see the separate manual for Intego Washing
Machine that accompanies NetBarrier X5.
Page 84
Intego NetBarrier X5 User’s Manual Page 84
Cookie Counter
NetBarrier X5 can also count the number of cookies for all users on your Mac, if you check the
Count the number of cookies received checkbox at the bottom of the cookies filter screen.
A display at the top of the screen tells you how many cookies your Mac has accepted since you
turned on, or last reset, the counter. At any time you can reset the counter to zero by clicking the
small arrow in the upper-right corner.
Page 85
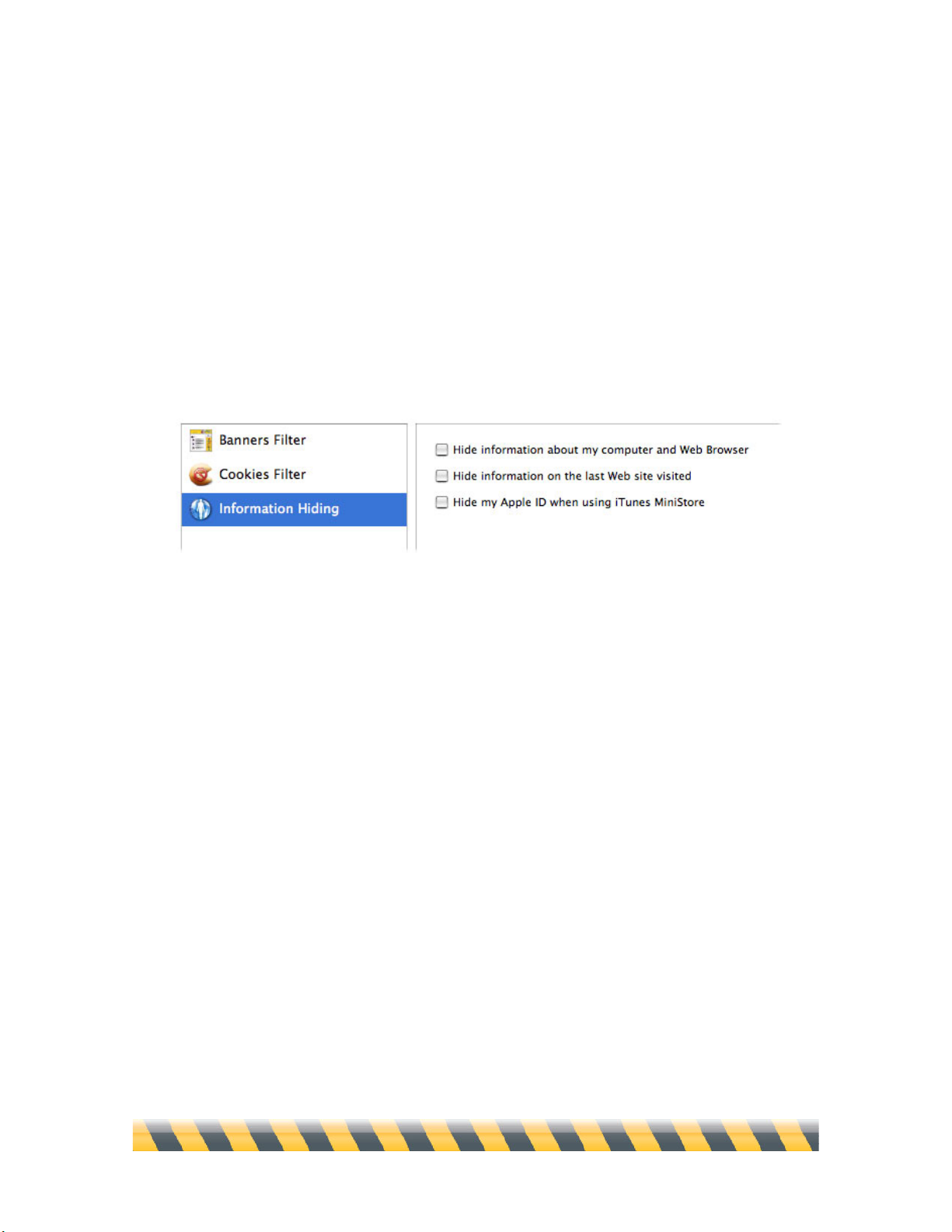
Intego NetBarrier X5 User’s Manual Page 85
Information Hiding
All Web browsers are set to reply to requests from Web sites, telling which platform you are using
(Mac, Windows, Linux, etc.) and which browser and version you are using. This information can
help the site deliver information in the best way, for example by turning on features that only work
for the Web browser that you’re using. On the other hand, some sites limit access by platform and
browser, in some cases forbidding access to everybody using a Mac. NetBarrier X5 can hide some
information concerning your computer, possibly permitting access where it would otherwise be
denied.
NetBarrier X5 can reply to these requests, and send only generic information. For example, your
computer will reply to the Web site that you’re using a Netscape or Mozilla browser, but with no
version number or platform. To do this, check the Hide information about my computer and
Web Browser checkbox.
Some sites also keep track of the last site you visited. Again, this can improve your Web experience
if, for example, a shopping site offers you discounts if you come from a specific Web site. But
unscrupulous sites might use this feature to follow your browsing habits in ways you don’t want. By
checking the Hide information on the last Web site visited checkbox, NetBarrier X5 prevents
your Mac from replying to this type of request.
Finally, if you use iTunes and display the iTunes MiniStore, iTunes sends your Apple ID to Apple’s
servers each time you click on a song. To block this, check Hide my Apple ID when using iTunes
MiniStore. This will not prevent you from purchasing songs from the iTunes Store, but will prevent
iTunes from sending information that links your browsing to your iTunes Store account.
Page 86

Intego NetBarrier X5 User’s Manual Page 86
7—The Four Lines of
Defense: Antivandal
Page 87

Intego NetBarrier X5 User’s Manual Page 87
Antivandal
NetBarrier X5’s Antivandal watches over data entering your Mac and filters it, looking for signs of
intrusion. This filtering is transparent—the only time NetBarrier X5 will show itself is if it detects
suspicious data. If this occurs, an alert displays. Otherwise, Antivandal silently monitors your
computer’s network activity at all times.
The Antivandal section has two parts that control how data enters your computer: Policy and Anti-
Spyware. The Stop List and Trusted Group store specific hosts, or IP addresses, that you deem
trustworthy or not.
Page 88

Intego NetBarrier X5 User’s Manual Page 88
Policy
The Antivandal panel provides policy tools to prevent six types of intrusions.
Buffer Overflow
Attacks
Attacks that may occur when certain software has flaws in the way it handles
memory.
Intrusion
Attempts
Attempts to access your Mac through a preset number of incorrect password
requests within a given period of time. Different settings are available for
AppleShare IP (ASIP), FTP, HTTP, IMAP, POP and SMTP.
Ping Attacks
Your Mac receives a number or frequency of ping requests so great that
responding would cause a strain on your Mac.
Ping Broadcasts
Ping requests to broadcast addresses, where a single ping is multiplied
throughout your local network.
Port Scans
Attempts by remote computers to search your Mac’s ports for vulnerabilities.
You may want to leave this unchecked if your computer is functioning as a
server.
SYN Flooding
Multiple TCP requests sent by an attacker who then doesn’t complete the final
stage of the exchange, causing the target computer to consume resources.
Page 89
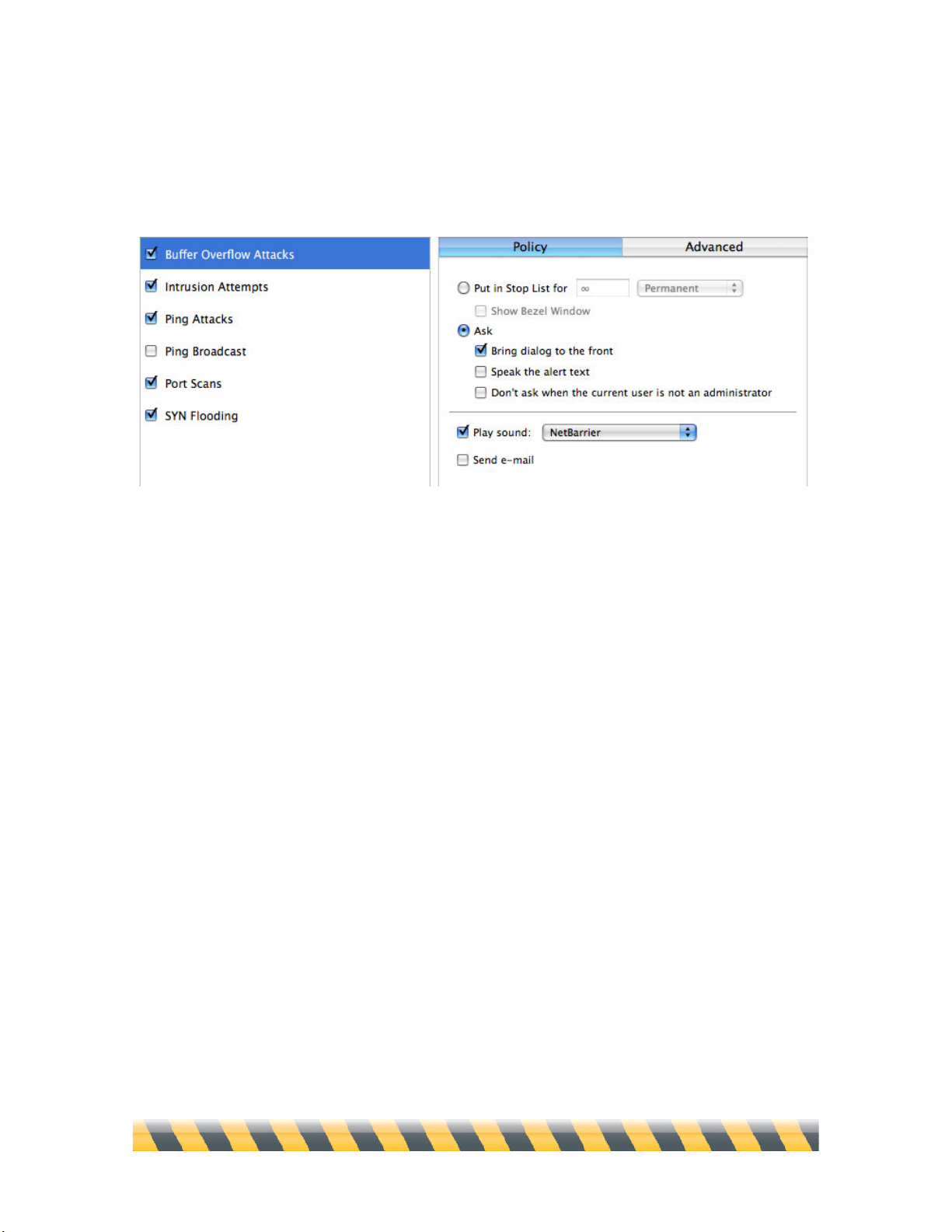
Intego NetBarrier X5 User’s Manual Page 89
Clicking the checkbox next to each of these enables or disables protection for that intrusion type.
Clicking on the name of the intrusion type shows the notification and action policies for that
intrusion type. Here, for example, we see the policy for Buffer Overflow Attacks.
These options are described in full in chapter 9, Understanding Alerts.
Page 90

Intego NetBarrier X5 User’s Manual Page 90
While an intrusion type is selected, clicking on the Advanced tab in the right-side pane brings up
additional options that are specific to that intrusion type. These are:
Buffer Overflow
Attacks
No advanced settings.
Intrusion
Attempts
You can separately set the number of incorrect password attempts permitted for
AppleShare IP (ASIP), FTP, HTTP, IMAP, POP and SMTP.
Ping Attacks
Ping flood sensitivity, measured in milliseconds (ms) permitted between ping
attempts. If your computer is on a network, it is normal that your network
administrator ping your computer from time to time. But if your computer is
isolated pings are rarer. One exception is if you have a DSL or cable
connection; your ISP might ping your computer to check if it is on-line.
Ping Broadcasts
No advanced settings.
Port Scans
Sensitivity is adjustable as a slider from low to high in increments according to
an internal calculation.
SYN Flooding
Sensitivity, measured in number of attempted connections allowed per second.
Page 91

Intego NetBarrier X5 User’s Manual Page 91
Options
Additional filtering options are available within the Options panel of the Policy tab. Click Options
to adjust these settings.
Stealth mode (prohibit
ping replies)
If this is checked, your computer will be invisible to other computers
on the Internet or on a local network. You will not, however, be
anonymous—any requests you send to other hosts will include your
computer’s IP address.
Stop unknown protocols
If this is checked, NetBarrier X5 automatically blocks any unknown
protocols.
Deny Apple Remote
Desktop Control
If this is checked, NetBarrier X5 blocks all access to your Mac by
Apple Remote Desktop software.
Allow PORT mode FTP
transfers
If this is checked, you will be able to make FTP transfers when
functioning in Client Only firewall mode.
The second part of this screen allows you to be notified by e-mail when an attack is detected. See
chapter 9, Understanding Alerts for more information.
Page 92

Intego NetBarrier X5 User’s Manual Page 92
Unifying Policy Options
Each type of intrusion has settings that determine how you’re alerted and what actions are taken
when that type of intrusion is detected. These settings are fully explored in chapter 9,
Understanding Alerts.
The “Use same policy for all types of protection” checkbox unifies all notifications and actions.
With this box unchecked, you could (for example) choose to receive an e-mail when a buffer
overlfow attack is detected, but only see an alert box when an intrusion attempt occurs. Checking
the box tells NetBarrier X5 that you want to get the same sort of response no matter what sort of
intrusion occurs.
When you turn on this option, you’ll see a dialog box that asks which settings should become the
model that other intrusion types will follow.
Page 93

Intego NetBarrier X5 User’s Manual Page 93
Anti-Spyware
NetBarrier X5 lets you control access from your Mac to the Internet and local networks by
individual applications. While your firewall settings may allow general network access, the Anti-
Spyware tab lets you choose how NetBarrier X5 reacts when specific applications try to access the
network. This helps you in two ways:
• If you wish to prevent users from accessing the network with specific applications, you can
block them in the Applications tab.
• If an application attempts to connect to the network behind your back, NetBarrier X5 stops it in
its tracks, alerts you, and waits for you to decide whether to allow it to do so or to block it.
Your Mac has many applications that access the Internet or other networks, including web
browsers, e-mail programs, FTP (file transfer) programs and instant messaging applications. But
there may also be programs that connect to the network without telling you, in order to verify the
serial numbers of software installed on your computer, collect and send personal information
without your awareness, or open a backdoor on your Mac to provide access to hackers or vandals.
NetBarrier X5 notifies you of such attempts and allows you to decide whether to allow them.
To turn on Application Blocking, check the Protect against Spyware checkbox in the upper-left
corner of the Anti-Spyware window.
Page 94

Intego NetBarrier X5 User’s Manual Page 94
Anti-Spyware works by first asking you to make a list of applications for which you want to apply
settings. These are known as “defined” applications, while all those that aren’t on the list are
“undefined”. In the example above, Google Earth is defined, while Internet Explorer (which isn’t on
the list) is undefined.
Once you’ve built this list, you can finely control communications from defined applications and set
a general policy for communications from undefined applications. Two typical configurations
would be:
• You run a computer lab and want people to be able to send e-mail using Apple’s Mail program,
but not browse the Web or play network games. You would define Mail as Allowed, but deny
all outgoing connections from other programs.
• You suspect that an application you downloaded to your Mac is sending unauthorized
communications, perhaps from hidden spyware built into the program. You define that program
and deny all communications from it, but allow all communications from undefined
applications.
Page 95

Intego NetBarrier X5 User’s Manual Page 95
Four behavior options are available for undefined applications:
Allow outgoing
connections
NetBarrier X5 allows all applications to access the Internet or any other
network. However, any firewall rules you may have defined concerning
access to and from specific ports still function. For example, if an FTP
program attempts to connect to a Web page, NetBarrier X5 does not block
the application, but if you have set up a firewall rule blocking port 20, the
standard FTP port, the data does not go through. If the FTP program
attempts to make a connection to a different port, it is not blocked.
Deny outgoing
connections
NetBarrier X5 blocks all access to the Internet or other network. This
supercedes all firewall rules you have defined.
Ask (Allow on
time-out)
NetBarrier X5 asks you for each application that attempts to connect to the
Internet or other network. If you do not respond within 90 seconds, the
application will be allowed to access the Internet, but only this time.
Ask (Deny on time-
out)
NetBarrier X5 asks you for each application that attempts to connect to the
Internet or other network. If you do not respond within 90 seconds, the
application will be denied access, but only this time.
Page 96
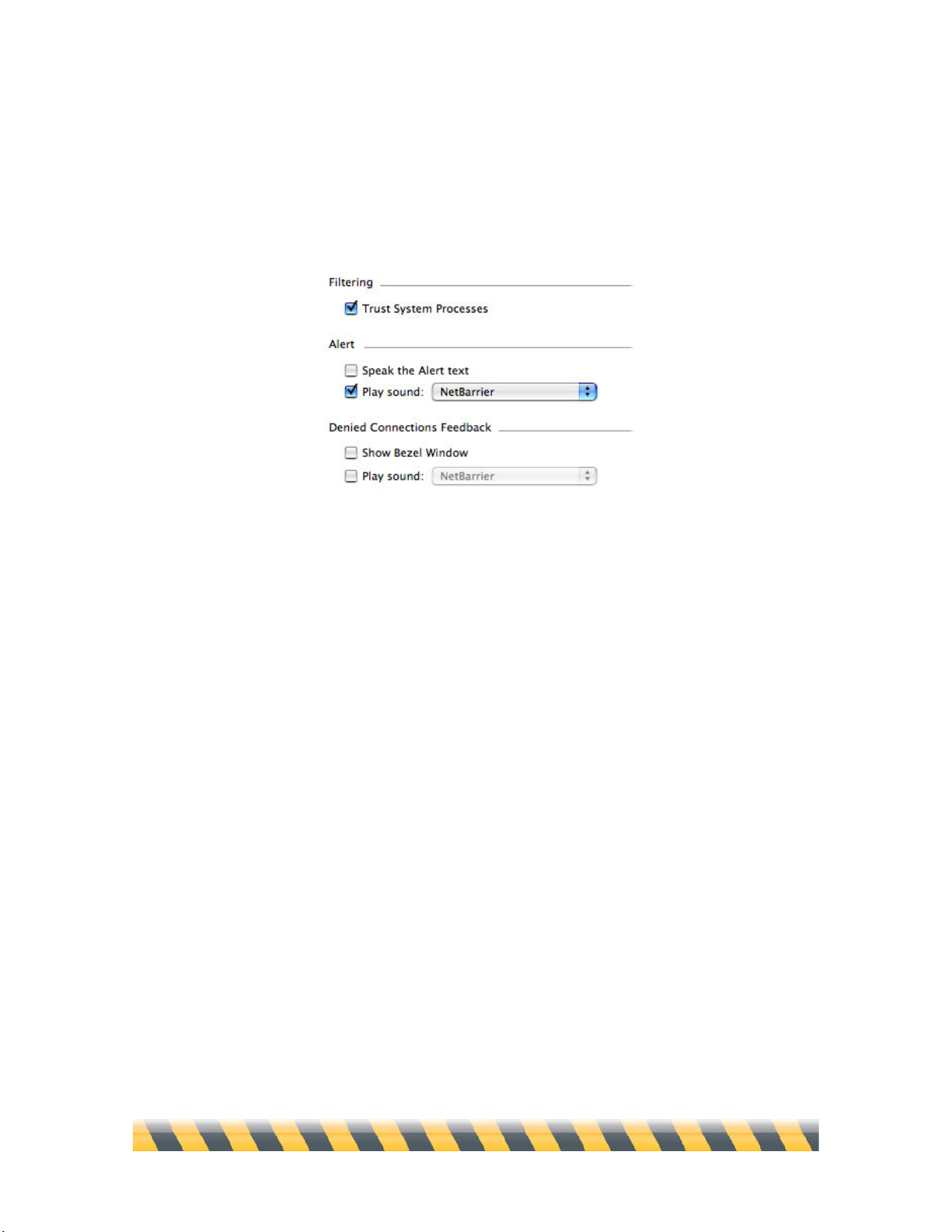
Intego NetBarrier X5 User’s Manual Page 96
Options
The Options button in the lower-left corner of the Anti-Spyware pane allows you to configure some
general Anti-Spyware settings.
The one option that’s special to Anti-Spyware is Trust System Processes, which allows
communications from the many parts of Mac OS X itself that request Internet or network access.
Such requests might relate to printing services, domain name resolution, checks for software
updates or clock synchronization. These are requests that come from parts of Mac OS X, not
separate applications. To trust these processes, and not be asked when they attempt to connect to the
Internet or network, check the Trust System Processes checkbox.
For details on other Anti-Spyware options, see chapter 9, Understanding Alerts for more
information.
Page 97
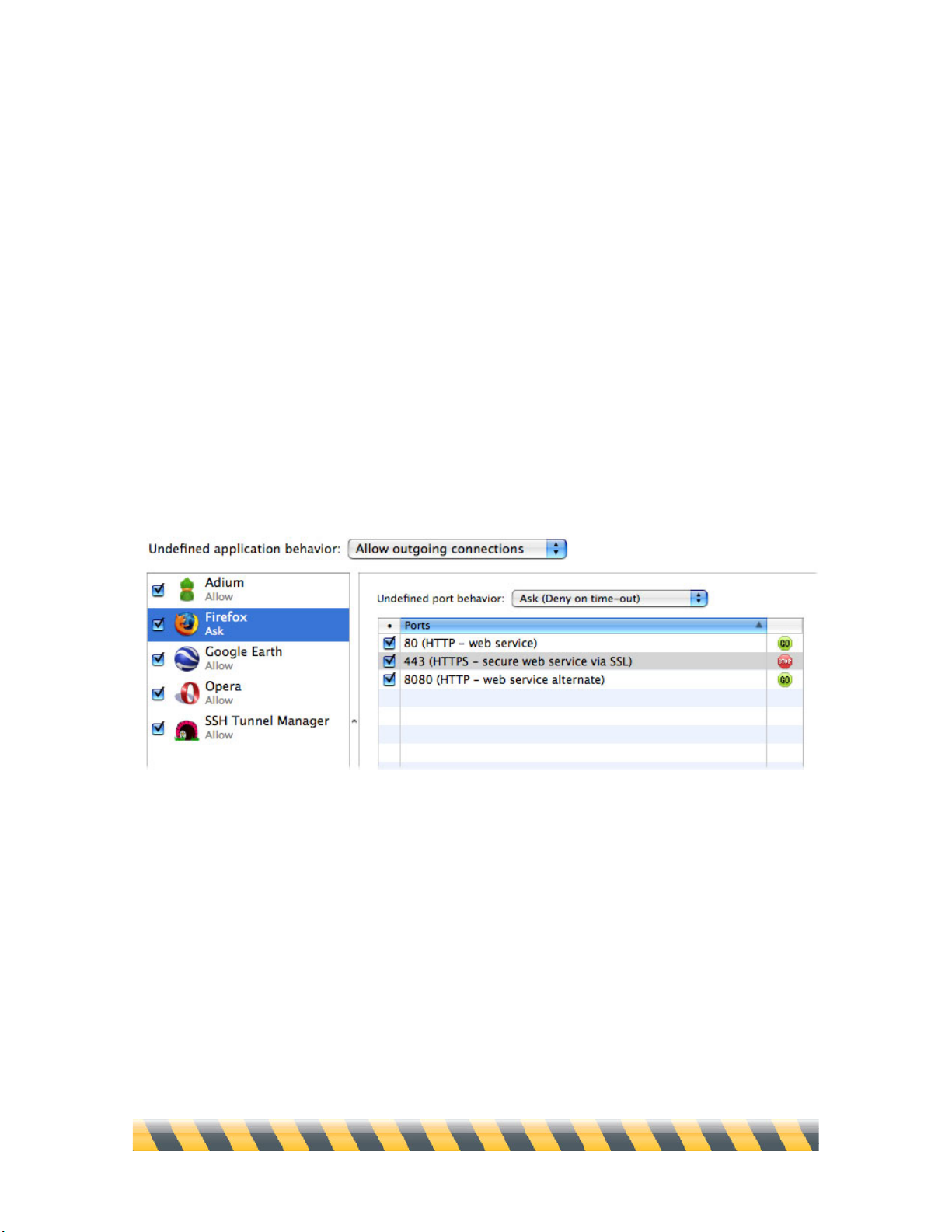
Intego NetBarrier X5 User’s Manual Page 97
Applications: Adding, Removing and Changing Settings
After you have chosen to allow or deny network access to undefined applications, define an
application by clicking the + button, then navigating through the Mac OS X dialog box to the
application itself to add it. Repeat the process for all the applications you wish to add. (To remove
an application from the list, click it and then click the – button at the bottom of the application list.)
You can then change the settings for each application to allow or block communications from the
application as a whole, or over specific ports. Similar to the process above, where you specify what
should happen when undefined applications attempt outgoing communications, here you define
what you’d like to happen when a specific application attempts communication from an undefined
port. Then you define a list of ports for that specific application that are exceptions to the general
rule.
In the above example:
• Five applications (listed on the left) have specific rules governing them; outgoing connections
are allowed from all other applications.
• Firefox is permitted to send two kinds of communications, via ports 80 and 8080.
• Communications by Firefox via port 443 are forbidden.
• Communications by Firefox via any other port raise an alert on your Mac’s screen; if you don’t
respond to allow the communication within 90 seconds, it is denied.
Page 98

Intego NetBarrier X5 User’s Manual Page 98
This list of ports contains three columns:
• The first column, containing checkboxes, indicates the port behavior that is currently activated
for the application. If the box next to a port is checked, the behavior you have specified is
active. If you want to deactivate this behavior, then uncheck the box. You can reactivate it later
by checking the box.
• The second column, Ports, provides information on the ports that the application uses to access
the network. It tells you the port number, and, in some cases, the protocol used and a brief
description. (This description appears automatically when you enter a port number that
NetBarrier X5 recognizes.) You can add a port number, or a range of port numbers, for
example 110-123.
• The third column contains one of two icons: a green, GO icon, indicates that network access is
allowed; a red, STOP icon, indicates that network access is denied.
• If you want to change an Allow setting to Deny, you can just click the green GO icon, and it
will change to the red STOP icon. You can also toggle from STOP to GO in the same manner.
To view an application on the Applications list in the Finder, hold down the Control key on your
keyboard and click on the name of an application. A contextual menu appears. Select Show in
Finder, and a Finder window opens revealing the location of the application.
Page 99
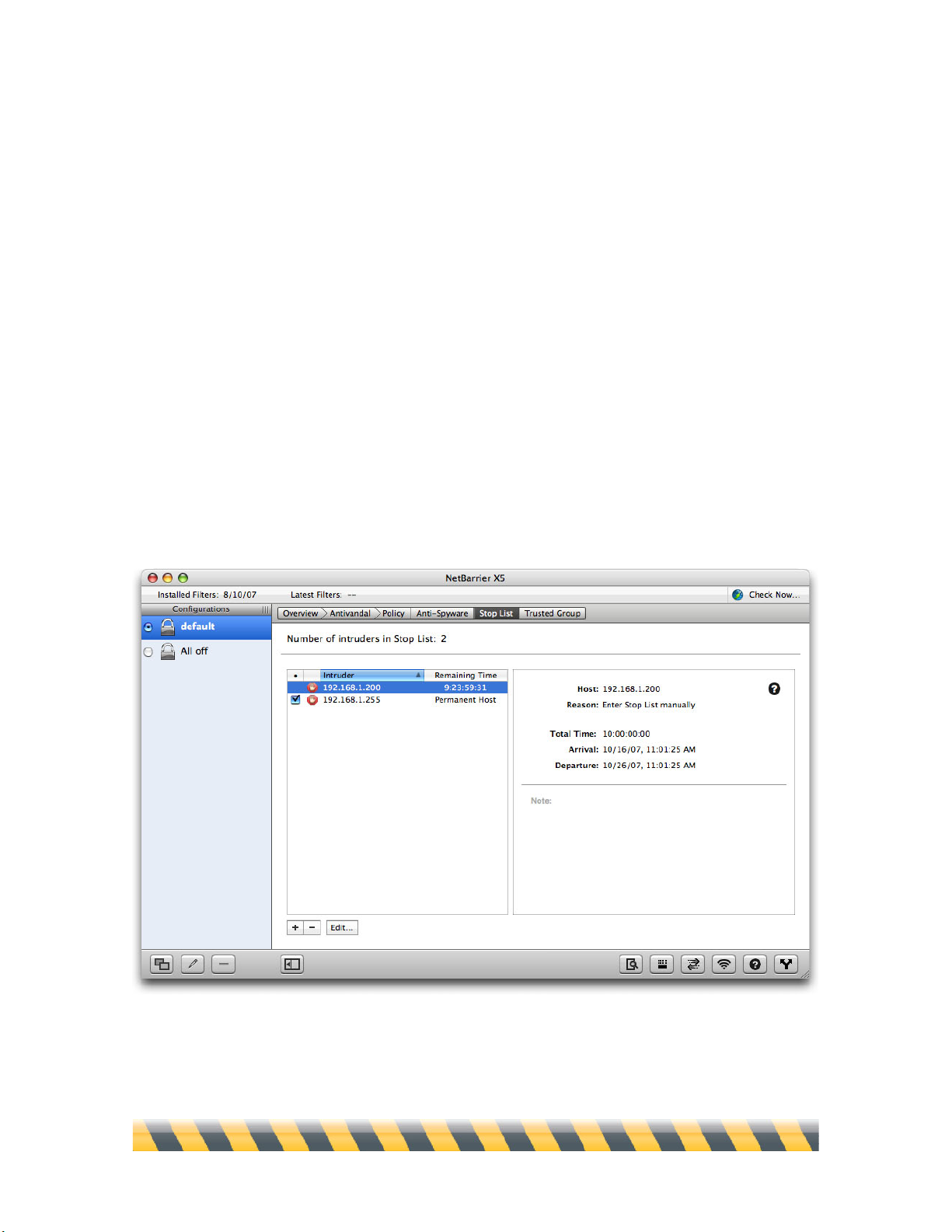
Intego NetBarrier X5 User’s Manual Page 99
The Stop List and Trusted Group
The Stop List ensures that once an attempted attack or intrusion has been foiled, communication
between the attacking machine and your Mac won’t occur for a period of time that you define.
The Trusted Group is the opposite of the Stop List: it lists “friendly” computers that are allowed to
connect to your Mac. While the Stop List protects you from foes, the Trusted Group opens the door
to your friends. NetBarrier X5’s Antivandal will not block access to computers listed in the Trusted
Group, nor will it set off alerts for any actions they carry out. However, computers in the Trusted
Group will still be affected by all active Firewall rules.
The interface for the Trusted Group window is essentially the same as for the Stop List window, so
we’ll examine them both at the same time, pointing out differences as necessary. Here’s the Stop
List window with some sample data.
Page 100

Intego NetBarrier X5 User’s Manual Page 100
The panel on the left displays information on the various IP addresses that are currently in the Stop
List or Trusted Group, if any.
Checkbox
You can temporarily disable a Stop List/Trusted Group item by unchecking
this box, which is checked by default when you add a host to either list.
When disabled, clicking it enables the item again. (This checkbox only
appears if the IP address is set to be blocked permanently.)
Intruder/Host
The second column shows the intruding IP address (in the Stop List) or
permitted IP address (in the Trusted Group).
Remaining Time
If you’ve set this IP address to be forbidden/permitted for a specific period
of time, this column shows how much time is remaining, updated every
second. Otherwise, this column says “Permanent Host” to indicate that the
IP address will be there until you remove it manually.
 Loading...
Loading...