Page 1

Page 2

Welcome to your new Imation® SECURE Hard Drive from Imation (www.imation.com). The Imation
SECURE™ Hard Drive product is a portable secure backup solution. It consists of an external hard drive
with the Imation SECURE Hard Drive security software from Imation and TotalMedia Backup software
from ArcSoft®, Inc. The Imation SECURE Hard Drive software allows users to protect the files on their
Imation SECURE Hard Drives by automatically encrypting and protecting the sensitive information.
(Encryption prevents unauthorized access to confidential data.) This user manual discusses how to
install, set up, and use the Imation SECURE Hard Drive software. It also includes some troubleshooting
information.
The Imation SECURE Hard Drive software is a Microsoft® Windows® application that is installed on a
user’s PC. It runs from the user’s PC or corporate server and automatically detects any Imation SECURE
Hard Drives connected to the machine.
After a user sets up authentication information for their drive (password, hint information, and,
optionally, a Bluetooth
®
device), the Imation SECURE Hard Drive software automatically and
transparently encrypts any data written to the drive after they have authenticated it. They do not have
to change their behavior—they work with files on the encrypted hard drive exactly the same way that
they do on standard unencrypted removable hard drives. If the user does not authenticate their Imation
SECURE Hard Drive, they cannot access the contents of the encrypted files.
If the drive contains unencrypted files, the software does not encrypt them unless the user chooses to
do so. Typically, unencrypted files are ones that the user adds while the drive is connected to a
computer that does not have the Imation SECURE Hard Drive software installed on it. The software
only encrypts files on authenticated Imation SECURE Hard Drives.
The Imation SECURE Hard Drive software also automatically decrypts the content of encrypted files on
the drive that the user opens. It re-encrypts the content when the user closes or saves the files after
making changes. If they save or copy files with encrypted content to their hard drive or other
removable storage devices, the content of the files they save or copy are unencrypted. They can then
use the files freely on machines that do not have the Imation SECURE Hard Drive software installed on
them.
System Requirements
The Imation SECURE Hard Drive 2.1 software is supported on Microsoft® Windows® XP Home/Pro,
32-bit version. It is also supported on 32- and 64-bit versions of Windows Vista, Windows 7, and
Windows 8.
For automatic backup, TotalMedia Backup, version 2.0 (and higher) by ArcSoft®, Inc. is the
recommended software to use with Imation SECURE Hard Drives. The drives contain the installation file
for this software when purchased.
Important Note: Users must have Java™ software, version 6, update 24 or higher from Oracle® Corp.
installed on their machine to use the Imation SECURE Hard Drive software. If the Imation SECURE Hard
Drive software does not run automatically, users can check their list of installed programs through the
Windows Control Panel to see if Java 6.0, update 24 or higher is installed on their PC. If it is not, they
can download Java 7.0 for free from
http://www.java.com.
Page 1
Page 3

Important Product Use Concepts
• The Imation SECURE Hard Drive software will encrypt any files written to an Imation SECURE
Hard Drive by an application, a DOS command window, or by Windows Explorer. Data
encryption is completely automatic.
• If the user connects their Imation SECURE Hard Drive to a PC that has the encryption software
installed on it and declines to authenticate it, it will become read-only. Only unencrypted files
will be readable. This allows the user to copy unencrypted files from their hard drive to the
machine, but they will be unable to write any data to it.
• The encrypted files on an Imation SECURE
Hard Drive are inaccessible to applications and the
Microsoft Windows operating system when users are working on machines that do not have the
Imation SECURE
Hard Drive software installed on them. The files are visible on the drive, but
they are encrypted.
• To remove authenticated drives, we recommend that users close all applications before safely
removing the drive through the Windows operating system and disconnecting it from the PC.
• They should not disconnect the cable that connects the Imation SECURE
Hard Drive to any
computer if they have not first safely removed the drive. Doing so can result in data loss and/or
corruption of the NTFS file system on the drive.
I. Installing the Imation SECURE Hard Drive Software
1. Verify that the machine for the Imation SECURE Hard Drive software meets the system
software requirements.
2. Log into the machine, using an account with administrator rights.
3. Connect an Imation SECURE
4. Through Windows Explorer, find and double-click the Imation SECURE
Hard Drive to the machine.
Hard Drive software
installation file (SecureHardDrive Installer.msi) located on the root of the drive.
5. Review the license agreement, accept the terms of the license agreement, and follow the
installation instructions that display.
The user then can log in as any type of user (administrator or non-administrator).
TAfter installation, the Imation SECURE Hard Drive software will appear as a padlock icon in
the notification area of the Windows taskbar (typically located in the lower right corner of the
desktop). The software is automatically initiated during system startup and therefore should
always be available unless the user selects the Upgrade Java feature.
T Td
Right-clicking the icon will display a context menu of the functions available in the Imation
SECURE
Hard Drive software.
Page 2
Page 4

Occasionally, informational messages will display, using temporary pop-up boxes to provide the
user with instructions or inform them of events that have been detected. Users do not need to
click on the messages to close them. The messages will disappear automatically.
II. Setting up Imation SECURE Hard Drive Authentication
Users must set up their Imation SECURE Hard Drive for use with the Imation SECURE Hard Drive
software. They do so by specifying authentication information (password, hint question and
answer) and, optionally, by also selecting a Bluetooth device for authentication. If they have a
Bluetooth device that has an Android™ operating system from Google™, Inc. installed on it, they
can also separately install the Android Imation SECURE Drive App to further increase security.
The Imation SECURE Hard Drive software automatically detects any Imation SECURE Hard
Drive connected to the user’s machine. If the user has not yet set up their drive for encryption,
the software will prompt the user with the Imation SECURE Setup dialog box to create the
authentication information for the device. The setup dialog box establishes both the encryption
password for the drive as well as a hint question and answer. This information, in conjunction
with a Bluetooth device if one is designated, can be used not only to authenticate the device for
use but also to retrieve or initiate changing authentication credentials.
(Using a personal pass phrase instead of a simple password provides significantly greater
security. Because the password is case-sensitive, the user will need to type it exactly the same
way whenever they enter it.)
Page 3
Page 5

If Bluetooth wireless technology is enabled for the computer to which the drive is connected,
the Utilize Bluetooth authentication check box on the setup dialog box is available. The user
can use this check box to access the Imation SECURE Bluetooth Preferences dialog box. The
dialog box enables the user to select a Bluetooth authentication option and specify a Bluetooth
device for authentication.
Authentication options
There are three authentication options:
• If the user chooses to save the password and hint information without selecting the Utilize
Bluetooth authentication check box, their authentication type is “Password only.”
• If the user wants to use either a password or Bluetooth device, they can select the Utilize
Bluetooth authentication check box and choose “Bluetooth OR password for convenience.”
• If the user wants the increased security of dual-factor authentication, they can choose
“Bluetooth AND password for security,” which requires them to provide both their password
and Bluetooth-enabled device.
Bluetooth security
When the user specifies a Bluetooth device to authenticate their drive, they can further enhance
the security of their Imation SECURE Hard Drive.
For Bluetooth devices that have the Android operating system installed on them, the Android
Imation SECURE Drive App generates a stronger authentication key when installed and used.
For Bluetooth devices that do not have the Android operating system installed on them, if the
user can modify the device name, they can strengthen the drive security by changing the
Bluetooth device name to a unique name.
A. Set up password and hint information
1. Connect an Imation SECURE Hard Drive that is not set up to work with the Imation
SECURE Hard Drive software to a computer that has the software installed on it.
The Imation SECURE Setup dialog box displays.
2. Enter a password in the Password and Confirm boxes.
3. Enter a hint question and answer.
4. To add a Bluetooth device if the Utilize Bluetooth authentication check box is enabled,
select the check box.
5. Click OK.
If the user has selected the check box, the Imation SECURE Bluetooth Preferences
dialog box displays (please refer to “Add a Bluetooth device” on page 5 for further
instructions).
– or –
If the user has not selected it, a message displays when the drive is ready for use.
Page 4
Page 6

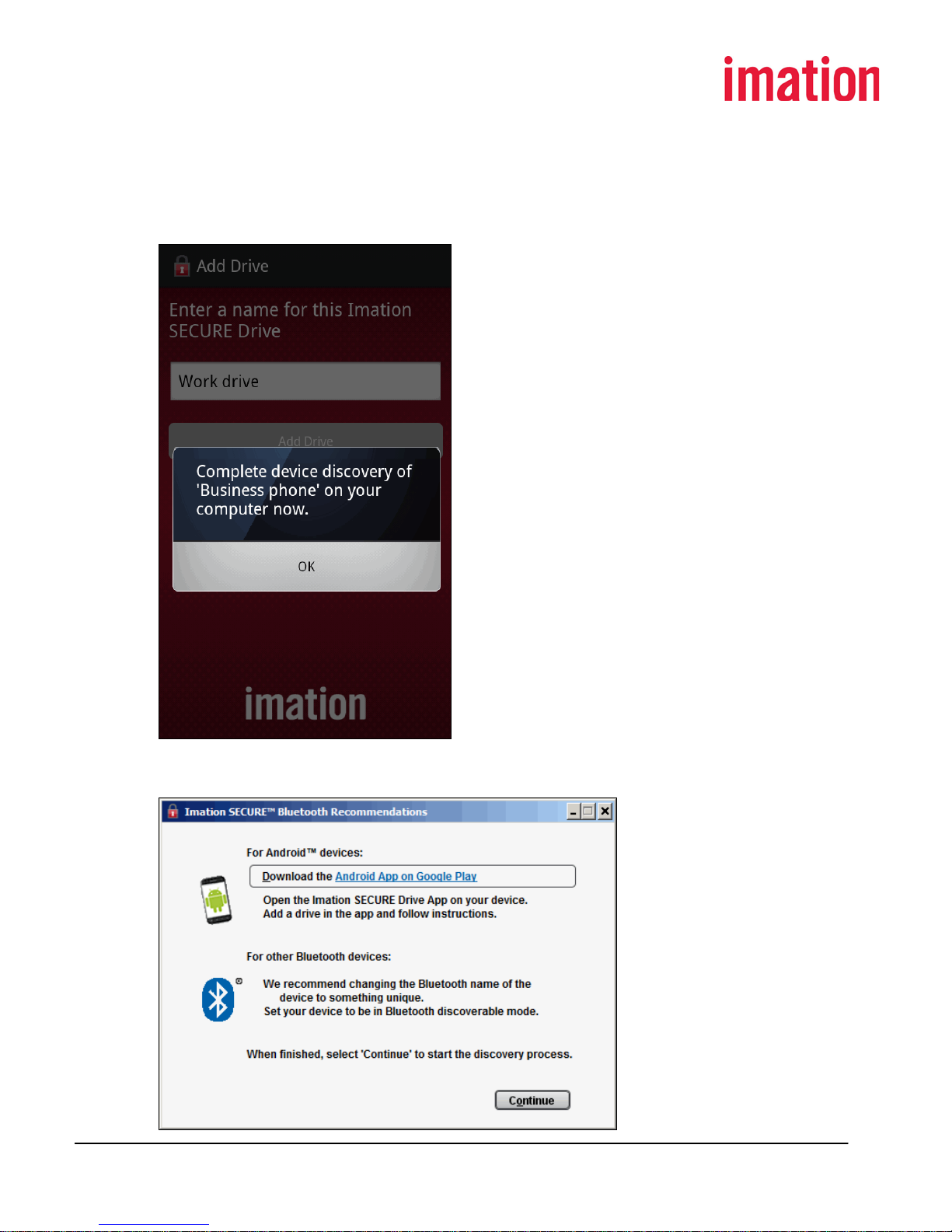
B. Add a Bluetooth device
1. If the Imation SECURE Bluetooth Preferences dialog box displays, choose a Bluetooth
authentication option.
2. Click Discover.
The Imation SECURE Bluetooth Recommendations dialog box displays.
3. Make sure the desired Bluetooth authentication device is within range of the computer,
enable its Bluetooth functionality, if necessary, and make the Bluetooth device
discoverable.
Page 5
Page 7

4. Follow the instructions relevant for the desired Bluetooth authentication device. Then,
click Continue.
All discoverable Bluetooth devices that are Bluetooth-enabled and within range display
in the Imation SECURE Bluetooth Preferences dialog box list.
5. Select the desired Bluetooth device in the list.
6. Click OK while the Bluetooth device is still discoverable.
7. In the Imation SECURE Enter Device Comment dialog box, enter a comment to help
identify the Bluetooth device later.
Note: This comment displays on the About Imation SECURE dialog box.
Page 6
Page 8
8. Click OK.
A message displays when the drive is ready for use.
III. Authenticating Imation SECURE Hard Drives
The authentication option that the user selects for their Imation SECURE Hard Drive determines
how they authenticate it.
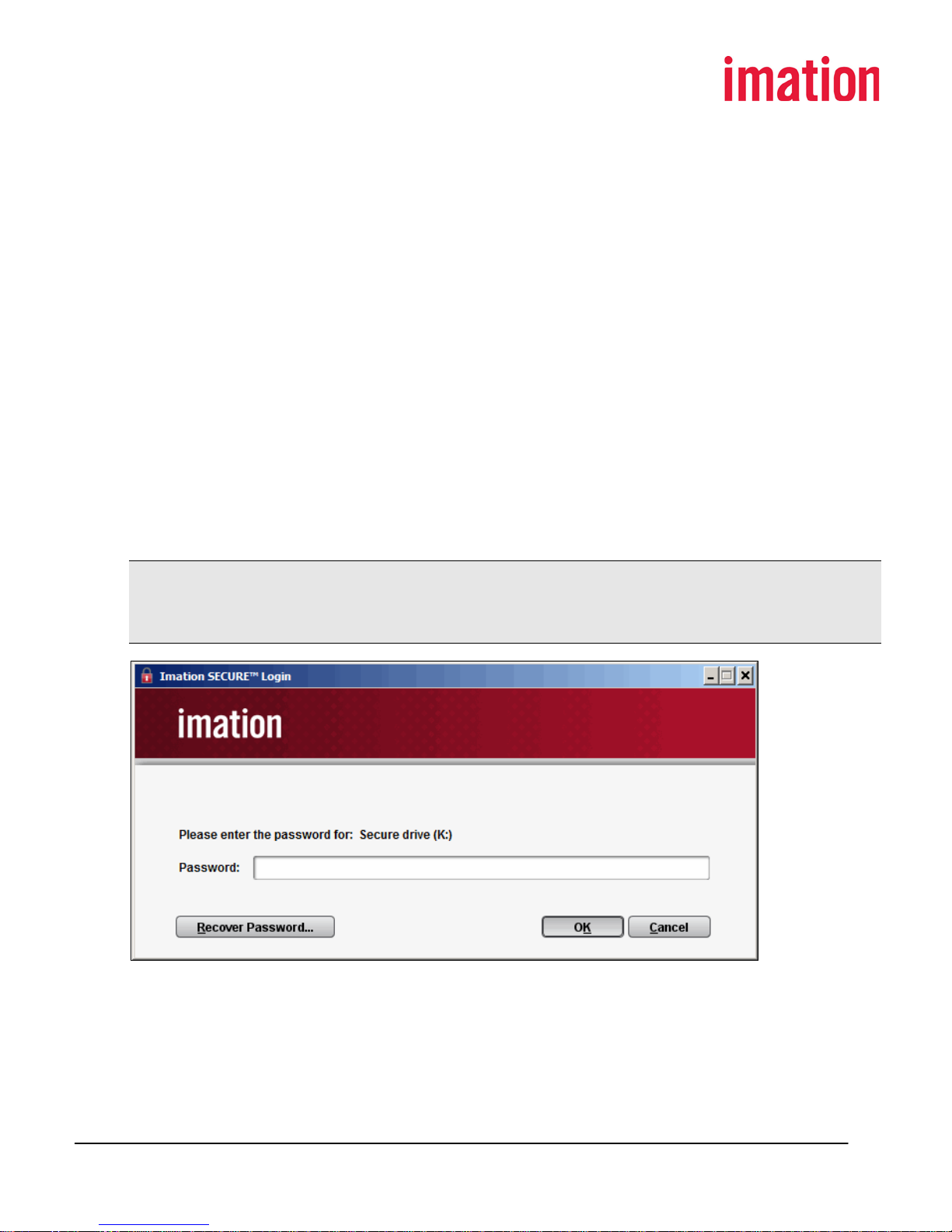
• For users who choose the “Password only” authentication option, the Imation SECURE
Login dialog box displays when the user connects their drive to the computer.
Authentication occurs after they enter their password. If they decline to provide a password
by clicking Cancel or closing the dialog box, the hard drive will be read-only.
• For users who choose the “Bluetooth OR password for convenience” authentication option,
authentication occurs automatically if the user’s Bluetooth authentication device is enabled
and within range. If their Bluetooth device is unavailable, the Imation SECURE Login dialog
box displays. They can then enter their password to authenticate the drive.
• For users who choose the “Bluetooth AND password for security” dual authentication
option, the Imation SECURE Login dialog box displays. To authenticate their device, the user
must enter their password and have their Bluetooth authentication device enabled and
within range. If the user cannot provide one of these two elements, they can use a different
two-factor combination for authentication (password and hint, hint and Bluetooth device).
Note: Unlike the other two authentication options, there is no password recovery mechanism for
dual-factor authentication. If the user does not remember their password, they must provide
their hint answer and their Bluetooth authentication device must be available. Otherwise, they
cannot authenticate their hard drive.
If the hard drive contains any files that are not encrypted, the Imation SECURE Hard Drive
software will not encrypt them unless the user has previously selected the Encrypt Unencrypted
Files on the Imation SECURE Hard Drive menu.
Page 7
Page 9

Once the hard drive is authenticated, the Imation SECURE Hard Drive software intercepts all file
operations to the hard drive and encrypts and decrypts them automatically.
Note: Any attempt to access the encrypted files on the hard drive before authentication will not
succeed. Difficulties accessing these files may persist even after authenticating due to Windows
file system caching. Ejecting and reinserting the hard drive will clear these issues.
IV. Working with the Android Imation SECURE Drive App
After the user has installed the Imation SECURE Drive App on their Android Bluetooth device,
they can configure the app for use with their Imation SECURE Hard Drive. Once the user
configures the app, they can use it to strengthen security while authenticating the drive.
If the user changes the authentication credentials for the drive through the Imation SECURE
Hard Drive software, the user must work with the app to retain use of it with the Bluetooth
device on which it is installed.
At any time, the user can remove the Imation SECURE Hard Drive from the app. If they have
problems keeping Bluetooth enabled while the device is in sleep mode, they can use the Wake
Lock feature to keep the Bluetooth functionality enabled.
Users should follow standard Android operating system procedures to install and uninstall the
Imation SECURE Drive App.
Configure app
Configuring the Imation SECURE Drive App consists of:
• Adding a drive to the app that corresponds to the Imation SECURE
Hard drive
• Allowing the Bluetooth device to become discoverable
• Completing discovery of the Bluetooth device through the Imation SECURE
Hard Drive
software
To configure the app
1. At a computer that has the Imation SECURE Hard Drive software installed on it, click
Discover in the Imation SECURE Bluetooth Preferences dialog box when setting up or
changing the authentication for an Imation SECURE Hard Drive.
For more information on setting up a drive, please refer to “Setting up Imation SECURE Hard
Drive Authentication” on page 3.
For more information on changing authentication, please refer to “Modifying Authentication
Credentials” on page 17.
2. On the Android Bluetooth device, install or open the app, if it is not already open.
Page 8
Page 10

3. If the user has just installed the app, touch the Add Drive button on the introductory screen
(This screen only displays immediately after installation.)
– or –
If the introductory screen no longer displays, touch the plus (+) sign at the top of the Drives
screen.
Page 9
Page 11

4. Enter a name for the desired Imation SECURE Hard Drive in the blank field of the Add Drive
screen.
5. Touch the Add Drive button.
6. In the Bluetooth permission request message, touch the Yes button to enable Bluetooth for
the Bluetooth device and make the device available for Bluetooth discovery.
Page 10
Page 12
7. In the app, touch OK in the confirmation message.
The Bluetooth symbol at the top of the Add Drive screen blinks while the device is
discoverable.
After the app has added it, the drive displays in the Drives screen.
8. In the Imation SECURE Hard Drive software, click Continue in the Imation SECURE
Bluetooth Recommendations dialog box.
Page 11
Page 13

9. Select the Android Bluetooth device in the Imation SECURE Bluetooth Preferences dialog
box list.
10. Click OK.
11. In the Imation SECURE Enter Device Comment dialog box, enter a comment to help identify
the Bluetooth device later.
The Imation SECURE Hard Drive software adds the Bluetooth device that has the app
installed on it as a Bluetooth authentication device for the drive.
Use app while authenticating a drive
In the app, a drive that is listed in the Drives screen can be unlocked or locked (indicated by the
appearance of the lock icon adjacent to the drive).
When the drive is unlocked, the unique authentication key information associated with it is
published over Bluetooth and available for use. To use the Android Bluetooth device for
authentication through the Imation SECURE Hard Drive software, the drive in the app must be
unlocked when the Imation SECURE Hard Drive is first connected to the computer.
If the user locks the drive for security reasons, the app hides the key information, so that it is no
longer available for authentication. Authenticated drives that are associated with the app are
unaffected by locking the drive on the app until they are disconnected and reconnected for
re-authentication. Drives that have not yet been authenticated cannot be authenticated with the
Android Bluetooth device while the drive in the app is locked.
Page 12
Page 14

Instead, for drives with the Bluetooth OR password authentication option, the user must enter
their password to authenticate their drive. For drives with the Bluetooth AND password
authentication option, they must provide both their password and hint answer.
To change the status of a drives
Touch the drive listed in the Drives screen. Each time that the user touches the drive, the status
switches from unlocked to locked and vice versa.
To unlock the drive for 60 seconds
The most convenient option for the user is to leave the drive that is listed on the Drives screen
unlocked. The more secure option is to keep the drive locked until they need to authenticate
their associated Imation SECURE Hard Drive.
In this case, instead of indefinitely unlocking the drive, the user can unlock it for authentication
for just for 60 seconds. When the user chooses this drive option, the app unlocks the drive for
60 seconds, then automatically re-locks it.
Page 13
Page 15

1. On the Drives screen, touch and hold the desired drive until the drive menu displays.
2. Touch the Unlock for 60 seconds option.
The lock icon for the drive changes from the locked to unlocked status for 60 seconds and
then reverts back to the original locked appearance.
Retain use of app when modifying authentication credentials
If a user is using the Imation SECURE Drive app and wants to continue using it after modifying
the authentication credentials of their Imation SECURE Hard Drive, they must:
• Specify the Android Bluetooth device again in the Imation SECURE Bluetooth Preferences
dialog box
• Make the Bluetooth device discoverable through the app
For more information on modifying authentication credentials, including Bluetooth preferences,
please refer to “Modifying Authentication Credentials” on page 17.
Page 14
Page 16

To retain use of the Imation SECURE Drive App when modifying authentication credentials
1. In the Imation SECURE Hard Drive software, start to modify the authentication credentials
for the Imation SECURE Hard Drive.
2. Move through this process until the Imation SECURE Bluetooth Preferences dialog box
displays.
3. If desired, choose a different Bluetooth authentication option.
4. Select the Use Current Bluetooth Device check box.
5. On the Android Bluetooth device, open the app and unlock the drive, if the drive is not
already open and unlocked.
6. On the Drives screen, touch and hold the drive associated with the Imation SECURE Hard
Drive until the drive menu displays.
7. Touch the Enable Setup option.
8. In the Bluetooth permission request message, touch Yes.
9. In the Imation SECURE Hard Drive software, click OK in the Imation SECURE Bluetooth
Preferences dialog box.
Delete drive from app
Users can delete drives from the Drives screen. Once a user has deleted a drive from the app,
the Imation SECURE Hard Drive software cannot use the Android Bluetooth device for
authentication. To authenticate their drive, they must enter their password and hint answer.
The user can specify the Bluetooth device again, with or without the app, when changing their
authentication credentials.
To delete a drive from the app
1. On the Drives screen, touch and hold the desired drive until the drive menu displays.
2. Touch the Delete Drive option in the menu.
3. In the confirmation message, touch the Delete button.
The drive no longer displays on the Drives screen.
Use the Wake Lock feature
During sleep mode for some Android Bluetooth devices, the Bluetooth feature is disabled. In this
case, users cannot authenticate the Imation SECURE Hard Drives that are associated with the
app, even if the drive in the app is unlocked.
The Wake Lock feature of the app enables the user to keep the Bluetooth feature enabled all of
the time, even when the Bluetooth device is in sleep mode. Using this feature increases the
amount of energy drained from the device’s battery, so it is recommended to only enable this
feature when necessary.
To keep Bluetooth enabled through the Wake Lock feature
1. With the Imation SECURE Drive App open, touch the menu button of the Bluetooth device,
which is located underneath the app screen.
2. Touch the Turn Wakelock ON option.
Page 15
Page 17

3. In the warning message, touch the Yes button.
4. To disable the Wake Lock feature, repeat this procedure and touch the Turn Wakelock OFF
option.
Access information about the app
Users can access basic information about the app through the Info screen.
To access the Info screen
1. With the Imation SECURE Drive App open, touch the menu button of the Bluetooth device,
which is located underneath the app screen.
2. Touch the Info option.
The Info screen displays.
Page 16
Page 18

V. Modifying Authentication Credentials
Users can modify any or all details of the authentication credentials for their Imation SECURE
Hard Drive through the Change Authentication option on the Imation SECURE Hard Drive
software menu. For example, they can change their authentication option, password, or
Bluetooth authentication device.
Verify credentials
To modify authentication, after selecting Change Authentication, the user must verify their
current credentials through the Imation SECURE Authenticate Changes to Credentials dialog
box. As with routine hard drive authentication, the verification requirements depend on the
authentication option that the used has selected for the hard drive.
• With password only and Bluetooth or password authentication, the user can choose to
provide either their password or hint answer for verification
• With Bluetooth and password authentication, the user must provide both their password
and hint answer for verification
Page 17
Page 19

Modify credential details
After the software verifies the user’s authentication credentials, the user can use the Imation
SECURE Change Authentication and Imation SECURE Bluetooth Preferences dialog boxes to
modify authentication details.
The Imation SECURE Change Authentication dialog box appears and functions the same way
as the Imation SECURE Setup dialog box. The only difference is that this dialog box displays
with some or all of the current password and hint information pre-populated when it opens.
Modify authentication option and/or Bluetooth device
With one exception, the Imation SECURE Bluetooth Preferences dialog box is the same dialog
box that the user accesses during setup of their hard drive and behaves the same way.
If the user previously specified a Bluetooth device for authentication, the Use Current Bluetooth
Device check box displays on the Bluetooth preferences dialog box. If they select this check
box, they can use the same Bluetooth device for authentication without having to re-discover all
available Bluetooth devices.
If the user has previously specified an Android Bluetooth device and installed and configured
the Imation SECURE
Drive App on it, they must enable the drive through the app when
changing their credentials if they want to continue using the app with the Bluetooth device.
VI. Using the Imation SECURE Hard Drive Software Menu
To view the Imation SECURE Hard Drive software menu, right-click the icon to display a
context menu of available functions. Select the menu entry to access the feature.
View Manual
This option enables the user to open this document, as long as they have the Adobe® Acrobat®
Reader software installed on their PC.
Change Authentication
This option enables the user to modify their authentication credentials. For more information,
please refer to “Modifying Authentication Credentials” on page 17.
Upgrade Java
This option stops the parts of the Imation SECURE Hard Drive software that use Java so that the
user can upgrade their Java software. If they do not choose this option, they may encounter
difficulties in upgrading it. After they upgrade Java, they must restart their PC to use the Imation
SECURE Hard Drive software again. Please note that this option does not initiate and run the
Java software upgrade.
Page 18
Page 20

Check Product Version
This option enables the user to find out if they have a current version of the Imation SECURE
Hard Drive software installed on their PC.
• If a newer version of the software is available, a message displays that contains a link that
the user can use to access an Imation Web site software download page. They can update
their software through the download page.
• If the software version is current, a message displays that the user is running the latest
version of the software.
• If the most current version of the software is unclear, a message displays that the Imation
SECURE Hard Drive software is unable to determine the most recent version. This message
enables the user to navigate to the Imation Support Web site to manually check for product
updates.
Encrypt Unencrypted Files
This option enables the user to choose to automatically encrypt all unencrypted files that exist
on their Imation SECURE Hard Drive. After the user selects Encrypt Unencrypted Files from the
context menu, the next time that they authenticate their drive, the Imation SECURE Hard Drive
software encrypts all unencrypted files on the drive.
About
This option displays information regarding the Imation SECURE Hard Drive and Imation SECURE
Hard Drive software, including software version number, drive information, type of encryption,
and current authentication information and status.
The license agreement text displays when the user clicks License Agreement.
VII. Accessing Encrypted Data without the Imation SECURE Hard Drive Software
After the Imation SECURE Hard Drive software encrypts data on a drive, the user can only
decrypt the information on machines that have the Imation SECURE Hard Drive software
installed on them. If they connect the drive to a machine that does not have the software
installed on it, the information will remain encrypted and inaccessible.
Note: When using a machine that does not have the Imation SECURE Hard Drive software
installed on it, if the user copies files to their Imation SECURE Hard Drive, the files will be written
to it unencrypted. When the user connects the hard drive to a machine that has the Imation
SECURE Hard Drive installed on it, the information will remain unencrypted unless they choose
to encrypt them through the Encrypt Unencrypted Files option on the Imation SECURE Hard
Drive menu.
VIII. Troubleshooting
Following are some common questions about installing and using the Imation SECURE Hard
Drive software.
Question: I copied the Imation SECURE Hard Drive software installation file to a location on my
computer from an Imation SECURE Hard Drive and tried to install it from that location. How
come I can’t install the software?
Answer: You must run the Imation SECURE Hard Drive software installation file directly from the
Imation SECURE Hard Drive. It will not function if copied to another location and executed.
Page 19
Page 21

Question: I want to use my Imation SECURE Hard Drive on a second computer. How do I do
this?
Answer: The Imation SECURE Hard Drive software can be installed on as many computers as
you wish. Simply run the installation file from the hard drive on the new computer that you want
to use.
Question: What happens if I format my Imation SECURE Hard Drive? Can I still use this hard
drive with the Imation SECURE Hard Drive software?
Answer: If you reformat the Imation SECURE Hard Drive in a machine that has Imation SECURE
Hard Drive software installed on it or insert a reformatted hard drive into such a machine, the
software copies the Imation SECURE Hard Drive software installation, user manual, and
TotalMedia Backup software installation files to the root of the hard drive and the setup dialog
box displays. You can then set up the hard drive for use with the software.
Question: Can I specify more than one Bluetooth device to authenticate my Imation SECURE
Hard Drive?
Answer: No, you can only specify one Bluetooth device per drive for authentication. However, if
have more than one drive, you use a range of Bluetooth devices or re-use the same Bluetooth
device for all drives.
Question: When specifying a Bluetooth device through the Imation SECURE Bluetooth
Preferences dialog box, I selected a Bluetooth option, made my device discoverable, and
clicked Discover. Why did my device not display in the list of Bluetooth devices?
Answer: Occasionally, the Imation SECURE Hard Drive software cannot find the Bluetooth name
for a device initially. However, if you click Discover again, the software will find it and the device
will display in the list.
Question: I successfully specified an iPod
®
as my Bluetooth authentication device. However,
when I try to authenticate, the Imation SECURE Hard Drive software does not recognize my
iPod as an authentication device. What can I do?
Answer: Unlike most Bluetooth devices, some Apple products with Bluetooth do not
automatically authenticate Imation SECURE Hard Drives. If a user experiences problems
authenticating their drive with an Apples device, they should make the Apple device
discoverable through Bluetooth before attempting to authenticate. (To make their Apple device
discoverable, they should follow the same procedure that they used when adding the device for
authentication.)
Question: My backup software is not working with the Imation SECURE Hard Drive software.
What can I do?
Answer: We do not claim compatibility with any backup software other than TotalMedia
Backup, version 2.0 or higher. The installation file for this backup software (TMB Software
Installer) is located on the root of the Imation SECURE Hard Drive when it is purchased.
Question: I have questions about the Imation SECURE Hard Drive software. How do I get help?
Answer: Email support at techsupport@imation.com or access the Imation Web site at
www.imation.com
and select Support to open the support page.
Page 20
Page 22

IX. Copyright and Trademark Information
© Imation Corp. Imation, Imation SECURE, and the Imation logo are trademarks of Imation Corp.
All other trademarks are property of their respective owners.
X. Contacting Imation
Email H techsupport@imation.com
Web site www.imation.com
Address 1 Imation Way, Oakdale, MN 55128-3421
66951534-A
Page 21
 Loading...
Loading...