Page 1

www.imagistics.com
User's Guide
Network Scanner
im9220
Page 2

im9220 i
Table of contents
1 Introduction
1.1 Introduction ....................................................................................... 1-3
1.1.1 ACKNOWLEDGEMENTS: .............................................................. 1-3
1.1.2 EXEMPTION ................................................................................... 1-3
1.1.3 OpenSSL Statement ...................................................................... 1-3
1.2 Composition of User's Guide .......................................................... 1-7
1.3 About this Manual ............................................................................. 1-8
1.3.1 Manual Composition ...................................................................... 1-9
1.3.2 Conventions Used in this Manual ................................................ 1-10
1.3.3 Utility Tools of This Product ......................................................... 1-11
1.3.4 How to read this Manual .............................................................. 1-12
2 Overview of the Scanning Features
2.1 Overview of Features and Connection Modes ............................... 2-3
2.1.1 Copied Data Processing Features ................................................. 2-3
2.1.2 Network Scanner Features ............................................................ 2-4
2.2 Product Specifications ..................................................................... 2-5
3 Before Using the Scanning Features
3.1 About the Control Panel ................................................................... 3-3
3.2 How to operate the Touch Panel .................................................... 3-5
3.3 How to Input Characters .................................................................. 3-7
3.3.1 About keys on the character input screen ..................................... 3-7
3.3.2 About character input .................................................................... 3-7
3.4 How to Search .................................................................................. 3-8
3.4.1 Destination Search (Search Features on the [Scan] screen) .......... 3-8
3.4.2 Searching a box/file ....................................................................... 3-9
4 About the Copied Data Processing Features
4.1 Overview of the Store/Recall Features ........................................... 4-3
4.1.1 About folders and boxes ................................................................ 4-4
Page 3

ii im9220
4.2 About Screens of the Store/Recall ..................................................4-6
4.2.1 About common keys on the list screens .........................................4-6
4.3 Registering a Personal Folder ..........................................................4-7
4.4 Deleting a Personal Folder ...............................................................4-9
4.5 Creating a Box (Personal Folder/Public Folder) ...........................4-11
4.6 Deleting a Box (Personal Folder/Public Folder/Confidential Folder) .
4-14
4.7 Selecting a Storage Location .........................................................4-17
4.8 About the Copied Data Storage Setting Screen ...........................4-25
4.9 Changing Data Transmission Method to PC ................................4-28
4.10 Output from the Internal HDD ........................................................4-31
4.11 About Output Setting Screen of the Recall Function ...................4-34
4.11.1 Keys on the setting screen ...........................................................4-34
4.11.2 The flow of operation of the Wait Output and Proof Output .........4-35
5 About the Network Scanner Features
5.1 Overview of the Network Scanner Features ...................................5-3
5.2 Send by an E-Mail ..............................................................................5-5
5.2.1 Items to be configured ....................................................................5-5
5.3 Store on the HDD ...............................................................................5-7
5.3.1 Items to be configured ....................................................................5-7
5.4 Send to the FTP server .....................................................................5-8
5.4.1 Items to be configured ....................................................................5-8
5.5 Send to the SMB server ..................................................................5-10
5.5.1 Items to be configured ..................................................................5-10
5.6 Send to a Group ...............................................................................5-12
5.7 Use the Network Scanner Features ...............................................5-13
6 Configuring Destination for the Network Scanner
Features
6.1 About Registration ............................................................................6-3
6.1.1 Change/delete destinations/storage locations ...............................6-3
6.1.2 The keys on the Address Input screen ...........................................6-3
6.2 Address Input Registering an E-Mail Address ................................6-5
6.3 Registering the HDD .........................................................................6-7
Page 4

im9220 iii
6.4 Registering the FTP server .............................................................. 6-9
6.5 Registering the SMB server ........................................................... 6-11
6.6 Registering a Group ....................................................................... 6-13
7 Using the Network Scanner Features
7.1 The keys on the Select Destinations/Storage Locations Screen . 7-3
7.2 Transmission to an E-Mail Address ................................................ 7-5
7.3 Storage on the HDD ......................................................................... 7-9
7.4 Transmission to the FTP server .................................................... 7-12
7.5 Transmission to the SMB server ................................................... 7-16
7.6 Transmission to a Group ................................................................ 7-20
8 Configuring the Network Scanner features
8.1 About the Scanner Setting Basic Screen ....................................... 8-3
8.2 Reading in from HDD ....................................................................... 8-7
8.2.1 Network Scanner Driver ................................................................. 8-7
8.3 To install the Network Scanner Driver ............................................ 8-9
8.4 Import Scanned Data to Computers ............................................. 8-10
8.4.1 TWAIN-compliant applications can be used to read in scanned data
8-10
8.5 Features and Settings of the Network Scanner Driver ............... 8-13
9 About the Confidential Folder
9.1 Overview of the Confidential Folder ............................................... 9-3
9.2 Creating a Box (Confidential Folder) ............................................... 9-4
9.3 Deleting a Box (Confidential Folder) ............................................... 9-6
9.4 Output from the Confidential Folder ............................................... 9-7
10 Troubleshooting
10.1 Cannot connect to the scanner ..................................................... 10-3
10.2 When an Error Message Appears ................................................. 10-5
10.2.1 Errors during scanning with the [Scan] function .......................... 10-5
10.2.2 Errors during scanning with the Store function ........................... 10-8
11 Utility Tools
11.1 JobEditor ......................................................................................... 11-3
Page 5

iv im9220
11.1.1 How to use JobEditor ...................................................................11-4
11.2 JobEditorServer ...............................................................................11-9
11.2.1 How to use JobEditorServer .......................................................11-10
12 Appendix
12.1 Glossary ............................................................................................12-3
12.2 Index .................................................................................................12-6
Page 6

1
Introduction
Page 7

Page 8

Introduction
1
im9220 1-3
1 Introduction
1.1 Introduction
Thank you very much for purchasing an Imagistics im9220 and Printer Controller (92BW-1).
This User's Guide describes the im9220’s scanning features. Be sure to read
the "User's Guide (Copy) ‘Safety Information’" before operating the im9220.
1.1.1 ACKNOWLEDGEMENTS:
- Imagistics and the Imagistics Logo are trademarks of Imagistics Interna-
tional Inc., registered in the U.S. Patent and Trademark office and/or other jurisdictions.
- Microsoft, MS, Windows and MS-DOS are registered trademarks or
trademarks of Microsoft Corporation in the United States and / or other
countries.
- IBM is a registered trademarks of the IBM Corporation.
- Macintosh and PowerMac are registered trademarks or trademarks of
Apple Computer, Inc. in the United States and / or other countries.
- Adobe, Adobe Logo, Acrobat, Acrobat Logo, PostScript and PostScript
Logo are registered trademarks or trademarks of Adobe Systems, Inc..
- RC4® is a registered trademark or trademark of RSA Security Inc. in the
United States and/or other countries.
- Other company names and product names used in this manual are the
registered trademarks or trademarks of their respective companies.
Copyright © 2005 Imagistics International Inc.
1.1.2 EXEMPTION
- No part of this manual may be used or duplicated without permission.
- Manufacturer and Sales Company will have no liability for any influences
caused by using the printing system and this User’s Guide.
- The information written in this Network Scanner User’s Guide is subject
to change without prior notice.
1.1.3 OpenSSL Statement
OpenSSL License
Copyright (c) 1998-2000 The OpenSSL Project. All rights reserved.
Page 9

1
Introduction
1-4 im9220
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must
display the following acknowledgment:
– "This product includes software developed by the OpenSSL Project for
use in the OpenSSL Toolkit. (http://www.openssl.org/)"
4. The names "OpenSSL Toolkit" and "OpenSSL Project" must not be used
to endorse or promote products derived from this software without prior
written permission. For written permission, please contact opensslcore@openssl.org.
5. Products derived from this software may not be called "OpenSSL" nor
may "OpenSSL" appear in their names without prior written permission
of the OpenSSL Project.
6. Redistributions of any form whatsoever must retain the following acknowledgment:
– "This product includes software developed by the OpenSSL Project for
use in the OpenSSL Toolkit (http://www.openssl.org/)"
THIS SOFTWARE IS PROVIDED BY THE OpenSSL PROJECT ``AS IS'' AND
ANY EXPRESSED OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT
SHALL THE OpenSSL PROJECT OR ITS CONTRIBUTORS BE LIABLE FOR
ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR
PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON
ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY,
OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY
WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
POSSIBILITY OF SUCH DAMAGE.
This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com).
This product includes software written by Tim Hudson (tjh@cryptsoft.com).
Original SSLeay License
Copyright (C) 1995-1998 Eric Young (eay@cryptsoft.com) All rights reserved.
Page 10

Introduction
1
im9220 1-5
This package is an SSL implementation written by Eric Young (eay@cryptsoft.com). The implementation was written so as to conform with Netscapes
SSL.
This library is free for commercial and non-commercial use as long as the following conditions are aheared to. The following conditions apply to all code
found in this distribution, be it the RC4, RSA, lhash, DES, etc., code; not just
the SSL code.
The SSL documentation included with this distribution is covered by the
same copyright terms except that the holder is Tim Hudson (tjh@cryptsoft.com).
Copyright remains Eric Young's, and as such any Copyright notices in the
code are not to be removed. If this package is used in a product, Eric Young
should be given attribution as the author of the parts of the library used. This
can be in the form of a textual message at program startup or in documentation (online or textual) provided with the package.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
1. Redistributions of source code must retain the copyright notice, this list
of conditions and the following disclaimer.
2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
3. All advertising materials mentioning features or use of this software must
display the following acknowledgement:
– "This product includes cryptographic software written by Eric Young
(eay@cryptsoft.com)"
– The word 'cryptographic' can be left out if the rouines from the library be-
ing used are not cryptographic related :-).
4. If you include any Windows specific code (or a derivative thereof) from
the apps directory (application code) you must include an acknowledgement:
– "This product includes software written by Tim Hudson (tjh@crypt-
soft.com)"
THIS SOFTWARE IS PROVIDED BY ERIC YOUNG ``AS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO,
THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES
(INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING
Page 11

1
Introduction
1-6 im9220
NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE
OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH
DAMAGE.
The licence and distribution terms for any publically available version or derivative of this code cannot be changed. i.e. this code cannot simply be copied and put under another distribution licence [including the GNU Public
Licence.]
Page 12

Introduction
1
im9220 1-7
1.2 Composition of User's Guide
This machine is provided with the following user's guides as printed matters.
im9220 User's Guide - Copier Operations
This guide describes an outline of the machine and copy operations.
Please refer to this guide for safety information, turning on/off the machine,
paper supply, dealing with machine trouble such as paper jam, and copy operation available on the machine.
im9220 User's Guide - POD Administrator's reference
This guide provides you with detailed information about the machine management and how to customize the machine according to your daily use.
Please refer to this guide for a setup and management of the machine including registration of copy paper, tray setting, and a network setup.
im9220 User's Guide - Network Scanner <This book>
This guide describes the operation of the network scanner function equipped
for the machine as standard.
Please refer to this guide for full information on reading data or storing data
(Scan to HDD, Scan to E-Mail, Scan to FTP, Scan to SMB).
im9220 User's Guide - Security Functions
This guide describes the security functions.
Please refer to this guide for how to use the Enhanced Security mode, and
for detailed machine operation in Enhanced Security mode.
The following user's guide is also provided as a PDF file.
im9220 User's Guide - 92BW-1 Printer Controller
This guide describes the operation of the printer function equipped for the
machine as option.
Please refer to this guide for how to use the PCL driver, Adobe PS driver, PS
driver, and Web Connection in user mode.
Page 13

1
Introduction
1-8 im9220
1.3 About this Manual
This manual is the User's Guide for im9220 Network Scanner features.
This manual describes the functions which can be used by pressing the [Box]
and [Scan] buttons on the control panel.
!
Detail
To use the [Scan] button, the optional printer controller is required. Contact your service representative for details of the printer controller.
2
Reminder
A screen display may change with destinations.
A button name etc. may become the display in a parenthesis.
Refer to the User’s Guide (Copy) or the User’s Guide (POD Administrator
Reference) on how to use other button.
Page 14

Introduction
1
im9220 1-9
1.3.1 Manual Composition
This manual is composed of the following 12 chapters:
Chapter 1 Introduction
This chapter describes this User's Guide.
Chapter 2 Overview of the Scanning Features
This chapter overviews the Network Scanner features and the Copied Data
Processing Features.
Chapter 3 Before Using the Scanning Features
This chapter describes how to use Control Panel, Touch Panel, character input and search features.
Chapter 4 About the Copied Data Processing Features
This chapter describes the Copied Data Processing Features.
Chapter 5 About the Network Scanner Features
This chapter describes the operational flow of the Network Scanner features.
Chapter 6 Configuring Destination for the Network Scanner Features
This chapter describes destination/storage location for the Network Scanner
features.
Chapter 7 Using the Network Scanner Features
This chapter describes in detail how to use the Network Scanner features.
Chapter 8 Configuring the Network Scanner features
This chapter describes how to configure the Network Scanner features and
how to use the Scanner Driver.
Chapter 9 About the Confidential Folder
This chapter describes the Confidential Folder.
Chapter 10 Troubleshooting
This chapter describes how to solve major troubles in the Network Scanner
features and the Copied Data Processing Features.
Chapter 11 Utility Tools
This chapter describes the accompanying utility tools, JobEditor and
JobEditorServer.
Chapter 12 Appendix
The glossary and index regarding the scanning features.
Page 15

1
Introduction
1-10 im9220
1.3.2 Conventions Used in this Manual
Notation of each product
The following abbreviations are used in this manual:
1. 92BW-1 Print Controller print controller
2. 92BW-1PS: PS3 option
3. im9220 Printer/Copier: copier (or main body printer)
4. A printing system that combines the above
(1), (2) and (3) products: printing system
5. Microsoft Windows 98: Windows 98
6. Microsoft Windows Me: Windows Me
7. Microsoft Windows NT4.0: Windows NT4.0 or Windows NT
8. Microsoft Windows 2000: Windows 2000
9. Microsoft Windows XP: Windows XP
10. Macintosh OS 8.x - 9.x Mac OS 9
11. Macintosh OS X v10.2x - v10.3x Mac OS X
12. Above OSs: Windows 98/Me
Windows NT4.0/2000/XP
Windows NT/2000/XP
Windows 95/98/Me/NT/2000/
XP
Mac OS 9/X
Page 16

Introduction
1
im9220 1-11
1.3.3 Utility Tools of This Product
The utility tools used in the Network Scanner features are as follows. For
more information on how to operate the utility tools, refer to the User's Guide
for the each or the corresponding pages of this manual.
Generic Scanner Driver (TWAIN-compliant)
This driver creates a connection between a computer and the copier, by
which the scanned data stored in the box are imported to the computer. You
are to use application software compliant with TWAIN scanner driver. Data
types that can be handled by this driver are limited only to the TIFF.
For more information, refer to "Reading in from HDD" on Page 8-7.
ScanDirect/Pro
This software creates a connection between a computer and the copier, by
which the scanned data stored in the box are imported to the computer. Data
types that can be handled by this software are the TIFF and the PDF.
For more information, refer to the User's Guide for ScanDirect/Pro.
JobEditor
This optional software creates a connection between a computer and the
copier. It stores the copied data in the computer, and sends back the copied
data stored and edited in the computer to the copier.
For more information, refer to "JobEditor" on Page 11-3.
JobEditorServer
This software creates a connection between a computer and the copier. It
stores the copied data in the computer automatically, and sends back the
copied data stored and edited in the computer to the copier.
For more information, refer to "JobEditorServer" on Page 11-9.
!
Detail
JobEditor and JobEditorServer are unavailable for the im9220.
To obtain JobEditor and JobEditorServer for older models, contact your
service representative.
Page 17
1
Introduction
1-12 im9220
1.3.4 How to read this Manual
About the Copied Data Processing Features
4
bizhub PRO 920 Scanner 4-7
4.3 Registering a Personal Folder
A Personal Folder is registered (created) for each user, where you manage
data you want to Store/Recall. Register a Personal Folder in the following
steps.
!
Detail
At maximum, 1000 Personal Folers can be registered.
1 Press [Box] on the control panel and
then press [Store] key.
2 Press the [Scan to HDD] key.
3 Select the [Personal Folder] key.
4 Press the [New Register] key.
5 Press the [FolderName Input] key to
display the character input screen.
Input any Folder Name.
Input a Folder Name within 64
characters in alphameric characters and signs.
For more information on how to input characters, refer to "How to
Input Characters" on Page 3-7.
The below characters cannot be registered as a Folder Name irre-
spectively whether they are upper or lower case.
Public, Admin, BoxAdmin
Reminder!
Explains important notices
on operating procedures.
[ ] are used for the terms
displayed on the screens.
Detail
Hints and Advices on
operating procedures.
Note
Explanations to supplement
the body.
Memoes may be included in
the body.
Describes operating
procedures.
Show an object and feature
of a procedure.
This page does not exist in the document.
Page 18

2
Overview of the Scanning
Features
Page 19

Page 20

Overview of the Scanning Features
2
im9220 2-3
2 Overview of the Scanning Features
2.1 Overview of Features and Connection Modes
im9220 copier has the Copied Data Processing Features and the Network
Scanner features.
2.1.1 Copied Data Processing Features
The Copied Data Processing features enable you to import and process copied documents that are converted to digital data (copied data) and stored on
the internal HDD of the copier using the accompanying utility tool, JobEditor.
The processed copied data can be returned to the internal HDD and re-output anytime.
Also, copied data on the internal HDD can be re-output whenever necessary.
With this, you can conveniently print out the document many times.
The Copied Data Processing Features are operated by using the [Box] button
on the control panel.
!
Detail
For more information on the Copied Data Processing Features, refer to
"About the Copied Data Processing Features" on Page 4-3.
For more information on JobEditor, refer to "JobEditor" on Page 11-3.
!
Detail
JobEditor and JobEditorServer are unavailable for the im9220.
To obtain JobEditor and JobEditorServer for older models, contact your
service representative.
Page 21

2
Overview of the Scanning Features
2-4 im9220
2.1.2 Network Scanner Features
The Network Scanner features enable the followings by converting a
scanned document to digital data.
- Sending data by an E-Mail. "Send by an E-Mail" (p.5-5)
- Storing on the internal HDD. "Store on the HDD" (p.5-7)
- Sending to the FTP server. "Send to the FTP server" (p.5-8)
- Sending to the SMB server. "Send to the SMB server" (p.5-10)
- Importing data stored on the
internal HDD to the network-connected computer.
– "Import Scanned Data to Computers" (p.8-10)
The Network Scanner features are operated by using the [Scan] button on
the control panel.
!
Detail
To use the network scanner features, the optional printer controller is required. Contact your service representative for details of the printer controller.
To use the copier as a network scanner, it needs to be connected to the
network. For more information on the network configuration, contact your
network administrator.
Page 22
Overview of the Scanning Features
2
im9220 2-5
2.2 Product Specifications
For information on the product specifications of the copier, the print controller and the network, refer to the User's Guide for the each or contact your
administrator for the each.
Product Specifications of Scanning Features
The specifications of the configurable items for reading except File Form, File
Name and Address are in accordance with that of the copier. For more information, refer to the User's Guide (Copy)
Item Specifications
Original type sheet/book/cubic object
Max. original size A3 (297mm × 420mm) /11" × 17" (279.4mm ×
432mm)
Cubic object Thickness: Max. 30mm
Weight: Max. 6.8kg
Original position Deep-left-sided
Scanning resolution 200dpi, 300dpi, 400dpi, 600dpi
Reading speed A4 : Simplex 92pages/minute
Duplex 46 pages/minute
8.5 × 11 : Simplex 92pages/minute
Duplex 46 pages/minute
Interface Ethernet(100BASE-TX/10Base-T)
Reading modes • Scan to HDD
• Scan to FTP
•Scan to SMB
•Scan to E-Mail
Compression method MMR compression for TIFF/PDF format files
Compression method can be changed to MH compression
For more information, contact your service representative.
Configurable items for reading Original Setting, Special Image, Zoom, Application,
Scan Size, Quality, Copy Mode, File Form, File
Name, Address
Page 23

2
Overview of the Scanning Features
2-6 im9220
Page 24

3
Before Using the
Scanning Features
Page 25

Page 26

Before Using the Scanning Features
3
im9220 3-3
3 Before Using the Scanning Features
3.1 About the Control Panel
For detailed information on names and functions of various parts of the Control Panel, refer to the User's Guide (Copy).
No. Name Description
1 [Mode Memory] key Displays screens for selecting job store/job recall
functions.
2 [Access] key Sets the machine to allow copying/scanning/
printing only when the User Authentication/Volume
Track password is entered.
3 [Box] key Press to store the image data in HDD of the main
body or on a PC over a network, or to recall the
stored data. The indicator of the key will light when
pressed. For details, see im9220 User’s Guide Network Scanner.
4 [Scan] key Press to scan the original images, or to specify the
address for data transmission. The indicator of the
key will light when pressed. For details, see im9220
User’s Guide - Network Scanner.
5 [Copy] key Press to operate copying functions. The indicator
of the key will light when pressed.
6 Keypad Enters numeric value such as print quantity.
7 [Proof Copy] key Outputs a single set of copies to confirm whether
the current settings are selected properly.
8 [Reset] key Restores copier to the initial settings.
9 [Interrupt] key Stops copying/scanning/printing in progress to
allow a simple copying job.
120 21 22 2 3 4 5 6 7 8 9
10121314141516171819
Page 27
3
Before Using the Scanning Features
3-4 im9220
10 [Stop] key Ceases the copying sequence; deletes the stored
memory.
11 [Start] key Activates each function. The Start LED lights in
green when machine operation is available, and
turns orange if any operation cannot be started.
12 Main Power indicator Lights in red when the main power switch is turned
on, then turns green when the subswitch is turned
on.
13 Data indicator Flashes while receiving print data.
14 [C] (clear) key Allows resetting of print quantity.
15 [Utility/Counter] key Displays the Utility Menu Screen or Counter
Screen.
16 [Mode Check] key Displays a screen showing all settings that are se-
lected for the current job.
17 Touch panel Displays machine and copying status, help
information, interactive screens, and touch keys for
selecting all functions.
18 [Accessibility] key Adjusts the response time when touch panel keys
or control panel keys are pressed.
19 Contrast adjustment dial Can be turned to adjust the brightness of the touch
panel (positioned at the back).
20 Power Save LED Lights when any power-saving mode is activated,
or machine power is off due to the timer function.
21 [Power Save] key Enables temporary use of the machine when the
Power Save LED is lit, or activates power-saving
mode for times when the copier is inactive.
22 [Help] key Displays a screen with help for the currently
selected function.
No. Name Description
Page 28

Before Using the Scanning Features
3
im9220 3-5
3.2 How to operate the Touch Panel
To operate the Network Scanner features/Copied Data Processing Features,
use the Touch Panel of the copier.
!
Detail
You can select an item by touching keys lightly on the Touch Panel.
Select a function
Touch a function displayed in a key to select the function.
The selected key is highlighted.
To input values
Touch lightly the KEYPAD on the Touch Panel to input the specified values.
!
Detail
You may also input values through the KEYPAD on the Control Panel.
For more information on how to input characters, refer to "How to Input
Characters" on Page 3-7.
Page 29
3
Before Using the Scanning Features
3-6 im9220
To switch between pages
When all items cannot be displayed in a single page, touch lightly the /
key to switch between pages.
Page 30

Before Using the Scanning Features
3
im9220 3-7
3.3 How to Input Characters
As you touch the item where you can input characters, the character input
screen appears.
You can input alphabets and signs. Character array is the same with computer keyboards.
3.3.1 About keys on the character input screen
Keys on the character input screen are described here.
3.3.2 About character input
The followings describe basic steps to input characters on the character input screen.
1 Press the corresponding key to input the desired character.
2 Press the [OK] key.
The character input screen closes. The input characters are displayed
on the corresponding column.
Button Function
/ This key moves a cursor.
Delete This key deletes the character on the left of the cursor.
OK This key determines the characters you input, and the charac-
ter input screen closes.
Cancel This key cancels the characters you input, and the character
input screen closes.
Shift This key switches between an upper case letter and a lower
case letter, and between numbers and signs.
Page 31

3
Before Using the Scanning Features
3-8 im9220
3.4 How to Search
The Network Scanner features/Copied Data Processing Features enables
you to search the registered destination and specified storage location by
their names. You can also search the stored UserBoxNumber.
3.4.1 Destination Search (Search Features on the [Scan] screen)
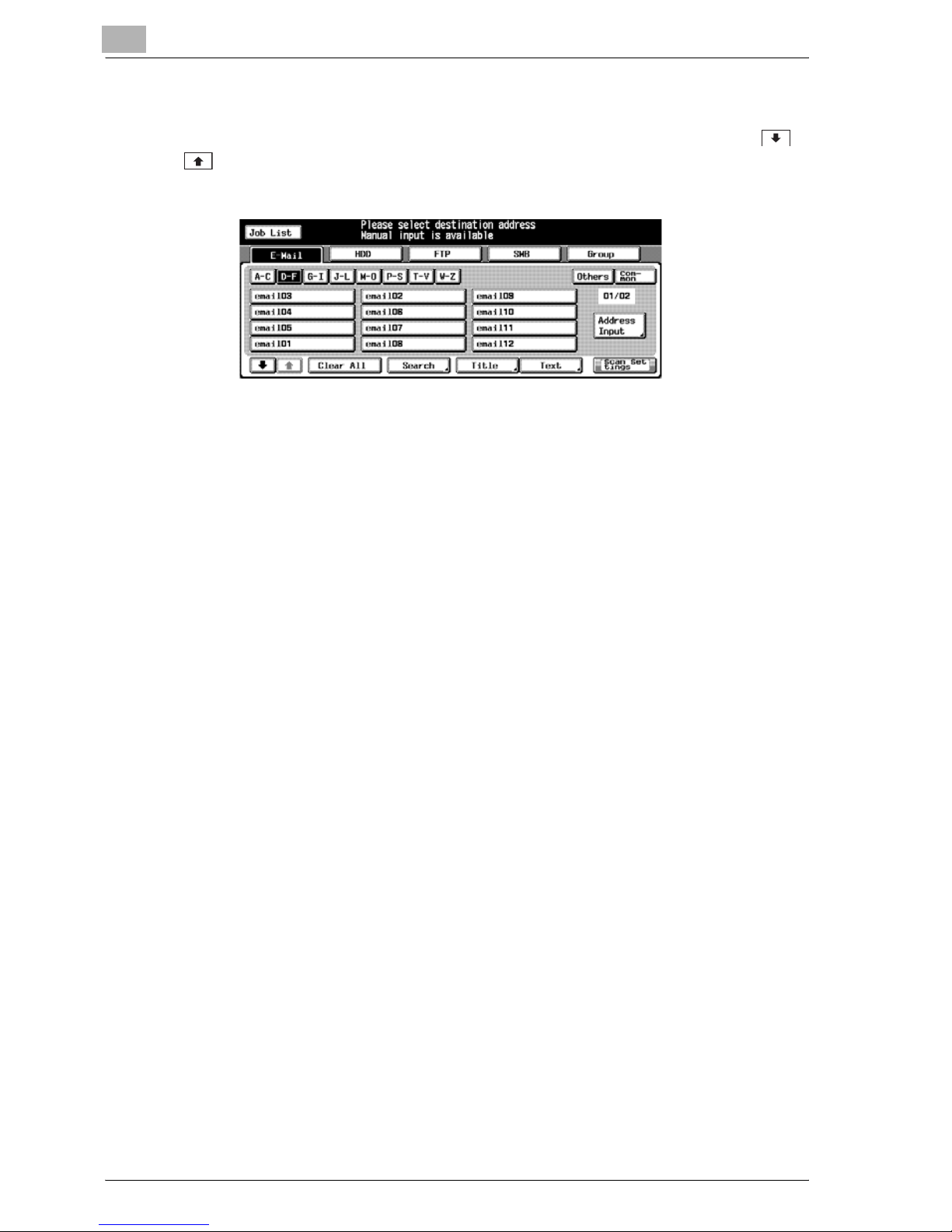
You can search the desired destination out of the registered destinations.
You can use the features on the [Scan] screen.
Search
In the [Scan] screen, you can search the registered destination by using the
[Search] key. Searchable destinations include E-Mail addresses, storage locations on the internal HDD, FTP server addresses and SMB server addresses.
The following is how to use the [Search] key.
1 Press the [Search] key.
The search letter input screen appears.
2 Input the Character for Search you registered, and press the [OK] key.
The desired destination will be displayed.
Page 32

Before Using the Scanning Features
3
im9220 3-9
!
Detail
You can search by at minimum one character.
If the search results are too many, press the [Search] key to add search
letters (The search letters you entered are saved until you operate scanning).
Pressing the [Cancel] key cancels the input search letters, and the search
letter input screen closes.
3.4.2 Searching a box/file
In the Copied Data Processing Features, you can search quickly the desired
box out of the boxes created on the internal HDD by its UserBoxNumber.
Also, if you know the Folder Name, Box Name and File Name, you can perform the Direct Call.
Number Search
In the [Box] screen, you can search the registered UserBoxNumber by using
the [Number Search] key.
The following is how to use the [Number Search] key.
1 Press the [Number Search] key.
The Number Search screen appears.
2 Input the UserBoxNumber you want to search, press the [OK] key.
The screen appears to display the list of files that are in the corresponding box.
When a corresponding box does not exist, the message "No correspondent box" appears. Confirm the UserBoxNumber, and return to
the step 1 to repeat the procedures.
Page 33

3
Before Using the Scanning Features
3-10 im9220
!
Detail
Pressing the [Cancel] key cancels the input UserBoxNumber, and the
Number Search screen closes.
If a password is configured for the box, you need to enter the password.
Direct Call
If you know all the registered Folder Name, Box Name and File Name, or if
you know the Box Name and File Name, you can select the file by using the
[Direct Call] key in the [Store] / [Recall] screen.
The following is how to use the [Direct Call] key.
1 Press the [Direct Call] key.
– If you press the [Direct Call] key
on the box list screen, the Box
Name input screen appears.
– If a folder or a box is Password-
protected, you cannot search it
with the Direct Call.
The Folder Name input screen appears.
2 Input the Folder Name and press
the [OK] key.
– For more information on how to
input characters, refer to "How
to Input Characters" on Page 3-
7.
The Box Name input screen appears.
3 Input the Box Name and press the
[OK] key.
– For more information on how to
input characters, refer to "How
to Input Characters" on Page 3-
7.
The File Name input screen appears.
Page 34

Before Using the Scanning Features
3
im9220 3-11
4 Input the File Name and press the
[OK] key.
– When a corresponding file does
not exist, the message "Failed
direct call" appears. Confirm
that the Folder Name, Box
Name and File Name are correct, and return to the step 1 to repeat
the procedures.
The screen appears with the desired file being selected.
!
Detail
For more information on how to input characters, refer to "How to Input
Characters" on Page 3-7.
If the desired file is not found, you are brought back to the list screen, and
the message is displayed on the upper left of the Touch Panel.
Page 35

Page 36

4
About the Copied Data
Processing Features
Page 37

Page 38

About the Copied Data Processing Features
4
im9220 4-3
4 About the Copied Data Processing Fea-
tures
4.1 Overview of the Store/Recall Features
You can import and process copied data stored on the internal HDD of the
copier using the accompanying utility tool, JobEditor. The processed copied
data can be returned to the internal HDD and re-output anytime. Copied data
on the internal HDD can be re-output whenever necessary. With this, you can
conveniently print out the document many times.
This enables you to combine a print job sent from a computer and copied
data to print as one job.
The store/recall function uses the [Store] and [Recall] screens displayed by
pressing the [Box] button on the control panel.
!
Detail
JobEditor and JobEditorServer are unavailable for the im9220.
To obtain JobEditor and JobEditorServer for older models, contact your
service representative.
When Security Strengthen Mode is ON, JobEditor and JobEditorServer
are not available. For more information, contact your administrator.
Personal A Personal B
Public
Confidential
Internal HDD
Original
Printing out
COPY/STORE
RECALL
TCP/IP Network Connection
Job Editor
Personal A
Copy
0001
Box
0001
Copy
0001
Box
0002
Copy
0001
Box
0003
Copy
0001
Box
0004
Copy
0001
Box
0005
Copy
0001
Box
0001
Page 39

4
About the Copied Data Processing Features
4-4 im9220
4.1.1 About folders and boxes
Copied data are managed by boxes created in folders on the internal HDD.
About Folders
Press the [Store] to store the data read in from the copier's ADF or the original scanning glass (scanned data) on the internal HDD. You can store data
in two types of folders, Personal Folder or Public Folder.
When you output the stored data on the internal HDD by using the [Recall]
screen, you can output files stored in three types of folders, Personal Folder,
Public Folder or Confidential Folder.
Details of each folder are as follows.
Personal Folder
A folder created for each user where data of the user is managed. A Password can be configured for each Personal Folder. For information on how to
add a Personal Folder, refer to "Registering a Personal Folder" on Page 4-7.
Public Folder
This folder is used as a public space. No Password can be configured for this
folder.
Confidential Folder
This folder stores data for confidential printing of the printing features. This
folder cannot be specified as a storage location by using the [Store] screen.
To use the [Confidential] function, the optional printer controller is required.
Contact your service representative for details of the printer controller.
About Boxes
Each folder has its boxes where data can be classified and managed.
Data are stored in these boxes.
A Password can be configured for a box. To open a box with a Password,
you need to input the Password.
Page 40

About the Copied Data Processing Features
4
im9220 4-5
Types of a folder, box and file
!
Detail
For more information on the Confidential Folder, refer to Chapter "9
About the Confidential Folder".
Types of a folder, box and file Number Create/Delete Naming
Personal Folder Multiple Able Able
Personal Folder - Box Multiple Able Able
Personal Folder - Box - File Multiple Able Able
Public Folder Single Unable Unable
Public Folder - Box Multiple Able Able
Public Folder - Box - File Multiple Able Able
Page 41

4
About the Copied Data Processing Features
4-6 im9220
4.2 About Screens of the Store/Recall
Screens of the Store/Recall include such screens on which to specify a storage location as the folder list screen (Personal Folder), the box list screen
(Personal Folder/Public Folder), and the file list screen.
There are also screens to create new folders (Personal Folder) or new boxes
(Personal Folder/Public Folder), screens to specify a storage location as a
UserBoxNumber, the Direct Call input screen and the Scanner Setting Basic
screen.
This page describes the keys on the list screens. The screens are different
depending on how to store data.
4.2.1 About common keys on the list screens
Here are the common keys on the folder list screen, the box list screen and
the file list screen.
Button Function
This is displayed on a Folder or a Box to which a password is configured.
Clear All Pressing this key deselects what you had selected, and you are
brought back to the first screen of the [Store]/[Recall].
/ Pressing these keys switches between pages when a whole list is
not displayed on a single page.
Cancel Pressing this key cancels each setting on the screen, and you are
brought back to the previous page.
OK Pressing this key determines the settings and brings you to the
next page. On the file list screen, pressing this key starts to transmit/output the selected file.
Page 42

About the Copied Data Processing Features
4
im9220 4-7
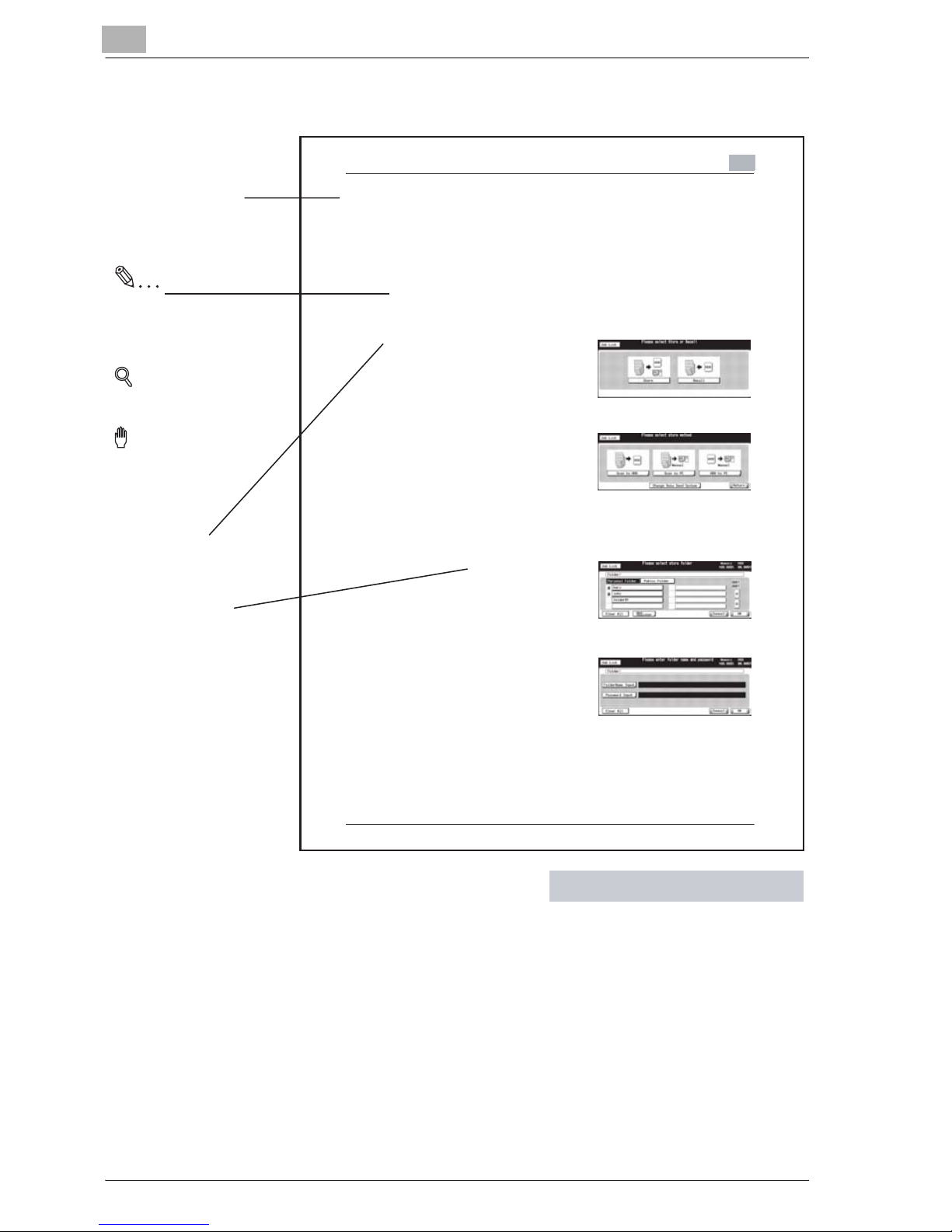
4.3 Registering a Personal Folder
A Personal Folder is registered (created) for each user, where you manage
data you want to Store/Recall. Register a Personal Folder in the following
steps.
!
Detail
At maximum, 1000 Personal Folders can be registered.
1 Press [Box] on the control panel and
then press [Store] key.
2 Press the [Scan to HDD] key.
3 Select the [Personal Folder] key.
4 Press the [New Register] key.
5 Press the [FolderName Input] key to
display the character input screen.
Input any Folder Name.
– Input a Folder Name within 64
characters in alphameric characters and signs.
– For more information on how to input characters, refer to "How to
Input Characters" on Page 3-7.
– The below characters cannot be registered as a Folder Name irre-
spectively whether they are upper or lower case.
Public, Admin, BoxAdmin
Page 43

4
About the Copied Data Processing Features
4-8 im9220
6 If you configure a Password for a
folder, press the [Password Input]
key to display the character input
screen. Input any Password.
– Input a Password within 64
characters in alphameric char-
acters and signs.
– The input Password is shown by "*".
– For more information on how to input characters, refer to "How to
Input Characters" on Page 3-7.
– Be sure to keep a record of the password.
7 Press the [OK] key.
The box list screen appears.
8 If you register only a folder, press
the [Cancel] key to go to the step 9.
If you register a box also, go to the
step 4 "Creating a Box (Personal
Folder/Public Folder)" on Page 4-
11.
9 Make sure that the Folder Name
you registered on the folder list is
displayed.
– If you want to register multiple
Personal Folders, return to the
step 4 and repeat the proce-
dures.
Page 44

About the Copied Data Processing Features
4
im9220 4-9
4.4 Deleting a Personal Folder
To delete a registered Personal Folder, follow the steps below.
1 Press [Box] on the control panel and
then press [Recall] key.
2 Press the [Personal Folder] key.
3 Select the folder you want to delete.
4 Press the [Folder Delete] key.
– If a Password is not configured
for the Folder, a screen appears
and confirms you whether to delete the folder. Go to the step 6.
If a Password is configured for the
Folder, the Password input screen appears.
5 Enter the Password and press the
[OK] key.
The confirmation screen appears
and confirms you whether to delete
the folder.
6 Press the [Yes] key.
The folder is deleted and the folder
list screen (Personal Folder) appears.
Page 45

4
About the Copied Data Processing Features
4-10 im9220
7 Confirm that the folder is deleted.
– When you want to delete those
Personal Folders or Personal
Boxes with unknown password,
your administrator can delete
such folders.
– Your administrator cannot have access to boxes in a Personal Fold-
er with unknown password. But deleting the folder enables him to
delete those boxes in the folder.
Page 46

About the Copied Data Processing Features
4
im9220 4-11
4.5 Creating a Box (Personal Folder/Public Folder)
The copied data are managed in boxes created in the folders of the internal
HDD (Personal Folder/Public Folder). Create a box by the following steps.
!
Detail
At maximum, 1000 Boxes can be registered.
1 Press [Box] on the control panel and
then press [Store] key.
2 Press the [Scan to HDD] key.
3 Select a folder in which you create a box.
– When you select a Personal
Folder
Press the [Personal Folder] key,
and select any folder from the
list. Press the [OK] key.
If a Password is configured for
the folder, the Password input screen appears. Enter the Password
and press the [OK] key.
– For more information on the types of folder, refer to "Overview of
the Store/Recall Features" on Page 4-3.
– When you select a Public Folder
Press the [Public Folder] key.
Page 47

4
About the Copied Data Processing Features
4-12 im9220
4 Press the [New Box] key.
– In case of Personal Folder
– In case of Public Folder
5 Press the [Box Name Input] key to
display the character input screen.
Enter any Box Name.
– Input a Box Name within 20
characters in alphameric char-
acters and signs.
– For more information on how to input characters, refer to "How to
Input Characters" on Page 3-7.
If you do not register a Box Name, the UserBoxNumber becomes the
Box Name.
6 If you configure a Password for a
box, press the [Password Input] key
to display the character input
screen. Enter any Password.
– Input a Password within 8 char-
acters in alphameric characters
and signs.
– Eight "*"s are displayed regardless of the number of characters you
input.
– For more information on how to input characters, refer to "How to
Input Characters" on Page 3-7.
– Be sure to keep a record of the password.
7 When you change the box number,
press the [Box Number Input] to
display the character input screen.
Enter any Box Number.
– Usually, there is no need to
change a Box Number.
Page 48

About the Copied Data Processing Features
4
im9220 4-13
– Input a 9 digit (000000001-999999998) Box Number.
– For more information on how to input characters, refer to "How to
Input Characters" on Page 3-7.
– The Box Number already registered cannot be used.
8 Press the [OK] key.
The file list screen appears.
9 If you register only a box, press the
[Return] and go to the step 10. If you
go on to store data on the internal
HDD, go to the steps 5 "Press the
[Store] key." on Page 4-18.
10 Make sure that the Box Name you registered on the box list is dis-
played.
– In case of Personal Folder
– In case of Public Folder
– If you have not registered a Box
Name, the Box Number becomes the Box Name, and the
Box Number is displayed on the
list.
If you want to register multiple boxes, return to the step 4 and repeat
the procedures.
Page 49

4
About the Copied Data Processing Features
4-14 im9220
4.6 Deleting a Box (Personal Folder/Public Folder/Confidential Folder)
Delete a box in the following steps.
1 Press [Box] on the control panel and
then press [Recall] key.
2 Select a folder.
– When you select a Personal
Folder
Press the [Personal Folder] key
to display the list. Select the
folder containing the box you
want to delete, and press the
[OK] key.
– When a password has been set, the password input screen is dis-
played. Enter the password and press the [OK] button.
– When you select a Public Folder
Press the [Public Folder] key.
– When you select a Confidential
Folder
Press the [Confidential] key.
3 Select the box you want to delete.
– When you select a Personal
Folder
Page 50

About the Copied Data Processing Features
4
im9220 4-15
– When you select a Public Folder
– When you select a Confidential
Folder
4 Press the [Box Delete] key.
– When you select a Personal
Folder
– When you select a Public Folder
– When you select a Confidential
Folder
If a Password is configured for
the box, the Password input
screen appears.
If a Password is not configured
for the box, a screen appears and confirms you whether to delete
the folder. Go to the step 6.
5 Enter the Password and press the
[OK] key.
The confirmation screen appears
and confirms you whether to delete
the box.
Page 51

4
About the Copied Data Processing Features
4-16 im9220
6 Press the [Yes] key.
The box is deleted, and the box list
screen appears.
7 Confirm that the box is deleted.
– When you select a Personal
Folder
– When you select a Public Folder
– When you select a Confidential
Folder
As for Public Boxes and Confidential Boxes, your administrator can delete such boxes even
when password is unknown.
Page 52

About the Copied Data Processing Features
4
im9220 4-17
4.7 Selecting a Storage Location
If you want not to print but to store copied data, select a storage location by
using the [Store] screen.
Copied data can be stored in either of the following three types of storage
locations.
Scan to HDDStoring data on the internal HDD enables you to print them
again anytime. Also, you can combine a print job sent from a computer and
copied data to print as one job.
Scan to PCCopied data can be sent to a computer. You can edit/process the
data to print.
HDD to PCCopied data stored on the internal HDD can be sent to a computer. You can edit/process the data to print.
Scan to HDD
You can store copied data on the internal HDD in the following steps.
0 A file can be registered to 10000 at the maximum for every box.
1 Press [Box] on the control panel and
then press [Store] key.
2 Press the [Scan to HDD] key.
3 Select a folder in which you store data.
– When you select a Personal
Folder
– Press the [Personal Folder] key
to display the list. Select the
folder and press the [OK] key.
– If a Password is configured for
the folder, the Password input screen appears. Enter the Password
and press the [OK] key.
Page 53

4
About the Copied Data Processing Features
4-18 im9220
– When you select a Public Folder
Press the [Public Folder] key.
– For information on how to create
a folder, refer to "Registering a
Personal Folder" on Page 4-7.
4 Select the box in which you store data and press the [OK] key.
– In case of Personal Folder
– In case of Public Folder
– Press the [Number Search] key
and enter a Box Number to select a box by Box Number. For
more information, refer to
"Number Search" on Page 3-9.
– For information on how to create
a box, refer to "Creating a Box (Personal Folder/Public Folder)" on
Page 4-11.
– If a Password is configured for the box, the Password input screen
appears. Enter the Password and press the [OK] key.
The file list screen appears.
5 Press the [Store] key.
– The selected Folder Name and
Box Name are displayed in the
Folder Name field and the Box
Name field respectively.
The File Name input screen appears.
6 Input a File Name and press the [OK] key.
– For more information on how to input characters, refer to "How to
Input Characters" on Page 3-7.
The setting screen appears.
Page 54

About the Copied Data Processing Features
4
im9220 4-19
7 Configure the necessary items.
– For more information on the
configurations on the Scanner
Setting Basic screen, refer to
"About the Copied Data Storage
Setting Screen" on Page 4-25.
8 Set an original and press the [Start] button.
The original is scanned, and the copied data are stored in a specified
box.
The continuous storage confirmation screen appears.
9 To continue storing data, press the
[Yes] key. To finish storing data,
press the [No] key.
– Pressing the [Yes] key displays
the file list screen. Return to the
step 5 and repeat the procedures.
Page 55

4
About the Copied Data Processing Features
4-20 im9220
Scan to PC
You can transmit copied data from the copier to a computer to store them
by using JobEditor/JobEditorServer. JobEditor or JobEditorServer needs to
be installed and configured.
!
Detail
For more information on JobEditor, refer to "JobEditor" on Page 11-3.
For more information on JobEditorServer, refer to "JobEditorServer" on
Page 11-9.
JobEditor is connected manually to the copier. JobEditorServer is connect automatically to the copier. For information on switching between
the manual and automatic connection, refer to "Changing Data Transmission Method to PC" on Page 4-28.
JobEditor and JobEditorServer are unavailable for the im9220.
To obtain JobEditor and JobEditorServer for older models, contact your
service representative.
Store copied data in a computer in the following steps.
1 Press [Box] on the control panel and
then press [Store] key.
2 Press the [Scan to PC] key.
The setting screen appears.
3 Configure the necessary items.
– For more information on the
configurations on the Scanner
Setting Basic screen, refer to
"About the Copied Data Storage
Setting Screen" on Page 4-25.
4 Set an original and press the [Start] button.
Page 56

About the Copied Data Processing Features
4
im9220 4-21
The transmitting screen and the continuous storage confirmation
screen appears.
5 Connect to the copier through JobEditor installed on the computer,
and store the copied data. JobEditorServer receives data automatically.
– For more information on how to operate JobEditor, refer to
"JobEditor" on Page 11-3.
– For more information on how to operate JobEditorServer, refer to
"JobEditorServer" on Page 11-9.
– JobEditor and JobEditorServer are unavailable for the im9220.
– To obtain JobEditor and JobEditorServer for older models, contact
your service representative.
6 To continue storing data, press the [Yes] key. To finish storing data,
press the [No] key.
– Pressing the [Yes] key displays the setting screen. Return to the
step 3 and repeat the procedures.
Page 57

4
About the Copied Data Processing Features
4-22 im9220
HDD to PC
You can transmit copied data stored on the internal HDD to a computer to
store them by using JobEditor/JobEditorServer.
JobEditor or JobEditorServer needs to be installed and configured.
!
Detail
For more information on JobEditor, refer to ""JobEditor" on Page 11-3.
For more information on JobEditorServer, refer to "JobEditorServer" on
Page 11-9.
JobEditor is connected manually to the copier. JobEditorServer is connect automatically to the copier. For information on switching between
the manual and automatic connection, refer to "Changing Data Transmission Method to PC" on Page 4-28.
JobEditor and JobEditorServer are unavailable for the im9220.
To obtain JobEditor and JobEditorServer for older models, contact your
service representative.
Transmit copied data stored on the internal HDD to a computer in the
following steps.
1 Press [Box] on the control panel and
then press [Store] key.
2 Press the [HDD to PC] key.
Page 58

About the Copied Data Processing Features
4
im9220 4-23
3 Select a Folder.
– When you select a Personal
Folder
– Press the [Personal Folder] key
to display the list. Select any
folder and press the [OK] key.
– If a Password is configured for
the Personal Folder, the Pass-
word input screen appears. Enter the Password.
– If you know the target file, press the [Direct Call] key to specify the
location directly. For more information, refer to "Direct Call" on
Page 3-10.
– When you select a Public Folder
– Press the [Public Folder] key.
4 Select a box and press the [OK] key.
– In case of Personal Folder
– In case of Public Folder
– If a Password is configured for
the box, the Password input
screen appears. Enter the Pass-
word.
– Press the [Number Search] key
and enter a Box Number to search a box by Box Number. For more
information, refer to "Number Search" on Page 3-9.
– If you know the target file, press the [Direct Call] key to specify the
location directly. For more information, refer to "Direct Call" on
Page 3-10.
5 Select a file and press the [OK] key.
– When you select a file and press
the [File Check] key, detailed
settings of the selected file are
displayed.
Data start to be transmitted to the
computer.
Page 59

4
About the Copied Data Processing Features
4-24 im9220
The transmitting screen and the continuous storage confirmation
screen appears.
6 Connect to the copier through JobEditor installed on the computer,
and store the copied data. JobEditorServer receives data automatically.
– For more information on how to operate JobEditor, refer to
"JobEditor" on Page 11-3.
– For more information on how to operate JobEditorServer, refer to
"JobEditorServer" on Page 11-9.
– JobEditor and JobEditorServer are unavailable for the im9220.
– To obtain JobEditor and JobEditorServer for older models, contact
your service representative.
7 To continue transmitting data, press the [Yes] key. To finish the trans-
mission, press the [No] key.
– Pressing the [Yes] key displays the file list screen. Return to the
step 5 and repeat the procedures.
Page 60

About the Copied Data Processing Features
4
im9220 4-25
4.8 About the Copied Data Storage Setting Screen
On the Copied Data Storage Setting screen, such settings as original settings and quality settings can be configured.
!
Detail
Those settings that can be configured on the Copied Data Storage Setting screen are for the features of the copier.
For more information on the settings, refer to the User's Guide (Copy).
Page 61

4
About the Copied Data Processing Features
4-26 im9220
Original Type
Pressing the [Original Type] key enables you to configure the following settings.
Scan Size
Pressing the [Scan Size] key enables
you to configure the following settings.
A3, A4R, A4, A5R, A5, B4, B5R, B5,
B6R, 11 x 17, 8.5 x 14, 8.5 x 11R, 8.5 x
11, 5.5 x 8.5R, 5.5 x 8.5, 8.12 x 13.25,
8.5 x 13, 8.25 x 13, 8x13, FullArea,
Auto
Simplex/Duplex
Pressing the [Simplex/Duplex] key enables you to select the [1-Sided] or [2Sided].
Zoom
Pressing the [Zoom] key enables you to
configure the following settings.
Image Text, Text/Photo, Photo, Dot
Matrix
Simplex/Duplex
1-Sided, 2-Sided
× 1.0
Manual Setting × 0.250 - 4.000
XY Zoom Zoom with Constant X and Y
Ratio, Set Individual Zoom
Enlarge B4>A3, A4>B4, A4>A3,
A5>A3
Reduce A4>B5, B4>A4, A3>A4,
A3>A5
Set Zoom × 4.000, × 2.000, × 0.500
Page 62

About the Copied Data Processing Features
4
im9220 4-27
Density/Background
Pressing the [Density/Background] key
enables you to configure the following
settings.
Original Setting
Pressing the [Original Setting] key enables you to configure the following settings.
Application
Pressing the [Application] key enables
you to configure the following settings.
Density Lighter, Std, Darker
Auto, Pre 1, Pre 2
Background
Removal
Lighter, Std, Darker
Original Direction
Normal, Upside Down,
Left, Right
Bind Right & Left Bind, Top
Bind
Special Original Normal, Mixed Original,
Z-Folded, Single Feed
Frame/Centre
Eraser
FrameErase/All Sides,
FrameErase/Each Side,
Centre Erase
Full Scan
Default Setting
Page 63

4
About the Copied Data Processing Features
4-28 im9220
4.9 Changing Data Transmission Method to PC
There are two methods to transmit copied data to the computer: an automatic transmission to the PC and a receive-operation on the PC.
To automatically transmit data to a PC, specify the target computer on the
copier, and install and configure the Utility Tool, JobEditorServer on the target PC.
To operate data receiving on a PC, install the Utility Tool, JobEditor on the
PC on the network. Connect to the copier through this tool to import copied
data to the PC.
Switch the method between the automatic transmission and the manual reception in the following steps.
!
Detail
Network settings are needed to transmit copied data to a computer. For
more information, contact your administrator.
JobEditor and JobEditorServer can be installed on Windows 2000/XP
Professional.
JobEditor and JobEditorServer are unavailable for the im9220.
To obtain JobEditor and JobEditorServer for older models, contact your
service representative.
Automatic Transmission to PC
If you configure the automatic transmission to a PC, the computer specified
on the copier can automatically receive copied data through JobEditorServer.
Page 64

About the Copied Data Processing Features
4
im9220 4-29
!
Detail
An administrator needs to specify the IP Address of the target computer
on the copier. For more information, contact your administrator.
For more information on JobEditorServer, refer to "JobEditorServer" on
Page 11-9.
JobEditor and JobEditorServer are unavailable for the im9220.
To obtain JobEditor and JobEditorServer for older models, contact your
service representative.
Configure the automatic transmission to the PC in the following steps.
1 Press [Box] on the control panel and
then press [Store] key.
2 Press the [Change Data Send Sys-
tem] key.
3 Press the [Transmit to PC] key.
– If you have not specified a target
computer on the copier, you
cannot select the [Transmit To
PC] key. For more information,
contact your administrator.
4 Press the [OK] key to close the screen.
Page 65

4
About the Copied Data Processing Features
4-30 im9220
Receiving Operation on PC
If you configure the receiving operation on a PC, the computer with JobEditor can receive copied data.
!
Detail
For more information on JobEditor, refer to "JobEditor" on Page 11-3.
JobEditor and JobEditorServer are unavailable for the im9220.
To obtain JobEditor and JobEditorServer for older models, contact your
service representative.
Configure the receiving operation on a PC in the following steps.
1 Press [Box] on the control panel and
then press [Store] key.
2 Press the [Change Data Send Sys-
tem] key.
3 Press the [Operate on PC] key.
4 Press the [OK] key.
Page 66

About the Copied Data Processing Features
4
im9220 4-31
4.10 Output from the Internal HDD
Copied data stored on the internal HDD with the [Store] screen or confidential print jobs transmitted from a computer can be output using the [Recall]
screen.
!
Detail
For more information on confidential output, refer to the optional User's
Guide (Printer).
1 Press [Box] on the control panel and
then press [Recall] key.
2 Specify the folder in which the data you output are stored.
– When you select a Personal
Folder
– Press the [Personal Folder] key
to display the list. Select any
folder and press the [OK] key.
– When you select a Public Folder
– Press the [Public Folder] key.
– When you select Confidential
– Press the [Confidential] key.
– For more information on the
types of folder, refer to "Overview of the Store/Recall Features" on Page 4-3.
– A Password may be configured
for the Personal Folder. In that case, the Password input screen appears. Enter the Password.
– If you know the target file, press the [Direct Call] key to specify the
location directly. For more information, refer to "Direct Call" on
Page 3-10.
Page 67

4
About the Copied Data Processing Features
4-32 im9220
3 Select a box and press the [OK] key.
– When you select a Personal
Folder
– When you select a Public Folder
– When you select a Confidential
– If a Password is configured for
the box, the Password input
screen appears. Enter the Pass-
word.
– Press the [Number Search] key
and enter a Box Number to
search a box by Box Number. For more information, refer to
"Number Search" on Page 3-9.
– If you know the target file, press the [Direct Call] key to specify the
location directly. For more information, refer to "Direct Call" on
Page 3-10.
The output setting screen appears.
4 Select a file from the list on the left
side, and press the [>>>] key.
– When you select a file and press
the [File Check] key, detailed
settings of the selected file are
displayed.
– For more information on the keys on the setting screen, refer to
"About Output Setting Screen of the Recall Function" on Page 4-
34.
When you select a Personal Folder/Public Folder
The selected file is added to the list on the right side.
5 Select [Wait Output], [Proof Output]
or [AutoOutput], and press the [OK]
key.
Hereafter, the Auto Output is explained. For more information on
Wait Output or Proof Output, refer
Page 68

About the Copied Data Processing Features
4
im9220 4-33
to "The flow of operation of the Wait Output and Proof Output" on Page
4-35.
The print quantity confirmation screen appears.
6 Input the print quantity on the KEY-
PAD and press the [OK] key.
The selected file is output.
The confirmation screen asks you
whether to continue to recall data.
7 To continue recalling data, press
the [Yes] key. To finish recalling data, press the [No] key.
– Pressing the [Yes] key displays
the file list screen. Return to the
step 4 and repeat the procedures.
Page 69

4
About the Copied Data Processing Features
4-34 im9220
4.11 About Output Setting Screen of the Recall Function
On the Output Setting screen of the Recall function, you can configure the
settings for outputting stored copied data or confidential output print jobs.
!
Detail
On how to open the setting screen, refer to "Output from the Internal
HDD" on Page 4-31.
4.11.1 Keys on the setting screen
Button Function
File Check Pressing this key displays a list of settings of the selected file.
File Combination You can output all the selected files at once. At maximum, you
can combine 5 files at one time.
Image Combination You can output images of all the selected files at once. At
maximum, you can combine 5 files at one time.
FileDelete Pressing this key deletes the selected file. On the confirmation
screen, press the [Yes] key to delete the file.
Clear All Reset all the output settings.
WaitOutput After recalling data, the [Machine] screen appears. You can
change the setting. For more information, refer to "The flow of
operation of the Wait Output and Proof Output" on Page 4-35.
Proof Output When a number of copies are printed, the [Machine] screen
appears after printing one copy. If you see no problem, press
the start button to restart the output. For more information, refer to "The flow of operation of the Wait Output and Proof Output" on Page 4-35.
AutoOutput If this key is pressed, the output starts without pressing the
start button.
Page 70

About the Copied Data Processing Features
4
im9220 4-35
4.11.2 The flow of operation of the Wait Output and Proof Output
Change settings
Change settings
Output the one sheet
for a confirmation
Exit the operation
as it is.
Exit the operation
as it is.
Output it by the present settings
Output it by the present settings
If it is in the state in which an output is
possible, [Start] button will shine green
In case of Wait Output
One sheet is outputted
In case of Proof Output
The confirmation screen asks you
whether to continue to recall data
The screen which confirm settings appears
Select a setting to change
and press the [Change] key
Screens vary depending on
the selected settings.
Press the [Exit] key
Press the [Proof Print] key
Press the [Cancel] or [Close] key
Press
the [Close] key
Output Application screen appears
Machine screen appears
Press the [Start] button
It is outputted
Confirm the outputted paper
Yes No
One sheet is outputted
Confirm the outputted paper
If you exit the job and you don't output it,
plese delete the present job from the
[Reserve] of [Job List] screen.
"Proof Stop" on the left above the screen
blinks and no more job is output.
For more information on the method of job
deletion, refer to the User's Guide of the
Copier.
Change settings and
press the [OK] key
Settings will be decided
Setting change is canceled
Repeat the step 4 (p.4-32)
and the succeeding steps
of
"Output from the
Internal HDD"
Page 71

Page 72

5
About the Network
Scanner Features
Page 73

Page 74

About the Network Scanner Features
5
im9220 5-3
5 About the Network Scanner Features
5.1 Overview of the Network Scanner Features
The Network Scanner features are operated on the [Scan] screen.
Data scanned by the Network Scanner features can be transmitted to the EMail addresses, the internal HDD, the FTP server and the SMB server. The
scanned data stored on the internal HDD can also be imported to the network-connected computers using the TWAIN-compliant applications and
the Network Scanner Driver.
!
Detail
To use the network scanner features, the optional printer controller is required. Contact your service representative for details of the printer controller.
!
Detail
"Send by an E-Mail" ....................................... p.5-5
"Store on the HDD" ........................................ p.5-7
"Send to the FTP server"................................ p.5-8
"Send to the SMB server" ............................ p.5-10
"Send to a Group" ........................................ p.5-12
"Import Scanned Data to Computers" ......... p.8-10
When the Security Strengthen mode is ON, A job is unacquirable using
applications compatible with TWAIN and network scanner driver. For
more information, contact your administrator.
Also, you can configure the density, lens mode, original size, resolution, original quality, file format and scan mode to perform scanning by using the features of the copier.
Page 75

5
About the Network Scanner Features
5-4 im9220
!
Detail
"About the Scanner Setting Basic Screen".....p.8-3
!
Detail
To use the copier as a network scanner, it needs to be connected to the
network. For more information on the network configuration, contact your
network administrator.
Original
SCAN
Copier
E-Mail
E-Mail server
Internal HDD
FTP server
FTP
SMB server
SMB
Internet
Page 76

About the Network Scanner Features
5
im9220 5-5
5.2 Send by an E-Mail
You can send the data read in from the copier's ADF or the original scanning
glass (scanned data) to an E-Mail address as an attached file.
For detailed information on how to operate the function, refer to "Transmission to an E-Mail Address" on Page 7-5.
5.2.1 Items to be configured
In order to send the scanned data to an E-Mail address, the following items
need to be configured.
Address (E-Mail address)
Select an E-Mail address from the registered addresses, or specify an address as you operate scanning. You can specify multiple addresses.
For information on how to register an address, refer to "Address Input Registering an E-Mail Address" on Page 6-5.
Title
You can choose an E-Mail title from 5 types, or you can input a title as you
operate scanning.
On how to input a title, refer to "Transmission to an E-Mail Address" on Page
7-5.
Text
You can choose a sentence from 5 types, or you can input a sentence as you
operate scanning.
On how to input a sentence, refer to "Transmission to an E-Mail Address" on
Page 7-5.
POP serverSMTP server
Internet
Original
SCAN
Copier
Page 77

5
About the Network Scanner Features
5-6 im9220
!
Detail
When the E-Mail is in excess of the maximum transmission size that has
been set, it is not sent to the SMTP server, but cancelled on the im9220.
Transmission from the copier is up to the STMP server. If the network or the
POP server has any problem, the mail may not reach a recipient. When you
send an important mail, do not forget to confirm the reception.
!
Detail
Depending on settings of the recipient server, the size of an attached file
is regulated. For more information, contact your administrator.
Page 78

About the Network Scanner Features
5
im9220 5-7
5.3 Store on the HDD
In order to store the data read in from the copier's ADF or the original scanning glass (scanned data) on the internal HDD, you need to configure boxes
on the internal HDD in advance. The scanned data are stored in the boxes.
The data stored in the boxes can be imported to computers through the network.
For detailed information on how to operate the function, refer to "Storage on
the HDD" on Page 7-9.
5.3.1 Items to be configured
In order to store the scanned data on the internal HDD, the following items
need to be configured.
Box Number
Specify a 9-digit-number for the box in which you store data.
Password
You can configure a password (8 digits at maximum).
A Box Number and Password can be registered in advance. On how to register them, refer to "Registering the HDD" on Page 6-7.
Original
SCAN
Copier
HDD
Page 79

5
About the Network Scanner Features
5-8 im9220
5.4 Send to the FTP server
You can send the data read in from the copier's ADF or the original scanning
glass (scanned data) to the FTP server.
The scanned data sent to the FTP server can be downloaded from computers that have access to the FTP server.
For detailed information on how to operate the function, refer to "Transmission to the FTP server" on Page 7-12.
5.4.1 Items to be configured
In order to send the scanned data to the FTP server, the following items need
to be configured.
Host Address
You specify an FTP server name or an IP Address of the FTP server.
File Path
You specify a directory in the FTP server.
Login Name
You specify a Login Name for the FTP server.
Password
You specify a corresponding Password to each Login Name for the FTP
server.
Port No.
You specify a Port No. when necessary.
For information on how to configure a Port No., refer to "Transmission to the
FTP server" on Page 7-12.
FTP server
Original
SCAN
Copier
Internet
Page 80

About the Network Scanner Features
5
im9220 5-9
Firewall
A selection is made to decide if the PASV mode is used or not.
You can register a Host Address, File Path, Login Name and Password in advance. For information on how to register them, refer to "Registering the FTP
server" on Page 6-9.
2
Reminder
Depending on a network condition, transmission to the FTP server may
damage the scanned data.
Make sure that the scanned data are not damaged.
Page 81

5
About the Network Scanner Features
5-10 im9220
5.5 Send to the SMB server
You can send the data read in from the copier's ADF or the original scanning
glass (scanned data) to the SMB server.
The scanned data sent to the SMB server can be file-shared with computers
with the SMB protocol.
For detailed information on how to operate the function, refer to "Transmission to the SMB server" on Page 7-16.
5.5.1 Items to be configured
In order to send the scanned data to the SMB server, the following items
need to be configured.
Host Address
You specify an SMB server name or an IP Address of the SMB server.
File Path
You specify a directory in the SMB server.
Login Name
You specify a Login Name for the SMB server.
Password
You specify a corresponding Password to each Login Name for the SMB
server.
You can register a Host Address, File Path, Login Name and Password in advance. For information on how to register them, refer to "Registering the
SMB server" on Page 6-11.
SMB server
Original
SCAN
Copier
Page 82

About the Network Scanner Features
5
im9220 5-11
2
Reminder
Depending on a network condition, transmission to the SMB server may
damage the scanned data.
Make sure that the scanned data are not damaged.
Page 83

5
About the Network Scanner Features
5-12 im9220
5.6 Send to a Group
If you register multiple destinations/storage locations as a Group, you can
send/store the data read in from the copier's ADF or the original scanning
glass (scanned data) to them at one time.
- At maximum, 100 destinations can be registered to one Group.
- Multiple E-Mail addresses can be registered.
- As for the HDD, FTP server and SMB server, one for each can be regis-
tered to a Group.
For detailed information on how to operate the function, refer to "Transmission to a Group" on Page 7-20.
For information on how to register a Group, refer to "Registering a Group" on
Page 6-13.
Original
SCAN
Copier
E-Mail Internal HDD FTP SMB
Group
Multiple
Select destinations at once
Single Single Single
Page 84

About the Network Scanner Features
5
im9220 5-13
5.7 Use the Network Scanner Features
To scan data using the Network Scanner features, follow the flow below.
Specifying destination
Configuring the scanner
Perform scanning
Registering destination
Did you register the destination?
Do you register the destination?
YES NO
YESNO
Chapter 6 Configuring Destination for the Network Scanner Features
Chapter 7 Using the Network Scanner Features
Chapter 8 Configuring the Network Scanner features
Page 85

Page 86

6
Configuring Destination
for the Network Scanner
Features
Page 87

Page 88

Configuring Destination for the Network Scanner Features
6
im9220 6-3
6 Configuring Destination for the Network
Scanner Features
6.1 About Registration
When you transmit scanned data to destinations/storage locations, you can
input a destination every time or you can also select it from the registered
destinations. Frequently used destinations are recommended to be registered in advance.
!
Detail
"Address Input Registering an E-Mail Address"p.6-5
"Registering the HDD".................................... p.6-7
"Registering the FTP server" .......................... p.6-9
"Registering the SMB server"....................... p.6-11
"Registering a Group" .................................. p.6-13
6.1.1 Change/delete destinations/storage locations
About how to change/delete destinations/storage locations, contact your
administrator.
6.1.2 The keys on the Address Input screen
You can register a destination in the Address Input screen.
On how to display the Address Input screen, refer to the step 1 to 3 for the
each registration. This page describes the common keys.
Page 89

6
Configuring Destination for the Network Scanner Features
6-4 im9220
!
Detail
Since the registration procedures for a Group are different from others,
there is no Destination Manual Input screen.
Destination Manual Input screen (HDD)
Destination Manual Input screen (E-Mail)
Destination Manual Input screen (FTP)
Destination Manual Input screen (SMB)
Button Function
Register The input is registered, and you are brought back to the Select
Destinations screen.
Scan Setting The Scanner Setting Basic screen appears.
Cancel The input is canceled, and you are brought back to the Select
Destinations screen.
OK The input is determined, and you are brought back to the Select
Destinations/Storage Locations screen. After transmitted once,
destination setting is cleared without being registered.
Page 90

Configuring Destination for the Network Scanner Features
6
im9220 6-5
6.2 Address Input Registering an E-Mail Address
When using the function to send the scanned data as an E-Mail attached file,
you can register the destination E-Mail address in advance. The registration
is done in the following steps.
!
Detail
For E-Mail/FTP/HDD/SMB, destinations can be registered as many as
500 in sum.
1 Press the [Scan] on the control panel.
The Select Destinations/Storage Locations screen appears.
2 Make sure that [E-Mail] is selected.
– In the initial settings, the Select
Destinations/Storage Locations
screen (E-Mail) is displayed. For
information on the initial settings
of the Scan screen, contact your
administrator of the copier.
3 Press the [Address Input] key.
– If the E-Mail address is already registered, the Name is displayed.
– In the initial settings, such index keys as [A-C] and [D-F] are dis-
played.
– On how to edit/delete a registered address, contact your adminis-
trator of the copier.
The Destination Manual Input screen appears.
4 Configure the necessary items on
the Address Input screen. Pressing
an each item displays the character
input screen.
– For more information on how to
input characters, refer to "How
to Input Characters" on Page 3-7.
– [Address]
Enter an E-Mail address within 250 characters in alphameric characters and signs.
– [Register Name]
Enter a Name that is displayed on the Select Destinations/Storage
Page 91

6
Configuring Destination for the Network Scanner Features
6-6 im9220
Locations screen (E-Mail) within 24 characters in alphameric characters and signs.
– If you do not input a Name, the first 24 characters of an E-Mail ad-
dress are displayed on the Select Destinations/Storage Locations
screen (E-Mail).
– [Character for Search]
Used as a search keyword when you search destinations. Needs to
be input within 24 characters in alphameric characters and signs.
5 Press the [Register] key.
The E-Mail address is registered, and you are brought back to the Select Destinations/Storage Locations screen (E-Mail).
6 Make sure that the registered Name
is displayed.
!
Detail
If the desired Name is not displayed on the page, press / to
switch between pages.
An administrator is to edit/delete once registered destinations. For more
information, contact your administrator.
Page 92

Configuring Destination for the Network Scanner Features
6
im9220 6-7
6.3 Registering the HDD
If you want to store the scanned data on the internal HDD, you need to register boxes on the internal HDD.The registration is done in the following
steps.
!
Detail
For E-Mail/FTP/HDD/SMB, destinations can be registered as many as
500 in sum.
1 Press the [Scan] on the control panel.
2 Press the [HDD] key.
– In the initial settings, the Select
Destinations/Storage Locations
screen (E-Mail) is displayed. For
information on the initial settings
of the Scan screen, contact your
administrator of the copier.
3 Press the [Address Input] key.
– If the Box Number is already
registered, the Name is displayed.
– In the initial settings, such index
keys as [A-C] and [D-F] are displayed.
– On how to edit/delete a registered Box Number, contact your ad-
ministrator of the copier.
The Address Input screen appears.
4 Configure the necessary items on
the Address Input screen. Pressing
an each item displays the character
input screen.
– For more information on how to
input characters, refer to "How
to Input Characters" on Page 3-7.
– If you want to use this copier as a scanner, it is recommended that
an administrator assigns a Box Number to each user and informs
the assignment by an E-Mail in advance.
– The Box Number can protect each user's data.
Page 93

6
Configuring Destination for the Network Scanner Features
6-8 im9220
– [UserBoxNumber]
Input a 9-digit (000000001-999999998) UserBoxNumber. Press the
[UserBoxNumber] key to change your UserBoxNumber. The boxes
in which scanned data are stored are managed by 9-digit UserBoxNumber. Be sure to record this number.
You need the number when you import scanned data from computers.
– Boxes of a same box number can be prepared. For a same box
number, one box with password and boxes without password of infinite number as far as the disk capacity permits can be prepared.
However, a same registration name cannot be used.
– [Register Name]
Input the Name that is displayed on the Select Destinations/Storage Locations screen (HDD) within 24 characters in alphameric
characters and signs.
– If a Name is not input, the UserBoxNumber will be registered as a
Name.
– [Character for Search]
Used as a search keyword when you search destinations. Needs to
be input within 24 characters in alphameric characters and signs.
– [Password]
Input a 8-digit Password for a box in alphameric characters and
signs.
– Eight "*"s are displayed regardless of the number of characters you
input.
5 Press the [Register] key.
Pressing this key brings you back to the Select Destinations/Storage
Locations screen (HDD).
6 Make sure that the registered Name
is displayed.
!
Detail
If the desired Name is not displayed on the page, press / to
switch between pages.
An administrator is to edit/delete once registered destinations. For more
information, contact your administrator.
Page 94

Configuring Destination for the Network Scanner Features
6
im9220 6-9
6.4 Registering the FTP server
If you want to send the scanned data to the FTP server, you can register the
destination FTP server. The registration is done in the following steps.
!
Detail
For E-Mail/FTP/HDD/SMB, destinations can be registered as many as
500 in sum.
1 Press the [Scan] on the control panel.
2 Press the [FTP] key.
– In the initial settings, the Select
Destinations/Storage Locations
screen (E-Mail) is displayed. For
information on the initial settings
of the Scan screen, contact your
administrator of the copier.
3 Press the [Address Input] key.
– If the FTP server is already reg-
istered, the Name is displayed.
– In the initial settings, such index
keys as [A-C] and [D-F] are displayed.
– On how to edit/delete the registered FTP server, contact your ad-
ministrator of the copier.
The Address Input screen appears.
4 Configure the necessary items on
the Address Input screen. Pressing
an each item displays the character
input screen.
– For more information on how to
input characters, refer to "How
to Input Characters" on Page 3-7.
– [Profile Name]
Input the Name that is displayed on the Select Destinations/Storage Locations screen (FTP) within 24 characters in alphameric
characters and signs.
Page 95

6
Configuring Destination for the Network Scanner Features
6-10 im9220
– If you do not input a Profile Name, the first 24 characters of a Host
Address are displayed on the Select Destinations/Storage Locations screen (FTP).
– [Character for Search]
Used as a search keyword when you search destinations. Needs to
be input within 24 characters in alphameric characters and signs.
– [Host Address]
Input an FTP server address within 63 characters in alphameric
characters and signs.
– [File Path]
Input a file path of the FTP server within 96 characters in alphameric
characters and signs.
– [Login Name]
Input an account of the FTP server within 47 characters in alphameric characters and signs.
– [Anonymous]
Pressing this key inputs "Anonymous" to the [Login Name] field.
– You may use this when you login an anonymous FTP server for
which an account is unnecessary to login.
– In some Anonymous FTP servers, an E-Mail address is used as a
Password.
– [Password]
Input a Password for the FTP server within 24 characters in alphameric characters and signs.
– "*"s are displayed according to the number of characters you input.
5 Press the [Register] key.
Pressing this key brings you back to the Select Destinations/Storage
Locations screen (FTP).
6 Make sure that the registered Name
is displayed.
!
Detail
If the desired Name is not displayed on the page, press / to
switch between pages.
An administrator is to edit/delete once registered destinations. For more
information, contact your administrator.
Page 96

Configuring Destination for the Network Scanner Features
6
im9220 6-11
6.5 Registering the SMB server
If you want to send the scanned data to the SMB server, you can register the
destination SMB server. The registration is done in the following steps.
!
Detail
For E-Mail/FTP/HDD/SMB, destinations can be registered as many as
500 in sum.
1 Press the [Scan] on the control panel.
2 Press the [SMB] key.
– In the initial settings, the Select
Destinations/Storage Locations
screen (E-Mail) is displayed. For
information on the initial settings
of the Scan screen, contact your
administrator of the copier.
3 Press the [Address Input] key.
– If the SMB server is already reg-
istered, the Name is displayed.
– In the initial settings, such index
keys as [A-C] and [D-F] are displayed.
– On how to edit/delete the registered SMB server, contact your ad-
ministrator of the copier.
The Address Input screen appears.
4 Configure the necessary items on
the Address Input screen. Pressing
an each item displays the character
input screen.
– For more information on how to
input characters, refer to "How
to Input Characters" on Page 3-
7.
– [Profile Name]
Input the Name that is displayed on the Select Destinations/Storage Locations screen (SMB) within 24 characters in alphameric
characters and signs.
Page 97

6
Configuring Destination for the Network Scanner Features
6-12 im9220
– If you do not input a Profile Name, the first 24 characters of a Host
Address are displayed on the Select Destinations/Storage Locations screen (SMB).
– [Character for Search]
Used as a search keyword when you search destinations. Needs to
be input within 24 characters in alphameric characters and signs.
– [Host Address]
Input an SMB server address within 63 characters in alphameric
characters and signs.
– [File Path]
Input a file path of the SMB server within 95 characters in alphameric characters and signs.
– [Login Name]
Input an account of the SMB server within 47 characters in alphameric characters and signs.
– [Password]
Input a Password for the SMB server within 31 characters in alphameric characters and signs.
– "*"s are displayed according to the number of characters you input.
5 Press the [Register] key.
Pressing this key brings you back to the Select Destinations/Storage
Locations screen (SMB).
6 Make sure that the registered Name
is displayed.
!
Detail
If the desired Name is not displayed on the page, press / to
switch between pages.
An administrator is to edit/delete once registered destinations. For more
information, contact your administrator.
Page 98

Configuring Destination for the Network Scanner Features
6
im9220 6-13
6.6 Registering a Group
If you want to send the scanned data to multiple destinations/storage locations, you can register them as a Group. The registration is done in the following steps.
!
Detail
At maximum, 100 groups can be registered.
1 Press the [Scan] on the control panel.
2 Press the [Group] key.
– In the initial settings, the Select
Destinations/Storage Locations
screen (E-Mail) is displayed. For
information on the initial settings
of the Scan screen, contact your
administrator of the copier.
3 Press the [Register] key.
– If the Group is already regis-
tered, the Name is displayed.
– On how to edit/delete the regis-
tered destination, contact your
administrator of the copier.
4 Press the [Group Name] key, and in-
put a Group name on the character
input screen.
– For more information on how to
input characters, refer to "How
to Input Characters" on Page 3-
7.
– A Group name is the Name that is displayed on the Select Destina-
tions/Storage Locations screen (Group) after the registration.
5 Select all the destinations that you
want to register to a Group.
– Pressing the [E-Mail], [HDD],
[FTP] or [SMB] key displays the
registered Names for each.
Page 99

6
Configuring Destination for the Network Scanner Features
6-14 im9220
– If a large number of registrations have been made and the desired
Name is not displayed on the page, press / to switch between pages.
– At maximum, 100 destinations can be registered to one Group.
Multiple E-Mail addresses can be registered. As for the HDD, FTP
server and SMB server, one for each can be registered to a Group.
6 Press the [List] key.
The list of destinations to be registered is displayed.
7 Confirm the list, and press the [OK]
key.
8 If there is no problem, press the [OK] key.
This brings you back to the Select Destinations/Storage Locations
screen (Group).
9 Make sure that the registered Name
is displayed.
!
Detail
If a large number of registrations have been made and the desired Name
is not displayed on the page, press / to switch between pages.
On the Select Destinations/Storage Locations screen (Group), press the
[List] key and then press the [Group] key to display the list of registered
destinations. Press the [Edit] key on this screen to change what to include
in a Group.
Page 100

7
Using the Network
Scanner Features
 Loading...
Loading...