Page 1

IBM Proventia Network Enterprise Scanner
User Guide
Version 2.3
Page 2
Copyright statement
© Copyright IBM Corporation 1997, 2009.
All Rights Reserved.
U.S. Government Users Restricted Rights — Use, duplication or disclosure restricted by GSA ADP Schedule Contract with
IBM Corp.
Publication Date: February 2009
Page 3

Trademarks and Disclaimer
IBM®and the IBM logo are trademarks or registered trademarks of International
Business Machines Corporation in the United States, other countries, or both.
ADDME
RealSecure®, SecurePartner™, SecurityFusion™, SiteProtector™, System Scanner™,
Virtual Patch®, X-Force®and X-Press Update are trademarks or registered
trademarks of Internet Security Systems
or both. Internet Security Systems, Inc. is a wholly-owned subsidiary of
International Business Machines Corporation.
Microsoft
in the United States, other countries, or both.
Other company, product and service names may be trademarks or service marks of
others.
References in this publication to IBM products or services do not imply that IBM
intends to make them available in all countries in which IBM operates.
Disclaimer: The information contained in this document may change without
notice, and may have been altered or changed if you have received it from a
source other than IBM Internet Security Systems (IBM ISS). Use of this information
constitutes acceptance for use in an “AS IS” condition, without warranties of any
kind, and any use of this information is at the user’s own risk. IBM Internet
Security Systems disclaims all warranties, either expressed or implied, including
the warranties of merchantability and fitness for a particular purpose. In no event
shall IBM ISS be liable for any damages whatsoever, including direct, indirect,
incidental, consequential or special damages, arising from the use or dissemination
hereof, even if IBM Internet Security Systems has been advised of the possibility of
such damages. Some states do not allow the exclusion or limitation of liability for
consequential or incidental damages, so the foregoing limitation may not apply.
™
, Ahead of the threat, BlackICE™, Internet Scanner®, Proventia®,
®
, Windows®, and Windows NT®are trademarks of Microsoft Corporation
™
, Inc. in the United States, other countries,
Reference herein to any specific commercial products, process, or service by trade
name, trademark, manufacturer, or otherwise, does not necessarily constitute or
imply its endorsement, recommendation, or favoring by IBM Internet Security
Systems. The views and opinions of authors expressed herein do not necessarily
state or reflect those of IBM Internet Security Systems, and shall not be used for
advertising or product endorsement purposes.
Links and addresses to Internet resources are inspected thoroughly prior to release,
but the ever-changing nature of the Internet prevents IBM Internet Security
Systems, Inc. from guaranteeing the content or existence of the resource. When
possible, the reference contains alternate sites or keywords that could be used to
acquire the information by other methods. If you find a broken or inappropriate
link, please send an email message with the topic name, link, and its behavior to
mailto://support@iss.net.
© Copyright IBM Corp. 1997, 2009 iii
Page 4

iv Enterprise Scanner: User Guide
Page 5

Contents
Trademarks and Disclaimer ......iii
About this book ...........vii
Related publications ...........viii
Technical support contacts .........viii
Part 1. Scanning from the Proventia
Manager ..............1
Chapter 1. Ad hoc scanning in the
Proventia Manager ..........3
Section A: Network configuration .......4
Configuring the management network interface . 4
Configuring the scanning network interface . . . 5
Configuring scanning interface DNS settings . . 6
Assigning perspective to a scanning interface . . 7
Configuring routes for perspective ......7
Section B: Policy configuration ........8
Defining assets for a discovery scan .....8
Displaying assessment checks by groups ....9
Displaying information about assessment checks 10
Selecting assessment checks with filters ....11
Configuring common assessment settings for an
Assessment policy ...........12
Defining assessment credentials for a policy . . 16
Defining the service names associated with TCP
and UDP ports ............18
Defining ports or assets to exclude from a scan 19
Configuring and saving a scan policy in the
Proventia Manager ...........20
Chapter 2. Interpreting scan results in
the Proventia Manager ........21
Running an ad hoc scan ..........22
Monitoring the status of a scan ........23
Viewing the results of an ad hoc scan .....24
Exporting scan results from Proventia Manager . . 24
Purging scan data from the database ......25
Part 2. Scanning from the
SiteProtector Console .......27
Chapter 3. Enterprise Scanner policies 29
Policy inheritance with Enterprise Scanner policies 30
Deploying an Enterprise Scanner policy from the
policy repository ............31
Migrating a locally managed Enterprise Scanner
agent into SiteProtector ..........32
Viewing asset or agent policies for Enterprise
Scanner................33
Getting vulnerability help for a SiteProtector
Console without Internet access .......34
Agent policies for Enterprise Scanner ......35
Agent policy descriptions for Enterprise Scanner 35
Network Locations policy ........36
Notification policy ...........38
Access policy .............39
Networking policy ...........40
Services policy ............43
Time policy .............44
Update Settings policy..........45
Asset policies for Enterprise Scanner ......45
Asset policy descriptions for Enterprise Scanner 45
Discovery policy............46
Assessment policy ...........48
Assessment Credentials policy .......55
Scan Control policy ...........57
Scan Window policy ..........59
Scan Exclusion policy ..........61
Network Services policy .........62
Ad Hoc Scan Control policy ........64
Chapter 4. Understanding scanning
processes in SiteProtector ......67
What is perspective? ...........68
Defining perspectives ...........69
Scan jobs and related terms .........71
Types of tasks .............72
Priorities for running tasks .........73
Stages of a scanning process .........74
Optimizing cycle duration, scan windows, and
subtasks for Enterprise Scanner........76
Chapter 5. Background scanning in
SiteProtector ............79
Determining when background scans run ....80
How policies apply to ad hoc and background scans 81
Background scanning checklists for Enterprise
Scanner................83
Enabling background scanning ........84
Defining when scanning is allowed ......85
Defining ports or assets to exclude from a scan . . 87
Defining network services .........88
Defining assessment credentials for a policy . . . 89
Chapter 6. Monitoring scans in
SiteProtector ............91
Viewing your scan jobs ..........92
Viewing discovery job results ........92
Viewing assessment job results ........93
Chapter 7. Managing scans in
SiteProtector ............95
Stopping and restarting scan jobs .......96
Suspending and enabling all background scans . . 97
Minimum scanning requirements .......98
© Copyright IBM Corp. 1997, 2009 v
Page 6

Scanning behaviors for ad hoc scans ......99
Part 3. Maintenance........139
Chapter 8. Interpreting scan results in
SiteProtector ...........103
OS identification (OSID) certainty ......104
How OSID is updated in Enterprise Scanner . . . 105
Setting up a Summary view for vulnerability
management .............106
Summary page for vulnerability management . . 106
Viewing vulnerabilities in the SiteProtector Console
using Enterprise Scanner .........108
Viewing vulnerabilities by asset in Enterprise
Scanner ..............108
Viewing vulnerabilities by detail in Enterprise
Scanner ..............111
Viewing vulnerabilities by object in Enterprise
Scanner ..............113
Viewing vulnerabilities by target operating
system in Enterprise Scanner .......114
Viewing vulnerabilities by vulnerability name in
Enterprise Scanner...........115
Running reports in the SiteProtector Console . . . 117
Types of assessment reports ........117
Viewing an Enterprise Scanner report in the
SiteProtector Console ...........119
Chapter 9. Logs and alerts......121
Log files and alert notification ........122
System logs ..............123
Getting log status information .......124
Enterprise Scanner (ES) logs ........124
Downloading Enterprise Scanner (ES) log files 126
Alerts log ..............127
Downloading and saving an Alerts log ....128
Clearing the Alerts log .........129
Finding specific events in the Alerts log . . . 129
Chapter 10. Ticketing and remediation 133
Ticketing and Enterprise Scanner .......134
Remediation process overview for Enterprise
Scanner ...............135
Remediation tasks for Enterprise Scanner ....136
Chapter 11. Performing routine
maintenance............141
Shutting down your Enterprise Scanner ....142
Removing an agent from SiteProtector .....143
Options for backing up Enterprise Scanner . . . 144
Backing up configuration settings ......145
Making full system backups ........146
Chapter 12. Updating Enterprise
Scanner..............147
XPU basics ..............148
Updating options ............149
Configuring explicit-trust authentication with an
XPU server ..............150
Configuring an Alternate Update location ....151
Configuring an HTTP Proxy ........153
Configuring notification options for XPUs ....153
Scheduling a one-time firmware update ....154
Configuring automatic updates .......154
Manually installing updates ........156
Chapter 13. Viewing the status of the
Enterprise Scanner agent ......157
Proventia Manager Home page .......158
Viewing agent status in the SiteProtector Console 160
Viewing agent status ...........160
Viewing the status of the CAM modules ....161
Troubleshooting the Enterprise Scanner sensor . . 161
Part 4. Appendixes ........163
Appendix. Safety, environmental, and
electronic emissions notices .....165
Index ...............177
vi
Enterprise Scanner: User Guide
Page 7

About this book
This section describes the audience for this guide; identifies related publications;
and provides contact information.
Audience
Users of this guide should understand their network topology, including the
criticality of network assets. In addition, because Enterprise Scanner can be
managed through the SiteProtector Console, you must have a working knowledge
of the SiteProtector system, including how to set up views, manage users and user
permissions, and deploy policies.
Topics
“Related publications” on page viii
“Technical support contacts” on page viii
© Copyright IBM Corp. 1997, 2009 vii
Page 8
Related publications
Use this topic to help you access information about your Enterprise Scanner
appliance.
Publications
The following documents are available for download from the IBM ISS
Documentation Web site at http://www.iss.net/support/documentation/.
v IBM Proventia Network Enterprise Scanner Version 2.3 Quick Start Card (Models
ES750 and ES1500)
v IBM Proventia Network Enterprise Scanner Version 2.3 Getting Started Guide
v IBM Proventia Network Enterprise Scanner Version 2.3 User Guide
License agreement
For licensing information on IBM Internet Security System products, download the
IBM Licensing Agreement from http://www.ibm.com/services/us/iss/html/
contracts_landing.html.
Technical support contacts
IBM Internet Security Systems (IBM ISS) provides technical support through its
Web site and by email or telephone.
The IBM ISS Web site
The IBM ISS Customer Support Web page at http://www.ibm.com/services/us/
iss/support/ provides direct access to online user documentation, current versions
listings, detailed product literature, white papers, and the Technical Support
Knowledgebase.
Hours of support
The following table provides hours for Technical Support at the Americas and
other locations:
Table 1. Hours of technical support
Location Hours
Americas 24 hours a day
All other locations Monday through Friday, 9:00 A.M. to 6:00
P.M. during their local time, excluding IBM
ISS published holidays
Note: If your local support office is located
outside the Americas, you may call or send
an email to the Americas office for help
during off-hours.
Contact information
For contact information, go to the IBM Internet Security Systems Contact Technical
Support Web page at http://www.ibm.com/services/us/iss/support/.
viii Enterprise Scanner: User Guide
Page 9

Part 1. Scanning from the Proventia Manager
This section explains how to manage scans from the Proventia Manager for the
Enterprise Scanner agent.
Chapters
Chapter 1, “Ad hoc scanning in the Proventia Manager,” on page 3
Chapter 2, “Interpreting scan results in the Proventia Manager,” on page 21
© Copyright IBM Corp. 1997, 2009 1
Page 10

2 Enterprise Scanner: User Guide
Page 11

Chapter 1. Ad hoc scanning in the Proventia Manager
This chapter explains how to use perspective and the high-level processes behind
ad hoc scanning from the Proventia Manager.
Section A: Network configuration
“Configuring the management network interface” on page 4
“Configuring the scanning network interface” on page 5
“Configuring scanning interface DNS settings” on page 6
“Assigning perspective to a scanning interface” on page 7
“Configuring routes for perspective” on page 7
Section B: Policy configuration
“Defining assets for a discovery scan” on page 8
“Displaying assessment checks by groups” on page 9
“Displaying information about assessment checks” on page 10
“Selecting assessment checks with filters” on page 11
“Configuring common assessment settings for an Assessment policy” on page 12
“Defining assessment credentials for a policy” on page 16
“Defining ports or assets to exclude from a scan” on page 19
“Configuring and saving a scan policy in the Proventia Manager” on page 20
© Copyright IBM Corp. 1997, 2009 3
Page 12
Section A: Network configuration
This section explains how to define the network interfaces for the management and
scanning ports, how to assign perspectives to network interfaces, and how to
configure the Enterprise Scanner appliance to select routes for traffic.
Configuring the management network interface
Use the Management Interface tab on the Network Interface Configuration page on
the appliance to configure the management interface network settings (ETH0).
About this task
You configured the management interface when you set up the appliance with the
Proventia Setup Assistant. Use the procedures in this topic to change those
settings.
Procedure
1. Click Configuration → Network Interfaces in the navigation pane.
2. Click the Management Interface tab, and then type or change the following
information:
Option Description
Host Name The fully qualified domain name for the
Interface The management port used by the
IP address The IP address of the management interface
Subnet Mask The IP address of the subnet mask for the
Gateway The address of the network gateway.
Enterprise Scanner agent. Use the format:
gateway1.example.com
Enterprise Scanner agent.
for the agent.
agent.
3. Select the Use Persistent IP if sensor is behind NAT if you want to avoid
conflicts with NAT rules, and then provide the IP address.
4. Click Save Changes.
4 Enterprise Scanner: User Guide
Page 13
Configuring the scanning network interface
Use the Scan Interface tab on the Network Interface Configuration page on the
appliance to configure the scanning interface network settings (ETH1 - ETH5).
About this task
You configured the scanning interface when you set up the appliance with the
Proventia Setup Assistant. Use the procedures in this topic to change those
settings.
Procedure
1. Click Configuration → Network Interfaces in the navigation pane.
2. Click the Scan Interface tab, and then type or change the following
information:
Option Description
Interface The Ethernet port of the interfaces for the
agent.
IP Address The IP address of the scanning network
interface for the agent.
Subnet Mask The IP address for the scanning network
interface subnet mask of the agent.
Gateway The address of the network gateway.
Maximum IPs per discovery subtask The maximum number of IP addresses to
discover in a subtask (of a task for each scan
job).
Note: This value applies to all discovery
scans that the agent runs.
Maximum assets per assessment subtask The maximum number of assets to scan in a
subtask (of a task for each scan job).
Note: This value applies to all assessment
scans that the agent runs.
Perspective (network location) The name of the network location to
associate with this scanning port.
Values: Global, the default, and any network
locations defined in the Network Locations
policy.
3. Click Save Changes.
Chapter 1. Ad hoc scanning in the Proventia Manager 5
Page 14
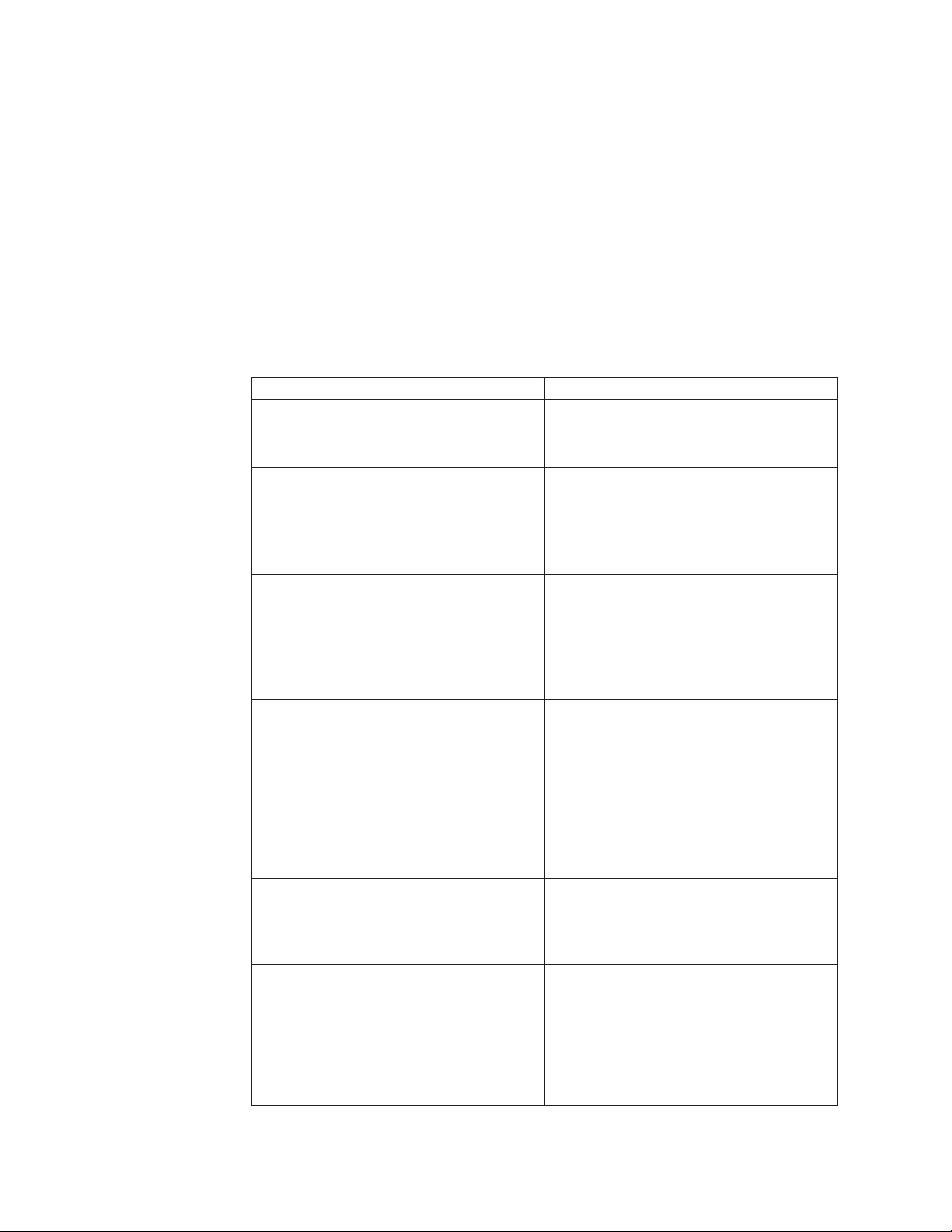
Configuring scanning interface DNS settings
Use the DNS tab on the Network Interface Configuration page on the appliance to
configure the DNS settings for the scanning interface.
About this task
You configured these settings when you set up the appliance with the Proventia
Setup Assistant. Use the procedures in this topic to change those settings.
Procedure
1. Click Configuration → Network Interfaces in the navigation pane.
2. Click the DNS tab.
3. Choose an option:
If you want to... Then...
Specify DNS settings
Add a DNS search path
Edit a DNS search path
Copy and paste a DNS search path
Remove a DNS search path
Change the order of a DNS search path
1. Type the IP addresses for the primary,
secondary, and tertiary DNS servers.
2. Click Save Changes.
1. In the DNS Search Path section, click the
Add icon.
2. Type the domain name to add to the
search list, and then click OK.
3. Click Save Changes.
1. In the DNS Search Path list, select a
domain name, and then click the Edit
icon.
2. Edit the domain name, and then click
OK.
3. Click Save Changes.
1. In the DNS Search Path section, select a
domain name, and then click the Copy
icon. The agent copies the search path to
the clipboard.
2. Click the Paste icon. The agent copies the
search path to the end of the list.
3. If necessary, edit the policy, and then
click OK.
4. Click Save Changes.
1. In the DNS Search Path section, select a
domain name, and then click the
Remove icon.
2. Click Save Changes.
1. In the DNS Search Path section, select a
domain name.
2. Click the Up or Down arrows.
Tip: It is more efficient to place the most
likely used search path at the top of the
list.
3. Click Save Changes.
6 Enterprise Scanner: User Guide
Page 15

Assigning perspective to a scanning interface
Use the Network Locations tab on the Network Locations page on the appliance to
assign a perspective (network location) to a scanning interface.
About this task
You can only configure the ETH0 and ETH1 interfaces in Proventia Setup. You
must configure the remaining interfaces on this page (Network Locations page).
When you register the agent with SiteProtector, the perspectives you set here
(ETH2 - ETH5) are not automatically imported by the Network Locations policy in
SiteProtector. You must redefine those perspectives for this policy in SiteProtector.
Procedure
1. Click Configuration → Network Locations in the navigation pane.
2. Click the Network Locations tab.
3. Click the Add icon.
4. Type a name for the perspective in the Network Locations Name field, and
then click OK.
Important: You can only assign one unique perspective per scanning port. You
cannot assign the same perspective to more than one scanning port.
Configuring routes for perspective
Use the Routes tab on the Network Locations page on the appliance to configure
the appliance to select paths for (routes) traffic.
About this task
In a multi-segmented network, you might experience unnecessary network traffic if
your agent traffic is routed through your default gateway. You can reduce network
traffic if you configure routes for perspectives that provide more direct routes to
targeted segments.
Procedure
1. Click Configuration → Network Locations in the navigation pane.
2. Click the Routes tab.
3. Click the Add icon.
4. Complete the following fields:
Option Description
Perspective The perspective for which you are defining a
route.
Destination Network A network segment for which you want to
define a specific route for a perspective.
Gateway The IP address of the router the agent
should use to find IP addresses in the
Destination Network. Use the IP address
that is on the same network as the agent,
not the IP address of the route from inside
the target segment.
Chapter 1. Ad hoc scanning in the Proventia Manager 7
Page 16
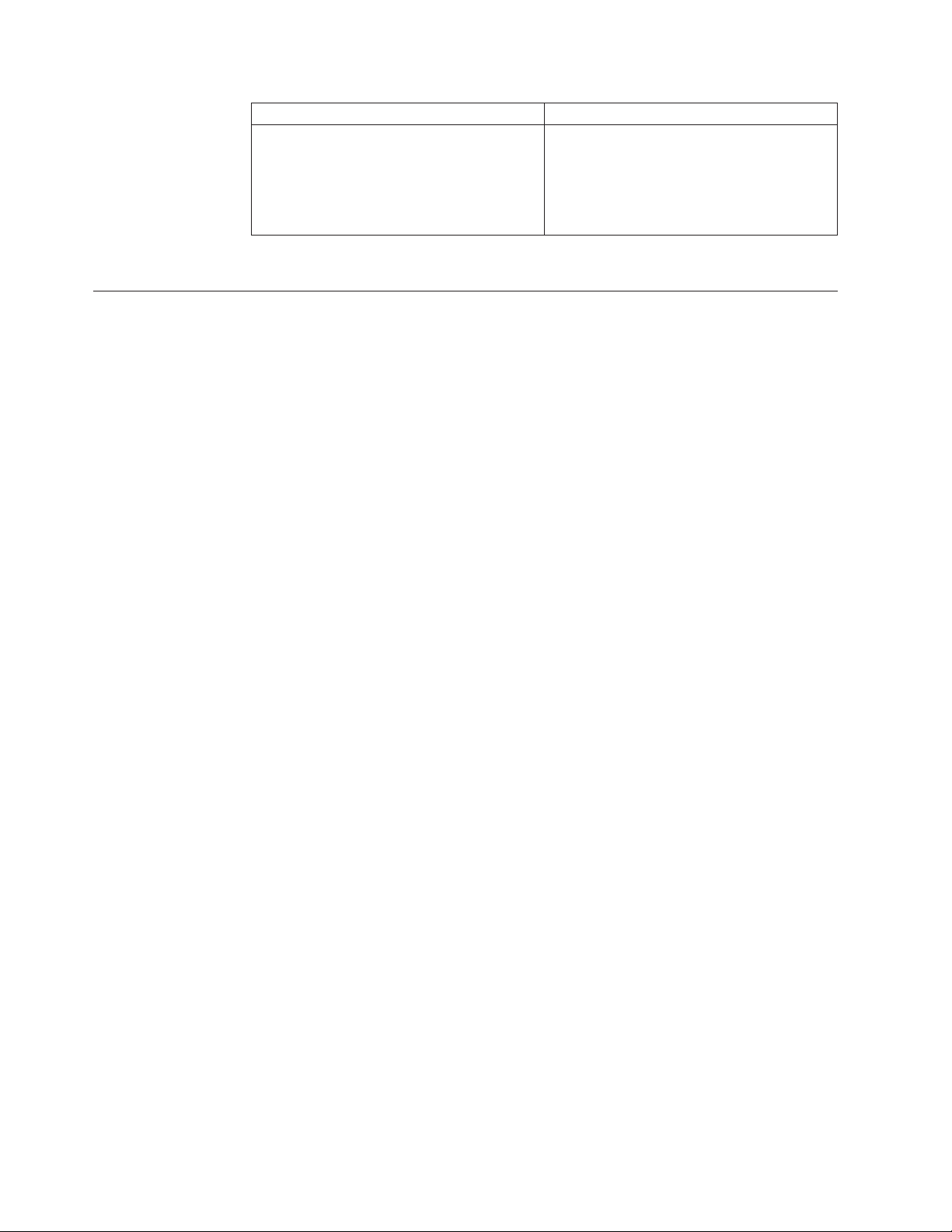
Option Description
Metric If you configure more than one route to the
5. Click Save Changes.
Section B: Policy configuration
This section explains how to configure policy settings in order to manage
vulnerabilities.
Defining assets for a discovery scan
Use the Discovery policy type on the Policy Management page on the appliance to
configure a policy that defines the parameters used to perform a discovery scan on
a portion of a network.
Before you begin
Before it can perform OS fingerprinting on an asset, your agent must find one
open and one closed port. To find an open and a closed port, the agent scans ports
1–1023 and any other ports specified in the applicable Network Services policy.
same segment for one perspective, a number
that indicates the preferred route. The closer
to 1, the more preferred the route.
Note: The numbers you use do not have to
be consecutive.
About this task
In a discovery task, a range of IP addresses is scanned to locate active network
interfaces, and the type of device associated with each active network interface is
determined through OS identification.
Procedure
1. Click Scan → Policy Management in the navigation pane.
2. Select Discovery from the Policy Types list, and then click Add.
3. Type a name for the scan policy.
4. Type the IP addresses (in dotted-decimal or CIDR notation) of the assets to
discover in the IP range(s) to scan box as in the following examples:
v Type an IP address, and then press ENTER.
v Type a range of IP addresses, and then press ENTER.
Example: 172.1.1.100-172.1.1.200
v Type a combination of both choices above, and then press ENTER.
Note: A red box appears around the IP range(s) to scan box until the data is
validated.
5. If you want to ping each IP address before scanning to exclude unreachable
hosts from the scan, select the Ping hosts in this range, before scanning, to
exclude unreachable hosts check box.
6. If you want to add newly discovered assets to the group where you have
defined the scan, rather than to the Ungrouped Assets group, select the Add
newly discovered assets to group check box.
8 Enterprise Scanner: User Guide
Page 17

7. If you want to add previously known assets that are already defined in other
groups to the scan group, select the Add previously known assets to group
check box.
Displaying assessment checks by groups
Use the Checks tab in the Assessment policy to group checks by any combination
of columns that you have chosen to display. For example, you might want to see
checks by category, then by severity within that category.
About this task
The current grouping selections are displayed just above the column headers of the
checks.
v If no groups are selected, the following message is displayed on the screen:
Right click on the column header to group by that column.
v If groups are selected, the group names are displayed on in the screen as in the
following example:
Procedure
1. Click Scan → Policy Management in the navigation pane.
2. Select Assessment from the Policy Types list, and then click Add.
3. Type a name for the scan policy.
4. Click the Checks tab.
5. Choose an option:
If you want to... Then...
Clear groupings Choose an option:
v Right-click any column header, and then
select Clear Groupings from the pop-up
menu.
v Click Clear Groupings.
Create groupings interactively
1. Right-click a column heading, and then
select Group By from the pop-up menu.
2. Repeat the previous step until you have
created the groupings that you want.
Chapter 1. Ad hoc scanning in the Proventia Manager 9
Page 18
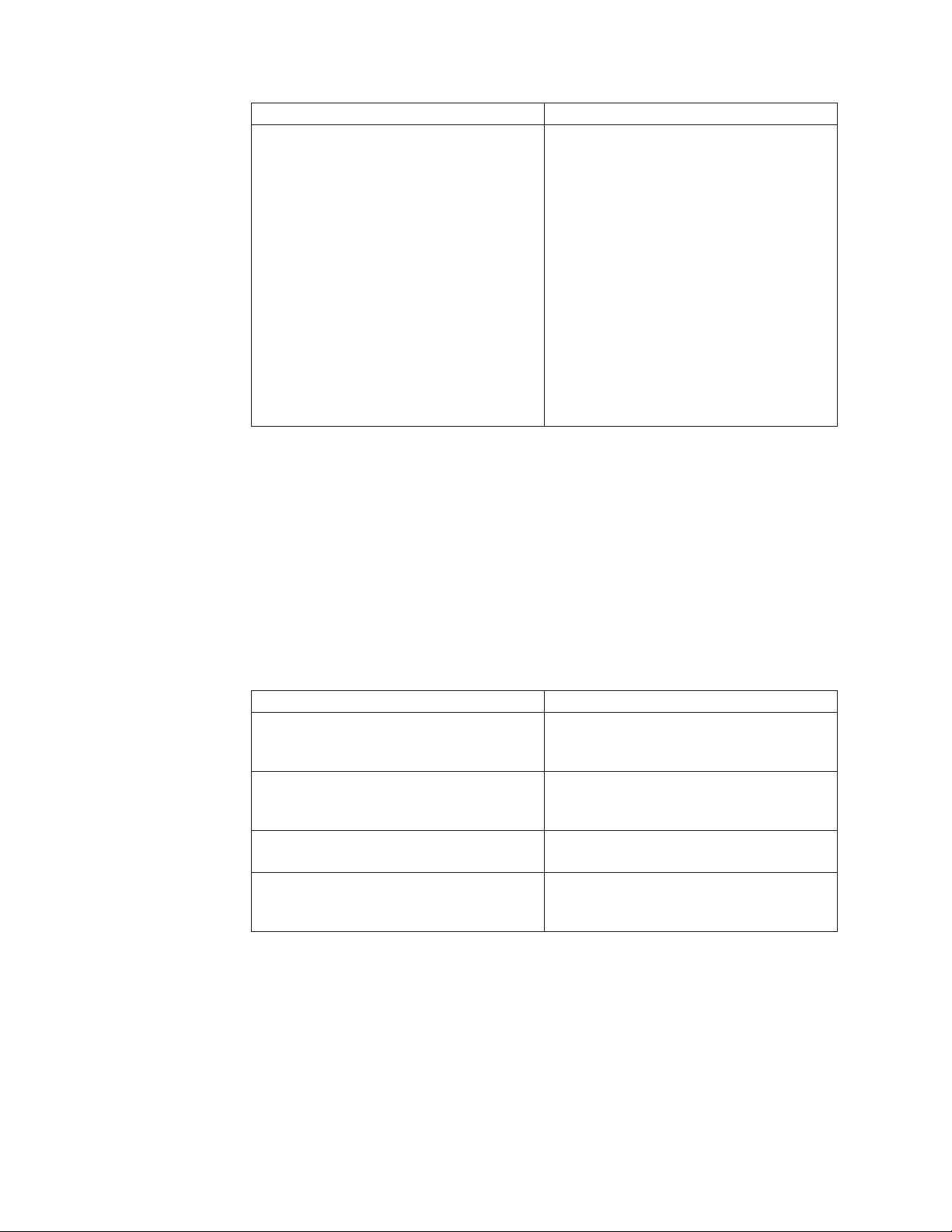
If you want to... Then...
Create groupings from a selection list
1. Click the Group By icon.
The Group by Columns window
appears.
2. Select a column to group by in the All
Columns list, and then click Add.
The column moves to the Group by these
Columns list.
3. Repeat the previous step for each column
that you want to group by.
4. If you want to remove items from the
list, select an item in the Group by these
Columns list, and then click Remove.
The item and any items below it move to
the All Columns list.
5. Click OK.
Displaying information about assessment checks
Use the Checks tab in the Assessment policy to choose how much information to
display about each assessment check in the Assessment policy.
Procedure
1. Click Scan → Policy Management in the navigation pane.
2. Select Assessment from the Policy Types list, and then click Add.
3. Type a name for the scan policy.
4. Click the Checks tab.
5. Choose an option:
If you want to... Then...
Add a single column Right-click a column and then select the
column to add from the pop-up menu.
Note: The column appears at the far right.
Remove a single column Right-click a column and then select the
column to remove.
Note: The column is removed.
Add multiple columns Click the Column to display icon, and then
select the check box for each column to add.
Remove multiple columns Click the Column to display icon, and then
clear the check box for each column to
remove.
10 Enterprise Scanner: User Guide
Page 19

Selecting assessment checks with filters
Use the Checks tab in the Assessment policy to provide filtering values on a
selected list of assessment checks.
About this task
The following rules apply to using regular expressions:
v The match occurs against all columns in the table, whether or not the column is
displayed.
v If you use more than one regular expression, every regular expression must
match for a check to be selected.
Procedure
1. Click Scan → Policy Management in the navigation pane.
2. Select Assessment from the Policy Types list, and then click Add.
3. Type a name for the scan policy.
4. Click the Checks tab.
5. Select the Filter check box, and then click Filter.
6. To filter with a regular expression, type one or more regular expressions on
separate lines in the Regular Expression box.
Tip: For example, use http.* to match the value in any column that starts with
http; or use .*http.* to match the value in any column that contains http.
7. To filter by one or more of the remaining filter types, select the values to filter
by in the filtering boxes.
Tip: You can select ranges of filtering values by holding down the SHIFT key
and random filtering values by holding down the CTRL key.
8. Click OK.
Chapter 1. Ad hoc scanning in the Proventia Manager 11
Page 20

Configuring common assessment settings for an Assessment policy
Use the Common Settings tab in the Assessment policy to choose settings that
define additional scanning behavior for the checks you have selected to run in an
assessment scan.
Procedure
1. Click Scan → Policy Management in the navigation pane.
2. Select Assessment from the Policy Types list, and then click Add.
3. Type a name for the scan policy.
4. Click the Common Settings tab.
5. Type the URL or file location for the assessment check Help documentation in
the Help HTML Prefix box:
v The IBM ISS Web site location of up-to-date assessment check
documentation.
v The file location of a locally stored version of the documentation.
6. If you want to run the checks that are enabled by default, including checks
added in an X-Press Update (XPU), select a policy in the Compliance Policies
section.
CAUTION:
Custom Policy (All) runs all vulnerability checks, including DOS checks.
7. Configure options for service discovery in the Service Discovery section:
Option Description
Discover and report TCP services Reports active TCP services for which the
Service Scan flag is enabled in the Network
Services policy.
Discover and report UDP services Reports active UDP services for which the
Service Scan flag is enabled in the Network
Services policy.
8. Configure options for assessment port ranges in the Assessment Port Ranges
section:
Option Description
Ports to scan with generic TCP checks The set of TCP ports to scan with generic
TCP checks. You can specify ports using any
of the following methods:
v Type a port or range of ports.
v Click Well known and select ports from
the list.
v Select All.
Note: A generic TCP check is one whose
target type is tcp.
12 Enterprise Scanner: User Guide
Page 21
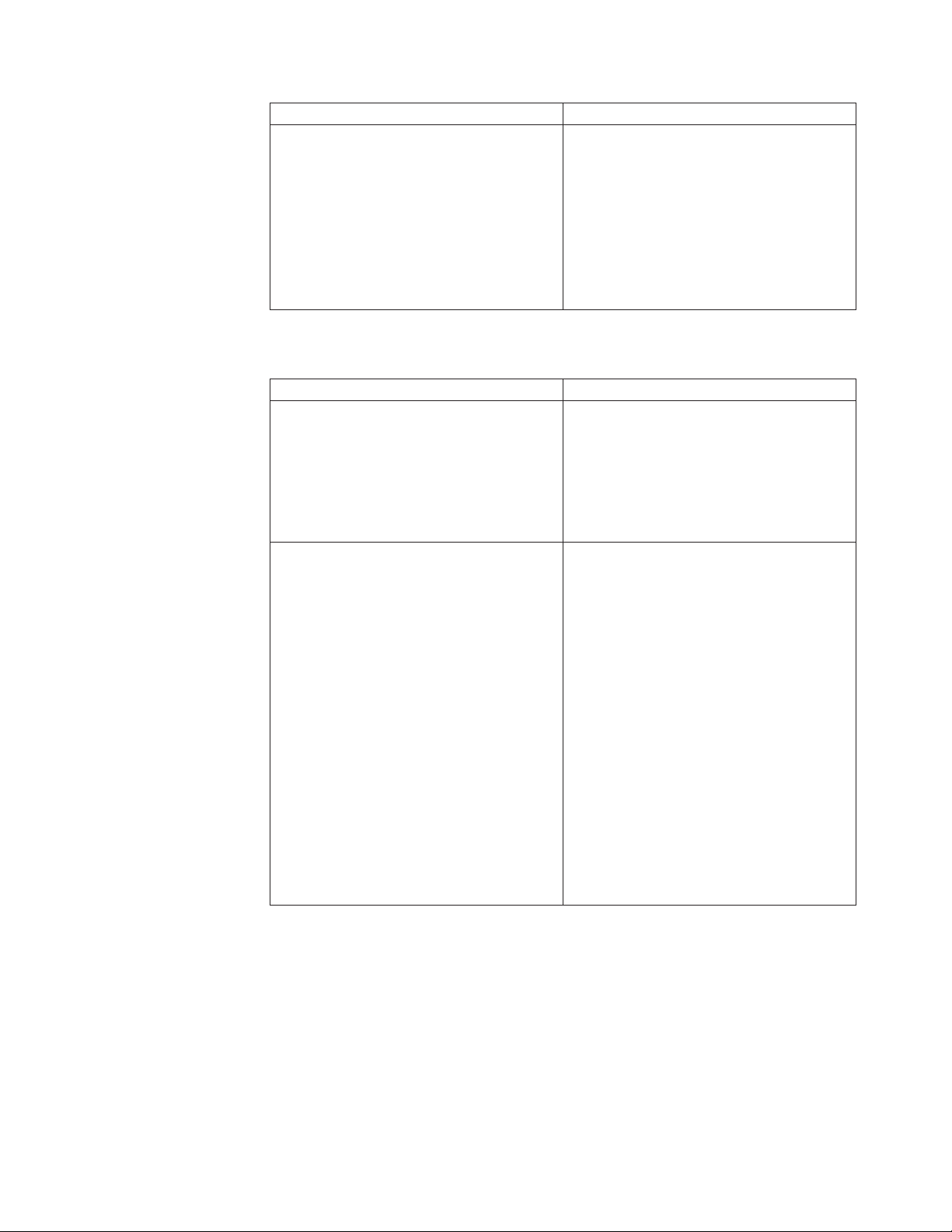
Option Description
Ports to scan with generic UDP checks The set of UDP ports to scan with generic
UDP checks. You can specify ports using any
of the following methods:
v Type a port or range of ports.
v Click Well known and select ports from
the list.
v Select All.
Note: A generic UDP check is one whose
target type is udp.
9. Configure options for using OS information in the Use of OS Information
section:
Option Description
Dynamically determine OS if previously
obtained information is older than
For unverified OS’s: Specify which checks to run if the OS is
The maximum age (in minutes) of usable OS
information.
If the OS information for an asset is older
than the time specified, Enterprise Scanner
reassesses OSID when it runs an assessment
scan.
Default: 120
uncertain.
v Run all checks (lowest performance): If
Enterprise Scanner is uncertain about the
OS of the asset, it runs all assessment
checks.
v Run all checks that apply to general OS
(intermediate performance): If Enterprise
Scanner is uncertain about the OS of the
asset, it runs checks for all versions of an
operating system. (For example, if
Enterprise Scanner is uncertain about
which version a Windows operating
system is, it runs all the checks for all
versions of Win dows operating systems.)
v Run only checks that apply to specific
OS (Best performance): If Enterprise
Scanner is uncertain about the OS of the
asset, runs only the checks that apply to
the exact version of the operating system.
10. Configure options for application fingerprinting in the Use of Application
Fingerprinting section:
Chapter 1. Ad hoc scanning in the Proventia Manager 13
Page 22
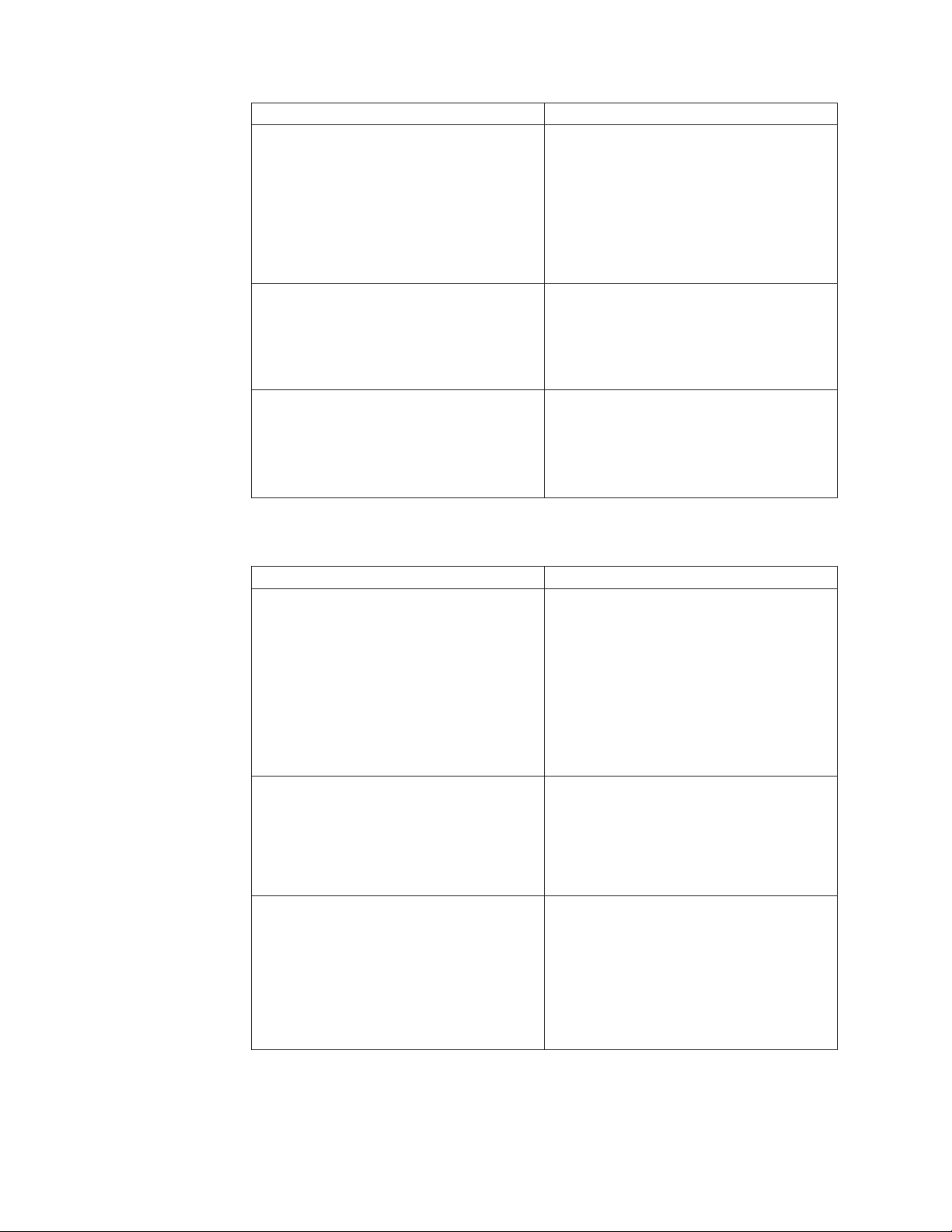
Option Description
Do not perform application fingerprinting Does not try to specifically identify which
applications are communicating over which
ports, and runs the checks as selected in the
Assessment policy.
This option does not identify applications
communicating over non-standard ports.
(Checks are run against standard ports as
defined in the Network Services policy.)
Fingerprint applications and run checks
that apply to application protocol (e.g.,
http)
Fingerprint applications and run checks
that apply to specific application (e.g.,
apache)
Identifies applications communicating over
specific ports, and then runs checks that
apply to the protocol in use.
This option identifies applications
communicating over non-standard ports.
Identifies applications communicating over
specific ports, and then runs checks that
apply only to the application identified.
This option identifies applications
communicating over non-standard ports.
11. The settings in the Account Verification section apply only if an Assessment
Credentials policy is available for the group being scanned.
Option Description
Verify account access level before using
Access domain controllers to verify access
level
Check local group membership to verify
access level
v If disabled, Enterprise Scanner assumes
that whatever is specified in the
Assessment Credentials policy is accurate.
v If enabled, Enterprise Scanner tries to
confirm that the access level specified in
the Assessment Credentials policy is
correct.
Important: You should enable the Check
local group membership to verify access
level if you enable account verification.
v If disabled, Enterprise Scanner does not
communicate with a Domain Controller in
the process of verifying access levels.
v If enabled, Enterprise Scanner tries to
communicate with a Domain Controller in
the process of verifying access levels.
v If disabled, Enterprise Scanner does not
try to confirm the access level for the
account during assessment by checking
which local groups the asset belong to.
v If enabled, Enterprise Scanner tries to
confirm the access level for the account
during assessment by checking which
local groups the asset belong to.
12. Configure the options for locking out accounts in the Account Lockout
Control section:
14 Enterprise Scanner: User Guide
Page 23
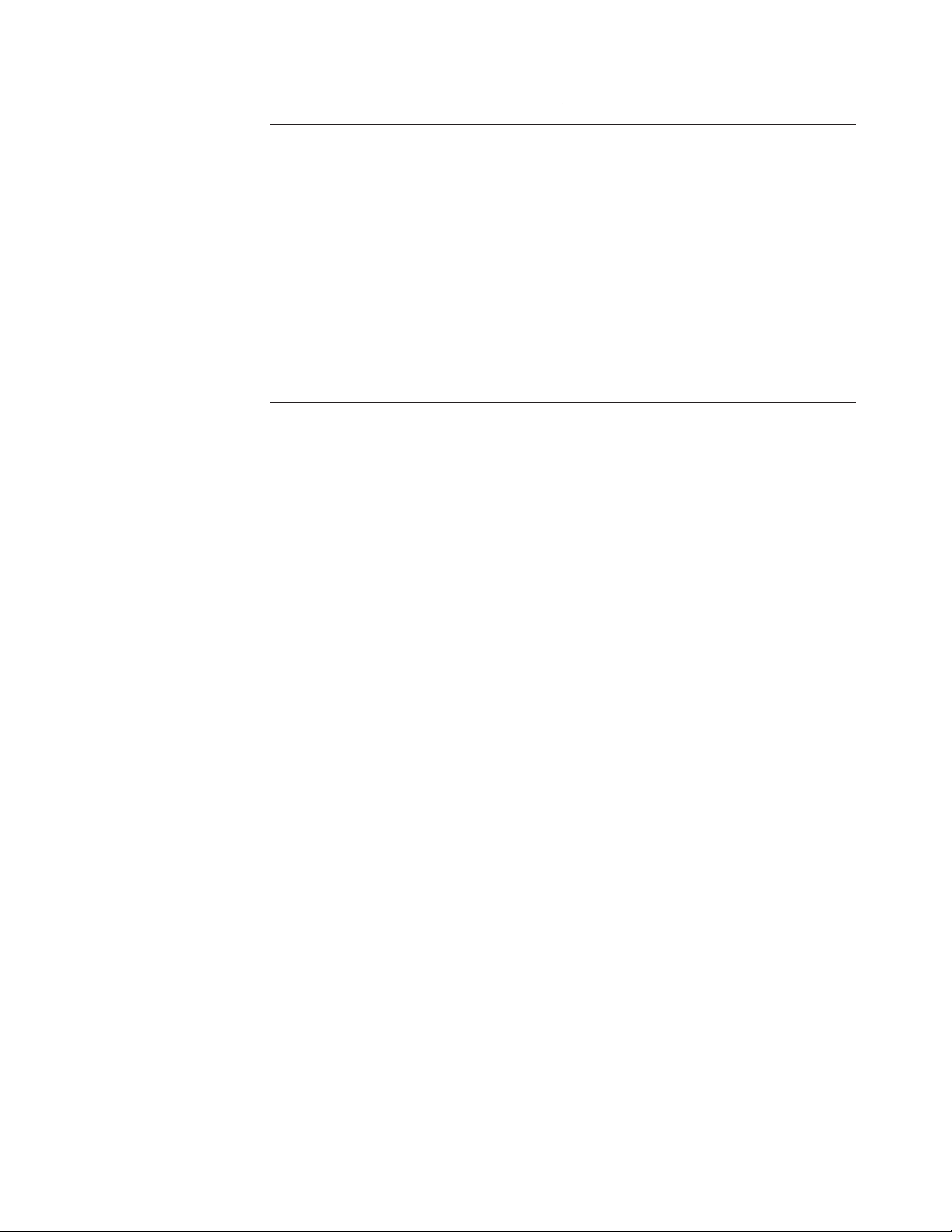
Option Description
Allowed account lockout Select a type of lockout:
v No lockout allowed: Enterprise Scanner
avoids running password guessing checks
if account lockout is enabled on the target
host, or if its status cannot be determined.
v Temporary lockout allowed: Enterprise
Scanner runs password guessing checks
only if the account lockout duration is less
than or equal to the value specified in the
Maximum Allowable Lockout Duration
option later in this section.
v Permanent lockout allowed:Enterprise
Scanner runs password guessing checks
even if the account lockout duration is set
to run infinitely.
Longest allowed temporary lockout Specifies the maximum time (in minutes)
that accounts are allowed to be locked out
by password guessing checks.
This value applies only if Temporary
Lockout Allowed is enabled. When
temporary lockout is allowed, password
guessing checks are run only against assets
whose lockout policy disables locked out
accounts for no more than the maximum
allowed lockout time.
Chapter 1. Ad hoc scanning in the Proventia Manager 15
Page 24
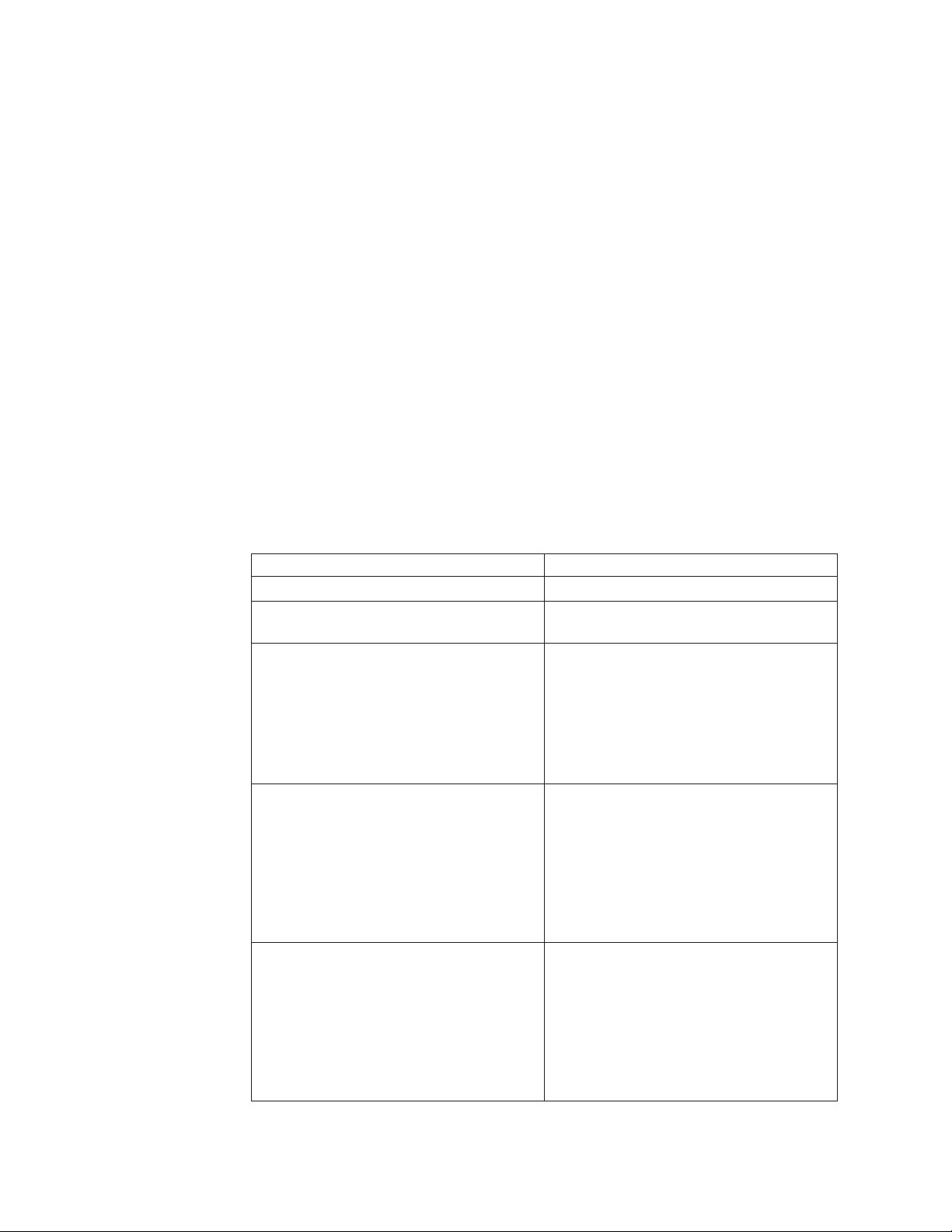
Defining assessment credentials for a policy
Use the Assessment Credentials policy type on the Policy Management page to
define authentication credentials for your assets.
About this task
The appliance uses authentication credentials to access accounts during assessment
scans. Enterprise Scanner uses all instances of the credentials that are defined for
the group when it scans assets in the group. You can define different instances of
this policy for different groups, which makes it possible to supply different log on
credentials to scan different parts of the network.
Important: The Assessment Credentials policy currently works only with assets
that run Windows operating systems.
Procedure
1. Click Scan → Policy Management in the navigation pane.
2. Select Assessment Credentials from the Policy Types list, and then click Add.
3. Confirm your password, and then click OK.
4. Type a name for the scan policy.
5. In the Assessment Credentials tab, click Add, and then provide the following
account information:
Option Description
Username The user identification for an account.
Password The password to use with the user name to
log into an account.
Account Type: Windows Local Indicates that the user account is defined
locally on a single Windows device. The
account is used to attempt to log in to a
single Windows device.
When you choose this option, you must
provide a Windows host name in the
Domain/Host box.
Account Type: Windows
Domain/Workgroup
Account Type: Windows Active Directory Indicates that the user account is defined in
Indicates that the user account is defined in
a Windows Domain or Workgroup. The
account is used to attempt to log in to all
Windows devices within the domain or
workgroup.
When you choose this option, you must
provide the Windows Domain or Workgroup
name in the Domain/Host box.
a Windows Active Directory Domain. The
account is used to attempt to log in to all
Windows devices within the Active
Directory domain.
16 Enterprise Scanner: User Guide
When you choose this option, you must
provide the Active Directory Domain name
in the Domain/Host box.
Page 25
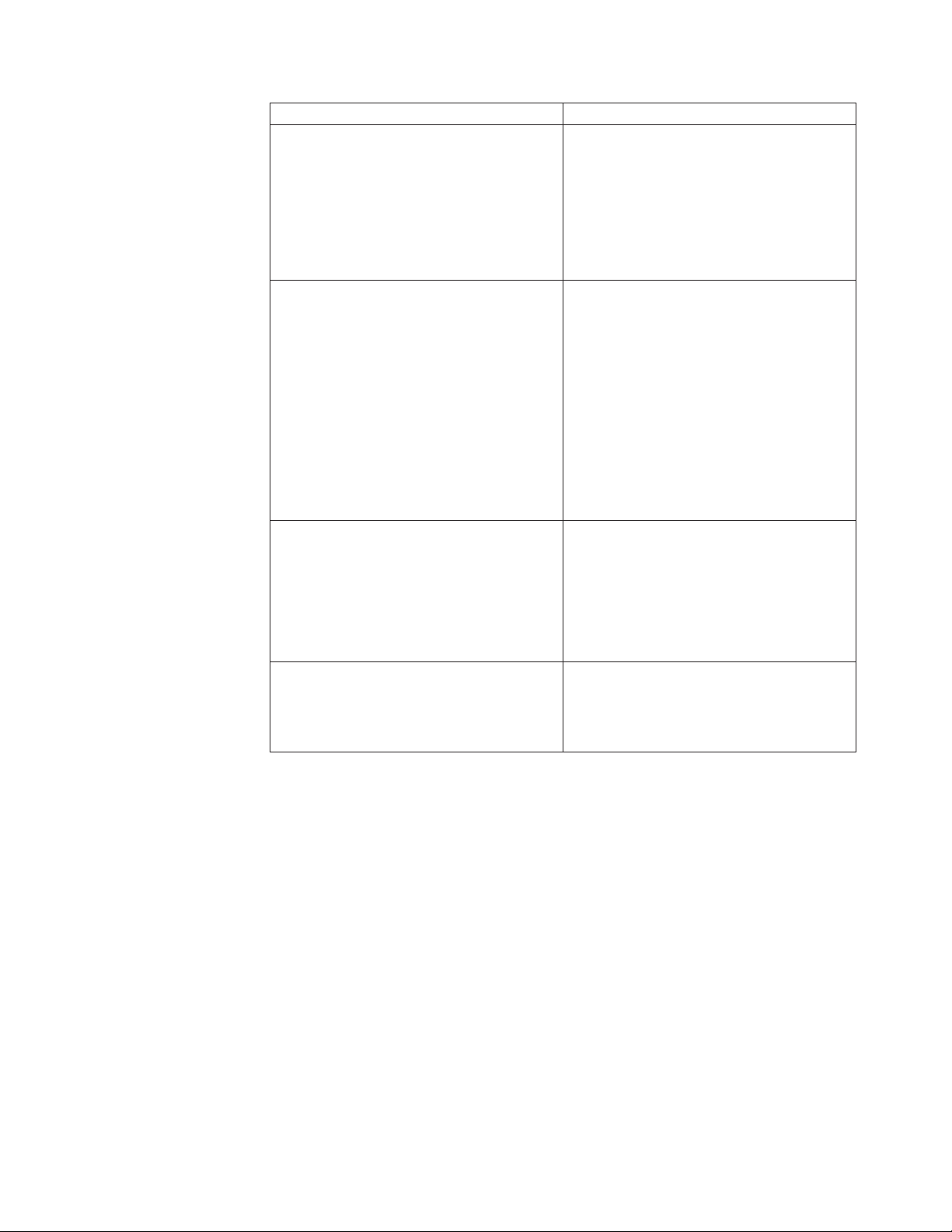
Option Description
Account Type: SSH Local
Account Type: SSH Domain
Domain/Host Applies to one of the following domains or
Account Level Applies to one of the following accounts:
Indicates that the user account is defined
locally on a single Unix device that allows
SSH logons. The account is used to attempt
login to a single Unix device.
When you choose this option, you must
provide an IP address in the Domain/Host
box.
Indicates that the user account is defined for
Unix devices that allow SSH logons. In this
context, ″Domain″ loosely refers to a set of
devices, rather than to a specific type of
domain. The account is used to attempt to
log in to all SSH devices covered by the
policy.
When you choose this option, you should
supply a descriptive name in the
Domain/Host box. This is for
documentation purposes only; it is not used
by Enterprise Scanner.
hosts:
v For Windows accounts, the domain or
host name to which the account applies.
v For SSH Local accounts, the IP address of
the device to which the account applies.
v For SSH Domain accounts, any text.
v Administrator
v User
v Guest
Important: To avoid locking an account, do not add the account more than
once.
Chapter 1. Ad hoc scanning in the Proventia Manager 17
Page 26
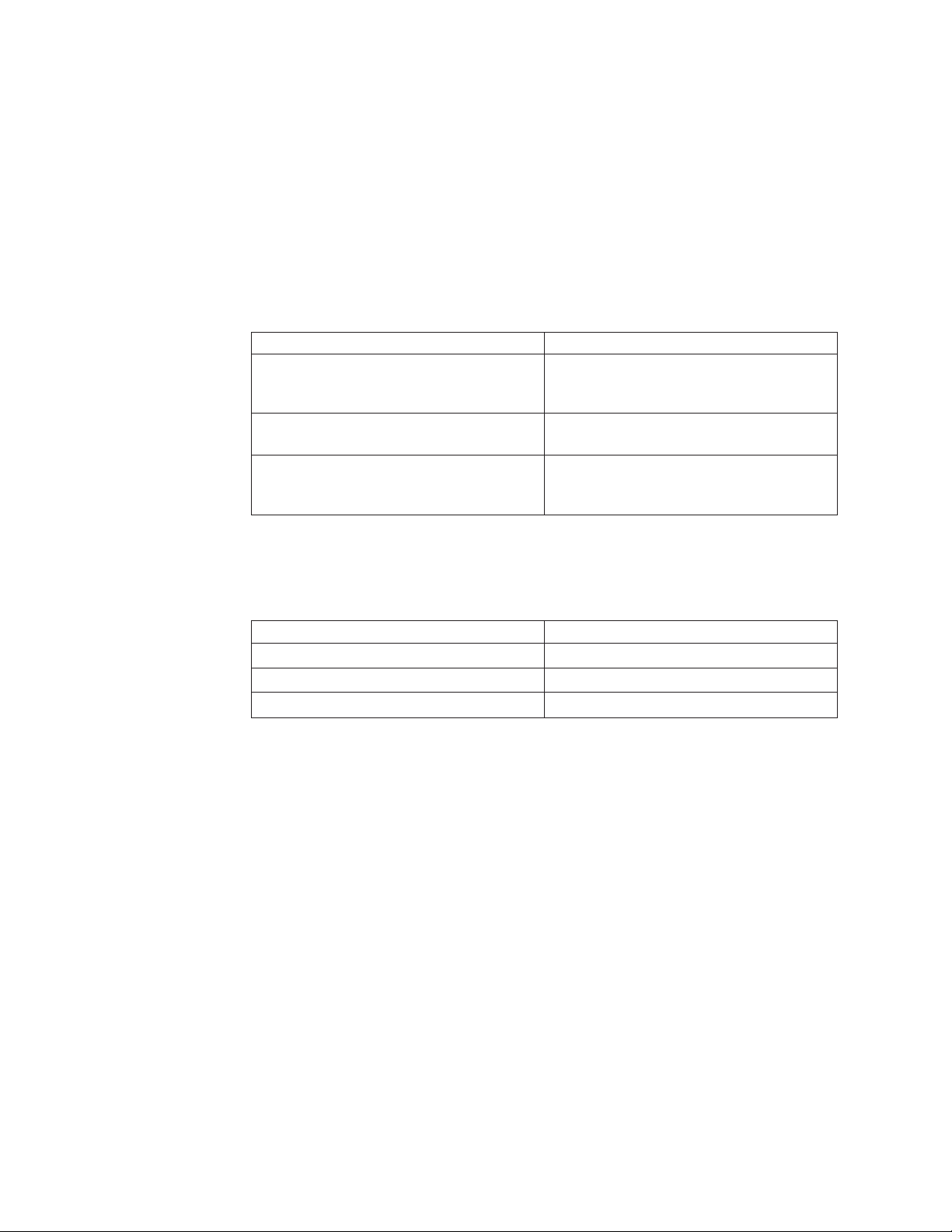
Defining the service names associated with TCP and UDP ports
Use the Network Services policy type on the Policy Management page to define
service names associated with TCP and UDP ports.
Procedure
1. Click Scan → Policy Management in the navigation pane.
2. Select Network Services from the Policy Types list, and then click Add.
3. Type a name for the scan policy.
4. For default or customized services, choose an option:
If you want to... Then...
Change the description of a service Slowly click Description two times to switch
to edit mode, and then change the
description.
Allow each service to operate over SSL in
at least some part of your network
Allow service scans for this service over
any TCP and UDP ports specified in the
Assessment policy
Note: You cannot change the Service name, Port, or Protocol of default
services. You cannot delete default services.
5. For customized services, choose an option:
Select the May use SSL check box for that
service.
Select the Service scan check box.
If you want to... Then...
Add a service Click the Add icon.
Modify a service Click the Modify icon.
Delete a service Click the Delete icon.
18 Enterprise Scanner: User Guide
Page 27
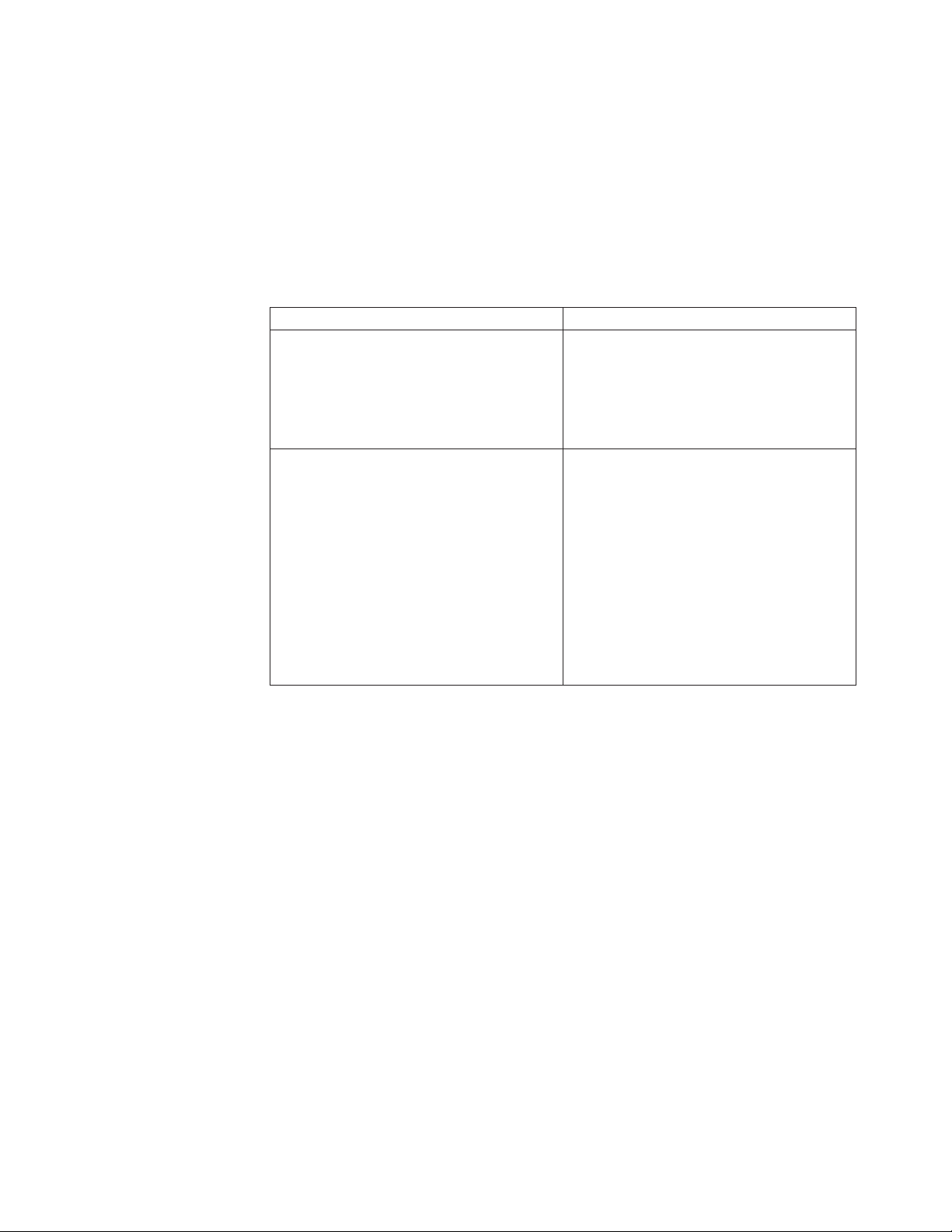
Defining ports or assets to exclude from a scan
Use the Scan Exclusion policy type on the Policy Management page to define
specific ports or assets to exclude from a scan of a group of assets.
Procedure
1. Click Scan → Policy Management in the navigation pane.
2. Select Scan Exclusion from the Policy Types list, and then click Add.
3. Type a name for the scan policy.
4. Choose an option:
If you want to... Then...
Exclude ports Use a combination of typing the ports to
exclude and choosing the ports:
v Type the ports to exclude, separated by
commas, in the Excluded Ports box.
v Click Well Known Ports, and then select
the ports to exclude.
Exclude assets Type the IP addresses (in dotted-decimal or
CIDR notation) of the hosts to exclude in the
Excluded Hosts box:
v Type an IP address, and then press ENTER.
v Type a range of IP addresses, and then
press ENTER.
Example: 172.1.1.100-172.1.1.200
v Type a combination of both choices above,
and then press ENTER.
Note: A red box is displayed around the
Excluded Hosts box until the data is
validated.
Chapter 1. Ad hoc scanning in the Proventia Manager 19
Page 28

Configuring and saving a scan policy in the Proventia Manager
Use the Policy Management page on the appliance to configure discovery and
assessment scan policies from Proventia Manager for auditing purposes, and then
use those policies for one-time (ad hoc) scans that you initialize from the LMI Scan
Control page.
Before you begin
You will not be able to run scans from Proventia Manager if the appliance is
registered with SiteProtector.
Procedure
1. Click Scan → Policy Management in the navigation pane.
2. Choose the scan policy that you want to configure from the Policy Types list,
and then click Add.
3. Type a name for the scan policy, and then configure the settings for the scan
policy. Policy names are limited to 32 characters using any combination of
letters or numbers. You cannot use a dash (-) or underscore (_) in the policy
name. You can run the following combinations of scans:
v Discovery scan
v Discovery and an assessment scan
You cannot run an assessment only scan from the Proventia Manager. The
following table lists which scan policies are required to run an ad hoc scan
from Proventia Manager:
Table 2. Policies used for ad hoc scanning in Proventia Manager
Scan policy Required
Discovery Yes
Assessment Yes
Assessment Credential No
Network Services No
Scan Exclusion No
*You should run a discovery scan policy first (to identify assets on the network) before you
run an assessment scan.
4. Click Save Changes to save the scan policy. You are now ready to run an ad
hoc scan using a configured scan policy.
5. Click Scan → Run Scan in the navigation pane. The LMI Scan Control page is
displayed in Proventia Manager.
20 Enterprise Scanner: User Guide
Page 29

Chapter 2. Interpreting scan results in the Proventia Manager
This chapter explains how to monitor and view scan results in the Proventia
Manager.
Topics
“Running an ad hoc scan” on page 22
“Monitoring the status of a scan” on page 23
“Viewing the results of an ad hoc scan” on page 24
“Exporting scan results from Proventia Manager” on page 24
“Purging scan data from the database” on page 25
© Copyright IBM Corp. 1997, 2009 21
Page 30

Running an ad hoc scan
Use the LMI Scan Control page on the appliance to define and run ad hoc scans
for assessment and discovery.
Before you begin
Before you can run a scan, make sure you have configured a scan from the Policy
Management page.
Procedure
1. Click Scan → Run Scan in the navigation pane.
2. Depending on what type of scan you are running (discovery or assessment),
provide a name for the scan job in the Discovery Job Name or Assessment Job
Name field.
Tip: The scan job name is useful when you want to view the results and status
of the scan.
3. From the fields provided in the LMI Scan area, determine what type of scan
you need to run, and then select a configured scan policy from the list. You can
run the following combinations of scans:
v Discovery scan
v Discovery and an assessment scan
You cannot run an assessment only scan from the Proventia Manager. Because
the appliance does not use a database to store asset information, you must run
a discovery scan followed by an assessment scan.
4. Select what network location (or perspective) you need to run the scan policy
against from the Perform scans from this perspective (Network location) list.
5. Click Save Changes to start the ad hoc scan.
22 Enterprise Scanner: User Guide
Page 31

Monitoring the status of a scan
Use the Scan Status page on the appliance to view the status of ad hoc discovery
and assessment scans you have initialized from the LMI Scan Control page.
About this task
While Proventia Manager processes the scan, you can perform one of the following
actions on the scan:
Table 3. Processing status of a scan
Action Icon Description
Pause
Resume
Cancel
Procedure
1. Click Scan → Scan Status in the navigation pane.
The Scan Status page appears with a table displaying the status of the scan.
Use the Pause option only
when a job is in the
processing status. Pausing a
job in any other status might
cause problems if you try to
resume or rerun the scan.
Resume the scan after you
have paused it
Cancel the scan altogether
Note: The results of the scan can take up to a minute to display on this page.
2. Click the link for the scan in the Name column to display the results of the
scan on the Scan Results page.
Chapter 2. Interpreting scan results in the Proventia Manager 23
Page 32

Viewing the results of an ad hoc scan
Use the Scan Results page on the appliance to analyze security-related data
discovered by an ad hoc scan.
Procedure
1. Click Scan → Scan Results in the navigation pane.
2. Choose the scan date (time stamp) from the List Scans list, and then click Go.
3. Select the scan job from the Scan Type list, and then click Go. The results of
the scan are displayed in the table.
4. Click View/Manage Log Files.
5. Select the scan job in the File Name list. The name of the log file contains the
date the scan was run and uses this format: lmiScans/mmddyyyy_xxxxx.log
6. Click Download to the download the log file for the scan to a directory on
your computer. Scan data files are located in the /var/log/esm/lmiScans
directory.
Exporting scan results from Proventia Manager
Use the Scan Reports page on the appliance to export scan results to HTML or
CSV files from Proventia Manager.
About this task
This feature provides basic reporting for ad hoc scans initialized from Proventia
Manager. It is not intended to replace the full analysis and reporting functions of
SiteProtector.
Procedure
1. Click Scan → Scan Reports in the navigation pane.
2. Select the discovery or assessment scan that you want to export from the List
Scans list.
3. Select how you want to sort the hosts in the report.
4. Select the Report checks which found no vulnerability check box if you want
to include information about checks that did not find a vulnerability.
5. Depending on the type of report you need to generate, click Generate HTML
Report or Generate CSV Files.
6. Save the file to your local system. Enterprise Scanner uses the following file
name convention for exported results:
Discovery: DiscoveryResults-<YYYYMMDD>-<HHMMSS><timezone>-<scannername>-<jobname>.csv
Assessment: AssessmentResults-<YYYYMMDD>-<HHMMSS><timezone>-<scannername>-<jobname>.csv
Example: A discovery scan that ran on March 30, 2008 at 1:20:39 PM EST with
a scanner name of testscan and a job name of testjob would display the
following file name: DiscoveryResults-20080330-132039EST-testscan-
testjob.csv
24 Enterprise Scanner: User Guide
Page 33

Purging scan data from the database
Use the Scan Results page on the appliance to schedule the removal of scan data
files from the /var/log/esm/lmiScans directory.
Procedure
1. Click Scan → Scan Results in the navigation pane.
2. Click the Purge Scan Data link. The Purge Scan Data window provides the
following information about the current scan data:
Field Description
Number of Scans The number of individual scans, not scan
Disk Space Used by Scans The amount of disk space consumed by the
Total Disk Space Available The amount of available disk space.
Earliest Scan The date of the first scan.
Latest Scan The date of the latest scan.
Purge Scans Older than: Number of Days The number of days in which all scan data
jobs.
scan data.
older than this amount are deleted from the
disk.
Note: When you purge scan data, that data
is also removed from the Scan Status page
and the Scan Results page.
3. Click Go.
Chapter 2. Interpreting scan results in the Proventia Manager 25
Page 34

26 Enterprise Scanner: User Guide
Page 35

Part 2. Scanning from the SiteProtector Console
This section explains how to manage scans from the SiteProtector Console for the
Enterprise Scanner agent.
Chapters
Chapter 3, “Enterprise Scanner policies,” on page 29
Chapter 4, “Understanding scanning processes in SiteProtector,” on page 67
Chapter 5, “Background scanning in SiteProtector,” on page 79
Chapter 6, “Monitoring scans in SiteProtector,” on page 91
Chapter 7, “Managing scans in SiteProtector,” on page 95
Chapter 8, “Interpreting scan results in SiteProtector,” on page 103
Chapter 9, “Logs and alerts,” on page 121
Chapter 10, “Ticketing and remediation,” on page 133
© Copyright IBM Corp. 1997, 2009 27
Page 36

28 Enterprise Scanner: User Guide
Page 37

Chapter 3. Enterprise Scanner policies
This chapter explains how to use Enterprise Scanner policies to customize your
scanning processes. The policies belong to meaningful categories based on their
scope and impact on scans.
Topics
“Policy inheritance with Enterprise Scanner policies” on page 30
“Deploying an Enterprise Scanner policy from the policy repository” on page 31
“Migrating a locally managed Enterprise Scanner agent into SiteProtector” on page
32
“Viewing asset or agent policies for Enterprise Scanner” on page 33
“Getting vulnerability help for a SiteProtector Console without Internet access” on
page 34
“Agent policies for Enterprise Scanner” on page 35
“Asset policies for Enterprise Scanner” on page 45
© Copyright IBM Corp. 1997, 2009 29
Page 38

Policy inheritance with Enterprise Scanner policies
The inheritance properties of policies in SiteProtector provide a flexible and
efficient method for setting up your scanning environment in a hierarchical group
structure.
General inheritance behavior
In general, inheritance works as follows:
v When you define a policy for a group in your group structure, the policy
automatically applies to the subgroups for the group unless a subgroup already
has its own version of the policy. Then, that subgroup retains its version of the
policy.
v You can break the inheritance at any level in the group structure by redefining
(overriding) the policy for a subgroup. When you define a policy for a
subgroup, the changes apply to its subgroups.
v If you have defined a policy for a subgroup that you want to apply to groups
above it, you can promote the policy to a higher group.
Inheritance with Enterprise Scanner policies
As you plan your Site grouping structure for vulnerability management, keep these
points in mind:
v Most asset policies follow the general rules of inheritance.
v Many agent policies apply only to a single agent or scanning network interface.
v Some asset and some agent policies have specialized inheritance characteristics.
These differences are described in more detail in the following topics.
Inheritance indicators
When you select a group in the left pane of the SiteProtector Console, policies
applicable to the group are displayed in the right pane. The inheritance indicators
of the policies are displayed in the Inheriting From column as follows:
Table 4. Policy inheritance indicators
If the Inheriting From Value is... Then...
blank The policy is defined at the group
level/agent selected in the left pane.
UNCONFIGURED You have chosen to override the policy with
one that is defined higher in the group
structure, but a higher-level policy is not
defined.
a_group_name The policy is inherited from the referenced
group.
Initially blank or unconfigured?
The initial inheritance indicators for agent policies can be blank or unconfigured
depending on whether you override SiteProtector group settings when you register
your agent with SiteProtector:
v If you override the settings, the settings for the agent are applied to the
SiteProtector policies, so that the Inheriting From column is blank.
30 Enterprise Scanner: User Guide
Page 39

v If you do not override the settings, the column follows the inheritance described
in the table above; however, you must configure those policies.
Deploying an Enterprise Scanner policy from the policy repository
Use the policy repository to create, edit, and deploy Enterprise Scanner policies in
SiteProtector. The repository keeps an archive of each saved version of your
policies. After creating or editing a policy, you must deploy it to the appropriate
Enterprise Scanner agents or groups.
About this task
Each time you edit a policy, SiteProtector saves a new version in the repository.
You can deploy any version of a policy to an Enterprise Scanner agent or group on
your Site. You can use the default repository in SiteProtector to manage all of your
policies, or create additional repositories to separate different types or groups of
policies.
Important: You cannot delete a policy from the repository if you have deployed it
anywhere in your Site.
Note: Central Responses can only use Network Objects that are in the default
repository.
Procedure
1. Choose an option:
v Drag the policy icon from the repository to the Enterprise Scanner group or
agent in the left pane.
v Right-click the policy icon in the repository, and then select Deploy from the
pop-up menu.
2. To deploy additional policies, click the Policies icon, and then click Add to
select more policies. The Deploy Policy window displays the policy you chose,
and the target(s) it will be deployed to.
3. Click OK.
4. To select a target to deploy the policy to, click the Targets icon, and then select
the Enterprise Scanner groups or agents to deploy this policy to.
5. Click the Schedule icon.
6. To deploy the policy immediately, select Now.
7. To schedule a specific date and time to deploy the policy, select Start Time,
click the list, and then select a date and time for deployment.
8. Click OK.
Chapter 3. Enterprise Scanner policies 31
Page 40

Migrating a locally managed Enterprise Scanner agent into SiteProtector
You must migrate the Enterprise Scanner agent out of the Locally Managed Agents
area to take advantage of the policy features available in SiteProtector.
About this task
If the policies for the Enterprise Scanner agent are managed locally (from Proventia
Manager), they will be displayed in the Locally Managed Agents node.
The Locally Managed Agents node is designed to be a temporary access point for
Enterprise Scanner agents whose local policies have not yet been imported into
SiteProtector. You should move these policies into the policy repository to manage
them in SiteProtector.
Procedure
1. Select the Policy view, and then select Locally Managed Agents.
2. Select the Enterprise Scanner agent, and then select Migrate to Repository from
the pop-up menu.
3. Type a unique policy name for any policy files that duplicate those already in
the repository.
4. Click OK. The policies for the Enterprise Scanner agent are displayed in the
Repository and can be deployed to other Enterprise Scanner groups or agents
in SiteProtector.
32 Enterprise Scanner: User Guide
Page 41

Viewing asset or agent policies for Enterprise Scanner
In the SiteProtector Console, you can view asset and agent policies together, or you
can view them separately. If you view the policies separately, you can use the
views and tabs in SiteProtector to easily move back and forth between asset and
agent policies.
Procedure
1. From the SiteProtector Console, click a tab with the Policy view.
2. From the left pane, select the asset or agent whose policies you want to view.
3. If you want to see policies from a different repository, select that repository.
4. Select Network Enterprise Scanner from the Agent Type list.
5. Select your version of Enterprise Scanner for the agent from the Version list.
Note: The version can apply to the agent whose properties you are defining or
to the agent responsible for scanning the group whose properties you are
defining.
Important: Enterprise Scanner policies can apply to one or more versions, as
indicated in the policy view. If you use multiple agents at different versions
that do not share the same policy, you must define separate policies for each
version.
6. Choose an option:
If you want to view... Then...
All policies Select All from the Mode list.
Asset policies Select Asset from the Mode list.
Agent policies Select Agent from the Mode list.
Chapter 3. Enterprise Scanner policies 33
Page 42

Getting vulnerability help for a SiteProtector Console without Internet access
If you use the SiteProtector Console on a computer without an Internet connection,
you need to store the vulnerability Help on the computer or one it can access over
your company’s network.
Procedure
1. Download the vulnerability Help file (XForceHelpFiles.zip)from
http://www.iss.net/security_center/reference/vuln to a directory on your
computer.
2. When the File Download window opens, click Save to store the files on your
computer.
Important: Do not click Open.
3. After you download the files, specify the full path, including the final
backslash, in the Help HTML Prefix box on the Common Settings panel for
Assessment Scans.
Example: c:\data\XF-help-files\
34 Enterprise Scanner: User Guide
Page 43

Agent policies for Enterprise Scanner
Agent policies apply to Enterprise Scanner appliances and describe operational
settings for the agents or global settings for all scans. In addition, some agent
policies apply to only one agent.
Agent policy descriptions for Enterprise Scanner
Agent policies apply to both ad hoc and background scans.
Contents of an agent policy
The general contents of an agent policy include:
v The passwords to use for local accounts
v Scan management (breaking scans down into smaller subtasks per task)
v The relative location of the agent on the network, known as its perspective
v Updates to the agent
v Network configuration settings and DNS servers for the network interfaces
v Log file management
Policy inheritance with agent policies
The following rules describe policy inheritance for agent policies:
v You must define a unique Access, Networking, Services, and Time policy for
each agent.
v You can set up the Notification and Update policies to inherit their definitions
from policies defined higher in the group structure.
v You can define only one Network Locations policy, to be used for all agents and
assets, at the Site level in your group structure.
In the SiteProtector Console, you select a group in the left pane and the applicable
policies are displayed in the right pane. If you expand the group or agent, the
policies are also displayed below the group or agent.
Chapter 3. Enterprise Scanner policies 35
Page 44

Network Locations policy
Use the Network Locations policy to define the perspective (network location) of
an agent and to define routes for those perspectives.
Note: The Network Locations policy does not automatically import the
perspectives you set up in the Network Locations tab in the Proventia Manager
(LMI). If you have defined perspectives in the Proventia Manager, you must
redefine those perspectives for this policy in SiteProtector.
What is perspective?
A perspective is a name that represents the network location of one or more
agents. You associate a perspective with a group to scan in the Scan Control policy.
The agent(s) assigned to that perspective in the Networking policy run the scans.
Default perspective
The Network Locations policy contains a default perspective, Global, which you
cannot delete. You can use the Global perspective without adding any additional
perspectives, or you can use it along with user-defined perspectives.
When to use additional perspectives
Perspective is most important when you have multiple scanners located at
different locations on your network. To distinguish among them, you must use
more than one perspective.
You can only assign one unique perspective per scanning port. You cannot assign
the same perspective to more than one scanning port.
Perspective names
When you choose a perspective name, choose a name that represents the location
on the network that the perspective references. Consider that, technically, a
perspective represents a set of subnets from which you would expect the same
results for scanning and monitoring your network regardless of where you
connected your scanners within that set of subnets.
Scanning without full permissions
To perform any Enterprise Scanner scan with SiteProtector SP™6.1 or later, a user
must have permission to view the Network Locations policy. This permission is
granted for the predefined user groups that provide full Enterprise Scanner
permissions. If you define users or user groups with restricted permissions, you
must grant this permission explicitly. The way you grant permission is based on
the inheritance behavior of your policy:
If you... Then...
Do not change the inheritance behavior of
the policy
Change the inheritance behavior of the
policy
You can define the permission once at the
Site level.
You must grant the permission for the group
where you need the permission and for all
the groups above it in the hierarchy.
36 Enterprise Scanner: User Guide
Page 45

Important: Users who do not have permission to view the Network Locations
policy, either through group association or by a specific grant, cannot run
Enterprise Scanner scans.
Assigning perspective to a scanning interface
Use the Network Locations tab in the Network Locations policy on the
SiteProtector Console to assign a perspective (network location) to a scanning
interface.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
2. In the navigation pane, select a group, and then open the Network Locations
policy for that group.
3. Click the Network Locations tab.
4. Click the Add icon.
5. Type a name for the perspective in the Network Locations Name field, and
then click OK.
Important: You can only assign one unique perspective per scanning port. You
cannot assign the same perspective to more than one scanning port.
Configuring routes for perspective
Use the Routes tab in the Network Locations policy on the SiteProtector Console to
configure the appliance to select paths for (routes) traffic.
About this task
In a multi-segmented network, you might experience unnecessary network traffic if
your agent traffic is routed through your default gateway. You can reduce network
traffic if you configure routes for perspectives that provide more direct routes to
targeted segments.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
2. In the navigation pane, select a group, and then open the Network Locations
policy for that group.
3. Click the Routes tab, and then click the Add new item to list icon.
4. Complete the following fields:
Option Description
Perspective The perspective for which you are defining a
route.
Destination Network A network segment for which you want to
define a specific route for a perspective.
Gateway The IP address of the router the agent
should use to find IP addresses in the
Destination Network. Use the IP address
that is on the same network as the agent,
not the IP address of the route from inside
the target segment.
Chapter 3. Enterprise Scanner policies 37
Page 46

Option Description
Metric If you configure more than one route to the
5. Click OK.
Notification policy
Use the Notification policy to configure responses sent from the Enterprise Scanner
appliance to the SiteProtector Console.
Event notification settings for Enterprise Scanner
Use the Event Notification tab in the Notification policy on the SiteProtector
Console to Enterprise Scanner enable the agent to send system events to the
SiteProtector Console.
About this task
You can configure three types of system events:
v System error events
v System warning events
v System informative events
same segment for one perspective, a number
that indicates the preferred route. The closer
to 1, the more preferred the route.
Note: The numbers you use do not have to
be consecutive.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
2. In the navigation pane, select a group, and then open the Notification policy
for that group.
3. Click the Event Notification tab.
4. Select the check boxes for each type of event to enable:
v Alert Logging for System Error Events
v Alert Logging for System Warning Events
v Alert Logging for System Informative Events
5. Select the Enable Event Delivery to SiteProtector Console check box for each
type of event to enable:
v System error notification
v System warning notification
v System informative event notification
38 Enterprise Scanner: User Guide
Page 47

Configuring advanced parameters for event notification
Use the Advanced Parameters tab in the Notification policy on the SiteProtector
Console to provide greater control over the event notification behavior of your
appliance.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
2. In the navigation pane, select a group, and then open the Notification policy
for that group.
3. Click the Advanced Parameters tab.
4. If the parameter you want to tune is not displayed in the Advanced Parameters
tab, follow these steps:
a. Click the Add icon.
b. Type the name of the parameter.
c. Type a description of the parameter.
d. Specify the value type and value of the parameter.
5. If the parameter you want to tune is already displayed in the Advanced
Parameters tab, click the value or description field and change the setting.
Attention: In most cases, it should not be necessary to change advanced
parameters. However, you should not change these parameters unless you are
instructed by IBM ISS Technical Support personnel.
6. Click OK.
Access policy
Use the Access policy on the SiteProtector Console to change agent passwords and
to enable (require) or disable the bootloader password for backing up or restoring
your agents.
Before you begin
To change a password, you must know the current password.
About this task
When you configure the appliance, you must supply passwords for these accounts:
Table 5. Appliance passwords
Account Purpose
root This password accesses the operating system
Admin (agent user) This password accesses the Proventia Setup
Admin (Web user) This password accesses Proventia Manager
of the appliance.
Assistant on the appliance if the Enterprise
Scanner agent is not managed by a
SiteProtector.
through a Web browser over a network
connection.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
Chapter 3. Enterprise Scanner policies 39
Page 48

2. In the navigation pane, select a group, and then open the Access policy for that
group.
3. For each password you want to change, complete the following steps:
a. Type the current password in the Current Password box.
b. Click Enter Password, type the new password in the Password and in the
Confirm password boxes, and then click OK.
4. If you want to require the use of the bootloader password to back up or restore
the agent, select the Enable bootloader password check box.
Important: If you enable the bootloader password, you must be connected to
the Enterprise Scanner agent with a serial connection and supply a password to
backup or to restore the agent.
Networking policy
Use the Networking policy on the SiteProtector Console to reconfigure the network
configuration settings for the management and scan interfaces and for the DNS
servers and search paths.
Configuring the management network interface
Use the Management Interface tab in the Networking policy on the SiteProtector
Console to configure the management interface network settings (ETH0).
About this task
You configured the management interface when you set up the appliance with the
Proventia Setup Assistant. Use the procedures in this topic to change those
settings.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
2. In the navigation pane, select a group, and then open the Networking policy
for that group.
3. Click the Management Interface tab, and then type or change the following
information:
Option Description
Host Name The fully qualified domain name for the
Enterprise Scanner agent. Use the format:
gateway1.example.com
Interface The management port used by the
Enterprise Scanner agent.
IP address The IP address for the management network
interface that connects to SiteProtector.
Subnet Mask The subnet mask for the management
network interface that connects to
SiteProtector.
Gateway The address of the network gateway.
4. Select the Use Persistent IP if sensor is behind NAT if you want to avoid
conflicts with NAT rules, and then provide the IP address.
40 Enterprise Scanner: User Guide
Page 49

Configuring the scanning network interface
Use the Scan Interface tab in the Networking policy on the SiteProtector Console to
configure the scanning interface network settings (ETH1 - ETH5).
About this task
You configured the scanning interface when you set up the appliance with the
Proventia Setup Assistant. Use the procedures in this topic to change those
settings.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
2. In the navigation pane, select a group, and then open the Networking policy
for that group.
3. Click the Scan Interface tab, and then type or change the following
information:
Option Description
Interface The Ethernet port of the interfaces for the
Enterprise Scanner agent.
IP Address The IP address of the scanning network
interface for the Enterprise Scanner agent.
Subnet Mask The IP address for the scanning network
interface subnet mask of the Enterprise
Scanner agent.
Gateway The address of the network gateway.
Maximum IPs per discovery subtask The maximum number of IP addresses to
discover in a subtask (of a task for each scan
job).
Note: This value applies to all discovery
scans that the agent runs.
Maximum assets per assessment subtask The maximum number of assets to scan in a
subtask (of a task for each scan job).
Note: This value applies to all assessment
scans that the agent runs.
Perspective (network location) The name of the network location to
associate with this scanning port.
Values: Global, the default, and any network
locations defined in the Network Locations
policy.
Chapter 3. Enterprise Scanner policies 41
Page 50

Configuring scanning interface DNS settings
Use the DNS tab in the Networking policy on the SiteProtector Console to
configure the DNS settings for the scanning interface.
About this task
You configured these settings when you set up the appliance with the Proventia
Setup Assistant. Use the procedures in this topic to change those settings.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
2. In the navigation pane, select a group, and then open the Networking policy
for that group.
3. Click the DNS tab.
4. Choose an option:
If you want to... Then...
Specify DNS settings
Add a DNS search path
Edit a DNS search path
Copy and paste a DNS search path
Remove a DNS search path
Change the order of a DNS search path
1. Type the IP addresses for the primary,
secondary, and tertiary DNS servers.
2. Click Save Changes.
1. In the DNS Search Path section, click the
Add icon.
2. Type the domain name to add to the
search list, and then click OK.
3. Click Save Changes.
1. In the DNS Search Path list, select a
domain name, and then click the Edit
icon.
2. Edit the domain name, and then click
OK.
3. Click Save Changes.
1. In the DNS Search Path section, select a
domain name, and then click the Copy
icon. The agent copies the search path to
the clipboard.
2. Click the Paste icon. The agent copies the
search path to the end of the list.
3. If necessary, edit the policy, and then
click OK.
4. Click Save Changes.
1. In the DNS Search Path section, select a
domain name, and then click the
Remove icon.
2. Click Save Changes.
1. In the DNS Search Path section, select a
domain name.
2. Click the Up or Down arrows.
Tip: It is more efficient to place the most
likely used search path at the top of the
list.
3. Click Save Changes.
42 Enterprise Scanner: User Guide
Page 51

Services policy
Use the Services policy on the SiteProtector Console to enable or disable access to
your appliance from SSH (Secure Shell) applications on your network and to
enable SNMP to monitor the Enterprise Scanner appliance for conditions that
warrant administrative attention.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
2. In the navigation pane, select a group, and then open the Services policy for
that group.
3. Choose an option:
If you want to... Then...
Enable SSH Select the Enabled check box to enable SSH;
Enable an SNMP Get
Enable an SNMP Trap
clear the Enabled check box to disable SSH.
Note: SSH is enabled and accessible to the
internal and external interfaces by default.
1. Select the SNMP Get Enabled box.
2. Provide a name for the system, a system
location, relevant contact information,
and an appropriate community name.
1. Select the SNMP Traps Enabled box.
2. Type the IP address in the Trap Receiver
Address field.
Note: This IP address is the server
address where the SNMP Manager is
running. The SNMP host must be
accessible to the appliance to send e-mail
notification.
3. Type the appropriate community name
(public or private) in the Trap
Community field.
4. Select a trap version from the Trap
Version list. The following versions are
available:
v V1: Simple Network Management
Protocol version 1
v V2c: Community-Based Simple
Network Management Protocol
version 2
4. Click Save Changes.
Chapter 3. Enterprise Scanner policies 43
Page 52

Time policy
Use the Time policy on the SiteProtector Console to change the date and the time
of the Enterprise Scanner agent, and to enable the network time protocol (NTP) to
synchronize the agent time with a network time server.
About this task
The Time policy always contains the last manually configured values for date and
time options, not the actual date and time. When you save the settings, the agent is
set to the currently configured values, whether you have changed them or not.
Important: To avoid resetting the time and date to the previously configured
values, update the time and date before you save the settings.
Procedure
1. From the SiteProtector Console, create a tab to display agent policies.
2. In the navigation pane, select a group, and then open the Time policy for that
group.
3. Choose an option:
If you want to... Then...
Change the date and time for the agent
Enable the network time protocol (NTP) Note: NTP synchronizes the configuration
1. Click the Date and Time arrow to see
the calendar.
2. Select the correct month and date.
Tip: Use the arrows at the top to change
the month and year in the calendar.
3. Select the hour and minutes in the Time
boxes.
4. Click outside the calendar to close it.
5. Click the Time Zone arrow and select
the correct time zone for your region.
6. Click Save Changes.
time with a network time server.
1. In the Network Time Protocol section,
select the Enable NTP check box.
2. Type the name of the server in the
Server box.
3. Save the Time policy.
4. Change the tab to an Agent view.
5. Right-click the agent or the group of
agents affected by the policy change, and
then select Refresh Agent from the
pop-up menu.
Important: To ensure that the agent
starts to use NTP time immediately, you
must refresh the agent. If you do not
refresh the agent, NTP time does not
take effect until the agent sends a
heartbeat to SiteProtector. If you cannot
save this policy and refresh the agent
immediately, set the time as described in
the Changing the date and time
procedure before you save the policy.
44 Enterprise Scanner: User Guide
Page 53

Update Settings policy
Use the Update Settings policy on the SiteProtector Console to configure how the
agent automatically locates, downloads, and installs available updates.
Asset policies for Enterprise Scanner
Asset policies apply to groups of assets and describe the security policy for those
assets.
Asset policy descriptions for Enterprise Scanner
Asset policies apply to both discovery scans and assessment scans depending on
the policy.
Scope of scanning
The following table identifies which asset policies apply to discovery scans, which
apply to assessment scans, and which apply to both:
Table 6. Asset policies
Policy Discovery Assessment
Assessment No Yes
Assessment Credentials Yes Yes
Discovery Yes No
Network Locations Yes Yes
Network Services No Yes
Scan Control Yes Yes
Scan Exclusion No Yes
Scan Window Yes Yes
Contents of an asset policy
The general contents of an asset policy include:
v Information about how to run discovery scans, assessment scans, or both types
of scans against the group
v The IP addresses to scan for discovery scans
v The checks to run, and other assessment parameters (for assessment scans
v The days to run scans and during which hours to run them
v Refreshed information from scans about the assets in a group
v The assets in the group, if any, that you do not want to scan
v The list of accounts and log on credentials to use for assets in a group
v The service names associated with TCP and UDP ports
Policy inheritance with asset policies
The following rules describe policy inheritance for agent policies:
v You can define only one Network Locations policy, to be used for all agents and
assets, at the Site level in your group structure.
Chapter 3. Enterprise Scanner policies 45
Page 54

v A Discovery policy applies to only the group where you define it.
v The remaining policies are inheritable. A subgroup inherits a policy from the
first group higher than itself in the group structure that has a defined policy.
In the SiteProtector Console, you select a group in the left pane and the applicable
policies are displayed in the right pane in a Policy tab.
Discovery policy
Use the Discovery policy on the SiteProtector Console to define parameters used to
perform discovery on a portion of a network.
In a discovery task, a range of IP addresses is scanned to locate active network
interfaces, and the type of device associated with each active network interface is
determined through OS identification.
Scope
The Discovery policy applies to background discovery scans. An ad hoc scan reads
this policy and uses its settings to initialize the ad hoc discovery scan. You can
change the settings in the ad hoc scan without changing the background policy.
Policy contents
Each Discovery policy defines the following information:
v A range of IP addresses to be scanned (specified as a combination of
dotted-decimal IP addresses and address ranges, and subnetworks specified in
CIDR notation).
v Whether to ping each IP address before scanning to exclude unreachable hosts
from the scan.
v Whether newly discovered assets should be added to the associated group.
v Whether previously known assets that do not already belong to the associated
group should be added to the group.
46 Enterprise Scanner: User Guide
Page 55

Defining assets to discover
Use the Discovery policy on the SiteProtector Console to define the parameters
used to perform a discovery scan on a portion of a network.
Before you begin
Before it can perform OS fingerprinting on an asset, your agent must find one
open and one closed port. To find an open and a closed port, the agent scans ports
1–1023 and any other ports specified in the applicable Network Services policy.
About this task
In a discovery task, a range of IP addresses is scanned to locate active network
interfaces, and the type of device associated with each active network interface is
determined through OS identification.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Discovery policy for
that group.
3. Type the IP addresses (in dotted-decimal or CIDR notation) of the assets to
discover in the IP range(s) to scan box as in the following examples:
v Type an IP address, and then press ENTER.
v Type a range of IP addresses, and then press ENTER.
Example: 172.1.1.100-172.1.1.200
v Type a combination of both choices above, and then press ENTER.
Note: A red box appears around the IP range(s) to scan box until the data is
validated.
4. If you want to ping each IP address before scanning to exclude unreachable
hosts from the scan, select the Ping hosts in this range, before scanning, to
exclude unreachable hosts check box.
5. If you want to add newly discovered assets to the group where you have
defined the scan, rather than to the Ungrouped Assets group, select the Add
newly discovered assets to group check box.
6. If you want to add previously known assets that are already defined in other
groups to the scan group, select the Add previously known assets to group
check box.
Chapter 3. Enterprise Scanner policies 47
Page 56

Assessment policy
Use the Assessment policy on the SiteProtector Console to define the checks to run
for assessment scans.
The Assessment policy contains the following tabs:
v Checks (display checks by groups, display information about checks, select
checks with filters)
v Common Settings
Scope
The Assessment policy applies only to assessment scans that run in the
background. Ad hoc scans read this policy and use its settings to initialize the ad
hoc Assessment policy. You can change the ad hoc version of the policy without
changing the saved background version.
Displaying information about assessment checks
Use the Checks tab in the Assessment policy on the SiteProtector Console to choose
how much information to display about each assessment check in the Assessment
policy.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Assessment policy for
that group.
3. Choose an option:
If you want to... Then...
Add a single column Right-click a column and then select the
column to add from the pop-up menu.
Note: The column appears at the far right.
Remove a single column Right-click a column and then select the
column to remove.
Note: The column is removed.
Add multiple columns Click Column to display icon, and then
select the check box for each column to add.
Remove multiple columns Click Column to display icon, and then
clear the check box for each column to
remove.
48 Enterprise Scanner: User Guide
Page 57

Displaying assessment checks by groups
Use the Checks tab in the Assessment policy on the SiteProtector Console to group
checks by any combination of columns that you have chosen to display. For
example, you might want to see checks by category, then by severity within that
category.
About this task
The current grouping selections are displayed just above the column headers of the
checks.
v Assessment checks
v If no groups are selected, the following message is displayed on the screen:
Right click on the column header to group by that column.
v If groups are selected, the group names are displayed on in the screen as in the
following example:
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Assessment policy for
that group.
3. Click the Checks tab.
4. Choose an option:
If you want to... Then...
Clear groupings Choose an option:
v Right-click any column header, and then
select Clear Groupings from the pop-up
menu.
v Click Clear Groupings.
Create groupings interactively
Create groupings from a selection list
1. Right-click a column heading, and then
select Group By from the pop-up menu.
2. Repeat the previous step until you have
created the groupings that you want.
1. Click the Group By icon.
The Group by Columns window
appears.
2. Select a column to group by in the All
Columns list, and then click Add.
The column moves to the Group by these
Columns list.
3. Repeat the previous step for each column
that you want to group by.
4. If you want to remove items from the
list, select an item in the Group by these
Columns list, and then click Remove.
The item and any items below it move to
the All Columns list.
5. Click OK.
Chapter 3. Enterprise Scanner policies 49
Page 58

Selecting assessment checks with filters
Use the Checks tab in the Assessment policy on the SiteProtector Console to
provide filtering values on a selected list of assessment checks.
About this task
The following rules apply to using regular expressions:
v The match occurs against all columns in the table, whether or not the column is
displayed.
v If you use more than one regular expression, every regular expression must
match for a check to be selected.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Assessment policy for
that group.
3. Click the Checks tab.
4. Select the Filter check box, and then click Filter.
5. To filter with a regular expression, type one or more regular expressions on
separate lines in the Regular Expression box.
Tip: For example, use http.* to match the value in any column that starts with
http; or use .*http.* to match the value in any column that contains http.
6. To filter by one or more of the remaining filter types, select the values to filter
by in the filtering boxes.
Tip: You can select ranges of filtering values by holding down the SHIFT key
and random filtering values by holding down the CTRL key.
7. Click OK.
50 Enterprise Scanner: User Guide
Page 59

Configuring common assessment settings
Use the Common Settings tab in the Assessment policy on the SiteProtector
Console to choose settings that define additional scanning behavior for the checks
you have selected to run in an assessment scan.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Assessment policy
for that group.
3. Click the Common Settings tab.
4. Type the URL or file location for the assessment check Help documentation in
the Help HTML Prefix box:
v The IBM ISS Web site location of the latest assessment check
documentation.
v The file location of a locally stored version of the documentation.
Note: If you do not have access to the Internet, but you want to view Help
for checks in the Assessment policy, you must copy the files to your hard
drive. See Getting vulnerability help for a SiteProtector Console without
Internet access for details.
5. If you want to run the checks that are enabled by default, including checks
added in an X-Press Update (XPU), select a policy in the Compliance Policies
section.
6. Configure options for service discovery in the Service Discovery section:
Option Description
Discover and report TCP services Reports active TCP services for which the
Service Scan flag is enabled in the Network
Services policy.
Discover and report UDP services Reports active UDP services for which the
Service Scan flag is enabled in the Network
Services policy.
7. Configure options for assessment port ranges in the Assessment Port Ranges
section:
Option Description
Ports to scan with generic TCP checks The set of TCP ports to scan with generic
TCP checks. You can specify ports using any
of the following methods:
v Type a port or range of ports.
v Click Well known and select ports from
the list.
v Select All.
Note: A generic TCP check is one whose
target type is tcp.
Chapter 3. Enterprise Scanner policies 51
Page 60

Option Description
Ports to scan with generic UDP checks The set of UDP ports to scan with generic
UDP checks. You can specify ports using any
of the following methods:
v Type a port or range of ports.
v Click Well known and select ports from
the list.
v Select All.
Note: A generic UDP check is one whose
target type is udp.
8. Configure options for using OS information in the Use of OS Information
section:
Option Description
Dynamically determine OS if SiteProtector
information is older than
For unverified OS’s: Specify which checks to run if the OS is
The maximum age (in minutes) of usable OS
information in SiteProtector.
If the OS information for an asset is older
than the time specified, Enterprise Scanner
reassesses OSID when it runs an assessment
scan.
Default: 120
uncertain.
v Run all checks (lowest performance): If
Enterprise Scanner is uncertain about the
OS of the asset, it runs all assessment
checks.
v Run all checks that apply to general OS
(intermediate performance): If Enterprise
Scanner is uncertain about the OS of the
asset, it runs checks for all versions of an
operating system. (For example, if
Enterprise Scanner is uncertain about
which version a Windows operating
system is, it runs all the checks for all
versions of Win dows operating systems.)
v Run only checks that apply to specific
OS (Best performance): If Enterprise
Scanner is uncertain about the OS of the
asset, runs only the checks that apply to
the exact version of the operating system.
9. Configure options for application fingerprinting in the Use of Application
Fingerprinting section:
52 Enterprise Scanner: User Guide
Page 61

Option Description
Do not perform application fingerprinting Does not try to specifically identify which
applications are communicating over which
ports, and runs the checks as selected in the
Assessment policy.
This option does not identify applications
communicating over non-standard ports.
(Checks are run against standard ports as
defined in the Network Services policy.)
Fingerprint applications and run checks
that apply to application protocol (e.g.,
http)
Fingerprint applications and run checks
that apply to specific application (e.g.,
apache)
Identifies applications communicating over
specific ports, and then runs checks that
apply to the protocol in use.
This option identifies applications
communicating over non-standard ports.
Identifies applications communicating over
specific ports, and then runs checks that
apply only to the application identified.
This option identifies applications
communicating over non-standard ports.
10. The settings in the Account Verification section apply only if an Assessment
Credentials policy is available for the group being scanned.
Option Description
Verify account access level before using
Access domain controllers to verify access
level
Check local group membership to verify
access level
v If disabled, Enterprise Scanner assumes
that whatever is specified in the
Assessment Credentials policy is accurate.
v If enabled, Enterprise Scanner tries to
confirm that the access level specified in
the Assessment Credentials policy is
correct.
Important: You should enable the Check
local group membership to verify access
level if you enable account verification.
v If disabled, Enterprise Scanner does not
communicate with a Domain Controller in
the process of verifying access levels.
v If enabled, Enterprise Scanner tries to
communicate with a Domain Controller in
the process of verifying access levels.
v If disabled, Enterprise Scanner does not
try to confirm the access level of the
account during assessment by checking
which local groups the asset belong to.
v If enabled, Enterprise Scanner tries to
confirm the access level of the account
during assessment by checking which
local groups the asset belong to.
11. Configure the options for locking out accounts in the Account Lockout
Control section:
Chapter 3. Enterprise Scanner policies 53
Page 62

Option Description
Allowed account lockout Select a type of lockout:
v No lockout allowed: Enterprise Scanner
avoids running password guessing checks
if account lockout is enabled on the target
host, or if its status cannot be determined.
v Temporary lockout allowed: Enterprise
Scanner runs password guessing checks
only if the account lockout duration is less
than or equal to the value specified in the
Maximum Allowable Lockout Duration
option later in this section.
v Permanent lockout allowed:Enterprise
Scanner runs password guessing checks
even if the account lockout duration is set
to run infinitely.
Longest allowed temporary lockout Specifies the maximum time (in minutes)
that accounts are allowed to be locked out
by password guessing checks.
This value applies only if Temporary
Lockout Allowed is enabled. When
temporary lockout is allowed, password
guessing checks are run only against assets
whose lockout policy disables locked out
accounts for no more than the maximum
allowed lockout time.
54 Enterprise Scanner: User Guide
Page 63

Assessment Credentials policy
Use the Assessment Credentials policy on the SiteProtector Console to define
authentication credentials for your assets.
The appliance uses authentication credentials to access accounts during assessment
scans. Enterprise Scanner uses all instances of the credentials that are defined for
the group when it scans assets in the group. You can define different instances of
this policy for different groups, which makes it possible to supply different log on
credentials to scan different parts of the network.
Important: The Assessment Credentials policy currently works only with assets
that run Windows operating systems.
Scope
The Assessment Credentials policy applies to all types of scans.
Defining assessment credentials for a policy
Use the Assessment Credentials policy on the SiteProtector Console to define
authentication credentials for your assets.
About this task
The appliance uses authentication credentials to access accounts during assessment
scans. Enterprise Scanner uses all instances of the credentials that are defined for
the group when it scans assets in the group. You can define different instances of
this policy for different groups, which makes it possible to supply different log on
credentials to scan different parts of the network.
Important: The Assessment Credentials policy currently works only with assets
that run Windows operating systems.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Assessment
Credentials policy for that group.
3. In the Assessment Credentials policy, click Add, and then provide the
following account information:
Option Description
Username The user identification for an account.
Password The password to use with the user name to
log into an account.
Account Type: Windows Local Indicates that the user account is defined
locally on a single Windows device. The
account is used to attempt to log in to a
single Windows device.
When you choose this option, you must
provide a Windows host name in the
Domain/Host box.
Chapter 3. Enterprise Scanner policies 55
Page 64

Option Description
Account Type: Windows
Domain/Workgroup
Account Type: Windows Active Directory Indicates that the user account is defined in
Account Type: SSH Local
Account Type: SSH Domain
Indicates that the user account is defined in
a Windows Domain or Workgroup. The
account is used to attempt to log in to all
Windows devices within the domain or
workgroup.
When you choose this option, you must
provide the Windows Domain or Workgroup
name in the Domain/Host box.
a Windows Active Directory Domain. The
account is used to attempt to log in to all
Windows devices within the Active
Directory domain.
When you choose this option, you must
provide the Active Directory Domain name
in the Domain/Host box.
Indicates that the user account is defined
locally on a single Unix device that allows
SSH logons. The account is used to attempt
login to a single Unix device.
When you choose this option, you must
provide an IP address in the Domain/Host
box.
Indicates that the user account is defined for
Unix devices that allow SSH logons. In this
context, ″Domain″ loosely refers to a set of
devices, rather than to a specific type of
domain. The account is used to attempt to
log in to all SSH devices covered by the
policy.
Domain/Host Applies to one of the following domains or
Account Level Applies to one of the following accounts:
Important: To avoid locking an account, do not add the account more than
once.
56 Enterprise Scanner: User Guide
When you choose this option, you should
supply a descriptive name in the
Domain/Host box. This is for
documentation purposes only; it is not used
by Enterprise Scanner.
hosts:
v For Windows accounts, the domain or
host name to which the account applies.
v For SSH Local accounts, the IP address of
the device to which the account applies.
v For SSH Domain accounts, any text.
v Administrator
v User
v Guest
Page 65

Scan Control policy
Use the Scan Control policy on the SiteProtector Console to define the duration of
scanning cycles and to assign user-defined perspectives to scans.
Background scanning is based on scanning cycles. Scanning cycles define how
frequently you want to rerun scans for a group.
Note: Background scans run during open scan windows that you define in the
Scan Window policy.
Important: This policy initiates background scanning, so you should configure it
after you have configured the other policies required for background scanning.
Scope
The Scan Control policy applies to background discovery and background
assessment scans. This policy does not affect ad hoc scans. Consequently, the
behavior for ad hoc scans is different:
v An ad hoc discovery scan runs only on the group where you define the scan.
v An ad hoc assessment scan applies to the group where you define the scan and
to all the subgroups. This is different from background scans in that background
scanning behavior is determined by which Scan Control policy applies to each
subgroup.
What is perspective?
When you scan a group of assets, you anticipate and interpret results based on the
location of your scanner relative to the location of the assets. Scanning a group of
assets from inside a firewall, for example, would produce different results from
scanning that same group of assets from outside the firewall. With Enterprise
Scanner, you use perspective to identify scanners by their location on the network,
such as inside or outside the firewall, and then you configure scans based on the
perspective from which you want to scan your assets. You define perspectives in
the Network Locations policy.
Chapter 3. Enterprise Scanner policies 57
Page 66

Defining scanning cycles and assigning perspectives to scans
Use the Scan Control policy on the SiteProtector Console to define the duration of
scanning cycles and to assign user-defined perspectives to scans.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Scan Control policy
for that group.
3. Select the Enable background discovery/assessment scanning of this group
check box, for the type(s) of background scanning you want to define, in the
Background Discovery and Background Assessment sections.
4. Configure background scanning for each type of scan:
Option Description
Job name The name you want displayed for the
scanning job in the Command Jobs window.
Note: This name identifies the scan when it
runs, so choose a meaningful name.
Cycle start date The date on which you want the scan cycle
to start.
Note: Future scans are created in
SiteProtector at midnight at the beginning of
the next refresh cycle.
Cycle duration The length (up to three digits) of the cycle as
in one of the following units:
v Hours (for Enterprise Scanner version 2.1
agents or later only)
v Days
v Weeks
v Months
Current cycle start date The beginning date of the current scan cycle.
(Display only.)
Next cycle start date The beginning date of the next scan cycle.
(Display only.)
Use Discovery’s start date/duration and
wait for discovery scan to complete before
scheduling assessment scan
Delays the start of the assessment scan until
the discovery scan has finished to ensure
that the discovery scan has identified all
discoverable assets before the assessment
scan begins.
Note: This check box applies to assessments
scans only.
5. If you want to scan from a user-defined perspective, select a perspective from
the Perform background scans from this perspective (Network location) box.
Tip: If you have not yet defined the perspective, click the Configure the
referenced list icon to open the Network Locations policy and define a new
perspective.
58 Enterprise Scanner: User Guide
Page 67

Scan Window policy
Use the Scan Window policy on the SiteProtector Console to define hours of
allowed scanning for discovery scans (scan windows), assessment scans (scan
windows), and the time zone in which you want the scanning to occur, which is
typically the time zone of the assets.
By default, scanning is allowed at any time. If you want to limit scanning, be sure
to define scan windows.
Scope
The Scan Window policy applies to background discovery and assessment scans.
For an ad hoc scan, you can choose whether to run the scan only during the
windows defined in this policy or to run the scan without restriction.
By default, all scan windows are open, so that scanning is allowed at any time.
When you open a Scan Window policy, however, the default changes; and all scan
windows are closed. If you modify a Scan Window policy, be sure to define scan
windows for discovery and for assessment scans.
Important: If you start a scan when there are no scan windows, the job appears in
the Command Jobs window in the idle state; but it will not run until you define
scan windows.
Important consideration for multiple agents
If you have multiple agents, you should stagger your scan windows so that the
discovery scan can finish before the assessment scan begins. If a discovery scan
adds assets to a group while an assessment scan is running, there is no guarantee
that those assets will be included in the assessment scan.
Chapter 3. Enterprise Scanner policies 59
Page 68

Defining when scanning is allowed
Use the Scan Window policy on the SiteProtector Console to define the days and
hours that scanning is allowed.
About this task
The Scan Window policy applies to background discovery and assessment scans.
For an ad hoc scan, you can choose whether to run the scan only during the
windows defined in this policy or to run the scan without restriction.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Scan Window policy
for that group.
3. Click the Discovery Windows tab or the Assessment Windows tab.
Note: Scanning hours are selected; non-scanning hours are not selected.
4. Select the periods of allowed scanning using the following methods:
If you want to... Then...
Allow scanning during specific hours Click and drag your cursor over the hours
in each day to allow scanning.
Allow scanning at any time Click Fill All.
Remove all defined scans periods Click Clear All.
Important: To enable background scanning, you must define at least one scan
window.
5. Click the Time Zone tab.
6. Select the time zone during which you want the scan windows to run from the
Time zone for scan windows list.
Note: Typically, you would choose the same time zone as the time zone of the
assets in the group. For example, you might be in the Eastern time zone but
scanning assets in the Pacific time zone. You would define your scanning hours
according to the considerations of the Pacific time zone and set your appliance
to the Pacific time zone.
60 Enterprise Scanner: User Guide
Page 69

Scan Exclusion policy
Use the Scan Exclusion policy on the SiteProtector Console to define specific ports
or assets to exclude from a scan of a group of assets.
Each Scan Exclusion policy defines the following information for the asset group
associated with the policy (and the groups that inherit from it):
v A list of ports against which no assessment checks will be run. (No checks run
against these ports on any host in the group. This applies to both TCP and UDP
ports.)
v A list of IP addresses not to scan.
Important: You should define the Scan Exclusion policy at a high level in your
group structure and allow the lower groups to inherit from it. If needed, you can
then override the policy at lower groups.
Scope
The Scan Exclusion policy applies to ad hoc and background assessment scans. It
does not apply to discovery scans.
Defining ports or assets to exclude from a scan
Use the Scan Exclusion policy on the SiteProtector Console to define specific ports
or assets to exclude from a scan of a group of assets.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Scan Exclusion policy
for that group.
3. Choose an option:
If you want to... Then...
Exclude ports Use a combination of typing the ports to
exclude and choosing the ports:
v Type the ports to exclude, separated by
commas, in the Excluded Ports box.
v Click Well Known Ports, and then select
the ports to exclude.
Exclude assets Type the IP addresses (in dotted-decimal or
CIDR notation) of the hosts to exclude in the
Excluded Hosts box:
v Type an IP address, and then press ENTER.
v Type a range of IP addresses, and then
press ENTER.
Example: 172.1.1.100-172.1.1.200
v Type a combination of both choices above,
and then press ENTER.
Note: A red box is displayed around the
Excluded Hosts box until the data is
validated.
Chapter 3. Enterprise Scanner policies 61
Page 70

Network Services policy
Use the Network Services policy on the SiteProtector Console to define service
names associated with TCP and UDP ports.
You can modify some properties of a default service in the policy, and you can add
your own customized services to the policy.
Scope
The Network Services policy applies to assessment scans that run as either
background or ad hoc scans.
Default settings
The IBM ISS X-Force defines the default Network Services policy and might
update the policy in an X-Press Update (XPU). The default policy applies to all
groups that do not override it. The service names defined in the policy are
referenced as target types in Enterprise Scanner check definitions. X-Force adds a
service name when a new check uses a service that was not previously defined in
the policy.
Policy inheritance
A Network Services policy defined in association with a group overrides the
default definitions only for those services explicitly referenced in the user-defined
policy. A user-defined Network Services policy includes only explicit overrides of
inherited service definitions, which ensures that all groups automatically inherit
XPU updates to the default Network Services policy.
Service definition
The network services policy includes the following information about each service:
v Service name
v Service description
v Port number
v Protocol (TCP or UDP)
v Whether some (or all) instances of the service operate over SSL on this port
within your network
v Whether to include the port in the service scan
v Whether you have customized a default service or created a custom service
62 Enterprise Scanner: User Guide
Page 71

Configuring a Network Services policy
Use the Network Services policy on the SiteProtector Console to define service
names associated with TCP and UDP ports.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Network Services
policy for that group.
3. For default or customized services, choose an option:
If you want to... Then...
Change the description of a service Slowly click Description two times to switch
to edit mode, and then change the
description.
Allow each service to operate over SSL in
at least some part of your network
Allow service scans for this service over
any TCP and UDP ports specified in the
Assessment policy
Note: You cannot change the Service name, Port, or Protocol of default
services. You cannot delete default services.
4. For customized services, choose an option:
Select the May use SSL check box for that
service.
Select the Service scan check box.
If you want to... Then...
Add a service Click the Add icon.
Modify a service Click the Modify icon.
Delete a service Click the Delete icon.
Chapter 3. Enterprise Scanner policies 63
Page 72

Ad Hoc Scan Control policy
Use the Ad Hoc Scan Control policy on the SiteProtector Console to define
Enterprise Scanner ad hoc scans for assessment and discovery.
Configuration options
For ad hoc scans you configure the following options:
v With the Ad Hoc Scan Control option, you determine whether to run
assessment or discovery scans, whether to run the scans only during available
scan windows, how to lower the impact on the network from scanning, and the
perspective to use.
v With the Assessment option, you select which checks to run for assessment
scans.
v With the Discovery option, you select which IP addresses to scan and how to
handle the hosts that you discover.
Running an ad hoc discovery scan with Enterprise Scanner
When you run an ad hoc discovery scan from the SiteProtector Console, you must
define the ranges of IP addresses to scan, including additional scanning control
parameters.
Procedure
1. In the SiteProtector navigation pane, create a tab with any view except for a
Policy view.
2. Expand the Site to see the group you want to scan.
3. Right-click the group to scan; if given a choice of Internet Scanner or
Enterprise Scanner, select Enterprise Scanner; and then select Scan from the
pop-up menu.
4. In the Ad Hoc Discovery section, select the Perform one-time discovery scan
of this group check box.
5. Type a Job name to identify the job when it appears in the Command Jobs
window.
6. If you want the scan to run only during your scheduled scanning windows,
select the Run only during open discovery windows check box.
7. Click Discovery in the left pane.
8. Type the range, or ranges, of IP addresses to scan in the IP range(s) to scan
box.
9. Type the IP addresses (in dotted-decimal or CIDR notation) of the assets to
exclude in the IP range(s) to scan box as in the following examples:
v Type an IP address, and then press ENTER.
v Type a range of IP addresses, and then press ENTER.
v Type a combination of both choices above, and then press ENTER.
Note: A red box appears around the IP range(s) to scan box until the data is
validated.
10. If you want to ping each IP address before scanning to exclude unreachable
hosts from the scan, select the Ping hosts in this range, before scanning, to
exclude unreachable hosts check box.
64 Enterprise Scanner: User Guide
Example: 172.1.1.100-172.1.1.200
Page 73

11. If you want to add newly discovered assets to the group where you have
defined the scan, rather than to the Ungrouped Assets group, select the Add
newly discovered assets to group check box.
12. If you want to add previously known assets (that are not in the group) to the
group, select the Add previously known assets to group check box.
13. Click OK. The ad hoc discovery scan is displayed in the Command Jobs
window.
Running an ad hoc assessment scan with Enterprise Scanner
When you run an ad hoc assessment scan from the SiteProtector Console, you can
use the default settings, or choose the checks you want to run and other scanning
parameters.
Procedure
1. In the SiteProtector navigation pane, create a tab with any view except for a
Policy view.
2. Expand the Site to see the group you want to scan.
3. Right-click the group to scan; if given a choice of Internet Scanner or
Enterprise Scanner, select Enterprise Scanner; and then select Scan from the
pop-up menu.
4. In the Ad Hoc Discovery section, select the Perform one-time discovery scan
of this group check box.
5. Type a Job name to identify the job when it appears in the Command Jobs
window.
6. If you want the scan to run only during your scheduled scanning windows,
select the Run only during open discovery windows check box.
7. Click Assessment in the left pane.
8. Configure the policy the same way you would configure the background
Assessment policy.
9. Select Global in the Perform scans from this perspective (Network location)
list.
10. Click the Advanced Settings tab.
11. In the Assessment Throttling section, use the Bandwidth Throttling slider to
set the amount of bandwidth the scan should consume.
The Enterprise Scanner agent will monitor threads once the value becomes
greater than you specified.
To enable logging, add the following advanced parameter to the logging
parameters in SiteProtector: esm.portN.debug.logging where N is the port
number of the scan interface
The agent writes the log information to iss-esm-<port number of scan
interface>.log.
12. Use the remaining sliders to enable settings that prevent the scan from
overwhelming or flooding a slow network:
Option Description
Connections per host The maximum number of connections the
scan should make per host.
SMB Connections The maximum number of SMB connections
the scan should make during a scan job.
Chapter 3. Enterprise Scanner policies 65
Page 74

Option Description
Half-Scan Connections The maximum number of connections the
scan should use for opening and closing
ports.
13. Click the Debug Settings tab.
14. In the Packet Capture section, select Enabled and then set the filters for the
agent to use during the ad hoc assessment scan for network analysis.
Note: Packet capturing is not available for ad hoc background scanning.
The agent writes the capture results to
<filename>_<interface>_<timestamp>.cap located in /cache/log/esm/
PacketCapture. To view the results of the capture file:
a. Start Proventia Manager, and then click Support → System Support File.
b. Click Generate Support Data File.
c. Download the file to your computer, extract it, and then open the file in
any PCAP compatible software.
15. Click OK. The ad hoc assessment scan appears in the Command Jobs window.
66 Enterprise Scanner: User Guide
Page 75

Chapter 4. Understanding scanning processes in SiteProtector
This chapter explains the high-level processes behind ad hoc and background
scanning. It also explains how policy settings affect those processes.
Use the following strategies for managing vulnerabilities with Enterprise Scanner:
v Use background scanning for automated vulnerability management.
v Use ad hoc scanning as needed to handle exceptional cases.
Topics
“What is perspective?” on page 68
“Defining perspectives” on page 69
“Scan jobs and related terms” on page 71
“Types of tasks” on page 72
“Priorities for running tasks” on page 73
“Stages of a scanning process” on page 74
“Optimizing cycle duration, scan windows, and subtasks for Enterprise Scanner”
on page 76
© Copyright IBM Corp. 1997, 2009 67
Page 76

What is perspective?
When you scan a group of assets, you anticipate and interpret results based on the
location of your agent relative to the location of the assets. Scanning a group of
assets from inside a firewall, for example, produces different results than scanning
the same group of assets from outside the firewall.
Perspective identifies network location
With Enterprise Scanner, you use perspective to define logical locations on your
network. When you add an agent to SiteProtector, you assign it to a perspective
that identifies the agent’s location on the network. When you configure a scan, you
choose the perspective from which you want to scan the IP addresses or the assets
in the group.
Default perspective
Enterprise Scanner contains one predefined perspective, Global. If you plan to scan
from just one location on your network, you may use the default perspective. Or,
you can create a user-defined perspective to use instead of the default.
Technical requirements
The network location that a perspective represents must meet the following
technical requirements:
v A perspective is a set of subnets from which you expect the same results from
scanning or monitoring your network regardless of where you connect the
agents within that set of subnets.
v Within that set of subnets, no network traffic is blocked and no network address
translation occurs.
Use for distributed scanning
Perspective makes it possible to easily distribute the workload among multiple
agents:
v If you have just one agent in a perspective, that agent performs all the scans that
run from that perspective.
v If you have two or more agents in a perspective, Enterprise Scanner
automatically balances the distribution of tasks among the agents in that
perspective.
Flexibility
Identifying agents by perspective instead of by a specific name or IP address
makes it easier to respond to changes in your scanning environment. If you add an
agent to a perspective, then that agent automatically shares the workload with the
other agents in that perspective. If you remove an agent from a perspective that
contains multiple agents, the remaining agents continue to run the scans assigned
to that perspective. In either case, no additional configuration is required, and
there is no interruption to your scanning cycles.
Use meaningful perspective names
The name you use for a perspective should reflect the implications of scanning
from that location. Using the example of setting up agents inside and outside a
68 Enterprise Scanner: User Guide
Page 77

firewall, descriptive perspective names might be Atlanta-InsideFirewall and
Atlanta-OutsideFirewall.
Placing agents in the correct perspective
A perspective name has no meaning to Enterprise Scanner. You must make sure
that the agents you add to each perspective make logical sense placed there. If you
add an agent to a perspective that is not logical for that agent, Enterprise Scanner
cannot determine that you have made a mistake.
Defining perspectives
To use perspectives, you must define the perspective, assign at least one agent to
the perspective, and then associate the perspective with a group of assets to scan.
Perspectives in policies
The exact role of perspective depends on the policy where you define or select it.
The following table describes how to use perspective in different policies:
Table 7. Perspectives in policies
Policy How to use Applies to...
Network Locations policy Define a perspective as a
Network Locations policy Assign an agent to a
Scan Control policy Identify the perspective from
network location
perspective
which you want to scan
groups of assets
The entire Site
A particular agent
The group, or groups, to
scan with that policy
The following image illustrates the relationships between perspectives and policies
described in the table labeled Perspectives in policies:
Chapter 4. Understanding scanning processes in SiteProtector 69
Page 78

Figure 1. Network locations and perspectives
To scan some asset groups from inside your firewall and others from within your
DMZ, follow these steps:
1. Set up two groups in SiteProtector:
v One group contains assets to scan from inside the firewall.
v One group contains assets to scan from the DMZ.
2. Define a perspective to identify the scanners at each place on your network.
3. Assign one or more scanners to each perspective.
4. Set up a scan control policy for each asset group and specify, in each policy, the
perspective from which scanning should occur.
70 Enterprise Scanner: User Guide
Page 79

Scan jobs and related terms
To tune your system correctly, you must understand how scan jobs run and how
the options you define in policies affect jobs and subtasks.
Definitions
The following table describes the terms used by the Enterprise Scanner agent in
the scanning process:
Table 8. Terms related to scanning jobs
Term Description
Criticality A user-assigned setting that indicates the
Scan job SiteProtector schedules a scan job in the
Task A scan job is divided into tasks as described
Subtask The portion of a task assigned to an agent at
relative importance of an asset to other
assets:
v Critical
v High
v Medium
v Unassigned (the default)
v Low
Command Jobs window, either at the
beginning of a refresh cycle or when you
initiate an ad hoc scan. The scan job divides
the scan into subtasks and displays its
progress. Scans might not start processing as
soon as they are posted if they run only
within scan windows and no scan window
is open.
in “Types of tasks” on page 72.
one time. A subtask includes the number of
IPs to discover or the number of assets to
scan based on settings in the Networking
policy for the agent that runs the scan. You
should change the following field names:
v Maximum IPs per Discovery Subtask
v Maximum Assets per Assessment Subtask
Assets with unassigned criticality
The criticality levels in the definition above are listed in order from highest to
lowest criticality. The Unassigned level is intentionally higher than the Low level for
the following reasons:
v The default criticality level for a newly discovered asset is Unassigned because
the criticality is unknown until you assign it another criticality level.
v Because you must specifically assign the Low level to an asset, Enterprise
Scanner places it below Unassigned assets because unassigned assets might be of
a higher criticality.
Chapter 4. Understanding scanning processes in SiteProtector 71
Page 80

Types of tasks
Scheduled and running scans
To make it easier to explain the scanning processes, scans are considered scheduled
when they are displayed in the Command Jobs window. Because jobs might not
start to scan immediately, they are considered scheduled until the job actually
starts to create tasks and run subtasks.
The importance of tasks and subtasks
Because a task assumes the criticality of the assets it contains, Enterprise Scanner
can assign priority factors to tasks based on asset criticality. Because tasks run in
units determined by subtask size, Enterprise Scanner can run subtasks that can run
to completion during an open scanning window.
This topic describes the types of tasks in a scan and explains which apply to
discovery and which apply to assessment scans.
A scanning job is organized by tasks. Tasks manage other tasks or subtasks, or they
manage the subtasks that actually scan your network and assets. Several factors,
including whether the scan is for discovery or assessment influence, which types of
tasks a scan job contains.
Common management tasks
Every scan, whether for discovery or assessment, includes the following
management tasks:
Table 9. Common management tasks for discovery and assessment scans
Management task Description
A job-level task A task that appears once for each type of
scan. It is identified by the name given to
the scan.
One or more Parent-level tasks A task that appears for each group and
subgroup affected by the scan. It is
identified by the following components:
v Parent
v Type_of_Scan, such as Ad Hoc Discovery
or Ad Hoc Assessment
v Name_of_Asset_Group
Base management tasks
For assessment scans, Enterprise Scanner uses a base task for each group in the
scan. The base task manages the scanning tasks for each criticality in a group. The
base task is identified as ″Base Assessment Scan for Group.″
72 Enterprise Scanner: User Guide
Page 81

Tasks per type of scan
The following table explains the tasks needed for discovery and assessment scans:
Table 10. Tasks per type of scan
Scan type Number of tasks
Discovery 1 job-level task
1 parent task
1 scanning task
Note: There is no way to prioritize the order
in which a discovery scan scans IP
addresses, therefore there is no reason to
divide the job into more than one scanning
task. The scanning task is divided into
subtasks, however, based on the maximum
number of IP addresses allowed per subtask.
Assessment 1 job-level task
1 parent task
1 base task for each group
1 scanning task for each asset criticality level
represented in each group
Priorities for running tasks
To determine the order for scanning your network, each task in a scan job is
assigned a priority.
The tasks for all jobs assigned to a perspective run in priority order as follows:
v Ad hoc scans run before background scans.
v Discovery scans run before assessment scans.
v Assessment scans run tasks in the order of the criticality of the assets in the task.
Criticality and assessment tasks
User-assigned criticality ratings indicate the relative importance of assets in a
group. A group can contain assets with different criticality ratings. When
Enterprise Scanner divides the job into tasks, it creates separate tasks for each
criticality level and assigns assets to the tasks with the corresponding criticality.
Consequently, the assets in an assessment task are of the same criticality, with the
following results:
v An assessment scan contains at least one task for each asset criticality
represented in each group.
v Asset criticality affects the priority of the task.
Example: If a scan job includes a group with one subgroup, and each group
contains assets with all levels of criticality, the job will run as at least ten tasks: one
task for each criticality in each group.
Chapter 4. Understanding scanning processes in SiteProtector 73
Page 82

Task prioritization
The following table explains the reasons behind prioritization of scanning tasks:
Table 11. Reasons for task prioritization
Type of scan Reason for prioritization
Ad hoc versus background Ad hoc scans run at higher priority than
background scans because ad hoc scans fill
extraordinary scanning needs:
v Ad hoc scans help you identify major
changes to your network or assess your
assets against newly identified threats.
v Background scans are cyclical scans for
ongoing vulnerability management.
Discovery versus assessment Assessment scans work only on already
discovered assets. Therefore, a discovery
task has a higher priority so that assets
maybe discovered before the assessment
scan runs.
Criticality of assets in assessment scans To ensure the best protection for your most
critical assets, your agent scans tasks in
order of criticality from highest to lowest.
Stages of a scanning process
Many factors affect when and how scan jobs run. This topic provides a process
that identifies the stages of a scanning cycle and explains the factors to consider at
each stage.
Dynamic prioritization
Scanning jobs are prioritized at the task level so that a scan job does not have to
finish before another scan job with higher priority tasks can be processed. When an
agent completes a subtask, it processes the next subtask with the highest priority
next.
Example: A background scan might be running when you start an ad hoc scan.
You do not have to stop the background scan. The background scan continues until
it has processed its current subtask, then the ad hoc scan takes priority and starts
to run.
74 Enterprise Scanner: User Guide
Page 83

The process for a scanning cycle
The following table describes the general process for a scanning cycle:
Table 12. The process of a scanning cycle
Stage Description
1 Scanning jobs are displayed in the Command Jobs window as they are scheduled:
v A job for a background scan is scheduled at midnight on the first day of the
refresh cycle defined in the Scan Control policy for a group.
v A job for an ad hoc scan is scheduled when you initiate the scan.
2 A job is ready to run follows this order:
v For background scans or ad hoc scans that run in scan windows, the job runs as
soon as an open scan window is available.
v For ad hoc scans that can run any time, the job runs as soon as possible after
you initiate it.
3 When a job is scheduled, the agent divides it into tasks:
v The first task created for all scans is a management (parent) task that oversees
the scanning tasks.
v For discovery scans, there is one additional scanning task.
v For assessment scans, additional scanning tasks are created based on the
priorities described in “Priorities for running tasks” on page 73.
4 When an agent is available to run the scan, the agent finds the task with the
highest priority. The agent then runs a subtask of that task. The subtask is equal to
the subtask size determined by the maximum number of IP addresses or of assets
defined for that agent in the Networking policy.
5 The remaining subtasks run as follows:
v If you have only one agent, the same agent takes the next subtask.
v If you have more than one agent, the first available agent takes the next subtask.
6 Subtasks continue to run until you pause or cancel the scan, or until one of the
following occurs:
v For ad hoc scans, until all the assets have been scanned.
v For background scans, until all the assets have been scanned or until the
scanning cycle ends, whichever occurs first.
Chapter 4. Understanding scanning processes in SiteProtector 75
Page 84

Optimizing cycle duration, scan windows, and subtasks for Enterprise Scanner
Background scanning jobs persist throughout a scan cycle, but are active only
during open scan windows.
The efficiency of background scanning relies on carefully calibrating the following
items:
v Quantity of IP addresses and assets to scan
v The duration of the scan cycle
v The size of subtasks and the size of the smallest scan window
Size of scan windows
You define scan windows for each day in multiples of hours. The shortest possible
scan window is one hour; the longest is 24 hours.
Calibration considerations
If a subtask does not finish during a scanning window, one of the following events
occur:
v If another scan window is available during the same scan cycle, the subtask
starts from the beginning and runs again in its entirety. The second subtask
scans every asset in the subtask, including any that the previous subtask already
scanned.
Important: Subtasks that carry over to another scan window during the same
scan cycle always start from the beginning, repeating any scanning that occurred
in that subtask before the scan window closed.
v If no more scan windows are available during the scan cycle, the unscanned
assets in the subtask, and any unscanned assets in the rest of the job, remain
unscanned.
Important: New scan cycles always start from the beginning of the command
job even if any tasks or subtasks from the previous scan cycle did not finish.
Discovery cycle duration
The duration of your discovery scan cycle will depend on how frequently you add
or change the assets on your network.
v If your network changes frequently, you should scan more frequently.
v If your network is fairly stable, you can scan less frequently.
Assessment cycle duration
The duration of your assessment scan cycle will depend on how important it is for
you to scan every asset during every scan cycle. Consider the following issues:
v If you define a scan cycle for a group that contains critical assets only, it is
probably important to your network security that you scan each asset during the
cycle.
v If you define a scan cycle for a group that contains assets with different levels of
criticality, you might be less concerned if the scan cycle does not scan all the
assets with lower criticality.
76 Enterprise Scanner: User Guide
Page 85

Achieving the right balance
If a refresh cycle is too short, you cannot scan all of your assets during the cycle. If
a scan window is too short to finish subtasks, you can rerun subtasks that were
nearly finished. To achieve the right balance, take the following actions:
v Try to size your subtasks according to the size of your smallest scan window.
v Try to size the quantity of IP addresses and assets to scan according to the
duration of your refresh cycle.
If you still are unable to finish your scanning in the time allowed, you can reduce
the number of checks you run, or you can add another Enterprise Scanner to the
perspective.
Chapter 4. Understanding scanning processes in SiteProtector 77
Page 86

78 Enterprise Scanner: User Guide
Page 87

Chapter 5. Background scanning in SiteProtector
This chapter describes the minimum requirements and options for defining
background scanning in the SiteProtector Console. Because ad hoc scans use some
of the background policies, this chapter also describes the impact of those shared
policies on ad hoc scans. In addition, checklists in this chapter guide you through
the process of setting up background scans.
Topics
“Determining when background scans run” on page 80
“How policies apply to ad hoc and background scans” on page 81
“Background scanning checklists for Enterprise Scanner” on page 83
“Enabling background scanning” on page 84
“Defining when scanning is allowed” on page 85
“Defining ports or assets to exclude from a scan” on page 87
“Defining network services” on page 88
“Defining assessment credentials for a policy” on page 89
© Copyright IBM Corp. 1997, 2009 79
Page 88

Determining when background scans run
This topic describes two important concepts for background scanning: scanning
refresh cycles and scanning windows. These concepts control when background
scans run.
Scanning refresh cycle
A scanning refresh cycle is the maximum duration (in days, weeks, or months) of a
background scan. You define separate scanning refresh cycles for discovery and for
assessment scans in a Scan Control policy. The cycles apply to the scans for all
groups that the policy controls.
Important points about refresh cycles
Refresh cycles affect scanning as follows:
v Refresh cycles apply to background discovery and background assessment scans;
they do not apply to ad hoc scans.
v At the end of a refresh cycle, any background scanning jobs that are still running
are stopped. Their status appears as expired.
v The refresh cycle begins at midnight on the first day of the cycle, and the jobs
for that cycle are scheduled in the Command Jobs window at that time.
Scanning windows
Scanning windows are the hours that are available for scanning each day of the
week. A scan that runs only during scanning windows pauses when a window
closes, and then resumes when the window reopens.
Scans affected by scanning windows
Scanning windows affect scans as follows:
v Scanning windows apply to all background scans for the groups controlled by a
particular Scan Windows policy.
v When you run an ad hoc scan, you choose whether to confine the scan to the
user-defined scanning windows.
Cycle and window dependencies
Background scanning for a group requires a refresh cycle and one or more
scanning windows. Although you define refresh cycles and scanning windows in
different policies, they work together to define the extent of your background
scans. The cycle defines the duration, or elapsed time, of the scan; the scanning
windows define the days and hours when scanning may occur during the cycle.
Flexibility
Because you define refresh cycles and scanning windows in different policies, you
can use the policy inheritance properties to more precisely define your scans. For
example, you can define refresh cycles and apply the Scan Control policy to a
group with several subgroups. For each subgroup, you can define different scan
windows to control the amount of scanning on different parts of your network at
different times. For more about policy inheritance, see Chapter 3, “Enterprise
Scanner policies,” on page 29.
80 Enterprise Scanner: User Guide
Page 89

How policies apply to ad hoc and background scans
Agent policies apply to both ad hoc and background scans, while asset policies
apply to both ad hoc and background scans; however, you can reconfigure some
asset policies when you define an ad hoc scan.
The following table describes ad hoc and background scans:
Table 13. Descriptions of ad hoc and background scans
Type of scan Description
Ad hoc One-time scans that you start manually for
discovery scans, assessment scans, or both,
typically in response to network changes or
newly discovered threats.
Note: You can run an ad hoc scan
immediately, or you can run it only during
the scan windows defined for the group in
the Scan Window policy.
Background Automatic, recurring scans that run on
separately definable refresh cycles for
discovery and for assessment scanning.
Asset policies and ad hoc scans
The following table defines configuration options for policies used by ad hoc scans:
Table 14. Asset policies for ad hoc and background scans
Background asset policies that... Include the following policies:
You can reconfigure scans
Differ for ad hoc scans Scan Control
Contain the same settings for ad hoc scans
as for background scans
v Assessment
v Discovery
v Assessment Credentials
v Network Services
v Scan Exclusion
Note: This policy applies only to
assessment scans, but it applies to both ad
hoc and background scans.
v Scan Window (optional)
Changing assessment and discovery policies
An ad hoc scan initially uses any settings currently configured in the Assessment
and Discovery policies for the group. You can run the scan with those settings, or
you can modify the settings. The following table describes the advantages of each
method:
Table 15. Changes to Assessment and Discovery policies
If you... Then you...
Use the configured settings Can easily start an ad hoc scan that
duplicates a configured background scan.
Chapter 5. Background scanning in SiteProtector 81
Page 90

Table 15. Changes to Assessment and Discovery policies (continued)
If you... Then you...
Modify the configured settings Cannot save the policy. Therefore, the
changes apply to only that ad hoc scan and
do not affect configured background scans.
Scan Control policy
You cannot configure refresh cycles or scan windows for ad hoc scans because they
are not included in the ad hoc Scan Control policy. The following table describes
how refresh cycles and scan windows from the background Scan Control policy
affect ad hoc scans:
Table 16. Ad Hoc Scan Control policy
Option from Background Scan Control
policy Impact on ad hoc scans
Scan Windows You can choose whether to run an ad hoc
scan only during the open scan windows
defined for background scans and to pause
when the windows close.
Refresh cycles Ad hoc scans are never bound by the refresh
cycles that apply to background scans. Ad
hoc scans continue to scan until they finish
or until you stop them. Ad hoc scans pause
when scan windows close if you select the
option to run the scans only during open
scan windows.
Scan window and refresh cycle examples
Assume the following points:
v Your scanning refresh cycle is every two days.
v Scanning windows run from 8:00 P.M. until midnight and from 1:00 A.M. until
4:00 A.M. each day.
Table 17. Examples of scan windows and refresh cycles with ad hoc scans
You start an ad hoc scan that takes three
hours. The scan runs from 11:00 P.M. until
At 11:00 P.M. on the...
First night of a refresh cycle 1:00 A.M. until 3:00 A.M. on the second day
Second night of a refresh cycle the scan runs from 1:00 A.M. until 3:00 A.M.
midnight, and then the scan runs from...
of the same refresh cycle.
on the first day of the next refresh cycle.
82 Enterprise Scanner: User Guide
Page 91

Background scanning checklists for Enterprise Scanner
This topic describes the minimum requirements to set up background discovery
and background assessment scanning. You should also use any other policies that
help you configure your scanning environment to meet your security goals.
Checklist for background discovery scanning
The following table describes the requirements for setting up background
discovery scanning for a group:
1. Apply a Discovery policy to the group.
2. Apply a Scan Window policy to the group (either directly or through
inheritance from a group that is at a higher level in the group structure).
3. Optional: Apply an Assessment Credentials policy to the group for better OS
identification.
4. Apply a Scan Control policy to the group (either directly or through inheritance
from a group that is at a higher level in the group structure).
Checklist for background assessment scanning
The following table describes the requirements for setting up background
assessment scanning for a group:
1. Verify that the group already contains assets, possibly from a recent discovery
scan.
2. Apply an Assessment policy to the group (either directly or through inheritance
from a group that is at a higher level in the group structure).
3. Apply a Scan Window policy to the group (either directly or through
inheritance from a group that is at a higher level in the group structure).
4. Optional: Apply an Assessment Credentials policy to the group for better OS
identification.
5. Apply a Scan Control policy to the group (either directly or through inheritance
from a group that is at a higher level in the group structure).
Chapter 5. Background scanning in SiteProtector 83
Page 92

Enabling background scanning
Use the Scan Control policy on the SiteProtector Console to define the duration of
refresh cycles and to assign user-defined perspectives to scans.
About this task
Background scanning is based on scanning refresh cycles. Refresh cycles define
how frequently you want to rerun scans for a group.
Note: Background scans run during open scan windows that you define in the
Scan Window policy.
Important: This policy initiates background scanning, therefore you configure it
after you have configured the other policies required for background scanning.
The Scan Control policy applies to background discovery and background
assessment scans. This policy does not affect ad hoc scans. Consequently, the
behavior for ad hoc scans is different:
v An ad hoc discovery scan runs only on the group where you define the scan.
v An ad hoc assessment scan applies to the group where you define the scan and
to all the subgroups. This is different from background scans in that background
scanning behavior is determined by which Scan Control policy applies to each
subgroup.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Scan Control policy
for that group.
3. Select the Enable background discovery/assessment scanning of this group
check box, for the type(s) of background scanning you want to define, in the
Background Discovery and Background Assessment sections.
4. Configure background scanning for each type of scan:
Option Description
Job name The name you want displayed for the
scanning job in the Command Jobs window.
Note: This name identifies the scan when it
runs, therefore choose a meaningful name.
Cycle start date The date on which you want the scan cycle
to start.
Note: Future scans are created in
SiteProtector at midnight at the beginning of
the next refresh cycle.
Cycle duration The length (up to three digits) of the cycle as
in one of the following units:
v Hours (for use with Enterprise Scanner 2.1
agents or later only)
v Days
v Weeks
v Months
Current cycle start date The beginning date of the current scan cycle.
(Display only.)
84 Enterprise Scanner: User Guide
Page 93

Option Description
Next cycle start date The beginning date of the next scan cycle.
Use Discovery’s start date/duration and
wait for discovery scan to complete before
scheduling assessment scan
5. If you want to scan from a user-defined perspective, select a perspective from
the Perform background scans from this perspective (Network location) box.
Tip: If you have not yet defined the perspective, click the Configure the
referenced list icon to open the Network Locations policy and define a new
perspective.
Defining when scanning is allowed
Use the Scan Window policy on the SiteProtector Console to define the days and
hours that scanning is allowed.
About this task
(Display only.)
Delays the start of the assessment scan until
the discovery scan has finished to ensure
that the discovery scan has identified all
discoverable assets before the assessment
scan begins.
Note: This check box applies to assessments
scans only.
The Scan Window policy applies to background discovery and assessment scans.
For an ad hoc scan, you can choose whether to run the scan only during the
windows defined in this policy or to run the scan without restriction.
By default, all scan windows are open, therefore scanning is allowed at any time.
When you open a Scan Window policy, however, the default changes; and all scan
windows are closed. If you modify a Scan Window policy, be sure to define scan
windows for discovery and for assessment scans.
Important: If you start a scan when there are no scan windows, the job appears in
the Command Jobs window in the Idle state. The job will not run until you define
scan windows.
The following rules apply to scan windows:
v You define the scan windows for discovery and assessment policies separately,
on separate tabs of the policy. Important: Be sure to define a scan window for
both types of scans if you intend to run both as background scans.
v You can define scan windows only in increments of hours, therefore the
minimum scan window is one hour.
v You can define as many scan windows as you want on any day of the week.
If you have multiple agents, you should stagger your scan windows so that the
discovery scan finishes before the assessment scan begins. If a discovery scan adds
assets to a group while an assessment scan is running, there is no guarantee that
those assets will be included in the assessment scan.
Chapter 5. Background scanning in SiteProtector 85
Page 94

Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Scan Window policy
for that group.
3. Click the Discovery Windows tab or the Assessment Windows tab.
Note: Scanning hours are selected; non-scanning hours are not selected.
4. Select the periods of allowed scanning using the following methods:
If you want to... Then...
Allow scanning during specific hours Click and drag your cursor over the hours
in each day to allow scanning.
Allow scanning at any time Click Fill All.
Remove all defined scans periods Click Clear All.
Important: To enable background scanning, you must define at least one scan
window.
5. Click the Time Zone tab.
6. Select the time zone during which you want the scan windows to run from the
Time zone for scan windows list.
Tip: Typically, you would choose the same time zone as the time zone of the
assets in the group. For example, you might be in the Eastern time zone but
scanning assets in the Pacific time zone. You would define your scanning hours
according to the considerations of the Pacific time zone and set your appliance
to the Pacific time zone.
86 Enterprise Scanner: User Guide
Page 95

Defining ports or assets to exclude from a scan
Use the Scan Exclusion policy on the SiteProtector Console to define the specific
ports, specific assets, or both, that you want to exclude from a scan of a group of
assets.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Scan Exclusion policy
for that group.
3. Choose an option:
If you want to... Then...
Exclude ports Use a combination of typing the ports to
exclude and choosing the ports:
v Type the ports to exclude, separated by
commas, in the Excluded Ports box.
v Click Well Known Ports, and then select
the ports to exclude.
Exclude assets Type the IP addresses (in dotted-decimal or
CIDR notation) of the hosts to exclude in the
Excluded Hosts box:
v Type an IP address, and then press ENTER.
v Type a range of IP addresses, and then
press ENTER.
Example: 172.1.1.100-172.1.1.200
v Type a series of individual IP addresses, a
range of addresses separated by commas,
or both, and then press ENTER.
Note: A red box is displayed around the
Excluded Hosts box until the data is
validated.
Chapter 5. Background scanning in SiteProtector 87
Page 96

Defining network services
Use the Network Services policy on the SiteProtector Console to define service
names associated with TCP and UDP ports.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Network Services
policy for that group.
3. For default or customized services, choose an option:
If you want to... Then...
Disable a service definition Clear the Enabled check box for that service.
Change the description of a service Slowly click Description two times to switch
Allow each service to operate over SSL in
at least some part of your network
Allow service scans for this service over
any TCP and UDP ports specified in the
Assessment policy
Note: You cannot change the Service name, Port, or Protocol of default
services. You cannot delete default services.
4. For customized services, choose an option:
to edit mode, and then change the
description.
Select the May use SSL check box for that
service.
Select the Service scan check box.
If you want to... Then...
Add a service Click the Add icon.
Modify a service Click the Modify icon.
Delete a service Click the Delete icon.
88 Enterprise Scanner: User Guide
Page 97

Defining assessment credentials for a policy
Use the Assessment Credentials policy on the SiteProtector Console to define
authentication credentials for your assets.
About this task
The appliance uses authentication credentials to access accounts during assessment
scans. Enterprise Scanner uses all instances of the credentials that are defined for
the group when it scans assets in the group. You can define different instances of
this policy for different groups, which makes it possible to supply different log on
credentials to scan different parts of the network.
Important: The Assessment Credentials policy currently works only with assets
that run Windows operating systems.
Procedure
1. From the SiteProtector Console, create a tab to display asset policies.
2. In the navigation pane, select a group, and then open the Assessment
Credentials policy for that group.
3. In the Assessment Credentials policy, click Add, and then provide the
following account information:
Option Description
Username The user identification for an account.
Password The password to use with the user name to
Account Type: Windows Local Indicates that the user account is defined
log into an account.
locally on a single Windows device. The
account is used to attempt to log in to a
single Windows device.
When you choose this option, you must
provide a Windows host name in the
Domain/Host box.
Account Type: Windows
Domain/Workgroup
Account Type: Windows Active Directory Indicates that the user account is defined in
Indicates that the user account is defined in
a Windows Domain or Workgroup. The
account is used to attempt to log in to all
Windows devices within the domain or
workgroup.
When you choose this option, you must
provide the Windows Domain or Workgroup
name in the Domain/Host box.
a Windows Active Directory Domain. The
account is used to attempt to log in to all
Windows devices within the Active
Directory domain.
When you choose this option, you must
provide the Active Directory Domain name
in the Domain/Host box.
Chapter 5. Background scanning in SiteProtector 89
Page 98

Option Description
Account Type: SSH Local
Account Type: SSH Domain
Domain/Host Applies to one of the following domains or
Account Level Applies to one of the following accounts:
Indicates that the user account is defined
locally on a single Unix device that allows
SSH logons. The account is used to attempt
login to a single Unix device.
When you choose this option, you must
provide an IP address in the Domain/Host
box.
Indicates that the user account is defined for
Unix devices that allow SSH logons. In this
context, ″Domain″ loosely refers to a set of
devices, rather than to a specific type of
domain. The account is used to attempt to
log in to all SSH devices covered by the
policy.
When you choose this option, you should
supply a descriptive name in the
Domain/Host box. This is for
documentation purposes only; it is not used
by Enterprise Scanner.
hosts:
v For Windows accounts, the domain or
host name to which the account applies.
v For SSH Local accounts, the IP address of
the device to which the account applies.
v For SSH Domain accounts, any text.
v Administrator
v User
v Guest
Important: To avoid inadvertently locking an account, do not add the account
more than once.
90 Enterprise Scanner: User Guide
Page 99

Chapter 6. Monitoring scans in SiteProtector
This chapter uses terms that define scanning parameters for scan jobs with
SiteProtector.
Topics
“Viewing your scan jobs” on page 92
“Viewing discovery job results” on page 92
“Viewing assessment job results” on page 93
© Copyright IBM Corp. 1997, 2009 91
Page 100

Viewing your scan jobs
Use the Command Jobs window on the SiteProtector Console to view the status of
a job, watch its progress, and view its final results.
Procedure
1. In the SiteProtector Console, right-click the Site or a group, and then select
Properties from the pop-up menu.
2. Select Command Jobs from the options in the left pane. The command jobs are
displayed for the selected group.
Tip: If you enable viewing of subgroups (View → Include Subgroups), jobs for
any subgroups of the Site or group you select are also displayed in the list.
Viewing discovery job results
You can open a running scan job in the Command Jobs window to see a snapshot
of the currently available information. Some information is not available until the
job has finished running. To see the latest information about a running job, you
must close and then reopen the window.
Procedure
1. In the SiteProtector Console, right-click the Site or a group, and then select
Properties from the pop-up menu.
2. Select Command Jobs from the options in the left pane. The command jobs are
displayed for the selected group.
3. Right-click a job in the Command Jobs window, and then select Open from the
pop-up menu.
4. Click Results in the left pane. The Remote Scan window is displayed on the
screen as in the example of the illustration above.
92 Enterprise Scanner: User Guide
 Loading...
Loading...