Page 1

Personal Computer
Using Your Personal Computer
PC 300PL Types 6862 and 6892
PC 300GL Types 6275 and 6285
Page 2

Page 3

Personal Computer
Using Your Personal Computer
PC 300PL Types 6862 and 6892
PC 300GL Types 6275 and 6285
IBM
Page 4
Note
Before using this information and the product it supports, be sure to read the general information
under Appendix D, “Product warranties and notices” on page 165.
Fourth Edition (July 1999)
The following paragraph does not apply to the United Kingdom or any country where such provisions
are inconsistent with local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES
THIS PUBLICATION “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR
FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied
warranties in certain transactions, therefore, this statement may not apply to you.
This publication could include technical inaccuracies or typographical errors. Changes are periodically
made to the information herein; these changes will be incorporated in new editions of the publication.
IBM may make improvements and/or changes in the product(s) and/or the program(s) described in this
publication at any time.
This publication was developed for products and services offered in the United States of America. IBM
may not offer the products, services, or features discussed in this document in other countries, and the
information is subject to change without notice. Consult your local IBM representative for information
on the products, services, and features available in your area.
Requests for technical information about IBM products should be made to your IBM reseller or IBM
marketing representative.
Copyright International Business Machines Corporation 1999. All rights reserved.
Note to U.S. Government Users — Documentation related to restricted rights — Use, duplication or
disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp.
Page 5

Contents
Safety Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ix
Laser compliance statement ................................ x
Lithium battery notice ................................... xi
About this book ...................................... xiii
Related publications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xv
Chapter 1. Your IBM personal computer ....................... 1
Identifying your computer ................................. 1
Desktop models . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1
Tower models . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3
What Your IBM personal computer offers ....................... 4
Microprocessor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
System memory . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
PCI bus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4
ISA bus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
Graphics subsystem . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
Audio subsystem . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5
Ethernet support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Hard disk drive ...................................... 6
CD-ROM drive . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Parallel port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6
Serial ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Universal Serial Bus ports ............................... 7
IBM-preinstalled software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7
Operating system support ............................... 8
Diagnostic software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8
System management features ............................. 9
Asset security features .................................. 9
Power management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Ease-of-use features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10
Ergonomic features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11
Expandability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12
External connectors . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14
Service and support ................................... 15
Features at a glance ..................................... 16
System specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Desktop model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18
Tower model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19
Copyright IBM Corp. 1999 iii
Page 6

Chapter 2. Setting Up Your Computer ......................... 21
Installing options? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 21
Selecting a location ..................................... 21
Setting up the computer (Tower Model) ........................ 22
Setting up the computer (desktop model) ........................ 24
Turn on power ........................................ 26
Finish the Installation .................................... 26
Chapter 3. Arranging your workspace ......................... 27
Comfort . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 27
Glare and lighting ...................................... 28
Air circulation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 28
Electrical outlets and cable lengths ............................ 28
Chapter 4. Operating your computer .......................... 29
Using controls and status indicators ........................... 29
Starting your computer - PC 300GL ........................... 31
Starting your computer - PC 300PL ........................... 32
Startup sequence information ............................. 33
Information for network administrators ....................... 34
Settings that affect the startup procedure ........................ 35
Starting your computer over a network ......................... 36
Shutting down your computer .............................. 36
Using mouse features .................................... 37
Mouse basics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 37
Using the ScrollPoint mouse .............................. 38
Using audio features .................................... 39
Using a CD-ROM drive .................................. 40
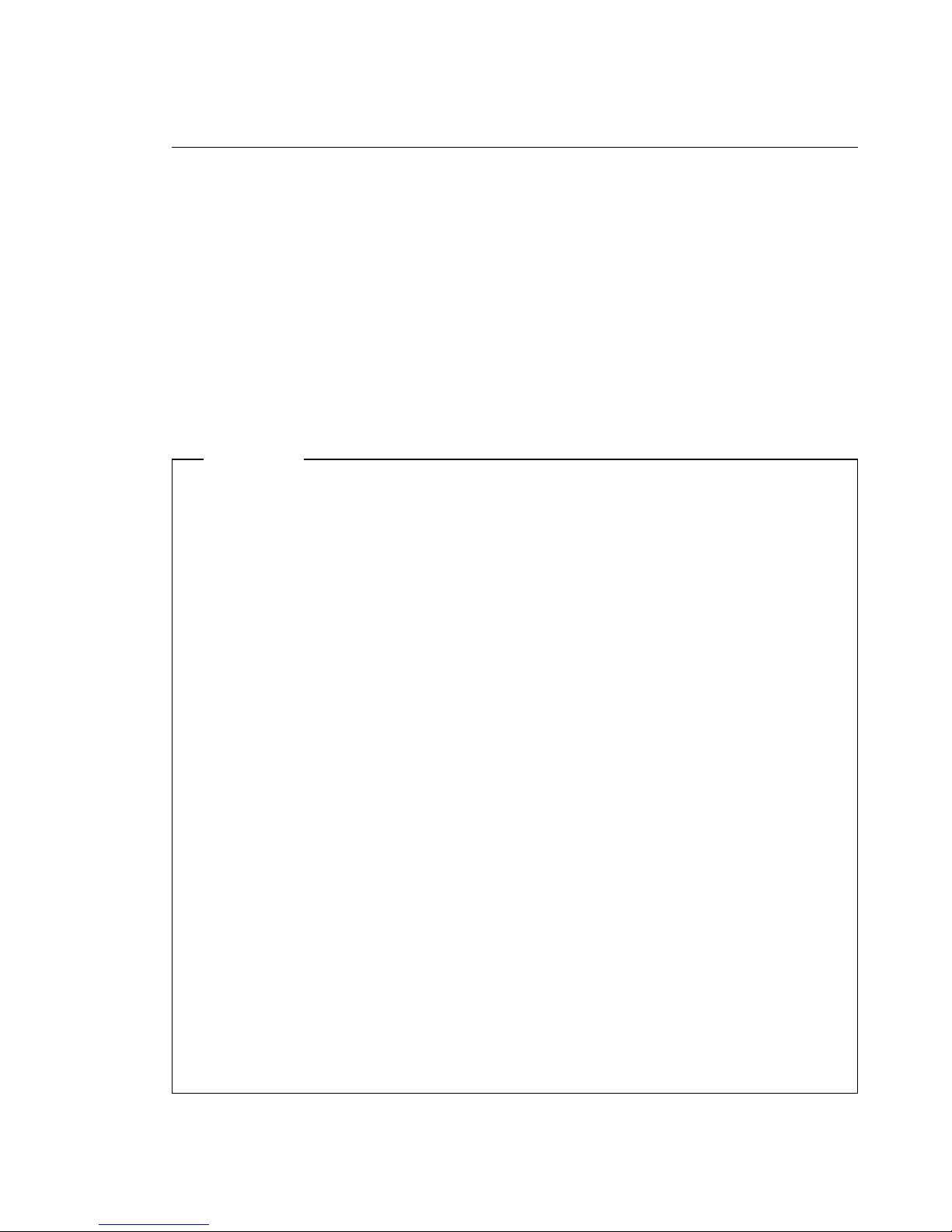
Handling a CD ...................................... 41
Loading a CD ....................................... 41
Loading a CD into a vertically positioned desktop model ............ 42
Using video features .................................... 46
Video device drivers .................................... 47
Using Universal Manageability features ......................... 48
Wake on LAN ...................................... 48
LANClient Control Manager (LCCM) ........................ 49
System Migration Assistant (SMA) .......................... 49
Alert on LAN support .................................. 49
DMI BIOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 50
System management controller ............................ 50
Built-in network protocols ............................... 51
Asset ID capability .................................... 51
Remote administration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 52
iv Using Your Personal Computer
Page 7

IBM System Management Tools ............................ 52
Using security features ................................... 52
Security provided through the Configuration/Setup Utility program ..... 53
Security U-bolt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Anti-intrusion features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 53
Component protection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 54
Data protection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Enhanced security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 55
Updating system programs ................................ 58
Chapter 5. Using the Configuration/Setup Utility program ............ 61
Starting and using the program .............................. 62
Viewing and changing settings ............................ 63
Exiting the program ................................... 65
Instructions for most frequently used procedures ................... 66
Viewing the system summary ............................. 66
Setting the date and time ................................ 67
Using a power-on password .............................. 67
Using an administrator password ........................... 71
Setting the startup sequence .............................. 75
Setting remote administration ............................. 76
Setting power management features ......................... 76
Configuration/Setup Utility option tables ........................ 80
System Summary . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 80
Product data . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 81
Devices and I/O Ports .................................. 82
Start Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 85
Date and Time ...................................... 87
System Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 87
Advanced Setup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89
ISA Legacy Resources .................................. 91
Power Management . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 93
Quick reference for network-related settings ...................... 95
Pentium III processor serial number feature ...................... 97
Chapter 6. Taking care of your computer ....................... 99
Basics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Cleaning your computer .................................. 99
Computer and keyboard ................................ 99
Monitor screen . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 99
Mouse . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 100
Replacing the battery ................................... 101
Moving your computer .................................. 101
Contents v
Page 8

Chapter 7. Solving problems . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 103
Using diagnostic tools .................................. 103
Power-On Self-Test (POST) .............................. 104
Error messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 105
POST message charts ................................. 108
POST Beep Codes ..................................... 124
POST Beep Code Table ................................ 124
Troubleshooting charts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 126
Diagnostic programs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 136
IBM Enhanced Diagnostics .............................. 136
PC Doctor for Windows ................................ 137
PC Doctor for Windows NT ............................. 138
CoSession Remote . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 138
Installing files from option diskettes .......................... 139
Managing TSR programs (DOS or Microsoft Windows 3.1x) ........... 139
Chapter 8. Getting help, service, and information ................ 141
Service support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 141
Before you call for service ................................ 142
Getting customer support and service ......................... 143
Using the World Wide Web ............................. 143
Using electronic support services .......................... 144
Getting information by fax .............................. 145
Getting help online ................................... 145
Getting help by telephone .............................. 145
Getting help around the world ........................... 147
Purchasing additional services ............................. 147
Enhanced PC support line .............................. 147
900-number operating system and hardware support line ........... 148
Network and server support line .......................... 148
Ordering support line services ............................ 149
Warranty and repair services ............................. 149
Ordering publications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 150
Appendix A. Computer records . . . . . . . . . . . . . . . . . . . . . . . . . . . . 151
Serial numbers and keys ................................. 151
Device records . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 153
Appendix B. Additional Ethernet information ................... 157
Connector and Cable Specifications .......................... 157
Diagnostic LEDs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
Error messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 158
vi Using Your Personal Computer
Page 9

Appendix C. Using the IBM Software Selections CD and the IBM
Ready-to-Configure Utility Program CD ...................... 163
Features of the IBM Software Selections CD and the IBM Ready-to-Configure
Utility Program CD ................................... 163
Starting the CD ...................................... 164
Appendix D. Product warranties and notices ................... 165
Warranty Statements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 165
IBM Statement of Limited Warranty for United States, Puerto Rico, and
Canada (Part 1 - General Terms) .......................... 165
IBM Statement of Warranty Worldwide except Canada, Puerto Rico, Turkey,
United States (Part 1 - General Terms) ...................... 168
Part 2 - Worldwide Country-Unique Terms .................... 171
Notices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 174
Year 2000 readiness and instructions ........................ 175
Trademarks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 175
Class B Notices ..................................... 176
Class A Notices ..................................... 177
Other Notices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 178
Power cord notice ................................... 181
Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 183
Contents vii
Page 10

viii Using Your Personal Computer
Page 11
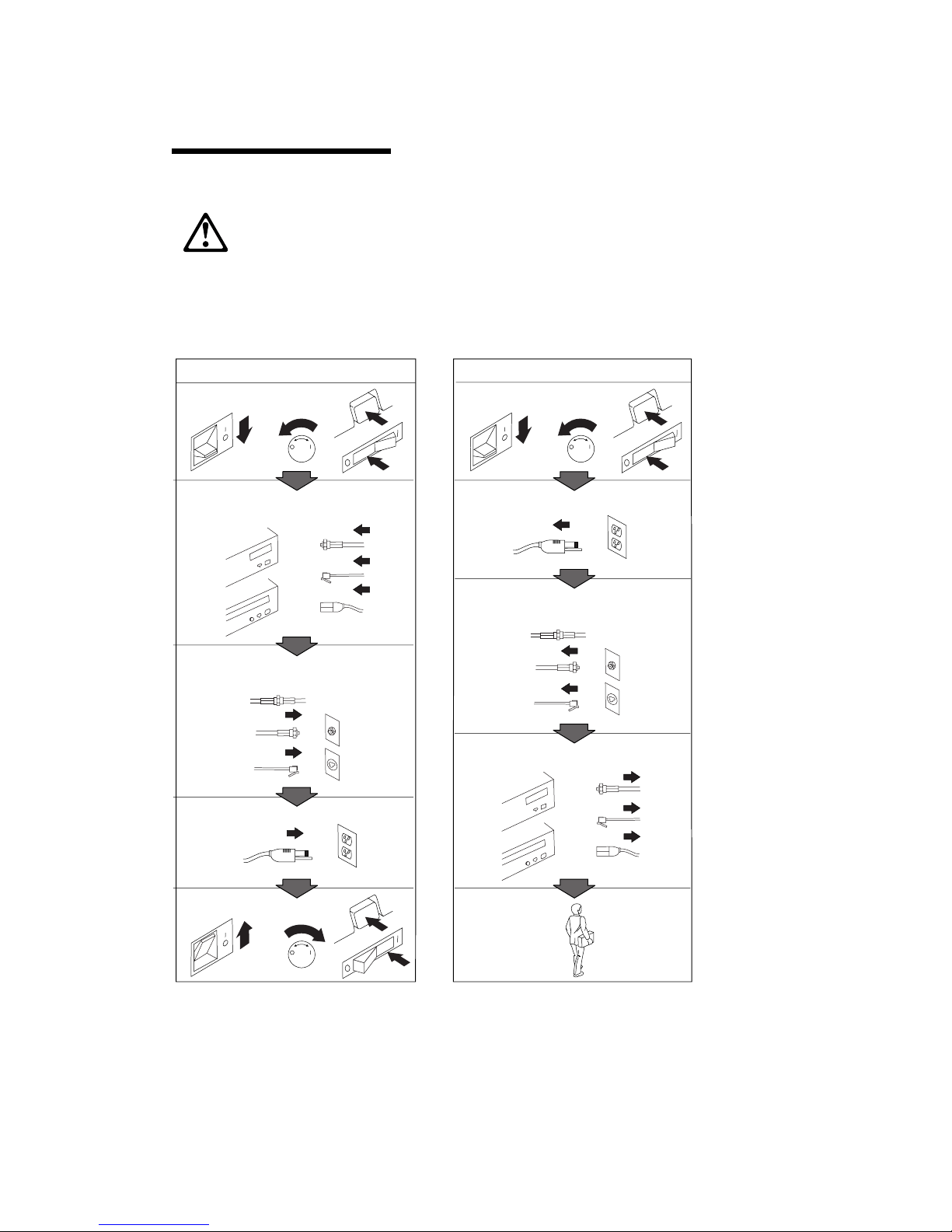
Safety Information
Turn ever ything OFF.
Attach signal cables to
receptacles.
First, remove power cord from
outlet.
To Disconnect
Turn device ON.
DANGER:
Turn ever ything OFF.
To Connect
Remove signal cables from
receptacles.
Remove all cables from devices.
Attach power cord to outlet.
First, attach all cables to devices.
Electrical current from power, telephone, and communication
cables is hazardous.To avoid shock hazard, connect and
disconnect cables as shown below when installing, moving or
opening the covers of this product or attached devices.The
power cord must be used with a properly grounded outlet.
Copyright IBM Corp. 1999 ix
Page 12
Laser compliance statement
Some IBM Personal Computer models are equipped from the factory with a
CD-ROM drive. CD-ROM drives are also sold separately as options. The CD-ROM
drive is a laser product. The CD-ROM drive is certified in the U.S. to conform to
the requirements of the Department of Health and Human Services 21 Code of
Federal Regulations (DHHS 21 CFR) Subchapter J for Class 1 laser products.
Elsewhere, the drive is certified to conform to the requirements of the International
Electrotechnical Commission (IEC) 825 and CENELEC EN 60 825 for Class 1 laser
products.
When a CD-ROM drive is installed, note the following.
CAUTION:
Use of controls or adjustments or performance of procedures other than those
specified herein might result in hazardous radiation exposure.
Removing the covers of the CD-ROM drive could result in exposure to hazardous
laser radiation. There are no serviceable parts inside the CD-ROM drive. Do not
remove the CD-ROM drive covers.
Some CD-ROM drives contain an embedded Class 3A or Class 3B laser diode. Note
the following.
DANGER
Laser radiation when open. Do not stare into the beam, do not view
directly with optical instruments, and avoid direct exposure to the beam.
x Using Your Personal Computer
Page 13
Lithium battery notice
CAUTION:
Danger of explosion if battery is incorrectly replaced.
When replacing the battery, use only IBM Part Number 33F8354 or an equivalent
type battery recommended by the manufacturer. The battery contains lithium
and can explode if not properly used, handled, or disposed of.
Do not:
Throw or immerse into water
Heat to more than 100°C (212°F)
Repair or disassemble
Dispose of the battery as required by local ordinances or regulations.
ATTENTION
Danger d'explosion en cas de remplacement incorrect de la batterie.
Remplacer uniquement par une batterie IBM de type 33F8354 ou d'un type
équivalent recommandé par le fabricant. La batterie contient du lithium et peut
exploser en cas de mauvaise utilisation, de mauvaise manipulation ou de mise au
rebut inappropriée.
Ne pas :
Lancer ou plonger dans l'eau
Chauffer à plus de 100°C (212°F)
Réparer ou désassembler
Mettre au rebut les batteries usagées conformément aux règlements locaux.
Safety Information xi
Page 14

xii Using Your Personal Computer
Page 15

About this book
This book helps you become familiar with your IBM Personal Computer and its
many features. It describes how to configure, operate, and maintain your computer.
In the unlikely event you experience problems, you can also find helpful
troubleshooting information and instructions for obtaining service.
Edition Note
This edition contains information about new models with some additional
features that might not be reflected in the online publications included with
some preloaded models. For the latest information about your computer, go to:
http://www.ibm.com/pc/us/desktop
The book is organized as follows:
Chapter 1, "Your IBM personal computer," contains an overview of the features
of your computer.
Chapter 2, "Setting up your computer," contains instructions for connecting the
keyboard, mouse, monitor, power cables, and other optional devices.
Chapter 3, "Arranging your workspace," contains information about setting up
your work area to optimize use of your computer. Safety considerations are
also discussed.
Chapter 4, "Operating your computer," contains instructions for the day-to-day
use and management of your computer. Startup and shutdown procedures,
information on using a CD-ROM drive, and system management and security
features are all included in this chapter.
Chapter 5, "Using the Configuration/Setup Utility program," contains
instructions for configuring your computer.
Chapter 6, "Taking care of your computer," contains information about the
proper handling and care of your computer.
Chapter 7, "Solving problems," contains information that will help you identify
and correct problems that might arise as you use your computer.
Chapter 8, "Getting help, service, and information," contains a description of the
wide variety of resources available from IBM to assist you in the use of your
computer. This chapter also describes how to obtain additional information
about IBM products.
Copyright IBM Corp. 1999 xiii
Page 16

Appendix A, "Computer records," contains forms for recording information
about your computer, which can be helpful if you decide to install any
additional options, or if you ever need to have your computer serviced.
Appendix B, "Additional Ethernet information," contains information about the
Ethernet controller included with some models, along with cable specifications
and error codes.
Appendix C, "Using the IBM Software Selections CD and the IBM
Ready-to-Configure Utility Program CD," describes features of the IBM Software
Selections CD and the IBM Ready-to-Configure Utility Program CD, and includes
instructions for using the CDs that come with your computer.
Appendix D, "Product warranties and notices," contains hardware product
warranty, trademark acknowledgments, electronic emission notices, and other
legal and general notices for your computer.
xiv Using Your Personal Computer
Page 17

Related publications
The following publications, together with this book, contain information about your
computer.
Installing Options in Your Personal Computer
This documentation contains instructions for adding memory, adapters, drives,
and other options to your computer. It is provided on the IBM
Ready-to-Configure Utility Program CD or the IBM Software Selections and is also
available from the IBM PC Web site.
Understanding Your Personal Computer
This online publication includes general information about using personal
computers and in-depth information about the specific features of your
computer. It is provided on your hard drive and on the IBM Ready-to-Configure
Utility Program CD or the IBM Software Selections CD.
About Your Software
This publication (provided only with computers that have IBM-preinstalled
software) contains information about the preinstalled software package.
The following publications contain more information about your computer.
Hardware Maintenance Manual
This publication contains information for trained service technicians. To order a
copy, see Chapter 8, “Getting help, service, and information” on page 141. It is
also available from the IBM PC Web site.
Technical Information Manual
This publication contains more information about the technical aspects of your
computer. It is available from the IBM PC Web site.
To access these publications using the World Wide Web, go to:
http://www.ibm.com/pc/us/support/
About this book xv
Page 18

xvi Using Your Personal Computer
Page 19

Chapter 1. Your IBM personal computer
Thank you for selecting an IBM Personal Computer. Your computer incorporates
many of the latest advances in personal computer technology and is easy to expand
and upgrade as your needs change. With its enhanced video and system
management capabilities, your computer is particularly suited for your corporate
intranet environment.
Identifying your computer
In most instances, the best way to identify your computer is by the machine
type/model number. The type/model number indicates the various features of the
computer, such as the type of microprocessor or the number of bays. You can find
this number on the small label on the front of your computer. An example of a
machine type/model number is 6862-123.
You need to know whether your computer is a PC 300PL or a PC 300GL. You also
need to know whether the computer is a desktop or tower.
PC 300PL tower models have 6 drive bays, 3 PCI slots and 3 ISA slots. PC 300PL
desktop models have 4 drive bays, 2 PCI slots, 1 ISA/PCI slot, and 1 ISA slot. All
PC 300PL models have an AGP slot on the system board.
PC 300GL tower models have 6 drive bays, 3 PCI slots, and 3 ISA slots. PC 300GL
desktop models have 4 drive bays, 2 PCI slots, 1 ISA/PCI slot, and 1 ISA slot.
There is no AGP slot on PC 300GL models.
The desktop model can be set on its side in a floor stand, but the orientation of the
drives will be vertical in that position, rather than horizontal. Towers and desktops
used in their normal orientations have horizontal drive bays.
Throughout this book, we will be describing PC 300PL and PC 300GL models, in
both desktop and tower versions. These naming conventions are used only where it
is appropriate. Instructions without these naming conventions apply to all the
computer models.
Desktop models
The desktop model PC 300PL comes with four drive bays and five expansion slots.
The fifth expansion slot is for an AGP adapter.
Copyright IBM Corp. 1999 1
Page 20

The desktop model PC 300GL comes with four drive bays and four expansion slots.
Some computers have a hard disk drive in bay 3 and a diskette drive in bay 4. If
your computer has a CD-ROM drive, it is installed in bay 1. You can install an
additional hard disk drive in bay 2.
Note: Keyboard and mouse vary by model.
2 Using Your Personal Computer
Page 21

Tower models
The PC 300PL tower model comes with six bays and seven expansion slots. The
seventh expansion slot is for an AGP adapter.
The PC 300GL tower model comes with six bays and six expansion slots. Some
computers have a hard disk drive in bay 6 and a diskette drive in bay 4. If your
computer has a CD-ROM drive, it is installed in bay 1. You can install additional
hard disk drives in bays 2, 3, and 5.
Note: Keyboard and mouse vary by model.
Chapter 1. Your IBM personal computer 3
Page 22
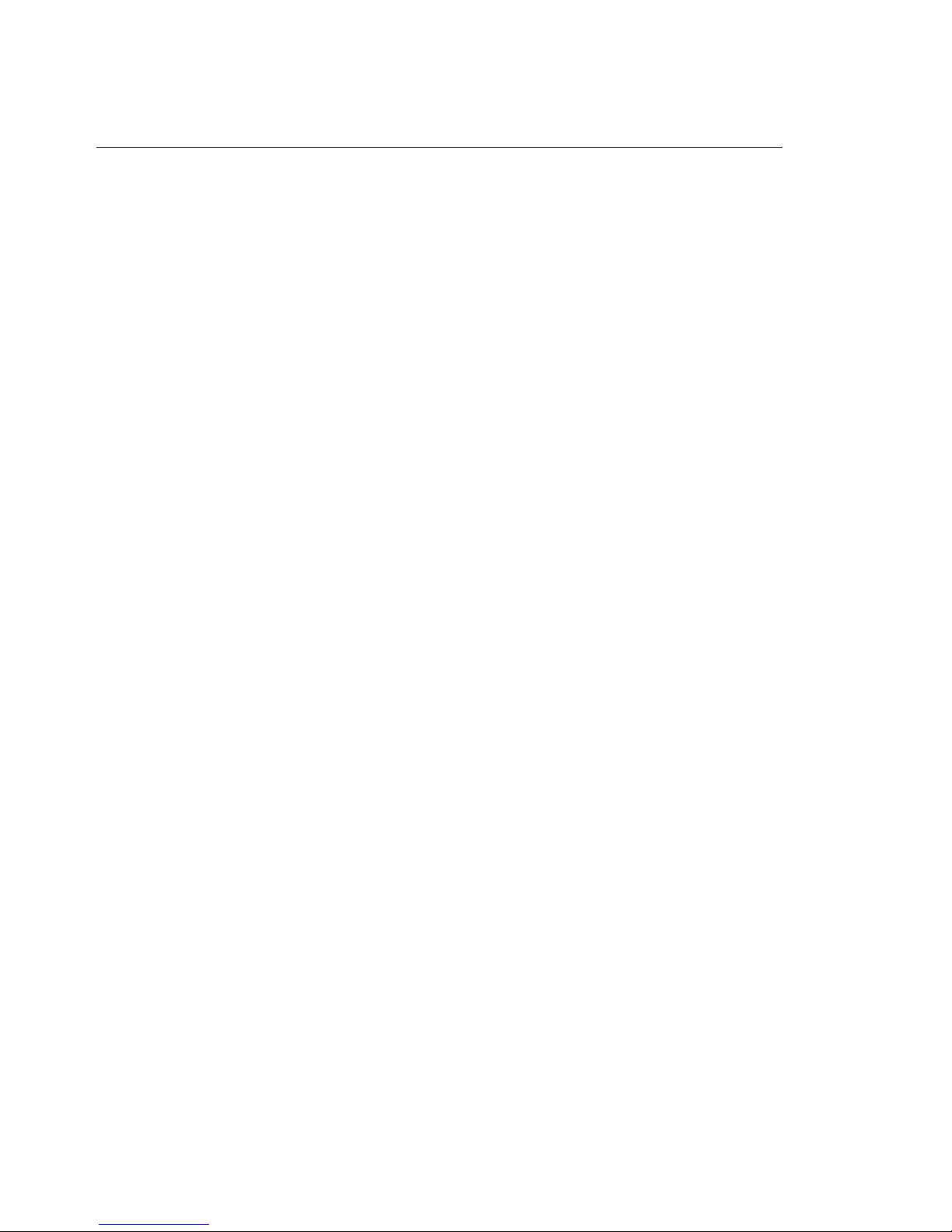
What Your IBM personal computer offers
This section describes many of the features of PC 300PL and PC 300GL models. To
view the hardware features specific to your system, see “Viewing the system
summary” on page 66.
Microprocessor
Your computer is equipped with either an Intel Pentium II, an Intel Celeron, or
an Intel Pentium III processor. All of these MMX microprocessors supply the
speed and power you need to take advantage of even the most complex programs.
In addition, the microprocessor incorporates new multimedia extensions into the
Intel architecture, which improves the performance of multimedia and
communications applications by accelerating calculations commonly performed for
audio, video, speech synthesis and recognition, 2D and 3D graphics, and data
communications.
Note: To view the speed of the microprocessor in your computer, see “Viewing the
system summary” on page 66.
Also, L2 cache memory, which helps speed the exchange of information between the
microprocessor and system memory, is standard on some models.
System memory
If your computer contains an Intel Pentium II or Pentium III processor, it comes
standard with nonparity or ECC (error checking and correction) 100 MHz SDRAM
(synchronous dynamic random access memory). If your computer contains an Intel
Celeron processor, it comes standard with nonparity 100 MHz SDRAM. These
types of memory use advanced technology to increase system performance.
Note: To view the amount of system memory in your computer, see “Viewing the
system summary” on page 66.
PCI bus
Your computer has a PCI (peripheral component interconnect) bus. PCI is an
advanced input/output (I/O) bus standard developed by the computer industry to
keep up with performance improvements of microprocessor buses and advanced
peripheral devices. The PCI bus adds to the capability of the ISA bus, speeding up
the exchange of information among the microprocessor and peripheral devices
within your computer system. This improves the overall performance of your
computer.
4 Using Your Personal Computer
Page 23

ISA bus
Your computer has an ISA (industry standard architecture) bus, which is a widely
used I/O (input/output) bus. The ISA bus is popular because so many adapters
and devices have been designed and marketed for it.
Graphics subsystem
Your computer has a high performance accelerated graphics port (AGP) graphics
subsystem that provides fast access to system memory for video functions.
Some models have an integrated S3 Trio3D graphics subsystem. This subsystem
provides a connector on the rear of the computer for attaching a monitor. Your
computer provides SGRAM (synchronous graphics RAM) video memory to further
improve video performance.
Note: To view the amount of video memory in your computer, see “Viewing the
system summary” on page 66.
For information on the refresh rates supported for the various resolutions
available with S3 Trio3D video, see “Using video features” on page 46.
If you decide to change the video capabilities of your computer and your computer
has an AGP connector, you can use the AGP connector on the system board for
installing a future AGP adapter. This connection can support bus speeds up to 133
MHz. Instructions for installing an AGP adapter are in Installing Options in Your
Personal Computer.
Some models might have a different graphics adapter, such as the Matrox G200,
Intense 3D Wildcat 4000, or the IBM Fire GL1. The systems with these new
graphics adapters do not have a video connector on the system board. The video
cable must be connected to the adapter itself. For information about obtaining the
latest device drivers for your graphics adapter, see Chapter 8, “Getting help,
service, and information” on page 141.
Audio subsystem
Some models have an integrated audio controller that provides all the digital audio
and analog mixing functions required for recording and playing high-quality sound
on your computer. This audio controller supports Sound Blaster Pro, Adlib, and
Microsoft Windows Sound System applications.
Chapter 1. Your IBM personal computer 5
Page 24

Ethernet support
Some models have an integrated Intel 10/100 Mbit, PCI Ethernet controller and an
RJ-45 connector for a high-performance network connection.
Hard disk drive
Some models come with a hard disk drive that has an enhanced integrated drive
electronics (EIDE) bus-master interface. The EIDE drive plugs into one of two EIDE
connectors located on the riser card in your computer. You can connect an
additional hard disk drive to the ribbon cable already attached to the riser card, or
you can purchase another cable and connect up to two hard disk drives or other
IDE or EIDE devices to the second connector on the riser card.
Notes:
1. In the desktop model, a maximum of three internal IDE or EIDE devices can be
installed, depending on the number of available bays.
2. For models with an IBM factory-installed CD-ROM, two ribbon cables (for
connecting IDE or EIDE devices) are shipped inside your computer.
Some models come with an ultra-wide SCSI (small computer system interface) hard
disk drive. These models have a SCSI adapter installed in one of the PCI expansion
slots. If your computer has an IBM-preinstalled SCSI adapter, refer to the SCSI
documentation provided with your computer for information on the adapter and for
instructions on installing SCSI devices.
CD-ROM drive
A CD-ROM drive is installed in some models. CD-ROM (compact disc read-only
memory) technology offers quick access to large amounts of information. A
compact disc can store more than 650 MB of data, such as the large files needed for
audio, still and full-motion video, and still and animated graphics. A CD-ROM
drive can play back or read from a CD, but it cannot write information on it.
Parallel port
Your computer has a parallel port that can be used to communicate with a parallel
printer or other parallel devices.
The parallel port can operate in several different modes. The default mode for your
computer is SPP (standard parallel port). However, your computer also supports
the ECP/EPP (extended capabilities port/enhanced parallel port) mode.
6 Using Your Personal Computer
Page 25

ECP/EPP has two advantages over SPP. When your computer is in ECP/EPP
mode, you can print documents faster than when the computer is in SPP mode, and
you can attach devices other than printers, such as communication and storage
devices, to the parallel port. You can set modes of operation for the parallel port
using the Configuration/Setup Utility program.
Note: To minimize electromagnetic interference (EMI), use braid-shielded cables
with metal ends when connecting a device to the parallel port.
Serial ports
Your computer has two standard 16550-UART serial ports that can be used to
communicate with devices such as modems, plotters, and printers.
Note: To minimize electromagnetic interference (EMI), use braid-shielded cables
with metal ends when connecting devices to these ports.
Universal Serial Bus ports
The universal serial bus (USB) interface is a state-of-the-art technology developed to
add more diversity and capabilities to personal computers. As a standard feature,
your computer has two USB ports, so you can take advantage of new USB devices
as they become available.
Using this new technology, you can plug different types of optional,
USB-compatible devices into the USB ports on your computer. Because USB
incorporates Plug and Play technology, you can install and remove devices easily
without turning off your computer or opening the cover. Once installed, the
devices configure automatically. In addition, an option called a hub can be
connected to a USB port on your computer, which enables you to plug in more than
one device at a time. A hub converts a single USB connector into multiple ports
where USB devices can be attached.
For more information, see the USB Web site at:
http://www.usb.org/
IBM-preinstalled software
IBM-preinstalled software is provided with some models. This software includes an
operating system, device drivers to support built-in features, and other support
programs.
Chapter 1. Your IBM personal computer 7
Page 26

Operating system support
Your computer is designed to use a variety of operating systems in order to meet
your particular needs. Computer models with IBM-preinstalled software use one of
the following operating systems:
Windows NT 4.0 Workstation
Windows 95 (OSR 2)
Windows 98 (when available)
Important
If your computer has Windows NT 4.0 Workstation, Windows 95, or Windows
98 preinstalled by IBM, drive C of your hard disk drive is formatted with a
partition size of 2 GB. See the IBM Welcome Center (part of the preinstalled
software) for additional details about the disk partition strategy for your
computer.
The following operating systems are supported by your computer:
1
Windows 98
Windows 95 (OSR 1)
PC DOS 7.0
OS/2 Warp 4.0
OS/2 Warp 3.0
OS/2 Warp Connect 3.0
Windows 3.11
Windows for Workgroups 3.11
Windows NT 3.51
Diagnostic software
If you have a problem with your computer, IBM provides an easy-to-use diagnostic
program that helps determine if a hardware component is causing the problem. If
your computer has preinstalled software, a startable IBM Enhanced Diagnostic
diskette image is provided is provided either on the IBM Ready-to-Configure Utility
1
The operating systems listed here are being tested for compatibility at the time this publication goes to
press. Additional operating systems might be identified by IBM as compatible with your computer
following the publication of this booklet. Corrections and additions to the list are available in IBM's
online compatibility report, which can be found on the World Wide Web
(http://www.ibm.com/pc/us/cdt/). For additional information, see Chapter 8, “Getting help,
service, and information” on page 141.
8 Using Your Personal Computer
Page 27

Program CD, the IBM Software Selections CD,or on the hard disk drive. See
“Diagnostic programs” on page 136 for more information.
System management features
Note: Some system management features might not be available for your
computer.
Features of some IBM Personal Computers make it possible for a network
administrator to manage and control the computer remotely over a network. These
features are:
Wake on LAN support
Alert on LAN support (PL models only)
Desktop Management Interface (DMI) BIOS and DMI software
System management controller (PL models only)
Integrated network protocols
Enablement for remote administration
Asset ID support (PL models only)
IBM System Management Tools
For information on settings for these features, refer to “Using Universal
Manageability features” on page 48.
Asset security features
Your computer has the following security features that help protect both your
hardware and software:
Security settings provided by the Configuration/Setup Utility program:
– Power-on and administrator password protection
– Startup-sequence control
– Hard disk drive and diskette drive access control
– I/O port control
– Enhanced security for administrator password and startup sequence (PL
models only)
Chassis-intrusion detector (PL models only)
Cover lock (in some models)
U-bolt and security cabling (optional)
Operating system security
Diskette write protection
Chapter 1. Your IBM personal computer 9
Page 28

Power management
Energy conservation is an important concern. Your computer has Advanced Power
Management (APM) and Advanced Configuration and Power Interface (ACPI)
features that allow you to set different levels of energy conservation for specific
components of your computer. You can view and change APM and ACPI settings
using the Configuration/Setup Utility program or the Windows 95 control panel.
APM BIOS
Automatic Hardware Power Management
Activity Monitor
Automatic Power On
Wake Up on Alarm
Serial Port/Modem Ring Detect
Ease-of-use features
The system board in your computer is designed to make upgrading and servicing
your computer easier. Cable connections for standard devices are located on the
riser card. This arrangement helps to eliminate cable tangle and clutter on the
system board, allows shorter cables, and makes it easier to remove the system board
or to upgrade external options. In addition, the system board is on a sliding
mechanism so that you can slide the system board in and out of the computer
frame.
Support for Plug and Play technology is built into the system board of your
computer. This feature makes adding options easier. When you add an adapter
that is Plug and Play-compatible, the adapter is configured automatically. In most
cases, no switches or jumpers have to be set on the adapter.
10 Using Your Personal Computer
Page 29

Ergonomic features
Your computer has ergonomic features that make it more comfortable to use. The
power switch and indicator lights are located for easy access and visibility. In
addition, you can easily change monitor settings to reduce or eliminate flicker and
jitter, and you can adjust the angle of the keyboard to make typing more
comfortable.
With some models, a keyboard extender is included with the keyboard. To attach
it, align the extender with the bottom edge of the keyboard and snap them together,
as shown below.
Chapter 1. Your IBM personal computer 11
Page 30
Expandability
You can easily expand the capabilities of your computer by adding memory, drives,
or adapters. Your computer has a riser card for connecting adapters to the ISA or
PCI bus. Examples of adapters that can be added to your computer include
graphics, SCSI (small computer system interface), and network adapters. Also,
some computers have an accelerated graphics port (AGP) connection on the system
board for attaching an AGP adapter.
Desktop model: The desktop model has four drive bays. Unoccupied drive bays
can be used for installing additional devices such as hard disk and other drives.
The following illustration shows the drive bays in the desktop model.
3.5-Inch Bay
3.5-Inch
Diskette Drive
5.25-Inch CD-ROM
Drive (Standard
in some models)
5.25-Inch Bay
for Optional Drive
The PC 300GL desktop model has four expansion slots. One or more of these slots
might be occupied, depending on the model of your computer. Unoccupied slots
can be used for installing adapters. The PC 300PL desktop model has an additional
AGP adapter expansion slot. The following illustration shows the locations of the
expansion slots.
Expansion Slots
AGP Expansion Slot
12 Using Your Personal Computer
Page 31
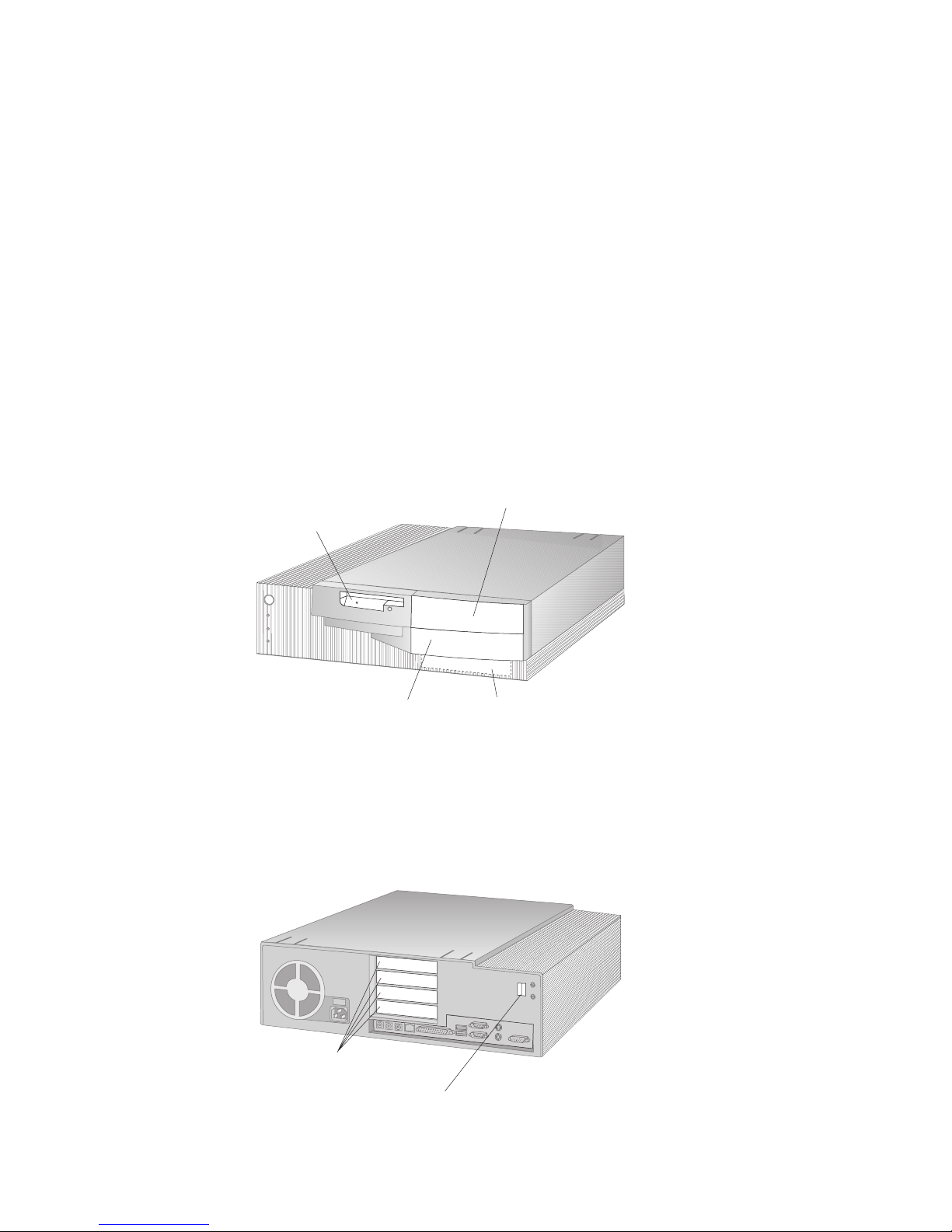
Tower model: The tower model has six drive bays. Unoccupied drive bays can
be used for installing additional devices such as hard disk and CD-ROM drives.
The following illustration shows the drive bays in the tower model.
Socket7
Socket7
3.5-Inch Bay
3.5-Inch
Diskette Drive
5.25-Inch Bay
for Optional Drive
5.25-Inch CD-ROM
Drive (Standard
in some models)
3.5-Inch Bay
for Optional Drive
The PC 300GL tower model has six expansion slots. One or more of these slots
might be occupied, depending on the model of your computer. Unoccupied slots
can be used for installing adapters. The PC 300PL tower model has an additional
AGP adapter expansion slot.
The following illustration shows the locations of the expansion slots.
Expansion Slots
APG Expansion Slot
Chapter 1. Your IBM personal computer 13
Page 32

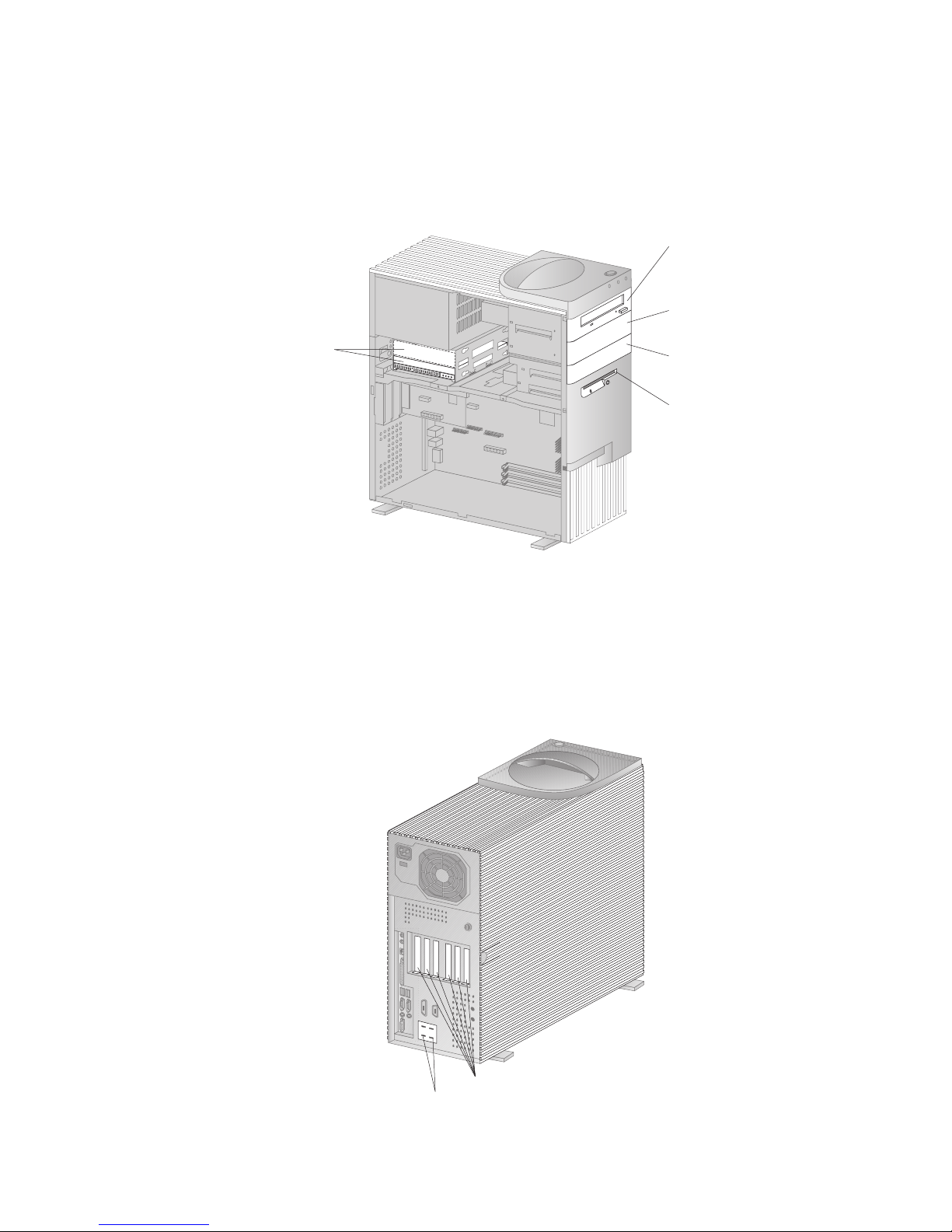
External connectors
Input/output (I/O) devices such as the mouse, keyboard, or printer attach to the
external connectors at the rear of the computer. The external connectors for the
desktop and tower models are shown below.
Desktop model: The following illustration shows the location of the external
connectors on the rear of the desktop model.
2
2
1
Monitor
USB 1
Parallel
Line In
PL Models Only
Microphone
Ethernet
Line Out
Keyboard
Mouse
Serial 1
Serial 2
USB 2
Green LED
Yellow LED
14 Using Your Personal Computer
Page 33

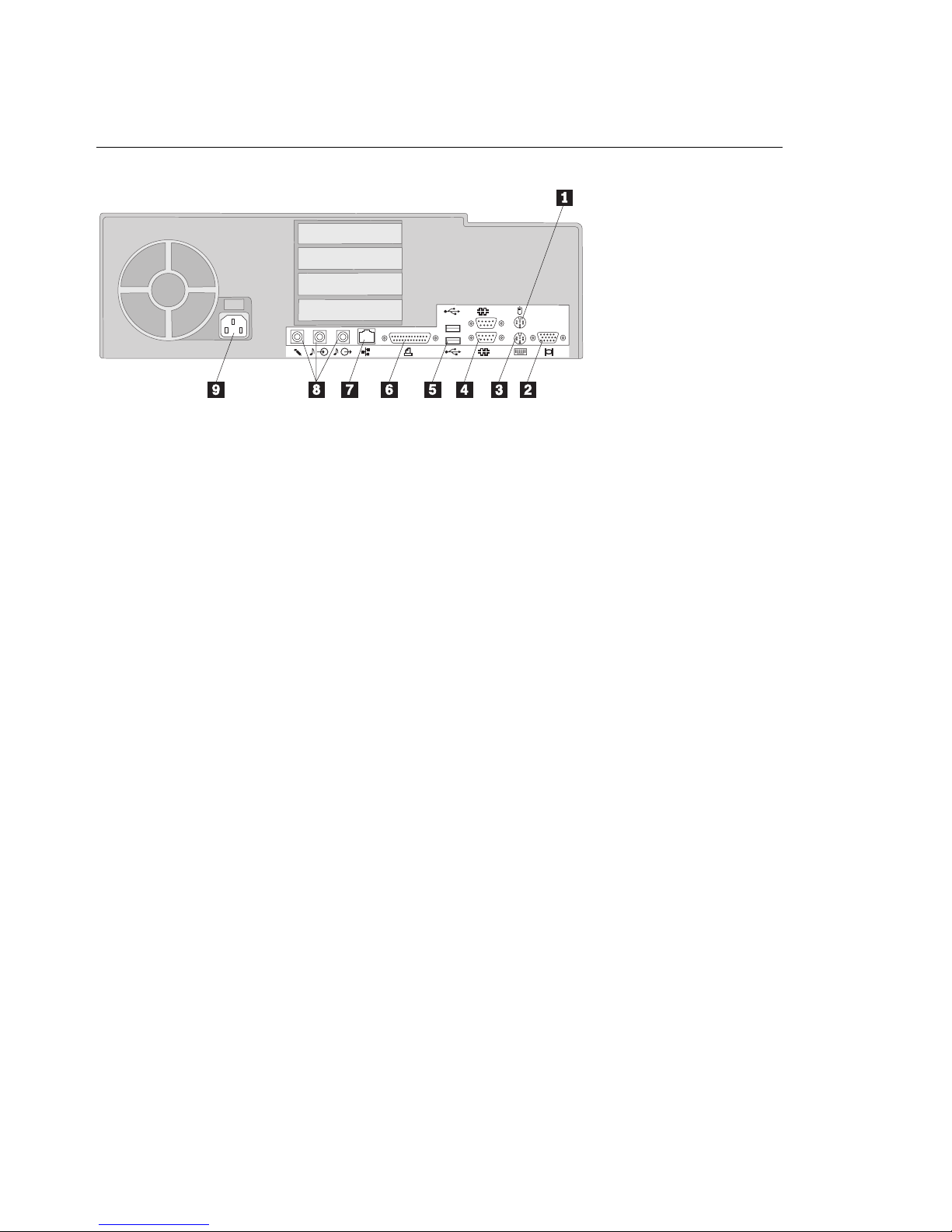
Tower model: The following illustration shows the location of the external
connectors on the rear of the tower model.
2
2
1
1
Monitor
USB 2
Parallel
Line In
Microphone
PL
Models
Only
Ethernet
Line Out
Keyboard
Mouse
Serial 1
Serial 2
USB 1
Yellow
LED
Green
LED
Note: Models equipped with a SCSI adapter have an external connector for
connecting SCSI devices. See the SCSI documentation provided with your
computer for more information.
Service and support
You can obtain assistance and service, from a number of sources. Help is available
on the World Wide Web and by phone, fax, and modem. For detailed information,
see Chapter 8, “Getting help, service, and information” on page 141.
Chapter 1. Your IBM personal computer 15
Page 34

Features at a glance
IBM PC 300GL Model features:
Microprocessor
Either an Intel Pentium II processor with
MMX technology with 66 and 100MHz FSB,
and Intel Pentium III processor with MMX
technology and 100MHz FSB, or an Intel
Celeron processor with MMX technology with
66MHz FSB
Either 512 KB L2 cache with ECC (Pentium
II-equipped models) or 128 KB L2 cache with
ECC (Celeron-equipped models)
System memory
Depending on the model, either two or three
168-pin DIMM sockets, 3.3 V
Models with two DIMM sockets expandable
to 256 MB; models with three DIMM sockets
expandable to 384 MB
ECC and nonparity SDRAM supported on
most models (some systems with Intel Celeron
do not support ECC)
100 MHz DIMMs supported
Diskette drive
One 3.5-inch, 1.44 MB drive is standard
Supports one diskette drive
Hard disk drive
Standard: One EIDE bus-master
SMART response Ultra DMA
CD-ROM drive
High-speed IDE CD-ROM drive (standard in
some models)
Mouse
Two-button
Network connection (some models only)
Intel 10/100 Ethernet
Wake on LAN
DHCP and RPL support
Graphics
AGP technology
S3 Trio3D
2 MB SGRAM (4 MB maximum)
2 MB upgrade option
Keyboard
104-key keyboard
Input/output features
ECP/EPP parallel port
Two serial ports
Two USB ports
Mouse port
Keyboard port
Monitor port
RJ-45 Ethernet port (optional)
Token Ring port (optional)
Audio subsystem (some models only)
Universal Manageability
System Xtra
Wake on LAN
Wake on Ring
Wake on Alarm
Year 2000 Ready
DMI BIOS
Asset security
Power-on password
Startup sequence control
Optional keylock
Security U-bolt option
Power
145 or 200 W, 115/230 V ac, 50/60 Hz
Built-in overload and surge protection
Power management features
Wake on LAN enabled
Note: View the System Summary screen within
the Configuration/Setup Utility program
to see the actual configuration of your
computer model (see “Viewing the system
summary” on page 66).
16 Using Your Personal Computer
Page 35

IBM PC 300PL model features:
Microprocessor
Either an Intel Pentium II processor with
MMX technology with 66 and 100MHz FSB,
an Intel Celeron processor with MMX
technology with 66MHz FSB, or an Intel
Pentium III processor with 100/133MHz FSB.
Either 512 KB L2 cache with ECC (Pentium II
and Pentium III-equipped models) or 128 KB
L2 cache with ECC (Celeron-equipped
models)
System memory
Expandable to 384 MB
Three 168-pin DIMM sockets, 3.3 V
ECC and nonparity SDRAM supported
100 MHz DIMMs supported
Diskette drive
One 3.5-inch, 1.44 MB drive is standard
Supports one diskette drive
Hard disk drive
Standard: One EIDE bus-master
SMART Response Ultra DMA
Ultra SCSI (Fast/Wide) on some models
CD-ROM drive
40X Max IDE CD-ROM drive in some models
Mouse
ScrollPoint
Network connection
Intel Ether Express Pro/100B
10 Base-T and 100-BaseTX connectivity
Wake on LAN
DHCP and RPL support
Graphics
AGP technology
S3 Trio3D
4 MB SGRAM
AGP expansion slot on system board
Some models might have an AGP 2X Matrox
Millennium G200, SR 9 with S3 Savage4
adapter, or other AGP video adapter
Keyboard
104-key keyboard
Audio subsystem
Integrated Crystal 4235 audio subsystem
SoundBlaster application support
Input/output features
ECP/EPP parallel port
Two serial ports
Two USB ports
Mouse port
Keyboard port
Monitor port
Microphone jack
Audio line-out jack
Audio line-in jack
RJ-45 Ethernet port
Universal Manageability
System Xtra
Wake on LAN
Wake on Ring
Wake on Alarm
Update POST/BIOS over the network
Remote reset from the network
Year 2000 Ready
Alert on LAN
DMI BIOS
Asset ID
System management controller
Asset Security
Enhanced security
Power-on administrator passwords
Startup sequence control
Alert on LAN
Asset ID
Security U-bolt option
Cover lock
Chassis-intrusion detector
Power
145 or 200 W, 115/230 V ac, 50/60 Hz
Built-in overload and surge protection
Power management features
Wake on LAN enabled
Note: View the System Summary screen within
the Configuration/Setup Utility program
to see the actual configuration of your
computer model (see “Viewing the system
summary” on page 66).
Chapter 1. Your IBM personal computer 17
Page 36

System specifications
System specifications are provided to assist you with the setup of your computer.
Desktop model
Dimensions
Height: 128 mm (5.0 in.)
Width: 450 mm (17.7 in.)
Depth: 440 mm (17.7 in.)
Weight
Minimum configuration as shipped: 9.9 kg
(22 lb)
Maximum configuration: 11.3 kg (25 lb)
Environment
Air temperature:
– System on: 10° to 32°C (50° to 90°F)
– System off: 10° to 43°C (50° to 110°F)
Humidity:
– System on: 8% to 80%
– System off: 8% to 80%
Maximum altitude: 2134 m (7000 ft)
Electrical input
Sine-wave input (50 to 60 Hz) is required
Input voltage:
– Low range:
- Minimum: 90 V ac
- Maximum: 137 V ac
- Voltage switch setting: 115 or 115 V
– High range:
- Minimum: 180 V ac
- Maximum: 265 V ac
- Voltage switch setting: 230 or 230 V
– Input kilovolt-amperes (kVA)
(approximately):
- Minimum configuration as shipped:
0.08 kVA
- Maximum configuration: 0.52 kVA
Note: Power consumption and heat output
vary depending on the number and
type of optional features installed and
the power management optional
features in use.
Heat output
Approximate heat output in British thermal
units (Btu) per hour:
– Minimum configuration: 245 Btu/hr (70
watts)
– Maximum configuration: 700 Btu/hr (204
watts)
Airflow
Approximately 0.56 cubic meters per minute
(20 cubic feet per minute)
Acoustical noise-emission values
Average sound-pressure levels:
– At operator position:
- Idle: PC 300PL - 34 dBA
PC 300GL - 35 dBA
- Operating: PC 300PL - 41 dBA
PC 300GL - 42 dBA
– At bystander position–1 meter (3.3 ft):
- Idle: PC 300PL - 29 dBA
PC 300GL 31 dBA
- Operating: PC 300PL - 34 dBA
PC 300GL - 36 dBA
Declared (upper limit) sound power levels:
– Idle: PC 300PL - 4.5 bels
PC 300GL - 4.7 bels
– Operating: PC 300PL - 5.0 bels
PC 300GL - 5.1 bels
Note: These levels were measured in
controlled acoustical environments according
to procedures specified by the American
National Standards Institute (ANSI) S12.10
and ISO 7779, and are reported in accordance
with ISO 9296. Actual sound-pressure levels
in your location might exceed the average
values stated because of room reflections and
other nearby noise sources. The declared
sound power levels indicate an upper limit,
below which a large number of computers
will operate.
18 Using Your Personal Computer
Page 37

Tower model
Dimensions
Height: 492 mm (19.4 in.)
Width: 200 mm (7.9 in.)
Depth: 445 mm (17.5 in.)
Weight
Minimum configuration as shipped: 15 kg (33
lb)
Maximum configuration: 17.3 kg (38 lb)
Environment
Air temperature:
– System on: 10° to 32°C (50° to 90°F)
– System off: 10° to 43°C (50° to 110°F)
Humidity:
– System on: 8% to 80%
– System off: 8% to 80%
Maximum altitude: 2134 m (7000 ft)
Electrical input
Sine-wave input (50 to 60 Hz) is required
Input voltage:
– Low range:
- Minimum: 90 V ac
- Maximum: 137 V ac
- Voltage switch setting: 115 or 115 V
– High range:
- Minimum: 180 V ac
- Maximum: 265 V ac
- Voltage switch setting: 230 or 230 V
– Input kilovolt-amperes (kVA)
(approximately):
- Minimum configuration as shipped:
0.08 kVA
- Maximum configuration: 0.51 kVA
Note: Power consumption and heat output
vary depending on the number and
type of optional features installed and
the power management optional
features in use.
Heat output
Approximate heat output in British thermal
units (Btu) per hour:
– Minimum configuration: 245 Btu/hr (70
watts)
– Maximum configuration: 969 Btu/hr (285
watts)
Airflow
Approximately 0.56 cubic meters per minute
(20 cubic feet per minute)
Acoustical noise-emission values
Average sound-pressure levels:
– At operator position:
- Idle: PC 300PL - 33 dBA
PC 300GL - 36 dBA
- Operating: PC 300PL - 35 dBA
PC 300GL - 37 dBA
– At bystander position–1 meter (3.3 ft):
- Idle: PC 300PL - 29 dBA
PC 300GL - 30 dBA
- Operating: PC 300PL - 32 dBA
PC 300GL - 33 dBA
– Declared (upper limit) sound power
levels:
- Idle: PC 300PL - 4.5 bels
PC 300GL - 4.7 bels
- Operating: PC 300PL - 4.8 bels
PC 300GL - 4.9 bels
Note: These levels were measured in
controlled acoustical environments according
to procedures specified by the American
National Standards Institute (ANSI) S12.10
and ISO 7779, and are reported in accordance
with ISO 9296. Actual sound-pressure levels
in your location might exceed the average
values stated because of room reflections and
other nearby noise sources. The declared
sound power levels indicate an upper limit,
below which a large number of computers
will operate.
Chapter 1. Your IBM personal computer 19
Page 38

20 Using Your Personal Computer
Page 39

Chapter 2. Setting Up Your Computer
This section provides information for connecting cables to your computer and
turning on the power.
Before You Begin
Read the “Safety Information” on page ix before setting up your computer.
You will need the following:
Computer
Computer power cord
Keyboard
Mouse
Monitor (sold separately with signal cable and power cord)
If you are missing an item, contact your place of purchase.
Installing options?
Set up and start your computer before installing any internal options (such as
memory or an adapter). Refer to Installing Options in Your PC for option installation
instructions.
Important: Be sure that you set up any additional devices according to the
manufactures instructions before you attach their cables to the connectors.
Selecting a location
Make sure you have an adequate number of properly grounded outlets for the
computer, monitor, and any other devices. Select a location for the computer where
it will remain dry. Leave about 50 mm (2 in.) of space around the computer for
proper air circulation.
For information about arranging your computer for comfort and ease-of-use, refer to
Chapter 3, “Arranging your workspace” on page 27.
Copyright IBM Corp. 1999 21
Page 40

Setting up the computer (Tower Model)
2
2
1
1
Mouse .1/
Monitor .2/
Keyboard .3/
Serial device/modem .4/
USB port .5/
Parallel printer .6/
Ethernet .7/
Audio (Microphone, Line
in, Line out)
.8/
Power cord .9/
22 Using Your Personal Computer
Page 41

Important information:
If there is a label covering the power connector, remove it. Connect the power
cords to the computer, monitor, and other devices first, then plug the cords into
properly grounded electrical outlets.
When the power cord is first plugged in, the computer powers on for a few
seconds, then powers off. This is normal operation.
In some circumstances, the computer might not power off immediately when
the power switch is pressed. In this case, hold the power switch down until the
power turns off.
Chapter 2. Setting Up Your Computer 23
Page 42
Setting up the computer (desktop model)
22
1
.1/ Mouse
.2/ Monitor
.3/ Keyboard
.4/ Serial device/modem
.5/ USB port
.6/ Parallel printer
.7/ Ethernet
.8/ Audio (microphone, line in, line out)
.9/ Power cord
24 Using Your Personal Computer
Page 43

Important information:
If there is a label covering the power connector, remove it. Connect the power
cords to the computer, monitor, and other devices first, then plug the cords into
properly grounded electrical outlets.
When the power cord is first plugged in, the computer powers on for a few
seconds, then powers off. This is normal operation.
In some circumstances, the computer might not power off immediately when
the power switch is pressed. In this case, hold the power switch down until the
power turns off.
Chapter 2. Setting Up Your Computer 25
Page 44

Turn on power
Turn on the monitor and other external devices first, and then turn on the
computer. You see a logo screen while the computer performs a short self-test.
Upon successful completion the logo screen disappears, the BIOS is loaded, and the
software is loaded (in models with preinstalled software).
Note: If you suspect a problem see Chapter 7, “Solving problems” on page 103.
Finish the Installation
Your computer has identification numbers (serial and type/model) that you might
need if you ever have your computer serviced. To locate these numbers, and record
this information, see Appendix A, “Computer records” on page 151.
See “Related publications” on page xv for sources of other information about your
computer.
For information about IBM-installed software, see About Your Software in your
applications package. Additional programs and device drivers are on the IBM
Ready-to-Configure Utility Program CD or the IBM Software Selections CD and in some
cases on other CDs and diskettes. If you are installing your own operating system,
make sure you install the device drivers after you install your operating system.
Installation instructions are provided with the media or README files on the
diskettes or CDs.
26 Using Your Personal Computer
Page 45

Chapter 3. Arranging your workspace
To get the most from your computer, arrange both the equipment you use and your
work area to suit your needs and the kind of work you do. Your comfort is of
foremost importance, but light sources, air circulation, and the location of electrical
outlets also can affect the way you arrange your workspace.
Comfort
Although no single working position is ideal for everyone, here are a few guidelines
to help you find a position that suits you best.
Sitting in the same position for a long time causes fatigue. A good chair can make a
big difference. The backrest and seat should adjust independently and provide
good support. The seat should have a curved front to relieve pressure on the
thighs. Adjust the seat so that your thighs are parallel to the floor and your feet are
either flat on the floor or on a footrest.
When using the keyboard, keep your forearms parallel to the floor and your wrists
in a neutral, comfortable position. Try to keep a light touch on the keyboard and
your hands and fingers relaxed. You can change the angle of the keyboard for
maximum comfort by adjusting the position of the keyboard feet.
Viewing Distance
Lower
Back
Support
Seat
Height
Adjust the monitor so the top of the screen is at, or slightly below, eye level. Place
the monitor at a comfortable viewing distance, usually 51 to 61 cm (20 to 24 in.),
and position it so you can view it without having to twist your body.
Copyright IBM Corp. 1999 27
Page 46

Glare and lighting
Position the monitor to minimize glare and reflections from overhead lights,
windows, and other light sources. Place the monitor at right angles to windows
and other light sources, when possible. Reduce overhead lighting, if necessary, by
turning off lights or using lower wattage bulbs. If you install the monitor near a
window, use curtains or blinds to block the sunlight. You might have to adjust the
Brightness and Contrast controls on the monitor as the room lighting changes
throughout the day.
Where it is impossible to avoid reflections or to adjust the lighting, an antiglare
filter placed over the screen might be helpful. However, these filters might affect
the clarity of the image on the screen; try them only after you have exhausted other
methods of reducing glare.
Dust buildup compounds problems associated with glare. Remember to clean your
monitor screen periodically using a soft cloth moistened with a nonabrasive liquid
glass cleaner.
Air circulation
Your computer and monitor produce heat. The computer has a fan that pulls in
fresh air and forces out hot air. The monitor lets hot air escape through vents.
Blocking the air vents can cause overheating, which might result in a malfunction or
damage. Place the computer and monitor so that nothing blocks the air vents;
usually, 51 mm (2 in.) of air space is sufficient. Also, make sure the vented air is
not blowing on someone else.
Electrical outlets and cable lengths
The location of electrical outlets and the length of power cords and cables that
connect to the monitor, printer, and other devices might determine the final
placement of your computer.
When arranging your workspace:
Avoid the use of extension cords. When possible, plug the computer power
cord directly into an electrical outlet.
Keep power cords and cables neatly routed away from walkways and other
areas where they might get kicked accidentally.
For more information about power cords, see “Power cord notice” on page 181.
28 Using Your Personal Computer
Page 47

Chapter 4. Operating your computer
This chapter provides information to help you in the day-to-day use of your
computer. It includes instructions for starting and shutting down your computer, as
well as information on using audio, video, system management, and security
features.
Using controls and status indicators
Look at the front of your computer. The buttons are controls that allow you to
perform a specific function, such as powering on the computer. The lights are
status indicators that tell you when a certain function, such as the diskette drive, is
in use.
Note: If your computer has a preinstalled CD-ROM drive, controls and status
indicators for the CD-ROM drive are available. For more information, see
“Using a CD-ROM drive” on page 40.
The following illustrations show the controls and status indicators for both models.
Descriptions of the controls and status indicators are on the next page.
Power Switch
Power-On Light
Hard-Disk
Drive Light
Client
(Workstation)
LAN Light
Diskette
Drive Light
Diskette
Eject Button
Desktop model
Copyright IBM Corp. 1999 29
Page 48

Socket7
Socket7
Hard-Disk
Drive Light
Diskette
Drive Light
Diskette
Eject Button
Client (Workstation)
LAN Light
Power Switch
Power-On Light
Tower model
The following list describes the controls and status indicators for your computer.
Power switch: Press this switch to turn your computer on or off. Do not turn
off your computer if the in-use light for the hard disk drive or diskette drive is
on.
Note: The power switch normally operates with a single touch. However, in
some circumstances the computer might not immediately power off. If
this happens, hold the power switch down for approximately 5 seconds,
and the computer will then power off.
Power-on light: This status indicator lights when you turn on your computer.
Hard disk drive light: When this light is on, it indicates that the hard disk
drive heads are being positioned or that your computer is reading from or
writing to the hard disk.
Client (Workstation) LAN Light: This light indicates network activity and is
present on models with integrated Ethernet only.
Diskette Eject Button: Push this button to release a diskette from the drive.
Diskette-Drive Light: When this light is on, it indicates that the diskette drive
heads are being positioned or that your computer is reading from or writing to
a diskette.
30 Using Your Personal Computer
Page 49

Starting your computer - PC 300GL
Before you begin
Please observe the following:
When the power cord is first plugged in, the computer appears to power on
for a few seconds, and then power off. This is a normal sequence to enable
the computer to self initialize.
What you see and hear when you start up your computer depends on
settings in the Configuration/Setup Utility program. See “Settings that
affect the startup procedure” on page 35 for more information.
To start the PC 300GL:
1. Turn on all devices connected to the computer.
2. Press and release the power switch on your computer. If you have not changed
any settings in the Configuration/Setup Utility program, including setting a
password, the following actions occur:
2
The video BIOS is initialized.
The IBM logo appears on the screen.
The power-on self-test (POST) is performed. If POST detects a problem, you
hear multiple beeps (or no beep) and an error message appears on the
screen. If POST does not detect a problem, you hear a single beep. Write
down any error code numbers and descriptions, and check for the error
code number in Chapter 7, “Solving problems” on page 103.
The computer allows you to enter the Configuration/Setup Utility program
(by pressing F1) or run a fast POST (by pressing Esc).
3. Listen for a beep, and the first screen of the operating system or application
program appears.
2
If you have changed settings for features (such as passwords or the startup sequence) in the
Configuration/Setup Utility program, see “Settings that affect the startup procedure” on page 35 for
important information.
Chapter 4. Operating your computer
31
Page 50

Starting your computer - PC 300PL
Before you begin
Please observe the following:
When the power cord is first plugged in, the computer appears to power on
for a few seconds, and then power off. This is a normal sequence to enable
the computer to self initialize.
What you see and hear when you start up your computer depends upon
settings in the Configuration/Setup Utility program. See “Settings that
affect the startup procedure” on page 35 for more information.
If you plan to start your computer over a network, see “Starting your
computer over a network” on page 36.
To start the PC 300PL:
1. Turn on all devices connected to the computer.
2. Press and release the power switch on your computer. If you have not changed
any settings in the Configuration/Setup Utility program, the following actions
occur:
3
The video BIOS is installed.
The IBM logo appears on the screen.
The power-on self-test (POST) is performed. If POST detects a problem, you
hear multiple beeps (or no beep) and an error message appears on the
screen. Write down any error code numbers and descriptions.
The computer allows you to enter the Configuration/Setup Utility program
(by pressing F1) or run a fast POST (by pressing Esc).
If you have a SCSI model, the SCSI BIOS is installed.
3. A DHCP (Dynamic Host Configuration Protocol) request is sent to the network,
and one of the following events occurs:
If you are properly connected to a network, a DHCP server dynamically
assigns an IP (Internet protocol) address to your computer and then loads a
startup image onto your computer.
3
If you have changed settings for features (such as passwords or the startup sequence) in the
Configuration/Setup Utility program, see “Settings that affect the startup procedure” on page 35 for
important information.
32 Using Your Personal Computer
Page 51

If the DHCP request is unsuccessful, the following message appears:
No IP address found for DHCP or BOOTP
and the operating system and application programs are loaded from the
hard disk drive.
If you have not plugged an Ethernet cable into the Ethernet connection on
your computer, the following message appears:
Media test failed; check cable
and the operating system and application programs are loaded from the
hard disk drive.
Startup sequence information
In keeping with IBM's commitment to provide computers designed to enhance
network manageability and control, the startup sequence of your computer has been
preset to automatically send a DHCP request when your computer starts. This
feature makes it easier for a network administrator to set up and manage computers
using network-management software such as IBM LANClient Control Manager (see
“Information for network administrators” on page 34).
With the preset startup sequence, when you start your computer with the Ethernet
cable attached and no startup diskette in the diskette drive, your computer sends a
DHCP request over the network. If the DHCP request is successful, an IP address is
assigned to your computer, and the operating system and other software is loaded.
The PC 300PL is shipped with this preset startup sequence:
First startup device [Diskette drive]
Second startup device [Network]
Third startup device [Hard disk drive]
Fourth startup device [Disabled]
If you want to change the startup-sequence settings for your computer, such as
removing Network from the startup sequence, see “Setting the startup sequence” on
page 75.
Note: The preceding startup sequence is not the default startup sequence for your
computer. If you change the settings in the Configuration/Setup Utility
program to default, the preceding settings will change.
Chapter 4. Operating your computer 33
Page 52

If you load the Default settings or if you move the Clear CMOS Request
jumper, the default settings for the startup sequence are shown here:
First startup device [Diskette drive]
Second startup device [Hard disk drive]
Third startup device [Network]
Fourth startup device [Disabled]
Your computer also supports RPL (remote program load), which you can select
instead of DHCP for the network startup of the integrated Ethernet. For more
information, see “Built-in network protocols” on page 51.
Information for network administrators
IBM LANClient Control Manager (LCCM) is a new class of PC-management
software for Windows NT servers. LCCM is an easy-to-use, graphical, server-based
application that supports the setup and management of IBM PCs over a network.
For more on LCCM, visit our Web site at:
http://www.ibm.com/pc/us/desktop/lccm/
34 Using Your Personal Computer
Page 53
Settings that affect the startup procedure
Settings for the following features in the Configuration/Setup Utility program can
affect the startup procedure for your computer:
Start Options, including the startup sequence, power-on status, power-on
self-test.
Security options, including the administrator and power-on passwords. For
more information, see “System Security” on page 87, “Using a power-on
password” on page 67, and “Using an administrator password” on page 71.
For more information on these settings, see Chapter 5, “Using the
Configuration/Setup Utility program” on page 61.
Important
If Power-On Self-Test is set to Enhanced, information about memory
configuration and test results are shown in the upper-left corner. Options for
running a quick POST or accessing the Configuration/Setup Utility program
appear in the lower-left corner of the screen. Quick mode is the default mode of
operation.
Note: The amount of available memory shown might be somewhat less than
expected because of basic input/output system (BIOS) shadowing in
random access memory (RAM).
If POST finishes without detecting any problems, the first screen of your
operating system or application program appears (if you have not set a
power-on password). If you have set a power-on password, a password prompt
appears. You must enter your password before the first screen of your
operating system or application program will appear.
If Power On Status is set to Enabled and POST detects a problem, you will hear
multiple beeps or no beep. In most cases, an error code appears in the top left
corner of the screen, and in some cases a description of the error is displayed
beside the code. (Note that the screen will sometimes display multiple error
codes and descriptions.) For more information about what caused an error
message to appear and what action to take, refer to “Solving POST error
message problems” on page 105 and “POST message charts” on page 108.
If you have enabled Power On status and you hear no beep at all during POST,
refer to “Troubleshooting charts” on page 126. You might need to have your
computer serviced.
Chapter 4. Operating your computer 35
Page 54

Starting your computer over a network
Your computer can "wake up" and be started remotely over a network if it has a
properly configured network connection to either the integrated Ethernet or a
network adapter with Wake on LAN.
4
For more information, see “Wake on LAN” on page 48 and “Setting the startup
sequence” on page 75.
Shutting down your computer
When you are ready to turn off your computer, follow the shutdown procedure for
your operating system to prevent the loss of unsaved data or damage to your
software programs. See your operating-system documentation for instructions.
Some operating systems allow you to set up the computer to automatically turn off
after the operating system has shut down. If you are not using this feature, you
must manually turn off the computer by pressing and releasing the power switch.
Important
Please observe the following:
If you plan to restart your computer, do not press Ctrl+Alt+Del to shut
down the computer while the operating system is running. Instead, follow
the shutdown procedure for your operating system, turn off the computer by
pressing and releasing the power switch, wait a few seconds until all the
status-indicator lights are off, and then restart your computer.
The power switch normally operates with a quick touch. However, in some
circumstances the computer might not immediately power off with a quick
touch. If this happens, hold the power switch down for approximately five
seconds, and the computer will then power off.
4
The integrated Ethernet feature is standard on some models only.
36 Using Your Personal Computer
Page 55

Using mouse features
A mouse is a device that you use to point to and select objects on the monitor screen.
Your computer comes with either a two-button mouse or the IBM ScrollPoint
Mouse. The ScrollPoint Mouse has two buttons and a mouse stick that allows you to
move within a document without having to use scroll bars (see “Using the
ScrollPoint mouse” on page 38).
The mouse that comes with your computer attaches with a cable to the PS/2 mouse
connector on the back of the computer.
Note: A mouse device designed to be used through a serial port or USB connection
can also be used with your computer.
Mouse basics
This section discusses using a mouse with two buttons. If a ScrollPoint mouse came
with your computer, use this section and also see “Using the ScrollPoint mouse” on
page 38.
Note: If you have never used a mouse before, it might feel a bit awkward at first.
However, with a little practice, the mouse movements will become more
natural.
To set up the mouse, place the mouse beside the keyboard on a flat surface or mouse
pad. A mouse pad is a flat, smooth foam-rubber pad available at most computer
stores. The mouse has a ball on the bottom, so working on a flat, smooth surface is
important. Most operating systems allow you to configure the mouse buttons for
either right-hand or left-hand operation. The mouse that comes with your computer
has two buttons, and when it is configured for right-handed user, the left button is
used for most tasks. When a mouse with two buttons is configured for a
left-handed user, the right button is used for most tasks. For more information, see
your operating system documentation.
To use the mouse, slide it from side to side and forward and backward over a flat
surface. When you see an item that you want to select on the screen, simply move
the pointer to that item (this is called pointing), and press and release either the left
or right button on the mouse (this is called clicking).
Chapter 4. Operating your computer 37
Page 56

To learn how to use the mouse with the software in your computer, see the
documentation accompanying the software. Some programs support only one
mouse button, others support two, and some support three. Despite the differences,
some terms are fairly standard throughout the industry.
Point Move the mouse so the pointer is on the object you want.
Click Press and release the mouse button once.
Double-click Rapidly press and release the mouse button twice.
Drag Point to an object, press the mouse button, and hold it down
as you move the mouse to relocate the object.
Drop After dragging an object to a new location, release the mouse
button.
Using the ScrollPoint mouse
The IBM ScrollPoint Mouse included with some computers is a full-function mouse
that you can use to point and select objects on the screen. The ScrollPoint Mouse
also provides a mini-stick navigator that you can use to scroll in any direction
without using scroll bars. This feature is particularly useful when you are viewing
Web pages, large documents, and spreadsheets.
If your computer has preinstalled software, the device drivers for the ScrollPoint
Mouse are already installed on the hard disk. Also, software is provided that you
can use to program the buttons and mini-stick with different functions , such as:
Zoom, which you can use to increase or decrease the size of an image
HyperJump and CyberJump, which enable a pop-up menu of tools and
shortcuts
For more information on programming the buttons and mini-stick, see the online
documentation provided with the application. Also, information about the
ScrollPoint Mouse is located on the World Wide Web at:
http://www.ibm.com/pc/us/ibmhome/scrollpoint/
38 Using Your Personal Computer
Page 57

Using audio features
Note: The following information applies to all PC 300PL computers and PC 300GL
computers equipped with a preinstalled audio adapters.
With the audio feature of your computer, you can play and record sound and
music. The audio controller supports SoundBlaster applications and is compatible
with the Microsoft Windows Sound System. The following ports are available at the
rear of the computer. The audio ports are 3.5 mm (1/8") mini-jacks.
Microphone or MIC: This audio port is used to connect a microphone to your
computer when you want to record voice or other sounds. This port can also be
used by speech recognition software.
Note: If you experience interference or speaker feedback while recording, try
reducing the microphone recording volume (gain).
Audio Line In or LINE IN: This audio port is used to send audio signals from
an external device (such as a CD player or stereo) to your computer so that the
signals can be recorded on the computer. (Use the audio mixer software
provided in your operating system to set the input level accordingly.)
Audio Line Out or OUT: This audio port is used to send audio signals from the
computer to stereo external devices, such as powered speakers with built-in
amplifiers, headphones, multimedia keyboards, or the Audio Line-In connector
on a stereo system.
Game/MIDI (PC 300GL models only): The Game/MIDI (musical instrument
digital interface) port can be used to connect a game control or musical device
such as an electronic keyboard. (The devices might require and optional
adapter cable. See the information provided with the device for more
information.)
Note: The internal speaker in your computer is disabled when an external
speaker is connected to the Line-Out port on your computer.
Procedures for playing and recording sound vary by operating system. Refer to
your operating system documentation for information and instructions.
Chapter 4. Operating your computer 39
Page 58

Using a CD-ROM drive
Some models come with a preinstalled CD-ROM drive. CD-ROM (compact disc
read-only memory) technology offers quick access to large amounts of information.
A compact disc can store more than 650 MB of data, such as the large files needed
for audio, still and full-motion video, and still and animated graphics. A CD-ROM
drive can play back or read from a CD, but it cannot write information to it.
CD-ROM drives use industry-standard, 12 cm (4.75-inch) CDs.
Follow these guidelines when using a CD-ROM drive:
Do not place the drive where there is:
– High temperature
– High humidity
– Excessive dust
– Excessive vibration or sudden shock
– An inclined surface
– Direct sunlight
Do not insert any object other than a CD into the drive.
Before moving the computer, remove the CD from the drive.
The following illustration shows the front bezel of the CD-ROM drive in the tower
model. A CD-ROM in a desktop model has features similar to those shown below.
Socket7
Socket7
Eject/Load Button
Tray
Indicator Light
Emergency-Eject Hole
Note: If you have installed a CD-ROM drive yourself and need additional
information, refer to the documentation that comes with the drive.
40 Using Your Personal Computer
Page 59

Handling a CD
When handling a CD, follow these guidelines:
Hold the CD by its edges. Do not touch the surface.
To remove dust or fingerprints, wipe the CD from the center to the outside.
Wiping the CD in a circular direction might cause loss of data.
Do not write or stick paper on the CD.
Do not scratch or mark the CD.
Do not place or store the CD in direct sunlight.
Do not use benzene, thinners, or other cleaners to clean the CD.
Do not drop or bend the CD.
Loading a CD
To load a disk into a CD-ROM drive:
1. Press the Eject/Load button. The tray slides out of the drive. (Do not manually
force the tray open.)
2. Place the disk in the tray with the label facing up.
3. Close the tray by pressing the Eject/Load button, or by gently pushing the tray
forward. When the tray is closed, the indicator light on the front of the drive
will activate to indicate that the drive is in use.
4. To eject the disk, press the Eject/Load button. When the tray slides out,
carefully remove the disk.
5. Close the tray by pressing the Eject/Load button, or by gently pushing the tray
forward.
Note: If the tray does not slide out of the drive when you press the Eject/Load
button, insert the pointed end of a large paper clip into the emergency-eject
hole located above and to the left of the CD-ROM indicator light.
Chapter 4. Operating your computer 41
Page 60

Loading a CD into a vertically positioned desktop model
The instructions in this section are for desktop models that are placed in a vertical
position. If you have a desktop model and do not vertically position the computer,
use the instructions in “Loading a CD” on page 41 when using the CD-ROM drive.
Note: If you place the desktop model in a vertical position, use a floor stand to
prevent damage to the computer due to overheating. A floor stand is an
available option from IBM. Look for more information on the World Wide
Web at:
http://www.ibm.com/pc/us/options/
A CD-ROM drive in a vertically positioned desktop model is placed on its side. In
order to load a CD into the drive securely, you must use the specific support
mechanisms, such as extendable tabs or a support wire, provided with the drive.
There are several CD-ROM drives available for your computer. They are alike
except for the support mechanisms used to hold the CD in place when it is inserted
into the CD-ROM drive. Use the information on the following pages to identify the
CD-ROM drive in your computer and then use the accompanying instructions for
loading and unloading a CD.
Note: If the tray does not slide out of the drive when you press the Eject/Load
button, insert the pointed end of a large paper clip into the emergency-eject
hole located above and to the left of the CD-ROM indicator light.
42 Using Your Personal Computer
Page 61
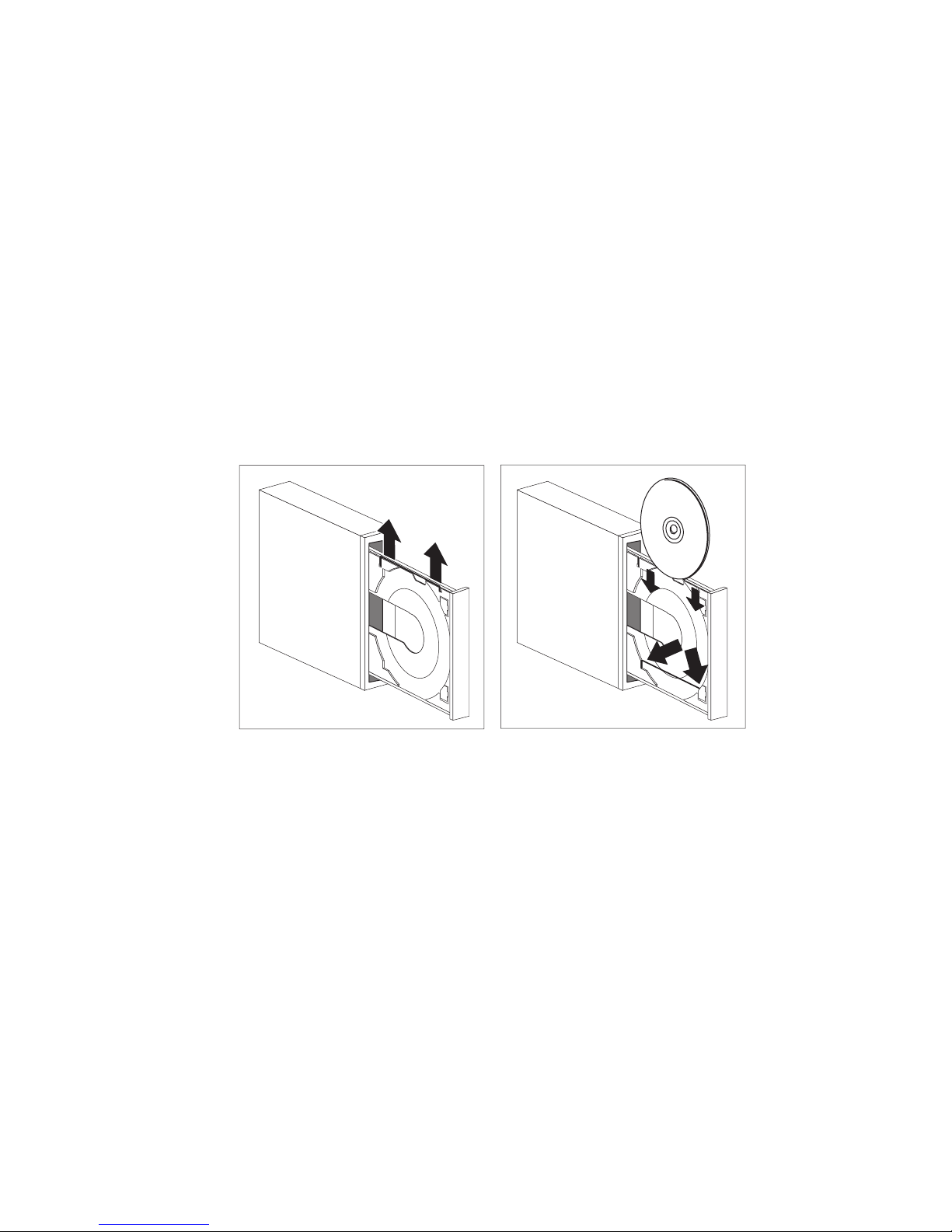
To load a CD into a CD-ROM drive with a support wire:
1. Press the Eject/Load button. The tray slides out of the drive. (Do not
manually force the tray open.)
2. Locate the wire that is installed in the right edge of the tray.
3. Gently flex the wire until you can remove each end from its socket.
4. Locate the two holes near the edge of the tray. (One hole is in the notch on
the inner end of the tray, and the other is in a spring-tab at the outer end.)
5. Insert the wire into the inner hole first, then flex the wire until you can
insert the other end of it into the spring-tab. When the wire is inserted
correctly, it is parallel to the edge of the tray and approximately 20 mm
(0.75 in.) in from the outside edge.
6. Because of the spring-tab, you can lift the support wire when you insert a
CD and let it hold the CD in place. Close the tray by pressing the
Eject/Load button, or by gently pushing the tray forward. When the tray is
closed, the indicator light on the front of the drive will activate to indicate
that the drive is in use.
7. To eject the CD, press the Eject/Load button. When the tray slides out,
carefully remove the CD. (If the wire on the tray is extended, retract it to
remove the CD.)
8. Close the tray by pressing the Eject/Load button, or by gently pushing the
tray forward.
Chapter 4. Operating your computer 43
Page 62
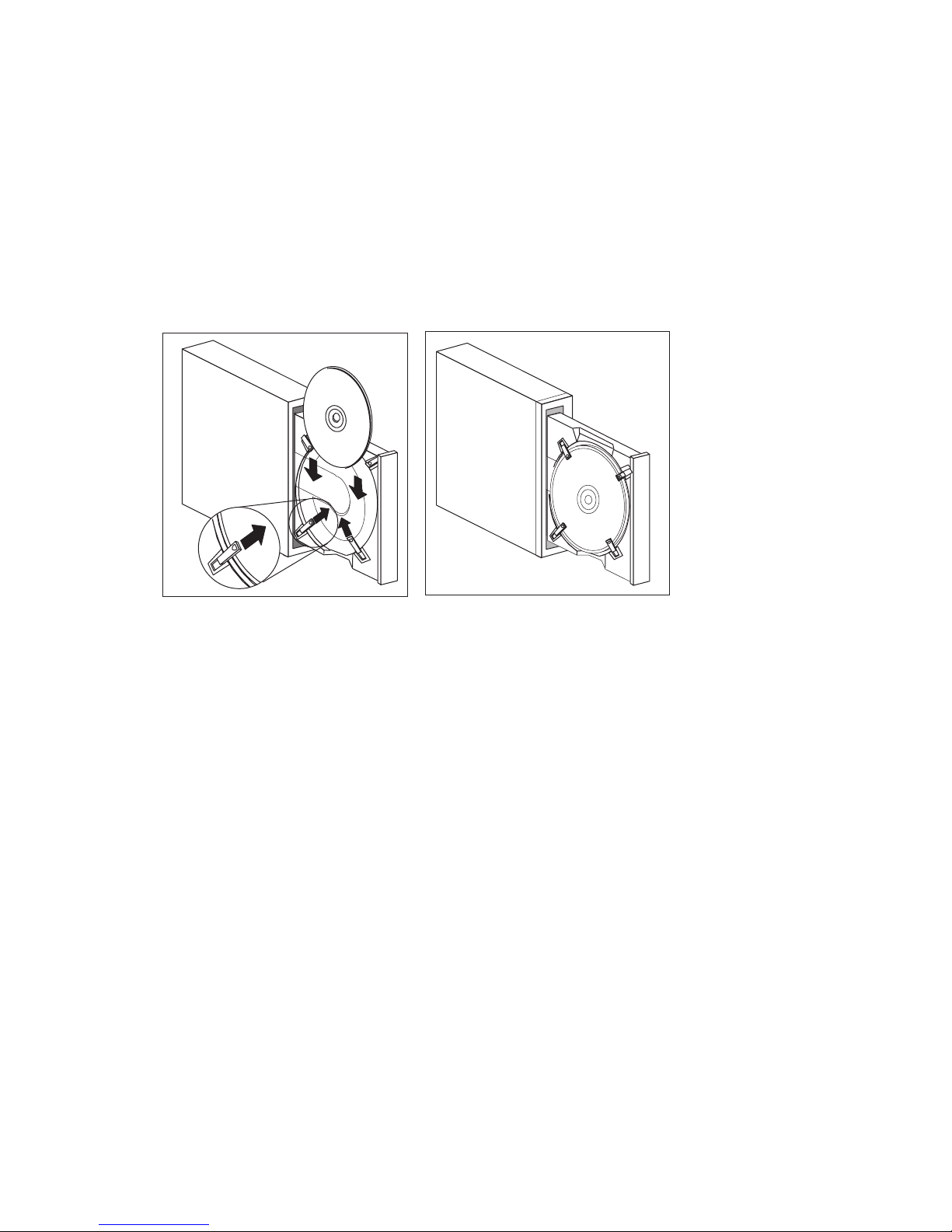
To load a CD into a CD-ROM with tabs that slide out:
1. Press the Eject/Load button. The tray slides out of the drive. (Do not
manually force the tray open.)
2. Extend the bottom two tabs on the tray.
3. Place the CD in the tray (with the label facing up) underneath the two
extended tabs, and hold the CD in place.
4. Close the tray by pressing the Eject/Load button, or by gently pushing the
tray forward. When the tray is closed, the indicator light on the front of the
drive will activate to indicate that the drive is in use.
5. To eject the CD, press the Eject/Load button. When the tray slides out,
retract the tabs to remove the CD.
6. Close the tray by pressing the Eject/Load button, or by gently pushing the
tray forward.
44 Using Your Personal Computer
Page 63
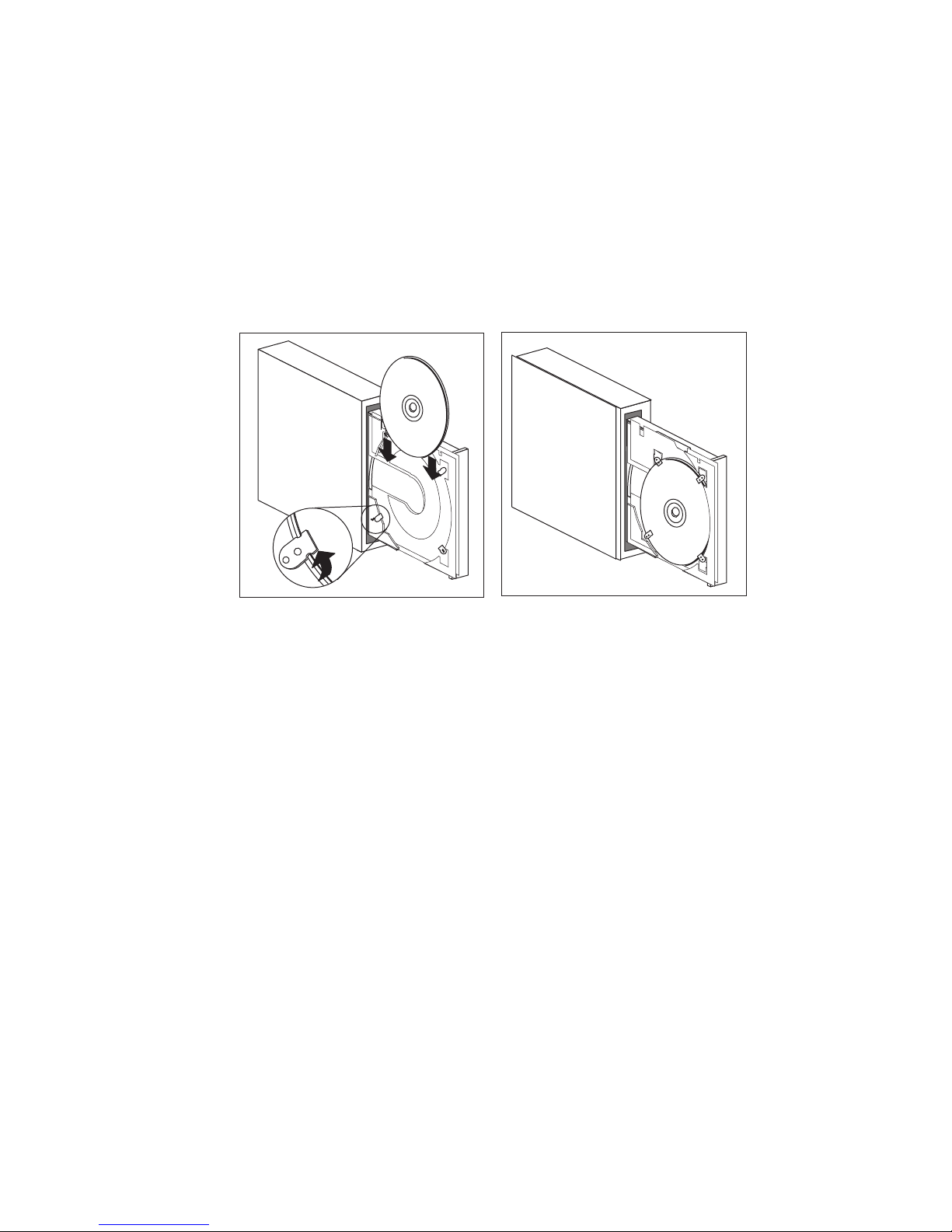
To load a CD into a CD-ROM with rotating tabs:
1. Press the Eject/Load button. The tray slides out of the drive. (Do not
manually force the tray open.)
2. Rotate the bottom two tabs on the tray.
3. Place the CD in the tray (with the label facing up) underneath the two
rotated tabs, and hold the CD in place.
4. Close the tray by pressing the Eject/Load button, or by gently pushing the
tray forward. When the tray is closed, the indicator light on the front of the
drive will activate to indicate that the drive is in use.
5. To eject the CD, press the Eject/Load button. When the tray slides out,
rotate the tabs to remove the CD.
6. Close the tray by pressing the Eject/Load button, or by gently pushing the
tray forward.
Chapter 4. Operating your computer 45
Page 64

Using video features
Your computer comes with an AGP SVGA (super video graphics array) controller.
SVGA is a video standard for displaying text and graphic images on a monitor
screen. Like other video standards, SVGA supports a variety of video modes. Video
modes are different combinations of resolution, refresh rate, and color depth defined
by a video standard for displaying text or graphics. (For general information on
video modes, refer to Understanding Your Personal Computer.)
Your computer provides support for 132 column modes. These are VESA modes
109 and 10A. SVGA provides higher-resolution graphics, faster refresh rates, and
more colors than previous video standards, such as video graphics array (VGA). At
the same time, SVGA supports all standard VGA modes.
To get the best possible image on your screen and to reduce flicker, you might need
to reset the resolution and refresh rate of your monitor. You can view and change
monitor settings through your operating system. Instructions for doing this are
included in a README file that is provided on the IBM Ready-to-Configure Utility
Program CD or the IBM Software Selections CD for your computer.
Refer to your operating system documentation for further information on monitor
settings.
Resolution Bits-per-Pixel Monitor Refresh Rate (Hz)
640 x 480 8/15/16/32 60/72/75/85
800 x 600 8/15/16/32 56/60/72/75/85
1024 x 768 8/15/16/32 43i5/60/70/75/85
1152 x 864 8/15/16 60/70/75/85
1280 x 1024 8/15/16 43i/60/75/85
1600 x 1200 8/15/16 48i/60/70/75/85
5
i denotes interlaced
46 Using Your Personal Computer
Page 65

Important
Before you change any monitor settings, be sure to review the information that
comes with your monitor. Using a resolution or refresh rate that is not
supported by your monitor might cause the screen to become unreadable and
damage the monitor. The information that comes with your monitor usually
includes the resolutions and refresh rates that the monitor supports. If you need
additional information, contact the manufacturer of the monitor.
To minimize screen flicker and jitter, set your monitor for the highest non-interlaced
refresh rate that the monitor supports. If your monitor complies with the VESA
Display Data Channel (DDC) standard, it is probably already set to the highest
refresh rate that the monitor and video controller can support. If you are not sure if
your monitor is DDC-compliant, refer to the documentation provided with the
monitor.
Video device drivers
To take full advantage of the video controller in your computer, some operating
systems and application programs require custom software, known as video device
drivers. These device drivers provide support for greater speed, higher resolution,
more available colors, and flicker-free images.
The video device drivers are provided on the Product Recovery for your computer.
Instructions for installing the device drivers are provided on the Software Selections
or Ready-to-Configure CD in the README file that corresponds to your operating
system. IBM also maintains the latest versions of video device drivers for all
IBM-manufactured computers on the World Wide Web.
If your computer has IBM-preinstalled software, video device drivers have already
been installed on the hard disk in your computer. However, the device driver
installation instructions in the README file will be helpful if you ever need to
reinstall the device drivers; if you want to change video resolution, color depth, or
monitor settings; or if you need information on obtaining and installing updated
device drivers.
Chapter 4. Operating your computer 47
Page 66

Using Universal Manageability features
Note: Although this section is intended primarily for network administrators, it
also provides useful information for the personal computer user.
This section describes system-management features that make it possible for a
network administrator to remotely manage and control the IBM personal computer
when it is linked to a network.
Universal Manageability is a general term for IBM hardware and software features
that provide enhanced value for a computer remotely managed over a network.
When used in conjunction with the appropriate network management software,
Universal Manageability features provide network administrators with the tools
necessary to remotely manage and monitor a networked computer. The Universal
Manageability features discussed in this section usually perform one or more of the
following functions:
Power on the computer
Monitor and relay system information about the computer
Track, control, and secure computer assets
Load software onto the computer
Note: In order to fully use some Universal Manageability features, additional
hardware or software (supplied by IBM or other manufacturers) might be
required.
IBM Universal Manageability tools streamline and automate PC systems
management and support tasks, such as asset deployment and tracking. These
leading-edge PC tools are available for IBM PCs at no additional charge, helping to
reduce Total Cost of Ownership of your networked PCs and allowing you to focus
vital company resources on essential business activities.
Wake on LAN
The Wake on LAN feature can be used by a network administrator to turn on your
computer remotely from an administrator console. When Wake on LAN is used in
conjunction with network-management software, such as TME 10 NetFinity, many
types of functions, such as data transfers, software updates, and POST and BIOS
updates can be performed remotely on your computer and other computers enabled
for Wake on LAN that are linked to your network. This updating can be done after
hours and on weekends, which saves time and increases productivity. Users are not
interrupted during normal working hours and LAN traffic is kept to a minimum.
Both the PC 300PL and PC 300GL support Wake on LAN. The PC 300PL has an
integrated Ethernet feature that has built-in support for Wake on LAN (and Alert on
48 Using Your Personal Computer
Page 67

LAN). Both the PC 300PL and PC 300GL support the installation of Wake on LAN
network adapters. For information on installing adapters, see Installing Options in
Your Personal Computer.
Note: If your computer has the integrated Ethernet feature, you can view the
Media Access Control (MAC) address through the Configuration/Setup
Utility program.
LANClient Control Manager (LCCM)
LANClient Control Manager is a graphical, server based program that aids in
system deployment by allowing mass unattended system installation of operating
systems, complete software images, device drivers, and BIOS updates. Used with
Wake on LAN, LCCM can remotely start up your system from a powered-off state,
which means all this can be done while the system is not being used. If you have
purchased an IBM PC, LCCM is available for download at no additional charge
(Internet access fees excepted).
For more information or to download this software visit:
http://www.ibm.com/pc/us/desktop/lccm
System Migration Assistant (SMA)
System Migration Assistant (SMA) delivers wizard-like functionality to help
administrators remotely transfer configurations, profile settings, printer drivers, and
files from an IBM or non-IBM PC to supported IBM systems. If you have purchased
an IBM PC, SMA is available for download at no additional charge (Internet access
fees excepted).
For more information or to download this software visit:
http://www.ibm.com/pc/us/software/sysmgmt/products/sma
Alert on LAN support
Note: The following information is for PC 300PL models only.
Support for Alert on LAN is built into your computer. Alert on LAN technology
provides notification of changes in the computer system even if the computer is
powered off. Working with DMI and Wake on LAN technologies, Alert on LAN
helps to manage and monitor the hardware and software features of your computer.
Examples of when Alert on LAN generates notifications are:
The computer cover has been removed
Internal computer components are removed
Chapter 4. Operating your computer 49
Page 68

POST fails during a Wake on LAN attempt
The computer is disconnected from the network or unplugged from the power
outlet
Alert on LAN can be integrated with network-management software such as Intel
LANDesk Client Manager and IBM Client Services for NetFinity Manager.
DMI BIOS
The BIOS (basic input output system) of your computer supports an interface called
DMI (Desktop Management Interface). DMI is software used to gather information
about the hardware and software in your computer so that network administrators
can remotely monitor and control your computer. DMI can be used to remotely
track many types of information about networked computers, including serial
numbers, memory attributes, product-specific characteristics of installed peripherals,
and operating system configuration information. This information can be accessed
using a DMI browser. DMI browsers are provided by all major operating systems
and all major LAN management packages (including TME 10 NetFinity, and Intel
LANDesk).
System management controller
Note: The following information is for some PC 300PL only.
Your computer is equipped with a system-management controller (LM80) integrated
with the system board. This controller provides hardware monitoring for
system-board temperatures, fan speed, power supply and processor voltages, and
the detection of the removal of the computer cover. Used with the DMI BIOS of the
computer, the system-management controller can also store the hardware test results
from the power-on self-test (POST).
Computers with preinstalled software can use this feature with the IBM PC System
Management software provided with the preinstalled software. Also, to view the
system-management information, use the NetFinity DMI browser that is provided
with your preinstalled software. For information on these software features, see
About Your Software.
50 Using Your Personal Computer
Page 69

A note about DMI
The BIOS (basic input output system) of your computer supports the Desktop
Management Interface (DMI). DMI provides an industry standard mechanism
for gathering system information so network administrators can remotely
monitor and control hardware and software components. DMI might be
compared to with other management interfaces such as Simple Network
Management Protocol (SNMP). DMI has the advantage of being supported
across all major operating systems and by all major network-management
packages, including TME 10 NetFinity and Intel LANDesk Client Manager.
Built-in network protocols
Note: The following information is for PC 300PL models only.
Networking features such as remote program load (RPL) and dynamic host
configuration protocol (DHCP) help a network administrator control your computer
remotely. The integrated Ethernet supports both of these features.
Contact your network administrator to determine how your computer should be
configured for your specific network environment.
Asset ID capability
Note: The following information is for PC 300PL models only.
For the latest information on personal computer security features, visit the IBM
SystemCare home page at:
http://www.ibm.com/pc/us/desktop/assetid/
IBM provides the basis for Asset ID6 support in your computer. Asset ID provides
the capability to access information about your computer that is stored in an
EEPROM module on the system board using a radio-frequency-enabled portable
scanner.
The Asset ID EEPROM contains pre-recorded information about the system,
including its configuration and the serial numbers of key components. The Asset ID
EEPROM also includes a number of blank fields you can record with your choice of
end-user information. The Asset ID can be scanned from a short distance. The
6
Asset ID allows your personal computer to be scanned by various radio frequency-emitting devices
supplied by independent companies. Asset ID is intended for use only with radio frequency
equipment that meets ANSI/IEEE C95.1 1991 RF Radiation Limits.
Chapter 4. Operating your computer
51
Page 70

scanning of the Asset ID does not require the computer cover to be removed or
even require the computer being removed from the box it is shipped in. This type
of wireless tracking enables quicker system deployment and improved asset control.
Remote administration
The system programs (POST/BIOS) of your computer can be updated remotely
across a network. A setting in the Configuration/Setup Utility program allows you
to enable the computer for remote administration. See “Setting remote
administration” on page 76.
IBM System Management Tools
IBM System Management Tools are provided either on the Software Selections that
comes with your computer or on your hard disk and on the IBM Ready-to-Configure
Utility Program CD. Some software might be available on the World Wide Web.
The IBM System Management Tools package includes the following components:
Desktop Management Interface (DMI) Service Provider 2.0
Desktop Management (DM) BIOS 2.0 Instrumentation
IBM PC System Monitor Instrumentation
IBM Alert on LAN
IBM SMART Reaction Client
Intel LANDesk Client Manager 3.1
Note: IBM Alert on LAN requires hardware support. This support is provided
with PC 300PL computer models only.
For detailed information on the IBM System Management Tools package and how to
install it, refer to the Overview section on the Software Selections or your
Ready-to-Configure CD. If your computer comes with IBM-preinstalled software,
information on IBM System Management Tools and instructions for installation are
also provided in the About Your Software booklet that comes with your computer.
Using security features
The security features provided by IBM are part of the on-going effort to help protect
the personal computer from theft or inappropriate access, and to maintain the
integrity of important data stored on the computer.
IBM provides many security features for the personal computer. Some of the
features are hardware-related, such as a cover lock or support for a security U-bolt;
others are specific to the software provided with the computer such as administrator
or power-on passwords.
52 Using Your Personal Computer
Page 71

For the latest information on personal computer security features, visit the IBM
SystemCare home page at:
http://www.ibm.com/pc/us/desktop/assetid/
Note: The features in this section might not be available for all IBM personal
computers.
Security provided through the Configuration/Setup Utility program
Security features provided through the Configuration/Setup Utility program
include:
Enhanced Security enablement (some models only)
Startup sequence control
Asset ID enablement (some models only)
SystemCare enablement (some models only)
Administrator and power-on password protection
Startup without keyboard or mouse access
Hard disk drive and diskette drive access control
Input/output port control
Virus protection
More information about these features is included in Chapter 5, “Using the
Configuration/Setup Utility program” on page 61.
Security U-bolt
Your computer supports the installation of a security U-bolt that helps protect
against the theft of the computer. Used with a steel cable and a lock, the security
U-bolt can secure your computer to a desk, table, or other fixture. The security
U-bolt is an optional feature available from IBM. For information on ordering a
security U-bolt, see us on the World Wide Web at:
http://www.ibm.com/pc/us/options/
Information about installing a security U-bolt is provided in Installing Options in
Your Personal Computer.
Anti-intrusion features
Note: The following information is for the PC 300PL models only.
IBM provides different anti-intrusion features that protect against unauthorized
access inside your computer. These features help protect against the theft of
computer components, such as the microprocessor, system-memory modules, or
drives.
Chapter 4. Operating your computer 53
Page 72

A cover lock is built into the chassis of some computers to prevent the cover from
being removed. Two identical keys for the cover lock are also supplied. A tag
attached to the keys has the key serial number and the address of the key
manufacturer.
Important
Record the serial number and the manufacturer address in the space provided in
Appendix A, “Computer records” on page 151, and store the tag in a safe place.
Because locksmiths are not authorized to duplicate the cover-lock keys, you
must order replacement keys from the key manufacturer. When ordering
replacement keys, you will need the key serial number.
A chassis-intrusion detector inside your computer can be set to alert the system
administrator each time the computer cover is removed. This detector is enabled
after you set an administrator password in the Configuration/Setup Utility
program. After the password is set, and after the computer cover is removed, a
POST error message (176) displays on the computer screen the next time the
computer is plugged in and powered on. You must enter the correct administrator
password in order to start up the computer. For information on setting passwords,
see Chapter 5, “Using the Configuration/Setup Utility program” on page 61.
If you have installed IBM System Management Tools from the software provided
with your computer, a DMI-compliant message will also display on the computer
screen, after the operating system is loaded. (For more information on IBM System
Management Tools, see the Overview section on the Ready-to-Configure Utility
Program CD, or refer to About Your Software.) Also, if your computer uses Alert on
LAN, and you are connected to a network that uses Intel LANDeskDesktop
Manager or IntelLANDesk Client Manager, a message is also sent to the network
administrator console notifying that the computer cover has been removed. For
more information, see “Alert on LAN support” on page 49 and contact your
network administrator.
Component protection
Your computer has serialized components that can be registered with a third-party
security company. (You can also register the entire system.) By registering
computer components, you can improve the chances of identifying the components
if they are ever stolen and recovered. For more information about component
registration, see:
http://www.retainagroup.com
54 Using Your Personal Computer
Page 73

Data protection
You can lose data from the hard disk drive for a variety of reasons. Security
violations, viruses, or hard disk drive failure can all contribute to the destruction of
data files. To protect against the loss of valuable information, IBM has incorporated
many data-saving features within your computer.
SMART hard disk drive: Your computer comes with a SMART
(Self-Monitoring, Analysis, and Reporting Technology) hard disk drive that is
enabled to report potential hard drive failures. If the hard drive detects an error, a
DMI-compliant warning message is sent to the computer screen, and, if the
computer is part of a network, to an administrator console. Once an error is
detected, the data on the hard disk drive can be backed up and the drive replaced.
SMART Reaction: To help back up important data, IBM provides SMART
Reaction software on computers with preinstalled software and also on the IBM
Ready-to-Configure Utility Program CD or IBM Software Selections CD. SMART
Reaction is a client/server software application that helps users and administrators
respond effectively to a warning issued by the SMART hard disk drive. For more
information on SMART Reaction, see “IBM System Management Tools ” in the
Overview section on the Software Selections CD, or refer to About Your Software.
Virus Protection: Your computer has built-in virus protection that can be enabled
through the Configuration/Setup Utility program. Also, IBM AntiVirus is loaded
on the hard disk drive of computers that have preinstalled software. IBM AntiVirus
is also on the IBM Software Selections CD.
Enhanced security
Your computer has a new, enhanced security feature that provides extra protection
for your administrator password, as well as your startup sequence settings. With
enhanced security, your administrator password and startup sequence are stored in
a highly-protected, nonvolatile, security EEPROM module that is separate from
CMOS memory and the EEPROM module that stores system programs. When your
administrator password and security sequence are protected by enhanced security,
they remain intact even if the battery in your computer expires or is removed by
someone.
Enhanced security can be enabled or disabled only when you update system
programs. The procedure for enabling enhanced security is explained under
“Enabling and disabling enhanced security” on page 56.
Chapter 4. Operating your computer 55
Page 74

If enhanced security is enabled and you have not set an administrator password,
your computer will operate as if enhanced security were disabled.
If enhanced security is enabled and you have set an administrator password, your
computer will operate as follows:
The contents of the security EEPROM (your administrator password and boot
sequence) will be protected from failure of the battery and CMOS memory.
The security EEPROM will be protected from unauthorized access because it
locks after your computer is turned on and the system programs have
completed their startup routine. Once it is locked, the security EEPROM cannot
be read from or written to by any software application or system software until
the computer is turned off and back on again. In a networking environment,
this might prevent certain functions from being performed remotely on your
computer.
There is an extra measure of protection for the system programs in your
computer. Normally, the entire contents of the system programs EEPROM is
write protected with a soft lock. A soft lock allows the Remote Administration
utility to function in a network environment. Enhanced security adds a hard
lock. With a hard lock, when your computer is turned on and the system
programs startup routine is completed, the Remote Administration update
utility is locked and cannot be unlocked until the computer is turned off and
back on again and the administrator password is entered. Note that, in a
networking environment, this prevents the system programs in your computer
from being updated remotely. Someone must be present at your computer to
turn it on and off and enter the administrator password.
A chassis-intrusion feature will alert you if the cover of your computer has been
removed. This feature will work if your computer is on or off when the cover
is removed. If the cover has been removed, a prompt for your administrator
password will appear on the screen, and your computer will remain in a
suspended state until your administrator password is entered.
As with nonenhanced security, your configuration settings are protected. The
settings cannot be changed in the Configuration/Setup Utility program until
your administrator password is entered. This means that any changes in
computer hardware that are detected by the system programs in your computer,
such as removal of a memory DIMM, will generate a configuration error until
the administrator password is entered.
Enabling and disabling enhanced security: Enhanced security can be enabled
or disabled only when you update the system programs in your computer.
To enable or disable enhanced security:
56 Using Your Personal Computer
Page 75

1. Insert a system programs update diskette into drive A in your computer.
System programs updates are available on the World Wide Web.
2. Turn on the computer. If it is on already, you must turn it off and back on
again.
3. The update begins, your computer halts, and you are prompted for your
administrator password (if you have set an administrator password). The
computer remains in a halted state until you enter the administrator password.
4. When you enter the administrator password, the update diskette will continue
to run, and you are given the option of enabling or disabling enhanced security.
Your choice is automatically recorded in the System Security menu of the
Configuration/Setup Utility program.
Setting, changing, and deleting an administrator password protected by
enhanced security: To set, change, or delete an administrator password protected
by enhanced security, do the following:
1. Turn off all attached devices and the computer.
2. Refer to Installing Options in Your Personal Computer for instructions on safety,
disconnecting all cables attached to the computer, and removing the computer
cover.
3. Locate the switch marked as 7 on the rocker switches on the system board.
Refer to the system board label inside the computer for the location of the
switch. Move the switch to the ON position. (To do this, push on the ON
side.)
4. Set, change, or delete your administrator password in the Configuration/Setup
Utility program. Refer to “Setting or changing an administrator password” on
page 72 or “Deleting an administrator password” on page 74 for instructions.
Note: You must know the administrator password to change or delete it.
5. Move the switch back to the OFF position after you have set, changed, or
deleted your password.
6. Replace the cover, and then turn on the computer.
Chapter 4. Operating your computer 57
Page 76

Erasing a lost or forgotten administrator password protected by enhanced
security:
Attention
When enhanced security is enabled, it is vital that you keep a record of your
administrator password in a secure place. If you forget or lose the administrator
password, the system board in your computer must be replaced in order to
regain access to the Configuration/Setup Utility program.
Updating system programs
System programs are the basic layer of software built into every IBM computer.
They include the power-on self test (POST), the basic input/output system (BIOS)
code, and the Configuration/Setup Utility program. POST is a set of tests and
procedures that is performed every time you turn on your computer. The BIOS is a
layer of software that translates instructions from other layers of software into
instructions that the computer hardware can understand. The Configuration/Setup
Utility program enables you to view and change the configuration and setup of
your computer.
In the past, the system programs were contained in a read-only memory (ROM)
module on the system board. If you wanted to update POST routines, BIOS
instructions, and the Configuration/Setup Utility program, you had to disassemble
the computer and replace modules, or you had to replace the system board. Now,
the system programs are stored in an EEPROM (electrically erasable programmable
read-only memory) module, which is also referred to as a flash memory. The contents
can be easily updated with an update (flash) diskette. The process of updating the
system programs EEPROM is often referred to as flashing the BIOS.
As part of the continuing work to improve quality, IBM might make changes and
enhancements to the system programs. When updates are released, they will be
available on the World Wide Web at http://www.ibm.com/pc/us/desktop/ or
through the PC Company Bulletin Board Service (see “Using electronic support
services” on page 144) in files that can be downloaded onto a diskette. Updates on
the Web site or BBS will have the file name NZKTnnA.EXE, where nn is a release
number. Instructions for using the system programs updates will be available in a
README file included in the downloaded files. When updating system programs
with a flash diskette, note the following:
If you have set an administrator password, your computer will halt and request the
administrator password. The update process will not begin until you enter the
password. If you have set an administrator password, the system programs update
58 Using Your Personal Computer
Page 77
will run only if you first perform a cold startup (the computer is turned off and
then turned on).
If your computer is connected to a network, the system programs can be updated
remotely using network-management software, such as IBM LANClient Control
Manager. See “Remote administration” on page 52 for more information.
Important Information - flash ROM recovery procedure
If power to your computer is interrupted while POST/BIOS is being updated,
your computer might not restart (reboot) correctly. If this happens, perform the
following procedure to recover:
1. Turn off the computer.
2. Remove the computer cover. Refer to Installing Options in Your Personal
Computer for safety information and the cover removal procedure.
3. Locate the row of eight switches on the system board. See the label on the
underside of the computer cover for an illustration of the switches. The
ROM recovery jumper is switch number 5.
4. To enable ROM recovery, turn on the switch (ROM recovery mode).
5. Insert the POST/BIOS update (flash) diskette into drive A.
6. Turn on the computer and follow the instructions on the monitor for flash
update.
7. After the update session completes, turn off the computer and remove the
diskette from drive A.
8. Move the switch to the off position (normal ROM operation).
9. Install the cover and reconnect any cables that were disconnected.
10. Turn on the computer to restart the operating system.
Chapter 4. Operating your computer 59
Page 78

60 Using Your Personal Computer
Page 79

Chapter 5. Using the Configuration/Setup Utility program
The Configuration/Setup Utility program is stored in the EEPROM (electrically
erasable programmable read-only memory) of your computer. You can use the
Configuration/Setup Utility program to view and change the configuration and
setup of your computer, regardless of which operating system you are using.
However, the settings you select in your operating system might override any
similar settings in the Configuration/Setup Utility program.
The following is a list of the options that appear in the main menu of the
Configuration/Setup Utility program.
System Summary
Product Data
Devices and I/O Ports
Start Options
Date and Time
System Security
Advanced Setup
ISA Legacy Resources
Power Management
This chapter contains the following sections:
“Starting and using the program” on page 62, which contains information about
starting, using, and exiting the Configuration/Setup Utility.
“Instructions for most frequently used procedures” on page 66, which contains
more detailed instructions and information for performing some of the more
common configuration tasks.
“Configuration/Setup Utility option tables” on page 80, which contains
descriptions of all items within the Configuration/Setup Utility Program.
“Quick reference for network-related settings” on page 95, which contains
concise step-by-step instructions for enabling network-related settings for your
computer.
Copyright IBM Corp. 1999 61
Page 80

Starting and using the program
To start the Configuration/Setup Utility program:
1. Turn on your computer. If your computer is already on when you start this
procedure, you must shut down the operating system, turn off the computer,
wait a few seconds until all in-use lights go off, and restart the computer. (Do
not use Ctrl+Alt+Del to restart the computer.)
2. When the Configuration/Setup Utility program prompt appears in the lower left
corner of the screen during startup, press F1. (The Configuration/Setup Utility
program prompt appears on the screen for only a few seconds. You must press
F1 quickly.)
3. If you have not set an administrator password, the Configuration/Setup Utility
program menu appears on the screen. If you have set an administrator
password, the Configuration/Setup Utility program menu will not appear until
you type your administrator password at the password prompt and press Enter.
See “Using a power-on password” on page 67 and “Using an administrator
password” on page 71 for more information.
The menu you see on your computer might look slightly different from the menu
shown here, but it will operate the same way.
Configuration/Setup Utility
Select Option:
System Summary
Product Data
Devices and I/O Ports
Start Options
Date and Time
System Security
Advanced Setup
ISA Legacy Resources
Power Management
Save Settings
Restore Settings
Load Default Settings
Exit Setup
62 Using Your Personal Computer
Page 81

Viewing and changing settings
The Configuration/Setup Utility program menu lists items that identify system
configuration topics. If a bullet () appears beside a menu item, then an additional
menu is available. If a right arrowhead (5) appears beside a menu item, then a
change to that item has been made or the Configuration/Setup Utility program
detected an error and attempted to correct it. Also, an additional menu might
follow a menu item with a beside it. If an asterisk (*) appears next to a menu
item, it indicates a system resource conflict. Resolve this conflict before exiting from
the Configuration/Setup Utility program so that your computer will function
properly. For information and instructions on resolving system resource conflicts,
refer to Installing Options in Your Personal Computer and the documentation that
comes with the hardware you want to install.
When working with the Configuration/Setup Utility program menu, you must use
the keyboard. Refer to the following table for the keys used to accomplish various
tasks.
Note: Active keys are displayed at the bottom of each screen; not all of the above
keys are active with every menu.
Keys Function
↑ ↓ Use these arrow keys to move between menu items until the item you
want is highlighted.
← → Use these arrow keys to display and toggle between choices for a menu
item.
Enter Press this key to select a highlighted menu item.
Esc Press this key to exit from a menu after viewing or making changes to
the settings in the menu.
+ Use this key in some menus to increase the numerical value of a setting.
− Use this key (the minus or hyphen key) in some menus to decrease the
numerical value of a setting.
0–9 Use these number keys in some menus to change the numerical value of
a setting.
F1 Press this key for help on a selected menu item.
F9 Press this key if you changed and saved the setting of a selected menu
item and you want to restore the setting that was active before you
made the change.
F10 Press this key to return the setting of a selected menu item to a default
value.
Chapter 5. Using the Configuration/Setup Utility program 63
Page 82

In the Configuration/Setup Utility program menus, the configuration information
you can change is enclosed in brackets like these [ ]. You cannot change
information that is not surrounded by brackets.
Important Information about Saving Configuration Settings
In most cases, when you add or remove hardware from your computer or erase
passwords, the BIOS (basic input/output system) detects the changes and then
updates the configuration automatically. Although the computer changes the
configuration settings automatically, you must save these changes in the
Configuration/Setup Utility program for the new configuration to take effect. If
you do not save the new settings, your operating system will not start. To save
the configuration after adding, removing hardware, or erasing passwords,
complete the following steps.
1. When you turn on the computer, an error message indicating that a
configuration change has occurred appears approximately 30 seconds after
the memory count numbers stop cycling in the top-left corner of the screen.
When the configuration error message disappears, the POST Startup Errors
screen appears, and you are prompted to Continue or Exit Setup. Select
Continue. (If you select Exit Setup, you will get another error message.)
2. The Configuration/Setup Utility program menu appears with a right
arrowhead (5) next to the menu category in which the configuration change
has occurred. Select this menu item if you want to view the new
configuration settings, and then press Esc to return to the
Configuration/Setup Utility program menu.
3. Select Save Settings from the Configuration/Setup Utility program menu.
4. Press Esc to exit from the Configuration/Setup Utility program, and follow
the instructions on the screen.
64 Using Your Personal Computer
Page 83

Exiting the program
When you finish viewing or changing settings in the Configuration/Setup Utility
program, follow these steps to exit from the program:
1. Press Esc to return to the Configuration/Setup Utility program menu.
(Depending on where you are in the program, you might have to press Esc
several times to get back to the Configuration/Setup Utility program menu.)
2. Before you exit from the Configuration/Setup Utility program menu, select Save
Settings if you want to save all settings as they currently appear. If you do not
complete this step, your settings will not be saved.
3. From the Configuration/Setup Utility program menu, press Esc, and follow the
instructions on the screen.
Chapter 5. Using the Configuration/Setup Utility program 65
Page 84

Instructions for most frequently used procedures
This section contains step-by-step instructions for some of the most frequently used
configuration and setup procedures for your computer.
Viewing the system summary
You can use the Configuration/Setup Utility program to view a summary of the
options and features in your computer. To view the system summary:
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select System Summary from the Configuration/Setup Utility program menu.
The System Summary screen appears.
Depending on your model and configuration, your screen might appear slightly
different from the one shown here.
System Summary
Processor Pentium III
Processor speed 400 MHz
7
Cache size 512 KB
Cache state Enabled
System memory 64 MB
Memory type ECC
Video controller S3 Incorporated. Trio3D (or
other AGP adapter)
Ethernet support Enabled
Audio support Enabled
Diskette drive A: 1.44 MB, 3.5"
Diskette drive B: Not Installed
IDE CD-ROM drive 0 Installed
Hard Disk drive 1 Not Installed
Hard disk drive 2 Not Installed
Hard disk drive 3 Not installed
7
MHz only denotes the internal clock speed of the microprocessor, not application performance; many
factors affect application performance.
66 Using Your Personal Computer
Page 85

Setting the date and time
Your computer has an internal clock that maintains the date and time. A battery
keeps the clock active when you turn off the computer.
To set the date and time:
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select Date and Time from the Configuration/Setup Utility program menu.
3. Type the date and time in the appropriate fields.
4. Press Esc to return to the Configuration/Setup Utility program menu.
5. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu and press Enter.
6. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Your operating system might also have a function for setting the date and time.
Refer to your operating system documentation for more information.
Using a power-on password
The power-on password feature deters unauthorized persons from gaining access to
the information stored in your computer. You do not need to set a power-on
password, but doing so allows you to control who can use your computer. When a
power-on password is set, you must type the password at a prompt that appears as
the computer starts.
When you set the power-on password, you can choose one of three password
prompt modes:
On In password prompt On mode, you are prompted for the power-on
password when you turn on the computer. Until the correct password is
entered, the computer's operating system will not start, and the keyboard
will remain locked. If you have a mouse connected to the mouse port, it
also will remain locked. If you have a mouse connected to a serial port,
it will be activated when the computer is started, regardless of whether a
password is set.
Note: If Remote Administration is enabled, you cannot select On.In
this case you should select Dual. If it is set to On when Remote
Administration is enabled, it will automatically be reset to Dual.
Chapter 5. Using the Configuration/Setup Utility program 67
Page 86

Off In password prompt Off mode (sometimes referred to as unattended
start mode), you are not prompted to enter your power-on password
when you turn on the computer. The computer will start the operating
system. However, if you have a mouse connected to the mouse port,
refer to the following text box.
Important information for mouse users
This information applies only to those who have a mouse connected
to the mouse port; a serial mouse is not affected by the password
prompt Off mode.
The password prompt Off mode prevents the computer from
detecting that a mouse is attached. Because the mouse device driver
will not be loaded automatically through the CONFIG.SYS or
AUTOEXEC.BAT files in this mode, an error message that the mouse
port is disabled will appear, and the computer will halt. To enable
the operating system to load without displaying the error message,
read the information below that applies to your operating system.
If you are using OS/2, do one of the following before enabling
password prompt Off mode:
Set the CONFIG.SYS file so the operating system does not stop on
a device-driver error. To do this, put the command
"PAUSEONERROR=NO" near the top of the CONFIG.SYS file.
or
Remove the mouse driver statement from the CONFIG.SYS file.
If you are using Windows NT, Windows 95, or Windows 98, do the
following:
When the computer is started and the mouse port disabled error
message appears, type either your power-on or administrator
password to enable the keyboard. Then use the keyboard to put
a check mark in the Do not display this message in the future
check box.
Once the operating system starts in password prompt Off mode, the
keyboard will remain locked. If you have a mouse connected to the
mouse port, it also will remain locked.
Although you are not prompted to type a password in this mode, you
can type either your power-on or administrator password anytime after
POST has completed, even after the operating system has loaded. If you
type a password, the keyboard will unlock, but the mouse connected to
the mouse port will remain disabled.
68 Using Your Personal Computer
Page 87

Password prompt Off mode is useful for network servers and other
computers that operate unattended. If a power failure occurs, the
computer will automatically restart and resume operating in this mode
when power is restored, without operator intervention.
Dual In the password prompt Dual mode, the startup behavior of the
computer depends on whether the computer is started from the
computer power switch or by an unattended method, such as a modem
or timer.
If you start the computer by using the power switch, the computer
operates the same as it does in password prompt On mode. Refer to
page 67 for further information.
If the computer is started by an unattended method, such as remotely
over a LAN, the computer operates the same as it does in password
prompt Off mode. Refer to page 68 for further information.
If both a power-on and administrator password are set, you can type either
password at the password prompt that appears as you start your computer. However,
if you want to change any settings in the Configuration/Setup Utility program, you
must type your administrator password at the password prompt that appears when
you try to access the Configuration/Setup Utility program. If you type your power-on
password at this prompt, you will be able to view limited information in the
Configuration/Setup Utility program, but you will not be able to change any
settings.
The password does not appear on the screen as you type it. If you type the wrong
password, you receive a screen message telling you so. If you type the wrong
password three times, you must turn the computer off and start again. When you
type the correct password, the keyboard and mouse will unlock, and the computer
will begin normal operation.
Setting and changing a power-on password: Use the Configuration/Setup
Utility program to set or change a power-on password. You can use any
combination of up to seven characters (A–Z, a–z, and 0–9) for this password.
You cannot use the numeric keypad to set the password, but must use the numbers
across the top of the alphanumeric keypad.
Attention: Keep a record of your power-on password in a secure place. When a
power-on password has been set, you cannot activate the keyboard and mouse
without first using the password. If you lose or forget your password, you cannot
change or delete it without removing the computer cover and moving a jumper on
Chapter 5. Using the Configuration/Setup Utility program 69
Page 88

the system board. Refer to “Erasing a lost or forgotten administrator password” on
page 74 for further information.
To set or change a power-on password:
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select System Security from the Configuration/Setup Utility program menu.
3. Select Power-On Password.
4. Type your password and press Down Arrow (↓).
5.Type your password again, then select Change password.
6. At Password Prompt, select Off, On, or Dual. Press Left Arrow (←) or Right
Arrow (→) to toggle between selections.
Note: If Remote Administration is enabled, you cannot select On. In this case
you should select Dual. If it is set to On when Remote Administration
is enabled, it will automatically be reset to Dual.
7. Select Change Power-On Password, and follow the instructions on the screen.
8. Press Esc twice to return to the Configuration/Setup Utility program menu.
9. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu.
10. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Deleting a Power-on password: Use the Configuration/Setup Utility program
to delete a power-on password.
To delete a power-on password:
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select System Security from the Configuration/Setup Utility program menu.
3. Select Power-On Password.
4. Select Delete Power-On Password and follow the instructions on the screen.
5. Press Esc twice to return to the Configuration/Setup Utility program menu.
6. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu.
70 Using Your Personal Computer
Page 89

7. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Using an administrator password
Important
If you have enhanced security enabled on your computer, see “Enhanced
security” on page 55 for important information about the administrator
password.
When enhanced security is enabled, it is vital that you keep a record of your
administrator password in a secure place. If you forget or lose the administrator
password, the system board in your computer must be replaced in order to
regain access to the Configuration/Setup Utility program.
Setting an administrator password deters unauthorized persons from changing
settings in the Configuration/Setup Utility program. When an administrator
password is set, you can change settings in the Configuration/Setup Utility program
only after typing the administrator password at the password prompt that appears
when you try to access the Configuration/Setup Utility program.
If you are responsible for maintaining the settings of several computers, you might
want to set an administrator password.
When you set an administrator password, a password prompt appears each time
you try to access the Configuration/Setup Utility program. The password does not
appear on the screen as you type it. If you type the wrong password, you receive a
screen message telling you so. If you type the wrong password three times, you
must turn the computer off and start again. When you type the correct password,
the Configuration/Setup Utility program menu appears.
If both a power-on and administrator password are set, you can type either of the
passwords at the password prompt that appears as you start your computer. However,
if you want to change any settings in the Configuration/Setup Utility program, you
must type your administrator password at the password prompt that appears when
you try to access the Configuration/Setup Utility program. If you type your power-on
password at this prompt, you will be able to view limited information in the
Configuration/Setup Utility program, but you will not be able to change any
settings.
Chapter 5. Using the Configuration/Setup Utility program 71
Page 90
Important Information for the PC 300PL
If you have set an administrator password on a PC 300PL system, read the
following.
The SystemCare and Asset ID settings in the Configuration/Setup Utility
program are enabled when your computer is shipped. If you set an
administrator password with the SystemCare and Asset ID settings enabled, the
following occurs:
The chassis-intrusion feature of your computer is enabled. Each time you
remove the computer cover and subsequently power on the computer, the
Power-On Self-Test (POST) notifies you that the cover has been removed.
The message displayed on the computer screen is the POST message 176.
To bypass the message, you must enter the correct administrator password.
Each time a component that is protected by asset security is removed and
the computer is powered on, a POST message notifies you of the removal.
Examples of such components are system-memory modules and the
microprocessor. The message that displays is the POST message 177.
To bypass the message, you must enter the correct administrator password.
Each time the computer passes through an access control checkpoint that
reads Asset ID information, a POST message notifies the system manager
that there has been a security breach when the computer is powered on, if
the movement of the PC was unauthorized. To bypass the message, you
must enter the correct administrator password.
Setting or changing an administrator password: Use the Configuration/Setup
Utility program to set or change an administrator password. You can use any
combination of up to seven characters (A–Z, a–z, and 0–9) for the password.
72 Using Your Personal Computer
Page 91

Attention
Keep a record of your administrator password in a secure place. If you lose or
forget the administrator password, you will not be able to access the
Configuration/Setup Utility program, and you will not be able to erase and reset
an administrator password. If you lose or forget your password, you must
complete one of the following steps in order to regain access to the
Configuration/Setup Utility program:
1. If enhanced security is disabled (default setting), you must remove the
computer cover and move a jumper on the system board. (Refer to “Erasing
a lost or forgotten administrator password” on page 74 for further
information.)
2. If enhanced security is enabled, you must replace the system board in your
computer.
To set or change an administrator password:
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select System Security from the Configuration/Setup Utility program menu.
3. Select Administrator Password.
4. Type your password and press Down Arrow (↓).
5. Type your password again.
6. At Power-On Password Changeable by User, select Yes or No. Press Left
Arrow (←) or Right Arrow (→) to toggle between selections. (If you select Yes
and an administrator password is set, the power-on password can be changed
without having to enter the administrator password. If you select No and an
administrator password is set, the power-on password cannot be changed unless
the administrator password is entered.)
7. Select Change Administrator Password and follow the instructions on the
screen.
8. Press Esc until you return to the Configuration/Setup Utility program menu.
9. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu.
10. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Chapter 5. Using the Configuration/Setup Utility program 73
Page 92

Deleting an administrator password: Use the Configuration/Setup Utility
program to delete an administrator password.
To delete an administrator password:
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select System Security from the Configuration/Setup Utility program menu.
3. Select Administrator Password.
4. Select Delete Administrator Password and follow the instructions on the screen.
5. Press Esc until you return to the Configuration/Setup Utility program menu.
6. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu.
7. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Erasing a lost or forgotten administrator password: This section applies to
lost or forgotten administrator passwords that are not protected by enhanced
security. For information on lost or forgotten passwords that are protected by
enhanced security, refer to “Erasing a lost or forgotten administrator password
protected by enhanced security” on page 58.
If you have lost or forgotten your administrator password and enhanced security is
disabled, you must remove the computer cover and move the Clear CMOS Request
jumper (also referred to as the password jumper) on the system board in order to
erase the password so that you can regain access to the Configuration/Setup Utility
program.
See Installing Options in Your Personal Computer for instructions on removing the
computer cover and moving jumpers. Refer to the system board label inside the
computer for the location of the Clear CMOS Request jumper.
Important
If you move the Clear CMOS Request jumper, you will lose all setup data stored
in the computer, and you will need to reconfigure the computer. Use the
Configuration/Setup Utility program to reconfigure the computer and to set a
new password.
74 Using Your Personal Computer
Page 93

Setting the startup sequence
Your computer can be started (or booted) from several devices including the hard
disk drive, diskette drive, CD-ROM drive, and from the network. The startup
program looks for these devices in a selected sequence. The Configuration/Setup
Utility program is used to select the startup sequence.
Note: The hard disk drive is the default startup device when no other devices are
ready. It does not appear in the choices provided by the
Configuration/Setup Utility program.
To set the startup sequence:
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select Start Options from the Configuration/Setup Utility program menu.
3. Select Startup Sequence from the Start Options menu.
4. Select the sequence and devices from the choices provided.
5. If Automatic Power On Startup Sequence is Enabled, select the sequence and
devices from the choices provided.
6. Press Esc until you return to the Configuration/Setup Utility program menu.
7. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu and press Enter.
8. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Chapter 5. Using the Configuration/Setup Utility program 75
Page 94

Setting remote administration
Enabling remote administration, allows system programs, such as the POST/BIOS,
in your computer to be remotely updated from a network server. If you have set an
administrator password for your computer, it does not have to be entered by the
server. Consult your network administrator for information on setting up your
network server to perform POST and BIOS updates.
To access remote administration:
1. Start the Configuration/Setup Utility program. See “Starting and using the
program” on page 62.
2. Select System Security.
3. Select Remote Administration.
4. Press Enter.
5. To enable update remote administration, select Enabled. To disable, select
Disabled.
6. Press Esc until you return to the Configuration/Setup Utility main menu.
7. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu.
8. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Setting power management features
Your computer comes with built-in energy-saving capabilities. Power management
features included with your computer are Advanced Power Management (APM)
and Advanced Configuration and Power Interface (ACPI) BIOS modes, and
Automatic Power On. This section describes the Power Management features in
your computer and provides instructions for using these features.
Attention: If a device, such as a monitor, does not have power-management
capabilities, it can be damaged when exposed to a reduced-power state. Before you
make energy-saving selections for your monitor, check the documentation that
comes with your monitor to see if it supports Display Power Management Signaling
(DPMS).
Setting ACPI BIOS mode: When Automatic Configuration and Power Interface
(ACPI) BIOS Mode BIOS mode is enabled, the operating system is allowed to
control the power management features of your computer and the settings for APM
76 Using Your Personal Computer
Page 95

BIOS mode are ignored. Not all operating systems support ACPI BIOS mode.
Refer to your operating system documentation to determine if ACPI is supported.
To set ACPI BIOS mode, complete the following steps.
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select Power Management from the Configuration/Setup Utility program menu.
3. Set ACPI BIOS Mode to Enabled or Disabled as desired using the Left Arrow
(←) or Right Arrow (→).
4. Press Esc to return to the Configuration/Setup Utility program menu.
5. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu.
6. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Setting APM features: With APM (Advanced Power Management), the
computer and monitor (if the monitor supports DPMS) can be set to go into a
reduced-power state if they are inactive for a specified length of time.
Time to Low Power: With this option, you can specify the amount of time that
the computer must be inactive before Power Management options begin to take
affect. You can select from 5 minutes to 1 hour.
System Power: With this option, you can select On if you want the computer
to remain on, or Off if you want the computer to shut down.
Display: With this option, you can select one of the following reduced-power
states:
– Standby: In this mode, the screen is blanked, but the screen image is
restored immediately when any activity is detected.
– Suspend: In this mode, the monitor uses less power than in Standby mode.
The screen is blanked, but the screen image is restored within a few seconds
after any activity is detected.
– OFF: In this mode, the monitor power is turned off. To restore power to
the monitor, you must press the monitor power switch. On some monitors,
you might have to press the power switch twice.
If OFF is selected, you must specify the Time to Display 'off'. You can
select 5 minutes to 1 hour.
Note: Time to display off is the amount of time after the reduced-power
state before the display enters the off state.
Chapter 5. Using the Configuration/Setup Utility program 77
Page 96

– Disable: In this mode, the monitor is unaffected by the power management
settings.
IDE Drives: This selection enables you to specify if the IDE drives should be
enabled or disabled when power management options take affect.
To set APM features:
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select Power Management from the Configuration/Setup Utility program menu.
3. Select APM.
4. Set APM BIOS Mode to Enabled.
5. Select values for power management (time to low power, system power,,
processor speed, display, and time to display off), as necessary.
6. Set IDE Drives to Enabled or Disabled.
Note: SCSI drives are not affected by APM.
7. Press Esc twice to return to the Configuration/Setup Utility program menu.
8. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu.
9. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Setting Automatic Power On features: The Automatic Power On features
within the Power Management menu allow you to enable and disable features that
automatically turn your computer on. You must also select the startup sequence
you want to use for the type of power-on event selected. If you select Automatic,
make sure Automatic Power On Startup Sequence in the Startup Sequence menu is
set to enabled. Otherwise, the system will use the Primary startup sequence.
Wake on LAN: The Wake on LAN feature built into your computer can be
used with network connections that support this feature. If your computer has
an integrated Ethernet connection, it supports Wake on LAN. Also, you can
install a PCI Wake on LAN network card in your computer. The network card
must connect to the Wake on LAN connector on the riser card inside your
computer. See Installing Options in Your Personal Computer for more information.
Also, you must set PCI Wake Up to enabled.
When you set Wake on LAN to Enabled, your computer will turn on when it
receives a specific signal from another computer on your local area network
(LAN).
78 Using Your Personal Computer
Page 97

Serial Port Ring Detect: If your computer has an external modem connected to
a serial port and you want the computer to turn on automatically when a ring is
detected on the modem, set this feature to Enabled.
MODEM Ring Detect: If your computer has an internal modem and you want
the computer to turn on automatically when a ring is detected on the modem,
set this feature to Enabled. The modem must support this feature and must be
attached to the Modem Ring Detect connector on the riser card in your
computer. See Installing Options in Your Personal Computer for more information.
Wake Up on Alarm: With this feature, you can specify a date and time at
which the computer will be turned on automatically. This can be either a single
event, a daily event, or a weekly event.
PCI Wake Up: If enabled, this setting allows your system to power on in
response to wake up requests from PCI devices that support this feature.
To set Automatic Power-On features:
1. Start the Configuration/Setup Utility program (see “Starting and using the
program” on page 62).
2. Select Power Management from the Configuration/Setup Utility program menu.
3. Select Automatic Power On.
4. Select the menu item for the feature you want to set. Use Left Arrow (←) or
Right Arrow (→) to select either Enabled or Disabled.
5. Select Startup Sequence for the feature. Use Left Arrow (←) or Right Arrow
(→) to select either Primary or Automatic.
6. Press Esc until you return to the Configuration/Setup Utility program menu.
7. Before you exit from the program, select Save Settings from the
Configuration/Setup Utility program menu.
8. To exit from the Configuration/Setup Utility program, press Esc and follow the
instructions on the screen.
Chapter 5. Using the Configuration/Setup Utility program 79
Page 98

Configuration/Setup Utility option tables
This section contains descriptions of the configuration options according to category.
System Summary
If you select the System Summary option from the Configuration/Setup Utility main
menu, you can view the following information about the features of your computer.
The Configuration/Setup Utility changes this information automatically if you add
or remove options, unless otherwise stated.
Item Description
Processor Indicates the type of microprocessor.
Processor Speed Indicates the microprocessor internal clock speed.
Cache Size Indicates the amount of cache memory in Kilobytes. Cache
memory is special buffer storage that holds frequently
used instructions and data, and works faster than main
memory.
Cache State Indicates the state of cache memory, enabled or disabled.
System Memory Indicates the amount of synchronous dynamic random
access memory (SDRAM).
Memory Type Indicates the type of memory, such as nonparity or error
checking and correction (ECC).
Video Controller Indicates the type of video controller, which processes
images on your monitor.
Ethernet Support Indicates the type of Ethernet controller, if installed.
Audio Support Indicates the type of audio controller, if installed.
Diskette Drive A Shows if diskette drive A is installed. The default is:
Drive A — 1.44 MB 3.5". To specify the drive capacity, see
Devices and I/O Ports on page 82.
Diskette Drive B Shows if diskette drive B is installed. The program cannot
detect the storage capacity of the drives. The default is:
Drive B — 1.2 MB 5.25". To specify the drive capacity, see
Devices and I/O Ports on page 82.
IDE Hard Disk Drive 0 Shows if an IDE device is installed.
IDE Hard Disk Drive 1 Shows if an IDE device is installed.
IDE CD-ROM Drive 2 Shows if a CD-ROM drive is installed.
IDE Hard Disk Drive 3 Shows if an IDE device is installed.
80 Using Your Personal Computer
Page 99

Product data
If you select the Product Data option from the Configuration/Setup Utility main
menu, you can view the following information about your computer model. The
Configuration/Setup Utility changes this information automatically if the EEPROM
(electrically erasable programmable read-only memory) or BIOS (basic input/output
system) code is upgraded.
Item Description
Machine Type/Model Shows the type and model of the computer.
Flash EEPROM Revision
Level
Indicates the revision level of the software installed in the
electrically erasable programmable read-only memory
(EEPROM).
Boot Block Revision Level Indicates the revision level of the boot (startup) record that
is flashed in at manufacturing.
System Board Identifier Shows the ID number of the system board.
System Serial Number Shows the serial number of the computer.
System UUID Shows a universally unique identifier for your computer.
BIOS Date Shows the date of the Basic Input/Output System code
that contains such basic hardware operations as interaction
with diskette drives, hard disk drives, and the keyboard.
BIOS Mode Shows the mode (Desktop) of the Basic Input/Output
System code.
Chapter 5. Using the Configuration/Setup Utility program 81
Page 100

Devices and I/O Ports
If you select the Devices and I/O Ports option from the Configuration/Setup Utility
main menu, you can view and, in some cases, change device or port settings.
Note: The specific device options might vary, depending on the computer model.
You can change port assignments or disable ports if you want to prevent
unauthorized transmission of data to any devices attached to the ports.
Item Description
Mouse You must select whether the mouse is installed or not in
this field.
Diskette Drive A If a drive is installed, this field shows the diskette storage
capacity of the drive. If you change or add a diskette
drive, you might need to use this option to set the correct
type.
Diskette Drive B If a drive is installed, this field shows the diskette storage
capacity of the drive. If you change or add a diskette
drive, you might need to use this option to set the correct
type.
Serial Port Setup
Serial Port A Address
Serial Port A IRQ
Serial Port B Address
Serial Port B IRQ
The Serial Port Setup menu shows the addresses and
interrupts for the built-in serial ports.
If you add adapter cards with serial ports, an error
message will notify you if you have an address conflict
among the serial ports. Ensure that each serial port has a
different address. If you change serial port addresses in
this menu, you might also need to make changes in the
software that uses serial ports. For instructions on
changing your software, see the user's guide or online
information that comes with the software.
USB Setup
USB Support
USB Keyboard/Mouse
Support
The USB Setup menu lets you enable or disable the
Universal Serial Bus feature.
Select Autodetect for USB Keyboard/Mouse Support if you
want this support to be enabled when a USB keyboard or
a USB mouse is detected after the computer is started.
Select Disabled if you will not be using a USB keyboard or
USB mouse.
82 Using Your Personal Computer
 Loading...
Loading...