Huawei Quidway S3500 Operation Manual

Operation Manual - Security
Quidway S3500 Series Ethernet Switches Table of Contents
Huawei Technologies Proprietary
i
Table of Contents
Chapter 1 802.1x Configuration...................................................................................................1-1
1.1 802.1x Overview ................................................................................................................ 1-1
1.1.1 802.1x Standard Overview...................................................................................... 1-1
1.1.2 802.1x System Architecture .................................................................................... 1-1
1.1.3 802.1x Authentication Process................................................................................ 1-2
1.1.4 Implementing 802.1x on the Ethernet Switch ......................................................... 1-3
1.2 Configuring 802.1x............................................................................................................. 1-3
1.2.1 Enabling/Disabling 802.1x....................................................................................... 1-4
1.2.2 Setting the Port Access Control Mode. ................................................................... 1-4
1.2.3 Setting the Port Access Control Method ................................................................. 1-5
1.2.4 Checking the Users that Log on the Switch via Proxy ............................................ 1-5
1.2.5 Setting the Supplicant Number on a Port................................................................ 1-6
1.2.6 Setting the Authentication in DHCP Environment................................................... 1-6
1.2.7 Configuring the Authentication Method for 802.1x User ......................................... 1-6
1.2.8 Enabling/Disabling Guest VLAN ............................................................................. 1-7
1.2.9 Setting 802.1x Re-authentication............................................................................ 1-8
1.2.10 Setting 802.1x Client Version Authentication...................................................... 1-10
1.2.11 Setting the Maximum Times of Authentication Request Message
Retransmission.............................................................................................................. 1-11
1.2.12 Configuring Timers.............................................................................................. 1-12
1.2.13 Enabling/Disabling a Quiet-Period Timer............................................................ 1-13
1.3 Displaying and Debugging 802.1x................................................................................... 1-13
1.4 802.1x Configuration Example......................................................................................... 1-14
Chapter 2 Portal Configuration.................................................................................................... 2-1
2.1 Portal Overview.................................................................................................................. 2-1
2.1.1 Introduction to Portal ............................................................................................... 2-1
2.1.2 Portal System Composition..................................................................................... 2-1
2.1.3 Procedures for Portal Authentication ...................................................................... 2-2
2.1.4 Portal Operating Modes .......................................................................................... 2-3
2.1.5 Portal Authentication-Free Users and Free IP Addresses...................................... 2-3
2.1.6 ARP Packet Handshaking Between Switch and User's PC.................................... 2-4
2.1.7 Portal Rate Limitation.............................................................................................. 2-4
2.2 Portal Configurations ......................................................................................................... 2-4
2.2.1 Configuration Prerequisites..................................................................................... 2-4
2.2.2 Portal Configuration Tasks...................................................................................... 2-5
2.2.3 Portal Direct Authentication Configuration Example............................................... 2-6
2.2.4 Re-DHCP Authentication Configuration Example................................................... 2-8

Operation Manual - Security
Quidway S3500 Series Ethernet Switches Table of Contents
Huawei Technologies Proprietary
ii
2.2.5 Layer 3 Portal Authentication Configuration Example .......................................... 2-10
2.3 Portal Authentication-Free User and Free IP address Configurations ............................ 2-11
2.3.1 Portal Authentication-Free User and Free IP Address Configuration Tasks ........ 2-11
2.3.2 Portal Authentication-Free User and Free IP Configuration Example .................. 2-12
2.4 Portal Rate limitation Configurations ............................................................................... 2-14
2.4.1 Portal Rate limitation Configuration Tasks............................................................ 2-14
2.4.2 Portal Rate limitation Configuration Example ....................................................... 2-14
2.5 Portal User Deletion......................................................................................................... 2-14
2.5.1 Portal User Deletion Configuration Tasks............................................................. 2-14
2.5.2 Portal User Deletion Configuration Example ........................................................ 2-15
Chapter 3 AAA and RADIUS Protocol Configuration ................................................................ 3-1
3.1 AAA and RADIUS Protocol Overview................................................................................ 3-1
3.1.1 AAA Overview ......................................................................................................... 3-1
3.1.2 RADIUS Protocol Overview .................................................................................... 3-1
3.1.3 Implementing AAA/RADIUS on Ethernet Switch .................................................... 3-2
3.2 AAA Configuration ............................................................................................................. 3-3
3.2.1 Creating/Deleting ISP Domain ................................................................................ 3-3
3.2.2 Configuring Relevant Attributes of ISP Domain ...................................................... 3-4
3.2.3 Creating a Local User ............................................................................................. 3-5
3.2.4 Setting Attributes of Local User............................................................................... 3-5
3.2.5 Disconnecting a User by Force ............................................................................... 3-7
3.2.6 Configuring Dynamic VLAN with RADIUS Server................................................... 3-7
3.3 Configuring RADIUS Protocol............................................................................................ 3-8
3.3.1 Creating/Deleting a RADIUS scheme ..................................................................... 3-9
3.3.2 Setting IP Address and Port Number of RADIUS Server...................................... 3-10
3.3.3 Setting RADIUS Packet Encryption Key ............................................................... 3-11
3.3.4 Setting Response Timeout Timer of RADIUS Server ........................................... 3-12
3.3.5 Setting Retransmission Times of RADIUS Request Packet ................................. 3-12
3.3.6 Enabling The Selection Of Radius Accounting Option.......................................... 3-13
3.3.7 Setting a Real-time Accounting Interval................................................................ 3-13
3.3.8 Setting Maximum Times of Real-time Accounting Request Failing to be
Responded .................................................................................................................... 3-14
3.3.9 Enabling/Disabling Stopping Accounting Request Buffer ..................................... 3-15
3.3.10 Setting the Maximum Retransmitting Times of Stopping Accounting Request .. 3-15
3.3.11 Configuring the User Re-authentication at Reboot ............................................. 3-16
3.3.12 Setting the Supported Type of RADIUS Server .................................................. 3-17
3.3.13 Setting RADIUS Server State ............................................................................. 3-18
3.3.14 Configuring the Quiet Time Interval .................................................................... 3-18
3.3.15 Setting Username Format Transmitted to RADIUS Server ................................ 3-19
3.3.16 Setting the Unit of Data Flow that Transmitted to RADIUS Server..................... 3-20
3.3.17 Configuring Local RADIUS Authentication Server .............................................. 3-20
3.4 Displaying and Debugging AAA and RADIUS Protocol................................................... 3-21

Operation Manual - Security
Quidway S3500 Series Ethernet Switches Table of Contents
Huawei Technologies Proprietary
iii
3.5 AAA and RADIUS Protocol Configuration Examples ...................................................... 3-22
3.5.1 Configuring FTP/Telnet User Authentication at Remote RADIUS Server ............ 3-22
3.5.2 Configuring FTP/Telnet User Authentication at Local RADIUS Server ................ 3-23
3.5.3 Configuring Dynamic VLAN with RADIUS Server................................................. 3-24
3.6 AAA and RADIUS Protocol Fault Diagnosis and Troubleshooting.................................. 3-25
Chapter 4 EAD Configuration.......................................................................................................4-1
4.1 EAD Overview.................................................................................................................... 4-1
4.2 EAD Network Applications................................................................................................. 4-1
4.3 EAD Configuration Tasks .................................................................................................. 4-2
4.4 EAD Configuration Example.............................................................................................. 4-3
Chapter 5 HABP Configuration....................................................................................................5-1
5.1 HABP Overview ................................................................................................................. 5-1
5.2 HABP configuration ........................................................................................................... 5-1
5.2.1 Configuring HABP Server ....................................................................................... 5-1
5.2.2 Configuring HABP Client......................................................................................... 5-2
5.3 Displaying and Debugging HABP Attribute ....................................................................... 5-2
Chapter 6 System-guard Configuration......................................................................................6-1
6.1 System-guard Overview .................................................................................................... 6-1
6.2 System-guard Configuration .............................................................................................. 6-1
6.2.1 Enabling system-guard function.............................................................................. 6-1
6.2.2 Setting the max detection count of the affected hosts ............................................ 6-2
6.2.3 Setting parameters of address learning .................................................................. 6-2
6.2.4 Enabling the Switch not to Learn the Destination IP Address ................................ 6-3
6.3 Displaying and Debugging System-guard .........................................................................6-4

Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-1
Chapter 1 802.1x Configuration
1.1 802.1x Overview
1.1.1 802.1x Standard Overview
IEEE 802.1x (hereinafter simplified as 802.1x) is a port-based network access control
protocol that is used as the standard for LAN user access authentication.
In the LANs complying with the IEEE 802 standards, the user can access the devices
and share the resources in the LAN through connecting the LAN access control device
like the LAN Switch. However, in telecom access, commercial LAN (a typical example
is the LAN in the office building) and mobile office etc., the LAN providers generally
hope to control the user’s access. In these cases, the requirement on the
above-mentioned “Port Based Network Access Control” originates.
“Port Based Network Access Control” means to authenticate and control all the
accessed devices on the port of LAN access control device. If the user’s device
connected to the port can pass the authentication, the user can access the resources in
the LAN. Otherwise, the user cannot access the resources in the LAN. It equals that the
user is physically disconnected.
802.1x defines port based network access control protocol and only defines the
point-to-point connection between the access device and the access port. The port can
be either physical or logical. The typical application environment is as follows: Each
physical port of the LAN Switch only connects to one user workstation (based on the
physical port) and the wireless LAN access environment defined by the IEEE 802.11
standard (based on the logical port), etc.
1.1.2 802.1x System Architecture
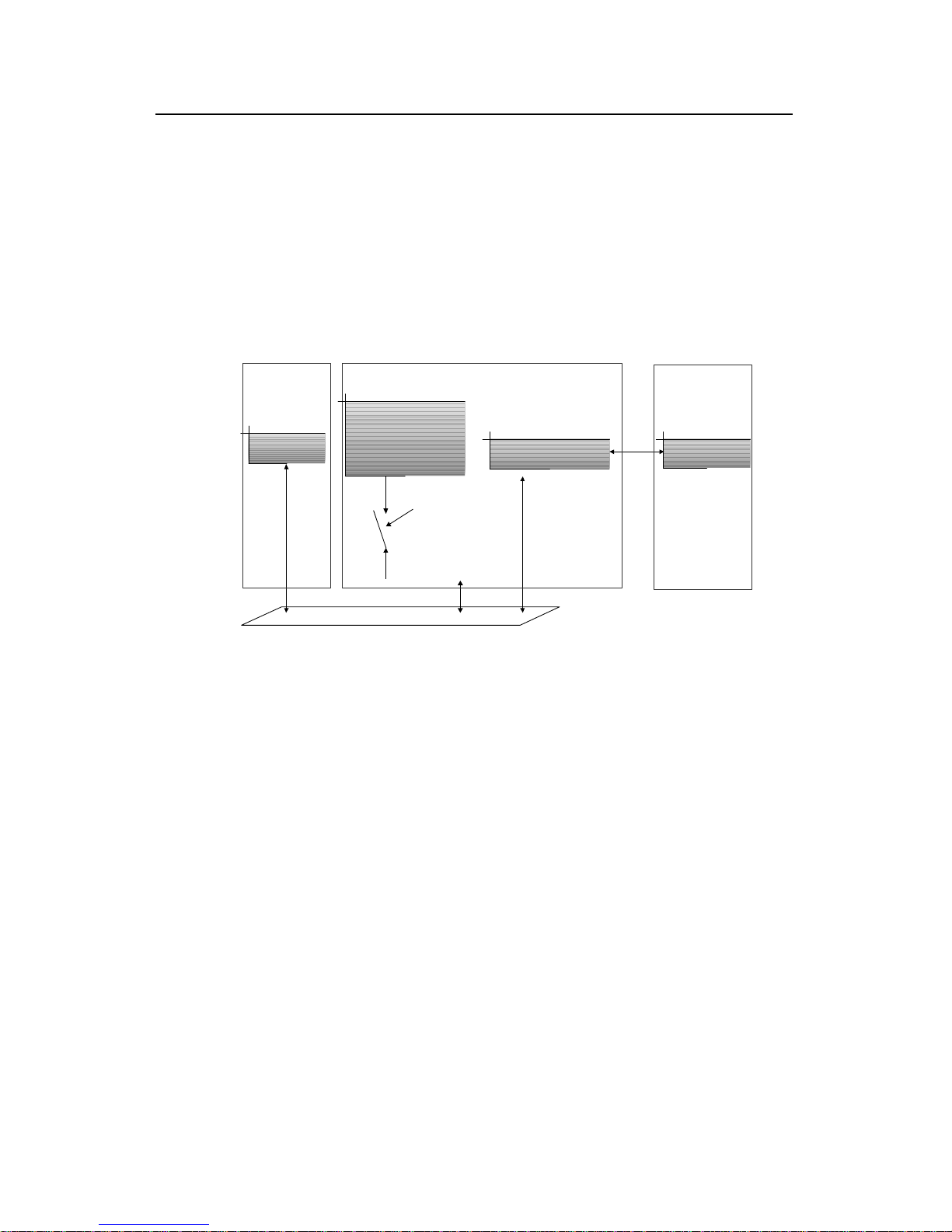
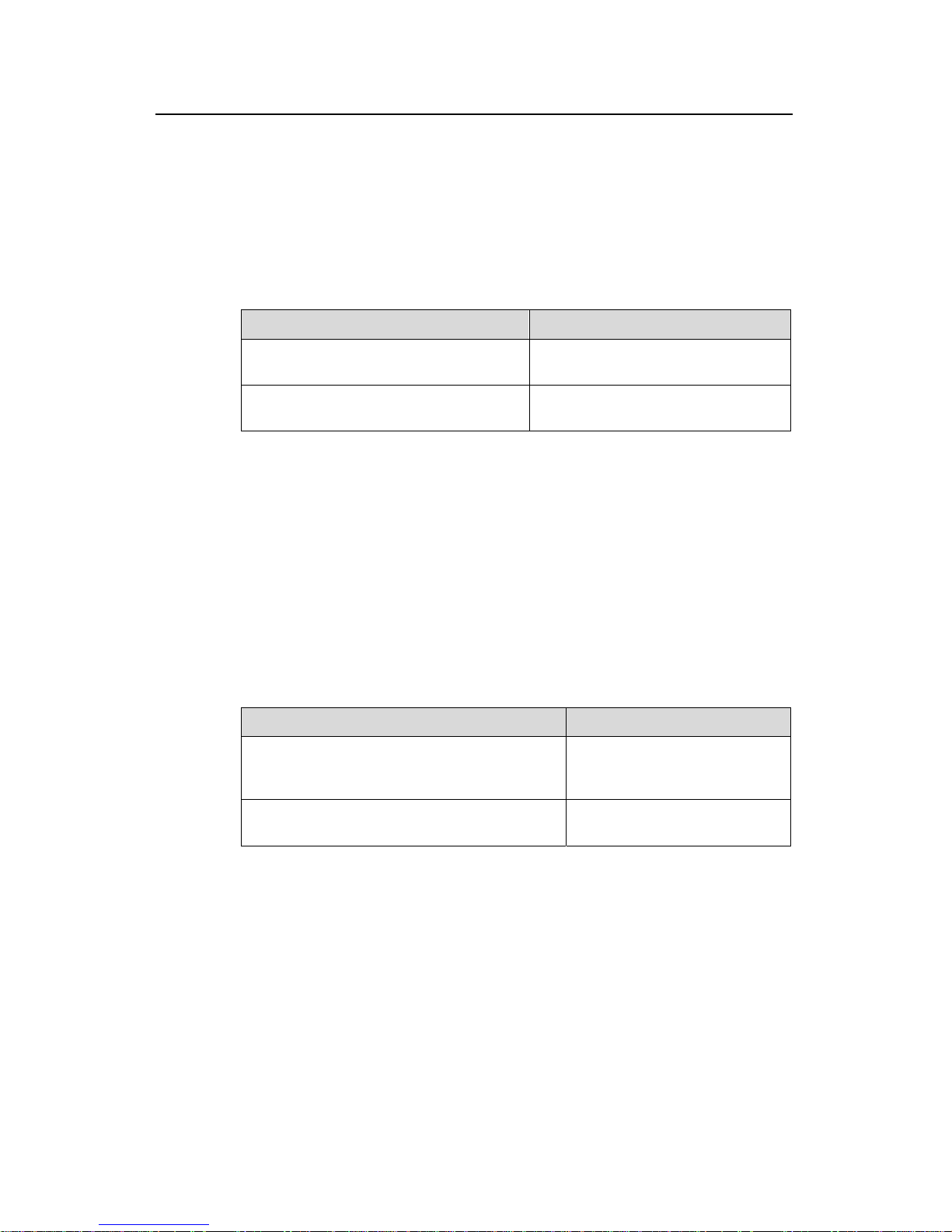
The system using the 802.1x is the typical C/S (Client/Server) system architecture. It
contains three entities, which are illustrated in the following figure: Supplicant System,
Authenticator System and Authentication Server System.
The LAN access control device needs to provide the Authenticator System of 802.1x.
The devices at the user side such as the computers need to be installed with the 802.1x
client Supplicant software, for example, the 802.1x client provided by Huawei
Technologies Co., Ltd. (or by Microsoft Windows XP). The 802.1x Authentication
Server system normally stays in the carrier’s AAA center.
Authenticator and Authentication Server exchange information through EAP
(Extensible Authentication Protocol) frames. The Supplicant and the Authenticator
exchange information through the EAPoL (Extensible Authentication Protocol over
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-2
LANs) frame defined by IEEE 802.1x. Authentication data are encapsulated in the EAP
frame, which is to be encapsulated in the packets of other AAA upper layer protocols
(e.g. RADIUS) so as to go through the complicated network to reach the Authentication
Server. Such procedure is called EAP Relay.
There are two types of ports for the Authenticator. One is the Uncontrolled Port, and the
other is the Controlled Port. The Uncontrolled Port is always in bi-directional connection
state. The user can access and share the network resources any time through the ports.
The Controlled Port will be in connecting state only after the user passes the
authentication. Then the user is allowed to access the network resources.
Supplicant
Authenticator
PAE
Authenticator
Server
Supplicant
System
Authenticator System
Authenticator
Server
System
EAP protocol
exchanges
carried in
higher layer
protocol
EAPoL
Controlled
Port
Port
unauthorized
LAN
Uncontrolled
Port
Services
offered
by
Authenticators
System
Figure 1-1 802.1x system architecture
1.1.3 802.1x Authentication Process
802.1x configures EAP frame to carry the authentication information. The Standard
defines the following types of EAP frames:
z EAP-Packet: Authentication information frame, used to carry the authentication
information.
z EAPoL-Start: Authentication originating frame, actively originated by the
Supplicant.
z EAPoL-Logoff: Logoff request frame, actively terminating the authenticated state.
z EAPoL-Key: Key information frame, supporting to encrypt the EAP packets.
z EAPoL-Encapsulated-ASF-Alert: Supports the Alerting message of Alert Standard
Forum (ASF).
The EAPoL-Start, EAPoL-Logoff and EAPoL-Key only exist between the Supplicant
and the Authenticator. The EAP-Packet information is re-encapsulated by the
Authenticator System and then transmitted to the Authentication Server System. The
EAPoL-Encapsulated-ASF-Alert is related to the network management information and
terminated by the Authenticator.
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-3
802.1x provides an implementation solution of user ID authentication. However, 802.1x
itself is not enough to implement the scheme. The administrator of the access device
should configure the AAA scheme by selecting RADIUS or local authentication so as to
assist 802.1x to implement the user ID authentication. For detailed description of AAA,
refer to the corresponding AAA configuration.
1.1.4 Implementing 802.1x on the Ethernet Switch
Quidway Series Ethernet Switches not only support the port access authentication
method regulated by 802.1x, but also extend and optimize it in the following way:
z Support to connect several End Stations in the downstream via a physical port.
z The access control (or the user authentication method) can be based on port or
MAC address.
In this way, the system becomes much securer and easier to manage.
1.2 Configuring 802.1x
The configuration tasks of 802.1x itself can be fulfilled in system view of the Ethernet
switch. When the global 802.1x is not enabled, the user can configure the 802.1x state
of the port. The configured items will take effect after the global 802.1x is enabled.
Note:
When 802.1x is enabled on a port, the max number of MAC address learning which is
configured by the command mac-address max-mac-count cannot be configured on
the port, and vice versa.
The Main 802.1x configuration includes:
z Enabling/disabling 802.1x
z Setting the port access control mode
z Setting the port access control method
z Checking the users that log on the switch via proxy
z Setting the maximum number of users via each port
z Setting the Authentication in DHCP Environment
z Configuring the authentication method for 802.1x user
z Enabling/Disabling Guest VLAN
z Setting 802.1x Re-authentication
z Setting 802.1x Client Version Authentication
z Setting the maximum times of authentication request message retransmission
z Configuring timers
z Enabling/disabling a quiet-period timer
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-4
Among the above tasks, the first one is compulsory, otherwise 802.1x will not take any
effect. The other tasks are optional. You can perform the configurations at
requirements.
1.2.1 Enabling/Disabling 802.1x
The following command can be used to enable/disable the 802.1x on the specified port
or globally. When it is used in system view, if the parameter interface-list is not specified,
802.1x will be globally enabled. If the parameter interface-list is specified, 802.1x will be
enabled on the specified port. When this command is used in Ethernet port view, the
parameter interface-list cannot be input and 802.1x can only be enabled on the current
port.
Perform the following configurations in system view or Ethernet port view.
Table 1-1 Enabling/disabling 802.1x
Operation Command
Enable the 802.1x
dot1x [ interface interface-list ]
Disable the 802.1x
undo dot1x [ interface interface-list ]
You can configure 802.1x on individual port before it is enabled globally. The
configuration will take effect right after 802.1x is enabled globally.
By default, 802.1x authentication has not been enabled globally and on any port.
1.2.2 Setting the Port Access Control Mode.
The following commands can be used for setting 802.1x access control mode on the
specified port. When no port is specified, the access control mode of all ports is
configured.
Perform the following configurations in system view or Ethernet port view.
Table 1-2 Setting the port access control mode.
Operation Command
Set the port access control mode.
dot1x port-control { authorized- force |
unauthorized-force | auto } [ interface
interface-list ]
Restore the default access control
mode of the port.
undo dot1x port-control [ interface
interface-list ]
By default, the mode of 802.1x performing access control on the port is auto (automatic
identification mode, which is also called protocol control mode). That is, the initial state
of the port is unauthorized. It only permits EAPoL packets receiving/transmitting and
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-5
does not permit the user to access the network resources. If the authentication flow is
passed, the port will be switched to the authorized state and permit the user to access
the network resources. This is the most common case.
1.2.3 Setting the Port Access Control Method
The following commands are used for setting 802.1x access control method on the
specified port. When no port is specified in system view, the access control method of
port is configured globally.
Perform the following configurations in system view or Ethernet port view.
Table 1-3 Setting the port access control method
Operation Command
Set port access control method
dot1x port-method { macbased |
portbased } [ interface interface-list ]
Restore the default port access
control method
undo dot1x port-method [ interface
interface-list ]
By default, 802.1x authentication method on the port is macbased. That is,
authentication is performed based on MAC addresses.
1.2.4 Checking the Users that Log on the Switch via Proxy
The following commands are used for checking the users that log on the switch via
proxy.
Perform the following configurations in system view or Ethernet port view.
Table 1-4 Checking the users that log on the switch via proxy
Operation Command
Enable the check for access
users via proxy
dot1x supp-proxy-check { logoff | trap }
[ interface interface-list ]
Cancel the check for access
users via proxy
undo dot1x supp-proxy-check { logoff |
trap } [ interface interface-list ]
These commands can be used to set on the specified interface when executed in
system view. The parameter interface-list cannot be input when the command is
executed in Ethernet Port view and it has effect only on the current interface. After
globally enabling proxy user detection and control in system view, only if you enable
this feature on a specific port can this configuration take effects on the port.
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-6
1.2.5 Setting the Supplicant Number on a Port
The following commands are used for setting number of users allowed by 802.1x on
specified port. When no port is specified, all the ports accept the same number of
supplicants.
Perform the following configurations in system view or Ethernet port view.
Table 1-5 Setting the maximum number of users via a specified port
Operation Command
Set maximum number of users via
specified port
dot1x max-user user-number
[ interface interface-list ]
Restore the maximum number of users on
the port to the default value
undo dot1x max-user [ interface
interface-list ]
By default, 802.1x allows up to 256 supplicants on each port for S3500 Series Ethernet
switches.
1.2.6 Setting the Authentication in DHCP Environment
If in DHCP environment the users configure static IP addresses, you can set 802.1x to
disable the switch to trigger the user ID authentication over them with the following
command.
Perform the following configurations in system view.
Table 1-6 Setting the Authentication in DHCP Environment
Operation Command
Disable the switch to trigger the user ID
authentication over the users who configure
static IP addresses in DHCP environment
dot1x dhcp-launch
Enable the switch to trigger the authentication
over them
undo dot1x dhcp-launch
By default, the switch can trigger the user ID authentication over the users who
configure static IP addresses in DHCP environment.
1.2.7 Configuring the Authentication Method for 802.1x User
The following commands can be used to configure the authentication method for
802.1x user. Three kinds of methods are available: PAP authentication (RADIUS server
must support PAP authentication), CHAP authentication (RADIUS server must support
CHAP authentication), EAP relay authentication (switch send authentication
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-7
information to RADIUS server in the form of EAP packets directly and RADIUS server
must support EAP authentication).
For EAP authentication, PEAP, EAP-TLS and EAP-MD5 methods are available on the
switch:
z EAP-TLS: The client and RADIUS server check in EAP-TLS approach mutually
the security certificate authority of the other’s, to guarantee the validity of the
certificates and prevent data from being illegally used.
z PEAP: As a kind of EAP protocol, protected EAP (PEAP) first establishes an
encrypted transport layer security (TLS) channel to provide integrity protection,
and then initiates a new type of EAP negotiation, to accomplish identity
authentication to the client.
Note:
For EAP authentication, the S3552G, S3552P, S3528G, S3528P, S3526E, S3526E
FM, S3526E FS and S3526C switches support the PEAP, EAP-TLS, and EAP-MD5
authentication. To enable any of the three, you just need to enable the EAP
authentication. However, the S3526, S3526 FM, and S3526 FS switches support
EAP-MD5 authentication only.
Perform the following configurations in system view.
Table 1-7 Configuring the authentication method for 802.1x user
Operation Command
Configure authentication method for
802.1x user (For S3552G, S3552P,
S3528G, S3528P, S3526E, S3526E FM,
S3526E FS and S3526C)
dot1x authentication-method { chap |
pap | eap }
Configure authentication method for
802.1x user (For S3526, S3526 FM and
S3526 FS)
dot1x authentication-method { chap |
pap | eap md5-challenge }
Restore the default authentication
method for 802.1x user
undo dot1x authentication-method
By default, CHAP authentication is used for 802.1x user authentication.
1.2.8 Enabling/Disabling Guest VLAN
After the Guest VLAN function is enabled, the switch broadcasts active authentication
packets to all ports on which 802.1x are enabled. If there is still some ports do not return
response packets after being re-authenticated for maximum times, the switch adds this
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-8
ports into Guest VLAN. After that, no 802.1x authentication is performed when the user
of the Guest VLAN visits the resources within this Guest VLAN. However, if the user
visits the outer resources, authentication is still needed. In this way, the requirements of
allowing unauthenticated users to access some resources are met, such as, the user
accesses some resources without installing 802.1x client, or the user upgrades 802.1x
client without authentication, and so on.
Perform the following configuration in system view or Ethernet port view.
Table 1-8 Enabling/disabling Guest VLAN
Operation Command
Enabling Guest VLAN dot1x guest-vlan vlan-id [ interface interface-list ]
Disabling Guest VLAN undo dot1x guest-vlan vlan-id [ interface interface-list ]
Note the following:
z Guest VLAN is only supported in the port-based authentication mode.
z A switch only can be configured with one Guest VLAN.
z Users who skip the authentication, fail in the authentication or get offline belong to
the Guest VLAN.
z Among S3500 series ethernet switches, S3552G, S3552P, S3528G, S3528P,
S3526E, S3526E FM, S3526E FS and S3526C support Guest VLAN, and S3526,
S3526 FM and S3526 FS don’t.
If dot1x dhcp-launch is configured on the switch, the Guest VLAN function cannot be
implemented because the switch does not send active authentication packet in this
mode.
1.2.9 Setting 802.1x Re-authentication
Note:
Among S3500 series ethernet switches, S3552G, S3552P, S3528G, S3528P, S3526E
FM, S3526E FS and S3526C support this function, and S3526, S3526 FM and S3526
FS don’t.
If the termination-action attribute on the RADIUS server is set to 1, the server then sets
the termination-action attribute in the access-accept packet which is sent to the switch
to 1. The switch re-authenticates the access user periodically after receiving this kind of
packets.
You can also enable 802.1x re-authentication on the switch through this configuration,
making the switch re-authenticates the access users periodically.

Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-9
I. Enabling 802.1x re-authentication
Before enabling the 802.1x re-authentication, you must enable the 802.1x feature both
on the port and globally.
Perform the following in system view or Ethernet port view.
Table 1-9 Enabling/disabling 802.1x user re-authentication
Operation Command
Enable 802.1x user
re-authentication
dot1x re-authenticate [ interface
interface-list ]
Disable 802.1x user
re-authentication
undo dot1x re-authenticate [ interface
interface-list ]
By default, 802.1x re-authentication is disabled on all ports.
In system view, if the interface-list parameter is not specified, it means that to enable
the 802.1x re-authentication feature on all interfaces; if the interface-list parameter is
specified, it means that to enable the feature on the specified interfaces. In Ethernet
port view, the interface-list parameter cannot be specified, and you can use command
only to enable the feature on the current interface.
II. Configuring 802.1x re-authentication timeout timer
The period of re-authentication is decided by the following two modes:
1) The switch takes the session-timeout value in the access-accept packet as the
authentication period.
2) The switch takes the value set by the user through the dot1x reauth-period
command as the authentication period. And this period defaults to 3600 seconds.
During the authentication, the switch takes the last received one as the authentication
period. For example, after the user configured the authentication period on the switch,
the switch receives the packet with the termination-action attributes of 1, and then the
switch takes the session-timeout value in the access-accept packet as the
authentication period.
Perform the following in system view.
Table 1-10 Configuring 802.1x re-authentication timeout timer
Operation Command
Configure parameters of
the timer
dot1x timer reauth-period reauth-period-value
Return to the defaults
undo dot1x timer reauth-period
By default, reauth-period-value is 3600 seconds.

Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-10
1.2.10 Setting 802.1x Client Version Authentication
Note:
Among S3500 series ethernet switches, S3552G, S3552P, S3528G, S3528P, S3526E,
S3526E FM, S3526E FS and S3526C support this function, and S3526, S3526 FM and
S3526 FS don’t.
After enabling 802.1x client version authentication, the switch authenticates the version
and validity of the 802.1x client of the access user, avoiding the access of the users at
the client with the defectively old version or at the invalid client.
I. Enabling 802.1x client version authentication
Perform the following in system view or Ethernet port view.
Table 1-11 Setting 802.1x client version authentication
Operation Command
Enable 802.1x client version
authentication
dot1x version-check [ interface
interface-list ]
Disable 802.1x client version
authentication
undo dot1x version-check [ interface
interface-list ]
By default, 802.1x client version authentication is disabled on all ports.
In system view, if the interface-list parameter is not specified, it means that to enable
the 802.1x client version authentication feature on all interfaces; if the interface-list
parameter is specified, it means that to enable the feature on the specified interfaces. In
Ethernet port view, the interface-list parameter cannot be specified, and you can use
command only to enable the feature on the current interface.
II. Configuring the maximum retry times for the switch to send version request
frame to the client
After sending client version request frame for the first time, if the switch receives no
response from the client response within a certain period of time (set by the version
authentication timeout timer), it resends version request again. When the switch
receives no response for the configured maximum times, it no longer authenticates the
version of the client, and perform the following authentications.
If configured, this command functions on all ports that enabled version authentication
function.
Perform the following in system view.
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-11
Table 1-12 Configuring the maximum retry times for the switch to send version request
frame to the client
Operation Command
Configure the maximum retry times for the
switch to send version request frame to the
client
dot1x retry-version-max
max-retry-version-value
Return to the defaults
undo dot1x retry-version-max
By default, the switch tries 3 times at the most to send version request frame to the
access user.
III. Configuring the timeout timer of version authentication
Perform the following in system view.
Table 1-13 Configuring the timeout timer of version authentication
Operation Command
Configure parameters of the timer
dot1x timer ver-period ver-period-value
Return to the defaults
undo dot1x timer ver-period
By default, ver-period-value is 1 second.
1.2.11 Setting the Maximum Times of Authentication Request Message
Retransmission
The following commands are used for setting the maximum retransmission times of the
authentication request message that the switch sends to the supplicant.
Perform the following configurations in system view.
Table 1-14 Setting the maximum times of the authentication request message
retransmission
Operation Command
Set the maximum times of the authentication
request message retransmission
dot1x retry max-retry-value
Restore the default maximum retransmission
times
undo dot1x retry
By default, the max-retry-value is 3. That is, the switch can retransmit the
authentication request message to a supplicant for 3 times at most.
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-12
1.2.12 Configuring Timers
The following commands are used for configuring the 802.1x timers.
Perform the following configurations in system view.
Table 1-15 Configuring timers
Operation Command
Configure timers
dot1x timer { handshake-period handshake-period-value |
quiet-period quiet-period-value | reauth-period
reauth-period-value | server-timeout server-timeout-value |
supp-timeout supp-timeout-value | tx-period
tx-period-value | ver-period ver-period-value }
Restore default
settings of the timers
undo dot1x timer { handshake-period | quiet-period |
reauth-period | server-timeout | supp-timeout | tx-period
| ver-period }
handshake-period: This timer begins after the user has passed the authentication.
After setting handshake-period, system will send the handshake packet by the period.
Suppose the dot1x retry time is configured as N, the system will consider the user
having logged off and set the user as logoff state if system doesn’t receive the response
from user for consecutive N times.
handshake-period-value: Handshake period. The value ranges from 1 to 1024 in units
of second and defaults to 15.
quiet-period: Specify the quiet timer. If an 802.1x user has not passed the
authentication, the Authenticator will keep quiet for a while (which is specified by
quiet-period timer) before launching the authentication again. During the quiet period,
the Authenticator does not do anything related to 802.1x authentication.
quiet-period-value: Specify how long the quiet period is. The value ranges from 10 to
120 in units of second and defaults to 60.
server-timeout: Specify the timeout timer of an Authentication Server. If an
Authentication Server has not responded before the specified period expires, the
Authenticator will resend the authentication request.
server-timeout-value: Specify how long the duration of a timeout timer of an
Authentication Server is. The value ranges from 100 to 300 in units of second and
defaults to 100 seconds.
supp-timeout: Specify the authentication timeout timer of a Supplicant. After the
Authenticator sends Request/Challenge request packet which requests the MD5
encrypted text, the supp-timeout timer of the Authenticator begins to run. If the
Supplicant does not respond back successfully within the time range set by this timer,
the Authenticator will resend the above packet.

Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-13
supp-timeout-value: Specify how long the duration of an authentication timeout timer of
a Supplicant is. The value ranges from 10 to 120 in units of second and defaults to 30.
tx-period: Specify the transmission timeout timer. After the Authenticator sends the
Request/Identity request packet which requests the user name or user name and
password together, the tx-period timer of the Authenticator begins to run. If the
Supplicant does not respond back with authentication reply packet successfully, then
the Authenticator will resend the authentication request packet.
tx-period-value: Specify how long the duration of the transmission timeout timer is. The
value ranges from 10 to 120 in units of second and defaults to 30.
reauth-period: Re-authentication timeout timer. During the time limit set by this timer,
the supplicant device launches 802.1x re-authentication.
reauth-period-value: Period set by the re-authentication timeout timer, ranging from 1 to
86400, in seconds. By default, the value is 3600.
ver-period: Client version request timeout timer. If the supplicant device failed to send
the version response packet within the time set by this timer, then the authenticator
device will resend the version request packet.
ver-period-value: Period set by the version request timeout timer, ranging from 1 to 30,
in seconds. By default, the value is 1.
1.2.13 Enabling/Disabling a Quiet-Period Timer
You can use the following commands to enable/disable a quiet-period timer of an
Authenticator (which can be a Quidway Series Ethernet Switch). If an 802.1x user has
not passed the authentication, the Authenticator will keep quiet for a while (which is
specified by dot1x timer quiet-period command) before launching the authentication
again. During the quiet period, the Authenticator does not do anything related to 802.1x
authentication.
Perform the following configuration in system view.
Table 1-16 Enabling/disabling a quiet-period timer
Operation Command
Enable a quiet-period timer
dot1x quiet-period
Disable a quiet-period timer
undo dot1x quiet-period
By default, quiet-period timer is disabled.
1.3 Displaying and Debugging 802.1x
After the above configuration, execute display command in any view to display the
running of the VLAN configuration, and to verify the effect of the configuration. Execute
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-14
reset command in user view to reset 802.1x statistics. Execute debugging command
in user view to debug 802.1x.
Table 1-17 Displaying and debugging 802.1x
Operation Command
Display the configuration, running
and statistics information of
802.1x
display dot1x [ sessions | statistics ]
[ interface interface-list ]
Reset the 802.1x statistics
information
reset dot1x statistics [ interface
interface-list ]
Enable the error/event/packet/all
debugging of 802.1x
debugging dot1x { error | event | packet |
all }
Disable the error/event/packet/all
debugging of 802.1x.
undo debugging dot1x { error | event |
packet | all }
1.4 802.1x Configuration Example
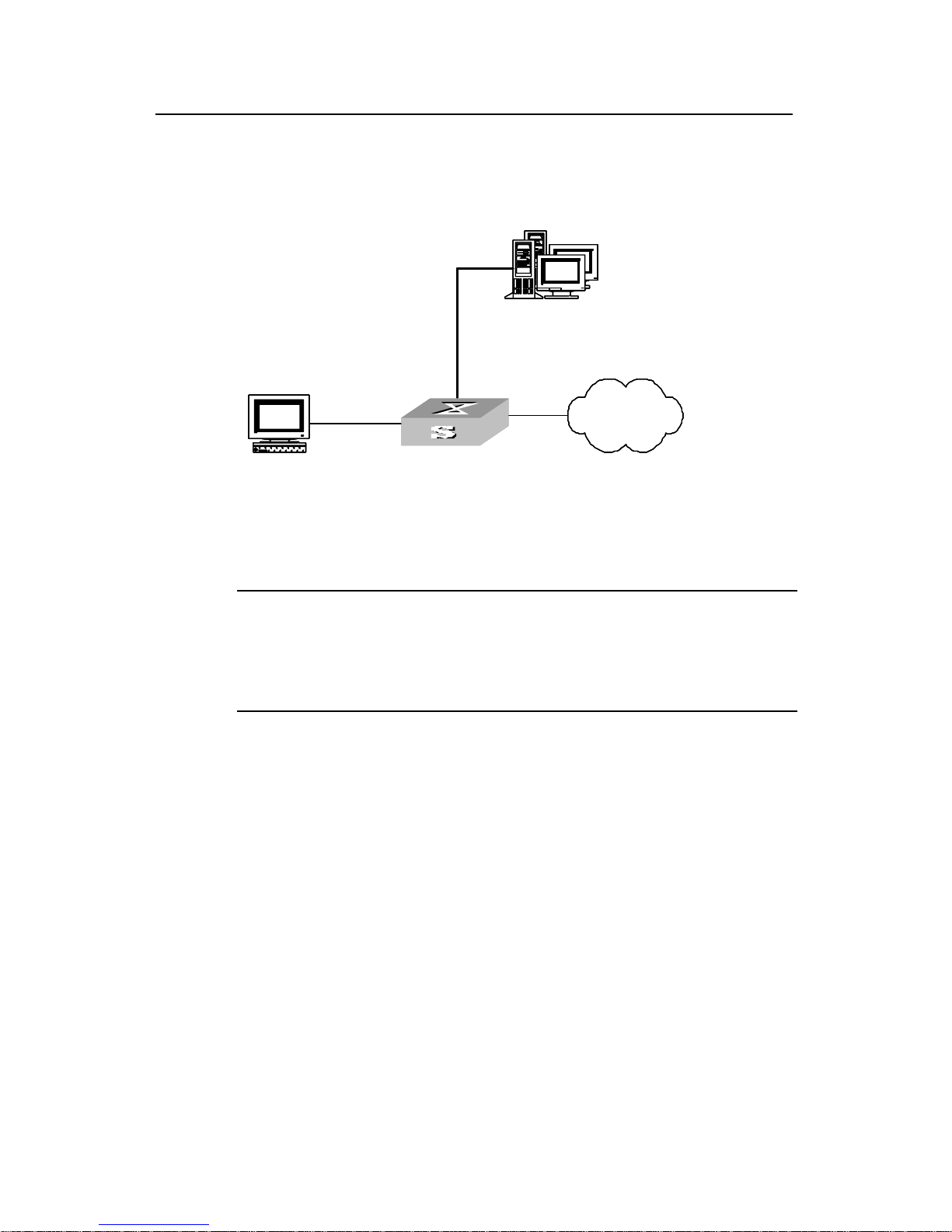
I. Networking requirements
As shown in the following figure, the workstation of a user is connected to the port
Ethernet 0/1 of the Switch.
The switch administrator will enable 802.1x on all the ports to authenticate the
supplicants so as to control their access to the Internet. The access control mode is
configured as based on the MAC address
All the supplicants belong to the default domain huawei163.net, which can contain up to
30 users. RADIUS authentication is performed first. If there is no response from the
RADIUS server, local authentication will be performed. For accounting, if the RADIUS
server fails to account, the user will be disconnected. In addition, when the user is
accessed, the domain name does not follow the user name. Normally, if the user’s
traffic is less than 2kbps consistently over 20 minutes, he will be disconnected.
A server group, consisting of two RADIUS servers at 10.11.1.1 and 10.11.1.2
respectively, is connected to the switch. The former one acts as the
primary-authentication/secondary-accounting server. The latter one acts as the
primary-accounting server. Set the encryption key as “name” when the system
exchanges packets with the authentication RADIUS server and “money” when the
system exchanges packets with the accounting RADIUS server. Configure the system
to retransmit packets to the RADIUS server if no response received in 5 seconds.
Retransmit the packet no more than 5 times in all. Configure the system to transmit a
real-time accounting packet to the RADIUS server every 15 minutes. The system is
instructed to transmit the user name to the RADIUS server after removing the user
domain name.
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-15
The user name of the local 802.1x access user is localuser and the password is
localpass (input in plain text). The idle cut function is enabled.
II. Networking diagram
Supplicant
Authentication Servers
(RADIUS Server Cluster
IP Address: 10.11.1.1
10.11.1.2)
Internet
Authenticator
Switch
Supplicant
Authentication Servers
(RADIUS Server Cluster
IP Address: 10.11.1.1
10.11.1.2)
Internet
Authenticator
Switch
Supplicant
Authentication Servers
(RADIUS Server Cluster
IP Address: 10.11.1.1
10.11.1.2)
Internet
Authenticator
Switch
E0/1
Supplicant
Authentication Servers
(RADIUS Server Cluster
IP Address: 10.11.1.1
10.11.1.2)
Internet
Authenticator
Switch
Supplicant
Authentication Servers
(RADIUS Server Cluster
IP Address: 10.11.1.1
10.11.1.2)
Internet
Authenticator
Switch
Figure 1-2 Enabling 802.1x and RADIUS to perform AAA on the supplicant
III. Configuration procedure
Note:
The following examples concern most of the AAA/RADIUS configuration commands.
For details, refer to the chapter AAA and RADIUS Protocol Configuration.
The configurations of accessing user workstation and the RADIUS server are omitted.
# Enable the 802.1x performance on the specified port Ethernet 0/1.
[Quidway] dot1x interface Ethernet 0/1
# Set the access control mode. (This command could not be configured, when it is
configured as MAC-based by default.)
[Quidway] dot1x port-method macbased interface Ethernet 0/1
# Create the RADIUS scheme radius1 and enters its view.
[Quidway] radius scheme radius1
#Set IP address of the primary authentication/accounting RADIUS servers.
[Quidway-radius-radius1] primary authentication 10.11.1.1
[Quidway-radius-radius1] primary accounting 10.11.1.2
# Set the IP address of the second authentication/accounting RADIUS servers.
[Quidway-radius-radius1] secondary authentication 127.0.0.1 1645
[Quidway-radius-radius1] secondary accounting 10.11.1.1

Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 1 802.1x Configuration
Huawei Technologies Proprietary
1-16
[Quidway-radius-radius1] quit
# Set the encryption key when the system exchanges packets with the authentication
RADIUS server.
[Quidway] local-server nas-ip 127.0.0.1 key name
[Quidway] radius scheme radius1
[Quidway-radius-radius1] key authentication name
# Set the encryption key when the system exchanges packets with the accounting
RADIUS server.
[Quidway-radius-radius1] key accounting money
# Set the timeouts and times for the system to retransmit packets to the RADIUS
server.
[Quidway-radius-radius1] timer 5
[Quidway-radius-radius1] retry 5
# Set the interval for the system to transmit real-time accounting packets to the
RADIUS server.
[Quidway-radius-radius1] timer realtime-accounting 15
# Configure the system to transmit the user name to the RADIUS server after removing
the domain name.
[Quidway-radius-radius1] user-name-format without-domain
[Quidway-radius-radius1] quit
# Create the user domain huawei163.net and enters isp configuration mode.
[Quidway] domain huawei163.net
# Specify radius1 as the RADIUS scheme for the users in the domain huawei163.net.
[Quidway-isp-huawei163.net] radius-scheme radius1
# Set a limit of 30 users to the domain huawei163.net.
[Quidway-isp-huawei163.net] access-limit enable 30
# Enable idle cut function for the user and set the idle cut parameter in the domain
huawei163.net.
[Quidway-isp-huawei163.net] idle-cut enable 20 2000
# Add a local supplicant and sets its parameter.
[Quidway] local-user localuser
[Quidway-luser-localuser] service-type lan-access
[Quidway-luser-localuser] password simple localpass
# Enable the 802.1x globally.
[Quidway] dot1x
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 2 Portal Configuration
Huawei Technologies Proprietary
2-1
Chapter 2 Portal Configuration
Note:
Among Quidway S3500 series Ethernet switches, S3552G, S3552P, S3528G and
S3528P support Portal.
2.1 Portal Overview
2.1.1 Introduction to Portal
Portal is also called Portal website. Portal authentication is also called web
authentication. Portal’s advantages include:
z Users do not need to install a client program.
z Powerful ability to support new services: Operators can implement information
inquiry, online shopping and other servers by Portal authentication.
Portal works on this principle: Unauthenticated users can only access the server for
special site. Any other accesses are redirected to a Portal server unconditionally. Users
can access the Internet only after authentication.
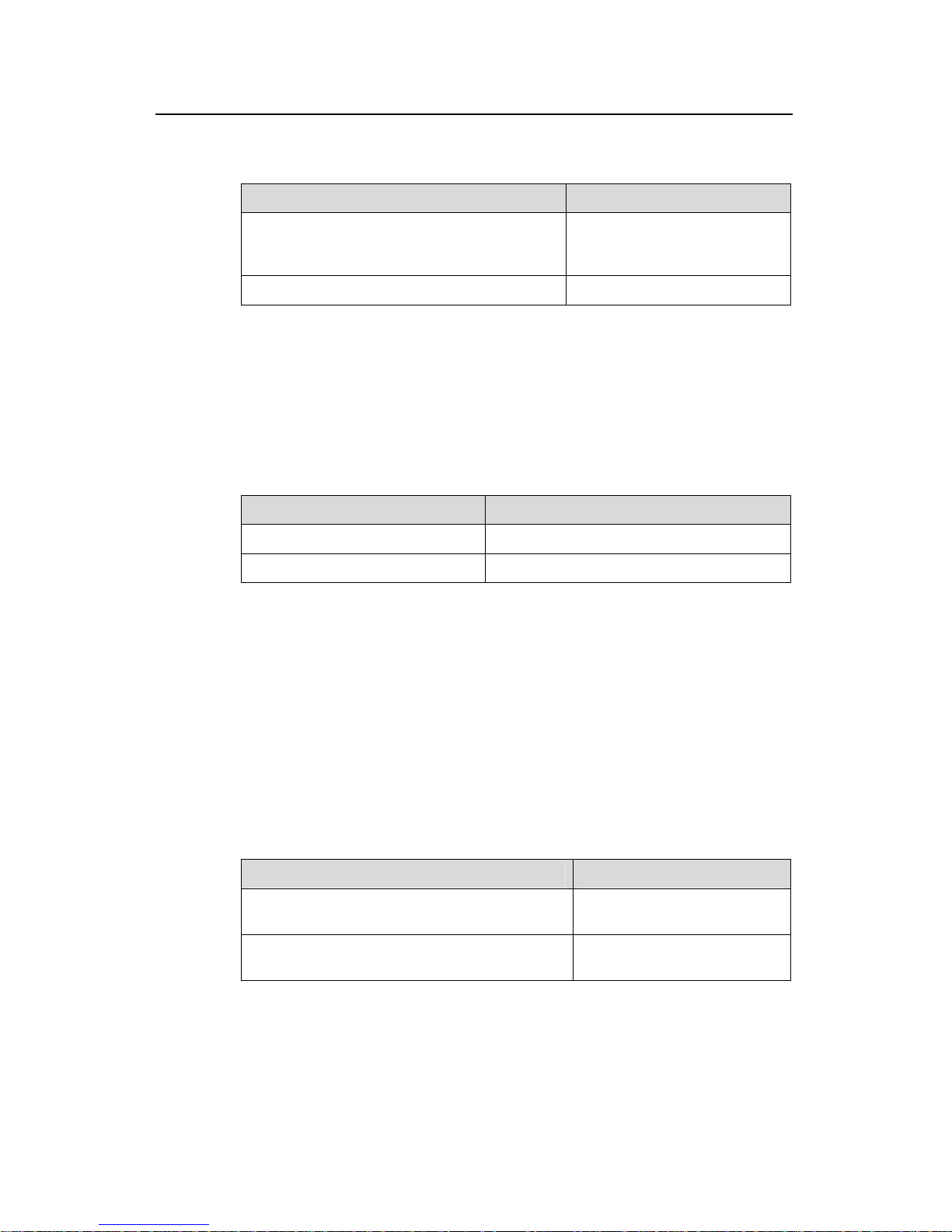
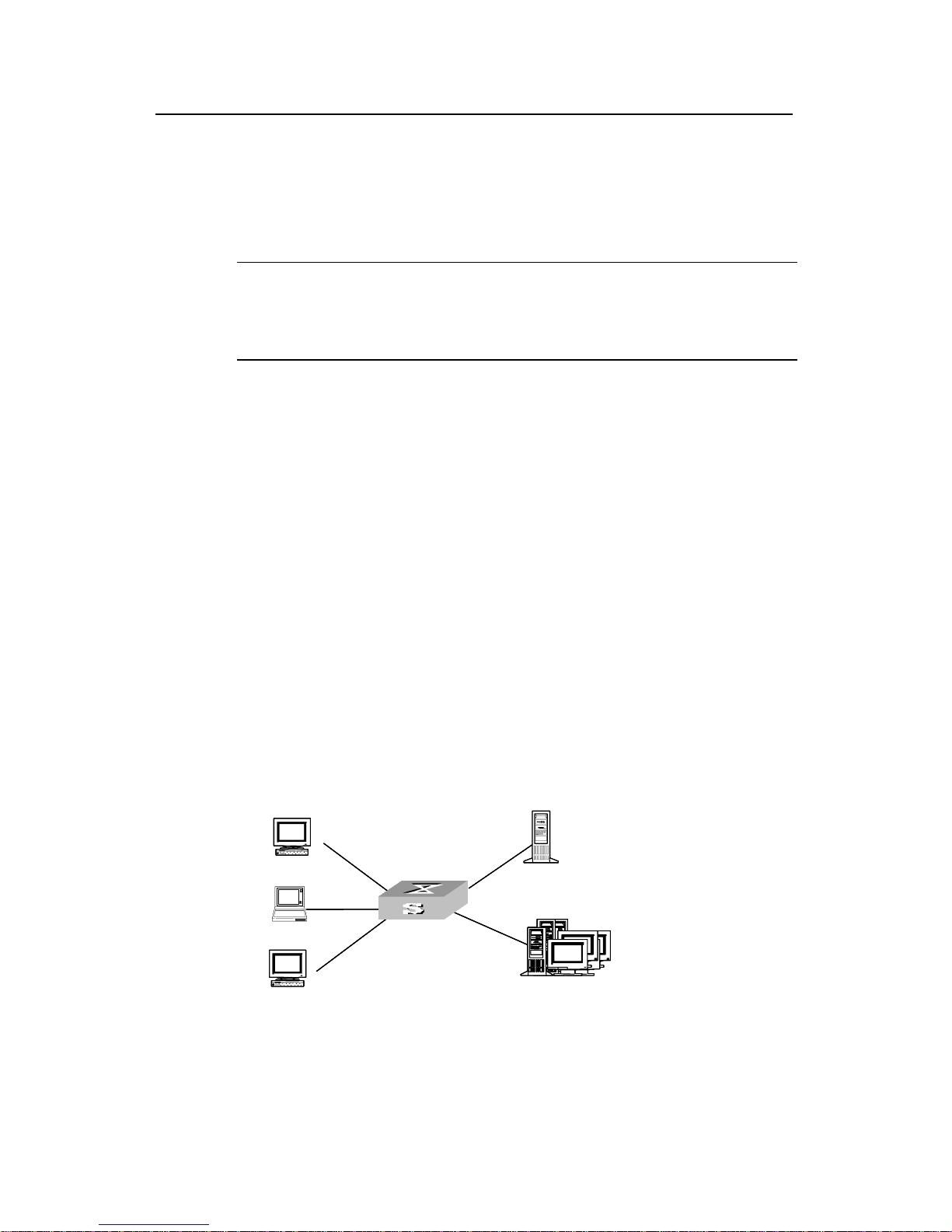
2.1.2 Portal System Composition
As shown in Figure 2-1, a Portal system consists of four basic factors: authentication
client, access device, Portal server and authentication/accounting server.
Access dev ice
Authentication client
Portal server
Authentication/ server
Authentication client
Authentication client
Access dev iceAccess dev ice
Authentication client
Portal server
Authentication client
Portal server
Authentication/Accounting server
Authentication client
Authentication client
Access dev iceAccess dev ice
Authentication client
Portal server
Authentication/ server
Authentication client
Authentication client
Access dev ice
Authentication client
Portal server
Authentication/ server
Authentication client
Authentication client
Access dev iceAccess dev iceAccess dev ice
Authentication client
Portal server
Authentication client
Portal server
Authentication client
Portal server
Authentication/Accounting server
Authentication client
Authentication client
Figure 2-1 Portal system composition
Operation Manual - Security
Quidway S3500 Series Ethernet Switches Chapter 2 Portal Configuration
Huawei Technologies Proprietary
2-2
z Authentication client: A web-based browser using HTTP/HTTPS (hypertext
transfer protocol/secure HTTP). Before users pass the authentication, all HTTP
requests are sent to the Portal server.
z Access device: Sends by force the HTTP request from the authentication client to
the Portal server unconditionally before users pass the authentication. The access
device communicates with the authentication/accounting server to implement
authentication and accounting. The access device in this manual refers to
Quidway S3552G, S3552P, S3528G and S3528P switches.
z Portal server: A web server, which users can access using the standard web
browser. The Portal server provides free portal services and the web-based
authentication interface. The access device and Portal server interact to
authenticate the client. Internet content providers (ICPs) can use the Portal server
to provide users with the information about their required sites.
z Authentication/Accounting server: Implements authentication and accounting. The
access device and the authentication/accounting server communicate through the
remote authentication dial-in user service (RADIUS) protocol.
Note:
When you use Portal services, no network address translation (NAT) devices can exist
among authentication clients, access devices, Portal servers and
authentication/accounting servers.
2.1.3 Procedures for Portal Authentication
On the Quidway series switches, the procedures for Portal authentication are as
follows:
z When receiving HTTP packets from a login user for the first time, the switch first
determines whether this login user is Portal user. If the user is Portal user, the
switch only allows the user to access the contents of the special sites (Portal
servers and configured free access addresses).
z When receiving the HTTP packets from a Portal user for access to other sites, the
switches redirect the packets to the Portal server by TCP spoofing.
z The Portal server provides web pages for the user to enter the username and
password, which are forwarded to the switch through the Portal server.
z The switch sends the user name and password to the authentication server for
authentication. The user is allowed to access the Internet only after authentication.
From then on, the switch no longer redirects the HTTP packets from the user.
 Loading...
Loading...