Huawei V300R005, Quidway NetEngine80 Configuration Manual

Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Quidway NetEngine80 Core Router
V300R005
Configuration Guide - Basic
Configurations
Issue
04
Date
2009-12-20
Part Number
00407347

Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Huawei Technologies Co., Ltd. provides customers with comprehensive technical support and service. For
any assistance, please contact our local office or company headquarters.
Huawei Technologies Co., Ltd.
Address: Huawei Industrial Base
Bantian, Longgang
Shenzhen 518129
People's Republic of China
Website: http://www.huawei.com
Email: support@huawei.com
Copyright © Huawei Technologies Co., Lt d. 2009. Al l right s reserved .
No part of this document may be reproduced or transmitted in any form or by any means without prior
written consent of Huawei Technologies Co., Ltd.
Trademarks and Permissions
and other Huawei trademarks are trademarks of Huawei Technologies Co., Ltd.
All other trademarks and trade names mentioned in this document are the property of their respective
holders.
Notice
The information in this document is subject to change without notice. Every effort has been made in the
preparation of this document to ensure accuracy of the contents, but all statements, information, and
recommendations in this document do not constitute the warranty of any kind, express or implied.

Quidway NetEngine80
Configuration Guide - Basic Configurations Contents
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
i
Contents
About This Document..................................................................................................................... 1
1 NE80 Core Router Overview....................................................................................................1-1
1.1 Introduction.................................................................................................................................................1-2
1.1.1 Overview...........................................................................................................................................1-2
1.1.2 Hardware Architecture ......................................................................................................................1-2
1.1.3 Software Architecture........................................................................................................................1-3
1.2 Characteristics of the NE80.........................................................................................................................1-5
1.2.1 Support for Flattened Network Architecture.....................................................................................1-5
1.2.2 Line-Speed Forwarding.....................................................................................................................1-6
1.2.3 Multiple Interfaces ............................................................................................................................1-6
1.2.4 Carrier-Class A vailability..................................................................................................................1-6
1.2.5 Rich Services.....................................................................................................................................1-6
1.2.6 Perfect Diff-Serv/QoS....................................................................................................................... 1-6
1.2.7 Excellent Security Mechanism..........................................................................................................1-7
1.2.8 Practical NMS...................................................................................................................................1-7
1.2.9 Flexible Networking Capabilities......................................................................................................1-8
1.3 Features List of the NE80............................................................................................................................1-8
2 Establishment of the Configuration Environment..............................................................2-1
2.1 Introduction.................................................................................................................................................2-2
2.1.1 Login Through the Console...............................................................................................................2-2
2.1.2 Login Through Telnet........................................................................................................................2-2
2.1.3 Login Through AUX Port..................................................................................................................2-2
2.2 Logging In to the Router Through the Console Port...................................................................................2-2
2.2.1 Establishing the Configuration Task..................................................................................................2-2
2.2.2 Establishing the Physical Connection ...............................................................................................2-3
2.2.3 Configuring Terminals.......................................................................................................................2-3
2.2.4 Logging In to the Router...................................................................................................................2-3
2.3 Logging In to Router Through Telnet..........................................................................................................2-4
2.3.1 Establishing the Configuration Task..................................................................................................2-4
2.3.2 Establishing the Physical Connection ...............................................................................................2-5
2.3.3 Configuring Login User Parameters..................................................................................................2-5

Contents
Quidway NetEngine80
Configuration Guide - Basic Configurations
ii
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
2.3.4 Logging In from the Telnet Client.....................................................................................................2-5
2.4 Logging In to the Router Through the AUX Port........................................................................................2-5
2.4.1 Establishing the Configuration Task..................................................................................................2-5
2.4.2 Establishing the Physical Connection ...............................................................................................2-6
2.4.3 Initializing and Configuring the Modem on the Interface.................................................................2-6
2.4.4 Configuring the Connection Between the Remote Terminal and the Router.....................................2-6
2.4.5 Logging In to the Router...................................................................................................................2-7
2.5 Configuration Examples..............................................................................................................................2-7
2.5.1 Example for Logging In Through the Console Port..........................................................................2-7
2.5.2 Example for Logging In Through Telnet...........................................................................................2-9
2.5.3 Example for Logging In Through the AUX Port.............................................................................2 -11
3 CLI Overview..............................................................................................................................3-1
3.1 Introduction.................................................................................................................................................3-2
3.1.1 Command Line Interface...................................................................................................................3-2
3.1.2 Command Levels...............................................................................................................................3-2
3.1.3 Command Line Views.......................................................................................................................3-3
3.2 Online Help.................................................................................................................................................3-6
3.2.1 Full Help............................................................................................................................................3-6
3.2.2 Partial help ........................................................................................................................................3-6
3.2.3 Error Messages of the Command Line Interface...............................................................................3-7
3.3 Features of Command Line Interface..........................................................................................................3-7
3.3.1 Editing...............................................................................................................................................3-7
3.3.2 Displaying.........................................................................................................................................3-8
3.3.3 Regular Expressions..........................................................................................................................3-8
3.3.4 History Commands..........................................................................................................................3-10
3.4 Shortcut Keys............................................................................................................................................3-11
3.4.1 Classifying Shortcut Keys...............................................................................................................3-11
3.4.2 Defining Shortcut Keys...................................................................................................................3-12
3.4.3 Use of Shortcut Keys.......................................................................................................................3-13
3.5 Configuration Examples............................................................................................................................3-13
3.5.1 Example for Using Shortcut Keys...................................................................................................3-13
3.5.2 Copying Commands Using Shortcut Keys......................................................................................3-14
3.5.3 Example for Using Tab....................................................................................................................3-14
4 Basic Configuration ...................................................................................................................4-1
4.1 Introduction.................................................................................................................................................4-2
4.2 Configuring the Basic System Environment ...............................................................................................4-2
4.2.1 Establishing the Configuration Task..................................................................................................4-2
4.2.2 Switching the Language Mode..........................................................................................................4-3
4.2.3 Configuring the Equipment Name.....................................................................................................4-3
4.2.4 Configuring the System Clock..........................................................................................................4-3
4.2.5 Configuring the Header Text.............................................................................................................4-4

Quidway NetEngine80
Configuration Guide - Basic Configurations Contents
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
iii
4.2.6 Configuring Command Levels..........................................................................................................4-4
4.3 Configuring Basic User Environment.........................................................................................................4-5
4.3.1 Establishing the Configuration Task..................................................................................................4-5
4.3.2 Configuring the Password for Switching User Levels ......................................................................4-6
4.3.3 Switching User Levels ......................................................................................................................4-6
4.3.4 Locking User Interfaces....................................................................................................................4-7
4.4 Displaying System Status Messages............................................................................................................4-7
4.4.1 Displaying System Configuration.....................................................................................................4-8
4.4.2 Displaying System Status..................................................................................................................4-8
4.4.3 Collecting System Diagostic Information.........................................................................................4-8
5 User Management ......................................................................................................................5-1
5.1 Introduction.................................................................................................................................................5-2
5.1.1 User Interface View...........................................................................................................................5-2
5.1.2 User Management .............................................................................................................................5-3
5.2 Configuring Console User Interface............................................................................................................5-5
5.2.1 Establishing the Configuration Task..................................................................................................5-5
5.2.2 Configuring Console Interface Attributes..........................................................................................5-6
5.2.3 Setting Console Terminal Attributes..................................................................................................5-7
5.2.4 Configuring the User Interface Priority............................................................................................. 5-7
5.2.5 Configuring User Authentication......................................................................................................5-8
5.2.6 Checking the Configuration............................................................................................................5-10
5.3 Configuring AUX User Interface ..............................................................................................................5-10
5.3.1 Establishing the Configuration Task................................................................................................5-10
5.3.2 Configuring AUX Interface Attributes............................................................................................5-11
5.3.3 Configuring AUX Terminal Attributes............................................................................................5-12
5.3.4 Configuring User Priority................................................................................................................5-13
5.3.5 Configuring Modem Attributes.......................................................................................................5-13
5.3.6 Configuring User Authentication....................................................................................................5-14
5.3.7 Checking the Configuration............................................................................................................5-15
5.4 Configuring VTY User Interface...............................................................................................................5-16
5.4.1 Establishing the Configuration Task................................................................................................5-16
5.4.2 Configuring Maximum VTY User Interfaces..................................................................................5-17
5.4.3 Configuring Limits for Incoming Calls and Outgoing Calls...........................................................5-17
5.4.4 Configuring Timeout of VTY User A uthorization...........................................................................5-18
5.4.5 Configuring VTY Terminal Attributes ............................................................................................5-18
5.4.6 Configuring User Authentication....................................................................................................5-19
5.4.7 Checking the Configuration............................................................................................................5-21
5.5 Managing User Interfaces..........................................................................................................................5-21
5.5.1 Establishing the Configuration Task................................................................................................5-21
5.5.2 Sending Messages to Other User Interfaces....................................................................................5-22
5.5.3 Clearing Online User.......................................................................................................................5-22

Contents
Quidway NetEngine80
Configuration Guide - Basic Configurations
iv
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
5.5.4 Checking the Configuration............................................................................................................5-22
5.6 Configuring User Management.................................................................................................................5-23
5.6.1 Establishing the Configuration Task................................................................................................5-23
5.6.2 Configuring Authentication Mode...................................................................................................5-24
5.6.3 Configuring Authentication Password.............................................................................................5-24
5.6.4 Setting Username and Password for AAA Local Authentication ....................................................5-24
5.6.5 Configuring Non-Authentication.....................................................................................................5-25
5.6.6 Configuring User Priority................................................................................................................5-26
5.6.7 Checking the Configuration............................................................................................................5-26
5.7 Configuring Local User Management.......................................................................................................5-26
5.7.1 Establishing the Configuration Task................................................................................................5-26
5.7.2 Creating Local User Account..........................................................................................................5-27
5.7.3 Configuring the Service Type of the Local User.............................................................................5-27
5.7.4 Configuring Local User Authority for FTP Directory.....................................................................5-28
5.7.5 Configuring Local User Status........................................................................................................5-28
5.7.6 Configuring Local User Priority......................................................................................................5-29
5.7.7 Configuring Access Restriction of the Local User..........................................................................5-29
5.7.8 Checking the Configuration............................................................................................................5-29
5.8 Configuration Examples............................................................................................................................5-30
5.8.1 Example for Configuring Logging In to the Router Through Password .........................................5-31
5.8.2 Example for Logging In to the Router Through AAA.....................................................................5-32
6 File System ..................................................................................................................................6-1
6.1 Introduction.................................................................................................................................................6-2
6.1.1 File System........................................................................................................................................6-2
6.1.2 Storage Devices.................................................................................................................................6-2
6.1.3 Files...................................................................................................................................................6-2
6.1.4 Directories.........................................................................................................................................6-2
6.2 Managing Storage Devices..........................................................................................................................6-2
6.2.1 Establishing the Configuration Task..................................................................................................6-2
6.2.2 Restoring Storage Devices with File System Troubles......................................................................6-3
6.2.3 Formatting Storage Devices..............................................................................................................6-3
6.3 Managing the Directory...............................................................................................................................6-4
6.3.1 Establishing the Configuration Task..................................................................................................6-4
6.3.2 Viewing the Current Directory..........................................................................................................6-5
6.3.3 Switching the Directory.....................................................................................................................6-5
6.3.4 Displaying the Directory of File........................................................................................................6-5
6.3.5 Creating a Directory..........................................................................................................................6-6
6.3.6 Deleting a Directory..........................................................................................................................6-6
6.4 Managing Files............................................................................................................................................6-6
6.4.1 Displaying Contents of Files.............................................................................................................6-7
6.4.2 Copying Files....................................................................................................................................6-7

Quidway NetEngine80
Configuration Guide - Basic Configurations Contents
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
v
6.4.3 Moving Files .....................................................................................................................................6-8
6.4.4 Renaming Files..................................................................................................................................6-8
6.4.5 Deleting Files....................................................................................................................................6-9
6.4.6 Deleting Files in the Recycle Bin......................................................................................................6-9
6.4.7 Undeleting Files ................................................................................................................................6-9
6.5 Running Files in Batch..............................................................................................................................6-10
6.6 Configuring Prompt Modes.......................................................................................................................6-10
6.7 Example of Configuration.........................................................................................................................6-11
7 Management of Configuration Files ......................................................................................7-1
7.1 Introduction.................................................................................................................................................7-2
7.1.1 Definitions.........................................................................................................................................7-2
7.1.2 Configuration Files and Current Configurations...............................................................................7-2
7.2 Managing Configuration Files.....................................................................................................................7-2
7.2.1 Establishing the Configuration Task..................................................................................................7-2
7.2.2 Configuring System Software for a Router to Load..........................................................................7-3
7.2.3 Configuring the Configuration File for Router to Load....................................................................7-3
7.2.4 Saving Configuration File.................................................................................................................7-4
7.2.5 Clearing Configuration Files.............................................................................................................7-4
7.2.6 Comparing Configuration Files.........................................................................................................7-5
7.2.7 Checking the Configuration..............................................................................................................7-5
8 FTP, TFTP and XModem ..........................................................................................................8-1
8.1 Introduction.................................................................................................................................................8-2
8.1.1 FTP....................................................................................................................................................8-2
8.1.2 TFTP .................................................................................................................................................8-2
8.1.3 XModem ...........................................................................................................................................8-2
8.2 Configuring the Router to be the FTP Server.............................................................................................. 8-3
8.2.1 Establishing the Configuration Task..................................................................................................8-3
8.2.2 Configuring the source address of FTP server...................................................................................8-4
8.2.3 Enabling the FTP Server ...................................................................................................................8-4
8.2.4 Configuring the Timeout Period........................................................................................................8-4
8.2.5 Configuring the Local Username and the Password..........................................................................8-5
8.2.6 Configuring Service Types and Authorization Information...............................................................8-5
8.2.7 Checking the Configuration..............................................................................................................8-6
8.3 Configuring FTP ACL.................................................................................................................................8-6
8.3.1 Establishing the Configuration Task..................................................................................................8-6
8.3.2 Enabling the FTP Server ...................................................................................................................8-7
8.3.3 Configuring the Basic ACL...............................................................................................................8-7
8.3.4 Configuring the Basic FTP ACL.......................................................................................................8-8
8.3.5 Checking the Configuration..............................................................................................................8-8
8.4 Configuring the Router to Be the FTP Client..............................................................................................8-9
8.4.1 Establishing the Configuration Task..................................................................................................8-9

Contents
Quidway NetEngine80
Configuration Guide - Basic Configurations
vi
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
8.4.2 Configuring the source address of FTP Client.................................................................................8-10
8.4.3 Logging In to the FTP Server..........................................................................................................8-10
8.4.4 Configuring Data Type and Transmission Mode for the File..........................................................8-10
8.4.5 Viewing Online Help of the FTP Command...................................................................................8-11
8.4.6 Uploading or Downloading Files....................................................................................................8-11
8.4.7 Managing Directories......................................................................................................................8-11
8.4.8 Managing Files................................................................................................................................8-12
8.4.9 Changing Login Users.....................................................................................................................8-13
8.4.10 Disconnecting from the FTP Server..............................................................................................8-13
8.4.11 Checking the Configuration...........................................................................................................8-14
8.5 Configuring TFTP.....................................................................................................................................8-14
8.5.1 Establishing the Configuration Task................................................................................................8-14
8.5.2 Configuring the source address of TFTP Client..............................................................................8-15
8.5.3 Downloading Files Through TFTP..................................................................................................8-15
8.5.4 Uploading Files Through TFTP ......................................................................................................8-15
8.6 Limiting the Access to the TFTP Server....................................................................................................8-16
8.6.1 Establishing the Configuration Task................................................................................................8-16
8.6.2 Configuring the Basic ACL.............................................................................................................8-16
8.6.3 Configuring the Basic TFTP ACL...................................................................................................8-17
8.7 Configuring XModem...............................................................................................................................8-17
8.7.1 Establishing the Configuration Task................................................................................................8-17
8.7.2 Getting a File Through XModem....................................................................................................8-18
8.8 Configuration Examples............................................................................................................................8-18
8.8.1 Example for Configuring the FTP Server........................................................................................8-18
8.8.2 Example for Configuring FTP ACL................................................................................................8-21
8.8.3 Example for Configuring the FTP Client........................................................................................8-23
8.8.4 Example for Configuring TFTP ......................................................................................................8-24
8.8.5 Example for Configuring XModem................................................................................................8-26
9 Telnet and SSH...........................................................................................................................9-1
9.1 Introduction.................................................................................................................................................9-2
9.1.1 Overview of User Login....................................................................................................................9-2
9.1.2 T elnet Te rm inal Services...................................................................................................................9-2
9.1.3 SSH Terminal Services......................................................................................................................9-4
9.2 Configuring T elnet Te rminal Services.........................................................................................................9-7
9.2.1 Establishing the Configuration Task..................................................................................................9-7
9.2.2 Establishing a Telnet Connection......................................................................................................9-8
9.2.3 Establishing a Telnet Redirection Connection...................................................................................9-8
9.2.4 Scheduled Telnet Disconnection.......................................................................................................9-9
9.2.5 Checking the Configuration..............................................................................................................9-9
9.3 Configuring SSH Users.............................................................................................................................9-10
9.3.1 Establishing the Configuration Task................................................................................................9-10

Quidway NetEngine80
Configuration Guide - Basic Configurations Contents
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
vii
9.3.2 Creating an SSH User .....................................................................................................................9-11
9.3.3 Configuring SSH for the VTY User Interface.................................................................................9-11
9.3.4 Generating a Local RSA Key Pair...................................................................................................9-12
9.3.5 Configuring the Authentication Mode for SSH Users.....................................................................9-12
9.3.6 (Optional)Configuring the Basic Authentication Information for SSH Users.................................9-14
9.3.7 (Optional)Authorizing SSH Users Through the Command Line ....................................................9-14
9.3.8 Configuring the Service Type of SSH Users................................................................................... 9-15
9.3.9 (Optional)Configuring the Authorized Directory of SFTP Service for SSH Users.........................9-15
9.3.10 Checking the Configuration..........................................................................................................9-15
9.4 Configuring the SSH Server......................................................................................................................9-16
9.4.1 Establishing the Configuration Task................................................................................................9-16
9.4.2 Enabling the STelnet Service...........................................................................................................9-17
9.4.3 Enabling the SFTP Service..............................................................................................................9-17
9.4.4 (Optional)Enabling the Earlier Version-Compatible Function ........................................................9-17
9.4.5 (Optional)Configuring the Number of the Port Monitored by the SSH Server...............................9-18
9.4.6 (Optional) Enabling the Trap Function............................................................................................9-18
9.4.7 (Optional)Configuring the Interval for Updating the Key Pair on the SSH Server.........................9-19
9.4.8 Checking the Configuration............................................................................................................9-19
9.5 Configuring the STelnet Client Function...................................................................................................9-20
9.5.1 Establishing the Configuration Task................................................................................................9-20
9.5.2 Enabling the First-Time Authentication on the SSH Client.............................................................9-21
9.5.3 (Optional) Configuring the SSH Client to Assign the RSA Public Key to the SSH Server ............9-21
9.5.4 Enabling the STelnet Client.............................................................................................................9-22
9.5.5 Checking the Configuration............................................................................................................9-22
9.6 Configuring the SFTP Client Function......................................................................................................9-23
9.6.1 Establishing the Configuration Task................................................................................................9-23
9.6.2 Configuring the First-Time Aut hentication on the SSH Client .......................................................9-24
9.6.3 Configuring the SSH Client to Assign the RSA Public Key to the SSH Server..............................9-24
9.6.4 Enabling the SFTP Client................................................................................................................9-25
9.6.5 (Optional) Managing the Directory.................................................................................................9-25
9.6.6 (Optional) Managing the File..........................................................................................................9-26
9.6.7 (Optional)Displaying the SFTP Client Command Help..................................................................9-27
9.6.8 Checking the Configuration............................................................................................................9-27
9.7 Maintaining Telnet and SSH......................................................................................................................9-28
9.7.1 Debugging Telnet Terminal Services...............................................................................................9-28
9.7.2 Debugging SSH Terminal Services.................................................................................................9-28
9.8 Configuration Examples............................................................................................................................9-29
9.8.1 Example for Configuring Te lnet Term inal Services........................................................................9-29
9.8.2 Example for Connecting the STelnet Client to the SSH Server.......................................................9-31
9.8.3 Example for Connecting the SFTP Client to the SSH Server..........................................................9-37
9.8.4 Example for Accessing the SSH Server Through Other Port Numbers...........................................9-42
9.8.5 Example for Authenticating SSH Through RADIUS......................................................................9-49

Contents
Quidway NetEngine80
Configuration Guide - Basic Configurations
viii
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
10 Router Maintenance ..............................................................................................................10-1
10.1 Introduction.............................................................................................................................................10-2
10.1.1 Online Upgrade introduction.........................................................................................................10-2
10.1.2 Device Operation Management.....................................................................................................10-2
10.1.3 Electronic Label ............................................................................................................................10-2
10.2 Upgrading the Board...............................................................................................................................10-2
10.2.1 Establishing the Configuration Task..............................................................................................10-3
10.2.2 Downloading the Board Software.................................................................................................10-3
10.2.3 Online Loading the Board Software..............................................................................................10-4
10.2.4 Upgrading the Stratum 3 Clock Board ..........................................................................................10-4
10.2.5 Resetting the Board.......................................................................................................................10-4
10.2.6 Checking the Configuration ..........................................................................................................10-4
10.3 Managing the Device Operation..............................................................................................................10-5
10.3.1 Setting the Temperature Warning T hreshold Upgradi ng the Board...............................................10-5
10.3.2 Disabling or Re-enabling the DASL Port of the LPU...................................................................10-5
10.3.3 Resetting the Device and Switching over the Channel..................................................................10-6
10.3.4 Displaying the Device Information...............................................................................................10-6
10.4 Configuring the Electronic Labelelectronic.............................................................................................10-7
10.4.1 Establishing the Configuration Task..............................................................................................10-7
10.4.2 Querying the Electronic Label.......................................................................................................10-7
10.4.3 Backing Up the Electronic Label ..................................................................................................10-7
10.5 Configuring a Cleaning Cycle for the Air Filter......................................................................................10-8
10.5.1 Establishing the Configuration Task..............................................................................................10-8
10.5.2 Configuring a Checking of the Air Filter based on the Device Temperature.................................10-8
10.5.3 Configuring a Cleaning Cycle for the Air Filter............................................................................10-9
10.5.4 Remonitoring the Cleaning Cycle of the Air Filter.......................................................................10-9
10.5.5 Checking the Configuration ..........................................................................................................10-9
11 System Software Upgrade ....................................................................................................11-1
11.1 Introduction.............................................................................................................................................11-2
11.1.1 System Software Upgrade.............................................................................................................11-2
11.1.2 License ..........................................................................................................................................11-2
11.2 Uploading the System Software and License Files..................................................................................11-3
11.2.1 Establishing the Configuration Task..............................................................................................11-3
11.2.2 Uploading the System Software and License to the Master MPU.................................................11-3
11.2.3 Copying the System Software and License to the Slave MPU......................................................11-4
11.2.4 Checking the Configuration...........................................................................................................11-4
11.3 Specifying the System Software for the Next Startup of the Router.......................................................11-5
11.3.1 Establishing the Configuration Task..............................................................................................11-5
11.3.2 Specifying the System Software for the Next Startup...................................................................11-5
11.3.3 (Optional) Configuring PA F Files.................................................................................................11-6
11.3.4 (Optional) Configuring Patch Packages ........................................................................................11-6

Quidway NetEngine80
Configuration Guide - Basic Configurations Contents
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
ix
11.3.5 Checking the Configuration...........................................................................................................11-7
12 Patch Management.................................................................................................................12-1
12.1 Introduction.............................................................................................................................................12-2
12.2 Checking the Running of Patch in the System........................................................................................12-3
12.2.1 Establishing the Configuration Task..............................................................................................12-3
12.2.2 Checking the Running of Patch on the MPU ................................................................................12-4
12.2.3 Checking the Running of Patch on the LPU..................................................................................12-5
12.3 Loading a Patch.......................................................................................................................................12-5
12.3.1 Establishing the Configuration Task..............................................................................................12-5
12.3.2 Uploading a Patch to the Root Directory of the Master MPU.......................................................12-6
12.3.3 Copying a Patch to the Root Directory of the Slave MPU............................................................12-6
12.4 Installing a Patch on the MPU.................................................................................................................12-7
12.4.1 Establishing the Configuration Task..............................................................................................12-7
12.4.2 Uploading the MPU Patch.............................................................................................................12-7
12.4.3 Activating the MPU Patch.............................................................................................................12-8
12.4.4 Running the MPU Patch................................................................................................................12-8
12.5 Stop Running the MPU Patch..................................................................................................................12-9
12.5.1 Establishing the Configuration Task..............................................................................................12-9
12.5.2 Deactivating the MPU Patch.........................................................................................................12-9
12.6 Unloading the MPU Patch.....................................................................................................................12-10
12.6.1 Establishing the Configuration Task............................................................................................12-10
12.6.2 Deleting the MPU Patch..............................................................................................................12-10
12.7 Installing a Patch on the LPU................................................................................................................12-11
12.7.1 Establishing the Configuration Task............................................................................................12-11
12.7.2 Uploading the LPU Patch............................................................................................................12-11
12.7.3 Activating the LPU Patch............................................................................................................12-12
12.7.4 Running the LPU Patch...............................................................................................................12-12
12.8 Stop Running the LPU Patch.................................................................................................................12-13
12.8.1 Establishing the Configuration Task............................................................................................12-13
12.8.2 Deactivating the LPU Patch........................................................................................................12-13
12.9 Unloading the LPU Patch......................................................................................................................12-13
12.9.1 Establishing the Configuration Task............................................................................................12-13
12.9.2 Deleting the LPU Patch...............................................................................................................12-14
A Glossary .................................................................................................................................... A-1
B Acronyms and Abbreviations ................................................................................................ B-1
Index ................................................................................................................................................ i-1

Quidway NetEngine80
Configuration Guide - Basic Configurations Figures
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
xi
Figures
Figure 1-1 Software architecture of the NE80-8...............................................................................................1-4
Figure 2-1 Networking diagram of logging in through the console port..........................................................2-7
Figure 2-2 New connection..............................................................................................................................2-8
Figure 2-3 Setting the port................................................................................................................................2-8
Figure 2-4 Setting the port communication param e ters....................................................................................2-9
Figure 2-5 Establishing the configuration environment through Telnet.........................................................2-10
Figure 2-6 Running the Telnet program on the PC.........................................................................................2-11
Figure 2-7 Establishing the remote configuration environment through AUX...............................................2-11
Figure 8-1 Networking diagram with FTP server basic functions..................................................................8-19
Figure 8-2 Networking diagram of configuring FTP ACL.............................................................................8-21
Figure 8-3 Configuring the FTP client............................................................................................................8-23
Figure 8-4 Networking diagram of configuring TFT P...................................................................................8-24
Figure 8-5 Setting the Base Directory of the TFTP server.............................................................................8-25
Figure 8-6 Specifying the file to be sent.........................................................................................................8-26
Figure 9-1 Telnet client services .......................................................................................................................9-2
Figure 9-2 Telnet redirection services...............................................................................................................9-3
Figure 9-3 Usage of Telnet shortcut keys.........................................................................................................9-3
Figure 9-4 Establishing an SSH channel in a LAN..........................................................................................9-5
Figure 9-5 Establishing an SSH channel in a WAN..........................................................................................9-5
Figure 9-6 Networking diagram of the Telnet terminal services mode...........................................................9-29
Figure 9-7 Networking diagram of connecting the STelnet client to the SSH server.....................................9-31
Figure 9-8 Networking diagram of connecting the SFTP client to the SSH server........................................9-37
Figure 9-9 Networking diagram of accessing the SSH server through other port numbers............................9-43
Figure 9-10 Networking diagram of authenticating the SSH through RADIUS............................................9-49
Figure 12-1 Conversion between the statuses of a patch................................................................................12-2

Quidway NetEngine80
Configuration Guide - Basic Configurations T ables
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
xiii
Tables
Table 1-1 Features list of the NE80 Series USR...............................................................................................1-8
Table 3-1 Command line views ........................................................................................................................3-4
Table 3-2 Common error messages of the command line.................................................................................3-7
Table 3-3 Keys for editing ................................................................................................................................3-7
Table 3-4 Keys for displaying...........................................................................................................................3-8
Table 3-5 Describes metacharacters..................................................................................................................3-9
Table 3-6 Access the history commands.........................................................................................................3-10
Table 3-7 System-defined shortcut keys.........................................................................................................3-11
Table 5-1 Example for the absolute numbering................................................................................................5-3

Quidway NetEngine80
Configuration Guide - Basic Configurations Contents
Issue 04 (2009-12-20)
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
i
Contents
About This Document..................................................................................................................... 1
Quidway NetEngine80
Configuration Guide - Basic Configurations About This Document
Issue 04 (2009-12-20)
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
1
About This Document
Purpose
This part describes the organization of this document, product version, intended audience,
conventions, and update history.
Related Versions
The following table lists the product versions related to this document.
Product Name Version
Quidway NetEngine80 Core Router V300R005
Intended Audience
This document is intended for:
z
Network planning engineer
z
Hardware installation engineer
z
Commissioning engineer
z
On-site maintenance engineer
z
System maintenance engineer
Organization
This document consists of twelve chapters and is orga nized as follows.
Chapter Content
1 NE80 Core Router Overview This chapter describes the architecture, functional
features and main functions of the NE80.

About This Document
Quidway NetEngine80
Configuration Guide - Basic Configurations
2
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
Chapter Content
2 Establishment of the Configuration
Environment
This chapter describes the procedures to set up the
configuration environments through CON, Telnet,
and AUX.
3 CLI Overview This chapter describes the command line interface,
command levels, command views and hot keys.
4 Basic Configurtion This chapter describes how to configure the basic
system environment on the router
5 User Management This chapter describes the basic concepts of the
user interface and the user management
6 File System This chapter describes the file system and its
configuration, uploading and downloading files
through FTP, TFTP and XModem, and the
management of configuration file.
7 Management of Configuration
Files
This chapter describes how to configure the file
management.
8 FTP,TFTP and XModem This chapter describes how to configure the basic
functions of the FTP server.
9 Telnet and SSH This chapter describes how to log in to the router
through Telnet and configure the router.
10 Router Maintenance This chapter describes the principle and concepts of
the router maintenance.
11 System Software Upgrade This chapter describes the principle and concepts of
the system software upgrade.
12 Patch Management This chapter describes the principle and concepts of
patch management.
Appendix A Glossary & B
Acronyms and Abbreviations
This chapter collates glossary and frequently used
acronyms and abbreviations in this manual.
Index This chapter collates important keywords used in
this manual to help the reader to access the required
information quickly.
Conventions
Symbol Conventions
The symbols that may be found in this document are defined as follows.

Quidway NetEngine80
Configuration Guide - Basic Configurations About This Document
Issue 04 (2009-12-20)
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
3
Symbol Description
Indicates a hazard with a high level of risk, which if not
avoided, will result in death or serious injury.
Indicates a hazard with a medium or low level of risk, which if
not avoided, could result in minor or moderate injury.
Indicates a potentially hazardous situation, which if not
avoided, could result in equipment damage, data loss,
performance degradation, or unexpected results.
Indicates a tip that may help you solve a problem or save time.
Provides additional information to emphasize or supplement
important points of the main text.
General Conventions
The general conventions that may be found in this document are defined as follows.
Convention Description
Times New Roman Normal paragraphs are in Times New Roman.
Boldface
Names of files, directories, folders, and users are in
boldface. For example, log in as user root.
Italic Book title s are in italics.
Courier New
Examples of information displayed on the screen are in
Courier New.
Command Conventions
The command conventions that may be found in this document are defined as follows.
Convention Description
Boldface
The keywords of a command line are in boldface.
Italic Command arguments are in italics.
[ ] Items (keywords or arguments) in square brackets [ ] are
optional.
{ x | y | ... } Optional items are grouped in braces and separated by
vertical bars. One item is selected.
[ x | y | ... ] Optional items are grouped in brackets and separated by
vertical bars. One item is selected or no item is selected.
About This Document
Quidway NetEngine80
Configuration Guide - Basic Configurations
4
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
Convention Description
{ x | y | ... } * Optional items are grouped in braces and separated by
vertical bars. A minimum of one item or a maximum of all
items can be selected.
[ x | y | ... ] * Optional items are grouped in brackets and separated by
vertical bars. Several items or no item can be selected.
&<1-n>
The parameter before the & sign can be repeated 1 to n
times.
# A line starting with the # sign is comments.
GUI Conventions
The GUI conventions that may be found in this document are defined as follows.
Convention Description
Boldface
Buttons, menus, parameters, tabs, windows, and dialog titles
are in boldface. For example, click OK.
> Multi-level menus are in boldface and separated by the ">"
signs. For example, choose File > Create > Folder.
Keyboard Operations
The keyboard operations that may be found in this document are defined as follows.
Format Description
Key
Press the key. For example, press Enter and press Tab.
Key 1+Key 2 Press the keys concurrently. For example, pressing
Ctrl+Alt+A means the three keys should be pressed
concurrently.
Key 1, Key 2 Press the keys in turn. For example, pressing Alt, A means
the two keys should be pressed in turn.
Mouse Operations
The mouse operations that may be found in this document are defined as follows.
Action Description
Click Select and release the primary mouse button without
moving the pointer.
Quidway NetEngine80
Configuration Guide - Basic Configurations About This Document
Issue 04 (2009-12-20)
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
5
Action Description
Double-click Press the primary mouse button twice continuously and
quickly without moving the pointer.
Drag Press and hold the primary mouse button and move the
pointer to a certain position.
Update History
Updates between document issues are cumulative. Therefore, the latest document issue
contains all updates made in previous issues.
Updates in Issue 04 (2009-12-20)
Fourth commercial release.
Updates in Issue 03 (2009-08-01)
Third commercial release.
Updates in Issue 02 (2008-10-20)
Second commercial release.
Updates in Issue 01 (2008-04-18)
First commercial release.

Quidway NetEngine80
Configuration Guide - Basic Configurations Contents
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
i
Contents
1 NE80 Core Router Overview....................................................................................................1-1
1.1 Introduction...................................................................................................................................................1-2
1.1.1 Overview..............................................................................................................................................1-2
1.1.2 Hardware Architecture.........................................................................................................................1-2
1.1.3 Software Architecture ..........................................................................................................................1-3
1.2 Characteristics of the NE80...........................................................................................................................1-5
1.2.1 Support for Flattened Network Architecture........................................................................................1-5
1.2.2 Line-Speed Forwarding........................................................................................................................1-6
1.2.3 Multiple Interfaces...............................................................................................................................1-6
1.2.4 Carrier-Class A vailability.....................................................................................................................1-6
1.2.5 Rich Services .......................................................................................................................................1-6
1.2.6 Perfect Diff-Serv/QoS..........................................................................................................................1-6
1.2.7 Excellent Security Mechanism.............................................................................................................1-7
1.2.8 Practical NMS......................................................................................................................................1-7
1.2.9 Flexible Networking Capabilities ........................................................................................................1-8
1.3 Features List of the NE80..............................................................................................................................1-8

Quidway NetEngine80
Configuration Guide - Basic Configurations Figures
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
iii
Figures
Figure 1-1 Software architecture of the NE80-8 ................................................................................................1-4

Quidway NetEngine80
Configuration Guide - Basic Configurations T ables
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
v
Tables
Table 1-1 Features list of the NE80 Series USR.................................................................................................1-8
Quidway NetEngine80
Configuration Guide - Basic Configurations 1 NE80 Core Router Overview
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
1-1
1 NE80 Core Router Overview
About This Chapter
The following table lists the contents of this chapter.
Section Describes
1.1 Introduction This section describes the hardware and software
architecture of the NE80
1.2 Characteristics of the This section describes the characteristics of the NE80
1.3 Features List of the This section describes the features of the NE80.

1 NE80 Core Router Overview
Quidway NetEngine80
Configuration Guide - Basic Configurations
1-2 Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
1.1 Introduction
This section describes the basic knowledge of the NE80 Series USR, including:
z
Overview
z
Hardware Architecture
z
Software Architecture
1.1.1 Overview
Nowadays the IP Metropolitan Area Network (MAN) has developed into a new stage. It is no
longer limited to merely supplying individual broadband internet access services, but covers
all-around services including enterprise interconnection, virtual leased line, IP telephone/
videoconferencing, content service, and security service. All these raise higher requirements
to MAN devices.
According to the development of IP MANs, Huawei launches the NE80 Series USR. The
NE80 has the following features: large capacity, high performance, high reliability, and
abundant service capability required by MANs, such as line-speed forwarding on high-speed
interface, Ethernet switching, Multi-Protocol Label Switching Virtual Private Network
(MPLS VPN), perfect Quality of Service (QoS) mechanism and carrier-class reliability, which
provide abundant service processing capabilities and flexible networking capability.
The NE80 incorporates the powerful IP service processing capability of routers and the
low-cost Ethernet switching capability of Layer 3 Ethernet switches, and serves as a powerful
core router or a Layer 3 Ethernet switch. Therefore, the NE80 is an optimal choice for new
MANs.
The NE80 is the fifth-generation router, oriented to the carrier's backbone edge networks, the
core and the convergence layer of MANs, and networks of various industries and enterprises.
The NE80 enriches and perfects the high-end router series of Huawei, for it provides
cost-effective network solutions, and offers more choices.
1.1.2 Hardware Architecture
The boards of the NE80 are classified into Switch and Routing Unit (MPU) and Line Card
(LC). The LCs include Line Processing Unit (LPU), Flexible Card Line Processing Unit
(LPUF) and service board.
MPU
The MPU completes such functions as system management, route control, data exchange, and
stratum-3 clock.
The NE80 have two MPUs for 1 + 1 redundancy. When one MPU fails, the service will be
automatically switched to the other MPU.
LPU
LPUs implement the interconnection and data forwarding with other devices. The NE80
supports the following LPUs:
z
Ethernet LPU

Quidway NetEngine80
Configuration Guide - Basic Configurations 1 NE80 Core Router Overview
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
1-3
z
POS LPU
z
cPOS LPU
z
ATM LPU
z
RPR LPU
z
E1 LPU
POS = Packet Over SONET/SDH
cPOS = channelized POS
ATM = Asynchronous Transfer Mode
RPR = Resilient Packet Ring
LPUF
LPUFs are LPUs whose PIM cards can be replaced. Each LPUF can hold two PIM cards. The
following PIM cards are supported:
z
10/100M auto-sensing Ethernet electrical interface PIM card
z
Gigabit Ethernet optical interface PIM PIC card
z
E1/T1 interface PIM card
z
E3 interface PIM card
z
T3 interface PIM card
Service Board
The NE80 provides Network Address Translation (NAT) service board. The NAT board
features large capacity and high performance, and can support the translation between private
and public network addresses. The NAT board is used to solve the problems like the shortage
of public network addresses and ensure the network security on the Internet.
For more information about the NE80 hardware system, refer to the Quidway NetEngiNE80
Core Router Installation Manual.
1.1.3 Software Architecture
The software system of the NE80 adopts the architecture of two physically independent
functional units, namely route control and packet forwarding. The architecture can improve
the stability and the processing performance of the system.
The system software consists of the following five parts: Network Management System
(NMS), Routing Process System (RPS), Forwarding Support Unit (FSU), Express Forwarding
Unit (EFU), Driver (DRV), and the switch fabric monitoring module running on the MPU
manages the MPU and monitors its operation.
DRV modules are distributed in the RPS, FSU and EFU for driving the hardware of the MPU
and the LPU. Figure 1-1 takes the NE80-8 for example to illustrate the NE80 software
architecture.
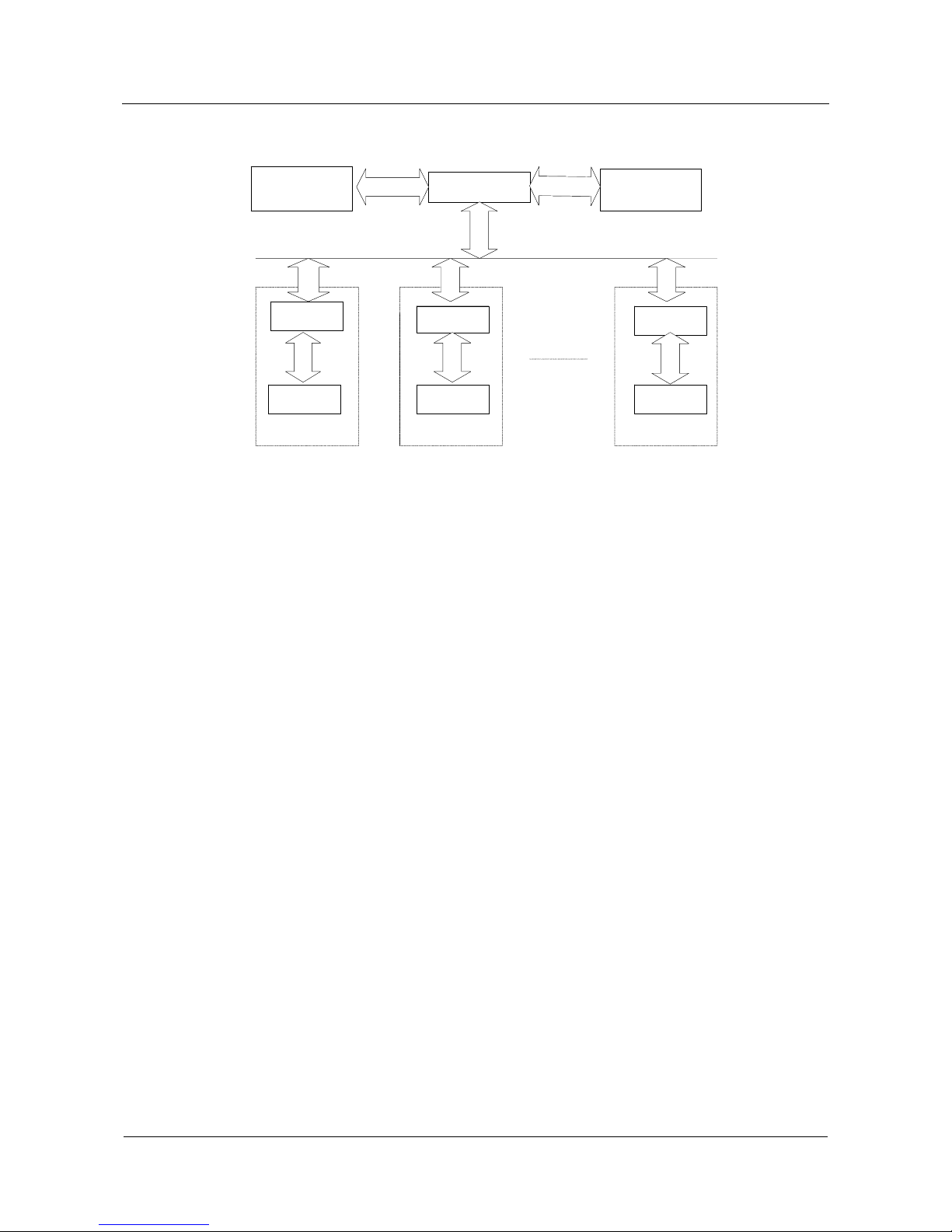
1 NE80 Core Router Overview
Quidway NetEngine80
Configuration Guide - Basic Configurations
1-4 Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
Figure 1-1 Software architecture of the NE80-8
RPS
Switch Fabric
Monitoring module
Switch Fabric
Monitoring module
FSU
EFU
Highway
FSU
EFU
Highway
FSU
EFU
Highway
Highway
Highway
Highway
Highway
Highway
Highway
RPS
Switch Fabric
Monitoring module
Switch Fabric
Monitoring module
FSU
EFU
Highway
LPU1
FSU
EFU
Highway
LPU2
FSU
EFU
LPU8
Highway
Highway
Highway
Highway
Highway
Highway
Highway
As the control and management unit of the system, the RPS runs on the active and standby
MPUs and performs the following tasks:
z
Route control
The RPS calculates and maintains the routes. In addition, it generates the Forward
Information Base (FIB) table and delivers it to each LPU for IP forwarding.
z
Label control
The RPS distributes labels, sets up and maintains the Label Switch Paths (LSPs). In addition,
it generates the FIB table and delivers it to each LPU for MPLS forwarding.
z
Traffic control
The RPS defines the traffic classification rules, configures the traffic parameters, configures
the queue resources and flow control parameters for Diff-Serv QoS.
z
Maintenance and management
The RPS maintains the devices, manages the network and devices, monitors the whole system,
diagnoses faults, and collects statistics for services.
Running on the CPU of the LPU, the FSU manages the service interfaces (configuring and
monitoring them), forwards data, controls the links, and negotiates the link parameters. In
addition, the FSU can maintain and manage local devices for LPUs and provide some system
monitoring and diagnosis services.
In addition to fast forwarding of IP packets, the EFU can provide such QoS functions as
traffic classifying, traffic measuring, traffic policing, traffic shaping, traffic scheduling, and
congestion avoiding and controlling. It can implement Diff-Serv, firewall, and Class of
Service (CoS) features according to different configuration requirements.
The Switch Fabric monitoring module monitors the internal switching network in the NE80
Series USR.
Implemented on the Huawei integrated network management platform, the NMS maintains
and controls devices uniformly.

Quidway NetEngine80
Configuration Guide - Basic Configurations 1 NE80 Core Router Overview
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
1-5
The NE80 applies the Versatile Ro uti ng Platform (VRP) software system. As a versatile
operating system platform for Huawei's data communications products, the VRP realizes a
modular architecture with IP services as the core. In addition to abundant functions and
features, the VRP provides some application-based capabilities such as scalability and
flexibility.
With the TCP/IP protocol stack as the core, the VRP integrates multiple crucial technologies
for data communications such as routing, QoS, VPN, and security, thus providing excellent
data forwarding capability for the routing device.
The VRP provides consistent network, user, and management interfaces for various hardware
platforms and flexible solutions for users. The VRP is open to sustainable development, which
can protect carriers' investment to its maximum extent.
1.2 Characteristics of the NE80
This section includes:
z
Support for Flattened Network Architecture
z
Line-Speed Forwarding
z
Multiple Interfaces
z
Carrier-Class A vailability
z
Rich Services
z
Perfect Diff-Serv/QoS
z
Excellent Security Mechanism
z
Practical NMS
z
Flexible Networking Capabilities
1.2.1 Support for Flattened Network Architecture
Modern telecom network has a hierarchical architecture, within which data services are
typically provided after they are processed by four vertical function layers. This classical
architecture will still exist for a certain period. This architecture reveals its deficiency
increasingly because IP services are becoming leading services in the network. Flattening of
the network architecture is the trend with the development of technolo gies an d the c han ge of
services.
The devices at the core layer of the telecom network are used with high efficiency because a
great amount of user data is processed there. Whereas, the devices out of the core layer are
used less efficiently due to sparse distribution of access users. Therefore, a flattened IP
network architecture should be employed if possible. Fewer network layers help carriers
utilize network devices more efficiently and slash the maintenance and management cost. The
operable and manageable IP network becomes the development trend of MANs and enterprise
networks at present.
The flattened network architecture puts forward higher requirements on the devices at the
convergence layer, that is, they need function as both access devices and core devices. The
NE80 is such a product that implements various services due to its abundant service features,
excellent hardware platform, and high reliability. For example, the NE80 can directly connect
downlink with Gigabit Ethernet switches or dedicated access devices, and uplink with
provincial backbone or national backbone networks. In addition, the NE80 can form a ring
network through Resilient Packet Ring (RPR) or connect to core devices through dual homing.

1 NE80 Core Router Overview
Quidway NetEngine80
Configuration Guide - Basic Configurations
1-6 Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
In this case, the NE80 may reduce the levels of the network construction to achieve the
flattened network, which improves the service quality and optimizes the network architecture.
1.2.2 Line-Speed Forwarding
The NE80 supports the IPv4/MPLS distributed forwarding at the line speed. Thus the NE80
can meet the bandwidth requirements when it is used as the Point of Presence (POP), the
convergence layer, or the switching node on the backbone networks.
1.2.3 Multiple Interfaces
At present, the NE80 provides the Fast Ethernet (FE) interface, Gigabit Ethernet (GE)
interface, E1/cE1 interface, E3 interface, T3 interface, Packet over SDH/SONET (POS)
interface, channelized POS (cPOS) interface, Asynchronous Transfer Mode (ATM) interface,
and RPR interface with high interface density. Users can select the cards flexibly as required
to meet the requirements for different networking solutions and network expansion.
1.2.4 Carrier-Class Availability
The key parts of the NE80 adopt redundant hot backup design, includin g system control, data
exchange, route processing system, internal management bus and power supply. All the
components are hot swappable. Thus, the router can meet the high reliability requirement
when it is used as the POP, the convergence layer, or the switching node on the backbone
networks
1.2.5 Rich Services
The IP multicast forwarding feature provides the foundation for carriers to carry on various
network voice and video services (Web TV, E-learning, telemedicine and video conference).
With the rich routing features, the router is adaptable to complex environments.
The policy service mechanism enables the system to have powerful performance optimization
capability, satisfactory attack defense capability and QoS guarantee while ensuring the line
rate processing and forwarding capability.
The application of the MPLS VPN service guarantees the delivery of services of carriers
using networks more economically and rationally with no need to increase the bandwidth.
The application of the NAT service supports addressing with public and private network
addresses mixed in the MAN to save IP addresses. In this way, the shortage of
public IP addresses can be solved.
Through Dynamic Host Configuration Protocol (DHCP) Relay and built-in DHCP Server, IP
addresses can be dynamically assigned to users and be managed.
1.2.6 Perfect Diff-Serv/QoS
The NE80 realizes the QoS feature when carrying the integrated service including the
real-time service. In particular, the NE80 provides various standard-based supports to
Diff-Serv, including:
z
Traffic classification
z
Traffic policing

Quidway NetEngine80
Configuration Guide - Basic Configurations 1 NE80 Core Router Overview
Issue 04 (2009-12-20) Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
1-7
z
Traffic shaping
z
Queue management
z
Queue Scheduling
Therefore, the NE80 can implement six groups of Per-Hop Behaviors (PHBs) defined in the
standard such as EF, AF1 to AF4 and BE as well as the other services.
The NE80 enables the network carriers to provide users with different QoS guarantee and
makes the Internet become the integrated network that carries data, voice and video services
simultaneously.
1.2.7 Excellent Security Mechanism
The NE80 provides the packet filtering/Access Control List (ACL) mechanism to prevent
illegal accesses and attacks of malicious packets.
The NE80 supports Unicast Reverse Path Forwarding (URPF) to prevent network attacks
based on the source address spoofing.
The NE80 supports port mirroring to analyze the traffic of a certain interface.
The NE80 provides multiple authentication methods (such as plain text authentication and
MD5) for key routing protocols, such as Open Shortest Path First (OSPF), Intermediate
System-Intermediate System (IS-IS), Routing Information Protocol (RIP) and Border
Gateway Protocol version 4 (BGP4).
The NE80 supports two user authentication modes: local authentication and Remote
Authentication Dial-In User Service (RADIUS) authentication to prevent illegal configuration
of the device.
The NE80 achieves the hardware-implemented NAT.
In addition, the NE80 provides abundant statistics including statistics of various types of
traffic, traffic sampling and NAT information statistics.
1.2.8 Practical NMS
Huawei Quidview NMS can manage Huawei's data communication products, supporting
Simple Network Management Protocol (SNMP) V1/V2c/V3 and the Client/Server model. It
can run on multiple operating systems, such as Windows NT/2000 and Unix (SUN, HP, and
IBM). The Quidview NMS can provide multi-language support and Graphic User Interface
(GUI).
The Quidview NMS can also be seamlessly integrated with the Huawei-dev el ope d n etw ork
management systems of other fixed network communication devices to achieve centralized
management of multiple devices. The Quidview NMS can also be integrated with the present
popular universal NMSs of the industry, such as HP OpenView, IBM NetView, What's up
Gold and SNMPc, to provide means of centralized management of devices from multiple
manufacturers.
The Quidview NMS provides the functions of managing the network topology (in real time),
faults, the performance, the configuration, device logs, security and users, QoS policy, and
VPN service. The Quidview NMS can also perform such functions as downloading, saving,
modifying and uploading NE80 configuration files and upgrading the NE80 software.

1 NE80 Core Router Overview
Quidway NetEngine80
Configuration Guide - Basic Configurations
1-8 Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
Issue 04 (2009-12-20)
1.2.9 Flexible Networking Capabilities
The NE80 has the capability of forwarding packets at the line speed, provides abundant access
means and rich service features, and offers switching capacities from 16 Gbit/s to 64 Gbit/s
for users.
The NE80 is suitable for multiple applications from the backbone core network to the edge
convergence network. The NE80 can be deployed in an IP backbone network, Intranet and
MAN core. The NE80 can also provide powerful service and flexible networking at the edge
network and the MAN convergence layer.
Diversified entire network solutions from the access network to the core network can be
provided for users when the NE80 is cooperated with Huawei's multi-service switches,
Quidway Series routers, broadband access series, LAN Switch Series, and Metro transmission
Series.
1.3 Features List of the NE80
Table 1-1 Featur es lis t of t he N E80 S eries US R
Attribute Description
LAN protocol Ethernet_II
VLAN (802.1Q)
Network
interconnection
Link layer
protocol
PPP and MP
HDLC
FR
IP over ATM
RPR
STP/RSTP/MSTP
Q-in-Q
VLANIF
Layer 2 VLAN
VLAN sub-interface
Network protocol IP service ARP
DHCP Relay
DHCP Server
IP Unnumbered
Policy routing
 Loading...
Loading...