HP V1910 User Manual

HP V1910 Switch Series
User Guide
*5998-2238*
Part number: 5998-2238 Document version: 2
1
The HP V1910 Switch Series User Guide describes the software features for the HP 1910 switches and guides you through the software configuration procedures. It also provides configuration examples to help you apply software features to different network scenarios.
This documentation set is intended for:
Network planners
Field technical support and servicing engineers
Network administrators working with the HP V1910 switches
Legal and notice information
© Copyright 2011 Hewlett-Packard Development Company, L.P.
No part of this documentation may be reproduced or transmitted in any form or by any means without prior written consent of Hewlett-Packard Development Company, L.P.
The information contained herein is subject to change without notice.
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY OF ANY KIND WITH REGARD TO THIS MATERIAL, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this material.
The only warranties for HP products and services are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.
Warranty
The Hewlett-Packard Limited Warranty Statement for this product and the HP Software License Terms which apply to any software accompanying this product are available on the HP networking Web site at http://www.hp.com/networking/warranty. The customer warranty support and services information are available on the HP networking Web site at http://www.hp.com/networking/support. Additionally, your HP-authorized network reseller can provide you with assistance, both with services that they offer and with services offered by HP.
2

Contents
Overview ······································································································································································ 1
Configuration through the web interface ··················································································································· 2
Web-based network management operating environment ·····························································································2 Logging in to the web interface··········································································································································2 Default login information ··············································································································································2 Example ··········································································································································································3 Logging out of the web interface ·······································································································································4 Introduction to the web interface········································································································································4 Web user level ·····································································································································································5 Introduction to the web-based NM functions ····················································································································5 Introduction to the common items on the web pages ··································································································· 13 Configuration guidelines·················································································································································· 15
Configuration at the CLI·············································································································································16
Getting started with the CLI ············································································································································· 16 Setting up the configuration environment················································································································· 16 Setting terminal parameters ······································································································································· 17 Logging in to the CLI··················································································································································· 20 CLI commands ··································································································································································· 21 initialize ······································································································································································· 21 ipsetup·········································································································································································· 21 password ····································································································································································· 22 ping ·············································································································································································· 23 quit················································································································································································ 23 reboot··········································································································································································· 24 summary······································································································································································· 24 upgrade ······································································································································································· 25 Configuration example for upgrading the system software image at the CLI···························································· 26
Configuration wizard·················································································································································28
Overview ··········································································································································································· 28 Basic service setup···························································································································································· 28 Entering the configuration wizard homepage ········································································································· 28 Configuring system parameters································································································································· 28 Configuring management IP address ······················································································································· 29 Finishing configuration wizard·································································································································· 31
IRF stack management ···············································································································································32
Configuring stack management ······································································································································ 32 Stack management configuration task list················································································································ 32 Configuring global parameters of a stack ··············································································································· 33 Configuring stack ports ·············································································································································· 35 Displaying topology summary of a stack ················································································································· 35 Displaying device summary of a stack ····················································································································· 36 Logging into a member switch from the master switch··························································································· 36
Stack configuration example ··········································································································································· 36 Configuration guidelines·················································································································································· 42
3
Summary·····································································································································································43
Displaying device summary············································································································································· 43 Displaying system information··································································································································· 43 Displaying device information··································································································································· 44
Device basic information configuration····················································································································46
Configuring device basic information ···························································································································· 46 Configuring system name ·········································································································································· 46 Configuring idle timeout period ································································································································ 46
System time configuration··········································································································································48
Configuring system time··················································································································································· 48 System time configuration example ································································································································ 49 Configuration guidelines·················································································································································· 51
Log management configuration ································································································································52
Configuring log management ········································································································································· 52 Configuration task list················································································································································· 52 Setting syslog related parameters ····························································································································· 52 Displaying syslog························································································································································ 53 Setting loghost····························································································································································· 55
Configuration management·······································································································································56
Back up configuration ······················································································································································ 56 Restore configuration························································································································································ 56 Save configuration···························································································································································· 57 Initialize ············································································································································································· 58
Device maintenance···················································································································································59
Software upgrade····························································································································································· 59 Device reboot ···································································································································································· 60 Electronic label·································································································································································· 61 Diagnostic information ····················································································································································· 61
File management························································································································································63
File management configuration······································································································································· 63 Displaying file list························································································································································ 63 Downloading a file····················································································································································· 64 Uploading a file·························································································································································· 64 Removing a file ··························································································································································· 64
Port management configuration································································································································65
Configuring a port ···························································································································································· 65 Setting operation parameters for a port··················································································································· 65 Viewing the operation parameters of a port ··········································································································· 69 Port management configuration example ······················································································································ 70
Port mirroring configuration ······································································································································74
Introduction to port mirroring··········································································································································· 74 Implementing port mirroring ······································································································································ 74 Configuring local port mirroring ····································································································································· 75 Configuration task list················································································································································· 75 Creating a mirroring group ······································································································································· 75 Configuring ports for a mirroring group ·················································································································· 76 Configuration examples ··················································································································································· 78 Local port mirroring configuration example············································································································· 78 Configuration guidelines·················································································································································· 81
4
User management ······················································································································································82
Overview ··········································································································································································· 82 Managing users ································································································································································ 82 Adding a local user···················································································································································· 82 Setting the super password········································································································································ 83 Switching to the management level ·························································································································· 84
Loopback test configuration ······································································································································85
Overview ··········································································································································································· 85 Loopback operation·························································································································································· 85 Configuration guidelines·················································································································································· 86
VCT··············································································································································································87
Overview ··········································································································································································· 87 Testing cable status··························································································································································· 87
Flow interval configuration········································································································································89
Overview ··········································································································································································· 89 Monitoring port traffic statistics ······································································································································· 89 Setting the traffic statistics generating interval········································································································· 89 Viewing port traffic statistics······································································································································ 89
Storm constrain configuration ···································································································································91
Overview ··········································································································································································· 91 Configuring storm constrain ············································································································································ 91 Setting the traffic statistics generating interval········································································································· 91 Configuring storm constrain ······································································································································ 92
RMON configuration ·················································································································································95
Working mechanism ·················································································································································· 95 RMON groups ···························································································································································· 96 Configuring RMON·························································································································································· 97 Configuration task list················································································································································· 97 Configuring a statistics entry ····································································································································· 99 Configuring a history entry ······································································································································100
Configuring an event entry ······································································································································101
Configuring an alarm entry ·····································································································································102
Displaying RMON statistics information ················································································································104
Displaying RMON history sampling information ··································································································106
Displaying RMON event logs··································································································································108
RMON configuration example······································································································································108
Energy saving configuration··································································································································· 113
Overview ·········································································································································································113
Configuring energy saving on a port ···························································································································113
SNMP configuration ··············································································································································· 115
SNMP mechanism ····················································································································································115
SNMP protocol version ············································································································································116
SNMP configuration ·······················································································································································116
Configuration task list···············································································································································116
Enabling SNMP ························································································································································117
Configuring an SNMP view ····································································································································119
Configuring an SNMP community ··························································································································121
Configuring an SNMP group ··································································································································122
Configuring an SNMP user ·····································································································································123
5
Configuring SNMP trap function·····························································································································125
SNMP configuration example ·······································································································································127
Interface statistics ···················································································································································· 133
Overview ·········································································································································································133
Displaying interface statistics·········································································································································133
VLAN configuration ················································································································································ 135
Introduction to VLAN ················································································································································135
VLAN fundamentals··················································································································································135
VLAN types································································································································································136
Introduction to port-based VLAN·····························································································································137
Configuring a VLAN·······················································································································································138
Configuration task list···············································································································································138
Creating VLANs ························································································································································138
Selecting VLANs························································································································································139
Modifying a VLAN····················································································································································140
Modifying ports·························································································································································142
VLAN configuration example ········································································································································143
Configuration guidelines················································································································································148
VLAN interface configuration································································································································· 149
Configuring VLAN interfaces·········································································································································149
Configuration task list···············································································································································149
Creating a VLAN interface ······································································································································149
Modifying a VLAN interface····································································································································150
Voice VLAN configuration······································································································································ 153
OUI addresses···························································································································································153
Voice VLAN assignment modes ······························································································································153
Security mode and normal mode of voice VLANs ································································································155
Configuring the voice VLAN··········································································································································155
Configuration task list···············································································································································155
Configuring voice VLAN globally ···························································································································157
Configuring voice VLAN on a port·························································································································157
Adding OUI addresses to the OUI list····················································································································159
Voice VLAN configuration examples····························································································································160
Configuring voice VLAN on a port in automatic voice VLAN assignment mode ··············································160 Configuring a voice VLAN on a port in manual voice VLAN assignment mode···············································165
Configuration guidelines················································································································································171
MAC address configuration··································································································································· 172
Configuring MAC addresses·········································································································································173
Configuring a MAC address entry ·························································································································173
Setting the aging time of MAC address entries·····································································································175
MAC address configuration example···························································································································176
MSTP configuration················································································································································· 177
STP177
STP protocol packets ················································································································································177
Basic concepts in STP ···············································································································································177
How STP works ·························································································································································178
RSTP··················································································································································································184
MSTP ················································································································································································185
STP and RSTP limitations ··········································································································································185
MSTP features····························································································································································185
6
MSTP basic concepts················································································································································185
How MSTP works······················································································································································189
Implementation of MSTP on devices ·······················································································································189
Protocols and standards···········································································································································190 Configuring MSTP···························································································································································190
Configuration task list···············································································································································190
Configuring an MST region·····································································································································190
Configuring MSTP globally······································································································································192
Configuring MSTP on a port····································································································································194
Displaying MSTP information of a port ··················································································································196
MSTP configuration example·········································································································································199
Configuration guidelines················································································································································203
Link aggregation and LACP configuration ············································································································ 205
Basic concepts···························································································································································205
Link aggregation modes···········································································································································206
Load sharing mode of an aggregation group·······································································································208
Configuring link aggregation and LACP······················································································································208
Configuration task list···············································································································································208
Creating a link aggregation group·························································································································209
Displaying information of an aggregate interface································································································211 Setting LACP priority·················································································································································211
Displaying information of LACP-enabled ports······································································································212
Link aggregation and LACP configuration example ···································································································214
Configuration guidelines················································································································································217
LLDP configuration··················································································································································· 218
Background ·······························································································································································218
Basic concepts···························································································································································218
How LLDP works························································································································································222
Compatibility of LLDP with CDP·······························································································································222
Protocols and standards···········································································································································223 Configuring LLDP·····························································································································································223
LLDP configuration task list·······································································································································223
Enabling LLDP on ports·············································································································································224
Configuring LLDP settings on ports··························································································································225
Configuring global LLDP setup ································································································································229
Displaying LLDP information for a port···················································································································231
Displaying global LLDP information ························································································································236
Displaying LLDP information received from LLDP neighbors·················································································238 LLDP configuration examples ·········································································································································238
Basic LLDP configuration example ··························································································································238
CDP-compatible LLDP configuration example ········································································································244
Configuration guidelines················································································································································250
IGMP snooping configuration ································································································································ 251
Overview ·········································································································································································251
Principle of IGMP snooping·····································································································································251
IGMP snooping related ports ··································································································································251
Work mechanism of IGMP snooping ·····················································································································252
IGMP snooping querier············································································································································254
Protocols and standards···········································································································································254 Configuring IGMP snooping··········································································································································254
Configuration task list···············································································································································254
7
Enabling IGMP snooping globally··························································································································255 Configuring IGMP snooping in a VLAN ················································································································256
Configuring IGMP snooping port functions ···········································································································257
Display IGMP snooping multicast entry information ·····························································································258
IGMP snooping configuration example························································································································259
Routing configuration·············································································································································· 266
Routing table ·····························································································································································266
Static route·································································································································································266
Default route ······························································································································································267
Configuring IPv4 routing················································································································································267
Displaying the IPv4 active route table ····················································································································267
Creating an IPv4 static route ···································································································································268
Static route configuration example ·······························································································································269
Precautions ······································································································································································273
DHCP overview ······················································································································································· 274
Introduction to DHCP······················································································································································274
DHCP address allocation···············································································································································274 Allocation mechanisms·············································································································································274
Dynamic IP address allocation process··················································································································275
IP address lease extension·······································································································································275
DHCP message format ···················································································································································276
DHCP options··································································································································································277
DHCP options overview ···········································································································································277
Introduction to DHCP options ··································································································································277
Introduction to Option 82 ········································································································································277
Protocols and standards·················································································································································278
DHCP relay agent configuration···························································································································· 279
Introduction to DHCP relay agent ·································································································································279
Application environment ··········································································································································279
Fundamentals ····························································································································································279
DHCP relay agent configuration task list······················································································································280
Enabling DHCP and configuring advanced parameters for the DHCP relay agent················································281 Creating a DHCP server group ·····································································································································282
Enabling the DHCP relay agent on an interface ·········································································································283
Configuring and displaying clients' IP-to-MAC bindings····························································································284
DHCP relay agent configuration example ···················································································································285
DHCP snooping configuration ······························································································································· 288
DHCP snooping overview··············································································································································288 Functions of DHCP snooping···································································································································288
Application environment of trusted ports················································································································289
DHCP snooping support for Option 82 ·················································································································290
DHCP snooping configuration task list ·························································································································290
Enabling DHCP snooping ··············································································································································291
Configuring DHCP snooping functions on an interface······························································································293
Displaying clients' IP-to-MAC bindings·························································································································293 DHCP snooping configuration example·······················································································································294
Service management configuration ······················································································································· 299
Configuring service management ·································································································································300
Diagnostic tools······················································································································································· 302
Ping ············································································································································································302
8
Trace route·································································································································································302
Diagnostic tool operations ·············································································································································303
Ping operation···························································································································································303
Trace route operation···············································································································································304
ARP management···················································································································································· 306
ARP overview ··································································································································································306
ARP function ······························································································································································306
ARP message format·················································································································································306
ARP operation ···························································································································································307
ARP table ···································································································································································307
Managing ARP entries····················································································································································308 Displaying ARP entries ·············································································································································308
Creating a static ARP entry······································································································································309
Static ARP configuration example···························································································································309
Gratuitous ARP ································································································································································313
Introduction to gratuitous ARP ·································································································································313
Configuring gratuitous ARP ·····································································································································313
ARP attack defense configuration ·························································································································· 315
ARP detection ··································································································································································315
Introduction to ARP detection···································································································································315
Configuring ARP detection·······································································································································317
Creating a static binding entry································································································································319
802.1X fundamentals ············································································································································· 320
Architecture of 802.1X···················································································································································320
Controlled/uncontrolled port and port authorization status·······················································································320
802.1X-related protocols ···············································································································································321
Packet formats ···························································································································································321
EAP over RADIUS······················································································································································323
Initiating 802.1X authentication····································································································································323
802.1X client as the initiator ···································································································································323
Access device as the initiator ··································································································································323
802.1X authentication procedures ·······························································································································324
A comparison of EAP relay and EAP termination ·································································································324
EAP relay ···································································································································································325
EAP termination·························································································································································327
802.1X configuration ············································································································································· 328
HP implementation of 802.1X·······································································································································328
Access control methods············································································································································328
Using 802.1X authentication with other features··································································································328
Configuring 802.1X ·······················································································································································329
Configuration prerequisites······································································································································329 802.1X configuration task list ·································································································································330
Configuring 802.1X globally ··································································································································330
Configuring 802.1X on a port ································································································································332
Configuration examples ·················································································································································334
802.1X configuration example ·······························································································································334
ACL assignment configuration example·················································································································341
AAA configuration ·················································································································································· 351
Overview ·········································································································································································351
Introduction to AAA··················································································································································351
9
Domain-based user management····························································································································352
Configuring AAA ····························································································································································352
Configuration prerequisites······································································································································352 Configuration task list···············································································································································352
Configuring an ISP domain ·····································································································································353
Configuring authentication methods for the ISP domain ······················································································354
Configuring authorization methods for the ISP domain························································································355
Configuring accounting methods for the ISP domain ···························································································356
AAA configuration example ··········································································································································358
RADIUS configuration ············································································································································· 363
Introduction to RADIUS·············································································································································363
Client/server model··················································································································································363
Security and authentication mechanisms ···············································································································363
Basic message exchange process of RADIUS ·······································································································364
RADIUS packet format··············································································································································365
Extended RADIUS attributes·····································································································································367
Protocols and standards···········································································································································368 Configuring RADIUS·······················································································································································368 Configuration task list···············································································································································368
Configuring RADIUS servers····································································································································369
Configuring RADIUS parameters ····························································································································370
RADIUS configuration example·····································································································································373
Configuration guidelines················································································································································378
Users ········································································································································································ 379
Configuring users····························································································································································379
Configuring a local user ··········································································································································379
Configuring a user group ········································································································································381
PKI configuration ····················································································································································· 383
PKI overview····································································································································································383
PKI terms ····································································································································································383
Architecture of PKI ····················································································································································383
Applications of PKI ···················································································································································384
Operation of PKI ·······················································································································································385
Configuring PKI·······························································································································································385
Configuration task list···············································································································································385
Creating a PKI entity·················································································································································388
Creating a PKI domain·············································································································································389
Generating an RSA key pair ···································································································································392
Destroying the RSA key pair····································································································································392
Retrieving a certificate··············································································································································393 Requesting a local certificate···································································································································395
Retrieving and displaying a CRL·····························································································································396
PKI configuration example·············································································································································397
Configuring a PKI entity to request a certificate from a CA·················································································397
Configuration guidelines················································································································································402
Port isolation group configuration·························································································································· 403
Overview ·········································································································································································403
Configuring a port isolation group ·······························································································································403
Port isolation group configuration example·················································································································404
10
Authorized IP configuration···································································································································· 406
Overview ·········································································································································································406
Configuring authorized IP··············································································································································406 Authorized IP configuration example ···························································································································407
Authorized IP configuration example ·····················································································································407
ACL configuration ··················································································································································· 410
ACL overview ··································································································································································410
Introduction to IPv4 ACL···········································································································································410
Effective period of an ACL·······································································································································411
ACL step·····································································································································································412
Configuring an ACL························································································································································412
Configuration task list···············································································································································412
Configuring a time range ········································································································································413
Creating an IPv4 ACL···············································································································································414
Configuring a rule for a basic IPv4 ACL ················································································································414
Configuring a rule for an advanced IPv4 ACL ······································································································416
Configuring a rule for an Ethernet frame header ACL··························································································419
Configuration guidelines················································································································································421
QoS configuration··················································································································································· 422
Introduction to QoS ························································································································································422
Networks without QoS guarantee ··························································································································422
QoS requirements of new applications ··················································································································422
Congestion: causes, impacts, and countermeasures ····························································································422
End-to-end QoS ·························································································································································424
Traffic classification ··················································································································································424
Packet precedences ··················································································································································425
Queue scheduling·····················································································································································427
Line rate ·····································································································································································429
Priority mapping ·······················································································································································430
Introduction to priority mapping tables ··················································································································431
QoS configuration ··························································································································································432
Configuration task lists ·············································································································································432
Creating a class ························································································································································434
Configuring match criteria·······································································································································435
Creating a traffic behavior ······································································································································437
Configuring traffic mirroring and traffic redirecting for a traffic behavior·························································438
Configuring other actions for a traffic behavior····································································································439
Creating a policy······················································································································································440
Configuring classifier-behavior associations for the policy··················································································440 Applying a policy to a port ·····································································································································441
Configuring queue scheduling on a port ···············································································································442
Configuring line rate on a port ·······························································································································443
Configuring priority mapping tables ······················································································································444
Configuring priority trust mode on a port ··············································································································445
Configuration guidelines················································································································································447
ACL/QoS configuration examples ························································································································ 448
ACL/QoS configuration example ·································································································································448
PoE configuration ···················································································································································· 458
PoE overview···································································································································································458
Advantages ·······························································································································································458
Composition ······························································································································································458
11
Protocol specification ···············································································································································459
Configuring PoE······························································································································································459
Configuring PoE ports ··············································································································································459
Configuring non-standard PD detection ·················································································································461
Displaying information about PSE and PoE ports··································································································462 PoE configuration example ············································································································································462
Support and other resources ·································································································································· 465
Contacting HP ·································································································································································465
Related information·························································································································································465
Conventions·····································································································································································465 Subscription service························································································································································466
Index ········································································································································································ 467
12

Overview
The HP V1910 Switch Series can be configured through the command line interface (CLI), web interface, and SNMP/MIB. These configuration methods are suitable for different application scenarios.
The web interface supports all V1910 Switch Series configurations.
The CLI provides some configuration commands to facilitate your operation. To perform other configurations not supported by the CLI, use the web interface.
1
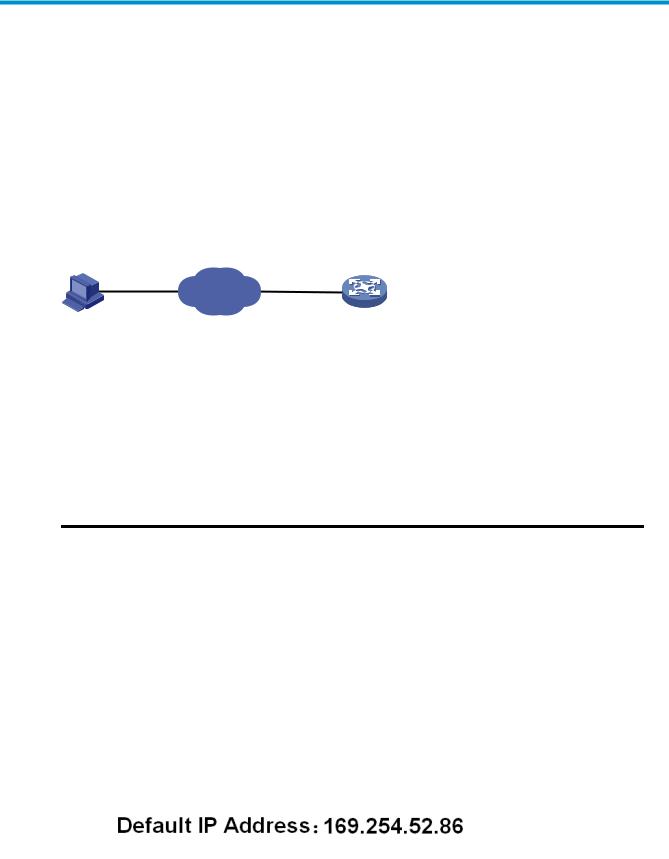
Configuration through the web interface
Web-based network management operating environment
HP provides the web-based network management function to facilitate the operations and maintenance on HP’s network devices. Through this function, the administrator can visually manage and maintain network devices through the web-based configuration interfaces.
a.Web-based network management operating environment
Logging in to the web interface
Default login information
The device is provided with the default Web login information. You can use the default information to log in to the web interface.
1.The default web login information
Information needed at login |
Default value |
|
Username |
admin |
|
|
|
|
Password |
None |
|
|
|
|
IP address of the device (VLAN-interface 1) |
Default IP address of the device, depending on the status |
|
of the network where the device resides. |
||
|
||
|
|
Table 1 The device is not connected to the network, or no DHCP server exists in the subnet where the device resides
If the device is not connected to the network, or no DHCP server exists in the subnet where the device resides, you can get the default IP address of the device on the label on the device, as shown in b. The default subnet mask is 255.255.0.0.
b.Default IP address of the device
2
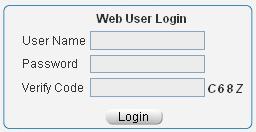
Table 2 A DHCP server exists in the subnet where the device resides
If a DHCP server exists in the subnet where the device resides, the device will dynamically obtain its default IP address through the DHCP server. You can log in to the device through the console port, and execute the summary command to view the information of its default IP address.
<Sysname> summary |
|
Select menu option: |
Summary |
IP Method: |
DHCP |
IP address: |
10.153.96.86 |
Subnet mask: |
255.255.255.0 |
Default gateway: |
0.0.0.0 |
<Omitted> |
|
Example
Assuming that the default IP address of the device is 169.254.52.86, follow these steps to log in to the device through the web interface.
Connect the device to a PC
Connect the GigabitEthernet interface of the device to a PC by using a crossover Ethernet cable (by default, all interfaces belong to VLAN 1).
Configure an IP address for the PC and ensure that the PC and device can communicate with each other properly.
Select an IP address for the PC from network segment 169.254.0.0/16 (except for the default IP address of the device), for example, 169.254.52.86.
Open the browser, and input the login information.
On the PC, open the browser (IE 5.0 or later), type the IP address http://169.254.52.86 in the address bar, and press Enter to enter the login page of the web interface, as shown in a. Input the username admin and verification code, leave the password blank, and click Login.
a.Login page of the web interface
3
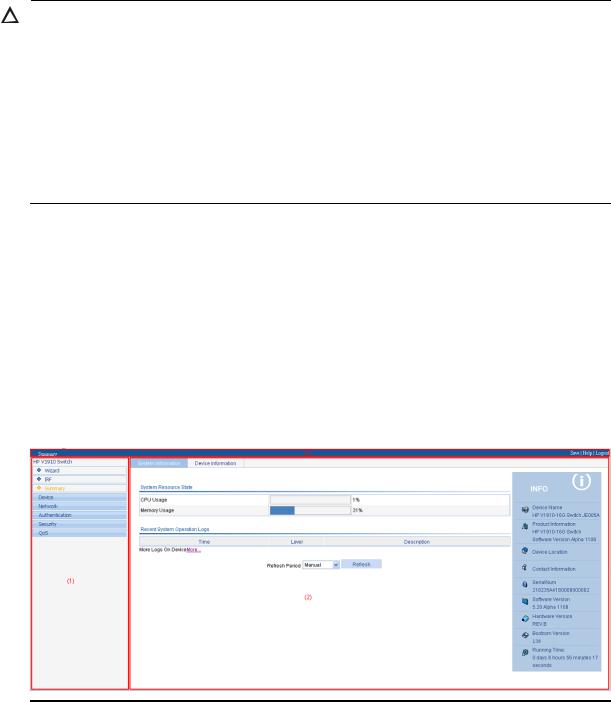
CAUTION:
The PC where you configure the device is not necessarily a web-based network management terminal. A web-based network management terminal is a PC used to log in to the web interface and is required to be reachable to the device.
After logging in to the web interface, you can select Device Users from the navigation tree, create a new user, and select Wizard or Network VLAN interface to configure the IP address of the VLAN interface acting as the management interface. For more information, see the corresponding configuration guides of these modules.
If you click the verification code displayed on the web login page, you can get a new verification code.
Up to five users can concurrently log in to the device through the web interface.
Logging out of the web interface
Click Logout in the upper-right corner of the web interface, as shown in a to quit the web console.
The system does not save the current configuration automatically. Therefore, it is recommended to save the current configuration before logout.
Introduction to the web interface
The Web interface is composed of three parts: navigation tree, title area, and body area, as shown in a.
a.Web-based configuration interface
(1) Navigation tree |
(2) Body area |
(3) Title area |
Navigation tree—Organizes the web-based NM functions as a navigation tree, where you can select and configure functions as needed. The result is displayed in the body area.
Body area—Allows you to configure and display features.
Title area—Displays the path of the current configuration interface in the navigation tree; provides the Help button to display the web related help information, and the Logout button to log out of the web interface.
4

CAUTION:
The web network management functions not supported by the device are not displayed in the navigation tree.
Web user level
Web user levels, from low to high, are visitor, monitor, configure, and management. A user with a higher level has all the operating rights of a user with a lower level.
Visitor—Users of this level can only use the network diagnostic tools ping and Trace Route. They can neither access the device data nor configure the device.
Monitor—Users of this level can only access the device data but cannot configure the device.
Configure—Users of this level can access device data and configure the device, but they cannot upgrade the host software, add/delete/modify users, or back up/restore configuration files.
Management—Users of this level can perform any operations to the device.
Introduction to the web-based NM functions
NOTE:
User level in 1 indicates that users of this level or users of a higher level can perform the corresponding operations.
1.Description of Web-based NM functions
Function menu |
|
Description |
User level |
||
Wizard |
|
IP Setup |
Allows you to perform quick configuration of the |
Management |
|
|
device. |
||||
|
|
|
|
||
|
|
|
|
|
|
|
|
|
Displays global settings and port settings of a |
Configure |
|
|
|
|
stack. |
||
|
|
Setup |
|
||
|
|
|
|
||
|
|
Allows you to configure global parameters and |
Management |
||
|
|
|
|||
|
|
|
stack ports. |
||
IRF |
|
|
|
||
|
|
|
|
||
|
Topology |
Displays the topology summary of a stack. |
Configure |
||
|
|
||||
|
|
Summary |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Device |
Displays the control panels of stack members. |
Configure |
|
|
|
Summary |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
System |
Displays the basic system information, system |
Monitor |
|
|
|
Information |
resource state, and recent system operation logs. |
||
Summary |
|
||||
|
|
|
|||
Device |
Displays the port information of the device. |
Monitor |
|||
|
|
||||
|
|
Information |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
System Name |
Displays and allows you to configure the system |
Configure |
|
Devi |
|
name. |
|||
Basic |
|
|
|||
|
|
|
|||
ce |
Web Idle |
Displays and allows you to configure the idle |
Configure |
||
|
|||||
|
|
||||
|
|
Timeout |
timeout period for logged-in users. |
||
|
|
|
|||
|
|
|
|
|
|
5

Function menu |
|
Description |
User level |
||
|
|
Software |
Allows you to configure to upload upgrade file |
Management |
|
|
|
Upgrade |
from local host, and upgrade the system software. |
||
|
|
|
|||
|
Device |
|
|
|
|
|
Reboot |
Allows you to configure to reboot the device. |
Management |
||
|
Maintenan |
|
|
|
|
Electronic Label |
Displays the electronic label of the device. |
Monitor |
|||
|
ce |
||||
|
|
Diagnostic |
Generates diagnostic information file, and allows |
Management |
|
|
|
Information |
you to view or save the file to local host. |
||
|
|
|
|||
|
|
|
|
|
|
|
System |
System Time |
Displays and allows you to configure the system |
Configure |
|
|
Time |
date and time. |
|||
|
|
|
|||
|
|
|
|
|
|
|
|
Loglist |
Displays and refreshes system logs. |
Monitor |
|
|
|
|
|
||
|
|
Allows you to clear system logs. |
Configure |
||
|
|
|
|||
|
Syslog |
|
|
|
|
|
Loghost |
Displays and allows you to configure the loghost. |
Configure |
||
|
|
||||
|
|
|
|
|
|
|
|
Log Setup |
Displays and allows you to configure the buffer |
Configure |
|
|
|
capacity, and interval for refreshing system logs. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
|
Allows you to back up the configuration file to be |
|
|
|
|
Backup |
used at the next startup from the device to the host |
Management |
|
|
|
|
of the current user. |
|
|
|
|
|
|
|
|
|
Configurati |
|
Allows you to upload the configuration file to be |
|
|
|
Restore |
used at the next startup from the host of the current |
Management |
||
|
on |
|
user to the device. |
|
|
|
|
|
|
|
|
|
|
Save |
Allows you to save the current configuration to the |
Configure |
|
|
|
configuration file to be used at the next startup. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Initialize |
Allows you to restore the factory default settings. |
Configure |
|
|
|
|
|
|
|
|
File |
File |
Allows you to manage files on the device, such as |
|
|
|
Managem |
displaying the file list, downloading a file, |
Management |
||
|
Management |
||||
|
ent |
uploading a file, and removing a file. |
|
||
|
|
|
|||
|
|
|
|
|
|
|
|
Summary |
Displays port information by features. |
Monitor |
|
|
Port |
|
|
|
|
|
Detail |
Displays feature information by ports. |
Monitor |
||
|
Managem |
||||
|
|
|
|
||
|
ent |
Setup |
Allows you to create, modify, delete, and |
Configure |
|
|
|
enable/disable a port, and clear port statistics. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Summary |
Displays the configuration information of a port |
Monitor |
|
|
|
mirroring group. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
Port |
Create |
Allows you to create a port mirroring group. |
Configure |
|
|
|
|
|
||
|
Mirroring |
Remove |
Allows you to remove a port mirroring group. |
Configure |
|
|
|
||||
|
|
|
|
|
|
|
|
Modify Port |
Allows you to configure ports for a mirroring |
Configure |
|
|
|
group. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Summary |
Displays the brief information of FTP and Telnet |
Monitor |
|
|
|
users. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
Users |
|
Allows you to configure a password for a |
|
|
|
Super Password |
lower-level user to switch from the current access |
Management |
||
|
|
||||
|
|
|
level to the management level. |
|
|
|
|
|
|
|
|
|
|
Create |
Allows you to create an FTP or Telnet user. |
Management |
|
|
|
|
|
|
|
6

Function menu |
|
Description |
User level |
|
|
|
Modify |
Allows you to modify FTP or Telnet user |
Management |
|
|
information. |
||
|
|
|
|
|
|
|
|
|
|
|
|
Remove |
Allows you to remove an FTP or a Telnet user. |
Management |
|
|
|
|
|
|
|
Switch To |
Allows you to switch the current user level to the |
Visitor |
|
|
Management |
management level. |
|
|
|
|
||
|
|
|
|
|
|
Loopback |
Loopback |
Allows you to perform loopback tests on Ethernet |
Configure |
|
interfaces. |
|||
|
|
|
|
|
|
|
|
|
|
|
VCT |
VCT |
Allows you to check the status of the cables |
Configure |
|
connected to Ethernet ports. |
|||
|
|
|
|
|
|
|
|
|
|
|
|
Port Traffic |
Displays the average rate at which the interface |
|
|
|
receives and sends packets within a specified time |
Monitor |
|
|
Flow |
Statistics |
||
|
interval. |
|
||
|
|
|
||
|
Interval |
|
|
|
|
Interval |
Allows you to set an interval for collecting traffic |
Configure |
|
|
|
|||
|
|
Configuration |
statistics on interfaces. |
|
|
|
|
||
|
|
|
|
|
|
|
|
Displays and allows you to set the interval for |
|
|
Storm |
Storm Constrain |
collecting storm constrain statistics. |
Configure |
|
Constrain |
Displays, and allows you to create, modify, and |
||
|
|
|
||
|
|
|
remove the port traffic threshold. |
|
|
|
|
|
|
|
|
Statistics |
Displays, and allows you to create, modify, and |
Configure |
|
|
clear RMON statistics. |
||
|
|
|
|
|
|
|
|
|
|
|
|
History |
Displays, and allows you to create, modify, and |
Configure |
|
|
clear RMON history sampling information. |
||
|
|
|
|
|
|
|
|
|
|
|
RMON |
Alarm |
Allows you to view, create, modify, and clear |
Configure |
|
|
alarm entries. |
||
|
|
|
|
|
|
|
|
|
|
|
|
Event |
Allows you to view, create, modify, and clear event |
Configure |
|
|
entries. |
||
|
|
|
|
|
|
|
|
|
|
|
|
Log |
Displays log information about RMON events. |
Configure |
|
|
|
|
|
|
Energy |
Energy Saving |
Displays and allows you to configure the energy |
Configure |
|
Saving |
saving settings of an interface. |
||
|
|
|
||
|
|
|
|
|
|
|
|
Displays and refreshes SNMP configuration and |
Monitor |
|
|
Setup |
statistics information. |
|
|
|
|
||
|
|
|
|
|
|
|
|
Allows you to configure SNMP. |
Configure |
|
|
|
|
|
|
|
|
Displays SNMP community information. |
Monitor |
|
|
Community |
|
|
|
|
Allows you to create, modify and delete an SNMP |
Configure |
|
|
|
|
||
|
|
|
community. |
|
|
SNMP |
|
|
|
|
|
|
|
|
|
|
Displays SNMP group information. |
Monitor |
|
|
|
|
||
|
|
Group |
|
|
|
|
Allows you to create, modify and delete an SNMP |
Configure |
|
|
|
|
||
|
|
|
group. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Displays SNMP user information. |
Monitor |
|
|
User |
|
|
|
|
Allows you to create, modify and delete an SNMP |
Configure |
|
|
|
|
||
|
|
|
user. |
|
|
|
|
|
|
|
|
|
|
|
7

Function menu |
|
Description |
User level |
||
|
|
|
Displays the status of the SNMP trap function and |
Monitor |
|
|
|
|
information about target hosts. |
||
|
|
Trap |
|
||
|
|
|
|
||
|
|
Allows you to enable or disable the SNMP trap |
Configure |
||
|
|
|
|||
|
|
|
function, or create, modify and delete a target host. |
||
|
|
|
|
||
|
|
|
|
|
|
|
|
|
Displays SNMP view information. |
Monitor |
|
|
|
View |
|
|
|
|
|
Allows you to create, modify and delete an SNMP |
Configure |
||
|
|
|
|||
|
|
|
view. |
||
|
|
|
|
||
|
|
|
|
|
|
|
Interface |
Interface |
Displays and allows you to clear the statistics |
Configure |
|
|
Statistics |
Statistics |
information of an interface. |
||
|
|
||||
|
|
|
|
|
|
|
|
Select VLAN |
Allows you to select a VLAN range. |
Monitor |
|
|
|
|
|
|
|
|
|
Create |
Allows you to create VLANs. |
Configure |
|
|
|
|
|
|
|
|
|
Port Detail |
Displays the VLAN-related details of a port. |
Monitor |
|
|
|
|
|
|
|
|
|
Detail |
Displays the member port information of a VLAN. |
Monitor |
|
|
VLAN |
|
|
|
|
|
Modify VLAN |
Allows you to modify the description and member |
Configure |
||
|
|
||||
|
|
ports of a VLAN. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Modify Port |
Allows you to change the VLAN to which a port |
Configure |
|
|
|
belongs. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Remove |
Allows you to remove VLANs. |
Configure |
|
|
|
|
|
|
|
|
|
Summary |
Displays information about VLAN interfaces by |
Monitor |
|
|
|
address type. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
VLAN |
Create |
Allows you to create VLAN interfaces and |
Configure |
|
|
configure IP addresses for them. |
||||
|
|
|
|||
|
Interface |
|
|
|
|
|
Modify |
Allows you to modify the IP addresses and status of |
Configure |
||
|
|
||||
|
|
VLAN interfaces. |
|||
|
|
|
|
||
Net |
|
|
|
||
Remove |
Allows you to remove VLAN interfaces. |
Configure |
|||
work |
|
||||
|
|
|
|
||
|
Summary |
Displays voice VLAN information globally or on a |
Monitor |
||
|
|
||||
|
|
port. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Setup |
Allows you to configure the global voice VLAN. |
Configure |
|
|
|
|
|
|
|
|
|
Port Setup |
Allows you to configure a voice VLAN on a port. |
Configure |
|
|
Voice |
|
|
|
|
|
OUI Summary |
Displays the addresses of the OUIs that can be |
Monitor |
||
|
VLAN |
||||
|
identified by voice VLAN. |
||||
|
|
|
|
||
|
|
|
|
|
|
|
|
OUI Add |
Allows you to add the address of an OUI that can |
Configure |
|
|
|
be identified by voice VLAN. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
OUI Remove |
Allows you to remove the address of an OUI that |
Configure |
|
|
|
can be identified by voice VLAN. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
MAC |
Displays MAC address information. |
Monitor |
|
|
|
|
|
||
|
MAC |
Allows you to create and remove MAC addresses. |
Configure |
||
|
|
||||
|
|
|
|
||
|
Setup |
Displays and allows you to configure MAC address |
Configure |
||
|
|
||||
|
|
aging time. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
MSTP |
Region |
Displays information about MST regions. |
Monitor |
|
|
|
|
|
|
|
8

Function menu |
|
Description |
User level |
|
|
|
|
Allows you to modify MST regions. |
Configure |
|
|
|
|
|
|
|
Global |
Allows you to set global MSTP parameters. |
Configure |
|
|
|
|
|
|
|
Port Summary |
Displays the MSTP information of ports. |
Monitor |
|
|
|
|
|
|
|
Port Setup |
Allows you to set MSTP parameters on ports. |
Configure |
|
|
|
|
|
|
|
Summary |
Displays information about link aggregation |
Monitor |
|
|
groups. |
||
|
Link |
|
|
|
|
|
|
|
|
|
Create |
Allows you to create link aggregation groups. |
Configure |
|
|
Aggregati |
|||
|
|
|
|
|
|
on |
Modify |
Allows you to modify link aggregation groups. |
Configure |
|
|
|||
|
|
|
|
|
|
|
Remove |
Allows you to remove link aggregation groups. |
Configure |
|
|
|
|
|
|
|
Summary |
Displays information about LACP-enabled ports |
Monitor |
|
LACP |
and their partner ports. |
||
|
|
|
||
|
|
|
|
|
|
|
Setup |
Allows you to set LACP priorities. |
Configure |
|
|
|
|
|
|
|
|
Displays the LLDP configuration information, local |
|
|
|
Port Setup |
information, neighbor information, statistics |
Monitor |
|
|
information, and status information of a port. |
|
|
|
|
|
|
|
|
|
|
Allows you to modify LLDP configuration on a port. Configure |
|
|
|
|
|
|
|
LLDP |
Global Setup |
Displays global LLDP configuration information. |
Monitor |
|
|
|
||
|
Allows you to configure global LLDP parameters. |
Configure |
||
|
|
|
||
|
|
|
|
|
|
|
Global |
Displays global LLDP local information and |
Monitor |
|
|
Summary |
statistics. |
|
|
|
|
||
|
|
|
|
|
|
|
Neighbor |
Displays global LLDP neighbor information. |
Monitor |
|
|
Summary |
||
|
|
|
|
|
|
|
|
|
|
|
|
|
Displays global IGMP snooping configuration |
|
|
|
|
information or the IGMP snooping configuration |
Monitor |
|
|
|
information in a VLAN, and allows you to view the |
|
|
|
Basic |
|
|
|
|
IGMP snooping multicast entry information. |
|
|
|
IGMP |
|
|
|
|
|
Allows you to configure IGMP snooping globally or |
Configure |
|
|
Snooping |
|
in a VLAN. |
|
|
|
|
||
|
|
|
|
|
|
|
|
Displays the IGMP snooping configuration |
Monitor |
|
|
Advanced |
information on a port. |
|
|
|
|
||
|
|
|
|
|
|
|
|
Allows you to configure IGMP snooping on a port. Configure |
|
|
|
|
|
|
|
|
Summary |
Displays the IPv4 active route table. |
Monitor |
|
IPv4 |
|
|
|
|
Create |
Allows you to create an IPv4 static route. |
Configure |
|
|
Routing |
|||
|
|
|
|
|
|
Remove |
Allows you to delete the selected IPv4 static routes. |
Configure |
|
|
|
|||
|
|
|
|
|
|
|
|
Displays information about the DHCP status, |
|
|
|
|
advanced configuration information of the DHCP |
|
|
DHCP |
DHCP Relay |
relay agent, DHCP server group configuration, |
Monitor |
|
|
|
DHCP relay agent interface configuration, and the |
|
|
|
|
DHCP client information. |
|
|
|
|
|
|
9

Function menu |
Description |
User level |
|
Allows you to enable/disable DHCP, configure |
|
|
advanced DHCP relay agent settings, configure a |
Configure |
|
DHCP server group, and enable/disable the DHCP |
|
|
|
|
|
relay agent on an interface. |
|
|
|
|
DHCP
Snooping
Displays the status, trusted and untrusted ports and |
Monitor |
|
DHCP client information of DHCP snooping. |
||
|
||
|
|
|
Allows you to enable/disable DHCP snooping, |
|
|
and configure DHCP snooping trusted and |
Configure |
|
untrusted ports. |
|
|
|
|
Displays the states of services: enabled or |
Configure |
|
|
|
|
disabled. |
||
|
Service |
Service |
|
||
|
|
|
|||
Allows you to enable/disable services, and set |
Management |
||||
|
|
|
|||
|
|
|
related parameters. |
||
|
|
|
|
||
|
|
|
|
|
|
|
Diagnostic |
Ping |
Allows you to ping an IPv4 address. |
Visitor |
|
|
|
|
|
||
|
Tools |
Trace Route |
Allows you to perform trace route operations. |
Visitor |
|
|
|
||||
|
|
|
|
|
|
|
|
|
Displays ARP table information. |
Monitor |
|
|
|
ARP Table |
|
|
|
|
|
Allows you to add, modify, and remove ARP |
Configure |
||
|
ARP |
|
|||
|
|
entries. |
|||
|
|
|
|||
|
Managem |
|
|
|
|
|
|
Displays the configuration information of gratuitous |
|
||
|
ent |
|
Monitor |
||
|
|
Gratuitous ARP |
ARP. |
||
|
|
|
|||
|
|
|
|
||
|
|
|
Allows you to configure gratuitous ARP. |
Configure |
|
|
|
|
|
|
|
|
ARP |
ARP Detection |
Displays ARP detection configuration information. |
Monitor |
|
|
|
|
|||
|
Anti-Attack |
Allows you to configure ARP detection. |
Configure |
||
|
|
||||
|
|
|
|||
|
|
|
|
|
|
|
|
|
Displays 802.1X configuration information |
Monitor |
|
|
|
|
globally or on a port. |
||
|
802.1X |
802.1X |
|
||
|
|
|
|||
|
Allows you to configure 802.1X globally or on a |
Configure |
|||
|
|
|
|||
|
|
|
port. |
||
|
|
|
|
||
|
|
|
|
|
|
|
|
Domain Setup |
Displays ISP domain configuration information. |
Monitor |
|
|
|
|
|
||
|
|
Allows you to add and remove ISP domains. |
Management |
||
|
|
|
|||
|
|
|
|
|
|
Auth |
|
Displays the authentication configuration |
Monitor |
||
|
information of an ISP domain. |
||||
entic |
Authentication |
|
|||
|
|
||||
|
|
||||
ation |
Allows you to specify authentication methods for an |
|
|||
|
Management |
||||
|
|
|
ISP domain. |
||
|
AAA |
|
|
||
|
|
|
|
||
|
|
Displays the authorization method configuration |
Monitor |
||
|
|
|
|||
|
|
|
information of an ISP domain. |
||
|
|
Authorization |
|
||
|
|
|
|
||
|
|
Allows you to specify authorization methods for an |
Management |
||
|
|
|
|||
|
|
|
ISP domain. |
||
|
|
|
|
||
|
|
|
|
|
|
|
|
Accounting |
Displays the accounting method configuration |
Monitor |
|
|
|
information of an ISP domain. |
|||
|
|
|
|
||
|
|
|
|
|
|
10

Function menu |
|
Description |
User level |
||
|
|
|
Allows you to specify accounting methods for an |
Management |
|
|
|
|
ISP domain. |
||
|
|
|
|
||
|
|
|
|
|
|
|
|
RADIUS Server |
Displays and allows you to configure RADIUS |
Management |
|
|
|
server information. |
|||
|
RADIUS |
|
|
||
|
|
|
|
||
|
RADIUS Setup |
Displays and allows you to configure RADIUS |
Management |
||
|
|
||||
|
|
parameters. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
|
Displays configuration information about local |
Monitor |
|
|
|
|
users. |
||
|
|
Local User |
|
||
|
|
|
|
||
|
|
Allows you to create, modify and remove a local |
Management |
||
|
|
|
|||
|
|
|
user. |
||
|
Users |
|
|
||
|
|
|
|
||
|
|
Displays configuration information about user |
Monitor |
||
|
|
|
|||
|
|
|
groups. |
||
|
|
User Group |
|
||
|
|
|
|
||
|
|
Allows you to create, modify and remove a user |
Management |
||
|
|
|
|||
|
|
|
group. |
||
|
|
|
|
||
|
|
|
|
|
|
|
|
Entity |
Displays information about PKI entities. |
Monitor |
|
|
|
|
|
||
|
|
Allows you to add, modify, and delete a PKI entity. |
Configure |
||
|
|
|
|||
|
|
|
|
|
|
|
|
|
Displays information about PKI domains. |
Monitor |
|
|
|
Domain |
|
|
|
|
|
Allows you to add, modify, and delete a PKI |
Configure |
||
|
|
|
|||
|
|
|
domain. |
||
|
|
|
|
||
|
|
|
|
|
|
|
PKI |
|
Displays the certificate information of PKI domains |
Monitor |
|
|
|
|
and allows you to view the contents of a certificate. |
||
|
|
|
|
||
|
|
Certificate |
Allows you to generate a key pair, destroy a key |
|
|
|
|
|
|
||
|
|
|
pair, retrieve a certificate, request a certificate, and |
Configure |
|
|
|
|
delete a certificate. |
|
|
|
|
|
|
|
|
|
|
CRL |
Displays the contents of the CRL. |
Monitor |
|
|
|
|
|
||
|
|
Allows you to receive the CRL of a domain. |
Configure |
||
|
|
|
|||
|
|
|
|
|
|
|
Port Isolate |
Summary |
Displays port isolation group information. |
Monitor |
|
|
|
|
|
||
|
Group |
Modify |
Allows you to configure a port isolation group. |
Configure |
|
|
|
||||
Secu |
|
|
|
|
|
|
|
Displays the configurations of authorized IP, the |
|
||
rity |
|
|
|
||
Authorized |
Summary |
associated IPv4 ACL list, and the associated IPv6 |
Management |
||
|
|||||
|
|
ACL list. |
|
||
|
IP |
|
|
||
|
|
|
|
||
|
|
Setup |
Allows you to configure authorized IP. |
Management |
|
|
|
|
|
|
|
|
|
Summary |
Displays time range configuration information. |
Monitor |
|
|
Time |
|
|
|
|
|
Create |
Allows you to create a time range. |
Configure |
||
|
Range |
||||
|
|
|
|
||
|
Remove |
Allows you to delete a time range. |
Configure |
||
|
|
||||
|
|
|
|
|
|
QoS |
|
Summary |
Displays IPv4 ACL configuration information. |
Monitor |
|
|
|
|
|
||
|
Create |
Allows you to create an IPv4 ACL. |
Configure |
||
|
|
||||
|
ACL IPv4 |
|
|
|
|
|
Basic Setup |
Allows you to configure a rule for a basic IPv4 ACL. |
Configure |
||
|
|
||||
|
|
|
|
|
|
|
|
Advanced |
Allows you to configure a rule for an advanced |
Configure |
|
|
|
Setup |
IPv4 ACL. |
||
|
|
|
|||
|
|
|
|
|
|
11

Function menu |
|
Description |
User level |
||
|
|
Link Setup |
Allows you to create a rule for a link layer ACL. |
Configure |
|
|
|
|
|
|
|
|
|
Remove |
Allows you to delete an IPv4 ACL or its rules. |
Configure |
|
|
|
|
|
|
|
|
Queue |
Summary |
Displays the queue information of a port. |
Monitor |
|
|
|
|
|
||
|
Setup |
Allows you to configure a queue on a port. |
Configure |
||
|
|
||||
|
|
|
|
|
|
|
Line Rate |
Summary |
Displays line rate configuration information. |
Monitor |
|
|
|
|
|
||
|
Setup |
Allows you to configure the line rate. |
Configure |
||
|
|
||||
|
|
|
|
|
|
|
|
Summary |
Displays classifier configuration information. |
Monitor |
|
|
|
|
|
|
|
|
|
Create |
Allows you to create a class. |
Configure |
|
|
|
|
|
|
|
|
Classifier |
Setup |
Allows you to configure the classification rules for a |
Configure |
|
|
|
class. |
|||
|
|
|
|
||
|
|
Remove |
Allows you to delete a class or its classification |
Configure |
|
|
|
rules. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Summary |
Displays traffic behavior configuration information. |
Monitor |
|
|
|
|
|
|
|
|
|
Create |
Allows you to create a traffic behavior. |
Configure |
|
|
|
|
|
|
|
|
|
Setup |
Allows you to configure actions for a traffic |
Configure |
|
|
Behavior |
behavior. |
|||
|
|
|
|||
|
|
|
|
|
|
|
|
Port Setup |
Allows you to configure traffic mirroring and traffic |
Configure |
|
|
|
redirecting for a traffic behavior |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Remove |
Allows you to delete a traffic behavior. |
Configure |
|
|
|
|
|
|
|
|
|
Summary |
Displays QoS policy configuration information. |
Monitor |
|
|
|
|
|
|
|
|
|
Create |
Allows you to create a QoS policy. |
Configure |
|
|
|
|
|
|
|
|
QoS Policy |
Setup |
Allows you to configure the classifier-behavior |
Configure |
|
|
|
associations for a QoS policy. |
|||
|
|
|
|
||
|
|
Remove |
Allows you to delete a QoS policy or its |
Configure |
|
|
|
classifier-behavior associations. |
|||
|
|
|
|
||
|
|
|
|
|
|
|
|
Summary |
Displays the QoS policy applied to a port. |
Monitor |
|
|
|
|
|
|
|
|
Port Policy |
Setup |
Allows you to apply a QoS policy to a port. |
Configure |
|
|
|
|
|
|
|
|
|
Remove |
Allows you to remove the QoS policy from the port. |
Configure |
|
|
|
|
|
|
|
|
Priority |
Priority |
Displays priority mapping table information. |
Monitor |
|
|
|
|
|||
|
Mapping |
Mapping |
Allows you to modify the priority mapping entries. |
Configure |
|
|
|
|
|||
|
|
|
|
|
|
|
Port Priority |
Port Priority |
Displays port priority and trust mode information. |
Monitor |
|
|
|
|
|||
|
Allows you to modify port priority and trust mode. |
Configure |
|||
|
|
|
|||
|
|
|
|
|
|
|
|
Summary |
Displays PSE information and PoE interface |
Monitor |
|
PoE |
PoE |
information. |
|||
|
|
||||
|
|
|
|||
|
|
Setup |
Allows you to configure a PoE interface. |
Configure |
|
|
|
|
|
|
|
12
Introduction to the common items on the web pages
Buttons and icons
1.Commonly used buttons and icons
Button and icon |
Function |
||
|
|
|
Used to apply the configuration on the current page. |
|
|
|
|
|
|
|
Used to cancel the configuration on the current page, and return to the |
|
|
|
corresponding list page or the Device Info page. |
|
|
|
|
|
|
|
Used to refresh the information on the current page. |
|
|
|
|
|
|
|
Used to clear all the information on a list or all statistics. |
|
|
|
|
|
|
|
Used to enter a page for adding an item. |
|
|
|
|
, |
Used to remove the selected items. |
||
|
|
|
|
|
|
|
|
|
|
|
Used to select all the entries on a list, or all the ports on the device panel. |
|
|
|
|
|
|
|
Used to deselect all the entries on a list, or all the ports on the device panel. |
|
|
|
|
|
|
|
Generally present on the configuration wizard; used to buffer but not apply |
|
|
|
the configuration of the current step and enter the next configuration step. |
|
|
|
|
|
|
|
Generally present on the configuration wizard; used to buffer but not apply |
|
|
|
the configuration of the current step and return to the previous configuration |
|
|
|
step. |
|
|
|
|
|
|
|
Generally present on the configuration wizard; used to apply the |
|
|
|
configurations of all configuration steps. |
|
|
|
|
|
|
|
Generally present on the “Operation” column on a list; used to enter the |
|
|
|
modification page of an item so that you can modify the configurations of |
|
|
|
the item. |
|
|
|
|
|
|
|
Generally present on the “Operation” column on a list; used to delete the |
|
|
|
item corresponding to this icon. |
|
|
|
|
|
|
|
|
|
|
|
Click the plus sign before a corresponding item. You can see the collapsed |
|
|
|
contents. |
|
|
|
|
Page display
The web interface can display a long list by pages, as shown in a. You can set the number of entries displayed per page, and use the First, Prev, Next, and Last links to view the contents on the first, previous, next, and last pages, or go to any page that you want to view.
13
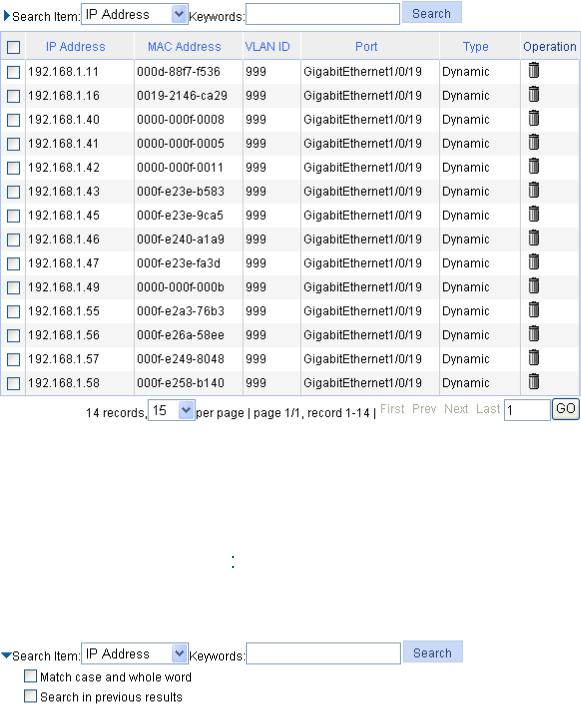
a.Content display by pages
Search function
On some list pages, the web interface provides basic and advanced search functions. You can use the search function to display those entries matching certain search criteria.
Basic search function—Select a search item from the drop-down list as shown in a, input the keyword, and click the Query button to display the entries that match the criteria.
Advanced search function—Click  before Search Item, as shown in a. You can select Match case and whole word, that is, the item to be searched must completely match the keyword, or you can select Search in previous results. If you do not select exact search, a fuzzy search is performed.
before Search Item, as shown in a. You can select Match case and whole word, that is, the item to be searched must completely match the keyword, or you can select Search in previous results. If you do not select exact search, a fuzzy search is performed.
a.Advanced search
Sorting function
On some list pages, the web interface provides the sorting function to display the entries in a certain order.
As shown in a, you can click the blue heading item of each column to sort the entries based on the heading item you selected. Then, the heading item is displayed with an arrow beside it. The upward arrow indicates the ascending order, and the downward arrow indicates the descending order.
14

a.Sort display (based on MAC address in the ascending order)
Configuration guidelines
The web console supports Microsoft Internet Explorer 6.0 SP2 and higher.
The web console does not support the Back, Next, Refresh buttons provided by the browser. Using these buttons may result in abnormal display of web pages.
When the device is performing the spanning tree calculation, you cannot log in to or use the web interface.
The Windows firewall limits the number of TCP connections, so when you use IE to log in to the web interface, sometimes you may be unable to open the web interface. To avoid this problem, turn off the Windows firewall before login.
If the software version of the device changes, when you log in to the device through the web interface, delete the temporary Internet files of IE; otherwise, the web page content may not be displayed correctly.
15
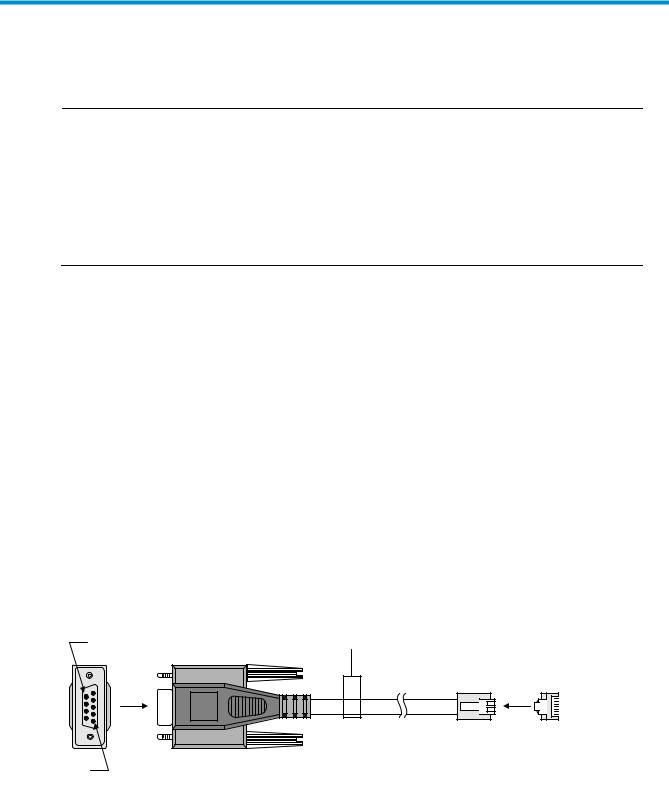
Configuration at the CLI
NOTE:
The HP V1910 Switch Series can be configured through the CLI, web interface, and SNMP/MIB, among which the web interface supports all V1910 Switch Series configurations. These configuration methods are suitable for different application scenarios. As a supplementary to the web interface, the CLI provides some configuration commands to facilitate your operation, which are described in this chapter. To perform other configurations not supported by the CLI, use the web interface.
You will enter user view directly after you log in to the device. Commands in the document are all performed in user view.
Getting started with the CLI
As a supplementary to the web interface, the CLI provides some configuration commands to facilitate your operation. For example, if you forget the IP address of VLAN-interface 1 and cannot log in to the device through the web interface, you can connect the console port of the device to a PC, and reconfigure the IP address of VLAN-interface 1 at the CLI.
This section describes using the CLI to manage the device.
Setting up the configuration environment
To set up the configuration environment, connect a terminal (a PC in this example) to the console port on the switch with a console cable.
A console cable is an 8-core shielded cable, with a crimped RJ-45 connector at one end for connecting to the console port of the switch, and a DB-9 female connector at the other end for connecting to the serial port on the console terminal.
a.Console cable
Use  a console cable to connect a terminal device to the switch, as follows:
a console cable to connect a terminal device to the switch, as follows:
Table 3 Plug the DB-9 female connector to the serial port of the console terminal or PC. Table 4 Connect the RJ-45 connector to the console port of the switch.
16
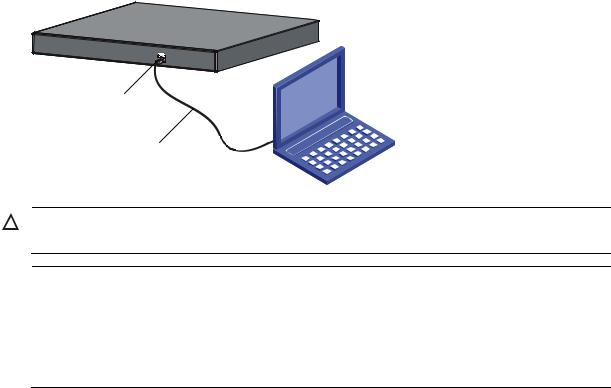
b.Network diagram for configuration environment setup
CAUTION:
Verify the mark on the console port to ensure that you are connecting to the correct port.
NOTE:
The serial port on a PC does not support hot swapping. When you connect a PC to a powered-on switch, connect the DB-9 connector of the console cable to the PC before connecting the RJ-45 connector to the switch.
When you disconnect a PC from a powered-on switch, disconnect the DB-9 connector of the console cable from the PC after disconnecting the RJ-45 connector from the switch.
Setting terminal parameters
To configure and manage the switch, you must run a terminal emulator program on the console terminal, for example, a PC. This section uses Windows XP HyperTerminal as an example.
The following are the required terminal settings:
Bits per second—38400
Data bits—8
Parity—None
Stop bits—1
Flow control—None
Emulation—VT100
Follow these steps to set terminal parameters, for example, on a Windows XP HyperTerminal:
Table 5 Select Start All Programs Accessories Communications HyperTerminal, and in the
Connection Description dialog box that appears, type the name of the new connection in the Name text box and click OK.
17
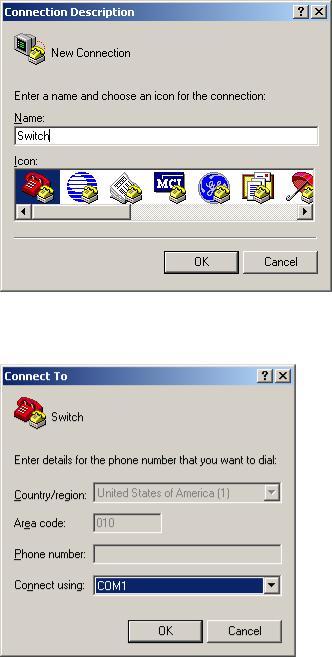
b.Connection description of the HyperTerminal
Table 6 Select the serial port to be used from the Connect using drop-down list, and click OK.
c.Set the serial port used by the HyperTerminal connection
Table 7 Set Bits per second to 38400, Data bits to 8, Parity to None, Stop bits to 1, and Flow control to
None, and click OK.
18
 Loading...
Loading...