HP procurve 8100fl Management And Configuration Manual

Management and
Configuration Guide
ProCurve Series 8100fl Switches
www.procurve.com


ProCurve Series 8100fl Switches
Software Release CY.02.05.xxxx or Greater
Management and Configuration Guide
March 2007

© Copyright 2005-2007 Hewlett-Packard Development Company,
L.P. The information contained herein is subject to change without notice. All Rights Reserved.
This document contains proprietary information, which is
protected by copyright. No part of this document may be
photocopied, reproduced, or translated into another
language without the prior written consent of HewlettPackard.
Publication Number
5990-8867
March 2007
Applicable Products
ProCurve Switch 8108fl (J8727A)
ProCurve Switch 8116fl (J8728A)
Trademark Credits
Ethernet is a registered trademark of Xerox Corporation.
Cisco® is a trademark of Cisco Systems, Inc.
Software Credits and Notices
This product includes software developed by Trimble
Navigation, Ltd.
Disclaimer
The information contained in this document is subject to
change without notice.
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY
OF ANY KIND WITH REGARD TO THIS MATERIAL,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS
FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not
be liable for errors contained herein or for incidental or
consequential damages in connection with the furnishing,
performance, or use of this material.
The only warranties for HP products and services are set
forth in the express warranty statements accompanying
such products and services. Nothing herein should be
construed as constituting an additional warranty. HP shall
not be liable for technical or editorial errors or omissions
contained herein.
Hewlett-Packard assumes no responsibility for the use or
reliability of its software on equipment that is not furnished
by Hewlett-Packard.
Warranty
See the Customer Support/Warranty booklet included with
the product.
A copy of the specific warranty terms applicable to your
Hewlett-Packard products and replacement parts can be
obtained from your HP Sales and Service Office or
authorized dealer.
Hewlett-Packard Company
8000 Foothills Boulevard, m/s 5551
Roseville, California 95747-5551
www.procurve.com

Contents
1 Getting Started
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2
Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2
Command Prompts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-3
Screen Simulations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-3
Related Publications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
Getting Documentation From the Web . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
Sources for More Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
Need Only a Quick Start? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
To Set Up and Install the Switch in Your Network . . . . . . . . . . . . . . . . 1-5
2 Using the Command Line Interface (CLI)
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-1
Accessing the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-2
CLI Access Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
Using the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
CLI Editing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
Scrolling Down a Line or a Screen . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
CLI Parameter Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-8
Setting CLI Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-9
Getting Help with CLI Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-10
Utilities and Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-11
Search Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-11
Entering Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-11
Address Notation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-11
Terminating Sessions and Exiting Modes . . . . . . . . . . . . . . . . . . . 2-11
iii

3 File and System Management
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-1
Maintaining Configuration Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-2
Saving Configuration Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-2
Changing Configuration Information . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-3
Displaying Configuration Information . . . . . . . . . . . . . . . . . . . . . . . . . . 3-3
Managing Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-4
Copy Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-4
File Management Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-5
Backing Up and Restoring Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-7
Backing Up System Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-7
Backing Up and Restoring Configuration Files . . . . . . . . . . . . . . . 3-7
Backing Up Startup Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . 3-8
Managing System Devices and Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-9
Determining Software Versions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-9
Updating Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-10
Rebooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-10
Managing Modules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-11
Management Modules and File Management . . . . . . . . . . . . . . . . 3-11
Replacing Modules and Redundancy . . . . . . . . . . . . . . . . . . . . . . . 3-11
Showing Redundancy Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-12
Switching Over Redundant Modules . . . . . . . . . . . . . . . . . . . . . . . 3-12
Monitoring System Hardware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-13
Showing Hardware Information . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-13
Showing Module Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-14
Showing Temperature, Fan, and Power Supply Status . . . . . . . . 3-14
iv
4 Configuring Basic System Information and Port
Parameters
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-2
Configuring Basic System Information. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-2
Setting the Management Module IP Address . . . . . . . . . . . . . . . . . . . . . 4-2
Setting the System Date and Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-4

Setting System Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-4
Setting the Host Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-4
Setting System ID, Location, and Contact . . . . . . . . . . . . . . . . . . . 4-5
Setting the Log in Banners . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-5
Configuring Terminal Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-6
Establishing a Telnet Connection . . . . . . . . . . . . . . . . . . . . . . . . . . 4-6
Configuring Terminal Line Parameters . . . . . . . . . . . . . . . . . . . . . . . . . 4-6
Saving and Using the New Configuration . . . . . . . . . . . . . . . . . . . . . . . 4-8
Configuring Port Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-9
Specifying Slot and Port Numbers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-9
Slot Numbering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-10
Activating or Disabling Ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-11
Modifying Port Speed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-12
Modifying Port Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-12
Disabling or Re-enabling Flow Control . . . . . . . . . . . . . . . . . . . . . . . . 4-12
Assigning a Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-13
5 Security Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-2
Configuring Passwords. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-2
Preventing Lock Outs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-2
Specifying the CLI-level Password . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-3
Specifying Privilege Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-4
Specifying Line-level Passwords . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-5
Recovering from Forgotten Passwords . . . . . . . . . . . . . . . . . . . . . . . . . 5-6
Using SSH . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-8
Establishing SSH Sessions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-8
Monitoring SSH Sessions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-9
Using SSH and Telnet Sessions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-10
Configuring Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-11
Configuring Authentication Method Lists . . . . . . . . . . . . . . . . . . . . . . 5-11
Configuring Authorization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-12
Configuring Login Prompts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-12
v

Configuring Accounting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-13
Configuring RADIUS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-15
Monitoring RADIUS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-16
Configuring TACACS+ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-17
Monitoring TACACS+ . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-18
6 VLAN Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-2
Layer 2 vs. Layer 3 VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-2
Ports, VLANs, and L3 Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-3
Port-based VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-3
Explicit and Implicit VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-3
Access Ports and Trunk Ports (802.1P and 802.1Q support). . . . . . . . . . . . 6-4
Configuring a VLAN. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Creating a VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Adding Ports to a VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-6
The Default VLAN and Trunk and Access Port Behavior . . . . . . . . . . 6-6
VLAN Nonstandard Defaults . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-6
Access Port Behavior . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-7
Trunk Port Behavior . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-7
Monitoring VLANs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-8
vi
7 Link Aggregation Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-2
Configuring Static Link Aggregations (LAG) . . . . . . . . . . . . . . . . . . . . . . . . . 7-3
Creating a LAG . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-3
Adding Physical Ports to the LAG . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-3
Link Aggregation Port Limitations . . . . . . . . . . . . . . . . . . . . . . . . . . 7-3
Configuring Dynamic Link Aggregations (LACP) . . . . . . . . . . . . . . . . . . . . . 7-4
Configuring Link Aggregations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-4
Creating the Aggregation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-5

Specifying the System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-5
Configuring the Port . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-5
Configuring the Partner System . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-6
Configuration Restrictions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-6
LAG and LACP Configuration Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-7
Monitoring LAG and LACP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-10
Monitoring LAG Configurations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-10
Monitoring LACP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-14
8 QoS Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-2
Basic QoS Operation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-2
Connecting Ingress and Egress Traffic . . . . . . . . . . . . . . . . . . . . . . . . . . 8-3
Using QoS Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-4
Spolicy Input Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-4
Spolicy Output Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-4
Differentiated Class . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-5
Random Detection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-5
Differential Class Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-7
Interface Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-8
QoS Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-8
9 Spanning-Tree Operation
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-2
802.1s Multiple Spanning Tree Protocol (MSTP) . . . . . . . . . . . . . . . . . . . . . 9-4
MSTP Structure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-5
Terminology . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-6
How MSTP Operates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-8
MST Regions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-8
Regions, Legacy STP and RSTP Switches, and the Common Spanning
Tree (CST) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-10
MSTP Operation with 802.1Q VLANs . . . . . . . . . . . . . . . . . . . . . . 9-10
vii

Operating Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-11
Transitioning from STP or RSTP to MSTP . . . . . . . . . . . . . . . . . . . . . . 9-13
Tips for Planning an MSTP Application . . . . . . . . . . . . . . . . . . . . . . . . 9-13
Configuring MSTP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-15
Configuring MSTP Operation Mode and Global Parameters . . . . . . . 9-17
Configuring Basic Port Connectivity Parameters . . . . . . . . . . . . . . . . 9-19
Configuring MST Instance Parameters . . . . . . . . . . . . . . . . . . . . . . . . . 9-22
Configuring MST Instance Per-Port Parameters . . . . . . . . . . . . . . . . . 9-25
Enabling or Disabling Spanning Tree Operation . . . . . . . . . . . . . . . . . 9-27
MSTP Show Commands and Troubleshooting . . . . . . . . . . . . . . . . . . . . . . 9-28
Displaying MSTP Statistics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-28
Displaying Statistics for a Specific MST Instance . . . . . . . . . . . . 9-30
Displaying the MSTP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-31
Displaying Debug Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-31
Displaying MAC Table Information . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-32
Operating Notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-33
Troubleshooting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-33
10
Multimedia Traffic Control with IP Multicast (IGMP)
viii
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-2
IGMP General Operation and Features . . . . . . . . . . . . . . . . . . . . . . . . 10-2
IGMP Terms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-2
CLI: Configuring and Displaying IGMP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-3
Enabling or Disabling IGMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-3
Configuring IGMP on a Per-Port Basis . . . . . . . . . . . . . . . . . . . . . . . . . 10-3
IGMP Show Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-6
Viewing the Current IGMP Configuration . . . . . . . . . . . . . . . . . . . 10-6
Viewing IGMP Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-7
How IGMP Operates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-8
IGMP Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-9
Operating Rules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-9
Operating Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-10
Operation With or Without IP Addressing . . . . . . . . . . . . . . . . . . . . . 10-10

Automatic Fast-Leave IGMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-11
Configuring Fast-Leave IGMP . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-13
Forced Fast-Leave IGMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-13
Configuring Forced Fast-Leave IGMP . . . . . . . . . . . . . . . . . . . . . 10-13
Using the Switch as Querier . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-14
Disabling or Re-enabling the Querier Function . . . . . . . . . . . . . 10-15
Disabling or Re-enabling Data-Driven IGMP . . . . . . . . . . . . . . . . . . . 10-16
Excluding Well-Known or Reserved Multicast Addresses from IP
Multicast Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-16
11 IP Routing Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-2
Configuring IP Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-3
Configuring IP Interfaces to Ports . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-3
Configuring IP Interfaces for a VLAN . . . . . . . . . . . . . . . . . . . . . . . . . . 11-3
Extending the IP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-4
Configuring Jumbo Frames . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-5
Layer 2 Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-6
Configuring Layer 2 Address and Port-to-Address Lock Filters . . . . 11-6
Layer 2 Filter Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-7
Example: Address Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-7
Configuring Address Resolution Protocol (ARP) . . . . . . . . . . . . . . . . . . . . 11-8
Clearing ARP Cache Entries . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-8
Configuring ARP Refresh Interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-8
Unresolved MAC Addresses for ARP Entries . . . . . . . . . . . . . . . . . . . 11-9
Configuring Proxy ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-9
Monitoring ARP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-9
Configuring Basic IP Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-10
Configuring DNS Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-10
Configuring IP Services (ICMP) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-10
Configuring IP Helper . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-10
Monitoring IP Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-11
Setting Memory Thresholds . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-13
ix

12
RIP Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-2
Configuring RIP on the Switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-2
Enabling and Disabling RIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-3
Specifying the Version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-3
Enabling Routing on a Network . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-3
Summarizing Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-3
Distributing Default Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-3
Setting Default Metrics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-4
Defining Administrative Distance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-4
Filtering Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-4
Limiting Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-4
Limiting Paths . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-5
Filtering Networks in Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-5
Redistributing Traffic from a Different Protocol . . . . . . . . . . . . . . . . 12-5
Adjusting Timers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-5
Configuring an Interface for RIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-6
Specifying RIP Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-6
Specifying RIP Version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-6
Enabling IP Broadcasts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-6
Configuration Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-7
Related Topics . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-8
x
13
OSPF Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-2
Supported Features . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-2
Multipath Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-3
OSPF Areas . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-3
OSPF Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-4
Configuring OSPF Router Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-5
Enabling OSPF . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-5
Setting the Router ID . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-5

Configuring OSPF Areas . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-6
Configuring Summary Ranges . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-7
Configuring Stub Areas . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-7
Configuring Stub Area Networks . . . . . . . . . . . . . . . . . . . . . . . . . . 13-7
Configuring Not-So-Stubby Areas (NSSA) . . . . . . . . . . . . . . . . . . 13-8
Enabling Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-8
Creating Virtual Links . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-9
Configuring General OSPF Parameters . . . . . . . . . . . . . . . . . . . . . . . . 13-9
Configuring the OSPF Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-10
Associating a Network with the OSPF Area . . . . . . . . . . . . . . . . 13-10
Distributing Default Information . . . . . . . . . . . . . . . . . . . . . . . . . 13-10
Setting the Reference Bandwidth . . . . . . . . . . . . . . . . . . . . . . . . 13-10
Configuring RFC 1583 Compatibility . . . . . . . . . . . . . . . . . . . . . . 13-10
Logging Adjacency Changes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-11
Redistribution . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-11
Setting Default Metric for Redistributed Routes . . . . . . . . . . . . 13-11
Configuring Shortest Path First Computation Timers . . . . . . . 13-11
Configuring OSPF Interface Parameters . . . . . . . . . . . . . . . . . . . . . . 13-12
Using OSPF Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-12
Specifying the Interface Cost . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-13
Specifying Intervals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-13
Ignoring Maximum Transmission Unit Checks . . . . . . . . . . . . . 13-14
Setting the Priority Level . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-14
Suppressing Routing Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-14
Alternative Area Border Router (ABR). . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-15
OSPF Configuration Example . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-16
Monitoring OSPF . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-18
OSPF Debug Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-20
14 Configuring Routing Policies
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-2
Route Preferences . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-2
Import Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-3
xi

Import-Source . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-3
Route-Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-4
Export Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-4
Export-Destination . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-4
Export-Source . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-5
Route-Filter . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-5
Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-5
Authentication Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-6
Using Route Maps . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-7
Configuring Next Hop Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-7
Configuring Simple Routing Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-8
Redistributing Static Routes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-8
Redistributing Directly Attached Networks . . . . . . . . . . . . . . . . . . . . 14-8
Redistributing RIP into RIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-8
Redistributing RIP into OSPF . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-9
Redistributing OSPF to RIP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-9
15
Access Control Lists (ACLs)
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-1
xii
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-2
Layer 3 Access Control List (ACLs) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-3
Creating an ACL . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-4
The “Any” Parameter and Wild Cards . . . . . . . . . . . . . . . . . . . . . . 15-5
How Multiple ACL Rules are Evaluated . . . . . . . . . . . . . . . . . . . . 15-6
Implicit Deny Rule . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-7
Editing ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-9
Applying ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-10
Applying ACLs to Interfaces . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-10
ACL Viewing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-11
Layer 2 Access Control Lists (ACLs) . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-13
Layer 2 Filters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-13
Layer 2 ACLS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-13
Monitoring Layer 2 ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-14

Protocols and Keywords. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-15
16 VRRP Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-2
Configuration Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-2
Setting the IP Address of the Virtual Router . . . . . . . . . . . . . . . . . . . . 16-3
Labeling the Virtual Router . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-3
Setting the Backup Priority . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-3
Setting the Advertisement Interval . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-3
Learning the Master Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-4
Setting Pre-empt Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-4
VRRP Configuration Notes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-4
Configuring VRRP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-6
Basic VRRP Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-6
Configuration of Router R1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-7
Configuration for Router R2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-7
VRRP Configuration with Two Routers . . . . . . . . . . . . . . . . . . . . . . . . 16-8
Configuration of Router R1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-9
Configuration of Router R2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-9
Monitoring VRRP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-10
17 Time Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17-2
Setting the Date and Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17-2
Using NTP. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17-3
Clock Synchronization . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 17-3
18 SNMP Configuration
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-2
Configuring Access to MIB Objects . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-3
xiii

Configuring SNMP Access . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-3
Configuring Community Strings . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-3
Configuring the SNMP Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-4
Configuring SNMP Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-4
Specifying the Notification Targets . . . . . . . . . . . . . . . . . . . . . . . . 18-4
Enabling/Disabling SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-5
MIB Modules . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-6
Loading MIBs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-7
Enabling/Disabling MIB Modules . . . . . . . . . . . . . . . . . . . . . . . . . . 18-8
Displaying SNMP Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-9
Troubleshooting SNMP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-10
SNMP Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 18-11
19
Performance Monitoring
Contents . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-1
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-2
Show Commands. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-2
Debug Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-5
Clear Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-6
xiv
Error Reporting and Message Logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-7
Disabling/Enabling Message Logging . . . . . . . . . . . . . . . . . . . . . . . . . . 19-7
Specifying Logging Locations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-7
Configuring the Syslog Host . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-8
Setting Source Interface for Syslog Messages . . . . . . . . . . . . . . . 19-8
Displaying Logging Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-8
Displaying Crash Log Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-9
Setting the Severity Level of Messages . . . . . . . . . . . . . . . . . . . . . 19-9
Controlling the Size of the Log and Messages . . . . . . . . . . . . . . 19-10
Time-Stamping Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-10
Setting Temperature Thresholds . . . . . . . . . . . . . . . . . . . . . . . . . 19-10
Configuring Port Mirroring. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-11
Operating Notes and Limitations . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-11
Setting Rate-Limits (2-port X2 Module) . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-12
Configuring MAC Rate-Limits . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-12

Operating Notes for Rate-Limiting . . . . . . . . . . . . . . . . . . . . . . . . . . . 19-13
Command Line Index
Index
xv

xvi

Getting Started
Contents
Overview. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2
Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2
Command Prompts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-3
Screen Simulations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-3
Related Publications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
Getting Documentation From the Web . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
Sources for More Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
Need Only a Quick Start? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-5
To Set Up and Install the Switch in Your Network . . . . . . . . . . . . . . . . 1-5
1
1-1
Getting Started
Overview
Overview
This Management and Configuration Guide is intended for use with the
following switches:
■ ProCurve Switch 8108fl
■ ProCurve Switch 8116fl
Note Each device uses the same command line functions. Together, these two
devices are referred to in this guide as the 8100fl switch.
This guide describes how to use the command line interface (CLI) to
configure, manage, monitor, and troubleshoot switch operation. The Product
Documentation CD-ROM shipped with the switch includes a copy of this
guide. You can also download a copy from the ProCurve Networking Web site.
(See “Getting Documentation From the Web” on page 1-4, below.) For
information on other product documentation for the 8100fl switch, refer to
“Related Publications” on page 1-4.
1-2
Conventions
This guide uses the following conventions for displaying command syntax.
Convention Description
boldface font Identifies commands that you enter as shown.
italic font Identifies elements for which you enter values.
screen font Indicates text that appears on your computer screen.
[ ] Identifies optional elements. Square brackets are also used to
indicate default system prompts on screen.
{ x | y | z } Indicates required elements of which you select one. Vertical bars
(|) are used to separate alternative, mutually exclusive elements.
[ x | y | z ] Indicates optional elements of which you select one.
string Indicates that the entry is a literal set of characters.
[ctrl][Enter] Represents a keystroke (or keystrokes) to type on your keyboard.
< > Indicates nonprinting characters for which you enter values.
Getting Started
Conventions
Command Prompts
The default configuration for your switch displays one of the following CLI
prompts:
ProCurve 8108fl#
ProCurve 8116fl#
To simplify recognition, this guide uses the hostname ProCurve to represent
command prompts for both models. For example:
ProCurve#
Note You can use the hostname command to change the text in the CLI prompt.
To configure an interface on the switch, you need to enter configuration mode
for that interface (for example, a physical port, LAG, or VLAN). The command
prompt display will vary according to the interface. Here are two examples:
ProCurve(config-interface-gig3/4)#
ProCurve(config-interface-vlan701)#
ProCurve(config-lag-13)#
This guide uses a generic prompt to represent commands that must be entered
from an interface configuration context:
ProCurve(config-if)#
Screen Simulations
Single lines of screen text and command output are represented like this:
ProCurve#show running-config
Screens containing more than one line of text and command output are shown
in table format like this:
ProCurve#show version
ProCurve Networking Switch 8100fl Series System Software
Version CY.02.02.0051
Copyright (c) 1998-2005 by ProCurve Networking.
Compiled on Sun Jan 22 20:20:26 PST 2006
Bootloader Version CY.02.02.0004
Switch uptime is 18 hours, 4 minutes, 28 seconds
...
1-3

Getting Started
Related Publications
Related Publications
Read Me First. The Read Me First shipped with your switch provides
software update information, product notes, and other information. A printed
copy is shipped with your switch.
Installation and Getting Started Guide. Use the Installation and
Getting Started Guide shipped with your switch to prepare for and perform
the physical installation. This guide steps you through connecting the switch
to your network and assigning IP addressing, as well as describing the LED
indications for correct operation and trouble analysis. A PDF version of this
guide is also provided on the Product Documentation CD-ROM shipped with
the switch.
Release Notes. Release notes are posted on the ProCurve Networking Web
site and provide information on new software updates:
■ New features and how to configure and use them
■ Software management, including downloading software to the switch
■ Software fixes addressed in current and previous releases
1-4
Getting Documentation From the Web
To download the latest version of documentation for your switch:
1. Go to the ProCurve Networking Web site at http://www.procurve.com.
2. Click on technical support.
3. Click on product manuals.
4. Click on the ProCurve Switch 8100fl series link to view or download the
most recent manuals and release notes for this product.
Sources for More Information
■ For more information on a specific command in the CLI, type the com-
mand name followed by “?” or use the [
CLI Commands” on page 2-10 for details).
■ For more information on ProCurve products and technology, visit the
ProCurve Networking Web site at:
http://www.procurve.com
Tab ] key (see “Getting Help with

Need Only a Quick Start?
Getting Started
Need Only a Quick Start?
IP Addressing. If you just want to give the switch an IP address so that it
can communicate on your network, ProCurve recommends that you use the
CLI to quickly configure IP addressing and enable Telnet access to the switch:
see “Setting the Management Module IP Address” on page 4-2 for details.
Note For an introduction and overview on using the CLI, refer to Chapter 2, “Using
the Command Line Interface (CLI)”. For instructions on setting up basic
features, see Chapter 4, “Configuring Basic System Information and Port
Parameters”.
To Set Up and Install the Switch in Your Network
For instructions on how to physically install the switch and its components in
your network, refer to the Installation and Getting Started Guide that
shipped with your switch. This provides information on the following:
■ Notes, cautions, and warnings related to installing the switch and its
related modules
■ Instructions for mounting the switch and physically installing its
modules, fans, and power
■ Procedures for setting up basic system information and passwords.
■ Descriptions for interpreting LED behavior on the switch.
1-5

— This page is intentionally unused. —

Using the Command Line Interface (CLI)
Contents
Using the Command Line Interface (CLI)
Accessing the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-2
CLI Access Modes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-4
Using the CLI . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
CLI Editing Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-5
Scrolling Down a Line or a Screen . . . . . . . . . . . . . . . . . . . . . . . . . . 2-7
CLI Parameter Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-8
Setting CLI Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-9
Getting Help with CLI Commands . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-10
Utilities and Conventions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-11
Search Command . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-11
Entering Parameters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-11
Address Notation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-11
Terminating Sessions and Exiting Modes . . . . . . . . . . . . . . . . . . . 2-11
2
2-1
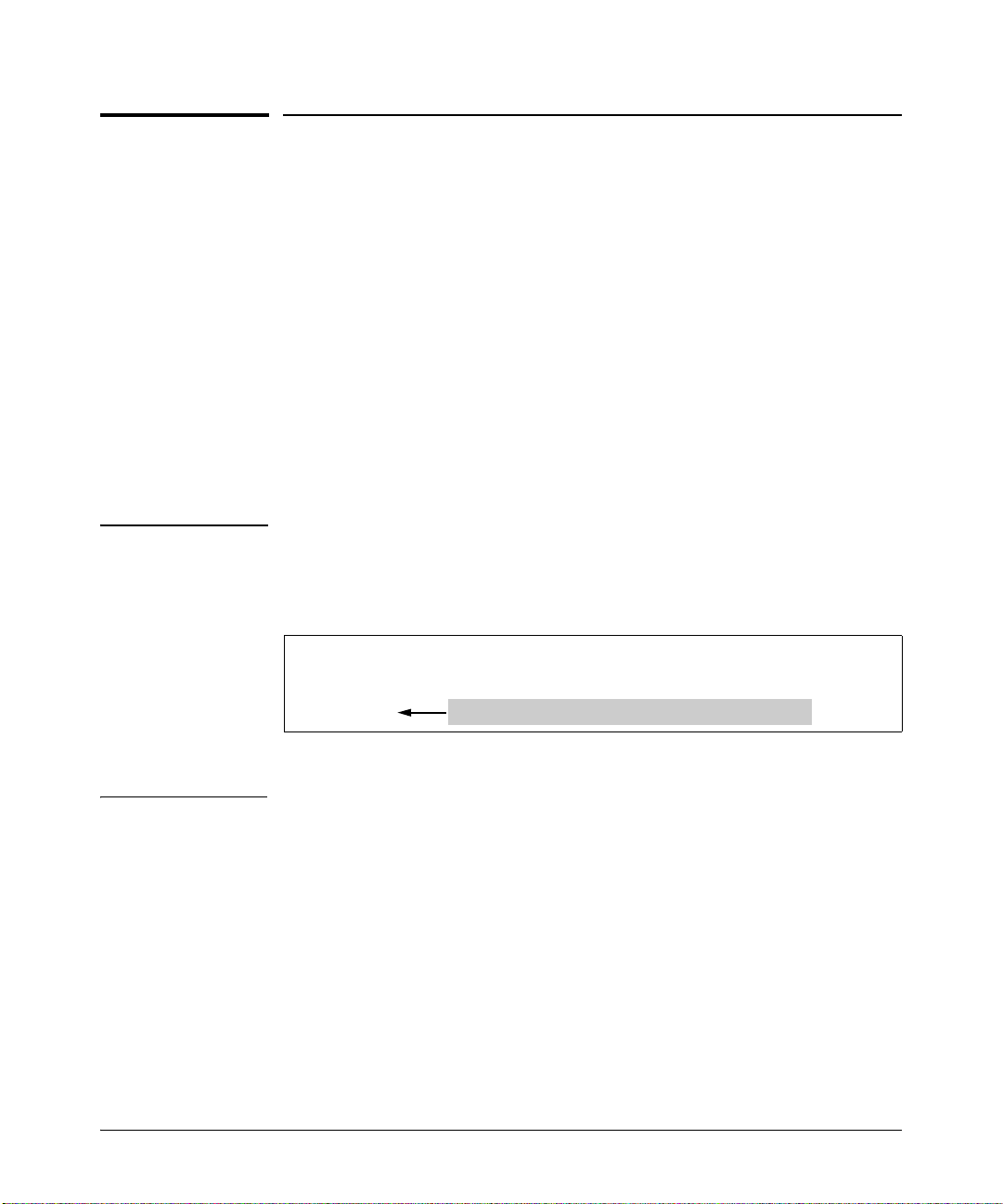
Using the Command Line Interface (CLI)
Accessing the CLI
Accessing the CLI
The CLI can be accessed through both serial and Telnet connections
(including Secure Shell). For initial log on, you must use a serial connection.
Once an IP address is assigned to the management interface (see “Setting the
Management Module IP Address” on page 4-2), you can access the CLI through
a Telnet connection. For more information on using Telnet and SSH sessions,
refer to Chapter 5, “Security Configuration”.
When accessing the CLI through Telnet, you will prompted for a password if
one has been set via local, RADIUS, or TACACS configuration. By default, the
password required is the password you enter for general access at initial setup
(see “Configuring Passwords” on page 5-2). You also have the option of
assigning a separate password for Privileged Exec mode access with the
enable secret command.
Note Up to 10 Tel net se ssions can run simultaneously on the switch. However, only
one user at at time is allowed in Configuration mode. If a second user enters
the configure command, the first user will be bumped out of configuration
mode and will see the following message:
2-2
ProCurve(config-line)#User [mgr] logged in as process [858]
has taken control of the config session
ProCurve#
All the commands that the first user entered before being bumped out of
configuration mode will be saved in the running configuration.
To access the CLI:
1. Once you connect to the device, you will see the following prompt:
ProCurve>
At this prompt ( > ), you are at the user Exec mode of the CLI command
structure. You can view system status at this level, but you do not have
permission to change system configurations. To make configuration and
system changes, you must be in (and have authorization to enter) the
Privileged Exec mode.
The command line prompt reverts to Privileged Exec mode

Using the Command Line Interface (CLI)
Accessing the CLI
Not e
For more information on the CLI Access modes and permissions, see
Table 2-1 on page 2-4.
2.
To access the Privileged Exec mode from the Exec mode, enter:
ProCurve>enable
You will be prompted for a password if one has been assigned. Otherwise,
the prompt will change to the Privileged Exec mode (#):
ProCurve#
From Privileged Exec mode, you can manage system-level functions and
enter Configuration mode to make configuration changes.
3.
To access Configuration mode, from Privileged Exec mode enter:
ProCurve#configure
The prompt will change to Configuration mode:
ProCurve(config)#
From Configuration mode, you can reach all other configuration levels
(for ports on interface modules, for specific protocols, and so on) from
this mode.
Not e s The CLI supports partial matching, so you do not need to enter the entire
name of a command or option.
CLI commands are not case sensitive.
To help identify the current command level or mode, the CLI prompt
changes at each level of the Configuration command structure.
2-3
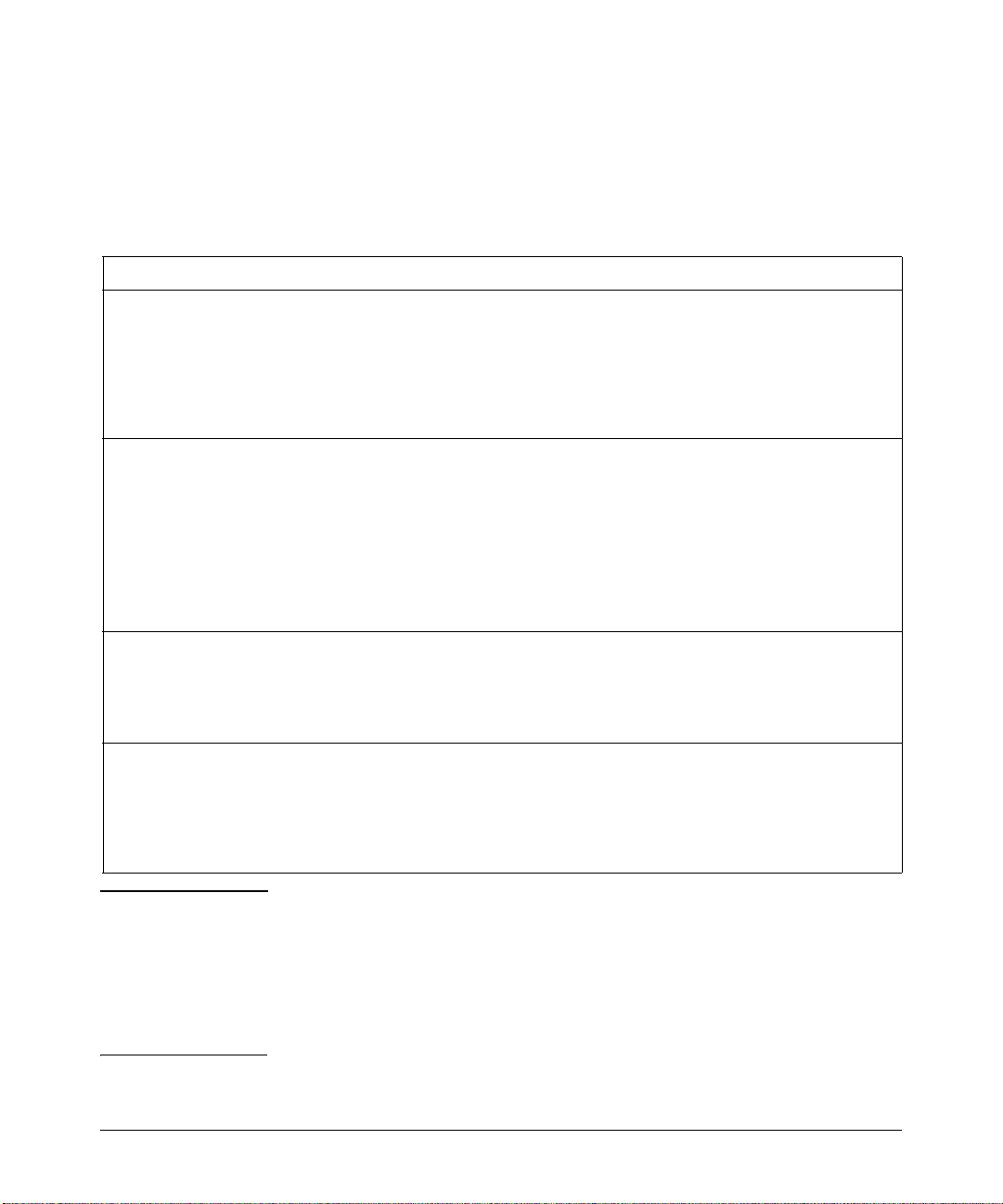
Using the Command Line Interface (CLI)
Accessing the CLI
CLI Access Modes
The CLI has four different access modes, each of which provides the ability
to perform the specific operations shown in Ta ble 2-1.
Table 2-1. CLI Access Modes
Access Mode Command Prompt Description
Exec ProCurve> Provides limited access to the system. Allows you to display status, perform
Privileged Exec ProCurve# Allows you to manage the system. Privileged Exec mode provides more facilities
Configuration ProCurve(config)# Allows you to configure all features and functions on the switch. These include
Boot PMOM> Certain tasks can be performed only from Boot mode. Enter the reboot command to
diagnostic operations, and power slots on and off. You can also perform basic
system-level tasks such as traceroute, launch ping requests, control terminal
configuration, and logout.
The Exec mode command prompt consists of the system name, followed by the angle
brackets (>). For procedures on how to change the system name using the hostname
command, refer to “Setting the Log in Banners” on page 4-5 .
than Exec mode. For example, you can display critical features such as router
configuration, access control lists and SNMP statistics.
The Exec mode command prompt consists of the system name, followed by the
pound sign (#).
To enter this mode, enter the enable command from the Exec mode, then supply a
password when prompted (if password protection has been configured).
To exit Privileged Exec mode and return to Exec mode, type disable and press
[Enter].
switch configuration, access control lists, routing protocols, spanning tree
configuration, and so on.
To enter Configuration mode, first enter Privileged Exec mode (enable command or
en), and then enter the configure or config command.
reset the switch. If the switch still fails to boot, contact ProCurve Customer Support.
To enter the Boot mode, boot the switch, and then interrupt the normal boot
sequence by pressing the [Esc] key. (Use the spacebar to skip the countdown
sequence). For information on how to update the boot PMOM software and boot
using the updated image, see “Updating Software” on page 3-10.
Notes The command prompt shows the hostname in front of the mode character(s).
The default name is “ProCurve 8108fl” or ‘ProCurve 8116fl” according to
model. To change the name, see “Setting the Host Name” on page 4-4.
When you are in Configuration mode, use the exit command or press [
to exit to the previous mode. Typing exit in Privileged Exec mode will quit the
session entirely (see “Terminating Sessions and Exiting Modes” on page 2-11).
2-4
Ctrl][z]

Using the Command Line Interface (CLI)
Using the CLI
Using the CLI
The CLI supports partial matching (also known as command completion), so
you do not need to enter the entire name of a command or option. As long as
you enter enough characters of the command or option name to be unique,
the CLI understands what you are typing. If you enter enough characters of a
command keyword to uniquely identify it and press the [
complete the command. For example, if you enter the following in Privileged
Exec mode and then press the [
ProCurve#show ru[Tab ]
The CLI completes the command as follows:
ProCurve#show running-config
If you do not enter enough characters to identify a unique command, the CLI
will flag the entry as an ambiguous command. For example:
Tab ] key as indicated:
Ta b] key, the CLI will
ProCurve#show r
% Ambiguous command: "show r"
When you mis-enter command syntax, or enter syntax that the CLI does not
recognize, the CLI will flag the syntax error with a ^ marker indicating the
word where the error has occurred.
For example:
ProCurve#show rum
^
% Invalid input detected at '^' marker.
Use the CLI editing commands (see Table 2-2 on page 2-6) to correct the error
and enter a valid command.
CLI Editing Commands
The switch provides line editing capabilities to move forward or backward on
a line, delete or transpose characters, and delete portions of a line. To use the
line editing commands, you need a VT-100 terminal or terminal emulator. For
more information on connecting a console and configuring a terminal, refer
to the Installation and Getting Started Guide for your switch.
2-5

Using the Command Line Interface (CLI)
Using the CLI
To enter a line-editing command, use the [Ctrl][key] combination for the
command by pressing and holding the [
associated with the command as detailed in the following table.
Table 2-2. CLI Line Editing Commands
Command Resulting Action
[Ctrl][A] Move to beginning of line
[Ctrl][B] Move back one character
[Ctrl][C] Abort current line
[Ctrl][D] Delete character under cursor
[Ctrl][E] Move to end of line
[Ctrl][F] Move forward one character
[Ctrl][G] None
[Ctrl][H] Delete character just prior to the cursor
[Ctrl][I] Insert one space (tab substitution)
[Ctrl][J] Carriage return (executes command)
Ctrl] key, then pressing the letter
[Ctrl][K] Delete characters from cursor to end of line
[Ctrl][L] Refresh current line
[Ctrl][M] Carriage return (executes command)
[Ctrl][N] Next command from history buffer
[Ctrl][O] None
[Ctrl][P] Previous command from history buffer
[Ctrl][Q
[Ctrl][R] Refresh current line
[Ctrl][S] Stop processing command
[Ctrl][T] Transpose character under cursor with the character just prior to
[Ctrl][U] Delete line from the beginning of line to cursor
[Ctrl][V] Follow by Ctrl-character to enter the Ctrl character.
[Ctrl][W] Delete one word backwards
[Ctrl][X] Move forward one word
] Resume processing command
the cursor
2-6
 Loading...
Loading...