Page 1

Users’ Guide
ProCurve Network Access Controller 800
www.procurve.com
Page 2

Page 3

ProCurve
Network Access Controller 800
Users Guide
Release 1.0
Page 4

© Copyright 2007 Hewlett-Packard Development Company, L.P.
All Rights Reserved.
This document contains information which is protected by
copyright. Reproduction, adaptation, or translation without
prior permission is prohibited, except as allowed under the
copyright laws.
Publication Number
5991-8571
August 2007
(rev-
h)
Disclaimer
The information contained in this document is subject to
change without notice.
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY
OF ANY KIND WITH REGARD TO THIS MATERIAL,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS
FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not
be liable for errors contained herein or for incidental or
consequential damages in connection with the furnishing,
performance, or use of this material.
Hewlett-Packard assumes no responsibility for the use or
reliability of its software on equipment that is not furnished
by Hewlett-Packard.
Trademark Credits
Microsoft, Windows, Windows 95, and Microsoft Windows
NT are registered trademarks of Microsoft Corporation.
Internet Explorer is a trademark of Microsoft Corporation.
Ethernet is a registered trademark of Xerox Corporation.
Netscape is a registered trademark of Netscape Corporation.
Warranty
See the Customer Support/Warranty booklet included with
the product.
A copy of the specific warranty terms applicable to your
Hewlett-Packard products and replacement parts can be
obtained from your HP Sales and Service Office or
authorized dealer.
Hewlett-Packard Company
8000 Foothills Boulevard, m/s 5551
Roseville, California 95747-5551
http://www.hp.com/go/hpprocurve
Page 5

Contents
1 Introduction
What you Need to get Started . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2
NAC 800 Home Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
System Monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8
The NAC 800 Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-10
About NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-10
NAC Policy Definition . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-10
Endpoint Testing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-11
Compliance Enforcement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-12
Automated and Manual Repair . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-12
Targeted Reporting . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-12
Technical Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-13
Additional Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-14
Upgrading . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-15
Conventions Used in This Document . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Navigation Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Tip Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Note Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Caution Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Warning Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Bold Font . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Task Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Italic Text . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Courier Font . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-18
Angled Brackets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-18
Square Brackets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-18
Terms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-19
Copying Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-20
SCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-20
PSCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-20
2 Clusters and Servers
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-2
Installation Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-3
iii
Page 6

Contents
Single-server Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-3
Multiple-server Installations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-3
3 System Configuration
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-4
Enforcement Clusters and Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-6
Enforcement Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-7
Adding an Enforcement Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-7
Editing Enforcement Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-9
Viewing Enforcement Cluster Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-10
Deleting Enforcement Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-11
Enforcement Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-13
Adding an Enforcement Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-13
Cluster and Server Icons . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-15
Editing Enforcement Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-15
Changing the Enforcement Server Network Settings . . . . . . . . . . . . . . . . 3-17
Changing the Enforcement Server Date and Time . . . . . . . . . . . . . . . . . . 3-17
Modifying the ES root Account Password . . . . . . . . . . . . . . . . . . . . . . . . 3-18
Viewing Enforcement Server Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-18
Deleting Enforcement Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-20
Enforcement Server Recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-20
Management Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-21
Viewing Network Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-21
Modifying Management Server Network Settings . . . . . . . . . . . . . . . . . . 3-23
Selecting a Proxy Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-23
Setting the Date and Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-24
Automatically Setting the Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-25
Manually Setting the Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-25
Selecting the Time Zone . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-26
Changing MS SNMP Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-26
Modifying the MS root Account Password . . . . . . . . . . . . . . . . . . . . . . . . 3-26
Checking for NAC 800 Upgrades . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-27
Changing the NAC 800 Console Timeout . . . . . . . . . . . . . . . . . . . . . . . . . 3-27
User Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-29
Adding a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-29
Searching for a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-32
Sorting the User Account Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-33
Copying a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-33
Editing a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-34
Deleting a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-35
iv
Page 7

Contents
User Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-37
Adding a User Role . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-37
Editing User Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-40
Deleting User Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-41
Sorting the User Roles Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-42
License . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-43
Updating Your License . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-43
Test Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-45
Manually Checking for Test Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-45
Selecting Test Update Times . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-46
Viewing Test Update Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-47
Quarantining . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-49
Selecting the Quarantine Method . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-49
Entering Basic 802.1X Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-51
Selecting the RADIUS Authentication method . . . . . . . . . . . . . . . . . . . . . 3-51
Configuring Windows Domain Settings . . . . . . . . . . . . . . . . . . . . . . . . . . 3-52
Configuring OpenLDAP Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-54
Configuring Novell eDirectory Settings . . . . . . . . . . . . . . . . . . . . . . . . . . 3-57
Adding 802.1X Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-60
Testing the Connection to a Device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-61
Cisco IOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-62
Cisco CatOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-63
Enterasys . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-65
Extreme ExtremeWare . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-67
Extreme XOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-69
Foundry . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-71
HP ProCurve Switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-73
HP ProCurve WESM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-76
HP ProCurve 420 AP or HP ProCurve 530 AP . . . . . . . . . . . . . . . . . . . . . 3-79
Nortel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-81
Other . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-83
Setting DHCP Enforcement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-85
Adding a DHCP Quarantine Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-87
Sorting the DHCP Quarantine Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-89
Editing a DHCP Quarantine Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-89
Deleting a DHCP Quarantine Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-90
Maintenance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-91
Initiating a New Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-91
Restoring From a Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-93
Downloading Support Packages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-94
v
Page 8

Contents
Cluster Setting Defaults . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-95
Testing Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-95
Selecting Test Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-95
Ordering Test Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-96
Recommended Test Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-97
Selecting End-user Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-98
Accessible Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-98
Exceptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-100
Always Granting Access to Endpoints and Domains . . . . . . . . . . . . 3-101
Always Quarantine Endpoints and Domains . . . . . . . . . . . . . . . . . . 3-102
Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-102
Enabling Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-102
End-user Screens . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-104
Specifying an End-user Screen Logo . . . . . . . . . . . . . . . . . . . . . . . . 3-104
Specifying the End-user Screen Text . . . . . . . . . . . . . . . . . . . . . . . . 3-105
Specifying the End-user Test Failed Pop-up Window . . . . . . . . . . . 3-106
Agentless Credentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-107
Adding Windows Credentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-107
Testing Windows Credentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-109
Editing Windows Credentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-109
Deleting Windows Credentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-110
Sorting the Windows Credentials Area . . . . . . . . . . . . . . . . . . . . . . 3-110
Logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-111
Setting ES Logging Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-111
Setting 802.1X Devices Logging Levels . . . . . . . . . . . . . . . . . . . . . . . . . 3-112
Setting IDM Logging Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-112
Advanced Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-114
Setting the Agent Read Timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-114
Setting the RPC Connection Timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-114
Setting the RPC Command Timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-115
4 Endpoint Activity
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-2
Filtering the Endpoint Activity Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-4
Filtering by Access Control or Test Status . . . . . . . . . . . . . . . . . . . . . . . . . 4-4
Filtering by Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-5
Limiting Number of Endpoints Displayed . . . . . . . . . . . . . . . . . . . . . . . . . 4-6
Searching . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-7
Access Control States . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-9
Test Status States . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-10
Viewing Endpoint Access Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-14
vi
Page 9

Selecting Endpoints to Act on . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-15
Acting on Selected Endpoints . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-16
Manually Retest an Endpoint . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-16
Immediately Grant Access to an Endpoint . . . . . . . . . . . . . . . . . . . . . . . . 4-16
Immediately Quarantine an Endpoint . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-17
Clearing Temporary Endpoint States . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-17
Viewing Endpoint Information . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-18
5 End-user Access
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-2
Endpoints Supported . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-3
Browser Version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-4
Browser Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-5
Agentless Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-6
Ports Used for Testing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-8
Firewall Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-9
Managed Endpoints . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-9
Unmanaged Endpoints . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-9
Allowing the Windows RPC Service Through the Firewall . . . . . . . . . . . . 5-9
Allowing NAC 800 through the OS X Firewall . . . . . . . . . . . . . . . . . . . . 5-12
End-user Access Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-15
Opening Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-16
Windows NAC Agent Test Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-17
Automatically Installing the Windows Agent . . . . . . . . . . . . . . . . . . 5-17
Removing the Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-20
Manually Installing the Windows Agent . . . . . . . . . . . . . . . . . . . . . . 5-20
How to View the Windows Agent Version Installed . . . . . . . . . . . . . 5-21
Mac OS Agent Test Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-22
Installing the MAC OS Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-22
Verifying the Mac OS Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-25
Removing the Mac OS Agent . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-29
ActiveX Test Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-30
Agentless Test Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-30
Testing Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-33
Test Successful Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-34
Temporary Quarantine Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-35
Testing Cancelled Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-36
Testing Failed Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-37
Setting the Temporary Access Period . . . . . . . . . . . . . . . . . . . . . . . . 5-38
Error Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-38
Contents
vii
Page 10

Contents
Customizing Error Messages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-40
6 NAC Policies
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-2
Standard NAC Policies . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-4
NAC Policy Group Tasks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Add a NAC Policy Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Editing a NAC Policy Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-5
Deleting a NAC Policy Group . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-6
NAC Policy Tasks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-7
Enabling or Disabling an NAC Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-7
Selecting the Default NAC Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-7
Creating a New NAC Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-7
Editing a NAC Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-12
Copying a NAC Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-12
Deleting a NAC Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-13
Moving a NAC Policy Between NAC Policy Groups . . . . . . . . . . . . . . . . 6-13
Assigning Endpoints and Domains to a Policy . . . . . . . . . . . . . . . . . . . . . 6-13
NAC Policy Hierarchy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-14
Setting Retest Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-14
Setting Connection Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-14
Defining Non-supported OS Access Settings . . . . . . . . . . . . . . . . . . . . . . 6-15
Setting Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-15
Selecting Action Taken . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-15
About NAC 800 Tests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-17
Viewing Information About Tests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-17
Selecting Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-17
Entering Software Required/Not Allowed . . . . . . . . . . . . . . . . . . . . . 6-17
Entering Service Names Required/Not Allowed . . . . . . . . . . . . . . . . 6-18
Entering the Browser Version Number . . . . . . . . . . . . . . . . . . . . . . . 6-19
Test Icons . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-19
viii
7 Quarantined Networks
Endpoint Quarantine Precedence . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-2
Using Ports in Accessible Services and Endpoints . . . . . . . . . . . . . . . . . . . . . 7-4
Determining Accessible Services Example . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-6
Always Granting Access to an Endpoint . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-13
Always Quarantining an Endpoint . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-15
New Users . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-16
Shared Resources . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-17
Page 11

Untestable Endpoints and DHCP Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-18
8 High Availability and Load Balancing
High Availability . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-2
Load Balancing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-6
9 Inline Quarantine Method
Inline . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-2
10 DHCP Quarantine Method
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-2
Configuring NAC 800 for DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-4
Setting Up a Quarantine Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-4
Router Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-4
Configuring the Router ACLs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-5
Configuring Windows Update Service for XP SP2 . . . . . . . . . . . . . . . . . . 10-5
11 802.1X Quarantine Method
About 802.1X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-2
NAC 800 and 802.1X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-4
Setting Up the 802.1X Components . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-7
Setting up the RADIUS Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-7
Using the NAC 800 IAS Plug-in to the Microsoft IAS RADIUS Server .
11-7
Configuring the Microsoft IAS RADIUS server . . . . . . . . . . . . . . . 11-10
Proxying RADIUS Requests to an Existing RADIUS Server Using the
Built-in NAC 800 RADIUS Server . . . . . . . . . . . . . . . . . . . . . . . . . 11-37
Using the Built-in NAC 800 RADIUS Server for Authentication . . 11-40
Configuring Non-HP Switches . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-40
Enabling NAC 800 for 802.1X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-43
NAC 800 Console Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-43
Setting Up the Supplicant . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-44
Contents
ix
Page 12

Contents
Setting Up the Authenticator . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-47
Cisco® 2950 IOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-47
Cisco® 4006 CatOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-48
Enterasys® Matrix 1H582-25 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-49
Extreme® Summit 48si . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-49
ExtremeWare . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-50
ExtremeXOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-50
Foundry® FastIron® Edge 2402 . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-51
HP ProCurve® 420AP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-51
HP ProCurve® 530AP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-52
HP ProCurve® 3400/3500/5400 . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-53
Nortel® 5510 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-54
12 Reports
Report Types . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-2
Generating Reports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-4
Viewing Report Details . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-6
Printing Reports . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-7
Saving Reports to a File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-8
Converting an HTML Report to a Word Document . . . . . . . . . . . . . . . . . . 12-9
13 System Administration
Launching NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-3
Launching and Logging into NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-3
Logging out of NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-3
Important Browser Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-3
Downloading New Tests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-4
System Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-5
Matching Windows Domain Policies to NAC Policies . . . . . . . . . . . . . . . 13-5
Setting the Access Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-5
Naming your Enforcement Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-6
Changing the MS Host Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-6
Changing the ES Host Name . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-6
Resetting your System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-6
Changing Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-7
Specifying an Email Server for Sending Notifications . . . . . . . . . . . . . . . 13-8
Windows 2003 Server Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-8
Entering Networks Using CIDR Format . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-9
Database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-10
Creating a Backup File . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-10
x
Page 13

Contents
Restoring from Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-10
Restoring the Original Database . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-11
Generating a Support Package . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-11
Supported VPNs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-12
Adding Custom Tests . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-13
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-13
References . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-13
Changing the Error Messages in a Test Script . . . . . . . . . . . . . . . . . . . . 13-13
Creating a Custom Test Class Script from Scratch . . . . . . . . . . . . . . . . . 13-18
BasicTests API . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-28
End-user Access Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-33
How NAC 800 Handles Static IP Addresses . . . . . . . . . . . . . . . . . . . . . . . . 13-34
Managing Passwords . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-35
Resetting the NAC 800 Server Password . . . . . . . . . . . . . . . . . . . . . . . . 13-36
Serial Console . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-36
Reset Appliance Mode . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-37
Resetting the NAC 800 Database Password . . . . . . . . . . . . . . . . . . . . . . 13-37
Changing the NAC 800 Administrator Password . . . . . . . . . . . . . . . . . . 13-37
Working with Ranges . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-39
Creating and Replacing SSL Certificates . . . . . . . . . . . . . . . . . . . . . . . . . . 13-41
Creating a New Self-signed Certificate . . . . . . . . . . . . . . . . . . . . . . . . . . 13-42
Using an SSL Certificate from a known Certificate Authority (CA) . . . 13-43
Moving an ES from One MS to Another . . . . . . . . . . . . . . . . . . . . . . . . . . 13-45
Recovering Quickly from a Network Failure . . . . . . . . . . . . . . . . . . . . . . . 13-46
A Tests Help
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-3
Browser Security Policy – Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-4
Browser Version . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-5
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-5
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-5
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-6
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-6
Internet Explorer (IE) Internet Security Zone . . . . . . . . . . . . . . . . . . . . . . A-6
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-6
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-6
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-7
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-7
xi
Page 14

Contents
Internet Explorer (IE) Local Intranet Security Zone . . . . . . . . . . . . . . . . . A-7
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-7
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-7
How Does this Affect me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-8
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-8
Internet Explorer (IE) Restricted Site Security Zone . . . . . . . . . . . . . . . . A-8
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-8
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-8
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-9
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-9
Internet Explorer (IE) Trusted Sites Security Zone . . . . . . . . . . . . . . . . . A-10
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-10
Test properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-10
Operating System – Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-11
IIS Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-11
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-11
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-11
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-11
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-11
Internet Explorer Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-11
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-11
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-12
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-12
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-12
MVM Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-12
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-12
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-12
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-12
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-12
Service Packs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-13
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-13
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-13
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-13
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-13
Windows 2000 Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-13
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-13
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-13
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-13
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-14
xii
Page 15

Contents
Windows Media Player Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-14
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-14
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-14
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-14
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-14
Windows Server 2003 SP1 Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-14
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-14
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-14
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-15
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-15
Windows Server 2003 SP2 Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-15
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-15
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-15
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-15
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-15
Windows Server 2003 Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-15
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-15
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-16
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-16
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-16
Windows XP SP2 Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-16
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-16
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-16
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-16
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-16
Windows XP Hotfixes . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-17
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-17
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-17
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-17
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-17
Windows Automatic Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-17
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-17
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-17
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-18
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-18
Security Settings – OS X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
Mac AirPort Preference . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
xiii
Page 16

Contents
Mac AirPort User Prompt . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-19
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-20
Mac AirPort WEP Enabled . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-20
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-20
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-20
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-20
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-20
Mac Bluetooth . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-20
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-20
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-20
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-21
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-21
Mac Firewall . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-21
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-21
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-21
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-21
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-21
Mac Internet Sharing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-22
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-22
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-22
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-22
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-22
Mac Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-22
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-22
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-22
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-22
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-23
Security Settings – Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-24
Allowed Networks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-24
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-24
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-24
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-24
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-24
MS Excel Macros . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-24
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-24
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-24
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-25
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-25
xiv
Page 17

Contents
MS Outlook Macros . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-25
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-25
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-25
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-26
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-26
MS Word Macros . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-26
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-26
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-26
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-27
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-27
Services Not Allowed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-27
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-27
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-27
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-27
What do I need to do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-28
Services Required . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-28
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-28
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-28
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-29
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-29
Windows Bridge Network Connection . . . . . . . . . . . . . . . . . . . . . . . . . . A-29
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-29
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-30
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-30
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-30
Windows Security Policy . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-30
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-30
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-30
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-31
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-31
Windows Startup Registry Entries Allowed . . . . . . . . . . . . . . . . . . . . . . A-32
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-32
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-32
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-32
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-33
Software – Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-34
Anti-spyware . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-34
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-34
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-34
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-34
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-34
xv
Page 18

Contents
Anti-virus . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-35
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-35
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-35
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-35
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-35
High-risk Software . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
MS Office Version Check . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-36
P2P . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-37
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-37
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-37
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-37
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-37
Personal Firewalls . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-37
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-37
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-37
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-38
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-38
Software Not Allowed . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-38
Description: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-38
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-38
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-39
Software Required . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-39
Description . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-39
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-39
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-39
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-39
Worms, Viruses, and Trojans . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-39
Description: . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-39
Test Properties . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-40
How Does this Affect Me? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-40
What Do I Need to Do? . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . A-40
xvi
B Important Browser Settings
Pop-up Windows . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-2
Active Content . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-3
Page 19

Minimum Font Size . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-5
Page Caching . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-6
Temporary Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . B-7
C Installation and Configuration Check List
Minimum System Requirements . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-2
IP Addresses, Hostname, Logins, and Passwords . . . . . . . . . . . . . . . . . . . . C-3
Single-server Installation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-3
Multiple-server Installations . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-3
Management Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-3
Enforcement Server 1 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-4
Enforcement Server 2 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-5
Enforcement Server 3 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-5
Proxy Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-6
Agentless Credentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-7
Quarantine . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-8
802.1X . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-8
802.1X Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-9
DHCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-10
Accessible services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-10
Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-12
Test Exemptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . C-13
Contents
D Glossary
Index
xvii
Page 20

Contents
(This page intentionally left blank.)
xviii
Page 21

Introduction
Chapter Contents
What you Need to get Started . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-2
NAC 800 Home Window . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-4
System Monitor . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-6
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-8
Technical Support . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-13
Additional Documentation . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-14
Upgrading . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-15
Conventions Used in This Document . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Copying Files . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-20
1
The NAC 800 Process . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-10
About NAC 800 . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-10
Navigation Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Tip Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Note Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Caution Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-16
Warning Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Bold Font . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Task Paragraph . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Italic Text . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-17
Courier Font . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-18
Angled Brackets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-18
Square Brackets . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-18
Terms . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-19
SCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-20
PSCP . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-20
1-1
Page 22

Introduction
What you Need to get Started
The following hardware and software is required to operate NAC 800:
■ One or more ProCurve NAC 800 appliances
■ Configuration information – See “Installation and Configuration
■ An Internet connection or a web proxy server that allows outbound
■ Workstation – A workstation running one of the following browsers
■ A ProCurve NAC Implementation Start-up Service, from an autho-
■ A ProCurve NAC Endpoint Integrity Agent License
What you Need to get Started
Check List” on page C-1
HTTPS communications from the MS
with 128-bit encryption:
•Windows –
Mozilla version 1.7
Mozilla Firefox version 1.5 or later
Internet Explorer 6.0
• Linux –
Mozilla version 1.7
Mozilla Firefox version 1.5 or later
rized ProCurve partner or ProCurve.
1-2
ProCurve NAC 800 is delivered as a hardware appliance that you install in your
network. After NAC 800 is installed in your network, you configure it using a
workstation with browser software installed.
The browser software must be configured as described in “Important Browser
Settings” on page B-1.
The following documents provide information on installation and configuration, and are available at www.procurve.com/nactools:
1. ProCurve Network Access Controller 800 Hardware Installation Guide
– Refer to this document first to see how to prepare for and perform the
physical installation of the appliance and how to establish initial
management access. This document contains appliance specifications,
safety information, and appliance certifications.
2. ProCurve Network Access Controller 800 Configuration Guide – Refer
to this document second, to understand the product's features,
capabilities, and use. This document explains how to configure the
appliance based on the usage model you choose to deploy in your
network.
Page 23

What you Need to get Started
Introduction
3. ProCurve Network Access Controller 800Users’ Guide – Refer to this
document last for information on configuring, monitoring activities,
creating NAC policies, and running reports.
1-3
Page 24

Introduction
NAC 800 Home Window
NAC 800 Home Window
The NAC 800 Home window (figure 1-1) is a centralized management console
that allows you to quickly assess the status of your network. The following
list and figure describe and show the key features:
1. Important status announcements – If there is anything that needs your
immediate attention, a status announcement is displayed at the top of the
window. Click clear to remove the announcement.
2. Username’s account – Click this icon to open the user account editing
window. See “User Accounts” on page 3-29 for details on creating and
editing user accounts. You must have administrator privileges to create
user accounts; however, any user can edit their own account.
3. Top 5 failed tests area – The Top 5 failed tests area indicates the tests that
fail the most. Click on an endpoint number or the Test results report option
to view details.
4. Window actions – Use these links to refresh the window, log out of the
console, and access online help.
5. Navigation pane – The menu items shown in this pane vary depending on
your permission level. See “User Roles” on page 3-37 for more information
on permissions. You must have administrator privileges to create and edit
user roles. Once you select a menu item from the navigation pane, use the
bread crumbs at the top of the windows to navigate throughout the
console (see figure 1-2. System Monitor Window on page 1-7).
1-4
6. Endpoint test status area – The Endpoint tests area displays the total
number of endpoints that NAC 800 has attempted to test, and what the
test status is for each endpoint. Click the number of endpoints to view
details.
7. Access control status area – The Access control area displays the total
number of endpoints that have attempted to connect to your network, and
what the access state is as a percentage and as a number. Click on the
number of endpoints to view details.
8. Enforcement server status area – The Enforcement server status area
provides status on your Enforcement servers. Click the System monitor
option to view details.
Page 25
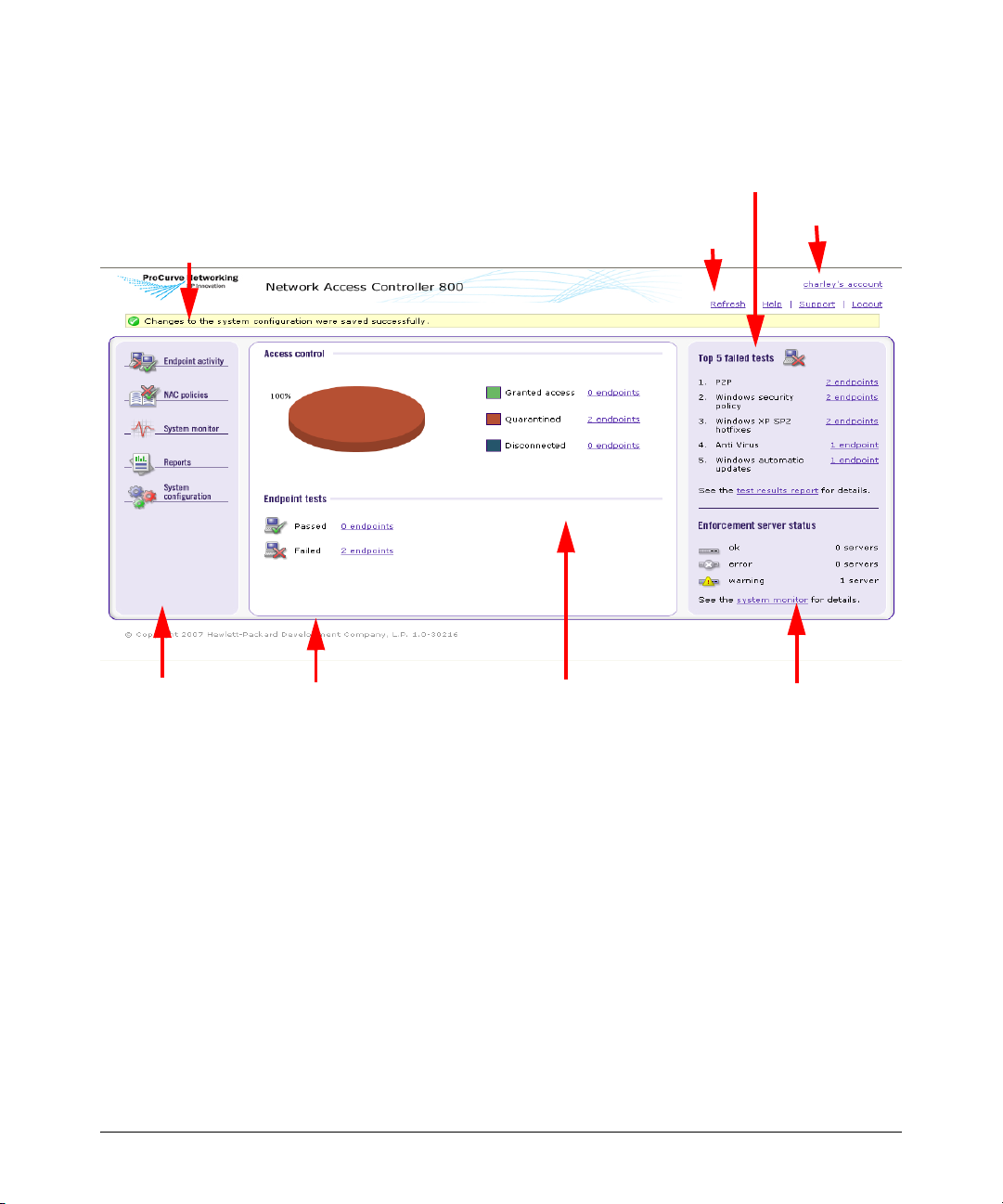
NAC 800 Home Window
3. Top 5 failed
tests area
Introduction
1. Important status
announcements
5. Navigation
pane
6. Test
status area
4. Window actions
7. Access control
status area
2. User name
8. Enforcement server
status area
Figure 1-1. NAC 800 Home Window
1-5
Page 26

Introduction
System Monitor
System Monitor
The System monitor window provides the following information:
■ Enforcement cluster name – The Enforcement clusters are listed by
name in the order they were created. Click on a cluster name to view
cluster details. You must have cluster-editing permissions to view and
edit cluster details.
■ Server name by cluster – The servers for each cluster are listed by
name in the order they were created. Click on a server name to view
server details. You must have cluster-editing permissions to view and
edit server details.
■ Cluster access mode – The cluster access mode is either normal, allow
all, or quarantine all. See “Enforcement Clusters and Servers” on page
3-6 for instructions on making the access mode selection.
■ Health status – Health status shows ok for servers with no problems,
and either warning or error for servers with problems. Click the server
name to view details.
■ Upgrade status – Upgrade status shows the status of any upgrades in
process.
■ % memory used – The amount of memory currently used by each
server is shown as a percentage of total memory available.
■ Endpoints tested/minute – The number of endpoints tested over the
last 15 minutes or less.
■ Endpoints queued – The number of tests running or scheduled to run
on that ES.
■ System load average – The number of processes waiting to run (top
command). In Linux, entering top at the command line returns a realtime look at processor activity.
1-6
Page 27
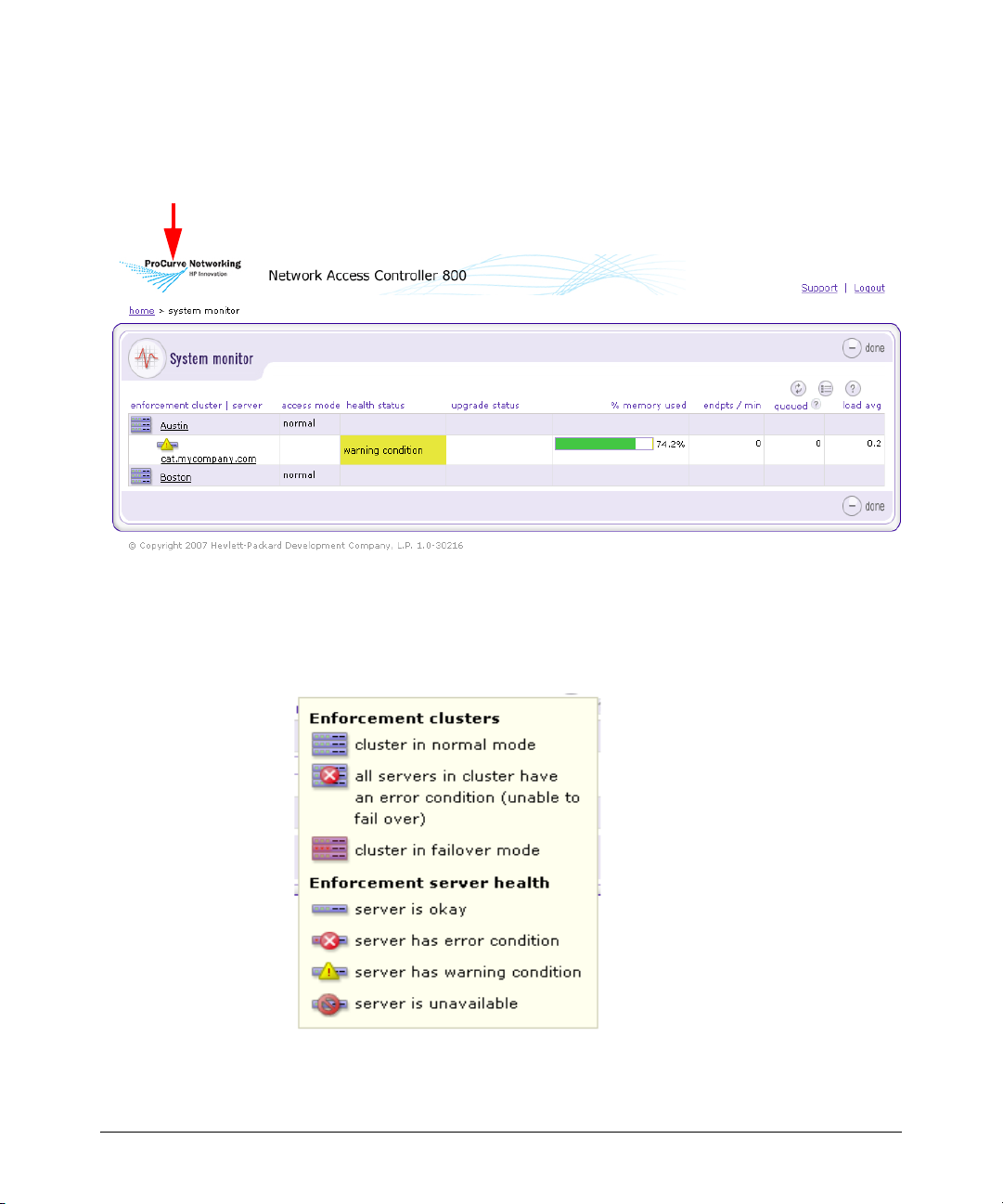
Breadcrumbs for navigation
Introduction
System Monitor
Figure 1-2. System Monitor Window
The following figure shows the legend for the System monitor window icons:
Figure 1-3. System Monitor Window Legend
1-7
Page 28
Introduction
Overview
Overview
NAC 800 protects the network by ensuring that endpoints are free from threats
and in compliance with the organization's IT security standards. NAC 800
systematically tests endpoints—with or without the use of a client or agent—
for compliance with organizational security policies, quarantining non-compliant machines before they damage the network.
NAC 800 ensures that the applications and services running on endpoints
(such as LAN, RAS, VPN, and WiFi endpoints) are up-to-date and free of
worms, viruses, trojans, P2P and other potentially damaging software. It
dramatically reduces the cost and effort of securing your network's weakest
links—the endpoints your IT group might not adequately control.
There are advantages and disadvantages inherent with each of the test method
technologies. Having a choice of testing solutions enables you to maximize
the advantages and minimize the disadvantages.
TIP: Agentless testing uses an existing Windows service (RPC). ActiveX testing
uses an ActiveX control. ProCurve agent testing installs an agent (ProCurve
NAC EI Agent) and runs as a new Windows service.
The trade-offs in the test methods are described in the following table:
Test method Trade-offs
Pros Cons
Agentless • Truly agentless, no install or download.
• No extra memory load on the client machine.
• Can begin testing, view test results, and give
network access without any end-user
interaction for
domains.
• Easiest of the three test methods to deploy.
• Saves administration time and is therefore
less expensive than agent-based solutions.
endpoints on your Windows
Table 1-1.Test Methods
1-8
• Requires RPC Service to be available to the
NAC 800 server (ports 139 or 445).
• Requires file and print sharing to be enabled.
• Not supported by legacy Windows™
operating systems and non-Windows
operating systems.
• If the endpoint is not on a domain, the user
must specify local credentials. A user often
does not know what credentials to enter.
Page 29

Test method Trade-offs
Pros Cons
Introduction
Overview
ActiveX plug-in • No installation or upgrade to maintain.
• Supports all Windows operating systems.
• Only Internet Explorer application access
required through personal firewall. Must
open port 1500.
ProCurve NAC EI
Agent
• Always available for retesting.
• The agent is automatically updated with
product updates.
• Supports all Windows platforms.
Table 1-1.Test Methods (cont.)
The following list highlights key features:
■ Enforcement options – NAC 800 provides multiple enforcement
options for quarantining endpoints that do not comply with your
security policy (Inline, DHCP, and 802.1X). This enables NAC 800 to
enforce compliance across complex, heterogeneous networks.
■ High availability and load balancing – A multi-server NAC 800 deploy-
ment is mutually supporting. Should one server fail, other nodes
within a cluster will automatically provide coverage for the affected
network segment.
• No retesting of endpoint once browser is
closed.
• Not supported by non-Windows operating
systems.
• Browser security settings must allow
ActiveX control operation of signed and safe
controls. This is the default for the Internet
zone. Raise the Internet zone setting and
make
NAC 800 part of the trusted zone.
• Requires interaction from end-users—they
must download the control before they can
access network.
• Install and upgrade to maintain.
• Requires one-time interaction from endusers—they must download and install
before they can access network.
Load balancing is achieved by an algorithm that spreads the endpoint
testing load across all Enforcement servers in a cluster.
■ Multiple-user, role-based access – In enterprise deployments
numerous individuals, each with varying responsibilities, typically
require access to information within NAC 800. Role-based access
enables system administrators to control who has access to the data,
the functions they are allowed to perform, and the information they
can view and act on. Role-based access ensures the integrity of the
enterprise-wide NAC 800 deployment and creates the separation of
duties that conforms to security best-practices.
1-9
Page 30

Introduction
Overview
■ Extensible – NAC 800’s easy-to-use open API allows administrators
to create custom tests for meeting unique organizational requirements. The API is fully exposed and thoroughly documented. Custom
tests are created using scripts and can be seamlessly added to existing
policies.
■ Compatible with existing heterogeneous network infrastructure – No
upgrades to your existing network infrastructure are required.
■ Variety of enforcement options – Permit, deny, or quarantine based
on test results.
■ Self-remediation – Reduces IT administration by empowering users
to bring their machines into compliance.
■ Subscription-based licensing – Includes all test updates and software
upgrades.
The NAC 800 Process
NAC 800 administrators create "NAC policies" that define which applications
and services are permitted, and specify the actions to be taken when endpoints
do not comply. NAC 800 automatically applies the NAC policies to endpoints
as they log into the network, and periodically as the endpoints remain logged
into the network. Based on results, endpoints are either permitted or quarantined to a specific part of the network, thus enforcing the organizational
security standards. NAC 800 tracks all testing and connection activity and
produces a range of reports for auditors, managers, and IT staff.
1-10
About NAC 800
NAC Policy Definition
NAC policies consist of individual tests that evaluate the security status of
endpoints attempting to access the network. Specific tests assess operating
systems, verify that key hotfixes and patches have been installed, ensure
antivirus and other security applications are present and up-to-date, detect
the presence of worms, trojans, and viruses, and check for potentially dangerous applications such as file sharing, peer-to-peer (P2P), or spyware. See
“Tests Help” on page A-1 for more information.
Key features include:
■ Out-of-the-box NAC policies – High, medium, and low security are
ready to use with no additional configuration required.
■ Standard tests – NAC 800 comes with a broad range of tests.
Page 31

Introduction
Overview
■ Automatic test updates – NAC 800 is automatically updated with tests
that cover newly released patches, hotfixes, software updates,
worms, and trojans, and recommended security settings for common
applications. New tests are automatically added to the test database
as frequently as hourly, ensuring immediate protection against newly
discovered threats.
■ Organization-specific policies – Any number of NAC policies can be
created and tailored to your organizational needs. Create policies for
like endpoints (for example, all Windows 2000 workstations), for an
IP range or specific IPs, or by geographic location.
Endpoint Testing
NAC 800 automatically tests all endpoints attempting to access your network
through a LAN, RAS, VPN, or WiFi connection. Tests are fast and you are kept
informed of test progress and results. After the initial compliance tests, NAC
800 periodically tests endpoints that have been granted access to ensure that
real-time system changes do not violate the NAC policy.
TIP: NAC 800 passes approximately 9 to 16 kilobytes of total data between a single
endpoint and a single NAC 800 server for a single testing session with the High
Security NAC policy (approximately 20 tests). It typically takes between 5 and
10 seconds to all tests in a policy on a 100Mb LAN. If your endpoints are taking
longer to test, there might be a configuration problem with DNS on the NAC
800 server.
NOTE: If the end-user selects ActiveX test and then closes the browser, their endpoint
is not retested until the end-user opens another browser session, reloading
the ActiveX agent.
Key features include:
■ Multiple test method options – Agentless, ActiveX, or ProCurve NAC
EI Agent. Select the most appropriate method for your environment
or endpoint.
■ Rapid testing and robust endpoint management – Thousands of
endpoints can be tested and managed simultaneously.
■ Continual testing – Endpoints are retested on an administrator-
defined interval as long as they remain connected to the network.
1-11
Page 32

Introduction
Overview
Compliance Enforcement
Based on endpoint test results, NAC 800 takes the appropriate action. Endpoints that test compliant with the applied policy are permitted access. Noncompliant endpoints are either quarantined, or are given access for a temporary period. Implement the necessary fixes during this period.
Key features include:
■ Flexible enforcement options – Grant or quarantine access criteria is
designated by the administrator and driven by the criticality of
selected tests and corporate security standards.
■ Manual overrides – Administrators can retest, quarantine, or grant
access to endpoints on demand.
■ User notifications – Users of non-compliant endpoints receive imme-
diate notification about the location of the endpoint deficiencies, as
well as step-by-step information about implementing the corrections
to achieve compliance.
■ Administrator notifications – Administrators receive a variety of noti-
fications and alerts based on testing and access activity.
■ Graduated enforcement – Allows controlled system rollout.
1-12
Automated and Manual Repair
■ Self-remediation – End-users are notified of where their endpoints are
deficient and provided with remediation instructions.
■ Access "grace period" – Non-compliant endpoints are granted access
for a temporary, administrator-defined period to facilitate remediation.
Targeted Reporting
NAC 800 reports provide concise security status information on endpoint
compliance and access activity. Specific reports are available for auditors,
managers, and IT staff members.
For more information, see “Reports” on page 12-1.
Page 33

Technical Support
Technical support is available through www.procurve.com.
Introduction
Technical Support
1-13
Page 34

Introduction
Additional Documentation
Additional Documentation
NAC 800 documentation is available in a number of media formats and is
accessible in a variety of ways:
■ Quick-start card – The Quick-start card provides a high-level overview
of the physical deployment options, software installation, post-installation configuration, the Users’ Guide, and how to get support.
■ Online help – Online help is an essential component that assists in the
installation, configuration, and ongoing management of NAC 800. You
can access the online help by clicking the question mark displayed in
the upper-right corner of the primary interface elements.
1-14
Page 35

Introduction
Upgrading
Upgrading
Upgrading is described in“Checking for NAC 800 Upgrades” on page 3-27.
CAUTION: Installing third-party software on the NAC 800 server is not supported. If you
install additional software on the NAC 800 server, you need to remove it in
order to troubleshoot any NAC 800 issues, and it will likely be partially or fully
overwritten during NAC 800 release upgrades or patch installs, compromising
the third-party software functionality. Additionally, installing third-party software and/or modifying the NAC 800 software can violate your license agreement.
1-15
Page 36

Introduction
Conventions Used in This Document
Conventions Used in This Document
The conventions used in this document are described in this section:
Navigation Paragraph
Navigation paragraphs provide a quick visual on how to get to the screen or
area discussed.
Example:
NAC 800 main window>>Configure system
Tip Paragraph
Tips provide helpful, but not required information.
Example:
TIP: Hover the cursor over the “x dhcp servers with errors” text to get additional
information in a pop-up window.
Note Paragraph
Notes notify you of important information.
Example:
NOTE: If there is no activity for 30 minutes, the configuration window times out and
you must log in again.
Caution Paragraph
Cautions notify you of conditions that can cause errors or unexpected results.
Example:
CAUTION: Do not rename the files or they will not be seen by NAC 800.
1-16
Page 37

Conventions Used in This Document
Introduction
Warning Paragraph
Warnings notify you of conditions that can lock your system or cause damage
to your data.
Example:
WARNING: Do not log in using SSH—this kills your session and causes your session to
hang.
Bold Font
Bold font indicates the text that appears on a window or screen.
Example:
9. If the Domains connection method is enabled (Credentials tab, enabled
check box), you must specify your Windows domain controller here.
Task Paragraph
Task paragraphs summarize the instructions that follow.
Example:
To enter LDAP information:
Italic Text
Italic text is used in the following cases:
■ Showing emphasis –
Low – You are not protected from potentially unsafe macros. (Not
recommended).
■ Indicating document titles –
NAC 800 Installation Guide
■ Indicating a variable entry in a command –
https://<IP_address>/index.html
In this case, you must replace <IP_address> with the actual IP
address, such as 10.0.16.99. Do not type the angled brackets.
1-17
Page 38

Introduction
Conventions Used in This Document
Courier Font
Courier font is used in the following cases:
■ Indicating path names –
Change the working directory to the following:
C:\Program Files\<MyCompany>\
■ Indicating text; enter exactly as shown –
ProCurve NAC EI Agent
Enter the following URL in the browser address field:
https://<IP_address>/index.html
In this case, you must replace <IP_address> with the actual IP
address, such as 10.0.16.99. Do not type the angled brackets.
■ Indicating file names –
SAIASConnector.ini
Angled Brackets
Angled brackets enclose variable text that needs to be replaced with your
specific values.
Example:
https://<IP_address>/index.html
In this case, you must replace <IP_address> with the actual IP address, such
as 10.0.16.99. Do not type the angled brackets.
1-18
Square Brackets
Square brackets are used in the following cases:
■ Indicating keys to press on the keyboard –
[Ctrl]+[Shift]+[r]
Page 39

Conventions Used in This Document
■ Indicating a variable section in a *.INI file –
[Global]
NASList=192.168.200.135
■ Indicating a list in a properties file –
Compliance.ObjectManager.DHCPConnectorServers=[192.168.51.130, 192.168.99.1]
Terms
Terms are defined in the “Glossary” on page D-1.
Example:
MAC Media Access Control – The unique number that identifies a
physical endpoint. Generally referred to as the MAC address.
Introduction
1-19
Page 40

Introduction
Copying Files
Copying Files
Whenever you copy a file from one machine to another, copy it using a secure
copy utility that uses the Secure Shell (SSH) protocol. The exact syntax of the
copy command will vary based on the utility you use.
Example:
10. Copy the /usr/local/nac/properties/NACAVPs.txt file from the
NAC 800 server to the ACS server using PSCP (or other secure copy
utility).
SCP
scp is a Linux/UNIX command used to copy files between Linux/UNIX
machines. It has the following syntax:
scp user@source:/directory/file user@destination:/directory/file
scp is included with Linux/UNIX.
1-20
PSCP
pscp is a program used to copy files between Windows and Linux/UNIX
machines.
To us e pscp, you must first save it from the following location to the Windows
machine:
http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html
Next, open a DOS (command) window on the Windows machine, and enter
the commands as follows:
To copy a file from a Linux machine to a Windows machine, enter the
following:
<pscp directory>\pscp fred@example.com:/etc/hosts
c:\temp\example-hosts.txt
You will be prompted to enter a password for the Linux/UNIX machine.
Page 41

Introduction
Copying Files
To copy a file from a Windows machine to a Linux machine, enter the
following:
<pscp directory>\pscp c:\documents\foo.txt fred@example.com:/tmp/foo
You will be prompted to enter a password for the Linux/UNIX machine.
NOTE: You can either enter the path to the PSCP.EXE file as part of the command,
or cd to the directory where you saved the PSCP.EXE file before entering the
pscp command.
1-21
Page 42

Introduction
Copying Files
(This page intentionally left blank.)
1-22
Page 43

Clusters and Servers
Chapter Contents
Overview . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-2
Installation Examples . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-3
2
2-1
Page 44

Clusters and Servers
Overview
Overview
NAC 800 uses clusters and servers. A "cluster" is a logical grouping of one or
more Enforcement servers (ESs) that are managed by one Management server
(MS).
A single-server installation is one where the MS and ES are on one server. The
ES is assigned to a Default cluster. This configuration is illustrated in figure 2-
1.
A multiple-server installation is one where the MS is on one server and there
are one or more ESs on separate servers. Each ES must be assigned to a
cluster. This configuration is illustrated in figure 2-2.
The responsibilities of the MS and ES are as follows:
■ Management server
•Configuration
• NAC policies
• Quarantining
• Endpoint activity
• License
• Test updates
■ Enforcement server
•Testing
• Access control
2-2
The quarantine method is defined per cluster; all of the Enforcement servers
in a given cluster use the same quarantine method (Inline, DHCP, or 802.1X).
When using multiple clusters, each cluster can have a different quarantine
method. Clusters cooperate to test and control access to the network,
although the ESs in each cluster are not able to communicate with any ES in
any other cluster.
Page 45

Clusters and Servers
Installation Examples
Installation Examples
Single-server Installation
The simplest installation is where the MS and ES are installed on the same
physical server as shown in the following figure:
Figure 2-1. Single-server Installation
Multiple-server Installations
By using at least three servers, one for the MS and two for Enforcement
servers, you gain the advantage of high availability and load balancing.
2-3
Page 46
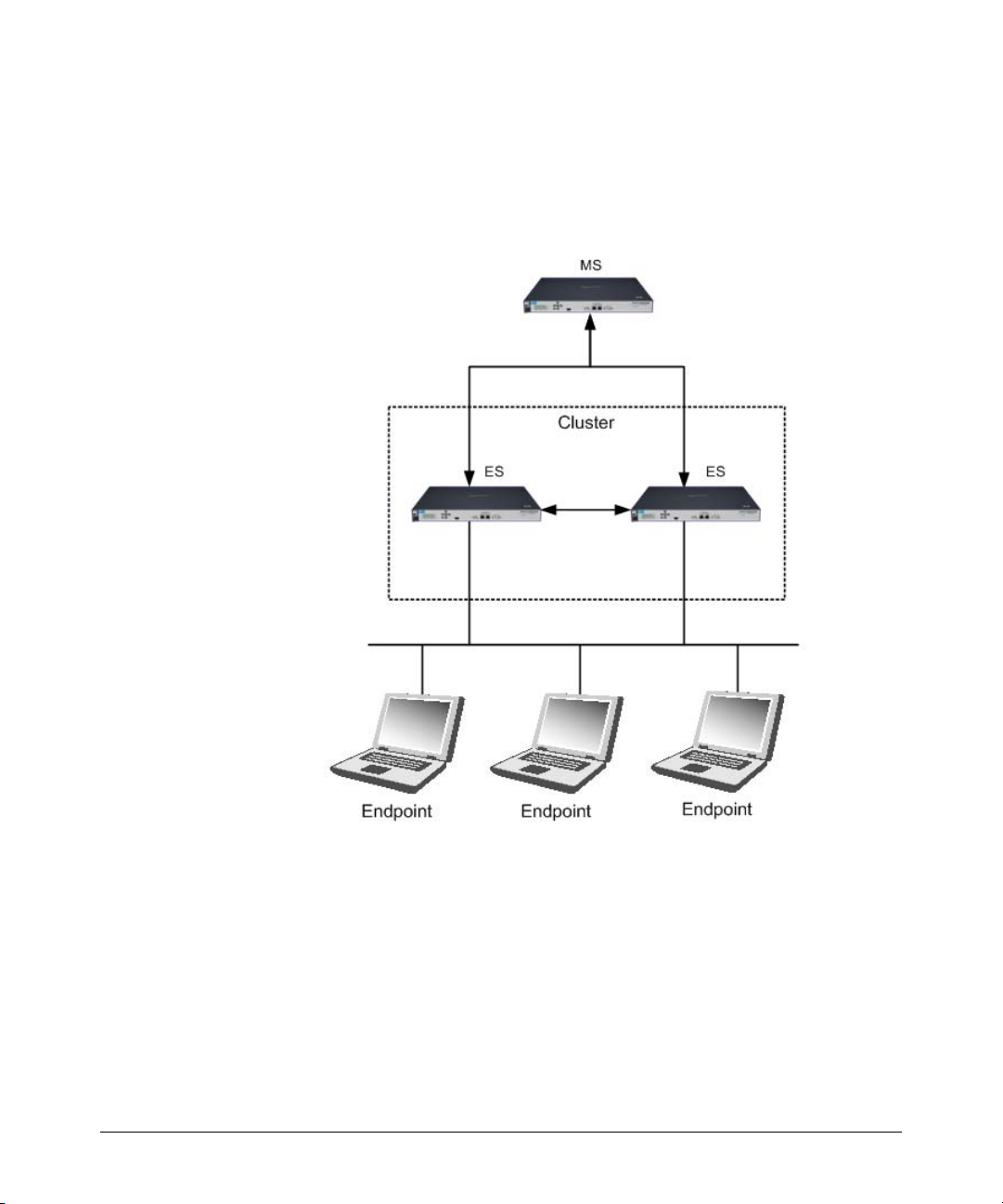
Clusters and Servers
Installation Examples
High availability is where Enforcement servers take over for any other
Enforcement server or servers that become unavailable. Load balancing is
where the testing of endpoints is spread evenly over all of the Enforcement
servers. A three-server installation is shown in the following figure:
2-4
Figure 2-2. Multiple-server Installation
Page 47
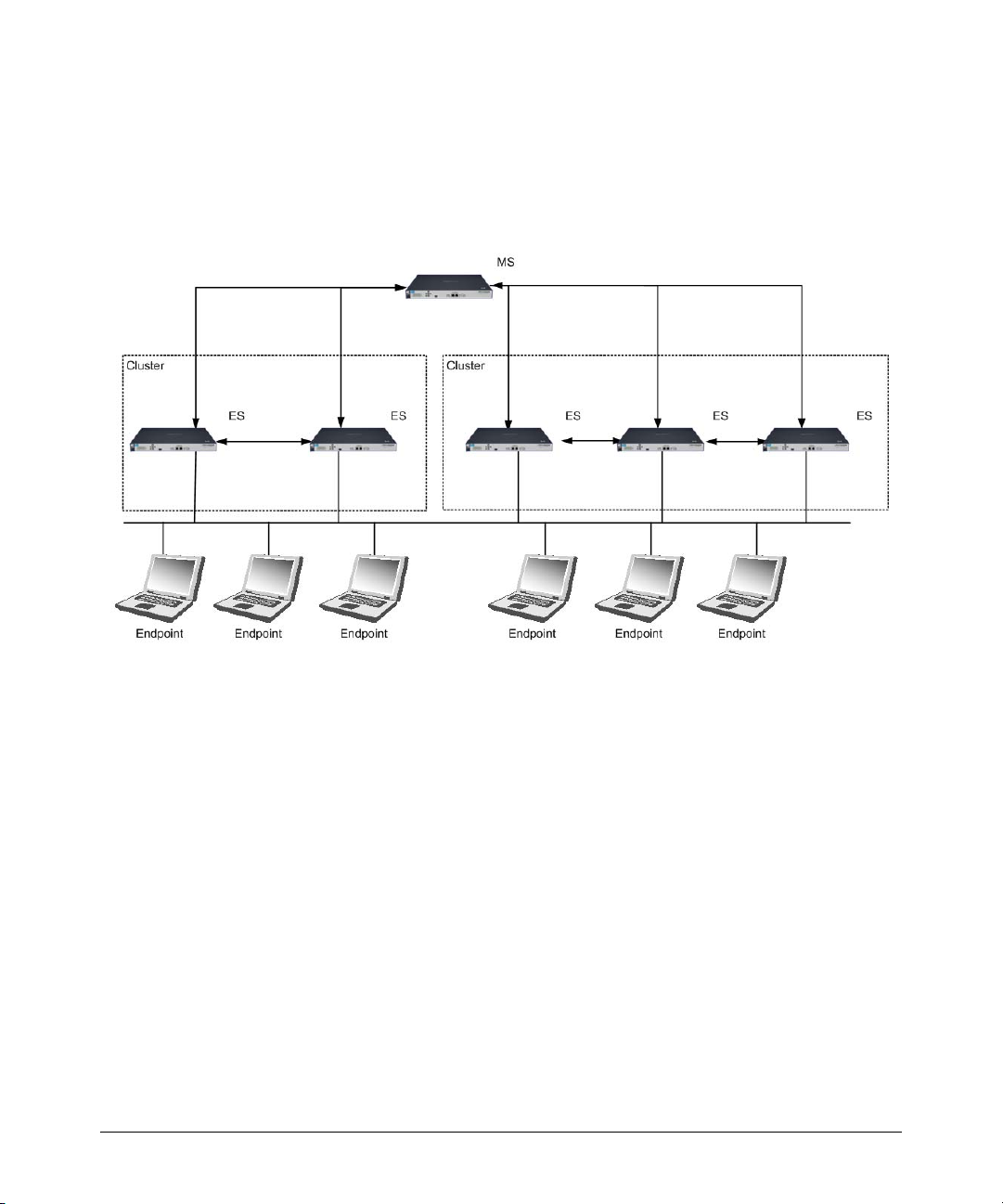
Clusters and Servers
Installation Examples
When your network is more complex, you can continue to add clusters as
shown in the following figure:
Figure 2-3. Multiple-server, Multiple-cluster Installation
The system configuration area allows you to select default settings for all
clusters, as well as override the default settings on a per-cluster basis. See
“System Configuration” on page 3-1 for task-based instructions.
The following recommendations should be followed when configuring your
network for best performance results:
■ A maximum of five ESs per cluster
■ A maximum of 10 ESs per MS
■ A maximum of 3000 endpoints per ES
When these recommendations are followed, the following applies:
■ 80% of the 3000 endpoints will be tested in 30 seconds or less
■ All endpoints are returned to the proper status within 15 minutes after
a network recovery (power failure, all endpoints attempting to reconnect, 3000 endpoints per ES)
2-5
Page 48

Clusters and Servers
Installation Examples
(This page intentionally left blank.)
2-6
Page 49

System Configuration
Chapter Contents
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-4
Enforcement Clusters and Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-6
Enforcement Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-7
Adding an Enforcement Cluster . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-7
Editing Enforcement Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-9
Viewing Enforcement Cluster Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-10
Deleting Enforcement Clusters . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-11
Enforcement Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-13
Adding an Enforcement Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-13
Cluster and Server Icons . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-15
Changing the Enforcement Server Network Settings . . . . . . . . . . . . . . . . 3-17
Changing the Enforcement Server Date and Time . . . . . . . . . . . . . . . . . . 3-17
Modifying the ES root Account Password . . . . . . . . . . . . . . . . . . . . . . . . 3-18
Modifying the ES root Account Password . . . . . . . . . . . . . . . . . . . . . . . . 3-18
Viewing Enforcement Server Status . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-18
Deleting Enforcement Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-20
Deleting Enforcement Servers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-20
Enforcement Server Recovery . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-20
Management Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-21
Viewing Network Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-21
Modifying Management Server Network Settings . . . . . . . . . . . . . . . . . . 3-23
Selecting a Proxy Server . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-23
Setting the Date and Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-24
Automatically Setting the Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-25
Manually Setting the Time . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-25
Selecting the Time Zone . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-26
Changing MS SNMP Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-26
Modifying the MS root Account Password . . . . . . . . . . . . . . . . . . . . . . . . 3-26
Checking for NAC 800 Upgrades . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-27
User Accounts . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-29
Adding a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-29
Searching for a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-32
3
3-1
Page 50

System Configuration
Sorting the User Account Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-33
Copying a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-33
Editing a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-34
Deleting a User Account . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-35
User Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-37
Adding a User Role . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-37
Editing User Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-40
Deleting User Roles . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-41
Sorting the User Roles Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-42
License . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-43
Updating Your License . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-43
Test Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-45
Manually Checking for Test Updates . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-45
Selecting Test Update Times . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-46
Viewing Test Update Logs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-47
Quarantining . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-49
Selecting the Quarantine Method . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-49
Entering Basic 802.1X Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-51
Selecting the RADIUS Authentication method . . . . . . . . . . . . . . . . . . . . . 3-51
Configuring Windows Domain Settings . . . . . . . . . . . . . . . . . . . . . . . . . . 3-52
Configuring OpenLDAP Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-54
Configuring Novell eDirectory Settings . . . . . . . . . . . . . . . . . . . . . . . . . . 3-57
Adding 802.1X Devices . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-60
Testing the Connection to a Device . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-61
Cisco IOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-62
Cisco CatOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-63
Enterasys . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-65
Extreme ExtremeWare . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-67
Extreme XOS . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-69
Foundry . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-71
HP ProCurve Switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-73
HP ProCurve WESM . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-76
HP ProCurve 420 AP or HP ProCurve 530 AP . . . . . . . . . . . . . . . . . . . . . 3-79
Nortel . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-81
Other . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-83
Setting DHCP Enforcement . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-85
Adding a DHCP Quarantine Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-87
Sorting the DHCP Quarantine Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-89
Editing a DHCP Quarantine Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-89
Deleting a DHCP Quarantine Area . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-90
3-2
Page 51

System Configuration
Maintenance . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-91
Initiating a New Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-91
Restoring From a Backup . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-93
Downloading Support Packages . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-94
Cluster Setting Defaults . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-95
Testing Methods . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-95
Selecting End-user Options . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-98
Accessible Services . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-98
Exceptions . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-100
Notifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-102
End-user Screens . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-104
Agentless Credentials . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-107
Logging . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-111
Setting ES Logging Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-111
Setting 802.1X Devices Logging Levels . . . . . . . . . . . . . . . . . . . . . . . . . 3-112
Setting IDM Logging Levels . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-112
Advanced Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-114
Setting the Agent Read Timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-114
Setting the RPC Connection Timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-114
Setting the RPC Command Timeout . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-115
3-3
Page 52

System Configuration
Introduction
Introduction
User logins and associated user roles determine the access permissions for
specific functionality within NAC 800. The following table shows the default
home window menu options that are available by user role:
User role Home window menu options available
System Administrator • Endpoint activity
• NAC policies
• System monitor
• Reports
• System configuration
Cluster Administrator • Endpoint activity
• System monitor
• Reports
• Enforcement clusters & servers
Help Desk Technician • Endpoint activity
• Reports
3-4
View-Only User • Endpoint activity
• Reports
Table 3-1.Default Menu Options
Only a system administrator can assign access permissions and access the
System configuration window. See Figure 1-1 on page 1-5 for the NAC 800 home
window of a user with system administration permissions. If you do not see
the System configuration menu option, you do not have system administrator
permissions.
NAC 800 configuration includes the following:
■ Enforcement clusters & servers – “Enforcement Clusters and
Servers” on page 3-6
■ Management server – “Management Server” on page 3-21
■ User accounts – “User Accounts” on page 3-29
■ User roles – “User Roles” on page 3-37
■ License – “License” on page 3-43
■ Test updates – “Test Updates” on page 3-45
Page 53

System Configuration
■ Quarantining – “Quarantining” on page 3-49
■ Maintenance – “Maintenance” on page 3-91
■ Cluster setting defaults
Introduction
• Testing Methods – “Testing Methods” on page 3-95
• Accessible services – “Accessible Services” on page 3-98
• Exceptions – “Exceptions” on page 3-100
• Notifications – “Notifications” on page 3-102
• End-user screens – “End-user Screens” on page 3-104
• Agentless credentials – “Agentless Credentials” on page 3-107
• Logging – “Logging” on page 3-111
• Advanced – “Advanced Settings” on page 3-114
NOTE: You can override any of the cluster default settings on a per-cluster basis.
3-5
Page 54

System Configuration
Enforcement Clusters and Servers
Enforcement Clusters and Servers
The Enforcement clusters & servers menu option (figure 3-3) is where you
configure Enforcement clusters and servers. You can perform the following
tasks:
■ Enforcement clusters
■ Enforcement servers
• Add, edit, or delete Enforcement clusters
• Set operating parameters for specific Enforcement clusters, which
differ from the default Enforcement cluster and server settings set up
on the System configuration window
• View available Enforcement clusters and associated servers
• View status of Enforcement clusters and servers
• Select cluster access mode (normal, allow all, or quarantine all)
• Add, edit, or delete Enforcement servers
• Set Enforcement server network settings, date and time, SNMP set-
tings, and password
• View available Enforcement servers
• View status, memory usage, and disk space usage of Enforcement
servers
3-6
Page 55

System Configuration
Enforcement Clusters
Enforcement Clusters
Adding an Enforcement Cluster
To add an Enforcement cluster:
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers
Figure 3-1. System Configuration Window, Enforcement Clusters & Servers Area
3-7
Page 56

System Configuration
Enforcement Clusters
1. Click Add an Enforcement cluster in the Enforcement clusters & servers area.
The Add Enforcement cluster window appears. The General area is
displayed by default.
Figure 3-2. Add Enforcement Cluster Window
a. Enter a name for the Enforcement cluster in the Cluster name field.
b. Select one of the following access modes:
– normal – Either allows or quarantines endpoints depending on the
setup of the enforcement sever
– allow all – Allows all endpoints
– quarantine all – Quarantines all endpoints
NOTE: If you are setting up a cluster for the first time, and you have not yet added
an ES, select allow all until you have finished configuring NAC 800.
c. Select a NAC policy group from the NAC policy group drop-down list
(see “NAC Policies” on page 6-1).
2. Click Quarantining in the Add Enforcement cluster window. Complete the
steps described in “Quarantining” on page 3-49.
3-8
Page 57

System Configuration
Enforcement Clusters
TIP: You can also access the quarantine area Enforcement cluster by clicking
Quarantining in the System configuration window (see “Quarantining” on
page 3-49 for more information).
3. The following cluster settings take on default values set from the System
configuration window. To set up operating parameters that differ from
those default settings, select the menu item of the settings you want to
change, then select the For this cluster, override the default settings check
box, and make the desired changes. Refer to the sections listed below to
set up the default values, or for more information on the specific settings.
• Testing methods – See “Testing Methods” on page 3-95
• Accessible services – See “Accessible Services” on page 3-98
• Exceptions – See “Exceptions” on page 3-100
• Notifications – See “Notifications” on page 3-102
• End-user screens – See “End-user Screens” on page 3-104
• Agentless credentials – See “Agentless Credentials” on page 3-107
• Logging – See “Logging” on page 3-111
• Advanced – See “Advanced Settings” on page 3-114
Editing Enforcement Clusters
To edit the Enforcement clusters settings:
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers
1. Click the cluster you want to edit. The Enforcement cluster window
appears, as shown in Figure 3-3 on page 3-11.
2. Click a menu option to access the cluster settings:
• General
• Quarantining
• Testing methods
• Accessible services
• Exceptions
• Notifications
• End-user screens
• Agentless credentials
• Logging
3-9
Page 58

System Configuration
Enforcement Clusters
• Advanced
3. Enter or change information in the fields you want to modify, as described
in “Adding an Enforcement Cluster” on page 3-7.
4. Click ok.
Viewing Enforcement Cluster Status
There are two ways NAC 800 provides Enforcement cluster status:
■ The icons next to the cluster name (see Figure 3-4 on page 3-13)
■ The Enforcement cluster window (see the following steps)
To view Enforcement cluster statistics:
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers
3-10
Page 59

System Configuration
Enforcement Clusters
Click a cluster name, for example Austin. The Enforcement cluster window
appears:
Figure 3-3. Enforcement Cluster Window, General Option
The statistics shown in this window are per cluster, where the statistics shown
in the Home window are system-wide.
Deleting Enforcement Clusters
NOTE: Enforcement clusters need to be empty before the delete option appears next
to the name in the NAC 800 console.
To delete Enforcement clusters:
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers
3-11
Page 60

System Configuration
Enforcement Clusters
1. Click delete next to the cluster you want to remove. The Delete Enforcem ent
cluster confirmation window appears.
2. Click yes. The System configuration window appears (figure 3-1).
3-12
Page 61

System Configuration
Enforcement Servers
Enforcement Servers
Adding an Enforcement Server
To add an Enforcement server:
NAC 800 home window>>System configuration>>Enforcement clusters &
servers
Figure 3-4. System Configuration Window, Enforcement Clusters & Servers Area
3-13
Page 62

System Configuration
Enforcement Servers
1. Click Add an Enforcement server in the Enforcement clusters & servers area.
The Add Enforcement server window appears.
Figure 3-5. Add Enforcement Server Window
2. Select a cluster from the Cluster drop-down list.
3. Enter the IP address for this Enforcement server in the IP address text box.
4. Enter the fully qualified hostname to set on this server in the Host name
text box.
5. Enter one or more DNS resolver IP addresses, separated by a commas,
semicolons, or spaces in the DNS IP addresses text box. For example,
10.0.16.100,10.0.1.1
6. Enter the password to set for the root user of the ES server’s operating
system in the Root password text box.
7. Re-enter the password to set for the root user of the ES server’s operating
system in the Re-enter root password text box.
8. Click ok.
3-14
Page 63

System Configuration
Enforcement Servers
Cluster and Server Icons
The following figure shows the legend explaining the Enforcement cluster and
server status icons:
Figure 3-6. Enforcement Cluster Legend
Editing Enforcement Servers
To edit Enforcement server settings:
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers
1. Click the Enforcement server you want to edit. The Enforcement server
window appears, as shown in Figure 3-7 on page 3-16.
3-15
Page 64

System Configuration
Enforcement Servers
2. Click the Configuration menu option to access the Enforcement server’s
settings. The Configuration area is displayed:
Figure 3-7. Enforcement Server Configuration Window
3. Edit the following setting(s):
• Enforcement server network settings – “Changing the Enforcement
Server Network Settings” on page 3-17
• Enforcement server date and time – “Changing the Enforcement
Server Date and Time” on page 3-17
• Enforcement server SNMP settings – “Modifying the ES root Account
Password” on page 3-18
• Enforcement server password – “Modifying the ES root Account
Password” on page 3-18
4. Click ok.
3-16
Page 65

System Configuration
Enforcement Servers
Changing the Enforcement Server Network Settings
CAUTION: Back up your system immediately after changing the MS or ES IP address. If
you do not back up with the new IP address, and later restore your system, it
will restore the previous IP address which can show an ES error condition
and cause authentication problems. See “Maintenance” on page 3-91 for
instructions on backing up and restoring your system.
To change the Enforcement server network settings:
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers>>Select an ES>>Configuration
Modify any of the following Network settings you want to change:
■ Enter a new Enforcement server in the Host name text field. For
example, garp.mycompany.com
■ Enter a new Enforcement server address in the IP address text field.
For example, 192.168.153.35
■ Enter a new netmask in the Network mask text field. For example,
255.255.255.0
■ Enter a new gateway in the Gateway IP address text field. For example
192.168.153.2
■ Enter one or more DNS resolver IP addresses, separated by commas,
semicolons, or spaces in the DNS IP addresses text box. For example:
10.0.16.100,10.0.1.1
NOTE: The NAC 800 Enforcement server’s host name must be a fully qualified domain
name (FQDN). For example, the FQDN should include the host and the
domain name—including the top-level domain.
For example, waldo.mycompany.com. Select names that are short, easy to
remember, have no spaces or underscores, and the first and last character
cannot be a dash (-).
NOTE: You cannot change the ES IP address for a single-server installation. You can
change the MS IP address for a single-server installation.
Changing the Enforcement Server Date and Time
To change the Enforcement server date and time:
3-17
Page 66

System Configuration
Enforcement Servers
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers>>Select an ES>>Configuration
1. Select a Region from the Region drop-down list in the Date and time area.
2. Select a time zone from the Time zone drop-down list.
3. Click ok.
NOTE: See “Selecting the Time Zone” on page 3-26 for information on changing the
time zone settings for the Management server.
WARNING: Manually changing the date/time by a large amount (other than a time zone
change) will require a restart of all servers. Rolling back the clock will have
adverse effects on the system.
Modifying the ES root Account Password
To change the Enforcement server root account password:
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers>>Select an ES>>Configuration
1. Enter the new password in the Root password text box in the Other settings
area.
2. Re-enter the password in the Re-enter root password text box.
3. Click ok.
Viewing Enforcement Server Status
There are two ways NAC 800 provides ES status:
■ The icons next to the server name (see Figure 3-6 on page 3-15)
■ The Status window (see the following steps). The Enforcement server
window allows you to view the following information:
•Health status
• Upgrade status
• Process/thread status
• System load average for the server
• Current endpoints being tested/minute for the server
3-18
Page 67

System Configuration
Enforcement Servers
• Percentage of memory used on the server
• Disk space usage for the server
To view Enforcement server status:
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers
1. Click the server for which you want to view the status. The Enforcement
server window appears:
Figure 3-8. Enforcement Server Window, Status Option
2. Click ok or cancel.
3-19
Page 68

System Configuration
Enforcement Servers
Deleting Enforcement Servers
NOTE: Servers need to be powered down for the delete option to appear next to the
name in the NAC 800 console.
To delete Enforcement servers:
NAC 800 Home window>>System configuration>>Enforcement clusters &
servers
1. Click delete next to the server you want to remove from the cluster. The
Delete Enforcement server confirmation window appears.
2. Click yes. The System configuration window appears.
Enforcement Server Recovery
If an existing ES goes down and comes back up, it can participate in its
assigned cluster, even if the MS is not available.
When a new ES is created, the MS must be available before the ES can
participate in a cluster.
3-20
Page 69

System Configuration
Management Server
Management Server
Viewing Network Settings
To view Management servers status:
NAC 800 Home window>>System configuration>>Management server
3-21
Page 70

System Configuration
Management Server
Figure 3-9. System Configuration, Management Server Window
1. Server status is shown in the Network settings area.
2. Click ok or cancel.
3-22
Page 71

System Configuration
Management Server
Modifying Management Server Network Settings
CAUTION: Back up your system immediately after changing the MS or ES IP address. If
you do not back up with the new IP address, and later restore your system, it
will restore the previous IP address which can show an ES error condition
and cause authentication problems. See “Maintenance” on page 3-91 for
instructions on backing up and restoring your system.
To modify Management server network settings:
NAC 800 Home window>>System configuration>>Management server
WARNING: Changing the Management server network settings will cause the network
interface to restart.
1. Click edit network settings in the Network settings area.
2. Enter the values you want to modify:
• Enter a new name in the Host name text field. For example,
garp.mycompany.com
NOTE: Select names that are short, easy to remember, have no spaces or under-
scores, and the first and last character cannot be a dash (-).
• Enter a new address in the IP address text field. For example,
192.168.153.35
• Enter a new netmask in the Network mask text field. For example,
255.255.255.0
• Enter a new gateway in the Gateway IP address text field. For example
192.168.153.2
• Enter one or more DNS resolver IP addresses, separated by commas,
semicolons, or spaces in the DNS IP addresses text box. For example:
10.0.16.100,10.0.1.1
3. Click ok.
Selecting a Proxy Server
Connecting to the Internet is necessary for updating tests, validating license
keys, and sending support packages.
3-23
Page 72

System Configuration
Management Server
To select a proxy server:
NAC 800 Home window>>System configuration>>Management server
1. Select Use a proxy server for Internet connections.
2. Enter the IP address of the server that will act as the proxy for Internet
connections in the Proxy server IP address text field.
3. Enter the port used for connecting to the proxy server in the Proxy server
port text field.
4. If your proxy server requires authentication, select the Proxy server is
authenticated check box.
a. Authentication method – Select the scheme used to authenticate
credentials on the proxy server. The following methods are
supported:
– Basic (not recommended) – The original and most compatible
authentication scheme for HTTP. Also the least secure because it
sends the user ID and password to the server unencrypted.
– Digest – Added in the HTTP 1.1 protocol, this scheme is signifi-
cantly more secure than basic authentication because it never
transfers the actual password across the network, but instead
uses it to encrypt a "nonce" value sent from the server.
– Negotiable – Using this scheme, the client and the proxy server
negotiate a scheme for authentication. Ultimately, either the basic
or digest scheme will be used.
b. Enter the ID of a user account on the proxy server in the User name
text box.
c. Enter the password of the user account specified in the User name text
box in the Password text box.
d. Re-enter the password.
3-24
5. Click ok.
Setting the Date and Time
The Date and time area allows you to configure the following:
■ Allow automatic synchronization with an NTP server
■ Manually set date and time for the Management server
■ Edit date and time:
• Set time zone
•Set date
Page 73

System Configuration
Management Server
• Set time
NOTE: Date and time settings are applied to the MS; however, you can set the time
zone for each ES.
Automatically Setting the Time
To automatically set the time:
NAC 800 Home window>>System configuration>>Management server
1. Select Automatically receive NTP updates from and enter one or more
Network Time Protocol (NTP) servers, separated by commas. The NTP
protocol allows NAC 800 to synchronize its date and time with other
endpoints on your network. For example, time.nist.gov.
2. Click ok.
TIP: Use of NTP is strongly recommended.
Manually Setting the Time
To manually set the time:
NAC 800 Home window>>System configuration>>Management server
1. Select Manually set date & time.
2. Click edit. The Date and time window appears:
Figure 3-10. Date & Time Window
3-25
Page 74

System Configuration
Management Server
3. Select the correct date and time.
4. Click ok.
5. Click ok.
CAUTION: Manually changing the date/time (other than a time zone change) a large
amount will require a restart of all servers. Rolling back the clock will have
adverse effects on the system.
Selecting the Time Zone
To set the time zone:
NAC 800 Home window>>System configuration>>Management server
1. Select the following:
a. Select a region from the Region drop-down list in the Date and time
area.
b. Select a time zone from the Time zone drop-down list.
2. Click ok.
Changing MS SNMP Settings
To change the Management server SNMP settings:
NAC 800 Home window>>System configuration>>Management server
1. Select the Enable SNMP check box to enable SNMP. Clear the check box
to disable SNMP. NAC 800 supports read-only SNMP v1 and v2.
2. Enter the Read community string. The default setting for network
equipment is often set to public. To prevent network information from
being divulged, change the community string to something unique.
3. Enter the SNMP Allowed source network. The value must be either
default or a network specified in CIDR notation.
4. Click ok.
Modifying the MS root Account Password
To change the Management server root account password:
3-26
Page 75

System Configuration
Management Server
NAC 800 Home window>>System configuration>>Management server
1. Enter the new password in the Root password text box in the Other settings
area.
2. Re-enter the password in the Re-enter root password text box.
3. Click ok.
Checking for NAC 800 Upgrades
To check for system upgrades:
NAC 800 Home window>>System configuration>>Management server
1. Click check for upgrades in the System upgrade area. A progress window
appears.
2. A status window appears indicating if upgrades are available.
a. If no upgrades are available, click ok to clear the status window.
b. Click ok to return to System configuration.
c. If an upgrade is available, click yes to upgrade your system.
CAUTION: Installation of an upgrade can take several hours to download all the software.
You can continue to use NAC 800 during the download process. NAC 800 will
automatically shutdown and restart after the software downloads.
TIP: Since upgrading can take longer than the default timeout setting of the NAC
800 Console, ProCurve recommends that you increase the timeout value
when you have limited bandwidth by performing the steps described in
“Changing the NAC 800 Console Timeout”.
Changing the NAC 800 Console Timeout
To change the timeout value for the console:
Command window
1. Log in to the NAC 800 server as root, either using SSH or directly with a
keyboard.
3-27
Page 76

System Configuration
Management Server
2. Enter the following at the command line:
setProperty.py -m
Compliance.UpgradeManager.UpgradeTimeout=<minutes>
Where:
<minutes> is the number of minutes of inactivity NAC 800 will wait before
requiring the user to log in to the console again. For example,30.
3-28
Page 77

System Configuration
User Accounts
User Accounts
NAC 800 allows you to create multiple user accounts. User accounts provide
and limit access to NAC 800 functions based on permissions (user roles) and
clusters assigned. See “User Roles” on page 3-37 for more information on
setting permissions for the user roles.
The User accounts menu option allows you to do the following:
■ View user accounts
■ Search by user ID, user name, or email address
■ Add a user account
■ Edit a user account
■ Delete a user account
Adding a User Account
To add a user account:
NAC 800 Home window>>System configuration>>User accounts
3-29
Page 78

System Configuration
User Accounts
Figure 3-11. System Configuration, User Accounts
3-30
Page 79

System Configuration
User Accounts
1. Click Add a user account. The Add user account window appears:
Figure 3-12. Add User Account
2. Enter the following information:
3. Select an Account status:
4. In the User roles area, select one of the following default roles for the user
• User ID – The user ID used to log into NAC 800
• Password – The password used to log into NAC 800
• Full name – The name associated with the user account
• Email address – The email address used for notifications
• enabled – This status allows an account to log into the console
• disabled – This status prevents an account from logging into the
console
account: (See “User Roles” on page 3-37 for more information about user
roles and permissions associated with user roles.)
3-31
Page 80

System Configuration
User Accounts
• Cluster Administrator
• View-Only User
• System Administrator
• Help Desk Technician
• You can select a custom user role if you have created any.
NOTE: Users must be assigned at least one role.
5. In the Clusters area, select a cluster or clusters.
NOTE: Users must be assigned at least one Enforcement cluster.
User Role Name Description
Cluster Administrator For their clusters, users having this role can configure their assigned
clusters, view endpoint activity, change endpoint access control, retest
endpoints, and generate reports.
View-Only User Users having this role can view endpoint activity and generate reports
about their clusters.
3-32
System Administrator Users having this role have all permissions.
Help Desk Technician For their clusters, users having this role can view endpoint activity,
change endpoint access control, retest endpoints, and run reports.
User-defined role Create your own user roles and definitions.
Table 3-2.Default User Roles
6. Click ok.
Searching for a User Account
To search for a user account:
NAC 800 Home window>>System configuration>>User accounts
1. Select one of the following from the Search drop-down list:
• user ID
• full name
• email address
Page 81

System Configuration
User Accounts
2. Enter the text to search for in the for field.
3. Click search.
TIP: Click reset to clear the text field and to refresh the display to show all accounts
after a search.
Sorting the User Account Area
To sort the user account area:
NAC 800 Home window>>System configuration>>User accounts
Click the column heading for user id, full name, email address, user roles, or
clusters. The user accounts reorder according to the column heading selected.
Click the column heading again to change from ascending to descending.
Copying a User Account
To copy a user account:
NAC 800 Home window>>System configuration>>User accounts
3-33
Page 82

System Configuration
User Accounts
1. Click copy next to the user account you want to duplicate. The Copy user
account window appears. The account information is duplicated from the
original account.
Figure 3-13. Copy User Account
2. Enter the User ID of the new account.
3. Enter the Password.
4. Re-enter the password.
5. Select the Account status (enable or disable).
6. Select the User role for the account.
7. Select the Cluster(s) that the user account can access.
8. Click ok.
Editing a User Account
To edit a user account:
3-34
Page 83

System Configuration
User Accounts
NAC 800 Home window>>System configuration>>User accounts
1. Click the name of the user account that you want to edit. The User account
window appears:
Figure 3-14. User Account
2. Change or enter information in the fields you want to change. See “Adding
a User Account” on page 3-29 for information on user account settings.
3. Click ok.
Deleting a User Account
You must always have at least one account with System Administrator permissions.
CAUTION: Do not delete or edit the account with which you are currently accessing the
interface. Doing so can produce an error and lock you out of the interface
until your session has timed out.
3-35
Page 84

System Configuration
User Accounts
To delete a user account:
NAC 800 Home window>>System configuration>>User accounts
1. Click delete next to the user account you want to remove. The Delete user
account confirmation window appears.
2. Click yes.
3-36
Page 85

System Configuration
User Roles
The User roles menu option allows you to configure the following:
■ View current user roles and details associated with those roles
■ Add a new user role
• Name the new user role
• Provide a detail description for the new user role
• Assign permissions to the new user role
■ Edit a user role
• Edit the name of the user role
• Edit the detail description of the user role
• Edit the assigned permissions for the user role
■ Delete a user role
Adding a User Role
To add a user role:
User Roles
NAC 800 Home window>>System configuration>>User roles
3-37
Page 86

System Configuration
User Roles
Figure 3-15. System Configuration Window, User Roles
3-38
Page 87

System Configuration
User Roles
1. Click add a user role in the User roles area. The Add user role window
appears.
Figure 3-16. Add User Role Window
2. Enter a descriptive name in the Role name field.
3. Enter a description of the role in the Description field.
4. Select the permissions for the user role. For more information about
permissions, the following table:
Permission Description
Configure clusters Allows you to add clusters, configure the settings of all your assigned clusters, and delete
any of your clusters.
Configure servers Allows you to configure all servers within your clusters
Configure the system Allows you to configure all system-level settings
View system alerts Allows you to view system alerts on your home screen
Generate reports Allows you to generate reports about any of your assigned clusters
Table 3-3.User Role Permissions
3-39
Page 88

System Configuration
User Roles
Permission Description
Manage NAC policies Allows you to manage the NAC policies for all of your clusters
View endpoint activity Allows you to view details about all endpoints in your clusters
Monitor system status Allows you to monitor the system status
Control Access Allows you to quarantine or grant network access to endpoints in your clusters
Retest endpoints Allows you to have endpoints in your clusters retested
Table 3-3.User Role Permissions (cont.)
Editing User Roles
NOTE: You cannot edit the System Administrator user role.
To edit user role s:
NAC 800 Home window>>System configuration>>User roles
3-40
Page 89

System Configuration
1. Click the role you want to edit. The user role window appears:
User Roles
Figure 3-17. User Role Window
2. Enter the information in the fields you want to change. See “Adding a User
Role” on page 3-37 for information on user role settings.
3. Click ok.
Deleting User Roles
NOTE: You cannot delete the System Administrator role.
To delete user roles:
NAC 800 Home window>>System configuration>>User roles
1. Click delete next to the user role you want to remove. The Delete user role
confirmation window appears.
2. Click yes.
3-41
Page 90

System Configuration
User Roles
Sorting the User Roles Area
To sort the user roles area:
NAC 800 Home window>>System configuration>>User roles
1. Click user role name or description column heading. The selected category
sorts in ascending or descending order.
2. Click ok.
3-42
Page 91

System Configuration
License
The License menu option allows you to configure the following:
■ View license start and end dates
■ View number of days remaining on license, and associated renewal
date
■ View remaining endpoints and servers available under license
Updating Your License
To update your license:
NAC 800 Home window>>System configuration>>License
License
3-43
Page 92

System Configuration
License
Figure 3-18. System Configuration Window, License
1. Click submit license request.
2. Click ok on the license validated pop-up window.
3-44
Page 93

System Configuration
Test Updates
Test Updates
The Test updates menu option allows you to configure the following:
■ View last successful test update date/time
■ Check for test updates (forces an immediate check for test updates)
■ Set time or times for downloading test updates
■ View test update logs
Manually Checking for Test Updates
To manually check for test updates:
NAC 800 Home window>>System configuration>>Test updates
3-45
Page 94

System Configuration
Test Updates
Figure 3-19. System Configuration Window, Test Updates
1. In the Last successful test update area, click check for test updates.
2. Click ok.
NOTE: It is important to check for test updates during the initial configuration of
NAC 800.
Selecting Test Update Times
To select test update times:
NAC 800 Home window>>System configuration>>Test updates
3-46
Page 95

System Configuration
1. Using the hour check boxes, select the time periods in which you would
like NAC 800 to check for available test updates.
By default, NAC 800 checks once every hour using the ProCurve Secure
Rule Distribution Center. All times listed are dependent upon the clock
setting and time zone of the hardware on which NAC 800 is running.
2. Click ok.
Test Updates
Viewing Test Update Logs
To view test update logs:
NAC 800 Home window>>System configuration>>Test updates
3-47
Page 96

System Configuration
Test Updates
1. Click the View test update log link just to the right of the Check for test
updates button. The Test update log window appears:
3-48
Figure 3-20. Test Update Log Window
The Test update log window legend is shown in the following figure:
Figure 3-21. Test Update Log Window Legend
Page 97

System Configuration
Quarantining
Quarantining
The Quarantining menu option allows you to configure the following by
cluster:
■ Select the quarantine method
■ Basic 802.1X settings
■ Set up authentication method
■ Add, edit, delete 802.1X devices
Selecting the Quarantine Method
To select the quarantine method:
NAC 800 Home window>>System configuration>>Quarantining
3-49
Page 98

System Configuration
Quarantining
Figure 3-22. System Configuration Window, Quarantining
1. Select a cluster.
2. In the Quarantine method area, select one of the following quarantine
methods:
• 802.1X – When using the 802.1X quarantine method, NAC 800 must sit
in a place on the network where it can communicate with your
RADIUS server, which communicates with your switch or router,
which performs the quarantining.
• DHCP – When configured with a DHCP quarantine area, NAC 800 must
sit inline with your DHCP server. All endpoints requesting a DHCP IP
address are issued a temporary address on a quarantine subnetwork.
Once the endpoint is allowed access, the IP address is renewed, and
the main DHCP server assigns an address to the main LAN. With a
multiple subnetwork or VLAN network, one quarantine area must be
configured for each sub-network.
3-50
Page 99

System Configuration
• Inline – When using the inline quarantine method, NAC 800 must be
placed on the network where all traffic to be quarantined passes
through NAC 800. It must be inline with an endpoint like a VPN.
3. Click ok.
Quarantining
Entering Basic 802.1X Settings
To enter basic 802.1X settings:
NAC 800 home window>>System configuration>>Quarantining>>802.1X
quarantine method radio button
1. Enter an IP address in the Identity Driven Manager (IDM) server IP address
text field.
2. Enter one or more non-quarantined subnets, separated by commas in the
Quarantine subnets text field. All subnets should be entered using CIDR
addresses.
3. Select a RADIUS server type by selecting one of the following radio buttons:
• Local – Enables a local RADIUS server on the Enforcement server
which can be configured to perform authentication itself or proxy to
another server.
• Remote IAS – Disables the local RADIUS server so that an IAS server
configured with the NAC IAS plug-in to point to an Enforcement
server can be used instead. When possible, a local RADIUS server that
proxies to the IAS server should be the preferred configuration.
4. Click ok.
Selecting the RADIUS Authentication method
To select the RADIUS authentication method:
NAC 800 home window>>System configuration>>Quarantining>>802.1X
quarantine method radio button
1. Select the Local radio button in the Basic 802.1X settings area.
2. Select an End-user authentication method:
• Manual – RADIUS server authentication settings are configured man-
ually from the command line. See “Enabling NAC 800 for 802.1X” on
page 11-43 for configuration information.
3-51
Page 100

System Configuration
Quarantining
• Windows domain – Authentication requests are handled by a Windows
domain through NTLM protocol. The Enforcement server must be
able to join to the domain for this to work. See “Configuring Windows
Domain Settings” on page 3-52 for more information.
• OpenLDAP – User credentials are queried from an OpenLDAP direc-
tory service. See “Configuring OpenLDAP Settings” on page 3-54 for
more information.
• Novell eDirectory – User credentials are queried from a Novell eDirec-
tory directory service. See “Configuring Novell eDirectory Settings”
on page 3-57 for more information.
• Proxy – Authentication requests are proxied to a remote RADIUS
server configured to allow the Enforcement server as a client NAS.
3. Click ok.
Configuring Windows Domain Settings
To configure Windows domain settings:
NAC 800 home window>>System configuration>>Quarantining>>802.1X
Quarantine method radio button>>Local radio button
3-52
 Loading...
Loading...