HP Presario 2100, Presario 2104, Presario 2103, Presario 2101, Presario 2102 User Manual
...
User Guide
HP Integrated Wireless LAN 54g™ Network Adapter
Document Part Number: 330895-001
February 2003
This guide explains how to use the HP Integrated Wireless LAN 54g™ Network Adapter that
comes with the Integrated 54g™ enabled notebook to access wireless local area networks at home
or at the office.


TABLE OF CONTENTS
Introduction..........................................................................................................................1
The Integrated 54g™ Solution .................................................................................................................... 1
Enterprise Users ..................................................................................................................................... 1
Home Users ............................................................................................................................................ 2
Using the Integrated 54g™ Enabled Notebook ......................................................................................... 2
Features and Requirements........................................................................................................................ 2
Completing the Setup..........................................................................................................3
Modes of Operation ..................................................................................................................................... 3
Infrastructure Mode ................................................................................................................................. 3
Characteristics ................................................................................................................................. 3
Advantages ...................................................................................................................................... 3
Disadvantages ................................................................................................................................. 3
Requirements .................................................................................................................................. 3
Ad Hoc Mode .......................................................................................................................................... 4
Characteristics ................................................................................................................................. 4
Advantages ...................................................................................................................................... 4
Disadvantages ................................................................................................................................. 4
Requirements .................................................................................................................................. 4
Configuring a Network Profile..................................................................................................................... 4
Configuring a Profile for a Listed Network That Does Not Require a WEP Key ..................................... 5
Configuring a Profile for a Listed Network That Requires a WEP Key.................................................... 7
Configuring a Profile for a Network That Is Not Listed and Does Not Require a WEP Key .................... 9
Configuring a Profile for a Network That Is Not Listed and Requires a WEP Key ................................ 11
Network Tasks....................................................................................................................14
View Status of This Connection................................................................................................................ 14
Change Settings of This Connection ....................................................................................................... 14
Changing the Values of the Network Adapter Properties ..................................................................... 14
Adding a New Network to the List of Preferred Networks ..................................................................... 16
Viewing or Modifying the Wireless Network Properties......................................................................... 16
Setting Up an Ad Hoc Group Network for Connecting to the Internet................................................... 18
Setting Up Internet Connection Sharing (ICS) on the Host Computer........................................... 18
User Guide Page i

Adding an Ad Hoc Network ............................................................................................................ 18
Adding an Ad Hoc Network That Does Not Require a WEP Key ...................................................18
Adding an Ad Hoc Network That Requires a WEP Key .................................................................21
Specifications.................................................................................................................... 24
Physical Characteristics ............................................................................................................................ 24
Temperature and Humidity Limitations....................................................................................................24
Power Characteristics ................................................................................................................................24
Networking Characteristics ....................................................................................................................... 24
Radio Characteristics.................................................................................................................................25
Regulatory Information..................................................................................................... 26
Operational Information ............................................................................................................................. 26
Wireless Interoperability ........................................................................................................................ 26
Safety ....................................................................................................................................................26
Regulatory Information .............................................................................................................................. 26
Canada—Industry Canada (IC) .............................................................................................................26
Europe—EU Declaration of Conformity................................................................................................. 27
France ...................................................................................................................................................27
Guidelines for Public WLAN Experimentation ................................................................................ 28
Metropolitan Departments .............................................................................................................. 29
USA—Federal Communications Commission (FCC) ............................................................................ 30
Interference Statement ...................................................................................................................31
Radio Approvals .................................................................................................................................... 31
Troubleshooting................................................................................................................ 32
Cannot Connect to the Network ................................................................................................................ 32
Performance and Connectivity Problems ................................................................................................32
Glossary............................................................................................................................. 34
Page ii User Guide

Introduction
THE INTEGRATED 54g™ SOLUTION
The Integrated 54g™ solution accesses wireless local area networks (WLANs), enables the sharing of a local
printer and files with others in the network, enables Internet connection sharing, and enables roaming about
the office—wire free. This wireless LAN solution is designed for both the home user and small businesses—
and it is scalable so that users can be added and new network features can be enabled as networking needs
grow.
The WEP (Wired Equivalent Privacy) protocol is a security protocol for wireless local area networks (defined
in IEEE Std 802.11, 1999 Edition) that encrypts data sent over radio waves. The use of the WEP key is optional
and can be enabled or disabled. If the network being connecting to has enabled WEP, WEP must also be
enabled in the network profile and the WEP key in the computer must be set to match the WEP key used by
the network. Otherwise, it is impossible to connect to the network.
The Integrated 54g™ enabled notebook makes a wireless connection to a network, as illustrated on the
following figure. Upon startup, the Integrated 54g™ enabled notebook detects certain WLANs (wireless
networks) that are within range. Before connecting to these and other wireless networks, a user must configure
a profile for each network. See "Completing the Setup" on page 3.
Networks 1 and 2 are infrastructure types of networks. The two notebook computers connected by radio waves
form an ad hoc type of network.
Network 1
Network 2
Figure 1: Types of Networks
ENTERPRISE USERS
Obtain the following information from the network administrator:
• Network names (SSID) of the specific wireless networks to connect to
• WEP (Wired Equivalent Privacy) key information (if any) for the networks to connect to
• For Microsoft Windows networking, the customer name and workgroup name
• For a network account, a user name and password
• An IP address (if not using a DHCP server)
• If any of the networks are connected to an authentication server
User Guide Page 1

Introduction
HOME USERS
The AP (access point) that communicates with the Integrated 54g™ enabled notebook has a preassigned
network name (SSID) that the notebook recognizes upon startup. To enable WEP, use any string of numbers
for the WEP key.
USING THE INTEGRATED 54g™ ENABLED NOTEBOOK
The Integrated 54g™ enabled notebook is an IEEE 802.11g based wireless LAN device. A LAN is composed
of two or more computers that are connected to each other to share files or common equipment such as a
printer or an Internet connection. A wireless LAN provides the same functionality of a wired network, but it
eliminates the need to install networking cables and other networking equipment. Not only is a wireless LAN
easier to deploy, but it also allows for roaming. For example, when using the Integrated 54g™ enabled
notebook, it is possible to roam from one room in the house to another, or from a conference room to an office
without being disconnected from the network.
FEATURES AND REQUIREMENTS
The Integrated 54g™ solution is an IEEE 802.11 based wireless LAN that includes the following features:
• Support for IEEE 802.11g draft specification
• Support for IEEE 802.11b standard
• 2.4-GHz band operation
• Network data rate of up to 54 Mbit/s
• Wired Equivalent Privacy (WEP) encryption
The following items are needed for participating in a wireless LAN:
• Integrated 54g™ enabled notebook computer running on a Microsoft Windows XP operating system
• Software drivers, software reference guide, and Help file
The Integrated 54g™ enabled notebook works with any IEEE 802.11b Wi-Fi CERTIFIED or IEEE 802.11g
access point or wireless client network adapter.
Page 2 User Guide

Completing the Setup
NOTE—Before starting, obtain the required network information from the network administrator or the wireless
access point installer (see “The Integrated 54g™ Solution” on page 1).
MODES OF OPERATION
A wireless LAN can be configured for two different modes of operation: infrastructure mode and ad hoc mode
(an ad hoc network is also known as a peer-to-peer network or a computer-to-computer network). Whereas
each mode has its advantages, one mode may be more appropriate than the other, depending on the location
and type of network connection.
INFRASTRUCTURE MODE
The key difference between the infrastructure type of network and an ad hoc network is that the infrastructure
network includes a base station (host) computer that has a built-in wireless network adapter and is connected
to a wireless access point (AP). This functionality allows computers on the infrastructure wireless LAN to
access the resources and tools of the wired LAN, including Internet access, e-mail, file sharing, and printer
sharing.
Characteristics
Networked computers communicate with each other through a dedicated AP. All data transmitted between the
computers on this wireless LAN passes through the AP.
Advantages
• Extended range. The access point extends the range of the wireless LAN. Each computer can
communicate with other computers equipped by wireless networks that are within the range of the access
point.
• Roaming. As the user moves around the home or office, the Integrated 54g™ enabled notebook
determines the best access point to use to ensure continuous communication with the network.
• Network connectivity. An access point can provide wireless LAN access to an existing wired network by
bridging the two networks together. This gives users of the wireless LAN access to all the functions of a
wired network—from file server access to access to e-mail and the Internet.
Disadvantages
Because the infrastructure mode offers more features, it requires additional components and setup time to
deploy.
Requirements
• A base station computer having a wired connection to the Internet
• A wireless network adapter
• A connection to an AP (access point)
User Guide Page 3

Completing the Setup
AD HOC MODE
An ad hoc network is the easiest to deploy and is ideal for home use or in small offices. This mode allows the
sharing of files with other employees, printing to a shared office printer, and access to the Internet through a
shared modem. With ad hoc networking, however, the computer is only able to communicate with other
wireless networks that are within a certain range and are in the same wireless workgroup.
Characteristics
Networked computers send data directly to each other without the need of an access point.
Advantages
• Simple setup
• Cost efficiency
Disadvantages
• Communication is limited to those who are located within a certain range.
• IEEE 802.1x security is not available.
Requirements
There are no other equipment requirements for operating in the ad hoc mode besides 2 WLAN enabled
notebooks or desktop PCs.
CONFIGURING A NETWORK PROFILE
To connect to a wireless network, a network profile for that network must be configured on the Integrated
54g™ enabled notebook. If the Integrated 54g™ enabled notebook computer came with the Integrated
54g™ network adapter already installed and set up at the factory, follow the network profile configuration
instructions provided below.
NOTE—For more information on how to configure a network profile and IEEE 802.1x authentication, click
Learn about setting up wireless network configuration on the Wireless Networks tab of Wireless
Network Connection Properties.
You can configure a network profile for networks that are listed under Available networks as well as those
that are not listed. When you have completed configuring a network profile, the network name and icon appear
at the top of the list under Preferred networks. The computer automatically connects to the network at the top
of the list. Follow the applicable instruction set below, based on whether or not the network is listed, whether
or not the network requires a WEP key, and whether or not the network is connected to an authentication
server (check with the network administrator to see if a WEP key is required and if the network is connected
to an authentication server).
NOTE—Both the network name and the network key are case-sensitive.
• “Configuring a Profile for a Listed Network That Does Not Require a WEP Key” on page 5
• “Configuring a Profile for a Listed Network That Requires a WEP Key” on page 7
• “Configuring a Profile for a Network That Is Not Listed and Does Not Require a WEP Key” on page 9
• “Configuring a Profile for a Network That Is Not Listed and Requires a WEP Key” on page 11
Page 4 User Guide
Completing the Setup
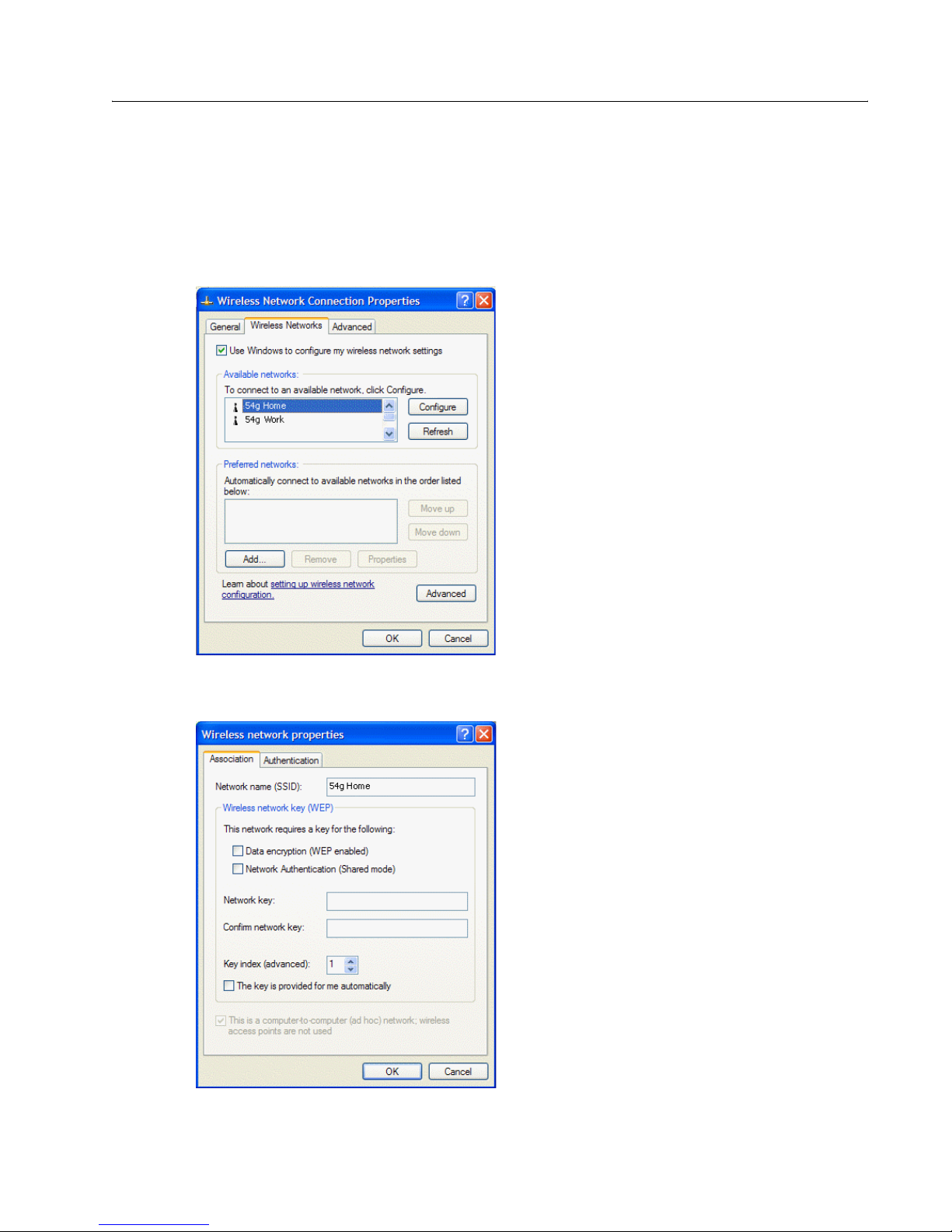
CONFIGURING A PROFILE FOR A LISTED NETWORK THAT DOES NOT REQUIRE A WEP
KEY
1 Click Start, then click Control Panel (Category View).
2 Click Network and Internet Connections.
3 Click Network Connections.
4 Right-click Wireless Network Connection, and then click Properties.
5 Click the Wireless Networks tab.
6 Under Available networks, click the network name, and then click Configure.
User Guide Page 5

Completing the Setup
7 The default settings in Microsoft Windows XP Service Pack 1 require IEEE 802.1x authentication. With IEEE
802.1x authentication enabled, connecting to a network requires a connection with an authentication server. If
the network has no authentication server, the connection is disabled every 3 minutes. Therefore, when
connecting to a network that has no authentication server, disable IEEE 802.1x authentication by doing the
following (if the network does have an authentication server, ignore this step):
• Click the Authentication tab.
• Clear the Enable network access control using IEEE 802.1x check box.
8 Click OK. The network name and icon appear at the top of the list under Preferred networks.
9 Click OK to activate the network connection. To verify that the network connection has been made, reopen
Wireless Network Connection Properties for that wireless network and click the Wireless Networks tab.
The computer is connected to the selected network when a blue bubble appears on top of the icon for that
network. If the bubble does not appear, click Refresh. If it still does not appear, try to access a Web page to
verify that an Internet connection exists.
Page 6 User Guide
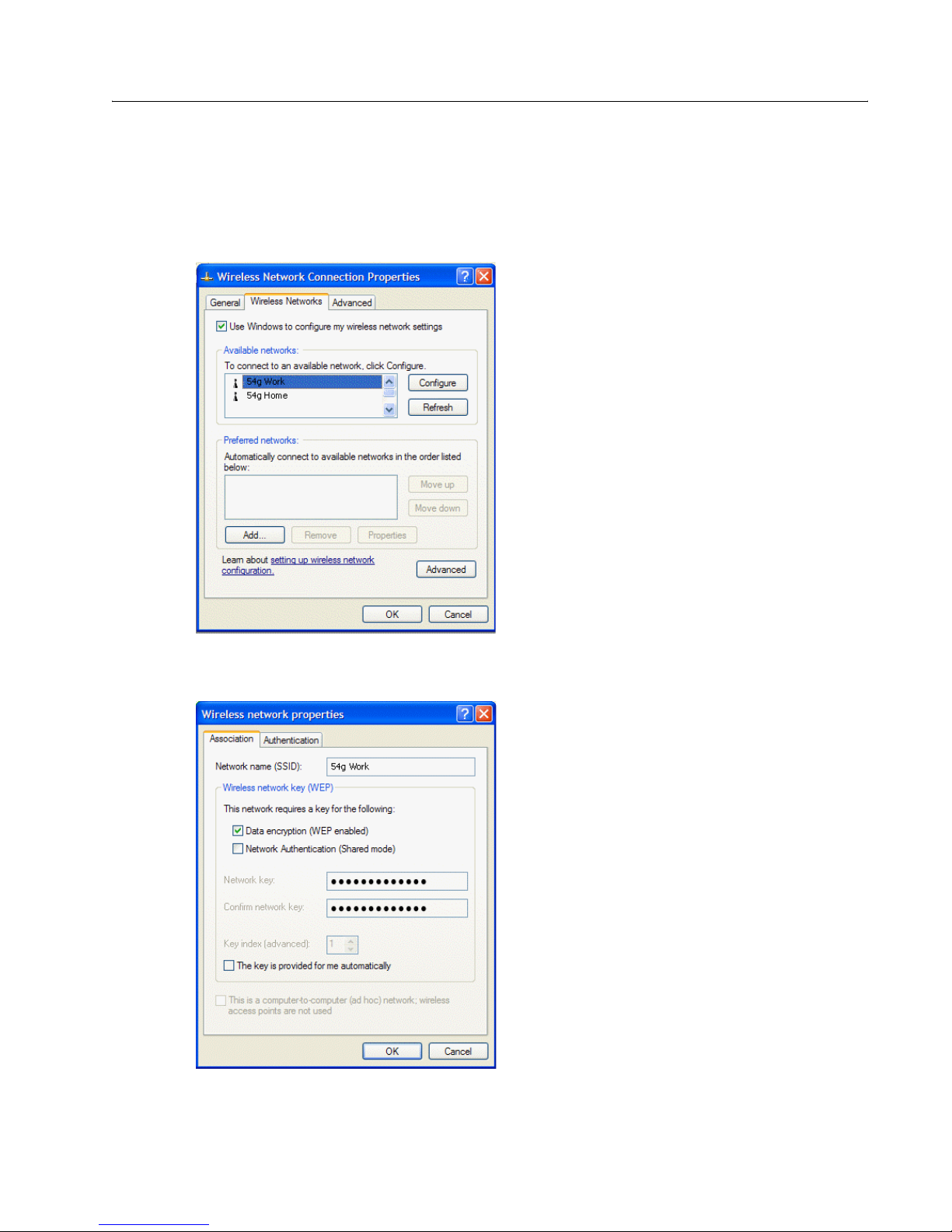
Completing the Setup
CONFIGURING A PROFILE FOR A LISTED NETWORK THAT REQUIRES A WEP KEY
1 Click Start, then click Control Panel (Category View).
2 Click Network and Internet Connections.
3 Click Network Connections.
4 Right-click Wireless Network Connection, and then click Properties.
5 Click the Wireless Networks tab.
6 Under Available networks, click the network name, and then click Configure.
User Guide Page 7
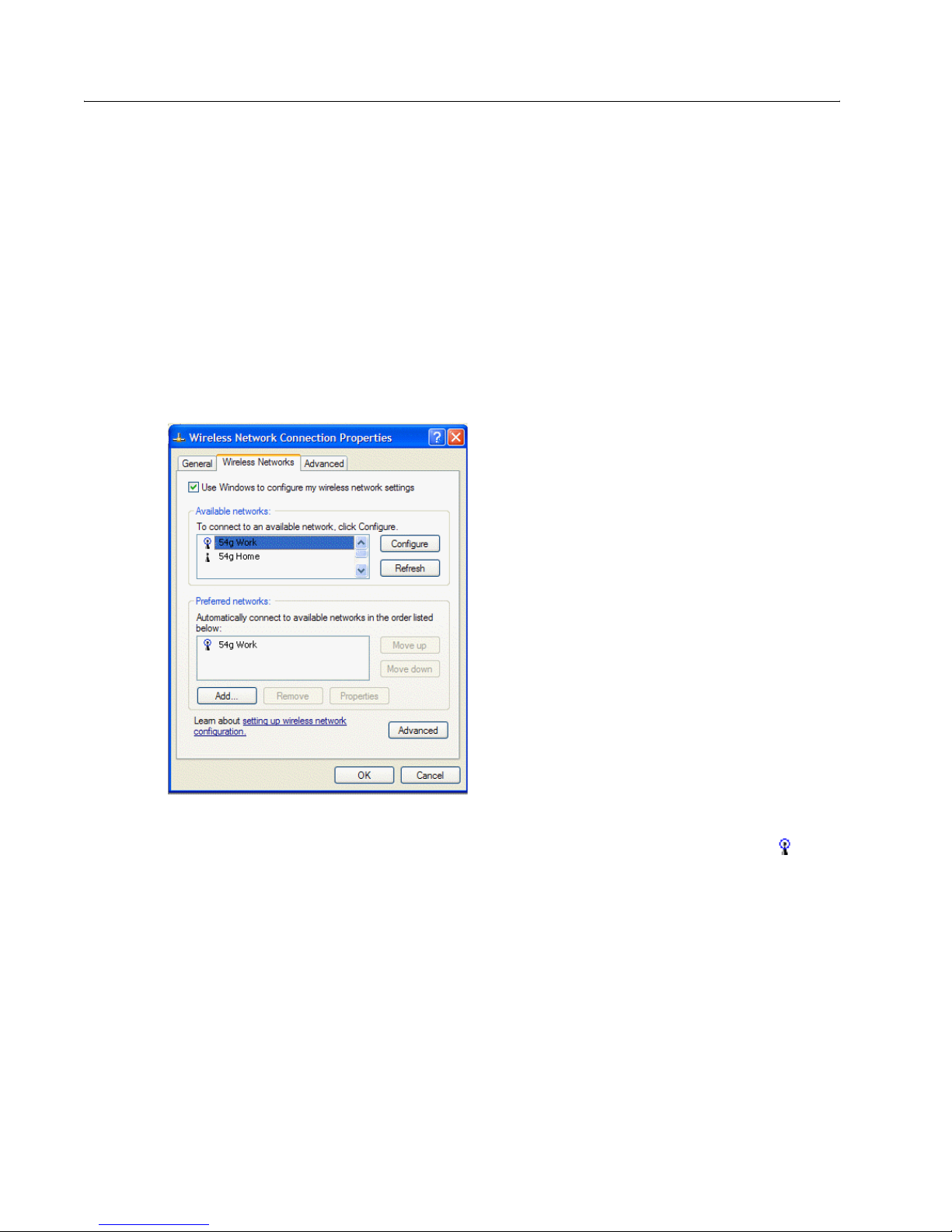
Completing the Setup
7 Select the Data encryption (WEP enabled) check box.
8 Clear the The key is provided for me automatically check box.
9 Type the network key in the Network key box and again in the Confirm network key box.
NOTE—It is not necessary to select the Key format or the Key length before typing the network key. These
settings automatically change to the appropriate setting as the network key is typed.
10 The default settings in Microsoft Windows XP Service Pack 1 require IEEE 802.1x authentication. With IEEE
802.1x authentication enabled, connecting to a network requires a connection with an authentication server. If
the network has no authentication server, the connection is disabled every 3 minutes. Therefore, when
connecting to a network that has no authentication server, disable IEEE 802.1x authentication by doing the
following (if the network does have an authentication server, ignore this step):
• Click the Authentication tab.
• Clear the Enable network access control using IEEE 802.1x check box.
11 Click OK. The network name and icon appear at the top of the list under Preferred networks.
12 Click OK to activate the network connection. To verify that the network connection has been made, reopen
Wireless Network Connection Properties for that wireless network and click the Wireless Networks tab.
The computer is connected to the selected network when a blue bubble appears on top of the icon for that
network. If the bubble does not appear, click Refresh. If it still does not appear, try to access a Web page to
verify that an Internet connection exists.
Page 8 User Guide
 Loading...
Loading...