Page 1

HP A6600 Routers
Layer 2 - LAN Switching
Configuration Guide
Abstract
This document describes the software features for the HP A Series products and guides you through the
software configuration procedures. These configuration guides also provide configuration examples to
help you apply software features to different network scenarios.
This documentation is intended for network planners, field technical support and servicing engineers, and
network administrators working with the HP A Series products.
Part number: 5998-1501
Software version: A6600-CMW520-R2603
Document version: 6PW101-20110630
Page 2

Legal and notice information
© Copyright 2011 Hewlett-Packard Development Company, L.P.
No part of this documentation may be reproduced or transmitted in any form or by any means without
prior written consent of Hewlett-Packard Development Company, L.P.
The information contained herein is subject to change without notice.
HEWLETT-PACKARD COMPANY MAKES NO WARRANTY OF ANY KIND WITH REGARD TO THIS
MATERIAL, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY
AND FITNESS FOR A PARTICULAR PURPOSE. Hewlett-Packard shall not be liable for errors contained
herein or for incidental or consequential damages in connection with the furnishing, performance, or use
of this material.
The only warranties for HP products and services are set forth in the express warranty statements
accompanying such products and services. Nothing herein should be construed as constituting an
additional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.
Page 3

Contents
MAC address table configuration ······························································································································ 1
How a MAC address table entry is created ·········································································································· 1
Types of MAC address table entries ······················································································································ 2
MAC address table-based frame forwarding ······································································································· 2
Configuring the MAC address table ······························································································································· 2
Configuring static, dynamic, and blackhole MAC address table entries ·························································· 2
Disabling MAC address learning ··························································································································· 3
Configuring the aging timer for dynamic MAC address entries ········································································· 4
Configuring the MAC learning limit on ports ········································································································ 5
Displaying and maintaining MAC address tables ········································································································ 5
MAC address table configuration example ··················································································································· 6
MAC information configuration ·································································································································· 8
How MAC information works ································································································································· 8
Configuring MAC information ········································································································································· 8
Enabling MAC information globally ······················································································································ 8
Enabling MAC information on an interface ·········································································································· 8
Configuring MAC information mode ····················································································································· 9
Configuring the interval for sending Syslog or trap messages ············································································ 9
Configuring the MAC information queue length ·································································································· 9
MAC information configuration example ······················································································································· 9
Ethernet link aggregation configuration ··················································································································· 11
Basic concepts ······················································································································································· 11
Aggregating links in static mode ························································································································· 14
Aggregating links in dynamic mode ··················································································································· 15
Load sharing criteria for link aggregation groups ····························································································· 17
Ethernet link aggregation configuration task list ········································································································· 17
Configuring an aggregation group ····························································································································· 17
Configuration guidelines ······································································································································ 17
Configuring a static aggregation group ············································································································· 18
Configuring a dynamic aggregation group ······································································································· 19
Configuring an aggregate interface ···························································································································· 21
Configuring the description of an aggregate interface or subinterface ·························································· 21
Configuring the MTU of a Layer 3 aggregate interface or subinterface ························································· 22
Specifying a card to process or forward traffic for a Layer 3 aggregate interface ······································· 22
Enabling link state traps for an aggregate interface ························································································· 23
Shutting down an aggregate interface ··············································································································· 23
Configuring load sharing for link aggregation groups ······························································································ 24
Configuring the global link-aggregation load sharing criteria ········································································· 24
Configuring group-specific load sharing criteria ······························································································· 25
Displaying and maintaining Ethernet link aggregation ····························································································· 25
Ethernet link aggregation configuration examples ····································································································· 26
Layer 2 static aggregation configuration example ···························································································· 26
Layer 2 dynamic aggregation configuration example ······················································································ 28
Layer 2 aggregation load sharing configuration example ··············································································· 30
Layer 3 static aggregation configuration example ···························································································· 33
Layer 3 dynamic aggregation configuration example ······················································································ 34
Layer 3 aggregation load sharing configuration example ··············································································· 36
iii
Page 4

Port isolation configuration ········································································································································ 39
Configuring an isolation group ···································································································································· 39
Assigning a port to the isolation group ·············································································································· 39
Displaying and maintaining isolation groups ············································································································· 39
Port isolation configuration example ··························································································································· 40
MSTP configuration ···················································································································································· 41
Why STP ································································································································································· 41
Protocol packets of STP ········································································································································· 41
Basic concepts in STP············································································································································ 41
How STP works ······················································································································································ 43
RSTP ················································································································································································· 48
MSTP ··············································································································································································· 49
Why MSTP ····························································································································································· 49
Basic concepts in MSTP ········································································································································ 50
How MSTP works ·················································································································································· 53
Implementation of MSTP on devices ···················································································································· 54
Protocols and standards ······································································································································· 54
MSTP configuration task list ·········································································································································· 54
Configuring MSTP ·························································································································································· 56
Configuring an MST region ································································································································· 56
Configuring the root bridge or a secondary root bridge ·················································································· 57
Configuring the work mode of an MSTP device ································································································ 58
Configuring the priority of a device ···················································································································· 58
Configuring the maximum hops of an MST region ··························································································· 59
Configuring the network diameter of a switched network ················································································ 59
Configuring timers of MSTP ································································································································· 60
Configuring the timeout factor ····························································································································· 61
Configuring the maximum port rate ···················································································································· 61
Configuring ports as edge ports ·························································································································· 62
Configuring path costs of ports ···························································································································· 62
Configuring port priority ······································································································································· 65
Configuring the link type of ports ························································································································ 65
Configuring the mode a port uses to recognize/send MSTP packets ····························································· 66
Enabling the output of port state transition information ···················································································· 67
Enabling the MSTP feature ··································································································································· 67
Performing mCheck ··············································································································································· 68
Configuring digest snooping ································································································································ 69
Configuring no agreement check ························································································································ 70
Configuring protection functions ·························································································································· 72
MSTP configuration example ········································································································································ 76
BPDU tunneling configuration ··································································································································· 81
BPDU tunneling implementation ··························································································································· 82
Configuring BPDU tunneling ········································································································································· 83
Configuration prerequisites ·································································································································· 83
Enabling BPDU tunneling ······································································································································ 83
Configuring destination multicast MAC address for BPDUs ············································································· 84
BPDU tunneling configuration examples······················································································································ 85
BPDU tunneling for STP configuration example ································································································· 85
BPDU tunneling for PVST configuration example ······························································································· 86
VLAN configuration ··················································································································································· 88
VLAN fundamentals ·············································································································································· 88
VLAN types ···························································································································································· 89
Configuring basic VLAN settings ································································································································· 90
iv
Page 5

Configuring basic settings of a VLAN interface ········································································································· 90
Port-based VLAN configuration ···································································································································· 91
Assigning an access port to a VLAN ·················································································································· 93
Assigning a trunk port to a VLAN ······················································································································· 94
Assigning a hybrid port to a VLAN ····················································································································· 95
Port-based VLAN configuration example ············································································································ 96
MAC-based VLAN configuration ·································································································································· 98
Configuring a MAC-based VLAN ························································································································ 99
MAC-based VLAN configuration example ······································································································· 100
Protocol-based VLAN configuration ··························································································································· 102
Introduction to protocol-based VLAN ················································································································ 102
Configuring a protocol-based VLAN ················································································································· 103
Protocol-based VLAN configuration example ·································································································· 104
IP subnet-based VLAN configuration ·························································································································· 107
Configuring an IP subnet-based VLAN ············································································································· 107
Displaying and maintaining VLAN ···························································································································· 108
Super VLAN configuration ····································································································································· 109
Configuring a super VLAN ········································································································································· 109
Displaying and maintaining super VLAN ·················································································································· 111
Super VLAN configuration example ·························································································································· 111
Isolate-user-VLAN configuration ····························································································································· 114
Configuring an isolate-user-VLAN ······························································································································ 114
Displaying and maintaining isolate-user-VLAN ········································································································· 115
Isolate-user-VLAN configuration example ·················································································································· 116
Voice VLAN configuration ······································································································································ 119
OUI addresses ····················································································································································· 119
Voice VLAN assignment modes ························································································································· 120
Security mode and normal mode of voice VLANs ··························································································· 122
Configuring a voice VLAN ·········································································································································· 123
Configuration prerequisites ································································································································ 123
Configuring QoS priority settings for voice traffic on an interface ································································ 123
Configuring a port to operate in automatic voice VLAN assignment mode ················································· 124
Configuring a port to operate in manual voice VLAN assignment mode ····················································· 125
Displaying and maintaining voice VLAN ·················································································································· 126
Voice VLAN configuration examples ························································································································· 126
Automatic voice VLAN mode configuration example ····················································································· 126
Manual voice VLAN assignment mode configuration example ····································································· 128
GVRP configuration ················································································································································· 131
GARP ···································································································································································· 131
GVRP ···································································································································································· 134
Protocols and standards ····································································································································· 134
GVRP configuration task list ········································································································································ 135
Configuring GVRP functions ······································································································································· 135
Configuring the garp timers ········································································································································ 136
Displaying and maintaining GVRP····························································································································· 137
GVRP configuration examples ···································································································································· 138
GVRP normal registration mode configuration example ················································································· 138
GVRP fixed registration mode configuration example ···················································································· 139
GVRP forbidden registration mode configuration example ············································································ 140
QinQ configuration ················································································································································ 143
Background and benefits ···································································································································· 143
How QinQ works ················································································································································ 143
v
Page 6

QinQ frame structure ·········································································································································· 144
Implementations of QinQ ··································································································································· 145
Modifying the TPID in a VLAN tag ···················································································································· 145
Protocols and standards ····································································································································· 146
QinQ configuration task list ········································································································································ 146
Configuring basic QinQ ············································································································································· 147
Enabling basic QinQ ·········································································································································· 147
Configuring VLAN transparent transmission ···································································································· 147
Configuring selective QinQ ········································································································································ 148
Configuring an outer VLAN tagging policy ····································································································· 148
Configuring an inner-outer VLAN 802.1p priority mapping ·········································································· 149
Configuring inner VLAN ID substitution ············································································································ 150
Configuring the TPID value in VLAN tags ················································································································· 151
QinQ configuration examples ···································································································································· 152
Basic QinQ configuration example ··················································································································· 152
Selective QinQ configuration example ············································································································· 154
VLAN transparent transmission configuration example ·················································································· 157
VLAN termination configuration ···························································································································· 160
VLAN termination types ······································································································································ 160
Application scenarios ········································································································································· 160
VLAN termination configuration task list ··················································································································· 162
Configuring TPID for VLAN-tagged packets ·············································································································· 162
Introduction to TPID ············································································································································· 162
Configuring TPID on Layer 3 Ethernet/aggregate subinterfaces ··································································· 163
Enabling an ambiguous Dot1q/QinQ termination-enabled subinterface to transmit broadcasts and
multicasts ······································································································································································· 164
Configuring Dot1q termination ··································································································································· 165
Configuring unambiguous Dot1q termination ·································································································· 165
Unambiguous Dot1q termination configuration example ··············································································· 165
Configuring ambiguous Dot1q termination ······································································································ 167
Ambiguous Dot1q termination configuration examples ·················································································· 168
Configuration examples for Dot1q termination supporting PPPoE server ····················································· 169
Configuring QinQ termination ··································································································································· 170
Configuring unambiguous QinQ termination ·································································································· 170
Unambiguous QinQ termination configuration example ················································································ 170
Configuring ambiguous QinQ termination ······································································································ 172
Ambiguous QinQ termination configuration example ···················································································· 173
Configuration example for QinQ termination supporting PPPoE server ······················································· 174
Configuration example for QinQ termination supporting DHCP relay ························································· 174
VLAN mapping configuration ································································································································ 178
Application scenario of one-to-one VLAN mapping ························································································ 179
Application scenario of one-to-two and two-to-two VLAN mapping ······························································ 180
Concepts and terms ············································································································································ 181
VLAN mapping implementations ······················································································································· 182
Configuring VLAN mapping ······································································································································· 183
Configuring one-to-one VLAN mapping ··········································································································· 183
Configuring one-to-two VLAN mapping ············································································································ 186
Configuring two-to-two VLAN mapping ············································································································ 187
VLAN mapping configuration examples ··················································································································· 191
One-to-one VLAN mapping configuration example ························································································ 191
One-to-two and two-to-two VLAN mapping configuration example ······························································ 195
LLDP configuration ··················································································································································· 199
Basic concepts ····················································································································································· 199
vi
Page 7

How LLDP works ·················································································································································· 203
Protocols and standards ····································································································································· 204
LLDP configuration task list ·········································································································································· 204
Performing basic LLDP configuration ·························································································································· 204
Enabling LLDP ······················································································································································ 204
Setting the LLDP operating mode ······················································································································· 205
Setting the LLDP re-initialization delay ·············································································································· 205
Enabling LLDP polling ········································································································································· 206
Configuring the advertisable TLVs ····················································································································· 206
Configuring the management address and its encoding format ···································································· 207
Setting other LLDP parameters ···························································································································· 208
Setting an encapsulation format for LLDPDUs ·································································································· 208
Configuring CDP compatibility ··································································································································· 209
Configuration prerequisites ································································································································ 209
Configuration procedure ···································································································································· 209
Configuring LLDP trapping ·········································································································································· 210
Displaying and maintaining LLDP ······························································································································· 210
LLDP configuration examples ······································································································································ 211
Basic LLDP configuration example ····················································································································· 211
CDP-compatible LLDP configuration example ··································································································· 214
Support and other resources ·································································································································· 216
Contacting HP ······························································································································································ 216
Subscription service ············································································································································ 216
Related information ······················································································································································ 216
Documents ···························································································································································· 216
Websites ······························································································································································ 216
Conventions ·································································································································································· 217
Index ········································································································································································ 219
vii
Page 8

MAC address table configuration
The MAC address table configuration applies only to Layer 2 interfaces, including Layer 2 Ethernet
interfaces and Layer 2 aggregate interfaces.
This document covers only the configuration of unicast MAC address table entries, including static,
dynamic, and blackhole MAC address table entries. For more information about configuring static
multicast MAC address table entries, see IP Multicast Configuration Guide.
The SAP cards support the MAC address table configuration only when they work in Layer 2 mode.
An Ethernet router uses a MAC address table for forwarding frames through unicast instead of broadcast.
This table describes from which port a MAC address (or host) can be reached. When forwarding a frame,
the router first looks up the MAC address of the frame in the MAC address table for a match. If an entry is
found, the router forwards the frame out of the outgoing port in the entry. If no entry is found, the router
broadcasts the frame out of all but the incoming port.
How a MAC address table entry is created
The entries in the MAC address table come from two sources: automatically learned by the router and
manually added by the administrator.
MAC address learning
The router can populate its MAC address table automatically by learning the source MAC addresses of
incoming frames on each port.
When a frame arrives at a port, Port A for example, the router performs the following tasks:
1. Checks the source MAC address (for example, MAC-SOURCE) of the frame.
2. Looks up the MAC address in the MAC address table.
3. If an entry is found, updates the entry. If no entry is found, adds an entry for MAC-SOURCE and Port
A.
The router performs the learning process each time it receives a frame from an unknown source MAC
address, until the MAC address table is fully populated.
After learning the source MAC address of a frame, the router looks up the destination MAC address in
the MAC address table. If an entry is found for the MAC address, the router forwards the frame out of the
specific outgoing port. In this example, it is Port A.
Manually configuring MAC address entries
With dynamic MAC address learning, a router does not distinguish between illegitimate and legitimate
frames. This can invite security hazards. For example, when a hacker sends frames with a forged source
MAC address to a port different from the one to which the real MAC address is connected, the router
creates an entry for the forged MAC address, and forwards frames destined for the legal user to the
hacker instead.
To enhance the security of a port, manually add MAC address entries to the MAC address table of the
router to bind specific user devices to the port. Because manually configured entries have higher priority
than dynamically learned ones, you can prevent hackers from stealing data using forged MAC
addresses.
1
Page 9

Types of MAC address table entries
A MAC address table can contain the following types of entries:
• Static entries, which are manually added and never age out.
• Dynamic entries, which can be manually added or dynamically learned and may age out.
• Blackhole entries, which are manually configured and never age out. Blackhole entries are
configured for filtering out frames with specific MAC addresses. For example, to block all packets
destined for a specific user for security concerns, configure the MAC address of this user as a
blackhole MAC address entry.
To adapt to network changes and prevent inactive entries from occupying table space, an aging
mechanism is adopted for dynamic MAC address entries. Each time a dynamic MAC address entry is
learned or created, an aging time starts. If the entry has not updated when the aging timer expires, the
router deletes the entry. If the entry has updated before the aging timer expires, the aging timer restarts.
A static or blackhole MAC address entry can overwrite a dynamic MAC address entry, but not vice
versa.
MAC address table-based frame forwarding
When forwarding a frame, the router adopts the following forwarding modes based on the MAC address
table:
• Unicast mode: If an entry is available for the destination MAC address, the router forwards the
frame out the outgoing interface indicated by the MAC address table entry.
• Broadcast mode: If the router receives a frame with the destination address being all ones, or no
entry is available for the destination MAC address, the router broadcasts the frame to all interfaces
except the receiving interface.
Configuring the MAC address table
These configuration tasks are all optional and can be performed in any order.
Configuring static, dynamic, and blackhole MAC address table entries
To fence off MAC address spoofing attacks and improve port security, manually add MAC address table
entries to bind ports with MAC addresses.
Also, configure blackhole MAC address entries to filter out packets with certain MAC addresses.
2
Page 10

Add or modify a static, dynamic, or blackhole MAC address table entry globally
To add or modify a static, dynamic, or blackhole MAC address table entry in system view:
To do… Use the command… Remarks
1. Enter system view
2. Add or modify a
dynamic or static MAC
address entry
3. Add or modify a
blackhole MAC address
entry
system-view —
mac-address { dynamic | static } mac-address
interface interface-type interface-number vlan
vlan-id
mac-address blackhole mac-address vlan
vlan-id
Add or modify a static or dynamic MAC address table entry on an interface
To add or modify a static or dynamic MAC address table entry in interface view:
To do… Use the command… Remarks
1. Enter system view
2. Enter interface view
3. Add or modify a static or
dynamic MAC address entry
system-view —
interface interface-type
interface-number
mac-address { dynamic | static }
mac-address vlan vlan-id
—
Required.
Ensure that you have created the
VLAN and assign the interface to
the VLAN.
Required.
Use either command.
Ensure that you have
created the VLAN and
assign the interface to the
VLAN.
Disabling MAC address learning
You may need to disable MAC address learning sometimes to prevent the MAC address table from being
saturated. For example, you may need to do it when your router is being attacked by a large amount of
packets with different source MAC addresses.
Disabling global MAC address learning
Disabling global MAC address learning disables the learning function on all ports.
To disable MAC address learning:
To do… Use the command… Remarks
1. Enter system view
2. Disable global MAC address
learning
Disabling MAC address learning on ports
After enabling global MAC address learning, you may disable the function on a single port, or on all
ports in a port group as needed.
system-view —
mac-address mac-learning disable
Required
Enabled by default
3
Page 11

To disable MAC address learning on an interface or a port group:
To do… Use the command… Remarks
1. Enter system view
system-view —
2. Enable global MAC address
learning
Enter Layer 2
3. Enter
interface
view or
port
group
view
4. Disable MAC address learning on
the interface or all ports in the port
group
Ethernet/aggregate
interface view
Enter port group view
For configuration about port groups, see the chapter “Ethernet interface configuration.”
Disabling MAC address learning on a VLAN
You may disable MAC address learning on a per-VLAN basis.
To disable MAC address learning on a VLAN:
To do… Use the command… Remarks
undo mac-address
mac-learning disable
interface interface-type
interface-number
port-group manual
port-group-name
mac-address mac-learning
disable
Optional.
Enabled by default.
Required.
Use either command.
Settings in Layer 2
Ethernet/aggregate interface view
take effect on the current interface
only.
Settings in port group view take
effect on all member ports in the
port group.
Required.
By default, MAC address learning
is enabled on ports.
1. Enter system view
2. Enable global MAC address
learning
3. Enter VLAN view
4. Disable MAC address
learning on the VLAN
system-view —
undo mac-address mac-learning
disable
vlan vlan-id —
mac-address mac-learning disable
Optional
Enabled by default
Required
Enabled by default
Configuring the aging timer for dynamic MAC address entries
The MAC address table uses an aging timer for dynamic MAC address entries for security and efficient
use of table space. If a dynamic MAC address entry has failed to update before the aging timer expires,
the router deletes the entry. This aging mechanism ensures that the MAC address table could timely
update to accommodate latest network changes.
Set the aging timer appropriately. A long aging interval may cause the MAC address table to retain
outdated entries, exhaust the MAC address table resources, and fail to update its entries to accommodate
the latest network changes. A short interval may result in the removal of valid entries and unnecessary
broadcasts, which may affect router performance.
4
Page 12

To configure the aging timer for dynamic MAC address entries:
To do… Use the command… Remarks
1. Enter system view
2. Configure the aging timer for
dynamic MAC address entries
system-view —
mac-address timer { aging
seconds | no-aging }
Optional
300 seconds by default
Reduce broadcasts on a stable network by disabling the aging timer to prevent dynamic entries from
aging out unnecessarily. By reducing broadcasts, you improve not only network performance, but also
security, because the chances for a data packet to reach unintended destinations are reduced.
Configuring the MAC learning limit on ports
As the MAC address table is growing, the forwarding performance of your router may degrade. To
prevent the MAC address table from getting so large that the forwarding performance is affected, limit
the number of MAC addresses that can be learned on a port.
To configure the MAC learning limit on a Layer 2 Ethernet interface, Layer 2 VE interface, Layer 2
aggregate interface, or all ports in a port group:
To do… Use the command… Remarks
1. Enter system view
Enter Layer 2
2. Enter
interface
view or
port
group
view
3. Configure the MAC learning limit
on the interface or port group, and
configure whether frames with
unknown source MAC addresses
can be forwarded or not when the
MAC learning limit is reached
Ethernet/aggregate
interface view
Enter port group view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
mac-address max-mac-count
count
Required.
Use either command.
Settings in Layer 2
Ethernet/aggregate interface
view take effect on the current
interface only.
Settings in port group view take
effect on all member ports in the
port group.
Required.
By default, the MAC learning
limit is not configured on ports.
Displaying and maintaining MAC address tables
To do… Use the command… Remarks
display mac-address [ mac-address [ vlan vlan-id ] |
Display MAC address table
information
[ [ dynamic | static ] [ interface interface-type
interface-number ] | blackhole ] [ vlan vlan-id ]
[ count ] ] [ | { begin | exclude | include }
regular-expression ]
5
Available in any view
Page 13

To do… Use the command… Remarks
Display the aging timer for
dynamic MAC address
entries
Display the system or
interface MAC address
learning state
Display MAC address
statistics
display mac-address aging-time [ | { begin |
exclude | include } regular-expression ]
display mac-address mac-learning [ interface-type
interface-number ] [ | { begin | exclude | include }
regular-expression ]
display mac-address statistics [ | { begin | exclude
| include } regular-expression ]
Available in any view
Available in any view
Available in any view
MAC address table configuration example
Network requirements
As shown in Figure 1:
• The MAC address of Host A is 000f-e235-dc71 and belongs to VLAN 1. It is connected to
GigabitEthernet 4/0/1 of the router. To prevent MAC address spoofing, add a static entry into the
MAC address table of the router for the host.
• The MAC address of Host B is 000f-e235-abcd and belongs to VLAN 1. Because this host once
behaved suspiciously on the network, you can add a blackhole MAC address entry for the MAC
address to drop all packets destined for the host.
• Set the aging timer for dynamic MAC address entries to 500 seconds.
Figure 1 Network diagram for MAC address table configuration
Configuration procedure
# Add a static MAC address entry.
<Router> system-view
[Router] mac-address static 000f-e235-dc71 interface gigabitethernet 4/0/1 vlan 1
# Add a blackhole MAC address entry.
[Router] mac-address blackhole 000f-e235-abcd vlan 1
# Set the aging timer for dynamic MAC address entries to 500 seconds.
[Router] mac-address timer aging 500
6
Page 14

# Display the MAC address entry for port GigabitEthernet 4/0/1.
[Router] display mac-address interface gigabitethernet 4/0/1
MAC ADDR VLAN ID STATE PORT INDEX AGING TIME(s)
000f-e235-dc71 1 Config static GigabitEthernet 4/0/1 NOAGED
--- 1 mac address(es) found ---
# Display information about the blackhole MAC address table.
[Router] display mac-address blackhole
MAC ADDR VLAN ID STATE PORT INDEX AGING TIME
000f-e235-abcd 1 Blackhole N/A NOAGED
--- 1 mac address(es) found ---
# View the aging time of dynamic MAC address entries.
[Router] display mac-address aging-time
Mac address aging time: 500s
7
Page 15

MAC information configuration
The SAP cards support this feature only when they work in Layer 2 mode.
To monitor a network, you need to monitor users joining and leaving the network. Because a MAC
address uniquely identifies a network user, monitor those users joining and leaving a network by
monitoring their MAC addresses.
With the MAC information function, Layer 2 Ethernet interfaces send Syslog or trap messages to the
monitor end in the network when they learn or delete MAC addresses. By analyzing these messages, the
monitor end can monitor users accessing the network.
How MAC information works
When a new MAC address is learned or an existing MAC address is deleted on a router, the router
writes related information about the MAC address to the buffer area used to store user information.
When the timer set for sending MAC address monitoring Syslog or trap messages expires, or when the
buffer is used up, the router sends the Syslog or trap messages to the monitor end immediately.
Configuring MAC information
Enabling MAC information globally
To enable MAC information globally:
To do… Use the command… Remarks
1. Enter system view
2. Enable MAC information
globally
Enabling MAC information on an interface
To enable MAC information on an interface:
To do… Use the command… Remarks
1. Enter system view
2. Enter Layer 2 Ethernet
interface view
3. Enable MAC information on
the interface
system-view —
mac-address information enable
system-view —
interface interface-type
interface-number
mac-address information enable
{ added | deleted }
Required
Disabled by default
—
Required
Disabled by default
To enable MAC information on an Ethernet interface, enable MAC information globally first.
8
Page 16

Configuring MAC information mode
To configure MAC information mode:
To do… Use the command… Remarks
1. Enter system view
system-view —
2. Configure MAC information
mode
mac-address information mode
{ syslog | trap }
Optional
trap by default
Configuring the interval for sending Syslog or trap messages
To prevent Syslog or trap messages from being sent too frequently, set the interval for sending Syslog or
trap messages.
To set the interval for sending Syslog or trap messages:
To do… Use the command… Remarks
1. Enter system view
2. Set the interval for sending
Syslog or trap messages
system-view
mac-address information interval
interval-time
—
Optional
One second by default
Configuring the MAC information queue length
To avoid losing user MAC address information, when the buffer storing user MAC address information is
used up, the user MAC address information in the buffer is sent to the monitor end in the network, even if
the timer set for sending MAC address monitoring Syslog or trap messages has not expired yet.
To configure the MAC information queue length:
To do… Use the command… Remarks
1. Enter system view
2. Configure the MAC
information queue length
system-view —
mac-address information
queue-length value
Optional
50 by default
MAC information configuration example
Network requirements
As shown in Figure 2:
• Host A is connected to a remote server (Server) through Router.
• Enable MAC information on GigabitEthernet 4/0/1 on Router. Router sends MAC address changes
in Syslog messages to Host B through GigabitEthernet 4/0/3. Host B analyzes and displays the
Syslog messages.
9
Page 17

Figure 2 Network diagram for MAC information configuration
Configuration procedure
1. Configure Router to send Syslog messages to Host B.
For more information, see Network Management and Monitoring Configuration Guide.
2. Enable MAC information.
# Enable MAC information on Router.
<Router> system-view
[Router] mac-address information enable
# Configure MAC information mode as Syslog.
[Router] mac-address information mode syslog
# Enable MAC information on GigabitEthernet 4/0/1.
[Router] interface gigabitethernet 4/0/1
[Router-GigabitEthernet4/0/1] mac-address information enable added
[Router-GigabitEthernet4/0/1] mac-address information enable deleted
[Router-GigabitEthernet4/0/1] quit
# Set the MAC information queue length to 100.
[Router] mac-address information queue-length 100
# Set the interval for sending Syslog or trap messages to 20 seconds.
[Router] mac-address information interval 20
10
Page 18

Ethernet link aggregation configuration
The SAP cards support the feature only when they work in Layer 2 mode.
The SAP cards can be installed on distributed routers only.
Ethernet link aggregation, or simply link aggregation, combines multiple physical Ethernet ports into one
logical link, called an aggregate link. Link aggregation delivers the following benefits:
• Increases bandwidth beyond the limits of any single link. In an aggregate link, traffic is distributed
across the member ports.
• Improves link reliability. The member ports back up one another dynamically. When a member port
fails, its traffic is switched to other member ports automatically.
As shown in Figure 3, Devic
physical Ethernet links are combined into an aggregate link, Link aggregation 1. The bandwidth of this
aggregate link is as high as the total bandwidth of these three physical Ethernet links. At the same time,
the three Ethernet links back up one another.
Figure 3 Diagram for Ethernet link aggregation
e A and Device B are connected by three physical Ethernet links. These
Basic concepts
Aggregation group, member port, aggregate interface
Link aggregation is implemented through link aggregation groups. An aggregation group is a group of
Ethernet interfaces combined together, which are called member ports of the aggregation group. For
each aggregation group, a logical interface, called an aggregate interface, is created. To an upper layer
entity that uses the link aggregation service, a link aggregation group looks like a single logical link and
data traffic is transmitted through the aggregate interface.
Aggregate interfaces have the following types: BAGG interfaces, also called Layer 2 aggregate
interfaces, and RAGG interfaces, also called Layer 3 aggregate interfaces. When you create an
aggregate interface, the switch automatically creates an aggregation group of the same type and number
as the aggregate interface. For example, when you create interface Bridge-aggregation 1, Layer 2
aggregation group 1 is created.
Assign Layer 2 Ethernet interfaces only to a Layer 2 aggregation group, and Layer 3 Ethernet interfaces
only to a Layer 3 aggregation group.
On a Layer 3 aggregate interface, you can create subinterfaces. These subinterfaces are logical
interfaces that operate at the network layer. They can receive VLAN tagged packets for their Layer 3
aggregate interface.
The rate of an aggregate interface equals the total rate of its member ports in the selected state, and its
duplex mode is the same as the selected member ports. For more information about the states of member
ports in an aggregation group, see “Aggregation states of member ports in an aggregation group.”
11
Page 19

Aggregation states of member ports in an aggregation group
A member port in an aggregation group can be in either of the following aggregation states:
• Selected: A selected port can forward user traffic.
• Unselected: An unselected port cannot forward user traffic.
Operational key
When aggregating ports, the system automatically assigns each port an operational key based on port
information such as port rate and duplex mode. Any change to this information triggers a recalculation of
the operational key.
In an aggregation group, all selected member ports are assigned the same operational key.
Configuration classes
Every configuration setting on a port may affect its aggregation state. Port configurations fall into the
following classes:
• Port attribute configurations, including port rate, duplex mode, and link status (up/down), which are
the most basic port configurations.
• Class-two configurations, as described in Table 1. A member port c
an be placed in the selected
state only if it has the same class-two configurations as the aggregate interface.
Table 1 Class-two configurations
Feature Considerations
Port isolation
QinQ
VLAN
MAC address learning
Whether the port has joined an isolation group, and the isolation group to
which the port belongs
QinQ enable state (enable/disable), TPID for VLAN tags, outer VLAN tags to be
added, inner-to-outer VLAN priority mappings, inner-to-outer VLAN tag
mappings, inner VLAN ID substitution mappings
Permitted VLAN IDs, PVID, link type (trunk, hybrid, or access), IP subnet-based
VLAN configuration, protocol-based VLAN configuration, VLAN tagging mode
MAC address learning capability, MAC address learning limit, forwarding of
frames with unknown destination MAC addresses after the MAC address
learning limit is reached
Class-two configurations made on an aggregate interface are automatically synchronized to all its
member ports. These configurations are retained on the member ports even after the aggregate interface
is removed.
Any class-two configuration change may affect the aggregation state of link aggregation member ports
and ongoing traffic. To make sure that you are aware of the risk, the system displays a warning message
every time you attempt to change a class-two configuration setting on a member port.
• Class-one configurations do not affect the aggregation state of the member port even if they are
different from those on the aggregate interface. GVRP and MSTP settings are examples of class-one
configurations.
The class-one configuration for a member port is effective only when the member port leaves the
aggregation group.
12
Page 20

yp
Reference port
When setting the aggregation state of the ports in an aggregation group, the system automatically picks
a member port as the reference port. A selected port must have the same port attributes and class-two
configurations as the reference port.
LACP
The IEEE 802.3ad LACP enables dynamic aggregation of physical links. It uses LACPDUs for exchanging
aggregation information between LACP-enabled devices.
1. LACP functions
Table 2 LACP functions
Category Description
Basic LACP functions
2. LACP priorities
Implemented through the basic LACPDU fields, including the system LACP priority,
system MAC address, port aggregation priority, port number, and operational
key.
Each member port in a LACP-enabled aggregation group exchanges information
with its peer. When a member port receives an LACPDU, it compares the received
information with the information received on the other member ports. In this way
the two systems reach an agreement on which ports should be placed in the
selected state.
LACP priorities have the following types: system LACP priority and port aggregation priority, as described
in Table 3.
Table 3 LACP priorities
T
e Description Remarks
Used by two peer devices (or systems) to determine which one is
System LACP
priority
Port aggregation
priority
3. LACP timeout interval
superior in link aggregation.
In dynamic link aggregation, the system that has higher system LACP
priority sets the selected state of member ports on its side first and
then the system that has lower priority sets port state accordingly.
Determines the likelihood of a member port to be selected on a
system. The higher port aggregation priority, the higher likelihood.
The smaller the
priority value,
the higher the
priority
The LACP timeout interval specifies how long a member port waits to receive LACPDUs from the peer port.
If a local member port fails to receive LACPDUs from the peer within three times the LACP timeout interval,
the member port assumes that the peer port has failed. Configure the LACP timeout interval as the short
timeout interval (1 second) or the long timeout interval (30 seconds).
13
Page 21

p
Link aggregation modes
Link aggregation has the following modes: dynamic and static. Dynamic link aggregation uses LACP and
static link aggregation does not. Table 4 c
Table 4 A comparison between static and dynamic aggregation modes
ompares the two aggregation modes.
Aggregatio
n mode
Static Disabled
Dynamic Enabled
LACP status on
member
orts
Pros Cons
Aggregation is stable. The
aggregation state of the member
ports are not affected by the peer
ports.
The administrator does not need to
maintain link aggregations. The
peer systems maintain the
aggregation state of the member
ports automatically.
In a dynamic link aggregation group:
• A selected port can receive and send LACPDUs.
• An unselected port can receive and send LACPDUs only if it is up and has the same class-two
configurations as the aggregate interface.
Aggregating links in static mode
LACP is disabled on the member ports in a static aggregation group. You must manually maintain the
aggregation state of the member ports.
The member ports do not adjust
the aggregation state according to
that of the peer ports. The
administrator must manually
maintain link aggregations.
Aggregation is unstable. The
aggregation state of member ports
is susceptible to network changes.
The static link aggregation procedure comprises:
• Selecting a reference port
• Setting the aggregation state of each member port
Selecting a reference port
The system selects a reference port from the member ports that are in the up state and have the same
class-two configurations as the aggregate interface.
The candidate ports are sorted by aggregation priority, duplex, and speed in this order: lowest
aggregation priority value, full duplex/high speed, full duplex/low speed, half duplex/high speed, and
half duplex/low speed. The one at the top is selected as the reference port. If two ports have the same
aggregation priority, duplex mode, and speed, the one with the lower port number wins out.
Setting the aggregation state of each member port
After selecting the reference port, the static aggregation group sets the aggregation state of each member
port, as shown in Figure 4.
14
Page 22

Figure 4 Set the aggregation state of a member port in a static aggregation group
To ensure stable aggregation state and service continuity, do not change port attributes or class-two
configurations on any member port.
If a static aggregation group has reached the limit on selected ports, any port joins the group is placed in
the unselected state to avoid traffic interruption on the current selected ports. Avoid this situation, however,
because it may cause the aggregation state of a port to change after a reboot.
Aggregating links in dynamic mode
LACP is automatically enabled on all member ports in a dynamic aggregation group. The protocol
automatically maintains the aggregation state of ports.
The dynamic link aggregation procedure comprises:
• Selecting a reference port
• Setting the aggregation state of each member port
Selecting a reference port
The local system (the actor) and the remote system (the partner) negotiate a reference port using the
following workflow:
1. Compare the system ID (comprising the system LACP priority and the system MAC address). The
system with the lower LACP priority value wins out. If they are the same, compare the system MAC
addresses. The system with the lower MAC address wins.
2. The system with the smaller system ID selects the port with the smallest port ID as the reference port.
A port ID comprises a port aggregation priority and a port number. The port with the lower
15
Page 23

aggregation priority value wins out. If two ports have the same aggregation priority, the system
compares their port numbers. The port with the smaller port number wins.
Setting the aggregation state of each member port
After the reference port is selected, the system with the lower system ID sets the state of each member port
in the dynamic aggregation group on its side as shown in Figure 5.
Figure 5 Set the state o
f a member port in a dynamic aggregation group
Meanwhile, the system with the higher system ID, being aware of the aggregation state changes on the
remote system, sets the aggregation state of local member ports the same as their peer ports.
To ensure stable aggregation state and service continuity, do not change port attributes or class-two
configurations on any member port.
In a dynamic aggregation group, when the aggregation state of a local port changes, the aggregation
state of the peer port also changes.
A port that joins a dynamic aggregation group after the selected port limit has been reached is placed in
the selected state if it is more eligible for being selected than a current member port.
16
Page 24

Load sharing criteria for link aggregation groups
In a link aggregation group, traffic may be load-shared across the selected member ports based on a set
of criteria, depending on your configuration.
Choose one of the following criteria or any combination for load sharing:
• MAC addresses
• IP addresses
Alternatively, configure the system to perform per-packet link aggregation.
Ethernet link aggregation configuration task list
Complete the following tasks to configure Ethernet link aggregation:
Task Remarks
Configuring an aggregation group
Configuring an
aggregate
interface
Configuring load
sharing for link
aggregation
groups
Configuring a static aggregation group
Configuring a dynamic aggregation group
Configuring the description of an aggregate interface or
subinterface
Configuring the MTU of a Layer 3 aggregate interface or
subinterface
Specifying a card to process or forward traffic for a Layer
3 aggregate interface
Enabling link state traps for an aggregate interface Optional
Shutting down an aggregate interface Optional
Configuring the global link-aggregation load sharing
criteria
Configuring group-specific load sharing criteria Optional
Configuring an aggregation group
Choose to create a Layer 2 or Layer 3 link aggregation group depending on the ports to be aggregated:
Select either task
Optional
Optional
Optional
Optional
• To aggregate Layer 2 Ethernet interfaces, create a Layer 2 link aggregation group.
• To aggregate Layer 3 Ethernet interfaces, create a Layer 3 link aggregation group.
Configuration guidelines
Removing an aggregate interface also removes the corresponding aggregation group. At the same time,
all member ports leave the aggregation group.
You cannot assign a port to a Layer 2 aggregation group if any of the features listed in Table 5 is
conf
igured on the port.
17
Page 25

Table 5 Features incompatible with Layer 2 aggregation groups
Feature Reference
RRPP RRPP in the High Availability Configuration Guide
MAC authentication
Port security Port security in the Security Configuration Guide
Packet filtering Firewall in the Security Configuration Guide
Ethernet frame filtering Firewall in the Security Configuration Guide
IP source guard IP source guard in the Security Configuration Guide
802.1X 802.1X in the Security Configuration Guide
Ports specified as source
interfaces in portal-free rules
MAC authentication in the Security Configuration Guide
Portal in the Security Configuration Guide
You cannot assign a port to a Layer 3 aggregation group if any of the features listed in Table 6 is
configured on the port.
Table 6 Interfaces that cannot be assigned to a Layer 3 aggregation group
Interface type Reference
Interfaces configured with IP addresses IP addressing in the Layer 3—IP Services Configuration Guide
Interfaces configured as DHCP/BOOTP
clients
DHCP in the Layer 3—IP Services Configuration Guide
VRRP VRRP in the High Availability Configuration Guide
Portal Portal in the Security Configuration Guide
If a port is used as a reflector port for port mirroring, do not assign it to an aggregation group. For more
information about reflector ports, see Network Management and Monitoring Configuration Guide.
Configuring a static aggregation group
To guarantee a successful static aggregation, make sure that the ports at both ends of each link are in the
same aggregation state.
Configuring a Layer 2 static aggregation group
To configure a Layer 2 static aggregation group:
To do... Use the command... Remarks
1. Enter system view
2. Create a Layer 2 aggregate
interface and enter Layer 2
aggregate interface view
system-view —
interface bridge-aggregation
interface-number
Required.
When you create a Layer 2
aggregate interface, the system
automatically creates a Layer 2
static aggregation group
numbered the same.
3. Exit to system view
quit —
18
Page 26

To do... Use the command... Remarks
4. Enter Layer 2 Ethernet
interface view
5. Assign the Ethernet interface
to the aggregation group
interface interface-type
interface-number
port link-aggregation group
number
Configuring a Layer 3 static aggregation group
To configure a Layer 3 static aggregation group:
To do... Use the command... Remarks
1. Enter system view
2. Create a Layer 3 aggregate
interface and enter Layer 3
aggregate interface view
3. Exit to system view
4. Enter Layer 3 Ethernet
interface view
5. Assign the Ethernet interface
to the aggregation group
system-view —
interface route-aggregation
interface-number
quit —
interface interface-type
interface-number
port link-aggregation group
number
Required.
Repeat these two steps to assign
more Layer 2 Ethernet interfaces to
the aggregation group.
Required.
When you create a Layer 3
aggregate interface, the system
automatically creates a Layer 3
static aggregation group
numbered the same.
Required.
Repeat these two steps to assign
more Layer 3 Ethernet interfaces to
the aggregation group.
Configuring a dynamic aggregation group
To guarantee a successful dynamic aggregation, make sure that the peer ports of the ports aggregated at
one end are also aggregated. The two ends can automatically negotiate the aggregation state of each
member port.
Configuring a Layer 2 dynamic aggregation group
To configure a Layer 2 dynamic aggregation group:
To do... Use the command... Remarks
1. Enter system view
2. Set the system LACP priority
system-view —
lacp system-priority system-priority
Optional.
By default, the system LACP
priority is 32,768.
Changing the system LACP priority
may affect the aggregation state
of the ports in a dynamic
aggregation group.
19
Page 27

To do... Use the command... Remarks
Required.
3. Create a Layer 2 aggregate
interface and enter Layer 2
aggregate interface view
interface bridge-aggregation
interface-number
When you create a Layer 2
aggregate interface, the system
automatically creates a Layer 2
static aggregation group
numbered the same.
4. Configure the aggregation
group to work in dynamic
aggregation mode
5. Exit to system view
6. Enter Layer 2 Ethernet
interface view
7. Assign the Ethernet interface
to the aggregation group
8. Assign the port an
aggregation priority
9. Set the LACP timeout interval
on the port to the short timeout
interval (1 second)
Required.
link-aggregation mode dynamic
quit —
interface interface-type
interface-number
port link-aggregation group
number
link-aggregation port-priority
port-priority
lacp period short
By default, an aggregation group
works in static aggregation mode.
Required.
Repeat these two steps to assign
more Layer 2 Ethernet interfaces to
the aggregation group.
Optional.
By default, the aggregation
priority of a port is 32,768.
Changing the aggregation priority
of a port may affect the
aggregation state of the ports in
the dynamic aggregation group.
Optional.
By default, the LACP timeout
interval on a port is the long
timeout interval (30 seconds).
Configuring a Layer 3 dynamic aggregation group
To configure a Layer 3 dynamic aggregation group:
To do... Use the command... Remarks
1. Enter system view
2. Set the system LACP
priority
3. Create a Layer 3
aggregate interface and
enter Layer 3 aggregate
interface view
system-view —
lacp system-priority
system-priority
interface route-aggregation
interface-number
20
Optional.
By default, the system LACP priority is
32,768.
Changing the system LACP priority may
affect the aggregation state of the ports
in the dynamic aggregation group.
Required.
When you create a Layer 3 aggregate
interface, the system automatically
creates a Layer 3 static aggregation
group numbered the same.
Page 28

To do... Use the command... Remarks
4. Configure the
aggregation group to
work in dynamic
aggregation mode
link-aggregation mode dynamic
Required.
By default, an aggregation group works
in static aggregation mode.
5. Exit to system view
6. Enter Layer 3 Ethernet
interface view
7. Assign the Ethernet
interface to the
aggregation group
8. Assign the port an
aggregation priority
9. Set the LACP timeout
interval on the port to the
short timeout interval (1
second)
quit —
interface interface-type
interface-number
port link-aggregation group
number
link-aggregation port-priority
port-priority
lacp period short
Required.
Repeat these two steps to assign more
Layer 3 Ethernet interfaces to the
aggregation group.
Optional.
By default, the aggregation priority of a
port is 32,768.
Changing the aggregation priority of a
port may affect the aggregation state of
ports in the dynamic aggregation group.
Optional.
By default, the LACP timeout interval on a
port is the long timeout interval (30
seconds).
Configuring an aggregate interface
Perform the following configurations on an aggregate interface:
• Configuring the description of an aggreg
• Configuring the MTU of a Layer 3 aggregate interface or su
• Specifying a card to process or forward traffic
ate interface or subinterface
binterface
for a Layer 3 aggregate interface
• Enabling link state traps for an aggregate interface
• Shutting down an aggregate interface
In addition to the prec
eding configurations, most of the configurations that can be performed on Layer 2
or Layer 3 Ethernet interfaces can also be performed on Layer 2 or Layer 3 aggregate interfaces.
Configuring the description of an aggregate interface or subinterface
Configure the description of an aggregate interface for administration purposes such as describing the
purpose of the interface.
To configure the description of an aggregate interface or subinterface:
To do... Use the command... Remarks
1. Enter system view
system-view —
21
Page 29

To do... Use the command... Remarks
Enter Layer 2
aggregate
2. Enter
aggregate
interface
view
3. Configure the description
of the aggregate interface
or subinterface
interface view
Enter Layer 3
aggregate
interface or
subinterface
view
interface bridge-aggregation
interface-number
interface route-aggregation
{ interface-number |
interface-number.subnumber }
description text
Use either command.
Optional.
By default, the description of an
interface is in the format of
interface-name Interface, such as
Bridge-Aggregation1 Interface.
Configuring the MTU of a Layer 3 aggregate interface or subinterface
The MTU of an interface affects IP packets fragmentation and reassembly on the interface.
To change the MTU of a Layer 3 aggregate interface or subinterface:
To do... Use the command... Remarks
1. Enter system view
2. Enter Layer 3 aggregate
interface or subinterface view
3. Configure the MTU of the
Layer 3 aggregate interface
or subinterface
system-view —
interface route-aggregation
{ interface-number |
interface-number.subnumber }
mtu size
—
Optional
1500 bytes by default
Specifying a card to process or forward traffic for a Layer 3 aggregate interface
If you do not specify a card to process or forward traffic for a Layer 3 aggregate interface whose member
ports are located on different cards, the traffic may be processed or forwarded by different cards from
time to time due to changes in the selected ports.
If you unplug the card configured to process traffic for a Layer 3 aggregate interface, traffic on the Layer
3 aggregate interface is interrupted. After you plug the card back in, the traffic is restored.
On a distributed router, use this feature to specify a card to process or forward traffic for a Layer 3
aggregate interface.
22
Page 30

To specify a card to process or forward traffic for a Layer 3 aggregate interface:
To do... Use the command... Remarks
1. Enter system view
2. Enter Layer 3 aggregate
interface view
3. Specify a card to process or
forward traffic for the current
interface
system-view —
interface route-aggregation
interface-number
service slot slot-number
—
Required.
By default, traffic on a Layer 3
aggregate interface whose member
ports are located on the same card is
processed or forwarded by the card
that houses the member ports, and
traffic on a Layer 3 aggregate interface
whose member ports are located on
different cards is processed or
forwarded by the card that houses the
first selected member port.
Enabling link state traps for an aggregate interface
Configure an aggregate interface to generate linkUp trap messages when its link goes up and linkDown
trap messages when its link goes down. For more information, see Network Management and Monitoring
Configuration Guide.
To enable link state traps on an aggregate interface:
To do... Use the command... Remarks
1. Enter system view
2. Enable the trap function
globally
Enter Layer 2
aggregate
3. Enter
aggregate
interface
view
4. Enable link state traps for
the aggregate interface
interface view
Enter Layer 3
aggregate
interface or
subinterface
view
system-view
snmp-agent trap enable [ standard
[ linkdown | linkup ] * ]
interface bridge-aggregation
interface-number
interface route-aggregation
{ interface-number |
interface-number.subnumber }
enable snmp trap updown
Shutting down an aggregate interface
Shutting down or bringing up an aggregate interface affects the aggregation state and link state of ports
in the corresponding aggregation group in the following ways:
—
Optional.
By default, link state trapping is
enabled globally and on all
interfaces.
Required.
Use either command.
Optional.
Enabled by default.
• When an aggregate interface is shut down, all selected ports in the corresponding aggregation
group become unselected and their link state becomes down.
23
Page 31

• When an aggregate interface is brought up, the aggregation state of ports in the corresponding
aggregation group is recalculated and their link state becomes up.
To shut down an aggregate interface:
To do... Use the command... Remarks
1. Enter system view
Enter Layer 2
aggregate
2. Enter
aggregate
interface
view
3. Shut down the aggregate
interface or subinterface
interface view
Enter Layer 3
aggregate
interface or
subinterface
view
system-view —
interface bridge-aggregation
interface-number
interface route-aggregation
{ interface-number |
interface-number.subnumber }
shutdown
Required.
Use either command.
Required.
By default, aggregate interfaces
or subinterfaces are up.
Shutting down an aggregate subinterface does not affect any aggregation group, because an aggregate
subinterface does not have an associated aggregation group.
Configuring load sharing for link aggregation groups
Determine how traffic is load-shared in a link aggregation group by configuring load sharing criteria. The
criteria can be IP addresses or MAC addresses carried in packets, or any combination.
Configure global or group-specific load sharing criteria. A link aggregation group preferentially uses the
group-specific load sharing criteria. If no group-specific load sharing criteria is available, the group uses
the global load sharing criteria.
Configuring the global link-aggregation load sharing criteria
To configure the global link-aggregation load sharing criteria:
To do... Use the command... Remarks
1. Enter system view
2. Configure the global
link-aggregation load
sharing criteria
system-view —
Required.
By default, the global link-aggregation
load sharing criteria is
link-aggregation load-sharing mode
{ destination-ip | destination-mac |
source-ip | source-mac | per-packet }
destination-mac and source-mac at
Layer 2, and destination-ip and
source-ip at Layer 3.
With this command configured, all
link-aggregation load sharing criteria
are changed.
24
Page 32

Configuring group-specific load sharing criteria
To configure load sharing criteria for a link aggregation group:
To do… Use the command… Remarks
1. Enter system view
Enter Layer
2
aggregate
2. Enter
aggregate
interface
view
3. Configure the load
sharing criteria for the
aggregation group
interface
view
Enter Layer
3
aggregate
interface
view
system-view —
interface bridge-aggregation
interface-number
Use either command.
interface route-aggregation
interface-number
Required.
By default, the global
link-aggregation load-sharing mode
{ destination-ip | destination-mac
|source-ip | source-mac | per-packet }
link-aggregation load sharing
criteria are applied.
The per-packet keyword is not
available on Layer 2 aggregate
interfaces.
Displaying and maintaining Ethernet link aggregation
To do... Use the command... Remarks
Display information for an
aggregate interface or multiple
aggregate interfaces
Display the local system ID
Display the global or
group-specific link-aggregation
load sharing criteria
Display detailed link aggregation
information for link aggregation
member ports
Display summary information
about all aggregation groups
display interface [ bridge-aggregation |
route-aggregation ] [ brief [ down ] ] [ | { begin
| exclude | include } regular-expression ]
display interface { bridge-aggregation |
route-aggregation } interface-number [ brief ]
[ | { begin | exclude | include }
regular-expression ]
display lacp system-id [ | { begin | exclude |
include } regular-expression ]
display link-aggregation load-sharing mode
[ interface [ { bridge-aggregation |
route-aggregation } interface-number ] ] [ |
{ begin | exclude | include }
regular-expression ]
display link-aggregation member-port
[ interface-list ] [ | { begin | exclude | include }
regular-expression ]
display link-aggregation summary [ | { begin |
exclude | include } regular-expression ]
Available in any
view
Available in any
view
Available in any
view
Available in any
view
Available in any
view
25
Page 33

To do... Use the command... Remarks
Display detailed information
about a specific or all
aggregation groups
Clear LACP statistics for a specific
or all link aggregation member
ports
Clear statistics for a specific or all
aggregate interfaces
display link-aggregation verbose
[ { bridge-aggregation | route-aggregation }
[ interface-number ] ] [ | { begin | exclude |
include } regular-expression ]
reset lacp statistics [ interface interface-list ]
reset counters interface [ { bridge-aggregation |
route-aggregation } [ interface-number ] ]
Available in any
view
Available in user
view
Available in user
view
Ethernet link aggregation configuration examples
In an aggregation group, only ports that have the same port attributes and class-two configurations (see
“Configuration classes”) as the refe
sure that all member ports have the same port attributes and class-two configurations as the reference port.
The other settings only need to be configured on the aggregate interface, not on the member ports.
Layer 2 static aggregation configuration example
Network requirements
rence port (see “Reference port”) can operate as selected ports. Make
As shown in Figure 6:
• Router A and Router B are connected through their respective Layer 2 Ethernet interfaces
GigabitEthernet 3/1/1 through GigabitEthernet 3/1/3.
• Configure a Layer 2 static aggregation group on Router A and Router B, respectively, and enable
VLAN 10 at one end of the aggregate link to communicate with VLAN 10 at the other end, and
VLAN 20 at one end to communicate with VLAN 20 at the other end.
• Enable traffic to be load-shared across aggregation group member ports based on the source and
destination MAC addresses.
Figure 6 Network diagram for Layer 2 static aggregation
26
Page 34

Configuration procedure
1. Configure Router A
# Create VLAN 10, and assign port GigabitEthernet 3/1/4 to VLAN 10.
<RouterA> system-view
[RouterA] vlan 10
[RouterA-vlan10] port gigabitethernet 3/1/4
[RouterA-vlan10] quit
# Create VLAN 20, and assign port GigabitEthernet 3/1/5 to VLAN 20.
[RouterA] vlan 20
[RouterA-vlan20] port gigabitethernet 3/1/5
[RouterA-vlan20] quit
# Create Layer 2 aggregate interface Bridge-Aggregation 1.
[RouterA] interface bridge-aggregation 1
[RouterA-Bridge-Aggregation1] quit
# Assign ports GigabitEthernet 3/1/1 through GigabitEthernet 3/1/3 to link aggregation group 1.
[RouterA] interface gigabitethernet 3/1/1
[RouterA-GigabitEthernet3/1/1] port link-aggregation group 1
[RouterA-GigabitEthernet3/1/1] quit
[RouterA] interface gigabitethernet 3/1/2
[RouterA-GigabitEthernet3/1/2] port link-aggregation group 1
[RouterA-GigabitEthernet3/1/2] quit
[RouterA] interface gigabitethernet 3/1/3
[RouterA-GigabitEthernet3/1/3] port link-aggregation group 1
[RouterA-GigabitEthernet3/1/3] quit
# Configure Layer 2 aggregate interface Bridge-Aggregation 1 as a trunk port and assign it to VLANs 10
and 20.
[RouterA] interface bridge-aggregation 1
[RouterA-Bridge-Aggregation1] port link-type trunk
[RouterA-Bridge-Aggregation1] port trunk permit vlan 10 20
Please wait... Done.
Configuring GigabitEthernet3/1/1... Done.
Configuring GigabitEthernet3/1/2... Done.
Configuring GigabitEthernet3/1/3... Done.
[RouterA-Bridge-Aggregation1] quit
# Configure Router A to use the source and destination MAC addresses of packets as the global
link-aggregation load sharing criteria.
[RouterA] link-aggregation load-sharing mode source-mac destination-mac
2. Configure Router B
Configure Router B using the same instructions that you used to configure Router A.
3. Verify the configurations
# Display summary information about all aggregation groups on Router A.
[RouterA] display link-aggregation summary
27
Page 35

Aggregation Interface Type:
BAGG -- Bridge-Aggregation, RAGG -- Route-Aggregation
Aggregation Mode: S -- Static, D -- Dynamic
Loadsharing Type: Shar -- Loadsharing, NonS -- Non-Loadsharing
Actor System ID: 0x8000, 000f-e2ff-0001
AGG AGG Partner ID Select Unselect Share
Interface Mode Ports Ports Type
-------------------------------------------------------------------------------
BAGG1 S none 3 0 Shar
The output shows that link aggregation group 1 is a load shared Layer 2 static aggregation group and it
contains three selected ports.
# Display the global link-aggregation load sharing criteria on Router A.
[RouterA] display link-aggregation load-sharing mode
Link-Aggregation Load-Sharing Mode:
destination-mac address, source-mac address
The output shows that all link aggregation groups created on the router perform load sharing based on
source and destination MAC addresses.
Layer 2 dynamic aggregation configuration example
Network requirements
As shown in Figure 7:
• Router A and Router B are connected through their respective Layer 2 Ethernet interfaces
GigabitEthernet 3/1/1 through GigabitEthernet 3/1/3.
• Configure a Layer 2 dynamic aggregation group on Router A and Router B, respectively. Enable
VLAN 10 at one end of the aggregate link to communicate with VLAN 10 at the other end, and
VLAN 20 at one end to communicate with VLAN 20 at the other end.
• Enable traffic to be load-shared across aggregation group member ports based on source and
destination MAC addresses.
Figure 7 Network diagram for Layer 2 dynamic aggregation
28
Page 36

Configuration procedure
1. Configure Router A
# Create VLAN 10, and assign the port GigabitEthernet 3/1/4 to VLAN 10.
<RouterA> system-view
[RouterA] vlan 10
[RouterA-vlan10] port gigabitethernet 3/1/4
[RouterA-vlan10] quit
# Create VLAN 20, and assign the port GigabitEthernet 3/1/5 to VLAN 20.
[RouterA] vlan 20
[RouterA-vlan20] port gigabitethernet 3/1/5
[RouterA-vlan20] quit
# Create Layer 2 aggregate interface Bridge-aggregation 1, and configure the link aggregation mode as
dynamic.
[RouterA] interface bridge-aggregation 1
[RouterA-Bridge-Aggregation1] link-aggregation mode dynamic
# Assign ports GigabitEthernet 3/1/1 through GigabitEthernet 3/1/3 to link aggregation group 1 one
at a time.
[RouterA] interface gigabitethernet 3/1/1
[RouterA-GigabitEthernet3/1/1] port link-aggregation group 1
[RouterA-GigabitEthernet3/1/1] quit
[RouterA] interface gigabitethernet 3/1/2
[RouterA-GigabitEthernet3/1/2] port link-aggregation group 1
[RouterA-GigabitEthernet3/1/2] quit
[RouterA] interface gigabitethernet 3/1/3
[RouterA-GigabitEthernet3/1/3] port link-aggregation group 1
[RouterA-GigabitEthernet3/1/3] quit
# Configure Layer 2 aggregate interface Bridge-Aggregation 1 as a trunk port and assign it to VLANs 10
and 20.
[RouterA] interface bridge-aggregation 1
[RouterA-Bridge-Aggregation1] port link-type trunk
[RouterA-Bridge-Aggregation1] port trunk permit vlan 10 20
Please wait... Done.
Configuring GigabitEthernet3/1/1... Done.
Configuring GigabitEthernet3/1/2... Done.
Configuring GigabitEthernet3/1/3... Done.
[RouterA-Bridge-Aggregation1] quit
# Configure the router to use the source and destination MAC addresses of packets as the global
link-aggregation load sharing criteria.
[RouterA] link-aggregation load-sharing mode source-mac destination-mac
2. Configure Router B
Configure Router B using the same instructions that you used to configure Router A.
29
Page 37

3.
Verify the configurations
# Display summary information about all aggregation groups on Router A.
[RouterA] display link-aggregation summary
Aggregation Interface Type:
BAGG -- Bridge-Aggregation, RAGG -- Route-Aggregation
Aggregation Mode: S -- Static, D -- Dynamic
Loadsharing Type: Shar -- Loadsharing, NonS -- Non-Loadsharing
Actor System ID: 0x8000, 000f-e2ff-0001
AGG AGG Partner ID Select Unselect Share
Interface Mode Ports Ports Type
-------------------------------------------------------------------------------
BAGG1 D 0x8000, 000f-e2ff-0002 3 0 Shar
The output shows that link aggregation group 1 is a load shared Layer 2 dynamic aggregation group
and it contains three selected ports.
# Display the global link-aggregation load sharing criteria on Router A.
[RouterA] display link-aggregation load-sharing mode
Link-Aggregation Load-Sharing Mode:
destination-mac address, source-mac address
The output shows that all link aggregation groups created on the router perform load sharing based on
source and destination MAC addresses.
Layer 2 aggregation load sharing configuration example
Network requirements
As shown in Figure 8:
• Router A and Router B are connected by their Layer 2 Ethernet interfaces GigabitEthernet 3/1/1
through GigabitEthernet 3/1/4.
• Configure two Layer 2 static aggregation groups (1 and 2) on Router A and Router B, respectively,
and enable VLAN 10 at one end of the aggregate link to communicate with VLAN 10 at the other
end, and VLAN 20 at one end to communicate with VLAN 20 at the other end.
• Configure the load sharing criterion for link aggregation group 1 as the source MAC addresses of
packets and the load sharing criterion for link aggregation group 2 as the destination MAC
addresses of packets to enable traffic to be load-shared across aggregation group member ports.
30
Page 38

Figure 8 Network diagram for Layer 2 aggregation load sharing configuration
Configuration procedure
1. Configure Router A
# Create VLAN 10, and assign the port GigabitEthernet 3/1/5 to VLAN 10.
<RouterA> system-view
[RouterA] vlan 10
[RouterA-vlan10] port gigabitethernet 3/1/5
[RouterA-vlan10] quit
# Create VLAN 20, and assign the port GigabitEthernet 3/1/6 to VLAN 20.
<RouterA> system-view
[RouterA] vlan 20
[RouterA-vlan20] port gigabitethernet 3/1/6
[RouterA-vlan20] quit
# Create Layer 2 aggregate interface Bridge-Aggregation 1, and configure the load sharing criterion for
the link aggregation group as the source MAC addresses of packets.
[RouterA] interface bridge-aggregation 1
[RouterA-Bridge-Aggregation1] link-aggregation load-sharing mode source-mac
[RouterA-Bridge-Aggregation1] quit
# Assign ports GigabitEthernet 3/1/1 and GigabitEthernet 3/1/2 to link aggregation group 1.
[RouterA] interface gigabitethernet 3/1/1
[RouterA-GigabitEthernet3/1/1] port link-aggregation group 1
[RouterA-GigabitEthernet3/1/1] quit
[RouterA] interface gigabitethernet 3/1/2
[RouterA-GigabitEthernet3/1/2] port link-aggregation group 1
[RouterA-GigabitEthernet3/1/2] quit
# Configure Layer 2 aggregate interface Bridge-Aggregation 1 as a trunk port and assign it to VLANs 10
and 20.
[RouterA] interface bridge-aggregation 1
[RouterA-Bridge-Aggregation1] port link-type trunk
[RouterA-Bridge-Aggregation1] port trunk permit vlan 10 20
Please wait... Done.
Configuring GigabitEthernet3/1/1... Done.
31
Page 39

Configuring GigabitEthernet3/1/2... Done.
[RouterA-Bridge-Aggregation1] quit
# Create Layer 2 aggregate interface Bridge-Aggregation 2, and configure the load sharing criterion for
the link aggregation group as the destination MAC addresses of packets.
[RouterA] interface bridge-aggregation 2
[RouterA-Bridge-Aggregation2] link-aggregation load-sharing mode destination-mac
[RouterA-Bridge-Aggregation2] quit
# Assign ports GigabitEthernet 3/1/3 and GigabitEthernet 3/1/4 to link aggregation group 2.
[RouterA] interface gigabitethernet 3/1/3
[RouterA-GigabitEthernet3/1/3] port link-aggregation group 2
[RouterA-GigabitEthernet3/1/3] quit
[RouterA] interface gigabitethernet 3/1/4
[RouterA-GigabitEthernet3/1/4] port link-aggregation group 2
[RouterA-GigabitEthernet3/1/4] quit
# Configure Layer 2 aggregate interface Bridge-Aggregation 2 as a trunk port and assign it to VLANs 10
and 20.
[RouterA] interface bridge-aggregation 2
[RouterA-Bridge-Aggregation2] port link-type trunk
[RouterA-Bridge-Aggregation2] port trunk permit vlan 10 20
Please wait... Done.
Configuring GigabitEthernet3/1/3... Done.
Configuring GigabitEthernet3/1/4... Done.
[RouterA-Bridge-Aggregation2] quit
2. Configure Router B
Configure Router B using the same instructions that you used to configure Router A.
3. Verify the configurations
# Display summary information about all aggregation groups on Router A.
[RouterA] display link-aggregation summary
Aggregation Interface Type:
BAGG -- Bridge-Aggregation, RAGG -- Route-Aggregation
Aggregation Mode: S -- Static, D -- Dynamic
Loadsharing Type: Shar -- Loadsharing, NonS -- Non-Loadsharing
Actor System ID: 0x8000, 000f-e2ff-0001
AGG AGG Partner ID Select Unselect Share
Interface Mode Ports Ports Type
-------------------------------------------------------------------------------
BAGG1 S none 2 0 Shar
BAGG2 S none 2 0 Shar
The output shows that link aggregation groups 1 and 2 are both load-sharing-capable Layer 2 static
aggregation groups and each contains two selected ports.
# Display all group-specific load sharing criteria on Router A.
[RouterA] display link-aggregation load-sharing mode interface
32
Page 40

Bridge-Aggregation1 Load-Sharing Mode:
source-mac address
Bridge-Aggregation2 Load-Sharing Mode:
destination-mac address
The output shows that the load sharing criterion for link aggregation group 1 is the source MAC
addresses of packets and that for link aggregation group 2 is the destination MAC addresses of packets.
Layer 3 static aggregation configuration example
Network requirements
As shown in Figure 9:
• Router A and Router B are connected by their Layer 3 Ethernet interfaces GigabitEthernet 4/1/1
through GigabitEthernet 4/1/3.
• Configure a Layer 3 static aggregation group on Router A and Router B, respectively, and configure
IP addresses and subnet masks for the corresponding Layer 3 aggregate interfaces.
• Enable traffic to be load-shared across aggregation group member ports based on source and
destination IP addresses.
Figure 9 Network diagram for Layer 3 static aggregation
Configuration procedure
1. Configure Router A
# Create Layer 3 aggregate interface Route-aggregation 1, and configure an IP address and subnet mask
for the aggregate interface.
<RouterA> system-view
[RouterA] interface route-aggregation 1
[RouterA-Route-Aggregation1] ip address 192.168.1.1 24
[RouterA-Route-Aggregation1] quit
# Assign Layer 3 Ethernet interfaces GigabitEthernet 4/1/1 through GigabitEthernet 4/1/3 to
aggregation group 1.
[RouterA] interface gigabitethernet 4/1/1
[RouterA-GigabitEthernet4/1/1] port link-aggregation group 1
[RouterA-GigabitEthernet4/1/1] quit
[RouterA] interface gigabitethernet 4/1/2
[RouterA-GigabitEthernet4/1/2] port link-aggregation group 1
[RouterA-GigabitEthernet4/1/2] quit
[RouterA] interface gigabitethernet 4/1/3
[RouterA-GigabitEthernet4/1/3] port link-aggregation group 1
[RouterA-GigabitEthernet4/1/3] quit
33
Page 41

# Configure the global link-aggregation load sharing criteria as the source and destination IP addresses
of packets.
[RouterA] link-aggregation load-sharing mode source-ip destination-ip
2. Configure Router B
Configure Router B using the same instructions that you used to configure Router A.
3. Verify the configurations
# Display summary information about all aggregation groups on Router A.
[RouterA] display link-aggregation summary
Aggregation Interface Type:
BAGG -- Bridge-Aggregation, RAGG -- Route-Aggregation
Aggregation Mode: S -- Static, D -- Dynamic
Loadsharing Type: Shar -- Loadsharing, NonS -- Non-Loadsharing
Actor System ID: 0x8000, 000f-e2ff-0001
AGG AGG Partner ID Select Unselect Share
Interface Mode Ports Ports Type
-------------------------------------------------------------------------------
RAGG1 S none 3 0 Shar
The output shows that link aggregation group 1 is a load-sharing-capable Layer 3 static aggregation
group that contains three selected ports.
# Display the global link-aggregation load sharing criteria on Router A.
[RouterA] display link-aggregation load-sharing mode
Link-Aggregation Load-Sharing Mode:
destination-ip address, source-ip address
The output shows that the global link-aggregation load sharing criteria are the source and destination IP
addresses of packets.
Layer 3 dynamic aggregation configuration example
Network requirements
As shown in Figure 10:
• Router A and Router B are connected by their Layer 3 Ethernet interfaces GigabitEthernet 4/1/1
through GigabitEthernet 4/1/3.
• Configure a Layer 3 dynamic aggregation group on Router A and Router B, respectively, and
configure IP addresses and subnet masks for the corresponding Layer 3 aggregate interfaces.
• Enable traffic to be load-shared across aggregation group member ports based on source and
destination IP addresses.
34
Page 42

Figure 10 Network diagram for Layer 3 dynamic aggregation
Configuration procedure
1. Configure Router A
# Create Layer 3 aggregate interface Route-aggregation 1, configure the link aggregation mode as
dynamic, and configure an IP address and subnet mask for the aggregate interface.
<RouterA> system-view
[RouterA] interface route-aggregation 1
[RouterA-Route-Aggregation1] link-aggregation mode dynamic
[RouterA-Route-Aggregation1] ip address 192.168.1.1 24
[RouterA-Route-Aggregation1] quit
# Assign Layer 3 Ethernet interfaces GigabitEthernet 4/1/1 through GigabitEthernet 4/1/3 to
aggregation group 1.
[RouterA] interface gigabitethernet 4/1/1
[RouterA-GigabitEthernet4/1/1] port link-aggregation group 1
[RouterA-GigabitEthernet4/1/1] quit
[RouterA] interface gigabitethernet 4/1/2
[RouterA-GigabitEthernet4/1/2] port link-aggregation group 1
[RouterA-GigabitEthernet4/1/2] quit
[RouterA] interface gigabitethernet 4/1/3
[RouterA-GigabitEthernet4/1/3] port link-aggregation group 1
[RouterA-GigabitEthernet4/1/3] quit
# Configure Router A to use the source and destination IP addresses of packets as the global
link-aggregation load sharing criteria.
[RouterA] link-aggregation load-sharing mode source-ip destination-ip
2. Configure Router B
Configure Router B using the same instructions that you used to as you configure Router A.
3. Verify the configurations
# Display summary information about all aggregation groups on Router A.
[RouterA] display link-aggregation summary
Aggregation Interface Type:
BAGG -- Bridge-Aggregation, RAGG -- Route-Aggregation
Aggregation Mode: S -- Static, D -- Dynamic
Loadsharing Type: Shar -- Loadsharing, NonS -- Non-Loadsharing
Actor System ID: 0x8000, 000f-e2ff-0001
AGG AGG Partner ID Select Unselect Share
Interface Mode Ports Ports Type
-------------------------------------------------------------------------------
RAGG1 D 0x8000, 000f-e2ff-0002 3 0 Shar
35
Page 43
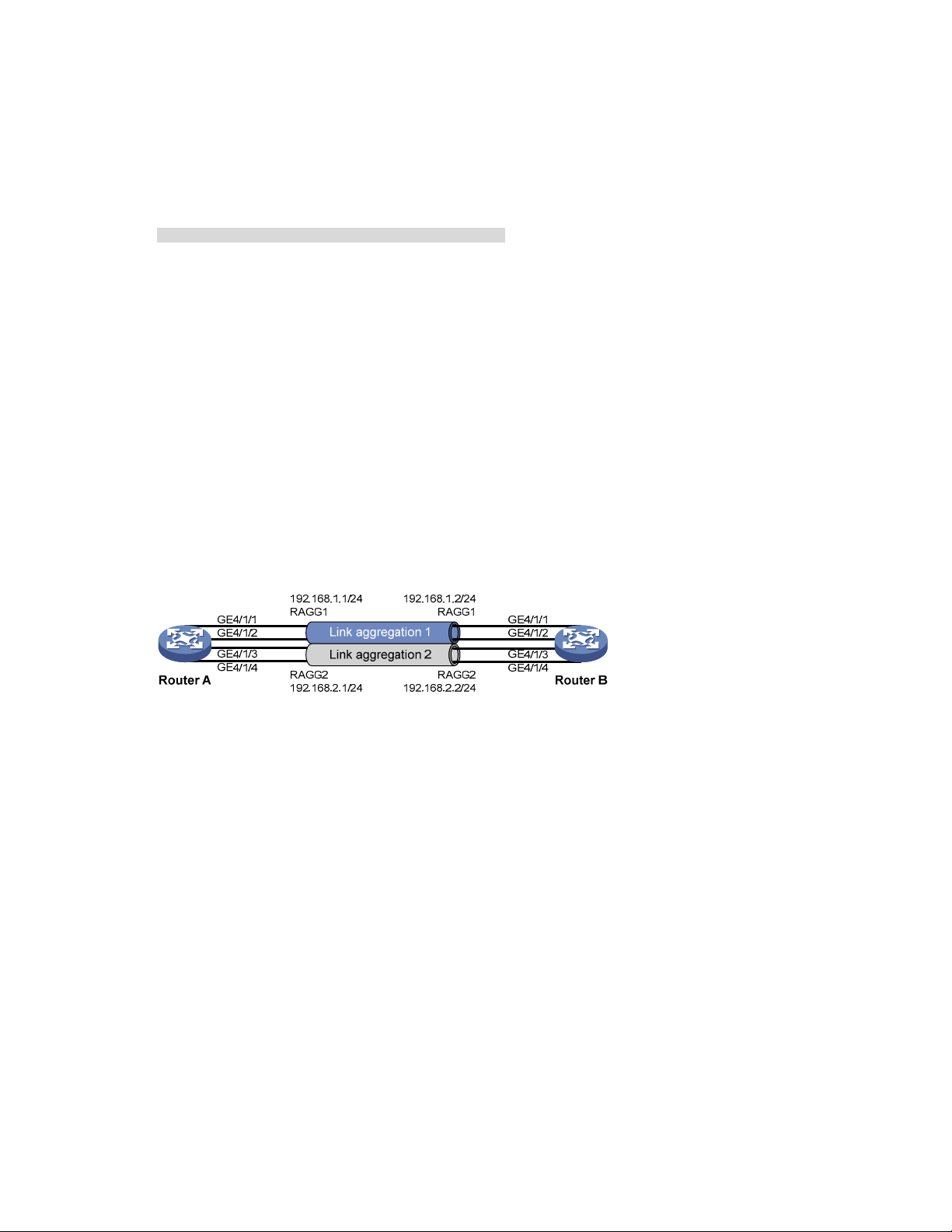
The output shows that link aggregation group 1 is a load-shared Layer 3 dynamic aggregation group and
it contains three selected ports.
# Display the global link-aggregation load sharing criteria on Router A.
[RouterA] display link-aggregation load-sharing mode
Link-Aggregation Load-Sharing Mode:
destination-ip address, source-ip address
The output shows that the global link-aggregation load sharing criteria are the source and destination IP
addresses of packets.
Layer 3 aggregation load sharing configuration example
Network requirements
As shown in Figure 11:
• Router A and Router B are connected by their Layer 3 Ethernet interfaces GigabitEthernet 4/1/1
through GigabitEthernet 4/1/4.
• Configure two Layer 3 static aggregation groups (1 and 2) on Router A and Router B, respectively,
and configure IP addresses and subnet masks for the corresponding Layer 3 aggregate interfaces.
• Configure link aggregation group 1 to perform load sharing based on source IP address and link
aggregation group 2 to perform load sharing based on destination IP address.
Figure 11 Network diagram for Layer 3 aggregation load sharing configuration
Configuration procedure
1. Configure Router A
# Create Layer 3 aggregate interface Route-Aggregation 1, configure it to perform load sharing based
on source IP address, and configure an IP address and subnet mask for the aggregate interface.
<RouterA> system-view
[RouterA] interface route-aggregation 1
[RouterA-Route-Aggregation1] link-aggregation load-sharing mode source-ip
[RouterA-Route-Aggregation1] ip address 192.168.1.1 24
[RouterA-Route-Aggregation1] quit
# Assign Layer 3 Ethernet interfaces GigabitEthernet 4/1/1 and GigabitEthernet 4/1/2 to aggregation
group 1.
[RouterA] interface gigabitethernet 4/1/1
[RouterA-GigabitEthernet4/1/1] port link-aggregation group 1
[RouterA-GigabitEthernet4/1/1] quit
[RouterA] interface gigabitethernet 4/1/2
[RouterA-GigabitEthernet4/1/2] port link-aggregation group 1
[RouterA-GigabitEthernet4/1/2] quit
36
Page 44

# Create Layer 3 aggregate interface Route-Aggregation 2, configure its link aggregation group to
perform load sharing based on destination IP address, and configure an IP address and subnet mask for
the aggregate interface.
[RouterA] interface route-aggregation 2
[RouterA-Route-Aggregation2] link-aggregation load-sharing mode destination-ip
[RouterA-Route-Aggregation2] ip address 192.168.2.1 24
[RouterA-Route-Aggregation2] quit
# Assign Layer 3 Ethernet interfaces GigabitEthernet 4/1/3 and GigabitEthernet 4/1/4 to aggregation
group 2.
[RouterA] interface gigabitethernet 4/1/3
[RouterA-GigabitEthernet4/1/3] port link-aggregation group 2
[RouterA-GigabitEthernet4/1/3] quit
[RouterA] interface gigabitethernet 4/1/4
[RouterA-GigabitEthernet4/1/4] port link-aggregation group 2
[RouterA-GigabitEthernet4/1/4] quit
2. Configure Router B
Configure Router B using the same instructions that you used to configure Router A.
3. Verify the configurations
# Display summary information about all aggregation groups on Router A.
[RouterA] display link-aggregation summary
Aggregation Interface Type:
BAGG -- Bridge-Aggregation, RAGG -- Route-Aggregation
Aggregation Mode: S -- Static, D -- Dynamic
Loadsharing Type: Shar -- Loadsharing, NonS -- Non-Loadsharing
Actor System ID: 0x8000, 000f-e2ff-0001
AGG AGG Partner ID Select Unselect Share
Interface Mode Ports Ports Type
-------------------------------------------------------------------------------
RAGG1 S none 2 0 Shar
RAGG2 S none 2 0 Shar
The output shows that link aggregation groups 1 and 2 are both load shared Layer 3 static aggregation
groups and each contains two selected ports.
# Display all group-specific load sharing criteria on Router A.
[RouterA] display link-aggregation load-sharing mode interface
Route-Aggregation1 Load-Sharing Mode:
source-ip address
37
Page 45

Route-Aggregation2 Load-Sharing Mode:
destination-ip address
The output shows that the load sharing criterion for link aggregation group 1 is the source IP address and
the load sharing criterion for link aggregation group 2 is the destination IP address.
38
Page 46

Port isolation configuration
This feature is available on only a SAP interface card working in bridge mode.
Usually, Layer 2 traffic isolation is achieved by assigning ports to different VLANs. To save VLAN
resources, port isolation is introduced to isolate ports within a VLAN, allowing for great flexibility and
security.
The routers support only one isolation group that is created automatically by the system as isolation group
1. You can neither remove the isolation group nor create other isolation groups.
Configuring an isolation group
Assigning a port to the isolation group
To add a port to the isolation group:
To do… Use the command… Remarks
1. Enter system view
system-view —
Enter
Ethernet
interface
2. Enter
interface
view or
port group
view
3. Assign the port or ports to
the isolation group as an
isolated port or ports
view
Enter Layer
2 aggregate
interface
view
Enter port
group view
interface interface-type
interface-number
interface
bridge-aggregation
interface-number
port-group manual
port-group-name
port-isolate enable
Required.
Use one of the commands.
• In Ethernet interface view, the subsequent
configurations apply to the current port.
• In Layer 2 aggregate interface view, the
subsequent configurations apply to the
Layer 2 aggregate interface and all its
member ports.
• In port group view, the subsequent
configurations apply to all ports in the port
group.
Required.
No ports are added to the isolation group by
default.
After you configure a command on a Layer 2 aggregate interface, the system starts applying the
configuration to the aggregate interface and its aggregation member ports. If the system fails to do that
on the aggregate interface, it stops applying the configuration to the aggregation member ports. If it fails
to do that on an aggregation member port, it simply skips the port and moves to the next port.
Displaying and maintaining isolation groups
To do… Use the command… Remarks
Display the isolation group
information
display port-isolate group [ | { begin |
exclude | include } regular-expression ]
39
Available in any view
Page 47

Port isolation configuration example
Network requirements
As shown in Figure 12,
• Users Host A, Host B, and Host C are connected to GigabitEthernet 3/0/1, GigabitEthernet 3/0/2,
and GigabitEthernet 3/0/3 of Router.
• Router is connected to the Internet through GigabitEthernet 3/0/4.
• GigabitEthernet 3/0/1, GigabitEthernet 3/0/2, GigabitEthernet 3/0/3, and GigabitEthernet
3/0/4 belong to the same VLAN.
Configure Router to enable Host A, Host B, and Host C to access the Internet when they are isolated from
one another.
Figure 12 Networking diagram for port isolation configuration
Internet
GE3/0/4
Router
GE3/0/1 GE3/0/3
GE3/0/2
Host A Host B Host C
Configuration procedure
# Add ports GigabitEthernet 3/0/1, GigabitEthernet 3/0/2, and GigabitEthernet 3/0/3 to the isolation
group.
<Router> system-view
[Router] interface gigabitEthernet 3/0/1
[Router-GigabitEthernet3/0/1] port-isolate enable
[Router-GigabitEthernet3/0/1] quit
[Router] interface gigabitEthernet 3/0/2
[Router-GigabitEthernet3/0/2] port-isolate enable
[Router-GigabitEthernet3/0/2] quit
[Router] interface gigabitEthernet 3/0/3
[Router-GigabitEthernet3/0/3] port-isolate enable
# Display information about the isolation group.
<Router> display port-isolate group
Port-isolate group information:
Uplink port support: No
Group ID: 1
Group members:
GigabitEthernet3/0/1 GigabitEthernet3/0/2 GigabitEthernet3/0/3
40
Page 48

MSTP configuration
The MSTP feature is available only on a SAP interface card in bridging mode.
As a Layer 2 management protocol, the STP eliminates Layer 2 loops by selectively blocking redundant
links in a network, and in the meantime, allows for link redundancy.
Like many other protocols, STP evolves as the network grows. The later versions of STP are the RSTP and
the MSTP. This chapter describes the features of STP, RSTP, and MSTP and the relationship among them.
Why STP
STP was developed based on the 802.1d standard of IEEE to eliminate loops at the data link layer in a
LAN. Devices running this protocol detect loops in the network by exchanging information with one
another and eliminate loops by selectively blocking certain ports to prune the loop structure into a
loop-free tree structure. This avoids proliferation and infinite cycling of packets that would occur in a loop
network and prevents decreased performance of network devices caused by duplicate packets received.
In the narrow sense, STP refers to IEEE 802.1d STP. In the broad sense, STP refers to the IEEE 802.1d STP
and various enhanced spanning tree protocols derived from that protocol.
Protocol packets of STP
STP uses BPDUs, also known as configuration messages, as its protocol packets.
STP-enabled network devices exchange BPDUs to establish a spanning tree. BPDUs contain sufficient
information for the network devices to complete spanning tree calculation.
In STP, BPDUs come in two types:
• Configuration BPDUs, used for calculating a spanning tree and maintaining the spanning tree
topology.
• TCN BPDUs, used for notifying the concerned devices of network topology changes, if any.
Basic concepts in STP
Root bridge
A tree network must have a root. Hence, the concept of root bridge was introduced in STP.
There is only one root bridge in the entire network, and the root bridge can change along with changes
of the network topology. Therefore, the root bridge is not fixed.
Upon initialization of a network, each device generates and sends out configuration BPDUs periodically
with itself as the root bridge. After network convergence, only the root bridge generates and sends out
configuration BPDUs at a certain interval, and the other devices forward the BPDUs.
Root port
On a non-root bridge, the port nearest to the root bridge is called the root port. The root port is
responsible for communication with the root bridge. Each non-root bridge has only one root port. The root
bridge has no root port.
41
Page 49

Designated bridge and designated port
Table 7 Description of designated bridges and designated ports
Classification Designated bridge Designated port
For a device
For a LAN
A device directly connected with the local
device and responsible for forwarding
BPDUs to the local device
The device responsible for forwarding
BPDUs to this LAN segment
The port through which the
designated bridge forwards BPDUs
to this device
The port through which the
designated bridge forwards BPDUs
to this LAN segment
As shown in Figure 13:
• If Device A forwards BPDUs to Device B through port A1, the designated bridge for Device B is
Device A, and the designated port of Device B is port A1 on Device A.
• Both Device B and Device C directly connect to the LAN. If Device B forwards BPDUs to the LAN, the
designated bridge for the LAN is Device B, and the designated port for the LAN is port B2 on Device
B.
Figure 13 A schematic diagram of designated bridges and designated ports
Path cost
Path cost is a reference value used for link selection in STP. By calculating path costs, STP selects relatively
robust links and blocks redundant links, and finally prunes the network into a loop-free tree.
42
Page 50

How STP works
The devices on a network exchange BPDUs to identify the network topology. Configuration BPDUs
contain sufficient information for the network devices to complete spanning tree calculation. Important
fields in a configuration BPDU include:
• Root bridge ID: consisting of the priority and MAC address of the root bridge.
• Root path cost: the cost of the path to the root bridge denoted by the root identifier from the
transmitting bridge.
• Designated bridge ID: consisting of the priority and MAC address of the designated bridge.
• Designated port ID: designated port priority plus port name.
• Message age: age of the configuration BPDU while it propagates in the network.
• Max age: maximum age of the configuration BPDU.
• Hello time: configuration BPDU transmission interval.
• Forward delay: the delay used by STP bridges to transit the state of the root and designated ports to
forwarding.
Calculation process of the STP algorithm
• Initial state
Upon initialization of a device, each port generates a BPDU with itself as the root bridge, in which the
root path cost is 0, designated bridge ID is the device ID, and the designated port is the port itself.
• Selection of the optimum configuration BPDU
Each device sends out its configuration BPDU and receives configuration BPDUs from other devices.
Table 8 des
cribes the process of selecting the optimum configuration BPDU.
Table 8 Selection of the optimum configuration BPDU
Step Actions
Upon receiving a configuration BPDU on a port, the device performs the following:
• If the received configuration BPDU has a lower priority than that of the configuration
BPDU generated by the port, the device discards the received configuration BPDU and
1
does not process the configuration BPDU of this port.
• If the received configuration BPDU has a higher priority than that of the configuration
BPDU generated by the port, the device replaces the content of the configuration BPDU
generated by the port with the content of the received configuration BPDU.
2
The device compares the configuration BPDUs of all ports and chooses the optimum
configuration BPDU.
The following are the principles of configuration BPDU comparison:
The configuration BPDU that has the lowest root bridge ID has the highest priority.
If all configuration BPDUs have the same root bridge ID, their root path costs are compared. Assume that
the root path cost in a configuration BPDU plus the path cost of a receiving port is S. The configuration
BPDU with the smallest S value has the highest priority.
43
Page 51

If all configuration BPDUs have the same ports value, their designated bridge IDs, designated port IDs,
and the IDs of the receiving
• Selection of the root bridge
Initially, each STP-enabled device on the network assumes itself to be the root bridge, with the root bridge
ID being its own device ID. By exchanging configuration BPDUs, the devices compare their root bridge
IDs to elect the device with the smallest root bridge ID as the root bridge.
• Selection of the root port and designated ports on a non-root device
Table 9 des
cribes the process of selecting the root port and designated ports.
Table 9 Selection of the root port and designated ports
Step Description
1
A non-root-bridge device regards the port on which it received the optimum configuration
BPDU as the root port.
Based on the configuration BPDU and the path cost of the root port, the device calculates a
designated port configuration BPDU for each of the rest ports.
• The root bridge ID is replaced with that of the configuration BPDU of the root port.
2
• The root path cost is replaced with that of the configuration BPDU of the root port plus
the path cost of the root port.
• The designated bridge ID is replaced with the ID of this device.
• The designated port ID is replaced with the ID of this port.
The device compares the calculated configuration BPDU with the configuration BPDU on
the port of which the port role is to be defined, and acts depending on the comparison
result:
• If the calculated configuration BPDU is superior, the device considers this port as the
3
designated port, replaces the configuration BPDU on the port with the calculated
configuration BPDU, and periodically sends out the calculated configuration BPDU.
• If the configuration BPDU on the port is superior, the device blocks this port without
updating its configuration BPDU. The blocked port can receive BPDUs but not send
BPDUs or forward data traffic.
When the network topology is stable, only the root port and designated ports forward traffic, while other
ports are all in the blocked state – they receive BPDUs but do not forward BPDUs or user traffic.
A tree-shape topology forms upon successful election of the root bridge, the root port on each non-root
bridge and the designated ports.
The following is an example of how the STP algorithm works. As shown in Figure 14, the priority of
D
evice A, Device B, and Device C is 0, 1, and 2, respectively, and the path costs among these links are
5, 10 and 4, respectively.
44
Page 52

p
Figure 14 Network diagram for the STP algorithm
• Initial state of each device
Table 10 Initial state of each device
Device Port name Configuration BPDU on the port
Device A
Device B
Device C
Port A1 {0, 0, 0, Port A1}
Port A2 {0, 0, 0, Port A2}
Port B1 {1, 0, 1, Port B1}
Port B2 {1, 0, 1, Port B2}
Port C1 {2, 0, 2, Port C1}
Port C2 {2, 0, 2, Port C2}
In Table 10, each configuration BPDU contains four fields: {root bridge ID, root path cost, designated
bridge ID, designated port ID}.
• Comparison process and result on each device
Table 11 Comparison process and result on each device
Device Comparison process
Configuration BPDU on
orts after comparison
• Port A1 receives the configuration BPDU of Port B1
{1, 0, 1, Port B1}, finds that its existing configuration
BPDU {0, 0, 0, Port A1} is superior to the received
configuration BPDU, and discards the received one.
• Port A2 receives the configuration BPDU of Port C1
• Port A1: {0, 0, 0, Port
A1}
• Port A2: {0, 0, 0, Port
A2}
Device A
{2, 0, 2, Port C1}, finds that its existing configuration
BPDU {0, 0, 0, Port A2} is superior to the received
configuration BPDU, and discards the received one.
• Device A finds that it is both the root bridge and
designated bridge in the configuration BPDUs of all its
ports, and thus considers itself as the root bridge. It
does not change the configuration BPDU of any port
and starts to periodically send out configuration
BPDUs.
45
Page 53

p
Device Comparison process
• Port B1 receives the configuration BPDU of Port A1
{0, 0, 0, Port A1}, finds that the received
configuration BPDU is superior to its existing
configuration BPDU {1, 0, 1, Port B1}, and updates its
configuration BPDU.
• Port B2 receives the configuration BPDU of Port C2
{2, 0, 2, Port C2}, finds that its existing configuration
BPDU {1, 0, 1, Port B2} is superior to the received
configuration BPDU, and discards the received one.
• Device B compares the configuration BPDUs of all its
Device B
ports, decides that the configuration BPDU of Port B1
is the optimum, and selects Port B1 as the root port
with the configuration BPDU unchanged.
• Based on the configuration BPDU and path cost of the
root port, Device B calculates a designated port
configuration BPDU for Port B2 {0, 5, 1, Port B2}, and
compares it with the existing configuration BPDU of
Port B2 {1, 0, 1, Port B2}. Device B finds that the
calculated one is superior, decides that Port B2 is the
designated port, replaces the configuration BPDU on
Port B2 with the calculated one, and periodically
sends out the calculated configuration BPDU.
• Port C1 receives the configuration BPDU of Port A2
{0, 0, 0, Port A2}, finds that the received
configuration BPDU is superior to its existing
configuration BPDU {2, 0, 2, Port C1}, and updates
its configuration BPDU.
• Port C2 receives the original configuration BPDU of
Port B2 {1, 0, 1, Port B2}, finds that the received
configuration BPDU is superior to the existing
configuration BPDU {2, 0, 2, Port C2}, and updates
its configuration BPDU.
• Device C compares the configuration BPDUs of all its
Device C
ports, decides that the configuration BPDU of Port C1
is the optimum, and selects Port C1 as the root port
with the configuration BPDU unchanged.
• Based on the configuration BPDU and path cost of the
root port, Device C calculates the configuration BPDU
of Port C2 {0, 10, 2, Port C2}, and compares it with
the existing configuration BPDU of Port C2 {1, 0, 1,
Port B2}. Device C finds that the calculated
configuration BPDU is superior to the existing one,
selects Port C2 as the designated port, and replaces
the configuration BPDU of Port C2 with the calculated
one.
Configuration BPDU on
orts after comparison
• Port B1: {0, 0, 0, Port
A1}
• Port B2: {1, 0, 1, Port
B2}
• Root port (Port B1): {0,
0, 0, Port A1}
• Designated port (Port
B2): {0, 5, 1, Port B2}
• Port C1: {0, 0, 0, Port
A2}
• Port C2: {1, 0, 1, Port
B2}
• Root port (Port C1): {0,
0, 0, Port A2}
• Designated port (Port
C2): {0, 10, 2, Port
C2}
46
Page 54

p
Device Comparison process
• Port C2 receives the updated configuration BPDU of
Port B2 {0, 5, 1, Port B2}, finds that the received
configuration BPDU is superior to its existing
configuration BPDU {0, 10, 2, Port C2}, and updates
its configuration BPDU.
• Port C1 receives a periodic configuration BPDU {0, 0,
0, Port A2} from Port A2, finds that it is the same as
the existing configuration BPDU, and discards the
received one.
• Device C finds that the root path cost of Port C1 (10)
(root path cost of the received configuration BPDU (0)
plus path cost of Port C1 (10)) is larger than that of
Port C2 (9) (root path cost of the received
configuration BPDU (5) plus path cost of Port C2 (4)),
decides that the configuration BPDU of Port C2 is the
optimum, and selects Port C2 as the root port with the
configuration BPDU unchanged.
• Based on the configuration BPDU and path cost of the
root port, Device C calculates a designated port
configuration BPDU for Port C1 {0, 9, 2, Port C1} and
compares it with the existing configuration BPDU of
Port C1 {0, 0, 0, Port A2}. Device C finds that the
existing configuration BPDU is superior to the
calculated one and blocks Port C1 with the
configuration BPDU unchanged. Then Port C1 does
not forward data until a spanning tree calculation
process is triggered by a new event, for example, the
link between Device B and Device C is down.
Configuration BPDU on
orts after comparison
• Port C1: {0, 0, 0, Port
A2}
• Port C2: {0, 5, 1, Port
B2}
• Blocked port (Port C1):
{0, 0, 0, Port A2}
• Root port (Port C2): {0,
5, 1, Port B2}
In Table 11, each configuration BPDU contains four fields: {root bridge ID, root path cost, designated
bridge ID, designated port ID}.
After the comparison processes described in the table above, a spanning tree with Device A as the root
bridge is established, and the topology is shown in Figure 15.
Figure 15 Topology of the final calculated spanning tree
The spanning tree calculation process in this example is only simplified process.
47
Page 55

The BPDU forwarding mechanism in STP
• Upon network initiation, every switch regards itself as the root bridge, generates configuration
BPDUs with itself as the root, and sends the configuration BPDUs at a regular hello interval.
• If it is the root port that received a configuration BPDU and the received configuration BPDU is
superior to the configuration BPDU of the port, the device increases the message age carried in the
configuration BPDU following a certain rule and starts a timer to time the configuration BPDU while
sending out this configuration BPDU through the designated port.
• If the configuration BPDU received on a designated port has a lower priority than the configuration
BPDU of the local port, the port immediately sends out its own configuration BPDU in response.
• If a path becomes faulty, the root port on this path no longer receives new configuration BPDUs and
the old configuration BPDUs are discarded due to timeout. In this case, the device generates a
configuration BPDU with itself as the root and sends out the BPDUs and TCN BPDUs. This triggers a
new spanning tree calculation process to establish a new path to restore the network connectivity.
However, the newly calculated configuration BPDU cannot be propagated throughout the network
immediately, so the old root ports and designated ports that have not detected the topology change
continue forwarding data along the old path. If the new root ports and designated ports begin to forward
data as soon as they are elected, a temporary loop may occur.
STP timers
STP calculation involves three important timing parameters: forward delay, hello time, and max age.
• Forward delay is the delay time for device state transition.
A path failure can cause spanning tree re-calculation to adapt the spanning tree structure to the change.
However, the resulting new configuration BPDU cannot propagate throughout the network immediately. If
the newly elected root ports and designated ports start to forward data right away, a temporary loop is
likely to occur.
For this reason, as a mechanism for state transition in STP, the newly elected root ports or designated
ports require twice the forward delay time before transiting to the forwarding state to ensure that the new
configuration BPDU has propagated throughout the network.
• Hello time is the time interval at which a device sends hello packets to the surrounding devices to
• Max age is a parameter used to determine whether a configuration BPDU held by the device has
RSTP
Developed based on the 802.1w standard of IEEE, RSTP is an optimized version of STP. It achieves rapid
network convergence by allowing a newly elected root port or designated port to enter the forwarding
state much quicker under certain conditions than in STP.
In RSTP, a newly elected root port can enter the forwarding state rapidly if this condition is met: the old
root port on the device has stopped forwarding data and the upstream designated port has started
forwarding data.
ensure that the paths are fault-free.
expired. A configuration BPDU beyond the max age is discarded.
In RSTP, a newly elected designated port can enter the forwarding state rapidly if this condition is met:
the designated port is an edge port (a port directly connects to a user terminal rather than to another
device or a shared LAN segment) or a port connected with a point-to-point link. If the designated port is
an edge port, it can enter the forwarding state directly. If the designated port is connected with a
48
Page 56

point-to-point link, it can enter the forwarding state immediately after the device undergoes handshake
with the downstream device and gets a response.
MSTP
Why MSTP
Limitations of STP and RSTP
STP does not support rapid state transition of ports. A newly elected root port or designated port must
wait twice the forward delay time before transiting to the forwarding state, even if it is a port on a
point-to-point link or an edge port.
Although RSTP supports rapid network convergence, it has the same drawback as STP does: All bridges
within a LAN share the same spanning tree, so redundant links cannot be blocked based on VLAN, and
the packets of all VLANs are forwarded along the same spanning tree.
Features of MSTP
Developed based on IEEE 802.1s, MSTP overcomes the shortcomings of STP and RSTP. In addition to the
support for rapid network convergence, it allows data flows of different VLANs to be forwarded along
separate paths, thus providing a better load sharing mechanism for redundant links. For more information
about VLANs, see the chapter “VLAN configuration.”
MSTP features the following:
• MSTP supports mapping VLANs to spanning tree instances by means of a VLAN-to-instance
mapping table. MSTP can reduce communication overheads and resource usage by mapping
multiple VLANs to one instance.
• MSTP divides a switched network into multiple regions, each containing multiple spanning trees that
are independent of one another.
• MSTP prunes a loop network into a loop-free tree, thus avoiding proliferation and endless cycling of
packets in a loop network. In addition, it provides multiple redundant paths for data forwarding,
thus supporting load balancing of VLAN data.
• MSTP is compatible with STP and RSTP.
49
Page 57

Basic concepts in MSTP
Figure 16 Basic concepts in MSTP
VLAN 1 MSTI 1
VLAN 2
Other VLANs
MST region 1
MSTI 2
MSTI 0
VLAN 1 MSTI 1
VLAN 2
Other VLANs
MSTI 2
MSTI 0
MST region 4
MST region 2 MST region 3
VLAN 1 MSTI 1
VLAN 2
Other VLANs
MSTI 2
MSTI 0
CST
VLAN 1 MSTI 1
VLAN 2&3
Other VLANs
MSTI 2
MSTI 0
Figure 17 Network diagram and topology of MST region 3
50
Page 58

As shown in Figure 16, a switched network comprises four MST regions, and each MST region comprises
four devices running MSTP. Figure 17
describes some basic concepts of MSTP.
MST region
An MST region consists of multiple devices in a switched network and the network segments among them.
All these devices have the following characteristics:
• MSTP-enabled
• Same region name
• Same VLAN-to-instance mapping configuration
• Same MSTP revision level configuration
• Physically linked with one another
Multiple MST regions can exist in a switched network. Assign multiple devices to the same MST region.
In Figure 16,
and all devices in each MST region have the same MST region configuration.
MSTI
MSTP can generate multiple spanning trees in an MST region, and each spanning tree is independent of
another and maps to the specific VLANs. Each spanning tree is referred to as an MSTI.
shows the networking topology of MST region 3. This section
the switched network comprises four MST regions, MST region 1 through MST region 4,
In Figure 17,
for example, MST region 3 comprises three MSTIs, MSTI 1, MSTI 2, and MSTI 0.
VLAN-to-instance mapping table
As an attribute of an MST region, the VLAN-to-instance mapping table describes the mapping
relationships between VLANs and MSTIs.
In Figure 17,
VLAN 2 and VLAN 3 to MSTI 2, and other VLANs to MSTI 0. MSTP achieves load balancing by means of
the VLAN-to-instance mapping table.
for example, the VLAN-to-instance mapping table of MST region 3 is: VLAN 1 to MSTI 1,
CST
The CST is a single spanning tree that connects all MST regions in a switched network. If you regard each
MST region as a device, the CST is a spanning tree calculated by these devices through STP or RSTP.
For example, the blue lines in Figure 16 repres
IST
An IST is a spanning tree that runs in an MST region. It is the section of the CIST in an MST region, and is
also called MSTI 0. ISTs in all MST regions and the CST jointly constitute the CIST of the entire network.
As shown in Figure 16,
MSTI 0 is the IST in MST region 3.
CIST
Jointly constituted by ISTs and the CST, the CIST is a single spanning tree that connects all devices in a
switched network.
ent the CST.
In Figure 16,
entire network.
Regional root
The root bridge of the IST or an MSTI within an MST region is the regional root of the IST or MSTI. Based
on the topology, different spanning trees in an MST region may have different regional roots.
for example, the ISTs in all MST regions plus the inter-region CST constitute the CIST of the
51
Page 59

For example, in MST region 3 in Figure 17, the regional root of MSTI 1 is Device B, the regional root of
MSTI 2 is Device C, and the regional root of MSTI 0 (also known as the IST) is Device A.
Common root bridge
The common root bridge is the root bridge of the CIST.
In Figure 16,
Roles of ports
A port can play different roles in different MSTIs. As shown in Figure 18, an MST region comprises
Device A, Device B, Device C, and Device D. Port A1 and port A2 of Device A connect to the common
root bridge. Port B2 and Port B3 of Device B form a loop. Port C3 and Port C4 of Device C connect to
other MST regions. Port D3 of Device D directly connects to a host.
Figure 18 Port roles
for example, the common root bridge is a device in MST region 1.
MSTP calculation involves these port roles:
• Root port: Forwards data for a non-root bridge to the root bridge. The root bridge does not have any
root port.
• Designated port: Forwards data to the downstream network segment or device.
• Alternate port: The backup port for a root port or master port. When the root port or master port is
blocked, the alternate port takes over.
• Backup port: The backup port of a designated port. When the designated port is blocked, the
backup port takes over without delay. When a loop occurs due to the interconnection of two ports of
the same MSTP device, the device blocks either of the two ports, and the blocked port is the backup
port.
• Edge port: An edge port does not connect to any network device or network segment, but directly
connects to a user host.
• Master port: A port on the shortest path from the local MST region to the common root bridge. The
master port is a root port on the IST or CIST and still a master port on the other MSTIs.
52
Page 60

• Boundary port: Connects an MST region to another MST region or to an STP/RSTP-running device.
Port states
In MSTP, a port may be in one of the following three states:
• Forwarding: the port receives and sends BPDUs, learns MAC addresses, and forwards user traffic.
• Learning: the port receives and sends BPDUs, learns MAC addresses, but does not forward user
• Discarding: the port receives and sends BPDUs, but does not learn MAC addresses or forwards user
When in different MSTIs, a port can be in different states.
In MSTP calculation, a boundary port’s role on an MSTI is consistent with its role on the CIST. But
that is not true with master ports. A master port on MSTIs is a root port on the CIST.
traffic. Learning is an intermediate port state.
traffic.
A port state is not exclusively associated with a port role. Table 12 lists the port
port role (“√” indicates that the port supports this state, while “—” indicates that the port does not support
this state).
Table 12 Port states supported by different port roles
Port role (right)
Port state
(below)
Forwarding √ √ — —
Learning √ √ — —
Discarding √ √ √ √
Root port/master
port
How MSTP works
MSTP divides an entire Layer 2 network into multiple MST regions, which are interconnected by a
calculated CST. Inside an MST region, multiple spanning trees are calculated, each being called an MSTI.
Among these MSTIs, MSTI 0 is the IST. Similar to STP, MSTP uses configuration BPDUs to calculate
spanning trees. The only difference between the two protocols is that an MSTP BPDU carries the MSTP
configuration on the device from which this BPDU is sent.
states supported by each
Designated port Alternate port Backup port
CIST calculation
The calculation of a CIST tree is also the process of configuration BPDU comparison. During this process,
the device with the highest priority is elected as the root bridge of the CIST. MSTP generates an IST within
each MST region through calculation, and, at the same time, MSTP regards each MST region as a single
device and generates a CST among these MST regions through calculation. The CST and ISTs constitute
the CIST of the entire network.
MSTI calculation
Within an MST region, MSTP generates different MSTIs for different VLANs based on the
VLAN-to-instance mappings. MSTP performs a separate calculation process, which is similar to spanning
tree calculation in STP, for each spanning tree. For more information, see “
53
Page 61

How STP works.”
In MSTP, a VLAN packet is forwarded along the following paths:
• Within an MST region, the packet is forwarded along the corresponding MSTI.
• Between two MST regions, the packet is forwarded along the CST.
Implementation of MSTP on devices
MSTP is compatible with STP and RSTP. STP and RSTP protocol packets can be recognized by devices
running MSTP and used for spanning tree calculation.
In addition to basic MSTP functions, many special functions are provided for ease of management, as
follows:
• Root bridge hold
• Root bridge backup
• Root guard
• BPDU guard
• Loop guard
• TC-BPDU guard
• BPDU drop
• Support for hot swapping of interface cards and active/standby changeover.
Protocols and standards
MSTP is documented in:
• IEEE 802.1d: Media Access Control (MAC) Bridges
• IEEE 802.1w: Part 3: Media Access Control (MAC) Bridges—Amendment 2: Rapid Reconfiguration
• IEEE 802.1s: Virtual Bridged Local Area Networks—Amendment 3: Multiple Spanning Trees
MSTP configuration task list
Before configuring MSTP, you need to know the role of each device in each MSTI: root bridge or leave
node. In each MSTI, one, and only one device acts as the root bridge, while all others as leaf nodes.
Complete these tasks to configure MSTP:
Task Remarks
Configuring an MST region Required
Configuring the root bridge or a secondary root bridge Optional
Configuring the work mode of an MSTP device Optional
Configuring the root
bridge
Configuring the priority of a device Optional
Configuring the maximum hops of an MST region Optional
Configuring the network diameter of a switched network Optional
Configuring timers of MSTP
Configuring the timeout factor Optional
54
Optional
Page 62

Task Remarks
Configuring the maximum port rate Optional
Configuring ports as edge ports Optional
Configuring the link type of ports Optional
Configuring the mode a port uses to recognize/send MSTP
packets
Enabling the output of port state transition information Optional
Enabling the MSTP feature Required
Configuring an MST region Required
Configuring the work mode of an MSTP device Optional
Configuring the timeout factor Optional
Configuring the maximum port rate Optional
Configuring ports as edge ports Optional
Configuring the leaf
nodes
Performing mCheck Optional
Configuring digest snooping
Configuring path costs of ports Optional
Configuring port priority Optional
Configuring the link type of ports Optional
Configuring the mode a port uses to recognize/send MSTP
packets
Enabling the output of port state transition information Optional
Enabling the MSTP feature Required
Optional
Optional
Optional
Configuring no agreement check Optional
Configuring protection functions Optional
If GVRP and MSTP are enabled on a device at the same time, GVRP packets are forwarded along the
CIST. Therefore, if you wish to advertise a certain VLAN within the network through GVRP in this case,
make sure that this VLAN is mapped to the CIST (MSTI 0) when you configure the VLAN-to-instance
mapping table. For more information about GVRP, see the chapter “GVRP configuration.”
MSTP is mutually exclusive with any of the following functions on a port: service loopback, RRPP, Smart
Link, and BPDU tunnel.
Configurations made in system view take effect globally. Configurations made in Ethernet interface view
take effect on the current interface only. Configurations made in port group view take effect on all
member ports in the port group. Configurations made in Layer 2 aggregate interface view take effect only
on the aggregate interface. Configurations made on an aggregation member port can take effect only
after the port is removed from the aggregation group.
After you enable MSTP on a Layer 2 aggregate interface, the system performs MSTP calculation on the
Layer 2 aggregate interface but not on the aggregation member ports. The MSTP enable state and
forwarding state of each selected port in an aggregation group is consistent with those of the
corresponding Layer 2 aggregate interface.
55
Page 63

Though the member ports of an aggregation group do not participate in MSTP calculation, the ports still
reserve its MSTP configurations for participating MSTP calculation after leaving the aggregation group.
Configuring MSTP
Configuring an MST region
Make the following configurations on the root bridge and on the leaf nodes separately.
To configure an MST region:
To do... Use the command... Remarks
1. Enter system view
2. Enter MST region view
3. Configure the MST region
name
4. Configure the
VLAN-to-instance mapping
table
5. Configure the MSTP revision
level of the MST region
6. Display the MST region
configurations that are not
activated yet
7. Activate MST region
configuration manually
8. Display the currently activated
configuration information of
the MST region
system-view —
stp region-configuration —
Optional.
region-name name
instance instance-id vlan vlan-list
vlan-mapping modulo modulo
revision-level level
check region-configuration Optional.
active region-configuration Required.
display stp region-configuration
[ | { begin | exclude | include }
regular-expression ]
The MST region name is the MAC
address by default.
Optional.
Use either command.
All VLANs in an MST region are
mapped to the CIST (or MSTI 0)
by default.
Optional.
0 by default.
Optional.
Available in any view.
Two or more MSTP-enabled devices belong to the same MST region only if they are configured to have
the same format selector (0 by default, not configurable), MST region name, the same VLAN-to-instance
mapping entries in the MST region and the same MST region revision level, and they are interconnected
via a physical link.
The configuration of MST region–related parameters, especially the VLAN-to-instance mapping table,
causes MSTP to launch a new spanning tree calculation process, which may result in network topology
instability. To reduce the possibility of topology instability caused by configuration, MSTP does not
immediately launch a new spanning tree calculation process when processing MST region–related
configurations. Instead, such configurations takes effect only after you activate the MST region–related
parameters by using the active region-configuration command, or enable MSTP by using the stp enable
command in the case that MSTP is not enabled.
56
Page 64

Configuring the root bridge or a secondary root bridge
MSTP can determine the root bridge of a spanning tree through MSTP calculation. Alternatively, specify
the current device as the root bridge or a secondary root bridge using the commands provided by the
system.
Note that:
• A device has independent roles in different MSTIs. It can act as the root bridge or a secondary root
bridge of one MSTI while being the root bridge or a secondary root bridge of another MSTI.
However, the same device cannot be the root bridge and a secondary root bridge in the same MSTI
at the same time.
• There is only one root bridge in effect in a spanning tree instance. If two or more devices have been
designated to be root bridges of the same spanning tree instance, MSTP selects the device with the
lowest MAC address as the root bridge.
• When the root bridge of an instance fails or is shut down, the secondary root bridge (if you have
specified one) can take over the role of the primary root bridge. However, if you specify a new
primary root bridge for the instance then, the secondary root bridge does not become the root
bridge. If you have specified multiple secondary root bridges for an instance, when the root bridge
fails, MSTP selects the secondary root bridge with the lowest MAC address as the new root bridge.
Configuring the current device as the root bridge of a specific spanning tree
To configure the current device as the root bridge of a specific spanning tree:
To do... Use the command... Remarks
1. Enter system view
2. Configure the current device
as the root bridge of a
specific spanning tree
system-view —
Required.
stp [ instance instance-id ] root
primary
By default, a device does not
function as the root bridge of any
spanning tree.
Configuring the current device as a secondary root bridge of a specific spanning tree
To configure the current device as a secondary root bridge of a specific spanning tree:
To do... Use the command... Remarks
1. Enter system view
2. Configure the current device
as a secondary root bridge of
a specific spanning tree
After specifying the current device as the root bridge or a secondary root bridge, you cannot change the
priority of the device.
system-view —
Required.
stp [ instance instance-id ] root
secondary
By default, a device does not
function as a secondary root
bridge.
Alternatively, you can also configure the current device as the root bridge by setting the priority of the
device to 0. For the device priority configuration, see “Configuring the priority of a device.”
57
Page 65

Configuring the work mode of an MSTP device
Being mutually compatible, MSTP and RSTP can recognize each other’s protocol packets. However, STP
is unable to recognize MSTP packets. For hybrid networking with legacy STP devices and for full
interoperability with RSTP-enabled devices, MSTP supports three work modes: STP-compatible mode,
RSTP mode, and MSTP mode.
• In STP-compatible mode, all ports of the device send out STP BPDUs,
• In RSTP mode, all ports of the device send out RSTP BPDUs. If the device detects that it is connected
with a legacy STP device, the port connecting with the legacy STP device automatically migrates to
STP-compatible mode.
• In MSTP mode, all ports of the device send out MSTP BPDUs. If the device detects that it is connected
with a legacy STP device, the port connecting with the legacy STP device automatically migrates to
STP-compatible mode.
Make this configuration on the root bridge and on the leaf nodes separately.
To configure the MSTP work mode:
To do... Use the command... Remarks
1. Enter system view
2. Configure the work mode of
MSTP
system-view —
stp mode { stp | rstp | mstp }
Configuring the priority of a device
After configuring a device as the root bridge or a secondary root bridge, you cannot change the priority
of the device.
During root bridge selection, if all devices in a spanning tree have the same priority, the one with the
lowest MAC address is selected as the root bridge of the spanning tree.
Device priorities participate in spanning tree calculation. The priority of a device determines whether it
can be elected as the root bridge of a spanning tree. A lower value indicates a higher priority. By setting
the priority of a device to a low value, you can specify the device as the root bridge of the spanning tree.
An MSTP-enabled device can have different priorities in different MSTIs.
Make this configuration on the root bridge only.
To configure the priority of a device in a specified MSTI:
To do... Use the command... Remarks
1. Enter system view
2. Configure the priority of the
current device in a specified
MSTI
system-view —
stp [ instance instance-id ] priority
priority
Required
MSTP mode by default
Required
32,768 by default
58
Page 66

Configuring the maximum hops of an MST region
By setting the maximum hops of an MST region, you can restrict the region size. The maximum hops
configured on the regional root bridge are used as the maximum hops of the MST region.
The regional root bridge always sends a configuration BPDU with a hop count set to the maximum value.
When a switch receives this configuration BPDU, it decrements the hop count by 1 and uses the new hop
count in the BPDUs it propagates. When the hop count of a BPDU reaches 0, it is discarded by the device
that received it. Thus, devices beyond the reach of the maximum hop can no longer take part in spanning
tree calculation, and thereby the size of the MST region is confined.
Make this configuration on the root bridge only. All devices other than the root bridge in the MST region
use the maximum hop value set for the root bridge.
To configure the maximum number of hops of an MST region:
To do... Use the command... Remarks
1. Enter system view
2. Configure the maximum hops
of the MST region
system-view —
stp max-hops hops
Required
20 by default
Configuring the network diameter of a switched network
Any two terminal devices in a switched network are interconnected through a specific path composed of
a series of devices. The network diameter is the number of devices on the path composed of the most
devices. The network diameter is a parameter that indicates the network size. A bigger network diameter
indicates a larger network size.
Make this configuration on the root bridge only.
To configure the network diameter of a switched network:
To do... Use the command... Remarks
1. Enter system view
2. Configure the network
diameter of the switched
network
Based on the network diameter you configured, MSTP automatically sets an optimal hello time, forward
delay, and max age for the device.
system-view —
stp bridge-diameter diameter
Required
7 by default
The configured network diameter is effective for the CIST only, and not for MSTIs. Each MST region is
considered as a device.
The network diameter must be configured on the root bridge. Otherwise, it does not take effect.
59
Page 67

Configuring timers of MSTP
The length of the forward delay time is related to the network diameter of the switched network. Typically,
the larger the network diameter is, the longer the forward delay time should be. Note that if the forward
delay setting is too small, temporary redundant paths may be introduced. If the forward delay setting is
too big, it may take a long time for the network to converge. HP recommends that you use the default
setting.
An appropriate hello time setting enables the device to timely detect link failures on the network without
using excessive network resources. If the hello time is set too long, the device takes packet loss as a link
failure and triggers a new spanning tree calculation process. If the hello time is set too short, the device
sends repeated configuration BPDUs frequently, which adds to the device burden and causes waste of
network resources. HP recommends that you use the default setting.
If the max age time setting is too small, the network devices frequently launches spanning tree
calculations, and may take network congestion as a link failure. If the max age setting is too large, the
network may fail to timely detect link failures and fail to timely launch spanning tree calculations, thus
reducing the auto-sensing capability of the network. HP recommends that you use the default setting.
MSTP involves three timers: forward delay, hello time and max age. Configure these three parameters for
MSTP to calculate spanning trees.
• To prevent temporary loops on a network, MSTP sets an intermediate port state called learning
between the discarding state and the forwarding state, that is, before a port in the discarding state
can transit to the forwarding state, it needs to go through the learning state. Forward delay is the
delay time for port state transition. This is to ensure that the state transition of the local port and that
of the peer occur in a synchronized manner.
• Hello time is the time interval at which a device sends configuration BPDUs to the surrounding
devices to ensure that the paths are fault-free. If a device fails to receive configuration BPDUs within
a certain period of time, it starts a new spanning tree calculation process.
• MSTP can detect link failures and automatically restore blocked redundant links to the forwarding
state. A device on the CIST determines whether a configuration BPDU received by a port has
expired according to the max age parameter. If yes, it starts a new spanning tree calculation
process. The max age set for an MSTI does not take effect.
These three timers set on the root bridge of the CIST apply on all devices on the entire switched network.
Make this configuration on the root bridge only.
To configure the timers of MSTP:
To do... Use the command... Remarks
1. Enter system view
2. Configure the forward delay
timer
3. Configure the hello timer
4. Configure the max age timer
system-view —
Optional
stp timer forward-delay time
stp timer hello time
stp timer max-age time
1500 centiseconds (15 seconds)
by default
Optional
200 centiseconds (2 seconds) by
default
Optional
2000 centiseconds (20 seconds)
by default
60
Page 68

The settings of hello time, forward delay and max age must meet the following formulae. Otherwise,
network instability occurs frequently.
• 2 × (forward delay – 1 second) ƒ max age
• Max age ƒ 2 × (hello time + 1 second)
HP recommends that you specify the network diameter with the stp bridge-diameter command and let
MSTP automatically calculate optimal settings of these three timers based on the network diameter.
Configuring the timeout factor
The timeout factor is a parameter used to decide the timeout time, as shown in the following formula:
Timeout time = timeout factor × 3 × hello time.
After the network topology is stabilized, each non-root-bridge device forwards configuration BPDUs to the
downstream devices at the interval of hello time to check whether any link is faulty. Typically, if a device
does not receive a BPDU from the upstream device within nine times the hello time, it assumes that the
upstream device has failed and starts a new spanning tree calculation process.
Sometimes a device may fail to receive a BPDU from the upstream device because the upstream device is
busy. A spanning tree calculation that occurs in this case not only is unnecessary, but also wastes the
network resources. In a very stable network, you can avoid such unwanted spanning tree calculations by
setting the timeout factor to 5, 6, or 7.
To configure the timeout factor:
To do... Use the command... Remarks
1. Enter system view
2. Configure the timeout factor of the
device
system-view —
stp timer-factor factor
Configuring the maximum port rate
The maximum rate of a port refers to the maximum number of BPDUs the port can send within each hello
time. The maximum rate of a port is related to the physical status of the port and the network structure.
Make this configuration on the root bridge and on the leaf nodes separately.
To configure the maximum rate of a port or a group of ports:
To do... Use the command... Remarks
1. Enter system view
2. Enter
interface
view or port
group view
Enter Ethernet interface
view, or Layer 2
aggregate interface view
Enter port group view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
Required
3 by default
Required.
Use either command.
3. Configure the maximum rate of the ports
stp transmit-limit limit
Required.
10 by default.
The higher the maximum port rate is, the more BPDUs are sent within each hello time, and the more
system resources are used. By setting an appropriate maximum port rate, you can limit the rate at which
61
Page 69

the port sends BPDUs and prevent MSTP from using excessive network resources when the network
becomes instable. HP recommends that you use the default setting.
Configuring ports as edge ports
If a port directly connects to a user terminal rather than another device or a shared LAN segment, this port
is regarded as an edge port. When a network topology change occurs, an edge port does not cause a
temporary loop. Because a device does not know whether a port is directly connected to a terminal, you
need to manually configure the port to be an edge port. After that, this port can transition rapidly from the
blocked state to the forwarding state without delay.
Make this configuration on the root bridge and on the leaf nodes separately.
To specify a port or a group of ports as edge port or ports:
To do... Use the command... Remarks
1. Enter system view
2. Enter
interface
view or port
group view
3. Configure the current ports as edge ports
Enter Ethernet interface
view, or Layer 2 aggregate
interface view
Enter port group view
With BPDU guard disabled, when a port set as an edge port receives a BPDU from another port, it
becomes a non-edge port again. To restore the edge port, re-enable it.
If a port directly connects to a user terminal, configure it as an edge port and enable BPDU guard for it.
This enables the port to transition to the forwarding state fast while ensuring network security.
Among loop guard, root guard and edge port settings, only one function (whichever is configured the
earliest) can take effect on a port at the same time.
Configuring path costs of ports
If you change the standard that the device uses in calculating the default path costs, you restore the path
costs to the default.
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
stp edged-port enable
Required.
Use either command.
Required.
All ports are non-edge ports
by default.
Path cost is a parameter related to the rate of a port. On an MSTP-enabled device, a port can have
different path costs in different MSTIs. Setting appropriate path costs allows VLAN traffic flows to be
forwarded along different physical links, thus achieving VLAN-based load balancing.
The device can calculate the default path cost automatically. You also have the option of configuring the
path cost for ports.
Make the following configurations on the leaf nodes only.
Specifying a standard that the device uses when calculating the default path cost
Specify a standard for the device to use in automatic calculation for the default path cost. The device
supports the following standards:
• dot1d-1998: The device calculates the default path cost for ports based on IEEE 802.1d-1998.
62
Page 70

• dot1t: The device calculates the default path cost for ports based on IEEE 802.1t.
• legacy: The device calculates the default path cost for ports based on a private standard.
To specify a standard for the device to use when calculating the default path cost:
To do... Use the command... Remarks
1. Enter system view
2. Specify a standard for the
device to use when
calculating the default path
costs of its ports
system-view —
stp pathcost-standard
{ dot1d-1998 | dot1t | legacy }
Required
Table 13 shows the mappings between the link speed and the path cost.
Table 13 Mappings between the link speed and the path cost
Path cost
Link speed Port type
0 — 65,535 200,000,000 200,000
Single Port
Aggregate interface
containing 2 selected
ports
10 Mbps
Aggregate interface
containing 3 selected
ports
Aggregate interface
containing 4 selected
ports
IEEE
802.1d-1998
100
IEEE 802.1t Private standard
2,000,000 2,000
1,000,000 1,800
666,666 1,600
500,000 1,400
100 Mbps
1000 Mbps
Single Port
Aggregate interface
containing 2 selected
ports
Aggregate interface
containing 3 selected
ports
Aggregate interface
containing 4 selected
ports
Single Port
Aggregate interface
containing 2 selected
ports
Aggregate interface
containing 3 selected
ports
200,000 200
100,000 180
19
66,666 160
50,000 140
20,000 20
10,000 18
4
6666 16
63
Page 71

Path cost
Link speed Port type
Aggregate interface
containing 4 selected
ports
IEEE
802.1d-1998
IEEE 802.1t Private standard
5000 14
Single Port
Aggregate interface
containing 2 selected
ports
10 Gbps
Aggregate interface
containing 3 selected
ports
Aggregate interface
containing 4 selected
ports
When calculating path cost for an aggregate interface, IEEE 802.1d-1998 does not take into account the
number of selected ports in its aggregation group as IEEE 802.1t does. The calculation formula of IEEE
802.1t is: Path Cost = 200,000,000/link speed (in 100 kbps), where link speed is the sum of the link
speed values of the selected ports in the aggregation group.
Configuring path costs of ports
When the path cost of a port changes, MSTP re-calculates the role of the port and initiates a state
transition.
To configure the path cost of ports:
To do... Use the command... Remarks
2000 2
1000 1
2
666 1
500 1
1. Enter system view
2. Enter
interface
view or port
group view
3. Configure the path cost of the ports
Configuration example
# Specify that the device use IEEE 802.1d-1998 to calculate the default path costs of its ports.
<Sysname> system-view
[Sysname] stp pathcost-standard dot1d-1998
# Set the path cost of GigabitEthernet 4/1/3 on MSTI 2 to 200.
<Sysname> system-view
[[Sysname] interface gigabitethernet 4/1/3
[Sysname-GigabitEthernet4/1/3] stp instance 2 cost 200
Enter Ethernet interface
view, or Layer 2
aggregate interface view
Enter port group view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
stp [ instance instance-id ]
cost cost
64
Required.
Use either command.
Required.
By default, MSTP
automatically calculates the
path cost of each port.
Page 72

Configuring port priority
The priority of a port is an important factor in determining whether the port can be elected as the root port
of a device. If all other conditions are the same, the port with the highest priority is elected as the root
port.
On an MSTP-enabled device, a port can have different priorities in different MSTIs, and the same port
can play different roles in different MSTIs, so that data of different VLANs can be propagated along
different physical paths, thus implementing per-VLAN load balancing. Set port priority values based on
the actual networking requirements.
Make this configuration on the leaf nodes only.
To configure the priority of a port or a group of ports:
To do... Use the command... Remarks
1. Enter system view
2. Enter
interface
view or port
group view
3. Configure the port priority
Enter Ethernet interface
view, or Layer 2
aggregate interface view
Enter port group view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
stp [ instance instance-id ]
port priority priority
When the priority of a port is changed, MSTP re-calculates the role of the port and initiate a state
transition.
Generally, a lower priority value indicates a higher priority. If you configure the same priority value for
all ports on a device, the specific priority of a port depends on the index number of the port. A lower
index number means a higher priority. Changing the priority of a port triggers a new spanning tree
calculation process.
Configuring the link type of ports
A point-to-point link is a link directly connecting two devices. If the two ports across a point-to-point link
are root ports or designated ports, the ports can rapidly transition to the forwarding state after a
proposal-agreement handshake process.
Required.
Use either command.
Required.
128 for all ports by default.
Make this configuration on the root bridge and on the leaf nodes separately.
To configure the link type of a port or a group of ports:
To do... Use the command... Remarks
1. Enter system view
Enter Ethernet
2. Enter
interface
view or port
group view
interface view, or
Layer 2 aggregate
interface view
Enter port group view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
65
Required.
Use either command.
Page 73

To do... Use the command... Remarks
Required.
3. Configure the link type of ports
A Layer 2 aggregate interface can be configured to connect to a point-to-point link. If a port works in
auto-negotiation mode and the negotiation result is full duplex, this port can be configured as connecting
to a point-to-point link.
If a port is configured as connecting to a point-to-point link, the setting takes effect for the port in all MSTIs.
If the physical link to which the port connects is not a point-to-point link and you force it to be a
point-to-point link by configuration, the configuration may incur a temporary loop.
stp point-to-point { auto |
force-false | force-true }
auto by default, namely, the
port automatically detects
whether its link is point-to-point.
Configuring the mode a port uses to recognize/send MSTP packets
A port can receive/send MSTP packets of two formats:
• dot1s: 802.1s-compliant standard format, and
• legacy: Compatible format
By default, the packet format recognition mode of a port is auto, namely the port automatically
distinguishes the two MSTP packet formats, and determines the format of packets it sends based on the
recognized format.
Configure the MSTP packet format on a port. After the configuration, when working in MSTP mode, the
port sends and receives only MSTP packets of the format you have configured to communicate with
devices that send packets of the same format.
Make this configuration on the root bridge and on the leaf nodes separately.
66
Page 74

To configure the MSTP packet format to be supported on a port or a group of ports:
To do... Use the command... Remarks
1. Enter system view
Enter Ethernet interface
2. Enter
interface
view or port
group view
3. Configure the mode the port uses to
recognize/send MSTP packets
view, or Layer 2
aggregate interface
view
Enter port group view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
stp compliance { auto | dot1s
| legacy }
Required.
Use either command.
Required.
auto by default.
MSTP provides the MSTP packet format incompatibility guard function. In MSTP mode, if a port is
configured to recognize/send MSTP packets in a mode other than auto, and receives a packet in a
format different from the specified type, the port becomes a designated port and remains in the
discarding state to prevent the occurrence of a loop.
MSTP provides the MSTP packet format frequent change guard function. If a port receives MSTP packets
of different formats frequently, this means that the MSTP packet format configuration contains errors. In
this case, if the port is working in MSTP mode, it is disabled for protection. Those ports closed thereby
can be restored only by the network administrators.
Enabling the output of port state transition information
In a large-scale, MSTP-enabled network, there are a large number of MSTIs, so ports may frequently
transition from one state to another. In this situation, you can enable devices to output the port state
transition information of all MSTIs or the specified MSTI so as to monitor the port states in real time.
Make this configuration on the root bridge and on the leaf nodes separately.
To enable output of port state transition information:
To do... Use the command... Remarks
1. Enter system view
2. Enable output of port state
transition information
system-view —
stp port-log { all | instance
instance-id }
Enabling the MSTP feature
You must enable MSTP for the device before any other MSTP-related configurations can take effect.
Make this configuration on the root bridge and on the leaf nodes separately.
To enable the MSTP feature:
To do... Use the command... Remarks
1. Enter system view
Required
system-view —
2. Enable the MSTP feature globally
stp enable Required.
67
Page 75

To do... Use the command... Remarks
Enter Ethernet
3. Enter
interface
view or port
group view
4. Enable the MSTP feature for the
ports
interface view, or
Layer 2 aggregate
interface view
Enter port group
view
To control MSTP flexibly, use the undo stp enable command to disable the MSTP feature for certain ports
so that they do not take part in spanning tree calculation and, thus, save the CPU resources of the device.
Performing mCheck
MSTP has three working modes: STP compatible mode, RSTP mode, and MSTP mode.
If a port on a device running MSTP (or RSTP) connects to a device running STP, this port automatically
migrates to the STP-compatible mode. However, it is not able to migrate automatically back to the MSTP
(or RSTP) mode, but remains working in the STP-compatible mode under the following circumstances:
interface interface-type
interface-number
port-group manual
port-group-name
stp enable
Required.
Use either command.
Optional.
By default, MSTP is enabled for
all ports after it is enabled for
the device globally.
• The device running STP is shut down or removed.
• The device running STP migrates to the MSTP (or RSTP) mode.
By then, you can perform an mCheck operation to force the port to migrate to the MSTP (or RSTP) mode.
Perform mCheck on a port through the following two approaches, which lead to the same result.
Performing mCheck globally
To perform global mCheck:
To do... Use the command... Remarks
1. Enter system view
2. Perform mCheck
Performing mCheck in interface view
To perform mCheck in interface view:
To do... Use the command... Remarks
1. Enter system view
2. Enter Ethernet interface view, or Layer
2 aggregate interface view
system-view —
stp mcheck Required
system-view —
interface interface-type
interface-number
—
3. Perform mCheck
stp mcheck Required
An mCheck operation takes effect on a device only when MSTP operates in RSTP or MSTP mode.
68
Page 76

Configuring digest snooping
With the digest snooping feature enabled, comparison of configuration digest is not needed for
in-the-same-region check, so the VLAN-to-instance mappings must be the same on associated ports.
With global digest snooping enabled, modification of VLAN-to-instance mappings and removing of the
current region configuration using the undo stp region-configuration command are not allowed. You can
only modify the region name and revision level.
You must enable digest snooping both globally and on associated ports to make it take effect. HP
recommends that you enable digest snooping on all associated ports first and then globally, thus making
the configuration take effect on all configured ports and reducing impact on the network.
HP recommends that you do not enable digest snooping on MST region edge ports, thus avoiding loops.
HP recommends that you enable digest snooping first and then MSTP. Do not configure digest snooping
when the network works well, thus avoiding traffic interruption.
As defined in IEEE 802.1s, interconnected devices are in the same region only when the MST
region-related configurations (region name, revision level, VLAN-to-instance mappings) on them are
identical. An MSTP-enabled device identifies devices in the same MST region by checking the
configuration ID in BPDU packets. The configuration ID includes the region name, revision level,
configuration digest that is in 16-byte length and is the result calculated via the HMAC-MD5 algorithm
based on VLAN-to-instance mappings.
Since MSTP implementations vary with vendors, the configuration digests calculated using private keys is
different. Hence, different vendors’ devices in the same MST region cannot communicate with each other.
Enabling the digest snooping feature on the port connecting the local device to a third-party device in the
same MST region can make the two devices communicate with each other.
Before enabling digest snooping, ensure that associated devices of different vendors are connected and
run MSTP.
Configuring the digest snooping feature
You can enable digest snooping only on a device that is connected to a third-party device that uses its
private key to calculate the configuration digest.
To configure digest snooping:
To do... Use the command... Remarks
1. Enter system view
Enter Ethernet
2. Enter
interface
view or port
group view
3. Enable digest snooping on the
interface or port group
interface view, or
Layer 2 aggregate
interface view
Enter port group
view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
stp config-digest-snooping
Required.
Use either command.
Required.
Not enabled by default.
4. Return to system view
5. Enable global digest snooping
quit —
stp config-digest-snooping
69
Required.
Not enabled by default.
Page 77

Digest snooping configuration example
1. Network requirements
As shown in Figure 19:
• Ro
uter A and Router B connect to Router C, which is a third-party device. All these devices are in the
same region.
• Enable digest snooping on Router A’s and Router B’s ports that connect Router C, so that the three
devices can communicate with one another.
Figure 19 Digest snooping configuration
MST region
GE4/1/1
Router A Router B
2. Configuration procedure
Router C
(Root bridge)
GE4/1/1 GE4/1/2
GE4/1/2
GE4/1/2
GE4/1/1
Root port
Designated port
Blocked port
Normal link
Blocked link
# Enable digest snooping on GigabitEthernet 4/1/1 of Router A and enable global digest snooping on
Router A.
<RouterA> system-view
[RouterA] interface gigabitethernet 4/1/1
[RouterA-GigabitEthernet4/1/1] stp config-digest-snooping
[RouterA-GigabitEthernet4/1/1] quit
[RouterA] stp config-digest-snooping
# Enable digest snooping on GigabitEthernet 4/1/1 of Router B and enable global digest snooping on
Router B.
<RouterB> system-view
[RouterB] interface gigabitethernet 4/1/1
[RouterB-GigabitEthernet4/1/1] stp config-digest-snooping
[RouterB-GigabitEthernet4/1/1] quit
[RouterB] stp config-digest-snooping
Configuring no agreement check
In RSTP and MSTP, two types of messages are used for rapid state transition on designated ports:
• Proposal: sent by designated ports to request rapid transition
• Agreement: used to acknowledge rapid transition requests
70
Page 78

Both RSTP and MSTP devices can perform rapid transition on a designated port only when the port
receives an agreement packet from the downstream device. The differences between RSTP and MSTP
devices are:
• For MSTP, the downstream device’s root port sends an agreement packet only after it receives an
agreement packet from the upstream device.
• For RSTP, the downstream device sends an agreement packet regardless of whether an agreement
packet from the upstream device is received.
Figure 20 shows the rapid state transition
mechanism on MSTP designated ports.
Figure 20 Rapid state transition of an MSTP designated port
Figure 21 shows rapid state transition of an RSTP designated port.
Figure 21 Rapid state transition of an RSTP designated port
If the upstream device is a third-party device, the rapid state transition implementation may be limited. For
example, when the upstream device uses a rapid transition mechanism similar to that of RSTP, and the
downstream device adopts MSTP and does not work in RSTP mode, the root port on the downstream
device receives no agreement packet from the upstream device and thus sends no agreement packets to
the upstream device. As a result, the designated port of the upstream device fails to transit rapidly and
can only change to the forwarding state after a period twice the forward delay.
In this case, enable the no agreement check feature on the downstream device’s port to enable the
designated port of the upstream device to transit its state rapidly.
71
Page 79

Configuration Prerequisites
• A device is connected to a third-party upstream device supporting MSTP via a point-to-point link.
• Configure the same region name, revision level and VLAN-to-instance mappings on the two devices,
thus assigning them to the same region.
Configuring the no agreement check function
To make the no agreement check feature take effect, enable it on the root port.
To configure no agreement check:
To do... Use the command... Remarks
1. Enter system view
Enter Ethernet interface
2. Enter
interface or
port group
view
3. Enable no agreement check
view, or Layer 2
aggregate interface
view
Enter port group view
No agreement check configuration example
1. Network requirements
As shown in Figure 22:
• R
outer A connects to Router B, a third-party device that has different MSTP implementation. Both
devices are in the same region.
• Router B is the regional root bridge, and Router A is the downstream device.
Figure 22 No agreement check configuration
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
stp no-agreement-check
Required.
Use either command.
Required.
Disabled by default.
2. Configuration procedure
# Enable no agreement check on GigabitEthernet 4/1/1 of Router A.
<RouterA> system-view
[RouterA] interface gigabitethernet 4/1/1
[RouterA-GigabitEthernet4/1/1] stp no-agreement-check
Configuring protection functions
An MSTP-enabled device supports the following protection functions:
• BPDU guard
72
Page 80

• Root guard
• Loop guard
• TC-BPDU guard
• BPDU drop
Configuration prerequisites
MSTP has been correctly configured on the device.
Enabling BPDU guard
For access layer devices, the access ports generally connect directly with user terminals (such as PCs) or
file servers. In this case, the access ports are configured as edge ports to allow rapid transition. When
these ports receive configuration BPDUs, the system automatically sets these ports as non-edge ports and
starts a new spanning tree calculation process. This causes a change of network topology. Under normal
conditions, these ports should not receive configuration BPDUs. However, if someone forges configuration
BPDUs maliciously to attack the devices, the network becomes instable.
MSTP provides the BPDU guard function to protect the system against such attacks. With the BPDU guard
function enabled on the devices, when edge ports receive configuration BPDUs, MSTP closes these ports
and notifies the NMS that these ports have been closed by MSTP. Those ports closed thereby are
re-activated by the device after a detection interval. For more information about this detection interval,
see Fundamentals Configuration Guide.
Make this configuration on a device with edge ports configured.
To enable BPDU guard:
To do... Use the command... Remarks
1. Enter system view
2. Enable the BPDU guard
function for the device
BPDU guard does not take effect on loopback test-enabled ports. For more information about loopback
test, see Interface Configuration Guide.
Enabling Root guard
The root bridge and secondary root bridge of a spanning tree should be located in the same MST region.
Especially for the CIST, the root bridge and secondary root bridge are generally put in a high-bandwidth
core region during network design. However, due to possible configuration errors or malicious attacks in
the network, the legal root bridge may receive a configuration BPDU with a higher priority. In this case,
the current legal root bridge is superseded by another device, causing an undesired change of the
network topology. As a result, the traffic that should go over high-speed links is switched to low-speed
links, resulting in network congestion.
To prevent this situation from happening, MSTP provides the root guard function. If the root guard
function is enabled on a port of a root bridge, this port keeps playing the role of designated port on all
MSTIs. Once this port receives a configuration BPDU with a higher priority from an MSTI, it immediately
sets that port to the listening state in the MSTI, without forwarding the packet (this is equivalent to
disconnecting the link connected with this port in the MSTI). If the port receives no BPDUs with a higher
priority within twice the forwarding delay, it reverts to its original state.
system-view —
stp bpdu-protection
Required
Disabled by default
Make this configuration on a designated port.
73
Page 81

To enable root guard:
To do... Use the command... Remarks
1. Enter system view
2. Enter
interface
view or port
group view
3. Enable the root guard function for the
ports
Among loop guard, root guard and edge port settings, only one function (whichever is configured the
earliest) can take effect on a port at the same time.
Enabling Loop guard
By keeping receiving BPDUs from the upstream device, a device can maintain the state of the root port
and blocked ports. However, due to link congestion or unidirectional link failures, these ports may fail to
receive BPDUs from the upstream devices. In this case, the device reselects the port roles: Those ports in
forwarding state that failed to receive upstream BPDUs become designated ports, and the blocked ports
transition to the forwarding state, resulting in loops in the switched network. The loop guard function can
suppress the occurrence of such loops.
The initial state of a loop guard-enabled port is discarding in every MSTI. When the port receives BPDUs,
the state transition is normal. Otherwise, it stays in the discarding state, thus avoiding the occurrence of
loops.
Enter Ethernet interface
view, or Layer 2
aggregate interface view
Enter port group view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
stp root-protection
Required.
Use either command.
Required.
Disabled by default.
Make this configuration on the root port and alternate ports of a device.
To enable loop guard:
To do... Use the command... Remarks
1. Enter system view
2. Enter
interface
view or port
group view
3. Enable the loop guard function for the ports
Do not enable loop guard on a port connecting user terminals. Otherwise, the port stays in the discarding
state in all MSTIs because it cannot receive BPDUs.
Among loop guard, root guard and edge port settings, only one function (whichever is configured the
earliest) can take effect on a port at the same time.
Enabling TC-BPDU guard
When receiving TC BPDUs (the BPDUs used to notify topology changes), a switch flushes its forwarding
address entries. If someone forges TC-BPDUs to attack the switch, the switch receives a large number of
TC-BPDUs within a short time and is busy with forwarding address entry flushing. This affects network
stability.
Enter Ethernet interface view,
or Layer 2 aggregate
interface view
Enter port group view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
stp loop-protection
Required.
Use either command.
Required.
Disabled by default.
74
Page 82

With the TC-BPDU guard function, set the maximum number of immediate forwarding address entry
flushes that the switch can perform within a certain period of time after receiving the first TC-BPDU. For
TC-BPDUs received in excess of the limit, the switch performs forwarding address entry flush only when
the time period expires. This prevents frequent flushing of forwarding address entries.
To enable TC-BPDU guard:
To do... Use the command... Remarks
4. Enter system view
5. Enable the TC-BPDU guard function
6. Configure the maximum number of
forwarding address entry flushes that the
device can perform within a specific time
period after it receives the first TC-BPDU
system-view —
stp tc-protection enable
stp tc-protection threshold
number
Optional
Enabled by default
Optional
6 by default
NOTE:
HP recommends that you do not disable this feature.
Table 14 Displaying and maintaining MSTP
To do... Use the command... Remarks
Display information about abnormally
blocked ports
Display BPDU statistics on ports
Display information about ports blocked
by STP protection functions
display stp abnormal-port [ | { begin |
exclude | include } regular-expression ]
display stp bpdu-statistics [ interface
interface-type interface-number [ instance
instance-id ] ] [ | { begin | exclude |
include } regular-expression ]
display stp down-port [ | { begin |
exclude | include } regular-expression ]
Available in any
view
Available in any
view
Available in any
view
Display the historical information of port
role calculation for the specified MSTI or
all MSTIs (on a centralized device)
Display the historical information of port
role calculation for the specified MSTI or
all MSTIs (on a distributed device)
Display the statistics of TC/TCN BPDUs
sent and received by all ports in the
specified MSTI or all MSTIs (on a
centralized device)
Display the statistics of TC/TCN BPDUs
sent and received by all ports in the
specified MSTI or all MSTIs (on a
distributed device)
Display the status and statistics of MSTP
(on a centralized device)
display stp [ instance instance-id ] history
[ | { begin | exclude | include }
regular-expression ]
display stp [ instance instance-id ] history
[ slot slot-number ] [ | { begin | exclude |
include } regular-expression ]
display stp [ instance instance-id ] tc [ |
{ begin | exclude | include }
regular-expression ]
display stp [ instance instance-id ] tc [ slot
slot-number ] [ | { begin | exclude |
include } regular-expression ]
display stp [ instance instance-id ]
[ interface interface-list ] [ brief ] [ |
{ begin | exclude | include }
regular-expression ]
75
Available in any
view
Available in any
view
Available in any
view
Available in any
view
Available in any
view
Page 83

To do... Use the command... Remarks
display stp [ instance instance-id ]
Display the status and statistics of MSTP
(on a distributed device)
[ interface interface-list | slot
slot-number ] [ brief ] [ | { begin |
exclude | include } regular-expression ]
Available in any
view
Display the MST region configuration
information that has taken effect
Display the root bridge information of all
MSTIs
Clear the statistics of MSTP reset stp [ interface interface-list ]
display stp region-configuration [ |
{ begin | exclude | include }
regular-expression ]
display stp root [ | { begin | exclude |
include } regular-expression ]
MSTP configuration example
Network requirements
As shown in Figure 23:
• All routers on the network are in the same MST region. Router A and Router B work on the
distribution layer, while Router C and Router D work on the access layer.
• Configure MSTP so that packets of different VLANs are forwarded along different spanning trees:
Packets of VLAN 10 are forwarded along MSTI 1, those of VLAN 30 are forwarded along MSTI 3,
those of VLAN 40 are forwarded along MSTI 4, and those of VLAN 20 are forwarded along MSTI
0.
• VLAN 10 and VLAN 30 are terminated on the distribution layer devices, and VLAN 40 is terminated
on the access layer devices, so the root bridges of MSTI 1 and MSTI 3 are Router A and Router B,
respectively, while the root bridge of MSTI 4 is Router C.
Available in any
view
Available in any
view
Available in user
view
Figure 23 Network diagram for MSTP configuration
76
Page 84

Configuration procedure
1. VLAN and VLAN member port configuration
Create VLAN 10, VLAN 20, and VLAN 30 on Router A and Router B, respectively, create VLAN 10,
VLAN 20, and VLAN 40 on Router C, and create VLAN 20, VLAN 30, and VLAN 40 on Router D.
Configure the ports on these routers as trunk ports and assign them to related VLANs. The detailed
configuration procedure is omitted.
2. Configuration on Router A
# Enter MST region view, configure the MST region name as example, map VLAN 10, VLAN 30, and
VLAN 40 to MSTI 1, MSTI 3, and MSTI 4, respectively, and configure the revision level of the MST region
as 0.
<RouterA> system-view
[RouterA] stp region-configuration
[RouterA-mst-region] region-name example
[RouterA-mst-region] instance 1 vlan 10
[RouterA-mst-region] instance 3 vlan 30
[RouterA-mst-region] instance 4 vlan 40
[RouterA-mst-region] revision-level 0
# Activate MST region configuration.
[RouterA-mst-region] active region-configuration
[RouterA-mst-region] quit
# Specify the current Router as the root bridge of MSTI 1.
[RouterA] stp instance 1 root primary
# Enable MSTP globally.
[RouterA] stp enable
3. Configuration on Router B
# Enter MST region view, configure the MST region name as example, map VLAN 10, VLAN 30, and
VLAN 40 to MSTI 1, MSTI 3, and MSTI 4, respectively, and configure the revision level of the MST region
as 0.
<RouterB> system-view
[RouterB] stp region-configuration
[RouterB-mst-region] region-name example
[RouterB-mst-region] instance 1 vlan 10
[RouterB-mst-region] instance 3 vlan 30
[RouterB-mst-region] instance 4 vlan 40
[RouterB-mst-region] revision-level 0
# Activate MST region configuration.
[RouterB-mst-region] active region-configuration
[RouterB-mst-region] quit
# Specify the current router as the root bridge of MSTI 3.
[RouterB] stp instance 3 root primary
# Enable MSTP globally.
[RouterB] stp enable
77
Page 85

4.
Configuration on Router C.
# Enter MST region view, configure the MST region name as example, map VLAN 10, VLAN 30, and
VLAN 40 to MSTI 1, MSTI 3, and MSTI 4, respectively, and configure the revision level of the MST region
as 0.
<RouterC> system-view
[RouterC] stp region-configuration
[RouterC-mst-region] region-name example
[RouterC-mst-region] instance 1 vlan 10
[RouterC-mst-region] instance 3 vlan 30
[RouterC-mst-region] instance 4 vlan 40
[RouterC-mst-region] revision-level 0
# Activate MST region configuration.
[RouterC-mst-region] active region-configuration
[RouterC-mst-region] quit
# Specify the current router as the root bridge of MSTI 4.
[RouterC] stp instance 4 root primary
# Enable MSTP globally.
[RouterC] stp enable
5. Configuration on Router D.
# Enter MST region view, configure the MST region name as example, map VLAN 10, VLAN 30, and
VLAN 40 to MSTI 1, MSTI 3, and MSTI 4, respectively, and configure the revision level of the MST region
as 0.
<RouterD> system-view
[RouterD] stp region-configuration
[RouterD-mst-region] region-name example
[RouterD-mst-region] instance 1 vlan 10
[RouterD-mst-region] instance 3 vlan 30
[RouterD-mst-region] instance 4 vlan 40
[RouterD-mst-region] revision-level 0
# Activate MST region configuration.
[RouterD-mst-region] active region-configuration
[RouterD-mst-region] quit
# Enable MSTP globally.
[RouterD] stp enable
6. Verifying the configurations
Use the display stp brief command to display brief spanning tree information on each router after the
network is stable.
# Display brief spanning tree information on Router A.
[RouterA] display stp brief
MSTID Port Role STP State Protection
0 GigabitEthernet4/1/1 ALTE DISCARDING NONE
0 GigabitEthernet4/1/2 DESI FORWARDING NONE
0 GigabitEthernet4/1/3 ROOT FORWARDING NONE
1 GigabitEthernet4/1/1 DESI FORWARDING NONE
78
Page 86

1 GigabitEthernet4/1/3 DESI FORWARDING NONE
3 GigabitEthernet4/1/2 DESI FORWARDING NONE
3 GigabitEthernet4/1/3 ROOT FORWARDING NONE
# Display brief spanning tree information on Router B.
[RouterB] display stp brief
MSTID Port Role STP State Protection
0 GigabitEthernet4/1/1 DESI FORWARDING NONE
0 GigabitEthernet4/1/2 DESI FORWARDING NONE
0 GigabitEthernet4/1/3 DESI FORWARDING NONE
1 GigabitEthernet4/1/2 DESI FORWARDING NONE
1 GigabitEthernet4/1/3 ROOT FORWARDING NONE
3 GigabitEthernet4/1/1 DESI FORWARDING NONE
3 GigabitEthernet4/1/3 DESI FORWARDING NONE
# Display brief spanning tree information on Router C.
[RouterC] display stp brief
MSTID Port Role STP State Protection
0 GigabitEthernet4/1/1 DESI FORWARDING NONE
0 GigabitEthernet4/1/2 ROOT FORWARDING NONE
0 GigabitEthernet4/1/3 DESI FORWARDING NONE
1 GigabitEthernet4/1/1 ROOT FORWARDING NONE
1 GigabitEthernet4/1/2 ALTE DISCARDING NONE
4 GigabitEthernet4/1/3 DESI FORWARDING NONE
# Display brief spanning tree information on Router D.
[RouterD] display stp brief
MSTID Port Role STP State Protection
0 GigabitEthernet4/1/1 ROOT FORWARDING NONE
0 GigabitEthernet4/1/2 ALTE DISCARDING NONE
0 GigabitEthernet4/1/3 ALTE DISCARDING NONE
3 GigabitEthernet4/1/1 ROOT FORWARDING NONE
3 GigabitEthernet4/1/2 ALTE DISCARDING NONE
4 GigabitEthernet4/1/3 ROOT FORWARDING NONE
Based on the above information, draw the MSTI mapped to each VLAN, as shown in Figure 24.
79
Page 87
Figure 24 MSTIs mapped to different VLANs
80
Page 88
BPDU tunneling configuration
The SAP cards support this feature only when they work in Layer 2 mode.
As a Layer 2 tunneling technology, BPDU tunneling enables Layer 2 protocol packets from geographically
dispersed customer networks to be transparently transmitted over specific tunnels across a service
provider network.
Dedicated lines are used in a service provider network to build user-specific Layer 2 networks. As a result,
a user network is broken down into parts located at different sides of the service provider network. As
shown in Figure 25, User
User A’s network is divided into network 1 and network 2, which are connected by the service provider
network. When a Layer 2 protocol (for example, STP) runs on both networks, the Layer 2 protocol packets
must be transmitted over the service provider network to implement Layer 2 protocol calculation (for
example, spanning tree calculation). When receiving a Layer 2 protocol packet, the PE cannot determine
whether the packet is from the user network or the service provider network, and must deliver the packet
to the CPU for processing. In this case, the Layer 2 protocol calculation in User A’s network is mixed with
that in the service provider network, and the user network cannot implement independent Layer 2
protocol calculation.
A has two devices: CE 1 and CE 2, and both services belong to VLAN 100.
Figure 25 BPDU tunneling application scenario
With BPDU tunneling, Layer 2 protocol packets from customer networks can be transparently transmitted
over the service provider network:
1. After receiving a Layer 2 protocol packet from CE 1, PE 1 encapsulates the packet, replaces its
destination MAC address with a specific multicast MAC address, and forwards the packet to the
service provider network.
2. The encapsulated Layer 2 protocol packet (called bridge protocol data unit, BPDU) is forwarded to
PE 2 at the other end of the service provider network, which de-encapsulates the packet, restores the
original destination MAC address of the packet, and then sends the packet to CE 2.
HP routers support BPDU tunneling for the following protocols:
• CDP
• DLDP
• EOAM
• GVRP
81
Page 89

• HGMP
• LACP
• LLDP
• PAGP
• PVST
• STP
• UDLD
• VTP
BPDU tunneling implementation
The BPDU tunneling implementations for different protocols are all similar. This section describes how
BPDU tunneling is implemented by taking the STP as an example.
The term STP in this document is in a broad sense. It includes STP, RSTP, and MSTP.
STP calculates the topology of a network by transmitting BPDUs among devices in the network. For more
information, see the chapter “MSTP configuration.”
To avoid loops in your network, enable STP on your routers. When the topology changes at one side of
the customer network, the routers at this side of the customer network send BPDUs to routers on the other
side of the customer network to ensure consistent spanning tree calculation in the entire customer network.
However, because BPDUs are Layer 2 multicast frames, all STP-enabled routers, both in the customer
network and in the service provider network, can receive and process these BPDUs. In this case, neither
the service provider network nor the customer network can correctly calculate its independent spanning
tree.
To allow each network to calculate an independent spanning tree with STP, BPDU tunneling was
introduced.
BPDU tunneling delivers the following benefits:
• BPDUs can be transparently transmitted. BPDUs of the same customer network can be broadcast in a
specific VLAN across the service provider network, so that the geographically dispersed networks of
the same customer can implement consistent spanning tree calculation across the service provider
network.
• BPDUs of different customer networks can be confined within different VLANs for transmission on the
service provider network. Thus, each customer network can perform independent spanning tree
calculation.
Figure 26 Network diagram for BPDU tunneling implementation
82
Page 90

As shown in Figure 26, the upper part is the service provider network (ISP network), and the lower part
represents two geographically dispersed segments of a customer network: User A network 1 and User A
network 2. Enabling the BPDU tunneling function on the edge devices (PE 1 and PE 2) in the service
provider network allows BPDUs of User A network 1 and User A network 2 to be transparently transmitted
in the service provider network, thus ensuring consistent spanning tree calculation throughout User A
network, without affecting the spanning tree calculation of the service provider network.
Assume a BPDU is sent from User A network 1 to User A network 2:
1. At the ingress of the service provider network, PE 1 changes the destination MAC address of the
BPDU from 0x0180-C200-0000 to a special multicast MAC address, 0x010F-E200-0003 (the
default multicast MAC address) for example. In the service provider network, the modified BPDU is
forwarded as a data packet in the VLAN assigned to User A.
2. At the egress of the service provider network, PE 2 recognizes the BPDU with the destination MAC
address 0x010F-E200-0003, restores its original destination MAC address 0x0180-C200-0000,
and then sends the BPDU to CE 2.
Make sure, through configuration, that the VLAN tags carried in BPDUs are neither changed nor removed
during the transparent transmission in the service provider network. Otherwise, the devices in the service
provider network will fail to transparently transmit the customer network BPDUs correctly.
Configuring BPDU tunneling
Configuration prerequisites
• Before configuring BPDU tunneling for a protocol, enable the protocol in the customer network first.
• Assign the port on which you want to enable BPDU tunneling on the PE device and the connected
port on the CE device to the same VLAN.
• Configure ports connecting network devices in the service provider network as trunk ports allowing
packets of any VLAN to pass through.
Enabling BPDU tunneling
Enable BPDU tunneling for different protocols in different views.
Settings made in Layer 2 Ethernet interface view or Layer 2 aggregate interface view take effect only on
the current port. Settings made in port group view take effect on all ports in the port group.
Before enabling BPDU tunneling for DLDP, EOAM, GVRP, HGMP, LLDP, or STP on a port, disable the
protocol on the port first. Before enabling BPDU tunneling for PVST on a port, you must also disable STP
and then enable BPDU tunneling for STP on the port first, because PVST is a special STP protocol.
Do not enable BPDU tunneling for DLDP, EOAM, LACP, LLDP, PAGP, or UDLD on the member port of a
Layer 2 aggregation group.
83
Page 91

Enabling BPDU tunneling for a protocol in Layer 2 Ethernet interface view or port group view
To enable BPDU tunneling for a protocol in Ethernet interface view or port group view:
To do... Use the command... Remarks
1. Enter system view
2. Enter
Ethernet
interface
view or
port
group
view
Enter Layer 2
Ethernet interface
view
Enter port group
view
system-view —
interface interface-type
interface-number
port-group manual
port-group-name
Required.
Use either command.
3. Enable BPDU tunneling for a
protocol
bpdu-tunnel dot1q { cdp | dldp |
eoam | gvrp | hgmp | lacp |
lldp | pagp | pvst | stp | udld |
vtp }
Required.
Disabled by default.
Enabling BPDU tunneling for a protocol in Layer 2 aggregate interface view
To enable BPDU tunneling for a protocol in Layer 2 aggregate interface view:
To do… Use the command… Remarks
1. Enter system view
2. Enter Layer 2 aggregate
interface view
3. Enable BPDU tunneling for a
protocol on the Layer 2
aggregate interface
system-view —
interface bridge-aggregation
interface-number
bpdu-tunnel dot1q { cdp | gvrp |
hgmp | pvst | stp | vtp }
—
Required
Disabled by default
Configuring destination multicast MAC address for BPDUs
By default, the destination multicast MAC address for BPDUs is 0x010F-E200-0003. Change it to
0x0100-0CCD-CDD0, 0x0100-0CCD-CDD1 or 0x0100-0CCD-CDD2 through the following
configuration.
To configure destination multicast MAC address for BPDUs:
To do… Use the command… Remarks
4. Enter system view
5. Configure the destination
multicast MAC address for
BPDUs
system-view —
bpdu-tunnel tunnel-dmac
mac-address
Optional
0x010F-E200-0003 by default
For BPDUs to be recognized, the destination multicast MAC addresses configured for BPDU tunneling
must be the same on the edge devices on the service provider network.
84
Page 92
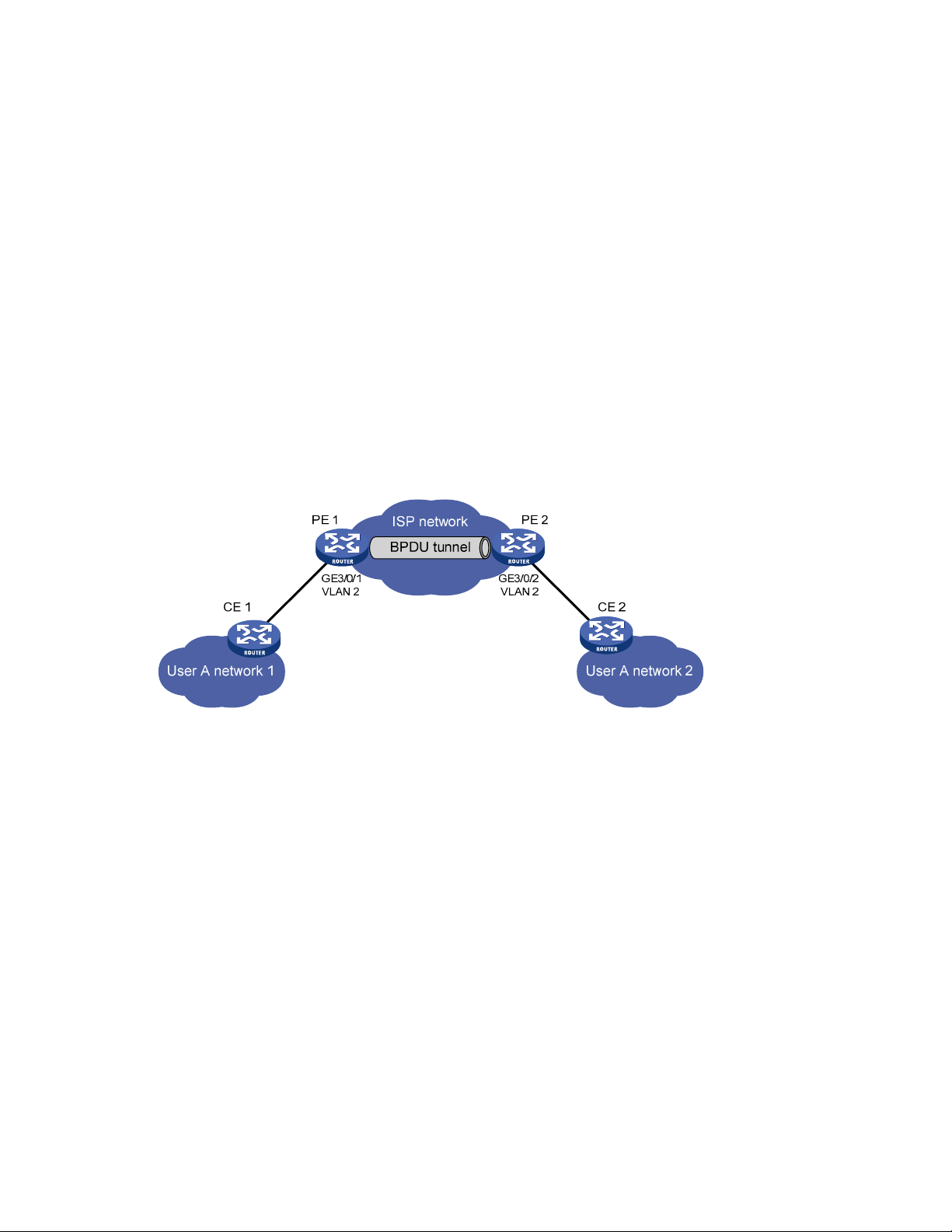
BPDU tunneling configuration examples
BPDU tunneling for STP configuration example
Network requirements
As shown in Figure 27:
• CE 1 and CE 2 are edges devices on the geographically dispersed network of User A. PE 1 and PE
2 are edge devices on the service provider network.
• All ports that connect service provider devices and customer devices are access ports and belong to
VLAN 2. All ports that interconnect service provider devices are trunk ports and allow packets of any
VLAN to pass through.
• MSTP is enabled on User A’s network.
It is required that, after the configuration, CE 1 and CE 2 implement consistent spanning tree calculation
across the service provider network, and that the destination multicast MAC address carried in BPDUs be
0x0100-0CCD-CDD0.
Figure 27 Network diagram for configuring BPDU tunneling for STP
Configuration procedure
1. Configuration on PE 1
# Configure the destination multicast MAC address for BPDUs as 0x0100-0CCD-CDD0.
<PE1> system-view
[PE1] bpdu-tunnel tunnel-dmac 0100-0ccd-cdd0
# Create VLAN 2 and assign GigabitEthernet 3/0/1 to VLAN 2.
[PE1] vlan 2
[PE1-vlan2] quit
[PE1] interface gigabitethernet 3/0/1
[PE1-GigabitEthernet3/0/1] port access vlan 2
# Disable STP on GigabitEthernet 3/0/1, and then enable BPDU tunneling for STP on it.
[PE1-GigabitEthernet3/0/1] undo stp enable
[PE1-GigabitEthernet3/0/1] bpdu-tunnel dot1q stp
2. Configuration on PE 2
# Configure the destination multicast MAC address for BPDUs as 0x0100-0CCD-CDD0.
<PE2> system-view
85
Page 93

[PE2] bpdu-tunnel tunnel-dmac 0100-0ccd-cdd0
# Create VLAN 2 and assign GigabitEthernet 3/0/2 to VLAN 2.
[PE2] vlan 2
[PE2-vlan2] quit
[PE2] interface gigabitethernet 3/0/2
[PE2-GigabitEthernet3/0/2] port access vlan 2
# Disable STP on GigabitEthernet 3/0/2, and then enable BPDU tunneling for STP on it.
[PE2-GigabitEthernet3/0/2] undo stp enable
[PE2-GigabitEthernet3/0/2] bpdu-tunnel dot1q stp
BPDU tunneling for PVST configuration example
Network requirements
As shown in Figure 28:
• CE 1 and CE 2 are edges devices on the geographically dispersed network of User A. PE 1 and PE
2 are edge devices on the service provider network.
• All ports that connect service provider devices and customer devices and those that interconnect
service provider devices are trunk ports and allow packets of any VLAN to pass through.
• PVST is enabled for VLANs 1 through 4094 on User A’s network.
After the configuration, it is required that CE 1 and CE 2 implement consistent PVST calculation across the
service provider network, and that the destination multicast MAC address carried in BPDUs be
0x0100-0CCD-CDD0.
Figure 28 Network diagram for configuring BPDU tunneling for PVST
Configuration procedure
1. Configuration on PE 1
# Configure the destination multicast MAC address for BPDUs as 0x0100-0CCD-CDD0.
<PE1> system-view
[PE1] bpdu-tunnel tunnel-dmac 0100-0ccd-cdd0
# Configure GigabitEthernet 3/0/1 as a trunk port and assign it to all VLANs.
[PE1] interface gigabitethernet 3/0/1
[PE1-GigabitEthernet3/0/1] port link-type trunk
[PE1-GigabitEthernet3/0/1] port trunk permit vlan all
# Disable STP on GigabitEthernet 3/0/1, and then enable BPDU tunneling for STP and PVST on it.
86
Page 94

[PE1-GigabitEthernet3/0/1] undo stp enable
[PE1-GigabitEthernet3/0/1] bpdu-tunnel dot1q stp
[PE1-GigabitEthernet3/0/1] bpdu-tunnel dot1q pvst
2. Configuration on PE 2
# Configure the destination multicast MAC address for BPDUs as 0x0100-0CCD-CDD0.
<PE2> system-view
[PE2] bpdu-tunnel tunnel-dmac 0100-0ccd-cdd0
# Configure GigabitEthernet 3/0/2 as a trunk port and assign it to all VLANs.
[PE2] interface gigabitethernet 3/0/2
[PE2-GigabitEthernet3/0/2] port link-type trunk
[PE2-GigabitEthernet3/0/2] port trunk permit vlan all
# Disable STP on GigabitEthernet 3/0/2, and then enable BPDU tunneling for STP and PVST on it.
[PE2-GigabitEthernet3/0/2] undo stp enable
[PE2-GigabitEthernet3/0/2] bpdu-tunnel dot1q stp
[PE2-GigabitEthernet3/0/2] bpdu-tunnel dot1q pvst
87
Page 95

VLAN configuration
This feature is available on only a SAP interface card working in bridge mode.
Ethernet is a network technology based on the CSMA/CD mechanism. As the medium is shared,
collisions and excessive broadcasts are common on Ethernet networks. To address the issue, VLAN was
introduced to break a LAN down into separate VLANs. VLANs are isolated from each other at Layer 2. A
VLAN is a bridging domain, and all broadcast traffic is contained within it, as shown in Figure 29.
Figure 29 A VLAN diagram
A VLAN is logically divided on an organizational basis rather than on a physical basis. For example, all
workstations and servers used by a particular workgroup can be assigned to the same VLAN, regardless
of their physical locations.
VLAN technology delivers the following benefits:
1. Confining broadcast traffic within individual VLANs. This reduces bandwidth waste and improves
network performance.
2. Improving LAN security. By assigning user groups to different VLANs, isolate them at Layer 2. To
enable communication between VLANs, routers or Layer 3 switches are required.
3. Flexible virtual workgroup creation. As users from the same workgroup can be assigned to the same
VLAN regardless of their physical locations, network construction and maintenance is much easier
and more flexible.
VLAN fundamentals
To enable a network device to identify frames of different VLANs, a VLAN tag field is inserted into the
data link layer encapsulation.
The format of VLAN-tagged frames is defined in IEEE 802.1Q issued by the Institute of IEEE in 1999.
In the header of a traditional Ethernet data frame, the field after the destination MAC address and the
source MAC address is the Type field indicating the upper layer protocol type, as shown in Figure 30.
88
Page 96

Figure 30 The format of a traditional Ethernet frame
IEEE 802.1Q inserts a four-byte VLAN tag after the DA&SA field, as shown in Figure 31.
Figure 31 The position and format of VLAN tag
A VLAN tag comprises the following fields: TPID, priority, CFI, and VLAN ID.
• The 16-bit TPID field with a value of 0x8100 indicates that the frame is VLAN-tagged.
• The 3-bit priority field indicates the 802.1p priority of the frame.
• The 1-bit CFI field specifies whether the MAC addresses are encapsulated in the standard format
when packets are transmitted across different media. A value of 0 indicates that MAC addresses are
encapsulated in the standard format. A value of 1 indicates that MAC addresses are encapsulated
in a non-standard format. The value of the field is 0 by default.
• The 12-bit VLAN ID field identifies the VLAN the frame belongs to. The VLAN ID range is 0 to 4095.
As 0 and 4095 are reserved, a VLAN ID actually ranges from 1 to 4094.
A network device handles an incoming frame depending on whether the frame is VLAN tagged and the
value of the VLAN tag, if any.
The Ethernet II encapsulation format is used here. Besides the Ethernet II encapsulation format, other
encapsulation formats, including 802.2 LLC, 802.2 SNAP, and 802.3 raw, are also supported by
Ethernet. The VLAN tag fields are also added to frames encapsulated in these formats for VLAN
identification.
For a frame with multiple VLAN tags, the router handles it according to its outer-most VLAN tag and
transmits its inner VLAN tags as payload.
VLAN types
Implement VLANs based on the following criteria:
• Port
• MAC address
• Protocol
• IP subnet
• Policy
• Other criteria
This chapter covers port-based VLAN, MAC-based VLAN, protocol-based VLAN, and IP-based VLAN. The
port-based VLAN implementation is the basis of all other VLAN implementations. To use any other VLAN
implementations, you must configure port-based VLAN settings.
89
Page 97

Configure all four types of VLANs on a port at the same time. When determining to which VLAN a packet
passing through the port should be assigned, the router looks up the VLANs in the default order of
MAC-based VLAN, IP-based VLAN, protocol-based VLAN, and port-based VLAN.
Configuring basic VLAN settings
To configure basic VLAN settings:
To do… Use the command… Remarks
1. Enter system view
system-view —
Optional.
Use this command to create VLANs in
bulk.
Required.
By default, only the default VLAN (VLAN
1) exists in the system.
If the specified VLAN does not exist, this
command creates the VLAN first.
Optional.
By default, the VLAN ID is used as the
name of a VLAN. For example, VLAN
0001.
Optional.
By default, the VLAN ID is used as the
description. For example, VLAN 0001.
2. Create VLANs
3. Enter VLAN view
4. Configure a name for the
VLAN
5. Configure the
description of the VLAN
vlan { vlan-id1 [ to vlan-id2 ] |
all }
vlan vlan-id
name text
description text
As the default VLAN, VLAN 1 cannot be created or removed.
You cannot manually create or remove VLANs reserved for special purposes.
You cannot use the undo vlan command to delete dynamic VLANs or VLANs with QoS policies applied.
To remove a control VLAN for a smart link group, control VLAN for an RRPP domain, source VLAN for
port mirroring, or remote probe VLAN for remote port mirroring, remove the configuration from the VLAN
first, and execute the undo vlan command.
After associating an isolate-user-VLAN with a secondary VLAN, you cannot add ports to, remove ports
from, or remove the VLANs. To do that, remove the association first.
Configuring basic settings of a VLAN interface
For hosts of different VLANs to communicate, you must use a router or Layer 3 switch to perform layer 3
forwarding. To achieve this, VLAN interfaces are used.
VLAN interfaces are virtual interfaces used for Layer 3 communication between different VLANs. They do
not exist as physical entities on routers. For each VLAN, create one VLAN interface. Assign the VLAN
interface an IP address and specify it as the gateway of the VLAN to forward traffic destined for an IP
subnet different from that of the VLAN.
90
Page 98

To configure basic settings of a VLAN interface:
To do… Use the command… Remarks
1. Enter system view
system-view —
2. Create a VLAN interface
and enter VLAN interface
view
3. Assign an IP address to the
VLAN interface
4. Configure the description of
the VLAN interface
5. Bring up the VLAN
interface
interface vlan-interface
vlan-interface-id
ip address ip-address
{ mask | mask-length }
[ sub ]
description text
undo shutdown
Required.
If the VLAN interface already exists, you
enter its view directly.
Optional.
By default, a VLAN interface is not assigned
with any IP address.
Optional.
By default, the VLAN interface name is used
as the description. For example,
Vlan-interface1 Interface.
Optional.
By default, a VLAN interface is in the up
state. The VLAN interface is up if one or
more ports in the VLAN is up, and goes
down if all ports in the VLAN go down.
A VLAN interface shut down with the
shutdown command. However, it is in the
DOWN (Administratively) state until you
bring it up, regardless of how the state of
the ports in the VLAN changes.
Before creating a VLAN interface for a VLAN, create the VLAN first.
Port-based VLAN configuration
Port-based VLANs group VLAN members by port. A port forwards traffic for a VLAN only after it is
assigned to the VLAN.
Port link type
Configure the link type of a port as access, trunk, or hybrid. The link types use the following VLAN tag
handling methods:
• An access port belongs to only one VLAN and sends traffic untagged. It is usually used to connect a
terminal device unable to recognize VLAN tagged-packets or when there is no need to separate
different VLAN members. As shown in Figure 32, R
recognize VLAN tagged-packets, and you must configure Router A’s ports that connect to the PCs as
access ports.
• A trunk port can carry multiple VLANs to receive and send traffic for them. Except traffic of the
default VLAN, traffic sent through a trunk port is VLAN tagged. Usually, ports connecting network
devices are configured as trunk ports. As shown in Figure 32, Rou
transmit packets of VLAN 2 and VLAN 3, and you must configure the ports interconnecting Router A
and Router B as trunk ports and assign them to VLAN 2 and VLAN 3.
• Like a trunk port, a hybrid port can carry multiple VLANs to receive and send traffic for them. Unlike
a trunk port, a hybrid port allows traffic of all VLANs to pass through VLAN untagged. Usually,
hybrid ports are configured to connect devices whose support for VLAN tagged-packets you are
uncertain about. As shown in Figure 32, Ro
uter C connects to a small-sized LAN in which some PCs
outer A is connected to common PCs that cannot
ter A and Router B need to
91
Page 99

Figure 32 Network diagram for port link type configuration
Default VLAN
belong to VLAN 2 and other PCs belong to VLAN 3. Configure on Router C the port connecting to
the LAN as a hybrid port to allow packets of VLAN 2 and VLAN 3 to pass through untagged.
By default, VLAN 1 is the default VLAN for all ports. Configure the default VLAN for a port as required.
Use the following guidelines when configuring the default VLAN on a port:
• An access port can join only one VLAN. The VLAN to which the access port belongs is the default
VLAN of the port. To change the default VLAN, assign the port to another VLAN.
• A trunk or hybrid port can join multiple VLANs, and you can configure a default VLAN for the port.
• Use a nonexistent VLAN as the default VLAN for a hybrid or trunk port but not for an access port.
After you remove the VLAN that an access port resides in with the undo vlan command, the default
VLAN of the port changes to VLAN 1. The removal of the VLAN specified as the default VLAN of a
trunk or hybrid port, however, does not affect the default VLAN setting on the port.
Do not set the voice VLAN as the default VLAN of a port in automatic voice VLAN assignment mode. For
information about voice VLAN, see the chapter “Voice VLAN configuration.”
HP recommends that you set the same default VLAN ID for the local and remote ports.
Make sure that a port is assigned to its default VLAN. Otherwise, when the port receives frames tagged
with the default VLAN ID or untagged frames (including protocol packets such as MSTP BPDUs), the port
filters out these frames.
The following table shows how ports of different link types handle frames:
Port type
Actions (in the inbound direction)
Untagged frame Tagged frame
Actions (in the outbound
direction)
• Receive the frame if its
VLAN ID is the same as
Access
Tag the frame with the
default VLAN tag.
the default VLAN ID.
• Drop the frame if its VLAN
ID is different from the
default VLAN ID.
Remove the VLAN tag and send
the frame.
92
Page 100

Port type
Actions (in the inbound direction)
Untagged frame Tagged frame
Trunk
Hybrid
Check whether the
default VLAN is
permitted on the port:
• If yes, tag the frame
with the default
VLAN tag.
• If not, drop the
frame.
• Receive the frame if its
VLAN is carried on the
port.
• Drop the frame if its VLAN
is not carried on the port.
Assigning an access port to a VLAN
Actions (in the outbound
direction)
• Remove the tag and send
the frame if the frame
carries the default VLAN tag
and the port belongs to the
default VLAN.
• Send the frame without
removing the tag if its VLAN
is carried on the port but is
different from the default
one.
Send the frame if its VLAN is
carried on the port. The frame
is sent with the VLAN tag
removed or intact depending
on your configuration with the
port hybrid vlan command. This
is true of the default VLAN.
Assign an access port to a VLAN in VLAN view, interface view (including Ethernet interface view and
Layer 2 aggregate interface view), or port group view.
To assign one or multiple access ports to a VLAN in VLAN view:
To do… Use the command… Remarks
1. Enter system view
2. Enter VLAN view
3. Assign one or a group of
access ports to the current
VLAN
system-view —
Required.
vlan vlan-id
port interface-list
If the specified VLAN does not exist, this
command creates the VLAN first.
Required.
By default, all ports belong to VLAN 1.
To assign an access port (in interface view) or multiple access ports (in port group view) to a VLAN:
To do…
1. Enter system view
2. Enter
interface
view or
Enter Ethernet
interface view
Use the
command…
system-view —
interface
interface-type
interface-number
Remarks
Required.
Use any command.
• The configuration made in Ethernet interface
93
 Loading...
Loading...