Page 1

hidglobal.com
ActivID® Appliance and
®
Zscaler
SAML 2.0 Channel Integration Handbook
Document Version 1.1 | Released | May 2013
Web Security
Page 2

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
2
Table of Contents
1.0 Introduction ..................................................................................................................................................... 3
1.1 Scope of Document .................................................................................................................................... 3
1.2 Prerequisites .............................................................................................................................................. 3
2.0 Zscaler Configuration ..................................................................................................................................... 4
2.1 Procedure 1: Enable SAML on Zscaler ...................................................................................................... 4
2.2 Procedure 2: Configure ActivID IDP in Zscaler .......................................................................................... 5
2.3 Procedure 3: Export ActivID Appliance IDP Certificate .............................................................................. 6
2.4 Procedure 4: Import ActivID Appliance IDP certificate ............................................................................... 8
2.5 Procedure 5: Export Zscaler Metadata ...................................................................................................... 9
2.6 Procedure 6: Modify Zscaler Metadata .................................................................................................... 10
3.0 ActivID Appliance Configuration ................................................................................................................. 11
3.1 Procedure 1: Create SAML Channel ........................................................................................................ 11
3.2 Procedure 2: Import Zscaler Metadata ..................................................................................................... 13
3.3 Procedure 3: Authorize the SAML Channel (Authentication Policies) ..................................................... 15
3.4 Procedure 4: Configure the Identity Provider ........................................................................................... 17
3.5 Procedure 5: Adding a New Authentication Policies Mapping ................................................................. 18
4.0 SAML Channel Authentication: An Overview ............................................................................................ 19
4.1 Prerequisite: Activate Web Soft Token .................................................................................................... 19
4.2 Sample Authentication ............................................................................................................................. 22
Copyright ................................................................................................................................................................. 24
Trademarks ............................................................................................................................................................. 24
Revision History ..................................................................................................................................................... 24
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 3

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
3
1.0 Introduction
The Zscaler® W eb Security solution ena bles organizatio ns to embrace ne w cloud applications and social m edia
technologies, while gaining advanced protection from accidental data loss, malicious attacks, and emerging
threats. Zscaler W eb Security enables organizations to s ecurely enable busines s beyond the corporat e network,
including such capabilities as:
• Advanced Threat Protection
• Cloud Application and Social Media Control
• Anti-Virus and Anti-Spyware
• Dynamic URL Filtering
Providing secure “one prompt” access via a web proxy over existing Int ernet connections requires strong , twofactor authentication to protect and identify users.
The HID® Global I den tity Assurance™ ActivID® Ap pl i ance works with Zscaler solution to pr o vi de vers at il e, s t rong
authentication that is flexible, scalable, and simple to manage.
The ActivID Appliance offers support for multiple authentication methods that are useful for diverse audiences
across a variety of service channels (SAML, RADIUS, etc.), including user name and password, mobile and PC
soft tokens, one-time passwords, and transparent Web soft tokens.
1.1 Scope of Do cument
This document explai ns how to conf igure Acti vID Appliance and Zscaler using S ecurit y Assertion Mar kup
Language (SAML). SAML 2.0 enables Web-bas ed authentication and author ization and can be us ed by
Zscaler to delegate user authentication to the ActivID App lianc e.
Integrating ActivID Applian c e capab iliti es with Zscaler provides multiple choices for user authentication.
This option is simple an d allows users to authenticate to t he ActivID Ap pliance IDP portal that has m any
authentication mec hanisms working out of the box, including on e-time password (OTP), W eb soft token
OTP, and Public Key Infrastructure (PKI) methods.
1.2 Prerequisites
• ActivID Appliance 7.2 (or greater) installed and configured.
• Zscaler Web Security.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 4

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
4
1. Logged into Zscaler as an administrator, navigate to the Administration
2.0 Zscaler Configuration
2.1 Procedure 1: Enab le SAML on Zsca ler
tab.
2. Under Manage Administrators & Roles, click Manage Users &
Authentication.
3. Select the Authenticate using SAML Sign-On option.
4. Click Done.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 5
ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
5
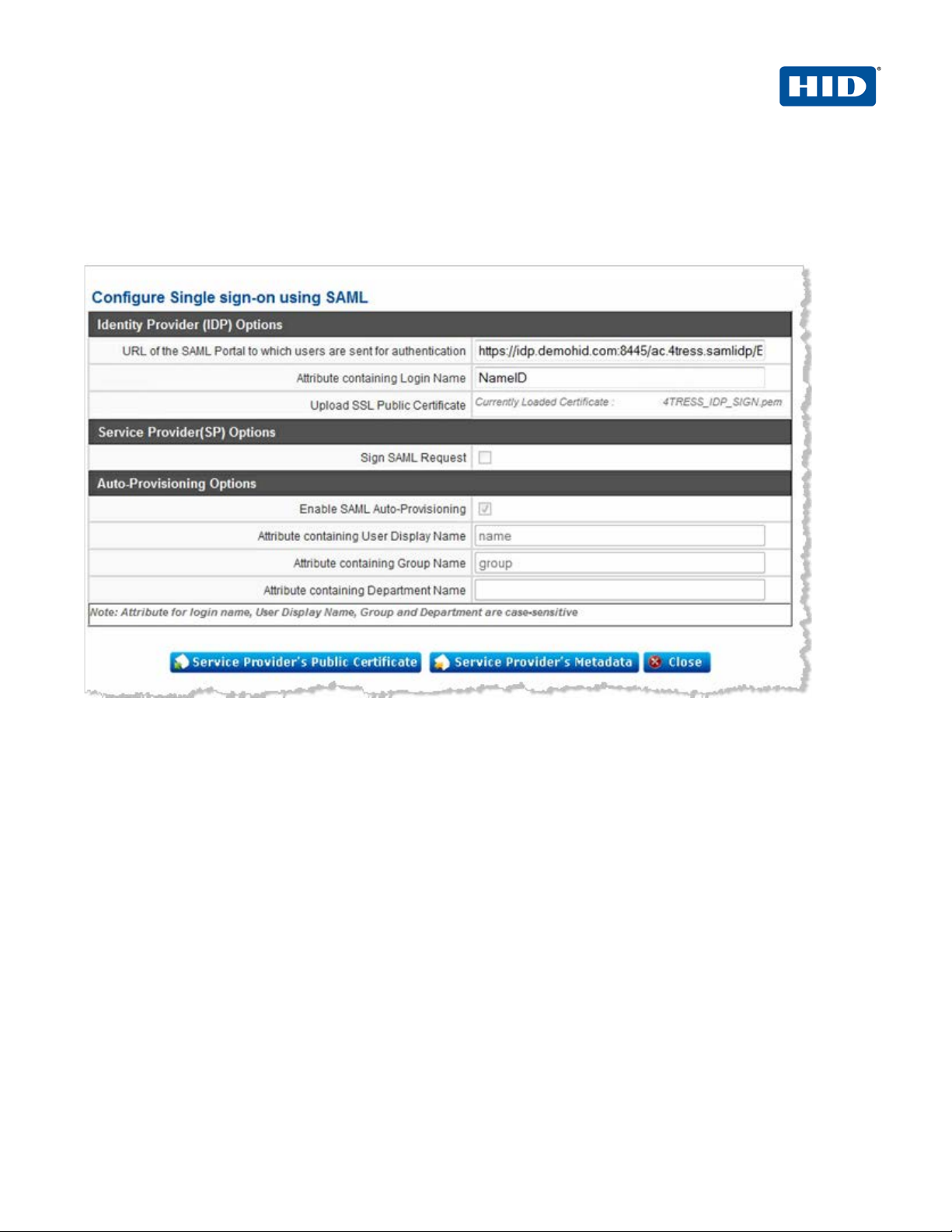
2.2 Procedure 2: Configure ActivID IDP in Zscaler
1. In the Configure User Authentication section of the Zscaler Administrator Console, click View SAML
Single Sign-On Parameters.
2. Enter the following parameters.
• URL of the ActivID Appliance to which users are sent for authentication. For example, change the
following URL to your ActivID Appliance Identity Provider.
https://<ACTIVID-APPLIANCE-FQDN>:8445/ac.4tress.samlidp/<SECURITY-DOMAINNAME>/binding/login-post.seam
• For Attribute containing Login Name, enter NameID.
3. To upload the SSL public Certificate of the ActivID Appliance, click Service Provider’s Public Certificate
(see the following section for steps to export your IDP certificate).
4. Click Done.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 6

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
6
2.3 Procedure 3: Export Act ivID Appliance IDP Certificate
1. Log on to the ActivID Appliance Management Console as an administrator.
2. When prompted, enter your User name and Password, and then click Submit.
3. Select the Configuration tab.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 7

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
7
4. In the Policies section of the menu to the left, expand the SAML menu, and then click ActivID Identity
Provider.
5. For Signing Certificate, click Download.
6. When prompted, click Open and then save the 4TRESS_IDP_SIGN.cer file to a desired location.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 8
ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
8
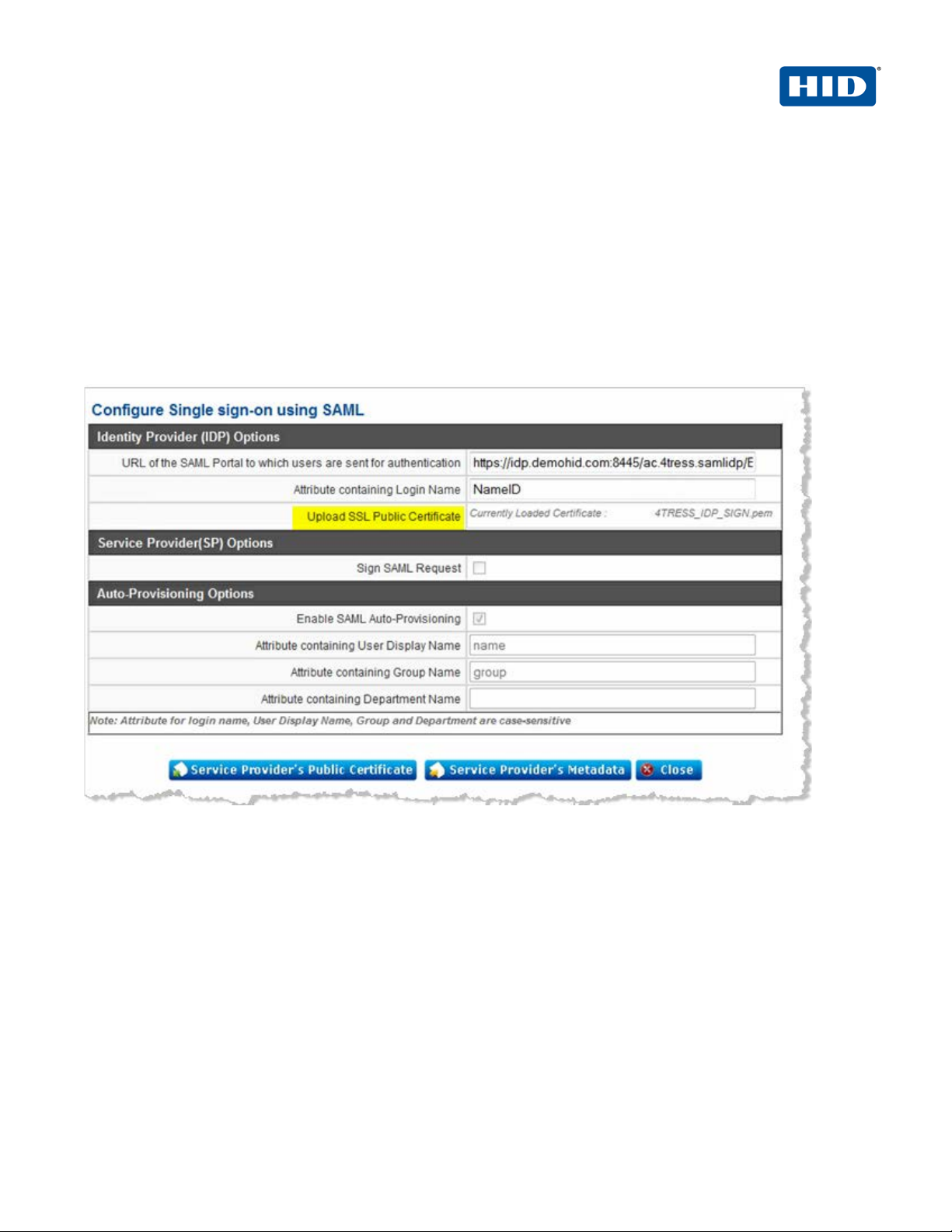
2.4 Procedure 4: Imp ort Act ivID Applian ce IDP certificate
1. Before you can import the 4TRESS_IDP_SIGN.cer file, you must convert it to a .pem file using the Openssl
tool. Run the following:
openssl x509 -outform der -in 4TRESS_IDP_SIGN.cer -out 4TRESS_IDP_SIGN.der
openssl x509 -inform der -in 4TRESS_IDP_SIGN.der -out 4TRESS_IDP_SIGN.pem
2. After you convert the file, you can import the file 4TRESS_IDP_SIGN.pem file by cli cking on Upload SSL
Public Certificate in the Zscaler Administrator Console Identity Provider (IDP) Options section, as
illustrated next:
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 9

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
9
2.5 Procedure 5: Export Z scaler M etadata
1. In the Configure User Authentication section in the Zscaler Administrator Console, click View SAML Single
Sign-On Parameters.
2. Click Service Provider’s Metadata.
3. Download the Zscaler-metadata-base.xml file.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 10

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
10
Note: The ActivID Appliance IDP only returns the configured attribute values within the as sertion if
it is
2.6 Procedure 6: Modify Zscal er Metad ata
Zscaler must be able to attribute values within the response to an authentication request before it can authorize
access via the Internet. You can configure these attributes for the ActivID App l iance.
the Zscaler SAML Authentication request contains a reference to the index. That is why
necessary to add this attribute (isDefault=”true”) in the Zscaler metadata.
The following snippets are examples for the attributes mail, group, and name:
<AttributeConsumingService index="0" isDefault="true">
<ServiceName xml:lang="en">Sample Service</ServiceName>
<ServiceDescription xml:lang="en">An example service that requires a human-
readable identifier and optional name and e-mail
address.</ServiceDescription>
<RequestedAttribute FriendlyName="mail"
Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" />
<RequestedAttribute FriendlyName="Name"
Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" />
<RequestedAttribute FriendlyName="group"
Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/group"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri" />
</AttributeConsumingService>
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 11

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
11
Important: You will use the ActivID Appliance Management Console and the ActivID Appliance
3.0 ActivID Appliance Configuration
This chapter describes how to configure the ActivID Appliance.
Configurer to perform these procedures. This chapter only provides a summary of steps. For complete
details, please have the following technical documents on hand for easy reference:
• ActivID Appliance IDP Solution Guide
• ActivID Appliance Administ rator Guide: Man agement Console
• ActivID Appliance Administrator Guide: Configurer Portal
3.1 Procedure 1: Create S AML Channel
1. Launch the ActivID Appliance Management Console.
2. When prompted, enter your User name and Password, and then click Submit.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 12

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
12
3. Navigate to the Configuration/Policies/Channels page.
4. In the pane to the left under Policies, click Channels.
5. In the page displayed to the right, click Add.
6. Specify a meaningful Name and Description, and then from the Type drop-down list, select SAML Service
Provider.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 13

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
13
3.2 Procedure 2: Import Z scaler Metadata
1. Navigate to the Zscaler SAML Details page.
2. Under the SAML Assertion Configuration section, deselect the option, Enable OneTimeUse condition.
3. Click File import and then type the federation metadata file path of the Zscaler metadata (the zscaler-
metadata-base.xml file).
4. Click Add to add the values that will be available to be returned in the SAML assertion (the values you edited
during Procedure 6: Modify Zscaler Metadata on page 10. The following dialog is displa yed.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 14

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
14
5. From the Select an assertion attribute drop-down list, select an option.
6. To map the attribute to specific values, from the Select the value type drop-down list, select either Static
value, User attribute, or a Predefined attribute, and then click OK.
You will see the following message when you are fini s hed.
You can check the list of values to be returned in SAML assertion. The following illustration is based on the values
listed in section 2.6 which covers how to modify Zscaler metadata.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 15

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
15
3.3 Procedure 3: Authorize the SAML Channel (Authentication Policies)
1. Connect to the Acti vID Appl ianc e AS Configurer.
2. When prompted, enter your Password, and then click Log in.
3. Select the Authentication Policies tab.
4. From the list of authentication policies, select the AT_EMPOTP polic y, and then click Edit.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 16

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
16
5. In the Available Channels box,select and move Zscaler SAML to the Selected Channels box, and then
click Update.
6. When returned to the Authentication Policies page, select the AT_EMPEPWD policy, and then click Edit.
7. In the Available Channels box,select and move Zsca ler SAML to the Selected Channels box, and then
click Update.
8. Return to the Management Console and edit the previously saved channel. You can view the permitted
(allowed) Authentication Policies by expanding the Allowed authentication Policies section, as illustrated
next.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 17

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
17
3.4 Procedure 4: Configure the Identity Provider
1. Log in to the ActivID Management Console.
2. In the pane to the left under Policies, expand SAML, and then click ActivID Identity Provider.
3. Deselect the option, Require signed authenticate requests.
The next step is to add the corresponding authentication policies and GUI template ID. Continue with section 3.5
Procedure 5: Adding a New Authentication Policies Mapping on page 18.
urn:oasis:names:tc:SAML:2.0:ac:classes:Password
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedPassword
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 18

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
18
3.5 Procedure 5: Adding a New Authentication Policies Mapping
1. Click Add to create new authentication po lici es m apping.
2. Enter the SAML Authentication Class. If you are editing, then you will see the class displayed and will not
be able to edit it (as illustrated).
3. From the ActivID Authentication Policy drop-down list, select an option.
4. From the GUI Template drop-down list, select an option.
5. Click Next.
6. To validate the new authentication policies mapping, click Ok.
The authentication policies mapping is created.
7. Click Save.
It takes a few minutes to save the configuration changes.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 19

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
19
4.0 SAML Channel Authentication: An Overview
4.1 Prerequisite: Activat e Web S oft Token
To use a Web token in the SAML context, users must enroll their laptops. This section explains how a user
accomplishes this task.
1. The User logs in to the Self Service Portal.
2. The user clicks Activate my device.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 20

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
20
3. The user clicks the link, A web soft token on my web browser.
If soft token configuration has been configured to use a web soft token with a PIN, then the user will be prompted
to enter a PIN.
4. The user clicks Activate.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 21

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
21
When the proper credentials have been accepted, the following message is displayed.
FIGURE 1: Illustration of User Authenticati o n with a We b Soft Token Launched in the Sign-In Page
5. The user opens a browser and enters the URL in th e web application. The URL is defined by the
administrator.
The user is redirected to the ActivID Appliance au the n tic ati on porta l.
6. The user authenticates as an ActivID Appliance user.
When authenticated, the user is redirected to the web applications pages.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 22

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
22
4.2 Sample Authentication
1. The user launches a browser and attempts to access the Internet.
2. The user is intercepted by Zscaler and must enter his/her email address as the Login Name.
The user is redirected to the ActivID Appliance IDP.
3. The user chooses an authentication method by clicking the Web Soft token One-time Password icon.
4. The user enters User name and then enters his/her PIN in the Web token.
5. The user copies and pastes the the resulting password into the Password field as illustrated next.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 23

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
23
If the authentication is accepted, then the user is redirected to a default browser Web page and can browse the
Internet – according to the security policy imposed by Zscaler.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 24

ActivID Appliance and Zscaler Web Security | SAML 2.0 Channel Integration Handbook
External Release | © 2012
24
Document
May 2013
Eco-System Workgroup
Initial release
1.1
Copyright
© 2012-2013 HID Globa l Cor poration/ASSA ABLOY AB. All rights reserved.
Trademarks
HID, the HID logo, ActivID, 4TRESS and/or other HID Global products or marks referenced herein are registered
trademarks or trademarks of HID Global Corporation in the United States and/or other countries.
The absence of a mark, product, service name or logo from this list does not constitute a waiver of the HID Global
trademark or other intellectual property rights concerning that name or logo. The names of actual companies,
trademarks, trade names, service marks, images and/or products mentioned herein are the trademarks of their
respective owners. An y rights not express l y granted h er ein are reserved.
Revision His tory
Date Author Description
Version
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 25

hidglobal.com
Americas
US Federal
Europe
Asia Pacific
Web
+1 510.574.0100
+1 571.522.1000
+33 (0) 1.42.04.84.00
+61 (0) 3.9809.2892
http://www.hidglobal.com/identity-assurance
Corporate Headquarters
15370 Barranca Parkway
Irvine, CA 92618
www.hidglobal.com
+1 949.732.2000
 Loading...
Loading...