Page 1

ActivIdentity® 4TRESS™
and Microsoft® Forefront™
Unified Access Gateway
Integration Handbook
Document Version 1.0 | Draft | July 17, 2012
Page 2

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 2
External Use | July 17, 2012 | © 2012 ActivIdentity
Name
Department
William Häggqvist
Professional Services
Isabel Fernandez
Technical Publications
Milan Khan
Professional Services
Paul Jones
Professional Services
Name
Department
Paul Jones
Professional Services
Milan Khan
Professional Services
Name
Department
Document Control
Document Contributors (Includes Reviewers)
Document Approvers
Document Revision(s)
Page 3

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 3
External Use | July 17, 2012 | © 2012 ActivIdentity
Table of Contents
1.0 Introduction ....................................................................................................................................................... 4
1.1 Scope of Document .................................................................................................................................... 4
1.2 Prerequisites .............................................................................................................................................. 4
1.3 Document References ................................................................................................................................ 4
2.0 Configuring 4TRESS......................................................................................................................................... 6
2.1 Adding the User Repository ....................................................................................................................... 6
2.2 Assigning the Repository to a User Type ................................................................................................. 10
2.3 Assigning the Repository to an Administration Group ............................................................................. 13
2.4 Assigning a Static Password for a User ................................................................................................... 16
2.5 Activating a Soft Token ............................................................................................................................ 19
3.0 Configuring Microsoft Forefront TMG ............................................................................................................. 25
3.1 Configuring TMG to Allow RADIUS Communication ............................................................................... 25
4.0 Configuring Microsoft Forefront UAG ............................................................................................................. 33
4.1 Initial Configuration ................................................................................................................................... 33
4.2 Adding the 4TRESS Server to UAG ......................................................................................................... 37
4.3 Adding the Portal Trunk............................................................................................................................ 39
4.4 Activating the Portal Trunk ....................................................................................................................... 44
5.0 Testing the Installation .................................................................................................................................... 46
Page 4

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 4
External Use | July 17, 2012 | © 2012 ActivIdentity
1.0 Introduction
The Microsoft® Forefront™ Unified Access Gateway 2010 enables a secure remote access service for both
managed and unmanaged computers as well as mobile devices. The gateway may be used to enable corporate
network access over a virtual private network (VPN) and publish files and/or applications for remote users.
ActivIdentity® solutions may be integrated with Microsoft Forefront Unified Access Gateway 2010 to provide a
strong authentication method that is flexible, scalable, and simple to manage. ActivIdentity offers the following
solution:
ActivIdentity® 4TRESS™ Authentication Appliance—Offers easy implementation and support for
multiple authentication methods that are useful for diverse audiences over the RADIUS channel,
including user name and password, mobile and PC soft tokens, one-time passwords, and transparent
Web soft tokens.
This document explains how to set up ActivIdentity 4TRESS Authentication Appliance, version FT2011 SP1 with
Microsoft Forefront Unified Access Gateway (UAG). Use this handbook to enable authentication to Microsoft
Forefront UAG over the RADIUS protocol using the RADIUS Front End feature of ActivIdentity 4TRESS.
1.1 Scope of Document
The scope of this document is limited to setting up the integration between Microsoft Forefront UAG and
ActivIdentity 4TRESS for authentication and does not include instructions on publishing applications on a
Forefront UAG trunk.
1.2 Prerequisites
The following pre-requisites should be met:
ActivIdentity 4TRESS Authentication Appliance has been set up according to ActivIdentity 4TRESS
Authentication Appliance Setup Guide
The RADIUS Front End feature of 4TRESS has been configured according to ActivIdentity 4TRESS
Authentication Appliance RADIUS Front End Solution Guide
The Soft Token Activation Portal feature of 4TRESS has been set up according to ActivIdentity
4TRESS Authentication Appliance Soft Token Solution Guide
A Windows Server 2008 R2 Enterprise edition with two network adapters available is joined to a
domain with a domain controller
Microsoft Forefront UAG is installed on the Windows Server 2008 R2 Enterprise edition server
1.3 Document References
The following documents provide a relevant background to the solution:
ActivIdentity Document References
ActivIdentity 4TRESS Authentication Appliance Setup Guide
ActivIdentity 4TRESS Authentication Appliance RADIUS Front End Solution Guide
Page 5

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 5
External Use | July 17, 2012 | © 2012 ActivIdentity
ActivIdentity 4TRESS Authentication Appliance Soft Token Solution Guide
External Document References
Microsoft Forefront UAG 2010 TechNet pages may be found at the following URL:
http://technet.microsoft.com/en-us/library/ff358694
Page 6
ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 6
External Use | July 17, 2012 | © 2012 ActivIdentity
2.0 Configuring 4TRESS
This section describes the configuration steps required to be made to the 4TRESS server component. These
changes are performed using the 4TRESS Management Console web interface.
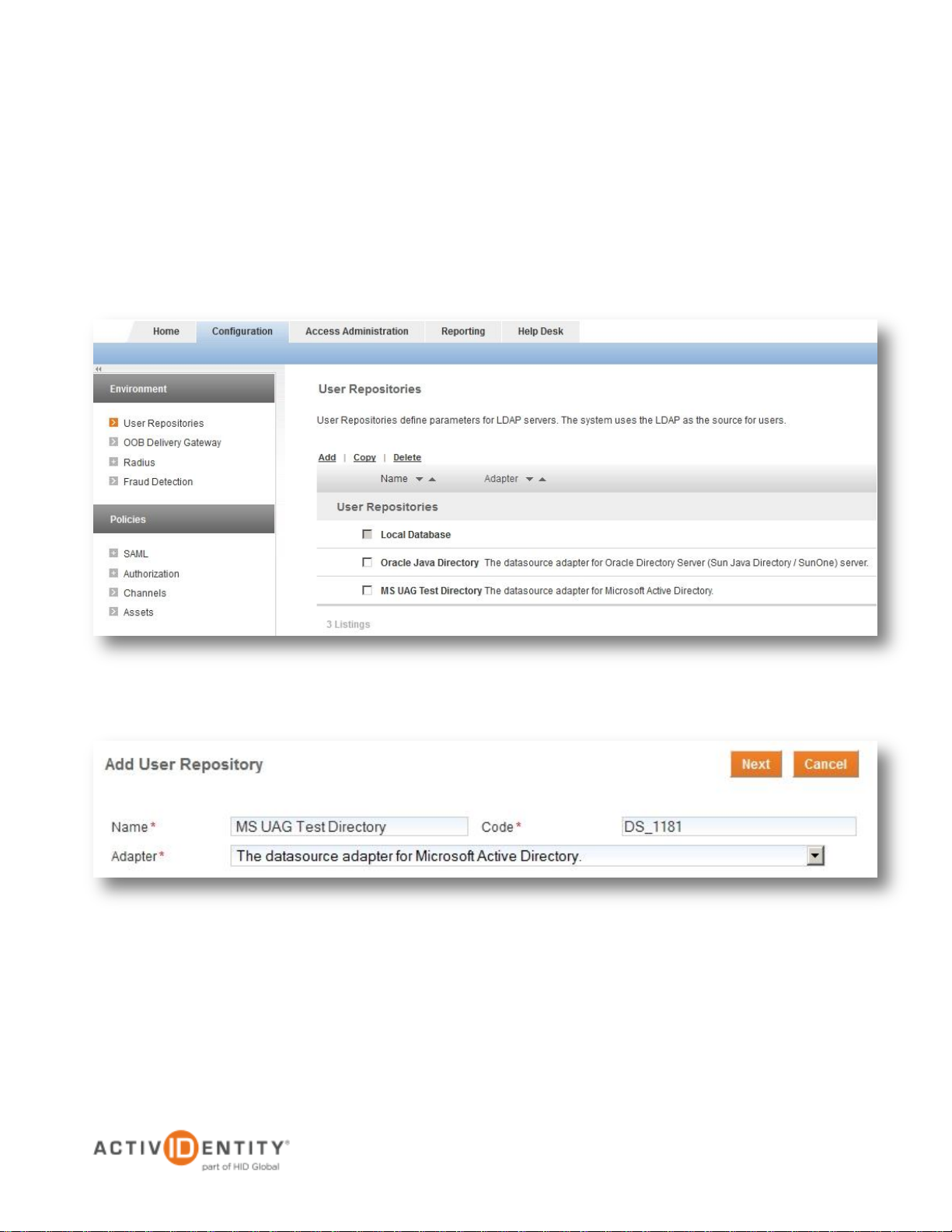
2.1 Adding the User Repository
For this environment, the Microsoft Active Directory hosted on the domain controller will be used as the user
repository. This LDAP server must be added and configured within 4TRESS.
1. Log on to the 4TRESS Management Console and select Configuration > User Repositories and click
Add
2. Specify a name for the directory and select the Adapter for Microsoft Active Directory. Optionally, modify
the Code. When done, click Next
Page 7

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 7
External Use | July 17, 2012 | © 2012 ActivIdentity
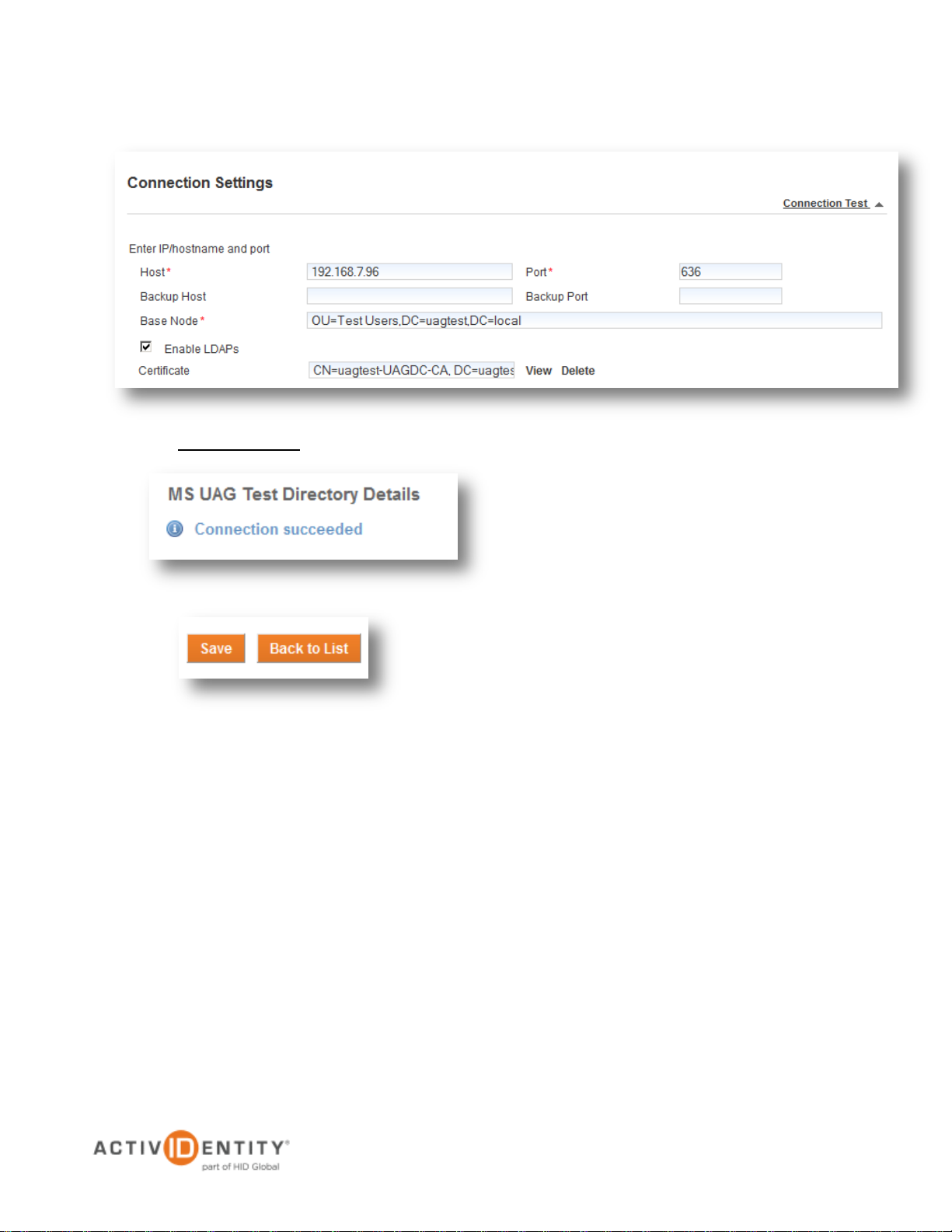
Enter IP/hostname and port
Host—Provide the IP address of
the domain controller
Backup Host—Optionally enter a
backup host
Base Node—Provide the base
node to use when connecting to
the directory
Port—Specify the port used by the
LDAPS connection
Backup port—Optionally enter a
backup port
Enable LDAPs—Check the box to
enable LDAPS
Configure user attributes and group attributes mapping
User Class—Leave the default
value
User ID Attribute—Leave the
default value
Account Status Attribute—
Leave the default value
LDAP Group Class—Leave the
default value
Group Member Attribute—Leave
the default value
GUID Attribute Name—Leave the
default value
Page 8

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 8
External Use | July 17, 2012 | © 2012 ActivIdentity
Configure connection login credentials
User DN—Provide the Distinguished Name of the user account used to connect to the
LDAP directory
Password—Enter the password for the account
Confirm Password—Repeat the password
3. When having entered all values, click the link Import LDAPs Root CA certificate
4. Browse for the certificate and click Open
Page 9
ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 9
External Use | July 17, 2012 | © 2012 ActivIdentity
6. If the test is successful, a message will be
displayed. After a successful test, press Save
to create the user repository
5. Click Connection Test to verify that the connection is correctly configured.
Page 10
ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 10
External Use | July 17, 2012 | © 2012 ActivIdentity
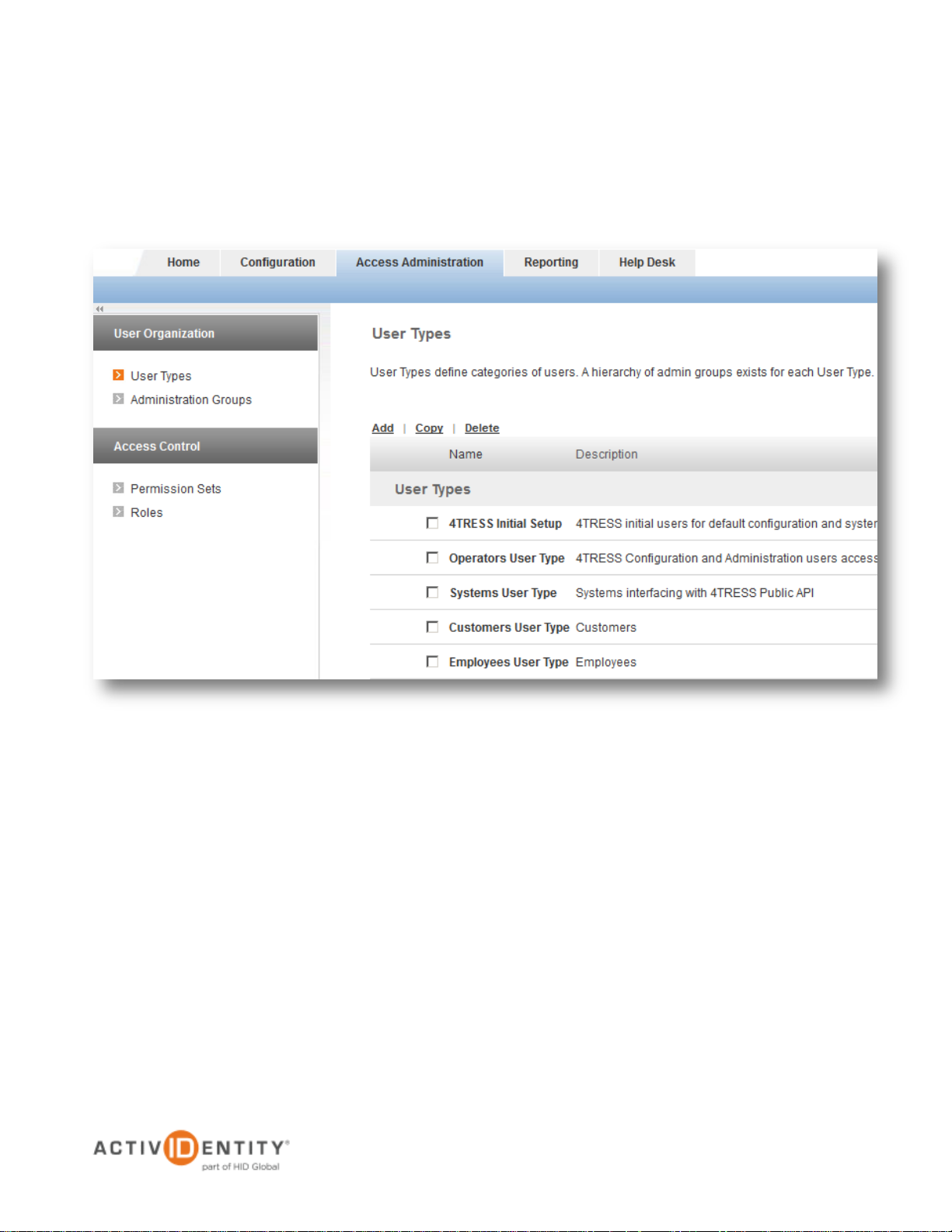
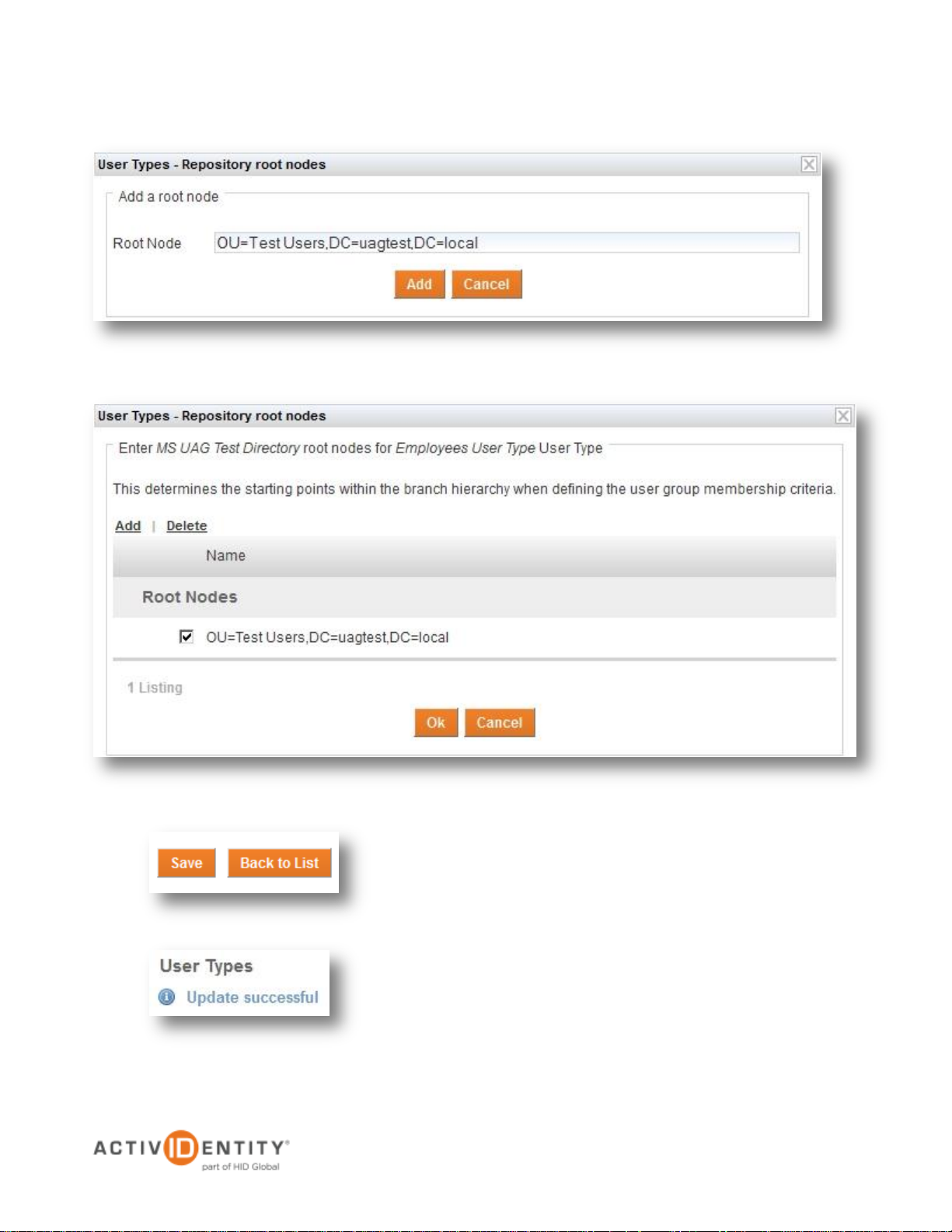
2.2 Assigning the Repository to a User Type
The user repository added in section 2.1 Adding the User Repository must be associated with a User Type in
4TRESS, or the users will not be included when performing a user lookup. This section describes the steps
required to successfully assign the repository to a given User Type.
1. Log on to the 4TRESS Management Console and select Access Administration > User Types. Then,
click one of the pre-configured User Types. For this example, we will use Employees User Type
Page 11
ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 11
External Use | July 17, 2012 | © 2012 ActivIdentity
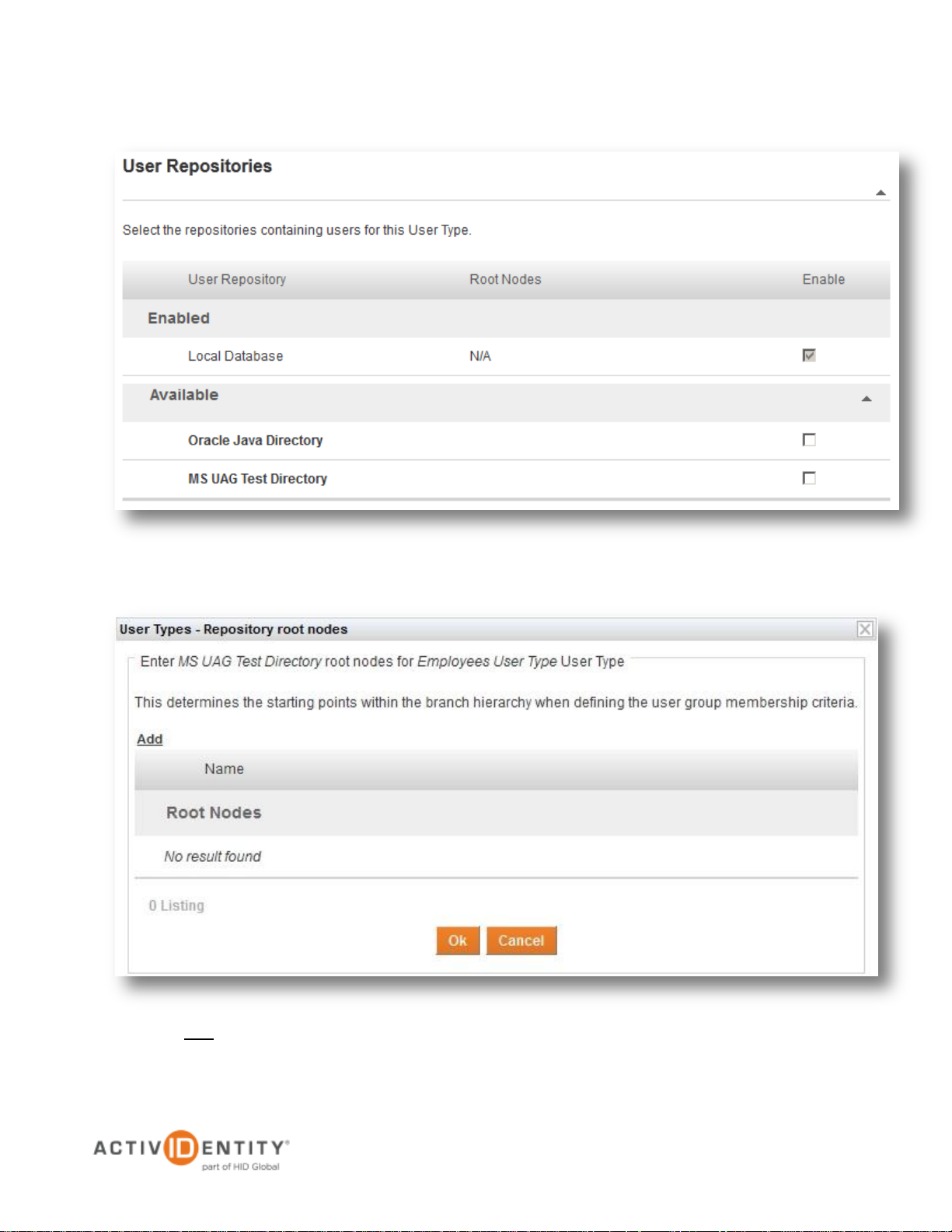
2. Expand the section User Repositories and then expand the section Available. Next, click the repository
created in section 2.1 Adding the User Repository
3. Press Add to set up a Root Node in the pop-up window that appears
Page 12
ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 12
External Use | July 17, 2012 | © 2012 ActivIdentity
5. Check the box and press OK to continue
6. Press Save to save the configuration
4. Specify the Root Node and click Add. It is possible to use the pre-defined value
Page 13

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 13
External Use | July 17, 2012 | © 2012 ActivIdentity
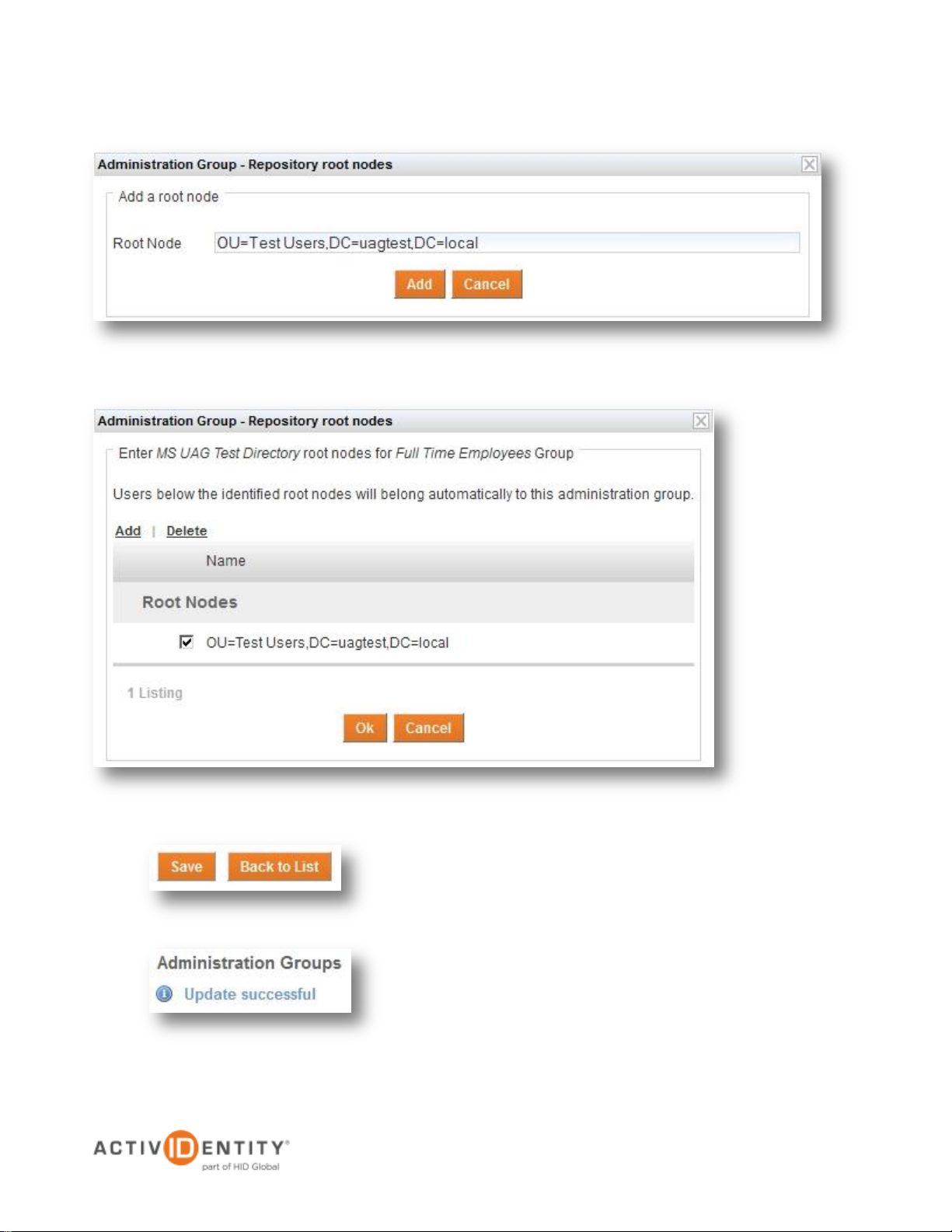
2.3 Assigning the Repository to an Administration Group
The user repository added in section 2.1 Adding the User Repository must also be associated with an
Administration Group. This section lists the operations required to perform this action.
1. Log on to the 4TRESS Management Console and select Access Administration > Administration
Groups. Then, click one of the pre-configured Administration Groups. For this example, we will use Full
Time Employees Administration Group
Page 14

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 14
External Use | July 17, 2012 | © 2012 ActivIdentity
2. Expand the section User Repositories and then expand the section Available. Next, click the repository
created in section 2.1 Adding the User Repository
3. Press Add to set up a Root Node in the pop-up window that appears
Page 15
ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 15
External Use | July 17, 2012 | © 2012 ActivIdentity
5. Check the box and press OK to continue
6. Press Save to save the configuration
4. Specify the Root Node and click Add. It is possible to use the pre-defined value
Page 16

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 16
External Use | July 17, 2012 | © 2012 ActivIdentity
1. Log on to the 4TRESS Management
Console and search for a test user using
the quick search function
2. At the Wallet section, select Create Password to assign a password for the user
2.4 Assigning a Static Password for a User
Because the user must authenticate to the Soft Token Portal to request activation, a password needs to be
configured for the user first.
Page 17

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 17
External Use | July 17, 2012 | © 2012 ActivIdentity
3. Select Employee Static Password and click Next
4. Specify a password for the user and click Next
Page 18

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 18
External Use | July 17, 2012 | © 2012 ActivIdentity
6. Press Close to close the window when the ‘Creation successful’ message
appears
7. When the Employee Static Password is listed under Authentication
Records, press Save
5. Select a time interval and click Save
Page 19

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 19
External Use | July 17, 2012 | © 2012 ActivIdentity
Note: The next steps assume the ActivIdentity PC Soft Token is installed on the End User
client machine.
2.5 Activating a Soft Token
This section describes the process of assigning a PC Soft Token for a user using the Soft Token Activation Portal
feature of 4TRESS.
1. Browse to the ActivIdentity Soft Token Activation Portal and select Activate Soft Token and PC Token in
the drop-down list
Page 20

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 20
External Use | July 17, 2012 | © 2012 ActivIdentity
2. Provide the user name and password and press Login to continue
3. Launch the PC Token software and copy the Serial Number
Page 21

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 21
External Use | July 17, 2012 | © 2012 ActivIdentity
4. Enter the Serial Number and press Request Activation
5. Copy the Activation Code
Page 22

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 22
External Use | July 17, 2012 | © 2012 ActivIdentity
6. Enter the Activation Code into the PC Soft Token and a Registration Code is returned.
7. Enter and confirm the Registration Code onto the Soft Token Activation Portal and press Activate
Page 23

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 23
External Use | July 17, 2012 | © 2012 ActivIdentity
8. Upon activation success, press OK
9. Press Next in the PC Soft Token window displayed in step 6 above and choose a PIN for the Soft Token.
When done, press Next
Page 24

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 24
External Use | July 17, 2012 | © 2012 ActivIdentity
10. Finally, click Finish to complete the wizard
Page 25

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 25
External Use | July 17, 2012 | © 2012 ActivIdentity
3.0 Configuring Microsoft Forefront TMG
The Microsoft Forefront TMG firewall disables all network traffic that is not explicitly allowed. Therefore, an
exception rule needs to be configured and activated in the TMG Firewall to allow the UAG server to forward the
authentication request to the 4TRESS server. This section describes the process of enabling communication to
take place between the UAG server and 4TRESS over the RADIUS protocol.
3.1 Configuring TMG to Allow RADIUS Communication
Administration of the TMG Firewall is performed by using the Microsoft TMG Management Console, which is
installed as part of the Microsoft Forefront UAG software.
1. Launch the Microsoft TMG Management Console and right-click Firewall Policy. Then Select New and
Access Rule…
Page 26

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 26
External Use | July 17, 2012 | © 2012 ActivIdentity
2. Next, specify a name for
the Access Rule, e.g.
4TRESS and click Next
3. Select Allow for the Rule
Action and click Next
Page 27

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 27
External Use | July 17, 2012 | © 2012 ActivIdentity
4. In the drop-down list,
select Selected protocols
and click Add…
5. Select the RADIUS protocol and click Add.
Click Next to proceed
Page 28

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 28
External Use | July 17, 2012 | © 2012 ActivIdentity
6. Click Add… to add
sources for which the rule
should apply
7. Select Address Range and enter the information for the 4TRESS
server as shown below. Click OK when done
Page 29

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 29
External Use | July 17, 2012 | © 2012 ActivIdentity
8. Select 4TRESS in the list of Address Ranges and click Add.
Then, click Next to continue
9. Click Add and select 4TRESS. Then, click Add again
Page 30

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 30
External Use | July 17, 2012 | © 2012 ActivIdentity
10. Click Next to continue
11. Click Next
Page 31

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 31
External Use | July 17, 2012 | © 2012 ActivIdentity
12. Review the information
and click Finish to
complete the Access Rule
13. When prompted, click Apply to save the changes and update the configuration
14. Enter a description for the change (optional) and click Apply
Page 32

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 32
External Use | July 17, 2012 | © 2012 ActivIdentity
15. Wait for the configuration to save
successfully and click OK
Important: Make sure the Access Rule created is not intercepted by another rule that
denies the communication to take place. Using the ActivIdentity RADIUS Ping Tool is a
convenient way of testing the connectivity.
Communication should now be allowed to and from the 4TRESS server over the RADIUS protocol.
Page 33

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 33
External Use | July 17, 2012 | © 2012 ActivIdentity
This section provides instructions on how to configure the Microsoft
Forefront UAG application to communicate with 4TRESS and how to
create a basic Portal Trunk to test the authentication.
Portal Trunk
The Portal Trunk of Microsoft Forefront UAG is
the website the End Users will access to
provide their credentials. Once authenticated
at the Portal Trunk, the End User is granted
access to the applications that are published.
1. Select Configure Network
Settings in the Wizard that
appears.
2. Click Next to continue the wizard
3. Set up the Internal and External network adapters
and click Next
4.0 Configuring Microsoft Forefront UAG
4.1 Initial Configuration
Launching the Forefront UAG Management Console for the first time will take a moment to initialize. When the
initialization is completed, a wizard will be displayed.
Page 34

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 34
External Use | July 17, 2012 | © 2012 ActivIdentity
4. Click Add and specify the IP
address range of the internal
network. When done, click
Next
5. Verify the settings and click
Finish to complete the
network configuration wizard
Page 35

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 35
External Use | July 17, 2012 | © 2012 ActivIdentity
6. Select Define Server
Topology to launch the wizard
7. Click Next
Page 36

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 36
External Use | July 17, 2012 | © 2012 ActivIdentity
8. Select Single Server and click Next
9. Click Finish to complete the wizard
12. Finally, click Yes to activate
the configuration
10. Optionally choose to join Microsoft Update
11. Click Close to end the wizard
Page 37

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 37
External Use | July 17, 2012 | © 2012 ActivIdentity
1. Launch UAG Management
Console
2. Click on Admin >
Authentication and
Authorization Servers…
3. Click Add…
4.2 Adding the 4TRESS Server to UAG
This section provides instructions on how to configure the 4TRESS as an authentication server within UAG.
Page 38

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 38
External Use | July 17, 2012 | © 2012 ActivIdentity
Server type—Select RADIUS
Server name—Specify a name
for the server, e.g. 4TRESS
IP address/host—Specify the IP
address of the 4TRESS server
Port—Specify the port the RFE
feature of 4TRESS is listening on
(default ports for 4TRESS RFE
are 1812 & 1813)
Alternate IP/host—Specify the
IP address of the 4TRESS server
again
Alternate port—Specify the
second port used by the
4TRESS RFE feature
Secret key—Specify the Secret
as configured for the channel in
4TRESS
Check the box Support
challenge-response mode
4. When all values are set, press OK to add the authentication server
Page 39

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 39
External Use | July 17, 2012 | © 2012 ActivIdentity
5. Click Close to exit to the
UAG Management
Console main menu
4.3 Adding the Portal Trunk
A Portal Trunk needs to be configured in Microsoft Forefront UAG. This is done from the UAG Management
Console. Before starting the trunk configuration, make sure that the server has been outfitted with a proper web
server certificate where the FQDN of the server is specified both in the Subject name field and as a DNS name in
the SubjectAlternativeName field.
1. Launch the Microsoft UAG Management Console and select HTTPS Connections. Next, click on the link
Click here to create an HTTPS trunk
Page 40

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 40
External Use | July 17, 2012 | © 2012 ActivIdentity
2. Press Next to continue the Create Trunk
wizard
3. Select Portal trunk and click Next
Page 41

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 41
External Use | July 17, 2012 | © 2012 ActivIdentity
Trunk name—Specify a name for the
trunk (this may not be equal to or a part of
the public host name)
Public host name—Specify the name of
the URL the End User will enter to access
the web page
IP address—Specify the IP address to be
used for accessing the web page. It is
recommended that the external IP address
is used.
HTTP port—Port to use for inbound and
outbound HTTP traffic
HTTPS port—Port to be used for inbound
and outbound HTTPS traffic
4. Define values for the configurable items listed above and click Next when done
Page 42

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 42
External Use | July 17, 2012 | © 2012 ActivIdentity
5. Select Add… to add an authentication server
to use for the trunk
6. In the list of available Authentication and
Authorization Servers, highlight 4TRESS and
click Select
7. Click Next to continue
Page 43

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 43
External Use | July 17, 2012 | © 2012 ActivIdentity
8. Select the certificate that will be used for the
Trunk
Important: Make sure the web
server certificate contains the
server’s FQDN in both the
Subject field and the
SubjectAlternativeName as a
DNSName
9. Review the information and click Finish to
create the Portal Trunk
Page 44

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 44
External Use | July 17, 2012 | © 2012 ActivIdentity
2. Click the cogwheel icon to activate the configuration
4.4 Activating the Portal Trunk
The next step is to configure the Portal Trunk to make use of the 4TRESS server for authentication.
1. Select the newly created HTTPS trunk from the left hand menu and verify that all settings are correct
Page 45

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 45
External Use | July 17, 2012 | © 2012 ActivIdentity
3. Press Activate to activate the configuration
4. When the configuration has been successfully activated, press Finish
Page 46

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 46
External Use | July 17, 2012 | © 2012 ActivIdentity
2. When asked to trust the site
with regards to pop-up windows,
press Yes
Note: After installing the components, the browser may have to be restarted.
5.0 Testing the Installation
When all of the above sections have been completed, the installation can be tested. To do this, an attempt to
authenticate the test user previously used will be made to the UAG portal. Make sure the certificate of the UAG
server is trusted.
1. From the machine where the PC Soft Token was installed, launch a web browser and go to the UAG URL
defined in step 4 of section 4.3 above, e.g. https://uagsrv.uagtest.local:443
3. Next, the UAG portal will attempt to install some software. Press Install to go ahead with the installation
as these components are needed for full site operability
Page 47

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 47
External Use | July 17, 2012 | © 2012 ActivIdentity
4. When the components have been successfully downloaded, enter the user name and generate an OTP,
then press Log On to authenticate
5. If the authentication is successful, the Application Portal will be displayed.
Page 48

ActivIdentity 4TRESS and Microsoft Unified Access Gateway | Integration Handbook
P 48
External Use | July 17, 2012 | © 2012 ActivIdentity
Americas +1 510.574.0100
US Federal +1 571.522.1000
Europe +33 (0) 1.42.04.84.00
Asia Pacific +61 (0) 2.6208.4888
Email info@actividentity.com
Web www.actividentity.com
Legal Disclaimer
ActivIdentity, the ActivIdentity (logo), and/or other ActivIdentity products or marks referenced
herein are either registered trademarks or trademarks of HID Global Corporation in the United
States and/or other countries. The absence of a mark, product, service name or logo from this
list does not constitute a waiver of the trademark or other intellectual property rights concerning
that name or logo. The names of other third-party companies, trademarks, trade names, service
marks, images and/or products that happen to be mentioned herein are trademarks of their
respective owners. Any rights not expressly granted herein are reserved.
 Loading...
Loading...