Page 1
hidglobal.com
4TRESS™ FT2011
Authentication Server
SAML 2.0 Channel
Integration Handbook
Document Version 2.3 | Released | May 2013
Page 2

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
2
Table of Contents
List of Figures ............................................................................................................................................................. 3
1.0 Introduction ....................................................................................................................................................... 4
1.1 Scope of Document .................................................................................................................................... 4
1.2 Prerequisites .............................................................................................................................................. 4
2.0 Juniper Secure Access Configuration ............................................................................................................... 5
2.1 Procedure 1: Create SAML Authentication Server .................................................................................... 5
2.2 Procedure 2: Define Juniper User Role(s) ................................................................................................. 7
2.3 Procedure 3: Define Juniper Authentication Realm ................................................................................... 8
2.4 Procedure 4: Configure Juniper Sign-In Page ........................................................................................... 9
2.5 Procedure 5: Juniper Sign-In Policies ...................................................................................................... 11
3.0 4TRESS Configuration .................................................................................................................................... 12
3.1 Procedure 1: Create SAML Channel ........................................................................................................ 12
3.2 Procedure 2: Import Juniper Metadata ..................................................................................................... 14
3.3 Procedure 3: Authorize the SAML Channel (Authentication Policies) ..................................................... 14
3.4 Procedure 4: Configure the Identity Provider ........................................................................................... 16
4.0 SAML Channel Authentication: An Overview ................................................................................................. 17
4.1 Prerequisite: Activate Web Soft Token .................................................................................................... 17
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 3

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
3
List of Figures
FIGURE 1: Illustration of User Authentication wit h a Web Soft Token Launched in the Sign-In Page ................ 18
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 4

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
4
1.0 Introduction
The Juniper® Networks SA Series SSL VPN Applian ces enable remote and mobile employees, customers, and
partners to gain secure access to corporate Virtual P r i v ate Network resources and applications. Providing secure
access via a VPN over existing Internet connections requires strong, two-factor authentication to protect
resources. The HID Global Identity Assurance™ soluti ons t hat work with Juniper Networks appliances incorporate
SSL VPN solutions with versatile, strong authentication that is flexible, scalable, and simple to manage. There are
two solutions:
• 4TRESS AAA Server for Remote Access—Addresses the sec urity risks associated with a mobile
workforce remotely accessing systems and data.
• 4TRESS Authentication Server (AS)—Offers support f or mul t i ple aut hentication methods that are
useful for diverse audiences across a variety of service channels (including SAML), including user
name and password, mobile and PC soft tokens, one-time passwords, and transparent Web soft
tokens.
1.1 Scope of Document
This document explains how to configure 4TRESS Authenticat ion Serv er (FT2011) and Juniper Secure Access
(SA) using Security Assertion Markup Language (SAML). SA ML 2.0 enables Web-based authentication and
authorization and can be used by Juniper SA to delegate user authentication to the 4TRESS Authentication
Server.
The integration of 4TRESS Authentication Server capabilities with Juniper SSL-protected Virtual Private Networks
enables multiple user authentication choices. User s can authenticate to the 4TRESS authentication portal using
whichever authentication mechanism is appropriate for the environment and company policies. Authentication
methods working out of the box include one-time passwords (OTP), Web soft token OTPs, an d P ubl ic K ey
Infrastructure (PKI) methods.
1.2 Prerequisites
• 4TRESS Authentication Server (FT2011 or greater) installed and configured.
• Juniper SA with SAML 2.0 capabilities installed and configured (at a minimum, Juniper Networks
Secure Access IVE Platform Version 7.1R5).
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 5
FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
5
2.0 Juniper Secure Access Configuration
This chapter describes how to manage Juniper Secure A c ce ss. When a user signs into a Juniper SA Series
appliance, the user specifies an authentication r ealm , which is associated with a specific authentication server.
The Juniper SA Series appliance forwards the user’s credentials to this authentication server to verify the user’s
identity. The first procedure is to create a new SAML server to validate authenticat ion requests.
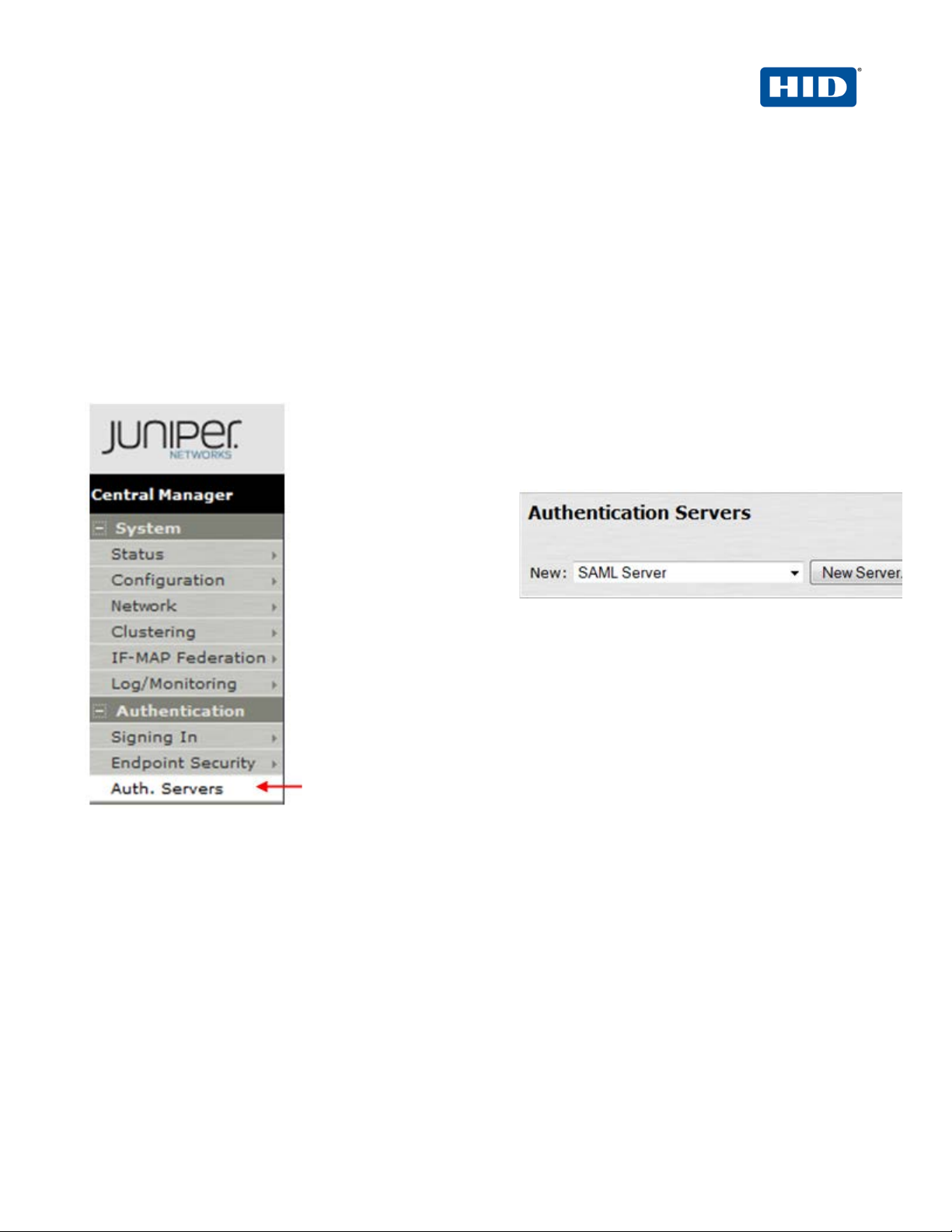
2.1 Procedure 1: Create SAML Authentication Server
Getting Started
1. In the Admin
console, expand the
Authentication
menu, and then
click Auth. Servers.
2. From the New drop-down list, select SAML
Server, and then click New Server.
The following dialog is displayed.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 6
FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
6
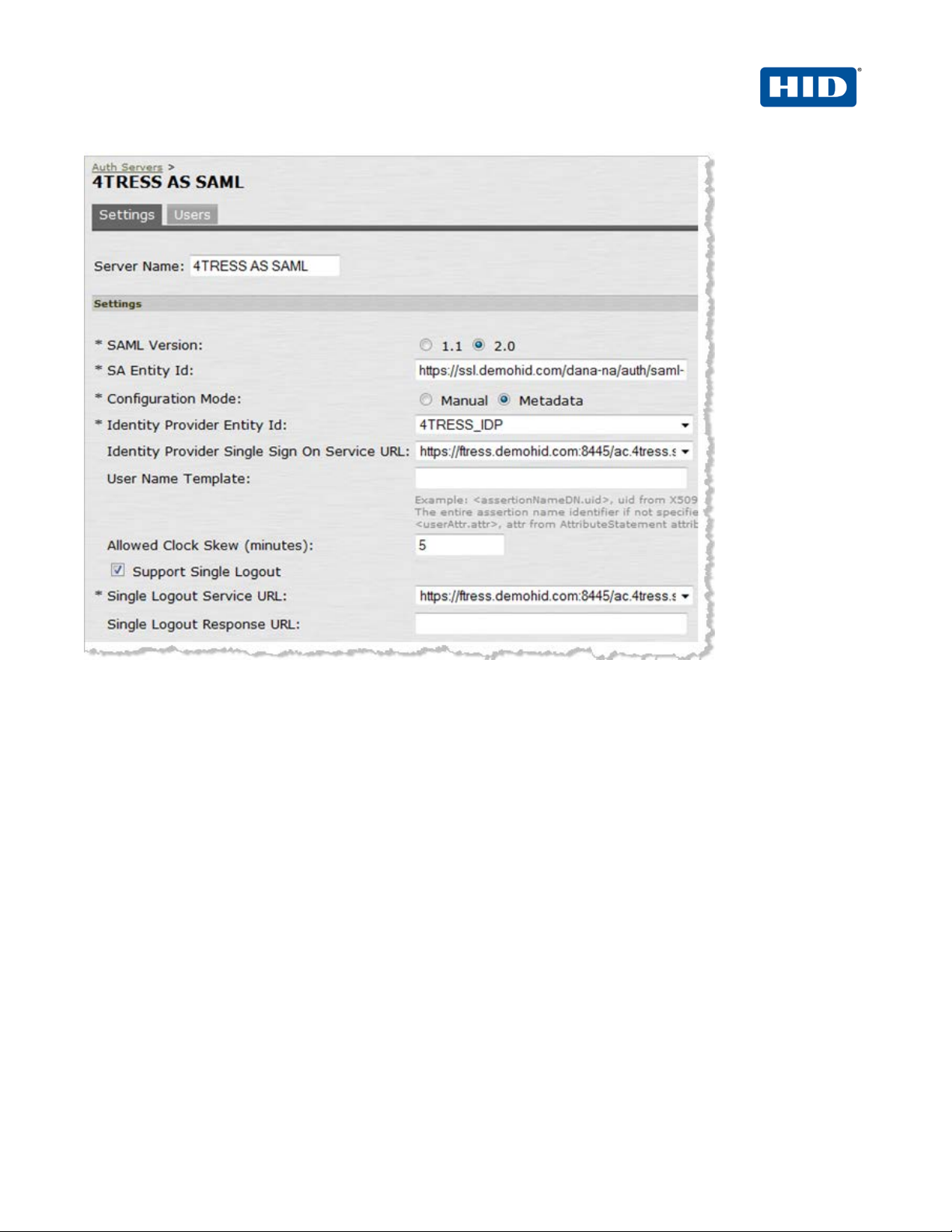
All data should be populated already, as illustrated above.
3. Proof the Settings tab page to be sure the following opt ions a nd attributes are correct.
• SAML Version—Select 2.0.
• SA Entity Id—This should be auto-populated. If not, then click Configure host name (not
illustrated).
• Single Logout Service URL—make sure it is correct.
• The other settings are default settings. Accept them.
• Configuration Mode—The Metadata option should be selected. Metadata is used to
configure the 4TRESS Identity Provider (IDP).
If there are issues, then you will have to retrieve the 4TRESS Metadata, which are available via the
4TRESS Management Console. See the illustration on the f oll owing page.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 7

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
7
4. Log in to the 4TRESS Management Console, navigate t o Configuration -> SAML -> 4TRESS Identity
Provider -> Export Metadata), and then set Metadata Validity. Save your changes, and then click
Download Metatdata to export t he f i le.
2.2 Procedure 2: Define Juniper User Role(s)
A user role is an entity that defines user session param et ers, personalization settings, and enabled access
features.
1. From the Admin console, expand the Users menu, p oi nt to User Roles, and then click New User Role.
2. Configure the new user role according to your requir ements.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 8

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
8
2.3 Procedure 3: Define Juniper Authentication Realm
An authentication realm specifies the conditi ons that users must meet in order to sign into the SA Series
appliance. A realm consists of a grouping of authenti ca tion resources.
1. From the Admin console, expand the Users menu, p oi nt t o User Realms, and then click New User Realm.
2. On the General tab, enter the following attributes.
• Name—Enter a name to label this realm.
• Description—Enter a meaningful description.
• In the Servers section:
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 9

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
9
• Select the SAML option from the Authentication drop-down list to specify an
authentication server to use for authenticating u se rs who sign i n t o this realm (for
example, the “4TRESS AS SAML”).
• Directory/Attribute—Accept the default (None).
• Accounting—Accept the default (None).
3. Click Save Changes.
2.4 Procedure 4: Configure Juniper Sign-In Page
1. From the Admin console, expand the Authentication menu, point to Signing In, and then cl i ck Sign-in
Pages.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 10

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
10
2. Accept all defaults as illustrated above.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 11

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
11
2.5 Procedure 5: Juniper Sign-In Policies
User sign-in policies determine the realm(s) that users can access.
1. To create or configure user sign-in policies, in the Admin console, expand the Authentication menu, point to
Signing In, and then click Sign-in Policies.
2. To create a new sign-in policy, click New URL.
3. In the Sign-in URL field, enter the URL that you want to associate with the policy. Use the format
<host>/<path>, where <host> is the host name of the Secure Access device and <path> is any string
you want users to enter.
4. For Sign-in Page, select the sign-in page that you want to associate with the policy.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 12
FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
12
Important: You will use the 4TRESS Management Console and the 4TRESS Configurer to perform
5. For Authentication realm, specify which realm(s) map to the policy and how users should pick from amongst
realms.
6. Click Save Changes.
3.0 4TRESS Configuration
these procedures. This chapter only provides a summary of steps. For complete details, please have
the following technical documents on hand for ea sy ref erence:
• 4TRESS AS Identity Provider Solution Guide
• 4TRESS AS Administrator Guide: Management C onsole
• 4TRESS AS Administrator Guide: Configurer Port al
3.1 Procedure 1: Create SAML Channel
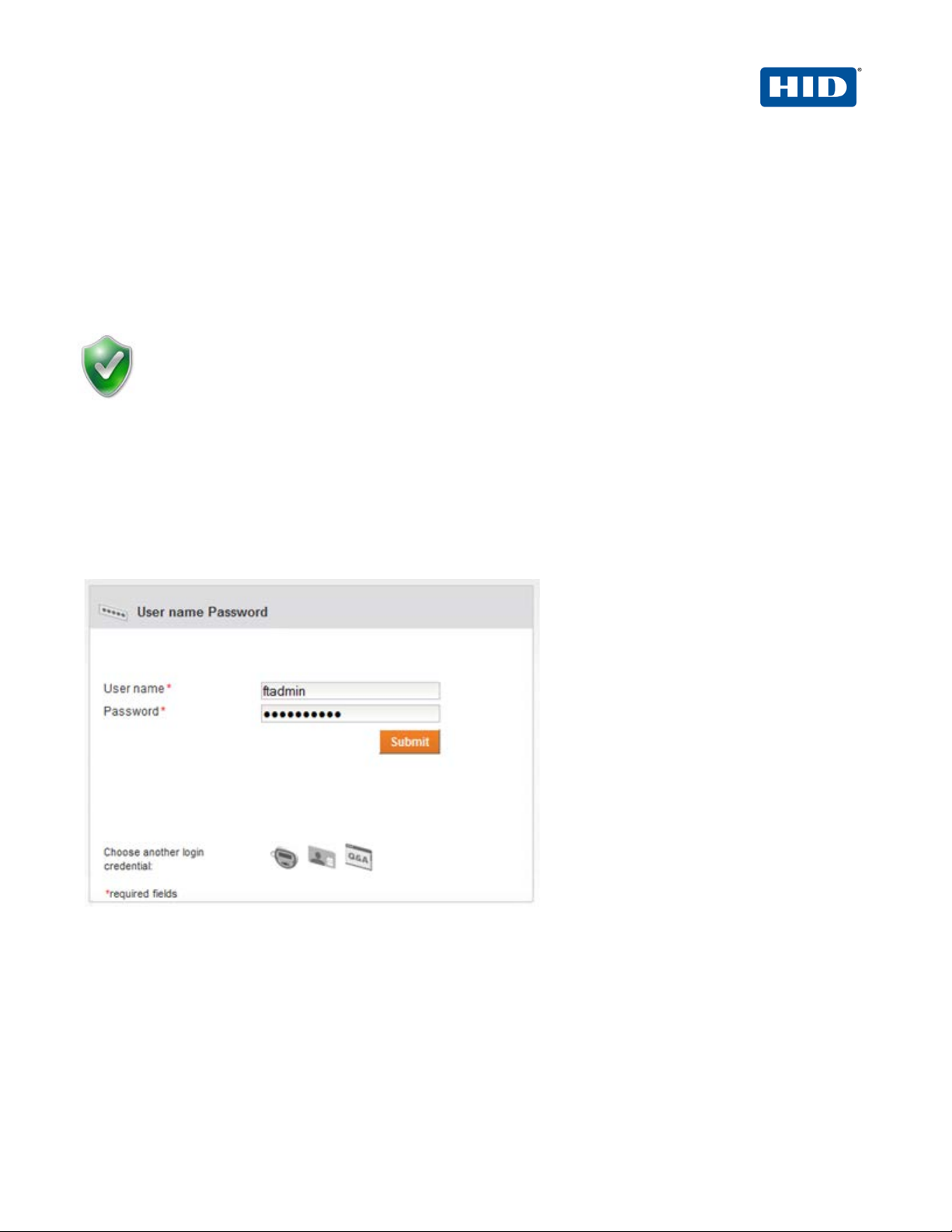
1. Launch the 4TRESS Management Console.
2. When prompted, enter your User name and Password, and then click Submit.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 13
FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
13
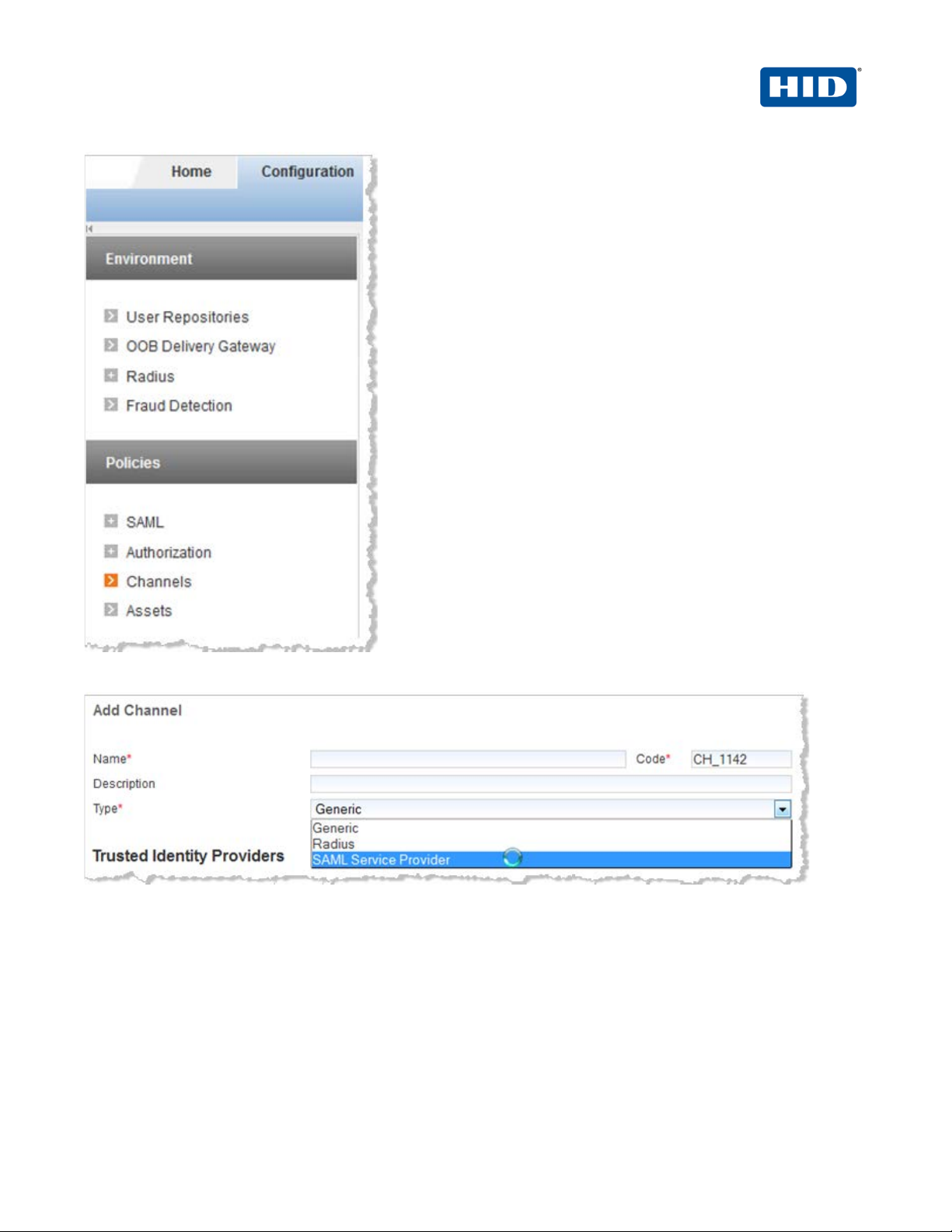
3. In the pane to the left under Policies, click Channels, and then in the page displ ayed to the right, click Add.
4. Specify a meaningful Name and Description, and then from the Type drop-down list, select SAML Service
Provider.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 14

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
14
3.2 Procedure 2: Import Juniper Metadata
1. Navigate to the Juniper SAML Details page.
2. Click File import.
3.3 Procedure 3: Authorize the SAML Channel (Authentication Policies)
1. Connect to the 4TRESS AS Configurer.
2. When prompted, enter your Password, and then click Log in.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 15

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
15
3. In the Available Channels box,select and move Juniper SAML to the Selected Channels box, and then
click Update.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 16

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
16
3.4 Procedure 4: Configure the Identity Provider
1. Log in to the 4TRESS Management Console.
2. In the pane to the left under Policies, expand SAML, and then click 4TRESS Identity Provider.
3. Select the corresponding authentication polici es and GUI template ID.
urn:oasis:names:tc:SAML:2.0:ac:classes:Password
urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedPassword
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 17

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
17
4.0 SAML Channel Authentication: An Overview
4.1 Prerequisite: Activate Web Soft Token
For a person to use a Web token in the SAML context, the laptop must be enrolled first.
1. From the Main menu, from the Service drop-down list, select Activate Soft Token.
2. From the Soft Token Type drop-down menu, select Web Soft Tok en, and then click Submit.
3. Enter your User Name and Password, and then click Login.
4. Click Activate. If soft token configuration has been configured to use a Web soft token with a PIN, then you
will be prompted to enter a PIN, also.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 18

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
18
When the proper login credentials have been accepted, t he following message is displayed.
Now, the Web token can be used to access Juniper realms.
FIGURE 1: Illustration of User Authentication with a Web Soft Token Launched in the Sign-In Page
The user opens a browser and enters the URL the administ rator has defined in the Juniper Sign-in policy. The
user is redirected to the 4TRESS AS authentication portal, and t hen authenticates as a 4TRESS user. When
authenticated, the user is redirected to the Junipe r pa ges.
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 19

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
19
Document
May 2012
Eco-System Workgroup
Initial release
2.0
February 2013
Eco-System Workgroup
Initial rebranding for HID Global
2.1
March 2013
Eco-System Workgroup
Copyedits to remove mentions of A A A and RADIUS.
2.2
May 2013
Eco-System Workgroup
Rebranded for updated HID “chain” and logo and copyright
2.3
Copyright
© 2012-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved.
Trademarks
HID, the HID logo, ActivID, 4TRESS, and/or other HID Global products or marks referenced herein are registered
trademarks or trademarks of HID Global Corporation in the United States and/or other countries.
The absence of a mark, product, service name or logo from this list does not constitute a waiver of the HID Global
trademark or other intellectual property right s c oncerning that name or logo. The names of actual companies,
trademarks, trade names, service marks, images and/or products mentioned herein are the trademarks of their
respective owners. Any rights not expressly granted herein are reserved.
Revision History
Date Author Description
Version
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
Page 20

FT2011 and Juniper Secure Access | SAML 2.0 Channel Integration Handbook
External Release | © 2012
20
+1 949.732.2000
Americas
US Federal
Europe
Asia Pacific
Web
+1 510.574.0100
+1 571.522.1000
+33 (0) 1.42.04.84.00
+61 (0) 3.9809.2892
http://www.hidglobal.com/identity-assurance
Corporate Headquarters
15370 Barranca Parkway
Irvine, CA 92618
www.hidglobal.com
-2013 HID Global Corporation/ASSA ABLOY AB. All rights reserved. Page |
 Loading...
Loading...