Page 1

Chapter 15: Customizing the public access interface 194
DRAFT
Source code for the internal pages
This section presents commented source code for the default internal pages.
Important: Do not create your own pages by saving a page from within your web
browser. The server side code is removed when you do this and the resulting
pages will not work. Use the examples in this section or those on the CD in
\HTML\Colubris\Internal as the basis for your pages.
Login page
<!-- Colubris -->
<!-- Default -->
<!-- iPass
<WISPAccessGatewayParam>
<Redirect>
<MessageType>100</MessageType>
<ResponseCode><% iPassGetRedirectResponseCode(); %></ResponseCode>
<AccessProcedure><% iPassGetAccessProcedure(); %></AccessProcedure>
<LocationName><% iPassGetLocationName(); %></LocationName>
<AccessLocation><% iPassGetAccessLocation(); %></AccessLocation>
<LoginURL><% iPassGetLoginUrl(); %></LoginURL>
<AbortLoginURL><% iPassGetAbortLoginUrl(); %></AbortLoginURL>
</Redirect>
</WISPAccessGatewayParam>
-->
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"
"http://www.w3.org/TR/1999/REC-html401-19991224/loose.dtd">
<html lang="en">
<head>
<meta http-equiv="content-type" content="text/html; charset=iso-8859-1">
<meta http-equiv="Expires" CONTENT="0">
<meta http-equiv="Cache-Control" CONTENT="no-cache">
<meta http-equiv="Pragma" CONTENT="no-cache">
<title>Login</title>
<style type="text/css">
<!--
.labels {
font-family: verdana, sans-serif;
}
#title {
font-size: 14px;
color: #000000;
padding-left: 5px;
}
#tags {
font-size: 10px;
color: #000000;
}
#error {
font-size: 12px;
color: #CC0000;
font-weight: bold;
}
#input {
font-family: verdana, sans-serif;
font-size: 11px;
Page 2

Chapter 15: Customizing the public access interface 195
width: 120px;
color: #003366;
}
#submit {
font-family: verdana, sans-serif;
font-size: 10px;
font-weight: bold;
color: #003366;
}
-->
</style>
<script language="Javascript">
//Make sure the required information was entered
function setfocus() {
if (document.forms[0]) {
document.forms[0].elements[0].focus();
}
}
//-->
</script>
</head>
<body bgcolor="#FFFFFF" onLoad="setfocus();">
DRAFT
<form action="/goform/HtmlLoginRequest" method="POST">
<table border="0" width="99%" height="70%" cellspacing="0" cellpadding="0">
<tr><td align="center" valign="middle">
<table border="0" width="300" cellspacing="0" cellpadding="3">
<tr bgcolor="#FFFFFF">
<td>
<img src="/logo.gif" alt="" width="125" height="50" border="0">
</td>
</tr>
<tr>
<td align="center">
<span class="labels" ID="title">
<%GetAuthenticationErrorMessage();%>
<%GetRadiusReplyMessage();%>
<%GetMsChapV2Failed();%>
</span>
</td>
</tr>
</table>
<br>
<table border="0" width="300" cellspacing="0" cellpadding="3" bgcolor="#CC0033">
<tr>
<td align="center" valign="middle" colspan="2">
<table border="0" width="300" cellspacing="0" cellpadding="4" bgcolor="#E6E6E6">
<tr>
<td align="right">
<span class="labels" ID="tags">Username:</span>
</td>
<td>
<input type="text" name="username" maxlength="30" size="32">
</td>
<td> </td>
</tr>
<tr>
<td align="right">
<span class="labels" ID="tags">Password:</span>
Page 3
Chapter 15: Customizing the public access interface 196
</td>
<td>
<input type="password" name="password" maxlength="30" size="32">
</td>
<td valign="bottom">
<input type="submit" name="login" value="Go >>">
</td>
</tr>
<tr>
<td>
<input type="hidden" name="original_url" value=<%GetOriginalUrl();%>>
</td>
</tr>
</table>
</td>
</tr>
</table>
</td></tr>
</table>
</form>
</body>
</html>
DRAFT
Transport page
<!-- Colubris -->
<!-- Default -->
<!-- iPass
<WISPAccessGatewayParam>
<AuthenticationReply>
<MessageType>120</MessageType>
<ResponseCode><% iPassGetLoginResponseCode(); %></ResponseCode>
<ReplyMessage><% GetRadiusReplyMessage(); %></ReplyMessage>
<LogoffURL><% iPassGetLogoffUrl(); %></LogoffURL>
</AuthenticationReply>
</WISPAccessGatewayParam>
-->
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<html>
<head>
<meta http-equiv="content-type" content="text/html; charset=iso-8859-1">
<meta http-equiv="Expires" CONTENT="0">
<meta http-equiv="Cache-Control" CONTENT="no-cache">
<meta http-equiv="Pragma" CONTENT="no-cache">
<meta http-equiv="refresh" content="1; URL=<%GetWelcomeUrl();%>">
<title>Transport</title>
<script type="text/javascript" language="Javascript">
<!-function opensessionwin(whichone) {
// Define the size of your remote window in pixels with "width" and "height."
remote =
window.open("","sessionwin","width=240,height=400,toolbar=0,location=0,directories=0,status=0,me
nubar=0,scrollbars=1,resizable=1");
if (remote.blur) remote.focus();
// Put the full url of your remote document where you see "URL".
remote.location.href = "<%GetSessionUrl();%>";
Page 4

Chapter 15: Customizing the public access interface 197
if (remote.opener == null) remote.opener = window;
remote.opener.name = "opener";
}
//-->
</script>
</head>
<body onload="opensessionwin();" bgcolor="#FFFFFF">
<font face="verdana, arial, helvetica" size="2">
<h4>This should take 1 second...</h4>
If you are not redirected within a few seconds, please <a href="<%GetWelcomeUrl();%>">click here</
a>.
If you have JavaScript disabled and the session page doesn't appear, please <a
href="<%GetSessionUrl();%>">click here</a>.
</font>
</body>
</html>
DRAFT
Session page
<!-- Colubris -->
<!-- Default -->
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<html>
<head>
<meta http-equiv="content-type" content="text/html; charset=iso-8859-1">
<meta http-equiv="Expires" CONTENT="0">
<meta http-equiv="Cache-Control" CONTENT="no-cache">
<meta http-equiv="Pragma" CONTENT="no-cache">
<% SetSessionRefreshInterval("20");%>
<title>Session</title>
</head>
<body bgcolor="#FFFFFF">
<table border="0" cellpadding="0" cellspacing="5" align="center" style="border:1px dotted #CC0000">
<tr>
<td colspan="2" align="center"> <img src="/logo.gif" alt="" width="125" height="50"
border="0"></td>
</tr>
<tr>
<td colspan="2">
<font face="verdana" size="3"><b>Session</b></font>
</td>
</tr>
<tr>
<td colspan="2" align="center">
<hr noshade size="1" color="#CCCCCC">
<font face="verdana" size="1" color="#FF0000">
Please bookmark this page for logout
</font>
<hr noshade size="1" color="#CCCCCC">
</td>
</tr>
<tr>
<td align="right"><font face="verdana" size="1">Status:</font></td>
<td><font face="verdana" size="1"><b><% GetSessionStateMessage(); %></b></font></td>
</tr>
<tr>
<td align="right"><font face="verdana" size="1">Session Time (Cur/Left/Max):</font></td>
Page 5

Chapter 15: Customizing the public access interface 198
<td><font face="verdana" size="1"><b><% GetSessionTime(); %> / <%
GetSessionRemainingTime(); %> / <% GetMaxSessionTime(); %></b></font></td>
</tr>
<tr>
<td align="right"><font face="verdana" size="1">Idle time (Cur/Left/Max):</font></td>
<td><font face="verdana" size="1"><b><% GetSessionIdleTime(); %> / <%
GetSessionRemainingIdleTime(); %> / <% GetMaxSessionIdleTime(); %></b></font></
td>
</tr>
<tr>
<td align="right"><font face="verdana" size="1">Received Packets (Cur/Left/Max):</font></td>
<td><font face="verdana" size="1"><b><% GetSessionInputPackets(); %> / <%
GetSessionRemainingInputPackets(); %> / <% GetMaxSessionInputPackets(); %></
b></font></td>
</tr>
<tr>
<td align="right"><font face="verdana" size="1">Received Octets (Cur/Left/Max):</font></td>
<td><font face="verdana" size="1"><b><% GetSessionInputOctets(); %> / <%
GetSessionRemainingInputOctets(); %> / <% GetMaxSessionInputOctets(); %></b></
font></td>
</tr>
<tr>
<td align="right"><font face="verdana" size="1">Transmit Packets (Cur/Left/Max):</font></td>
<td><font face="verdana" size="1"><b><% GetSessionOutputPackets(); %> / <%
GetSessionRemainingOutputPackets(); %> / <% GetMaxSessionOutputPackets(); %></
b></font></td>
</tr>
<tr>
<td align="right"><font face="verdana" size="1">Transmit Octets (Cur/Left/Max):</font></td>
<td><font face="verdana" size="1"><b><% GetSessionOutputOctets(); %> / <%
GetSessionRemainingOutputOctets(); %> / <% GetMaxSessionOutputOctets(); %></
b></font></td>
</tr>
<tr>
<td colspan="2" align="right" valign="bottom">
<form action="/goform/HtmlLogout" method="post" >
<input type="submit" name="logoutsession" value="Logout">
</form>
</td>
</tr>
</table>
DRAFT
Fail page
</body>
</html>
<!-- Colubris -->
<!-- Default -->
<!-- iPass
<WISPAccessGatewayParam>
<LogoffReply>
<MessageType>130</MessageType>
<ResponseCode><% iPassGetLogoutResponseCode(); %></ResponseCode>
</LogoffReply>
</WISPAccessGatewayParam>
-->
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<html>
<head>
<meta http-equiv="Expires" CONTENT="0">
<meta http-equiv="Cache-Control" CONTENT="no-cache">
<meta http-equiv="Pragma" CONTENT="no-cache">
Page 6

Chapter 15: Customizing the public access interface 199
<title>Window</title>
</head>
<body bgcolor="#FFFFFF">
<table border="0" cellpadding="0" cellspacing="0" width="178" style="border:1px dotted #CC0000">
<tr>
<td colspan="2"> <img src="/logo.gif" alt="" width="125" height="50" border="0"></td>
</tr>
<tr>
<td> </td>
<td><font face="verdana" size="1"><b><%GetAuthenticationErrorMessage();%></b></font></td>
</tr>
</table>
</body>
</html>
DRAFT
Page 7

Chapter 15: Customizing the public access interface 200
DRAFT
Source code for the external pages
Sample external pages are provided on the CD in the folder
\HTML\Colubris\External. Three versions are included for each page: HTML,
ASP, and PHP.
Welcome page
HTML
<!-This file remains on your webserver and is fully customisable by you.
You also have access to the CGI variables which are defined in the URL
that calls this page.
For example, in this file the calling welcome-url is:
welcome-url=https://207.35.116.198:8888/colubris-php/
welcome.php?site=%s&user=%u&wantedurl=%o
-->
<html>
<head>
<title>Welcome</title>
</head>
<body>
Welcome
</body>
</html>
ASP
<!-This file remains on your webserver and is fully customisable by you.
You also have access to the CGI variables which are defined in the URL
that calls this page.
For example, in this file the calling welcome-url is:
welcome-url=https://207.35.116.198:8888/colubris-php/
welcome.php?site=%s&user=%u&wantedurl=%o
-->
<%@ Language=VBScript %>
<%
site = Request("site")
user = Request("user")
wantedurl = Request("wantedurl")
%>
<html>
<head>
<title>Welcome</title>
</head>
<body>
Welcome <%=user%>, to <%=site%>
<br>
The URL you were trying to access was <a href="<%=wantedurl%>"><%=wantedurl%></a>.
</body>
</html>
Page 8
Chapter 15: Customizing the public access interface 201
DRAFT
PHP
<!-This file remains on your webserver and is fully customisable by you.
You also have access to the CGI variables which are defined in the URL
that calls this page.
For example, in this file the calling welcome-url is:
welcome-url=https://207.35.116.198:8888/colubris-php/
welcome.php?site=%s&user=%u&wantedurl=%o
-->
<? /*
PHP makes QUERY STRING variables immediatly available to any
PHP scripts you embed in your file.
*/ ?>
<html>
<head>
<title>Welcome</title>
</head>
<body>
Welcome <? echo $user; ?>, to <? echo $site; ?>
<br>
The URL you were trying to access was <a href="<? echo $wantedurl; ?>"><? echo $wantedurl; ?></
a>.
Goodbye page
</body>
</html>
HTML
<!-This file remains on your webserver and is fully customisable by you.
For example, in this file the calling goodbye-url is:
goodbye-url=https://207.35.116.198:8888/colubris-php/goodbye.php?site=%s&user=%u
-->
<html>
<head>
<title>Logout</title>
</head>
<body>
Thank you.
</body>
</html>
ASP
<!-This file remains on your webserver and is fully customisable by you.
For example, in this file the calling goodbye-url is:
goodbye-url=https://207.35.116.198:8888/colubris-php/goodbye.php?site=%s&user=%u
-->
<%@ Language=VBScript %>
<%
site = Request("site")
user = Request("user")
Page 9

Chapter 15: Customizing the public access interface 202
wantedURL = Request("wantedURL")
%>
<html>
<head>
<title>Logout</title>
</head>
<body>
Thank you <%=user%>
</body>
</html>
DRAFT
PHP
<!-This file remains on your webserver and is fully customisable by you.
You also have access to the CGI variables which are defined in the URL
that calls this page.
For example, in this file the calling goodbye-url is:
goodbye-url=https://207.35.116.198:8888/colubris-php/goodbye.php?site=%s&user=%u
-->
Login Error page
<? /*
PHP makes QUERY STRING variables immediatly available to any
PHP scripts you embed in your file.
*/ ?>
<html>
<head>
<title>Logout</title>
</head>
<body>
Thank you <? echo $user; ?>.
</body>
</html>
HTML
<!-This file remains on your webserver and is fully customisable by you.
You also have access to the CGI variables which are defined in the URL
that calls this page.
For example, in this file the calling login-err-url is:
login-err-url=https://207.35.116.198:8888/colubris-php/login-error.php?site=%s&user=%u
-->
<html>
<head>
<title>Login Error</title>
</head>
<body>
There has been a login error.
Page 10

Chapter 15: Customizing the public access interface 203
</body>
</html>
DRAFT
ASP
<!-This file remains on your webserver and is fully customisable by you.
You also have access to the CGI variables which are defined in the URL
that calls this page.
For example, in this file the calling login-err-rl is:
login-err-url=https://207.35.116.198:8888/colubris-php/login-error.php?site=%s&user=%u
-->
<%@ Language=VBScript %>
<%
site = Request("site")
user = Request("user")
wantedurl = Request("wantedurl")
%>
<html>
<head>
<title>Login Error</title>
</head>
<body>
Sorry <%=user%><br>
There has been a login error.
</body>
</html>
PHP
<!-This file remains on your webserver and is fully customisable by you.
You also have access to the CGI variables which are defined in the URL
that calls this page.
For example, in this file the calling login-err-url is:
login-err-url=https://207.35.116.198:8888/colubris-php/login-error.php?site=%s&user=%u
-->
<? /*
PHP makes QUERY STRING variables immediately available to any
PHP scripts you embed in your file.
*/ ?>
<html>
<head>
<title>Login Error</title>
</head>
<body>
Sorry <? echo $user; ?>.<br>
There has been a login error.
</body>
</html>
Page 11

Chapter 15: Customizing the public access interface 204
DRAFT
Remote login page
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"
"http://www.w3.org/TR/1999/REC-html401-19991224/loose.dtd">
<html lang="en">
<head>
<meta http-equiv="content-type" content="text/html; charset=iso-8859-1">
<meta http-equiv="Expires" CONTENT="0">
<meta http-equiv="Cache-Control" CONTENT="no-cache">
<meta http-equiv="Pragma" CONTENT="no-cache">
<title>Login</title>
<style type="text/css">
<!--
.labels {
font-family: verdana, sans-serif;
}
#title {
font-size: 14px;
color: #000000;
padding-left: 5px;
}
#tags {
font-size: 10px;
color: #000000;
}
#error {
font-size: 12px;
color: #CC0000;
font-weight: bold;
}
#input {
font-family: verdana, sans-serif;
font-size: 11px;
width: 120px;
color: #003366;
}
#submit {
font-family: verdana, sans-serif;
font-size: 10px;
font-weight: bold;
color: #003366;
}
-->
</style>
<script language="Javascript">
//Make sure the required information was entered
function setfocus() {
if (document.forms[0]) {
document.forms[0].elements[0].focus();
}
}
//-->
</script>
</head>
<body bgcolor="#FFFFFF" onLoad="setfocus();">
<form action="https://cn3000.wireless.colubris.com:8090/goform/HtmlLoginRequest"
method="POST">
Page 12

Chapter 15: Customizing the public access interface 205
<table border="0" width="99%" height="70%" cellspacing="0" cellpadding="0">
<tr><td align="center" valign="middle">
<table border="0" width="300" cellspacing="0" cellpadding="3">
<tr bgcolor="#FFFFFF">
<td>
<img src="/logo.gif" alt="" width="125" height="50" border="0">
</td>
<td valign="bottom" align="right">
<span class="labels" ID="title">
</td>
<td valign="bottom" align="right">
<span class="labels" ID="title">
</td>
<td valign="bottom" align="right">
<span class="labels" ID="title">
</td>
</tr>
</table>
<br>
<table border="0" width="300" cellspacing="0" cellpadding="3" bgcolor="#CC0033">
<tr>
<td align="center" valign="middle" colspan="2">
<table border="0" width="300" cellspacing="0" cellpadding="4" bgcolor="#E6E6E6">
<tr>
<td align="right">
<span class="labels" ID="tags">Username:</span>
</td>
<td>
<input type="text" name="username" maxlength="30" size="32">
</td>
<td> </td>
</tr>
<tr>
<td align="right">
<span class="labels" ID="tags">Password:</span>
</td>
<td>
<input type="password" name="password" maxlength="30" size="32">
</td>
<td valign="bottom">
<input type="submit" name="login" value="Go >>">
</td>
</tr>
</table>
</td>
</tr>
</table>
DRAFT
</td></tr>
</table>
</form>
</body>
</html>
Page 13

Chapter 15: Customizing the public access interface 206
DRAFT
Page 14

Chapter 16: Customizing CN3200 and customer settings 207
Chapter 16: Customizing CN3200 and customer settings
DRAFT
Chapter 16
Customizing CN3200 and customer settings
This chapter presents a summary of the configuration settings you can
define to customize the operation of your public access network and
customer accounts.
Page 15

Chapter 16: Customizing CN3200 and customer settings 208
DRAFT
Overview
The CN3200 uses a third-party RADIUS server to store configuration settings for
customer accounts, accounting data, as well as certain operating settings for the
public access network. The configuration settings are stored in profiles, which
you must create before the public access interface can be used.
The minimum setup you must define is as follows:
• Define RADIUS client settings for the CN3200
Any device that uses the authentication services of a RADIUS server is called
a RADIUS client. Therefore, each CN3200 is considered to be a RADIUS client
and you must define client settings for each one that you intend to install.
See page 213 for details.
• Create a RADIUS profile for the CN3200
Before it can activate the public access interface, the CN3200 must log into a
RADIUS server and retrieve certain operating settings which you must define.
Therefore, you must create at least one RADIUS profile for use by the CN3200.
If you have multiple CN3200s, they can all be associated with a single RADIUS
profile.
See page 214 for details.
• Create a RADIUS profile for one or more customers
The customer profile is used to authenticate customers when they login. It
contains settings that define the characteristics of their account.
Page 16

Chapter 16: Customizing CN3200 and customer settings 209
DRAFT
RADIUS attributes
Attributes are configuration parameters that you can attach to a RADIUS profile.
The CN3200 supports standard RADIUS attributes and a Colubris Networks
vendor-specific attribute.
Standard RADIUS
attributes
The CN3200 supports the following RADIUS attributes. (Attributes starting with
MS are Microsoft and are not standard.)
Access Request
• Acct-Session-Id
• NAS-Port
• NAS-Port-Type
• User-Name
• Calling-Station-Id
• Called-Station-Id
• User-Password
• CHAP-Password
• CHAP-Challenge
• MSCHAP-Challenge
• MSCHAP-Response
• MSCHAPv2-Response
• EAP-Message
• State
• NAS-Identifier
• NAS-Ip-Address
• Framed-MTU
• Connect-Info
• Service-Type
• Message-Authenticator
Access Accept
• MS-MPPE-Recv-Key
• MS-MPPE-Send-Key
• Service-Type
• EAP-Message
• Class
• Idle-Timeout
• Session-Timeout
• Acct-Interim-Interval
• Tunnel-type
• Tunnel-meduim-type
• Tunnel-private-group
Access Reject
• MSCHAP-Error
• Reply-Message
• EAP-Message
Access Challenge
• EAP-Message
• State
Accounting Request
•User-Name
• NAS-Port
• NAS-Port-Type
• NAS-Identifier
• NAS-Ip-Address
• Acct-Status-Type
• Calling-Station-Id
• Called-Station-Id
• Acct-Event-Timestamp
• Acct-Delay-Time
• Acct-Session-Id
• Acct-Authentic
• Acct-Session-Time
• Acct-Input-Octets
• Acct-Input-Gigawords
• Acct-Input-Packets
• Acct-Output-Octets
• Acct-Output-Gigawords
• Acct-Output-Packets
• Acct-Terminate-Cause
• Class
• Framed-Ip-Address
Accounting Response
• No attribute
Interim accounting updates
To enable interim accounting updates for each customer you must define a value
for the RADIUS attribute Acct-Interim-Interval. This sets the frequency with which
the CN3200 will send accounting information to the RADIUS server.
Page 17

Chapter 16: Customizing CN3200 and customer settings 210
DRAFT
Colubris Networks
vendor-specific
attributes
In certain cases, the set of standard RADIUS attributes needs to be extended to
specify custom settings for specific types of equipment. These are called vendorspecific attributes. Colubris Networks has defined two vendor-specific attributes
to support special features on the CN3200, such as the customization of the web
interface and the security certificate. This attribute are:
• Colubris-AVPair
• Colubris-Intercept
These attributes conform to RADIUS RFC 2865.
You may need to define these attributes on your RADIUS server if they are not
already present. In this case, you need to specify the following:
Colubris-AVPair
• SMI network management private enterprise code = 8744
• Vendor-specific attribute type number = 0
• Attribute type = string
Colubris-Intercept
• SMI network management private enterprise code = 8744
• Vendor-specific attribute type number = 1
• Attribute type = integer
Attribute value summary
The following values are permitted for the Colubris-AVPair attribute. These
values are described in greater detail later in this chapter and in Chapter 15.
Important: It is important to specify the attribute values exactly as shown below.
Adding extra spaces between options will result in errors.
CN3200 profile
access-list=
name,action,protocol,address,port,[account,[interval]]
use-access-list=usename
white-list=protocol,address,[port]
ssl-certificate=URL [%s] [%n]
configuration-file=URL [%s] [%n]
mac-address=address[,username[,password]]
default-user-idle-timeout=seconds
default-user-smtp-redirect=hostname:port
default-user-session-timeout=seconds
login-page= URL_of_page
transport-page= URL_of_page
session-page= URL_of_page
fail-page= URL_of_page
logo= URL_of_gif_file
messages= URL_of_text_file
welcome-url= URL_of_page [placeholder]
goodbye-url= URL_of_page [placeholder]
login-err-url= URL_of_page [placeholder]
login-url= URL_of_the_page [placeholder]
ssl-noc-certificate= URL_of_the_Certificate
ssl-noc-ca-certificate= URL_of_the_certificate
Customer profile
smtp-redirect=hostname:port
use-access-list=usename
one-to-one-nat=value
max-input-packets=value
max-output-packets=value
max-input-octets=value
max-output-octets=value
welcome-url= URL_of_page [placeholder]
goodbye-url= URL_of_page [placeholder]
login-err-url= URL_of_page [placeholder]
group=value
essid=value
Page 18

Chapter 16: Customizing CN3200 and customer settings 211
DRAFT
RADIUS limitations
The maximum number of attributes the CN3200 can receive in one request is
limited by the maximum packet size of the UDP protocol which is 64K. Some
networks may drop fragmented UDP packets which may leave you with less than
the maximum size.
Page 19
Chapter 16: Customizing CN3200 and customer settings 212
DRAFT
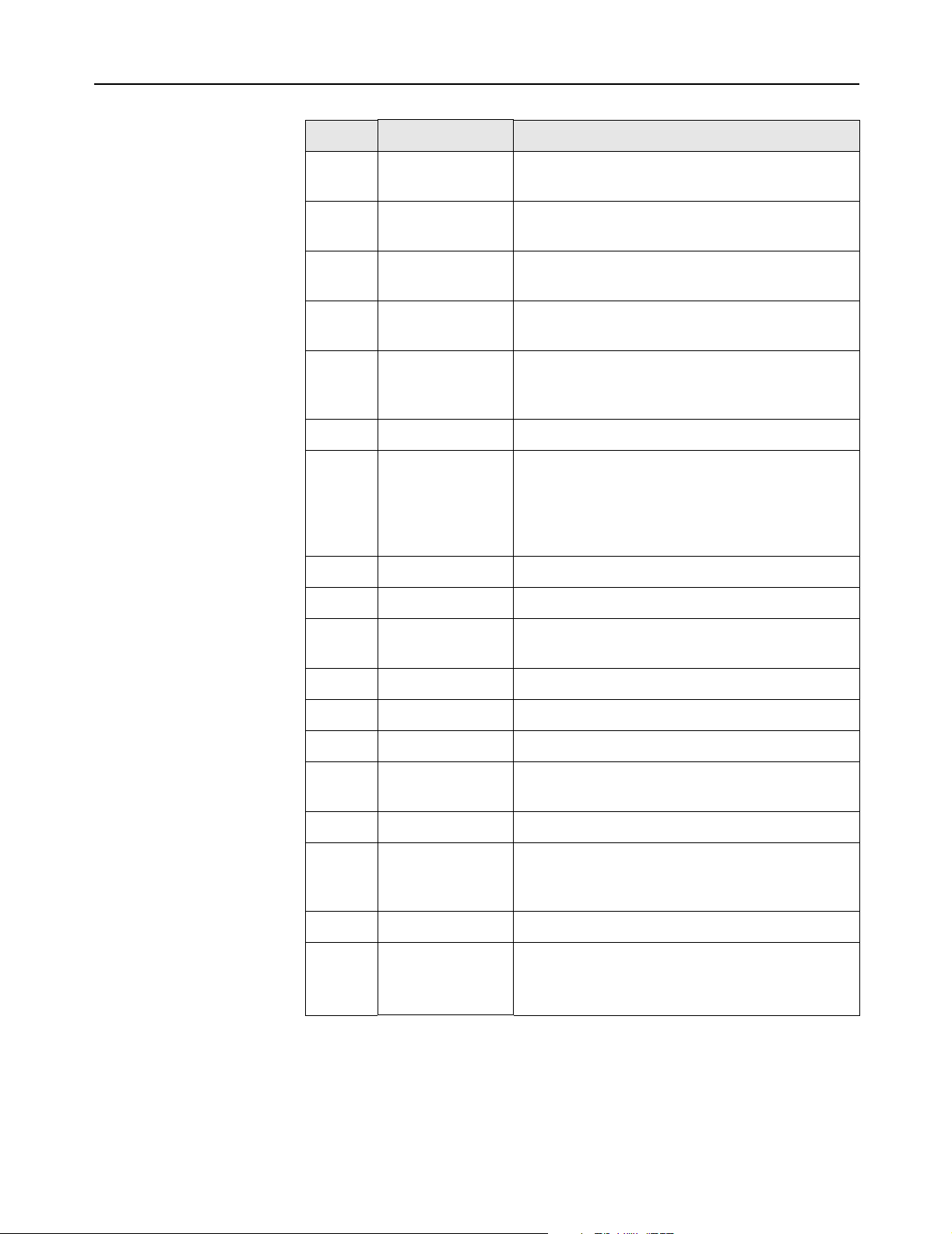
Terminate-AcctCause values
Terminate Acct Cause values are supported as follows:
ID Cause Notes
1 User Request Supported. Indicates that the customer logged
out.
2 Lost Carrier Supported. Indicates that the client station is no
longer alive.
4 Idle Timeout Supported. Customer exceeded the idle timeout
value defind for the session.
5 Session Timeout Supported. Customer exceeded maximum time
defined for the session.
6 Admin Reset Supported. Customer session was terminated by
the CN3200 administrator via SNMP or the
management tool.
7 Admin Reboot Not Supported. (not applicable)
8 Port Error Supported. If two customers are detected using
the same IP address, both are logged out with
this error. Another cause is if an error is
encountered in an access list definition. For
example, an invalid host was specified.
9 NAS Error Not Supported. (not applicable)
10 NAS Request Not Supported. (not applicable)
11 NAS Reboot Supported. Customer was logged out because
the CN3200 was restarted.
12 Port Unneeded Not Supported. (not applicable)
13 Port Preempted Not Supported. (not applicable)
14 Port Suspended Not Supported. (not applicable)
15 Service
Unavailable
16 Callback Not Supported. (not applicable)
17 User Error Supported. An 801.1x client initiated a second
18 Host Request Not Supported. (not applicable)
0x8744
(34628
decimal)
Termination Colubris-specific termination cause. See page
Not Supported. (not applicable)
authentication request for a customer, and this
request was refused.
229 for details.
Page 20

Chapter 16: Customizing CN3200 and customer settings 213
DRAFT
Creating a RADIUS client entry for the CN3200
Any device that uses the authentication services of a RADIUS server is called a
RADIUS client (or RAS client on some systems). Therefore, each CN3200 is
considered to be a RADIUS client and you must define client settings for each
one that you intend to install.
Configuration
settings
Managing shared
secrets
You may need to supply the following information when setting up a RADIUS
client entry:
• Client IP address: This is the IP address assigned to the CN3200’s Internet
port. If the CN3200 is using a PPTP connection to communicate with the
RADIUS server, then this is the address assigned to the CN3200 by the PPTP
server.
• Shared secret: Secret the CN3200 will use to authenticate the packets it
receives from the RADIUS server.
If you are using a PPPoE, DHCP, or PPTP VPN connection when communicating
with the RADIUS server, make sure that the shared secret for each CN3200 is
the same. Also, ensure that all possible IP addresses have been configured on
the RADIUS server.
The username and password assigned to each CN3200 can be different,
enabling you to differentiate between devices.
Page 21

Chapter 16: Customizing CN3200 and customer settings 214
DRAFT
Creating a profile for the CN3200 on the RADIUS server
Before it can activate the public access interface, the CN3200 must log into a
RADIUS server and retrieve certain operating settings that you must define.
Therefore, you must create at least one RADIUS profile for use by the CN3200. If
you have multiple CN3200s, they can all be associated with a single RADIUS
profile.
Supported standard
RADIUS attributes
This section presents all standard RADIUS attributes that are supported by a
CN3200 profile.
Note: In the following definitions, strings are defined as 1 to 253 characters in
length.
Access request
• Acct-Session-Id (32-bit unsigned integer): Random value generated per
authentication by the CN3200.
• NAS-Identifier (string): The NAS ID set on the Security > RADIUS page for the
RADIUS profile being used.
• NAS-Ip-Address 32-bit unsigned integer): The IP address of the port the
CN3200 is using to communicate with the RADIUS server.
• NAS-Port (32-bit unsigned integer): Always 0.
• NAS-Port-Type (32-bit unsigned integer): Always set to 19, which represents
WIRELESS_802_11.
• Calling-Station-Id (string): The MAC address of the CN3200’s LAN port in IEEE
format. For example: 00-02-03-5E-32-1A.
• Called-Station-Id (string): The MAC address of the CN3200’s LAN port in IEEE
format. For example: 00-02-03-5E-32-1A.
• User-Name (string): The username assigned to the CN3200 on the Security >
Authentication page.
• User-Password (string): The password assigned to the CN3200 on the
Security > Authentication page. Encoded as defined in RFC 2865. Only
present when the authentication method for the RADIUS profile is set to PAP.
• CHAP-Password (string): The password assigned to the CN3200 on the
Security > Authentication page. Encoded as defined in RFC 2865. Only
present when the authentication method for the RADIUS profile is set to CHAP.
• CHAP-Challenge (string): Randomly generated by the product. As defined in
RFC 2865. Only present when the authentication method for the RADIUS
profile is set to CHAP. Length = 19 bytes.
• MSCHAP-Challenge (string): As defined in RFC 2433. Only present when the
authentication method for the RADIUS profile is set to MSCHAPv1 or
MSCHAPv2. Length = 8 bytes.
• MSCHAP-Response (string): As defined in RFC 2433. Only present when the
authentication method for the RADIUS profile is set to MSCHAPv1. Length =
49 bytes.
• MSCHAPv2-Response (string): As defined in RFC 2759. Only present when
the authentication method for the RADIUS profile is set to MSCHAPv2. Length
= 49 bytes.
• EAP-Message (string): As defined in RFC 2869. Only present when the
authentication method for the RADIUS profile is set to EAP-MD5.
Page 22
Chapter 16: Customizing CN3200 and customer settings 215
• State (string): As defined in RFC 2865.
• Framed-MTU (32-bit unsigned integer): Hard-coded to 1496.
• Connect-Info (string): The string "HTTPS".
• Service-Type (32-bit unsigned integer): As defined in the config.cfg file. Token
name = service-type-device.
• Message-Authenticator (string): As defined in RFC 2869. Always present even
when not doing an EAP authentication. length = 16 bytes.
• Colubris-AVPair: See the description in the section that follows.
DRAFT
Access accept
• Acct-Interim-Interval (32-bit unsigned integer): When present, it enables the
transmission of RADIUS accounting requests of the Interim Update type.
Specify the number of seconds between each transmission.
• Session-Timeout (32-bit unsigned integer): Maximum time a session can be
active. The CN3200 re-authenticates itself when this timer expires. Omitting
this attribute or specifying 0 will disable the feature. (Note that the
authentication interval is also configurable on the Security > Authentication
page.
• Idle-Timeout (32-bit unsigned integer): Not supported.
• Class (string): As defined in RFC 2865.
• EAP-Message (string): Only supported when authentication is EAP-MD5. Note
that the content will not be read as the RADIUS Access Accept is overriding
whatever indication contained inside this packet.
• Colubris-AVPair: See the description in the section that follows.
Access reject
None.
Access challenge
None.
Accounting request
Accounting information is generated by default. To disable accounting support,
open the Security > Authentication -> Advanced Settings page.
• Acct-Session-Id (32-bit unsigned integer): Random value generated by the
CN3200.
• NAS-Identifier (string): The NAS ID set on the Security > RADIUS page for the
profile being used.
• NAS-Ip-Address (32-bit unsigned integer): The IP address of the port the
CN3200 is using to communicate with the RADIUS server.
• NAS-Port (32-bit unsigned integer): Always 0.
• NAS-Port-Type (32-bit unsigned integer): Always set to 19, which represents
WIRELESS_802_11.
• Calling-Station-Id (string): The MAC address of the CN3200’s LAN port in IEEE
format. For example: 00-02-03-5E-32-1A.
• Called-Station-Id (string): The MAC address of the CN3200’s LAN port in IEEE
format. For example: 00-02-03-5E-32-1A.
Page 23

Chapter 16: Customizing CN3200 and customer settings 216
• User-Name (string): The RADIUS username assigned to the CN3200 on the
Security > Authentication page.
• Class (string). As defined in RFC 2865.
• Framed-IP-Address (32-bit unsigned integer): IP Address of the CN3200’s LAN
port.
• Acct-Status-Type (32-bit unsigned integer): Supported values are Accounting-
On (7) and Accounting-Off (8).
• Acct-Event-Timestamp (32-bit unsigned integer): As defined in RFC 2869.
• Acct-Delay-Time (32-bit unsigned integer): As defined in RFC 2869.
• Acct-Authentic (32-bit unsigned integer): Always set to 1 which means
RADIUS.
DRAFT
Accounting response
None.
Colubris-AVPair
attribute
For each CN3200 profile you can specify one or more instances of a ColubrisAVPair attribute that will be returned upon successful authentication (RADIUS
Accept). Possible values for all instance are grouped into the following
categories:
Feature Description
Custom HTML pages and
URLs, and supporting files
Access list Enables you to create one or more access
White list The white list defines the set of network
Custom security certificate Enables you to replace the Colubris Networks
Configuration file Enables you to store a configuration file at a
MAC authentication Enables you to authenticate devices based on
Enables you to customize the public access
interface. See Chapter 15 for details.
groups which define the set of network
resources that are available to authenticated
customers.
resources that are available to customers before
they are authenticated.
certificate with your own.
central location to automatically update all your
CN3200s.
their MAC addresses.
Access lists
Default user idle timeout Default idle timeout for all customers.
Default user session timeout Default session timeout for all customers.
Default SMTP server Default SMTP server to use for email redirection.
The value of a Colubris-AVPair attribute is always a string. These strings are
always of the form: <item>=<value>
Access lists enable you to create public areas on your network that all customers
can browse, and protected areas that are restricted to specific customer
accounts or groups.
Page 24
Chapter 16: Customizing CN3200 and customer settings 217
DRAFT
Each access list is a set of rules that governs how the CN3200 controls access to
network resources. You can create multiple access lists, each with multiple rules
to manage the traffic on your public access network.
Default setting
By default no access lists are defined. This means that:
• Unauthenticated customers cannot reach any network resources other than
the CN3200 login page.
• Authenticated customer have access to any network resource connected to the
CN3200’s Internet port.
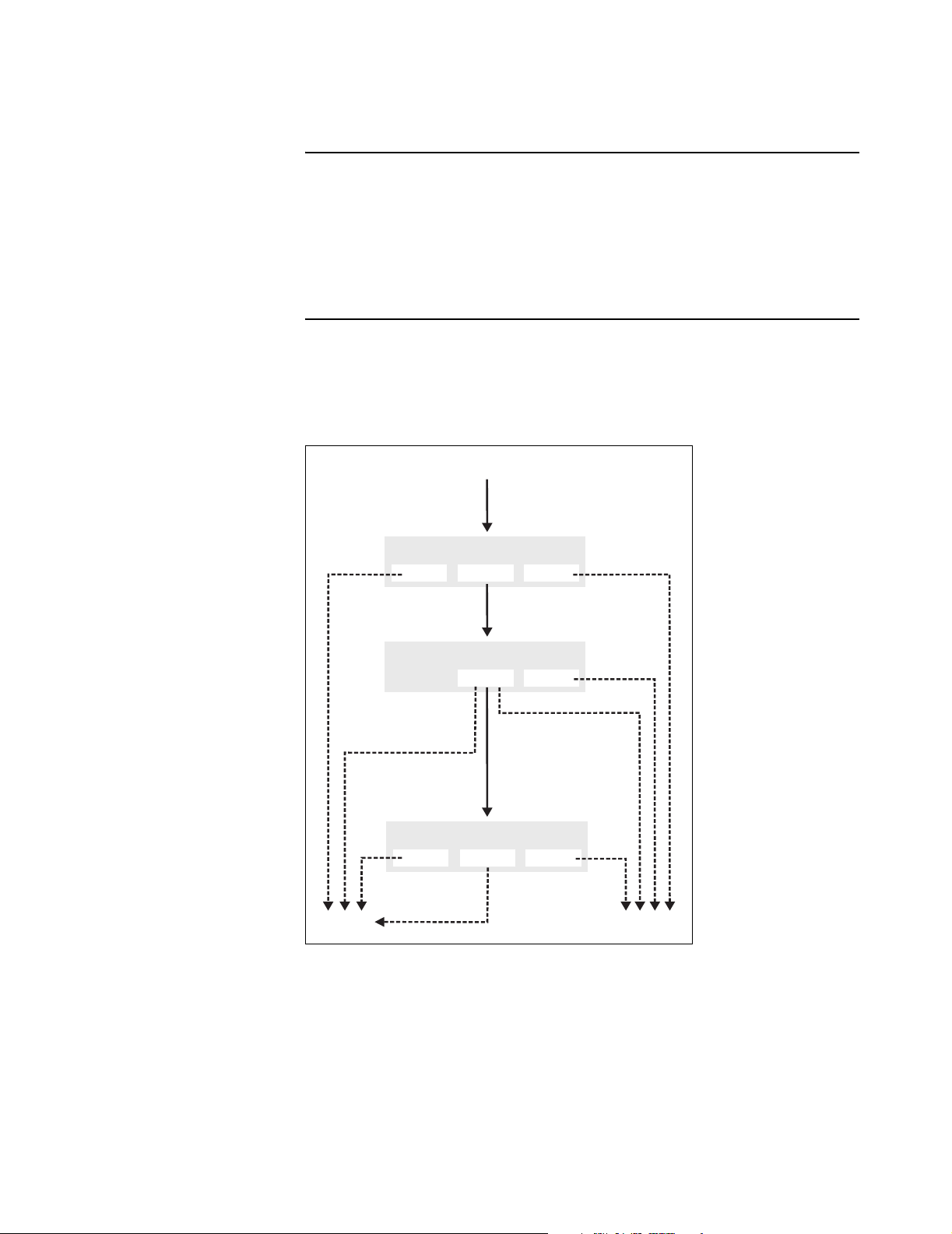
How access lists work
Each customer and each access point can be associated with its own access list.
Incoming traffic cascades through the currently active lists. Traffic that is
accepted or denied by a list is not available to the list that follows it. Traffic that
passes through all lists without being accepted or denied is dropped.
Customer session
Site Profile Access List
DENY
Unauthenticated
Customer Profile Access List
DENY
How traffic flows through the access lists.
NO MATCH ACCEPT
White List
NO MATCH ACCEPT
Authenticated and no
user access list exists
Authenticated and
an access list exists
NO MATCH ACCEPT
Internet portDropped
Note: The white list is a less-powerful version of the access list that is maintained
for compatibility with previous releases. Its functionality is completely superseded
by the access list feature. The access list feature should be used in its place.
Page 25
Chapter 16: Customizing CN3200 and customer settings 218
DRAFT
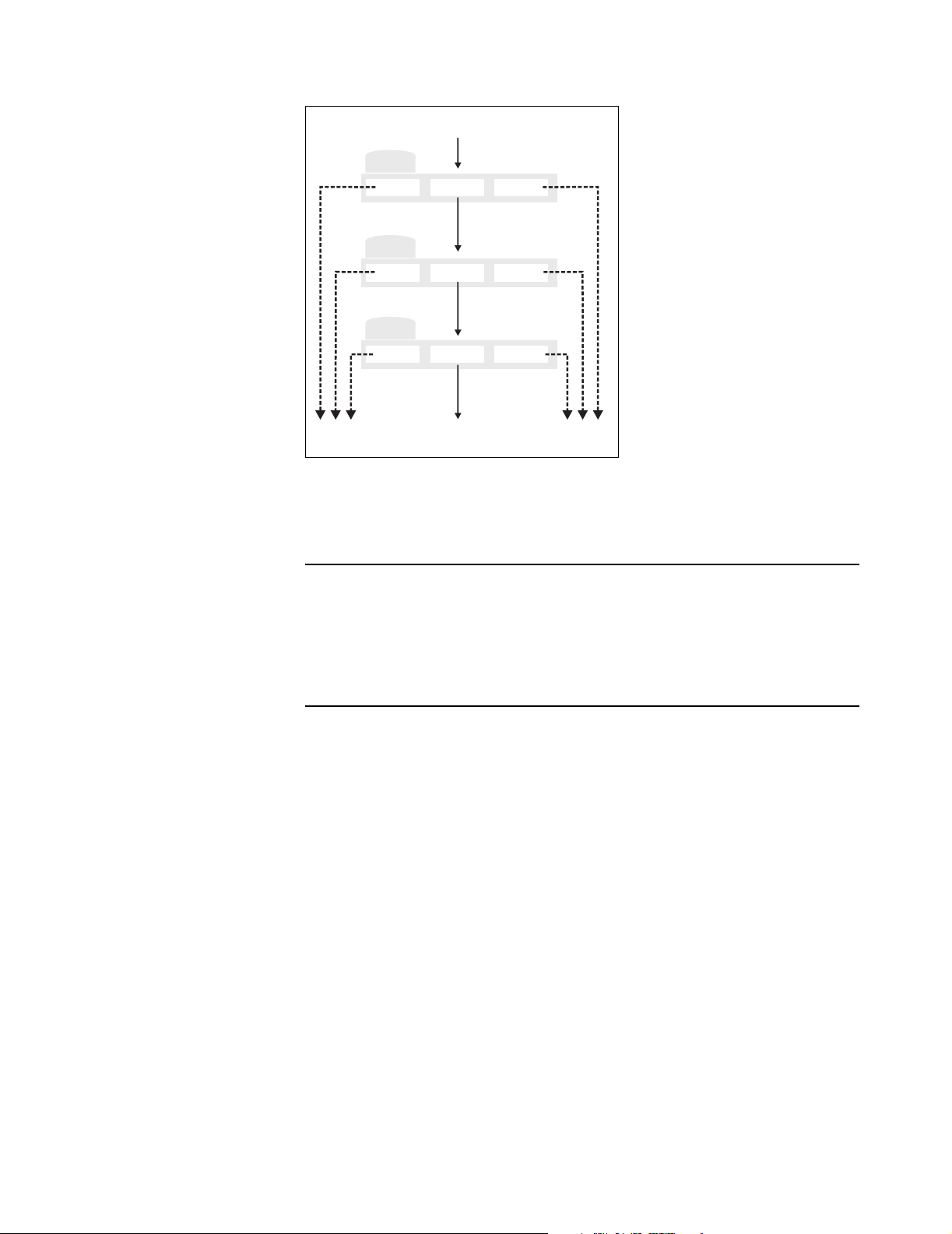
Within each access list, traffic cascades through the list rules in a similar manner.
Incoming traffic
Rule 1
DENY
Rule 2
DENY
Rule 3
DENY
NO MATCH
NO MATCH
NO MATCH
ACCEPT
ACCEPT
ACCEPT
DENY
How traffic flows through the access list rules.
NO MATCH ACCEPT
Rules are numbered according to the order in which they are added. Only data
that is not accepted or denied by a rule is available to the next rule in the list.
Accounting support
Each rule in an access list can be configured with an account name for billing
purposes. The CN3200 will send billing information based on the amount of
traffic matched by the rule.
This lets you create rules to track and bill traffic to particular destinations.
Tips on using the access list
With certificates
• If you replaced the default SSL certificate on the CN3200 with one signed by a
well-known CA, you should define the access list to permit access to the CA
certificate for all non-authenticated customers. This enables the customer’s
browser to verify that the certificate is valid without displaying any warning
messages.
• Customers may have configured their web browsers to check all SSL
certificates against the Certificate Revocation List (CRL) maintained by the CA
that issued the certificate. The location of the CRL may be configured in the
browser, or embedded in the certificate. The access list should be configured
to permit access to the CRL, otherwise the customer’s browser will time out
before displaying the login page.
Remote login page
If you are using the remote login page feature, make sure that access to the web
server hosting the page must is granted to all unauthenticated customers.
SMTP redirect
If an unauthenticated customer establishes a connection to their email server, the
SMTP redirect feature will not work once the customer logs in. The customer’s
email will still be sent to the original email server.
To avoid this, do not use an access list to open TCP port 25 for unauthenticated
customers.
Page 26

Chapter 16: Customizing CN3200 and customer settings 219
DRAFT
Defining and activating access lists
Access lists are defined by adding the following Colubris-AVPair value string to
the RADIUS profile for a CN3200.
access-list=value
Access lists are activated by adding the following Colubris-AVPair value string to
the RADIUS profile for a CN3200 or a customer.
use-access-list=value
You can define up to 32 access lists. Only one list can be active per profile.
The access list is applied before the white list.
Colubris-AVPair value string
access-list=
name,action,protocol,address,port,[account,[interval]]
use-access-list=usename
Where:
Parameter Description
name
usename
action
protocol
address
port
Specify a name (up to 32 characters long) to identify the access list
this rule applies to. If a list with this name does not exist, a new list
is created. If a list with this name exists, the rule is added to it.
Specify the name of an existing access list. This list is activated for
the current profile. Lists are checked in the order they are activated.
Specify what action the rule takes when it matches incoming traffic.
Two options are available:
• ACCEPT - Allow traffic matching this rule.
• DENY - Reject traffic matching this rule.
Specify the protocol to check: tcp, udp, icmp, all
Specify one of the following:
• IP address or domain name (up to 107 characters in length)
• Subnet address. Include the network mask as follows:
address/subnet mask For example: 192.168.30.0/24
• Use the keyword all to match any address.
• Use the keyword none if the protocol does not take an address
range (ICMP for example).
Specify a specific port to check or a port range as follows:
• none - Used with ICMP (since it has no ports).
• all - Check all ports.
• 1-65535[:1-65535] - Specify a specific port or port range.
account
interval
Specify the name of the customer account the CN3200 will send
billing information to for this rule. Account names must be unique
and can be up to 32 characters in length.
Specify time between interim accounting updates. If you do not
enable this option, accounting information is only sent when a
customer connection is terminated. Range: 5-99999 seconds in 15
second increments.
Page 27

Chapter 16: Customizing CN3200 and customer settings 220
DRAFT
Note: Spaces can be used instead of commas as separators.
Example
This topology shows wireless deployment for a fictitious university campus.
The RADIUS profile for the CN3200 contains:
access-list=everyone,ACCEPT,tcp,192.168.50.2,80
access-list=students,ACCEPT,tcp,192.168.50.1,80,students_reg,500
access-list=students,ACCEPT,all,192.168.40.0/24,all
access-list=students,DENY,all,192.168.20.0/24,all
access-list=students,DENY,all,192.168.30.0/24,all
access-list=students,ACCEPT,all,all.all,student_internet_use,5000
access-list=faculty,ACCEPT,tcp,192.168.50.1,80,faculty_reg,500
access-list=faculty,ACCEPT,all,192.168.30.0/24,all
access-list=faculty,DENY,all,192.168.20.0/24,all
access-list=faculty,DENY,all,192.168.40.0/24,all
access-list=faculty,ACCEPT,all,all.all,faculty_internet_use,5000
use-access-list=everyone
The RADIUS profile for the students contains:
use-access-list=students
The RADIUS profile for the faculty contains:
use-access-list=faculty
This definition creates three access lists: everyone, students, and faculty.
Everyone
This list applies to all users (students, teachers, guests), whether they are
authenticated or not. This is because the list is active on the CN3200, which is
accomplished with the entry:
use-access-list=everyone
It enables everyone to access the public web server.
Students
This list applies to authenticated students only. It is composed of the following
entries:
access-list=students,ACCEPT,tcp,192.168.50.1,80,students_reg,500
Enables web traffic to the registration web server. Accounting data is recorded in
the account students_reg.
access-list=students,ACCEPT,all,192.168.40.0/24,all
Enables traffic to reach the student segment.
access-list=students,DENY,all,192.168.20.0/24,all
access-list=students,DENY,all,192.168.30.0/24,all
These two entries deny access to the faculty subnet and the NOC.
access-list=students,ACCEPT,all,all.all,student_internet_use,5000
Enables all other traffic to reach the Internet (via routers on the backbone LAN
and the router in the NOC). If this last rule did not exist, this traffic would be
dropped.
Page 28

Chapter 16: Customizing CN3200 and customer settings 221
Faculty
This list applies to authenticated faculty members only. It is composed of the
following entries:
access-list=faculty,ACCEPT,tcp,192.168.50.1,80,faculty_reg,500
Enables web traffic to the registration web server. Accounting data is recorded in
the account faculty_reg.
access-list=faculty,ACCEPT,all,192.168.30.0/24,all
Enables traffic to reach the faculty segment.
access-list=faculty,DENY,all,192.168.20.0/24,all
access-list=faculty,DENY,all,192.168.40.0/24,all
These two entries deny access to the student subnet and the NOC.
access-list=faculty,ACCEPT,all,all.all,faculty_internet_use,5000
Enables all other traffic to reach the Internet (via routers on the backbone LAN
and the router in the NOC). If this last rule did not exist, this traffic would be
dropped.
DRAFT
White list
A white list enables you to specify the set of network resources that an
unauthenticated customer has access to. You can define a specific white list for
each CN3200. These definitions are automatically implemented by the CN3200
by adding the appropriate rules to the firewall.
Note: The white list has been superseded by the access list feature. However,
the white list remains supported for backwards compatibility.
Colubris-AVPair value string
white-list=protocol,address,[port]
Where:
Parameter Description
protocol
address
port1
Specify the protocol to allow traffic on: tcp, udp, icmp, all.
Specify the IP address or domain name of a host, or the IP
address of a subnet. Use the keyword all to match any
address. When specifying an IP subnet you must include the
network mask in the following format:
address/subnet mask
Specify the specific port to allow traffic on, or a range. Not valid if
the all option is used for protocol. Use the following syntax to
specify a range:
1-65535[:1-65535]
A range must be suppled for tcp or udp. A single port must be
specified for icmp.
Note: Spaces can be used instead of commas as separators.
The white list applies to the CN3200 itself, and all client stations connected to it.
This means that if you are using customized URLs for the public access interface,
the URLs for the Login Error and Goodbye pages must specify hosts that are
included in the white list.
You can specify up to 128 Colubris-AVPair values containing white list definitions.
Page 29

Chapter 16: Customizing CN3200 and customer settings 222
DRAFT
Examples
white-list=all,192.168.1.10
white-list=tcp,adm.colubris.com,80:90
white-list=udp,192.168.1.0/255.255.255.0,8090:8090
white-list=tcp,192.168.1.0/24,443
Custom SSL
certificate
The CN3200 can retrieve a custom SLL security certificate to replace the
Colubris Networks certificate that is included by default. For more information on
certificates, see Chapter 14.
Colubris-AVPair value string
ssl-certificate=URL [%s] [%n]
Where:
Parameter Description
URL
By using the following placeholder, you can customize the URL for each CN3200.
This is useful when you need to update multiple units.
Placeholder Description
%s The login name assigned to the CN3200.
%n
The certificate is encoded using PKCS#12 format, and will contain:
• the private key of the web server
• the certificate of the web server
The file is locked using a password.
Specify the URL that points to the new certificate.
The NAS ID assigned to the CN3200.
Configuration file
Example
ssl-certificate=http://www.colubris.com/%s_certificate
The CN3200 can retrieve and load a new configuration file automatically, based
on an URL you specify.
Colubris-AVPair value string
configuration-file=URL [%s] [%n]
Where:
Parameter Description
URL
By using the following placeholder, you can customize the URL for each CN3200.
This is useful when you need to update multiple units.
Placeholder Description
%s The login name assigned to the CN3200.
%n
Specify the URL that points to the new configuration file.
The NAS ID assigned to the CN3200.
Example
configuration-file=http://www.colubris.com/%s_configfile
Page 30
Chapter 16: Customizing CN3200 and customer settings 223
DRAFT
MAC authentication
The CN3200 can authenticate devices based on their MAC address. This is
useful for authenticating devices that do not have a web browser (cash registers,
for example). It can also be used to authenticate the CN300.
To make use of this feature you need to define a RADIUS user account for each
device as follows:
• username: Set this to the username you specified in the mac-address value
string. If no username is specified, set the account name to the MAC address
of the device. Use dashes to separate characters in the address. For example:
00-20-E0-6B-4B-44.
• password: Set this to the password you specified in the mac-address value
string. If no password is specified, set this to the same password that is used
for the user account you defined for the CN3200 on the Security >
Authentication page.
Important: The username and password are not encrypted for transmission so it
is important that the link with the RADIUS server is secure.
Colubris-AVPair value string
mac-address=address[,username[,password]]
Where:
Parameter Description
address
Specify the MAC address of the device to authenticate. Use
dashes to separate characters in the address. Do not use
colons (:). For example: 00-20-E0-6B-4B-44.
Default user idle
timeout
username
password
Specify the username to associate with this MAC address.
Maximum 253 alphanumeric characters. The username field
cannot contain a comma.
Specify the password to associate with this MAC address.
Maximum 253 alphanumeric characters. The password field
cannot contain a comma.
Example
Consider the scenario where several CN300s are installed with a CN3200. If the
CN300s are going to perform firmware upgrades from a remote web or FTP
server, they will need to log in to the public access network. By using MAC-based
authentication, this can easily be accomplished. (This also requires that the
access list on the CN3200 permits access to the web or FTP server.)
Use this to set the default idle timeout for all customers whose RADIUS profile
does not contain a value for the RADIUS attribute idle-timeout.
Colubris-AVPair value string
default-user-idle-timeout=seconds
Where:
Parameter Description
seconds
Specify the maximum amount of time a customer session
can be idle. Once this time expires, the session is
automatically terminated. A value of 0 means no timeout.
Page 31

Chapter 16: Customizing CN3200 and customer settings 224
DRAFT
Default user
session timeout
Default SMTP
server
Use this to set the default session timeout for all customers whose RADIUS
profile does not contain a value for the RADIUS attribute session-timeout.
Colubris-AVPair value string
default-user-session-timeout=seconds
Where:
Parameter Description
seconds
Use this to set the default SMTP server address for all customer sessions. This
address is used if a specific server is not set for a particular customer. See page
228 for details.
Specify the maximum amount of time a customer session
can be connected. Once this time expires, the session is
automatically terminated. A value of 0 means no timeout.
Colubris-AVPair value string
default-user-smtp-redirect=hostname:port
Where:
Parameter Description
hostname
Specify the the IP address or domain name of the e-mail
server. Maximum length is 253 characters.
port
Specify the the on the e-mail server to relay to. Range: 1 to
65535.
Page 32

Chapter 16: Customizing CN3200 and customer settings 225
DRAFT
Creating customer profiles on the RADIUS server
You must create at least one RADIUS customer profile. Multiple customer
accounts can be associated with a single RADIUS profile.
Supported RADIUS
attributes
This section presents all RADIUS and Colubris attributes that are supported by
for a CN3200 profile.
Note: In the following definitions, strings are defined as 1 to 253 characters in
length.
Access request
• Acct-Session-Id (32-bit unsigned integer): Random value generated by the
CN3200.
• NAS-Identifier (string): The NAS ID set on the Security > RADIUS page for the
profile being used.
• NAS-Ip-Address (32-bit unsigned integer): The IP address of the port the
CN3200 is using to communicate with the RADIUS server.
• NAS-Port (32-bit unsigned integer): A virtual port number starting at 1.
Assigned by the CN3200.
• NAS-Port-Type (32-bit unsigned integer): Always set to 19, which represents
WIRELESS_802_11.
• Calling-Station-Id (string): The MAC address of the CN3200’s LAN port in IEEE
format. For example: 00-02-03-5E-32-1A.
• State (string): As defined in RFC 2865.
• Framed-MTU (32-bit unsigned integer): Hard-coded value of 1496. The value is
always four bytes lower than the wireless MTU maximum which is 1500 bytes
in order to support IEEE802dot1x authentication.
• Connect-Info (string): The string "HTTPS".
• Service-Type (32-bit unsigned integer): As defined in the config.cfg file. Token
name = service-type-user.
• Message-Authenticator (string): As defined in RFC 2869. Always present even
when not doing an EAP authentication. length = 16 bytes.
• User-Name (string): The username assigned to the customer or a device when
using MAC authentication.
• User-Password (string): The password supplied by a customer or device when
logging in. Encoded as defined in RFC 2865. Only present when the
authentication method for the RADIUS profile is set to PAP.
• CHAP-Password (string): The password assigned to the CN3200 on the
Security > Authentication page. Encoded as defined in RFC 2865. Only
present when the authentication method for the RADIUS profile is set to CHAP.
• CHAP-Challenge (string): Randomly generated by the product. As defined in
RFC 2865. Only present when the authentication method for the RADIUS
profile is set to CHAP. Length = 19 bytes.
• MSCHAP-Challenge (string): As defined in RFC 2433. Only present when the
authentication method for the RADIUS profile is set to MSCHAPv1 or
MSCHAPv2. Length = 8 bytes.
• MSCHAP-Response (string): As defined in RFC 2433. Only present when the
authentication method for the RADIUS profile is set to MSCHAPv1. Length =
49 bytes.
Page 33

Chapter 16: Customizing CN3200 and customer settings 226
• MSCHAPv2-Response (string): As defined in RFC 2759. Only present when
the authentication method for the RADIUS profile is set to MSCHAPv2. Length
= 49 bytes.
• EAP-Message (string): As defined in RFC 2869. Only present when the
authentication method for the RADIUS profile is set to EAP-MD5.
• Colubris-AVPair: See the description in the section that follows.
DRAFT
Access accept
• Acct-Interim-Interval (32-bit unsigned integer): When present, it enables the
transmission of RADIUS accounting requests of the Interim Update type.
Specify the number of seconds between each transmission.
• Session-Timeout (32-bit unsigned integer): Maximum time a session can be
active. The CN3200 re-authenticates itself when this timer expires. Omitting
this attribute or specifying 0 will disable the feature. (Note that the
authentication interval is also configurable on the Security > Authentication
page.
• Idle-Timeout (32-bit unsigned integer): Maximum idle time in seconds allowed
for the customer. Once reached, the customer session is terminated with
termination-cause IDLE-TIMEOUT. Omitting the attribute or specifying 0
disables the feature.
• Class (string): As defined in RFC 2865.
• EAP-Message (string): Only supported when authentication is EAP-MD5. Note
that the content will not be read as the RADIUS Access Accept is overriding
whatever indication contained inside this packet.
• MS-MPPE-Recv-Key: As defined by RFC 3078.
• MS-MPPE-Send-Key: As defined by RFC 3078.
• Tunnel-type: Only used when assigning a specific VLAN number to a
customer. In this case it must be set to "VLAN".
• Tunnel-medium-type = Only used when assigning a specific VLAN number to a
customer. In this case it must be set to "802".
• Tunnel-private-group = Only used when assigning a specific VLAN number to a
customer. In this case it must be set to the VLAN number.
Access reject
• MSCHAP-Error (string): A MSCHAP specific error as defined by RFC 2433.
• Reply-Message (string): This string (as defined in RFC 2865) is recorded and
passed as is to the GetReplyMessage() asp function. Only a single instance is
supported.
• EAP-Message (string): Only supported when authentication is EAP-MD5 or
with IEEE802dot1x. Note that the content will not be read as the RADIUS
Access Reject is overriding whatever indication contained inside this packet.
As defined in RFC 2869.
• Colubris-Intercept: See the description in the section that follows.
• Colubris-AVPair: See the description in the section that follows.
Access challenge
• EAP-Message (string): One or more occurrences of this attribute is supported
inside the same packet. All occurrence are concatenate and transmitted to the
IEEE802dot1x client as is. As defined in RFC 2869.
• State (string): As defined in RFC 2865.
Page 34

Chapter 16: Customizing CN3200 and customer settings 227
DRAFT
Accounting request
Accounting information is generated by default. To disable accounting support,
open the Security > Authentication page.
• Acct-Session-Id (32-bit unsigned integer): Random value generated by the
CN3200.
• NAS-Identifier (string): The NAS ID set on the Security > RADIUS page for the
profile being used.
• NAS-Ip-Address (32-bit unsigned integer): The IP address of the port the
CN3200 is using to communicate with the RADIUS server.
• NAS-Port (32-bit unsigned integer): A virtual port number starting at 1.
Assigned by the CN3200.
• NAS-Port-Type (32-bit unsigned integer): Always set to 19, which represents
WIRELESS_802_11.
• Calling-Station-Id (string): The MAC address of the CN3200’s LAN port in IEEE
format. For example: 00-02-03-5E-32-1A.
• The MAC address of the wireless port the customer is associated with.Class
(string): As defined in RFC 2865.
• User-Name (string): The username assigned to the customer or to a device
when using MAC authentication.
• Framed-IP-Address (32-bit unsigned integer): IP Address of the customer’s
station.
• Acct-Status-Type (32-bit unsigned integer): Supported value are Start (1),
Interim Update (3), and Stop (2).
• Acct-Event-Timestamp (32-bit unsigned integer): As defined in RFC 2869.
• Acct-Delay-Time (32-bit unsigned integer): As defined in RFC 2865.
• Acct-Authentic (32-bit unsigned integer): Always set to 1 which means
RADIUS.
• Acct-Session-Time (32-bit unsigned integer): Number of seconds this session
since this session was authenticated. Only present when Acct-Status-Type is
Interim-Update or Stop.
• Acct-Input-Octets (32-bit unsigned integer): Low 32-bit value of the number of
octets/bytes received by the customer. Only present when Acct-Status-Type is
Interim-Update or Stop.
• Acct-Input-Gigawords (32-bit unsigned integer): High 32-bit value of the
number of octets/bytes received by the customer. Only present when AcctStatus-Type is Interim-Update or Stop.
• Acct-Input-Octets (32-bit unsigned integer): Number of packets received by the
customer. Only present when Acct-Status-Type is Interim-Update or Stop.
• Acct-Output-Octets (32-bit unsigned integer): Low 32-bit value of the number of
octets/bytes sent by the customer. Only present when Acct-Status-Type is
Interim-Update or Stop.
• Acct-Output-Gigawords (32-bit unsigned integer): High 32-bit value of the
number of octets/bytes sent by the customer. Only present when Acct-StatusType is Interim-Update or Stop. As defined in 2869.
• Acct-Output-Octets (32-bit unsigned integer): Number of packets sent by the
customer. Only present when Acct-Status-Type is Interim-Update or Stop.
• Acct-Terminate-Cause (32-bit unsigned integer): Termination cause for the
session See RFC 2866 for possible values. Only present when Acct-StatusType is Stop.
Page 35

Chapter 16: Customizing CN3200 and customer settings 228
DRAFT
Accounting response
None.
Colubris-AVPair
attribute
For each customer profile you can specify one or more instances of a ColubrisAVPair attribute that will be sent when requesting authentication (RADIUS
Requrest) or returned upon successful authentication (RADIUS Accept).
Possible values for all instance are grouped into the following categories:
Feature Description RADIUS packet
SMTP redirection Activates support for the CN3200 e-
mail redirection feature.
URLs for custom
HTML pages
Access list Activates support for an access list Access accept
One-to-one NAT Activates support for one-to-one NAT
Quotas Enables upload and download limits
Group name Sends the group name of the wireless
Enables you to customize the public
access interface for a particular
customer. See Chapter 15 for details.
(See page 90 for details).
to be set individually for each
customer.
access point the customer is
associated with.
Access accept
Access accept
Access accept
Access accept
Access request
Colubris-Intercept
attribute
SMTP redirection
SSID Sends the SSID of the wireless
access point the customer is
associated with.
For each customer profile, you can specify the Colubris-Intercept attribute to
redirect traffic from this customer into a GRE tunnel.
Access request
Attribute value
• 0: Do not intercept customer traffic.
• 1: Intercept customer traffic and redirect into GRE tunnel.
Setting up an intercept
1. Open the Network > GRE page and define a tunnel to carry th e intercepted
traffic.
2. Open the Wireless > WLAN profiles page and click the appropiate WLAN
profile.
3. Enable the Intercepted user traffic option in the Traffic Tunneling (GRE)
box, and set it to the GRE tunnel you just defined.
The CN3200 is able to provide SMTP email service on a per-customer basis.
This enables customers to send e-mail while on the road without the restrictions
imposed by most ISPs regarding the source address of outgoing mail. It works by
intercepting the call to a customer’s e-mail server and redirecting it to an SMTP
server that you configure.
Page 36

Chapter 16: Customizing CN3200 and customer settings 229
Important: For mail redirection to work, the customer's email server name must
be publicly known. If the e-mail server name cannot be resolved, mail redirection
will fail.
Important: If an unauthenticated customer establishes a connection to their
email server, the SMTP redirect feature will not work once the customer logs in.
The customer’s email will still be sent to the original email server. To avoid this,
do not use an access list to open TCP port 25 for unauthenticated customers.
DRAFT
Colubris-AVPair value string
smtp-redirect=address
Where:
Parameter Description
Access list
address
Specify the IP address or domain name of the e-mail server
which will be used to send outgoing redirected mail.
Example
smtp-redirect=smtp.colubris.com
An access list is a set of rules that govern how the CN3200 controls customer
access to network resources. Access lists are defined in the profile for the
CN3200 (see page 216) and are activated in the customer profiles as needed.
Only one access list can be activated per profile. Access lists are applied before
any white lists.
Colubris-AVPair value string
use-access-list=usename
Where:
Parameter Description
usename
Specify the name of an existing access list. This list is
activated for the current profile. Lists are checked in the order
they are activated.
One-to-one NAT
Quotas
Add this attribute if the customer requires a unique IP address when NAT is
enabled on the CN3200. For more information see “One-to-one NAT” on
page 90.
Colubris-AVPair value string
one-to-one-nat=value
Where:
Parameter Description
value
These attributes let you define upload and download limits for each customer.
Limits can be defined in terms of packets or octets (bytes).
Set this to 1 to activate one-to-one NAT support.
Page 37

Chapter 16: Customizing CN3200 and customer settings 230
DRAFT
Colubris-AVPair value string
max-input-packets=value
max-output-packets=value
max-input-octets=value
max-output-octets=value
Where:
Parameter Description
Group name
value
When a customer session is terminated based on a quota, a new non-standard
termination cause is used. The value for this termination cause is 0x8744. You
can customize this by modifying the value of "quota-exceeded-cause" in the
"IPRULESMGR" section of the configuration file. See Chapter 16 for instructions
on how to do this.
The text value of for the termination cause is defined in the message.txt file under
the token "stat-quota-exceeded". The default value for this token is "Logged out.
(Quota Exceeded.)". This value can be displayed with the ASP function
GetAuthenticationErrorMessage(). See page 184 for details.
For packets: 32-bit unsigned integer value.
For octets: 64-bit unsigned integer value.
Displaying quota information
A series of ASP functions are available that enable you to display quota
information on the session page. For details, see “Session quotas” on page 188.
This feature only applies when location-aware authenticaiton is being used
(Security > Authentication > Advanced).
Add this attribute to have the CN3200 send the group name of the access point
the customer is associated with in the Access request packet.
SSID
Colubris-AVPair value string
group=value
Where:
Parameter Description
value
Add this attribute to have the CN3200 send the SSID of the access point the
customer is associated with in the Access request packet.
Name of the access point the customer is associated with.
Colubris-AVPair value string
ssid=value
Where:
Parameter Description
value
SSID of the access point the customer is associated with.
Page 38

Chapter 16: Customizing CN3200 and customer settings 231
DRAFT
VLAN support
Set the following standard RADIUS attributes to assign VLAN numbers on a percustomer basis.
Note: The CN3200 does not directly support VLANs. VLAN support is available
when usingg CN300s as satellites stations only.
RADIUS attributes
tunnel-type=VLAN
tunnel-medium-type=802
tunnel-type=value
Where:
Parameter Description
value
VLAN number to assign.
Page 39

Chapter 16: Customizing CN3200 and customer settings 232
DRAFT
Creating administrator profiles on the RADIUS server
If you want to support multiple administrator names and passwords, you must
use a RADIUS server to manage them. The CN3200 only supports a single
admin name and password internally.
Important: Improper configuration of the administrator profile could expose the
CN3200 to access by any customer with a valid account. The only thing that
distinguishes an administrative account from that of a standard customer account
is the setting of the service type. Make sure that a customer is not granted
access if service type is not Administrative,
This is the reason why it may be prudent to use RADIUS Server 2 to handle
administrator logins. This practice reduces the risk of a bad configuration on the
RADIUS server side creating a security hole.
Supported RADIUS
attributes
Admin Access Request
• User-Name (string): The username assigned to the customer or a device when
using MAC authentication.
• NAS-Identifier (string): The NAS ID set on the Security > RADIUS page for the
profile being used.
• Service-Type (32-bit unsigned integer): As defined in RFC 2865. Set to a value
of 6, which indicates SERVICE_TYPE_ADMINISTRATIVE.
• Framed-MTU (32-bit unsigned integer): Hard-coded value of 1496. The value is
always four bytes lower than the wireless MTU maximum which is 1500 bytes
in order to support IEEE802dot1x authentication.
• MSCHAP-Challenge (string): As defined in RFC 2433. Only present when the
authentication scheme on the Security > RADIUS page is set to MSCHAPv1
or MSCHAPv2. Length = 8 bytes.
• MSCHAP-Response (string): As defined in RFC 2433. Only present when the
authentication scheme on the Security > RADIUS page is set to MSCHAPv1.
Length = 49 bytes.
Admin Access Accept
• None supported.
Admin Access Reject
• None supported
Admin Access Challenge
• None supported
Admin Accounting Request
• Not supported
Admin Accounting Response
• Not supported
Page 40

Chapter 17: Sample setup - Backend software 233
Chapter 17: Sample setup - Backend software
DRAFT
Chapter 17
Sample setup - Backend software
This chapter provides step-by-step instructions for installing and
configuring the necessary backend software to support a public access
hotspot. You can use this setup as a platform to experiment with the
CN3200 feature set.
IMPORTANT: Before reading this chapter you should familiarize
yourself with the concepts discussed in Chapter 15 and Chapter 16.
Page 41

Chapter 17: Sample setup - Backend software 234
DRAFT
Overview
This sample will be constructed using the following components:
• a fully-functional evaluation version of Funk Steel Belted Radius Server
• an SSL-capable version of the Apache open source web server
• a win32 version of PHP
• a win32 version of MySQL open source database software
• various HTML pages, scripts, RADIUS profiles designed to illustrate how to
exploit the information provided by a CN3200 in a backend system, including
creation of SSL certificates,
• a set of PHP scripts for easy administration of the database
CAUTION
Prerequisites
The installation described in this chapter should not be used in a live setup
without making the appropriate changes to guarantee the security of the web
server and other components. If you do not know how to do this yourself, you
should contact a security expert for assistance. It is beyond the scope of this
document to address these security issues.
Important: Apache 1.2.x should never be used in a production environment on a
Windows server.
IN NO EVENT SHALL COLUBRIS NETWORKS INC. BE LIABLE TO ANY PARTY FOR DIRECT, INDIRECT, SPECIAL, INCIDENTAL, OR
CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OF THIS SOFTWARE AND ITS DOCUMENTATION, EVEN IF COLUBRIS
NETWORKS INC. HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. COLUBRIS NETWORKS INC. SPECIFICALLY
DISCLAIMS ANY WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND
FITNESS FOR A PARTICULAR PURPOSE. THE SOFTWARE PROVIDED HEREUNDER IS ON AN "AS IS" BASIS FOR NONPRODUCTION USE ONLY, AND COLUBRIS NETWORKS INC. HAS NO OBLIGATION TO PROVIDE MAINTENANCE, SUPPORT,
UPDATES, ENHANCEMENTS, OR MODIFICATIONS.
Software
• Windows 2000 Professional, Server, or Advanced Server (with Service Pack
3), and all recommended updates
• Steel Belted Radius v 4.0 from Funk Software (evaluation version)
•PHP
•MySQL
• phpMyAdmin
• The Colubris Backend archive.
See “Retrieve software” on page 237 for information on obtaining this software.
Hardware
• a network hub
• a second network hub or a cross-over cable
• a computer capable of running Windows 2000 Professional, Server, or
Advanced Server, connected to the hub
• optionally, you can add a second computer capable of running a web server
• a CN3200
• a second computer with a JavaScript-enabled web browse
Skills
• Familiarity with the installation and operation of TCP/IP-based networks.
• Basic knowledge of Windows 2000, including how to use a Windows
command-line session.
Page 42

Chapter 17: Sample setup - Backend software 235
DRAFT
Equipment setup
This section illustrates the hardware setup that was used to create the sample
backend configuration described in this chapter. If you duplicate this setup, you
will not have to change any of the IP addresses supplied in the example.
Topology
The goal of this setup is to simulate a working environment with the least amount
of equipment. To this end, the ‘public network’ is considered to be any device
connected to the LAN port on the CN3200. The ‘protected network resources’
are connected to the Internet port on the CN3200. In this example, both Server 1
and Server 2 are on the protected network. Server 1 is used to host a remote
login page and a RADIUS server. Server 2 is used to simulate an external web
server.
See “Wiring details” on page 358 for information on how to build an x-over cable.
To test the setup when installation and configuration is complete, you will use the
client station to browse the web server installed on Server 2. The CN3200 will
intercept the request and redirect the web browser to the public access login
page. After you log in, the CN3200 will display the welcome page. This page will
contain the URL of the originally requested web server (Server 2). You can then
click the URL to reach Server 2.
Page 43

Chapter 17: Sample setup - Backend software 236
DRAFT
About the
components
Server 1
Server 1 hosts the remote login page and RADIUS server. The following software
is installed on it:
• Funk Steel Belted Radius Server
• Apache web server with SSL support (OpenSA package)
• PHP server-side scripting language
• MySQL database
• Colubris Backend archive which contains configuration files for RADIUS and
MySQL as well as new pages for public access interface
Server 2
Server 2 is can be used to test the setup once it is complete. You should install a
web server on this computer. This example uses IIS running on Windows 2000
professional.
If you are only using one server, then Server 1 already has a web server running
on it.
Client station
The client station is required to test the setup once it is complete. It requires a
web browser. The DHCP server on the CN3200 will assign an IP address to this
computer.
Page 44

Chapter 17: Sample setup - Backend software 237
DRAFT
Step 1: Retrieve software
Server 1
Create temporary directory on Server 1. For this example, use the directory
c:\opensource.
Download the following software into this directory.
• Funk Steel Belted Radius Server v4.04 (funk.com)
Evaluation version (not open source)
• OpenSA v1.0.4
http://www.opensa.org/files/1.0.4/opensa_1.0.4bin.exe
Contains Apache web server and SSL support
• PHP v4.3.2
http://www.php.net/downloads.php
Filename is php-4.3.2-Win32.zip
• phpMyAdmin v.2.5.2-pl1
http://sourceforge.net/projects/phpmyadmin/
Filename is phpMyAdmin-2.5.2-pl1-php.zip
If this version is not available, then you may be able to find it here:
http://museum.php.net/win32
• MySQL v3.23.49 or higher (www.mysql.com)
• MySQL Connector/ODBC v3.51.06
http://www.mysql.com
Server 2
• Colubris Backend archive (backend.zip). This file is available on the CD or on
the Colubris web site in the Support section.
No software other than Windows 2000 Professional, Server, or Advanced Server
(with Service Pack 3) is required.
Page 45

Chapter 17: Sample setup - Backend software 238
DRAFT
Step 2: Install configure software on Server 1
Windows 2000
Colubris backend
archive
1. Install Windows 2000 Professional, Server, or Advanced Server and then
install Service Pack 3. Make sure you also install all the latest updates.
2. Disable the IAS and IIS services on Windows 2000 Server, or Advanced
Server. This is required so that they do not conflict with Steel-Belted Radius
and Apache.
3. Connect Server 1 to the hub and assign a static IP address to it. For this
example, use the address 192.168.2.99.
4. Shut down and restart Server 1.
1. Extract the contents of backend.zip into a working directory. For this
example, use the directory c:\colubris.
2. If the address of Server 1is not 192.168.2.99, then:
•Edit c:\colubris\radius\example.rif, and replace all instances of the
address 192.168.2.99 with the IP address (or domain name) of Server 1.
•Edit c:\colubris\web\demo-php\login.php, and replace all instances of
the address 192.168.2.99 with the IP address (or domain name) of Server
1.
•Edit c:\colubris\web\demo-php\noc\noc.asp, and replace all instances of
the address 192.168.2.99 with the IP address (or domain name) of Server
1.
Steel-Belted Radius
•Edit c:\colubris\web\demo-php\upload\login.html, and replace all
instances of the address 192.168.2.99 with the IP address (or domain
name) of Server 1.
Note: In a production setup you should use the domain name to identify Server 1
to avoid getting security warnings from web browsers due to X.509 certificate
inconsistencies.
1. Retrieve Funk Steel Belted Radius Server v4.04 Evaluation version, from
funk.com.
2. Run the executable installation file and accept all default installation settings.
When prompted, select the 30 day trial.
Important
If you encounter the following error message when trying to start the Steel-Belted
Radius NT Service:
Services: Error 1068: The dependency service or group failed to
start.
Refer to Tech Note RD230 on the Funk web site for a solution.
http://notesnt.funk.com/TechNotenewweb.nsf/0/
6aa7095c3c6b0e4f85256aca0003b458?OpenDocument
Page 46

Chapter 17: Sample setup - Backend software 239
DRAFT
Apache
1. Run c:\opensource\opensa_1.0.4bin.exe and accept all default installation
settings.
2. After installation is complete, open a Windows command-line session.
3. Run c:\opensa\apache\apache.exe. This starts the web server.
4. Launch your web browser and point it to: http://localhost
The following page should open:
5. Close the command-line session. This stops the Apache server.
6. Launch a new command-line session.
7. Run c:\opensa\apache\apache.exe –D SSL. This starts Apache in secure
mode.
Page 47

Chapter 17: Sample setup - Backend software 240
8. Point your web browser to: https://localhost
The following message box should open:
DRAFT
Sample pages
This message is displayed because:
• the default SSL certificate that comes with the OpenSA version of Apache
does not match the DNS name present in the certificate
and
• the default SSL certificate has not been signed by a certificate authority
known to your web browser.
Later in this example, instructions are provided for eliminating this message.
9. Click Yes . The OpenSA test page will open again. This time in an HTTPS
session.
10. Close the command-line session Apache is running in.
Sample pages are provided to enable you to modify the public access interface
as described in Chapter 15: Customizing the public access interface. Install these
sample pages as follows:
1. Copy the directory c:\colubris\web\demo-php to the directory
c:\opensa\apache\htdocs
Page 48

Chapter 17: Sample setup - Backend software 241
DRAFT
PHP 4.2.3
MySQL
1. Extract php-4.x.x-Win32.zip into c:\
2. Rename c:\php-4.x.x to c:\php.
3. Copy the following files as indicated. If you are prompted to replace the files,
do so.
File Source Target
php.ini c:\colubris\php\ %SystemRoot%
This is typically \WINNT. You can
check the actual location using
the following command in a
command-line session: echo
%systemroot%.
phpinfo.php c:\colubris\php\ c:\OpenSA\Apache\htdocs
php4ts.dll c:\Php c:\OpenSA\Apache\
httpd.conf c:\colubris\Apache c:\OpenSa\Apache\conf\
1. Extract mysql-4.0.14b-win.zip into a temporary directory, and then run
setup.exe. Accept all default installation options.
2. Double click MyODBC-3.51.06.exe. Accept all default installation options.
Configure the OBDC
data source
At the end of the installation procedure, MySQL will be installed in c:\mysql.
The OBDC database acts as the repository for all the parameters for each user
account. The Steel-Belted Radius server retrieves account information from the
database and uses the database to maintain accounting and usage information
for each user.
1. Open a command-line session.
2. Run odbcad32.exe.
The following window opens:
Page 49

Chapter 17: Sample setup - Backend software 242
3. Click the System DSN tab.
4. Click Add.
5. Select MySQL ODBC 3.51 Driver, then click Finish.
DRAFT
Page 50

Chapter 17: Sample setup - Backend software 243
6. Fill in the appropriate fields in the Driver configuration window as follows:
• Data Source Name: Name of the datasource. For this example, it must be
set to Radius.
• Host / Server Name (or IP): Location of the datasource. For this example, it
must be set to localhost.
DRAFT
phpMyAdmin
Setting the path
• Database name: Name of the database. For this example, it must be set to
radius.
7. Click OK.
8. Click OK.
1. Extract phpMyAdmin-2.5.2-pl1-php.zip into the
directory: c :\OpenSA\Apache\htdocs.
2. Rename:\OpenSA\Apache\htdocs\phpMyAdmin-2.5.2-pl1 to
phpMyAdmin.
To adjust the path, do the following:
1. Right-click My Computer on the desktop.
2. Click Properties.
3. Click Advanced.
4. Click Environment Variables.
5. In the System variables window, click the Path entry, and then click Edit.
6. Make sure that the Variable value field terminates as follows:
;c:\Php;c:\Php\dlls;C:\OpenSA\Apache;C:\OpenSA\OpenSSL\bin;c:\M
ySQL\bin
Important: The order of the entries in this field must be as illustrated above, and no duplicate
entries must exist.
7. Click OK, OK, OK.
Page 51

Chapter 17: Sample setup - Backend software 244
DRAFT
Start mysql
Test PHP
1. Run c:\mysql\bin\winmysqladmin.exe
2. When prompted to enter a username and password click Cancel.
3. Shut down and restart Server 1.
1. Open a command-line session.
2. Run c:\opensa\apache\apache.exe -D SSL.
3. Point your web browser to http://localhost/phpinfo.php. The following page
opens:
Create the sample
RADIUS database
4. Close the command-line session Apache is running in.
A batch file is provided that will automatically create the database entries needed
for this example. This saves you the trouble of making these entries manually.
1. Start a windows command-line session.
2. Change to the directory: c:\colubris\mysql\
3. Run the batch file: createdb.cmd
For example:
mysqladmin: DROP DATABASE radius failed;
error: 'Can't drop database 'radius'. Database doesn't exist'
Database "radius" created
Displaying users present in database
u_username u_user_type
hotspot 1
user 2
admin 4
www.noc-cn3000.com 1
Note: It is normal to see the following error when the createdb.cmd is run the first
time: DROP DATABASE radius failed
Page 52

Chapter 17: Sample setup - Backend software 245
DRAFT
Step 3: Configure Steel-Belted Radius on Server 1
Modify the default
configuration files
Start and connect to
the server
The backend.zip file contains modified configuration settings for the Steel-Belted
Radius server to make it work in this example.
1. Open a command-line session.
2. Execute the command: net stop “Steel-Belted Radius”
This stops the Steel-Belted Radius server. (It was automatically started after
installation.)
3. Copy the following files from c:\colubris\radius\ to c:\radius\service\.
• Sqlacct.acc
• Sqlacct2.acc
• Sqlauth.aut
If you are prompted to replace the files, do so.
4. If you are using an older version of Steel-Belted Radius, you should also copy
the files in c:\colubris\radius\older_version\ to c:\radius\service\.
1. Open a command-line session.
2. Execute the command: net start “Steel-Belted Radius”
3. On the Start menu, click Steel-Belted Radius, then click Steel-Belted
Radius Administrator. The following window opens.
Page 53

Chapter 17: Sample setup - Backend software 246
4. Click Connect. This connects you to the Steel-Belted Radius server.
If you see any error messages in the Status window, you must resolve them
before continuing. For example:
DRAFT
Define a RAS client
for the CN3200
One common error is to forget to terminate the IAS and IIS services and then
reboot. These services will continue to interfere with the Steel-Belted Radius
server until you reboot.
Any device that uses the services of a RADIUS server to perform authentication
tasks is called a RADIUS client, and must have its own RAS Client settings.
To complete this section you need to know the IP address assigned to the
Internet port on the CN3200. For this example, use the address 192.168.2.1.
1. Select RAS Clients.
2. Click Add.
Page 54

Chapter 17: Sample setup - Backend software 247
3. Choose a name for the CN3200. For this example, use the name COLUBRIS.
This is a nickname that is used by Steel-Belted Radius to identify the client
and is not configured on the CN3200.
4. Click OK.
5. Specify the address of the CN3200’s Internet port. For this example, specify
192.168.2.1.
6. Set Make/model to Colubris Wireless LAN Routers.
DRAFT
7. Click Edit authentication shared secret.
8. Specify a carefully chosen shared secret. In a production environment you
should use a combination of at least eight uppercase/lowercase letters as
well as digits. For simplicity, this example uses the shared secret: secret.
9. Click Set.
10. Click Save.
Page 55

Chapter 17: Sample setup - Backend software 248
DRAFT
Create RADIUS
profiles
RADIUS profiles must be created for each user group that will be authenticated
on the public access interface. Rather than enter this information manually, you
can import it from the .rif (Radius Interchange Format) files that are included in
the archive.
This will create four profiles:
DEMO-DEVICES
This is the profile used by the CN3200.
• login name: hotspot
• password: hotspot
DEMO-USERS
Profile used by customers of the public access network.
• login name: user
• password: user
DEMO-ADMIN
Profile used by administrators who want to login to the management tool on the
CN3200.
• login name: admin
• password: admin
DEMO-NOC-DEVICES
This is the profile used by the CN3200 when configured for NOC authentication.
• login name: www.noc-cn3000.com
• password: www.noc-cn3000.com
1. On the File menu, click Import.
2. Select the file example.rif in c:\colubris\radius\.
3. Click the Profiles tab, click Select All, then click OK.
This returns you to the main screen. Leave this window open and proceed to
the next section.
Page 56

Chapter 17: Sample setup - Backend software 249
DRAFT
Update the SteelBelted Radius
configuration
1. Return to the Steel-Belted Radius Configurator window.
2. Click Servers.
3. Click Disconnect.
4. Open a command-line session and execute the command:
net stop “Steel-Belted Radius”
net start “Steel-Belted Radius”
5. Return to the Steel-Belted Radius Configurator window.
6. Click Connect.
7. Click Configuration
8. In the Authentication methods box, select SQL and click Activate (if it is
not already active). Deactivate all other authentication methods.
9. Click Save.
Page 57

Chapter 17: Sample setup - Backend software 250
DRAFT
Step 4: Install web server certificates on Server 1
Certificates enable client station to validate the identity of a web server. Refer to
Chapter 14: SSL certificates for complete discussion of certificates and examples
on how to create them. You can use the sample provided with this demo in
c:\colubris\certificates or create your own. Once you have created your
certificates install them as explained in this section.
Install the public
key certificate
Install the private
key certificate
The web server public key certificate will be contained in a password-protected
file. To avoid entering the password every time you start the server, you should
decrypt the certificate before installing it.
1. Open a command-line session.
2. Go to the directory c:\colubris\certificates.
3. Run the command: decryptkey certificate > server.key
Replace certificate with the name of the certificate file. If you are using the
sample provided, the PEM pass phrase is: www.company.com. For example:
C:\colubris\certificates>decryptkey www.company.com >
server.key
read RSA key
Enter PEM pass phrase:
writing RSA key
The unencrypted certificate is written to server.key.
4. Copy server.key to c:\OpenSA\Apache\conf\ssl.key\. Overwrite an existing
file if prompted.
The web server public key certificate will be contained in a .pem file.
1. Open a command-line session.
2. Copy the certificate file (.pem) to the file server.crt. For example:
c:\colubris\certificates>copy www.company.com.pem server.crt
Verify the
certificates
3. Copy server.crt to c:\OpenSA\Apache\conf\ssl.crt\. Overwrite an existing
file if prompted.
1. Launch a command-line session.
2. Edit the file c:\WINNT\system32\drivers\etc\hosts file and add the following
line:
192.168.2.99 www.company.com
If you generated your own certificate replace www.company.com with the
name you specified in your certificate.
Page 58

Chapter 17: Sample setup - Backend software 251
3. Go to the directory: c:\OpenSA\Apache
4. Stop the web server with the command: apache -k stop.
5. Restart the web server in SSL mode with the command: apache.exe –D
SSL
6. Close all active web browsers.
DRAFT
7. Open a new browser window and point it to: https://www.company.com
Depending on how you obtained the key, you may see the following message
box:
Page 59

Chapter 17: Sample setup - Backend software 252
8. Click View Certificate. You should see the details of the certificate you just
installed. For example:
DRAFT
Page 60

Chapter 17: Sample setup - Backend software 253
DRAFT
Step 5: Install and configure the CN3200
Follow the directions in Chapter 4: Installation then continue with the instructions
in this section.
Start Apache
Assign a static
address
Make sure that the Apache web server is running. If not, then:
1. Launch a new command-line session.
2. Run c:\opensa\apache\apache.exe –D SSL. This starts Apache in secure
mode.
Perform the following steps using the CN3200 Management tool.
1. On the Network menu, click Ports.
2. Click Internet port in the table.
3. Select Static and then click Configure.
4. Make the following settings:
• IP address: Assign an address. For this example, use the address:
192.168.2.1
• Address mask: Assign an appropriate mask. For this example, use the
mask: 255.255.255.0.
• Default gateway: Leave blank. In a real setup this would be set to the
address of the router providing access to the Internet.
Page 61

Chapter 17: Sample setup - Backend software 254
DRAFT
Configure RADIUS
settings
The CN3200 must be configured to communicate with the Steel-Belted Radius
server. For a detailed explanation of configuration issues, see Chapter 16:
“Customizing CN3200 and customer settings” on page 207.
1. On the Security menu, click RADIUS. The RADIUS settings page opens.
2. Configure the following parameters:
• Primary server address: Specify the address of Server 1. For this example,
use the address: 192.168.2.99
• Primary server secret: Specify the secret you defined on when configuring
Steel-Belted Radius. For this example, use the secret: secret
3. Click Save.
Page 62

Chapter 17: Sample setup - Backend software 255
4. Click Authentication. The Authentications settings page opens.
5. In the Customers box, set Authenticate via to RADIUS profile 1.
6. Configure the CN3200 box as follows:
• Authenticate via: Set to RADIUS profile 1.
• Login name: Set to hotspot.
• Password: Set to hotspot.
7. Enable Authenticate customers with 802.1x.
8. Click Save. The CN3200 will attempt to connect to the Steel-Belted Radius
server. If successful, the status light will change from red to green.
You can use the Statistics page on the Steel-Belted Radius Administrator to
view progress of the connection.
DRAFT
When you click the Save button in the management tool, the number of
Accepts should be incremented. That means that all settings are properly
configured on the CN3200 and Steel-Belted Radius.
If the number of Rejects is incremented instead, there may be a problem with
a badly set username and/or password. Check the log file in
c:\radius\service. It is named yyyymmdd.log, where yyyy is the year, mm
is the month and dd the day. For example, 20030822.log for August 22, 2003.
If the number of Silent Discards is incremented, it probably means that
either the IP address of the CN3200 and/or the shared secret has not been
properly configured on the RAS client tab.
You can increase the amount of information in the log file by changing the
following values in the c:\radius\service\radius.ini file, and restarting SteelBelted Radius:
[Configuration]
LogLevel = 0
TraceLevel = 0
Change both values from 0 to 2.
Page 63

Chapter 17: Sample setup - Backend software 256
DRAFT
Certificates
You can replace the certificate that is installed on the CN3200 with your own to
eliminate the warning message clients see when they try to login to the public
access interface. Refer to Chapter 14: SSL certificates for complete discussion of
certificates and examples on how to create and install them.
Important: Do not install the same certificate as the one installed on your web
server. You need to use a valid signed certificate to remove the warning
Page 64

Chapter 17: Sample setup - Backend software 257
DRAFT
Step 6: Install and configure software on Server 2
Server 2 will be used to test if the customer is successfully redirected to the
originally requested page.
1. Install Windows 2000 Professional, Server, or Advanced Server, and then
install Service Pack 3.
2. Make sure that IIS is running.
3. Connect Server 2 to the hub and assign a static IP address to it. For this
example, use the address 192.168.2.100.
Page 65

Chapter 17: Sample setup - Backend software 258
DRAFT
Step 7: Test the installation
To test the installation you will use the client station to log onto the public access
interface. For this to work, the CN3200 must be configured as the clients default
gateway. If you set up your equipment to match the setup of this example, this is
automatic. If not, adjust the configuration of the client accordingly.
1. Start the client station’s web browser and enter the IP address (or domain
name) of Server 2.
2. The CN3200 should intercept the URL and redirect the browser to the login
page. You should see the modified login page shown below. (Depending on
the type of certificate you installed on the CN3200 you may see a security
warning first.)
If you see the default login page (Register does not appear), it means that the
CN3200 could not retrieve the URLs for the modified pages. Click Tools in
the management tool and examine the messages in the log file to fix the
error.
The register button shows how to register an unauthenticated customer using
a remote, secure web page.
3. To login, specify user as both the username and password.
4. Once you have been authenticated, the welcome page should open.
Page 66

Chapter 17: Sample setup - Backend software 259
5. Click the link. You will be redirected to the web server on Server 2.
DRAFT
Page 67

Chapter 17: Sample setup - Backend software 260
DRAFT
Step 8: Test the remote login page feature
The sample files you installed on Server 1 also include definitions to allow testing
of the remote login page feature. This feature enables the CN3200 to redirect
customers to a remote URL to login instead of using the internal login page. For
more information see “Using a remote login page” on page 173.
Enable the remote
login feature
1. On the Start menu, click Steel-Belted Radius, then click Steel-Belted
Radius Administrator. The following window opens.
2. Click Connect. This connects you to the Steel-Belted Radius server.
3. Click Profiles.
Page 68

Chapter 17: Sample setup - Backend software 261
4. Select DEMO-DEVICES.
5. Click the Return list attributes tab and remove the rem- in front of remlogin-url:
login-url=https://192.168.2.99/demo-php/
login.php?NASip=%i&NASid=%n&original_url=%o
DRAFT
Test the remote
login feature
6. This overrides the setting for the login-page = entry in the RADIUS profile.
However, it is good practice to remove the login-page entry.
7. Click OK.
8. Click Save.
9. Open the CN3200’s management tool and go to the Security >
Authentication page.
10. Click Force Authenticate.
11. Wait about 1 minute before continuing to let the CN3200 download the
change
1. Start the client station’s web browser and enter the IP address (or domain
name) of Server 2.
2. The CN3200 should intercept the URL and redirect the browser to the remote
login page on 192.168.2.99. (Depending on the type of certificate you
installed on the CN3200 you may see a security warning first.)
Page 69

Chapter 17: Sample setup - Backend software 262
The register button shows how to register an unauthenticated customer using
a remote, secure web page.
3. To login, specify user as both the username and password. The Welcome
page should open.
DRAFT
4. Click the link. You should be redirected to the web server on Server 2.
Page 70

Chapter 17: Sample setup - Backend software 263
DRAFT
Step 9: Test the NOC authentication feature
The sample files you installed on Server 1 also include definitions that enable you
to test the NOC authentication feature. This feature allows you to validate
customer logins using a remote server instead of using the CN3200. See page
176 for a description of this feature and its benefits.
Enable NOC
authentication
1. Open the CN3200’s management tool.
2. On the Security menu, click Authentication, then click the Advanced
Settings button.
3. Enable NOC Authentication.
4. Select the Internet Port as the Active Interface.
5. Click Save.
Page 71

Chapter 17: Sample setup - Backend software 264
6. On the Security menu, click Authentication.
7. Specify www.noc-cn3000.com for Login name and Password.
DRAFT
Test NOC
authentication
8. Click Save.
9. Wait about 1 minute for the CN3200 to download the changes.
1. Start the client station's web browser and enter the IP address (or domain
name) of Server 2.
2. The CN3000 should intercept the URL and redirect the browser to the remote
NOC login page on 192.168.2.99.
(Depending on the type of certificate you installed on Server 2 you may see a
security warning first.)
Page 72

Chapter 17: Sample setup - Backend software 265
3. To login, specify user as both the username and password. The Welcome
page should open.
DRAFT
4. Click the link. You should be redirected to the web server on Server 2.
Page 73

Chapter 17: Sample setup - Backend software 266
DRAFT
Tools
Batch files
Several batch files are included in c:\colubris\scripts to make management of
the web server, MySQL database, and Steel-Belted Radius easier when using a
command-line session. To use this files place them into a directory that appears
in your path.
Apache
apache-start.cmd
apache-ssl-start.cmd
apache-stop.cmd
apache-restart.cmd
If you installed OpenSA in a different location than c:\, edit the scripts and
change the value of the APACHEDIR variable to your installation directory.
Mysql
mysql-start.cmd
mysql-stop.cmd
mysql-restart.cmd
Steel-Belted Radius
radius-start.cmd
radius-stop.cmd
radius-restart.cmd
Starting services
mysql-restart.cmd
apache-restart.cmd
radius-restart.cmd
phpMyadmin
phpMyadmin provides an easy-to-use interface to the MySQL database. You can
use this interface to add or edit user accounts. The following is a quick overview.
1. Point your web browser to: https://localhost/phpMyAdmin
The following screen opens:
Page 74

Chapter 17: Sample setup - Backend software 267
2. Select radius in the column on the left side of the page.
3. Click users on the left and then click the Browse tab.
DRAFT
• By clicking Edit, you can modify the information for an existing user.
• You can add a new user by clicking:
• Insert new row, and fill in all the parameters,
or
• Edit an existing user, modify its parameters, then choose Insert as new
row and click the Go button. Note that in this case, you should clear the
field u_user_id, since this is a primary key for the user table. Duplicates
are not allowed for this field.
Page 75

Chapter 17: Sample setup - Backend software 268
DRAFT
Troubleshooting
The CN3200’s authentication system is not up.
1. The IP address for the RADIUS server may be incorrect: check that a
RADIUS server has been configured in the CN3200’s Security > RADIUS
configuration panel, and that the RADIUS server is reachable from the
CN3200.
One way to do this is to ping its IP address using Tools > Ping. If the ping
fails, verify the connection between the CN3200 and the RADIUS server.
2. Check that the RADIUS server is receiving authentication requests from the
CN3200. Launch the Steel-Belted Radius administrator, connect to the
server, and go to Statistics.
• If the total number of Transactions is 0, the CN3200 is not properly
connected to the server, either directly or through other networking devices.
• If the number of Silent Discards is non-zero, it means the CN3200 and the
server have a different shared secret. They should always be the same.
• If the number of Rejects is non-zero, it means the CN3200 is using an
invalid login name/password pair.
• If the number of Accepts is non-zero, it means the positive answer from the
server is not being received by the CN3200. There may be routing
problems between the CN3200 and the RADIUS server.
There is a timeout while the customer is being redirected to
the login page.
In the case, the URL displayed in the address field of the customer’s web browser
is of the form: https://dnsname:8090/index.asp, it means the CN3200 has been
able to perform a DNS reverse-lookup, but the customer’s computer is not able to
resolve the resulting name.
Page 76

Chapter 17: Sample setup - Backend software 269
There is probably something wrong with the configuration of the DNS for the
entry related to the CN3200.
DRAFT
After logout, the goodbye page cannot be displayed
Check that the IP address and port number for the web server hosting the
goodbye page is defined in the access list for the RADIUS profile for the CN3200.
Page 77

Chapter 17: Sample setup - Backend software 270
DRAFT
Page 78

Chapter 18: Sample setup - Steel-Belted Radius 271
Chapter 18: Sample setup - Steel-Belted Radius
DRAFT
Chapter 18
Sample setup - Steel-Belted Radius
This chapter provides a walkthrough of a sample RADIUS configuration
using Steel-Belted Radius.
The CN3200 is compliant with RFC 2865 and RFC 2866 and will work
with a variety of RADIUS servers. This example is for illustrative purposes
only and does not imply that you need to use Steel-Belted Radius over
any other brand.
IMPORTANT: Before reading this chapter you should familiarize
yourself with the concepts discussed in in Chapter 15 and Chapter 16.
Page 79

Chapter 18: Sample setup - Steel-Belted Radius 272
DRAFT
Overview
This sample will be constructed using a fully-functional evaluation version of
Steel Belted Radius Server from Funk Software that will be installed on a
computer running Windows NT 4.0 or Windows 2000.
The difference between this sample and the backend example in Chapter 18, is
as follows:
• This example illustrates how to manually configure profiles on the Steel-Belted
Radius server. In the backend sample they are automatically created using
predefined scripts.
• The backend sample uses an OBDC database to store profile properties. In
this example, all properties are stored in Steel-Belted Radius. Dynamic
tracking of usage and accounting information is only possible when using an
OBDC database, therefore this example is best suited to installations that
require user authentication only.
Prerequisites
Software
• Windows 2000 Professional, Server, or Advanced Server (with Service Pack
3), and all recommended updates
• Steel Belted Radius Server version 4 from Funk Software
• Internet Explorer 6.0 service pack 1, and all recommended updates
Hardware
• a network hub
• a second network hub or a cross-over cable
• two computers capable of running Windows 2000 Professional, Server or
Advanced Server
• a CN3200
• a third computer with a JavaScript-enabled web browser, with or standard
Ethernet adapter
Skills
• Familiarity with the installation and operation of TCP/IP-based networks.
• Basic knowledge of Windows 2000, including how to use a Windows
command-line session.
Page 80

Chapter 18: Sample setup - Steel-Belted Radius 273
DRAFT
Equipment setup
This section illustrates the hardware setup that was used to create the sample
configuration described in this chapter. If you duplicate this setup, you will not
have to change any of the IP addresses supplied in the example.
Topology
About the
components
The goal of this setup is to simulate a working environment with the least amount
of equipment. To this end, the ‘public network’ is considered to be any device
connected to the LAN port on the CN3200. The ‘protected network resources’
are connected to the Internet port on the CN3200. In this example, both Server 1
and Server 2 are on the protected network. Server 1 hosts the RADIUS server.
Server 2 is used to simulate an external web server.
See “Wiring details” on page 358 for information on how to build a x-over cable.
To test the setup when installation and configuration is complete, you will use the
client station to browse the web server installed on Server 2. The CN3200 will
intercept the request and display public access login page. Your login information
will be validated using the the Funk Steel Belted Radius Server installed on
Server 1. After you are authenticated, the CN3200 will display the welcome page.
This page will contain the URL of the originally requested web server (Server 2).
You can then click the URL to reach Server 2.
Server 1
Server 1 hosts the Funk Steel Belted Radius Server.
Server 2
Server 2 is required to test the setup once it is complete. You should install a web
server on this computer. This example uses IIS running on Windows 2000
professional.
Client station
The client station is required to test the setup once it is complete. It requires a
web browser. The DHCP server on the CN3200 will assign an IP address to this
computer.
Page 81

Chapter 18: Sample setup - Steel-Belted Radius 274
DRAFT
Step 1: Install software on Server 1
Windows 2000
Steel-Belted Radius
1. Install Windows 2000 Professional, Server, or Advanced Server and then
install Service Pack 3. Make sure you also install all recommended updates.
2. Disable the IAS and IIS services on Windows 2000 Server, or Advanced
Server. This is required to avoid conflicts with Steel-Belted Radius and
Apache.
3. Connect Server 1 to the hub and assign a static IP address to it. For this
example, use the address 192.168.2.99.
4. Shut down and restart Server 1.
1. Retrieve Funk Steel Belted Radius Server v4 Evaluation version, from
funk.com.
2. Run the executable installation file and accept all default installation settings.
When prompted, select the 30 day trial.
Important
If you encounter the following error message when trying to start the Steel-Belted
Radius NT Service:
Services: Error 1068: The dependency service or group failed to
start.
Refer to Tech Note RD230 on the Funk web site for a solution.
Internet Explorer
Install Internet Explorer 6 SP1 on the server. The support files included with this
application are required for proper operation.
Page 82

Chapter 18: Sample setup - Steel-Belted Radius 275
DRAFT
Step 1: Add support for Colubris Networks attributes
Note: If you do not want to modify the files yourself, modified versions are
available in the Colubris Backend archive which can be found on the CD or on
the Colubris Networks web site.
Do the following on server 1:
1. Create an file named colubris.dct in the folder: c:\radius\service
2. Edit the file so that it contains the following entries.
@radius.dct
ATTRIBUTE Colubris-AVPAIR 26 [vid=8744 type1=0 len1=+2 data=string] RO
For more information on the format of this file, see
c:\radius\service\readme.dct.
3. Edit c:\radius\service\dictiona.dcm. Add the following line to the end of this
file, just after the last line beginning with an '@'.
@colubris.dct
4. Edit c:\radius\service\vendor.ini. Add the following lines to the end of the
file.
vendor-product = Colubris CN3200
dictionary = Colubris
ignore-ports = no
port-number-usage = per-port-type
help-id = 0
5. Restart Steel-Belted Radius. For example, start a command line session and
then issue the commands:
net stop "Steel-Belted RADIUS"
net start "Steel-Belted RADIUS"
Page 83

Chapter 18: Sample setup - Steel-Belted Radius 276
DRAFT
Step 2: Connect to the Steel-Belted Radius server
Do the following on server 1:
1. On the Start menu, click Steel-Belted Radius, then click Steel-Belted
Radius Administrator. The following window opens.
2. Click Connect. This connects you to the Steel-Belted Radius server.
Page 84

Chapter 18: Sample setup - Steel-Belted Radius 277
If you see any error messages in the Status window, you must resolve them
before continuing. For example:
A common cause for these errors is to forget to terminate the IAS and IIS
services and then reboot. These services will continue to interfere with the
Steel-Belted Radius server until you stop and terminate them, then reboot.
DRAFT
Page 85

Chapter 18: Sample setup - Steel-Belted Radius 278
DRAFT
Step 3: Create a RADIUS client profile for the CN3200
Any device that uses the services of a RADIUS server to perform authentication
tasks is called a RADIUS client, and must have its own RAS Client profile.
Therefore, you must create a profile for the CN3200.
To complete this section you need to know the IP address assigned to the
Internet port on the CN3200. For this example, use the address 192.168.2.1.
Note: The configuration settings you make here will match the settings you make
on the CN3200 later.
1. Select RAS Clients.
2. Click Add.
3. Choose a name for the CN3200. For this example, use the name COLUBRIS.
This is a nickname that is used by Steel-Belted Radius to identify the client
and is not configured on the CN3200.
4. Click OK.
5. Specify the address of the CN3200’s Internet port. For this example, specify
192.168.2.1.
Page 86

Chapter 18: Sample setup - Steel-Belted Radius 279
6. Set Make/model to Colubris CN3200.
7. Click Edit authentication shared secret.
8. Specify a carefully chosen shared secret. In a production environment you
should use a combination of at least eight uppercase/lowercase letters as
well as digits. For simplicity, this example uses the shared secret: secret.
9. Click Set.
10. Click Save.
DRAFT
Page 87

Chapter 18: Sample setup - Steel-Belted Radius 280
DRAFT
Step 4: Define RADIUS profiles
RADIUS profiles are used to manage and control all authentication tasks. Each
profile contains two sets of attributes:
• Check list attributes: These attributes must be contained in the user’s
authentication request for the authentication to be successful.
• Return list attributes: These attributes are returned once authentication is
successful.
For this example you will create a RADIUS profile for:
• the CN3200
• Public access customers subscribing to SMTP redirection
• Public access customers not subscribing to SMTP redirection
• CN3200 administrators
Defining a CN3200
profile
1. Click Profiles.
2. Click Add.
3. Specify a name for the profile. For this example, use the name HOTSPOTS.
Click OK.
4. Click the Check list attributes tab.
5. Click the Ins button. The Add New Attribute dialog box opens.
6. Select Service-Type and set it to the value Administrative. Click Add.
7. Click Close.
Page 88

Chapter 18: Sample setup - Steel-Belted Radius 281
8. Click the Returned list attributes tab.
You can now specify the attributes that will be returned to the CN3200 after it
is successfully authenticated. This enables you to define a number of
important operating characteristics, including:
• The location of custom HTML pages that must be downloaded by the
CN3200.
• One or more access lists for specifying the set of network resources
customers have access to.
For this example, you should create the following three entries:
A colubris-AVPair access-list=all,ACCEPT,tcp,192.168.2.99,80
This access list permits all users on the public network to access the web
server at 192.168.2.99. The typical role of such a server would be to
display information about the public access network: how to get an
account, how to login, etc.
B Colubris-AVPair access-list=cust,ACCEPT,tcp,192.168.2.100,80
This access list permits only authenticated customers to access the web
server at 192.168.2.100.
DRAFT
C Colubris-AVPair use-access-list=all
This activates the access list all for the HOTSPOTS profile. The cust
access list will be activated in the CUSTOMERS-NO-SMTP and
CUSTOMERS-SMTP-REDIRECT profiles.
(Refer to “Creating a profile for the CN3200 on the RADIUS server” on
page 214 for a complete list of all supported attributes.)
To add each entry:
•Click Ins. Select Colubris-AVPair and enter the appropriate string. For
example:
• Once all entries are complete, the Return list attributes tab should look
like this:
Page 89

Chapter 18: Sample setup - Steel-Belted Radius 282
•Click Save.
DRAFT
Defining a
Customer profile
The CN3200 supports an SMTP redirection feature which enables customers to
send outgoing mail without being directly connected to their SMTP server.
To use this feature, the customer profiles need to be split into two types: those
with SMTP redirection and those without it. To this end, this example will create
two profiles: CUSTOMERS-SMTP-REDIRECT and CUSTOMERS-NO-SMTP.
Note: This example assumes the SMTP server is located on Server 2, although
no such software is actually installed.
To define the customer profiles, do the following:
1. Click Profiles.
2. Click Add. The Add New Profile dialog box opens.
3. Specify CUSTOMERS-NO-SMTP as the name and click OK.
4. Click Add.
5. Specify CUSTOMERS-SMTP-REDIRECT as the name and click OK.
6. Click the Check list attributes tab.
7. Click the Ins button. The Add New Attribute dialog box opens.
8. Select Service-Type and set it to the value Framed. Click Add.
9. Click Done.
Page 90

Chapter 18: Sample setup - Steel-Belted Radius 283
10. Click the Returned list attributes tab.
You can now specify the attributes that will be returned after a customer is
successfully authenticated. This enables you to define a number of important
operating characteristics, including:
DRAFT
• The access list that is in use.
• Support for SMTP mail redirection.
• Settings for session timeouts and accounting updates.
For this example, you should create the following four entries:
A Idle-Timeout 30
This causes the CN3200 to log the customer out if the session is idle for
more than 30 seconds
B Session-Timeout 360
This causes the CN3200 to log the customer out if the session is active
for more than 360 seconds.
C Colubris-AVPair smtp-redirect=192.168.2.100
This provides access to the fictional SMTP server on 192.168.2.100.
Used for the CUSTOMERS-SMTP-REDIRECT profile only.
D Colubris-AVPair use-access-list=cust
This access list was defined in the HOTSPOTS profile. It is activated here
to provide access to the web server on 192.168.2.100.
(Refer to “Creating a profile for the CN3200 on the RADIUS server” on
page 214 for a complete list of all supported attributes.)
To create the entries:
•Click Ins. The Add New Attribute dialog box opens.
Page 91

Chapter 18: Sample setup - Steel-Belted Radius 284
• Select Colubris-AVPAIR and enter the appropriate string.
•Click Add.
• Repeat until all entries are done, the click Close.
• Once all entries are complete, the Return list attributes tab should look
like this:
DRAFT
Defining an
CN3200
administrator
profile
11. In the Profile Name box, select CUSTOMERS-NO-SMTP. Define the same
set of attributes, except for:
Colubris-AVPair smtp-redirect=192.168.2.100
By defining an administrator profile you can enable multiple administrators to log
in to the management tool on the CN3200. Each administrator can have their
own login name and password. Refer to “Creating administrator profiles on the
RADIUS server” on page 232 for more information.
Note: Only one administrator can log in at a time.
Note: Setting up administrator profiles is optional and is not required for proper
operation of this sample.
To define the customer profiles, do the following:
1. Click Profiles.
2. Click Add. The Add New Profile dialog box opens.
3. Specify ADMIN as the name and click OK.
4. Click the Check list attributes tab.
5. Click the Ins button. The Add New Attribute dialog box opens.
Page 92

Chapter 18: Sample setup - Steel-Belted Radius 285
6. Select Service-Type and set it to the value Administrative. Click Add.
7. Click Close.
DRAFT
Return list attributes are not supported for administrators.
8. Click Save.
Page 93

Chapter 18: Sample setup - Steel-Belted Radius 286
DRAFT
Step 5: Define user accounts
RADIUS user accounts need to be created for each individual user. The account
specifies the login name and password the user will use to login. All other
properties are obtained from one of the profiles that were just defined.
For this example you will create the following RADIUS user accounts:
Username Password Associate with profile
customer1 customer1 CUSTOMERS-NO-SMTP
customer2 customer2 CUSTOMERS-SMTP-REDIRECT
hotspot hotspot Hotspots
admin admin ADMIN
Defining user
accounts
Repeat the following procedure to create each user account.
1. Click Users.
2. Click Add.
3. Specify the Username and click OK.
4. Click Set password. Define the password and click Set.
Page 94

Chapter 18: Sample setup - Steel-Belted Radius 287
5. In the Profile name box, select the profile which will be used as the basis for
the account. The settings for the profile will appear. For example:
6. Click Save.
DRAFT
Page 95

Chapter 18: Sample setup - Steel-Belted Radius 288
DRAFT
Step 6: Install and configure the CN3200
Assign a static
address
Configure RADIUS
settings
1. On the Network menu, click Ports.
2. Click Internet port in the table.
3. Select Static and then click Configure.
4. Make the following settings:
• IP address: Assign an address. For this example, use the address:
192.168.2.1
• Address mask: Assign an appropriate mask. For this example, use the
mask: 255.255.255.0.
• Default gateway: Leave blank. In a real setup this would be set to the
address of the router providing access to the Internet.
The CN3200 must be configured to communicate with the Steel-Belted Radius
server. For a detailed explanation of configuration issues, see Chapter 16:
“Customizing CN3200 and customer settings” on page 207.
1. On the Security menu, click RADIUS. The RADIUS settings page opens.
2. Configure the following parameters:
• Primary server address: Specify the address of Server 1. For this example,
use the address: 192.168.2.99
• Primary server secret: Specify the secret you defined on when configuring
Steel-Belted Radius. For this example, use the secret: secret
Page 96

Chapter 18: Sample setup - Steel-Belted Radius 289
3. Click Save.
4. Click Authentication. The Authentications settings page opens.
5. In the Customers box, set Authenticate via to RADIUS profile 1.
6. Configure the CN3200 box as follows:
• Authenticate via: Set to RADIUS profile 1.
• Login name: Set to hotspot.
• Password: Set to hotspot.
7. Enable Authenticate customers with 802.1x.
8. Click Save. The CN3200 will attempt to connect to the Steel-Belted Radius
server. If successful, the status light will change from red to green.
Note: You can use the Statistics page on the Steel-Belted Radius Administrator to
view progress of the connection.
DRAFT
When you click the Save button in the management tool on the CN3200, the
number of Accepts should be incremented. That means that all settings are
properly configured on the CN3200 and Steel-Belted Radius.
If the number of Rejects is incremented instead, there may be a problem with
a badly set username and/or password. Check the log file in
c:\radius\service. It is named 2001mmdd.log, where mm is the month and
dd the day. For example, 20011022.log for October 22, 2001.
If the number of Silent Discards is incremented, it probably means that
either the IP address of the CN3200 and/or the shared secret has not been
properly configured on the RAS client tab.
You can increase the amount of information in the log file by changing the
following values in the c:\radius\service\radius.ini file, and restarting SteelBelted Radius:
[Configuration]
LogLevel = 0
TraceLevel = 0
Change both values from 0 to 2.
Page 97

Chapter 18: Sample setup - Steel-Belted Radius 290
DRAFT
Page 98

Chapter 18: Sample setup - Steel-Belted Radius 291
DRAFT
Step 7: Install Server 2
This example assumes Windows 2000 and IIS are installed on Server 2. You can
any another operating system and web server.
1. Install Windows 2000 Professional, Server, or Advanced Server and then
install Service Pack 3.
2. Make sure that IIS is running.
3. Connect Server 2 to the LAN and assign a static IP address to it. For this
example, use the address 192.168.2.100.
Page 99

Chapter 18: Sample setup - Steel-Belted Radius 292
DRAFT
Step 8: Test the installation
To test the installation, use the client station to log onto the public access
interface. For this to work, the CN3200 must be configured as the client’s default
gateway. If you set up your equipment to match the setup of this example, this is
automatic. If not, adjust the configuration of the client accordingly.
1. Start the client station’s web browser and enter the IP address (or domain
name) of Server 2 in the address bar.
2. The CN3200 should intercept the HTTP request and display the login page.
Depending on the type of certificate that is installed on the CN3200 you may
see a security warning first.
3. To login, specify customer1 as both the username and password. The
CN3200 session page should open.
Page 100

Chapter 18: Sample setup - Steel-Belted Radius 293
4. You should automatically be redirected to the web server on Server 2.
DRAFT
Testing
administrator
logins
If you configured administrator accounts on the RADIUS server, you can test
them now as follows:
1. Open the CN3200 management tool with your web browser.
2. On the main menu, click Management. The Management tool configuration
page opens.
3. For Authenticate via select RADIUS profile 1.
4. Click Save.
5. Logout.
6. Login with username and password admin.
 Loading...
Loading...