Page 1

Page 2

LIMITED WARRANTY
Hawking Technology guarantees that every HWU54G Mini Wireless-G USB Network
Adapter is free from physical defects in material and workmanship under normal use
for two (2) years from the date of purchase. If the product proves defective during this
two-year warranty period, call Hawking Customer Service in order to obtain a Return
Authorization number. Warranty is for repair or replacement only. Hawking
Technology does not issue any refunds. BE SURE TO HAVE YOUR PROOF OF
PURCHASE. RETURN REQUESTS CAN NOT BE PROCESSED WITHOUT
PROOF OF PURCHASE. When returning a product, mark the Return Authorization
number cle arly on the outside of the package and include your original proof of
purchase.
IN NO EVEN SHALL HAWKING TECHNOLOGY’S LIABILTY EXCEED THE
PRICE PAID FOR THE PRODUCT FROM DIRECT, INDIRECT, SPECIAL,
INCIDENTAL OR CONSEQUENTIAL DAMAGES RESULTING FROM THE USE
OF THE PRODUCT, ITS ACCOMPANYING SOFTWARE OR ITS
DOCUMENTATION.
Hawking Technology makes no warranty or repre sentation, expressed, implied or
statutory, with respect to its products or the contents or use of this documentation and
all accompanying sof tware, and specifically disclaims its quality, performance,
merchantability, or fitness for any particular purpose. Hawking Techno logy reserves
the right to revise or updates its products, software, or documentation without
obligation to notify any individual or entity. Please direct all inquiries
to:techsupport@hawkingtech.com
Page 3

Federal Communication Commission
Interference Statement
This equipment has been tested and found to compl y with the limits for a Class B
digital device, pursuant to Part 15 of FCC Rules. These limits are designed to
provide reasonable protection against harmful interference in a residential installation.
This equipment generates, uses, and can radiate radio frequency energy and, if not
installed and used in accordance with the instructions, may cause harmful
interference to radio communications. However, there is no guarantee that
interference will not occur in a particular installation. If this equipment do es cause
harmful interference to radio or television reception, which can be determined by
turning the equipment off and on, the user is encouraged to try to correct the
interference by one or more of the following measures:
1. Reorient or relocate the receiving antenna.
2. Increase the separation between the equipment and receiver.
3. Connect the equipment into an outlet on a circuit different from that to which the
receiver is connected.
4. Consult the dealer or an experienced radio technician for help.
FCC Caution
This device and its antenna must not be co-located or operating in conjunction with
any other antenna or transmitter.
This device complies with Part 15 of the FCC Rules. Operation is subject to the
following two conditions: (1) this device may not cause harmful interference, and (2)
this device must accept any interference received, including interference that may
cause undesired operation.
Any changes or modifications not expressly approved by the party responsible for
compliance could void the authority to operate equipment.
Federal Communications Commission (FCC) Radiation Exposure Statement
This equipment complies with FCC radiation exposure set forth for an
uncontrolled environment. In order to avoid the possibility of exceeding the
FCC radio frequency exposure limits, human proximity to the antenna shall not
be less than 2.5cm (1 inch) during normal operation.
Page 4

Federal Communications Commission (FCC) RF Exposure Requirements
SAR compliance has been established in the laptop computer(s) configurations with
PCMCIA slot on the side near the center, as tested in the application for Certification,
and can be used in laptop computer(s) with substantially similar physical dimensions,
construction, and electrical and RF characteristics. Use in other devices such a PDAs
or lappads is not authorized. This transmitter is restricted for use with the specific
antenna(s) tested in the application for Certification. The antenna(s) used for this
transmitter must not be co-located or operating in con junction with any other antenna
or transmitter.
R&TTE Compliance Statement
This equipment complies with all the requirements of DIRECTIVE 1999/5/EC OF THE
EUROPEAN PARLIAMENT AND THE COUNCIL of March 9, 1999 on radio
equipment and telecommunication termi nal Equipment and the mutual recognition of
their conformity (R&TTE)
The R&TTE Directive repeals and replaces in the directive 98/13/EEC
(Telecommunications Terminal Equipment and Satellite Earth Station Equipment) As
of April 8, 2000.
Safety
This equipment is designed with the utmost care for the safety of those who install and
use it. However, special attention must be paid to the dangers of electric shock and
static electricity when working with electrical equipment. All guidelines of this and of
the computer manufacture must therefore be allowed at all times to ensure the safe
use of the equipment.
EU Countries Intended for Use
The ETSI version of this device is intended for home and office use in Austria,
Belgium, Denmark, Finland, France, Germany, Greece, Ireland, Italy, Luxembourg,
t he Netherlands, Portugal, Spain, Sweden, and the United Kingdom.
The ETSI version of this device is also authorized for use in EFTA member states:
Iceland, Liechtenstein, Norway, and Switzerland.
Page 5

CONTENTS
1 INTRODUCTION................................ ................................... 1
1.1 Features ..........................................................................................................................1
1.2 Specifications .................................................................................................................1
1.3 Package Contents...........................................................................................................2
2 INSTALLATION PROCEDURE................................ .............. 3
3 CONFIGURATION UTILITY.................................................. 7
3.1 General...........................................................................................................................7
3.1.1 Preference Setting ......................................................................................................9
3.1.2 Site Survey..........................................................................................................................9
3.2 Profiles.........................................................................................................................10
3.2.1 Configure the Profile ................................................................................................ 12
3.2.2 Enable WPA............................................................................................................. 14
3.3 Current Statistics..........................................................................................................15
3.4 About............................................................................................................................16
4 TROUBLESHOOTING ......................................................... 17
Page 6

1 Introduction
The Hawking Technologies Mini Wireless -G USB 2.0 Network Adapter is designed to be fully compliant with
both IEEE 802.11b and IEEE 802.11g wireless networking standards. The HWU54G uses the latest in
wireless chip technology and is capable of transferring data wirelessly at speeds up to 54 Mbps! In addition
to being a high-speed wireless adapter, the Mini Wireless-G Adapter is the size of a finger. This lets you
take the Wireless-G adapter wherever you go so you’ll never have to worry about connecting again. The
combination of speed and size make this Wireless -G network adapter one of the best on the market.
The Hi-Gain Wireless -G USB Network Adapter supports 64/128-bit WEP data encryption that protects your
wireless network from outside intruders. Furthermore, it supports the latest in wireless security, WPA (Wi-Fi
Protected Access) , a feature that combines IEEE 802.1x and TKIP (Temporal Key Integrity Protocol)
technologies. With the WPA feature, users are required to authenticate themselves before accessing APs or
AP Routers. The data transmitted within the network is encrypted/decrypted by a secret key that is
dynamically changed.
Whether you are trying to connect to a local hotspot or surfing the web while you read a book in the
park, the HWU54G gives the power and versatility to connect anywhere, anytime.
1.1 Features
• Complies with IEEE 802.11g (2.4GHz, OFDM) and IEEE 802.11b standards.
Works with both IEEE 802.11b and IEEE 802.11g products.
•
• High-speed transfer data rate - up to 54Mbps.
• High throughput supports multimedia data bandwidth requirements.
Supports 64/128-bit WEP and WPA (TKIP with IEEE 802.1x with) WLAN security.
•
• Automatic data rate fallback increases data security and reliability.
• Supports the most popular operating systems: Windows 2000/XP.
Supports USB 2.0/1.1/1.0 interface.
•
1.2 Specifications
• Standard: IEEE 802.11b/g
• Host Interface: USB 2.0/1.1/1.0
USB Port: Mini-USB
•
• Frequency Band: 2.4000 ~ 2.4835GHz (Industrial Scientific Medical Band)
• Modulation: OFDM with BPSK, QPSK, 16QAM, 64QAM (11g)
BPSK, QPSK, CCK (11b)
1
Page 7

Data Rate: 54/48/36/24/18/12/11/9/6/5.5/2/1Mbps auto fallback
•
• Security: 64/128-bit WEP Data Encryption, WPA (TKIP with IEEE 802.1x)
• Antenna: Internal
Drivers: Windows 2000/XP
•
• LEDs: Power, LinkTransmit Power: 16 dBm
• Temperature: 32~131°F (0 ~55°C)
Humidity: Max. 95% (NonCondensing)
•
• Certification: FCC, CE
1.3 Package Contents
Before you begin the installation, please check the items of your package. The package should include the
following items:
• One Mini USB Wireless-G Adapter
One Quick Installation Guide
•
• One CD (Driver/Utility/User Manual)
If any of the above items is missing, contact your supplier as soon as possible.
2
Page 8
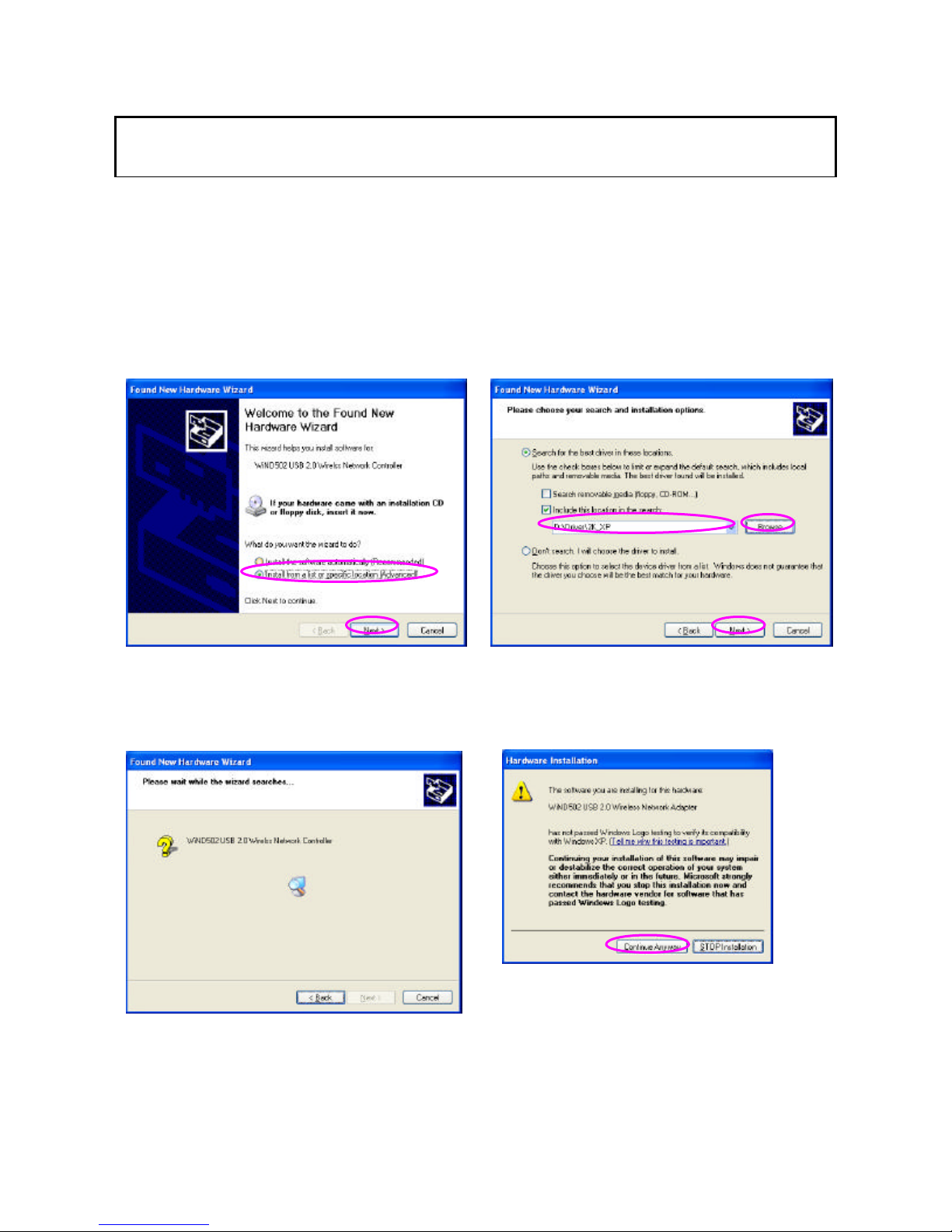
2 Installation Procedure
Before you proceed with the installation, please notice following descriptions.
Note: The following installation was performed under Window s XP. (Procedures are similar for
Windows 98SE/Me/2000.)
I. Install the Driver
A. Insert the Installation CD into your CD -ROM driver.
B. Insert the USB adapter to the USB port of your laptop or desktop PC.
C. Choose the selection “Install from a list or
specific location (Advanced)” and click “Next”.
D. Click “Browse” to search for the driver. Choose
the location to “D:\Driver\xxx” ( “D” is where your
CD-ROM Driver, “xxx ” is the OS system of your
computer) and click “Next”.
E. A Windows driver warning message appears,
click “Continue Anyway”.
3
Page 9

F. The wizard will install the driver automatically. Click “Finish” to complete the installation.
II. Install the Utility
A. Execute the "Utility \setup.exe" program from the installation CD.
B. The InstallShield Wizard box will appear, click “Next” to continue.
C. Choose the selection “I accept the terms in the
license agreement” and click “Next”.
D. Enter your “User Name ” and “Organization” which is
only for reference, then click “Next”.
4
Page 10

E. If you want to change the destination folder, click
“Change”, or click “Next” to continue.
F. There is no different among the three-setup types.
Click “Next” directly.
G. The wizard will install the driver automatically. Click “Finish” to complete the installation.
5
Page 11

III. Using the Utility
Go to Start \All Programs\Envara Configuration Utility and select “EnvaraGui”. This will load the Wireless Utility.
6
Page 12

3 Configuration Utility
The Configuration Utility is a powerful application that helps you configure the adapter and monitor the
link status and the statistics durin g the communication process.
However, there are some restrictions on the utility. Before using the utility, you should study and learn
them.
1. If you want to connect to an 11g (54Mbps) network, please ensure to install the adapter to a PC or
laptop with an USB 2.0 interface. This adapter can only support 11b when connected to a USB
1.1/1.0 port on your computer.
2. This adapter will only work in 11b (11Mbps) mode when Ad Hoc mode has been selected as the
network type. (Defined by the Wi-Fi organization). If you want to enable the data rate up to 54Mbps
(11g), please follow steps listed below.
A. Go to “Network Connections”.
B. Right Click the “Wireless Network Connection ” and select “Properties”.
C. From the pop-up screen, click “Configure”.
D. Enter into “Advanced ” page of the “Properties” screen.
E. Change the setting of “IBSS Originator Phy -Mode” from “802.11b” to “802.11g”.
3.1 General
From the “General” screen, you can view all the information of the network you are connecting to.
7
Page 13

.
adjust
Parameter Description
Connected to (SSID)
Network Mode There are two network types: Infrastructure and Ad Hoc. This field shows
Channel / Frequency
Max. Network Rate This field shows the maximum link rate of the network, that is 54Mbps for
Security Display the security setting of the network. “Disabled” means there is no
Power Save This field displays the power save scheme for the adapter (that is Max
Active Profile
Radio Status
Enable Radio Button
Link Quality
Received
Sent
Network Rate The data rate in this field varies from one wireless environment to another
Preferences Button If you want to change the unit of link quality or the update interval for
View Site Button To view the available wireless networks nearby, click the “View Site”
Displays the wireless network that the adapter is connecting to.
the current network type.
Display the radio channel and the frequen cy in use by the adapter.
802.11g and 11Mbps for 11b.
security setting on the network.
performance/Max battery life/Auto).
This field shows the current connection profile.
This field shows the transmitter’s status (On or Off).
This button is used to enable and disable radio transmission.
The higher the percentage, the better the connection to the AP.
This field shows the current received baud rate (measure d in Kbytes/sec).
This field shows the current sent baud rate (measured in Kbytes/sec).
It displays the current data rate at that point in time so that you may
the direction of the adapter or distance from other wireless stations.
transmitted and received data, click this button to change the settings.
button.
8
Page 14

Quality, Network Name, Mode, Security, etc. This information will help you
3.1.1 Preference Setting
This preference screen enables you to change the unit used to measure link quality or the time interval
used to refresh the data. The default settings is “10” for “Statistics Update Interval” and “Percent” for
“Parameter Display Units”. If you want to set up as default values, click “Defaults”.
3.1.2 Site Survey
T his screen shows all wireless networks nearby. If you want to connect to any network on the list,
double-click the item on the list or click “Connect”, and the adapter will automatically connect to the
selected network.
Parameter Description
Available Networks/AP ’s List The list displays the information of wireless networks in cluding Link
decide which network you want to connect to.
9
Page 15

Parameter Description
Connect Button Select one of the networks from the list and click “Connect”, the adapter
will connect to the network automatically. You can also right click the
network and select “Connect”.
Save Profile Button Save the selected network as a profile. This profile will be listed in the
profiles list table so that you can easily connect to that specific network
without using the “Site Survey.” You can also right click the SSID and
select “Save as Profile”.
Edit Connect Button If the network you are trying to connect to has a different WEP security
setting, you can click this button to update the settings of the adapter.
Note that the WEP setting has to be the same with the network. You can
also right click the connection network and select “Edit Connect”.
Rescan Button C lick the “Rescan” button to refresh the data of all wireless networks
nearby.
AP View/Network View Button This button will change the way the available networks are displayed.
“Network View” displays the network information simply.
3.2 Profiles
The Profiles let you easily manage the wireless networks that your frequently connect to. Simply save
the settings of the different wireless networks your frequent and select the saved profile each time you
connect to them. The Profiles save you time and make connecting easier.
10
Page 16

to connect to one of the profiles in
Parameter Description
Auto-Selection Profiles If a profile is set as an Auto-Selection profile the utility will attempt to
automatically connect the adapter to the respective profile in the order
they are listed in the Profile list. All networks that you have previously
connected to will be listed. If you want
the list, double -click the item on the list or right click the network and
select “Connect”.
Additional Profiles You can create additional profiles here as other selections. The adapter
Right Click Function List Add – Add a new profile in the list.
will not connect to the additional profiles in the list automatically.
If you want to change the connection to one of the profiles, double -click
the profile or select the profile and click “Connect”. You can click “New”
and “Edit” to configure the profile list.
Edit – Edit the selected profile.
Duplicate – Copy the same profile to the list.
Delete – Delete the selected profile.
Connect – Connect to the profile.
Add/Remove to/from Auto -Selection – Add the profile to the
“Auto-Selection Profiles” or remove it from “Auto-Selection Profiles” to
“Additional Profiles”.
Export Profile – Save the profile as a new file.
Import Profiles – Import the profile file to the list.
Export All Profiles – Save all the profiles as a new file.
11
Page 17

is setting is only available for Ad Hoc mode. The channel setting should
3.2.1 Configure the Profile
When you click “New” or “Edit” in the Profiles page the “Profile Configuration” screen will appear. In this
screen, there are two pages: General and Security.
General
Parameter D escription
Name
Network Name (SSID) The SSID (up to 32 printable ASCII characters) is the unique name
Network Mode Infrastructure – This operation mode requires the presence of an 802.11
Power Save
Channel / Frequency Th
Change the name of your Profile for easier identification.
identify a wireless network . The ID prevents the unintentional merging of
two co -located WLANs.
You may specify a SSID for the adapter so that it will only connect to a
network when that specific SSID is present.
Access Point. All communication is done via the Access Point.
Ad-Hoc – Select this mode if you want to connect to another wireless
station in the Wireless LAN network without an Access Point.
Enable the adapter to enter power saving mode when it is idle.
be the same with the network you are connecting to.
12
Page 18

selected radio button. The WEP keys are used to encrypt data transmitted
Auto-Select Profile Member If you select the check box, this profile will be put in the “Auto-Selection
Profiles” list.
Parameter Description
Defaults The default values are Ad Hoc mode and channel one. If you want to set
up to default, click this button.
Encryption
Parameter Description
Security None – Disable the WEP Data Encryption.
WEP – Enable the WEP Data Encryption. When the item is selected, you
have to continue setting the WEP Key Length and the encryption keys.
Use 802.1x This function is not activated yet. It will not implement if you enable it.
Encryption Key
(Key1 ~ Key4)
Select the default encryption key from Key 1 to Key 4 by using the
on the wireless network. Fill the text box by following the rules below.
64-bit – Input 10-digit Hex values (in the “A-F”, “a-f” and “0-9” range) as
the encryption keys . For example: “0123456aef “.
128-bit – Input 26 -digit Hex values (in the “A-F”, “a-f” and “0-9” range) as
the encryption keys . For example: “01234567890123456789abcdef “.
13
Page 19

3. Click “Configure
”
to configure the WPA
1. From here, right click the icon to
3.2.2 Enable WPA
Wi-Fi Protected Access (WPA) is a specification of standards-based, interoperable security
enhancements that strongly increase the level of data protection (encryption) and access control
(authentication) for existing and future wireless LAN systems. The technical components of WPA
include Temporal Key Integrity Protocol (TKIP) for dynamic key exchange, and 802.1x for
authentication.
WPA function is enabled in the following software system:
1. Windows XP Service Pack 1 with Windows XP Support Patch for Wi-Fi Protected Access program
in addition.
2. Configure the card by Wireless built -in utility (Wireless Zero Configuration).
selec t “View Available Wireless
Networks” .
2. Click “Advanced” from
“Wireless Network Connection”.
function for the current network.
14
Page 20

PSK mode, WEP is also able to be the encryption
Parameter Description
Network Authentication Open –No authentication is needed among the wireless network.
Shared – Only wireless stations using a shared key (WEP Key identified)
are allowed to connecting each other.
WPA – This mode is for users with an authentication server (Radius
Server), WPA-enabled access point, and a WPA-enabled client. Once
WPA is enabled, all clients and access points on the network must be
WPA-enabled in order to access the network.
WPA-PSK – It is a special mode designed for home and small business
users who do not have access to network authentication servers. In this
mode, known as Pre -Shared Key, the user manually enters the starting
password in their access point or gateway, as well as in each PC on the
wireless network. WPA takes over automatically from that point, keeping
unauthorized users that don't have the matching password from joining
the network, while encrypting the data traveling between authorized
devices.
Data Encryption WEP – In WPA or WPA-
method for the transmission data.
TKIP – TKIP (Temporal Key Integrity Protocol) changes the temporal key
every 10,000 packet s (a packet is a kind of message transmitted over a
network.) This insures much greater security than the standard WEP
security.
Note: All devices in the network should use the same encryption method
to ensure the communication.
3.3 Current Statistics
This option enables you to view the signal strength and the statistical information of successful Tx and
Rx baud rate. You may reset the counters by clicking “Reset”. The “SNR” indicates the rate of noise
and signal in the environment, the bigger of the value, the better the signal strength.
15
Page 21

3.4 About
By choosing this option, you can view basic information such as the Driver, Firmware and Utility
Version. And you can click the hyperlink to connect the website for the information of the wireless
chipset vendor.
16
Page 22

4 Troubleshooting
This chapter provides solutions to problems usually encountered during the installation and operation
of the adapter.
1. Why can’t the USB adapter work or only work in 11b mode while connect to USB 2.0 port?
If this situation oc curs, please upgrade the driver of your USB port. This problem may be the
compatibility issue with the old driver of the USB port.
2. What is the IEEE 802.11g standard?
802.11g is the new IEEE standard for high-speed wireless LAN communications that provides for
up to 54 Mbps data rate in the 2.4 GHz band. 802.11g is quickly becoming the next mainstream
wireless LAN technology for the home, office and public networks.
802.11g defines the use of the same OFDM modulation technique specified in IEEE 802.11a for
the 5 GHz frequency band and applies it in the same 2.4 GHz frequency band as IEEE 802.11b.
The 802.11g standard is backwards compatible with 802.11b.
The standard specifically calls for:
A. A new physical layer for the 802.11 Medium Access Control (MAC) in the 2.4 GHz frequency
band, known as the extended rate PHY (ERP). The ERP adds OFDM as a mandatory new
coding scheme for 6, 12 and 24 Mbps (mandatory speeds), and 18, 36, 48 and 54 Mbps
(optional speeds). The ERP includes the modulation schemes found in 802.11b including
CCK for 11 and 5.5 Mbps and Barker code modulation for 2 and 1 Mbps.
B. A protection mechanism called RTS/CTS that governs how 802.11g devices and 802.11b
devices interoperate.
3. What is the IEEE 802.11b standard?
The IEEE 802.11b Wireless LAN standard subcommittee, which formulates the standard for the
industry. The objective is to enable wireless LAN hardware from different manufactures to
communicate.
4. What does IEEE 802.11 feature support ?
The product supports the following IEEE 802.11 functions:
l CSMA/CA plus Acknowledge Protocol
l Multi-Channel Roaming
l
Automatic Rate Selection
l RTS/CTS Feature
l Fragmentation
l Power Management
5. What is Ad-hoc?
An Ad-hoc integrated wireless LAN is a group of computers, each has a Wireless LAN adapter,
Connected as an independent wireless LAN. Ad hoc wireless LAN is applicable at a
departmental scale for a branch or SOHO operation.
17
Page 23

6. What is Infrastructure ?
An integrated wireless and wireless and wired LAN is called an Infrastructure c onfiguration.
Infrastructure is applicable to enterprise scale for wireless access to central database, or
wireless application for mobile workers.
7. What is BSS ID?
A specific Ad hoc LAN is called a Basic Service Set (BSS). Computers in a BSS must be
configured with the same BSS ID.
8. What is WEP?
WEP is Wired Equivalent Privacy, a data privacy mechanism based on a 40 bit shared key
algorithm, as described in the IEEE 802 .11 standard.
9. What is TKIP?
TKIP is a quick-fix method to quickly overcome the inheren t weaknesses in WEP security,
especially the reuse of encryption keys. TKIP is involved in the IEEE 802.11i WLAN security
standard, and the specification might be officially released by early 2003.
10. What is AES?
AES (Advanced Encryption Standard), a chip-based security, has been developed to ensure the
highest degree of security and authenticity for digital information, wherever and however
communicated or stored, while making more efficient use of hardware and/or software than
previous encryption standards. It is also included in IEEE 802.11i standard. Compare with AES,
TKIP is a temporary protocol for replacing WEP security until manufacturers implement AES at
the hardware level.
11. Can Wireless products support printer sharing ?
Wireless products perform the same function as LAN products. Therefore, Wireless products can
work with Netware, Windows 2000, or other LAN operating systems to support printer or file
sharing.
12. Would the information be intercepted while transmitting on air?
WLAN features two-fold protection in security. On the hardware side, as with Direct Sequence
Spread Spectrum technology, it has the inherent security feature of scrambling. On the software
side, WLAN series offer the encryption function (WEP) to enhance security and Access Control.
Users can set it up depending upon their needs.
13. What is DSSS? What is FHSS ? And what are their differences?
Frequency-hopping spread-spectrum (FHSS) uses a narrowband carrier that changes frequency
in a pattern that is known to both transmitter and receiver. Properly synchronized, the net effect
is to maintain a sing le logical channel. To an unintended receiver, FHSS appears to be
short-duration impulse noise. Direct-sequence spread -spectrum (DSSS) generates a redundant
bit pattern for each bit to be transmitted. This bit pattern is called a chip (or chipping code). The
longer the chip is, the greater the probability that the original data can be recovered. Even if one
or more bits in the chip are damaged during transmission, statistical techniques embedded in the
radio can recover the original data without-the need for retransmission. To an unintended
18
Page 24

receiver, DSSS appears as low power wideband noise and is rejected (ignored) by most
narrowband receivers.
14. What is Spread Spectrum ?
Spread Spectrum technology is a wideband radio frequency technique developed by the military
for use in reliable, secure, mission -critical communication systems. It is designed to trade off
bandwidth efficiency for reliability, integrity, and security. In other words, more bandwidth is
consumed than in the case of narrowband transmission, but the trade off produces a signal that
is, in effect, louder and thus easier to detect, provided that the receiver knows the parameters of
the spread-spectrum signal being broadcast. If a receiver is not tuned to the right frequency, a
spread –spectrum sign al looks like background noise. There are two main alternatives, Direct
Sequence Spread Spectrum (DSSS) and Frequency Hopping Spread Spectrum (FHSS).
19
 Loading...
Loading...