HandEra WF10020 Users Manual

Rhein Tech Laboratories, Inc.
360 Herndon Parkway
Suite 1400
http://www.rheintech.com
Report #: 2007132
Client: HandEra, Inc.
Model: WF10020
Standards: FCC 15.247
FCC ID: URZ-WF10020 Herndon, VA 20170
Appendix I: Manual
Please refer to the following pages for a copy of the module manual and a copy of the host manual. The FCC
compliance information for the module appears on page 16 of this file, and SAR data appears on the last page
of this file.
Page 44 of 77

1009-00064
Revision 1.0
WF-10020
User Manual
Revision Date
6/13/2007
CONTACT INFORMATION
Company: HandEra Inc.
2859 104thStreet
Des Moines, IA 50322
Phone: (515)-252-7522
Fax: (515)-252-7525
Web: www.HandEra.com
DOCUMENT MODIFICATION LOG
Description of changes Rev. Date
Initial release 1.0 6/13/2006
Copyright © 2007 HandEra, Inc. All rights reserved. No part of this documentation may be reproduced or
transmitted in any form or by any means or used to make any derivative work (such as translation, transformation, or
adaptation) without express written consent from HandEra.
Windows CE is a registered trademark of Microsoft.
Palm OS® is a registered trademark of Palm Trademark Holding Company, LLC.
HandEra reserves the right to revise this documentation and to make changes in content from time to time without
obligation on the part of HandEra to provide notification of such revision or changes.
HandEra makes no representations or warranties that the documentation is free of errors. The documentation is
provided on an ‘as is’ basis.
WF10020 2

1 General Description
The WF-10020 offers complete drivers for embedded operating systems such as WinCE and Linux. Additional
security can be added to the WF-10020 by using the optional security supplicant software offered by HandEra
1.1 Features
IEEE Std 802.11b compliant
Simple, high speed SPI interface
Low power design
Bluetooth coexistence Packet Traffic Arbitration (PTA) support
Data Rates 1,2, 5.5 11 Mbps (802.11B)
RoHS 2006 compliant
Support for IEEE 802.11i and WPA security enhancements
EEProm to Store MAC address
WF10020 4
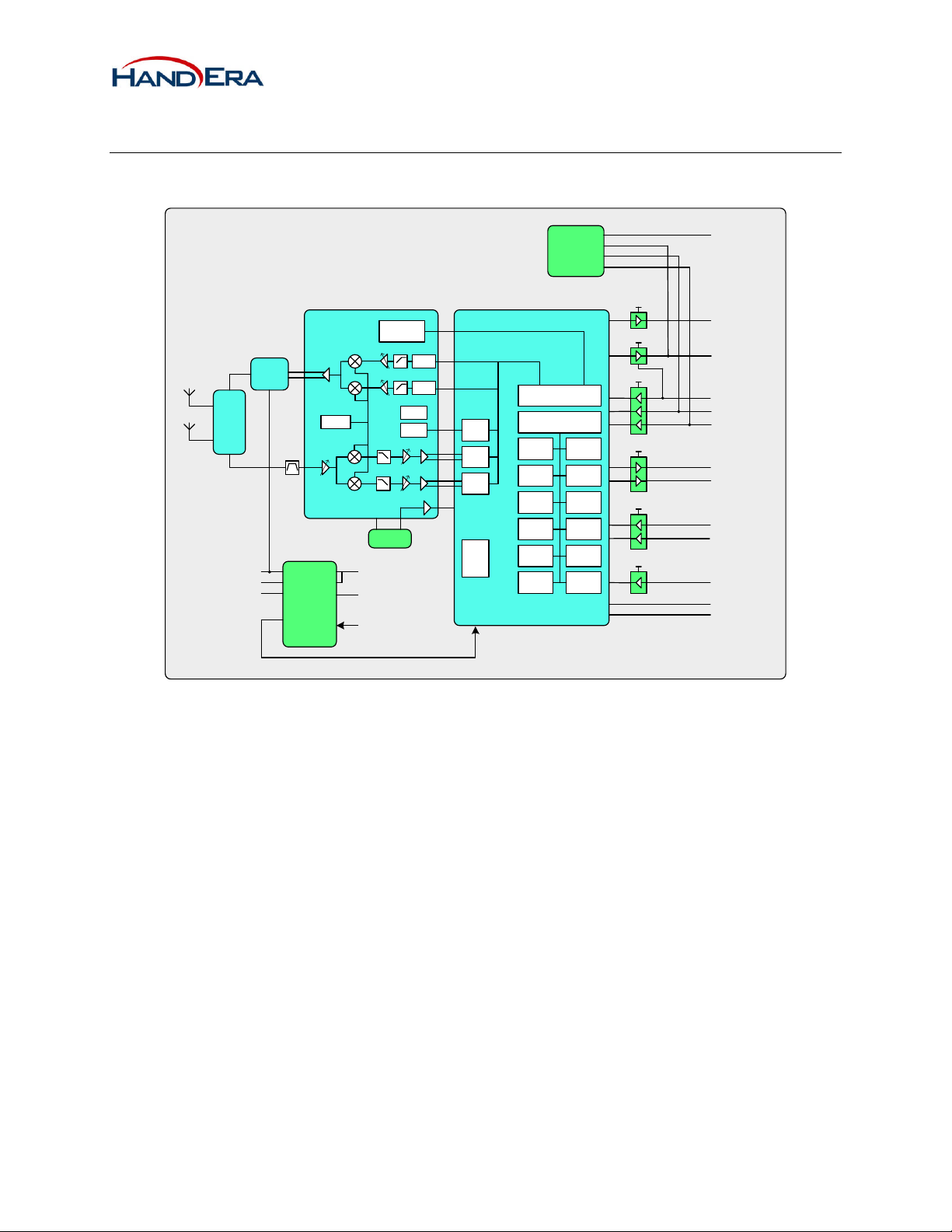
2 Electrical
2.1 Block Diagram
Antenna
VCORE
Switch
V_PA
VDD
PA
REGULATORS
RF Transceiver
3-Wire
Interface
Synth
XTAL
44MHz
VIN_3V
VIN_2V
WIFI_ON
AGC
RSSI
EEPROM
Baseband/MAC
1Kbit
VIN_HIO
EE_CS-
SPI_INT
VIN_HIO
DAC
DAC
Tx (I)
Tx (Q)
RSSI
A/D
Rx (I)
A/D
Rx (Q)
A/D
DC/DC
PHY &HW MAC
ARM7TDMI-S
DMA SCU
ICUROM
SRAM SDIO
SPITimers
AES SPIO
UARTWEP
VDD
VIN_BTIO
VIN_BTIO
VDD
SPI_MISO
WIFI_CS-
SPI_MOSI
SPI_CLK
BT_PRI
BT_BT
BT_RXIND
BT_WL
BT_RXIND
MODE 0
MODE 1
Figure 1 - Block Diagram
WF10020 5
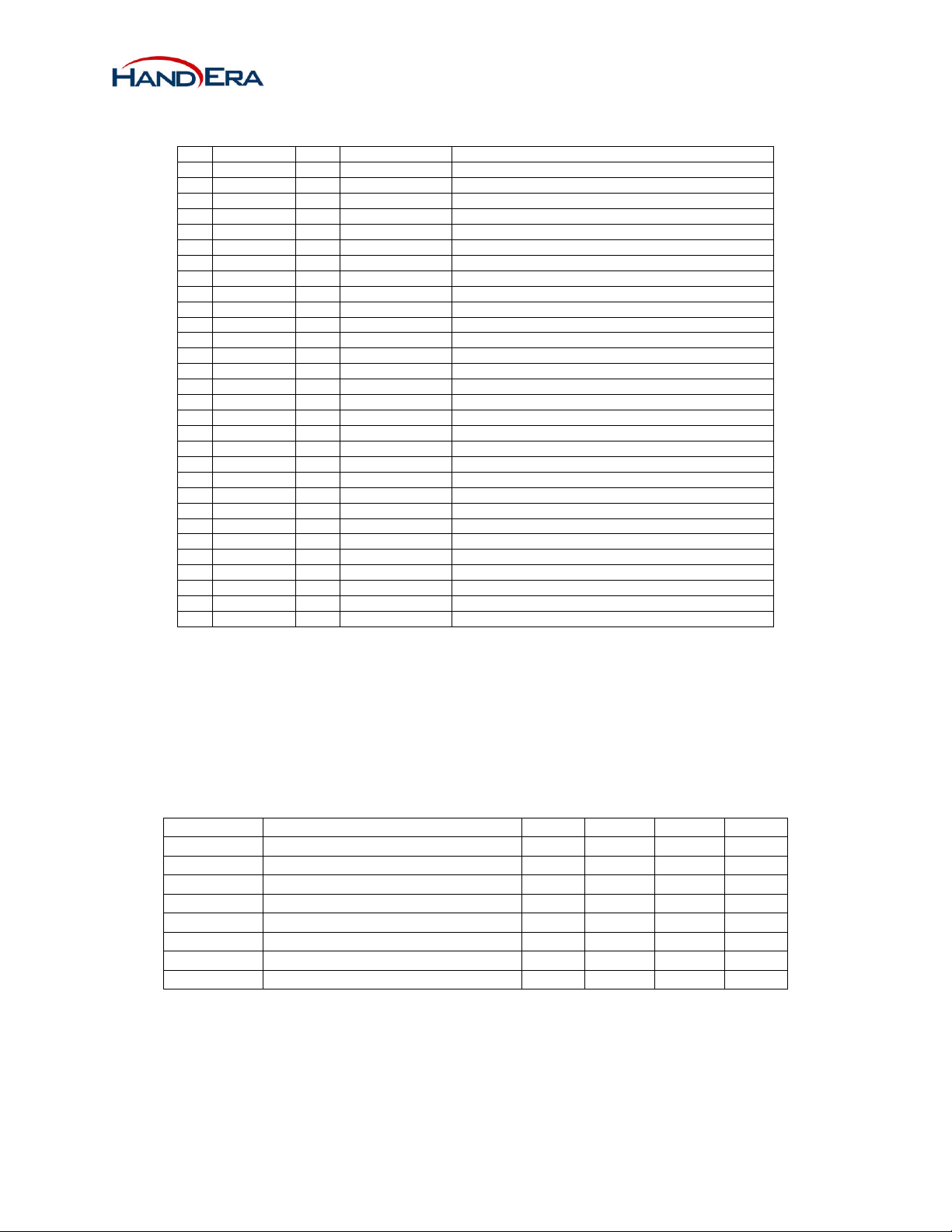
2.2 Connector Pin out
Pin Name Type Power Domain Description
1 SPI_INT O VIN_HIO SPI Interrupt
2 SDAT2
3 SPI_MOSI I VIN_HIO SPI Master Out/Slave In
4 SDAT3
5 SPI_MISO O VIN_HIO SPI Master In/Slave Out
6 SD_CMD
7 SPI_CLK I VIN_HIO SPI Clock
8 SD_CLK
9 WIFI_CS- I VIN_HIO SPI Chip select for WIFI module
10 SDAT0
11 MODE0
12 SDAT1
13 MODE1
14 EE_CS15 VIN_HIO PWR VIN_HIO SPI I/O Ring Power Supply
16 NC - --- NC
17 VIN_2V PWR VIN_2V Core Power Supply
18 BT_PRI
19 MODE2
20 BT_BT
21 WIFI_ON I VIN_HIO Enable Module
22 BT_RXIND3O VIN_BTIO WLAN receive indicator
23 MODE3
24 BT_WL
25 MODE4
26 VIN_BTIO PWR VIN_BTIO Bluetooth I/O Ring Power Supply
27 GND PWR Ground
28 VIN_3V PWR VIN_3V Main Power Supply
29 GND PWR Ground
30 NC - --- No Connect
1
1
1
1
2
3
3
3
I/O --- N SD data bit[2]
I/O --- SD data bit[3]
1
I/O --- SD Command
1
5
5
4
4
4
I --- SD Clock
I/O --- SD data bit[0]
I 2.85V SPI/SDIO interface selection
I/O --- SD data bit[1]
I 2.85V SPI/SDIO interface selection
I VIN_HIO EEProm Chip Select
I VIN_BTIO Bluetooth high priority traffic indicator
I --- NC
I VIN_BTIO Bluetooth arbitration signal
I --- No Connect
O VIN_BTIO WLAN arbitration signal
I --- NC
Table 1 - Connector Pin out
Notes:
1. WF-10020 only supports SPI, SDIO reserved for future models.
2. Not required if host stores the MAC address.
3. Optional. Used on systems with co-located Bluetooth device.
4. MODE2, MODE3 and MODE4 reserved for future products.
5. MODE0 and MODE1 must be tied low for SPI.
2.3 DC Characteristics
Symbol Parameter Min Nom Max Unit
V
IN_3V
V
IN_2V
V
IN_BTIO
V
IN_HIO
I
IN_3V
I
IN_2V
I
IN_BTIO
I
IN_HIO
Main Power Supply 3.1 - 3.6 V
Core Power Supply 2.25 - 3.6 V
Bluetooth I/O Ring Power Supply 1.2 - 3.6 V
SPI I/O Ring Power Supply 0.9 - 3.6 V
Main supply current 375 mA
Core supply current 85 mA
Bluetooth I/O Ring current 500 μA
SPI I/O Ring current 500 μA
Table 2
WF10020 6
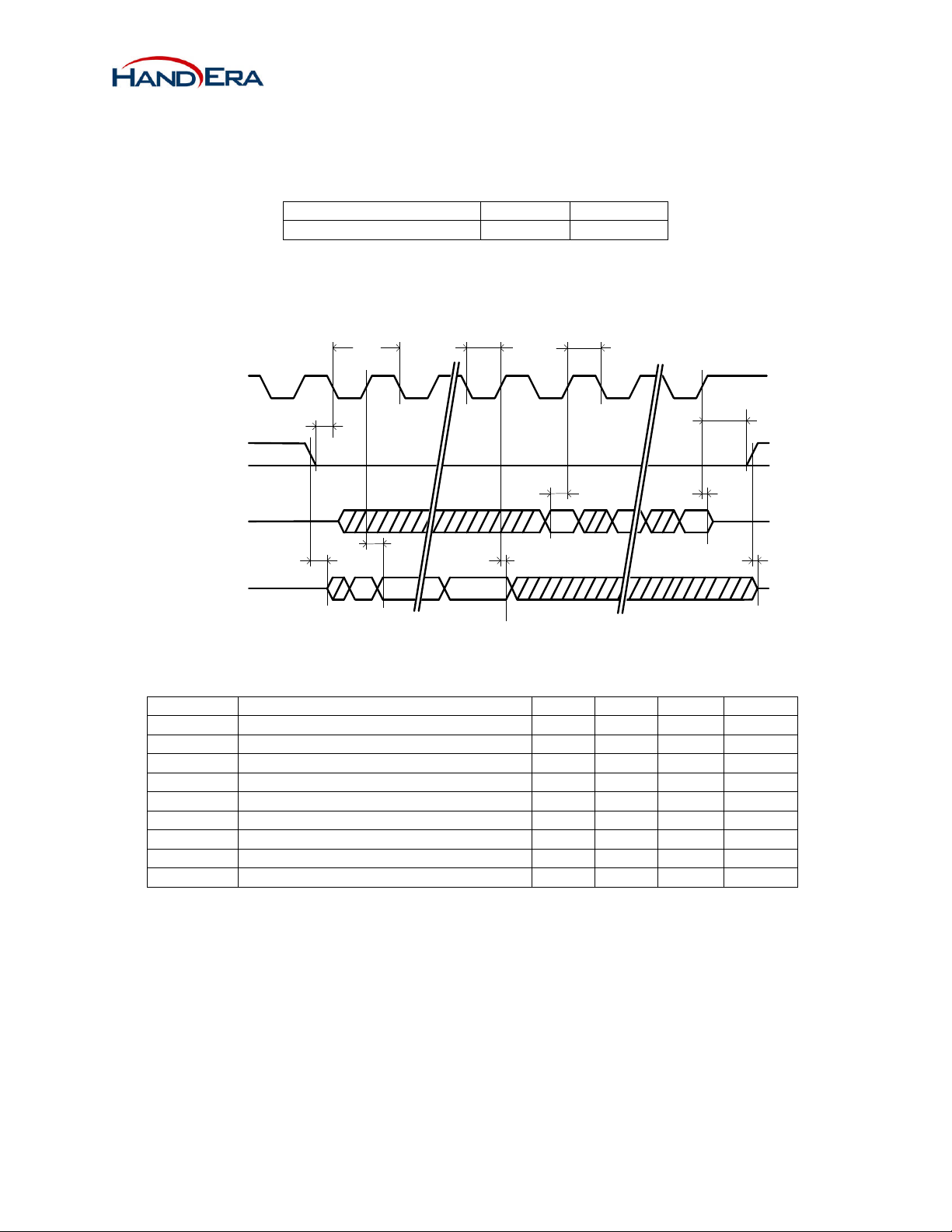
2.4 Interface Selection
The pins MODE0 and MODE1 are used to select between SPI and SDIO. The WF-10020 only supports SPI,
therefore, MODE0 and MODE should be set low.
Interface MODE0 MODE1
SPI 0 0
Table 3 - Interface selection
2.5 SPI Timing Diagram
SPI_CLK
WIFI_CS-
SPI_MOSI
SPI_MISO
t
t
EN_MISO
SU_SS
t
DLP_MISO
t
SCK
t
WL
t
OHP_MISO
t
SU_MOSI
t
WH
t
HO_SS
t
IH_MOSI
t
DIS_MISO
Figure 2 – SPI Timing Diagram (SPI_MISO clocked on rising edge of SPI_CLK)
Symbol Parameter Min Typ Max Units
t
SCK
t
WH
t
WL
t
SU_SS
t
HO_SS
t
SU_MOSI
t
IH_MOSI
t
EN_MISO
t
DIS_MISO
Period of SPI_SCK 15.0 - - ns
Clock high time 7.0 - - ns
Clock low time 7.0 - - ns
Setup time for WIFI_CS- 3.0 - - ns
Hold time for WIFI_CS- 0.0 - - ns
Setup time for SPI_MOSI 4.0 - - ns
Input hold time for SPI_MOSI 0.0 - - ns
Output enable time for SPI_MISO - - 8.0 ns
Output disable time for SPI_MISO - - 6.0 ns
Table 4 – AC Characteristics for SPI
WF10020 7
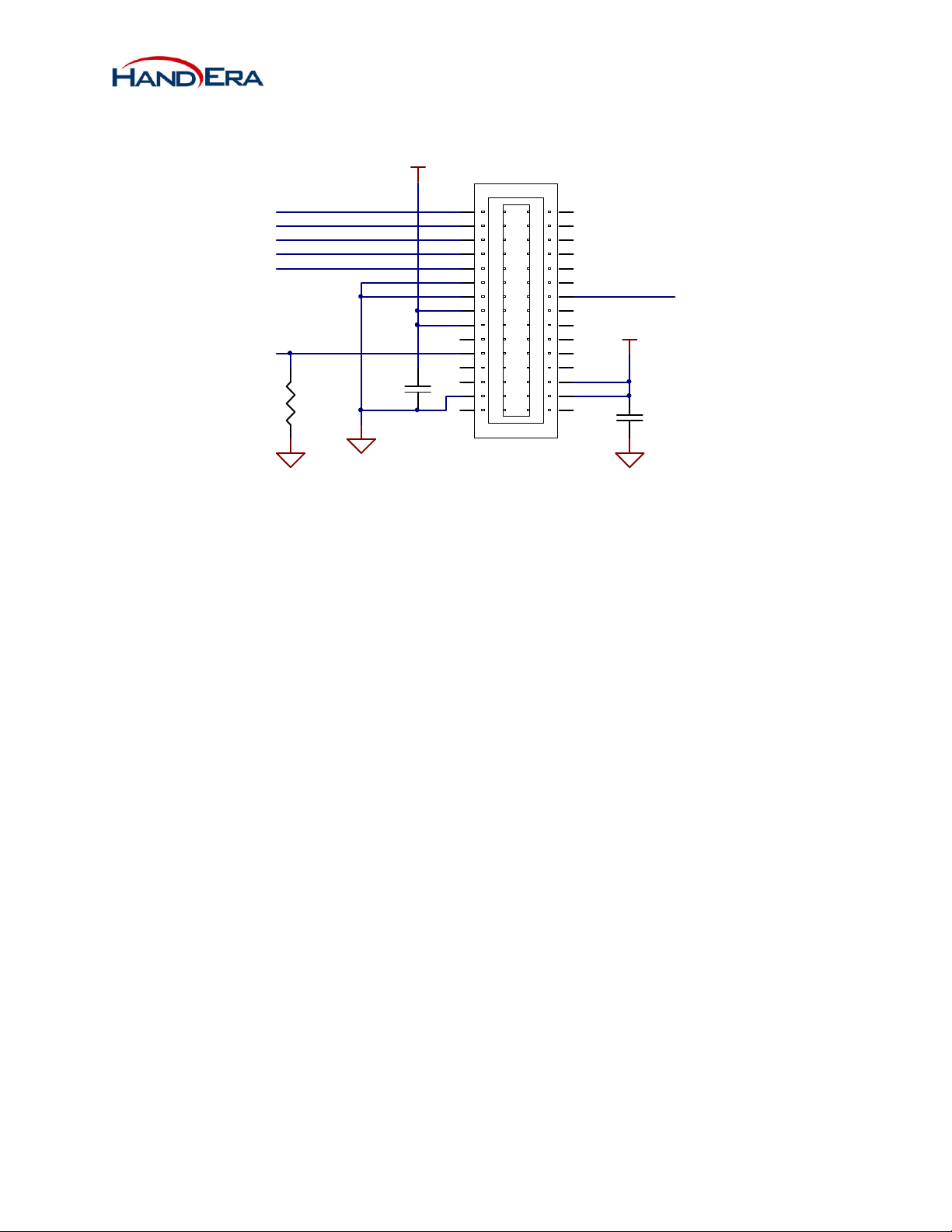
2.6 Host Schematic Example (SPI)
V3.3
J1
SPI_INT
SPI_MOSI
SPI_MISO
SPI_CLK
WIFI_CS-
WIFI_ON
R1
100K
GND
Mode0
Mode1
C1
2.2uF
GND
1 2
3 4
5 6
7 8
9 10
11 12
13 14
15 16
17 18
19 20
21 22
23 24
25 26
27 28
29 30
DF23 1.5MM RECEPTACLE
EE_CS-
V3.3
C2
2.2uF
GND
Figure 3 - Simple Host Example (SPI)
2.7 WLAN + Bluetooth Co-location
The WF-10020 supports the IEEE 802.15 recommended practice of Packet Traffic Arbitration (PTA) to avoid
simultaneous transmission with co-located Bluetooth devices. PTA is a system protocol that employs an arbitration
algorithm by which WLAN and Bluetooth contend for the medium. PTA is implemented using a simple four-line
interface on the WF-10020.
BT_WL
BT_BT
BT_PRI
BT_RXIND
Note: For systems that do not contain a co-located BT device, these lines can be left unconnected.
2.8 Regulatory Approvals
FCC Part 15 Class B
FCC Part 15.247, 15.205, 15.209 in USA
ETS 300 328 in Europe
CE Mark
WF10020 8
2.9 Performance
Receiver
802.11B 1Mbps 2Mbps 5.5Mbps 11Mbps Units
Sensitivity
1
Typical values, PER < 8%
1
-91 -87 -83 -83 dBm
Transmitter
802.11B 1Mbps 2Mbps 5.5Mbps 11Mbps Units
Output Power
2
Typical values, channel 6.
2
16.1 16.1 17.6 17.6 dBm
WF10020 9
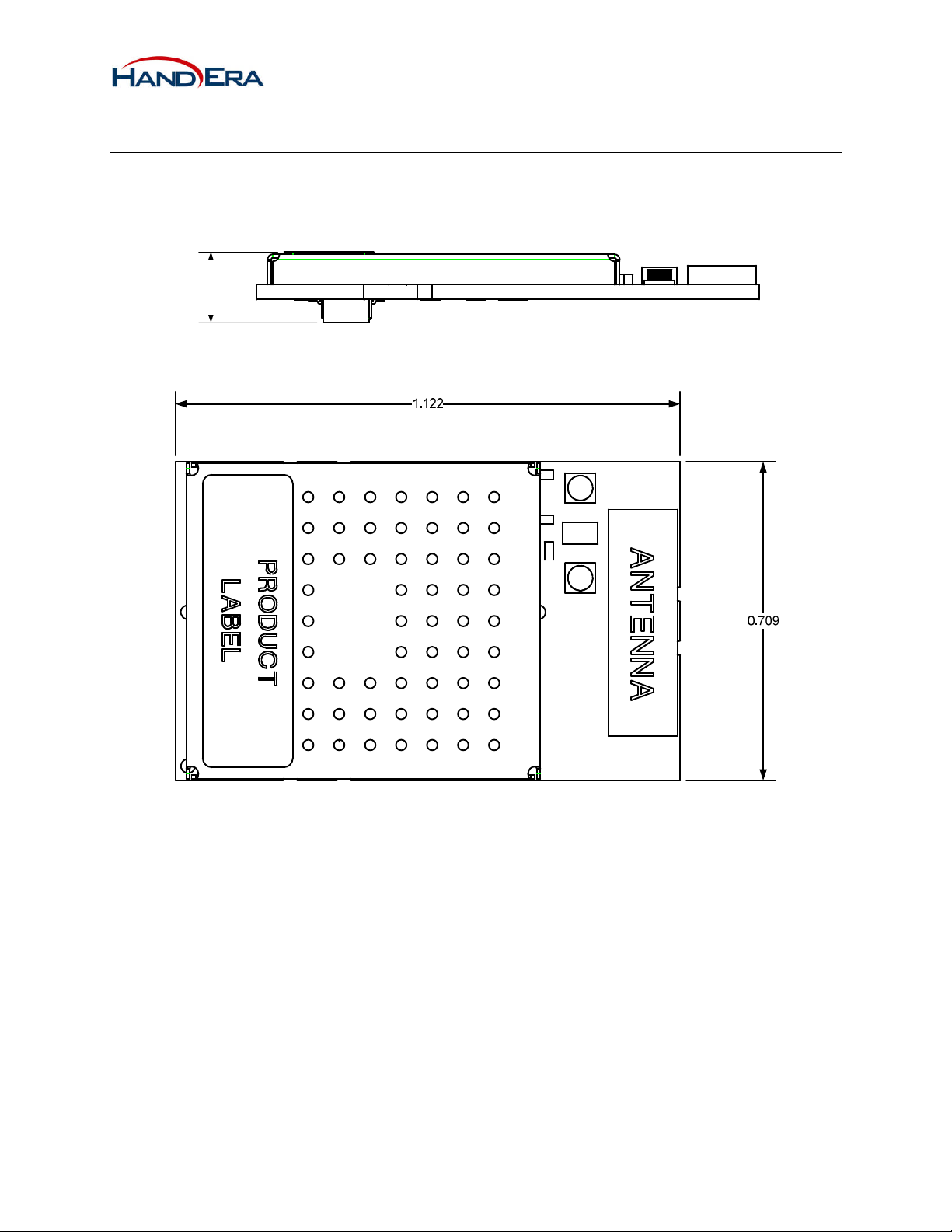
3 Mechanical
3.1 Dimensions
Note: All dimensions in inches.
0.157
Figure 4 – Side View
Figure 5 – Front View
WF10020 10
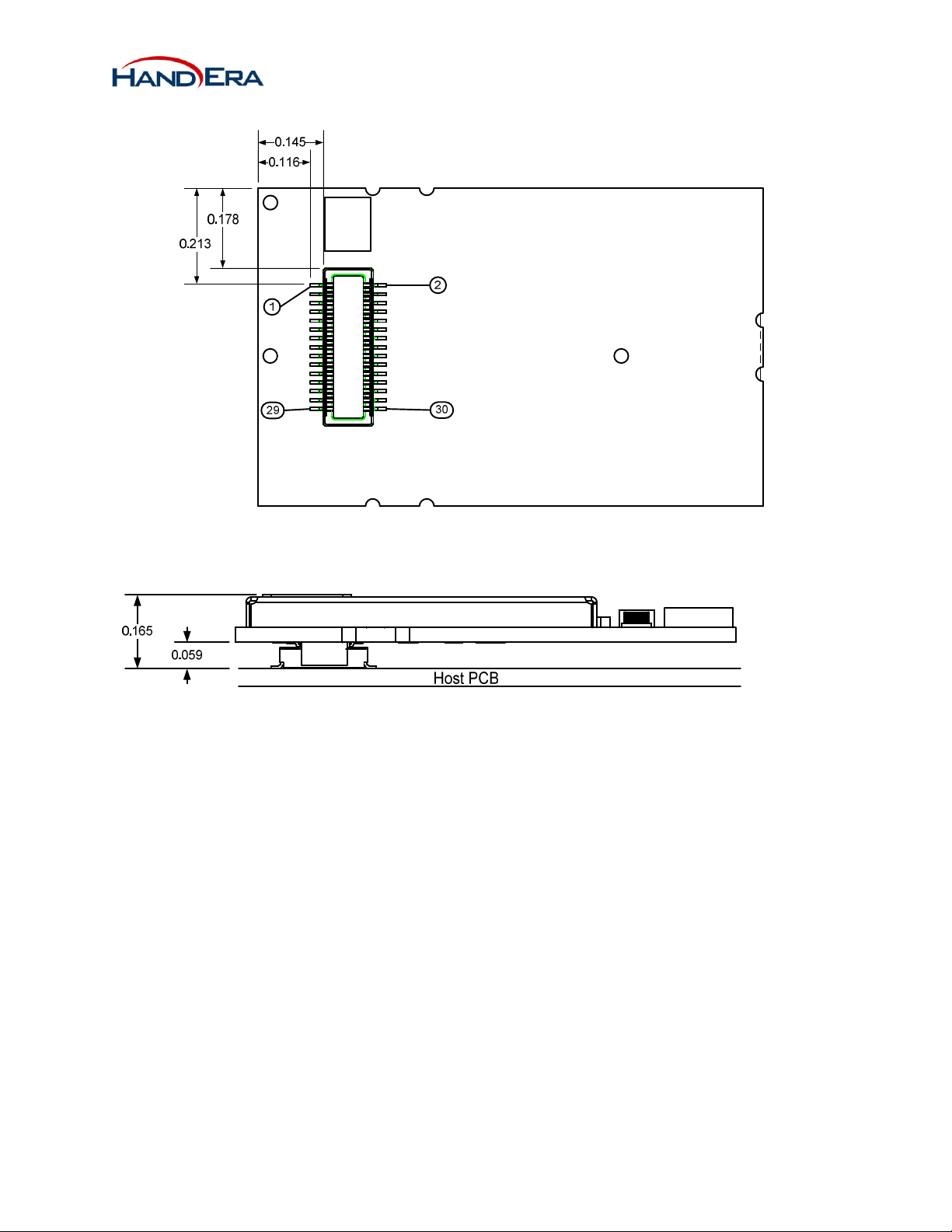
Figure 6 – Bottom View
Figure 7 - Host to Module
WF-10020 connector: Molex 55560-0307, or Hirose DF23C-30DP-0.5V(92)
Host PCB connector: Molex 54722-0307, or Hirose DF23C-30DS-0.5V(92)
3.2 Environmental
Non-Operational Conditions:
Ambient temperature: -30°C to +125°C.
Relative humidity: 5-95%, non-condensing.
Operational Conditions:
Ambient temperature: -30°C to +85°C.
Relative humidity: 5-95%, non-condensing.
WF10020 11
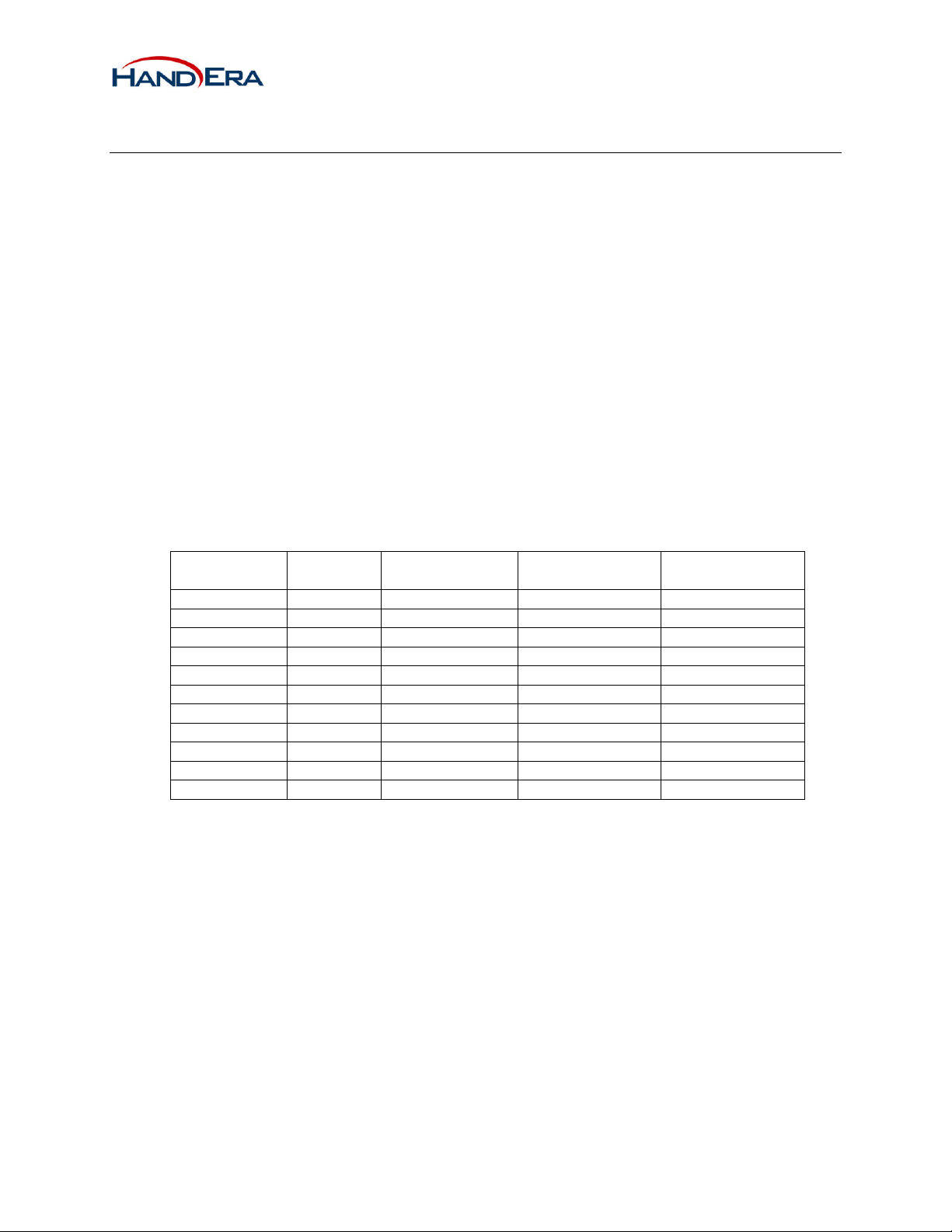
4 Software
4.1 Platform Support
Drivers for the following platforms currently exist for the WF-10020 module.
4.1.1 Intel PXA270
WinCE 5.0
Linux 2.6
MX21
4.1.2 Freescale MX21
PalmOS 5.4
WinCE 5.0
4.1.3 Samsung S3C2410
WinCE 5.0
4.2 Feature Matrix
Feature Palm base
driver
WEP Yes Yes Yes Yes
TKIP No Yes Yes Yes
AES/CCMP No Yes Yes No
WPA-PSK No Yes Yes Yes
EAP-TLS No No Yes Yes
EAP-TTLS No No Yes No
EAP-PEAP No No Yes Yes
LEAP No No No No
CCX No No No No
Roaming No Yes Yes (handled by OS)
PowerSave Yes Yes Yes Yes
Palm - Personal
security
Palm - Enterprise
security
WinCE 5.0
4.3 Definitions
4.3.1 WEP
40 bit / 64 bit encryption keys
104 bit / 128 bit encryption keys
RC4 encryption standard is used to encrypt data using encryption keys entered by the user
4.3.2 WPA
There are several meanings for WPA (Wi-Fi Protected Access). WPA is a commercial term developed by the Wi-Fi
consortium to add better security to legacy or WEP products. The core of WPA1 is the TKIP key management
protocol. WPA1 was designed to run on legacy wireless hardware.
WF10020 12

4.3.3 WP1
TKIP – Temporal Key Integrity Protocol is used by WPA as a method to periodically generate new keys. This
helps to provide protection so that keys cannot be easily broken by surveillance. TKIP was devised to upgrade
security on existing WEP products without requiring new encryption support in hardware.
RC4 – Encryption standard used to encrypt data using TKIP managed keys. RC4 is generally implemented in
the 802.11 chipset for speed.
802.1X – Access Control method, used to determine if a device is allowed access to the network. 802.1X
provides a family of protocols for user authentication, including PAP, MS-CHAP, and EAP. EAP (Extensible
Authentication Protocol) does not actually perform authentication itself, but rather provides a framework for
processing higher-level authentication methods, such as TLS and PEAP. The authentication server may reside
locally in an access point, or in a remote server which communicates to the access point (and the supplicant)
through the RADIUS (Remote Access Dial Up Server) protocol.
High-level authentication methods (EAP-methods) – Protocols such as TLS and PEAP that perform
authentication using the EAP protocol as a transport. These authentication methods often include encryption
key generation and two-way authentication (both device and network). TLS (Transport Layer Security) is a
standardized version of the Netscape security protocol SSL, and uses digital certificates for user authentication.
PEAP (Protected-EAP) is an encrypted version of EAP in which the EAP exchanges are performed in a
protected “tunnel.”
LEAP – Cisco Light-EAP, developed before the 802.1X standard was complete. LEAP provides the same
functionality as 802.1X, with the authentication server implemented inside Cisco access points. LEAP is
considered more secure than WEP but less secure than WPA1.
MIC – The Message Integrity Checker is used to detect tampering with packets on an active wireless link. The
MIC can also invoke countermeasures if tampering is detected, such as temporarily shutting down the network.
WPA “Personal” usage model: WPA-PSK
This configuration is sometimes called “WPA Personal”. PSK stands for “Pre-Shared Keys” and refers to a
manual process of initial key distribution. The word “distribution” is used because a single key is provided
to many users of the same access point. For example, a system administrator might distribute the key to
many users of a single access point. The users need to manually enter the key provided by the system
administrator into their computers through a preferences panel. Afterwards, TKIP takes over management
of the keys.
WPA “Enterprise” usage model: WPA-EAP
This configuration provides automatic key management using an 802.1X authentication server. This is
sometimes called “WPA Enterprise”, and requires more sophisticated infrastructure. Generally special
software such as a RADIUS Server program is required to run on a server. This software is responsible for
authenticating users.
There are many high-level authentication/key distribution methods that can be used with WPA-EAP. The
method specified by WPA is TLS.
4.3.4 WPA2
WPA2 (Wi-Fi Protected Access 2). WPA2 is a commercial term developed by the Wi-Fi consortium to refer to
the more generic IEEE 802.11i suite of security protocols. The core of WPA2 is the CCMP key management
protocol and the AES encryption engine.
CCMP – Counter Mode-CBC MAC Protocol is used as a superset replacement of TKIP in WPA2.
AES - Advanced Encryption Standard is an encryption method that is used to encrypt data using CCMP
managed keys. AES is provided by the 802.11 chipset.
RSN – A network in which all stations use 802.11i advanced security protocol is called a Robust Security
Network. If legacy devices are allowed to connect, the network is called a TSN (Transitional Security
Network).
WPA2 cannot be implemented on legacy 802.11 chipsets because of the required hardware AES support.
WF10020 13

4.3.5 CCX
Cisco Compatible Extensions(CCX) are a collection of protocols defined by Cisco for wireless security, forming a
super-set of WPA and 802.11i. In addition to authentication and encryption, CCX includes specifications for power
management, roaming, and VOIP. As of 2005 there are four different versions, each version adding extensions to the
previous version.
V1 – 802.11, 802.1X, WEP, LEAP, CKIP (Cisco TKIP), multiple SSID support.
V2 – WPA, roaming, power management.
V3 – WPA2, EAP-FAST, Wi-Fi multimedia.
V4 – PEAP-MSCHAP, voice metrics, AP-directed roaming.
WF10020 14
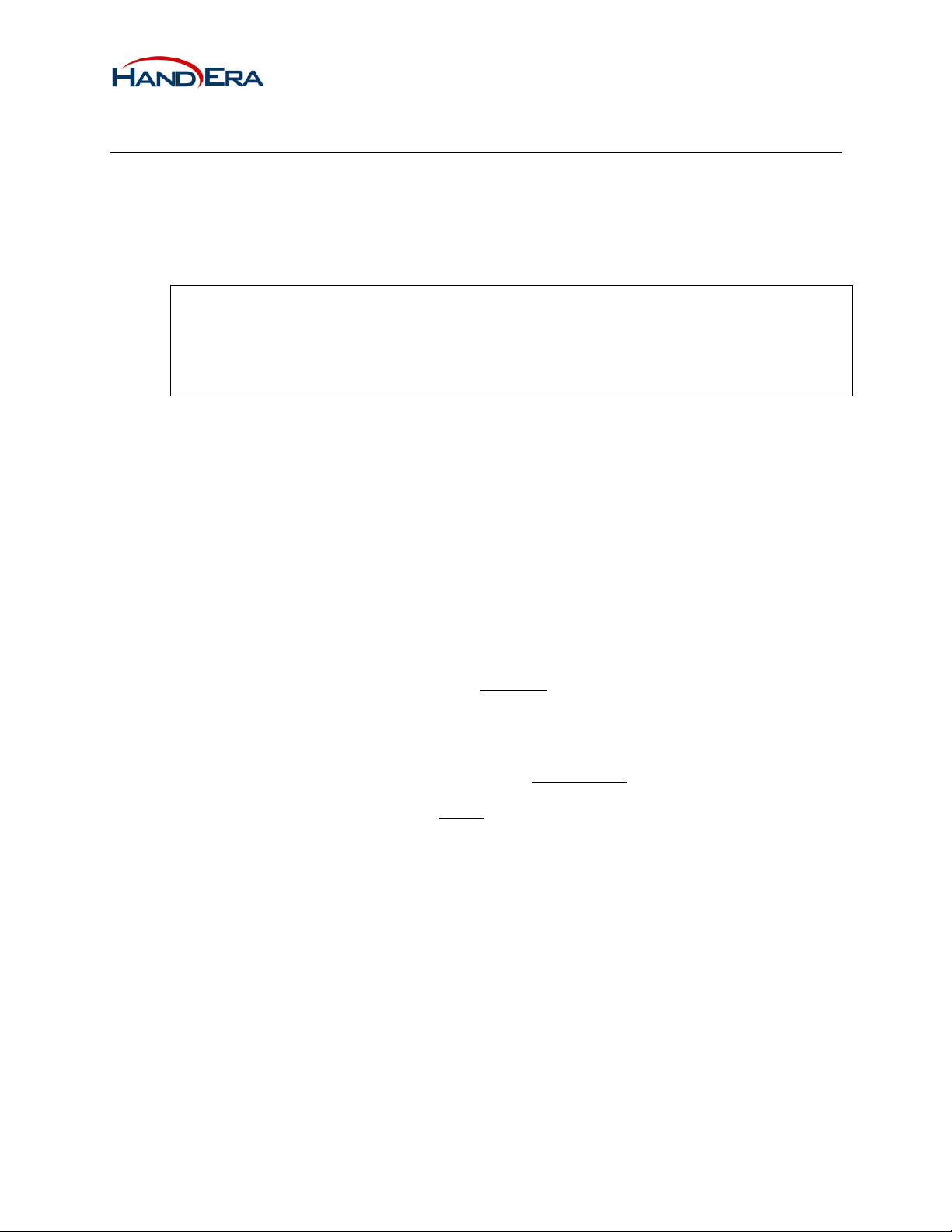
5 Appendix A: Agency Certifications
5.1 United States (FCC):
The WF-10020 802.11b Module complies with Part 15 of the FCC rules and regulations. Compliance with
the labeling requirements, FCC notices and antenna usage guidelines is required.
1
The HandEra WF-10020 802.11b Module may only be used with antennas that have been tested
and approved for use with this module. All other antennas must be tested to comply with FCC §
15.203 (Unique Antenna Connectors) and § 15.247 (Emissions) and will require a Class 2
Permissive Change or a new Certification.
Co-location with transmitters other than Bluetooth model WML-C29, FCC ID: POOWML-C29XX, is not allowed.
IMPORTANT NOTE: In the event that these conditions can not be met, then the FCC authorization is
no longer considered valid and the FCC ID can not be used on the final product.
WF10020 15

5.1.3 FCC Notices
This device complies with Part 15 of the FCC rules. Operation is subject to the following two conditions: (1) This
device may not cause harmful interference, and (2) this device must accept any interference received, including
interference that may cause undesired operation.
Note: This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to
Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful
interference in a residential installation. This equipment generates, uses, and can radiate radio frequency
energy and, if not installed and used in accordance with the instructions, may cause harmful interference to
radio communications. However, there is no guarantee that interference will not occur in a particular
installation. If this equipment does cause harmful interference to radio or television reception, which can be
determined by turning the equipment off and on, the user is encouraged to try to correct the interference by
one or more of the following measures:
Re-orient or relocate the receiving antenna
Increase the separation between the equipment and receiver
Connect equipment and receiver to outlets on different circuits,
Consult the dealer or an experienced radio/TV technician for help.
The use of shielded I/O cables is required when connecting this equipment to any and all peripheral or host devices.
Failure to do so may violate FCC rules.
Note: Changes or modifications not covered in this manual must be approved in writing by the manufacturer's
Regulatory Engineering Department. Changes or modifications made without written approval may void the
user's authority to operate this equipment.
WF10020 16

Figure A-1. Required FCC Label for OEM products containing the WF-10020 802.11b Module
Contains FCC ID: URZ-WF10020
The enclosed device complies with Part 15 of the FCC Rules. Operation is subject to the following two
conditions: (i.) this device may not cause harmful interference and (ii.) this device must accept any
interference received, including interference that may cause undesired operation.

Icon User Manual
Table of Contents
Introduction
Orientation
The Icon Application Environment
Input Techniques
The Address Book
The Music Player
The Library Menu
The Internet Menu
Browsing the Web
Email
RSS Reader
The Tools Menu
The Utilities Menu
The Games Menu
Appendix
Detailed Table of Contents
Introduction
Congratulations! You now have in your hands the most powerful, flexible, and easy-to-use
personal data assistant (PDA) available today. The fact that it has no screen and is designed
specifically for use by blind students and professionals makes the unit even more compelling. The
device's developers have vast experience in the field of blindness and technology and many are
users of such devices themselve s.
Let's take a moment to go over the organization of this manual: Conventions used in this
Document.
This documentation represents multiple key sequences, or rather, keys that are to be pressed
simultaneously, by separating the individual keys with a plus sign. So, if you were asked to press
and hold the pound key while you press the number 1, the key would look like this: # + 1. Keys
that are to be pressed in succession, or one after another, are separated by a comma. For
example, the keypad shortcut used to get to the RSS application from the Applications Menu is to
press 4 followed by 3 and will appear as 4, 3.
Top of Page
Orientation
Input and Output Connections
The following connections come standard on the Icon:
• 802.11b wireless internet connectivity

• Bluetooth connectivity
• Stereo speakers
• Internal mono microphone
• Stereo microphone jack
• 3.5 MM headphone jack
• Mini headset jack
• Mini-SD card slot
• Power connector
• Record button
• Speaker switch button
• Volume control
• Telephone keypad with additional navigation and function keys.
• USB connection Docking Station
You may also elect to purchase an optional docking station with either a braille or QWERTY
keyboard. This docking station provides the small hand-held unit with a full keyboard, phone
modem, Ethernet connector, USB connectivity, better stereo speakers, and 4 times the normal
battery life. This accessory will prove especially useful to those students and professionals who
prefer a full sized keyboard with the convenience and power of the PDA.
Location and Definition of Buttons
The Icon is designed for easy, intuitive one-handed operation when it's not being used in a
docking station. You might hold it in the palm of one hand, and enter commands with the other; or
you can easily operate it with one hand while it's on a desk or clipped to a pocket or belt in the
included carrying case. For this orientation, place your Icon so that the keypad faces up and the
earpiece (an oval-shaped bump with vertical ridges) is furthest away from you. We will be
reviewing the Icon's buttons and features by surface in the following order:
• The Front Face
• The Left Edge
• The Top Edge
• The Bottom Edge
• The Power Connector
• The Back Face
(There are no input elements on the right edge of the Icon)
Front Face
The way you navigate through the Icon's suite of programs will be familiar to you if you've ever
used a cell phone; except that every feature is accessible without a screen, and the buttons have
been designed to be prominent and easy to tell apart.
On the lower half of the front face, you'll find twelve equally sized keys grouped together. These
make up the telephone keypad. The telephone keypad will allow you to use numeric shortcuts to
get to any program from the applications menu; enter contact numbers; and write text.
The Icon phone pad is laid out like a standard telephone keypad, and like a standard telephone
keypad, allows for entering either numbers or letters depending on context. When you're in the
Icon menu system, all key presses on the phone pad will be treated as digits; however, when
you're in an application that requires text input, such as the word processor or your list of songs in
the music player, you will press one of the 9 main number keys to get the letter or punctuation
symbol you want. By default, you have one second between presses before the system inputs the
letter you have selected. You may change the time Icon waits to input the character in the general
settings section of the Utilities Menu described later in this manual.

On the upper half of the face, just above the telephone keypad, there are several more buttons.
Directly above the telephone keypad is a row of 3 keys. The corner-shaped key on the left is the
OK button: this button agrees to any action the Icon's operating system needs confirmation to
perform, can open a highlighted file or program, saves changes in a dialog, and answers yes to
Icon questions. The central button, which is rectangular, is called the Program Menu button: when
you press it within an application, you'll get a list of options relevant to the task you're working on.
For example, in the music player application, you'll be able to access options such as Shuffle and
What's Playing? To the right of the Program Menu button, you'll notice another corner-shaped
key; this one is the Cancel button, and pressing it briefly will allow you to abort, or call off, any
operation you've chosen by mistake. In addition, cancel will exit a program or menu, and answers
no to Icon questions. A long press of about a second will turn the Icon on and off. A short tone
and a vibration mean the unit is on; a double tone and double vibration mean it is off.
The central group of buttons is shaped like a diamond and is made up of five parts. The corners
of the diamond are the up, down, left and right arrow keys; the round button in the center is the
select key. You'll use the arrow keys for navigating through menus and lists of options, as well as
for navigating text in documents.
In text environments, the left and right arrows move backward and forward by character; the up
and down arrows move backward and forward by line. Holding down the up and down arrows will
move you to the top and bottom of a document respectively. Holding down the left and right arrow
keys will take you to the beginning or end of the current line. Holding down the 0 key while using
the arrow keys moves in larger steps: doing so with the left and right will move by word; doing so
with the up and down arrows will move by paragraph. Finally, holding down pound while pressing
the up and down arrows will move you by page.
In menus, the up and down arrows move through your choices. The right arrow key will open a
submenu any time one is available: otherwise it will open the highlighted application. The left
arrow key will return you to the previous level in a menu system.
The select key will allow you to select and confirm actions such as choosing a program or playing
a song. The Select key also stops and starts continuous reading in a text environment, stops and
starts media playback, and toggles between pause and reco rding in the voice recorder.
Now, direct your attention to the top part of the arrow diamond. Flanking the up arrow key are two
more buttons. The one on the right is the Help key - valuable for new and seasoned users alike, a
brief press of the Help key will provide a message relevant to your current place in the system.
For example, if you're setting the date and time, the Help key will place you in the section of the
user's manual that lists the steps necessary to set date and time correctly. Once you're done
reviewing the information brought up by the help key, simply press Cancel to return to what you
were working on when you first pressed Help. A longer press, of about a second, will turn on
KeyLearn Mode. Once you're in KeyLearn Mode, press any key to find out what it does; press the
Help key again, for one second, to turn KeyLearn mode off.
The key on the left is the Status key. Pressing it briefly will repeat the last message spoken by the
Icon. Pressing it twice in rapid succession will yield program specific status. For example, if you
are downloading e-mail, press status twice quickly, and Icon will tell you where it is in the
receiving process and how far it has to go. Pressing and holding it for about a second will bring
up the status application, where you can arrow up and down to check your battery level, the time,
pending appointments, whether your wireless connection is on or off, and the software version
the Icon is running. If you would like the last phrase spoken by the Icon to be spelled, press the
status key followed by the help key.
Finally, move your hands above the Status and Help keys. The last three keys on the unit are two
dot-like keys with a bar in the middle. Whenever you find these keys at the top of the Icon, you'll
know you're oriented in the right position. The left and right round keys are named Program Key 1

and Program Key 2. Later, you'll learn how to set each of these to a favorite application or
function. For example, one could start the media player, and the other could open the calendar.
By default, a long press of Program Key 2 turns your wireless connection on and off. The central
key on this row, a rectangular bar, is the Applications key. A quick press of this key brings up the
Icon's main menu, from which you can access every application. A longer press will bring up the
Icon's task manager, where you can review and manage your currently open applications.
The Left Edge
On the left edge of the Icon, you'll find several buttons relevant to sound input and output.
Starting at the top, just below the left-hand speaker, you'll notice a long rocker switch. This is the
Icon's volume control. A press of the upper part of the control will raise the Icon's volume, and a
downward press will lower it. Unless the Icon is reading text, you will also hear an announcement
of "louder" or "softer" as you increase or decrease the unit's volume, as well as an announcement
of "loudest" or "softest" when you have changed the volume to the loudest or softest setting.
Sometimes, you may want to control the volume of media content on the Icon without altering the
volume of the speech output; or you may want to raise or lower the volume of speech but keep
the media volume the same. Hold down the star key while raising or lowering the volume to
control only the volume of the speech output. When you do this, you will still get the audible
announcement of "softer" or "louder" as long as the Icon is speaking text. Hold down the 0 key
while raising and lowering the volume to control only the volume of media content. When you do
this while media is playing, you will get no announcement by way of confirmation, but you will be
able to hear the media getting louder or quieter. If you change the media volume while no media
is playing, you will hear a set of beeps, low to high while the volume is being increased and high
to low when it is being decreased.
Directly underneath the volume control, there is a round button that toggles the Icon's audio
between the external speakers and the earpiece mounted above the keypad. When you have
headphones plugged into the Icon, this button will have no effect. Toggling between the speakers
and the mounted earpiece allows you to choose between a robust stereo sound and a private
listening experience. The earpiece is especially handy if you need to jot down a quick note or look
up a phone number while you're in public and headphones are inconvenient.
You'll find one more button below the speaker/earpiece toggle, separated by a small ridge. This
lowest button is called the Quick Record button. Later, you'll learn how to manage the file names,
quality and storage locations of your recordings, but the Quick Record button allows rapid audio
capture without any prior setup. Just press it for about two seconds to start recording, and then
press Cancel to stop. All files recorded this way are saved in a mono, low-bitrate format suitable
for up-close voice recording. They are automatically tagged with the time and date they were
taken, and saved to the Recordings folder of the Icon's internal flash disk.
The Top Edge
The top edge of the unit contains three audio jacks and a Mini-SD slot. The left-most jack accepts
cables from external microphones. The Mini-SD slot is located at the center of the top edge just to
the right of the microphone jack. You can buy Mini-SD cards for this slot that will expand the
Icon's onboard storage and allow you to swap data with the owners of other SD-compatible
devices. The headphone jack is located just to the right of the Mini-SD slot. It accepts standard
3.5MM headphone jacks, so you can continue to use your favorite pair of headphones with the
Icon. The third jack on the top edge of the unit is a sub-mini headset jack and accepts
combination microphone/headphone headsets typically used as accessories with mainstream cell
phones. This type of headset is ideal for making verbal notes while you're using the Icon

The Bottom Edge
On the bottom edge of the unit and toward the left side, there is a textured slide switch. This is
your Keypad Lock. Normally, it should be in the left position, so that you can use the keypad to
type. If you want to lock your keypad to avoid accidental key presses, slide this switch to the right,
and the unit, if it is on, will announce "keypad locked". Sliding this switch back to the left will
cause the unit to announce, "Keypad unlocked". If you find that your Icon doesn't seem to be
receiving key presses, it's a good idea to check the Keypad Lock switch to make sure it's in the
left side position.
Interface Connector
The center portion of the bottom edge contains the connector into which you plug your
power/sync cable. This cable is used for three purposes:
• charging the battery,
• connecting the unit to your PC,
• and connecting other USB devices to the unit.
The cable contains a flat connector with releases on the left and right to help keep the connecter
attached. One side of the connector is completely smooth, and the other side has an inlaid
rectangle that contains some embossed text. The side with this textured rectangle should be
facing up when you plug the connector into the Icon. Since the connector to the cable contains
several fairly delicate pins, it is important to check that the connector is being inserted properly,
and it should connect without the need for much force. Press in on both releases when you want
to disconnect this cable from your Icon.
A short cable runs from the bottom of the connecter and ends in a box that contains three ports.
On the bottom edge are a USB client and a USB host; on the top edge, to the left of where the
cable exits the box, is the alternating current (AC) connecter into which you plug the wall unit to
charge the device's battery. Remember that the Icon can charge itself through your PC'S USB
port, so the AC charger is necessary only when you don't have a PC connection available or
when it is more convenient to use the Icon for long periods of time away from your PC (for
example, if you've integrated it into your home stereo system).
Battery Care and Use
Your Icon uses a lithium-ion battery with a rating of 1700 milliamp hours. Given this power level
and the typical usage patterns and the power consumption of the unit, you may expect to get
about six to eight hours of steady use from the device when the wireless radio is off and about
three to four hours of usage with the radio on. Expect about four times this battery performance
when using the batteries in either of the docking stations. If you need more time away from AC
power, you may consider purchasing an additional battery and use it to supply another charge
when the first battery's charge fades. To change batteries, power the unit off, change the battery,
and turn the power back on. It's a good idea to have the replacement battery ready to insert
before removing the current battery, as you have only about 45 seconds to make the change
before the clock settings are lost.
Warning
Do NOT remove the battery while the Icon is running. Removing the battery while the unit is
running is strongly discouraged by the manufacturer. Removing the battery while your Icon is on
may cause data loss, data corruption, and loss of the clock settings.
Resetting Your Icon
In the rare instance that your unit locks up or begins to act strangely, you may need to reset. To
access the reset button, you need to remove the battery compartment door, locate the deep
round recess that contains the reset button, and press it with a small object such as a stylus or
 Loading...
Loading...