Page 1

Table of Contents
1 WLAN Service Configuration ···················································································································1-1
WLAN Service Overview·························································································································1-1
Terminology·····································································································································1-1
Client Access···································································································································1-2
802.11 Overview·····································································································································1-5
CAPWAP Overview·································································································································1-5
Introduction to CAPWAP·················································································································1-5
CAPWAP Link Backup ····················································································································1-5
WLAN Topologies···································································································································1-7
WLAN Topologies for ACs ··············································································································1-7
WLAN Topologies for Fat APs ······································································································1-10
Protocols and Standards·······················································································································1-11
Configuring WLAN Service···················································································································1-12
Configuration Task List··················································································································1-12
Enabling WLAN Service (only supported on ACs)········································································1-12
Configuring Global WLAN Parameters (only supported on fat APs)·············································1-12
Specifying the uplink interface (only supported on fat APs)··························································1-13
Specifying a Country Code············································································································1-14
Configuring Software Version Automatic Update··········································································1-14
Configuring a WLAN Service Template·························································································1-14
Configuring an AP (only supported on ACs)·················································································1-16
Configuring Auto AP······················································································································1-17
Configuring CAPWAP Dual-Link (Supported only on ACs)···························································1-17
Configuring the Radio of an AP·····································································································1-18
Configuring a Radio Policy on an AC or the Radio of a Fat AP····················································1-19
Configuring 802.11n······················································································································1-20
Displaying and Maintaining WLAN Service···················································································1-21
Configuring AP Group (only supported on ACs)···················································································1-22
Configuring an AP Group··············································································································1-23
Applying the AP Group in a User Profile·······················································································1-23
Displaying and Maintaining AP Group···························································································1-24
Configuring SSID-Based Access Control······························································································1-24
Specifying a Permitted SSID in a User Profile··············································································1-24
WLAN Service Configuration Examples ·······························································································1-25
WLAN Service Configuration Example (On an AC)······································································1-25
WLAN Auto-AP Configuration Example (On an AC)·····································································1-27
CAPWAP Dual-Link Configuration Example (On an AC)······························································1-28
802.11n Configuration Example····································································································1-29
WLAN Service Configuration Example (on a FAT AP) ·································································1-30
AP Group Configuration Examples·······································································································1-31
AP Group Configuration without Roaming····················································································1-31
AP Group Configuration for Inter-AC Roaming·············································································1-34
i
Page 2

z Support for some features varies by router model.
z Refer to the command manual of this module for command and parameter support, default values
and value ranges of the MSR series routers.
z All the models of the MSR series routers are centralized devices.
z The MSR series routers can serve as APs only.
1 WLAN Service Configuration
WLA
Wh n configuring WLAe N service, go to these sections for information you are interested in:
z WLAN Service Overv
z 802.11 Overview
z CAPWAP Overview
z WLAN Topologies
z Protocols and Standards
z Configuring WLAN Service
z Configuring AP Group (only supported on ACs)
z Configuring SSID-Based Access Co
z
WLAN Service Configuration Examples
z AP Group Configuration Exam
iew
ntrol
ples
N Service Overview
Wireless Local Area Networks (WLAN) have become very popular because they are very easy to setup
and use, and have low maintenance cost. Generally, one or more access points (APs) can cov
g or an area. A WLAN is not completely wireless becau
buildin se the servers in the backbone are fixed.
The WLAN solution allows you to provide the following wireless LAN services to yo
z WLAN client connectivity to conventional 802.3 LANs
z Secured WLAN access with different authentication and encryption methods
z Seam
less roaming of WLAN clients in the mobility domain
ur customers:
er a
Terminology
Client
A handheld compute
Acce
ss point (AP)
An AP bridges frames between wireless and wired networks.
r or laptop with a wireless Network Interface Card (NIC) can be a WLAN client.
1-1
Page 3

Access controller (AC)
An AC can control and manage all APs in a WLAN. The AC communi cates with an authentication server
for WLAN client authentication.
Fat AP
A fat AP controls an d mana ges all as soci at ed wirele ss stations and bridges frames between wired and
wireless networks.
SSID
Service set identifier. A client scans all networks at first, and then selects a specific SSID to con nect to a
specific wireless network.
Wireless medium
A medium that is used for transmitting frames between wireless client s. Radio f requency is use d as the
wireless medium in the WLAN system.
Distribution system
A distribution system is used to forward frames to their destinations. It is the backbone to transmit
frames between access points.
Split MAC
In split MAC mode, APs and ACs manage different services. An AP manages real-time services, such
as beacon generation, power management, fragmentation and defragmentation. An AC manages
services related to packet distribution, association, dissociation and reassociation.
Client Access
A client access process involves three steps: active/passive scanning, authentication and association.
Figure 1-1 Establish a client acces
s
Scanning
1) Active scanning
1-2
Page 4
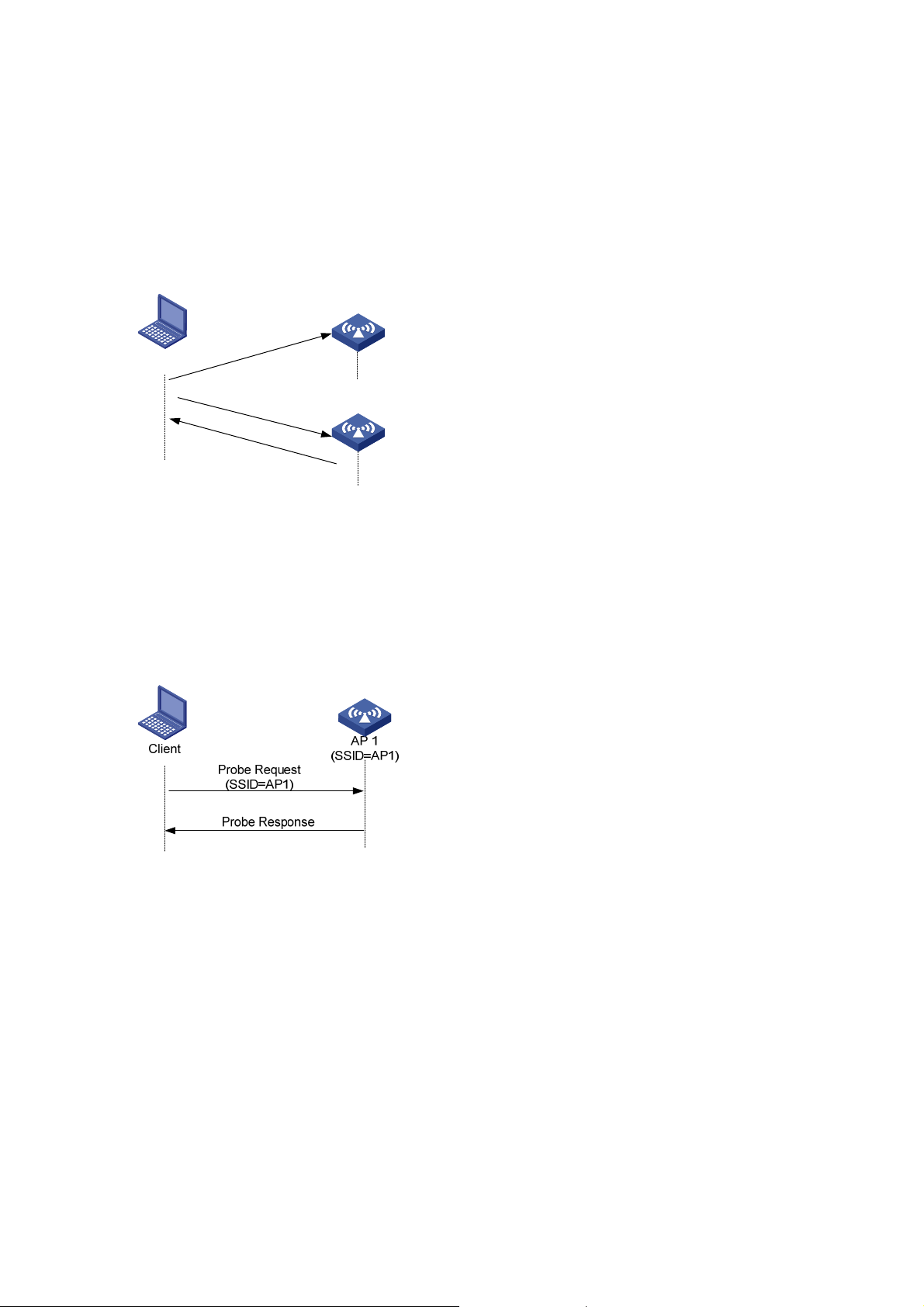
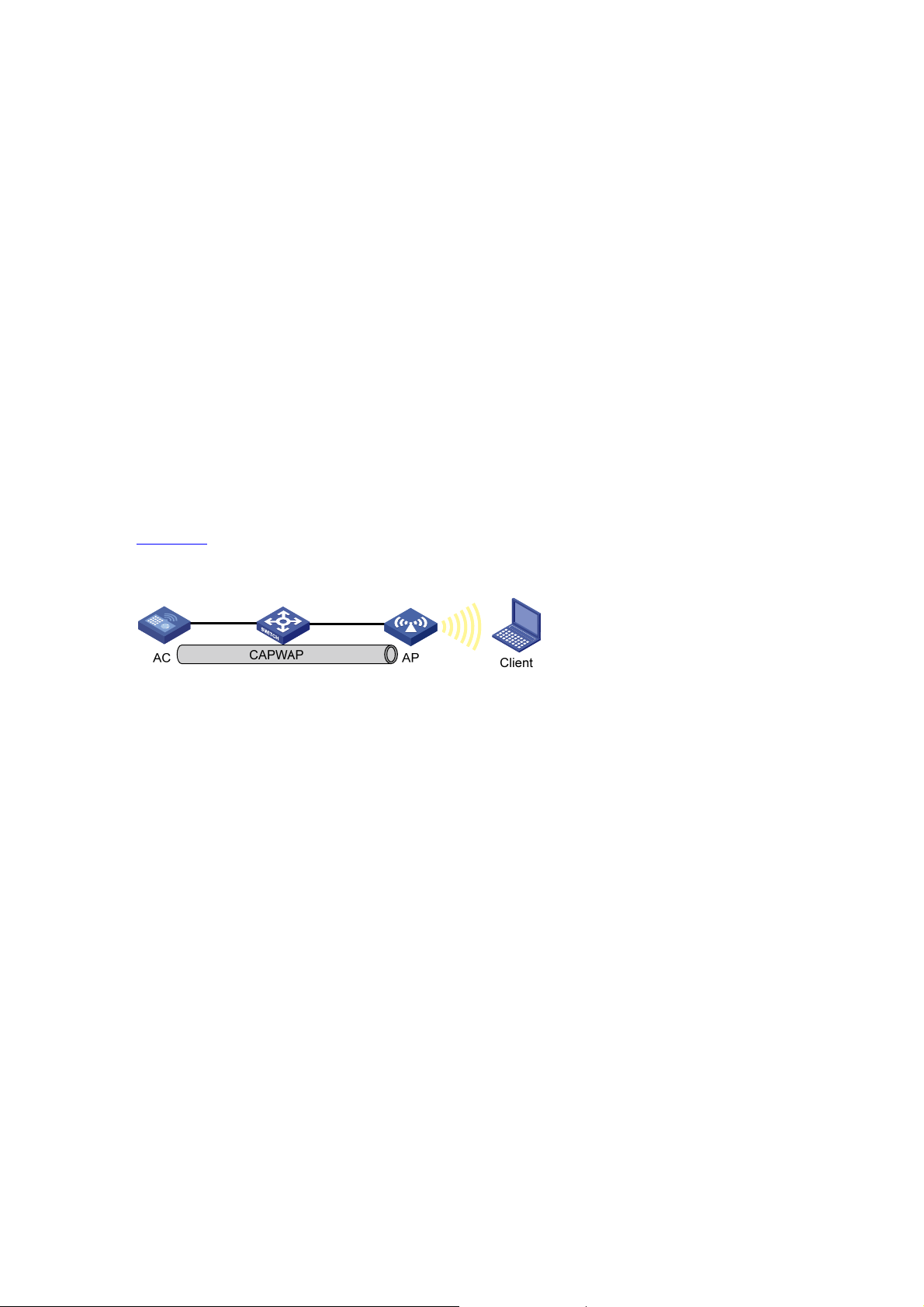
Active scanning is used by clients to scan surrounding wireless net wo rks an d locate a com p ati ble one.
Active scanning falls into two modes according to whether a specified SSID is carried in a probe
request.
z A client sends a probe request (with the SSID null): The client prepares a list of channels and
broadcasts a probe request frame on each of them. APs that receive the probe request send a
probe response. The client associates with the AP with the strongest signal. This active scanning
mode enables a client to know whether an AP can provide wireless services.
Figure 1-2 Active scanning (the SSID of the probe request is nul
AP 1
t
s
e
u
eq
R
e
Client
b
o
Pr
SS
(
Pr
(
SSI
Pr
o
b
e
)
l
ul
n
=
D
I
o
b
e
R
e
qu
e
s
t
D
=
n
u
l
l
es
)
p
on
s
e
R
AP 2
l)
z A client sends a probe request (with a specified SSID): In this case, the client only unicasts a probe
request because the probe request it sends carries the specified SSID. When an AP receives the
probe request, it sends a probe response. This active scanning mo de enable s a client to acce ss a
specified wireless network.
Figure 1-3 Active scanning (the probe request carries the specified SSID)
2) Passive scanning
Passive scanning is used by clients to discover surrounding wireless networks through listening to the
beacon frames periodically sent by an AP. The client prepares a list of channels and list ens to beacons
on each of these channels. In this case, the AP needs to peri odically broadcast beacon frames. Passive
scanning is used by a client when it wants to save battery power. Typically, VoIP clients adopt the
passive scanning mode.
1-3
Page 5

Authentication
To prevent illegal clients from accessing a network, authentication is needed between clients and ACs
or between clients and fat APs. There are two types of authentication:
z Open system authentication
z Shared key authentication
For details about the two types of authentication, refer to WLAN Security Configuration in the WLAN
Volume.
g Figure 1-4 Passive scannin
Association
A client that wants to access a wireless network via an AP must be associated with that AP. Once the
client chooses a compatible network with a specified SSID and authenticates to an AP, it sends an
association request frame to the AP. The AP sends an association response to the client and adds the
client’s information in its database. At a time, a client can associate with only one AP. An association
process is always initiated by the client, but not by the AP.
Other related frames
1) De-authentication
An AC or a fat AP sends a de-authentication frame to remove a client from the wireless system.
De-authentication can occur due to many reasons, such as:
z Receiving an association/disassociation frame from a client which is unauthenticated.
z Receiving a data frame from a client which is unauthenticated.
z Receiving a PS-poll frame from a client which is unauthenticated.
z The validity timer for a client expires and the port is not secured.
2) Dissociation
A client sends a dissociation frame to an AP to end the association between them. Dissociation can
occur due to many reasons, such as:
z Receiving a data frame from a client which is authenticated and unassociated.
z Receiving a PS-Poll frame from a client which is authenticated and unassociated.
A dissociation frame is either unicast or broadcast.
3) Re-association
When a client is roaming from one AP to another AP, it sends a re-association request to the new AP.
The AP relays this re-asso ciation request to the AC. The AC then informs the previous AP to delete the
client’s information from its datab ase, informs the ne w AP to add the client’s information in its d atabase
and conveys successful re-association information to the client.
1-4
Page 6
When a client leaves the coverage of an AP, and then needs to re-join the AP, it must re-associate with
the AP.
802.11 Overview
The WLAN-MAC primarily includes the implementation of IEEE 802.11 MAC layer functionality. Various
modes of MAC are:
z Local-MAC Architecture
z Split-MAC Architecture
In local-MAC architecture, most WLAN services are provided by the AP only. Currently, local-MAC
architecture is not supported.
In split-MAC architecture, the AP and the AC manage different services.
CAPWAP Overview
Introduction to CAPWAP
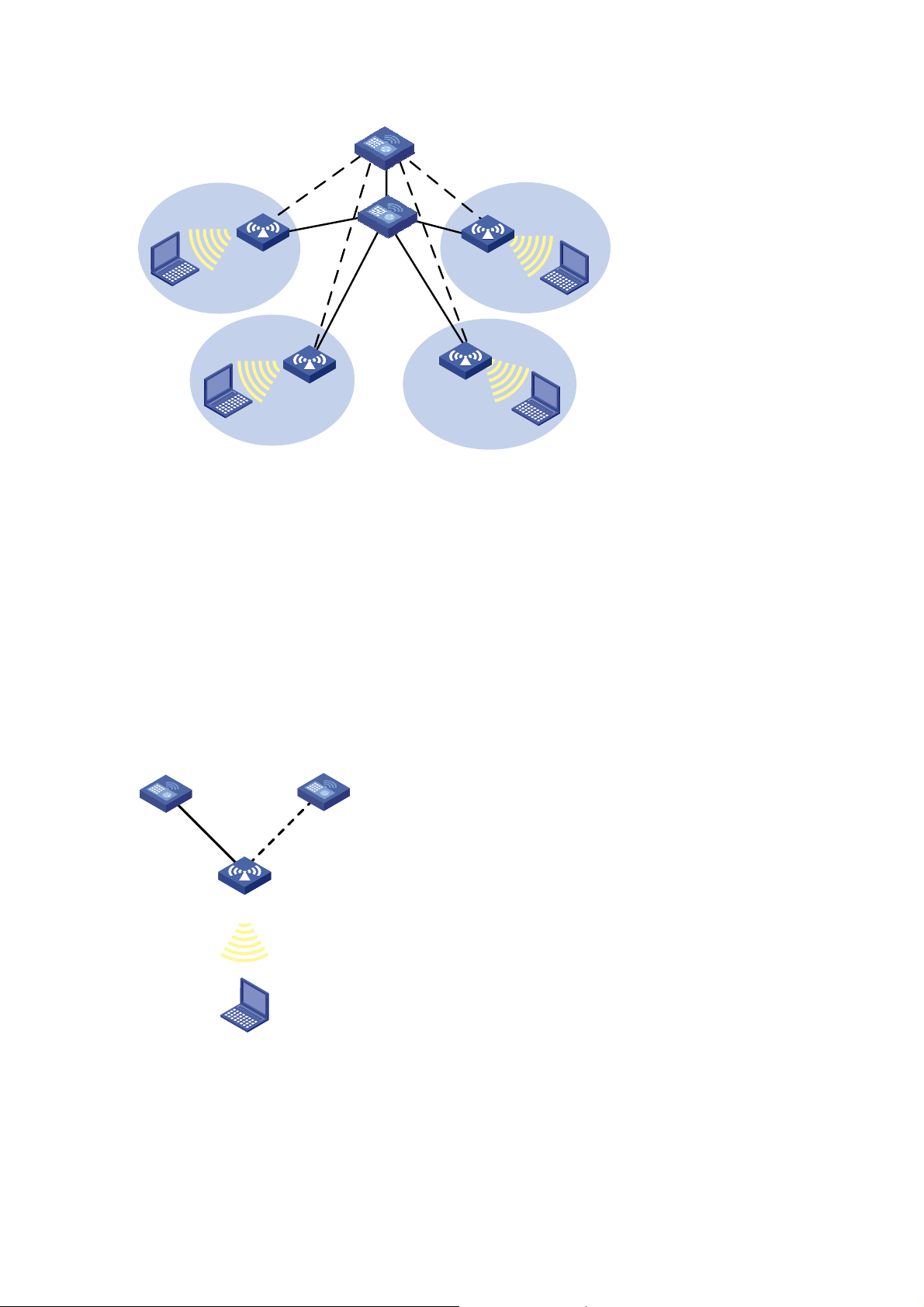
Control And Provisioning of Wireless A ccess Points (CAPWAP) defines how an AP communicates with
an AC. It provides a generic encapsulati on and transport mechani sm between AP and AC, as shown in
Figure 1-5.
Figure 1-5 CAPWAP
CAPWAP runs on an AP and an AC to provide a secured connectio n in between. It is built on a standard
client/server model and employs UDP.
On an AP, CAPWAP provides a data tunnel to encapsulate data packets to be sent to the AC. These
packets can be raw 802.11 packets or 802.11 to 802.3 translated packets. On an AC, CAPWAP
provides a control tunnel to support remote AP config uration and m anagement, and WLA N and mobile
management.
With CAPWAP, the AC can dynamically configure an AP based on the information provided by the
administrator.
CAPWAP supports both IPv4 and IPv6.
CAPWAP Link Backup
Dual link establishment
To achieve AC backup, an AP can establish two tunnels with two ACs that must have the same AP
configurations. Only the AC which works in master mode provides services to all the APs in the network
and the slave AC acts as the backup AC. If the master AC fails, APs should quickly use the services
provided by the slave AC. A heartbeat mechanism is used between these two ACs, which ensures that
failure of the master will be detected quickly by the backup AC.
1-5
Page 7
y Figure 1-6 LWAPP dual link topolog
AC 2
AP 1
AC 1
AP 2
AP 4
AP 3
In the above figure, AC1 is working in mast er mode and providing services to AP1, AP2, AP3 and AP4.
AC2 is working in slave mode. A Ps are connected to AC2 t hrough LW APP slave tunnels. AC1 and AC2
can be configured as backup for each other and should start master/slave detection. Whe n AC2 detects
AC1 is down, AC2 will convert the work mode from slave to master . All APs which are connected to AC2
through slave tunnels will transform the tunnels to master tunnels and use AC2 as the master AC. Once
AC 1 is reachable again, it will remain the backup.
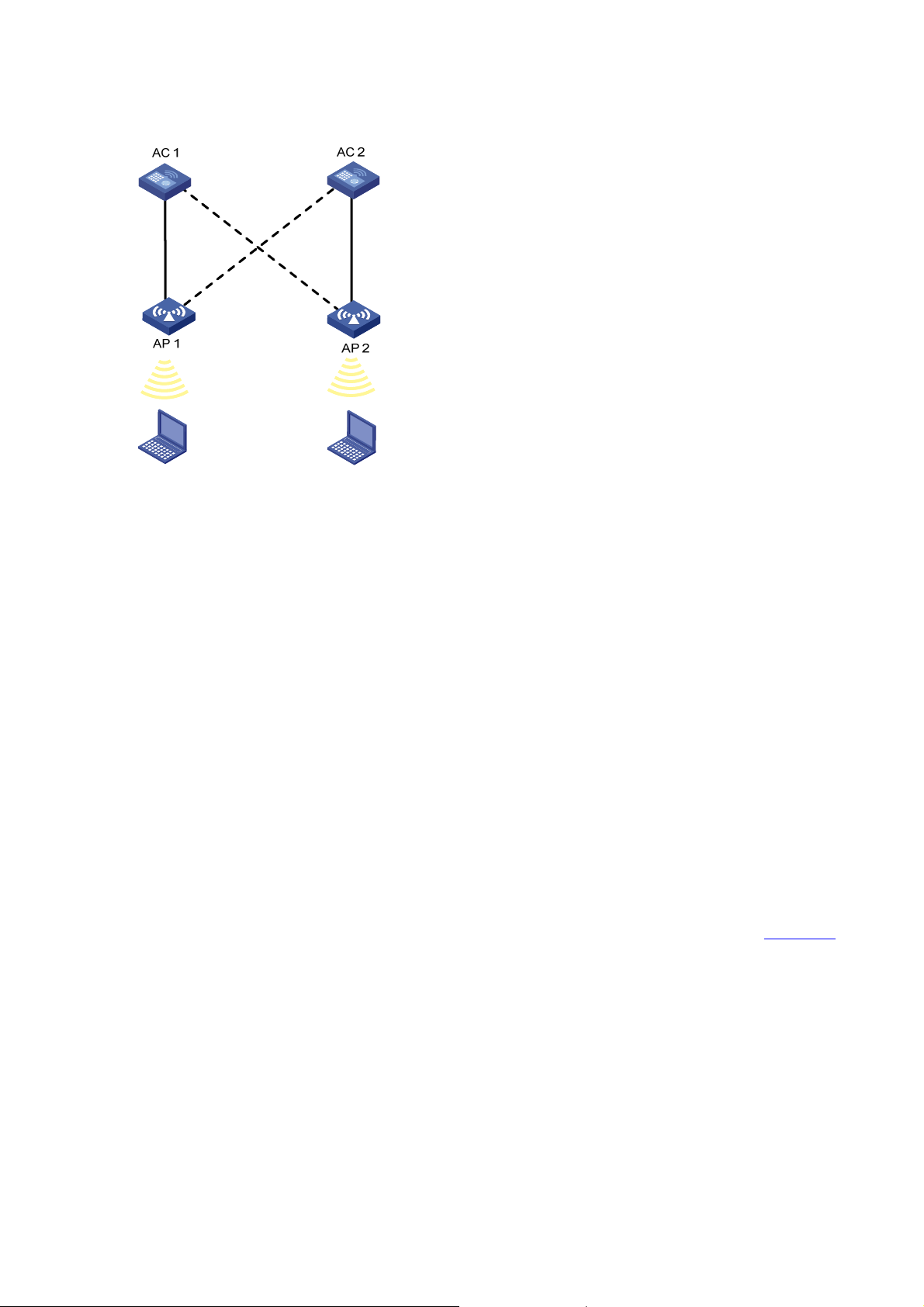
Primary AC recovery
Figure 1-7 Primary AC recovery
Primary AC
AC 1
AP
AC 2
In the above figure, AC 1 acting as the primary AC is the master (which ha s the connection priority of 7),
and it establishes a CAPWAP connection with the AP; AC 2 acts as the slave AC. If AC 1 goes down,
AC 2 will act as the master until recovery of the CAPWAP. This means once AC 1 is reachable again,
the AP will establish a connection with AC 1 acting as the primary AC and disconnect from AC 2.
1-6
Page 8
Dual work mode
Figure 1-8 Dual work mod
e
Dual work mode indicates that an AC can provide both mast er and slave connect ions. An AC will act as
the master for some APs and a ct as the slave for so me other APs. In the above scenario, AC 1 acts as
the master for AP 1 and slave for AP 2. Similarly, AC 2 acts as the master for AP 2 and slave for AP 1.
WLAN Topologies
WLAN Topologies for ACs
WLAN topologies for ACs consist of:
z Single BSS
z Multi-ESS
z VLAN-based WLAN
z Centralized WLAN
Single BSS
The coverage of an AP is called a basic service set (BSS). Each BSS is identified by a BSSID. The most
basic WLAN network can be established with only one BSS. All wireless cli ents associate with the same
BSS. If these clients have the same authorization, they can communicate with each other.
shows a single-BSS WLAN.
Figure 1-9
1-7
Page 9
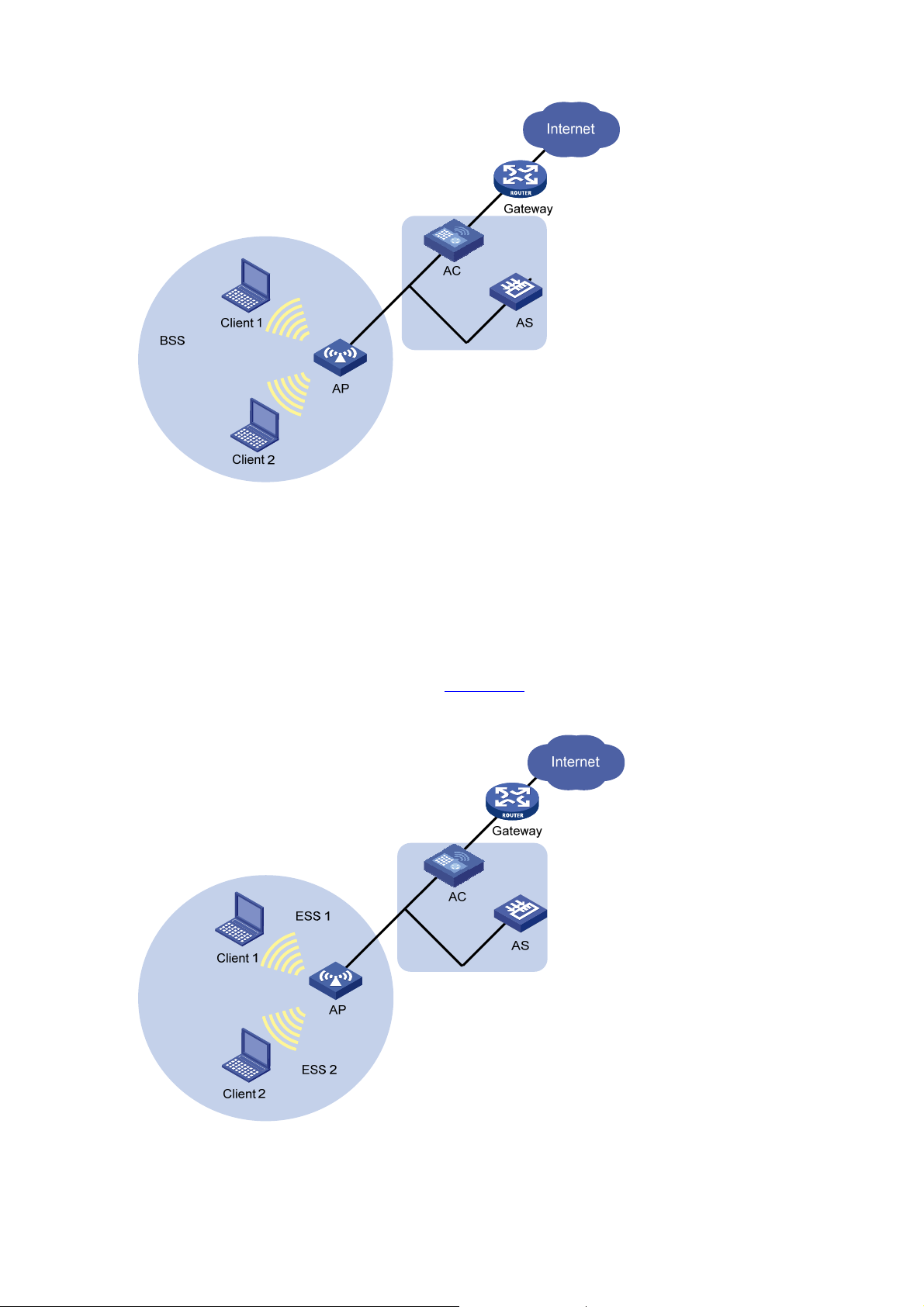
k Figure 1-9 Single BSS networ
The clients can communicate with each other and reach a host in the Internet. Communications
between clients within the same BSS are carried out through the AP and the AC.
Muti-ESS
All the clients under the same logical administration form an extended service set (ESS). This
multi-ESS topology describes a scenario where more than one ESS exists. When a mobile client joins
the AP, it can join one of the available ESSs.
Figure 1-10 shows a multi-ESS network.
Figure 1-10 Multi-ESS network
1-8
Page 10
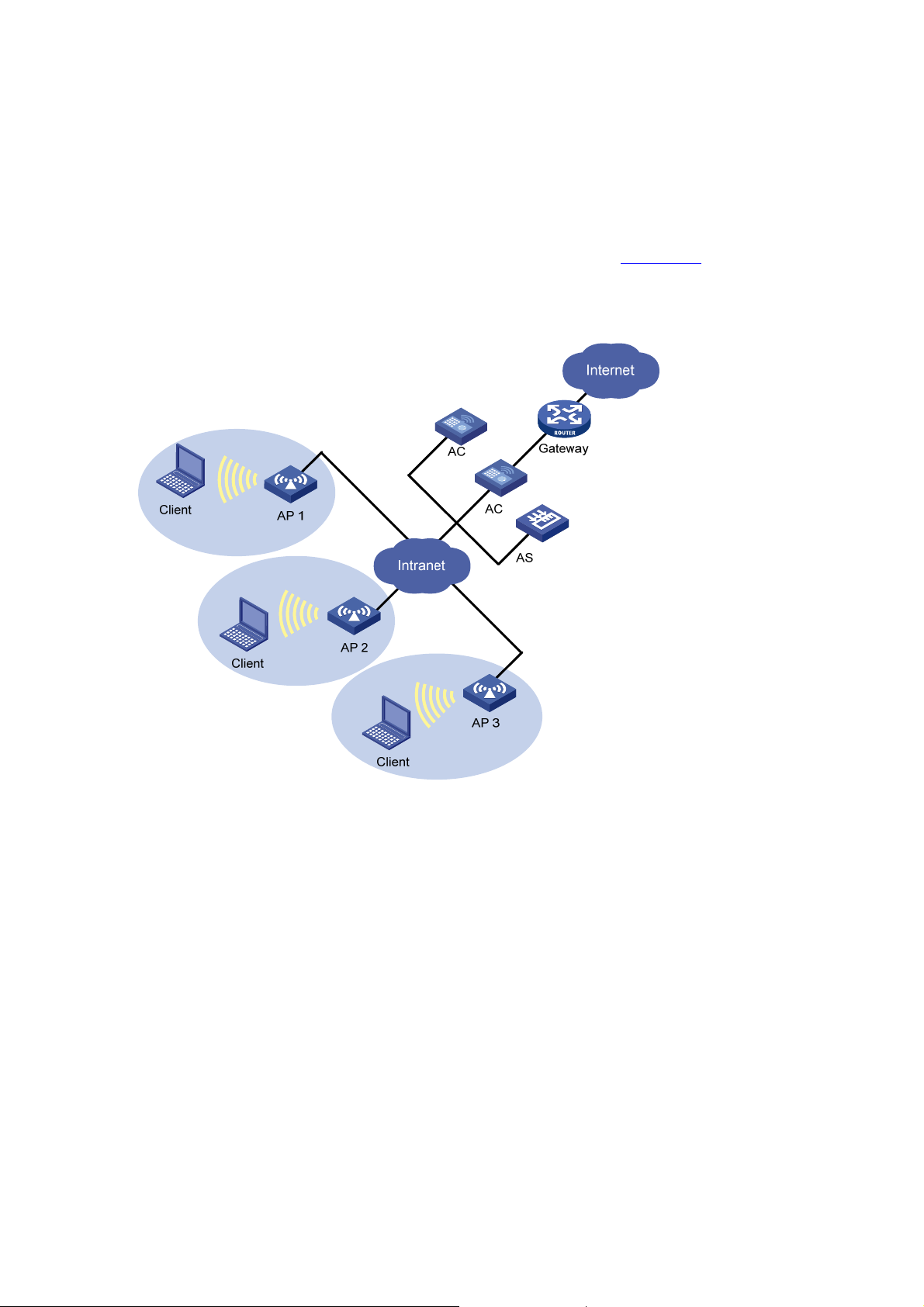
Generally, an AP can provide more than one ESS at the same time. The configuration of ESS is
distributed mainly from AC to AP, and the AP can broadcast the current information of ESS by beacon or
probe response frames. Clients can select an ESS it is interested to join.
Different ESS domains can be configured on the AC. The AC can be configured to allow associated
APs to accept clients in these ESS domains once their credentials are accepted.
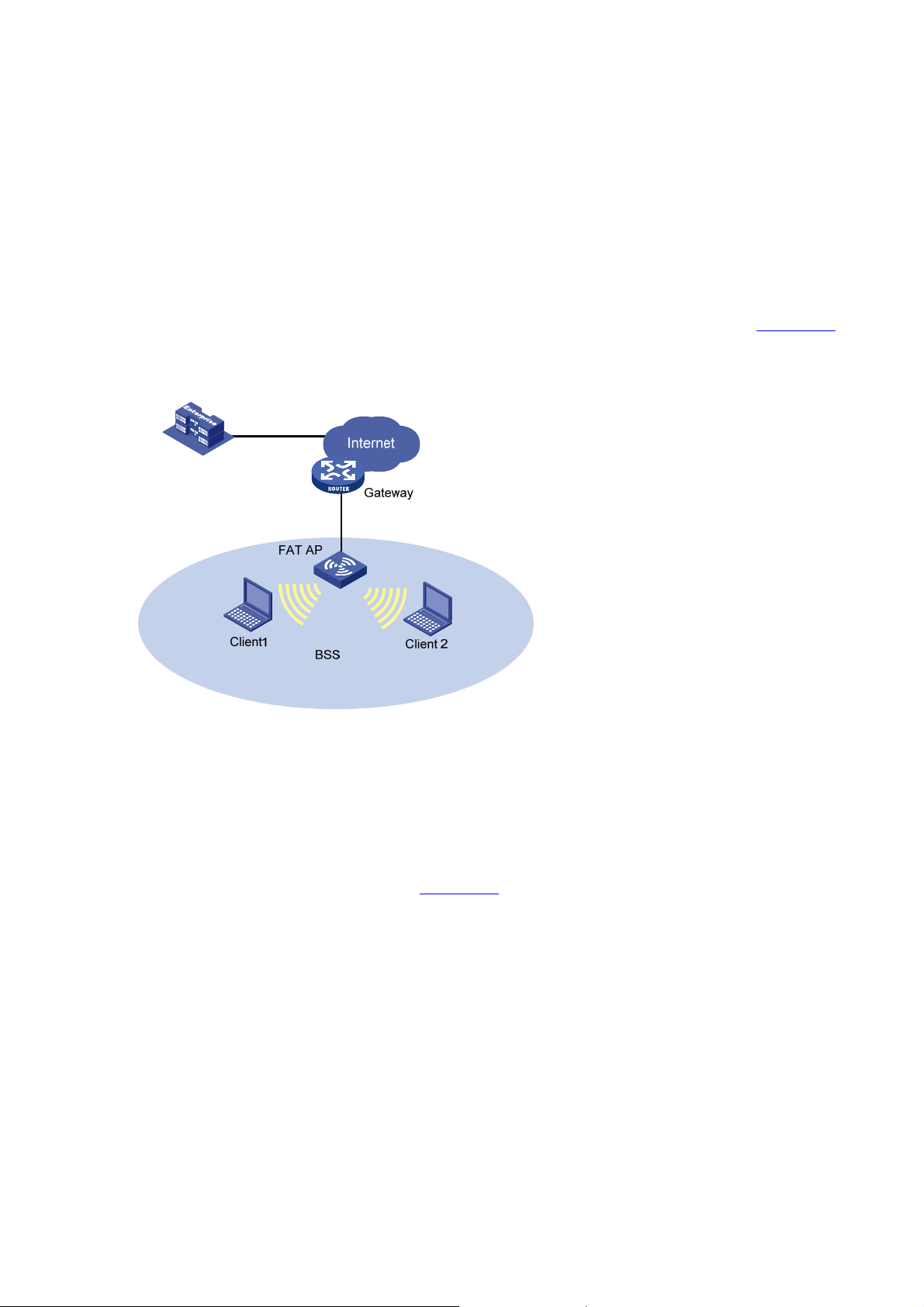
Centralized WLAN
Centralized WLAN is a unified solution for wireless local area n etworks. Figure 1-1 1 shows a centralized
WLAN network.
Figure 1-11 Centralized WLAN network
In this network, there are two ACs and three APs. An AP can connect with an AC directly, or over a
Layer 2 or Layer 3 network. The other AC serves as the backup.
During initialization, an AP obtains its basic network configuration parameters, such as its own IP
address, gateway address, domain name and DNS server address from a DHCP server.
An AP uses a discovery mechanism to locate the AC. For example, using the unicast discovery
mechanism, the AP can request the DNS server to provide the IP address of the AC.
The following describes a basic communication process in the centralized WLAN network.
1) A client gets associated with an AP in the network.
2) The AP communicates with the AC for authenticating the client’s credential.
3) The AC contacts the authentication server to authenticate the client.
4) Once the wireless client passes authentication, it can access authorized WLAN services and
communicate with other wireless clients or wired devices.
1-9
Page 11
WLAN Topologies for Fat APs
WLAN topologies for fat APs consist of:
z Single BSS
z Multi-ESS
z Single ESS Multi-BSS
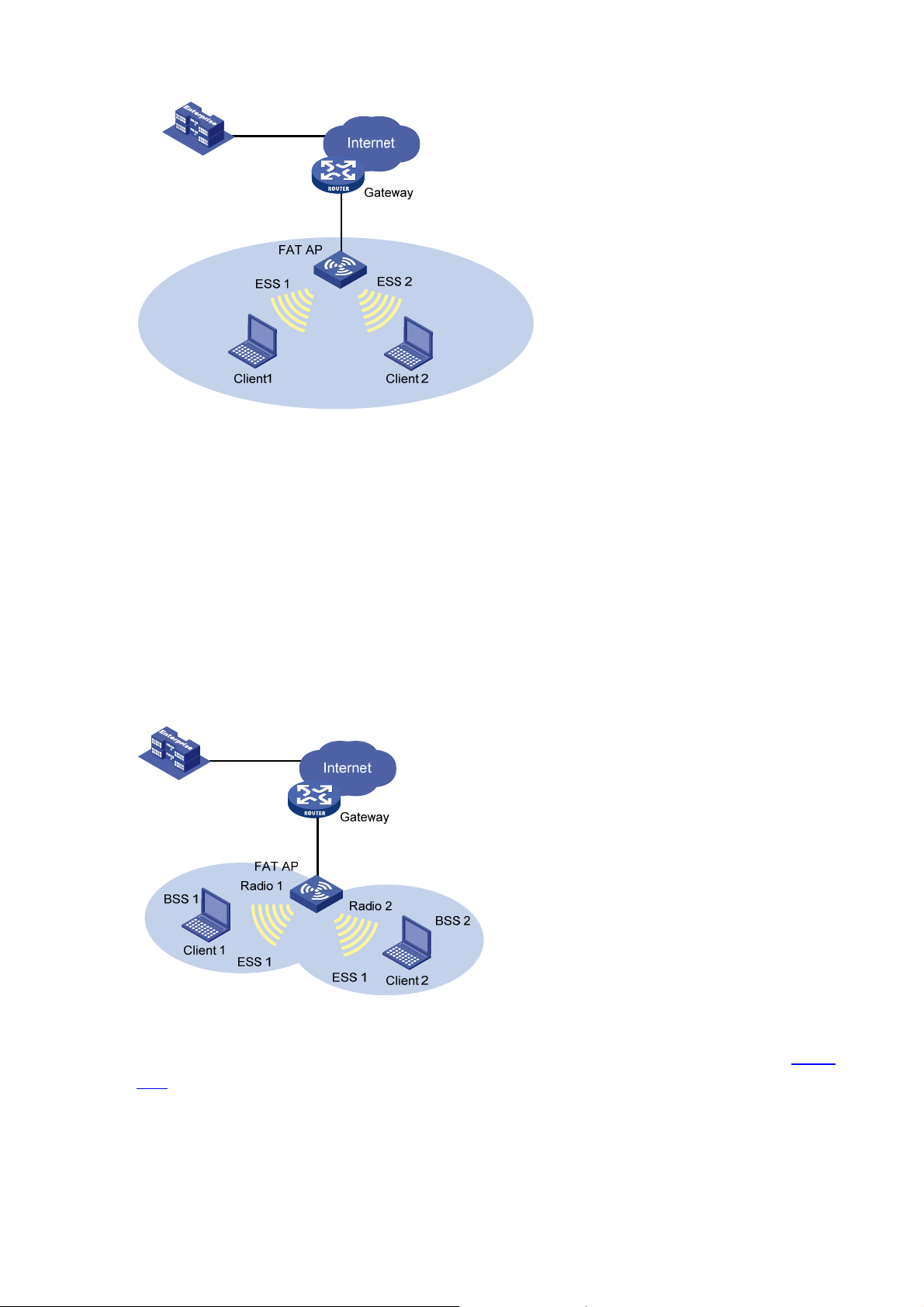
Single BSS
The coverage of an AP is called a basic service set (BSS). Each BSS is identified by a BSSID. The most
basic WLAN network can be established with only one BSS. All wireless cli ents associate with the same
BSS. If these clients have the same authorization, they can communicate with each other.
shows a single BSS network.
Figure 1-12 Single BSS network
Figure 1-12
The clients can communicate with each other or reach a host in the Internet. Communi cations between
clients within the same BSS are carried out through the fat AP.
Muti-ESS
This topology describes a scenario where more than one ESS exists. When a mobile client joins the fat
AP, it can join one of the available ESSs.
Figure 1-13 shows a multi-ESS network.
1-10
Page 12
k Figure 1-13 Multi-ESS networ
Generally a fat AP can provide more than one logical ESS at the same time. The fat AP can br oadcast
the current information of ESS by beacon or probe response frames. Clients can select an ESS it is
interested to join.
Different ESS domains can be configured on the fat AP. The fat AP can be configured to accept cl ients
in these ESS domains once their credentials are acceptable.
Single ESS Muti-BSS (The multi-radio case)
This topology describes a scenario where a fat AP has two radios that are in the same ESS but belong
to different BSSs.
Figure 1-14 Single ESS Multiple BSS network
This network scenario can be used when both 802.11a and 802.11b/g need to be supported.
1-14 shows two clients connected to different radios belong to the same ESS but different BSSs.
Protocols and Standards
z ANSI/IEEE Std 802.11, 1999 Edition
z IEEE Std 802.11a
Figure
1-11
Page 13

z IEEE Std 802.11b
z IEEE Std 802.11g
z IEEE Std 802.11i
z IEEE Std 802.11-2004
Configuring WLAN Service
Configuration Task List
Task Description
Enabling WLAN Service (only supported on ACs) Required
Configuring Global WLAN Parameters (only supported on fat
APs)
Specifying the uplink interface (only supported on fat APs) Optional
Specifying a Country Code Required
Configuring Software Version Automatic Update Optional
Configuring a WLAN Service Template Required
Configuring an AP (only supported on ACs) Required
Configuring Auto AP Optional
Configuring CAPWAP Dual-Link (Supported only on ACs) Optional
Configuring the Radio of an AP Required
Configuring a Radio Policy on an AC or the Radio of a Fat AP Required
Configuring 802.11n Optional
Enabling WLAN Service (only supported on ACs)
WLAN service is a component of the Comware platform, and can be enabled or disabled at runtime.
Optional
Follow these steps to enable WLAN service:
To do… Use the command… Remarks
Enter system view
system-view
—
By default, WLAN service is
Enable WLAN service
wlan enable
enabled and “WLAN service
enabled” is displayed.
Configuring Global WLAN Parameters (only supported on fat APs)
Follow these steps to configure global WLAN parameters:
To do… Use the command… Remarks
Enter system view
system-view
1-12
—
Page 14

To do… Use the command… Remarks
Configure the client idle
timeout interval for the fat AP
Configure the keep alive
interval for the fat AP
Enable the fat AP to respond
to broadcast probe requests
wlan client idle-timeout
interval
wlan client keep-alive interval
wlan broadcast–probe reply
Specifying the uplink interface (only supported on fat APs)
A fat AP is used to set up the connectio n between a station and the wired network. Therefore, the fat AP
should have one interface connected to the wired network. This interface is called the uplink interface of
the fat AP, as shown in
Figure 1-15 Uplink interface of the fat AP
Figure 1-15.
Optional
By default, the idle timeout
interval is 3600 seconds.
Optional
By default, keep–alive function
is disabled.
Optional
Enabled by default.
If clients want to access the wired network through the fat AP, the interface of the fat AP that connects to
the wired network should be specified as the uplink interface, so that WLAN services will be provided as
long as the uplink interface is up.
Following these steps to specify the uplink interface of the fat AP:
To do… Use the command… Remarks
Enter system view
system-view
1-13
—
Page 15

To do… Use the command… Remarks
Specify the uplink interface
Specifying a Country Code
A country code identifies the country in which you want to operate radios. It determines characteristics
such as operating power level and total number of channels available for the transmission of frames.
You must set the valid country code or area code before configuring an AP.
Follow these steps to specify the country code:
To do… Use the command… Remarks
Enter system view
Specify the country code
wlan uplink-interface
interface-type
interface-number
system-view
wlan country-code
code
Optional
By default, no interface is
configured as an uplink
interface.
—
By default, the country code is
CN.
For information about country codes, refer to WLAN Services Command in the WLAN Volume.
Configuring Software Version Automatic Update
A fit AP is a zero-configuration device. It can automatically discover an AC after power-on. To ensure
that a fit AP can associate with an AC, their software versions must be consistent by default, which
complicates maintenance. This task allows you designate the software version of an AP on the AC, so
that they can associate with each other even if their software versions are inconsistent.
Follow these steps to configure software version automatic update:
To do… Use the command… Remarks
Enter system view
Designate the software version
of a given AP model with a
given hardware version
system-view
wlan apdb model-name
hardware-version
software-version
—
Optional
By default, the software version
will be the value initialized by
the driver, namely, the software
versions of the fit AP and the
AC should be consistent.
Configuring a WLAN Service Template
A WLAN service template includes attributes such as SSID, WLAN-ESS interface binding,
authentication method (open-system or shared key) information. A service template can be of clear or
1-14
Page 16

crypto type. If a clear type service template exist s, you cannot change it to crypto. To do so, you must
delete the clear type service template, and configure a new service template with type as crypto.
Follow these steps to configure a service template:
To do… Use the command… Remarks
Enter system view
Create a WLAN-ESS interface
Exit interface view
Create a WLAN service
template and enter WLAN
service template view
Specify the service set
identifier
Disable the advertising of
SSID in beacon frames
Bind the WLAN-ESS interface
to the service template
system-view
interface wlan-ess
interface-index
quit
wlan service-template
service-template-number { clear |
crypto }
ssid
ssid-name
beacon ssid-hide
bind wlan-ess
interface-index
—
—
Support for this command
depends on the device model.
This command is only
supported on ACs.
—
Required
No WLAN service template is
created by default.
Required
By default, no SSID is set.
Optional
By default the SSID is
advertised in beacon frames.
Note that hiding the SSID
does very little to increase
security.
Required
By default, no interface is
bound to the service template.
Support for this command
depends on the device model.
This command is only
supported on ACs.
Enable local forwarding
Specify an authentication
method
Specify the maximum
associated clients per BSS
Enable the service template
client forwarding-mode local
[ vlan vlan-id-list ]
authentication-method { open
system | shared key }
client max-count
max-number
service-template enable
Optional
Remote forwarding is enabled
by default.
This command is only
supported on ACs.
Required
For related configuration
about the shared key, refer to
WLAN Security in the WLAN
Volume.
Optional
64 by default.
Required
Disabled by default.
1-15
Page 17

Configuring an AP (only supported on ACs)
Access Points are used to setup connections between the AC and stations. An AP uses radio signals to
communicate with wireless clients and uses an uplink interface to conne ct to the wired network.
Follow these steps to configure an AP on the AC:
To do… Use the command… Remarks
Enter system view
Specify the AP name and
its model number and
enter AP template view
Configure a description for
the AP
Configure the echo
interval for the AP
Set the CIR for packets
sent from AC to AP
Configure the jumbo
frame threshold
Enable the AP to respond
to broadcast probe
requests
Specify the client idle
timeout interval
system-view
wlan a p
description
echo-interval
ap-name model model-name
description-string
interval
cir committed-information-rate [ cbs
committed-burst-size ]
jumboframe enable
value
broadcast-probe reply
client idle-timeout
interval
—
The model number needs to
be specified only during new
AP template creation.
Optional
By default, the echo interval is
10 seconds.
Optional
By default, no CIR is set for
an AP.
By default, the jumbo frame
functionality is disabled.
Optional
By default, an AP only
responds to unicast probe
request frames (frames with
SSID).
Optional
By default, the client idle
timeout is 3600 seconds.
If no data is received from an
associated client within the
interval, the AP will remove it
from the network.
Optional
Specify the client keep
alive interval
client keep-alive
interval
By default, the client
keep-alive function is
disabled.
Configure the priority for
the AP to connect to the
AC
Exit AP template view
priority level priority
quit
Optional
The default is 4.
—
Optional
Configure the discovery
policy type as unicast
wlan lwapp discovery-policy
unicast
By default, the AC receives
broadcast discovery
messages.
Enable/disable WLAN
radios
wlan radio { disable | enable }
{ radio-policy radio-policy-nam e | all |
dot11a | dot11b | dot11g }
Required
By default, no WLAN radio is
enabled.
1-16
Page 18

Configuring Auto AP
The auto AP feature allows an AP to automatically connect to an AC. When you deploy a wireless
network with many APs, the auto AP function avoids configuration of many AP serial IDs, thus
simplifying configuration.
Follow these steps to configure auto AP:
To do… Use the command… Remarks
Enter system view
Enable the auto-AP function
Enter AP template view
Set auto-AP serial ID
Exit AP template view
Convert auto AP into
configured AP
system-view
wlan auto-ap enable
wlan ap ap-name model
model-name
serial-id auto
quit
wlan auto-ap persistent
{ name auto-ap-name
[ new-ap-name ] | all }
Configuring CAPWAP Dual-Link (Supported only on ACs)
Follow these steps to configure CAPWAP dual-link:
To do… Use the command… Remarks
Enter system view
system-view
—
Optional
Enabled by default.
The model number of the AP is
specified only if an AP template
is created
Required
—
Optional
—
Specify the address of the
backup AC
Enter AP template view
Specify the AP connection
priority for the AC
wlan backup-ac { ip ipv4-address |
ipv6 ipv6-address }
wlan a p ap-name model model-name
priority level priority
Required.
By default, no backup AC
address exists.
The model number needs to
be specified only during new
AP template creation.
Optional
By default, the AP connection
priority of the AC is 4.
If an AC has an AP
connection priority of 7, the
AC becomes the primary AC.
When the primary AC fails
and then recovers, it will
re-establish connections with
APs and become the master
AP.
1-17
Page 19

You must ensure that the two ACs have the same AP configurations. Otherwise, a switchover between
master and slave ACs will fail.
Configuring the Radio of an AP
Follow these steps to configure the radio of an AP (on an AC):
To do… Use the command… Remarks
Enter system view
Enter AP template view
Specify a radio type for the
radio and enter radio view
Map a service template to the
current radio
Specify a channel number for
the radio
Specify the maximum radio
power
system-view
wlan ap ap-name model
model-number
radio radio-number [ type
{ dot11a | dot11b | dot11g } ]
service-template
service-template-number
channel { channel-number |
auto }
max-power max-power
Specify the type of preamble preamble { long | short }
—
—
Required
The default varies by device.
WLAN supports customizing
the default radio type for AP
models.
Required
Optional.
By default, auto mode is
enabled.
Optional.
By default, the maximum radio
power varies with radio types
and country codes
Optional.
By default, the short preamble
is supported.
Note that this command does
not apply to 802.11a radios.
Enable Adaptive Noise
Immunity (ANI) function
ani enable
Optional.
By default, ANI is enabled.
Optional.
By default, the default_rp
Bind a radio policy to the
current radio
radio-policy radio-policy-name
radio policy is bound to a
radio.
The radio policy must have
been configured with the wlan
radio-policy command.
Enable the radio
radio enable
Required
Follow these steps to configure the radio of a fat AP:
1-18
Page 20

To do… Use the command… Remarks
Enter system view
Enter radio interface view
Specify a radio type for the
radio
Bind a service template to a
WLAN-ESS interface for the
radio
Specify a channel number for
the radio
Specify the maximum radio
power
system-view
interface wlan-radio
interface-number
radio-type { dot11b | dot11g |
dot11a }
service-template
service-template-number
interface wlan-bss
interface-number
channel { channel-number |
auto }
max-power max-power
Specify the type of preamble preamble { long | short }
—
—
Required
The default radio type
depends on the device model.
Required
Optional
By default, auto mode is
enabled.
Optional
By default, the maximum radio
power varies with radio types
and country codes.
Optional.
By default, the short preamble
is supported.
Note that this command does
not apply to 802.11a radios.
Configuring a Radio Policy on an AC or the Radio of a Fat AP
Follow these steps to configure a radio policy on an AC or the radio of a fat AP:
To do… Use the command… Remarks
Enter system view
Create a
radio policy
and enter
Enter radio
policy view or
radio view
radio policy
view (on an
AC)
Enter radio
view (on a fat
AP)
Set the interval for sending
beacon frames
Set the number of beacon
intervals between DTIM
frames
system-view
wlan radio-policy
policy-name
interface wlan-radio
radio-number
beacon-interval
interval
dtim counter
—
—
Optional
By default, the beacon interval
is 100 time units (TUs).
Optional
By default, the DTIM counter
is 1.
Specify the maximum length
of packets that can be
transmitted without
fragment-threshold
size
fragmentation
1-19
Optional
By default, the fragment
threshold is 2346 bytes.
Page 21

To do… Use the command… Remarks
Specify the request to send
(RTS) threshold length
Set the maximum number of
retransmission attempts for
frames larger than the RTS
threshold
Specify the maximum number
of attempts to transmit a frame
shorter than the RTS
threshold
Specify the interval for the AP
to hold received packets
Specify the maximum number
of associated clients
rts-threshold
long-retry threshold
short-retry threshold
max-rx-duration
size
count
count
interval
client max-count max-number
Optional
By default, the RTS threshold
is 2346 bytes.
Optional
By default, the long retry
threshold is 4.
Optional
By default, the short retry
threshold is 7.
Optional
By default, the interval is 2000
milliseconds.
Optional
The default depends on the
device model.
This command is only
supported on ACs.
Configuring 802.11n
As the next generation wireless LAN technology, 802.11n supports both 2.4GHz and 5GHz bands. It
provides higher-speed services to customers by using the following two methods:
1) Increasing bandwidth: 802.11n can bond two adjacent 20-MHz channels together to form a
40-MHz channel. During data forwarding, the two 20-MHz channels can work separately with one
acting as the primary channel and the other acting as the se condary channel o r work together as a
40-MHz channel. This provides a simple way of doubling the data rate.
2) Improving channel utilization through the following ways:
z 802.11n introduces the A-MPDU frame format. By using only one PHY header, each A-MPDU can
accommodate multiple Message Protocol Data Units
removed. This reduces the overhead in transmission and the number of ACK frames to be used,
and thus improves network throughput.
z Similar with MPDU aggregation, multiple MAC Service Data Units (MSDU) can be aggregated into
a single A-MSDU. This reduces the MAC header overhead and thus improves MAC layer
forwarding efficiency.
z To improve physical layer performance, 802.11n introduces the short GI function, which shortens
the GI interval of 800 us in 802.11a/g to 400 us. This can increase the data rate by 10 percent.
Follow these steps to configure 802.11n:
(MPDUs) which have their PHY headers
To do… Use the command… Remarks
Enter system view
Enter AP template view
Enter radio view
system-view
wlan ap ap-name model
model-name
radio radio-number type
{ dot11an | dot11gn }
1-20
—
—
—
Page 22

To do… Use the command… Remarks
Specify the bandwidth mode
for the radio
Enable access permission for
802.11n clients only
Enable the short GI function
Enable the A-MSDU function
Enable the A-MPDU function
Enable the radio
channel band-width { 20 | 40 }
client dot11n-only
short-gi enable
a-msdu enable
a-mpdu enable
radio enable
Optional
By default, the radio operates
in 20 MHz mode.
Optional
By default, an 802.11a/n radio
permits both 802.11a and
802.11n clients to access, and
an 802.11g/n radio permits
both 802.11g and 802.11n
clients to access.
Optional
Enabled by default.
Optional
Enabled by default.
Optional
Enabled by default.
Required
Disabled by default.
Before enabling the radio, you
must configure the Modulation
and Coding Scheme (MCS).
For mandatory and supported
802.11n rates, refer to WLAN
RRM Configuration in the
WLAN Volume.
For information about Modulation and Coding Scheme (MCS) index and mandatory and supported
802.11n rates, refer to WLAN RRM Configuration in the WLAN Volume.
Displaying and Maintaining WLAN Service
On an AC
To do… Use the command… Remarks
Display AP information
Display the model information
of a specified AP or all APs
supported on the AC
Display the reboot log
information of an AP
display wlan ap { all | name
[ verbose ]
display wlan ap-model { all | name
ap-name }
display wlan ap reboot-log name
ap-name
ap-name }
Available in any view
Available in any view
Available in any view
Display WLAN radio policy
information
display wlan radio-policy
[ radio-policy-name ]
1-21
Available in any view
Page 23

To do… Use the command… Remarks
Display WLAN service template
information
Display WLAN statistics
Display WLAN client
information
Reset AP connection(s) reset wlan ap { all | name ap-name } Available in user view
Clear WLAN AP reboot logs
Clear WLAN statistics
Cut off WLAN client(s)
display wlan service-template
[ service-template-number ]
display wlan statistics { client [ all |
mac-address mac-address ] | radio
[ ap-name ] }
display wlan client { ap ap-name
[ radio radio-number ] | mac-address
mac-address | service-template
service-template-number } [ verbose ]
reset wlan ap reboot-log { all | name
ap-name }
reset wlan statistics { radio [ ap-name ]
| client [ all | mac-address ] }
reset wlan client { all | mac-address
mac-address }
Available in any view
Available in any view.
Available in any view
Available in user view
Available in user view
Available in user view
On a fat AP
To do… Use the command… Remarks
display wlan client { interface
Display WLAN client
information
Display WLAN service template
information
Display WLAN client statistics
Cut off client(s)
Clear WLAN client statistics
wlan-radio [ wlan-radio-number ] |
mac-address mac-address |
service-template
service-template-number } [ verbose ]
display wlan service-template
[ service-template-number ]
display wlan statistics client { all |
mac-address mac-address }
reset wlan client { all | mac-address
mac-address }
reset wlan statistics client { all |
mac-address mac-address }
Configuring AP Group (only supported on ACs)
Some wireless service providers need to control the access p ositions of client s. For example, as sh own
in the figure below, to meet security or billing needs, it is require d to conne ct wireless client s 1, 2 and 3
to the wired network through APs 1, 2 and 3 respectively. To achieve this, you can configure an AP
group and then apply the AP group in a user profile.
Available in any view
Available in any view
Available in any view
Available in user view
Available in user view
1-22
Page 24

l Figure 1-16 Client access contro
RADIUS server
Internet
AC
Configuring an AP Group
Follow these steps to configure an AP group:
To do… Use the command… Remarks
Enter system view
Create an AP group and enter
AP group view
AP 1
AP 2
Client 3
system-view
wlan ap-group value
Client 1
Client 2
—
—
Add specified APs into the AP
group
Configure a description for the
AP group
ap template-name-list
description text
Applying the AP Group in a User Profile
Follow these steps to apply the AP group in a user profile:
To do… Use the command… Remarks
Enter system view
Enter user profile view
system-view
user-profile profile-name
Required
No AP is added by default.
You can use this command
repeatedly to add multiple
APs, or add up to 10 APs in
one command line.
A nonexistent AP can be
added.
Optional
Not configured by default.
—
Required
If the user profile does not
exist, you need to create it
first.
Apply the AP group in the user
profile
wlan permit-ap-group value
1-23
Required
No AP group is applied in the
user profile by default.
Page 25

To do… Use the command… Remarks
Return to system view
Enable the user profile
For more information about user profile, refer to User Profile Configuration in the System Volume.
quit
user-profile profile-name enable
Displaying and Maintaining AP Group
—
Required
Not enabled by default.
Note that:
The name of the user profile
must be identical to that of the
external group on the RADIUS
server.
To support roaming, all ACs in
a mobility group must have the
same profile name configured.
To do… Use the command… Remarks
Display AP group information
display wlan ap-group [ value
Configuring SSID-Based Access Control
When a user wants to access a WLAN temporarily, the administrator can specify a permitted SSID in
the corresponding user profile so that the user can access the WLAN only through the SSID.
Specifying a Permitted SSID in a User Profile
After completing the configuration, the user profile needs to be enabled to take ef fect.
Follow these steps to specify a permitted SSID:
To do… Use the command… Remarks
Enter system view
Enter user profile view
system-view
user-profile profile-name
]
—
Required
If the specified user profile does
not exist, this command will
create it and enter its view.
Available in any view
Required
Specify a permitted
SSID
Return to system view
wlan permit-ssid ssid-name
quit
1-24
No permitted SSID is specified
by default, that is, users can
access the WLAN without SSID
limitation.
—
Page 26

To do… Use the command… Remarks
Enable the user profile
user-profile profile-name enable
z For more information on user access control, refer to AAA Configuration in the Security Volume.
z For more information on user profile, refer to User Profile Configuration in the System Volume.
WLAN Service Configuration Examples
WLAN Service Configuration Example (On an AC)
Network requirements
As shown in the following figure, an AC is connected to an L2 switch. AP1 (serial ID SZ001) and AP2
(serial ID SZ002) are connected to the AC through the L2 switch. AP 1, AP2 and the AC are in the same
network. AP1 and AP2 get their IP address from the DHCP server.
Required
Not enabled by default.
It is required to configure basic WLAN service settings on the AC.
Figure 1-17 WLAN service configuration
Configuration procedure
# Enable WLAN service, which is enabled by default.
<AC> system-view
[AC] wlan enable
# Create the WLAN ESS interface.
<AC> system-view
[AC] interface WLAN-ESS 1
[AC-WLAN-ESS1] quit
# Define a WLAN service template and bind the WLAN-ESS interface to this service template.
1-25
Page 27

[AC] wlan service-template 1 clear
[AC-wlan-st-1] ssid abc
[AC-wlan-st-1] bind WLAN-ESS 1
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] client max-count 10
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Configure a radio policy (the default radio policy default-rp will be used if you don’t want to configure
a new radio policy for customizing related parameters).
[AC] wlan radio-policy radpolicy1
[AC-wlan-rp-radpolicy1] beacon-interval 200
[AC-wlan-rp-radpolicy1] dtim 4
[AC-wlan-rp-radpolicy1] rts-threshold 2300
[AC-wlan-rp-radpolicy1] fragment-threshold 2200
[AC-wlan-rp-radpolicy1] short-retry threshold 6
[AC-wlan-rp-radpolicy1] long-retry threshold 5
[AC-wlan-rp-radpolicy1] max-rx-duration 500
# Configure AP1 on the AC.
<AC> system-view
[AC] wlan ap ap1 model WA2100
[AC-wlan-ap-ap1] serial-id 210235A29G007C000020
[AC-wlan-ap-ap1] description L3Office
# Configure the radio of AP1, and bind service template 1 and radio policy radiopolicy1 to the radio.
[AC-wlan-ap-ap1] radio 1 type dot11a
[AC-wlan-ap-ap1-radio-1] channel 149
[AC-wlan-ap-ap1-radio-1] max-power 10
[AC-wlan-ap-ap1-radio-1] radio-policy radiopolicy1
[AC-wlan-ap-ap1-radio-1] service-template 1
[AC-wlan-ap-ap1-radio-1] quit
[AC-wlan-ap-ap1] quit
# Configure AP2 on the AC.
[AC] wlan ap ap2 model WA2100
[AC-wlan-ap-ap2] serial-id 210235A29G007C000021
[AC-wlan-ap-ap2] description L4Office
# Configure the radio of AP2, includin g binding radi o policy radiopolicy1 and service template 1 to the
radio.
[AC-wlan-ap-ap2] radio 1 type dot11a
[AC-wlan-ap-ap2-radio-1] channel 149
[AC-wlan-ap-ap2-radio-1] max-power 10
[AC-wlan-ap-ap2-radio-1] radio-policy radiopolicy1
[AC-wlan-ap-ap2-radio-1] service-template 1
[AC-wlan-ap-ap2-radio-1] quit
[AC-wlan-ap-ap2] quit
# Enable all radios.
1-26
Page 28

[AC] wlan radio enable all
WLAN Auto-AP Configuration Example (On an AC)
Network requirements
As shown in the following figure, an AC is connected to a Layer 2 switch. AP1 (serial ID SZ001) and
AP2 (serial ID SZ002) are connected to the AC through the L2 switch. AP1, AP2 and the AC are in the
same network. AP1 and AP2 get their IP address from the DHCP server. It is required to enable the
auto-AP function to enable APs to automatically connect to the AC.
Figure 1-18 WLAN service configuration
Configuration procedure
# Create a WLAN ESS interface.
<AC> system-view
[AC] interface WLAN-ESS 1
[AC-WLAN-ESS1] quit
# Define a WLAN service template and bind the WLAN-ESS interface to this service template.
[AC] wlan service-template 1 clear
[AC-wlan-st-1] ssid abc
[AC-wlan-st-1] bind WLAN-ESS 1
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Configure a radio policy (the default radio policy default_rp will be used if you don’t want to configure
a new radio policy for customizing related parameters).
[AC] wlan radio-policy radpolicy1
[AC-wlan-rp-radpolicy1] beacon-interval 200
[AC-wlan-rp-radpolicy1] dtim 4
[AC-wlan-rp-radpolicy1] rts-threshold 2300
[AC-wlan-rp-radpolicy1] fragment-threshold 2200
[AC-wlan-rp-radpolicy1] short-retry threshold 6
[AC-wlan-rp-radpolicy1] long-retry threshold 5
[AC-wlan-rp-radpolicy1] max-rx-duration 500
1-27
Page 29

[AC-wlan-rp-radpolicy1] quit
# Configure the AP auto configuration feature.
[AC] wlan auto-ap enable
# Configure a common AP for model WA2100 (For each AP model, one common auto AP configuration
is required).
[AC] wlan ap ap1 model WA2100
[AC-wlan-ap-ap1] serial-id auto
# Configure the radio of the common AP.
[AC-wlan-ap-ap1] radio 1 type dot11a
[AC-wlan-ap-ap1-radio-1] max-power 10
[AC-wlan-ap-ap1-radio-1] radio-policy radiopolicy1
[AC-wlan-ap-ap1-radio-1] service-template 1
[AC-wlan-ap-ap1-radio-1] radio enable
CAPWAP Dual-Link Configuration Example (On an AC)
Network requirements
As shown in the following figure, AC1 and AC2 are connected to a L2 switch. An AP is connected to
AC1 and AC2 through the L2 switch. AC1 , AC2 and the AP are in the same network. The AP gets its IP
address from the DHCP server. The IP address of AC1 is 10.18.1.1 and the IP address of AC2 is
10.18.1.2. AC1 is working in master mod e while AC2 is working in slave mode. When AC2 detects AC1
is down, AC2 will convert its work mode from slave to master. The AP which is connected to AC2
through a slave tunnel will transform the tunnel mode to master and use AC2 as the master AC.
Figure 1-19 CAPWAP dual link configuratio
n
Configuration procedure
1) Configuration on AC1.
# Define the WLAN ESS interface.
<AC1> system-view
[AC1] interface WLAN-ESS 1
[AC1-WLAN-ESS1] quit
# Define a WLAN service template and bind the WLAN-ESS interface to this service template.
1-28
Page 30

[AC1] wlan service-template 1 clear
[AC1-wlan-st-1] ssid abc
[AC1-wlan-st-1] bind WLAN-ESS 1
[AC1-wlan-st-1] authentication-method open-system
[AC1-wlan-st-1] service-template enable
[AC1-wlan-st-1] quit
# Specify the backup AC address.
[AC1] wlan backup-ac ip 10.18.1.2
# Configure the AP on AC1.
[AC1] wlan ap ap1 model WA2100
[AC1-wlan-ap-ap1] serial-id 210235A29G007C000020
# Configure the radio of the AP.
[AC1-wlan-ap-ap1] radio 1 type dot11g
[AC1-wlan-ap-ap1-radio-1] service-template 1
[AC1-wlan-ap-ap1-radio-1] radio enable
2) Configuration on AC2.
# Define the WLAN ESS interface.
<AC2> system-view
[AC2] interface wlan-ess 1
[AC2-WLAN-ESS1] quit
# Define a WLAN service template and bind the WLAN-ESS interface to this service template.
[AC2] wlan service-template 1 clear
[AC2-wlan-st-1] ssid abc
[AC2-wlan-st-1] bind WLAN-ESS 1
[AC2-wlan-st-1] authentication-method open-system
[AC2-wlan-st-1] service-template enable
[AC2-wlan-st-1] quit
# Specify the backup AC address.
[AC2] wlan backup-ac ip 10.18.1.1
# Configure the AP on AC2.
[AC2] wlan ap ap1 model WA2100
[AC2-wlan-ap-ap1] serial-id 210235A29G007C000021
# Configure the radio of the AP.
[AC2-wlan-ap-ap1] radio 1 type dot11g
[AC2-wlan-ap-ap1-radio-1] service-template 1
[AC2-wlan-ap-ap1-radio-1] radio enable
802.11n Configuration Example
Network requirements
As shown below, an AP is connected to an AC with IP address 10.18.1.1/24 through a Layer 2 switch.
Configure the AP to support 802.11n.
1-29
Page 31

Configuration procedure
# Configure a WLAN-ESS interface.
<AC> system-view
[AC] interface wlan-ess 1
[AC-WLAN-ESS1] quit
# Configure a service template and bind the WLAN-ESS interface with the service template.
[AC] wlan service-template 1 clear
[AC-wlan-st-1] ssid abc
[AC-wlan-st-1] bind WLAN-ESS 1
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
n Figure 1-20 802.11n configuratio
# Configure the AP on the AC.
[AC] wlan ap ap1 model WA2610E-AGN
[AC-wlan-ap-ap1] serial-id 210235A29G007C000020
# Configure the radio of the AP to operate in 802.11g/n mode.
[AC-wlan-ap-ap1] radio 1 type dot11gn
# Configure the working bandwidth of the radio as 40MHz.
[AC-wlan-ap-ap1-radio-1] channel band-width 40
[AC-wlan-ap-ap1-radio-1] service-template 1
[AC-wlan-ap-ap1-radio-1] radio enable
WLAN Service Configuration Example (on a FAT AP)
Network requirements
z As shown below, a fat AP is connected to a Layer 2 switch. The IP address of the fat AP is
10.18.1.10.
z It is required to configure WLAN service on the FAT AP.
Figure 1-21 Network diagram for WLAN service configuration
IP network
L2 switch
FAT AP
Client
1-30
Page 32

Configuration procedure
# Define the WLAN BSS interface.
<Sysname> system-view
[Sysname] interface wlan-bss 1
[Sysname-WLAN-BSS1] quit
# Define a WLAN service template and enable it.
[Sysname] wlan service-template 1 clear
[Sysname-wlan-st-1] ssid abc
[Sysname-wlan-st-1] authentication-method open-system
[Sysname-wlan-st-1] service-template enable
[Sysname-wlan-st-1] quit
# Configure the radio of the fat AP.
[Sysname] interface wlan-radio 1/0/1
[Sysname-WLAN-Radio1/0/1] radio-type dot11a
[Sysname-WLAN-Radio1/0/1] channel 149
[Sysname-WLAN-Radio1/0/1] service-template 1 interface wlan-bss 1
# Configure global WLAN parameters.
<Sysname> system-view
[Sysname] wlan client idle-timeout 3600
[Sysname] wlan client keep-alive 100
[Sysname] wlan broadcast-probe reply
AP Group Configuration Examples
AP Group Configuration without Roaming
Network requirements
As shown in the figure below, configure an AP group and apply it in a user profile on the AC, so that a
client can only access the WLAN through AP 1.
1-31
Page 33

Figure 1-22 Client access control configuration diagram
AC
10.100.100.200/24
AP 1
Client Client
Configuration procedure
1) Configuration on the AC
# Enable port security.
RADIUS server
10.100.100.100/24
L2 switch
AP 2
<AC> system-view
[AC] port-security enable
# Enable EAP authentication mode.
[AC] dot1x authentication-method eap
# Create a RADIUS scheme.
[AC] radius scheme wlan-user-policy
# Specify the RADIUS server and keys for authentication and accounting.
[AC-radius-wlan-user-policy] server-type extended
[AC-radius-wlan-user-policy] primary authentication 10.100.100.100
[AC-radius-wlan-user-policy] primary accounting 10.100.100.100
[AC-radius-wlan-user-policy] key authentication wlan
[AC-radius-wlan-user-policy] key accounting wlan
# Specify the IP address of the AC.
[AC-radius-wlan-user-policy] nas-ip 10.100.100.200
[AC-radius-wlan-user-policy] quit
# Configure an ISP domain named universal by referencing the configured RADIUS scheme.
[AC] domain universal
[AC-isp-universal] authentication default radius-scheme wlan-user-policy
[AC-isp-universal] authorization default radius-scheme wlan-user-policy
[AC-isp-universal] accounting default radius-scheme wlan-user-policy
[AC-isp-universal] quit
# Configure domain universal as the default domain.
1-32
Page 34

[AC] domain default enable universal
# Configure port security on interface WLAN-ESS 1.
[AC] interface wlan-ess 1
[AC-WLAN-ESS1] port-security port-mode userlogin-secure-ext
[AC-WLAN-ESS1] port-security tx-key-type 11key
[AC-WLAN-ESS1] undo dot1x multicast-trigger
[AC-WLAN-ESS1] undo dot1x handshake
[AC-WLAN-ESS1] quit
# Configure a service template.
[AC] wlan service-template 1 crypto
[AC-wlan-st-1] ssid test
[AC-wlan-st-1] bind wlan-ess 1
[AC-wlan-st-1] authentication-method open-system
[AC-wlan-st-1] cipher-suite ccmp
[AC-wlan-st-1] security-ie rsn
[AC-wlan-st-1] service-template enable
[AC-wlan-st-1] quit
# Configure AP1.
[AC] wlan ap ap1 model wa2100
[AC-wlan-ap-ap1] radio 1 type dot11g
[AC-wlan-ap-ap1-radio1] service-template 1
[AC-wlan-ap-ap1-radio1] radio enable
[AC-wlan-ap-ap1-radio1] return
# Add AP1 to AP group 11, apply the AP group to user profile management and enable the user profile.
<AC> system-view
[AC] wlan ap-group 11
[AC-ap-group11] ap ap1
[AC-ap-group11] quit
[AC] user-profile management
[AC-user-profile-management] wlan permit-ap-group 11
[AC-user-profile-management] quit
[AC] user-profile management enable
2) Configuration on the RADIUS server
# Specify the name of the user profile in the external group checkbox on the RADIUS server.
Log in to the CAMS management platform. On the left navigation tree, select Service Management >
Service Config. Then click Add on the page to enter the following configuration page.
Select the Access Control checkbox and add name management.
If no user profile name is specified, all APs are permitted.
1-33
Page 35

e Figure 1-23 Specify a user profile nam
3) Verify the configuration
The AP group applied in the user profile contain s only AP 1, and thus a client can only access the WLAN
through AP 1.
AP Group Configuration for Inter-AC Roaming
Network requirements
As shown in the figure below , AC1 and A C2 belong to the same m obility group. Configure an AP group
on the ACs so that a client can still access the WLAN when it moves from between APs.
Figure 1-24 AP group configuration for inter-AC roaming
Configuration procedure
Configuration on the RADIUS server is similar with that in AP Group Configuration without Roaming and
thus is omitted.
1) Configuration on AC 1
# Configure AP 1.
1-34
Page 36

<AC1> system-view
[AC1] port-security enable
[AC1] dot1x authentication-method eap
[AC1] interface wlan-ess 1
[AC1-WLAN-ESS1] port-security port-mode userlogin-secure-ext
[AC1-WLAN-ESS1] port-security tx-key-type 11key
[AC1-WLAN-ESS1] undo dot1x multicast-trigger
[AC1-WLAN-ESS1] undo dot1x handshake
[AC1-WLAN-ESS1] quit
[AC1] wlan service-template 1 crypto
[AC1-wlan-st-1] ssid abc
[AC1-wlan-st-1] bind wlan-ess 1
[AC1-wlan-st-1] authentication-method open-system
[AC1-wlan-st-1] cipher-suite ccmp
[AC1-wlan-st-1] security-ie rsn
[AC1-wlan-st-1] service-template enable
[AC1-wlan-st-1] quit
[AC1] wlan ap ap1 model WA2100
[AC1-wlan-ap-ap1] serial-id 210235A045B05B1236548
[AC1-wlan-ap-ap1] radio 1 type dot11g
[AC1-wlan-ap-ap1-radio-1] service-template 1
[AC1-wlan-ap-ap1-radio-1] radio enable
[AC1-wlan-ap-ap1-radio-1] quit
[AC1-wlan-ap-ap1] quit
# Configure mobility group abc and enable the mobility group.
[AC1] wlan mobility-group abc
[AC1-wlan-mg-abc] source ip 10.18.1.1
[AC1-wlan-mg-abc] member ip 10.18.1.2
[AC1-wlan-mg-abc] mobility-group enable
[AC1-wlan-mg-abc] return
# Configure AP group 1, add AP 1 and AP 2 in it, apply it in user profile management, and enable the
user profile.
<AC1> system-view
[AC1] wlan ap-group 1
[AC1-ap-group1] ap ap1 ap2
[AC1-ap-group1] quit
[AC1] user-profile management
[AC1-user-profile-management] wlan permit-ap-group 1
[AC1-user-profile-management] quit
[AC1] user-profile management enable
2) Configuration on AC 2
# Configure AP 2.
<AC2> system-view
[AC2] port-security enable
[AC2] dot1x authentication-method eap
1-35
Page 37

[AC2] interface wlan-ess 1
[AC2-WLAN-ESS1] port-security port-mode userlogin-secure-ext
[AC2-WLAN-ESS1] port-security tx-key-type 11key
[AC2-WLAN-ESS1] undo dot1x multicast-trigger
[AC2-WLAN-ESS1] undo dot1x handshake
[AC2-WLAN-ESS1] quit
[AC2] wlan service-template 1 crypto
[AC2-wlan-st-1] ssid abc
[AC2-wlan-st-1] bind wlan-ess 1
[AC2-wlan-st-1] authentication-method open-system
[AC2-wlan-st-1] cipher-suite ccmp
[AC2-wlan-st-1] security-ie rsn
[AC2-wlan-st-1] service-template enable
[AC2-wlan-st-1] quit
[AC2] wlan ap ap1 model WA2100
[AC2-wlan-ap-ap1] serial-id 210235A22W0076000103
[AC2-wlan-ap-ap1] radio 1 type dot11g
[AC2-wlan-ap-ap1-radio-1] service-template 1
[AC2-wlan-ap-ap1-radio-1] radio enable
[AC2-wlan-ap-ap1-radio-1] quit
[AC2-wlan-ap-ap1] quit
# Configure mobility group abc and enable the mobility group.
[AC2] wlan mobility-group abc
[AC2-wlan-mg-abc] source ip 10.18.1.2
[AC2-wlan-mg-abc] member ip 10.18.1.1
[AC2-wlan-mg-abc] mobility-group enable
[AC2-wlan-mg-abc] quit
# Configure AP group 1, add AP 1 and AP 2 in it, apply it in user profile management, and enable the
user profile.
[AC2] wlan ap-group 1
[AC2-ap-group1] ap ap1 ap2
[AC2-ap-group1] quit
[AC2] user-profile management
[AC2-user-profile-management] wlan permit-ap-group 1
[AC2-user-profile-management] quit
[AC2] user-profile management enable
3) Verify the configuration
Since AP 1 and AP 2 are permitted in the AP group, a client can roam between them.
1-36
 Loading...
Loading...