F-SECURE INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61, Internet Gatekeeper Administrator's Manual
Page 1

F-Secure Internet
Gatekeeper
Windows 2000/2003 Server
Administrator’s Guide
Page 2

"F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure
product names and symbols/logos are either trademarks or registered trademarks of F-Secure
Corporation. All product names referenced herein are trademarks or registered trademarks of their
respective companies. F-Secure Corporation disclaims proprietary interest in the marks and names of
others. Although F-Secure Corporation makes every effort to ensure that this information is accurate,
F-Secure Corporation will not be liable for any errors or omission of facts contained herein. F-Secure
Corporation reserves the right to modify specifications cited in this document without prior notice.
Companies, names and data used in examples herein are fictitious unless otherwise noted. No part of
this document may be reproduced or transmitted in any form or by any means, electronic or
mechanical, for any purpose, without the express written permission of F-Secure Corporation.
Copyright © 1993-2006 F-Secure Corporation. All rights reserved. Portions Copyright © 1991-2005
Kaspersky Lab.
This product includes software developed by the Apache Software Foundation (http://
www.apache.org/). Copyright © 2000-2005 The Apache Software Foundation. All rights reserved.
This product includes PHP, freely available from http://www .php.net/. Copyright © 1999-2005 The PHP
Group. All rights reserved.
This product includes code from SpamAssassin. The code in the files of the SpamAssassin distribution
are Copyright © 2000-2002 Justin Mason and others, unless specified otherwise in that particular file.
All files in the SpamAssassin distribution fall under the same terms as Perl itself, as described in the
“Artistic License”.
This product may be covered by one or more F-Secure patents, including the following: B2353372,
GB2366691, GB2366692, GB2366693, GB2367933, GB2368233. #12000041-6E30
Page 3

Contents
About This Guide 10
How This Guide is Organized ............................................................................................ 11
Conventions Used in F-Secure Guides.............................................................................. 13
Symbols .................................................................................................................... 13
Chapter 1 Introduction 15
1.1 Overview....................................................................................................................16
1.2 How the Product Works .............................................................................................17
1.2.1 F-Secure Anti-Virus for Internet Gateways.....................................................17
1.2.2 F-Secure Anti-Virus for Internet Mail..............................................................19
1.2.3 F-Secure Content Scanner Server.................................................................21
1.3 Features.....................................................................................................................21
1.4 F-Secure Anti-Virus Mail Server and Gateway Products ...........................................24
Chapter 2 Deployment 26
2.1 Overview....................................................................................................................27
2.2 Network Requirements...............................................................................................28
2.3 Deployment Scenarios...............................................................................................29
2.3.1 F-Secure Anti-Virus for Internet Gateways.....................................................29
2.3.2 F-Secure Anti-Virus for Internet Mail..............................................................34
Chapter 3 Installation 42
3.1 Recommended System Requirements ................................................................ ... ...43
3.1.1 Which SQL Server to Use for the Quarantine Database?..............................45
3
Page 4

3.1.2 Web Browser Software Requirements ...........................................................46
3.2 Centrally Administered or Stand-alone Installation? ............................................ ... ...47
3.2.1 Installation Overview for Centrally Administered Installation..........................47
3.2.2 Installation Overview for Stand-alone Installation...........................................49
3.3 Installation Instructions...............................................................................................50
3.4 After the Installation ...................................................................................................69
3.4.1 Importing Product MIB files to F-Secure Policy Manager Console.................69
3.4.2 Configuring the Product..................................................................................70
3.5 Upgrading F-Secure Internet Gatekeeper..................................................................72
3.5.1 Upgrade Instructions ......................................................................................72
3.5.2 From the Try-Before-You-Buy Version...........................................................76
3.6 Uninstallation..............................................................................................................77
Chapter 4 Basics of Using F-Secure Internet Gatekeeper 78
4.1 Introduction ................................................................................................................79
4.2 Using F-Secure Policy Manager ................................................................................79
4.2.1 F-Secure Anti-Virus for Internet Gateways Settings.......................................80
4.2.2 F-Secure Anti-Virus for Internet Mail Settings................................................80
4.2.3 F-Secure Content Scanner Server Settings ...................................................80
4.2.4 F-Secure Management Agent Settings ..........................................................81
4.2.5 Changing Settings That Have Been Modified During Installation or Upgrade81
4.3 Using F-Secure Internet Gatekeeper Web Console...................................................82
4.3.1 Logging in the F-Secure Internet Gatek ee pe r Web Conso l e for the Fir st Tim e .
82
4.3.2 Checking the Product Status... ... .... ... ... ... .... ... ................................................86
Chapter 5 Administering F-Secure Anti-Virus for Internet Gateways 92
5.1 Overview - HTTP Scanning........................................................................................93
5.2 Configuring F-Secure Anti-Virus for Internet Gateways.............................................94
5.2.1 Network Configuration....................................................................................94
5.3 Configuring Web Traffic Scanning ...........................................................................107
5.3.1 Content Control ....................... .....................................................................107
5.3.2 Notifications..................................................................................................115
5.3.3 Performance.................................................................................................119
5.3.4 Administration...............................................................................................122
4
Page 5

5.3.5 Access Control .............................................................................................123
5.4 Monitoring Logs................... .....................................................................................127
5.4.1 Error Log.......................................................................................................128
5.4.2 Access Log...................................................................................................129
5.4.3 Logfile.log.....................................................................................................129
5.5 Viewing Statistics .....................................................................................................130
5.5.1 Viewing HTTP Scanning Statistics with F-Secure Internet Gatekeeper Web
Console130
5.5.2 Viewing Statistics with F-Secure Policy Manager Console ............ ... ... .... ... .135
5.6 Examples of HTTP Notifications ..............................................................................136
5.6.1 Virus Warning Message .............................. ... ..............................................137
5.6.2 Block Warning Message...............................................................................138
5.6.3 Banned Site Warning Message....................................................................139
Chapter 6 Administering F-Secure Anti-Virus for Internet Mail 140
6.1 Overview - SMTP Scanning.....................................................................................141
6.2 Configuring F-Secure Anti-Virus for Internet Mail ....................................................142
6.2.1 SMTP Settings..............................................................................................143
6.2.2 SMTP Connections.......................................................................................146
6.2.3 Content Scanner Servers..... ... ... .... ... ... ........................................................149
6.2.4 Quarantine....................................................................................................151
6.2.5 Spooling........................................................................................................158
6.2.6 Logging.........................................................................................................162
6.2.7 Intranet Hosts...............................................................................................164
6.3 Configuring SMTP Traffic Scanning.........................................................................166
6.3.1 Inbound and Outbound Traffic......................................................................166
6.3.2 Receiving ................................ .................................... .................................166
6.3.3 Spam Control................................................................................................172
6.3.4 Blocking........................................................................................................172
6.3.5 Virus Scanning ........................... .... ..............................................................177
6.3.6 Virus Outbreak Response ........................... ... ... ...........................................182
6.3.7 File Type Recognition........................ ... ... .... .................................................183
6.3.8 Disclaimer.....................................................................................................185
6.3.9 Mail Delivery................................... ... ... ... .... ... ..............................................187
6.3.10 Security Options...........................................................................................191
6.4 Monitoring Logs................... .....................................................................................195
5
Page 6

6.5 Viewing Statistics .....................................................................................................199
6.5.1 Viewing Statistics with F-Secure Internet Gatekeeper Web Console...........199
6.5.2 Viewing Statistics with F-Secure Policy Manager . ... .... .................................206
6.6 Notifications..............................................................................................................208
Chapter 7 Administering F-Secure Content Scanner Server 209
7.1 Overview..................................................................................................................210
7.2 Configuring F-Secure Content Scanner Server .......................................................211
7.2.1 Service Connections................ ... .... ... ...........................................................211
7.3 Configuring Scanning Settings.................................................................................216
7.3.1 Virus Scanning ........................... .... ..............................................................216
7.3.2 Spam Filtering ..............................................................................................220
7.3.3 Threat Detection...........................................................................................222
7.3.4 Advanced......................................................................................................224
7.4 Configuring and Viewing Statistics...........................................................................226
7.4.1 Configuring Virus Statistics...........................................................................226
7.4.2 Viewing Virus and Spam Statistics with F-Secure Internet Gatekeeper Web
Console227
7.4.3 Viewing Virus and Spam Statistics with F-Secure Policy Manager Console235
7.5 Monitoring Logs................... .....................................................................................239
7.5.1 Logfile.log.....................................................................................................239
Chapter 8 Administering F-Secure Spam Control 240
8.1 Introduction ..............................................................................................................241
8.2 Spam Control Settings .............................................................................................242
8.3 Realtime Blackhole List Configuration .....................................................................248
8.3.1 Enabling Realtime Blackhole Lists ...............................................................248
8.3.2 Optimizing F-Secure Spam Control Performance........................................250
Chapter 9 Administering F-Secure Management Agent 251
9.1 F-Secure Management Agent Settings....................................................................252
9.2 Configuring Alert Forwarding ...................................................................................254
Chapter 10 Quarantine Management 258
10.1 Introduction ..............................................................................................................259
6
Page 7

10.2 Configuring Quarantine Options...............................................................................260
10.3 Searching the Quarantined Content.........................................................................260
10.4 Query Results Page................................... ... ... ... .... ... ... ... ........................................265
10.5 Viewing Details of a Quarantined Message .............................................................267
10.6 Reprocessing the Quarantined Content...................................................................268
10.7 Releasing the Quarantined Content.........................................................................269
10.8 Removing the Quarantined Content.........................................................................271
10.9 Deleting Old Quarantined Content Automatically.....................................................271
10.10Quarantine Database Settings.................................................................................273
10.11Quarantine Logging..................................................................................................273
10.12Quarantine Statistics................................................................................................273
Chapter 11 Security and Performance 275
11.1 Introduction ..............................................................................................................276
11.2 Optimizing Security..................................................................................................276
11.2.1 Virus Scanning ..................................... ... .... ... ... ...........................................276
11.2.2 Access Control .............................................................................................277
11.2.3 Data Trickling................................................................................................277
11.3 Optimizing Performance...........................................................................................277
11.3.1 Virus Scanning ..................................... ... .... ... ... ...........................................277
Chapter 12 Updating Virus and Spam Definition Databases 280
12.1 Overview..................................................................................................................281
12.2 Automatic Updates...................................................................................................281
12.3 Configuring Automatic Updates ...............................................................................282
12.3.1 Summary......................................................................................................283
12.3.2 Automatic Updates.......................................................................................286
12.3.3 Policy Manager Proxies................................................................................289
Chapter 13 Troubleshooting 291
13.1 Testing the Connections ..........................................................................................292
13.1.1 Checking that F-Secure Anti-Virus for Internet Gateways is Up and Running ...
292
13.1.2 Checking that F-Secure Anti-Virus for Internet Mail is Up and Running.......292
7
Page 8

13.1.3 Checking that F-Secure Content Scanner Server is Up and Running..........293
13.1.4 Checking that the Network Connection to the Original Mail Server is Working..
293
13.2 Starting and Stopping F-Secure Internet Gatekeeper Components ................ .... ... .294
13.3 Frequently Asked Questions....................................................................................295
AppendixA Warning Messages 296
A.1 HTTP Warning Messages....................................................................................... 297
A.2 SMTP Warning Messages .......................................................................................298
A.3 Virus Outbreak Notification Messages.....................................................................299
AppendixB Specifying Hosts 300
B.1 Introduction ............................................................................................................. 301
B.2 Domain.....................................................................................................................301
B.3 Subnet......................................................................................................................301
B.4 IP Address.............. ... .... ... ... ... ... .... ...........................................................................302
B.5 Hostname.................................................................................................................302
AppendixC Access Log Variables 304
C.1 List of Access Log Variables ................................................................................... 305
AppendixD Mail Log Variables 309
D.1 List of Mail Log Variables ........................................................................................ 310
AppendixE Configuring Mail Servers 312
E.1 Configuring the Network.......................................................................................... 313
E.2 Configuring Mail Servers..........................................................................................314
E.2.1 L otus Domino ................................. ... ... ... .... ... ... ... ........................................314
E.2.2 Microsoft Exchange 5.5................................................................................315
E.2.3 Microsoft Exchange 2000.............................................................................315
AppendixF Advanced Deployment Options 319
F.1 Introduction ............................................................................................................. 320
F.2 Transparent Proxy....................................................................................................320
8
Page 9

F.2.1 Examples......................................................................................................322
F.2.2 Transparent Proxy with Linux and Unix Based Systems..............................327
F.2.3 Transparent Proxy with Cisco, Nortel and Lucent........................................329
F.3 HTTP Load Balancing..............................................................................................329
F.3.1 Round-Robin DNS Based Load Balancing...................................................330
F.3.2 Load Balancing with Proxy Auto-Configuration (PAC) or Web Proxy Auto-Dis-
covery Protocol (WPAD).............................. ... ..............................................331
F.3.3 Load Balancing with Proxy or Firewall..........................................................333
F.3.4 Hardware and Software Load-balancing Solutions ......................................335
F.3.5 Load Balancing and High Availability with Clustering...................................337
F.4 Load Balancing With Windows Network Load Balancing Service............................339
F.4.1 Requirements ...............................................................................................339
F.4.2 Setting Up Network Load Balancing Services..............................................340
F.5 Deployment Scenarios for Environments with Multiple Sub-domains......................349
F.5.1 Scenario 1: F-Secure Anti-Virus for Internet Mail as an Upstream Mail Transfer
Agent............................................................................................................349
F.5.2 Scenario 2: F-Secure Anti-Virus for Internet Mail as Interim Ma il Transfer Agent
352
F.5.3 Scenario 3: F-Secure Anti-Virus for Internet Mail for each Sub-domain.......356
AppendixG Services and Processes 360
G.1 List of Services and Processes..................................... ... ....................................... 361
AppendixH Error Codes 365
H.1 Introduction ............................................................................................................. 366
H.2 F-Secure Anti-Virus for Internet Gateways ..............................................................366
H.3 F-Secure Anti-Virus for Internet Mail........................................................................374
H.4 F-Secure Content Scanner Server...........................................................................391
Technical Support 409
Introduction ...................................................................................................................... 410
F-Secure Online Support Resources ...............................................................................410
Web Club ................. ... .....................................................................................................412
Virus Descriptions on the Web .........................................................................................412
About F-Secure Corporation
9
Page 10

ABOUT THIS GUIDE
How This Guide is Organized..................................................... 11
Conventions Used in F-Secure Guides..................................... 13
10
Page 11

How This Guide is Organized
F-Secure Internet Gatekeeper Administrator's Guide is divided into the
following chapters and appendixes.
Chapter 1. Introduction. General information about F-Secure Internet
Gatekeeper and other F-Secure Anti-Virus for Mail Serve r and Ga te wa y
products.
Chapter 2. Deployment. Describes possible deployment scenarios in
the corporate network.
Chapter 3. Installation. Instructions on how to install and upgrade
F-Secure Internet Gatekeeper.
Chapter 4. Basics of Using F-Secure Internet Gatekeeper. Instructions
on when to use F-Secure Policy Manager and F-Secure Internet
Gatekeeper Web Console in centrally managed F-Secure Internet
Gatekeeper installations.
Chapter 5. Administering F-Secure Anti-Virus for Internet Gateways.
Instructions on how to configure F-Secure Anti-Virus for Internet
Gateways general settings before you start using it. It also contains
instructions how to configure HTTP and FTP-over-HTTP scanning and to
use access control to allow and deny access to specified sites on the
Internet.
About This Guide 11
Chapter 6. Administering F-Secure Anti-Virus for Internet Mail.
Instructions on how to configure F-Secure Anti-Virus for Internet Mail
general settings before you start using it, and how to configure virus
scanning to detect and disinfect viruses and other malicious code from
e-mails.
Chapter 7. Administering F-Secure Content Scanner Server.
Instructions how to configure F-Secure Content Scanner Server before
you start using F-Secure Anti-Virus for Internet Gateways and F-Secure
Anti-Virus for Internet Mail.
Chapter 8. Administering F-Secure Spam Control. Information about
and instructions on how to configure F-Secure Spam Control.
Page 12

12
Chapter 9. Administering F-Secure Ma nagement Agent. Instructions on
how to configure F-Secure Management Agent.
Chapter 10. Quarantine Management. Instructions on how to manage
and search quarantined content.
Chapter 1 1. Security and Performance. Instructions on how to optimize
security and performance.
Chapter 12. Updating Virus and Spam Definition Databases.
Instructions on how to keep virus definition databases up-to-date.
Chapter 13. Troubleshooting. Instructions on how to check that
F-Secure Internet Gatekeeper is running and answers to frequently as ked
questions.
Appendix A. Warning Messages. Lists variables that can be included in
virus warning messages.
Appendix B. Specifying Hosts. Instructions on how to specify hosts in
F-Secure Anti-Virus for Internet Gateways.
Appendix C. Access Log Variables. Lists variables that can be used in
the access log.
Appendix D. Mail Log Variables. Lists variables that can be used in the
F-Secure Anti-Virus for Internet Mail mail log.
Appendix E. Configuring Mail Servers. Instructions on how to configure
mail servers to work with F-Secure Internet Gatekeeper.
Appendix F. Adva nced Deployment Options. Info rmation about differen t
methods that you can use when setting up a transparent proxy and HTTP
load balancing services.
Appendix G. Services and Pro cesses. Lists services and processes that
are running on the system after the installation.
Appendix H. Error Codes. Describes error codes.
Technical Support. . Contains the contact information for assistance.
About F-Secure Corporation. Describes the company background and
products.
Page 13

Conventions Used in F-Secure Guides
This section describes the symbols, fonts, and terminology used in this
manual.
Symbols
WARNING: The warning symbol indicates a situation with a
risk of irreversible destruction to data.
IMPORTANT: An exclamation m ark provides important information
that you need to consider.
REFERENCE - A book refers you to related information on the
topic available in another document.
NOTE - A note provides additional information that you should
consider.
l
13
Fonts
TIP - A tip provides information that can help you perfor m a task
more quickly or easily.
⇒ An arrow indicates a one-step procedure.
Arial bold (blue) is used to refer to menu names and commands, to
buttons and other items in a dialog box.
Arial Italics (blue) is used to refer to other chapters in the manual, book
titles, and titles of other manuals.
Arial Italics (black) is used for file and folder names, for figure and table
captions, and for directory tree names.
Courier New is used for messages on your computer screen.
Page 14

14
Courier New bold is used for information that you must type.
SMALL CAPS (BLACK) is used for a key or key combination on your
keyboard.
PDF Document
For More Information
Arial underlined (blue)
Arial italics is used for window and dialog box names.
This manual is provided in PDF (Portable Document Format). The PDF
document can be used for online viewing and printing using Adobe®
Acrobat® Reader. When printing the manual, please print the entire
manual, including the copyright and disclaimer sta tements.
Visit F-Secure at http://www.f-secure.com for documentation, training
courses, downloads, and service and supp o rt contacts.
In our constant attempts to improve our documentation, we would
welcome your feedback. If you have any questions, comments, or
suggestions about this or any other F-Secure document, please contact
us at documentation@f-secure.com
is used for user interface links.
.
Page 15

1
INTRODUCTION
Overview..................................................................................... 16
How the Product Works.............................................................. 17
Features..................................................................................... 21
F-Secure Anti-Virus Mail Server and Gateway Products............ 24
15
Page 16

16
1.1 Overview
Malicious code, such as computer viruses, is one of the main threats for
companies today. When users began to use office applications with
macro capabilities to write documents and distribute them via mail and
groupware servers, macro viruses started spreading rapidly.
After the millennium, the most common spreading mechanism has been
the e-mail. Today about 90% of viruses arrive via e-mail. E-mails provide
a very fast and efficient way for viruses to spread without any user
intervention and this is why e-mail worm outbreaks, like Sobig, Netsky
and Mydoom, cause a lot of damage around the world.
The Internet is used by more and more people every day. It opens
another, so far dormant channe l for viruse s to spread, HTTP. Web surfing
is increasing rapidly as we are using the web to find information not only
for business but also for other purposes, such as hobbies, health, and so
on. It is very important to realize this early and to be proactive in
protecting our resources.
F-Secure Anti-Virus Mail Server and Gateway products are designed to
protect your company's mail and groupware servers and to sh ield the
company network from any malicious code that travels in HTTP,
FTP-over-HTTP or SMTP traffic. The protection can be implemented on
the gateway level to screen all incoming and outgoing e-mail (SMTP),
web surfing (HTTP) and file transfer (FTP-over-HTTP) traffic.
Furthermore, it can be implemented on the mail server level so that it not
only protects inbound and outbound tr affic but also in ternal mail traffic and
public sources, such as Public Folders on Microsoft Excha nge servers.
Providing the protection already on the gateway level has plenty of
advantages. The protection is easy and fast to set up and install, and it
complements the virus protection that is installe d on the workstations. The
protection is also invisible to the end users which ensur es that the system
cannot be by-passed and makes it easy to maintain. Of course, protecting
the gateway level alone is not enough to provide a complete anti-virus
solution; file server and workstation level protection is needed, too.
Why clean 1000 workstations when you can clean one attachment at the
gateway level?
Page 17

1.2 How the Product Works
F-Secure Internet Gatekeeper is a suite of real-time services to protect
the corporate network against computer viruses and malicious code
coming in web (HTTP and FTP-over-HTTP) and e-mail (SMTP) traffic.
F-Secure Internet Gatekeeper is comprised of the following
components: F-Secure Anti-Virus for Inte rnet Gateways, F-Secure
Anti-Virus for Internet Mail and F-Secure Content Scanner Server.
1.2.1 F-Secure Anti-Virus for Internet Gateways
F-Secure Anti-Virus for Internet Gateways is an HTTP proxy server which
acts as a gateway between the corporate network and the Internet. If a
client computer requests a file from a Web server, it asks the proxy server
to retrieve the file instead of downloading it directly from the Internet.
F-Secure Anti-Virus for Internet Gateways processes the request to make
sure that the content does not contain any malicious code and it should
not be blocked. F-Secure Anti-Virus for Internet Gateways returns only
allowed Web content and virus-free files to the requesting client. All files
and web pages downloaded via HTTP and FTP-over-HTT P are ch ecked
for viruses and malicious code on the fly.
CHAPTER 1 17
Introduction
Page 18

18
Figure 1-1 Web traffic flow after F-Secure Anti-Virus for Internet Gateways has
been installed
F-Secure Anti-Virus for Internet Gateways provides comprehensive virus
protection and content filtering. It can be configured to do any of the
following:
Deny access to specified Web sites,
Block files by content types, filenames and extensions,
Block files that exceed a specified file size,
Scan files by content types, filenames and extensions, and
Automatically disinfect or drop the infected content.
If F-Secure Anti-Virus for Internet Gateways finds disallowed or malicious
content, it denies access to the file and shows a warning message to the
end-user. The warning message can be customized.
Page 19

F-Secure Anti-Virus for Internet Gateways can be deployed transparently
to end-users. Since all HTTP and FTP-over-HTTP requests and
downloads pass through the proxy server, F-Secur e Anti-Virus for Internet
Gateways provides effective access control and protection against
viruses and malicious content.
1.2.2 F-Secure Anti-Virus for Internet Mail
F-Secure Anti-Virus for Internet Mail operates as a mail gateway that
accepts incoming and outgoing e-mails, processes mail bodies and
attachments and delivers processed e-mail messages to the designated
SMTP server for further processing and delivery.
CHAPTER 1 19
Introduction
Content
Blocking
Virus and Spam
Outbreak Detection
Spam
Control
When F-Secure Anti-Virus for Internet Mail receives an e-mail message
from an Internet or internal network source, it extracts all dangerous
objects such as attached files and embedded OLE objects, and blocks
them immediately. For example, attachment s can be str ipp ed from e-mai l
messages by their filenames or extensions, and messages that contain
malformed or suspicious headers can be blocked. After F-Secure
Anti-Virus for Internet Mail has checked e-mail messages for disallowed
content, it scans the mail message body and attachments for viruses and
other malicious code.
Massive spam and virus outbreaks consist of millions of messages which
share at least one identifiable pattern that can be used to distinguish the
outbreak. Any message that contains one or more of these patterns can
be assumed to be a part of the same spam or virus outbreak.
F-Secure Anti-Virus for Internet Mail can identify these patterns from the
message envelope, headers and body, in any language, message format
and encoding type. It can detect spam messages and new viruses during
the first minutes of the outbreak.
F-Secure Spam Control is a separate product component that uses
heuristic spam analysis to filter inbound mails for spam, which supports
DNS Blackhole List (DNSBL) functionality.
Page 20

20
Figure 1-2 Mail traffic flow after F-Secure Anti-Virus for Internet Mail has been
installed
If F-Secure Anti-Virus for Internet Mail finds an infected attachment or
other malicious content, it can do any of the following:
Block the whole e-mail message,
Strip the infected attachment,
Send a customizable virus warning message to the sender,
recipient or both, or
Place the infected attachment to the quarantine for further
processing.
Page 21

1.2.3 F-Secure Content Scanner Server
F-Secure Content Scanner Server is the back-end component that
provides anti-virus and spam scanning services for F-Secure Anti-Virus
for Internet Gateways and F-Secure Anti-Virus for Internet Mail. F-Secure
Content Scanner Server receives data for validation via Simple Content
Inspection Protocol (SCIP).
1.3 Features
F-Secure Internet Gatekeeper, as well as all other F-Secure Anti-Virus
Mail Server and Gateway products, has the following features and
capabilities.
Alerting F-Secure Internet Gatekeeper has extensive monitoring, reporting and
alerting functions that can be used to notify any administrator in the
company network about any infected content that F-Secure Internet
Gatekeeper has found.
CHAPTER 1 21
Introduction
Powerful and Always
Up-to-date
F-Secure Internet Gatekeeper uses the award-winning F-Secure
Anti-Virus scanners to ensure the highest possible detection rate and
disinfection capability . The daily virus definition database updates provide
a protection that is always up-to-date.
F-Secure Internet Gatekeeper uses the threat detection engine to detect
possible virus outbreaks before they become widespread. The threat
detection engine analyzes messages and identifies threat patterns as
they are released to the Internet within an outbreak.
F-Secure Anti-Virus scanner consisten tly ranks at the top when comp ared
to competing products. Our team of dedicated virus r esearchers is on call
24-hours a day responding to new and emerging threats. F-Secure
releases tested virus definition updates on a daily basis, to make sure our
customers are receiving the highest quality service and protection.
Page 22

22
Easy to Administer F-Secure Internet Gatekeeper can be centrally managed with F-Secure
Policy Manager. You can configure F-Secure Internet Gatekeeper
settings with F-Secure Policy Manager any time you want. In stand-alone
mode, the F-Secure Internet Gatekeeper Web Console can be used to
administer F-Secure Internet Gatekeeper.
F-Secure Internet Gatekeeper Web Console can be used to check the
status of F-Secure Internet Gatekeeper at a glance. It is also used to
manage quarantined items both in centrally managed and stand-alone
installations.
Superior Protection High level of protection with low maintenance costs.
Superior detection rate with multiple scanning engines.
Unparalleled malicious code detection and disinfection. F-Secure
Internet Gatekeeper detects all known viruses, worms and
Trojans, including Java and ActiveX viruses.
Heuristic scanning detects also unknown Windows and macro
viruses.
Recursive scanning of ARJ, BZ2, CAB, GZ, JAR, LZH, MSI,
RAR, T AR, TGZ, Z and ZIP archive files.
Automatic daily virus definition database updates.
Suspicious and unsafe attachments can be stripped away from
e-mails.
Password protected archives can be treated as unsafe.
Intelligent file type recognition.
Virus Outbreak
Detection
Possible virus outbreaks are transparently detected before they
become widespread.
The product can notify the administrator about virus outbreaks.
Unsafe messages can be quarantined and reprocessed
automatically.
Page 23

CHAPTER 1 23
Introduction
Transparen cy and
Scalability
Usability Easy to install and configure.
Protection against
Spam
Viruses are intercepted before they enter the network and sp read
to workstations and servers.
Real-time scanning of internal, inbound and outbound mail
messages.
The company network can be configured so that users cannot
bypass the system, which means that e-mails and files cannot be
downloaded without them being scanned first.
Can be administered centrally with F-Secure Policy Manager.
Can be monitored with the convenient F-Sec ure In te rn et
Gatekeeper Web Console.
Contains new quarantine management fe atures: you can manage
and search quarantined content with the F-Secure Internet
Gatekeeper Web Console.
Possible spam messages are transparently detected before they
become widespread.
Efficient and fast spam detection based on different analyses on
the e-mail content.
Multiple filtering mechanisms guarantee the high accuracy of
spam detection.
Sp am detection works in every language and message format.
Page 24

24
1.4 F-Secure Anti-Virus Mail Server and Gateway Products
The F-Secure Anti-Virus product line consists of workstation, file server,
mail server and gateway products.
F-Secure Internet Gatekeeper is a high performance, totally
automated web (HTTP and FTP-over-HTTP) and e-mail (SMTP)
virus scanning solution for the gateway level. F-Secure Internet
Gatekeeper works independently of firewall and e-mail server
solutions, and does not affect their performance.
F-Secure Anti-Virus for Microsoft Exchange™ protects your
Microsoft Exchange users from malicious code contained within
files they receive in mail messages and documents they open
from shared databases. Malicious code is also stopped in
outbound messages and in notes being posted on Public Folders.
The product operates transparently and scans files in the
Exchange Server Information Store in real-time. Manual and
scheduled scanning of user mailboxes and Public Folders i s also
supported.
F-Secure Anti-Virus for MIMEsweeper™ provides a powerful
anti-virus scanning solution that tightly integrates with Clearswift
MIMEsweeper for SMTP and MIMEsweeper for Web products.
F-Secure provides top-class anti-virus software with fast and
simple integration to Clearswift MAILsweeper and WEBsweeper,
giving the corporation the powerful combination of complete
content security.
F-Secure Internet Gatekeeper for Linux™ provides a
high-performance solution at the Internet gateway level, stopping
viruses and other malicious code before the spread to end users
desktops or corporate servers. The product scans SMTP, HTTP,
FTP and POP3 traffic for vi ruses, worms and trojans, and blocks
and filters out specified file types. ActiveX and Java code can
also be scanned or blocked. The product receives updates
Page 25

automatically from F-Secure, keeping the virus protection always
up to date. A powerful and easy-to-use manage ment console
simplifies the installation and configuration of the product.
F-Secure Messaging Security Gateway™ delivers the
industry’s most complete and effective security for e-mail. It
combines a robust enterprise-class messaging platform with
perimeter security, antispam, antivirus, secure messaging and
outbound content security capabilities in an easy-to-deploy,
hardened appliance.
CHAPTER 1 25
Introduction
Page 26

2
DEPLOYMENT
Overview..................................................................................... 27
Deployment Scenarios............................................................... 29
26
Page 27

2.1 Overview
CHAPTER 2 27
Deployment
Depending on the corporate network structure, you might consider
various scenarios of deploying F-Secure Internet Gatekeeper. This
chapter describes some possible deployment scenarios of F-Secure
Internet Gatekeeper in the corporate ne two rk - use th e on e th at best fits
your needs and your own network design strategy.
Although the scenarios are given separately for web traffic and e-mail
scanning components, you can install them to the same host if required.
To determine which option is the most suitable, consider your existing
network configuration and estimate the peak and mean loads that the
server needs to handle.
Page 28

28
2.2 Network Requirements
This network configuration is valid for all scenarios described in this
chapter. Make sure that the following network traffic can travel:
Service Process Inbound ports Outbound ports
F-Secure Anti-Virus for
Internet Gateways
F-Secure Anti-Virus for
Internet Mail
F-Secure Content Scanner
Server
F-Secure Internet
Gatekeeper Web Console
F-Secure Automatic
Update Agent
FSNRB %ProgramFiles%\F-Secure\
%ProgramFiles%\F-Secure\
Anti-Virus for Internet
Gateways\bin\httpscan.exe
%ProgramFiles%\F-Secure\
Anti-Virus Agent for Internet
Mail\fsavagsm.exe
%ProgramFiles%\F-Secure\
Content Scanner Server\
fsavsd.exe
%ProgramFiles%\F-Secure\
Web User Interface\
bin\fswebuid.exe
F-Secure Automatic Update.exe 371 (UDP), only if
Common\fnrb32.exe
3128 (TCP) DNS (53, UDP/TCP),
HTTP (80), HTTPS (443)
and/or other ports used
with upstream proxy and
web servers
SMTP (25) DNS (53, UDP/TCP),
SMTP (25) and/or other
ports used with mail
servers
18971 (TCP) +
1024-65536 (TCP), only
with F-Secure Anti-Virus
for Internet Mail on a
separate host
25023 DNS (53, UDP and TCP),
BackWeb Polite Protocol
is used
- DNS (53, UDP/TCP),
DNS (53, UDP/TCP),
HTTP (80) or other known
port used for HTTP proxy
1433 (TCP), only with the
dedicated SQL server
DNS (53, UDP and TCP),
HTTP (80)
HTTP (80)
FSMA (AMEH) %ProgramFiles%\F-Secure\
F-Secure Quarantine
Manager
Common\fameh32.exe
%ProgramFiles%\F-Secure\
Quarantine Manager\fqm.exe
- DNS (53, UDP/TCP),
SMTP (25)
- DNS (53, UDP/TCP),
1433 (TCP), only with the
dedicated SQL server
Page 29

2.3 Deployment Scenarios
This section describes the F-Secure Anti-Virus for Internet Gateways and
F-Secure Anti-Virus for Internet Mail deployment scenarios.
2.3.1 F-Secure Anti-Virus for Internet Gateways
There are four different deployment scenarios for F-Secure Anti-Virus for
Internet Gateways.
Scenario 1: On a Dedicated Machine
CHAPTER 2 29
Deployment
Figure 2-1 F-Secure Anti-Virus for Internet Gateways deployed on a dedicated
machine
Advantages
Simple to set up.
Disadvantages
End-users have to change the proxy settings of their web
browsers.
Configuration on End-User Workstations
Specify F-Secure Anti-Virus for Internet Gateways as HTTP and
HTTPS proxy in the web browser settings.
Page 30

30
F-Secure Anti-Virus for Internet Gateways Configuration
Add end-user workstations to the list of hosts which are allowed
to connect to F-Secure Anti-Virus for Internet Gateways. For
more information, see “Connections to F-Secure Anti-Virus for
Internet Gateways”, 123
Firewall Configuration
Allow HTTP and HTTPS requests only from F-Secure Anti-Virus
for Internet Gateways.
DNS Configuration
No changes are required.
Scenario 2: As a Downstream Proxy
Figure 2-2 F-Secure Anti-Virus for Internet Gateways deployed as a downstream
proxy
Advantages
End-users do not have to change the proxy settings of their web
browsers.
Configuration on End-User Workstations
The proxy settings in web browers do not have to be changed if
the existing proxy server is defined as a DNS name (for example,
proxy.example.com) or if they use the automatic proxy detection.
Otherwise, specify F-Secure Anti-Virus for Internet Gateways as
HTTP and HTTPS proxy in the web browser settings.
Page 31

F-Secure Anti-Virus for Internet Gateways Configuration
Add end-user workstations to the list of hosts which are allowed
to connect to F-Secure Anti-Virus for Internet Gateways. For
more information, see “Connections to F-Secure Anti-Virus for
Internet Gateways”, 123
Define the existing HTTP proxy or cache server as the re m ote
proxy server in the proxy chaining settings. For more information,
see “Proxy Chaining”, 98
HTTP Proxy or Cache Server Configuration
• Configure the HTTP proxy or cache server to accept incoming
requests only from F-Secure Anti-Virus for Internet Gateways.
Firewall Configuration
No changes are required if the firewall is configured to accept
HTTP and HTTPS requests from the existing HTTP proxy or
cache server.
DNS Configuration
Reassign existing HTTP proxy A (address) and PTR (pointer)
records to F-Secure Anti-Virus for Internet Gateways.
CHAPTER 2 31
Deployment
Upstream and downstream proxies can be installed on the same
server as long as they do not use same port numbers.
Page 32
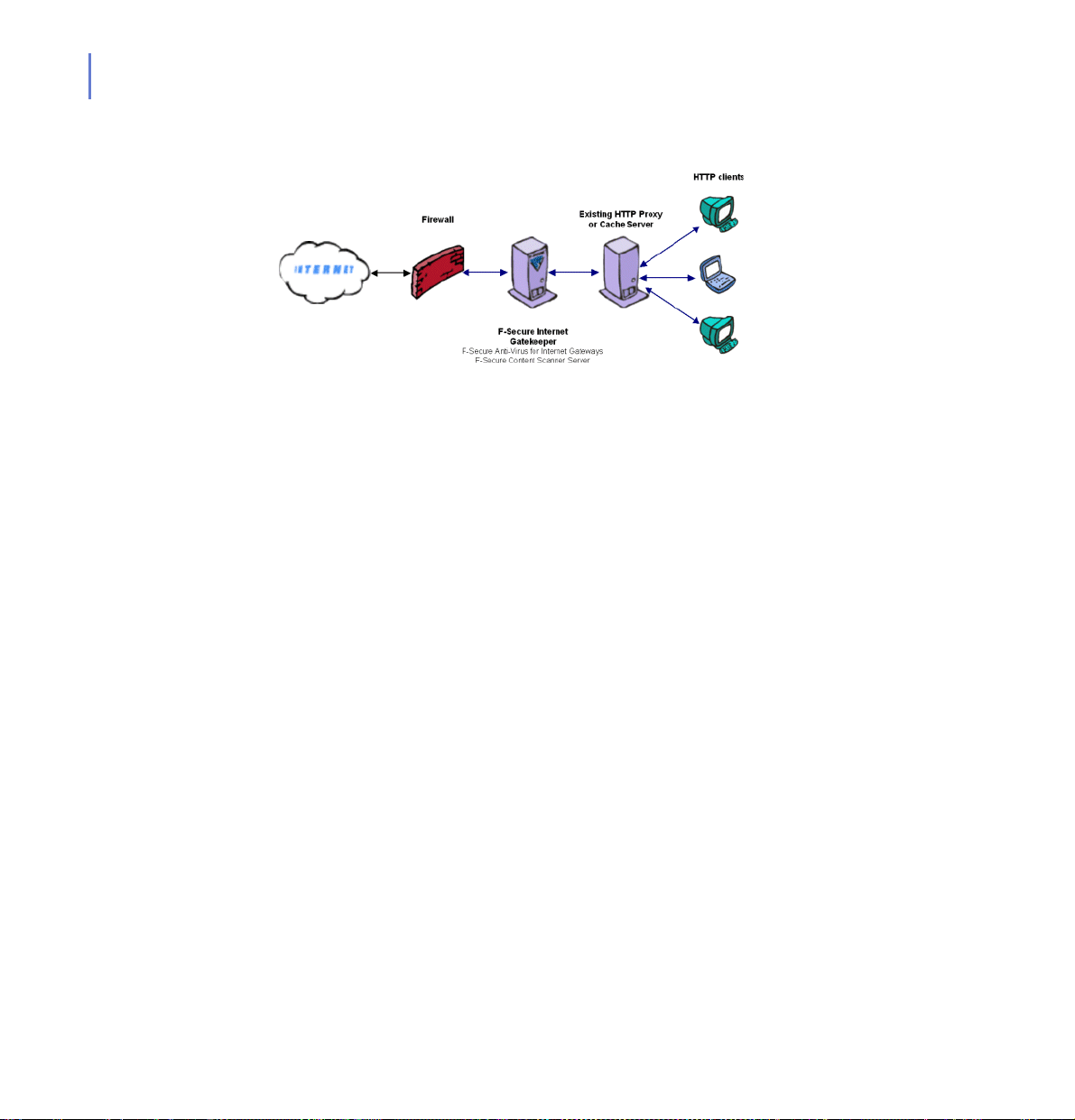
32
Scenario 3: As an Upstream Proxy
Figure 2-3 F-Secure Anti-Virus for Internet Gateways deployed as an upstream
proxy
Advantages
End-users do not have to change the proxy settings of their web
browsers.
Disadvantages
If virus definition databases are not up-to-date, there is a risk of
malicious code getting to the cache server and HTTP clients
accessing it there.
Configuration on End-User Workstations
Web browser proxy settings do not have to be changed.
F-Secure Anti-Virus for Internet Gateways Configuration
Define the existing HTTP proxy or cache server i n the list of host s
which are allowed to connect to F-Secure Anti-Virus for Internet
Gateways. For more information, see “Connections to F-Secure
Anti-Virus for Internet Gateways”, 123.
Page 33
CHAPTER 2 33
Deployment
HTTP Proxy or Cache Server Configuration
Configure HTTP proxy or cache server to forward all HTTP
requests to F-Secure Anti-Virus for Internet Gateways.
Firewall Configuration
Allow HTTP and HTTPS requests only from F-Secure Anti-Virus
for Internet Gateways.
DNS Configuration
No changes are required.
Upstream and downstream proxies can be installed on the same
server as long as they do not use same port numbers.
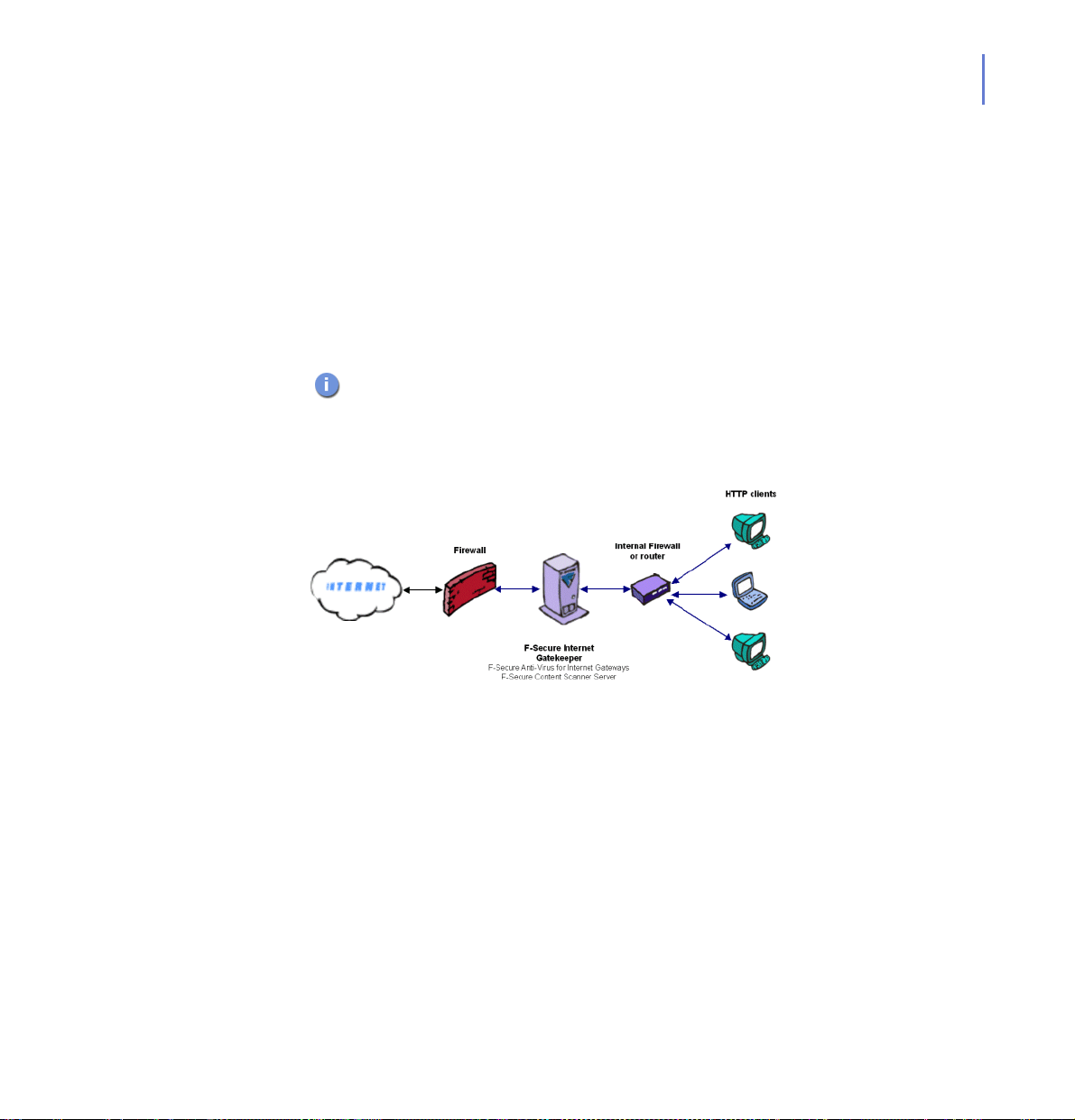
Scenario 4: Transparent Deployment with a Firewall or a Router
Figure 2-4 F-Secure Anti-Virus for Internet Gateways deployed transparently with
a firewall or a router
Advantages
End-users do not have to change the proxy settings of their web
browsers.
Disadvantages
An internal firewall is needed.
Page 34

34
Configuration on End-User Workstations
Web browsers do not have to be configured to use the proxy,
HTTP requests are sent directly.
Adjust the routing table to forward requests to a firewall or router
if necessary.
F-Secure Anti-Virus for Internet Gateways Configuration
Add the internal firewall or router and end-user workstations to
the list of hosts which are allowed to connect to F-Secure
Anti-Virus for Internet Gateways. For more information, see
“Connections to F-Secure Anti-Virus for Internet Gateways”, 123
Internal Firewall or Router Configuration
Forward HTTP requests to F-Secure Anti-Virus for Internet
Gateways.
Firewall Configuration
Allow HTTP and HTTPS requests only from F-Secure Anti-Virus
for Internet Gateways.
DNS Configuration
No changes are required.
2.3.2 F-Secure Anti-Virus for Internet Mail
There are three different deploym ent scenarios for F-Secure Anti-Virus for
Internet Mail.
Page 35

Scenario 1: On a Dedicated Machine
Figure 2-5 F-Secure Anti-Virus for Internet Mail deployed on a dedicated machine
Advantages
The mail server may run on any operating system using any
hardware.
All inbound, outbound and internal mails are scanned.
The overall performance is better as the virus scanning is
performed on a dedicated machine.
CHAPTER 2 35
Deployment
Disadvantages
The network configuration has to be changed.
DNS Configuration
If the mail server has a DNS name (for example,
smtp.example.com) which is used for SMTP, the name should be
reassigned to the host which runs F-Secure Anti-Virus for Internet
Mail.
Firewall Configuration
Route all incoming mails to F-Secure Anti-Virus for Internet Mail.
Page 36

36
Configuration on End-User Workstations
If the mail server for outgoing mails is specified as a DNS name
(for example, smtp.example.com), e-mail client configurations do
not have to be changed. Otherwise, e-mail clients should be
configured to send e-mails to F-Secure Anti-Virus for Internet
Mail.
The settings for received e-mails do not have to be changed.
F-Secure Anti-Virus for Internet Mail Configuration
Add end-user workstations to the list of the Intranet Hosts. All
e-mails that come from computers defined on the Intranet Hosts
list are treated as outbound. For more information, see “Intranet
Hosts”, 164.
Specify the existing mail server address as the inbound and
outbound mail server for F-Secure Anti-Vir us for Internet Mail. For
more information, see “Mail Delivery”, 187.
Enable and configure the verify recipients feature in F-Secure
Anti-Virus for Internet Mail. For more information, see
“Receiving”, 166.
Specify the maximum message size that F-Secure Anti-Virus for
Internet Mail accepts to the same value as in the mail server. For
more information, see “Receiving”, 166.
Mail Server Configuration
Add F-Secure Anti-Virus for Internet Mail to the list of hosts where
the mail server accepts mail.
Note that the DNS host name may have been changed.
Page 37

Scenario 2: With a Mail Server on the Same Machine
Figure 2-6 F-Secure Anti-Virus for Internet Mail deployed with a mail server on
the same machine
Advantages
F-Secure Anti-Virus for Internet Mail does not require an
additional server.
E-mail clients, DNS and firewall configurations do not have to be
changed.
CHAPTER 2 37
Deployment
Disadvantages
This type of deployment may cause extra load on the server.
The mail server port needs to be changed, and in some cases
this may cause interoperability problems.
DNS and Firewall Configuration
No changes are required, only the mail server configuration has
to be changed.
Configuration on End-User Workstations
No changes are required.
Page 38

38
Mail Server Configuration
Change the port number that the mail server listens to something
other than 25 (e.g. 26).
Configure the mail server to accept incoming SMTP connections
only from F-Secure Anti-Virus for Internet Mail (i.e. from localhost,
or 127.0.0.1).
F-Secure Anti-Virus for Internet Mail Configuration
Add end-user workstations to the list of the Intranet Hosts. All
e-mails that come from intranet hosts are treated as outbound.
For more information, see “Intranet Hosts”, 164.
Specify localhost and the new port number of the mail server as
the inbound and outbound mail server for F-Secure Anti-V irus for
Internet Mail. For more information, see “Mail Delivery”, 187.
Enable and configure the verify recipients feature in F-Secure
Anti-Virus for Internet Mail. For more information, see
“Receiving”, 166.
Specify the maximum message size that F-Secure Anti-Virus for
Internet Mail accepts to the same value as in the mail server. For
more information, see “Receiving”, 166.
Scenario 3: As a Mail Gateway With An Inbound Mail Server
Figure 2-7 F-Secure Anti-Virus for Internet Mail deployed with an inbound mail
server
Page 39

Advantages
E-mail clients can send mails using other protocol(s) than SMTP.
The internal mail server may run on any operating system using
any hardware.
Disadvantages
Internal mails are not scanned.
DNS and Firewall Configuration
No changes are required in firewall configuration.
Configuration on End-User Workstations
No changes are required.
Internal Mail Server Configuration
Configure the internal mail server to send all outbound e-mails to
F-Secure Anti-Virus for Internet Mail instead of to the external
mail server.
F-Secure Anti-Virus for Internet Mail Configuration
CHAPTER 2 39
Deployment
Configure F-Secure Anti-Virus for Internet Mail to send inbound
mails to the internal mail server. For more information, see “Mail
Delivery”, 187.
Add end-user workstations and the internal mail server to the list
of the Intranet Hosts. All e-mails that com e from intranet hosts a re
treated as outbound. For more information, see “Intranet Hosts”,
164.
Enable and configure the verify recipients feature in F- Secure
Anti-Virus for Internet Mail. For more information, see
“Receiving”, 166.
Specify the maximum inbound message size that F-Secure
Anti-Virus for Internet Mail accepts to the same value as in the
internal mail server. For more information, see “Receiving”, 166.
Page 40

40
Scenario 4: Multiple F-Secure Internet Gatekeeper installations
with Centralized Quarantine Management
Figure 2-8 Two installation of F-Secure Anti-Virus for Internet Mail deployed with
centralized quarantine management
SQL Server Used for the Centralized Quarantine Database
There is a common SQL server where the quarantine dat abase is
located.
The SQL server can be installed on a ded ica te d server or o n one
of the servers running F-Secure Internet Gatekeeper.
Page 41

CHAPTER 2 41
Deployment
F-Secure Anti-Virus for Internet Mail Configuration
When installing the product, configure each instance of the
product to use the same SQL server and database.
Make sure that the SQL server, the database name, user name
and password are identical in the quarantine configuration for all
F-Secure Internet Gatekeeper instances.
The quarantine database settings can be changed through the
Web Console only.
When using the centralized quarantine management, make sure
that the Windows Server service (lanmanserver) is enabled and
running on the system.
Advanced Deployment Scenarios in Environments with Multiple
Sub-domains
For information on advanced deployment scenarios, see “Deployment
Scenarios for Environments with Multiple Sub-domains”, 349.
Page 42

3
INSTALLATION
Recommended System Requirements....................................... 43
Centrally Administered or Stand-alone Installation?................... 47
Installation Instructions............................................................... 50
After the Installation.................................................................... 69
Upgrading F-Secure Internet Gatekeeper.................................. 72
Uninstallation.............................................................................. 77
42
Page 43

3.1 Recommended System Requirements
Operating system: Windows 2000 Server Family:
Microsoft® Windows 2000 Server with
the latest service pack
Microsoft® Windows 2000 Advanced
Server with the latest service pack
Windows 2003 Server Family:
Microsoft® Windows Server 2003,
Stan dard Edition with late st service p ack
Microsoft® Windows Server 2003,
Enterprise Edition with latest service
pack
Microsoft® Windows Server 2003 R2,
Standard Edition
Microsoft® Windows Server 2003 R2,
Enterprise Edition
CHAPTER 3 43
Installation
Windows 2003 Server 64-bit Family:
Microsoft ® Windows Server 2003,
Standard x64 Edition
Microsoft® Windows Server 2003,
Enterprise x64 Edition
For Microsoft Windows Server 2003 Service
Pack 1 related support information, see
http://support.f-secure.com/enu/corporate/
w2003sp1/
Page 44

44
If you plan to install the product on Microsoft
Windows 2000 platform, then the latest
Microsoft Data Access Components (MDAC,
version 2.8 or newer) needs to be installed to the
system before the product installation. The latest
version of MDAC can be downloaded from this
page: http://msdn.microsoft.com/data/mdac/
downloads/default.aspx.
Processor: Intel® Pentium® 4 2GHz or faster processor
Memory: 1 GB of RAM
Disk space to install: 260 MB on NTFS partition
Disk space for
processing:
Network: 100Mbps Fast Ethernet NIC, switched network
SQL server (for
quarantine
database):
F-Secure Policy
Manager version:
10 GB or more
connection
Microsoft SQL Server 2000 (Enterprise,
Standard or Workgroup edition) with Service
Pack 4
Microsoft SQL Server 2005
Microsoft SQL Server 2000 Desktop Engine
(MSDE) with Service Pack 4
For more information, see “Which SQL Server to
Use for the Quarantine Database?”, 45.
When centralized quarantine management is
used, the SQL server must be reachable from
the network and file sharing must be enabled.
F-Secure Policy Manager 6.0 or newer.
F-Secure Policy Manager is required only in
centrally managed environments.
Page 45

CHAPTER 3 45
Installation
The system requirements are dependent on how much HTTP and
SMTP traffic there is in the corporate network.
3.1.1 Which SQL Server to Use for the Quarantine Database?
As a minimum requirement, the quarantine database should have the
capacity to store information about all inbound and outbound mail to and
from your organization that would normally be sent during 2-3 days.
Take into account the following SQL server specific considerations when
deciding which SQL server to use:
MSDE: When using Microsoft SQL Server Desktop Engine (MSDE), the
quarantine database size is limited to 2 GB.
MSDE includes a concurrent workload governor that limits the
scalability of MSDE. For more information, see
http://msdn.microsoft.com/library/?url=/library/en-us/architec/
8_ar_sa2_0ciq.asp?frame=true.
It is not recommended to use MSDE if you are planning to use
centralized quarantine management with multiple F-Secure
Internet Gatekeeper installations.
MSDE is delivered together with F-Secure Internet
Gatekeeper, an d you can install it during the F-Secure Internet
Gatekeeper Setup. For more information, see “Installation
Instructions”, 50.
Page 46

46
Microsoft SQL Server
2000
If your organization sends a large amount of e-mails, it is
recommended to use Microsoft SQL Server 2000.
It is recommended to use Microsoft SQL Server 2000 if you are
planning to use centralized quarantine management with multiple
F-Secure Internet Gatekeeper installations. For more information,
see “Scenario 4: Multiple F-Secure Internet Gatekeeper
installations with Centralized Quarantine Management”, 40
Note that the product does not support Windows Authentication
when connecting to Microsoft SQL Server 2000. The Microsoft
SQL Server 2000 that the product will use for the quarantine
database should be configured to use Mixed Mode
authentication.
If you plan to use Microsoft SQL Server 2000, you must
purchase it and obtain your own license before you start to
deploy F-Secure Internet Gatekeeper. To purchase Microsoft
SQL Server 2000, please contact your Microsoft reseller.
3.1.2 Web Browser Software Requirements
In order to administer the product with F-Secure Internet Gatekeeper W eb
Console, one of the following web browsers is required:
Microsoft Internet Explorer 6.0 or later
Netscape Communicator 7.1 or later
Mozilla 1.2 or later
Mozilla Firefox 1.5 or later
Opera 7.2 or later
Konqueror 2.1 or later
Any other web browser supporting HTTP 1.0, SSL, Java scripts and
cookies may be used as well. Microsoftc Internet Explorer 5.5 or earlier
cannot be used to administer the product.
Page 47

3.2 Centrally Administered or Stand-alone Installation?
F-Secure Internet Gatekeeper can be managed either locally with
F-Secure Internet Gatekeeper Web Console or centrally with F-Secure
Policy Manager Console. You can select the management method when
you install the product.
If you already use F-Secure Policy Manager to administer o ther F-Secure
products, it is recommended to install F-Secure Internet Gatekeeper in
centralized administration mode. The installation instructions in this
manual are for centrally managed installations. For more information
about centrally managed administration, see “Basics of Using F-Secure
Internet Gatekeeper”, 78.
The quarantined mails are managed using the F-Secure Internet
Gatekeeper Web Console in both centrally administered and
stand-alone installations. In centrally managed environments all
other features are managed with F-Secure Policy Manager.
Before you start to install F-Secure Internet Gatekeeper, uninstall any
potentially conflicting products, such as anti-virus, file encryption, and disk
encryption software that employ low-level device drivers. Close all
Windows applications before starting the installation.
CHAPTER 3 47
Installation
The release notes document contains the latest information about
the product and might have changes to system requirements and
the installation procedure. It is highly recommended to read the
release notes before you proceed with the insta llation.
3.2.1 Installation Overview for Centrally Administered Installation
If you want to administer F- Secure Internet Gatekeeper centrally, start by
installing F- Secure Policy Manager (if it is not already inst alled ) a nd then
install F- Secure Internet Gatekeeper.
Page 48

48
The general installation plan is as follows:
1. Install F- Secure Policy Manager Server and F-Secure Installation
Packages from F- Secure Policy Manager Setup.
For installation instructions, see the chapter Installing F-Secure Policy
Manager Server in F-Secure Policy Manager Administrator’s Guide.
2. Install F- Secure Policy Manager Console from F- Secure Policy
Manager Console Setup.
For installation instructions, see the chapter Installing F-Secure Policy
Manager Console in F-Secure Policy Manager Administrator’s Guide.
3. Run F- Secure Policy Manager Console for the first time to create the
management key pair and the policy domain. It is recommended to do
this immediately after installing F- Secure Policy Manager Console.
For instructions on how to generate the management key pair, see
the chapter Installing F-Secure Policy Manager Console in F-Secure
Policy Manager Administrator’s Guide. For instructions on how to
create the policy domain, see section Managing Domains and Hosts
in F-Secure Policy Manager Administrator’s Guide.
4. Install F- Secure Internet Gatekeeper. For the installation instructions,
go to “Installation Instructions”, 50.
5. Import the product MIB file to F-Secure Policy Manager, if they cannot
be uploaded there during the installation. For more information, see
“Importing Product MIB files to F-Secure Policy Manager Console”,
69.
6. Before you start using the system, check and configure settings for
F-Secure Content Scanner Server, F-Secure Anti-Virus for Internet
Mail, F-Secure Anti-Virus for Internet Gateways and F-Secure
Management Agent. Distribute the policy. For more information, see
“Configuring the Product”, 70.
7. Make sure the virus and spam defi nitio n databases ar e up da te d . For
more information, see “Updating Virus and Spam Definition
Databases”, 280.
Page 49

3.2.2 Installation Overview for Stand-alone Installation
The general installation plan is as follows:
1. Install F- Secure Internet Gatekeeper. See the installation instructions
in “Installation Instructions”, 50. Note that when F- Secure Internet
Gatekeeper is installed in stand-alone mode, some of the screens
included in these installation instructions will not be displayed.
2. Check and configure settings for F-Secure Content Scanner Server,
F-Secure Anti-Virus for Internet Mail, F-Secure Anti-Virus for Internet
Gateways and F-Secure Management Agent. For more information,
see “Configuring the Product”, 70.
3. Make sure the virus and spam defi nit ion databases ar e up da te d . Fo r
more information, see “Updating Virus and Spam Definition
Databases”, 280.
CHAPTER 3 49
Installation
Page 50

50
3.3 Installation Instructions
The installation instructions in this section are valid for both centrally
managed and stand-alone installations, but the options to select are
determined by the administration mode you are going to use. The
administration modes are explained in “Centrally Administered or
Stand-alone Installation?”, 47.
Step 1. Download and execute the installation p ackage. If you have the F-Secu re
CD, insert it in your CD-ROM drive and select F-Secure Internet
Gatekeeper from the Install Software menu.
Step 2. Read the information in the Welcome screen and click Next to continue.
Page 51

CHAPTER 3 51
Installation
Step 3. Read the License Agreement. If you accept the agreement, select the
I accept this agreement check box and click Next to continue.
Page 52

52
Step 4. Enter the product keycode and click Next to continue.
If you are installing the evaluation version, this screen is not
displayed.
Page 53

CHAPTER 3 53
Installation
Step 5. Installable components are displayed. The options available may vary
depending on the keycode you entered in the previous step. Select the
components to install and click Next to continue.
If you are installing only F-Secure Anti-Virus for Internet Gateways or
F-Secure Anti-Virus for Internet Mail, some of the following installation
steps are skipped.
Page 54

54
Step 6. Select the destination folder where you want to install F-Secure Internet
Gatekeeper components. Click Next to continue.
Page 55

Step 7. Select the administration method you want to use to manage your
F-Secure Internet Gatekeeper:
Select Centralized administration through network to use
F-Secure Policy Manager Console to remotely manage all
F-Secure Internet Gatekeeper components. For more
information, see “Basics of Using F-Secure Internet Gatekeeper”,
78.
If you want to manage F-Secure Internet Gatekeeper locally,
select Stand-alone installation.
CHAPTER 3 55
Installation
Click Next to continue.
Page 56
56
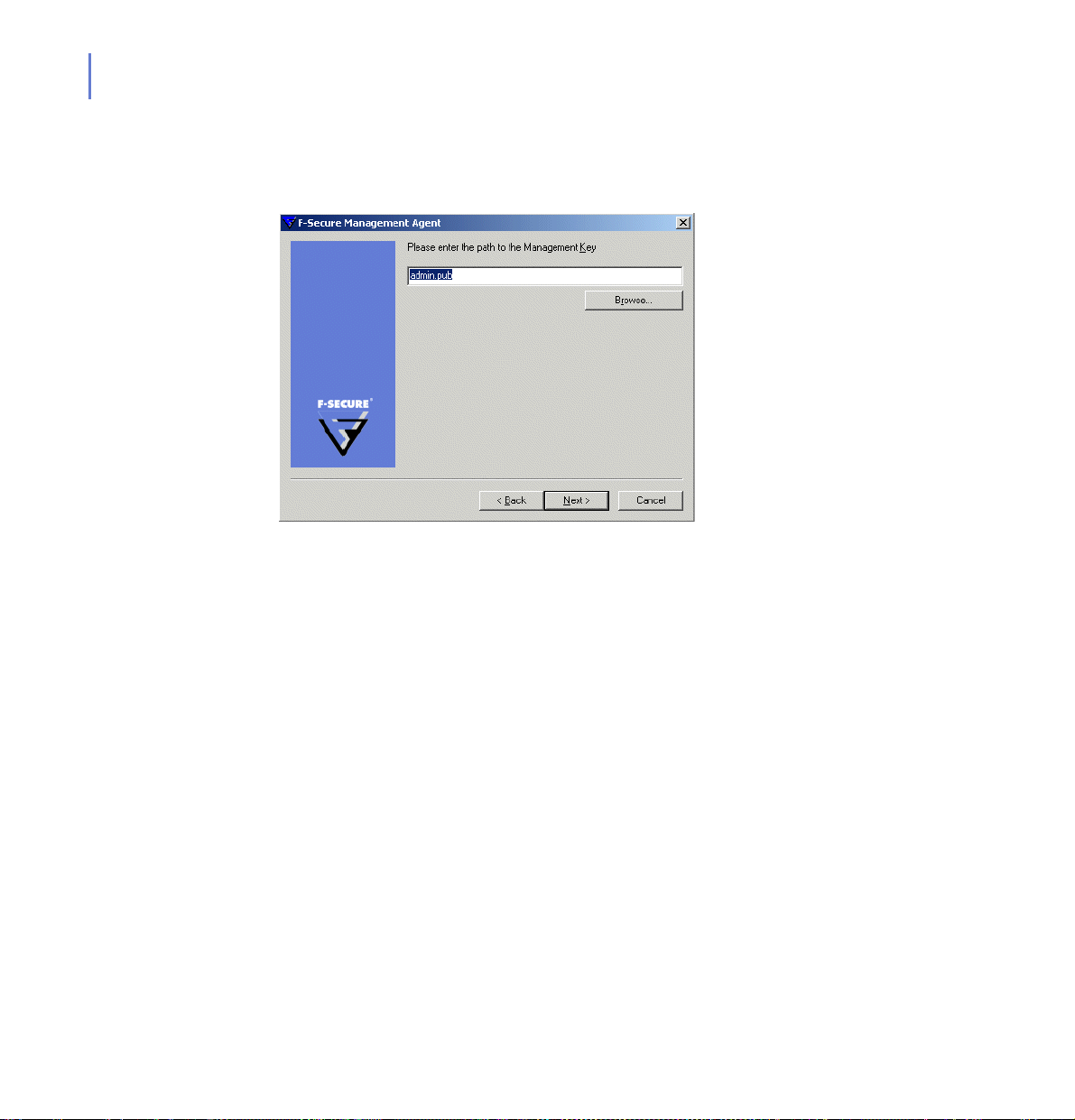
Step 8. Enter the path or click Browse to locate the management key. This is the
key that you created during the F-Secure Policy Manager Console Setup .
Click Next to continue.
Page 57

CHAPTER 3 57
Installation
Step 9. Select the network communication method. If you are using F-Secure
Policy Manager to manage F-Secure Internet Gatekeeper, select
F-Secure Policy Manager Server. Click Next to continue.
Page 58

58
Step 10. Enter the IP address of the F-Secure Policy Manager Server. Click Next
to continue.
Page 59

CHAPTER 3 59
Installation
Step 11. Specify the IP address or the DNS address and the administration TCP
port number (by default 8080) of F-Secure Policy Manager Server. The
administration port is used because the Setup program needs to upload
new MIB files to F-Secure Policy Manager Server. Click Next to continue.
If the product MIB files cannot be uploaded to F-Secure Policy
Manager Server during installation, you can import them manually.
For more information, see “Importing Product MIB files to F-Secure
Policy Manager Console”, 69.
Page 60

60
Step 12. Select the Quarantine Management mode:
If you have only one F-Secure Internet Gatekeeper instal lation, or
you do not want to manage quarantined e-mails centrally, select
the default option, Local quarantine management.
If you have multiple installations and you want to manage
quarantined e-mails centrally, select Centralized quarantine
management.
Centralized quarantine management can be used also when the
product is installed in stand-alone mode. Centralized quarantine
management does not depend on F-Secure Policy Mana ger in any
way.
Page 61

CHAPTER 3 61
Installation
Step 13. Specify where the SQL server database for storing quarantined content
should be created.
For small environments select the default option, Install and use
Microsoft SQL Server Desktop Engine (MSDE). This option
installs the quarantine database on the same server with
F-Secure Internet Gatekeeper.
If you select this option, the MSDE Installation Directory page will
be displayed next.
If you already have Microsoft SQL Server or Microsoft SQL
Server Desktop Engine (MSDE) installed, select the second
option.
The Microsoft SQL Server or MSDE can be on the same server
with F-Secure Internet Gatekeeper, or on a separate server. The
SQL server does not need to be dedicated for F-Secure Internet
Gatekeeper; it may be used for other purposes, too.
If you select this option, the SQL Server and Database Details
page will be displayed next.
Page 62

62
Step 14. a) Specify MSDE Installation Directory
Specify where the MSDE program and data files will be installed. Then
enter a password for the database server administrator account. Do not
leave the password empty. Re-enter the password in the Confirm
password field. F-Secure Internet Gatekeeper will use this account when
operating the quarantine database.
Page 63

CHAPTER 3 63
Installation
b) Specify SQL Server and Database Details
Enter the computer name of the SQL server , or click Browse to locate the
server. Then enter the database server administrator account and
password. The Setup will use them to connect the SQL server where the
quarantine database will reside.
Step 15. If you selected to install Microsoft SQL Server Desktop Engine (MSDE) in
Step 13 . , 61, the Setup installs it now. Wait until the installation is
complete.
If there has been a previous installation of MSDE on the same
computer, and the Setup detects an existing MSDE Data directory
that is not empty, you will be prompted to remove that directory
manually. For instructions, see http://support.microsoft.com/kb/
320873/EN-US/
Page 64

64
Step 16. The setup wizard displays a list of components to be installed. Click Start
to install the components to your computer.
Page 65

CHAPTER 3 65
Installation
Step 17. The setup wizard displays the progress of the installation. Wait until the
installation is ready.
Page 66
66
Step 18. The setup wizard displays the installation result for each component af ter
the installation is completed. Click Next to continue.
Page 67

Step 19. Click Finish to complete the installation.
If you were doing an upgrade installation and are prompted to
restart your computer, select Restart now. The new software
version will be operational after the restart.
CHAPTER 3 67
Installation
Page 68

68
Step 20. After the installation, the product updates virus definition databases
automatically. If the product is installed in centralized administration
mode, it downloads the new databases from the F-Secure Policy
Manager Server. If the product is installed in stand-alone mode, the
databases are downloaded directly from F-Secure's update servers
through the Internet.
If F-Secure Sp am Control is installed, the product updates Spam Control
databases automatically after the installation. F-Secure Spam Control
database updates are always downloaded directly from F-Secure's
update servers, even in centrally administered installations.
The product connects to the threat detection center immediately after the
installation.
If the company firewall blocks the Internet access or the Internet is not
reachable for some other reason, database update processes may fail.
For network traffic requirements, see “Network Requirements”, 28.
If database update processes fail, it is strongly recommended to update
the databases manually before the product is taken into use. For more
information, see “Updating Virus and Spam Definition Databases”, 280.
Page 69

CHAPTER 3 69
Installation
3.4 After the Installation
This section describes what you have to do after the installation to take
F-Secure Internet Gatekeeper into use.
3.4.1 Importing Product MIB files to F-Secure Policy Manager Console
If you are using the product in centrally managed mode, there are cases
when the F-Secure Internet Gatekeeper MIB JAR file cannot be uploaded
to F-Secure Policy Manager Server during the installation. In these cases
you will have to import the MIB files to F-Secure Policy Manager. You will
have to import the MIB files if:
F-Secure Internet Gatekeeper is located in a different network
segment than F-Secure Policy Manager, and there is a firewall
between them blocking access to Policy Manager’s
administrative port (8080).
F-Secure Policy Manager Server has been configured so that
administrative connections from anywhere else than the localhost
are blocked. This is the default F-Secure Policy Manager Server
configuration.
The recommended way is to import the MIBs via F-Secure Policy
Manager Console’s Tools menu. The F-Secure Internet Gatekeeper MIB
JAR file is located on the F-Secure CD in the \software\fsig\mibs\
directory. You can import the MIBs as follows:
1. Open the Tools menu and select the Installation packages... option.
2. Click Import....
3. When the Import Installation Packages dialog opens, browse to
locate the fsigk661mib.jar file. Then click Open.
4. After importing the new MIB files, restart F-Secure Policy Manager
Console.
Another possibility for importing the product MIBs is to run the
imptmib.exe utility from the F-Secure CD.
Page 70

70
3.4.2 Configuring the Product
By default, F-Secure Internet Gatekeeper has very strict access control
settings for security reasons. You have to configure F-Secure Internet
Gatekeeper before you can use it properly. Follow these instructions
before you start using F-Secure Internet Gatekeeper:
F-Secure Anti-Virus for Internet Mail
1. Make sure th at you defin e the int er na l ne two rk ad d resse s of yo ur
company with the Intranet Hosts setting. For more information, see
“Intranet Hosts”, 164.
2. Specify hosts that are allowed or not allowed to connect to F- Secure
Anti-Virus for Internet Mail in the Allowed hosts and Denied hosts
settings. For more information, see “SMTP Connections”, 146.
3. Configure the virus scanning to specify the type of traffic you want to
scan.
For mail traffic scanning, see “Configuring SMTP Traffic
Scanning”, 166.
Make sure that you limit users who are allowed to receive
e-mail messages to the users in the corporate network. For
more information, see “Receiving”, 166.
4. Configure mail delivery on the Mail Routing Table. For more
information, see “Mail Delivery”, 187.
F-Secure Anti-Virus for Internet Gateways
1. If you already have a web proxy in your network, check the proxy
chaining settings. For more information, see “Proxy Chaining”, 98.
2. Configure network and performance settings to make sure that
F-Secure Internet Gatekeeper works properly. For more information,
see “Configuring F-Secure Anti-Virus for Internet Gateways”, 94, and
“Configuring F-Secure Content Scanner Server”, 211.
Page 71

CHAPTER 3 71
Installation
3. Configure the virus scanning and access control settings to specify
the type of traffic you want to scan and sites where you want to deny
the access.
For HTTP and FTP-over-HTTP scanning, see “Configuring Web
Traffic Scanning”, 107.
Make sure that you specify which hosts are allowed to connect to
F-Secure Anti-Virus for Internet Gateways. For more information,
see “Connections to F-Secure Anti-Virus for Internet Gateways”,
123.
F-Secure Anti-Virus for Internet Gateways should be configured so
that it can be accessed only from trusted networks. This way, it is
possible to provide protection against attacks coming from the
Internet targeting F-Secure Internet Gatekeeper server.
Page 72

72
3.5 Upgrading F-Secure Internet Gatekeeper
This section describes the needed configuration changes, if any, when
upgrading F-Secure Internet Gatekeeper.
3.5.1 Upgrade Instructions
If you are using F-Secure Internet Gatekeeper 6.4x or 6.50, you can
upgrade it to F-Secure Internet Gatekeeper 6.61 without uninstalling the
previous version. The setup upgrades F-Secure Internet Gatekeeper
automatically and takes the previous settings into use.
IMPORTANT: F-Secure Internet Gate keeper 6.61 uses an upd ated
quarantine database schema. It is highly recommended that you
make a complete backup of the existing quarantine database
before the upgrade.
IMPORTANT: F-Secure Internet Gatekeeper 6.61 cannot
reprocess the e-mails and attachments quarantined by the version
6.4x. You should handle or delete these e-mails manually, using
Windows Explorer, before or after the upgrade. They are not
deleted during the upgrade installation.
Follow these instructions to upgrade F-Secure Internet Gatekeeper:
Step 1. Upgrade the product
1. Run the Setup wizard. For instructions, see ”Centrally Administered
or Stand-alone Installation?”, 47.
2. Depending on the F-Secure products that are installed on the system
already, the setup suggests upgrading several or all components.
Select the components you want to upgrade.
3. Specify how the inbound mail routing is to be handled. The table
displays the domain, IP address and port number information read
from the previous version’s configuration (see the example in the
figure below). You can also add a new inbound mail server.
Page 73

CHAPTER 3 73
Installation
Figure 3-1 Inbound Mail Routing Table displayed during F-Secure Internet
Gatekeeper upgrade
IMPORTANT: If this, or any other setting defined during the
installation needs to be changed later on, the setting must be
defined as Final in the F-Secure Policy Manager Console before
distributing the policies. This applies only to centrally administered
installations. Please note that the Final flag is used in a different
manner in most of the other F-Secure products.
Page 74

74
4. Specify how the outbound mail routing is to be handled. The table
displays the domain, IP address and port number information read
from the previous version’s configuration (see the example in the
figure below). You can also add the information for a new outbound
mail server.
Figure 3-2 Outbound Mail Routing Table displayed during F-Secure Internet
Gatekeeper upgrade
Page 75

CHAPTER 3 75
5. Specify the IP addresses and port numbers of primary F-Secure
Content Scanner Servers where F-Secure Anti-Virus for Internet Mail
sends files to be scanned.
Figure 3-3 Primary F-Secure Content Scanner Servers list displayed during
F-Secure Internet Gatekeeper upgrade
Installation
6. Specify the IP addresses and port numbers of backup F-Secure
Content Scanner Servers where F-Secure Anti-Virus for Internet Mail
sends files to be scanned when it cannot connect to primary servers.
7. After the components have been upgraded, select Restart now to
restart the computer immediately. Then click Finish to complete the
installation.The new software is op erational after the restart.
Step 2. Configure the product
Configure F-Secure Internet Gatekeeper. For more information, see
“Configuring F-Secure Anti-Virus for Internet Gateways”, 94, “Configuring
F-Secure Anti-Virus for Internet Mail”, 142 and “Configuring F-Secure
Content Scanner Server”, 211.
Page 76

76
Step 3. Update the virus definition databases
Update the virus definition databases. Normally this is done automatically.
For more information on updating the virus defin itio n da tabases, se e
“Updating Virus and Spam Definition Databases”, 280.
Step 4. Enable the mail delivery
Enable mail delivery again by returning the F-Secure Anti-Virus for
Internet Mail / Settings / Inbound Mail / Receiving / Accept Mail and
F-Secure Anti-Virus for Internet Mail / Settings / Outbound Mail /
Receiving / Accept Mail settings to normal.
Review Settings
Review the following settings after the upgrade:
Quarantine settings, see “Quarantine”, 151.
Notification settings and messages for virus scanning and
stripped and suspicious attachments, see “ Blocking”, 172 and
“Virus Scanning”, 177.
Spam Control settings, see “Spam Control Settings”, 242.
Virus outbreak settings, see “Virus Outbreak Response”, 182.
The new quarantine management query, reprocessing and database
options are available only with F-Secure Internet Gatekeeper Web
Console.
3.5.2 From the Try-Before-You-Buy Version
When you have obtained a license and a keycode for the full, licensed
version of F-Secure Internet Gatekeeper, you can upgrade the product in
one of the following ways:
a. When the Evaluation Version Activation or Evaluation Version
Expired dialog appears, click the Register Keycode button and
enter the keycode you received.
b. Run TNBUTIL utility as follows:
Page 77

3.6 Uninstallation
To uninstall F-Secure Internet Gatekeeper, select Add/Remove Programs
from the Windows Control Panel. To uninstall F-Secure Internet
Gatekeeper completely, uninstall the components in the following order:
F-Secure Anti-Virus for Internet Mail,
F-Secure Anti-Virus for Internet Gateways,
F-Secure Spam Control (if it was installed)
F-Secure Automatic Update Agent, (if it was installed)
F-Secure Content Scanner Server
Microsoft SQL Server Desktop Engine (MSDE) (if it was
CHAPTER 3 77
Installation
tnbutil.exe /KEYCODE:<full_keycod e>
where <full_keycode> is the keycode you received. TNBUTIL
can be found under %ProgramFiles%\F-Secure\TNB directory.
The product checks the license status every 10 minutes. The
licensed version of the product will be activated the next time the
product checks the current license status.
installed).
Some quarantined and locked files may remain in Quarantine and
working directories after you uninstall F-Secure Internet
Gatekeeper. Check and make sure that nothing important remains
in these directories before you delete them.
Page 78

BASICS OF USING
4
F-S
G
Introduction................................................................................. 79
Using F-Secure Policy Manager................................................. 79
Using F-Secure Internet Gatekeeper Web Console................... 82
ECURE INTERNET
ATEKEEPER
78
Page 79

Basics of Using F-Secure Internet Gatekeeper
4.1 Introduction
This chapter contains a brief introduction into using F-Secure Policy
Manager for administering F-Secure Internet Gatekeeper in centrally
managed installations. In addition, it describes how to monitor the status
of F-Secure Internet Gatekeeper components with the F-Secur e Internet
Gatekeeper Web Console.
Chapters 5-7 contain more detailed information on how you can configure
and administer F-Secure Internet Gatekeeper with F-Secure Policy
Manager.
4.2 Using F-Secure Policy Manager
If your corporate network utilizes F-Secure Policy Manager to configure
and manage F-Secure products, you can add F-Secure Internet
Gatekeeper to the existing F-Secure Policy Manager environment. In the
centralized administration mode, F-Secure Policy Manager Console is
used to change settings and view statistics of the F-Secure Internet
Gatekeeper.
CHAPTER 4 79
In the centralized administration mode you can open F-Secure Internet
Gatekeeper components from the Windows Start menu > Programs >
F-Secure Policy Manager Console. When the Policy Manager Console
opens, go to the Advanced Mode user interface by selecting View >
Advanced Mode (this step is required in F-Secure Policy Manager version
5.50 and later). Then select the Policy tab to view the F-Secure Internet
Gatekeeper components.
F-Secure Policy Manager Console is used to create policies for F-Secure
Anti-Virus for Internet Gateways, F-Secure Anti-Virus for Inte rnet Mail and
F-Secure Content Scanner Server which are running on se lected hosts or
groups of hosts. Policies are created by assigning values to variables
shown on the Policy tab of the Properties pane in F-Secure Policy
Manager Console. To assign a value, select a variable – marked by the
leaf icon – in the Properties pane (the middle p ane) and enter the value in
the Editor pane (the right pane).
Page 80

80
After a policy is created, it must be distributed to hosts by choosing
Distribute from the File menu.
The Status tab of the Properties pane shows statistics and the settings
that were configured during the installation of F-Secure Internet
Gatekeeper. Statistics are updated periodically and can be reset by
choosing Reset Statistics on the Policy tab of the Properties pane.
For a better view, you can enlarge the panes by dragging their borders.
For detailed information on installing and using F-Secure Policy Manager
Console, see the F-Secure Policy Manager Administrator’s Guide.
4.2.1 F-Secure Anti-Virus for Internet Gateways Settings
Use the variables under the F-Secure Anti-Virus for Internet Gateways /
Settings / branch to define settings for the F-Secure Anti-Virus for Internet
Gateways.
For detailed descriptions of F-Secure Anti-Virus for Internet Gateways
settings, see “Configuring F-Secure Anti-Virus for Internet Gateways”, 94.
For detailed descriptions of HTTP traffic scanning settings, see “Virus
Scanning”, 107.
4.2.2 F-Secure Anti-Virus for Internet Mail Settings
Use the variables under the F-Secure Anti-Virus for Internet Mail /
Settings / branch to define settings for the F-Secure Anti-Virus for Internet
Mail.
For detailed descriptions of F-Secure Anti-Virus for Internet Mail settings,
see “Configuring F-Secure Anti-Virus for Internet Mail”, 142. For detailed
descriptions of SMTP traffic scanning settings, see “Configuring F-Secure
Anti-Virus for Internet Mail”, 142.
4.2.3 F-Secure Content Scanner Server Settings
Use the variables under the F-Secure Content Scan ner Server / Settings /
branch to define settings for the F-Secure Content Scanner Server.
Page 81

CHAPTER 4 81
Basics of Using F-Secure Internet Gatekeeper
For detailed descriptions of F-Secure Content Scanner Server settings,
see “Configuring F-Secure Content Scanner Server”, 211.
4.2.4 F-Secure Management Agent Settings
Use the variables under the F-Secure Management Agent / Settings /
branch to define settings for the F-Secure Management Agent.
For detailed descriptions of F-Secure Management Agent settings, see
“F-Secure Management Agent Settings”, 252.
4.2.5 Changing Settings That Have Been Modified During Installation or Upgrade
If you want to change a setting that has been modified loca lly du rin g
installation or upgrade, you need to mark the setting as Final in the
restriction editor. The settings descriptions in this manual indicate the
settings for which you need to use the Final restriction. You can also
check in F-Secure Policy Manager Console whether you need to use the
Final restriction for a setting. Do the following:
1. Select the Policy tab and then select the setting you want to check.
2. Now select the Status tab to see if the setting has been modified
locally.
If the setting is not shown in grayed font in the Status view, then
the product uses the setting from the base policy an d th er ef or e
the Final restriction is not needed.
If the setting is shown in normal black font, then the setting has
been modified locally. You must mark the setting as Final when
you change it.
Page 82

82
4.3 Using F-Secure Internet Gatekeeper Web Console
In centrally managed installations of F-Secure Internet Gatekeeper, the
F-Secure Internet Gatekeeper Web Console can be used for monitoring
the system status and statistics. It can also be used for viewing the
settings currently in use and executing some operations. However, in
centrally managed installations it cannot be used for configuring the
system or scanning settings; use F-Secure Policy Manager for this
instead.
4.3.1 Logging in the F-Secure Internet Gatekeeper Web Console for the First Time
Before you log in the F-Secure Internet Gatekeeper Web Console for the
first time, check that Java script and cookies are enabled in the browser
you use.
F-Secure Internet Gatekeeper web user interface does not support
Microsoft Internet Explorer 5.0 or 5.5.
Microsoft Internet Explorer users:
The address of the F-Secure Internet Gatekeeper Web Console,
https://127.0.0.1:25023/, should be added to the Trusted sites in
Internet Explorer Security optio ns. This ensures that the F-Secure
Internet Gatekeeper Web Console works properly.
Page 83

CHAPTER 4 83
Basics of Using F-Secure Internet Gatekeeper
When you log in for the first time, your browser will display a Security Alert
dialog window about the security certificate for F-Secure Internet
Gatekeeper Web Console. You can create a security certificate for
F-Secure Internet Gatekeeper Web Console before logging in, and then
install the certificate during the login process.
If your company has an established process for creating and
storing certificates, you can follow that process to create and store
the security certificate for F-Secure Internet Gatekeeper Web
Console.
Step 1.Create the security certificate
1. Browse to the F-Secure Internet Gatekeeper Web Console
installation directory, for example:
C:\Program Files\F-Secure\F-Secure Internet Gatekeeper\Web User
Interface\bin\
2. Locate the certificate creation utility, makecert.bat, and double click it
to run the utility.
3. The utility creates a certificate that will be issued to all local IP
addresses, and restarts the F-Secure Internet Gatekeeper Web
Console service to take the certificate into use. Wait until the utility
completes, and the window closes. Now you can proceed to logging
in.
Step 2.Log in and install the security certificate
1. Select Programs > F-Secure Internet Gatekeeper > F-Secure Internet
Gatekeeper Web Console, or
enter the address of the F-Secure Internet Gatekeeper and the port
number in your web browser. Note that the protocol used is https. For
example:
https://127.0.0.1:25023
2. The Security Alert about the F-Secure Internet Gatekeeper Web
Console certificate is displayed. If you install the certificate now, you
will not see the Security Alert window again.
Page 84

84
If you are using Internet Explorer 7, click Continue and then
Certificate Error.
3. Click View Certificate to view the certificate information.
4. The Certificate window opens. Click Install Certificate to proceed to
the Certificate Import Wizard.
5. Follow the instructions in the Certificate Import Wizard.
If you are using Internet Explorer 7, in the Place all certificates in the
following store selection, select the Trusted Root Certification
Authorities store.
If you are using Internet Explorer 6, you are pr ompted to add the new
certificate in the Certificate Root Store when the wizard has
completed. Click Yes to do so.
6. If the Security Alert window is still displayed, click Yes to proceed or
log back in to the F-Secure Internet Gatekeeper Web Console.
Page 85

CHAPTER 4 85
Basics of Using F-Secure Internet Gatekeeper
7. When the login page opens, enter the user name and the password.
Note that you must have administrator rights to the host. Then click
Log In.
Figure 4-1 F-Secure Internet Gatekeeper Web Console Login page
8. You will be forwarded to the home p age, which displays a summary of
the system status.
Page 86

86
Figure 4-2 F-Secure Internet Gatekeeper Home page
4.3.2 Checking the Product Status
You can check the overall product status on the Home page. The Home
page displays a summary of the component statuses and most impor tant
statistics. From the Home page you can also open the product logs and
proceed to configure the product components.
This section describes the statistics and operations available on the
Home page.
Page 87

CHAPTER 4 87
Basics of Using F-Secure Internet Gatekeeper
F-Secure Anti-Virus for Internet Mail
The Home page displays the status the F-Secure Anti- Virus for Internet
Mail as well as a summary of the F-Secure Anti-Virus for Internet Mail
statistics.
Click Configure to configure F-Secure Anti-Virus for Internet Mail. For
more information, see “Configuring F-Secure Anti-V ir us for In tern et Mail ”,
142.
Click Show Mail Log to view the mail log.
F-Secure Anti-Virus for Internet Gateways
The Home page displays the status the F-Secure Anti- Virus for Internet
Gateways as well as a summary of the F-Secure Anti-Virus for Internet
Gateways statistics.
Click Configure to configure F-Secure Anti-Virus for Internet Gateways.
For more information, see “Configuring F-Secure Anti-Virus for Internet
Gateways”, 94.
Click Show Error Log to view the error log. Click Show Access Log to
view the access log.
Page 88

88
F-Secure Content Scanner Server
The Home page displays the status the F-Secure Cont ent Scanner
Server as well as a summary of the F-Secure Content Scanner Server
statistics.
Status indicator Shows the status of F-Secure Content
Scanner Server.
Last time virus definition
databases updated
Database update version Shows the version of the database update
Scanned files Shows how many files the server has
Last time infection found Shows the date and time when an infection
Click Configure to configure F-Secure Content Scanner Server. For more
information, see “Configuring F-Secure Content Scanner Server”, 211.
Shows the date and time when the virus
signature databases were last updated.
used by the product. The version is shown in
YYYY-MM-DD_NN format, where
YYYY-MM-DD is the release date of the
update and NN is the number of the update
for that day.
processed.
was found last time.
Page 89

CHAPTER 4 89
Basics of Using F-Secure Internet Gatekeeper
F-Secure Automatic Update Agent
Status indicator Shows the status of F-Secure Automatic
Update Agent.
Last update check Shows the last date and time when F-Secure
Automatic Update Agent polled the F-Sec ure
Update Server for new updates.
Next update check Shows the next date and time when
F-Secure Automatic Update Agent will poll
the F-Secure Update Server for new
updates.
Click Configure to configure F-Secure Automatic Update Agent. For
more information, see “Automatic Updates”, 281.
F-Secure Management Agent
Status indicator Shows the status of F-Secure Management
Agent.
Management method Shows if the host is standalone (configured
locally) or networked (at least sometimes
connected through a network or a temporar y
link).
Last connection to the
server
Click Configure to configure the F-Secure Managemen t Agen t. For more
information, see
Click Show F-Secure Log to view the F-Secure log file (LogFile.log) in a
new Internet browser window. You can then download and save the
LogFile.log for later use by clicking Download.
In centrally managed F-Secure Internet
Gatekeeper installations shows the last date
and time when F-Secure Management
Agent connected to F-Secure Policy
Manager Server.
Page 90

90
Click Export Settings to open a list of all F-Secure Internet Gatekeeper
Settings in a new Internet browser window. You can then save the file for
later use by selecting File > Save As....
Click Export Statistics to open a list of all F-Secure Internet Gatekeeper
Statistics in a new Internet browser window. You can then save or print
the file for later use by selecting File > Save As.....
Click Configure Console to configure the F-Secure Internet Gatekeeper
Web Console. For instructions, see “Configuring the F-Secure Internet
Gatekeeper Web Console”, 90.
Configuring the F-Secure Internet Gatekeeper Web Console
On the F-Secure Internet Gatekeeper Web Console Configuration page
you can specify settings for connections to the server. You can also open
the F-Secure Internet Gatekeeper Web Console access log from this
page.
Session timeout Specify the time how long a client can be
connected to the server. When the session
expires, the F-Secure Internet Gatekeeper
Web Console displays a warning. The
default value is 60 minutes.
Click Show Access Log to view the F-Secure Internet Gatekeeper Web
Console access log. Note that the Web Console access log differs from
standard web server access logs, as it logs only the first request per
session.
Listen on Specify the IP address of the F-Secure
Internet Gatekeeper Web Console Server.
Port Specify the port where the server listens for
connections. The default port is 25023.
Accept connections from
the following hosts
Specify a list of hosts which are allowed to
connect to F-Secure Internet Gatekeeper
Web Console.
Page 91

CHAPTER 4 91
Basics of Using F-Secure Internet Gatekeeper
To add a new host in the list, click Add to add new a new line in the table
and then enter the IP address of the host.
Page 92

ADMINISTERING
5
F-S
FOR INTERNET
G
Overview - HTTP Scanning........................................................ 93
Configuring F-Secure Anti-Virus for Internet Gateways............. 94
Configuring Web Traffic Scanning............................................ 107
Monitoring Logs........................................................................ 127
Viewing Statistics...................................................................... 130
Examples of HTTP Notifications............................................... 136
ECURE ANTI-VIRUS
ATEWAYS
92
Page 93

Administering F-Secure Anti-Virus for Internet Gateways
5.1 Overview - HTTP Scanning
F-Secure Anti-Virus for Internet Gateways takes care of HTTP traffic
scanning. This chapter describes how to configure and administer
F-Secure Anti-Virus for Internet Gateways.
F-Secure Anti-Virus for Internet Gateways is an HTTP proxy server and
acts as a gateway between the corporate network and the Internet.
Before you start using F-Secure Anti-Virus for Internet Gateways,
configure the general settings under the Network Configuration and
Logging branches to make sure that F-Secure Anti-Virus for Internet
Gateways works properly. You should modify the ge neral settings when
your network infrastructure changes or when you want to optimize the
security or the performance of F-Secure Anti-Virus for Internet Gateways.
If you want to configure the virus scanning and access control settings to
specify the type of traffic you want to scan and sites you want to deny
access, see “Configuring Web Traffic Scanning”, 107.
In centrally managed mode you can open F-Secure Internet Gatekeeper
components from the Windows S tart menu > Programs > F-Secure Policy
Manager Console. When the Policy Manager Console opens, go to the
Advanced Mode user interface by selecting View > Advanced Mode.
Then select the Policy tab and the F-Secure Anti-Virus for Internet
Gateways component.
CHAPTER 5 93
Page 94

94
5.2 Configuring F-Secure Anti-Virus for Internet Gateways
Change the F-Secure Anti-Virus for Internet Gateways settings to set up
the working directory, connection, logging and advanced settings. For
information on how to change HTTP scanning settings, see “Content
Control”, 107.
After you have configured F-Secure Anti-Virus for Internet Gateways you
can use the Export Settings functionality on the F-Secure Internet
Gatekeeper Web Console Home page to get a full list of the modified
settings for later use. For more information, see “
Status”, 86
The F-Secure Content Scanner settings also have an effect on how the
HTTP and FTP-over-HTTP traffic is scanned. The default settings apply
in most system configurations, but it might be a good idea to check that
they are valid for your system.
.
Checking the Product
5.2.1 Network Configuration
You can configure the network settings in F-Secure Anti-Virus for Internet
Gateways / Settings / Network Configuration.
All HTTP settings apply also to FTP-over-HTTP.
Binding
You can define how F-Secure Anti-Virus for Internet Gateways listens to
requests that come from the end users or down-stream proxies from the
F-Secure Anti-Virus for Internet Gateways / Settings / Network
Configuration / Binding branch.
Page 95

CHAPTER 5 95
Administering F-Secure Anti-Virus for Internet Gateways
Figure 5-1 Network Configuration / Binding settings
Listen Specify the port that F-Secure Anti-Virus for
Internet Gateways should listen to for
incoming HTTP requests. Users must have
this port configured in the web browser proxy
settings. By default, the listen port is 3128.
If the product is running on a multi-homed
host, you can also specify the IP address it
should listen for incoming requests. Enter it
before the port number and sep arate it with a
colon. Example: <ip_address>:<port>.
Allow CONNECT ports Specify a list of ports for which the proxy
CONNECT method is allowed. Separate
each entry with a space.
Page 96

96
Usually the proxy CONNECT method is
used when a web browser requests an
HTTPS connection through an HTTP proxy.
By default, the CONNECT method is allowed
to port 443 (HTTPS port).
For more detailed information about the
proxy CONNECT method, see http://
www.kb.cert.org/vuls/id/150227.
IMPORTANT: Traffic that passes through
ports that you list in the Allow CONNECT
ports field passes through th e F-Secure
Anti-Virus for Internet Gateways without
scanning.
Connection
You can configure the timeout and persistent connections settings from
F-Secure Anti-Virus for Internet Gateways / Settings / Network
Configuration / Connection.
Figure 5-2 Network Configuration / Connection settings
Page 97

CHAPTER 5 97
Administering F-Secure Anti-Virus for Internet Gateways
Timeout
Keep alive
Specify how long (in seconds) F-Secure
Anti-Virus for Internet Gateways waits for
response from the web server before it
timeouts. The connection can timeout while:
Requesting web page contents (sendin g an
HTTP GET request).
Sending data to bulletin boards, newsgroup s
and mailing lists and submitting forms
(sending HTTP POST and PUT requests).
Maintaining reliable communication by
sending positive acknowledgments that TCP
packets have arrived (the time between
ACKs on TCP packets i n responses).
Specify whether persistent connections are
allowed or not. If you allow persistent
connections, connections from clients to
F-Secure Anti-Virus for Internet Gateways
are not automatically closed after each
request. For more information how to
optimize Keep alive settings, see
“Optimizing Performance”, 277.
Keep alive timeout
Maximum keep alive
requests
Specify how long F-Secure Anti-Virus for
Internet Gateways should wait for the next
request from the client using the persistent
connection before the connection is closed.
Specify how many requests one connection
can have when Keep alive is enabled. After
a client has made the specified amount of
requests, the connection is closed and a new
connection is opened for the next request.
Page 98

98
Max connections per host
If the value is set to 0, a connection can have
an unlimited amount of requests. Set
Maximum keep alive requests to high for
maximum server performance.
Specify the maximum number of
simultaneous connections that F-Secure
Anti-Virus for Internet Gateways accepts
from a particular host. Should th er e be m ore
incoming connections from this host than the
specified value, the excess connections will
be rejected. Zero (0) means no limit.
If the F-Secure Anti-Virus for Internet
Gateways is chained with a downstream
proxy, the maximum number of connections
accepted from a host may need to be
increased to avoid network connection
errors on hosts interacting with the
downstream proxy.
Proxy Chaining
If you use an existing upstream proxy server in your corporate network,
you can set up Proxy Chaining. F-Secure Anti-Virus for Internet Gateways
can forward all requests to the existing proxy server. You can configure
these settings from F-Secure Anti-Virus for Internet Gateways / Settings /
Network Configuration / Proxy Chaining.
The proxy chaining settings are applicable only if F-Secure Internet
Gatekeeper is installed as a downstream proxy.
Page 99

CHAPTER 5 99
Administering F-Secure Anti-Virus for Internet Gateways
Figure 5-3 Network Configuration / Proxy Chaining settings
Remote proxy server Specify the address and port number of the
proxy server where F-Secure Anti-Virus for
Internet Gateways forwards all requests.
Specify the address in format
“hostname[:port]”. Leave the field empty if
you do not want to forward requests.
No proxy Specify a space-separated list of IP
addresses, subnets, hosts and domains. A
request to a host which matches one or
more of these is always served directly,
without forwarding to the configured remote
proxy server. For more information, see
“Specifying Hosts”, 300.
Proxy domain Specify the default domain name for the
proxied requests. If F-Secure Anti-Virus for
Internet Gateways encounters a request to a
host without a domain name, it generates a
redirection response to the same domain
with the configured domain appended.
For example, if a request is http://intra and
the Proxy Domain value is set to
example.com, the request is forwarded to
http://intra.example.com.
Page 100

100
Proxy max forwards Specify the maximum number of proxies
through which a single request may pass.
Setting a maximum number of proxy
forwards prevents infinite proxy loops and
denial of service attacks. By default, the
value is 10.
Proxy Via Specify how HTTP/1.1 V ia headers should
be handled. Via headers can be used to
control the flow of proxy requests in a proxy
server chain.
Off - Via headers are not processed in any
way. If a request or reply contains a Via
header, it passes through F-Secure
Anti-Virus for Internet Gateways unchanged.
On - For each reply and request that passes
through F-Secure Anti-Virus for Internet
Gateways, via information is appended to
the Via header line.
Full - For each reply and request that passes
through F-Secure Anti-Virus for Internet
Gateways, via information is appended to
the Via header line and each generated Via
header has the proxy server version shown
in the comment field.
Block - F-Secure Anti-Virus for Internet
Gateways removes previous Via headers
from all outgoing messages and does not
generate new ones. Incoming message
headers are not processed.
By default, HTTP Via headers are off.
Adding new Via headers to request s may b e
a security risk, as they are sent in clear text
format in the Internet.
 Loading...
Loading...