Page 1

F-Secure Anti-Virus for
Microsoft Exchange
Administrator’s Guide
Page 2

"F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure
product names and symbols/logos are either trademarks or registered trademarks of F-Secure
Corporation. All product names referenced herein are trademarks or registered trademarks of their
respective companies. F-Secure Corporation disclaims proprietary interest in the marks and names of
others. Although F-Secure Corporation makes every effort to ensure that this information is accurate,
F-Secure Corporation will not be liable for any errors or omission of facts contained herein. F-Secure
Corporation reserves the right to modify specifications cited in this document without prior notice.
Companies, names and data used in examples herein are fictitious unless otherwise noted. No part of
this document may be reproduced or transmitted in any form or by any means, electronic or
mechanical, for any purpose, without the express written permission of F-Secure Corporation.
Copyright © 1993-2006 F-Secure Corporation. All rights reserved.
Portions Copyright © 1991-2006 Kaspersky Lab.
This product includes software developed by the Apache Software Foundation (http://
www.apache.org/). Copyright © 2000-2006 The Apache Software Foundation. All rights reserved.
This product includes PHP, freely available from http://www .php.net/. Copyright © 1999-2006 The PHP
Group. All rights reserved.
This product includes code from SpamAssassin. The code in the files of the SpamAssassin distribution
are Copyright © 2000-2002 Justin Mason and others, unless specified otherwise in that particular file.
All files in the SpamAssassin distribution fall under the same terms as Perl itself, as described in the
“Artistic License”.
This product may be covered by one or more F-Secure patents, including the following:
GB2353372 GB2366691 GB2366692 GB2366693 GB2367933 GB2368233
GB2374260
12000040-7B15
Page 3

Contents
About This Guide 9
How This Guide Is Organized ............................................................................................ 10
Conventions Used in F-Secure Guides.............................................................................. 12
Symbols .................................................................................................................... 12
Chapter 1 Introduction 14
1.1 Overview....................................................................................................................15
1.2 How F-Secure Anti-Virus for Microsoft Exchange Works........................... ... ... .... ... ...16
1.3 Key Features..............................................................................................................19
1.4 F-Secure Anti-Virus Mail Server and Gateway Products ...........................................21
Chapter 2 Deployment 23
2.1 Installation Modes......................................................................................................24
2.2 Network Requirements...............................................................................................24
2.3 Deployment Scenarios...............................................................................................25
2.3.1 Minimum Installation...... .... .............................................................................25
2.3.2 Medium to Large Installation ............. .............................................................27
2.3.3 Performance-Critical Installation.....................................................................28
2.3.4 Microsoft Exchange Cluster Environment ......................................................30
Chapter 3 Installation 32
3.1 System Requirements...................... ... ... .... ... .............................................................33
3.1.1 Minimum System Requirements..................................... ... ... .... ......................33
3.1.2 Which SQL Server to Use for the Quarantine Database?..............................35
3
Page 4

3.1.3 Web Browser Software Requirements ...........................................................36
3.2 Improving Reliability and Performance ......................................................................37
3.3 Centrally Administered or Stand-alone Installation? ..... ... ....... ... ... ... .... ... ... ... ... .... ... ...38
3.4 Installation Overview..................................................................................................38
3.5 Installing F-Secure Anti-Virus for Microsoft Exchange......................... ... ... ... ... .... ... ...40
3.6 After the Installation ...................................................................................................59
3.6.1 Importing Product MIB files to F-Secure Policy Manager Console.................59
3.6.2 Configuring the Product..................................................................................60
3.7 Upgrading the Previous Version ............................. ... ................................................60
3.8 Upgrading the Evaluation Version................. ... ... .... ... ... ... ..........................................63
3.9 Uninstalling F-Secure Anti-Virus for Microsoft Exchange ..........................................64
Chapter 4 Using F-Secure Anti-Virus for Microsoft Exchange 65
4.1 Overview....................................................................................................................66
4.2 Administering F-Secure Anti-Virus for Microsoft Exchange .......................................66
4.3 Using the Web Console .............................................................................................67
4.3.1 Logging in for the First Time................. ... .... ... ... ... ..........................................67
4.4 Checking the Product Status......................................................................................70
4.5 Configuring the Web Console................ .... ... ... ... .... ...................................................73
4.6 Using F-Secure Policy Manager Console ..................................................................74
4.7 Modifying Settings and Viewing Statistics..................................................................75
4.7.1 Centrally Administered Mode .........................................................................75
4.7.2 Stand-alone Mode..........................................................................................76
4.8 Manually Processing Mailboxes and Public Folders..................................................77
4.8.1 Centrally Administered Mode .........................................................................77
4.8.2 Stand-alone Mode..........................................................................................86
4.8.3 Creating Scanning Operations ....... ... ... ... .... ... ................................................87
4.9 Configuring Alert Forwarding ...................................................................................119
4.9.1 Centrally Administered Mode .......................................................................119
4.9.2 Stand-Alone Mode........................................................................................122
4.10 Viewing Alerts ..........................................................................................................123
4
Page 5

Chapter 5 Centrally Managed Administration 125
5.1 Overview..................................................................................................................126
5.2 F-Secure Anti-Virus for Microsoft Exchange Settings..............................................126
5.2.1 Real-Time Processing..................................................................................128
5.2.2 Manual Processing.......................................................................................159
5.2.3 Scheduled Processing..................................................................................174
5.2.4 Content Scanner Servers........................................ .... ... ... ... .... ....................175
5.2.5 Quarantine....................................................................................................178
5.2.6 Reporting......................................................................................................182
5.2.7 Advanced......................................................................................................182
5.3 F-Secure Anti-Virus for Microsoft Exchange Statistics.............................................184
5.3.1 Common.......................................................................................................185
5.3.2 Real-Time Processing..................................................................................186
5.3.3 Manual Processing.......................................................................................189
5.3.4 Quarantine....................................................................................................192
5.4 F-Secure Content Scanner Server Settings.............................................................193
5.4.1 Interface........................................................................................................195
5.4.2 Virus Scanning.............. .... ... ... .....................................................................196
5.4.3 Virus Statistics................... ... ... .....................................................................199
5.4.4 Database Updates........................................................................................201
5.4.5 Spam Filtering..............................................................................................202
5.4.6 Threat Detection Engine.......... ... .... ... ...........................................................204
5.4.7 Proxy Configuration......................................................................................205
5.4.8 Advanced......................................................................................................206
5.5 F-Secure Content Scanner Server Statistics ...........................................................208
5.5.1 Server...........................................................................................................208
5.5.2 Scan Engines ...............................................................................................209
5.5.3 Common.......................................................................................................210
5.5.4 Spam Control................................................................................................210
5.5.5 Virus Statistics................... ... ... .....................................................................211
5.6 F-Secure Automatic Update Agent Settings ............................................................212
5.7 F-Secure Management Agent Settings....................................................................214
Chapter 6 Administration with Web Console 216
6.1 Overview..................................................................................................................217
5
Page 6

6.2 F-Secure Anti-Virus for Microsoft Exchange Settings..............................................218
6.2.1 Summary......................................................................................................218
6.2.2 Virus Scanning.............. .... ... ... .....................................................................220
6.2.3 Stripping Attachments ............. .....................................................................236
6.2.4 Content Filtering................................... ... .... ... ... ... ... .....................................246
6.2.5 Manual Scanning..........................................................................................253
6.2.6 Quarantine....................................................................................................257
6.2.7 Advanced......................................................................................................267
6.2.8 Internal Domains............... ... ... ... ..................................................................2 73
6.3 F-Secure Content Scanner Server Settings.............................................................275
6.3.1 Summary......................................................................................................275
6.3.2 Database Updates........................................................................................282
6.3.3 Scan Engines ...............................................................................................284
6.3.4 Proxy Configuration......................................................................................289
6.3.5 Archive Scanning.................................. ... .... ... ... ... ........................................292
6.3.6 Advanced......................................................................................................295
6.3.7 Interface........................................................................................................297
6.4 F-Secure Automatic Update Agent Settings ............................................................298
6.4.1 Summary......................................................................................................299
6.4.2 Automatic Updates.......................................................................................301
6.4.3 PM Proxies...................................................................................................303
6.5 F-Secure Management Agent Settings....................................................................304
Chapter 7 Quarantine Management 307
7.1 Introduction ..............................................................................................................308
7.2 Configuring Quarantine Options...............................................................................309
7.3 Searching the Quarantined Content.........................................................................310
7.4 Query Results Page................................................ ... ... ... ... .... ... ... ...........................3 14
7.5 Viewing Details of a Quarantined Message .............................................................316
7.6 Reprocessing the Quarantined Content...................................................................318
7.7 Releasing the Quarantined Content.........................................................................319
7.8 Removing the Quarantined Content.........................................................................321
7.9 Deleting Old Quarantined Content Automatically.....................................................321
7.10 Quarantine Logging..................................................................................................322
7.11 Quarantine Statistics................................................................................................323
6
Page 7

7.12 Moving the Quarantine Storage ...............................................................................324
Chapter 8 Administering F-Secure Spam Control 326
8.1 Overview..................................................................................................................327
8.2 Spam Control Settings in Centrally Managed Environments ...................................328
8.3 Spam Control Settings in Web Console...................................................................331
8.4 Realtime Blackhole List Configuration .....................................................................336
8.4.1 Enabling Realtime Blackhole Lists ...............................................................336
8.4.2 Optimizing F-Secure Spam Control Performance........................................338
Chapter 9 Updating Virus and Spam Definition Databases 340
9.1 Overview..................................................................................................................341
9.2 Automatic Updates with F-Secure Automatic Update Agent....................................341
9.3 Configuring Automatic Updates ...............................................................................342
9.4 Manual Updates.......................................................................................................342
9.4.1 Using FSUPDATE........................................................................................342
9.4.2 Updating the Virus Definition Database Remotely Using LATEST.ZIP........343
AppendixA Deploying the Product on a Cluster 344
A.1 System and Network Recommendations................................................................ 345
A.2 Installation Overview................................................................................................347
A.3 Creating Quarantine Storage..................................... ... ... ... .... .................................348
A.3.1 Quarantine Storage in Active-Passive Cluster .............................................348
A.3.2 Quarantine Storage in Active-Active Cluster ................................................353
A.4 Installing the Product........................................... .....................................................356
A.4.1 Installing on Active-Passive Cluster .............................................................356
A.4.2 Installing on Active-Active Cluster ................................................................358
A.5 Administering the Cluster Installation with F-Secure Policy Manager......................360
A.6 Using the Quarantine in the Cluster Installation.......................................................363
A.7 Troubleshooting .......................................................................................................363
AppendixB Variables in Warning Messages 364
List of Variables................................................................................................................ 365
Outbreak Management Alert Variables............................................................................ 367
7
Page 8

AppendixC Services and Processes 368
Chapter D Troubleshooting 374
D.1 Overview..................................................................................................................375
D.2 Starting and Stopping...............................................................................................375
D.3 Viewing the Log File.................................................................................................375
D.4 Common Problems and Solutions............................................................................376
D.4.1 Installing Service Packs............................................................... ...... ... .... ... .379
D.4.2 Securing the Quarantine................................................. ... ... .... ... .................379
D.4.3 Administration Issues...................................................................................380
D.5 Frequently Asked Questions....................................................................................381
D.6 F-Secure Automatic Update Agent Troubleshooting................................................386
Technical Support 392
F-Secure Online Support Resources ............................................................................... 393
Web Club ....................... ... ...............................................................................................395
Virus Descriptions on the Web .........................................................................................395
8
Page 9

ABOUT THIS GUIDE
How This Guide Is Organized.................................................... 10
Conventions Used in F-Secure Guides..................................... 13
9
Page 10

10
How This Guide Is Organized
F-Secure Anti-Virus for Microsoft Exchange Administrator's Guid e is
divided into the following chapters:
Chapter 1. Introduction. General information about F-Secure Anti-V irus
for Microsoft Exchange and other F-Secure Anti-Virus Mail Server and
Gateway products.
Chapter 2. Deployment. Instructions and examples how to set up your
network environment before you can install F-Secure Anti-Virus for
Microsoft Exchange.
Chapter 3. Installation. Instructions how to install and set up F-Secure
Anti-Virus for Microsoft Exchange.
Chapter 4. Using F-Secure Anti-Virus for Microsoft Exchange.
Instructions how to use and administer F-Secure Anti-Virus for Microsoft
Exchange.
Chapter 9. Updating V irus and Sp am Definition Databases . Instructions
how to update your virus definition database.
Chapter 5. Centrally Managed Administration. Instructions how to
remotely administer F-Secure Anti-Virus for Microsoft Exchange and
F-Secure Content Scanner Server when they have been installed in
centralized administration mode.
Chapter 6. Administration with Web Console. Instructions how to
administer F-Secure Anti-Virus for Microsoft Exchange with the Web
Console.
Chapter 8. Administering F-Secure Spam Control. General information
about and instructions on how to configure F-Secure Spam Control.
Appendix A. Deploying the Product on a Cluster. Describes how the
product can be deployed and used on the cluster environment.
Appendix B. Variables in Warning Messages. Lists variables that can
be included in virus warning messages.
Appendix C. Services and Processes. Describes services, devices and
processes of F-Secure Anti-Virus for Microsoft Exchange.
Page 11

About This Guide 11
Chapter D. Troubleshooting. Solutions to some common problems.
Technical Support. Contains the contact information for assistance.
About F-Secure Corporation. Describes the company backgrou nd and
products.
See the F-Secure Policy Manager Administrator's Guide for detailed
information about installing and using the F-Secure Policy Manager
components:
F-Secure Policy Manager Console, the tool for remote
administration of F-Secure Anti-Virus for Microsoft Exchange.
F-Secure Policy Manager Server, which enables communication
between F-Secure Policy Manager Console and the managed
systems.
Page 12
12
Conventions Used in F-Secure Guides
This section describes the symbols, fonts, and terminology used in this
manual.
Symbols
WARNING: The warning symbol indicates a situation with a
risk of irreversible destruction to data.
IMPORTANT: An exclamation mark provides important information
that you need to consider.
REFERENCE - A book refers you to related information on the
topic available in another document.
NOTE - A note provides additional information that you should
consider.
l
Fonts
TIP - A tip provides information that can help you perf or m a task
more quickly or easily.
⇒ An arrow indicates a one-step procedure.
Arial bold (blue) is used to refer to menu names and commands, to
buttons and other items in a dialog box.
Arial Italics (blue) is used to refer to other chapters in the manual, book
titles, and titles of other manuals.
Arial Italics (black) is used for file and folder names, for figure and table
captions, and for directory tree names.
Courier New is used for messages on your compute r screen.
Page 13

Courier New bold is used for information that you must type.
SMALL CAPS (BLACK) is used for a key or key combination on your
keyboard.
13
PDF Document
For More Information
Arial underlined (blue)
Arial italics is used for window and dialog box names.
This manual is provided in PDF (Portable Document Format). The PDF
document can be used for online viewing and printing using Adobe®
Acrobat® Reader. When pr inting the manual, please print the entire
manual, including the copyright and disclaimer statements.
Visit F-Secure at http://www.f-secure.com for documentation, training
courses, downloads, and service and supp o rt contacts.
In our constant attempts to improve our documentation, we would
welcome your feedback. If you have any questions, comments, or
suggestions about this or any other F-Secure document, please conta ct
us at documentation@f-secure.com
is used for user interface links.
.
Page 14

1
INTRODUCTION
Overview..................................................................................... 15
How F-Secure Anti-Virus for Microsoft Exchange Works........... 16
Key Features.............................................................................. 19
F-Secure Anti-Virus Mail Server and Gateway Products............ 21
14
Page 15

1.1 Overview
CHAPTER 1 15
Introduction
Malicious code, such as computer viruses, is one of the main threats for
companies today. In the past, malicious code spread mainly via disks and
the most common viruses were the ones that infected disk boot sectors.
When users began to use office applications with macro capabilities such as Microsoft Office - to write documen t s and distribu te them via mail
and groupware servers, macro viruses started spreading rapidly.
After the millennium, the most common spreading mechanism has been
the e-mail. Today about 90% of viruses arrive via e-mail. E-mails provide
a very fast and efficient way for viruses to spread themselves without any
user intervention and that is why e-mail worm outbreaks, like Sober,
Netsky and Bagle, have caused a lot of damage around the world.
F-Secure Anti-Virus Mail Server and Gateway products are designed to
protect your company's mail and groupware servers and to shield the
company network from any malicious code that travels in HTTP or SMTP
traffic. In addition, they protect your company network against spam. The
protection can be implemented on the gateway level to screen all
incoming and outgoing e-mail (SMTP), web surfing (HTTP and
FTP-over-HTTP) and file transfer (FTP) traffic. Furthermore, it can be
implemented on the mail server level so that it does not only protect
inbound and outbound traffic but also internal mail traffic and public
sources, such as Public Folders on Microsoft Exchange servers.
Providing the protection already on the gateway level has plenty of
advantages. The protection is easy and fast to set up and install,
compared to rolling out antivirus protection on hundreds or thousands of
workstations. The protection is also invisible to the end users which
ensures that the system cannot be by-passed and makes it easy to
maintain. Of course, protecting the gateway level alone is not enough to
provide a complete antivirus solution; file server and workstation level
protection is needed, also.
Why clean 1000 workstations when you can clean one attachment at the
gateway level?
Page 16

16
1.2 How F-Secure Anti-Virus for Microsoft Exchange Works
F-Secure Anti-Virus for Microsoft Exchange is designed to detect and
disinfect viruses and other malicious code from e-mail transmissions
through Microsoft Exchange 2000/2003 Server. Scanning is done in real
time as the mail passes through Microsoft Exchange Server. On-demand
scanning of user mailboxes and Public Folders is also available.
Scanning
Attachments and
Message Bodies
Flexible and Scalable
Anti-Virus Protection
F-Secure Anti-Virus for Microsoft Exchange scans attachments and
message bodies for malicious code. It can also be instructed to remove
particular attachments according to the file name or the file extension. In
addition, it can filter out messages containing keywords that have been
defined as disallowed.
If the intercepted mail contains malicious code, F-Secure Anti-Virus for
Microsoft Exchange can be configured to disinfect or drop the content.
Any malicious code found during the scan process can be placed in the
Quarantine, where it can be further examined. Stripped attachments can
also be placed in the Quarantine for further examination.
F-Secure Anti-Virus for Microsoft Exchange is installed on Microsoft
Exchange 2000/2003 Server and it intercepts mail traveling through
mailboxes and Public folders. Intercepted attachments and documents
are sent to F-Secure Content Scanner Server, which returns disinfected
files back to F-Secure Anti-Virus for Microsoft Exchange.
The two-component product architecture ensures that the anti-virus
protection does not increase the load on the protected system and that
the infected data is never stored on the production network. It also
enables you to implement a server pool, so you can share the traffic load
between multiple F-Secure Content Scanner Servers and have backup
servers if the traffic to primary servers stops for some reason.
Page 17

Alerting F-Secure Anti-Virus for Microsoft Exchange has extensive alerting
functions, which means that the system administrator can specify a
recipient inside the company network to be notified about the infection
found in the data content. Of course, the network administrator can be
notified about the infection also.
CHAPTER 1 17
Introduction
Powerful and Always
Up-to-date
Virus and Spam
Outbreak Detection
Stand-alone and
Centralized
Administration Modes
F-Secure Anti-Virus for Microsoft Exchange uses the award-winning
F-Secure Anti-Virus scanner to ensure the highe st possible detection rate
and disinfection capability. The daily F-Secure Anti-Virus signature
database updates provide F-Secure Anti-Virus for Microsof t Exchange an
always up-to-date protection capability.
F-Secure Anti-Virus scanner consistently r anks at the top when compar ed
to competing products. Our team of dedicated virus resea rchers is on call
24-hours a day responding to new and emerging threats. In fact,
F-Secure is one of the only companies to release tested virus definition
updates on a daily basis, to make sure our customers are receiving the
highest quality service and protection.
Massive spam and virus outbreaks consist of millions of messages which
share at least one identifiable pattern that can be used to distinguish the
outbreak. Any message that contains one or more of these patterns can
be assumed to be a part of the same spam or virus outbreak.
F-Secure Anti-Virus for Microsoft Exchange can identify these patterns
from the message envelope, headers and body, in any language,
message format and encoding type. It can detect spam messages and
new viruses during the first minutes of the outbreak.
F-Secure Anti-Virus for Microsoft Exchange can be installed either in
stand-alone or centrally administered mode. Depending on how it has
been installed, F-Secure Anti-Virus for Microsoft Exchange is managed
either with the Web Console or F-Secure Policy Manager.
Scalability and
Reliability
F-Secure Policy Manager provides a scalable way to manage the security
of multiple applications on multiple operating systems, from one central
location. F-Secure Policy Manager is comprised of two components,
F-Secure Policy Manager Console and F-Secure Policy Manager Server,
Page 18

18
which are used to administer applications. They are seamlessly
integrated with the F-Secure Management Agents that handle all
management functions on local hosts.
Easy to Administer If F-Secure Anti-Virus for Microsoft Exchange is installed in stand-alone
mode it can be managed with the web-based user interface. With Web
Console, you can configure F-Secure Anti-Virus for Microsoft Exchange
settings, set up scheduled scans or run manual processes any time you
want.
If F-Secure Anti-Virus for Microsoft Exchange has been installed in
centrally administered configuration, it is managed with F-Secure Policy
Manager. With its graphical user interface, F-Secure Policy Manager
Console provides a centralized view of the domains and hosts in your
network and lets you configure the security policies for all F-Secure
components. F-Secure Policy Manager receives status information from
F-Secure Anti-Virus for Microsoft Exchange.
F-Secure Policy Manager Server is the server side component that
handles communication between F-Secure Anti-Virus for Microsoft
Exchange and F-Secure Policy Manager Console. It exchanges security
policies, software updates, status information, statistics, alerts, and other
information between F-Secure Policy Manager Console and all managed
systems.
Figure 1-1 (1) E-mail arrives from the Internet to F-Secure Anti-Virus for Microsoft
Exchange, which (2) filters malicious content from mails and attachments, and (3)
delivers cleaned files forward.
Page 19

1.3 Key Features
F-Secure Anti-Virus for Microsoft Exchange provides the following
features and capabilities.
Superior Protection Superior detection rate with multiple scanning engines.
Automatic malicious code detection and disinfection.
Heuristic scanning detects also unknown Windows and macro
viruses.
Recursive scanning of ARJ, BZ2, CAB, GZ, JAR, LZH, MSI,
RAR, TAR, TGZ, Z and ZIP archive files.
Automatic daily virus definition database updates.
Suspicious and unsafe attachments can be stripped away from
e-mails.
Password protected archives can be treated as unsafe.
Intelligent file type recognition.
Message filtering based on keywords in message subjects and
text.
Utilizes the low-level Anti-Virus API (AV API 2.0) for Microsoft
Exchange 2000 Server, and AV AP 2.5 for Microsoft Exchange
2003 Server.
CHAPTER 1 19
Introduction
Virus Outbreak
Detection
The virus outbreak detection is an additional active layer of
protection that automatically detects virus outbreaks and
quarantines suspicious messages.
Virus outbreaks are transparen tly detected and infected
messages are quarantined before the outbreak becomes
widespread.
The product can notify the administrator about virus outbreaks.
Quarantined unsafe messages can be reprocessed
automatically.
Page 20

20
Transparen cy and
Scalability
Viruses are intercepted before they can enter the network and
spread out on workstations and servers.
Real-time scanning of internal, inbound and outbound mail
messages and Public Folder notes.
Automatic protection of new mailboxes and Public Folders.
Total transparency to end-users. Users cannot bypass the
system, which means that messages and documents cannot be
exchanged without scanning.
Support for Windows 2000 Advanced Server or Windows Server
2003 clusters. Both Active-Passive and Active-Active clusters are
supported.
Management Controlling and monitoring the behavior of the products remotely.
Starting predefined operations remotely.
Monitoring statistics provided by the products remotely with
F-Secure Policy Manager or F-Secure Anti-Virus for Microsoft
Exchange Web Console.
Possibility to configure and manage stand-alone installations with
the convenient F-Secure Anti-Virus for Microsoft Exchange Web
Console.
Contains new quarantine managemen t features: you can manage
and search quarantined content with the F-Secure Anti-Virus for
Microsoft Exchange Web Console.
Protection against
Spam
Possible spam messages are transparently detected before they
become widespread.
Efficient spam detection based on different analyses on the
e-mail content.
Multiple filtering mechanisms guarantee the high accuracy of
spam detection.
Spam detection works in every language and message format.
Page 21

1.4 F-Secure Anti-Virus Mail Server and Gateway Products
The F-Secure Anti-Virus product line consists of workstation, file server,
mail server, gateway and mobile products.
F-Secure Internet Gatekeeper is a high performance, totally
automated web (HTTP and FTP-over-HTTP) and e-mail (SMTP)
virus scanning solution for the gateway level. F-Secure Internet
Gatekeeper works independently of firewall and e-mail server
solutions, and does not affect their performance.
F-Secure Anti-Virus for Microsoft Exchange™ protects your
Microsoft Exchange users from malicious code contained within
files they receive in mail messages and documents they open
from shared databases. Malicious code is also stopped in
outbound messages and in notes being posted on Public Folders.
The product operates transparently and scans files in the
Exchange Server Information Store in real-time. Manual and
scheduled scanning of user mailboxes and Public Folders is a lso
supported.
F-Secure Anti-Virus for MIMEsweeper™ provides a powerful
anti-virus scanning solution that tightly integrates with Clearswift
MIMEsweeper for SMTP and MIMEsweeper for Web products.
F-Secure provides top-class anti-virus software with fast and
simple integration to Clearswift MAILsweeper and WEBsweeper,
giving the corporation the powerful combination of complete
content security.
F-Secure Internet Gatekeeper for Linux™ provides a
high-performance solution at the Internet gateway level, stopping
viruses and other malicious code before the spread to end users
desktops or corporate servers. The product scans SMTP, HTTP,
FTP and POP3 traffic for viruses, worms and trojans, and blocks
and filters out specified file types. ActiveX and Java code can
also be scanned or blocked. The product receives updates
CHAPTER 1 21
Introduction
Page 22

22
automatically from F-Secure, keeping the virus protection always
up to date. A powerful and easy-to-use management console
simplifies the installation and configuration of the product.
F-Secure Messaging Security Gateway™ delivers the
industry’s most complete and effective security for e-mail. It
combines a robust enterprise-class messaging platform with
perimeter security, antispam, antivirus, secure messaging and
outbound content security capabilities in an easy-to-deploy,
hardened appliance.
Page 23

2
DEPLOYMENT
Installation Modes....................................................................... 24
Network Requirements............................................................... 24
Deployment Scenarios............................................................... 25
23
Page 24
24
2.1 Installation Modes
F-Secure Anti-Virus for Microsoft Exchange can be installed either in
stand-alone or centrally administered mode. In stand-alone installation,
F-Secure Anti-Virus for Microsoft Exchange is managed with Web
Console. In centrally administered mode, it is managed centrally with
F-Secure Policy Manager components: F-Secure Policy Manager Server
and F-Secure Policy Manager Console.
To administer F-Secure Anti-Virus for Microsoft Exchange in the centrally
administered mode, you have to install the following components:
F-Secure Policy Manager Server (on a dedicated machine)
F-Secure Policy Manager Console (on the administ ra to r's
machine)
2.2 Network Requirements
This network configuration is valid for all scenarios described in this
chapter. Make sure that the following network traffic can travel:
Service Process Inbound ports Outbound ports
F-Secure Content Scanner
Server
F-Secure Anti-Virus for
Microsoft Exchange Web
Console
F-Secure Automatic
Update Agent
%ProgramFiles%\F-Secure\
Content Scanner Server\
fsavsd.exe
%ProgramFiles%\F-Secure\
Web User Interface\
bin\fswebuid.exe
F-Secure Automatic Update.exe 371 (UDP), only if
18971 (TCP) +
1024-65536 (TCP), only
with F-Secure Anti-Virus
for Internet Mail on a
separate host
25023 DNS (53, UDP and TCP),
BackWeb Polite Protocol
is used
DNS (53, UDP/TCP),
HTTP (80) or other known
port used for HTTP proxy
1433 (TCP), only with the
dedicated SQL server
DNS (53, UDP and TCP),
HTTP (80)
Page 25
Service Process Inbound ports Outbound ports
CHAPTER 2 25
Deployment
FSNRB %ProgramFiles%\F-Secure\
Common\fnrb32.exe
FSMA (AMEH) %ProgramFiles%\F-Secure\
Common\fameh32.exe
F-Secure Quarantine
Manager
%ProgramFiles%\F-Secure\
Quarantine Manager\fqm.exe
2.3 Deployment Scenarios
Depending on the number of protected systems and the amount of data
traffic, you might consider various scenarios of deploying F-Secure
Anti-Virus for Microsoft Exchange. There are various ways to deploy
F-Secure Anti-Virus for Microsoft Exchange that are suitable to different
environments.
If the mail traffic is not very heavy, see “Minimum Installation”, 25.
If the mail traffic is rather heavy, see “Medium to Large
Installation”, 27.
For very large, performance-critical installations, see
“Performance-Critical Installation”, 28.
For Microsoft Exchange Cluster Environments, see “Microsoft
Exchange Cluster Environment”, 30.
- DNS (53, UDP/TCP),
HTTP (80)
- DNS (53, UDP/TCP),
SMTP (25)
- DNS (53, UDP/TCP),
1433 (TCP), only with the
dedicated SQL server
2.3.1 Minimum Installation
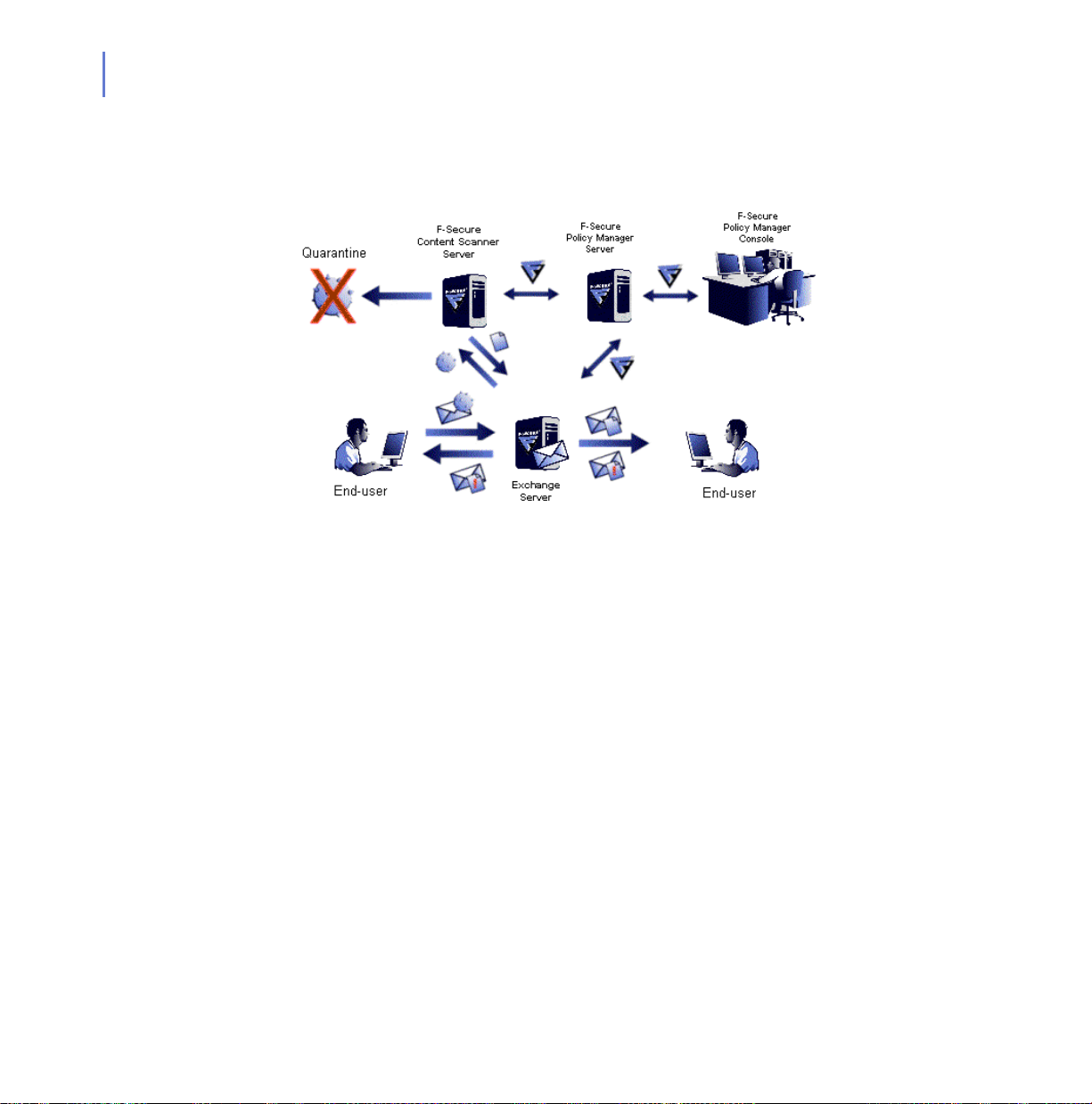
If the mail traffic is not very heavy, you can install F-Secure Content
Scanner Server on the same machine that runs Microsoft Exchange
Server. In this case, both F-Secure Content Scanner Server and
F-Secure Anti-Virus for Microsoft Exchange will reside on the Microsoft
Exchange Server.
Page 26
26
You can administer F-Secure Anti-Virus for Microsoft Exchange and
F-Secure Content Scanner Server by using the F-Secure Anti-Virus for
Microsoft Exchange Web Console.
Figure 2-1 F-Secure Anti-Virus for Microsoft Exchange minimum installation
Alternatively, you can choose to install F-Secure Policy Manager to
enable centralized administration of F-Secure Content Scanner Server
and F-Secure Anti-Virus for Microsoft Exchan ge.
Page 27
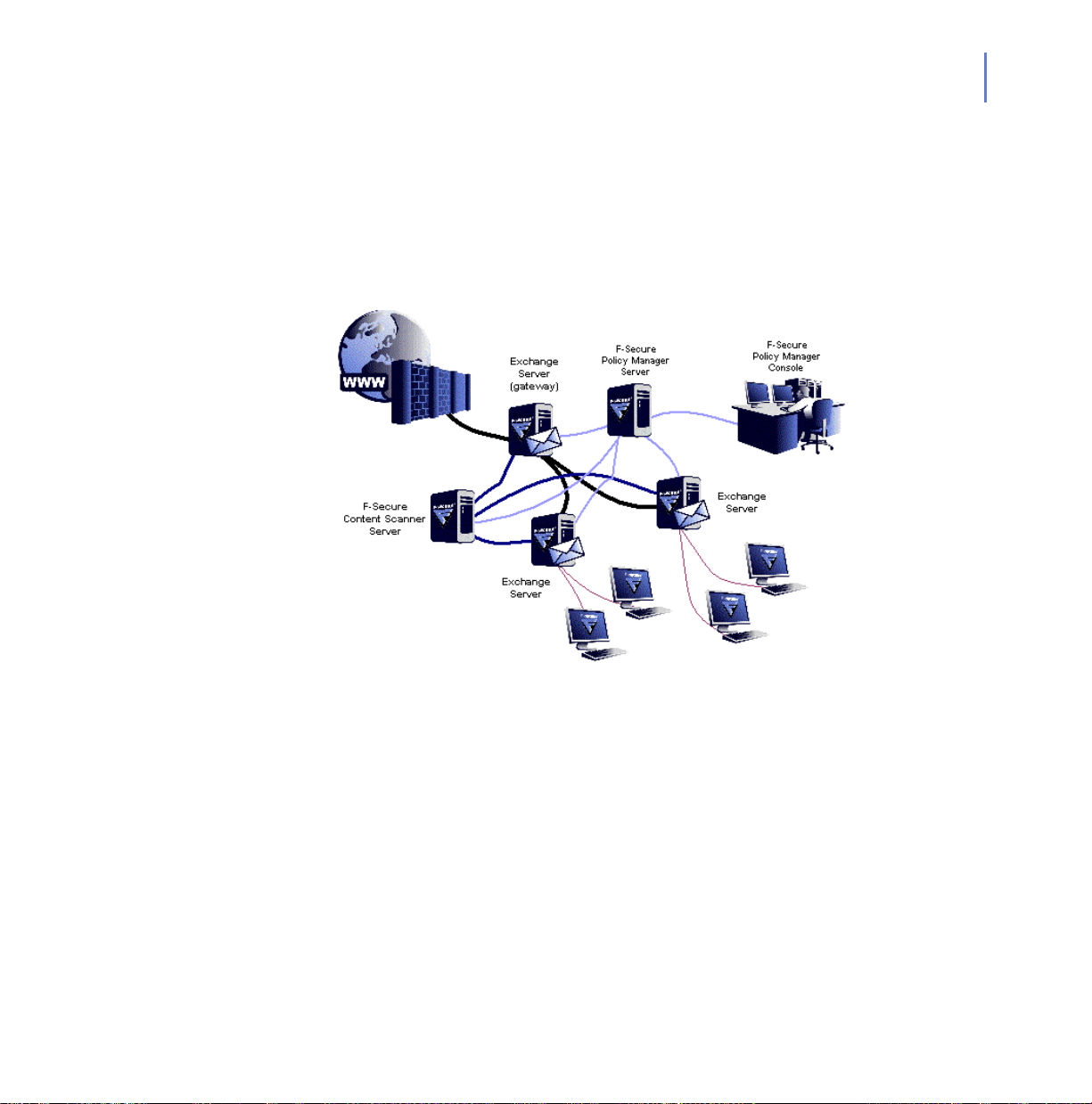
2.3.2 Medium to Large Installation
If the mail traffic is rather heavy, F-Secure Content Scanner Server should
be installed on a dedicated machine. This minimizes the extr a load on the
Microsoft Exchange Server.
You should install F-Secure Anti-V irus for Microsoft Exchange in
centralized administration mode on each Microsoft Exchange Server.
CHAPTER 2 27
Deployment
Figure 2-2 F-Secure Anti-Virus for Microsoft Exchange, medium to large
installation
Page 28
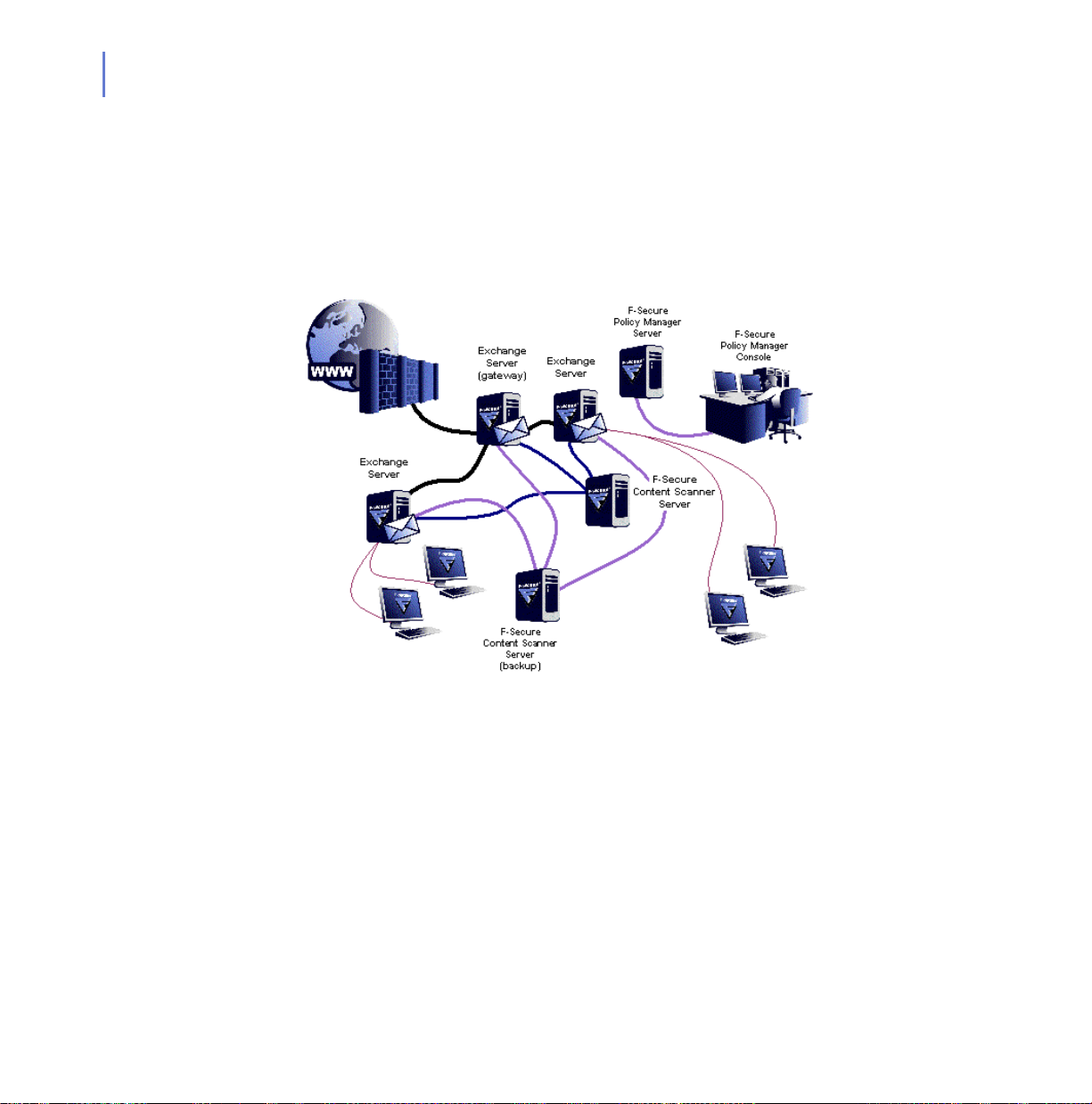
28
2.3.3 Performance-Critical Installation
In very large, performance-critical installations you should use multiple
F-Secure Content Scanner Server installations. Each F-Secure Content
Scanner Server should be installed on a dedicated machine. F-Secure
Anti-Virus for Microsoft Exchange can share the virus scanning load
between multiple F-Secure Content Scanner Servers.
Figure 2-3 F-Secure Anti-Virus for Microsoft Exchange with multiple F-Secure
Content Scanner Servers
Page 29
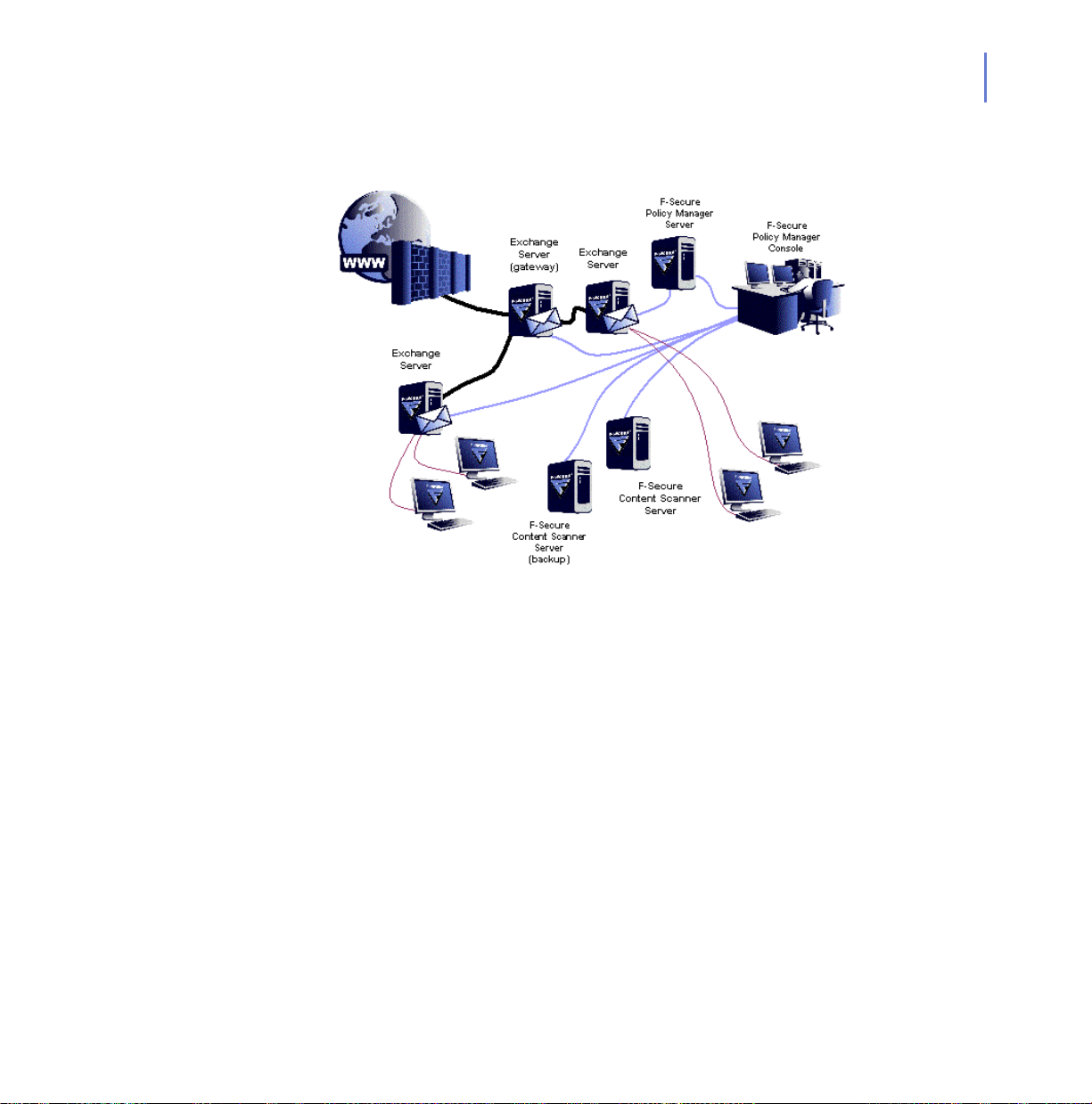
CHAPTER 2 29
Deployment
F-Secure Anti-Virus for Microsoft Exchange should be installed in
centralized administration mode on each Microsoft Exchange Server.
Figure 2-4 F-Secure Anti-Virus for Microsoft Exchange installed on each
Microsoft Exchange Server
Page 30

30
2.3.4 Microsoft Exchange Cluster Environment
F-Secure Anti-Virus for Microsoft Exchange can be installed on a
Windows 2000 Advanced Server or Windows Server 2003 Enterprise
Edition cluster. The product supports standard two-node Active-Passive
and Active-Active clusters.
Microsoft Exchange need s to be properly configured and running in
the cluster before installing F-Secure Anti-Virus for Microsoft
Exchange.
F-Secure Anti-Virus for Microsoft Exchange needs to be installed
separately on both cluster nodes. When installing in Microsoft Exchange
cluster environment, the product must be installed in centrally managed
mode, so that you can configure and manage the product with F-Secure
Policy Manager. Changing the product settings with F-Secure Anti-Virus
for Microsoft Exchange Web Console is not supported in cluster
environments, but it can be used for some quarantine management
functions.
The settings on both cluster nodes must be identical. To ensure this,
place the servers as their own domain in the F-Secure Policy Manager
Console and configure all the settings on the domain level, not on th e
host level.
It is recommended to install a local F-Secure Content Scanner Server on
both cluster nodes. However, if a remote F-Secure Content Scanner
Server is used, the dedicated IP address of each cluster node must be
visible to the remote F-Secure Content Scanner Server.
When installing the product, the setup program detects Microsoft
Exchange Cluster automatically. The setup program also creates a cluster
resource for the product automatically. The cluster resource makes it
possible to use the product in the cluster, by giving the control of the
resource to the cluster service. This and other resources together
guarantee that the product works properly in the clu ster in ever y situa tion.
Y ou can che ck the state of the re source in Micro soft Cluster Administrator
console, under the same branch where th e Exch an g e reso ur ce s res i de .
For detailed instructions, see “Deploying the Product on a Cluster”, 344.
Page 31

CHAPTER 2 31
Deployment
A Note about Installing on Active-Passive Cluster
The product can be installed either on an active or a p assive cluster node.
When installing on a passive node (which does not have active Microsoft
Exchange services), the setup program may display a notification about
missing Microsoft Exchange components, but the installation can be
continued.
Page 32

3
INSTALLATION
System Requirements................................................................ 33
Improving Reliability and Performance....................................... 37
Installation Overview.................................................................. 38
Installing F-Secure Anti-Virus for Microsoft Exchange............... 40
After the Installation.................................................................... 59
Upgrading the Previous Version................................................. 60
Upgrading the Evaluation Version.............................................. 63
Uninstalling F-Secure Anti-Virus for Microsoft Exchange........... 64
32
Page 33

3.1 System Requirements
F-Secure Anti-Virus for Microsoft Exchange is installed on the computer
running Microsoft Exchange Server and requires the following hardware
and software.
3.1.1 Minimum System Requirements
F-Secure Anti-Virus for Microsoft Exchange has to be installed to the
same machine that runs Microsoft Exchange Server. You need to log in
with administrator-level privileges to install F-Secure Anti-Virus for
Microsoft Exchange.
In order to install the product successfully on a non-en glish version
of the operating system, your default system loca le sh ou ld be the
same as the language of the operating system. You can set the
locale in Control Panel > Regional Options > General > Y our locale
(location).
CHAPTER 3 33
Installation
Operating system:
Microsoft® Windows 2000 Server with
the latest service pack
Microsoft® Windows 2000 Advanced
Server with the latest service pack
Microsoft® Windows Server 2003,
Stan dard Edition with late st service p ack
Microsoft® Windows Server 2003,
Enterprise Edition with latest service
pack
Microsoft® Windows Server 2003 R2,
Standard Edition
Microsoft® Windows Server 2003 R2,
Enterprise Edition
Microsoft Exchange
Server:
Microsoft® Exchange Server 2000 with
Service Pack 3 or later
Microsoft® Exchange Server 2003
Processor: Intel Pentium 4 2GHz or faster
Page 34

34
Memory: 1 GB
Disk space to install: 260 MB
Disk space for
processing:
SQL server (for
quarantine
database):
F-Secure Policy
Manager version:
10 GB or more. The required disk space
depends on the number of mailboxes, amount of
data traffic and the size of the Information Store.
Microsoft SQL Server 2000 (Enterprise,
Standard or Workgroup edition) with
Service Pack 4
Microsoft SQL Server 2000 Desktop
Engine (MSDE) with Service Pack 4
Microsoft SQL Server 2005 (Enterprise,
Standard, Workgroup or Express
edition)
For more information, see “Which SQL Server to
Use for the Quarantine Database?”, 35.
When centralized quarantine management is
used, the SQL server must be reachable from
the network and file sharing must be enabled.
F-Secure Policy Manager 6.0 or newer.
F-Secure Policy Manager is required only in
centrally managed environments.
For Microsoft Windows Server 200 3 Service Pack 1 related support
information, see
http://support.f-secure.com/enu/corporate/w2003sp1/
The release notes document contains the latest information about
the product and might have changes to system requirements and
the installation procedure. It is highly recommended to read the
release notes before you proceed with the installation.
Page 35

CHAPTER 3 35
Installation
3.1.2 Which SQL Server to Use for the Quarantine Database?
As a minimum requirement, the Quarantine database should have the
capacity to store information about all inbound and outbound mail to and
from your organization that would normally be sent during 2-3 days.
Take into account the following SQL server specific considerations when
deciding which SQL server to use:
Microsoft SQL Server
Desktop Engine and
SQL Server 2005
Express Edition
When using Microsoft SQL Server Desktop Engine (MSDE), the
Quarantine database size is limited to 2 GB.
MSDE includes a concurrent workload governor that limits the
scalability of MSDE. For more information, see
http://msdn.microsoft.com/library/?url=/library/en-us/architec/
8_ar_sa2_0ciq.asp?frame=true.
It is not recommended to use MSDE or SQL Server 2005
Express Edition if you are planning to use centralized quarantine
management with multiple F-Secure Anti-Virus for Microsoft
Exchange installations.
MSDE is delivered together with F-Secure Anti-Virus for
Microsoft Exchange, and you can inst all it dur ing the F-Secure
Internet Anti-Virus for Microsoft Exchange Setup. For more
information, see “Installation Overview”, 38.
Page 36

36
Microsoft SQL
Server 2000/2005
If your organization sends a large amount of e-mails, it is
recommended to use Microsoft SQL Server 2000/2005.
It is recommended to use Microsof t SQL Server 2000/2005 if you
are planning to use centralized quarantine management with
multiple F-Secure Anti-Virus for Microsoft Exchange installations.
For more information, see “Performance-Critical Installation”, 28.
Note that the product does not support Windows Authentication
when connecting to Microsoft SQL Server 2000/2005. The
Microsoft SQL Server 2000/2005 that the product will use for the
Quarantine database should be configured to use Mixed Mode
authentication.
If you plan to use Microsoft SQL Server 2005, you must
purchase it and obtain your own license before you start to
deploy F-Secure Anti-Virus for Microsoft Exchange. To
purchase Microsoft SQL Server 2005, contact your Microsoft
reseller.
3.1.3 Web Browser Software Requirements
In order to administer the product with F-Secure Anti-Virus for Microsoft
Exchange Web Console, one of the following web browsers is required:
Microsoft Internet Explorer 6.0 or later
Netscape Communicator 8.1 or later
Mozilla Firefox 1.5 or later
Opera 9.00 or later
Konqueror 3.5 or later
Any other web browser supporting HTTP 1.0, SSL, Java scripts and
cookies may be used as well. Microsoft Internet Explorer 5.5 or earlier
cannot be used to administer the product.
Page 37

3.2 Improving Reliability and Performance
You can improve the system reliability and overall performance by
upgrading the following components.
Processor If the system load is high, a fast processor on the Microsoft Exchange
Server speeds up the e-mail message processing. As Microsoft
Exchange Server handles a large amount of data, a fast processor alone
is not enough to guarantee a fast operation of F-Secure Anti-Virus for
Microsoft Exchange.
Memory Memory consumption is directly proportional to the size of processed
mails - scanning a single mail may use memory in amounts up to three
times the size of the mail concerned. If the average size of mail messages
is big, or Microsoft Exchange Server has to process large messages
regularly , increasing the amo unt of physical memory increa ses the overall
performance.
If large messages are processed only now and then, it might be enough
to increase the size of the virtual memory. In this case, large messages
will slow the system down.
CHAPTER 3 37
Installation
Hard Drive Hard drive size is an important reliability factor. Hard drive performance is
crucial for Microsoft Exchange Server to perform well. For best
performance, a RAID system is recommended; for servers with only
moderate load, SCSI hard disks are adequate. If your server has an IDE
hard disk, DMA access support is recommended.
Operating System It is highly recommended to have the latest service packs for the
operating system being used. These fixes make the platfo rm mo re stable
and thus increase the reliability of the system.
Page 38

38
3.3 Centrally Administered or Stand-alone Installation?
F-Secure Anti-Virus for Microsoft Exchange can be managed either with
F-Secure Anti-Virus for Microsoft Exchange Web Console or F-Secure
Policy Manager Console. You can select the management method when
you install the product.
If you already use F-Secure Policy Manager to administer oth er F-Secure
products, it is recommended to install F-Secure An ti-Virus for Microsoft
Exchange in centralized administration mode.
The quarantined mails are managed using the F-Secure Anti-Virus for
Microsoft Exchange Web Console in both centrally administered and
stand-alone installations. In centrally managed environments all other
features are managed with F-Secure Policy Manager.
When installing in Microsoft Exchange cluster environment, the
product must be installed in centrally managed mode, so that you
can configure and manage the product with F-Secure Policy
Manager.
3.4 Installation Overview
Before you start to install F-Secure Anti-Virus for Micro soft Exchange,
uninstall any potentially conflicting products, such as anti-virus, file
encryption, and disk encryption software that employ low-level device
drivers. Close all Windows applications before starting the installation.
Page 39

CHAPTER 3 39
Installation
F-Secure Anti-Virus for Microsoft Exchange can be installed to the same
computer that runs F-Secure Anti-Virus for Servers 5.50. You should
uninstall any potentially conflicting products, such as other anti-virus, file
encryption, and disk encryption software, which employ low-level device
drivers, before you install F-Secure Anti-Virus for Microsoft Exchange.
If you want to run F-Secure Anti-Virus for Servers 5.50 on the same
computer where you install F-Secure Anti-Virus for Microsoft
Exchange, make sure that F-Secure Anti-Virus for Servers 5.50 is
installed before you install F-Secure Anti-Virus for Microsoft
Exchange.
To administer F-Secure Anti-Virus for Microsoft Exchange in centralized
administration mode, you need to install F-Secure Policy Manager
Console and F-Secure Policy Manager Server. Detailed information on
F-Secure Policy Manager Console and F-Secure Policy Manager Server
is provided in the F-Secure Policy Manager Administrator's Guide.
Follow these steps to set up F-Secure Anti-Virus for Microsoft Exchange:
Centralized Administration mode:
1. Run F-Secure Policy Manager setup to set up F-Secure Policy
Manager Server. See F-Secure Policy Manager Administrator’s
Guide for instructions.
2. Install F-Secure Anti-Virus for Microso ft Exchange. For more
information, see “Installing F-Secure Anti-Virus for Microsoft
Exchange”, 40.
3. Import the product MIB files to F-Secure Policy Manager, if they
cannot be uploaded there during the installation. For more
information, see “Importing Product MIB files to F-Secure Policy
Manager Console”, 59.
4. Check that F-Secure Automatic Update Agent can retrieve the latest
virus definition databases. For more informatio n, se e “Updating Virus
and Spam Definition Databases”, 340.
Page 40

40
Stand-alone mode:
1. Install F-Secure Anti-Virus for Microsoft Exchange. For more
information, see “Installing F-Secure Anti-Virus for Microsoft
Exchange”, 40.
2. Check that F-Secure Automatic Update Agent can retrieve the latest
virus definition databases. For more informatio n, se e “Updating Virus
and Spam Definition Databases”, 340.
After the installation is complete, check and configure settings for
F-Secure Content Scanner Server, F-Secure Anti-Virus for Microsoft
Exchange and F-Secure Management Agent.
3.5 Installing F-Secure Anti-Virus for Microsoft Exchange
Follow these instructions to install F-Secure Content Scanner Server and
F-Secure Anti-Virus for Microsoft Exchange.
Step 1. 1. Insert the F-Secure CD in your CD-ROM drive.
2. Select F-Secure Anti-Virus for Microsoft Exchange from the Install
Software menu.
Step 2. Read the information in the Welcome screen.
Page 41

Click Next to continue.
Step 3. Read the licence agreement.
CHAPTER 3 41
Installation
Page 42

42
If you accept the agreement, check the I accept the agreement
checkbox and click Next to continue.
Step 4. Enter the product keycode.
Click Next to continue.
Page 43

Step 5. Choose the components to install.
If you want to install F-Secure Content Scanner Server and F-Secure
Anti-Virus for Microsoft Exchange on the Microsoft Exchange Server
computer, select all components. Click Next to continue.
CHAPTER 3 43
Installation
When you install F-Secure Spam Control, or F-Secure Content
Scanner Server in stand-alone mode, F-Secure Automatic Update
Agent is automatically installed to provide virus definition dat abase
updates. For more information, see “Automatic Updates with
F-Secure Automatic Update Agent”, 341.
Page 44

44
Step 6. Choose the destination folder for the installation.
Click Next to continue.
Page 45

Step 7. Choose the administration method.
If you install F-Secure Anti-Virus for Microsoft Exchange in stand-alone
mode, you cannot configure settings and receive alerts and status
information in F-Secure Policy Manager Console. Click Next to continue.
If you selected the stand-alone installation, continue to Step 10. , 48.
CHAPTER 3 45
Installation
If you select the stand-alone mode, use the F-Secure Anti-V irus for
Microsoft Exchange Web Console to change product settings and
statistics. For more information, see “Administration with Web
Console”, 216.
Page 46

46
Step 8. Enter the path to the public management key file admin.pub that was
created during F-Secure Policy Manager Console setup.
You can transfer the public key in various ways (use a shared folder on
the file server, a floppy disk, or send the key as an attachment in an
e-mail message). Click Next to continue.
Page 47

CHAPTER 3 47
Installation
Step 9. Enter the IP address or URL of the F-Secure Policy Manager Server you
installed earlier.
Click Next to continue.
If the product MIB files cannot be uploaded to F-Secure Policy
Manager during installation, you can import them manually.
For more information, see “Importing Product MIB files to F-Secure
Policy Manager Console”, 59.
Page 48

48
Step 10. Enter an SMTP address that will be used by F-Secure Anti-Virus for
Microsoft Exchange to send warning and informational messages to
end-users.
The SMTP address should be a valid, existing address that is allowed to
send messages. Click Next to continue.
Page 49

CHAPTER 3 49
Installation
Step 11. Sele ct the user account that F-Secure Outbreak Manager should use.
Select either the local system account or enter the name and password
for the user account that F-Secure Outbreak Manager should use. The
account is used to run the outbreak handler scripts or programs.
If you do need to see the outbreak handler script running on the desktop
select Allow to interact with desktop. By default, the script or program
runs in the background.
For more information, see “Outbreak Management”, 156. Click Next to
continue.
If you want to use the default \SYSTEM account, do not enter any
password.
Make sure that the account has all the necessary privileges to run
the outbreak handler script.
Page 50

50
Step 12. Specify the Quarantine management method.
If you want to manage quarantines locally, select Local quarantine
management. Select Centralized quarantine management if you install
the product on multiple instances. For more information, see “Microsoft
Exchange Cluster Environment”, 30.
Click Next to continue.
Page 51

Step 13. Specify the location of the Quarantine database.
If you want to install the Quarantine database on the same server as the
product installation, select (a) Install and use Microsoft SQL Server
Desktop Engine.
If you are using Microsoft SQL Server or Microsoft SQL Server Desktop
Engine already, select (b) Use the existing inst allation of MIcrosoft SQL
Server or MSDE.
CHAPTER 3 51
Installation
Click Next to continue.
Page 52

52
a Specify the installation directory for Microsoft SQL Server
Desktop Engine and data files.
Enter the username and password for the server administrator
account. Click Next to continue.
b Specify the computer name of the SQL Server where you wan t to
create the Quarantine database.
Enter the username and password to log on to the server. Click
Next to continue.
Page 53

CHAPTER 3 53
Installation
If the server has a database with the same name, you can either
use the existing database, remove the existin g da tabase and
create a new one or keep the existing database and cre ate a new
one with a new name.
Page 54

54
Step 14. Select whether you want to install the product with F-Secure World Map
Support.
The product can collect and send statistics about viruses and other
malware to the F-Secure World Map service. if you agree to send
statistics to F-Secure World Map, select Yes and click Next to continue.
Page 55

Step 15. If you selected the centralized administration mode, the installation
program connects to specified F-Secure Policy Manager Se rver
automatically to install F-Secure Anti-Virus for Microsoft Exchange MIB
files. If the installation program cannot connect to F-Secure Policy
Manager Server, the following dialog opens.
Make sure that the computer where you are inst alling F-Secure Anti-V irus
for Microsoft Exchange is allowed to connect to the administration port on
F-Secure Policy Manager Server, or if you use proxy, make sure that the
connection is allowed from the proxy to the server. Check that any firewall
does not block the connection.
If you want to skip installing MIB files, click Cancel. You can install MIB
files later either manually or by running the Setup again.
CHAPTER 3 55
Installation
Page 56

56
Step 16. The list of components that will be installed is displayed.
Click Start to install listed components.
Page 57

Step 17. The installation status of the components is displayed.
Click Next to continue.
CHAPTER 3 57
Installation
Page 58

58
Step 18. The installation is completed.
Click Finish to close the Setup wizard.
Step 19. If you are installing F-Secure Spam Control, the setup prompts you to
select whether to restart the Microsoft Exchange Information Store
service automatically to complete the installation. Click Yes to restart the
Information Store service automatically.
Page 59

CHAPTER 3 59
Installation
3.6 After the Installation
This section describes what you have to do after the installation. These
steps include:
Importing product MIBs to F-Secure Policy Manager (if that is
required), and
Initial configuration of the product.
3.6.1 Importing Product MIB files to F-Secure Policy Manager Console
If you are using the product in centrally managed mode, there are cases
when the F-Secure Anti-Virus for Microsof t Exchange MIB JAR file cannot
be uploaded to F-Secure Policy Manager Server during the in stallation. In
these cases you will have to import the MIB files to F-Secure Policy
Manager. You will have to import the MIB files if:
F-Secure Anti-Virus for Microsoft Exchange is located in a
different network segment than F-Secure Policy Manager, and
there is a firewall between them blocking access to Policy
Manager’s administrative port (8080).
F-Secure Policy Manager Server has been configured so that
administrative connections from anywhere else than the localhost
are blocked.
The recommended way is to import the MIBs via F-Secure Policy
Manager Console Tools menu. You can do it as follows:
1. Open the Tools menu and se lect the Installation packages... op tion.
2. Click Import....
3. When the Import Installation Packages dialog opens, browse to
locate the fsavmse660.mib.jar file located under the Jars subdirectory
in the setup package. Then click Open.
4. After importing the new MIB files, restart F-Secure Policy Manager
Console.
Page 60

60
3.6.2 Configuring the Product
After the installation, F-Secure Anti-Virus for Microsoft Exchange is
functional, but it is using mostly default values. It is highly recommended
to go through all the settings of all installed components. You should also
retrieve the latest virus definition database updates.
Configure F-Secure Anti-Virus for Microsoft Exchange.
If F-Secure Anti-Virus for Microsoft Exchange has been installed
in the centralized administration mode, use F-Secure Policy
Manager Console to configure the settings for F-Secure Content
Scanner Server and F-Secure Anti-Virus for Microsoft Exchange
and distribute the policy. For more information, see “Centrally
Managed Administration”, 125.
If F-Secure Anti-Virus for Microsoft Exchange has been installed
in stand-alone mode, use the F-Secure Anti-Virus for Microsoft
Exchange Web Console to configure the settings of F-Secure
Anti-Virus for Microsoft Exchange. For more information, see
“Administration with Web Console”, 216.
Specify the domains which should be considered to be internal
domains. For more information, see “Internal Domains”, 159.
Retrieve virus definition database updates. For more information,
see “Updating Virus and Spam Definition Databases”, 340.
3.7 Upgrading the Previous Version
If you have a previous version of F-Secure Anti-Virus for Microsoft
Exchange installed on your computer, you can upgrade it easily. You do
not need to remove your previous version, F-Secure Setup uninstalls it
automatically.
Page 61

CHAPTER 3 61
During upgrade the setup will stop and restart Microsoft Exchange
Information Store, IIS Admin Service and all services that depend on
them:
Microsoft Exchange Information Store
World Wide Web Publishing Service
Simple Mail Transport Protocol (SMTP)
Microsoft Exchange Routing Engine
Microsoft Exchange POP3
Network News Transport Protocol (NNTP)
Microsoft Exchange MTA Stacks
Microsoft Exchange Information Store
Microsoft Exchange IMAP4
IIS Admin Service
Installation
Page 62

62
Follow these instructions to upgrade F-Secure Anti-Virus for
Microsoft Exchange:
1. Run the Setup program. For more information, see “Installing
F-Secure Anti-Virus for Microsoft Exchange”, 40.
2. Depending on the installed F-Secure products, F-Secure Setup will
suggest upgrading one or more components.
Select the components you want to upgrade.
3. The setup needs to stop and restart Micr osoft Exchange Server
related services during the upgrade.
Click OK to continue.
4. After the Setup finishes, restart the computer if the Setup program
prompts you to do so.
Page 63

5. Configure F-Secure Anti-Virus for Microsoft Exchange. For more
information, see “Centrally Managed Administration”, 125. If you
installed F-Secure Anti-Virus for Microsoft Exchange in stand-alone
mode, see “Administration with Web Console”, 216.
6. that F-Secure Automatic Update Agent can retrieve the latest virus
definition databases. For more information, see “Updating Virus and
Spam Definition Databases”, 340.
3.8 Upgrading the Evaluation Version
If you want to use F-Secure Anti-Virus for Microsoft Exchange af ter your
evaluation period expires, you need a new keycode. Contact your
software vendor or renew your license online.
After you have received the new keycode, you can either reinstall
F-Secure Anti-Virus for Microsoft Exchange with your new keycode (see
“Installing F-Secure Anti-Virus for Microsoft Exchange”, 40) or register the
new keycode from F-Secure Settings and Statistics.
To register the new keycode from F-Secure Settings and Statistics
1. Open F-Secure Settings and Statistics by double-clicking the
F-Secure icon in the Windows system tray and select F-Secure
Anti-Virus for Microsoft Exchange to open the evaluation screen.
CHAPTER 3 63
Installation
2. Click Register Keycode... and enter the new keycode you have
received.
Page 64

64
If you do not want to continue to use F-Secure Anti-Virus for Microsoft
Exchange after your evaluation license expires, you should uninstall the
software.
3.9 Uninstalling F-Secure Anti-Virus for Microsoft Exchange
To uninstall F-Secure Anti-Virus for Microsoft Exchange, select Add/
Remove Programs from the Windows Control Panel. To uninstall
F-Secure Anti-Virus for Microsoft Exchange completely, uninstall the
components in the following order:
1. F-Secure Anti-Virus for Microsoft Exchange
2. F-Secure SNMP Support (if it was installed)
3. F-Secure Spam Control
4. F-Secure Content Scanner Server
5. F-Secure Automatic Update Agent
IMPORTANT: If there is another F-Secure Anti-Virus product
installed on the same computer, check whether it uses F-Secure
Automatic Update Agent or F-Secure Policy Manager for getting
virus definition database updates. If the other product gets the
updates from F-Secure Policy Manager, you can uninstall F-Secure
Automatic Update Agent.
Page 65

4
USING F-SECURE
A
NTI-VIRUS FOR
ICROSOFT EXCHANGE
M
Overview..................................................................................... 66
Administering F-Secure Anti-Virus for Microsoft Exchange........ 66
Using the Web Console.............................................................. 67
Checking the Product Status...................................................... 70
Configuring the Web Console..................................................... 73
Using F-Secure Policy Manager Console................................... 74
Modifying Settings and Viewing Statistics.................................. 75
Manually Processing Mailboxes and Public Folders.................. 77
Configuring Alert Forwarding.................................................... 119
Viewing Alerts........................................................................... 123
65
Page 66

66
4.1 Overview
F-Secure Anti-Virus for Microsoft Exchange can be used either in the
stand-alone mode, or in the centrally administered mode, based on your
selections during the installation and the initial setup.
4.2 Administering F-Secure Anti-Virus for Microsoft Exchange
In the centralized administration mode, you can administer F-Secure
Anti-Virus for Microsoft Exchange and F-Secure Content Scanner
Servers with F-Secure Policy Manager. You can use the F-Secure
Anti-Virus for Microsoft Exchange Web Console to start and stop
F-Secure Anti-Virus for Microsoft Exchange, check its curren t status and
to connect to F-Secure Web Club for support, but you cannot change any
settings with it.
In the stand-alone mode, you use the F-Secure Anti-Virus for Microsoft
Exchange Web Console to start and stop F-Secure Anti- Virus for
Microsoft Exchange, modify its settings, edit scheduled tasks and start
manual processing.
To open the F-Secure Anti-Virus for Microsoft Exchange Web Console,
start it from F-Secure Settings and Sta tistics or select F-Secure Anti-Virus
for Microsoft Exchange from the Windows Start menu > Programs >
F-Secure Anti-Virus for Microsoft Exchange > F-Secure Anti-Virus for
Microsoft Exchange Web Console. You can open F-Secure Settings and
Statistics by double-clicking the F-Secure icon in the Windows system
tray.
Page 67

4.3 Using the Web Console
In centrally managed installations of F-Secure Anti-Virus for Microsoft
Exchange, the F-Secure Anti-Virus for Microsoft Exchange Web Console
can be used for monitoring the system status and st atistics. It can also be
used for viewing the settings currently in use and executing some
operations. However, in centrally managed installations it cannot be used
for configuring the system or scanning settings; use F-Secure Policy
Manager for this instead.
4.3.1 Logging in for the First Time
F-Secure Anti-Virus for Microsof t Exchange W eb Console does not
support Microsoft Internet Explorer 5.5 or older.
Microsoft Internet Explorer 6.0 users:
The address of the F-Secure Anti-Virus for Microsoft Exchange Web
Console, https://127.0.0.1:25023/, should be add ed to the Trusted sites in
Internet Explorer 6.0 Security Options. This ensures that the F-Secure
Anti-Virus for Microsoft Exchange Web Console works properly in all
environments.
CHAPTER 4 67
Using F-Secure Anti-Virus for Microsoft Exchange
Before you log in the F-Secure Anti-Virus for Microsoft Exchange Web
Console for the first time, check that Java script and cookies are enabled
in the browser you use.
When you log in for the first time, your browser will display a Security Alert
dialog window about the security certificate for F-Secure Anti-Virus for
Microsoft Exchange Web Console. You can create a security certificate
for F-Secure Anti-Virus for Microsoft Exchange Web Console before
logging in, and then install the certificate during the login process.
If your company has an established process for creating and
storing certificates, you can follow that process to create and store
the security certificate for F-Secure Anti-Virus for Microso ft
Exchange Web Console.
Page 68

68
Step 1. Create the security certificate
1. Browse to the F-Secure Anti-Virus for Microsoft Exchange Web
Console installation directory, for example:
C:\Program Files\F-Secure\Web User Interface\bin\
2. Locate the certificate creation utility, makecert.bat, and double click it
to run the utility.
3. The utility creates a certificate that will be issued to all local IP
addresses, and restarts the F-Secure Anti-Virus for Microsoft
Exchange Web Console service to take the certificate into use. Wait
until the utility completes, and the window closes. Now you can
proceed to logging in.
Step 2. Log in and install the security certificate
1. Select Programs>F-Secure Anti-Virus for Microsoft
Exchange>F-Secure Anti-Virus for Microsoft Exchange W eb Console,
or enter the address of the F-Secure Anti-Virus for Microsoft
Exchange and the port number in your web browser. Note, that the
protocol used is https. For example:
https://127.0.0.1:25023
2. The Security Alert about the F-Secure Anti-Virus for Microsoft
Exchange Web Console certificate is displayed. If you install the
certificate now, you will not see the Security Alert window again. Click
View Certificate to view the certificate information and to install the
certificate.
3. The Certificate window opens. Click Install Certificate to proceed to
the Certificate Import Wizard.
4. Follow the instructions in the Certificate Import Wizard. When the
wizard has completed, you are prompted to add the new certificate in
the Certificate Root Store. Click Yes.
5. If the Security Alert window is still displayed, click Yes to proceed.
6. When the login page opens, en ter the user name and the password.
Note, that you must have administrator rights to the host. Then click
Log In.
Page 69

CHAPTER 4 69
Using F-Secure Anti-Virus for Microsoft Exchange
Figure 4-1 F-Secure Anti-Virus for Microsoft Exchange Web Console Login
page
7. You will be forwarded to the home page, which displays a summary of
the system status.
Figure 4-2 F-Secure Anti-Virus for Microsoft Exchange Home page
Page 70

70
4.4 Checking the Product Status
You can check the overall product status on the Home page. The Home
page displays an overview of each compon ent status and most important
statistics of the installed F-Secure Anti-Virus for Microsoft Exchange
components. From the Home page you can also open the product logs
and proceed to configure the product components.
This section describes the statistics and operations available on the
Home page.
F-Secure Anti-Virus for Microsoft Exchange
The Home page displays the status the F-Secure Anti-Virus for Microsoft
Exchange as well as a summary of the F-Secure Anti-Virus for Microsoft
Exchange statistics.
Status indicator Displays the status of F-Secure Anti-Virus for
Microsoft Exchange.
Processed messages Displays the total number of messages that
have been processed.
Infected messages Displays the number of infected messages
found since the last reset of statistics.
Stripped attachments Displays the number of attachments that have
been stripped.
Click Configure to configure F-Secure Anti-V irus for Microsof t Exchange.
For more information, see “Overview”, 217.
Page 71

CHAPTER 4 71
Using F-Secure Anti-Virus for Microsoft Exchange
F-Secure Content Scanner Server
The Home page displays the status the F-Secure Content Scanner
Server as well as a summary of the F-Secure Content Scanner Server
statistics.
Status indicator Displays the status of F-Secure Content
Scanner Server.
Last time virus definition
databases updated
Database update version Displays the version of the virus definition
Scanned files Displays the number of files the server has
Last time infection found Displays the last infection detected by the
Click Configure to configure F-Secure Content Scanner Server. For more
information, see “F-Secure Content Scanner Server Settings”, 275.
Displays the last date and time when the
virus definition databases were updated.
database update.
The version is shown in YYYY-MM-DD_NN
format, where YYYY-MM-DD is the release
date of the update and NN is the number of
the update for that day.
scanned for viruses.
server.
F-Secure Automatic Update Agent
Status indicator Displays the status of F-Secure Automatic
Update Agent.
Communication method Displays the currently used client protocol.
Last connection to the
server
Displays the last date and time when
F-Secure Automatic Update Agen t polled the
F-Secure Automatic Update Server for new
updates.
Page 72

72
Click Configure to configure F-Secure Automatic Update Agent. For
more information, see “Updating Vi rus and Spam Definition Databases”,
340.
F-Secure Management Agent
Status indicator Displays the status of F-Secure
Management Agent.
Management method Displays if the host is standalone (configured
locally) or networked (at least sometimes
connected through a network or a temporar y
link).
Click Configure to configure the F-Secure Manage ment Agen t. For more
information, see “F-Secure Management Agent Settings”, 304.
Toolbar Buttons
Click Show F-Secure Log to view the F-Secure log file (LogFile.log) in a
new Internet browser window. Click Download to download and save the
LogFile.log for later use.
Click Export Settings to open a list of all F-Secure Anti-Virus for
Microsoft Exchange settings in a new Internet browser window. Select
File > Save As... to save the file for later use.
Click Export Statistics to open a list of all F-Secure Anti-Virus for
Microsoft Exchange statistics in a new Internet browser window. Select
File > Save As... to save or print the file for later use.
Click Configure Console to configure the F-Secure Anti-Virus for
Microsoft Exchange Web Console. For instructions, see “Configuring the
Web Console”, 73.
Click Help to open the online help.
Page 73

Using F-Secure Anti-Virus for Microsoft Exchange
4.5 Configuring the Web Console
On the F-Secure Anti-Virus for Microsoft Exchange Web Console
Configuration page you can specify setti ngs for connections to the server.
You can also open the F-Secure Anti-Virus for Microsoft Exchange Web
Console access log from this page.
Limit session timeout Specify the length of time a client can be
connected to the server. When the session
expires, the F-Secure Anti-Virus for
Microsoft Exchange Web Console displays a
warning. The default value is 60 minutes.
Click Show Access Log to view the F-Secure Anti-Virus for Microsoft
Exchange Web Console access log. Note that the Web Console access
log differs from standard web server access logs, as it logs only the first
request per session.
Listen on address Specify the IP address of the F-Secure
Anti-Virus for Microsoft Exchange Web
Console Server.
CHAPTER 4 73
Port Specify the port where the server listens for
connections. The default port is 25023.
Accept connections from
the following hosts
To add a new host in the list, click Add to add new a new line in the table
and then enter the IP address of the host.
Specify a list of hosts which are allowed to
connect to F-Secure Anti-Virus for Microsoft
Exchange Web Console.
Page 74

74
4.6 Using F-Secure Policy Manager Console
In the centralized administration mode, you can open F-Secure Anti-V irus
for Microsoft Exchange components from the Windows Start menu >
Programs > F-Secure Policy Manager Console. When the Policy
Manager Console opens, go to the Advanced Mode user interface by
selecting View > Advanced Mode (this step is required in F-Secure Policy
Manager version 5.50 and later). Then select the Policy tab to view the
F-Secure Anti-Virus for Microsoft Exchange components.
F-Secure Policy Manager Console is used to create policies for F-Secure
Anti-Virus for Microsoft Exchange installations that are running on
selected hosts or groups of hosts. Policies are created by assigning
values to variables shown on the Policy tab of the Properties pane (the
middle pane) in F-Secure Policy Manager Console. To assign a value,
select a variable – marked by the leaf icon – in the Properties pane and
enter the value in the Editor pane (the right pane).
After a policy is created, it must be distributed to hosts by choosing
Distribute from the File menu.
After changing the settings and distributing the po licy, you have to wait for
F-Secure Anti-Virus for Microsoft Exchange to poll the policy.
For testing purposes you may also want to change the polling
intervals. T o do that, select the domain in F-Secure Policy Manager
console and set the Incoming Packages Polling Interval and
Outgoing Packages Update Interval variables to 30-45 seconds.
The variables are located under each of the two trees in the
F-Secure Management Agent / Settings / Communications branch.
Note that since the default polling interval is 10 minutes, it might
take up to 10 minutes for the new setting to take effect.
Alternatively, you can click Poll the server now in F-Secure
Management Agent.
For detailed information on installing and using F-Secure Policy Manager
console, see the F-Secure Policy Manager Administrator’s Guide.
Page 75

Using F-Secure Anti-Virus for Microsoft Exchange
4.7 Modifying Settings and Viewing Statistics
This section describes how you can modify product settings and view
product statistics in both centrally administered and stand-alone mode.
4.7.1 Centrally Administered Mode
To change F-Secure Anti-Virus for Microsoft Exchange settings in the
centrally administered mode, select F-Secure Anti-Virus for Microsoft
Exchange from the Properties pane. Make sure the Policy t ab is selected
and assign values to variables under the Settings branch. Modify settings
by assigning new values to the basic leaf node variables (marked by the
leaf icons) shown in the Policy tab of the Properties pane. Initially, every
variable has a default value, which is displayed in gray. Select the
variable from the Properties pane and enter the new value in the Editor
pane to change it. You can either type the new value or select it from a list
box. If you enter an invalid value, it will be displayed in red in the
Properties pane. Click Clear to revert to the default value or Undo to
cancel the most recent change that has not been distributed. For detailed
explanations of all variables, see “F-Secure Anti-Virus for Microsoft
Exchange Settings”, 126.
CHAPTER 4 75
Settings that are configured during the installation and the initial
setup require that you select the Final check box from the Product
View pane. These settings include Primary and Backup Content
Scanner Servers and Quarantine settings.
Select the Status tab of the Properties pane to view statistics and the
settings that were configured during the installation of F-Secur e Content
Scanner Server and F-Secure Anti-Virus for Microsoft Exchange.
Statistics are updated periodically and can be reset by choosing Reset
Statistics on the Policy tab of the Properties pane. For more information,
see “F-Secure Anti-Virus for Microsoft Exchange Statistics”, 184.
Page 76

76
Changing Settings That Have Been Modified During Installation
or Upgrade
If you want to change a setting that has been modified locally du ring
installation or upgrade, you need to mark the setting as Final in the
restriction editor. The settings descriptions in this manual indicate the
settings for which you need to use the Final restriction. You can also
check in F-Secure Policy Manager Console whether you need to use the
Final restriction for a setting. Do the following:
1. Select the Policy tab and then select the setting you want to check.
2. Now select the Status tab to see if the setting has been modified
locally.
If the setting is not shown in grayed font in the Status view, then
the product uses the setting from the base po licy an d th er ef or e
the Final restriction is not needed.
If the setting is shown in normal black font, then the setting has
been modified locally. You must mark the setting as Final when
you change it.
4.7.2 Stand-alone Mode
To change F-Secure Anti-Virus for Microsoft Exchange settings in
stand-alone mode, open the F-Secure Anti-Virus for Microsoft Exchange
Web Console and select the variables you want to change from the
options tree. For detailed explanations of all variables, see
“Administration with Web Console”, 216.
To view statistics for real-time scanning, select Summary on the options
tree. To reset all counters to zero, click Reset Statistics.
To view statistics for the latest manual scan, select Manual Scanning on
the options tree. The Manual Scanning property page displays the
following statistics: the number of processed mailboxes, the number of
processed Public Folders, the numbers of processed, infected, and
suspicious messages in mailboxes and in the Public Folders. Manual
scanning statistics are reset every time a new manual scan is performed.
Page 77

Using F-Secure Anti-Virus for Microsoft Exchange
4.8 Manually Processing Mailboxes and Public Folders
You can scan mailboxes and Public Folders for viruses and strip
attachments manually at any time. You can also create scheduled scan
tasks to scan mailboxes and Public Folders periodically.
4.8.1 Centrally Administered Mode
You can perform virus scans and strip attachments manually by using
controls under the F-Secure Anti-Virus for Microsoft Exchange /
Operations branch.
To start a manual scan, select Start under F-Secure Anti-Virus for
Microsoft Exchange / Operations / Manual Scanning. Click Start
in the Editor pane. Choose Distribute from the File menu.
To stop a manual scan, select Stop under F-Secure Anti-Virus for
Microsoft Exchange / Operations / Manual Scanning. Click Stop
in the Editor pane. Choose Distribute for the File menu.
To view the scanning report - the total numbers of mailboxes and
Public Folders, and the numbers of processed mailboxes and
Public Folders, open the Reports tab.
For information how to configure options for manual scans, see
“Manual Processing”, 159.
CHAPTER 4 77
Creating Scheduled Operation
Open F-Secure Anti-V irus for Microsof t Exchange > Settings > Sch eduled
Processing settings branch and click Add to start the Scheduled
Operation Wizard.
Page 78

78
Step 1. Enter the name for the new task and select how frequently you want the
operation to be performed.
Once - Only once at the specified time.
Daily - Every day at the specified time, starting from the specified
date.
Weekly - Every week at the specified time on the same day when
the first operation is scheduled to start.
Monthly - Every month at the specified time on the same date
when the first operation is scheduled to start.
Do not use any special characters in the task name.
Click Next to continue.
Step 2. Specify whether you want to process all messages or only those
messages that have not been processed previously during the manual
processing.
Page 79

CHAPTER 4 79
Using F-Secure Anti-Virus for Microsoft Exchange
Specify how many concurrent transactions the scanner can have with
F-Secure Content Scanner Server.
Click Next to continue.
Page 80

80
Step 3. Choose mailboxes that should be processed during the scheduled
operation.
Do not scan mailboxes - Do not process any mailboxes.
Scan all mailboxes - Process all mailboxes.
Scan only included mailboxes - Process all mailboxes specified in
the list.
Scan all except excluded mailboxes - Process all except those
mailboxes specified in the list.
Click Add to add a new mailbox to the list. Click Edit to edit a previously
created entry. Click Remove to remove the selected folder or Remove All
to remove all entries from the list.
By default, F-Secure Anti-Virus for Microsoft Exchange examines all
mailboxes.
Click Next to continue.
Page 81

CHAPTER 4 81
Using F-Secure Anti-Virus for Microsoft Exchange
Step 4. Choose settings for virus scanning of mailboxes during the scheduled
operation, and Click Next to continue.
For settings descriptions, see “Virus Scanning”, 130.
Page 82

82
Step 5. Choose settings for stripping attachments during the scheduled
operation, and click Next to continue.
For settings descriptions, see “Stripping Attachments”, 147.
Page 83

CHAPTER 4 83
Using F-Secure Anti-Virus for Microsoft Exchange
Step 6. Select Public Folders that should be processed during the scheduled
operation.
Do not scan Public Folders - Do not process any Public Folders.
Scan all Public Folders - Process all notes posted to all Public
Folders.
Scan only included Public Folders - Process all notes posted to
Public Folders specified in the list.
Scan all except excluded Public Folders - Process all notes
posted to all Public Folders, except those specified in the list.
Click Add to add a new Public Folder to the list. Click Edit to edit a
previously created entry. Click Remove to remove the selected folder or
Remove All to remove all entries from the list.
By default, F-Secure Anti-Virus for Microsoft Exchange processes all
Public Folders.
Click Next to continue.
Page 84

84
Step 7. Choose settings for virus scanning of Public Folders during the scheduled
operation, and click Next to continue.
For settings descriptions, see “Virus Scanning”, 130.
Page 85

Using F-Secure Anti-Virus for Microsoft Exchange
Step 8. Choose settings for stripping attachments during the scheduled
operation, and click Next to continue.
CHAPTER 4 85
Page 86

86
Step 9. The Scheduled Operation Wizard displays the summary of created
operation. Click Finish accept the new scheduled operation and to exit
the wizard.
4.8.2 Stand-alone Mode
Specify the manual scanning settings on the Manual Scanning property
pages. After you have specified the manual scanning settings, select the
Manual Processing and click Start.
Under Progress, you can view the pr ogress of the manu al scan - the total
numbers of mailboxes and Public Folders, and the numbers of processed
mailboxes and Public Folders. In the bottom of the property page, the
results of the previous manual scan are shown - the numbers of
processed, infected and suspicious messages in the mailboxes and in the
Public Folders.
Page 87

Using F-Secure Anti-Virus for Microsoft Exchange
4.8.3 Creating Scanning Operations
To process mailboxes manually, you need to set up a manual processing
task. For more information, see “Creating Manual Scanning Operation”,
87.
If you want to run scanning tasks frequently, you can set up scheduled
operations. For more information, see “Creating Scheduled Operation”,
102.
Creating Manual Scanning Operation
Start the Manual Scanning Wizard by clicking the Configure... button on
the Manual Scanning page.
Step 1. Specify Messages to Process
CHAPTER 4 87
1. Specify whether you want to process all messages or only those
messages that have not been processed previously.
2. Specify how many concurrent transactions the scanner can have with
F-Secure Content Scanner Server.
Page 88

88
3. Click Next to continue.
If F-Secure Anti-Virus for Microsoft Exchange is operating on a
system that has multiple processors or you are using a
high-performance computer, you can increase performance by
increasing the number of concurrent transactions.
If you want to use the default settings for most of the scanning
settings, click Last to proceed to the last page of the Manual
Scanning wizard where you can see a summary of the scanning
task settings.
Step 2. Select Mailboxes to Process
1. Choose mailboxes that should be processed during the manual
scanning operation.
Do not process mailboxes - Do not process any mailboxes.
Process all mailboxes - Process all mailboxes.
Process only these mailboxes - Process all specified mailboxes.
Process all except these mailboxes - Process all except specified
mailboxes.
Page 89

Using F-Secure Anti-Virus for Microsoft Exchange
Click Add... to a dd a new mailbox to the list. Click the checkb ox in
the column to mark a mailbox to be removed. Click Clear
to remove all currently marked entries from the list.
By default, F-Secure Anti-Virus for Microsoft Exchang e examines all
mailboxes.
2. Click Next to continue.
Step 3. Specify Virus Scanning Settings for Mailboxes
CHAPTER 4 89
Page 90

90
1. Choose settings for virus scanning of mailboxes.
Attachments to scan Specify which message attachments are
checked for viruses.
Do not scan attachments for viruses - Process
messages without scanning any attachment s for
viruses.
Scan all attachments - Scan all message
attachments regardless of filename extension.
Scan all attachments with these extensions Scan all attachments with specified filename
extensions.
Scan all attachments except with these
extensions - Scan all attachments except those
with specified filename extensions.
You can add new file types on the extensions
lists by typing the file extensions in the file
extensions text boxes. Separate the extensions
by spaces.
Scan mail message
body
Specify whether the body of the e-mail message
should be scanned for malicious code.
By default, F-Secure Anti-Virus for Microsoft
Exchange scans message bodies.
Although scanning message bodies can slow
down the performance, it is recommended as a
virus can be carried inside a message body.
Page 91

CHAPTER 4 91
Using F-Secure Anti-Virus for Microsoft Exchange
Enable File Type
Recognition
Action
Action on infected
attachments
Trojans and other malicious code can disguise
themselves with filename extensions which are
usually considered safe to use. Intelligent File
Type Recognition ca n recognize the real file type
of the message attachment and use that while
the attachment is processed. Specify whether
you want to use Intelligent File Type Recognition
or not.
By default, Intelligent File Type Recognition is
disabled during the real-time processing.
Intelligent File T ype Recognition strengthens the
security - you can block unsafe content that has
a safe filename extension (for example, a
Microsoft Word document using the ‘r tf’ filename
extension) and you do not accidentally block
safe content that has unsafe filename extension
(for example, a text file using the ‘doc’ filena m e
extension). Intelligent File T ype Recognition can
degrade the system performance.
Specify whether infected attachments should be
disinfected or dropped.
Disinfect attachment - Try to disinfect the
infected attachment. If the disinfection
succeeds, the recipient receives the dis infected
file instead of the original one. If the disinfection
fails, the infected attachment is dropped, and it
is not delivered to the recipient.
Drop attachment - Do not disinfect or deliver
infected attachments. All infected attachments
are dropped.
Page 92

92
By default, F-Secure Anti-Virus for Microsoft
Exchange tries to disinfect infected attachments.
Quarantine infected
attachments
Send warning
message to mailbox
owner
Specify whether infected attachments should be
placed in the Quarantine or not. For more
information, see “Quarantine Management”,
307.
Specify whether to send a message to the
mailbox owner when an infected attachment is
found. Click Edit... to edit the informational text
file that replaces the infected attachment if it is
dropped.
2. Click Next to continue.
Step 4. Specify Attachment Stripping Settings for Mailboxes
Page 93

CHAPTER 4 93
Using F-Secure Anti-Virus for Microsoft Exchange
1. Choose settings for stripping attachments.
Strip attachments Specify which attachments should be stripped
from messages and public folder notes.
Do not strip - Do not strip any attachments.
Strip all att achments - Strip all attachments from
all messages and notes.
Strip all attachme nts except these allowed - S trip
all except specified attachments.
Strip only these disallowed attachments - Strip
only specified attachments.
You can add new file types on the attachments
lists by typing the file extensions in the allowed
and disallowed attachments text boxes.
Separate the extensions by spaces.
Enable File Type
Recognition
Action
Action on stripped
attachment
Trojans and other malicious code can disguise
themselves with filename extensions which are
usually considered safe to use. Intelligent File
Type Recognition can recognize the real file type
of the message attachment and use that while
the attachment is processed. Specify whether
you want to use Intelligent File Type Recognition
or not.
Specify whether stripped attachments should be
quarantined or dropped.
Quarantine attachment - All stripped
attachments are placed in the Quarantine. For
more information, see “Quarantine
Management”, 307.
Drop attachment - All stripped attachments are
deleted automatically.
Page 94

94
By default, F-Secure Anti-Virus for Microsoft
Exchange quarantines stripped attachments.
Send informational
message to the
mailbox owner
Notify administrator Specify whether the administrator should be
Specify whether an informational message
should be sent to the owner of the mailbox when
an attachment is stripped. Click Edit to edit the
message.
notified when F-Secure Anti-Virus for Microsoft
Exchange strips an attachment.
Do not notify - Do not send any notification to the
administrator.
Send informational alert - Send an informational
alert to the administrator.
Send warning alert - Send a warning alert to the
administrator.
Send security alert - Send a security alert to the
administrator.
2. Click Next to continue.
Page 95

Using F-Secure Anti-Virus for Microsoft Exchange
Step 5. Select Public Folders to Process
1. Select Public Folders that should be processed.
Do not process public folders - Do not process any Public
Folders.
Process all public folders - Process all notes posted to all Public
Folders.
Process only included public folders - Process all notes posted to
the listed Public Folders.
Process all except excluded public folders - Process all notes
posted to all Public Folders, except the listed ones.
CHAPTER 4 95
The notes and attachments to be processed in the selected
folders are defined with the Attachments to Scan and Scan
Mail Message Body settings.
Click Add to add a new Public Folder to the list. Click Clear to
remove the selected folder or Clear All to re move all en tries fr om th e
list. By default, F-Secure Anti-Virus for Microso ft Exchange processes
all Public Folders.
2. Click Next to continue.
Page 96

96
Step 6. Specify Virus Scanning Settings for Public Folders
1. Choose settings for virus scanning of Public Folders.
Attachments to s can Specify which message attachments are
checked for viruses.
Do not scan attachments for viruses - Do not
scan any attachments.
Scan all attachments - Scan all message
attachments.
Scan all attachments with these extensions -
Scan all attachments with specified filename
extensions.
Scan all attachments except with these
extensions - Scan all attachments except those
with specified filename extensions.
Page 97

CHAPTER 4 97
Using F-Secure Anti-Virus for Microsoft Exchange
You can add new file types on the extensions
lists by typing the file extensions in the file
extensions text boxes. Separate the extensions
by spaces.
Scan mail message
body
Enable File Type
Recognition
Action
Specify whether the body of the e-mail message
should be scanned for malicious code.
By default, F-Secure Anti-Virus for Microsoft
Exchange scans message bodies.
Although scanning message bodies can slow
down the performance, it is recommended as a
virus can be carried inside a message body.
Trojans and other malicious code can disguise
themselves with filename extensions which are
usually considered safe to use. Intelligent File
Type Recognition can recognize the real file type
of the message attachment and use that while
the attachment is processed. Specify whether
you want to use Intelligent File Type Recognition
or not.
By default, Intelligent File Type Recognition is
disabled during the real-time processing.
Intelligent File T ype Recognition strengthens the
security - you can block unsafe content that has
a safe filename extension (for example, a
Microsoft Word document using the ‘rtf’ filename
extension) and you do not accidentally block
safe content that has unsafe filename extension
(for example, a text file using the ‘doc’ filename
extension). Intelligent File Ty pe Recognition can
degrade the system performance.
Action on infected
attachments
Specify whether infected attachments should be
disinfected or dropped.
Page 98

98
Disinfect attachment - Try to disinfect the
infected attachment. If the disinfection
succeeds, the recipient receives the disinfected
file instead of the original one. If the disinfection
fails, the infected attachment is dropped, and it
is not delivered to the recipient.
Drop attachment - Do not disinfect or deliver
infected attachments. All infected attachments
are dropped.
By default, F-Secure Anti-Virus for Microsoft
Exchange tries to disinfect infected attachments.
Quarantine infected
attachments
Send warning
message to the
originator
Specify whether infecte d attachments should be
placed in the Quarantine or not. For more
information, see “Quarantine Management”,
307.
Specify whether to send a war ning message to
the originator of the public folder message,
which contained an infected attachment. Click
Edit to edit the message.
2. Click Next to continue.
Page 99

Using F-Secure Anti-Virus for Microsoft Exchange
Step 7. Specify Attachment Stripping Settings for Public
Folders
CHAPTER 4 99
1. Choose settings for stripping attachments.
Strip attachments Specify which attachments should be stripped
from messages and public folder notes.
Do not strip - Do not strip any attachments.
Strip all att achments - Strip all attachments from
all messages and notes.
Strip all attachme nts except these allowed - S trip
all except specified attachments.
Strip only these disallowed attachments - Strip
only specified attachments.
Page 100

100
You can add new file types on the attachments
lists by typing the file extensions in the allowed
and disallowed attachments text boxes.
Separate the extensions by spaces.
Enable File Type
Recognition
Action
Action on stripped
attachments
Send the
informational
message to the
originator
Trojans and other malicious code can disguise
themselves with filename extensions which are
usually considered safe to use. Intelligent File
Type Recognition can recognize the real file type
of the message attachment and use that while
the attachment is processed. Specify whether
you want to use Intelligent File Type Recognition
or not.
Specify whether stripped attachments should be
quarantined or dropped.
Quarantine attachment - All stripped
attachments are placed in the Quarantine. For
more information, see “Quarantine
Management”, 307.
Drop attachment - All stripped attachments ar e
deleted automatically.
By default, F-Secure Anti-Virus for Microsoft
Exchange quarantines stripped attachments.
Specify whether an informational message
should be sent to the originator of the message
when an attachment is stripped. Click Edit to
edit the message.
 Loading...
Loading...