Page 1

®
RestoreIT
User’s Guide
Network
Page 2

Copyright Notice
Copyright© 2006 FarStone Technology, Inc.
All Rights Reserved.
No part of this publication may be copied, transmitted, stored in a retrieval system, or translated
into any language in any form or by any means without the expressed written permission of
FarStone Technology, Inc.
FarStone grants you the right to use one copy of the enclosed software program ("SOFTWARE") on a
single computer. If the SOFTWARE is installed on a network, or more than one user can run the
SOFTWARE at the same time, you must purchase an additional license for each additional user or
computer.
Trademarks
• RestoreIT® and RestoreIT® Network are registered trademarks of FarStone Technology, Inc.
• Microsoft®, Windows® and MS-DOS® are registered trademarks of Microsoft Corporation.
• Pentium is a registered trademark of Intel Corporation.
• Other product names mentioned in this manual may be trademarks or registered trademarks of
their respective companies and are hereby acknowledged.
Printed in the United States of America.
FarStone Technology, Inc.
6 Morgan, Suite 160
Irvine, CA 92618
Phone: (949) 458-3666
Fax: (949) 458-3633
Technical Support:
For technical support, please contact us at:
http://www.farstone.com/home/ensite/support/support.shtml
Or use our online support system and FAQ at www.farstone.com.
Copyright © 2000-2006 FarStone Technology, Inc. All rights reserved.
Page 3

Contents
Chapter 1 Introduction..............................................................................- 6 -
........................................................................................................................- 6 - 1-1 Introduction to RestoreIT Network
..........................................................................- 6 - 1-2 RestoreIT Network Component Introduction and Features
Chapter 2 Installation .............................................................................- 10 -
...............................................................................................................................................- 10 - 2-1 System Requirements
................................................................................................................................- 10 - 2-2 Installing RITN Administrator
................................................................................................................................................- 11 - 2-3 Installing RITN Client
...........................................................................................................................- 13 - 2-4 Remotely Deploying RITN Client
Chapter 3 Using RITN Administrator .......................................................- 17 -
.....................................................................................................................- 17 - 3-1 Introduction to RITN Administrator
...............................................................................................................................- 17 - 3-2 Launching RITN Administrator
...............................................................................................................................................- 17 - 3-3 Member Management
......................................................................................................................................- 18 - 3-3.1 Creating a New Group
.............................................................................................................................................- 18 - 3-3.2 Renaming a Group
................................................................................................................................................- 18 - 3-3.3 Deleting a Group
...............................................................................................................- 18 - 3-3.4 Moving a Client to another Group
.............................................................................................................................................- 18 - 3-3.5 Renaming a Client
.................................................................................................................................................- 19 - 3-3.6 Deleting a Client
................................................................................................................................- 1 9 - 3-3.7 Viewing Client Properties
.................................................................................................................................- 19 - 3-4 Backing up Client Computers
................................................................................- 19 - 3-4.1 Manually Creating a Backup for Client Computers
..............................................................................................- 20 - 3-4.2 Automatically Backing up Client Computer
....................................................................................................................................- 21 - 3-5 Restoring Client Computers
....................................................................................................- 21 - 3-5.1 Manually Restoring Client Computer(s)
...........................................................................................- 23 - 3-5.2 Automatically Restoring Client Computer(s)
......................................................................................................................................- 23 - 3-6 Mange RITN Client Policies
3-6.1 Enabling/Disabling Incremental Backup....................................................................................................- 23 -
..........................................................................................................- 24 - 3-6.2 Enabling/Disabling File-level Backup
.........................................................................................................................- 25 - 3-6.3 RITN Client Function Control
....................................................................................................................................- 25 - 3-7 RITN Administrator Options
Port Settings.................................................................................................................................................................................... - 26 -
............................................................................................................................................. - 26 - Administrator Password Settings
.................................................................................................................................................................................... - 26 - Log File Size
................................................................................................................................................................................... - 26 - Refresh Time
Chapter 4 Using RITN Client.....................................................................- 28 -
.....................................................................................................................................- 28 - 4-1 Introduction to RITN Client
.......................................................................................................................- 28 - 4-2 Connecting to RITN Administrator
..................................................................................................................................................- 28 - 4-3 Opening RITN Client
..........................................................................................................................................- 29 - 4-4 Backing up Your System
.............................................................................................................................................- 30 - 4-5 Restoring Your System
......................................................................................................................................................- 30 - 4-5.1 Quick Restore
............................................................................................- 30 - 4-5.2 Restoring to any Incremental Backup Point
...............................................................................................................................- 31 - 4-6 File Level Backup and Restore
.......................................................................................................................- 31 - 4-6.1 How to Restore a Specific File
............................................................................................................- 32 - 3-6.2 Backing up Specific Files or Folders
.....................................................................................................- 32 - 3-6.2 Configuring File-Level Backup Settings
Chapter 5 Removing RestoreIT Network .................................................- 37 -
...............................................................................................................................- 37 - 5-1 Removing RITN Administrator
...................................................................................................................- 37 - 5-2 Removing RestoreIT Network Clinet
Page 4

Chapter 6 Software License Agreement....................................................- 39 -
- 4 -
Page 5

1
Introduction
Page 6
Chapter 1
Introduction
Instant recovery from a system crash, virus attack, and accidental data deletion.
1-1 Introduction to RestoreIT Network
RestoreIT Network 4.0 is a revolutionary real time system restoration utility that runs over a TCP/IP
network. Once installed, it continually
computers and allows an administrator or client to recover lost data after a system crash, virus
attack, faulty software installation, accidental file deletion or unintentional formatting of their hard
drive. In merely a few minutes, if not seconds, all of the content of a hard drive can be restored back
to a point in time when the computer was functioning properly. File-Level Backup and Restore
further allow users to restore individual files without rolling back their whole system.
RestoreIT Network allows network administrators to manage client computers’ backup strategies and
remotely backup their systems over a network. Network administrators can even control the server
computer (RITN Administrator) or any client computer over the network by using the included RestoreIT
Desktop Tool.
1-2 RestoreIT Network Component Introduction and Features
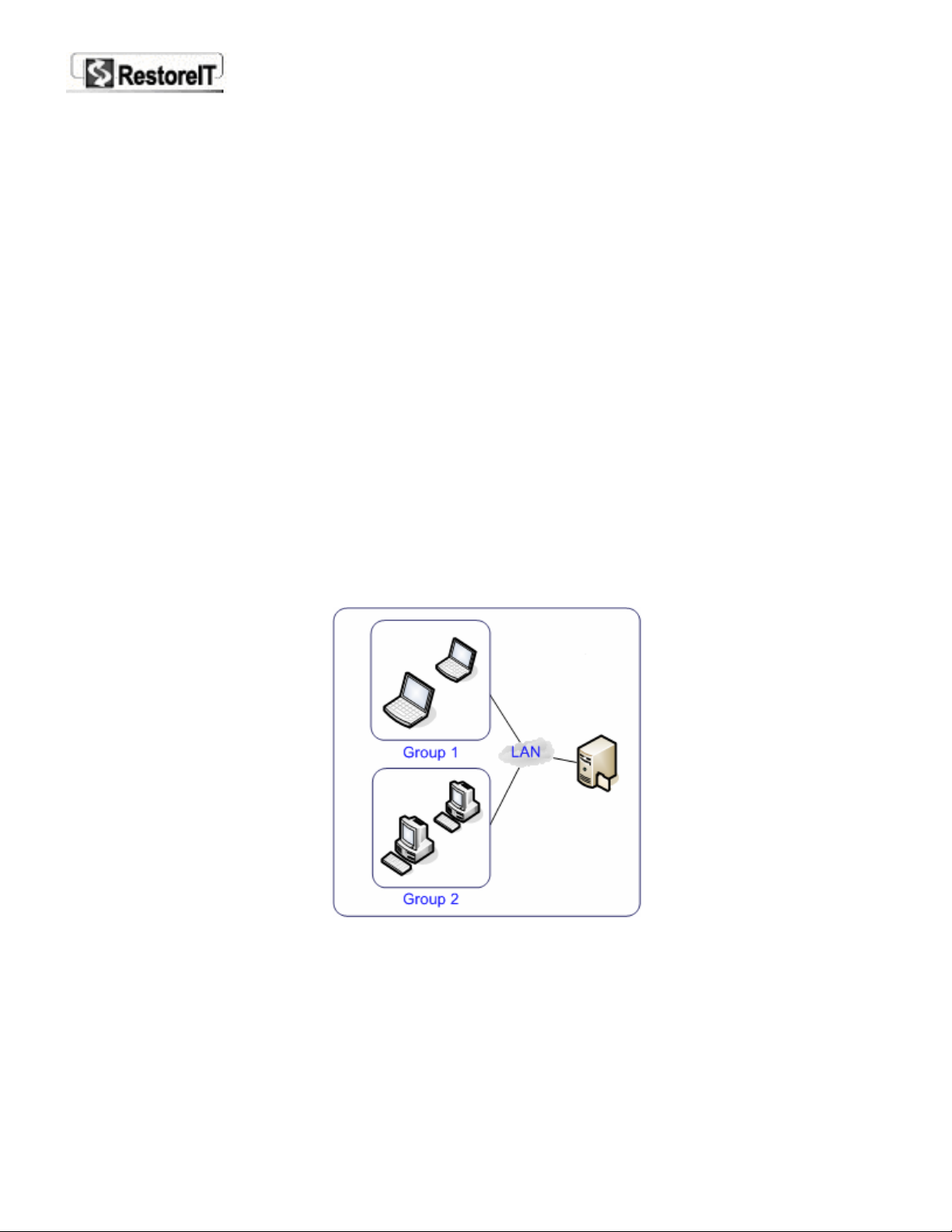
RestoreIT Network is based on a client-server model. One server (RITN Administrator) and several clients
(RITN Client) structure is shown below. One RITN Administrator can manage up to 100 clients at a time.
monitors and keeps a complete record of all activities on client
¾ RITN Administrator -- RestoreIT Network server module
RITN Administrator (referred as “RITN Administrator” thereafter) resides on the server computer of the
local area network (LAN). It allows the network administrator to manage all clients’ or group’s
backup/restore strategy in a user friendly interface. Once installed, a network administrator can
simultaneously deploy RITN Client on multiple client computers through the RITN Administrator interface.
Features of RITN Administrator:
Page 7

z Remotely create Backup Point
Manually create a backup image on client computers though RITN Administrator. An administrator can
choose to back up Drive C: only or the whole hard disk on the client computer. The backup image file is
stored in a RestoreIT Secure Area on client computers.
z Set backup/restore schedule for client computers
Set a schedule for clients that automatically create/restore a Backup Point at specified times.
z Enable/Disable system backup and File Level Backup
Disable the system backup and/or file-level backup functions on specified clients. Once disabled, the
previous settings for backup/restore schedule or file-level settings will stop functioning. The client can
not manually perform these operations.
z Show/Hide RITN Client main interface
Hide the RITN Client main interface to prevent any manual operation on the client side. Once prevented,
the client computer can only perform backup/restoration according to RITN Administrator’s settings or
commands.
z Group clients
Divide clients in groups to help manage the members. Administrators can regroup clients at any time.
z View Client’s logs
RestoreIT Network records any activities on RITN Administrator, such as client’s login, changing settings,
and performing a backup or restoration. Administrators can choose to view an individual client log or all
clients’ logs.
z Be remotely controlled through RestoreIT Remote Desktop Tool
Control RITN Administrator on any computer in the LAN through the included RestoreIT Remote Desktop
Tool.
z Password protection
The Administration Password is required to login RestoreIT Network Administrator and enter Pre-OS
mode on Client side.
z Easy to use
A clear and friendly Graphical User Interface (GUI) makes RestoreIT Network easy to use. Even a
new network administrator can manage clients, configure settings and perform backup/restore
operations without difficulty.
¾ RITN Client -- RITN Client module
RITN Client (referred as “RITN Client” thereafter) resides on the client for each computer in the local area
network. Client users can perform operations including system backup and restoration, file-level backup,
setting and restoring files. All operations requiring authorization from the network administrator can be
done through RITN Administrator.
Features of RITN Clients:
z Incremental System Backup
Back up the Drive C: or the whole hard disk as an image file to store on the local hard disk. System
backup takes an incremental backup mechanism. It only and incrementally backs up all changes (e.g.
additions/deletions) since the last backup point was created. It takes only seconds to complete and is
stored in a hidden protected RestoreIT Secure Area on the local hard disk. System incremental backups
Page 8

can be done on RITN Client (only when authorized), through RITN Administrator or automatically done
by schedule.
z File-Level Backup and Restore
Back up and restore previous versions of a specific file after it has been deleted, changed or
overwritten, without having to restore the entire system to an earlier point in time. File-level
settings and restoration should be done on
settings and to restore files should be authorized by the network administrator from the RITN
Administrator.
z 100% Protection
RITN Client, but the ability to configure file-level backup
RestoreIT Network allows users to instantly recover from accidental disk formatting, file deletion,
virus attacks or a system crash on client computers. It offers complete system protection, 24 hours
a day, 365 days a year.
z Kill viruses, rescue files
Network users can download files and open e-mail attachments without having to worry about virus
attacks. Infected or damaged files can be rescued in seconds if a problem occurs.
z Only a fraction of disk space used
RestoreIT Network uses a unique real-time incremental backup technology, taking up only 5-10
percent of available hard disk space.
z Easy to use
A clear and friendly Graphical User Interface (GUI) makes RestoreIT easy to use (only if allowed by
RITN Administrator). Even a novice can easily restore a computer back to working order without
having to call technical support.
z Intelligent Data Integrity Check
RestoreIT Network checks the integrity of the data in the latest Incremental Backup Point and
marks it as “a
mbiguous” if any inconsistencies are found.
- 8 -
Page 9

Chapter 2
Installation
Page 10

Chapter 2
Installation
2-1 System Requirements
Administrator Computer
Microsoft Windows 2000 (SP4)/XP/2003 Server
450 MHz Pentium III processor (or compatible) or better
30 MB of free hard disk drive
256 MB of RAM
Microsoft Internet Explorer 5.5 or higher
10/100Mbps Network Adaptor
TCP/IP Internet Protocol
Client Computer
Windows 2000 Pro(SP4)/XP Pro/XP Media Center
Intel Pentium processor at 133 MHz
20MB for the program and 5 to 10% of the total hard drive space (at least 1000 MB) for backup activities.
256 MB of RAM
10/100Mbps Network Adaptor
TCP/IP Internet Protocol
Microsoft Internet Explorer 5.5 or higher
CD/DVD recorder (optional)
2-2 Installing RITN Administrator
Follow the steps below to install RITN Administrator on the server computer of the LAN:
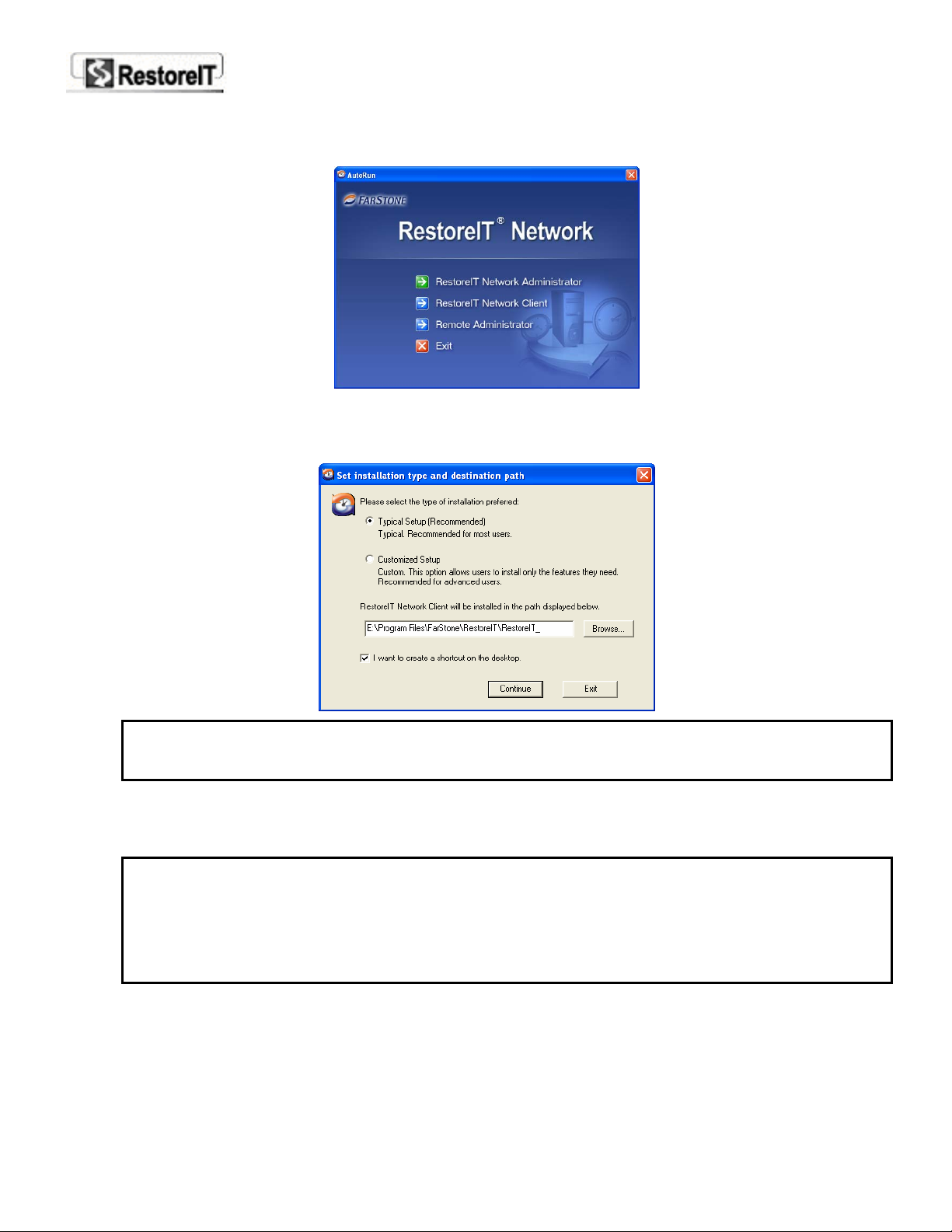
1. Insert the RestoreIT Network CD-ROM disc. The Installation Guide (shown below) should start
automatically. If it does not, run autorun.exe directly from the disc.
2. Click RestoreIT Network Administrator to start the Setup wizard.
3. When the RITN Administrator install screen appears, select Next to go to the next step.
4. When the License Agreement screen appears, select I accept the terms… to continue.
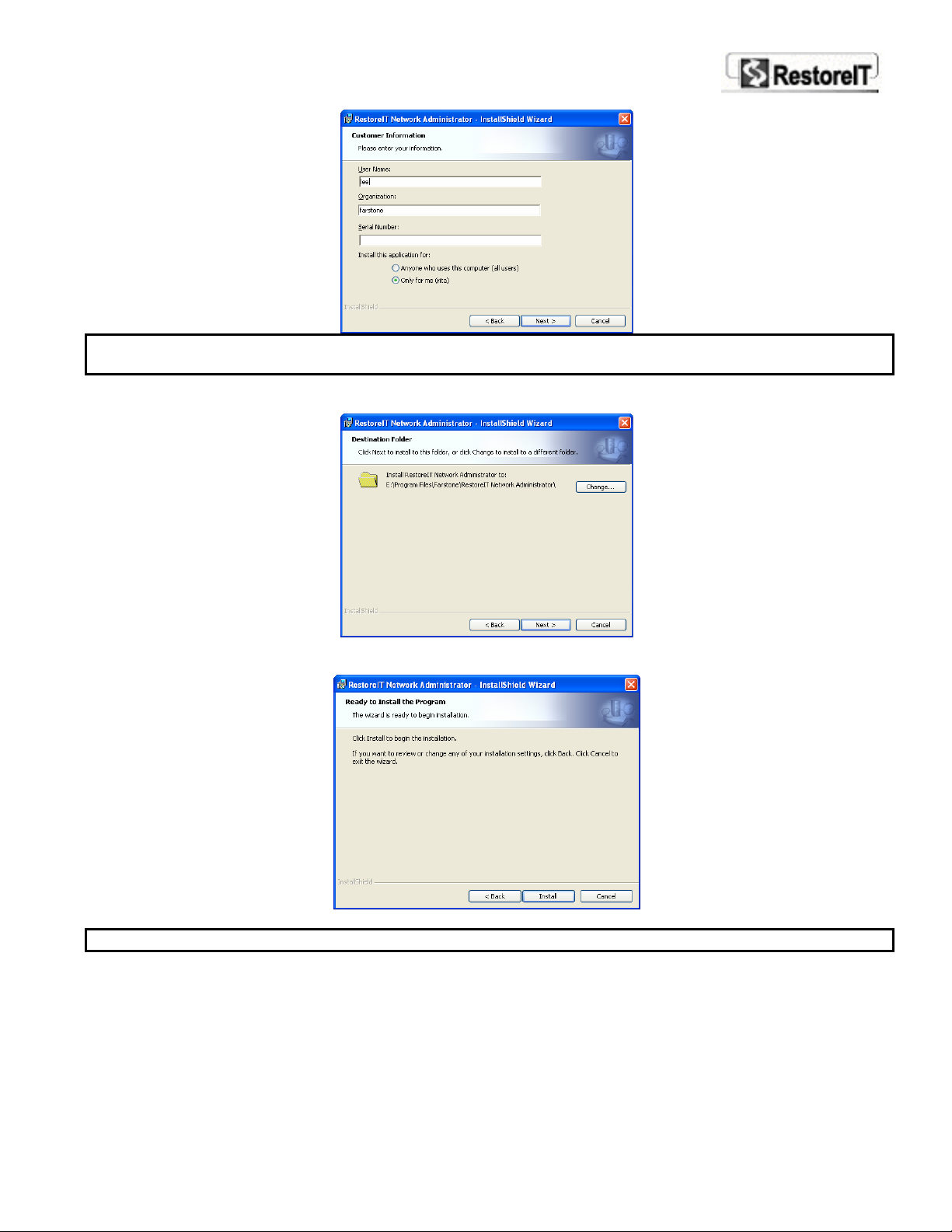
5. Enter the required information and your serial number. Select Continue to continue.
Page 11
Note: If you do not enter a serial number RestoreIT will install a trial version that has limitations on
time and functions of the application.
6. RITN Administrator will be installed in the path displayed. You can click Browse to choose
another location to install the program, or leave it as default. Click Next to continue.
7. A prompt message appears to confirm your settings. Click Install once you have confirmed the
settings to start the installation process.
8. After RITN Administrator is successfully installed. Click Finish to exit the Setup wizard.
Note: You do not need to restart the computer after the installation of RITN Administrator.
2-3 Installing RITN Client
Once RITN Administrator is installed, you can remotely deploy RITN Client on multiple computers over
the LAN by using the Remote Install Tool from the RITN Administrator main interface. Please refer to
the next section for related instructions.
- 11 -
Page 12
Follow the steps below to install RITN Client program on a single client computer:
1. Insert the RestoreIT Network Installation Disc. The Installation Guide (shown below) should start
automatically. If it does not, run autorun.exe directly from the disc.
2. Click RestoreIT Network Client to start the Setup wizard.
3. The RITN Client install screen appears, select Continue to go to the next step.
4. When the License Agreement screen appears, select I Accept to continue.
5. Select an install type, Typical Setup (Recommend) or Customized Setup.
Note: Typical Setup will apply default settings in the following steps to install RITN Client on
the computer. We recommend that normal users choose Typical Setup. Customized Setup
allows manual settings and is recommended for advanced users.
RITN Client will be installed in the path displayed. You can choose anther location to install RITN
Client, or leave it as default.
6. Click Continue and RITN Client will check the disk status to see if there is enough space to
create a RestoreIT Secure Area.
Note: RestoreIT Secure Area is space allocated from the hard drive. It is a hidden, protected
area, used to store the system Incremental Backup Points, and File Backup Records. The
RestoreIT Secure Area cannot be resized after it is created. For better performance, we
recommend that you allocate at least 10% of your total hard drive space for the RestoreIT
Secure Area.
Note: Typical Setup will skip this step
After the system check, RITN Client will give a recommended size for the Secure Area (at least
1000 MB is required), and available space and list the space usage of each partition.
- 12 -
Page 13
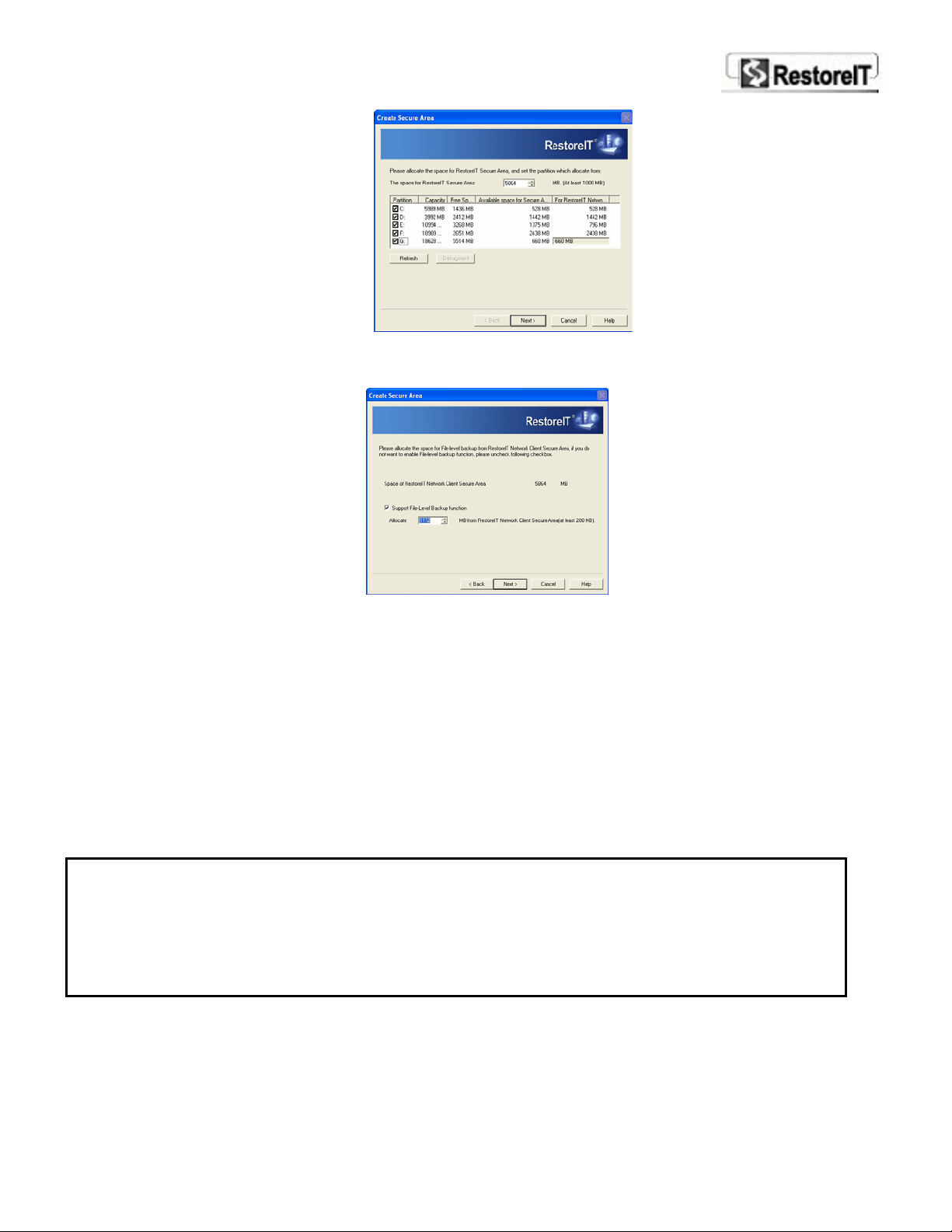
You can modify each partition usage according to your need. Click Refresh below the partition
list to activate your modification.
7. After you have designated the partition space, click Next to continue.
Specify a size from the RestoreIT Secure Area to save File-Level Backup data (At least 200MB is
required).
8. Click Next to continue the installation.
9. You will be prompted to restart the computer. Please eject the RestoreIT Network Installation
Disc and click OK. RestoreIT should start an initialization and create the Secure Area. After that it
will automatically restart the computer and create an initial backup point. When Windows starts,
the installation process is complete.
2-4 Remotely Deploying RITN Client
Once RITN Administrator is installed, you can remotely deploy RITN Client on multiple computers over
the LAN by using Remote Install Tool from the RITN Administrator main interface.
Note: Before the RITN Administrator performs a remote setup, please make sure the Sharing and
Security module in Local Security Settings is set to “Classic” on the client computer.
To set this option, click Run from Start Menu on windows, type in “secpol.msc” to launch Local
Security Settings window. Locate Security Settings>Local Policies> Security Option from the
directory in the left panel. Find the item Network access: sharing and security model for local
accounts from the policy list in the right panel, double click it. In the popup dialog box, select
Classic-local users authenticate as themselves, and click Apply.
To deploy RestoreIT on multiple computers:
1. Select Tools Æ Remote Install Tool from the menu bar of RITN Administrator main interface.
2.
Select the RestoreIT Network Installer from the installer list and click Next continue.
- 13 -
Page 14

3. (For single setup only)
Select Install to single computer tab (shown as below).
Enter the computer name. You can click Browse button to locate it from the local area network list.
In Login options, enter the user name and password so that the installer can get the remote setup
authentication on the client computer.
4. (For multiple setups only)
Select Install to multiple computers tab (shown as below).
Note: To be able to install RITN Client program on multiple computer in a group on a LAN
simultaneously, make sure a Windows account with the same user name and password is
created on all of these computers beforehand.
First you need to configure a group’s login information. Click on one group name, and enter the same user
name and password that was previously created in Login options on the right side. Remember to check
the box “Remember password” below.
Then select the target computer to install the program to.
- 14 -
Page 15

You can choose a whole group by clicking the box before the group name. When a whole group is selected,
it will use the group configuration you have set just now as the login option for all the computers.
You can also double click a group name to unfold it and select specific computers from the list. You can
specify the login option for each computer individually. Highlight the target computer and specify login
settings in the right. When setting the login option for a computer, you can use the group configuration by
checking the “Use group config” box, or enter another account name and password, and check
“Remember password” option.
Note: Setting login option for a computer does not select it as a target computer to install the program
on. Please remember to check the box before the computer name after you have set login option for it.
5. Click Next to start installing RITN Client on the selected computer. This may take a few minutes to
complete and it requires a restart of the client computer. As the client computer restarts, the program
should be successfully installed.
6. You will the see progress information on the RITN Administrator side. Click Finish to exit when the
operation complete.
- 15 -
Page 16

Chapter 3
Using RITN Administrator
- 16 -
Page 17

Chapter 3
Using RITN Administrator
3-1 Introduction to RITN Administrator
RITN Administrator is the server side of RestoreIT Network. It is installed on the server computer of the
local area network (LAN). It allows the network administrator to manage all Clients’ or Group’s
backup/restore strategy in a user friendly interface.
3-2 Launching RITN Administrator
To launch RITN Administrator in Windows, double-click the RestoreIT icon on the desktop, or
select Start on the Windows taskbar, then All Programs Æ RestoreIT Network Administrator Æ
RestoreIT Network RITN Administrator.
Enter the administrator password to start the program (shown below).
Note: Upon launching the program for the first time after installation, you will be asked to set the
administrator password. Follow the on-screen message to set the password. You can change it any
time from RITN Administrator Æ Tools Æ Options Æ Set Password.
The left panel is the member list. Here you can group your clients, rename them, view client
properties and log files.
The upper area of the right part is the functions page. Here you can perform backup and restore
operations, set schedules and configure settings for clients.
The lower area of the right part is the log of activities on the RITN Administrator.
3-3 Member Management
Each time when a client computer enters Windows and connects to the network server, it will
automatically log into the RITN Administrator. All clients logged into the RITN Administrator will
Page 18

appear in the left panel of the main interface. You can divide your clients into groups to help your
management. Before a client is grouped, it is shown under the default group.
Note: The administrator can not manually add a client in the RITN Administrator main interface. It
only displays the clients that have logged into the RITN Administrator.
3-3.1 Creating a New Group
To create a new group:
1. Select Groups Æ New Group from the menu bar of the RITN Administrator main interface, or
right click on an existing group name and select New Group from the right-click menu.
2. Enter a name for the group and click OK.
Note: A group name cannot contain any of the following characters: / \ : * ? “ < > |
3-3.2 Renaming a Group
You can change the name of an existing group.
To rename a group:
1. Select an existing group (highlighted in blue) and choose Groups Æ Rename from the menu
bar of the RITN Administrator main interface, or right click on an existing group name and
select Rename from the right-click menu.
2. Enter the new name in the name box. Click on any place outside the name box to finish.
3-3.3 Deleting a Group
You can delete an existing group. All the clients under the deleted group will automatically moved
the default group.
To delete a group:
1. Select an existing group (highlighted in blue) and choose Groups Æ Delete from the menu bar
of the RITN Administrator main interface, or right click on an existing group name and select
Delete from the right-click menu.
2. A confirmation dialog box should appear to get your confirmation. Click Yes to delete the target
group and all clients under it will be moved to the default group.
3-3.4 Moving a Client to another Group
You regroup your clients by moving it to another group. Note: you can move one client at a time.
To move a Client to another group, do either of the following:
z Directly drag-and-drop a client to another group. Or
z Select a client (highlighted in blue) and choose Groups Æ Change to from the menu bar of the
RITN Administrator main interface, choose the group name you want to move to. Or
z Right click on the wanted client and select Change to, then the group name you want to move
it to.
3-3.5 Renaming a Client
As default, the client name is the computer name on which the RITN Client is installed. You can
change the client name in RestoreIT Network to help you recognize and manage this resource. Note:
Renaming can only be occur when the client is online.
To rename a client:
z Select a client (highlighted in blue) and choose Groups Æ Rename from the menu bar of the
RITN Administrator main interface, choose the group name you want to move it to. Or
- 18 -
Page 19

z Right click on the wanted client and select Change to, then the group name you want to move
it to.
3-3.6 Deleting a Client
You can delete a client from client list.
To delete a client:
1. Select the wanted client (highlighted in blue) and choose Groups Æ Delete from the menu bar
of the RITN Administrator main interface, or right click on the client name and select Delete
from the right-click menu.
2. A confirmation dialog box should appear to get your confirmation. Click Yes to delete it from the
RITN Administrator.
3-3.7 Viewing Client Properties
You can view detailed information of a client, including its computer name, IP address, MAC address
and the usage of the RestoreIT Secure Area on the client computer.
To view a Client’s properties:
Select the wanted client (highlighted in blue) and choose Groups Æ Properties from the menu bar
of the RITN Administrator main interface, or right click on the client name and select Properties
from the right-click menu. The Properties dialog box should appear.
Note: You can also change a client name in the Properties dialog box.
3-4 Backing up Client Computers
RestoreIT Network allows the network administrator to remotely back up specified client computers
from the RITN Administrator. A manual backup can be performed at any time. In addition, backup
schedules can be set to automatically back up at specified times.
3-4.1 Manually Creating a Backup for Client Computers
You can specified an online client or a group of clients and create a backup point for them. The
backup file is stored in the RestoreIT Secure Area on the respective local hard drive.
Note: Creating an Incremental Backup Point (IBP) requires a restart of the client computer.
To create an IBP for client computer:
3. Select an online client or a group from the left panel of the RITN Administrator main interface.
Note:
1. If you choose a group, make sure all clients have logged into the RITN Administrator.
2. If some clients are not online, the IBP will not be created for the offline client. When you choose
to restore to this IBP later, these excluded computers cannot be restored.
4. Choose Backup page from the function panel in the upper right of the RITN Administrator main
interface.
5. Enter a name for the backup point in the Incremental Backup Point Name box.
- 19 -
Page 20

6. Click Create Now to start the operation.
Once the operation starts, the Client icon in the RITN Administrator interface should change to
working status
and you will see a progressive status bar in the function panel (shown below).
Note: The backing up process runs in background on the client computer. There will be no
interference with the current operation of client computer usage.
However, RestoreIT needs to lock the hard drive during the backup process. If any program is
currently writing to or reading from the hard drive on the client computer, it will not create the
backup. You will be notified if the backup operation failed on any client computer. You can also
check if the operation succeeded from the Historic Record panel.
7. When the IBP is successfully created, click Finish to return.
3-4.2 Automatically Backing up Client Computer
RITN Administrator allows you to set a schedule for a specified client or a group of clients to create a
Backup Point automatically.
Note: If the computer or any computer of the group is not started at the schedule backup time, you
will be notified of the situation and be provided with the choice of continuing or canceling the
operation.
To set backup schedule:
1. Select an online client or a group from the left panel of the RITN Administrator main interface.
2. Choose Schedule page from the function panel in the upper right of the RITN Administrator
main interface. (shown blow).
Here are detailed instructions on to choose these options:
z Create a Backup Point Automatically
◊ Create new Backup Point at every system startup
- 20 -
Page 21

If this option is chosen, a new IBP will be created on the client computer every time it boots
up.
◊ Create a new Backup Point every (number of) days
Specify a number between 1 and 30 days.
If this option is chosen, a new IBP will be created on the client computer every number of
day(s) that is set. Note: These days are not accumulated. For example, if the setting is for
every two days and the computer does not start up within six days, only one IBP will be
created the next time it is started.
z Create a Backup Point while system is running
◊ Create new Backup Point every (number of) hour(s) since system starts up
Specify a number from 1 to 24.
If this option is chosen, a new IBP will be created every specified number of hour(s) since the
client computer starts up.
3. After you have made your selection, click Apply to activate your settings.
Once a schedule is set for a client, and if the client computer is offline at the scheduled time, the
backup job will be automatically canceled and you will be notified with a dialog box in the RITN
Administrator.
If it is set for a group, if some client computers of this group are offline at the scheduled time, you
will be notified with a dialog box in the RITN Administrator asking if you would like to continue the
backup on the online clients. You can choose to cancel the job or continue to backup the online
computers.
3-5 Restoring Client Computers
RestoreIT Network allows the network administrator to remotely restore specified client computers
from the RITN Administrator. You can perform a manual restoration any time, or set a schedule to
automatically restore at the specified time.
3-5.1 Manually Restoring Client Computer(s)
You can specify an online client or a group of clients to restore their system.
To manually restore Client computer(s):
1. Select an online client or a group from the left panel of the RITN Administrator main interface.
Note:
1. If you choose a group, make sure all clients have logged into the RITN Administrator.
2. If some clients are not online, you will be notified in a later step. You can choose to
continue with the operation but only online computers will be restored.
2. Choose Restore page from the function panel in the upper right of the RITN Administrator main
interface.
All available backup points will be listed in the box (shown below)
- 21 -
Page 22

Note:
If you have chosen a client, all IBP of the client computer will be listed, including those created
from the RITN Administrator, created from RITN Client or those automatically created according
to schedule.
If you have chosen a group, only those “group backup points” manually created from RITN
Administrator will be listed.
3. Select a Backup Point to restore (highlighted in blue) and click Next.
4. Select a restore mode. You can choose to restore the Drive C: only or the entire hard disk.
Click Next to continue.
5. Some detailed information and possible results of the restoration will be displayed for you to
confirm your settings.
The restoration requires a restart of the client computer. To avoid unexpected errors, click
Notify Now link to send a message to the client about the restoration. (Optional)
6. After you have confirmed your selections, click Restore Now to start the operation.
If you choose to restore a client, skip the next step.
7. If you choose to restore a group, you will be prompted to confirm your operation. Click OK to
continue.
Note:
If there are some offline clients, you will be notified with a message asking if you would like to
continue with the online clients. Click OK to continue.
8. The client computer should be forced to restart and begin the restoration.
Once the restoration begins, the client icon should change to working status
a progressive status bar in the function panel.
Note:
The restoration cannot be canceled once it starts. You cannot perform any other operation on the
working clients during this process.
When restoring a group, the time needed for these computers will be different, depending on the
data amount involved with each computer. Whenever a computer finishes restoration the icon of
this computer will be changed back to normal status in the RITN Administrator interface.
, and you will see
9. When the restoration finishes, the client computer should automatically restart to Windows. The
icon of the computer in the RITN Administrator interface will change back to normal status.
Note:
If you have chosen to restore a group, the time needed for each computer is different, depending
- 22 -
Page 23

on the data amount involved with each one. Whenever a computer finishes restoration, the icon
of this computer will be changed back to normal status in the RITN Administrator interface.
After all the computers have been successfully restored, click Finish to return.
3-5.2 Automatically Restoring Client Computer(s)
RITN Administrator allows to automatically restore a client computer or a group of computers to the
latest backup point on their computer(s) each time the system(s) starts up.
Note:
The “latest backup point” here means the one among all backup points there, including those
created by the network administrator from the RITN Administrator, those created by the client
themselves or those automatically created according to a schedule.
Based on this concept, if you choose a group to enable a restore schedule for, the latest backup
point of each computer is different. It would be the latest backup point of the individual
computers.
To enable restore schedule for Client computer(s):
1. Select an online client or a group from the left panel of the RITN Administrator main interface.
2. Choose Schedule from the function panel in the upper right of the RITN Administrator main
interface. (shown below)
3. Check the option box under Incremental Restore Schedule and choose to restore drive C: or
the entire hard disk from the dropdown menu.
4. Click Apply to apply your settings. If the settings are successfully applied, the Apply button will
change to gray.
3-6 Manage RITN Client Policies
RestoreIT Network allow the network administrator to manage RITN Client policies like
enabling/disabling incremental backup and/or file-level backup, disabling certain functions on RITN
Client, or hiding the entire RITN Client interface to prevent any manual operations on the client side.
3-6.1 Enabling/Disabling Incremental Backup
Normally incremental backup should be enabled to protect client computers continuously. In some
cases like installing new software; it may require disabling of the function temporarily. RITN
Administrator provides a conveniently way to enable/disable incremental backup feature on specified
client computer(s), while not affecting other clients.
Once the incremental backup feature is disabled:
The network administrator cannot manually create an IBP from the RITN Administrator for the client;
The client cannot use any IBP function. (The IBP function on the RITN Client interface will be disabled)
Previous scheduled IBP backup/restore tasks will be stopped. (The Schedule settings on the RITN
Administrator interface will be disabled.)
- 23 -
Page 24

To disable/enable incremental backup:
1. Select a client or a group from the left panel of the RITN Administrator main interface.
Note:
This operation will take effect for both online and offline clients.
2. Choose Settings from the function panel in the upper right of the RITN Administrator main
interface.
3. Check the Enable Incremental Backup box under Backup.
4. Click Apply to activate the settings. If the settings are successfully applied, the Apply button will
change to gray.
3-6.2 Enabling/Disabling File-level Backup
File-Level Backup feature backs up previous versions of a specific file on the client computer after it
has been deleted, changed or overwritten. It allows clients to restore individual files without having
to restore the entire system to an earlier point in time.
Configuring files to back up and the operation of restoring files should be done on
ability to configure file-level backup settings and to restore files should be authorized by the network
administrator from the RITN Administrator.
Normally file-level backup should be enabled to ensure clients’ files get continuous protection, but in
some cases you may need to disable the feature for some clients temporarily.
Once the file-level backup feature is disabled:
Client user cannot configure file backup settings or restore any files; (The File-Level Backup
functions is disabled in the RITN Client interface)
All existing file backup tasks of the executed client will stop working;
All previously created file backups still exist in the RestoreIT Secure Area on the client computer, but
will not be able to use for restoration until this feature is re-enabled;
To disable/enable File-level backup:
1. Select a client or a group from the left panel of the RITN Administrator main interface.
RITN Client, but the
Note:
This operation will take effect for both online and offline clients.
2. Choose Settings from the function panel in the upper right of the RITN Administrator main
interface.
3. Check the Enable File-level Backup box under Backup in the upper part of this page.
4. Click Apply to activate the settings. If the settings are successfully applied, the Apply button will
change to gray.
- 24 -
Page 25

3-6.3 RITN Client Function Control
RestoreIT Network allows the network administrator to disable incremental and file-level functions on
RITN Client, so that client user cannot manual create/restore an IBP, configure file backup settings
or restore files. It also allows the administrator to hide the RITN Client interface to prevent any
manual operations on the client side.
To control RITN Client functions:
Select a client or a group from the left panel of the RITN Administrator main interface.
Note:
This operation will take effect for both online and offline clients.
Choose Settings from the function panel in the upper right of RITN Administrator main interface.
The lower part of this page is the client interface and function control options. (shown below)
Here is a detailed instruction on to choose these options:
z Show Client User Interface
If this box is checked, the RITN Client user interface can be open on client side. Client users
can perform all allowed functions from this interface. If this box is cleared, the RITN Client
interface cannot open and all functions cannot be used. The following options should be
grayed and unable to be selected.
◊ Incremental Backup
Note: These options are available only when the Enable Incremental Backup box under
Backup in this page is checked.
Allow to create Incremental Backup Point
If this box is checked, users can create an IBP from RITN Client interface.
Allow to restore ibp
If this box is checked, users can restore an IBP from RITN Client interface.
◊ File-Level Backup
Note: These options are available only when the Enable Incremental Backup box under
Backup in this page is checked.
Allow to configure File-Level Backup settings
If this box is checked, users can specify files to back up from RITN Client interface.
Allow to restore files
If this box is checked, users can perform a File-Level Restore from the RITN Client
interface.
After you have made your selection, click Apply to activate your settings. If the settings are
successfully applied, the Apply button will change to gray.
3-7 RITN Administrator Options
- 25 -
Page 26

In RITN Administrator Options, you can configure the listen port of RestoreIT Network, set an
administrator password; set refresh time span and log file size.
To configure RITN Administrator options:
Select Tools Æ Options from the RITN Administrator menu bar.
The Options dialog box should display (shown below).
Here are detailed instructions on to choose these options:
Port Settings
Under connections, set the working port for RITN Administrator to listen. Normally, the port
should be set between 1024 to 65535.
Administrator Password Settings
The administrator password is required each time when launching RITN Administrator and
when entering a Pre-OS mode to restore the computer.
The password is set at the first time when launching RITN Client after installation. You can
change it any time in this Options dialog box. Click Set Password to change it.
The password consists of English characters and number. The length should between 1 to 32
characters. Note: English characters are case sensitive.
Log File Size
Specify a file size (at least 50KB) to limit the log file of each client to this size. Once the
maximum size is reached, the previous logs will be automatically cleared.
Refresh Time
RITN Administrator and RITN Client send messages to each other in real time. When a
message cannot be sent, RestoreIT Network will try to re-send the message according to the
refresh time you set here. The number should be set between 1 to 120.
- 26 -
Page 27

Chapter 4
Using RITN
Client
Page 28

Chapter 4
Using RITN Client
4-1 Introduction to RITN Client
RITN Client continually monitors and keeps a complete record of all activities on the hard drive. It
allows users to restore lost data after a system crash, virus attack, faulty software installation,
accidental file deletion or unintentional formatting of the hard drive.
4-2 Connecting to RITN Administrator
After the RITN Client has been successfully installed, it will automatically connect to the RITN
Administrator each time the computer starts, and the RestoreIT tray icon
area of Windows Taskbar.
If the RITN Client cannot find the server, you can manually specify the server address and port to locate it.
Follow the steps below to manually specify the server address:
1. Right click the tray icon
below).
Note: When the RITN Client has not connected to the Administrator, the tray icon looks like
and select Settings. The RITN Client Settings dialog should appear (shown
will appear in the notification
.
2. Select General and click Modify. You should be asked to enter the administrator password. Ask your
network administrator for the password and enter it.
3. Check the box “Use static IP address” and enter the IP address of the server and port used by
RestoreIT Network in corresponding blanks.
4. Click Save to save your changes. Your computer will restart to activate your settings. As the
computer starts, it should automatically connect to your specified address.
4-3 Opening
RITN Client
Page 29

Note: clients can open the RITN Client interface only when allowed by the Administrator.
To launch the
RITN Client in Windows, double-click the RestoreIT icon in the system tray or the
desktop icon.
After launching the program, you will see the main interface of the
RITN Client. (shown as below).
The default page is a Quick Start tab. It provides an overview of your system backup status and also
allows you to perform most functions of the client module. If you have any questions on using
RestoreIT, you can view the Help file or contact support online from the I need help section.
4-4 Backing up Your System
Besides automatic backups to predefined schedules and backup operations perform by the network
administrator from the Administrator’s console, clients can manually create Incremental Backup
Points at any time.
Note: This function is available only when allowed by the Administrator.
To create an Incremental Backup Point
1. Select the Quick Start page and click Quick Backup under I want to perform…, or select the
System Backup page and click Quick Backup.
2. Enter a name for the backup point. You can choose to leave the default name. Click Next to start
creating the Incremental Backup Point.
3. RestoreIT will lock the hard drive during this process. If any program is currently writing to or
reading from the hard drive, it will stop creating the backup point. If your computer locks up
during this time, restart it manually and try again.
Note: RestoreIT does not create new backup points if it is unable to lock your hard drive.
Close ALL applications when you create a new backup point.
- 29 -
Page 30

4. Select Finish when the Incremental Backup Point has been successfully created.
4-5 Restoring Your System
Besides restoring via the Administrator’s console, clients can also restore their computer from their
side.
Note: This function is available only when allowed by the Administrator.
Clients can perform a Quick Restore – Restoring to the latest IBP, or restore to any previous backup
point.
4-5.1 Quick Restore
Quick Restore allows you to quickly restore your computer to the state it was in when the most
recent Incremental Backup Point was created.
To perform a Quick Restore
1. Select the Quick Start page and click Quick Restore under I want to perform…, or select the
System Restore page and click Quick Restore.
2. The restoration dialog box will appear and ask you to choose whether to restore Drive C: Only or
the Entire System. Click Next after you have made your selection.
3. Confirm your selection and click Continue.
4. RestoreIT should prompt you that the computer will restart. Click Yes to restart the computer.
5. Your computer will restart and your system will revert back to the most recent backup point.
4-5.2 Restoring to any Incremental Backup Point
To restore an Incremental Backup Point
1. Select System Restore on the main interface, and then Restore to any Incremental Backup
Point.
2. All available records are listed in the box. Choose the Incremental Backup Point that you would
like to restore to and click Restore Now.
- 30 -
Page 31

3. Choose to restore the Entire hard drive or Only C: drive and then press Next. A dialog box will
appear to show information on the selected backup point. Select Next after you have made sure
this is the correct backup point to be restored. RestoreIT will restart your computer and your
system will revert back to the selected backup point.
4. After the system has been successfully restored, it will automatically restart to Windows.
Note: 1. Choosing to execute an Incremental Backup Point will clear all existing Incremental
Backup Points that were created after that point.
2. After restoring Only C: drive, all existing Incremental Backup Points that were
created before that point, can only be used to restore the primary drive.
3. RestoreIT does not recommend restoring an ambiguous backup point. It will warn
users twice during the restoring process.
4-6 File Level Backup and Restore
RestoreIT allows you to select particular files to get continuous file-level backup protection. Once
protected, RestoreIT will create a backup version whenever the file is deleted, changed or
overwritten. You can choose to restore the old version later without having to restore the entire
system to an earlier point in time
4-6.1 How to Restore a Specific File
This function allows you to retrieve previous versions of a specific file after it was deleted, changed
or overwritten, without doing an entire restore operation.
To restore a specific file
1. Select the File Level Restore page and then File Level Restore, or select Quick Restart and
then File-Level Restore.
2. The File Restore window will open (show below).
In the left pane, you can expand file folders to locate which file you want to retrieve. The top right
pane displays available files located in the selected directory. Click a file to see all backed up
- 31 -
Page 32

versions; this is displayed in the bottom right pane. Here you can select a version and click
Restore, or click Open to preview the file.
Note: By default, all files in the My Documents folder, and all files with *.doc *.txt *.cpp
*.ppt *.xls *.pdf *.rtf extensions .
To specify which file or folder to back up, go to Settings Æ File Backup Æ Files and
Folders, or use the File Level Backup Wizard on the Backup page, to add a file or folder to
the list.
Note: You can also right-click a specific file in Window Explorer and select File-Level Recovery to
open the File Restore window.
3-6.2 Backing up Specific Files or Folders
The File Level Backup Wizard guides you to add specific files or folder to be protected.
To add files or folders to File Level Backup using the Wizard
1. Select the File-Level Restore page and then click File-Level Backup Wizard.
2. The File-Level Backup Wizard will launch. Select Add a file or Add a folder and click Next.
3. Follow the on-screen instructions to add files or folders. Click Finish to exit the wizard.
3-6.2 Configuring File-Level Backup Settings
The file backup settings provide you with a convenient way to configure your File Level Backup
settings. You can configure which files/folders or what types of file need to be protected, and
configure other settings such as number of backup copies and the space limitation.
¾ Files and Folders
This page allows you to specify the general file types (extensions), folders or specific file that
RestoreIT needs to automatically back up.
- 32 -
Page 33

All files and folder protected by RestoreIT are listed in the box on this page. By default, all files on
the hard drive with “.doc”, “.txt”, “.xls”, “.ppt”, “.pdf”, and “.rtf” extensions, and all type of files in
My Documents are included.
Adding Files to be protected
Click Add Files: to start adding any specific file(s).
Click Add and select the file(s) you wish to add from your hard drive to the protected file list.
Click Delete to exclude any file from the list and RestoreIT will stop protecting this file or file type
(extension).
Adding Folders to be protected
Click Add Directory to start adding a folder to the protected list.
Click Add and select the folder from your hard drive.
- 33 -
Page 34

Click Browse to select the folder to be protected.
You can choose to back up all files or only the specified file types (files with certain extensions).
If the types you want to backup are not on the list, you can manually add a file type by clicking Add
and type the file extension to be included.
Check the Include sub-folders box if you want to back up the files in sub-folders.
Excluding Files or Folders from the Backup List
Select a file or folder and click the Delete button to exclude it from the Backup File List.
- 34 -
Page 35

¾ Other
Here you can set other File Level Backup settings.
• Copies: You can choose to back up a specified number of copies (between 1 to 50 copies), or
unlimited numbers of copies until the file backup space is used up. (RestoreIT will prompt you to
delete unneeded backup versions if the file backup space is used up.)
• Space limitation: You can specify a size limit (between 1MB to 200MB). RestoreIT will not back
up a file if its size exceeds the limit. You can also set RestoreIT to prompt you if the backup
space is less than your pre-set percentage. You can specify a percentage between 5 and 30
percent.
• Other: Select this option to display the back up progress when performing a File-level back up.
- 35 -
Page 36

Chapter 5
Removing RestoreIT
Network
Page 37

Chapter 5
Removing RestoreIT Network
5-1 Removing RITN Administrator
Follow the steps below to safely remove
1. If the
the program.
2. Select Start on the Windows taskbar, then All Programs Æ RITN Administrator Æ Uninstall
RestoreIT Network Administrator
3. Confirm that you would like to remove
RITN Administrator will be removed completely when your computer restarts.
4.
You can also safely remove
5-2 Removing RestoreIT Network Clinet
Please remove
Note: You can remove the program on one computer at a time.
RITN Administrator program is running in Windows, we suggest you close it before removing
RITN Administrator from Windows Control Panel.
RITN Clients from Windows Control Panel on local system.
RITN Administrator
RITN Administrator.
Page 38

Chapter 6
Software License
Agreement
Page 39

Chapter 6
Software License Agreement
FARSTONE TECHNOLOGIES INC. (FARSTONE) END USER LICENSE AGREEMENT FOR SECUREPC,
HEREAFTER REFERRED TO AS THE "SOFTWARE"
PLEASE READ CAREFULLY: THE USE OF THIS "SOFTWARE" IS SUBJECT TO THE "SOFTWARE"
LICENSE TERMS OF FARSTONE AND OTHER LICENSORS WHOSE SOFTWARE MAY BE BUNDLED WITH
THIS PRODUCT.
BY YOUR USE OF THE "SOFTWARE" INCLUDED WITH THIS PRODUCT YOU AGREE TO THE LICENSE
TERMS REQUIRED BY THE LICENSOR OF THE "SOFTWARE", AS SET FORTH BELOW. IF YOU DO NOT
AGREE TO THE LICENSE TERMS APPLICABLE TO THE "SOFTWARE", YOU MAY RETURN THE ENTIRE
UNUSED PRODUCT FOR A FULL REFUND.
In return for acquiring a license to use the farstone "software", which may include software from
third party licensors, trial versions or copies of the "software" and patches made available by farstone,
and the related documentation, you agree to the following terms and conditions:
A. Single User License: This Agreement grants you, the Licensee, a License to:
(a) use the "Software" on a single computer system or network, and only by a single user at a time.
If you wish to use the "Software" for more users, you will need an additional License for each user.
(b) make one copy of the "Software" in machine-readable form solely for back-up purposes, provided
you reproduce FarStone's copyright proprietary legends. Notwithstanding the foregoing, the
"Software" may be used on the home, laptop or other secondary computer of the principal user of the
"Software", and an additional copy of the "Software" may be made to support such use. As used in
this License, the "Software" is "in use" when it is either loaded into RAM or installed on a hard drive
or other permanent memory device. The "Software" may be "in use" on only one computer at any
given time. (Different License terms and fees are applicable for networked or multiple user
applications.) As a specific condition of this License, you agree to use the "Software" in compliance
with all applicable laws, including copyright laws, and that you will not copy, transmit, perform or
distribute any audio or other content using the "Software" without obtaining all necessary Licenses or
permissions from the owner of the content.
B. Multiple User License: This Agreement grants you, the Licensee, a License to:
Make one copy of the "Software" in machine-readable form solely for back-up purposes, provided you
reproduce FarStone's copyright proprietary legends.
You must acquire and dedicate a License for each separate computer on which any part or portion of
the "Software" is installed or run As used in this License, the "Software" or any part or portion of the
"Software" is "in use" when it is either loaded into RAM or installed on a hard drive or other
permanent memory device including any networked or shared environment where either direct or
indirect connections are made through software or hardware which pools or aggregates connections.
As a specific condition of this License, you agree to use the "Software" in compliance with all
applicable laws, including copyright laws, and that you will not copy, transmit, perform or distribute
any audio or other content using the "Software" without obtaining all necessary Licenses or
permissions from the owner of the content.
C. Restrictions: You may not distribute copies of the "Software" to others or electronically transfer
the "Software" from one computer to another over a network. You may not post or otherwise make
available the "Software", or any portion thereof, in any form, on the Internet. You may not use the
"Software" in a computer service business, including in time-sharing applications. The "Software"
Page 40

contains trade secrets and, in order to protect them, you may not decompile, reverse engineer,
disassemble, or otherwise reduce the "Software" to a human-perceivable form. YOU MAY NOT
MODIFY, ADAPT, TRANSLATE, RENT, LEASE, LOAN, RESELL FOR PROFIT, DISTRIBUTE, NETWORK OR
CREATE DERIVATIVE WORKS BASED UPON THE "SOFTWARE" OR ANY PART THEREOF.
D. Ownership: As Licensee, you own the media upon which the "Software" is recorded or fixed, but
FarStone and its Licensors retain title and ownership of the "Software" recorded on the original media
and all subsequent copies of the "Software", regardless of the form or media in which or on which the
original and other copies may exist. This License does not grant, convey or in any way transfer
ownership of the "Software".
E. Separation of Components: The "Software" is licensed as a single product. Its component parts
may not be separated for use on more than one computer, not withstanding reference to Section B of
this License agreement where Multiple user Licenses have been purchased.
F. Confidentiality: You agree to maintain the "Software" in confidence and that you will not disclose
the "Software" to any third party without the express written consent of FarStone. You further agree
to take all reasonable precautions to preclude access of unauthorized persons to the "Software".
G. Terms: This License shall continue for as long as you use the "Software". However, it will terminate
if you fail to comply with any of its terms and conditions. You may terminate the License at any time by
destroying the "Software" (including the related documentation) together with all copies or
modifications in any form. FarStone will have the right to terminate our License immediately if you fail
to comply with any term or condition of this Agreement. Upon any termination, including termination
by you, you must destroy the "Software" (including the related documentation), together with all copies
or modifications in any form. The Limitations, Warranties and Liability set out below shall continue in
force even after any termination
H. Transfer: You may transfer the "Software" License to someone else, only if you assign all of your
rights under this License, cease all use of the "Software", erase or destroy any copy (including the hard
drive copy) made in support of your use of the "Software", and the other person agrees to the terms of
this License.
If the "Software" is an upgrade from other "Software", whether from us or another supplier, you may
use or transfer the "Software" only in conjunction with the upgraded "Software", unless you destroy it.
If the "Software" is an upgrade from FarStone, you may only use that upgraded "Software" in
accordance with this License.
I. Special Terms Applicable to Databases. Where a database is included with the "Software", you
acknowledge that it is licensed only in connection with the use of the "Software" to perform disk
creation, and that the database and all data derived there from must be maintained in confidence in
accordance with the provisions of Section E of this document. This License does not grant you any
rights to distribute or disclose such a database or data contained therein.
J. Limited Warranty: FarStone and its Licensor warrant only that the media upon which the
"Software" is furnished will be free from defects in material or workmanship under normal use and
service for a period of thirty (30) days from the date of delivery to you. FARSTONE AND ITS
LICENSORS DO NOT AND CANNOT WARRANT THE PERFORMANCE OR RESULTS YOU MAY OBTAIN BY
USING THE "SOFTWARE" OR DOCUMENTATION. THE FOREGOING STATES THE SOLE AND EXCLUSIVE
REMEDIES FARSTONE AND ITS LICENSORS WILL PROVIDE FOR BREACH OF WARRANTY. EXCEPT FOR
THE FOREGOING LIMITED WARRANTY, FARSTONE AND ITS LICENSORS MAKE NO WARRANTIES,
EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED, AS TO NON-INFRINGEMENT OF THIRD PARTY
RIGHTS, MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow the
- 40 -
Page 41

exclusion of implied warranties or limitations on how long an implied warranty may last, so the above
limitations may not apply to you. This warranty gives you specific legal rights and you may also have
other rights, which vary from state to state.
The entire liability of FarStone and its Licensors, and your exclusive remedy for a breach of this
warranty, shall be: (a) the replacement of any media not meeting the above limited warranty which is
returned to FarStone; or (b) if FarStone or its distributor is unable to deliver replacement media which
is free from defects in materials or workmanship, you may terminate this Agreement by returning the
"Software" and your money will be refunded.
K. Limitation of Liability: IN NO EVENT WILL FARSTONE OR ITS LICENSORS BE LIABLE TO YOU FOR
ANY INCIDENTAL, CONSEQUENTIAL OR INDIRECT DAMAGES, INCLUDING ANY LOST PROFITS, LOST
SAVINGS, OR LOSS OF DATA, EVEN IF FARSTONE OR A LICENSOR HAS BEEN ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES, OR FOR ANY CLAIM BY ANY OTHER PARTY. Some states do not allow
the exclusion or limitation of special, incidental, or consequential damages, so the above limitation or
exclusion may not apply to you.
L. Bundling: In no case may the "SOFTWARE" be bundled with hardware or other software without
written permission from FarStone.
M. Export: You acknowledge that the laws and regulations of the United States and/or other countries
may restrict the export and re-export of the "Software". You agree that you will not export or re-export
the "Software" or documentation in any form in violation of applicable law in the United States and/or
foreign law.
N. General: You acknowledge that you have read this Agreement, understand it, and that by using the
"Software" you agree to be bound by its terms and conditions. You further agree that it is the complete
and exclusive statement of the agreement between FarStone and you, and supersedes any proposal or
prior agreement, oral or written, and any other communication between FarStone and you relating to
the subject matter of this Agreement. No additional or any different terms will be enforceable against
FarStone unless FarStone gives its express consent, including an express waiver of the terms of this
Agreement, in writing signed by an officer of FarStone. You assume full responsibility for the use of the
"Software" and agree to use the "Software" legally and responsibly.
Should any provision of this Agreement be declared unenforceable in any jurisdiction, then such
provision shall be deemed severable from this Agreement and shall not affect the remainder hereof.
FarStone reserves all rights in the “Software” not specifically granted in this Agreement.
Should you have any questions concerning this Agreement, you may contact FarStone by writing to:
FarStone Technology, Inc.
Legal Department
6 Morgan, Suite 304
Irvine, CA 92618
Phone: (949) 458-3666
- 41 -
 Loading...
Loading...