Page 1

Farstone Firewall
Version 1.0
User’s Guide
1
Page 2

Copyright Notice
No part of this publication may be copied, transmitted, stored in a
retrieval system or translated into any language in any form or by any
means without the express written permission of FarStone Technology,
Inc.
FarStone grants to you the right to use one copy of the enclosed
software program (The "SOFTWARE") on a single computer. If the
Software is installed on a network or more than one user can run the
Software at the same time, you must purchase an additional license for
each user or workstation.
Trademarks
FarStone and FarStone Firewall are registered trademarks of
FarStone Technology, Inc. Microsoft
, Windows and MS-DOS are
registered trademarks of Microsoft Corporation. Other product names
mentioned in this manual may also be trademarks or registered
trademarks of their respective companies.
FarStone Technology, Inc.
Headquarters: North America
15550-B Rockfield Blvd., Suite 100
Irvine, CA 92618
Tel: (949) 458-3666
Fax: (949) 458-3633
Technical Support:
Please contact your retailer or use our online support system at
www.farstone.com. For your convenience, you will find answers to
frequently asked questions on our website at
Follow the links to the support section.
Copyright
1998-2002 FarStone Technology, Inc. All rights reserved.
2
www.farstone.com.
Page 3

Contents
CHAPTER 1 INTRODUCTION........................................................6
1.1 WHAT IS FARSTONE FIREWALLTM? ............................................6
1.2 FEA TURES AND BENEFITS...........................................................6
CHAPTER 2 INSTALLATION..........................................................8
2.1 SYSTEM REQUIREMENTS............................................................8
2.2 INSTALLING FARSTONE FIREWALLTM..........................................8
CHAPTER 3 STARTING FARSTONE FIREWALLTM................12
3.1 STARTING FARSTONE FIREWALLTM..........................................12
3.2 TOOLBAR-MAIN BUTTONS........................................................13
CHAPTER 4 USING FARSTONE FIREWALLTM........................15
4.1 NETWORK MONITOR.................................................................15
4.1.1 Event Report..................................................................................15
4.1.2 Save Logs....................................................................................... 16
4.1.3 Open Logs...................................................................................... 17
4.1.4 Clear Logs......................................................................................17
4.2 APPLICATION MANAGEMENT.....................................................17
4.2.1 Setting Access Rule for Application............................................ 18
4.2.2 Delete Application..........................................................................19
4.3 COMPUTER GROUP MANAGEMENT..........................................20
4.3.1 Add an IP Address......................................................................... 21
4.3.2 Add a Range of IP Addresses......................................................21
4.3.3 Delete a Computer........................................................................ 22
4.4 INTERNET LOCK ........................................................................23
4.5 DISCONNECT/CONNECT ...........................................................24
4.6 CLEAR.......................................................................................25
4.7 USER ACCOUNT........................................................................27
4.7.1 Create a new account...................................................................27
4.7.2 Delete an account ......................................................................... 28
4.7.3 Switch user..................................................................................... 28
CHAPTER 5 FIREWALL SETTINGS...........................................31
3
Page 4

5.1 SETTING SECURITY LEVEL .......................................................31
5.2 INTERNET LOCK SETTINGS.......................................................32
5.3 OTHER SETTINGS.....................................................................33
CHAPTER 6 UNINSTALLING.......................................................35
6.1 UNINSTALLING FARSTONE FIREWALLTM...................................35
CHAPTER 7 APPENDIX................................................................38
7.1 SOFTWARE LICENSE AGREEMENT............................................38
7.2 TECHNICAL SUPPORT & PRODUCT UPGRADE .........................42
4
Page 5

Chapter 1
Introduction
5
Page 6

Chapter 1 Introduction
1.1 What is FarStone FirewallTM?
FarStone FirewallTM creates barriers to prevent unauthorized access to
your computer from a network.
FarStone Firewall
comprehensive protection from data thieves and hackers. FarStone
Firewall
lets you monitor, control and log your network activities.
TM
protects your computers according to pre-set security rules and
TM
is security software that provides you with
1.2 Features and Benefits
FarStone FirewallTM can:
• Protect your system from data thieves and hackers.
• Display the current network access activities.
• Stop unauthorized access attempts.
• Alert the user when an intrusion is detected.
• Log all network traffic automatically.
• Set the security level (high, medium, low) according to user’s need.
• Block a specific IP address or a range of IP addresses.
• Display and block any program communication to and from your system.
• Support multiple languages: English, Traditional Chinese and simplified
Chinese.
• Clear temporary files and Internet history safely and easily
• Manage your own account and switch between users without closing
program.
6
Page 7

Chapter 2
Installation
7
Page 8
Chapter 2 Installation
2.1 System Requirements
• Windows 98/Me/2000/XP
• 50MB of hard disk space
• 256 VGA colors o r hig her
• 32MB RAM
• Intel Pentium (or compatible) 100MHz processor or better
2.2 Installing FarStone FirewallTM
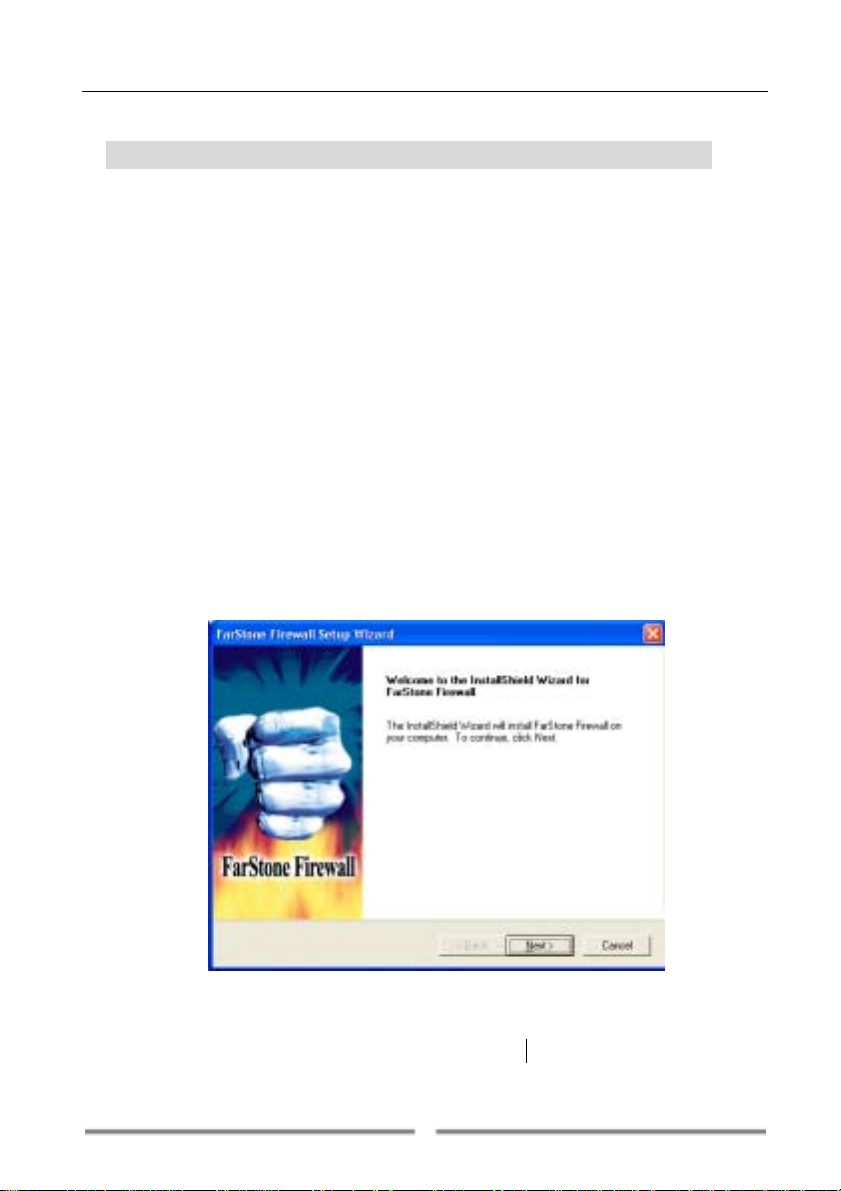
Step 1: Before starting the installation, close any applications that are
running.
Step 2: Insert the FarStone Firewall
“setup.exe” file directly to begin the installation (Figure 2-1).
TM
CD into your CD drive and run the
Figure 2-1
Step 3: Carefully read the Software License Agreement. If you accept the
terms of the agreement, select Yes to continue.
8
Page 9

Step 4: Enter your user name, company name (if applicable) and serial
number (Figure 2-2). If you have purchased the CD-ROM, the serial
number can be found on the back of the CD jewel case.
Figure 2-2
Step 5: The Setup Wizard will suggest a folder in which to install the
Farstone Firewall
TM
program files (Figure 2-3). If you would like to store the
program files in another location, select Browse to open the file browser
and select a new folder.
9
Page 10
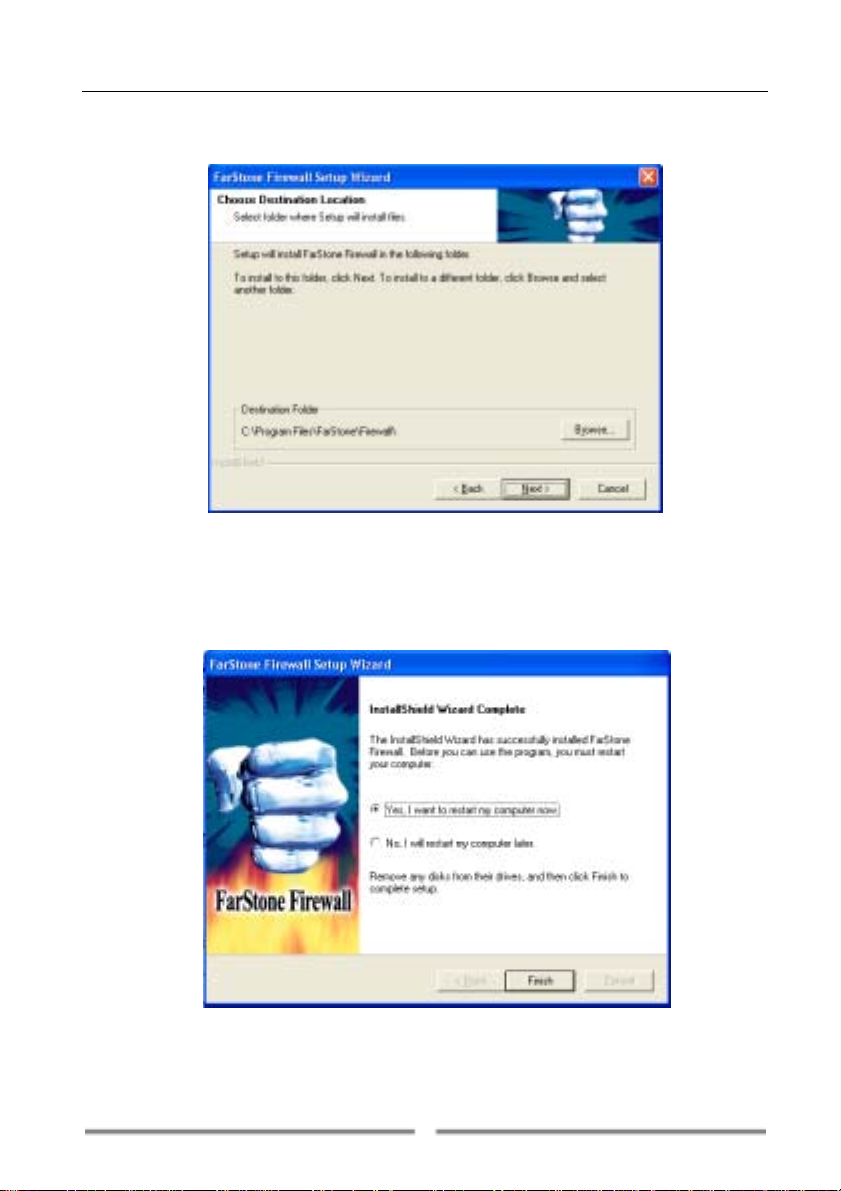
Figure 2-3
Step 6: Select Next to continue the installation.
Step 7: Select Finish to complete the installation. You must restart your
computer before using FarStone Firewall
TM
.
Figure 2-4
10
Page 11

Chapter 3
Starting
TM
FarStone Firewall
11
Page 12
Chapter 3 Starting FarStone FirewallTM
3.1 Starting FarStone FirewallTM
After installation, the FarStone FirewallTM icon will be displayed on the
Windows desktop. To start the FarStone Firewall
on the Farstone Firewall
Programs->FarStone Firewall
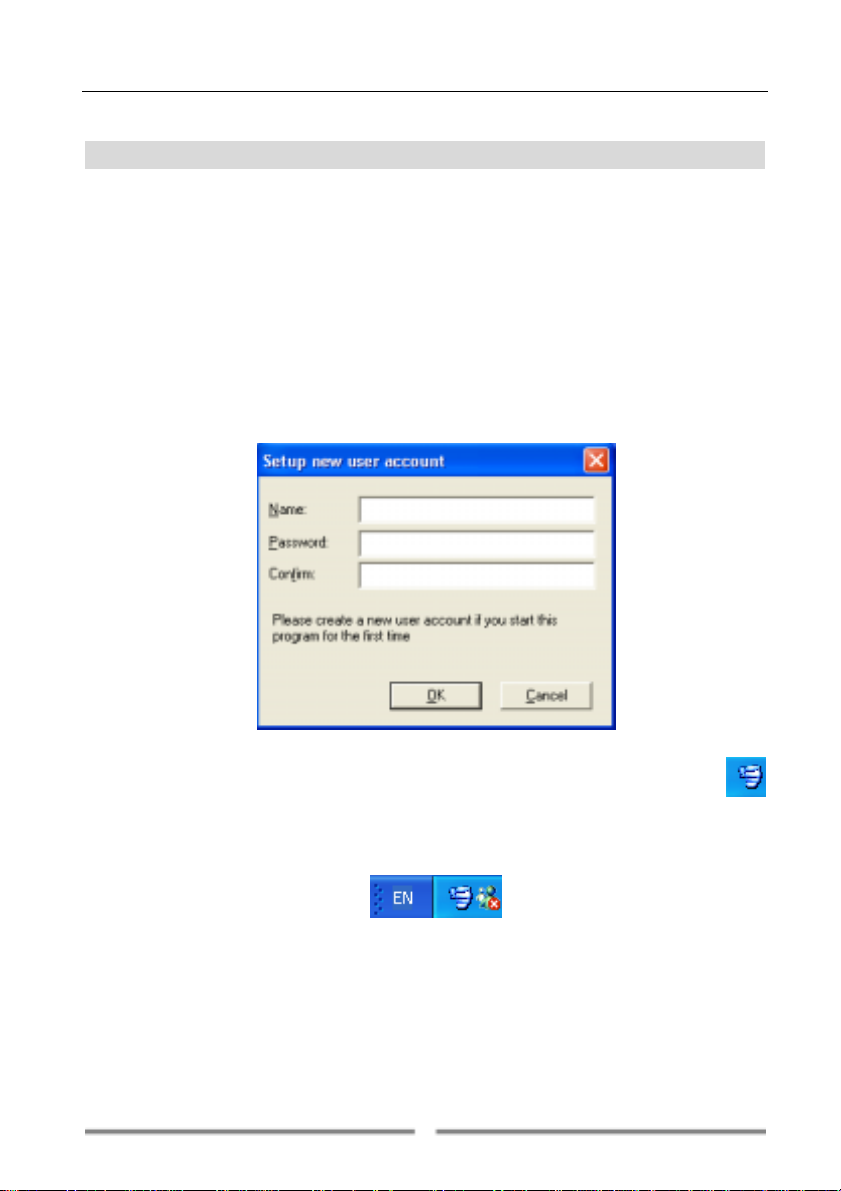
If Farstone Firewall
TM
icon or select Start on the taskbar then
TM
-> FirewallTM.
TM
is started for the first time, it will prompt user to setup
TM
program, double-click
a new user account. This account possesses administrator privileges.
When FarStone Firewall
TM
is minimized, the FarStone FirewallTM icon
will be displayed in the bottom right corner of the Windows taskbar, near
the clock (Figure 3-1).
Figure 3-1
12
Page 13

3.2 Toolbar-Main Buttons
Network Monitor
Displays and logs the programs that are accessing your
computer through the network.
Application Management
Allows or blocks an application from communicating over the
network.
Computer Group Management
Allows a computer or group of computers to access your
computer from the network or blocks a computer or group of
computers from accessing your computer from the network.
Lock
Block traffic of all Internet applications except those possess
time lock privilege.
Forbid/Allow Communications
Disconnects or connects your computer to the network
Clear
Clear temporary files as temporary Internet files, recent files,
files in recycle bin, cookies, etc.
Switch user
Switch between users without closing program.
Help
Gives users support on how to use FarStone Firewall
TM
13
Page 14

Chapter 4
Using FarStone Firewall
TM
14
Page 15

Chapter 4 Using FarStone FirewallTM
4.1 Network Monitor
To monitor a program’s network activity, select from the FarStone
Firewall
top-right frame of FarStone Firewall
TM
toolbar. All applications that are running will be listed in the
TM
(Figure 4-1).
Figure 4-1
The information display in the top right frame includes:
(1) The directory for the application.
(2) The time of the connection.
(3) The IP address of the computer that is accessing the network.
(4) The communication port.
(5) The traffic status.
4.1.1 Event Report
Some unacknowledged or unauthorized network attacks will steal
information from your computer. These attacks can also crash your
computer and leave you with the infamous "blue screen of death." Hackers
can access the data and your system (possi bly wiping out all of your
information as you watch helplessly) through these attacks. Event report is
an important feature of network monitoring. It lists all attacks in the bottom
right frame. The most common attacks are:
• Ping Command: Ping is an ICMP-based command used to verify the
15
Page 16

availability of a computer on the network.
• ICMP - Internet Control Message Protocol: By using ICMP, other people
can easily obtain information from your system.
• Trojan Horse - Trojan horse is a program that transmits without the user’s
knowledge. These types of programs often allow hackers to break into
and control your system.
• IGMP Packet – An IGMP Packet may result in a system crash.
• Port Scanning – A port is used by protocols such as TCP and UDP to
identify a communication instance (e.g. HTTP service port is 80, and FTP
service port is 21). Once connected to the Internet, some ports will be
opened for outside connections. FarStone Firewall
TM
can detect and block
any port scanning activities to remove these potential threats.
• Access Shares - Network shares inclu de files, folders, drives, printers, etc.
When you connect to the Internet, you are sharing a network with millions
of people around the world, meaning you are at risk of disclosing your
private information to others. FarStone Firewall
TM
can block unauthorized
access to your system.
4.1.2 Save Logs
To keep a record of the network activities that have occurred on your
computer, sel ect Save Logs or select Log->Save on the file menu. These
logs will be saved as *.txt files under the FarS tone Firewall
folder. After successfully saving these logs, a pop-up window will inform
users that the logs have been saved (Figure 4-2).
TM
program
Figure 4-2
16
Page 17

4.1.3 Open Logs
To view the recent history of the network activities, select Log->Open to
open the log file.
4.1.4 Clear Logs
To clear all logs displayed in the Event Report frame, select Clear Logs
on the left frame of FarStone Firewall
TM
interface.
4.2 Application Management
By using Application Management, users can supervise the applications
installed on their computers that are attempting to connect to the network.
There are 2 ways to run Application Management:
(1) Select
(2) Select Window->Application from the file menu.
All applications that have attempted to access the network will be listed in
the right frame(Figure 4-3). You can manage the connection of any
programs in the right frame and set the access rule for each application.
on the FarStone FirewallTM toolbar; or
17
Page 18
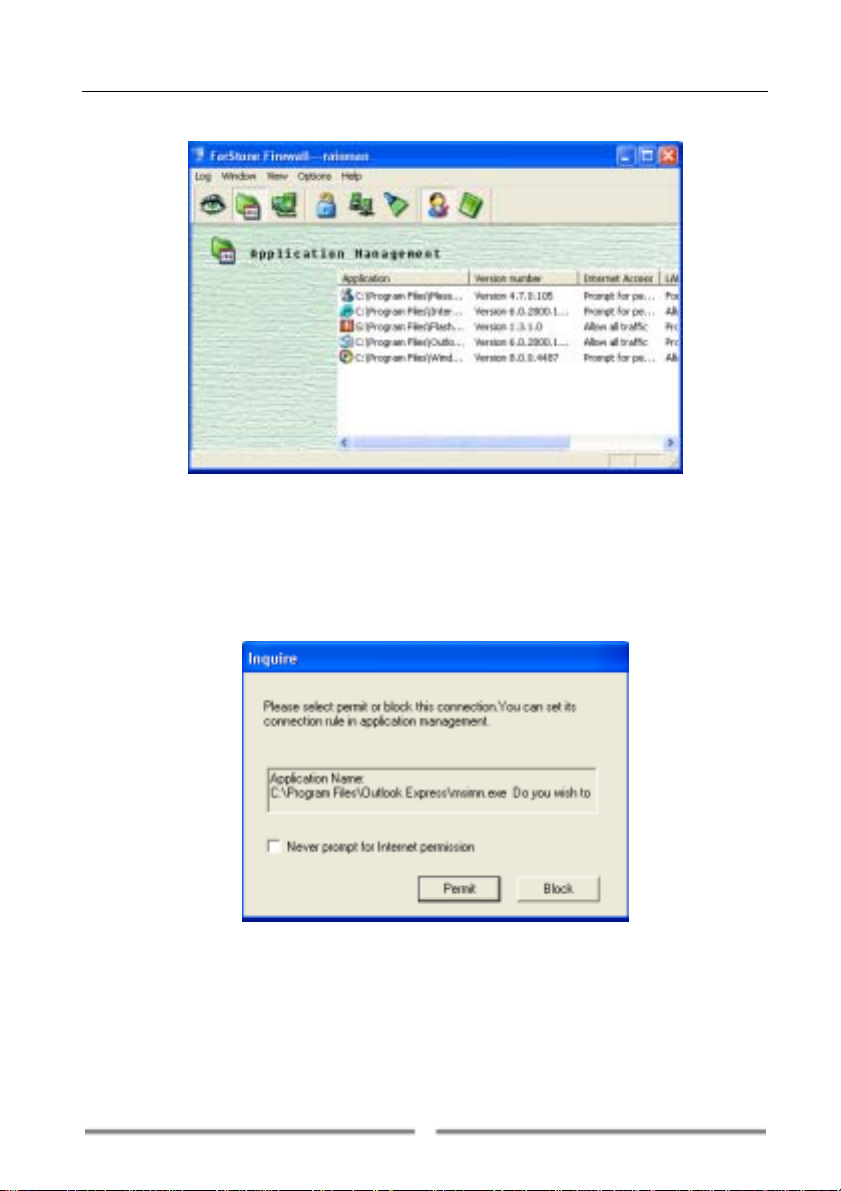
Figure 4-3
4.2.1 Setting Access Rule for Application
When an application attempts to connect to the network for the first time
after FarStone Firewall
permission to connect to the network (Figure 4-4).
If you check the box ‘Never prompt for permission again’, FarStone
Firewall
TM
will not ask for permission again when this application is trying to
connect to the network.
You can also set these access rules for the applications listed in the right
frame by double-clicking on the application to open the Application
TM
is installed, FarStone FirewallTM will ask for
Figure 4-4
18
Page 19

window (Figure 4-5). Then select a connection access rule for this
application.
Figure 4-5
There are three different rules:
• Inquire each time: Each time this application attempts to connect to the
network, the program will ask for permission.
• Allow all traffic: No restrictions for the connection of this application.
• Forbid all traffic: Forbid this application from connecting to the network.
4.2.2 Delete Application
To cancel the access rules of an application, right-click on the selected
application from the right frame, then select Delete from the drop menu
(Figure 4-6
).
19
Page 20

Figure 4-6
Once the application is removed from the list, the program will ask for
permission when trying to connect to the network the next time.
4.3 Computer Group Management
Users can also set the connection rules for the computers on the network.
By entering the computer IP addresses, you can control the connection to
or from any computer on the network.
Select
to open Computer Group Management (Figure 4-7).
Figure 4-7
20
Page 21

4.3.1 Add an IP Address
Select Add a computer on the left frame of the Computer Group
Management interface to open the dialog box (Figure 4-8).
This function is also available by right-clicking on the blank space on the
right frame and selecting Add an IP address from the drop menu.
Figure 4-8
Enter the description and the IP address of the computer you want to add.
Then, select a connection rule from the drop-down menu.
There are two different rules:
• Allow all traffic: Allows outgoing and incoming traffic from/to this
computer.
• Forbid all: Forbids all traffic from/to this computer.
4.3.2 Add a Range of IP Addresses
Users can set rules for a group of computers as well. Select Add a
computer group or right-click on blank space on the right frame. Then,
select Add an IP Section to open the dialog box (Figure 4-9).
21
Page 22

Figure 4-9
Enter the description, the starting IP and the ending IP in the text box. All
computers within the entered IP section will be added into a computer list.
Then, you can set a connection rule for these computers.
There are two different rules:
• Allow all traffic: Allows outgoing and incoming traffic from/to this computer.
• Forbid all: Forbids all traffic from/to this computer.
4.3.3 Delete a Computer
If you want to remove the connection rules of a computer or group,
right-click on the computer displayed in the computer list and select Delete
from the drop-down menu (Figure 4-10).
22
Page 23

Figure 4-10
4.4 Internet Lock
To disconnect Internet applications from network quickly, you can
press
applications, except those possess time lock privilege, will be locked and
can not connect to Internet.
Note: An application with time lock privilege can still connect to Internet as
usual after selecting Internet lock.
To grant lock time privilege to an application, press
to application management window, then right-click on a program to which
you want to grant time lock privilege and select properties from drop menu.
directly or select Options->Lock from menu bar. All
button to switch
23
Page 24

Figure 4-11
Select Yes radio button on the bottom of the dialog box then Ok. You can
also deprive this program of the privilege by selecting NO radio button.
Figure 4-12
4.5 Disconnect/Connect
One of the most useful methods to protect your computer from network
attacks is to disconnect from the network. If you stop the connection, no
24
Page 25

one can access your computer except you.
To disable the network connection, select
or select
Options->Disconnect from the menu bar. You can connect to the network
again by repeating the same steps.
4.6 Clear History
The powerful clear tool in Farstone Firewall
temporary files and history safely and quickly.
Select Options->Clear Options from menu bar to open the window
(Figure 4-13) and select the files you want to clear in it.
TM
enables users to clear
Figure 4-13
The files and folders can be cleared by Farstone Firewall
TM
include:
1. Temporary Internet Files Folder:
The Temporary Internet Files folder is used to store data received from
the Internet.
2. Cookies:
Cookies are small files on your computer in which stored websites
information.
3. URL History:
25
Page 26

URL list stores the address of recent visited websites.
4. Auto-Match List:
Auto-match list is the folder that stores the information you filled in
Internet Explorer.
5. Favorites Folder:
A folder contains the websites list or other folders saved by users.
6. Temporary System files:
A temporary system file is a file that is created to temporarily store
system information in order to free memory for other purposes, or to act
as a safety net to prevent data loss when a program performs certain
functions.
7. Recycle Bin:
When you delete any of these items from your hard disk, Windows
places it in the recycle bin. Items in the recycle bin remain there until you
decide to permanently delete them from your computer.
8. Recent Document files folder:
A folder contains the files you opened most recently.
9. Search for File History:
The information of the files you recently searched for.
10. Search for Computer History:
The information of the computers you recently searched for.
11. Network Connection History:
The information of the computers you recently connected with.
12. Recent Viewed Pages:
Recent viewed pages folder contains the information of web pages that
are being recently viewed.
13. Password Record:
The password record let system remember your password entered
before.
14. ‘Run’ Command History:
‘Run’ command history contains the command you entered in Start
Menu->Run
After select the files you want to clear. Select Options->Clear from menu
bar to clear all of them. You can also press
files directly.
26
button to clear these
Page 27

4.7 User Account
When multiple users share a Farstone Firewall
accidentally changed. With user account, you can manage your own
Firewall and prevent others from changing your settings.
Note: Only Firewall administrator can manage user account.
TM
, sometimes settings are
4.7.1 Create a new account
To create a new user account, select Options->User accounts from the
menu bar to open Accounts management window.
Figure 4-14
27
Page 28
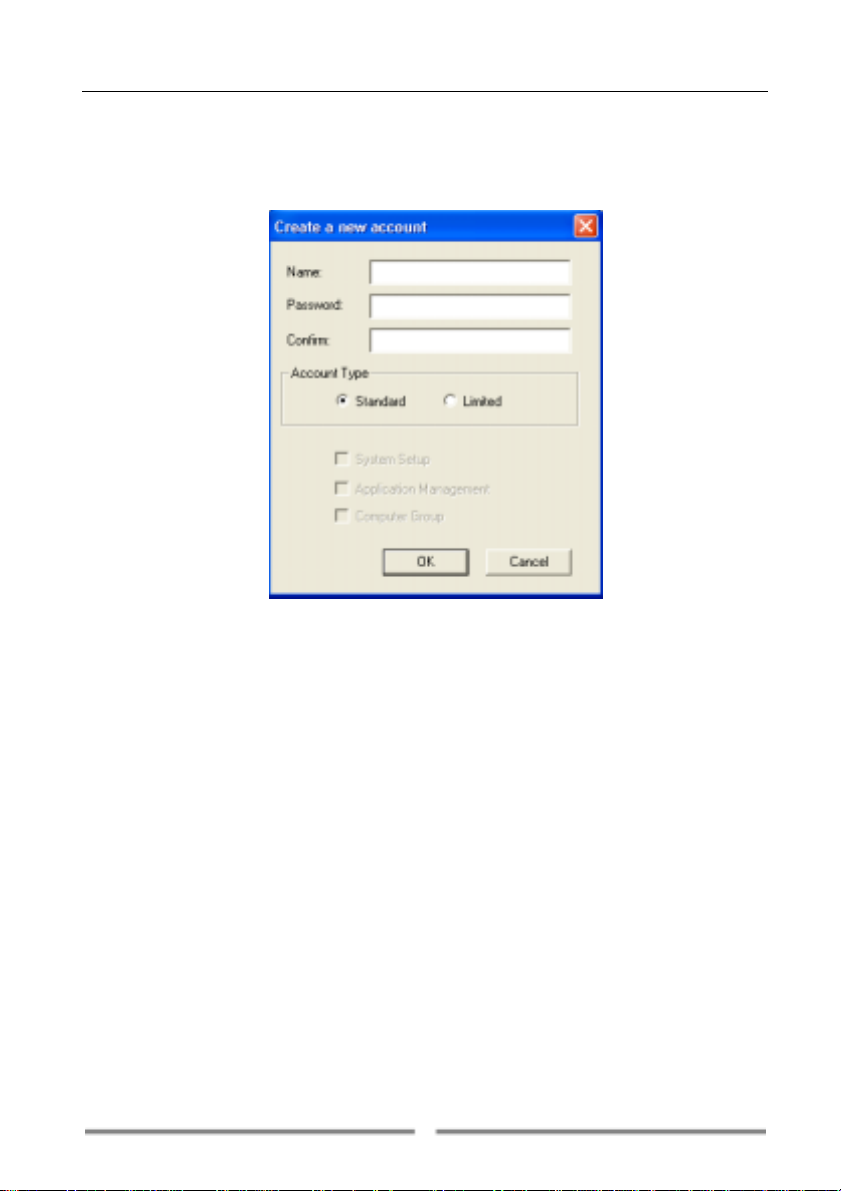
Click on Create, then type the user name and password in the box, and
then select the account type by clicking the radio box.
Figure 4-15
There are two types of user account: standard user account and limited
user account. Standard user shares administrator privileges as changing
Firewall settings, managing application connection and setting computer
group (But standard user can’t manage user account). You can also create
an account with limited privileges by selecting the check boxes.
4.7.2 Delete an account
To delete a user account, select Options->Accounts from menu bar. Then
select the account you want to delete and click on Delete (figure 4-14).
Note: Administrator account can’t be deleted.
4.7.3 Switch user
With user accounts, you can switch between users without closing Fire wall
28
Page 29

program. This function is available only if you select Enable Password
Protection in accounts management window
Figure 4-16
To switch between users, press
or select Options->Switch User
from menu bar. Then type the user name and password in the box.
29
Page 30

Chapter 5
Firewall Settings
30
Page 31
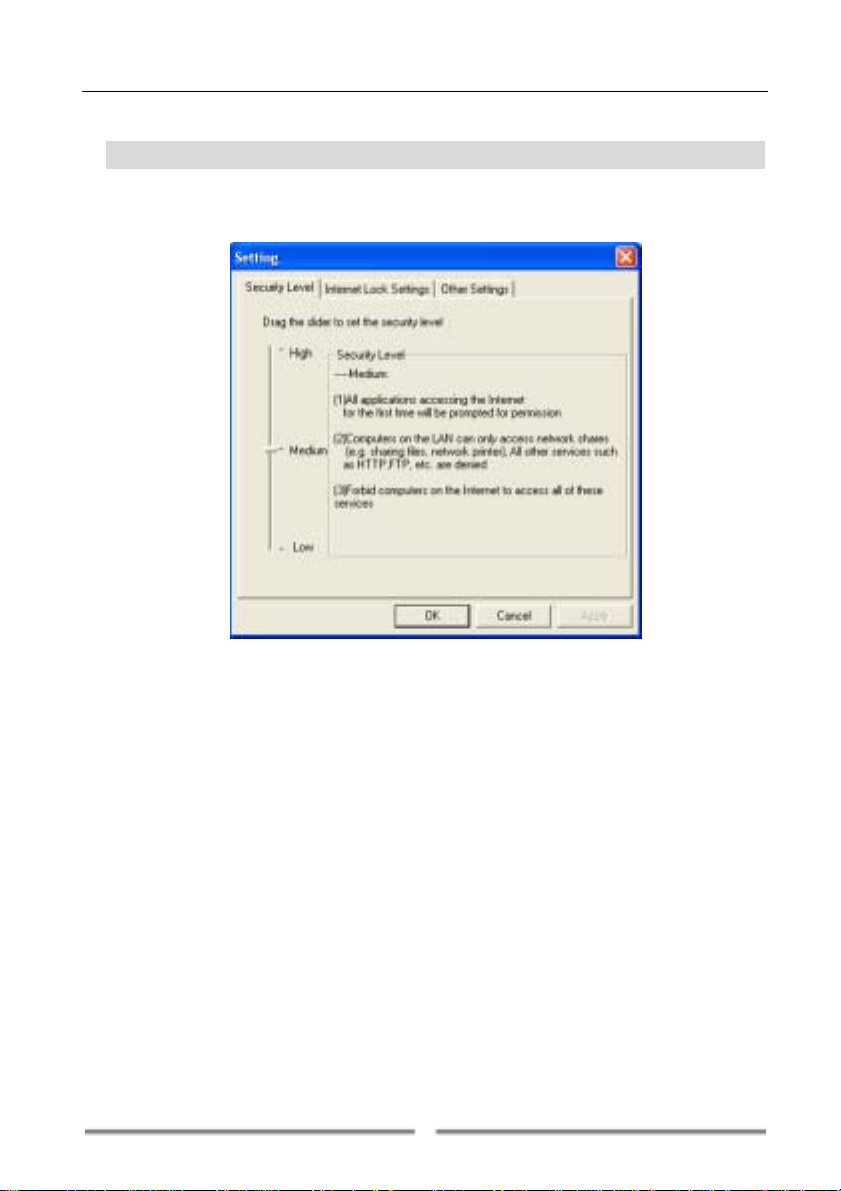
Chapter 5 Firewall Settings
From the Options menu of FarStone FirewallTM, select Settings to open
the Settings window (Figure 5-1).
Figure 5-1
5.1 Setting Security Level
There are three security levels that can be set:
• Low: FarStone Firewall will ask for permission when an application is
accessing the Internet for the first time. Only computers on the local area
network can access your network shares (e.g. files and printer). The
computers on the Internet are denied access to these services.
• Medium: FarStone Firewall will ask for permission when an application
is accessing the Internet for the first time. Computers on the network
cannot access your network shares (e.g. files and printer). Your computer
will be invisible on the network.
• High: FarStone Firewall will ask for permission when an application is
accessing the Internet for the first time. Computers on the network cannot
31
Page 32

access your network shares (e.g. files and printer). All ports on your
computer will be unusable by others unless they have been approved. Your
computer will be invisible on the network.
5.2 Internet Lock Settings
You can not only lock Internet applications manually (described in 4.4), but
also let Firewall lock them automatically.
No changes made to computer: All applications but those possess lock
time privilege will be locked if no changes made to computer for a preset
time.
Screen saver displays: All applications but those possess lock time
privilege will be locked if screen saver displays.
Figure 5-2
32
Page 33

5.3 Other Settings
Figure 5-3
• Auto-run at system st artup: The program will automatically be launched
when the computer starts up.
• Enable Alert: An alert sound will be played when other computers or
programs attack your system. You may also select the desired alert sound
by selecting Browse.
• Show Alert Window: A pop-up window will be displayed when other
computers or programs attack your system.
Event Log: Set the location for saving logs and the number of days to
keep the logs
33
Page 34

Chapter 6
Uninstalling
34
Page 35

Chapter 6 Uninstalling
6.1 Uninstalling FarStone FirewallTM
Step 1: Close any other programs that are running.
Step 2: If the FarStone Firewall
right-click on the icon and select Close.
Note: If you enabled password protection, Firewall will prompt you to enter
user name and password.
Step 3: To uninstall FarStone Firewall
taskbar, then select:
(a) Programs/FarStone Firewall/Uninstall Firewall or
(b) Start/Settings/ Control Panel and double click on the Add/Remove
Programs icon to open the Add/Remove Programs dialog,
Select FarStone Firewall
launch the Uninstallation Wizard (Figure 6-1). Select OK to begin
uninstalling FarStone Firewall
TM
icon is displayed in the system tray,
TM
, select Start in the Windows
TM
, then select Add/Remove. Either method will
TM
from your computer.
Figure 6-1
Step 4: If password protection is enabled in Options->User
Accounts, you will be required to enter administrator name
and password to continue uninstalling Firewall
35
TM
.
Page 36

Figure 6-2
Step 5: Select Finish to complete the uninstall process (Figure 6-3) .
Figure 6-3
36
Page 37

Chapter 7
Appendix
37
Page 38

Chapter 7 Appendix
7.1 Software License Agreement
FARSTONE TECHNOLOGY, INC. (FARSTONE) END-USER LICENSE
AGREEMENT FOR FARSTONE FIREWALL
REFERRED TO AS THE "SOFTWARE"
PLEASE READ CAREFULLY. THE USE OF THIS "SOFTWARE" IS
SUBJECT TO THE "SOFTW A RE" LICENSE TERMS OF FARSTONE AND
OTHER LICENSORS WHOSE SOFTWARE MAY BE BUNDLED WITH
THIS PRODUCT.
BY YOUR USE OF THE "SOFTWARE" INCLUDED WITH THIS
PRODUCT, YOU AGREE TO THE LICENSE TERMS REQUIRED BY THE
LICENSOR OF THE "SOFTWARE" AS SET FORTH BELOW. IF YOU
DO NOT AGREE TO THE LICENSE TERMS APPLICABLE TO THE
"SOFTWARE", YOU MAY RETURN THE ENTIRE UNUSED PRODUCT
FOR A FULL REFUND.
In return for acquiring a License to use the FarStone "Software", which may
include software from third party licensors, trial versions or copies of the
"Software" and patches made available by FarStone and the related
documentation, you agree to the following terms and conditions:
A. Single User License: This Agreement grants you, the Licensee, a
License to:
(a) Use the "Software" on a single computer system or network, and only
by a single user at a time. If you wish to use the "Software" for more users,
you will need an additional License for each user.
(b) Make one copy of the "Software" in machine-readable form solely for
back-up purposes, provided you reproduce FarStone's copyright
proprietary legends. Notwithstanding the foregoing, the "Software" may be
used on the home, laptop or other secondary computer of the principal
user of the "Software", and an additional copy of the "Software" may be
made to support such use. As used in this License, the "Software" is "in
use" when it is either loaded into RAM or installed on a hard disk or other
permanent memory device. The "Software" may be "in use" on only one
computer at any given time. (Different License terms and fees are
applicable for networked or multiple user applications.) As a specific
condition of this License, you agree to use the "Software" in compliance
with all applicable laws, including copyright laws, and that you will not copy ,
transmit, perform or distribute any audio or other content using the
"Software" without obtaining all necessary Licenses or permissions from
the owner of the content.
TM
, HEREAFTER
38
Page 39

B. Multiple User License: This Agreement grants you, the Licensee, a
License to:
Make one copy of the "Software" in machine-readable form solely for
back-up purposes, provided you reproduce FarStone's copyright
proprietary legends.
You must acquire and dedicate a License for each separate computer on
which any part or portion of the "Software" is installed or run. As used in
this License, the "Software" or any part or portion of the "Software" is "in
use" when it is either loaded into RAM or installed on a hard disk or other
permanent memory device including any networked or share d environment
where either direct or indirect connections are made through software or
hardware which pools or aggregates connections.
As a specific condition of this License, you agree to use the "Software" in
compliance with all applicable laws, including copyright laws, and that you
will not copy, transmit, perform or distribute any audio or other content
using the "Software" without obtaining all necessary Licenses or
permissions from the owner of the content.
C. Restrictions: You may not distribute copies of the "Software" to others
or electronically transfer the "Software" from one computer to another over
a network. You may not post or otherwise make available the "Software",
or any portion thereof, in any form, on the Internet. You may not use the
"Software" in a computer service business, including in time-sharing
applications. The "Software" contains trade secrets and, in order to
protect them, you may not decompile, reverse engineer, disassemble, or
otherwise reduce the "Software" to a human-perceivable form. YOU MAY
NOT MODIFY, ADAPT, TRANSLATE, RENT, LEASE, LOAN, RESELL
FOR PROFIT, DISTRIBUTE, NETWORK OR CREATE DERIVATIVE
WORKS BASED UPON THE "SOFTWARE" OR ANY PART THEREOF.
D. Ownership: As Licensee, you own the media upon which the
"Software" is recorded or fixed, but FarStone and its Licensors retain title
and ownership of the "Software" recorded on the original media and all
subsequent copies of the "Software", regardless of the form or media in
which or on which the original and other copies may exist. This License
does not grant, convey or in any way transfer ownership of the "Software".
E. Separation of Components: The "SOFTWARE" is licensed as a single
product. Its component parts may not be separated for use on more than
one computer, not withstanding reference to Section B of this License
agreement where Multiple user Licenses have been purchased.
F. Confidentiality: You agree to maintain the "Software" in confidence and
that you will not disclose the "Software" to any third party without the
express written consent of FarStone. You further agree to take all
39
Page 40

reasonable precautions to preclude access of unauthorized persons to the
"Software".
G. Term: This License shall continue for as long as you use the "Sof tware".
However, it will terminate if you fail to comply with any of its terms and
conditions. You may terminate the License at any time by destroying the
"Software" (including the related document ation) together with all copies or
modifications in any form. FarStone will have the right to terminate our
License immediately if you fail to comply with any term or condition of this
Agreement. Upon any termination, including termination by you, you
must destroy the "Software" (including the related documentation),
together with all copies or modifications in any form. The Limitations,
Warranties and Liability set out below shall continue in force even after any
termination.
H. Transfer: You may transfer the "Software" License to someone else,
only if you assign all of your rights under this License, cease all use of the
"Software", erase or destroy any copy (including the hard disk copy) made
in support of your use of the "Software", and the other person agrees to the
terms of this License.
If the "Software" is an upgraded from other "Software", whether from us or
another supplier , you may use or transfer the "Software" only in conjunction
with the upgraded "Software", unless you destroy it. If the "Software" is
an upgrade from a FarSton e, you may only use that upgraded "Sof tware" in
accordance with this License.
I. Special Terms Applicable to Databases. Where a database is
included with the "Software", you acknowledge that it is licensed only in
connection with the use of the "Software" to perform disc creation, a nd that
the database and all data derived there from must be maintained in
confidence in accordance with the provisions of Section E of this document.
This License does not grant you any rights to distribute or disclose such a
database or data contained therein.
J. Limited Warranty: FarStone and its Licensor warrant only that the
media upon which the "Software" is furnished will be free from defects in
material or workmanship under normal use and service for a period of thirty
(30) days from the date of delivery to you. FARSTONE AND ITS
LICENSORS DO NOT AND CANNOT WARRANT THE PERFORMANCE
OR RESULTS YOU MAY OBTAIN BY USING THE "SOFTWARE" OR
DOCUMENTATION. THE FOREGOING STATES THE SOLE AND
EXCLUSIVE REMEDIES FARSTONE AND ITS LICENSORS WILL
PROVIDE FOR BREACH OF WARRANTY. EXCEPT FOR THE
FOREGOING LIMITED WARRANTY, FARSTONE AND ITS LICENSORS
MAKE NO WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, BUT
40
Page 41

NOT LIMITED, AS T O NO N-INFRI NGEMENT OF TH IRD PARTY RIGHTS,
MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
Some states do not allow the exclusion of implied warranties or limitations
on how long an implied warranty may last, so the above limitations may not
apply to you. This warranty gives you specific legal rights and you may
also have other rights, which vary from state to state.
The entire liability of FarStone and its Licensors, and your exclusive
remedy for a breach of this warranty, shall be: (a) the replacement of any
media not meeting the above limited warranty which is returned to
FarStone; or (b) if FarStone or its distributor is unable to deliver
replacement media which is free from defects in materials o r workm anship,
you may terminate this Agreement by returning the "Software" and your
money will be refunded.
K. Limitation of Liability: IN NO EVENT WILL FARSTONE OR ITS
LICENSORS BE LIABLE TO YOU FOR ANY INCIDENTAL,
CONSEQUENTIAL OR INDIRECT DAMAGES, INCLUDING ANY LOST
PROFITS, LOST SAVINGS, OR L OF THE POSSIBILITY OF SUCH
DAMAGES, OR FOR ANY CLAIM BY ANY OTHER PARTY. Some states
do not allow the exclusion or limitation of special, incidental, or
consequential damages, so the above limitation or exclusion may n ot apply
to you.
L. Bundling: In no case may the "SOFTWARE" be bundled with hardware
or other software without written permission from FarStone.
M. Export: You acknowledge that the laws and regulations of the United
States and/or other countries may restrict the export and re-export of the
"Software". You agree that you will not export or re-export the "Software"
or documentation in any form in violation of applicable law in the United
States and/or foreign law.
N. General: You acknowledge that you have read this Agreement,
understand it, and that by using the "Software" you agree to be bound by
its terms and conditions. You further agree that it is the complete and
exclusive statement of the agreement between FarStone and you, and
supersedes any proposal or prior agreement, oral or written, and any other
communication between FarStone and you relating to the subject matter of
this Agreement. No additional or any different terms will be enforceable
against FarStone unless FarStone gives its express consent, including an
express waiver of the terms of this Agreement, in writing signed by an
officer of FarStone. You assume full responsibility for the use of the
"Software" and agree to use the "Software" legally and responsibly.
41
Page 42

Should any provision of this Agreement be declared unenforceable in any
jurisdiction, then such provision shall be deemed severable from this
Agreement and shall not affect the remainder hereof. FarStone reserves
all rights in the “Software” not specifically granted in this Agreement.
7.2 Technical Support & Product Upgrade
Please contact your retailer, or use our online support system at
www.farstone.com.
For your convenience, you will find answers to frequently asked questions
on our website at www.farstone.com
section.
Technical support: support@farstone.com
Headquarters:
FarStone Technology, Inc.
Legal Department
15550-B Rockfield Blvd., Suite 100
Irvine, CA 92618
. Follow the links to the support
42
 Loading...
Loading...