F5 FirePass Administrator's Manual

FirePassTM Server Administrator Guide
version 4.0
MAN-0081-00


Product Version
Legal Notices
This manual applies to product version 4.0 of the FirePass™ Server Administrator Guide.
Copyright
Copyright © 1999-2003, F5 Networks, Inc. All rights reserved.
F5 Networks, Inc. (F5) believes the information it furnishes to be accurate and reliable. However, F5
assumes no responsibility for the use of this information, nor any infringement of patents or other rights of
third parties which may result from its use. No license is granted by implication or otherwise under any
patent, copyright, or other intellectual property right of F5. F5 reserves the right to change specifications at
any time without notice.
Trademarks
F5, F5 Networks, the F5 logo, BIG-IP, 3-DNS, iControl, GLOBAL-SITE, SEE-IT, EDGE-FX, FireGuard,
Internet Control Architecture, IP Application Switch, Packet Velocity, iRules, SYN Check, FirePass, and
Webifyer are registered trademarks or trademarks of F5 Networks, Inc. in the U.S. and certain other
countries. All other trademarks mentioned in this document are the property of their respective owners. F5
Networks' trademarks may not be used in connection with any product or service except as permitted in
writing by F5.
Export Regulation Notice
This product may include cryptographic software. Under the Export Administration Act, the United States
government may consider it a criminal offense to export this product from the United States.
Export Warning
This is a Class A product. In a domestic environment this product may cause radio interference in which
case the user may be required to take adequate measures.
FCC Compliance
This equipment generates, uses, and may emit radio frequency energy. The equipment has been type tested
and found to comply with the limits for a Class A digital device pursuant to Part 15 of FCC rules, which
are designed to provide reasonable protection against such radio frequency interference.
Operation of this equipment in a residential area may cause interference, in which case the user at his own
expense will be required to take whatever measures may be required to correct the interference.
Any modifications to this device, unless expressly approved by the manufacturer, can void the user's
authority to operate this equipment under part 15 of the FCC rules.
Canadian Regulatory Compliance
This class A digital apparatus complies with Canadian I CES-003.
Standards Compliance
The product conforms to ANSI/UL Std 1950 and Certified to CAN/CSA Std. C22.2 No. 950.
FirePass™ Server Administrator Guide i

ii

Table of Contents


1
Introducing the FirePass Server
The FirePass remote access solution ........................................................................................1-1
The FirePass server models ........................................................................................................1-1
The FirePass server features .......................................................................................................1-2
Overview of features ............................................................................................................1-2
FirePass server features .......................................................................................................1-3
About this guide ..............................................................................................................................1-4
Audience ..................................................................................................................................1-4
Finding help and technical support resources ..........................................................................1-5
2
Deploying the FirePass Server
Overview of deploying the FirePass server .............................................................................2-1
Summary of tasks for installing and deploying the FirePass server ............................2-1
Configuring a firewall to work with the FirePass server ......................................................2-2
Overview of the firewall configuration process ............................................................2-3
About the traffic between a remote user’s browser and the FirePass server ........2-5
About the traffic between the FirePass server and network services .....................2-6
About the traffic between FirePass server and application services ........................2-7
About the traffic between the FirePass server and the Desktop Agent .................2-9
Understanding name resolution issues for FirePass servers with
a private IP address .................................................................................................................... 2-11
Installing the FirePass server .................................................................................................... 2-12
Unpacking the FirePass server ......................................................................................... 2-12
Installing the FirePass server in an equipment rack .................................................... 2-12
Connecting the FirePass server to a network and powering up ............................. 2-12
Performing the initial FirePass IP configuration ........................................................... 2-14
Testing network connectivity ..................................................................................................2-16
Using the Administrative Console to configure the FirePass server .............................. 2-17
Logging Into the Administrative Console ...................................................................... 2-17
Changing the superuser password ................................................................................ 2-18
Installing your license ......................................................................................................... 2-19
Displaying a list of current settings and licensed features ........................................ 2-19
Using the Administrative Console to access the Maintenance Console ............... 2-20
Logging out of the Administrative Console .................................................................. 2-20
Using the Maintenance Console ............................................................................................... 2-21
What’s next? ................................................................................................................................ 2-23
Table of Contents
3
Setting Up FirePass Server Security
Overview of setting up FirePass server security .....................................................................3-1
Working with groups ....................................................................................................................3-2
Working with user accounts ....................................................................................................3-11
FirePass™ Server Administrator Guide v
Creating groups ......................................................................................................................3-3
Deleting groups ......................................................................................................................3-4
Moving users to a different group ......................................................................................3-4
Showing a list of all users in a group .................................................................................3-4
Using Windows domain-based group mapping ...............................................................3-4
Using LDAP-based group mapping ....................................................................................3-6
Manually adding user accounts ....................................................................................... 3-11
Importing user accounts from a Windows domain server ....................................... 3-13
Importing user accounts from an LDAP server .......................................................... 3-15
Importing user accounts from a comma or tab delimited text file ......................... 3-16

Table of Contents
Using signup templates to add user accounts .............................................................. 3-16
Using NFS user permissions from a UNIX password file ......................................... 3-17
Changing user accounts ................................................................................................... 3-19
Activating, deactivating, or deleting user accounts .................................................... 3-19
Assigning administrative privileges to a user account ............................................... 3-19
Searching for user accounts ............................................................................................. 3-21
Generating a My Desktop client software installation key ....................................... 3-21
Installing My Desktop client software at a user’s computer ..................................... 3-22
Setting up FirePass server authentication .............................................................................. 3-23
Converting to internal database authentication .......................................................... 3-23
Setting up RADIUS server authentication ................................................................... 3-24
Setting up a RADIUS server to work with the FirePass server ............................... 3-25
Setting up Windows domain server authentication ................................................... 3-25
Setting up LDAP server authentication ........................................................................ 3-27
Setting Up VASCO DigiPass authentication ................................................................ 3-28
Setting up certificates .................................................................................................................. 3-29
Changing the FirePass server name ................................................................................ 3-30
Generating a server certificate request ......................................................................... 3-30
Installing or renewing a server certificate ..................................................................... 3-31
Using client certificates to authenticate a user’s computer ...................................... 3-31
Limiting access to the administrative console by IP address ............................................. 3-35
What’s next? ................................................................................................................................. 3-35
4
Configuring the FirePass Webifyers
Overview of the FirePass Webifyers ..........................................................................................4-1
Configuring the My Files Webifyer ............................................................................................4-3
Defining Network Folder Favorites for the My Files Webifyer ................................4-3
Limiting a group’s access to the Network Folder Favorites ......................................4-3
Enabling virus scanning and file uploading for the My Files Webifyer ......................4-4
Configuring advanced settings for the My Files Webifyer ............................................4-4
Using client certification validation for the My Files Webifyer ..................................4-5
Configuring the My NFS Webifyer ............................................................................................4-6
Defining favorites for the My NFS Webifyer .................................................................4-6
Defining NFS shared folders for the My NFS Webifyer ...............................................4-7
Limiting a group’s access to the NFS Favorites .............................................................4-7
Using client certification validation for the My NFS Webifyer ..................................4-7
Configuring the My Intranet Webifyer .....................................................................................4-8
Defining intranet favorites for the My Intranet Webifyer ............................................4-8
Limiting a group’s access to the Intranet Favorites .................................................... 4-10
Using client certification validation for the My Intranet Webifyer ........................ 4-10
Configuring the My E-mail Webifyer ...................................................................................... 4-11
Configuring an email account .......................................................................................... 4-11
Obtaining each user’s email information based on an LDAP query ...................... 4-12
Disabling email attachment downloads ........................................................................ 4-13
Obtaining email addresses from an LDAP server ...................................................... 4-13
Using client certification validation for the My E-mail Webifyer ............................ 4-14
Configuring the Terminal Services Webifyer ....................................................................... 4-15
Configuring screen resolution and Terminal Services Favorites ............................. 4-15
Limiting a group’s access to the Terminal Service Favorites ................................... 4-17
Using client certification validation for the Terminal Service Webifyer ............... 4-17
Configuring the AppTunnels Webifyer .................................................................................. 4-18
Configuring AppTunnel Favorites .................................................................................. 4-18
Compressing traffic between the client and the FirePass server ........................... 4-20
Limiting a group’s access to the AppTunnels Favorites ............................................. 4-20
vi

Table of Contents
Using client certification validation for the AppTunnels Webifyer ........................ 4-20
Configuring the Host Access Webifyer ................................................................................. 4-21
Configuring Host Access Favorites ............................................................................... 4-21
Displaying active host access sessions .......................................................................... 4-22
Limiting a group’s access to the host access favorites .............................................. 4-22
Using client certification validation for the Host Access Webifyer ....................... 4-22
Configuring SSL-VPN ................................................................................................................. 4-23
Configuring global SSL VPN settings ............................................................................. 4-24
Configuring global SSL VPN packet filter rules ........................................................... 4-25
Configuring global SSL VPN timeout rules .................................................................. 4-26
Configuring global SSL VPN client appearance ........................................................... 4-26
Configuring the SSL VPN Webifyer for a group ........................................................ 4-27
Configuring group packet filter rules ............................................................................ 4-29
Configuring drive mappings for the SSL VPN Webifyer ........................................... 4-29
Launching applications automatically with the SSL VPN Webifyer ........................ 4-30
Using client certification validation for the SSL VPN Webifyer ............................. 4-30
Configuring the My Desktop Webifyer ................................................................................. 4-31
Configuring the My Desktop server ports .................................................................. 4-31
Configuring My Desktop Webifyer for cluster servers ............................................ 4-32
Disabling bridge access to desktops .............................................................................. 4-32
Using client certification validation for the My Desktop Webifyer ....................... 4-33
Configuring the Guest Access Webifyer ..................................................................... 4-33
Configuring the X-Windows Access Webifyer ................................................................... 4-35
Configuring X-Windows hosts for remote access ..................................................... 4-35
Using client certificate validation for Webifyers ................................................................... 4-38
5
Managing, Monitoring, and Maintaining the FirePass Server
Maintaining the network configuration settings .....................................................................5-1
Configuring IP addresses and subnets ...............................................................................5-1
Configuring routing tables and rules .................................................................................5-2
Configuring Domain Name Servers (DNS) .....................................................................5-4
Configuring host names ........................................................................................................5-5
Configuring services ..............................................................................................................5-5
Configuring Desktop services .............................................................................................5-8
Other network settings ........................................................................................................5-8
Configuring IPSec for the FirePass server ................................................................................5-9
Managing FirePass licenses ......................................................................................................... 5-11
Obtaining a license for the first time .............................................................................. 5-11
Installing your license ......................................................................................................... 5-11
Adding capacity or features to your license ................................................................. 5-11
Mapping FirePass users to NFS users .................................................................................... 5-12
Specifying HTTP and SSL proxies ........................................................................................... 5-14
Configuring an SNMP agent .....................................................................................................5-15
Shutting down and restarting FirePass .................................................................................... 5-17
Shutting down the FirePass server ................................................................................. 5-17
Restarting the FirePass server or services .................................................................... 5-17
Stopping and starting the bridge .................................................................................... 5-18
Backing up and restoring the FirePass server ...................................................................... 5-19
Specifying the email server ...................................................................................................... 5-20
Specifying the FirePass administrator’s email address ......................................................... 5-20
Granting Administrator privileges to other users ................................................................ 5-21
Specifying the time, time zone, and NTP server ................................................................. 5-22
Configuring client caching and compression settings ......................................................... 5-23
Managing log files ........................................................................................................................ 5-25
FirePass™ Server Administrator Guide vii

Table of Contents
Updating the FirePass server’s firmware ............................................................................... 5-27
Adding definitions for other types of browsers .................................................................. 5-28
Monitoring the FirePass server ............................................................................................... 5-29
Monitoring the load on a FirePass server .................................................................... 5-29
Displaying FirePass server statistics .............................................................................. 5-30
Capturing network packets to troubleshoot networking problems ..................... 5-30
Customizing the user’s home page .......................................................................................... 5-31
Providing SSH access for Technical Support ......................................................................... 5-31
6
Using FirePass Reports
Overview of FirePass server reports ........................................................................................6-1
Using the Logon report ................................................................................................................6-2
Using the My Desktop Activations report ...............................................................................6-3
Using the Session report ..............................................................................................................6-4
Using HTTP Log reports ..............................................................................................................6-5
Using the Application Log report ..............................................................................................6-6
Using the Summary report ..........................................................................................................6-7
Using the Group report ...............................................................................................................6-8
7
Configuring FirePass Failover Servers and Cluster Servers
Using FirePass failover servers ...................................................................................................7-1
Installing FirePass failover servers ....................................................................................7-1
Configuring the IP addresses for failover servers .........................................................7-1
Powering up failover servers .............................................................................................7-2
Configuring the failover settings .......................................................................................7-3
Making a standby server the active server .....................................................................7-4
Using FirePass server clusters ....................................................................................................7-5
Installing multiple FirePass servers as a cluster .............................................................7-5
Powering up FirePass server clusters ..............................................................................7-5
Configuring FirePass server clusters ................................................................................7-6
Preliminary configuration .....................................................................................................7-6
Configuring clustered servers .............................................................................................7-7
Accessing a slave server’s configuration while connected to a master server ........7-8
Displaying statistics for a FirePass server cluster ..........................................................7-8
Index
viii

1
Introducing the FirePass Server
• The FirePass remote access solution
• The FirePass server models
• The FirePass server features
• About this guide
• Finding help and technical support resources


The FirePass remote access solution
The FirePass™ server is a network appliance providing remote users with
secure access to corporate networks, using any standard Web browser. The
FirePass server can be installed in a few hours and it requires no
modifications to corporate applications. No configuration or setup is
required at the user’s remote location. If the user’s Web browser can
connect to Web sites on the Internet, then that browser can connect to the
the FirePass server.
The FirePass server provides a web-based alternative to traditional
remote-access technologies such as modem pools, RAS servers, and
IPSec-layer Virtual Private Networks (VPNs). By leveraging the browser as
a standard “thin client,” FirePass server enables a corporation or
organization to extend secure remote access easily and cost-effectively to
anyone connected to the Internet with no special software or configuration
on the remote device. Also, no additions or changes are necessary to the
back-end resources being accessed. This approach eliminates the IPSec
VPN support burden and adds application functionality well beyond mere
connectivity.
Introducing the FirePass Server
The FirePass server provides full access to network and desktop resources,
including:
• File servers
•Email
• Intranet
• Terminal servers
• Legacy mainframe, AS/400, and Telnet applications
• Client/server applications
• All desktop PC applications
The FirePass server models
The FirePass server is available in two models:
◆
FirePass 1000:
• Supports up to 100 concurrent users
• 1U rackmount chassis
• Includes one 10/100 Ethernet port and supports an option for a second
10/100 Ethernet port
• 200 watt power supply
◆
FirePass 4000:
• Supports up to 1000 concurrent users
• 2U rackmount chassis
• Includes two 10/100 Ethernet ports
• 480 watt power supply
FirePass™ Server Administrator Guide 1 - 1

Chapter 1
The FirePass server features
Overview of features
◆
Security
FirePass server was built from the ground up to adhere to the highest
standards of best security practices.
• Encryption—FirePass server offers several strengths of encryption,
depending on the capability of the browser in use and on the optional
security settings of the FirePass implementation. FirePass server
offers encryption keys up to 1024 bits.
• Authentication—FirePass server includes an internal user database for
password authentication, and it can use existing RADIUS, LDAP, and
Windows domain servers for authentication. Administrators can
require different authentication methods for different groups. If you
want to use two-factor authentication, FirePass server supports RSA
SecurID
built-in implementation of VASCO Digipass
• Access Control—FirePass server grants access to specific
applications to individuals or to groups of users. With FirePass
server’s access controls, you can restrict individuals and groups to
particular resources. For example, partners can be have restricted
access to an extranet server only, while sales staff can connect to
email, the company Intranet, and the CRM system.
®
token-based authentication, and also offers an optional,
®
.
◆
Availability
Unlike IPSec VPNs, Web-based remote access works over all ISP
connections and works from behind other firewalls. ISPs cannot detect
and block FirePass server conversations as they might with detected
IPSec traffic. Failover and clustering options provide high availability
and high capacity. FirePass servers can be clustered to support up to
10,000 concurrent connections on a single logical URL without
performance degradation.
◆
Ease of use, deployment, maintenance, and management
FirePass server installs in a few hours. Users are presented with an
intuitive, browser-based interface and they require minimal training after
a brief introduction. FirePass server can be upgraded in the field over the
Web. Automatic release update notifications prompt the FirePass server
administrator to download new versions when they become available.
Features and capacity can also be added over the Web.
1 - 2

FirePass server features
The following features are available on both FirePass server models.
◆
Standard Web browser support
FirePass server can be used with most standard browsers supporting
secure HTTP (also known as HTTPS). These include Internet Explorer®,
Netscape Navigator®, Opera®, and Mozilla®.
◆
WAN security
FirePass server supports common encryption technologies, including
RC4 and 3DES. It uses standard SSL encryption from the client browser
to the FirePass server.
◆
Authentication
FirePass server performs basic authentication using an internal database.
It also supports two-factor (token-based) authentication methods like
RSA SecurID® and VASCO Digipass.
FirePass server authenticates devices using signed digital certificates.
FirePass server can be integrated with LDAP directories and Windows
Domain Servers.
Introducing the FirePass Server
◆
Application access using standard Webifyers
FirePass server provides access to virtually all corporate and desktop
applications, including email, file, and Intranet access, client-server
application access, legacy host application access (mainframe, AS/400,
X-Windows, and Telnet), and Terminal Services/Citrix® application
access.
◆
Mobile device access
FirePass server provides email, file, and Intranet access from
mini-browsers on mobile devices. These include Internet-enabled (WAP
and iMode) telephones, PDAs (PalmOS® and Pocket PC), and RIM
Blackberries™.
◆
Administration
FirePass server provide a web–based Administrator Console. The
Console includes tools for installing and managing the FirePass server,
including user and group enrollment and management, clustering and
failover configuration, certificate generation and installation, and user
interface customization.
◆
Audit trail
FirePass server provides audit tools including full-session audit trails,
drill-down session queries, and customizable reports and queries.
◆
Client/Server application support
FirePass server offers a Client-Server Connector™ providing
application-specific tunnels for client-server applications like
Microsoft® Outlook®, ERP package applications, and custom TCP/IP
applications.
FirePass™ Server Administrator Guide 1 - 3
FirePass server also provides a VPN Connector™ giving full network
access comparable to that offered by a traditional IPSec VPN connection.

Chapter 1
About this guide
◆
Desktop Access
FirePass server offers web–based access to authorized desktops with
support for remote control, lightweight email/file access, guest access,
and Web conferencing.
◆
High availability
FirePass servers can be configured to failover to hot standby servers.
◆
Scalability
FirePass server clusters support up to 10,000 users on a single logical
server.
This FirePass Administrator Guide provides information and step-by-step
instructions for installing and administering the FirePass™ 1000 and 4000
servers.
This guide is available as an Adobe Acrobat file (.pdf). (To install a free
version of Adobe Acrobat Reader, see http://www.adobe.com.)
Audience
This guide is for system and network administrators who install and
configure IT equipment and software. This guide assumes that
administrators have experience installing software and working with
network configurations.
1 - 4
Introducing the FirePass Server
Finding help and technical support resources
You can find additional technical documentation about the FirePass server
in the following locations:
◆
Release notes
Release notes containing the latest information for the current version of
FirePass server are available from the Administrative Console. Click the
Maintenance tab and then click the Online Update link. Release notes
include a list of new features and enhancements, a list of fixes, and a list
of known issues.
◆
Online help for FirePass features
You can find help online for virtually all screens on the Administrative
Console. Click the Help Page button in the upper right of the panel.
◆
Technical support through the World Wide Web
®
The F5
provides the latest technical notes, answers to frequently asked questions,
updates for the Administrator Kit (in PDF format), updates for the
release notes, and the Ask F5 natural language question and answer
engine.
Networks Technical Support web site, http://tech.f5.com,
Conventions used in this manual
Information that you type appears in a bold, monospace font. For example:
admin
A Tip suggests ways to make administration easier or faster. For example:
Tip
An easy way to enter a user agent string is to copy and paste the string from
the Logons report.
A Note or Important contains important information. For example:
Note
If you are powering up a server cluster, always power up the master server
first.
Important
If your superuser password is lost, con tact Technical Support.
A Warning describes actions that can cause data loss or problems. For
example:
FirePass™ Server Administrator Guide 1 - 5
WARNING
Do not turn the FirePass server off by using the Power switch on the front
panel.

Chapter 1
1 - 6

2
Deploying the FirePass Server
• Overview of deploying the FirePass server
•Configuring a firewall to work with the FirePass
server
• Understanding name resolution issues for FirePass
servers with a private IP address
• Installing the FirePass server
• Testing network connectivity
• Using the Administrative Console to configure the
FirePass server
• Using the Maintenance Console
• What’s next?

Deploying the FirePass Server
Overview of deploying the FirePass server
This section contains an overview of the tasks for deploying the FirePass™
server.
Summary of tasks for installing and deploying the FirePass server
Table 2.1 provides a summary of the tasks for installing and deploying the
FirePass server.
Task For more information, see
Configure the firewalls at your site to allow traffic to and
from the FirePass server.
If the FirePass server has a private IP address, set up
name resolution for internal users and client software.
Install the FirePass server, and power it up. Using the
WAN port, create an isolated network to reach the
FirePass server using its factory default IP address.
Enter basic configuration information using either the
Administrative Console (recommended) or the
Maintenance Console (available as a backup).
Connect the FirePass server to the network. Test that the
FirePass server is accessible on the network, and test
DNS resolution of the FirePass server’s host name inside
and outside firewall.
After the FirePass server is up and running and the
network connections are working, use the Administrative
Console to finish configuring the server from a Web
browser.
(Recommended) Change the superuser password. Changing the superuser password, on page 2-18
Configure one or more authentication methods for
FirePass users. Then add groups and user accounts.
Configuring a firewall to work with the FirePass server, on
page 2-2
Understanding name resolution issues for FirePass
servers with a private IP address, on page 2-11
Installing the FirePass server, on page 2-12
Using the Administrative Console to configure the
FirePass server, on page 2-17
Testing network connectivity, on page 2-16
Using the Administrative Console to configure the
FirePass server, on page 2-17
Chapter 3, Setting Up FirePass Server Security
Configure the FirePass server’s Webifyers that you want
to make available to users. For example, configure the
SSL VPN Webifyer, if necessary.
Install a new SSL certificate. Setting up certificates, on page 3-29
(Optional) If necessary, customize the appearance of the
user’s home panel, such as the logo and terms used for
logging in.
Table 2.1 Overview of FirePass Deployment Tasks
FirePass™ Server Administrator Guide 2 - 1
Chapter 4, Configuring the FirePass Webifyers
Customizing the user’s home page, on page 5-31
Chapter 2
Configuring a firewall to work with the FirePass
server
The FirePass server enables remote access by communicating through
secure tunnels between remote users at untrusted or unprivileged hosts on
the Internet and your corporate LAN. This section describes the firewall
ports at your site that must be opened to allow traffic to and from the
FirePass server so that it can operate correctly.
The particular firewall ports that you must open at your site depend on
where you install the FirePass server relative to the firewalls, and which
network and application services the server must access. There are some
ports that must be open in all situations, such as ports 80 and 443 for HTTP
and HTTPS, on the external firewall between the FirePass server and remote
Web browsers. If the FirePass server is installed in a DMZ with an internal
firewall separating it from the corporate network, you also have to open
other ports as necessary to allow access to network services such as DNS,
and to use particular application services such as e-mail.
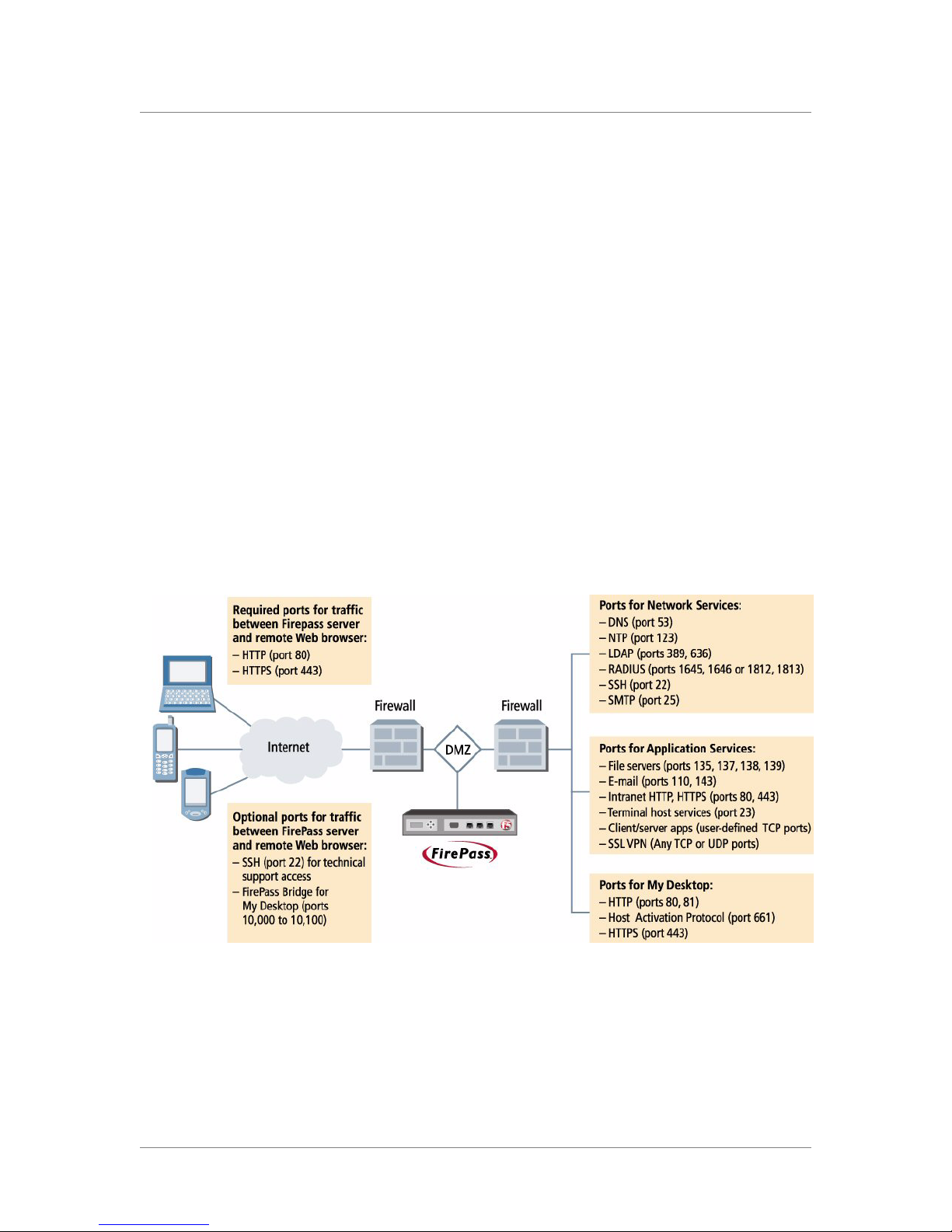
The illustration in Figure 2.1 shows the services and ports used by the
FirePass server.
.
Figure 2.1 Allowing traffic on firewall ports for a FirePass server
For more information on configuring the firewall ports, see the foll owin g
section and the tables on pages 2-6 through 2-10.
2 - 2

Overview of the firewall configuration process
During the process of firewall configuration, you might consider opening
the firewall ports in phases. In the initial phase, you could focus on opening
the ports that allow access to the FirePass server from both inside and
outside the firewall when you specify the server’s host name in a Web
browser. In this initial phase, you might also open the ports for SMTP so
that the FirePass server can send email messages to the FirePass
administrator. For this initial phase, the following ports need to be opened:
• Assuming there is a firewall between the Internet and the FirePass server,
the firewall must allow inbound traffic on ports 80 (HTTP) and 443
(SSH) as a base configuration with a destination address of the publicly
accessible FirePass address.
• The firewall must also allow the FirePass server access to network
services such as NTP, DNS, and SMTP (on ports 123, 53, and 25). The
network services might be located on an external network (Internet), or
on the internal corporate network. The location of the network services
and your particular deployment scenario determines which firewall’s
ports must be open, assuming there is a firewall between the FirePass
server and these services.
• If there is a firewall between the FirePass server and the corporate LAN,
the firewall must allow traffic on ports 80, 443, and 661.
Deploying the FirePass Server
To verify that the FirePass server has access to DNS and SMTP services
after you have opened the ports and installed the FirePass server, you can
use the instructions in Testing network connectivity, on page 2-16.
After you have verified that the FirePass server has access to DNS and
SMTP services and that you can access the server from a Web browser from
either side of the firewall, then you can open up the specific ports that are
necessary for your particular deployment. See the following tables in this
section that describe the ports and services. For example, if you are using
LDAP for authentication, you must open ports 389 and 636. Here are some
other examples of application services you might need to support:
• To support My Files, the FirePass server needs access to Windows file
servers using Microsoft Networking (ports 135, 137, 138, 139).
• To support My Email, the FirePass server needs access to POP/IMAP
and LDAP (ports 110, 143, 389, 636).
• To support Host Access, the FirePass server needs access to Telnet (port
23).
The services are sometimes hosted locally behind a firewall, and sometimes
hosted remotely. If the services are hosted remotely, the external firewall
must allow the FirePass server to make connections to those services on
specific TCP/IP ports.
To allow access to the FirePass server from the Internet, you can create
either Network Address Translation (NAT) rules or port forwarding rules on
the firewall to forward inbound packets to the server. The advantage of
static NAT is that it does not require you to forward each individual port to
FirePass™ Server Administrator Guide 2 - 3

Chapter 2
the FirePass server. To use static NAT, configure a rule that forwards all
allowable traffic from the public IP address to the private IP assigned to the
FirePass server. However, some firewalls only allow static NAT using a
public IP address other than its own public interface. In this case, you must
use port forwarding by setting up rules to forward the appropriate ports to
the private IP address assigned to the FirePass server.
Firewalls can be classified as stateful and non-stateful. Stateful firewalls
allow bi-directional communication (that is, they create a return rule for an
allowed service). Older firewalls, especially ones based on Linux IP chains,
are often non-stateful; they do not allow bi-directional communications. If
you have a stateful firewall (most newer commercial firewalls are stateful),
you only need to define rules for the actual traffic; the replies are
automatically allowed to pass. If you have a non-stateful firewall, you also
must define rules for traffic coming in and the replies with the ACK
(acknowledgement) bit set for those protocols.
For completeness, the following tables list the types of traffic (in pairs of
request and response) that must be allowed through the firewalls for each
category of FirePass server functionality.
All traffic associated with the FirePass server falls into in one of these
categories:
• Traffic between the remote user’s browser and the FirePass server. (See
About the traffic between a remote user’s browser and the FirePass
server, on page 2-5.)
• Traffic between the FirePass server and network services, such as LDAP,
RADIUS, and DNS. (See About the traffic between the FirePass server
and network services, on page 2-6.)
• Traffic between the FirePass server and application services, such as file
servers, email servers, and the Intranet. (See About the traffic between
FirePass server and application services, on page 2-7.)
• Traffic between the FirePass server and corporate LAN using My
Desktop. (See About the traffic between the FirePass server and the
Desktop Agent, on page 2-9.)
2 - 4
Note
A particular type of traffic shown in the tables is only required if Required
appears in the Comment column for the traffic, or, as stated previously, if
you are enabling an application service that requires the port to be opened.
Deploying the FirePass Server
About the traffic between a remote user’s browser and the
FirePass server
To allow traffic between a remote user’s browser and the FirePass server,
you must open the firewall ports as shown in Table 2.2.
The FirePass bridge ports (10000-10100) are optional ports in the external
firewall that are used to distribute sessions to ensure that port 443 is open for
new requests. These ports are configurable, and can be set to any of the high
TCP/IP ports (1025 – 65535). If the number of concurrent My Desktop users
is low—less than 5 concurrent users on the FirePass 1000, or less than 20 on
the FirePass 4000—then there is no requirement to open the high TCP/IP
ports (1025 to 65535). The server uses the high ports if they are available,
otherwise it uses port 443.
During installation, or in case of severe malfunction, you may need to give
Technical Support access to your Maintenance Console using Secure Shell
(SSH). To allow this access while blocking routine SSH access, the FirePass
server provides temporary, encrypted keys, further protected by a
passphrase. For more information about providing SSH access to Technical
Support, see Providing SSH access for Technical Support, on page 5-31.
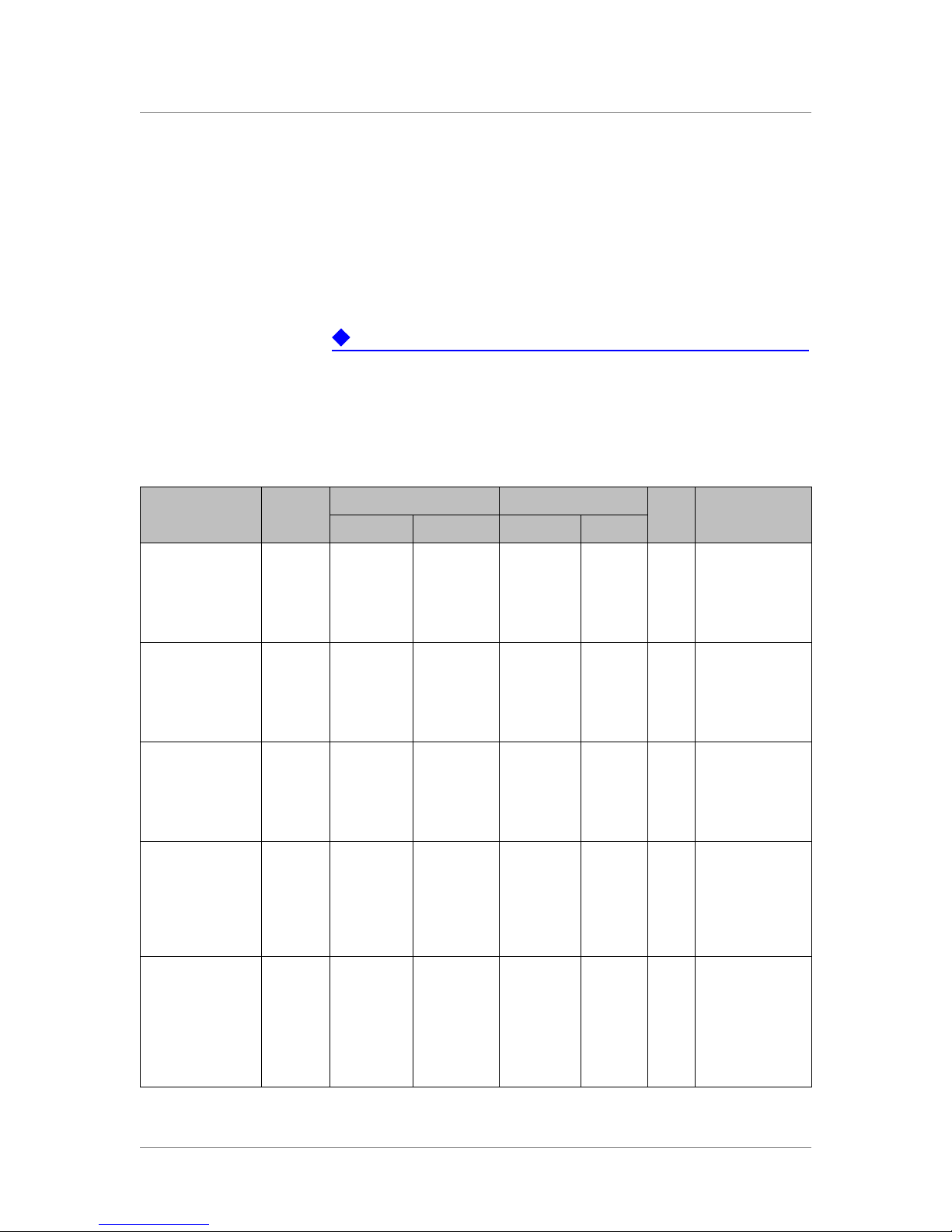
Source Destination
Traffic Type Protocol
HTTP TCP Remote
HTTP
(response)
HTTPS TCP Remote
HTTPS
(response)
FirePass
bridge
FirePass
bridge
Response
SSH TCP Local LAN 1025 to
TCP FirePass
TCP FirePass
TCP Remote
TCP FirePass
Browser
server
Browser
server
Browser
server
1025 to
65535
80 Remote
1025 to
65535
443 Remote
1025 to
65535
10000 to
10100
65535
FirePass
server
Browser
FirePass
server
Browser
FirePass
server
Remote
Browser
FirePass
server
Ack
bit
80 Required
1025 to
65535
443 Required
1025 to
65535
10000 to
10100
1025 to
65535
22 Optional
yes Required
yes Required
yes Optional for
CommentAddress Ports Address Ports
Optional for
My Desktop
My Desktop
SSH
(response)
TCP FirePass
Table 2.2 Traffic between a remote user’s browser and the FirePass server
FirePass™ Server Administrator Guide 2 - 5
server
22 Local LAN 1025 to
65535
Yes Optional
Chapter 2
About the traffic between the FirePass server and network
services
The FirePass server needs access to the network services listed in Table 2.3,
some of which are optional and depend on your particular configuration. If
the services are hosted across a firewall from the FirePass server, you must
open the firewall ports to allow the FirePass server to access these services.
Important
Configure your internal DNS server such that your FirePass server host
name resolves to the server’s local IP address. This is to ensure that traffic
from the same side of the firewall can reach the FirePass server. You can do
this on a WINS server or on a DNS server if the DNS server is hosted
locally. (See Understanding name resolution issues for FirePass servers
with a private IP address, on page 2-11.)
Source Destination
Traffic Type Protocol
DNS TCP Local LAN 1025 to
DNS (response) TCP FirePass
server
NTP UDP Local LAN 1025 to
NTP (response) UDP FirePass
SSH TCP Local LAN 1025 to
SSH (response) TCP FirePass
SecurID
authentication
SecurID
authentication
(response)
TCP FirePass
TCP Local LAN 1645, 1646 FirePass
server
server
server
65535
53 Local LAN 1025 to
65535
123 Local LAN 1025 to
65535
22 Local LAN 1025 to
1025 to
65535
FirePass
server
FirePass
server
FirePass
server
Local LAN 1645,
server
53
65535
123
65535
22 Optional
65535
1646
1025 to
65535
Ack
bit
Yes
Yes Optional
Yes Optional
CommentAddress Ports Address Ports
Optional
LDAP TCP FirePass
LDAP (Response) TCP Local LAN 389, 636 FirePass
Table 2.3 Traffic between FirePass server and network services
2 - 6
server
1025 to
65535
FirePass
server
server
389,
636
1025 to
65535
Required for
LDAP
authentication
Yes Required for
LDAP
authentication
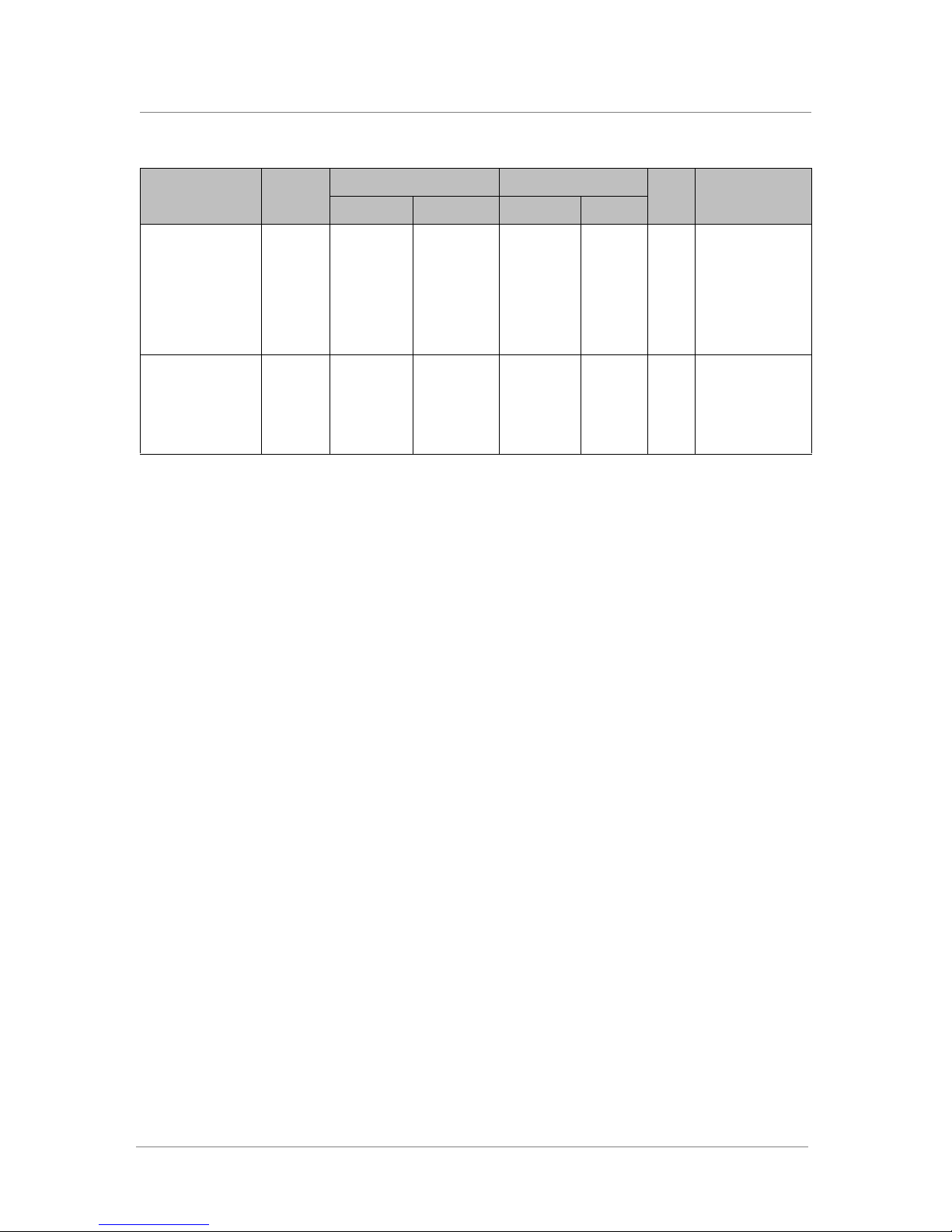
Deploying the FirePass Server
Traffic Type Protocol
RADIUS TCP FirePass
server
RADIUS
(response)
SMTP Services TCP FirePass
SMTP Services
(response)
TCP Local LAN 1645, 1646 FirePass
server
TCP Local LAN 25 FirePass
Source Destination
1025 to
65535
1025 to
65535
Local LAN 1645,
1646
1025 to
server
Local LAN 25
server
65535
1025 to
65535
Ack
bit
Yes Required for
Yes
CommentAddress Ports Address Ports
Required for
RADIUS
authentication
RADIUS
authentication
Table 2.3 Traffic between FirePass server and network services (Continued)
About the traffic between FirePass server and application services
To allow traffic between the FirePass server and application services on the
corporate LAN, you must open the firewall ports as shown in Table 2.4. The
application services include the following services, some of which are
optional and depend on your particular configuration:
• File servers
•Email servers
• Intranet
• Terminal servers
• Legacy mainframe and AS/400 applications
• Client/server applications
•SSL VPN
FirePass™ Server Administrator Guide 2 - 7
A FirePass server that needs to use any of these application services must be
able to communicate with the local LAN on several ports. Most of these
ports are listed in Table 2.4 with the default port assignments. (Your
network may vary). Microsoft Networking requires four ports, two TCP/IP
ports and two UDP ports. Port 135 is the RPC port, port 139 is the NetBIOS
session, port 137 is the NetBIOS name service, and port 138 is the datagram.
These ports must be configured to allow users to use the My Files Webifyer
to view network file shares. A WINS server helps address resolution from
NetBIOS to TCP/IP to work properly.
Chapter 2
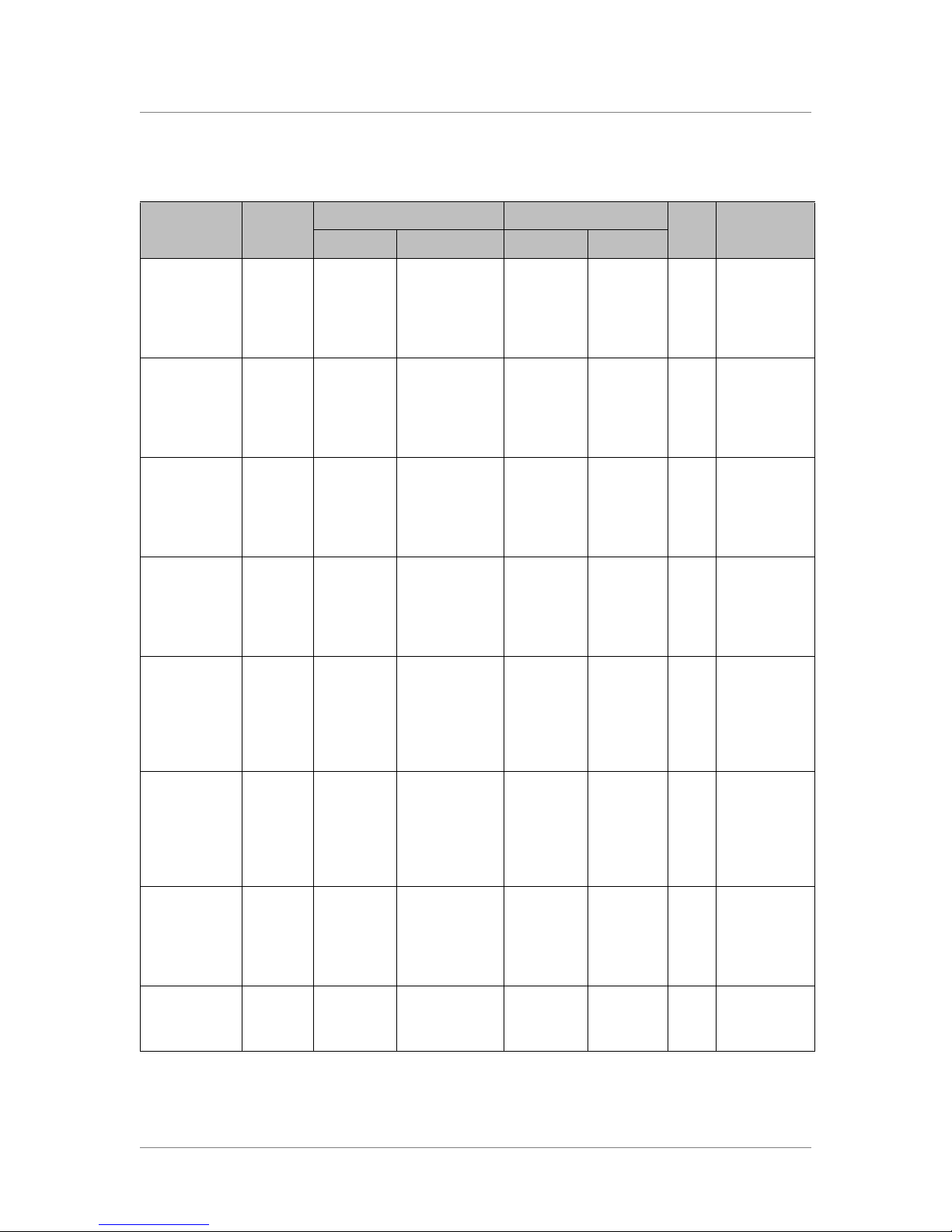
Source Destination
Traffic Type Protocol
HTTP TCP Local LAN 1025 to 65535 FirePass
server
HTTP
(response)
HTTPS TCP Local LAN 1025 to 65535 FirePass
HTTPS
(response)
IMAP TCP FirePass
IMAP
(Response)
POP TCP FirePass
POP
(Response)
TCP FirePass
server
TCP FirePass
server
server
TCP Local LAN 143 FirePass
server
TCP Local LAN 110 FirePass
80 Local LAN 1025 to
server
443 Local LAN 1025 to
1025 to 65535 Local LAN 143 Required for
server
1025 to 65535 Local LAN 110 Required for
server
Ack
bit
80 Required
Yes Required
65535
443
Yes
65535
1025 to
65535
1025 to
65535
Yes Required for
Yes Required for
CommentAddress Ports Address Ports
email
email
email
email
Microsoft
Networking
Microsoft
Networking
(Response)
Microsoft
Networking
Microsoft
Networking
(Response)
Telnet/3270 TCP FirePass
Telnet/3270
(Response)
Client/Server
applications
TCP FirePass
server
TCP Local LAN 135, 139 FirePass
UDP FirePass
server
UDP Local LAN 137, 138 FirePass
server
TCP Local LAN 23 FirePass
TCP FirePass
server
1025 to 65535 Local LAN 135, 139 Required for
server
1025 to 65535 Local LAN 137, 138 Required for
server
1025 to 65535 Local LAN 23 Required for
server
1025 to 65535 Local LAN User-defin
Table 2.4 Traffic between FirePass server and application services
1025 to
65535
1025 to
65535
1025 to
65535
ed TCP
File services
Yes Required for
File services
File services
Yes Required for
File services
Host Access
Yes Required for
Host Access
Required for
each App
tunnel
2 - 8
Deploying the FirePass Server
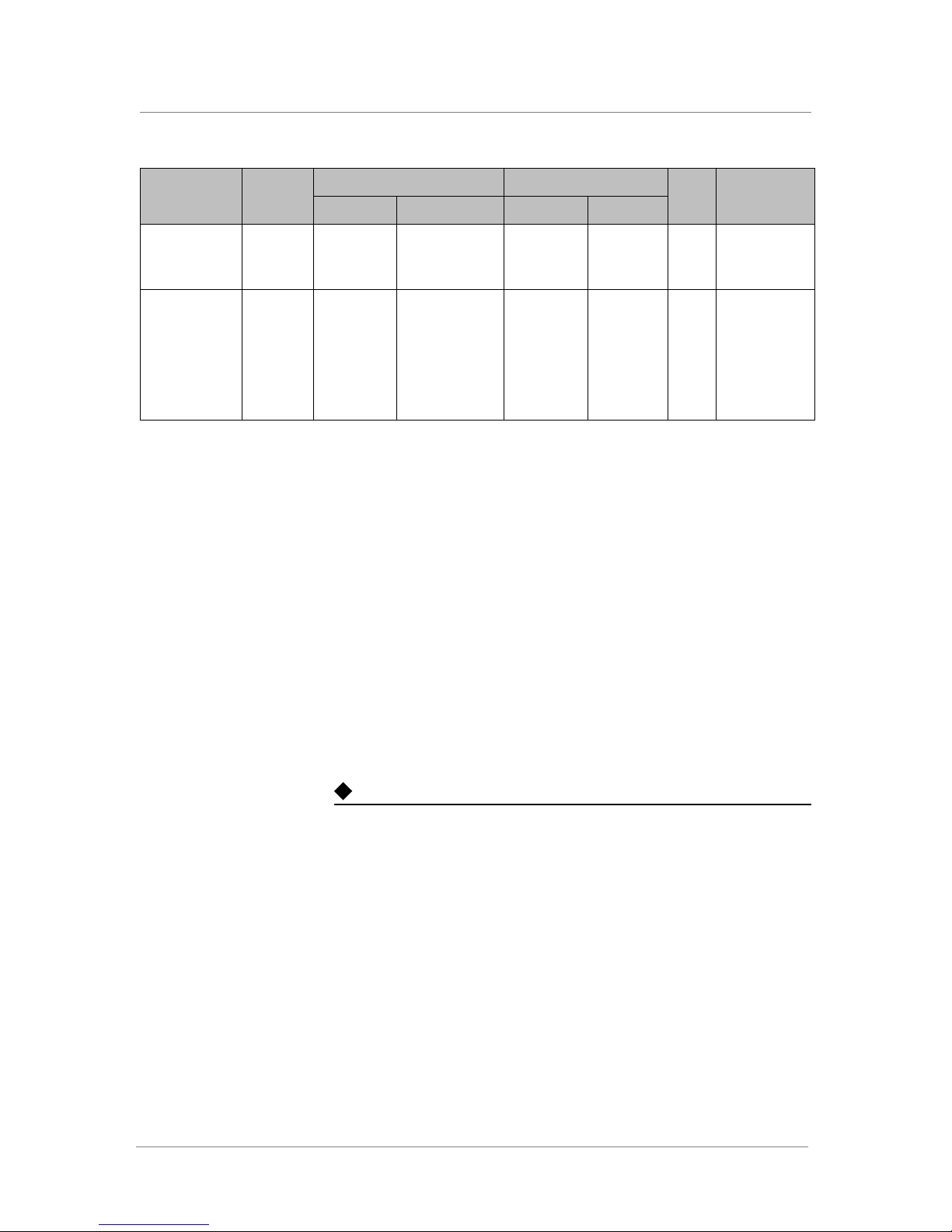
Traffic Type Protocol
Client/Server
applications
(response)
SSL VPN
Connector
SSL VPN
Connector
(response)
TCP Local LAN User-defined
TCP
UDP
ICMP
TCP
UDP
ICMP
Source Destination
TCP
FirePass
server
Local LAN Any ports as
1025 to 65535 Local LAN Any ports
needed
FirePass
server
FirePass
server
1025 to
65535
as needed
1025 to
65535
Ack
bit
Yes Required for
Yes Required for
CommentAddress Ports Address Ports
each App
tunnel
Required for
SSL VPN as
needed
SSL VPN as
needed
Table 2.4 Traffic between FirePass server and application services (Continued)
About the traffic between the FirePass server and the Desktop
Agent
To allow traffic from the FirePass server to the corporate LAN using the My
Desktop feature, you must open firewall ports as shown in Table 2.5.
The FirePass client on the desktop computer on the local LAN uses ports 80
and 81 to initiate communications with the FirePass server during My
Desktop sessions. The FirePass server “wakes” the client on port 661, then
communicates with it on port 443. The client then initiates a new connection
on port 81 back to the FirePass server.
Host Activation Protocol (HAP) is a registered port (661) which allows the
FirePass server to initiate a session with the FirePass Desktop Agent. The
FirePass server communicates with the Agent on port 443.
Note
The port numbers in the following table are default values which you can
change. For more information, see Configuring the My Desktop Webifyer,
on page 4-31.
FirePass™ Server Administrator Guide 2 - 9
Chapter 2
Source Destination
Traffic Type Protocol
HTTP TCP Local LAN 1025 to 65535 FirePass
server
HTTP
(response)
Host Activation
Protocol (HAP)
Host Activation
Protocol (HAP)
(response)
HTTPS TCP FirePass
HTTPS
(response)
TCP FirePass
server
TCP FirePass
server
TCP Local LAN 661 FirePass
server
TCP Local LAN 443 FirePass
80, 81 Local LAN 1025 to
1025 to 65535 Local LAN 661 Required for My
server
1025 to 65535 Local LAN 443
server
80, 81 Required for My
65535
1025 to
65535
1025 to
65535
Table 2.5 Traffic between FirePass server and corporate LAN using My Desktop
Ack
bit
Yes Required for My
Yes Required for My
Yes
CommentAddress Ports Address Ports
Desktop
Desktop
Desktop
Desktop
2 - 10
 Loading...
Loading...