Extreme Networks Sentriant AG, Sentriant AG 5.2 Software User's Manual

Sentriant AG Software Users Guide, Version 5.2
Extreme Networks, Inc.
3585 Monroe Street
Santa Clara, California 95051
(888) 257-3000
(408) 579-2800
http://www.extremenetworks.com
Published: January 2009
Part number: 120502-00 Rev 01

AccessAdapt, Alpine, Altitude, BlackDiamond, EPICenter, Essentials, Ethernet Everywhere, Extreme Enabled,
Extreme Ethernet Everywhere, Extreme Networks, Extreme Standby Router Protocol, Extreme Turbodrive,
Extreme Velocity, ExtremeWare, ExtremeWorks, ExtremeXOS, Go Purple Extreme Solution, ScreenPlay, Sentriant,
ServiceWatch, Summit, SummitStack, Triumph, Unified Access Architecture, Unified Access RF Manager,
UniStack, the Extreme Networks logo, the Alpine logo, the BlackDiamond logo, the Extreme Turbodrive logo, the
Summit logos, and the Powered by ExtremeXOS logo are trademarks or registered trademarks of Extreme
Networks, Inc. or its subsidiaries in the United States and/or other countries.
sFlow is a registered trademark of InMon Corporation.
Specifications are subject to change without notice.
All other registered trademarks, trademarks, and service marks are property of their respective owners.
© 2009 Extreme Networks, Inc. All Rights Reserved.

Table of Contents
List of Figures ............................................................................................................................... 15
List of Tables ................................................................................................................................ 21
Chapter 1: Introduction.................................................................................................................. 23
Sentriant AG Home Window .......................................................................................................23
System Monitor.........................................................................................................................24
Sentriant AG v5.2 for v4.x Users ................................................................................................26
Overview ..................................................................................................................................29
The Sentriant AG Process.....................................................................................................31
About Sentriant AG .............................................................................................................31
NAC Policy Definition ....................................................................................................31
Endpoint Testing...........................................................................................................31
Compliance Enforcement ...............................................................................................32
Automated and Manual Repair........................................................................................32
Targeted Reporting ........................................................................................................33
Technical Support.....................................................................................................................33
Additional Documentation..........................................................................................................33
Installing and Upgrading............................................................................................................34
Conventions Used in This Document ...........................................................................................34
Navigation Paragraph...........................................................................................................34
Note Paragraph ...................................................................................................................34
Caution Paragraph...............................................................................................................34
Warning Paragraph ..............................................................................................................35
Bold Font ...........................................................................................................................35
Task Paragraph ...................................................................................................................35
Italic Text...........................................................................................................................35
Courier Font .......................................................................................................................36
Angled Brackets..................................................................................................................36
Square Brackets..................................................................................................................36
Terms ................................................................................................................................37
Copying Files ............................................................................................................................37
SCP ...................................................................................................................................37
PSCP .................................................................................................................................37
Users’ guide online help ............................................................................................................38
Chapter 2: Clusters and Servers ..................................................................................................... 43
Single-server Installation......................................................................................................44
Multiple-server Installations .................................................................................................44
Chapter 3: System Configuration .................................................................................................... 47
Introduction .............................................................................................................................47
Enforcement Clusters and Servers...............................................................................................48
Enforcement Clusters ................................................................................................................49
Sentriant AG Software Users Guide, Version 5.2
3

Adding an Enforcement Cluster ............................................................................................49
Editing Enforcement Clusters ...............................................................................................51
Viewing Enforcement Cluster Status......................................................................................51
Deleting Enforcement Clusters..............................................................................................52
Enforcement Servers .................................................................................................................53
Adding an ES......................................................................................................................53
Cluster and Server Icons ......................................................................................................54
Editing ESs ........................................................................................................................55
Changing the ES Network Settings........................................................................................56
Changing the ES Date and Time ...........................................................................................57
Modifying the ES SNMP Settings..........................................................................................58
Modifying the ES root Account Password ...............................................................................58
Viewing ES Status ...............................................................................................................58
Deleting ESs.......................................................................................................................59
ES Recovery .......................................................................................................................60
Management Server...................................................................................................................60
Viewing Network Settings.....................................................................................................60
Modifying MS Network Settings ............................................................................................62
Selecting a Proxy Server.......................................................................................................63
Setting the Date and Time ...................................................................................................63
Automatically Setting the Time.............................................................................................64
Manually Setting the Time ...................................................................................................64
Selecting the Time Zone ......................................................................................................65
Enabling SNMP ..................................................................................................................65
Modifying the MS root Account Password ..............................................................................66
Checking for Sentriant AG Upgrades .....................................................................................66
Changing the Sentriant AG Upgrade Timeout .........................................................................67
User Accounts ..........................................................................................................................67
Adding a User Account ........................................................................................................67
Searching for a User Account ...............................................................................................70
Sorting the User Account Area..............................................................................................71
Copying a User Account .......................................................................................................71
Editing a User Account ........................................................................................................72
Deleting a User Account ......................................................................................................73
User Roles................................................................................................................................74
Adding a User Role .............................................................................................................74
Editing User Roles ..............................................................................................................77
Deleting User Roles.............................................................................................................78
Sorting the User Roles Area..................................................................................................78
License ....................................................................................................................................78
Updating Your License Key ..................................................................................................78
Test Updates ............................................................................................................................79
Manually Checking for Test Updates .....................................................................................80
Selecting Test Update Times................................................................................................81
Viewing Test Update Logs ....................................................................................................81
Quarantining, General................................................................................................................82
Selecting the Quarantine Method..........................................................................................83
Selecting the Access Mode...................................................................................................84
Quarantining, 802.1X................................................................................................................84
Entering Basic 802.1X Settings............................................................................................85
Authentication Settings .......................................................................................................85
4
Sentriant AG Software Users Guide, Version 5.2

Selecting the RADIUS Authentication method..................................................................85
Configuring Windows Domain Settings.............................................................................86
Configuring OpenLDAP Settings......................................................................................88
Adding 802.1X Devices .......................................................................................................91
Testing the Connection to a Device .......................................................................................92
Cisco IOS ...........................................................................................................................93
Cisco CatOS .......................................................................................................................95
CatOS User Name in Enable Mode..................................................................................97
Enterasys ...........................................................................................................................98
Extreme ExtremeWare..........................................................................................................99
Extreme XOS ....................................................................................................................101
Foundry............................................................................................................................102
HP ProCurve Switch ..........................................................................................................104
HP ProCurve WESM xl or HP ProCurve WESM zl ..................................................................107
HP ProCurve 420 AP or HP ProCurve 530 AP ......................................................................110
Nortel ..............................................................................................................................112
Other ...............................................................................................................................113
Quarantining, DHCP ................................................................................................................115
DHCP Server Configuration ................................................................................................115
Setting DHCP Enforcement ................................................................................................115
Adding a DHCP Quarantine Area.........................................................................................117
Sorting the DHCP Quarantine Area......................................................................................119
Editing a DHCP Quarantine Area.........................................................................................119
Deleting a DHCP Quarantine Area .......................................................................................120
Quarantining, Inline ................................................................................................................120
Post-connect ..........................................................................................................................120
Allowing the Post-connect Service Through the Firewall ........................................................120
First Time Selection ..........................................................................................................121
Setting Sentriant AG Properties ..........................................................................................121
Configuring a Post-connect System .....................................................................................121
Launching Post-connect Systems........................................................................................123
Post-connect in the Endpoint Activity Window......................................................................123
Adding Post-connect System Logos and Icons ......................................................................124
Maintenance...........................................................................................................................125
Initiating a New Backup.....................................................................................................126
Restoring From a Backup ...................................................................................................127
Downloading Support Packages ................................................................................................127
Cluster Setting Defaults ...........................................................................................................127
Testing Methods ...............................................................................................................128
Selecting Test Methods................................................................................................128
Ordering Test Methods.................................................................................................129
Recommended Test Methods........................................................................................129
Selecting End-user Options ................................................................................................130
Accessible Services ...........................................................................................................130
Exceptions........................................................................................................................132
Always Granting Access to Endpoints and Domains.........................................................132
Always Quarantine Endpoints and Domains....................................................................134
Notifications.....................................................................................................................134
Enabling Notifications .................................................................................................134
End-user Screens ..............................................................................................................136
Specifying an End-user Screen Logo .............................................................................136
Specifying the End-user Screen Text .............................................................................137
Sentriant AG Software Users Guide, Version 5.2
5

Specifying the End-user Test Failed Pop-up Window.......................................................138
Agentless Credentials ........................................................................................................139
Adding Windows Credentials.........................................................................................139
Testing Windows Credentials ........................................................................................140
Editing Windows Credentials ........................................................................................141
Deleting Windows Credentials.......................................................................................141
Sorting the Windows Credentials Area ...........................................................................142
Logging..................................................................................................................................142
Setting ES Logging Levels..................................................................................................142
Setting 802.1X Devices Logging Levels ...............................................................................144
Advanced Settings ..................................................................................................................144
Setting the Agent Read Timeout .........................................................................................144
Setting the RPC Command Timeout ....................................................................................145
Chapter 4: Endpoint Activity......................................................................................................... 147
Filtering the Endpoint Activity Window ......................................................................................148
Filtering by Access Control or Test Status ............................................................................148
Filtering by Time...............................................................................................................149
Limiting Number of Endpoints Displayed.............................................................................150
Searching.........................................................................................................................150
Access Control States ..............................................................................................................151
Endpoint Test Status ...............................................................................................................152
Enforcement Cluster Access Mode ............................................................................................155
Viewing Endpoint Access Status ...............................................................................................156
Selecting Endpoints to Act on ..................................................................................................157
Acting on Selected Endpoints...................................................................................................158
Manually Retest an Endpoint..............................................................................................158
Immediately Grant Access to an Endpoint............................................................................158
Immediately Quarantine an Endpoint ..................................................................................159
Clearing Temporary Endpoint States....................................................................................159
Viewing Endpoint Information...................................................................................................160
Troubleshooting Quarantined Endpoints ....................................................................................162
Chapter 5: End-user Access ......................................................................................................... 167
Test Methods Used .................................................................................................................167
Agent Callback..................................................................................................................167
Endpoints Supported...............................................................................................................168
Browser Version ......................................................................................................................169
Firewall Settings .....................................................................................................................170
Managed Endpoints...........................................................................................................170
Unmanaged Endpoints.......................................................................................................170
Making Changes to the Firewall ..........................................................................................170
Windows Endpoint Settings......................................................................................................170
IE Internet Security Setting................................................................................................170
Agent-based Test Method...................................................................................................171
Ports Used for Testing .................................................................................................171
Windows Vista Settings ................................................................................................171
Agentless Test Method.......................................................................................................171
Configuring Windows 2000 Professional for Agentless Testing .........................................171
Configuring Windows XP Professional for Agentless Testing .............................................172
6
Sentriant AG Software Users Guide, Version 5.2

Configuring Windows Vista for Agentless Testing ............................................................173
Defining the Agentless Group Policy Object....................................................................174
Ports Used for Testing .................................................................................................182
Allowing the Windows RPC Service through the Firewall..................................................182
ActiveX Test Method..........................................................................................................184
Ports Used for Testing .................................................................................................184
Windows Vista Settings ................................................................................................184
Mac OS X Endpoint Settings ....................................................................................................184
Ports Used for Testing .......................................................................................................184
Allowing Sentriant AG through the OS X Firewall ..................................................................184
End-user Access Windows........................................................................................................187
Opening Window ...............................................................................................................188
Windows NAC Agent Test Windows .....................................................................................189
Automatically Installing the Windows Agent ...................................................................189
Removing the Agent ....................................................................................................191
Manually Installing the Windows Agent..........................................................................192
How to View the Windows Agent Version Installed...........................................................193
Mac OS Agent Test Windows ..............................................................................................194
Installing the MAC OS Agent ........................................................................................194
Verifying the Mac OS Agent..........................................................................................197
Removing the Mac OS Agent ........................................................................................200
ActiveX Test Windows ........................................................................................................201
Agentless Test Windows.....................................................................................................202
Testing Window.................................................................................................................204
Test Successful Window ....................................................................................................204
Testing Cancelled Window..................................................................................................205
Testing Failed Window.......................................................................................................205
Error Windows...................................................................................................................207
Customizing Error Messages .....................................................................................................207
Chapter 6: NAC Policies .............................................................................................................. 215
Standard NAC Policies.............................................................................................................216
NAC Policy Group Tasks ..........................................................................................................216
Add a NAC Policy Group ....................................................................................................216
Editing a NAC Policy Group................................................................................................217
Deleting a NAC Policy Group ..............................................................................................218
NAC Policy Tasks ....................................................................................................................219
Enabling or Disabling an NAC Policy ...................................................................................219
Selecting the Default NAC Policy ........................................................................................219
Creating a New NAC Policy ................................................................................................219
Editing a NAC Policy .........................................................................................................225
Copying a NAC Policy ........................................................................................................225
Deleting a NAC Policy........................................................................................................226
Moving a NAC Policy Between NAC Policy Groups ................................................................226
Assigning Endpoints and Domains to a Policy ......................................................................226
NAC Policy Hierarchy ........................................................................................................227
Setting Retest Time...........................................................................................................227
Setting Connection Time....................................................................................................227
Defining Non-supported OS Access Settings ........................................................................228
Setting Test Properties ......................................................................................................228
Selecting Action Taken ......................................................................................................228
About Sentriant AG Tests.........................................................................................................230
Sentriant AG Software Users Guide, Version 5.2
7

Viewing Information About Tests.........................................................................................230
Selecting Test Properties ...................................................................................................230
Entering Software Required/Not Allowed........................................................................230
Entering Service Names Required/Not Allowed...............................................................231
Entering the Browser Version Number ...........................................................................231
Test Icons ........................................................................................................................232
Chapter 7: Quarantined Networks .................................................................................................233
Endpoint Quarantine Precedence..............................................................................................233
Using Ports in Accessible Services and Endpoints ......................................................................234
Always Granting Access to an Endpoint .....................................................................................236
Always Quarantining an Endpoint..............................................................................................237
New Users..............................................................................................................................237
Shared Resources ...................................................................................................................238
Untestable Endpoints and DHCP Mode .....................................................................................238
Windows Domain Authentication and Quarantined Endpoints ......................................................239
Chapter 8: High Availability and Load Balancing ........................................................................... 241
High Availability......................................................................................................................241
Load Balancing.......................................................................................................................245
Chapter 9: Inline Quarantine Method ............................................................................................ 247
Chapter 10: DHCP Quarantine Method .......................................................................................... 249
Configuring Sentriant AG for DHCP ...........................................................................................250
Setting up a Quarantine Area..............................................................................................251
Router Configuration .........................................................................................................251
Configuring the Router ACLs ........................................................................................251
Configuring Windows Update Service for XP SP2..................................................................251
Chapter 11: 802.1X Quarantine Method........................................................................................ 253
About 802.1X.........................................................................................................................253
Sentriant AG and 802.1X.........................................................................................................254
Setting up the 802.1X Components ..........................................................................................258
Setting up the RADIUS Server ............................................................................................258
Using the Sentriant AG IAS Plug-in to the Microsoft IAS RADIUS Server ..........................258
Configuring the Microsoft IAS RADIUS Server ................................................................260
Proxying RADIUS Requests to an Existing RADIUS Server Using the Built-in Sentriant AG
RADIUS Server ...........................................................................................................281
Using the Built-in Sentriant AG RADIUS Server for Authentication...................................284
Enabling Sentriant AG for 802.1X.......................................................................................284
Sentriant AG User Interface Configuration .....................................................................284
Setting up the Supplicant ..................................................................................................285
Windows XP Professional Setup ....................................................................................286
Windows XP Home Setup .............................................................................................287
Windows 2000 Professional Setup................................................................................288
Windows Vista Setup ...................................................................................................290
Setting up the Authenticator ..............................................................................................292
Cisco® 2950 IOS........................................................................................................293
Cisco® 4006 CatOS ....................................................................................................293
8
Sentriant AG Software Users Guide, Version 5.2

Enterasys® Matrix 1H582-25 ......................................................................................294
Extreme® Summit 48si ...............................................................................................294
ExtremeWare ..............................................................................................................295
ExtremeXOS................................................................................................................296
Foundry® FastIron® Edge 2402...................................................................................296
HP ProCurve 420AP ....................................................................................................297
HP ProCurve 530AP ....................................................................................................297
HP ProCurve 3400/3500/5400 ....................................................................................299
Nortel® 5510.............................................................................................................299
Creating Custom Expect Scripts ....................................................................................300
Chapter 12: API........................................................................................................................... 305
Overview ................................................................................................................................305
Setting Sentriant AG Properties ................................................................................................306
Setting Firewall Rules..............................................................................................................307
Sentriant AG Events Generated.................................................................................................307
Examples of Events Generated............................................................................................308
Java Program and Command for Events ...............................................................................310
Sentriant AG Requests Supported.............................................................................................310
Examples of Requests........................................................................................................311
Post-connect Request Example...........................................................................................313
Java Program and Command for Requests ...........................................................................314
Chapter 13: Remote Device Activity Capture ................................................................................. 315
Creating a DAC Host................................................................................................................315
Downloading the EXE File ..................................................................................................316
Running the Windows Installer ...........................................................................................316
Adding Additional Interfaces ..............................................................................................323
Configuring the MS and ES for DAC ....................................................................................324
Adding Additional ESs .......................................................................................................324
Starting the Windows Service .............................................................................................325
Viewing Version Information ...............................................................................................326
Removing the Software ......................................................................................................326
Sentriant AG to Infoblox Connector ...........................................................................................328
Configuring the Infoblox Server...........................................................................................328
Configuring Sentriant AG ...................................................................................................328
Chapter 14: Reports .................................................................................................................... 331
Generating Reports..................................................................................................................332
Viewing Report Details.............................................................................................................334
Printing Reports......................................................................................................................336
Saving Reports to a File ...........................................................................................................336
Converting an HTML Report to a Word Document .......................................................................336
Chapter 15: DHCP Plug-in............................................................................................................ 339
Installation Overview ...............................................................................................................340
DHCP Plug-in and the Sentriant AG User Interface.....................................................................342
Installing the Plug-in .........................................................................................................342
Enabling the Plug-in and Adding Servers .............................................................................345
Viewing DHCP Server Plug-in Status ...................................................................................347
Sentriant AG Software Users Guide, Version 5.2
9

Editing DHCP Server Plug-in Configurations.........................................................................348
Deleting a DHCP Server Plug-in Configuration......................................................................348
Disabling a DHCP Server Plug-in Configuration ....................................................................349
Enabling a DHCP Server Plug-in Configuration .....................................................................349
Chapter 16: System Administration...............................................................................................351
Launching Sentriant AG...........................................................................................................351
Launching and Logging into Sentriant AG ............................................................................351
Logging out of Sentriant AG ...............................................................................................351
Important Browser Settings ................................................................................................351
Restarting Sentriant AG System Processes.................................................................................351
Managing your Sentriant AG License.........................................................................................352
Entering a New License Key ...............................................................................................352
Downloading New Tests ...........................................................................................................353
System Settings ......................................................................................................................354
DNS/Windows Domain Authentication and Quarantined Endpoints .........................................354
Matching Windows Domain Policies to NAC Policies .............................................................355
Setting the Access Mode....................................................................................................355
Naming Your Enforcement Cluster ......................................................................................356
Changing the MS Host Name..............................................................................................356
Changing the ES Host Name ..............................................................................................356
Changing the MS or ES IP Address .....................................................................................356
Resetting your System .......................................................................................................357
Resetting your Test Data ....................................................................................................358
Changing Properties ..........................................................................................................359
Specifying an Email Server for Sending Notifications............................................................360
Entering Networks Using CIDR Format ......................................................................................360
Database................................................................................................................................361
Creating a Backup File.......................................................................................................361
Changing the Backup Timeouts ..........................................................................................361
Restoring from Backup ......................................................................................................362
Restoring to a new Server.............................................................................................362
Restoring to the Same Server .......................................................................................362
Restoring the Original Database..........................................................................................363
Generating a Support Package............................................................................................364
System Requirements..............................................................................................................364
Supported VPNs......................................................................................................................365
Adding Custom Tests...............................................................................................................366
Introduction......................................................................................................................366
References .......................................................................................................................366
Changing the Error Messages in a Test Script.......................................................................366
Creating a Custom Test Class Script from Scratch ................................................................370
BasicTests API..................................................................................................................378
End-user Access Windows........................................................................................................386
How Sentriant AG Handles Static IP Addresses ..........................................................................387
Managing Passwords ...............................................................................................................388
Resetting the Sentriant AG Server Password.........................................................................389
Resetting the Sentriant AG Database Password ....................................................................390
Changing the Sentriant AG Administrator Password ..............................................................390
When the Password is Known .......................................................................................390
10
Sentriant AG Software Users Guide, Version 5.2

When the Password is Unknown....................................................................................390
NTLM 2 Authentication ...........................................................................................................391
Working with Ranges ...............................................................................................................391
Creating and Replacing SSL Certificates....................................................................................393
Creating a New Self-signed Certificate.................................................................................393
Using an SSL Certificate from a known Certificate Authority (CA)...........................................395
Moving an ES from One MS to Another......................................................................................396
Recovering Quickly from a Network Failure ................................................................................397
VLAN Tagging.........................................................................................................................398
iptables Wrapper Script ...........................................................................................................399
Updating Rules without an Internet Connection .........................................................................400
Downloading the Files........................................................................................................400
Updating Rules .................................................................................................................401
Supporting Network Management System ..................................................................................401
Enabling ICMP Echo Requests ...........................................................................................401
Enable Temporary Ping ................................................................................................401
Enable Persistent Ping.................................................................................................402
Restricting the ICMP Request.......................................................................................402
Changing the Community Name for SNMPD.........................................................................403
SNMP MIBs......................................................................................................................404
Chapter 17: Patch Management ................................................................................................... 407
Flagging a Test to Launch a Patch Manager ...............................................................................407
Selecting the Patch Manager....................................................................................................408
Specifying the Number of Retests.............................................................................................408
Specifying the Retest Frequency...............................................................................................408
SMS Patch Management..........................................................................................................409
SMS Concepts ........................................................................................................................409
Sentriant AG/SMS/Sentriant AG Process....................................................................................409
Sentriant AG Setup .................................................................................................................410
Learning More About SMS .......................................................................................................410
Appendix A: Requirements ........................................................................................................... 411
Appendix B: Configuring the Post-connect Server.......................................................................... 413
Overview ................................................................................................................................413
Extracting the ZIP File.............................................................................................................413
Windows...........................................................................................................................413
Linux ...............................................................................................................................414
ZIP File Contents ....................................................................................................................414
Setting up a Post-connect Host ................................................................................................415
Windows...........................................................................................................................415
Linux ...............................................................................................................................416
Viewing Logs ..........................................................................................................................418
Testing the Service..................................................................................................................418
Windows.......................................................................................................................................................418
Linux ............................................................................................................................................................418
Configuring Your Sensor...........................................................................................................419
Sentriant AG Software Users Guide, Version 5.2
11

Allowing Sentriant AG Through the Firewall ...............................................................................419
Appendix C: Tests Help................................................................................................................ 421
Browser Security Policy—Windows............................................................................................421
Browser Version ................................................................................................................423
Internet Explorer (IE) Internet Security Zone ........................................................................423
Internet Explorer (IE) Local Intranet Security Zone ...............................................................424
Internet Explorer (IE) Restricted Site Security Zone ..............................................................424
Internet Explorer (IE) Trusted Sites Security Zone ................................................................425
Operating System—Windows ....................................................................................................426
IIS Hotfixes ......................................................................................................................426
Internet Explorer Hotfixes ..................................................................................................427
Microsoft Office Hotfixes....................................................................................................427
Microsoft Applications Hotfixes ..........................................................................................428
Microsoft Servers Hotfixes..................................................................................................428
Microsoft Tools Hotfixes.....................................................................................................428
Service Packs ...................................................................................................................429
Windows 2000 SP4 Hotfixes..............................................................................................429
Windows 2003 SP1 Hotfixes..............................................................................................429
Windows 2003 SP2 Hotfixes..............................................................................................430
Windows Automatic Updates ..............................................................................................430
Windows Media Player Hotfixes ..........................................................................................431
Windows Vista™ SP0 Hotfixes ...........................................................................................431
Windows XP SP1 Hotfixes .................................................................................................432
Windows XP SP2 Hotfixes .................................................................................................432
Security Settings—OS X ..........................................................................................................433
Mac AirPort WEP Enabled..................................................................................................433
Mac AirPort Preference ......................................................................................................433
Mac AirPort User Prompt ...................................................................................................433
Mac Anti-virus ..................................................................................................................434
Mac Bluetooth ..................................................................................................................434
Mac Firewall .....................................................................................................................434
Mac Internet Sharing.........................................................................................................435
Mac QuickTime® Updates .................................................................................................435
Mac Security Updates........................................................................................................436
Mac Services ....................................................................................................................436
Security Settings—Windows.....................................................................................................436
Allowed Networks..............................................................................................................437
Microsoft Excel Macros ......................................................................................................437
Microsoft Outlook Macros...................................................................................................438
Microsoft Word Macros ......................................................................................................438
Services Not Allowed .........................................................................................................439
Services Required .............................................................................................................440
Windows Bridge Network Connection...................................................................................441
Windows Wireless Network SSID Connections ......................................................................441
Windows Security Policy ....................................................................................................441
Windows Startup Registry Entries Allowed ...........................................................................442
Wireless Network Connections ............................................................................................443
Software—Windows.................................................................................................................444
Anti-spyware.....................................................................................................................444
Anti-virus .........................................................................................................................444
High-risk Software.............................................................................................................445
12
Sentriant AG Software Users Guide, Version 5.2

Microsoft Office Version Check ...........................................................................................445
P2P .................................................................................................................................445
Personal Firewalls .............................................................................................................446
Software Not Allowed ........................................................................................................446
Software Required.............................................................................................................447
Worms, Viruses, and Trojans ..............................................................................................447
Appendix D: Database Design (Data Dictionary)............................................................................. 449
test_result table ......................................................................................................................450
Device table ...........................................................................................................................451
sa_cluster...............................................................................................................................453
sa_node .................................................................................................................................453
sa_user ..................................................................................................................................454
cluster_to_user .......................................................................................................................454
user_group .............................................................................................................................454
user_to_groups .......................................................................................................................455
group_to_permission ...............................................................................................................455
Appendix E: Ports used in Sentriant AG......................................................................................... 457
Appendix F: MS Disaster Recovery ............................................................................................... 463
Overview ................................................................................................................................463
Installation Requirements ..................................................................................................463
Installing the Standby MS..................................................................................................463
Ongoing Maintenance ........................................................................................................464
Failover process ................................................................................................................464
Appendix G: Licenses .................................................................................................................. 467
Extreme Networks End-User License Agreement.........................................................................467
Other Licenses........................................................................................................................469
Apache License Version 2.0, January 2004 .........................................................................470
ASM ................................................................................................................................471
Open SSH ........................................................................................................................472
Postgresql ........................................................................................................................474
Postgresql jdbc ................................................................................................................475
xstream ............................................................................................................................475
Libeay (Open SSL) ............................................................................................................475
Junit Common Public License - v 1.0 .................................................................................476
Open SSL.........................................................................................................................478
The GNU General Public License (GPL) Version 2, June 1991...............................................479
Pullparser ........................................................................................................................482
Xpp3................................................................................................................................482
The GNU Lesser General Public License (LGPL) Version 2.1 .................................................483
Ojdbc ..............................................................................................................................487
JavaMail Sun Microsystems, Inc. ........................................................................................489
jcharts .............................................................................................................................491
PyXML Python License (CNRI Python License).....................................................................491
IO-Stty and IO-Tty .............................................................................................................492
Concurrent .......................................................................................................................493
Crypto ++ .........................................................................................................................493
WinPcap...........................................................................................................................494
Sentriant AG Software Users Guide, Version 5.2
13

Activation.........................................................................................................................496
JAVA OPTIONAL PACKAGE ................................................................................................497
jsp-api package.................................................................................................................498
Appendix H: Glossary................................................................................................................... 503
Index .......................................................................................................................................... 513
14
Sentriant AG Software Users Guide, Version 5.2

List of Figures
Figure 1: Sentriant AG Home Window .....................................................................................24
Figure 2: System Monitor Window...........................................................................................25
Figure 3: System Monitor Window Legend ...............................................................................26
Figure 4: Online help.............................................................................................................39
Figure 5: Index tab ................................................................................................................40
Figure 6: Search tab..............................................................................................................41
Figure 7: Single-server Installation..........................................................................................44
Figure 8: Multiple-server Installation .......................................................................................45
Figure 9: Multiple-server, Multiple-cluster Installation ..............................................................46
Figure 10: System Configuration, Enforcement Clusters & Servers................................................49
Figure 11: Add Enforcement Cluster .........................................................................................50
Figure 12: Enforcement Cluster, General ...................................................................................52
Figure 13: System Configuration, Enforcement Clusters & Servers................................................53
Figure 14: Add Enforcement Server ..........................................................................................54
Figure 15: Enforcement Cluster Legend.....................................................................................55
Figure 16: Enforcement Server .................................................................................................56
Figure 17: Enforcement Server, Status ......................................................................................59
Figure 18: System Configuration, Management Server ................................................................61
Figure 19: Management Server Network Settings........................................................................62
Figure 20: Date & Time ...........................................................................................................64
Figure 21: System Configuration, User Accounts ........................................................................68
Figure 22: Add User Account ...................................................................................................69
Figure 23: Copy User Account ..................................................................................................72
Figure 24: User Account ..........................................................................................................73
Figure 25: System Configuration, User Roles .............................................................................75
Figure 26: Add User Role.........................................................................................................76
Figure 27: User Role ...............................................................................................................77
Figure 28: System Configuration, License..................................................................................79
Figure 29: System Configuration, Test Updates ..........................................................................80
Figure 30: Test Update Log......................................................................................................82
Figure 31: Test Update Log Window Legend ..............................................................................82
Figure 32: System Configuration, Quarantining ..........................................................................83
Figure 33: System Configuration, Windows Domain ....................................................................87
Figure 34: System Configuration, OpenLDAP .............................................................................89
Figure 35: Add 802.1X Device .................................................................................................91
Figure 36: Add 802.1X Device, Test Connection Area Option 1 ...................................................92
Figure 37: Add 802.1X Device, Test Connection Area Option 2 ...................................................92
Figure 38: Add Cisco IOS Device ..............................................................................................94
Figure 39: Add Cisco CatOS Device...........................................................................................96
Figure 40: Add Enterasys Device ..............................................................................................98
Figure 41: Add ExtremeWare Device .......................................................................................100
Sentriant AG Software Users Guide, Version 5.2
15

List of Figures
Figure 42: Add Extreme XOS Device .......................................................................................101
Figure 43: Add Foundry Device...............................................................................................103
Figure 44: Add HP ProCurve Device ........................................................................................105
Figure 45: Add HP ProCurve WESM xl/zl Device .......................................................................108
Figure 46: Add HP ProCurve 420/530 AP Device .....................................................................110
Figure 47: Add Nortel Device .................................................................................................112
Figure 48: Add Other Device ..................................................................................................114
Figure 49: System Configuration, Quarantining, DHCP Enforcement...........................................116
Figure 50: Add a Quarantine Area ...........................................................................................117
Figure 51: Quarantine Area ....................................................................................................119
Figure 52: Post-connect Configuration Message .......................................................................121
Figure 53: System Configuration, Post-connect ........................................................................122
Figure 54: Post-connect Launch Window .................................................................................123
Figure 55: Post-connect Quarantine Details .............................................................................124
Figure 56: System Configuration, Maintenance ........................................................................126
Figure 57: Backup Successful Message...................................................................................127
Figure 58: System Configuration, Testing Methods ...................................................................128
Figure 59: System Configuration, Accessible Services...............................................................131
Figure 60: System Configuration, Exceptions ...........................................................................133
Figure 61: System Configuration, Notifications.........................................................................135
Figure 62: System Configuration, End-user Screens..................................................................137
Figure 63: System Configuration, Agentless Credentials ............................................................139
Figure 64: Agentless Credentials, Add Windows Administrator Credentials ..................................140
Figure 65: System Configuration, Logging Option .....................................................................143
Figure 66: System Configuration, Advanced Option ..................................................................145
Figure 67: Endpoint Activity, All Endpoints Area ......................................................................147
Figure 68: Endpoint Activity, Menu Options.............................................................................149
Figure 69: Timeframe Drop-down List .....................................................................................150
Figure 70: Display Endpoints Drop-down .................................................................................150
Figure 71: Search Criteria ......................................................................................................151
Figure 72: Highlighted Fields .................................................................................................151
Figure 73: Endpoint Mouseover Pop-up Window .......................................................................153
Figure 74: Failed Endpoint.....................................................................................................155
Figure 75: Failed Endpoint Allow All Mode ..............................................................................156
Figure 76: Failed Endpoint Allow All Mode Mouse Over.............................................................156
Figure 77: Access Control and Endpoint Test Status.................................................................157
Figure 78: Endpoint, General Option .......................................................................................160
Figure 79: Endpoint Activity, Endpoint Test Results Option.......................................................161
Figure 80: Local Area Connection Properties............................................................................172
Figure 81: Local Area Connection Properties............................................................................173
Figure 82: Group Policy Management Window..........................................................................174
Figure 83: New GPO Window..................................................................................................175
Figure 84: Group Policy Object Editor .....................................................................................175
Figure 85: Network Access Window.........................................................................................176
Figure 86: Network Security Window.......................................................................................177
Figure 87: Network Connection Properties Window ...................................................................178
16
Sentriant AG Software Users Guide, Version 5.2

List of Figures
Figure 88: Remote Procedure Call Properties Window ...............................................................178
Figure 89: Remote Registry Properties Window ........................................................................179
Figure 90: Windows Firewall Window ......................................................................................180
Figure 91: Microsoft Peer-to-Peer Window ...............................................................................181
Figure 92: Double Arrow Icon .................................................................................................182
Figure 93: Mac System Preferences ........................................................................................185
Figure 94: Mac Sharing .........................................................................................................186
Figure 95: Mac Ports .............................................................................................................187
Figure 96: End-user Opening Window......................................................................................188
Figure 97: End-user Installing Window ....................................................................................189
Figure 98: End-user Agent Installation Failed...........................................................................190
Figure 99: End-user Agent Installation Window (Start) ..............................................................191
Figure 100: End-user Agent Installation Window (Finish) ............................................................191
Figure 101: Add/Remove Programs ...........................................................................................192
Figure 102: Security Certificate ................................................................................................193
Figure 103: Run or Save to Disk ...............................................................................................193
Figure 104: Start Mac OS Installer ...........................................................................................194
Figure 105: Mac OS Installer 1 of 5..........................................................................................195
Figure 106: Mac OS Installer 2 of 5..........................................................................................195
Figure 107: Mac OS Installer 3 of 5..........................................................................................196
Figure 108: Mac OS Installer 4 of 5..........................................................................................196
Figure 109: Mac OS Installer 5 of 5..........................................................................................197
Figure 110: Applications, Utilities Folder ..................................................................................198
Figure 111: Activity Monitor .....................................................................................................199
Figure 112: Mac Terminal........................................................................................................200
Figure 113: End-user ActiveX Plug-in Failed ..............................................................................201
Figure 114: End-user Login Credentials.....................................................................................202
Figure 115: End-user Login Failed ............................................................................................203
Figure 116: End-user Testing ...................................................................................................204
Figure 117: End-user Testing Successful...................................................................................204
Figure 118: End-user Testing Cancelled ....................................................................................205
Figure 119: End-user Testing Failed Example 1 .........................................................................206
Figure 120: End-user Testing Failed, Printable Results ...............................................................207
Figure 121: End-user Error.......................................................................................................207
Figure 122: NAC Policies .........................................................................................................215
Figure 123: NAC Policies Window Legend .................................................................................216
Figure 124: Add NAC Policy Group ...........................................................................................217
Figure 125: Edit NAC Policy Group ...........................................................................................218
Figure 126: Default NAC Policy ................................................................................................219
Figure 127: Add a NAC Policy, Basic Settings Area ....................................................................220
Figure 128: Add a NAC Policy, Domains and Endpoints ..............................................................222
Figure 129: Add NAC Policy, Tests Area ....................................................................................224
Figure 130: NAC Policy Test Icons............................................................................................232
Figure 131: System Configuration, Accessible Services ...............................................................235
Figure 132: System Configuration, Exceptions ...........................................................................236
Figure 133: Inline Installations.................................................................................................242
Sentriant AG Software Users Guide, Version 5.2
17

List of Figures
Figure 134: DHCP Installation..................................................................................................243
Figure 135: 802.1X Installation ...............................................................................................244
Figure 136: Inline Installations.................................................................................................248
Figure 137: DHCP Installation..................................................................................................250
Figure 138: 802.1X Components..............................................................................................254
Figure 139: Sentriant AG 802.1X Enforcement ..........................................................................256
Figure 140: 802.1X Communications........................................................................................257
Figure 141: Windows Components Wizard .................................................................................259
Figure 142: Networking Services ..............................................................................................259
Figure 143: IAS, Register Server in Active Directory ...................................................................260
Figure 144: IAS, Properties Option ...........................................................................................261
Figure 145: IAS, Properties ......................................................................................................261
Figure 146: IAS, New Client, Name and Address........................................................................262
Figure 147: IAS, New Client, Additional Information ..................................................................263
Figure 148: IAS, New Remote Access Policy..............................................................................264
Figure 149: IAS, Remote Access Policy, Access Method .............................................................264
Figure 150: IAS, Remote Access Policy, Group Access ...............................................................265
Figure 151: IAS, Remote Access Policy, Find Group ...................................................................265
Figure 152: Remote Access Policy, Select Group .......................................................................266
Figure 153: IAS, Remote Access Policy, Authentication Method ..................................................266
Figure 154: Error Message .......................................................................................................268
Figure 155: Protected EAP Properties .......................................................................................269
Figure 156: IAP, Remote Access Policy, Properties ....................................................................270
Figure 157: IAS, Remote Access Policy, Configure .....................................................................270
Figure 158: IAS, Remote Access Policy, Add Attribute................................................................271
Figure 159: IAS, Remote Access Logging Properties ...................................................................273
Figure 160: Sentriant AG-to-IAS Connector................................................................................274
Figure 161: IAS, Add/Remove Snap-in ......................................................................................275
Figure 162: IAS, Add/Remove Snap-in, Certificates....................................................................275
Figure 163: IAS, Import Certificate...........................................................................................276
Figure 164: Active Directory, Properties ....................................................................................278
Figure 165: Active Directory, Store Passwords............................................................................278
Figure 166: Active Directory Users and Computers .....................................................................280
Figure 167: Active Directory, User Account Properties ................................................................280
Figure 168: Enabling 802.1X in the User Interface ....................................................................285
Figure 169: Windows XP Pro Local Area Connection, General Tab ................................................286
Figure 170: Windows XP Pro Local Area Connection Properties, Authentication Tab ......................287
Figure 171: Windows 2000 Local Area Connection Properties, General Tab ..................................289
Figure 172: Windows 2000 Local Area Connection Properties, Authentication Tab ........................289
Figure 173: Wired AutoConfig Properties ...................................................................................290
Figure 174: Windows Vista Local Area Connection, Networking Tab .............................................291
Figure 175: Windows Vista Local Area Connection Properties, Authentication Tab .........................292
Figure 176: Nortel Initialization Script ......................................................................................300
Figure 177: Nortel Re-authentication Script ..............................................................................301
Figure 178: Nortel Exit Script ..................................................................................................301
Figure 179: Sentriant AG API Communication ...........................................................................306
18
Sentriant AG Software Users Guide, Version 5.2

List of Figures
Figure 180: The DAC InstallShield Wizard Welcome Window .......................................................317
Figure 181: RDAC Installer, Setup Type ....................................................................................317
Figure 182: RDAC Installer, Choose Destination Location............................................................318
Figure 183: RDAC Installer, Confirm New Folder ........................................................................318
Figure 184: RDAC Installer, Select Features ..............................................................................319
Figure 185: RDAC Installer, NIC Selection ................................................................................319
Figure 186: RDAC Installer, TCP Port Filter Specification ...........................................................320
Figure 187: RDAC Installer, Enforcement Server Specification ....................................................320
Figure 188: RDAC Installer, Ready to Install the Program ...........................................................321
Figure 189: RDAC Installer, InstallShield Wizard Complete .........................................................322
Figure 190: Example wrapper.conf File .....................................................................................323
Figure 191: NAC Endpoint Activity Capture Service ....................................................................326
Figure 192: RDAC Uninstall Complete ......................................................................................327
Figure 193: Reports ................................................................................................................333
Figure 194: NAC Policy Results Report .....................................................................................334
Figure 195: Test Details Report ................................................................................................335
Figure 196: DHCP Plug-in .......................................................................................................339
Figure 197: System Configuration, Quarantining, DHCP ..............................................................343
Figure 198: DHCP Plug-in InstallShield Wizard window ..............................................................344
Figure 199: DHCP Plug-in Customer Information window ............................................................344
Figure 200: DHCP Plug-in Ready to Install the Program window ..................................................345
Figure 201: DHCP Plug-in InstallShield Wizard Complete window................................................345
Figure 202: Add DHCP Plug-in Configuration.............................................................................346
Figure 203: DHCP Plug-in Server Added Example ......................................................................347
Figure 204: DHCP Plug-in Legend ............................................................................................347
Figure 205: DHCP Plug-in Configuration ...................................................................................348
Figure 206: Restore System .....................................................................................................363
Figure 207: Login ...................................................................................................................363
Figure 208: Test Script Code....................................................................................................367
Figure 209: Example InstallCustomTests Output ........................................................................369
Figure 210: testTemplate.py ....................................................................................................371
Figure 211: checkOpenPorts.py script .......................................................................................374
Figure 212: snmpd.conf Example File .......................................................................................403
Figure 213: Initiate a Patch Manager Check Box ........................................................................407
Figure 214: Microsoft Office Hotfixes Critical Updates................................................................427
Sentriant AG Software Users Guide, Version 5.2
19

List of Figures
20
Sentriant AG Software Users Guide, Version 5.2

List of Tables
Table 1: Sentriant AG v5.2 for v4.x Users...............................................................................26
Table 2: Test Methods ..........................................................................................................29
Table 3: Sentriant AG Technical Support................................................................................33
Table 4: Default Menu Options ..............................................................................................47
Table 5: Default User Roles ..................................................................................................70
Table 6: User Role Permissions .............................................................................................76
Table 7: Accessible Services and Endpoints Tips...................................................................132
Table 8: Troubleshooting Quarantined Endpoints...................................................................162
Table 9: Default Test Names and Descriptions ......................................................................209
Table 10: Expect Script Commands and Parameters ................................................................301
Table 11: Report Types and Fields.........................................................................................331
Table 12: DHCP Plug-in Configuration File Values...................................................................341
Table 13: Service Stop and Restart Commands .......................................................................352
Table 14: CIDR Naming Conventions .....................................................................................360
Table 15: Sentriant AG System Requirements.........................................................................364
Table 16: BasicTests API ......................................................................................................379
Table 17: Sentriant AG Passwords .........................................................................................388
Table 18: Browser Vulnerabilities...........................................................................................421
Table 19: Ports in Sentriant AG .............................................................................................457
Sentriant AG Software Users Guide, Version 5.2
21

List of Tables
22
Sentriant AG Software Users Guide, Version 5.2

1 Introduction
This chapter provides the following:
● A description of the Home window (“Sentriant AG Home Window” on page 23)
● A description of the System monitor window (“Sentriant AG Home Window” on page 23)
● A quick-reference for v4.1 users
(“Sentriant AG v5.2 for v4.x Users” on page 26)
● An overview of Sentriant AG and the key features
(“Overview” on page 29)
● How to get help (“Technical Support” on page 33)
● Other documents (“Additional Documentation” on page 33)
● Where to get installation and upgrading information (“Installing and Upgrading” on page 34)
● How to read this document (“Conventions Used in This Document” on page 34)
● How to copy files between systems (“Copying Files” on page 37)
Sentriant AG Home Window
The Sentriant AG Home window (Figure 1) is a centralized management user interface that allows you
to quickly assess the status of your network. The following list and figure describe and show the key
features:
1 Important status announcements—If there is anything that needs your immediate attention, a status
announcement is displayed at the top of the window. Click clear to remove the announcement.
2 My account—Click this icon to open the user account editing window. See “User Accounts” on page
67 for details on creating and editing user accounts. You must have administrator privileges to
create user accounts; however, any user can edit their own account.
3 Top 5 failed tests area—The Top 5 failed tests area indicates the tests that fail the most. Click on an
endpoint number or the Test results report option to view details.
4 Window actions—Use these buttons to refresh the window, log out of the user interface, and access
online help.
5 Navigation pane—The menu items shown in this pane vary depending on your permission level.
See “User Roles” on page 74 for more information on permissions. You must have administrator
privileges to create and edit user roles. Once you select a menu item from the navigation pane, use
the bread crumbs at the top of the windows to navigate throughout the user interface (see Figure 2.
System Monitor Window on page 25).
6 Endpoint test status area—The Endpoint tests area displays the total number of endpoints that
Sentriant AG has attempted to test, and what the test status is for each endpoint. Click the number
of endpoints to view details.
Sentriant AG Software Users Guide, Version 5.2
23
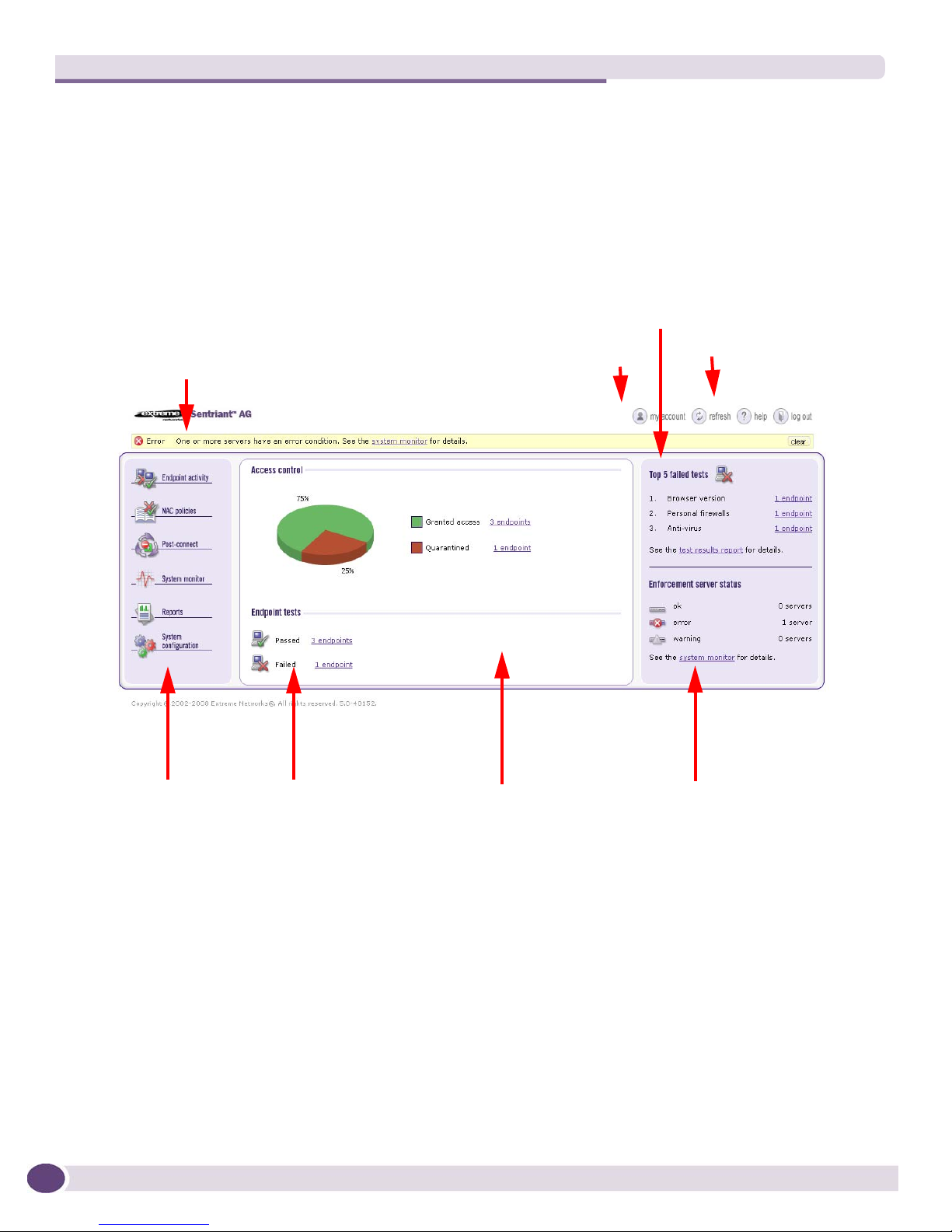
Introduction
7 Access control status area—The Access control area displays the total number of endpoints that
have attempted to connect to your network, and what the access state is as a percentage and as a
number. Click on the number of endpoints to view details.
8 Enforcement server (ES) status area—The Enforcement server status area provides status on your
ESs. Click the System monitor option to view details.
Figure 1: Sentriant AG Home Window
3. Top 5 failed
tests area
1. Important status
announcements
2. My account
4. Window actions
5. Navigation
pane
6. Test
status area
System Monitor
The System monitor window provides the following information:
● Enforcement cluster name—The Enforcement clusters are listed by name in the order they were
created. Click on a cluster name to view cluster details. You must have cluster-editing permissions to
view and edit cluster details.
24
7. Access control
status area
Sentriant AG Software Users Guide, Version 5.2
8. Enforcement server
status area
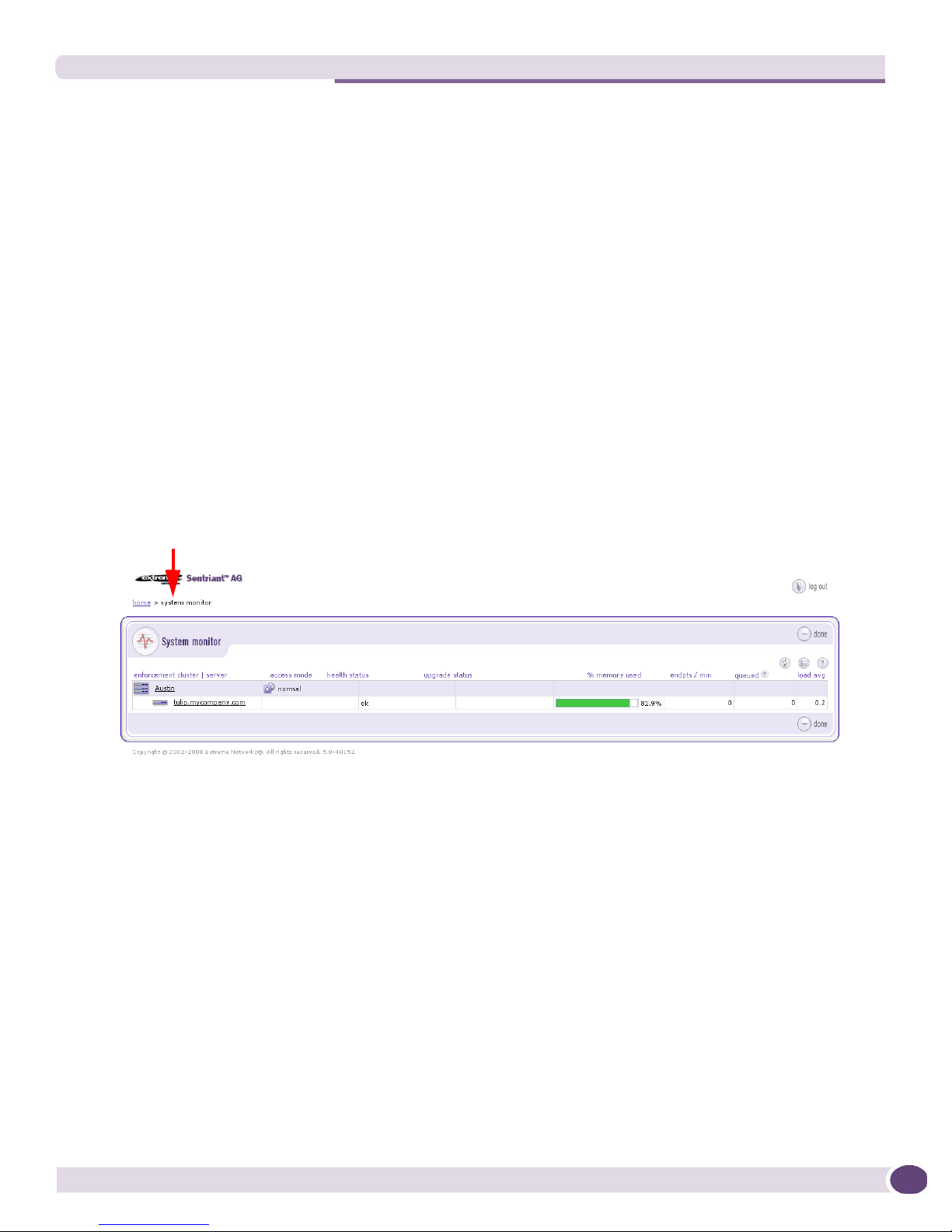
Introduction
● Server name by cluster—The servers for each cluster are listed by name in the order they were
created. Click on a server name to view server details. You must have cluster-editing permissions to
view and edit server details.
● Cluster access mode—The cluster access mode is either normal or allow all. See “Enforcement
Clusters and Servers” on page 48 for instructions on making the access mode selection.
● Health status—Health status shows ok for servers with no problems, and either warning or error for
servers with problems. Click the server name to view details.
● Upgrade status—Upgrade status shows the status of any upgrades in process.
● % memory used—The amount of memory currently used by each server is shown as a percentage of
total memory available.
● Endpoints tested/minute—The number of endpoints tested over the last 15 minutes or less.
● Endpoints queued—The number of tests running or scheduled to run on that ES.
● System load average—The number of processes waiting to run (top command). In Linux, entering
top at the command line returns a real-time look at processor activity.
Figure 2: System Monitor Window
Breadcrumbs for navigation
Sentriant AG Software Users Guide, Version 5.2
25
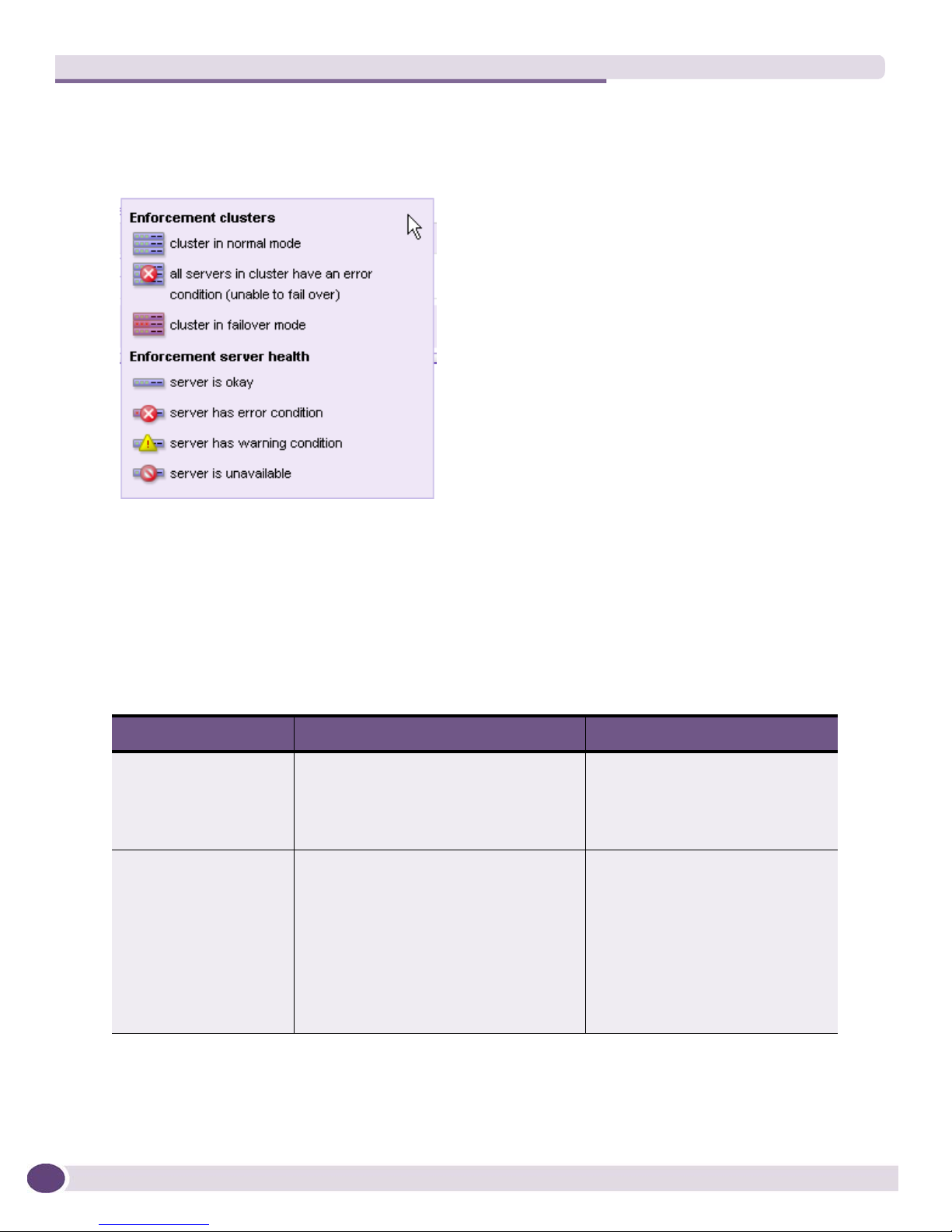
Introduction
The following figure shows the legend for the System monitor window icons:
Figure 3: System Monitor Window Legend
Sentriant AG v5.2 for v4.x Users
The user interface has been completely redesigned in this release of Sentriant AG. The following table
provides a quick-reference for users familiar with Sentriant AG v4.x. The first column shows the v4.x
task with the corresponding v5.2 user interface location in the second column.
Table 1: Sentriant AG v5.2 for v4.x Users
Sentriant AG 4.x Sentriant AG 5.0 Notes
System configuration
button
General tab • License key—System
System configuration menu option The System configuration button was
previously towards the top right of
the main window. The System
configuration menu option is now at
the bottom left of the home window.
The General tab tasks are now on
configuration>>License
• Name of network—System
configuration>>Enforcement clusters &
servers
• Default NAC policy—NAC policy
• Administrator login—System
configuration>>User accounts
two different windows: System
configuration and NAC policies.
The Network name no longer applies;
use cluster and server names
instead.
26
Sentriant AG Software Users Guide, Version 5.2
Table 1: Sentriant AG v5.2 for v4.x Users (continued)
Sentriant AG 4.x Sentriant AG 5.0 Notes
Introduction
System tab • Interface and DNS configuration—
System configuration>>Select a
server>>Configuration
• Date & time settings—System
configuration>>Management server
Quarantine tab • Accessible services and endpoints—
System configuration>>Accessible
services OR System
configuration>>Enforcement clusters &
servers>>Select add an Enforcement
cluster or Select an existing
cluster>>Accessible services
• Quarantine method—System
configuration>>Quarantining>>Select a
cluster to override the default setting
• Quarantine area—System
configuration>>Quarantining>>DHCP
quarantine method>>Add a quarantine
area
• Routing on the endpoint—System
configuration>>Quarantining>>DHCP
quarantine method>>Add a quarantine
area
System tab tasks are on the System
configuration window.
Accessible services are set as cluster
defaults. These defaults can be
overridden when creating or editing a
cluster.
The default quarantine method for all
clusters is 802.1X. This default can
be overridden for all clusters and per
cluster.
The DHCP quarantine option has two
selections now: Static routes on the
endpoints or Router access control
lists.
Notification tab System configuration>>Notifications OR
System configuration>>Select an
Enforcement cluster>>Notifications
Test s t a b • Check for test updates—System
configuration>>Test updates
• Endpoint testing exemptions—System
configuration>>Exceptions
Thresholds tab The thresholds and stoplight have been
removed.
End-user access tab • End-user testing methods—System
configuration>>Testing methods
• End-user testing options—System
configuration>>Testing methods
• End-user testing screen
customization—System
configuration>>End-user screens
• Enable test failed pop-up—System
configuration>>End-user screens
Notifications are set as cluster
defaults, but can be overridden when
creating or editing a cluster.
Exemptions is now called exceptions.
The home window now provides
system status.
End-user tab tasks are on the System
configuration window. They are set as
cluster defaults, but can be
overridden when creating or editing a
cluster.
Sentriant AG Software Users Guide, Version 5.2
27
Introduction
Table 1: Sentriant AG v5.2 for v4.x Users (continued)
Sentriant AG 4.x Sentriant AG 5.0 Notes
Credentials tab System configuration>>Agentless
credentials
Monitor and report zone Home window System status is shown on the home
Manage system
zone>>System mode
Access policies zone Home window>>NAC policies Access policies are now called NAC
View activity tab Home window>>Endpoint activity Devices are now called Endpoints.
N/A Home window>>System monitor
Access policy
editor>>Viewing last
device results
System configuration>>Enforcement
clusters & servers>>Select or add an
Enforcement cluster>>General
Endpoint activity
Windows domain credentials are on
the System configuration window
(Agentless credentials). They are set
as cluster defaults, but can be
overridden when creating or editing a
cluster.
RDBMS and LDAP credentials have
been removed.
window and on the System monitor
window.
policies.
Reports tab Home window>>Reports
Proxy settings (command
line)
nac.properties file
updates
Backing up data
(command line)
Restoring data (command
line)
Diagnostics link Not currently available. May be added in a
Tests tab>>View test
update logs
System configuration>>Management server
and via the command line for times when
the license has not yet been validated.
Use a script to update properties files
(nac-es.properties and nac-
ms.properties).
System configuration>>Maintenance
System configuration>>Maintenance
future release.
System configuration>>Test updates>>View
test update log.
Proxy servers can be configured for
test updates and license validation
only.
Property file updates should no
longer be made directly, but
imported using the
setProperty.py script.
28
Sentriant AG Software Users Guide, Version 5.2
Introduction
Overview
Sentriant AG protects the network by ensuring that endpoints are free from threats and in compliance
with the organization's IT security standards. Sentriant AG systematically tests endpoints—with or
without the use of a client or agent—for compliance with organizational security policies, quarantining
non-compliant machines before they damage the network.
Sentriant AG ensures that the applications and services running on endpoints (such as LAN, RAS, VPN,
and WiFi endpoints) are up-to-date and free of worms, viruses, trojans, P2P and other potentially
damaging software. It dramatically reduces the cost and effort of securing your network's weakest
links—the endpoints your IT group might not adequately control.
There are advantages and disadvantages inherent with each of the test method technologies. Having a
choice of testing solutions enables you to maximize the advantages and minimize the disadvantages.
NOTE
Agentless testing uses an existing Windows service (RPC). ActiveX testing uses an ActiveX control. Extreme
Networks, Inc. agent testing installs an agent (Sentriant AG Agent) and runs as a new Windows service.
The trade-offs in the test methods are described in the following table:
Table 2: Test Methods
Trade-offs
Test method
Pros Cons
Agentless • Truly agentless, no install or
download.
• No extra memory load on the client
machine.
• Can begin testing, view test results,
and give network access without any
end-user interaction for
your Windows domains.
• Easiest of the three test methods to
deploy.
• Saves administration time and is
therefore less expensive than
agent-based solutions.
endpoints on
• Requires RPC Service to be
available to the Sentriant AG server
(ports 139 or 445).
• Requires file and print sharing to be
enabled.
• Not supported by legacy Windows™
operating systems and non-Windows
operating systems.
• If the endpoint is not on a domain,
the user must specify local
credentials. A user often does not
know what credentials to enter.
Sentriant AG Software Users Guide, Version 5.2
29
Introduction
Table 2: Test Methods (continued)
Trade-offs
Test method
Pros Cons
ActiveX plug-in • No installation or upgrade to
maintain.
• Supports all Windows operating
systems.
• Only Internet Explorer application
access required through personal
firewall. Must open port 1500.
Sentriant AG
Agent
• Always available for retesting.
• The agent is automatically updated
with product updates.
• Supports all Windows platforms.
The following list highlights key features:
• No retesting of endpoint once
browser is closed.
• Not supported by non-Windows
operating systems.
• Browser security settings must allow
ActiveX control operation of signed
and safe controls. This is the
default for the Internet zone. Raise
the Internet zone setting and make
Sentriant AG part of the trusted
zone.
• Requires interaction from
end-users—they must download the
control before they can access
network.
• Install and upgrade to maintain.
• Requires one-time interaction from
end-users—they must download and
install before they can access
network.
● Enforcement options—Sentriant AG provides multiple enforcement options for quarantining
endpoints that do not comply with your security policy (Inline, DHCP, and 802.1X). This enables
Sentriant AG to enforce compliance across complex, heterogeneous networks.
● High availability and load balancing—A multi-server Sentriant AG deployment is mutually
supporting. Should one server fail, other nodes within a cluster will automatically provide coverage
for the affected network segment.
Load balancing is achieved by an algorithm that spreads the endpoint testing load across all ESs in a
cluster.
● Multiple-user, role-based access—In enterprise deployments numerous individuals, each with
varying responsibilities, typically require access to information within Sentriant AG. Role-based
access enables system administrators to control who has access to the data, the functions they are
allowed to perform, and the information they can view and act on. Role-based access ensures the
integrity of the enterprise-wide Sentriant AG deployment and creates the separation of duties that
conforms to security best-practices.
● Extensible—Sentriant AG’s easy-to-use open API allows administrators to create custom tests for
meeting unique organizational requirements. The API is fully exposed and thoroughly documented.
Custom tests are created using scripts and can be seamlessly added to existing policies.
● Compatible with existing heterogeneous network infrastructure—No upgrades to your existing
network infrastructure are required.
● Variety of enforcement options—Permit, deny, or quarantine based on test results.
30
Sentriant AG Software Users Guide, Version 5.2
 Loading...
Loading...