
Ridgeline Concepts and Solutions Guide
Software Version 3.0
Extreme Networks, Inc.
3585 Monroe Street
Santa Clara, California 95051
(888) 257-3000
(408) 579-2800
http://www.extremenetworks.com
Published: February 2011
Part Number: 100396-00 Rev. 01

AccessAdapt, Alpine, Altitude, BlackDiamond, EPICenter, Essentials, Ethernet Everywhere, Extreme Enabled,
Extreme Ethernet Everywhere, Extreme Networks, Extreme Standby Router Protocol, Extreme Turbodrive, Extreme
Velocity, ExtremeWare, ExtremeWorks, ExtremeXOS, Go Purple Extreme Solution, Ridgeline, ScreenPlay, Sentriant,
ServiceWatch, Summit, SummitStack, Triumph, Unified Access Architecture, Unified Access RF Manager, UniStack,
the Extreme Networks logo, the Alpine logo, the BlackDiamond logo, the Extreme Turbodrive logo, the Summit
logos, and the Powered by ExtremeXOS logo are trademarks or registered trademarks of Extreme Networks, Inc. or
its subsidiaries in the United States and/or other countries.
Active Directory is a registered tradement of Microsoft.
sFlow is a registered trademark of InMon Corporation.
XenServer is a trademark of Citrix.
vCenter is trademark of VMware.
Specifications are subject to change without notice.
All other registered trademarks, trademarks, and service marks are property of their respective owners.
© 2011 Extreme Networks, Inc. All Rights Reserved.
2
Ridgeline Concepts and Solutions Guide

Table of Contents
Preface......................................................................................................................................................... 9
Introduction...............................................................................................................................................................9
Terminology ......................................................................................................................................................9
Conventions ...........................................................................................................................................................10
Related Publications...............................................................................................................................................11
Chapter 1: Ridgeline Overview................................................................................................................13
Introduction.............................................................................................................................................................13
Ridgeline Features .................................................................................................................................................13
Inventory Management ...................................................................................................................................16
Network Views ................................................................................................................................................17
Device Groups and Port Groups .....................................................................................................................17
Map Views.......................................................................................................................................................17
Ridgeline Scripts .............................................................................................................................................17
The Alarm Manager ........................................................................................................................................17
The Configuration Manager and the Firmware Manager ................................................................................18
The IP/MAC Address Finder ...........................................................................................................................18
Real-Time Statistics ........................................................................................................................................18
Ridgeline Reports............................................................................................................................................19
Role-based Access Management ...................................................................................................................19
Distributed Server Mode .................................................................................................................................19
EAPS Monitoring and Configuration Verification.............................................................................................20
Ridgeline Software Architecture .............................................................................................................................20
Extreme Networks Switch Management.................................................................................................................21
SNMP and MIBs..............................................................................................................................................21
The Remote Monitoring (RMON) MIB......................................................................................................22
Traps and Smart Traps ...................................................................................................................................22
Device Status Polling ......................................................................................................................................22
Telnet Polling ...........................................................................................................................................22
Edge Port Polling Using the MAC Address Poller....................................................................................23
Updating Device Status with the Ridgeline Database..............................................................................23
Extreme Networks Device Support .................................................................................................................23
Third-Party Device Support .............................................................................................................................23
Chapter 2: Getting Started with Ridgeline ............................................................................................. 25
Starting Ridgeline ...................................................................................................................................................25
Starting the Ridgeline Server ........................................................................................................................26
Starting the Ridgeline Server in a Linux or Solaris Environment .............................................................26
Launching the Ridgeline Client .......................................................................................................................26
Getting Help ...........................................................................................................................................................29
Working with Ridgeline Windows ...........................................................................................................................29
Modifying Table Views ....................................................................................................................................31
Sorting Table Rows..................................................................................................................................31
Resizing Table Columns ..........................................................................................................................31
Moving Table Columns ............................................................................................................................31
Removing Columns From a Table ...........................................................................................................31
Moving Tabbed Windows in Ridgeline ............................................................................................................32
Ridgeline User Roles..............................................................................................................................................32
Ridgeline Concepts and Solutions Guide
1

Creating the Device Inventory ................................................................................................................................32
Using Discovery ..............................................................................................................................................33
Adding Devices Individually ............................................................................................................................34
Setting Up Default Device Contact Information...............................................................................................35
Using Network Views..............................................................................................................................................36
Device Groups and Port Groups .....................................................................................................................38
Map Views.......................................................................................................................................................38
Displaying Device Inventory Information ................................................................................................................39
Viewing Device Properties......................................................................................................................................40
Opening a Telnet Session to a Device ...................................................................................................................41
Collecting Device Information for Extreme Support ........................................................................................43
Managing Device Configurations and Firmware.....................................................................................................44
Using the Ridgeline Alarm Manager.......................................................................................................................45
Predefined Alarms...........................................................................................................................................45
The Alarm Log Browser ..................................................................................................................................46
Using Basic Ridgeline Reports ...............................................................................................................................46
Chapter 3: Organizing Devices and Ports Into Groups ........................................................................ 51
About Ridgeline Groups .........................................................................................................................................51
Displaying Groups in the Network Views Folder .............................................................................................51
Group Membership Guidelines .......................................................................................................................53
Managing Device Groups and Port Groups............................................................................................................53
Creating a Group.............................................................................................................................................53
Adding a Device to a Device Group ................................................................................................................54
Adding Ports to a Port Group ..........................................................................................................................55
Adding Ports from a Single Device to a Port Group .................................................................................55
Adding Ports from Multiple Devices to a Port Group................................................................................57
Copying or Moving Groups .............................................................................................................................58
Removing Devices or Ports from Groups........................................................................................................59
Modifying the Properties of a Group ...............................................................................................................59
Displaying Group Details.................................................................................................................................60
Exporting Group Information ...........................................................................................................................61
Chapter 4: Using Map Views ...................................................................................................................63
About Network Topology Maps ..............................................................................................................................63
Map Elements .................................................................................................................................................65
Device Nodes ...................................................................................................................................65
Subgroup Nodes...............................................................................................................................66
Hyper Nodes.....................................................................................................................................66
Decorative Nodes .............................................................................................................................66
Text Nodes .......................................................................................................................................66
Clouds...............................................................................................................................................66
Links .................................................................................................................................................66
Navigating Maps .............................................................................................................................................68
Zooming In and Out on a Map .................................................................................................................68
Using the Navigation Box.........................................................................................................................68
Creating Maps ........................................................................................................................................................69
Creating a Map for a Device Group ................................................................................................................70
Specifying Map Properties ..............................................................................................................................70
Laying Out the Map.........................................................................................................................................71
Creating User-Defined Links ...........................................................................................................................71
Removing Inactive Links from the Map ...........................................................................................................72
Adding Graphic Elements to the Map .............................................................................................................73
Adding a Device Annotation............................................................................................................................74
Exporting Maps ...............................................................................................................................................74
Deleting Maps .................................................................................................................................................75
2
Ridgeline Concepts and Solutions Guide

Chapter 5: Provisioning Network Resources ........................................................................................ 77
Provisioning Example.............................................................................................................................................77
Creating a VLAN .............................................................................................................................................77
Modifying a VLAN ...........................................................................................................................................80
Troubleshooting for Provisioning Tasks .................................................................................................................83
Viewing Logged Information about Provisioning Tasks..........................................................................................84
Chapter 6: Managing Ethernet Services................................................................................................. 87
E-Line Service ........................................................................................................................................................87
E-LAN Service........................................................................................................................................................88
Bandwidth Profiles ..........................................................................................................................................89
Configuring Ethernet Services................................................................................................................................89
Creating an Ethernet Service ..........................................................................................................................89
Modifying an Ethernet Service ........................................................................................................................94
Creating a Customer Profile............................................................................................................................95
Creating a Bandwidth Profile...........................................................................................................................96
Viewing Ethernet Services Information...................................................................................................................98
Using the All Table and All Map View .............................................................................................................98
Using the Services View .................................................................................................................................99
Displaying Ethernet Service Details .....................................................................................................................100
Chapter 7: Importing Services ..............................................................................................................103
Importing E-Line and E-L AN Services.................................................................................................................103
Chapter 8: Managing PBB Networks .................................................................................................... 113
SVLANs, BVLANs, CVLANs and ISIDs................................................................................................................114
Configuring BVLANs ............................................................................................................................................114
Creating a BVLAN.........................................................................................................................................115
Modifying a BVLAN .......................................................................................................................................116
Viewing PBB Information......................................................................................................................................118
Displaying PBB Details.........................................................................................................................................120
BVLAN, CVLAN, and SVLAN Details............................................................................................................121
ISID Details ...................................................................................................................................................122
Chapter 9: Managing and Monitoring VPLS Domains ........................................................................ 123
Hierarchical VPLS (H-VPLS)................................................................................................................................124
VPLS Support in Ridgeline...................................................................................................................................125
Viewing VPLS Information....................................................................................................................................125
Displaying VPLS Details.......................................................................................................................................127
Displaying Pseudowire Details......................................................................................................................127
Configuring VPLS.................................................................................................................................................128
Running VPLS Configuration Scripts ............................................................................................................128
Chapter 10: Managing VLANs ...............................................................................................................131
Configuring and Monitoring VLANs with Ridgeline...............................................................................................131
Configuring VLANs...............................................................................................................................................132
Provisioning VLANs ......................................................................................................................................132
Creating a VLAN ....................................................................................................................................132
Modifying a VLAN ..................................................................................................................................136
Running VLAN Configuration Scripts ............................................................................................................138
Viewing VLAN Information ...................................................................................................................................139
Displaying VLAN Details.......................................................................................................................................140
Viewing VLAN Services Information..............................................................................................................140
Displaying VLAN Details for an Individual Device .........................................................................................141
Ridgeline Concepts and Solutions Guide
3

Displaying VMAN Details ..............................................................................................................................141
Categorizing VLANs With Network Names ..........................................................................................................141
Creating a Network Name.............................................................................................................................141
Assigning VLANs to a Network Name...........................................................................................................142
Filtering the VLANs Table Based on Network Name ....................................................................................142
Chapter 11: Managing Virtual Machines ..............................................................................................145
Overview ..............................................................................................................................................................145
Introduction to the XNV Feature....................................................................................................................145
VM Port Configuration............................................................................................................................145
VM Authentication Process....................................................................................................................146
Ridgeline Authentication .................................................................................................................146
Network (VMMAP) Authentication ..................................................................................................146
Local Authentication .......................................................................................................................146
File Synchronization...............................................................................................................................146
Network Management and Inventory .....................................................................................................147
Example XNV Configuration .........................................................................................................................147
Managing the XNV Feature, VM Tracking............................................................................................................148
Limitations .....................................................................................................................................................148
Identifying VMMs and VMs ...........................................................................................................................149
Virtual Machine Manager Table .............................................................................................................149
Adding and Importing VMs............................................................................................................................150
Editing VM Manager Settings........................................................................................................................151
Deleting a VM Manager ................................................................................................................................152
Enabling VM Tracking On a Switch...............................................................................................................152
Editing List of Devices and Ports ..................................................................................................................156
Policy Match Condition Combinations..................................................................................................................159
Creating a Virtual-Port Profile...............................................................................................................................159
Attaching Policies, VPPs, and VMs......................................................................................................................161
Attaching a VPP to a VM...............................................................................................................................162
Attaching a Policy to a VPP ..........................................................................................................................165
Detaching VPPs ...................................................................................................................................................167
Detaching a VPP from a VM .........................................................................................................................167
Detaching a VPP from a Policy .....................................................................................................................168
Viewing Information on the VMs Tab....................................................................................................................169
All Table and All Map Views..........................................................................................................................169
Device Group/Subgroup Views .....................................................................................................................171
VM Details View ............................................................................................................................................172
VM Properties view ................................................................................................................................172
NIC Tab..................................................................................................................................................173
History Tab-VM Movement History ........................................................................................................173
Device Details with VM Monitoring................................................................................................................174
VM Monitoring Audit Log...............................................................................................................................175
Chapter 12: Managing Your EAPS Configuration ...............................................................................177
Configuring EAPS ................................................................................................................................................177
Creating an EAPS Domain............................................................................................................................178
Modifying an EAPS Domain..........................................................................................................................179
Creating a Shared Link ..........................................................................................................................180
Deleting an EAPS Domain ............................................................................................................................180
Viewing EAPS Information ...................................................................................................................................181
The EAPS Map View.....................................................................................................................................182
EAPS Node Icons ..................................................................................................................................182
Link Status .............................................................................................................................................183
Displaying EAPS Domain Details.........................................................................................................................184
Displaying EAPS Details for a Selected Device............................................................................................184
4
Ridgeline Concepts and Solutions Guide

Verifying EAPS Information..................................................................................................................................185
Running EAPS Reports........................................................................................................................................186
EAPS Summary Report ................................................................................................................................186
EAPS Log Reports ........................................................................................................................................187
Chapter 13: Managing Network Security.............................................................................................. 189
Security Overview ................................................................................................................................................189
Management Access Security ..............................................................................................................................189
Using RADIUS for Ridgeline User Authentication .........................................................................................190
Configuring a RADIUS Server for Ridgeline User Authentication ..........................................................190
Example: Setting up a VSA to Return Ridgeline Role Information.........................................................191
Example: Setting the Service Type for a Built-in Ridgeline Role ...........................................................192
Securing Management Traffic .......................................................................................................................192
Using SNMPv3 for Secure Management ...............................................................................................192
Using SSHv2 to Access Network Devices. ............................................................................................193
Securing Ridgeline Client-Server Traffic .......................................................................................................194
Monitoring Switch Configuration Changes ...........................................................................................................195
Using the MAC Address Finder ............................................................................................................................196
Using Alarms to Monitor Potential Security Issues...............................................................................................196
Device Syslog History...........................................................................................................................................197
Network Access Security with VLANs ..................................................................................................................198
Chapter 14: Policies ............................................................................................................................... 201
Overview ..............................................................................................................................................................201
Viewing Policies for Devices .........................................................................................................................202
Creating a New Policy ..........................................................................................................................................203
Copying a Policy to Create a New Policy......................................................................................................209
Editing a Policy..............................................................................................................................................210
Deleting a Policy ...........................................................................................................................................211
Detaching a Policy ........................................................................................................................................212
Attaching a Policy..........................................................................................................................................212
Categorizing Policies............................................................................................................................................213
Categorizing Policy Rules .............................................................................................................................214
Creating and Managing Roles ..............................................................................................................................214
Viewing Active Policies for Devices...............................................................................................................214
Chapter 15: Tuning and Debugging Ridgeline ....................................................................................215
Monitoring and Tuning Ridgeline Performance ....................................................................................................215
Disabling Ridgeline Management for a Device ......................................................................................215
Polling Types and Frequencies .....................................................................................................................216
SNMP Polling.........................................................................................................................................216
MAC Address Polling .............................................................................................................................216
Telnet Polling .........................................................................................................................................217
Performance of the Ridgeline Server ............................................................................................................217
Tuning the Alarm System .....................................................................................................................................217
Disabling Unnecessary Alarms .....................................................................................................................218
Limiting the Scope of Alarms ........................................................................................................................219
Using Device Groups and Port Groups for Alarm Scopes .....................................................................221
The Alarm and Event Log Archives...............................................................................................................221
Using the MIB Poller Tools...................................................................................................................................221
Defining a MIB Collection..............................................................................................................................222
The MIB Poller Summary ..............................................................................................................................223
Loading, Starting and Stopping a Collection ..........................................................................................224
The MIB Collection Detail Report...........................................................................................................224
The MIB Poller Detail Report .................................................................................................................225
Viewing the XML Collection Definition ...................................................................................................226
Ridgeline Concepts and Solutions Guide
5

Exporting the Collected Data .................................................................................................................226
The MIB Query Tool......................................................................................................................................226
Reconfiguring Ridgeline Ports..............................................................................................................................227
Using the Ridgeline Debugging Tools ..................................................................................................................228
Reconfiguring the FreeRadius Server ..................................................................................................................228
Chapter 16: Creating and Running Ridgeline Scripts.........................................................................229
About Ridgeline Scripts ........................................................................................................................................229
Bundled Ridgeline Scripts .............................................................................................................................230
The Ridgeline Script Interface ..............................................................................................................................230
Managing Ridgeline Scripts..................................................................................................................................232
Creating a New Ridgeline Script ...................................................................................................................233
Specifying Run-Time Settings for a Script.....................................................................................................236
Specifying Permissions and Launch Points for a Script ................................................................................237
Running a Script............................................................................................................................................238
Importing Scripts into Ridgeline ....................................................................................................................242
Categorizing Scripts ......................................................................................................................................243
Specifying an Ridgeline Script as an Alarm Action .......................................................................................244
Configuring Script Tasks ...............................................................................................................................244
Using the Audit Log to Troubleshoot Ridgeline Scripts ........................................................................................246
Audit Log View ..............................................................................................................................................246
Filtering the Audit Log View ...................................................................................................................247
Displaying Audit Log Details for a Script .......................................................................................................247
Rerunning a Script ........................................................................................................................................248
About ExtremeXOS Scripts ..................................................................................................................................248
Chapter 17: Using Identity Management .............................................................................................. 249
Identity Management Software License ...............................................................................................................249
Overview ..............................................................................................................................................................249
Role-Based Access Control..................................................................................................................................250
Roles, Policies, and Rules ............................................................................................................................250
Roles......................................................................................................................................................250
Policies...................................................................................................................................................251
Role Hierarchy ..............................................................................................................................................251
Role Inheritance ............................................................................................................................................253
LDAP Attributes and Server Selection ..........................................................................................................254
Enabling Monitoring on Switches and Ports .........................................................................................................254
Editing Monitored Device Ports ............................................................................................................................259
Disabling Monitoring......................................................................................................................................260
Enabling Role-based Access Control on New Devices ........................................................................................261
Disabling Role-based Access Control...........................................................................................................265
Creating Roles......................................................................................................................................................265
Defining a New Role .....................................................................................................................................266
Creating a Child Role with Conditions Inherited from Its Parent............................................................268
Creating a Child Role with Conditions Inherited from a Different Role ..................................................271
Viewing Roles ...............................................................................................................................................272
Viewing Role Details ..............................................................................................................................273
Editing Roles .................................................................................................................................................274
Deleting Roles...............................................................................................................................................275
Policy Match Condition Combinations..................................................................................................................276
Attaching Policies to Roles............................................................................................................................276
Deleting a Policy Attached to a Role.............................................................................................................278
Error and Results Handling ...........................................................................................................................279
Configuring Directory Servers ..............................................................................................................................279
Viewing the Server Directory.........................................................................................................................280
Managing Global Directory Servers ..............................................................................................................280
6
Ridgeline Concepts and Solutions Guide

Configuring a New Directory Server..............................................................................................................280
Editing LDAP Client Properties .....................................................................................................................283
Deleting a Directory Server ...........................................................................................................................285
Viewing Network User Information .......................................................................................................................286
Network User Dashboard Reports ................................................................................................................286
Users Table...................................................................................................................................................287
Active Users Tab....................................................................................................................................288
Inactive and Active Users Tab ...............................................................................................................289
Displaying Network User Details ..........................................................................................................................290
Displaying Identity Management Reports.............................................................................................................292
Chapter 18: Managing Network Device Configurations and Updates ...............................................293
Archiving Device Configurations...........................................................................................................................293
Baseline Configurations .......................................................................................................................................294
Identifying Changes in Configuration Files....................................................................................................295
Automatic Differences Detection...................................................................................................................295
Device Configuration Management Log ...............................................................................................................296
Managing Firmware Upgrades .............................................................................................................................297
Automated Retrieval of Firmware Updates from Extreme.............................................................................297
Detection of Firmware Obsolescence for Network Components...................................................................297
Appendix A: Troubleshooting ...............................................................................................................299
Troubleshooting Aids............................................................................................................................................299
About Ridgeline Window ...............................................................................................................................299
Enabling the Java Console ...........................................................................................................................300
Ridgeline Client Issues.........................................................................................................................................300
Ridgeline Database ..............................................................................................................................................301
Ridgeline Server Issues .......................................................................................................................................302
VLAN Management ..............................................................................................................................................305
Alarm System .......................................................................................................................................................305
Ridgeline Inventory...............................................................................................................................................307
Printing .................................................................................................................................................................307
Reports.................................................................................................................................................................308
Configuration Manager.........................................................................................................................................308
Appendix B: Configuring Devices for Use With Ridgeline ................................................................. 309
Configuring Ridgeline as a Syslog Receiver ........................................................................................................309
Setting Ridgeline as a Trap Receiver...................................................................................................................310
The Ridgeline Third-party Device Integration Framework ....................................................................................310
Ridgeline Inventory Integration .....................................................................................................................311
The Abstract Type Library XML file........................................................................................................311
The OID folder .......................................................................................................................................314
The dpsimages.zip File ..........................................................................................................................314
Telnet Integration ..........................................................................................................................................315
Alarm Integration...........................................................................................................................................316
Editing the Events.xml file......................................................................................................................316
Adding the MIB(s) to Ridgeline ..............................................................................................................317
Launching Third Party Applications...............................................................................................................317
Appendix C: Using SSH for Secure Communication ..........................................................................319
Overview of Tunneling Setup ...............................................................................................................................319
Step 1: Install PuTTY on the Ridgeline Client ......................................................................................................320
Step 2: Configure the PuTTY Client .....................................................................................................................320
Step 3: Installing OpenSSH Server ......................................................................................................................323
Step 4: Configure Microsoft Firewall to Allow SSH Connects ..............................................................................328
Step 5: Initiate Ridgeline Server/Client Communication.......................................................................................330
Ridgeline Concepts and Solutions Guide
7

Appendix D: Configuring RADIUS for Ridgeline Authentication ....................................................... 331
Step 1. Create an Active Directory User Group for Ridgeline Users ....................................................................331
Step 2. Associate Users with the Ridgeline Group...............................................................................................332
Step 3. Enable Ridgeline as a RADIUS Client .....................................................................................................334
Step 4. Create a Remote Access Policy for Ridgeline Users ...............................................................................336
Step 5. Edit the Remote Access Policy to add a VSA..........................................................................................341
Step 6. Configure Ridgeline as a RADIUS Client .................................................................................................347
Appendix E: Ridgeline Utilities .............................................................................................................349
Package Debug Info Utility ...................................................................................................................................349
Port Configuration Utility.......................................................................................................................................350
The DevCLI Utility ................................................................................................................................................351
Using the DevCLI Commands.......................................................................................................................352
DevCLI Examples .........................................................................................................................................353
Inventory Export Scripts .......................................................................................................................................354
Using the Inventory Export Scripts................................................................................................................354
Inventory Export Examples ...........................................................................................................................356
The SNMPCLI Utility.............................................................................................................................................356
Using the SNMPCLI Utility ............................................................................................................................357
SNMPCLI Examples .....................................................................................................................................358
The AlarmMgr Utility.............................................................................................................................................358
Using the AlarmMgr Command.....................................................................................................................358
AlarmMgr Output...........................................................................................................................................360
AlarmMgr Examples......................................................................................................................................360
The FindAddr Utility..............................................................................................................................................361
Using the FindAddr Command......................................................................................................................361
FindAddr Output............................................................................................................................................363
FindAddr Examples.......................................................................................................................................363
The TransferMgr Utility.........................................................................................................................................363
Using the TransferMgr Command.................................................................................................................364
TransferMgr Examples..................................................................................................................................366
The ImportResources Utility .................................................................................................................................366
Using the ImportResources Command .........................................................................................................366
Importing from a File.......................................................................................................................367
Importing from an LDAP Directory..................................................................................................367
Importing from an Windows Domain Controller or NIS Server .......................................................367
ImportResources Examples ..........................................................................................................................368
FreeRadius Server Configuration Commands.......................................................................................
...............368
8
Ridgeline Concepts and Solutions Guide
Preface
This preface provides an overview of this guide, describes guide conventions, and lists other useful
publications.
Introduction
This guide provides the required information to use the Ridgeline software. It is intended for use by
network managers who are responsible for monitoring and managing Local Area Networks, and
assumes a basic working knowledge of:
● Local Area Networks (LANs)
● Ethernet concepts
● Ethernet switching and bridging concepts
● Routing concepts
● The Simple Network Management Protocol (SNMP)
NOTE
If the information in the Release Notes shipped with your software differs from the information in this
guide, follow the Release Note.
Terminology
When features, functionality, or operation is specific to the Summit, Alpine, or BlackDiamond switch
family, the family name is used. Explanations about features and operations that are the same across all
Extreme switch product families simply refer to the product as the “Extreme device” or “Extreme
switch.” Explanations about features that are the same for all devices managed by Ridgeline (both
Extreme devices and others) are simply refer to “devices.”
Ridgeline Concepts and Solutions Guide
9
Conventions
Conventions
Tab le 1 and Ta bl e 2 list conventions that are used throughout this guide.
Table 1: Notice Icons
Icon Notice Type Alerts you to...
Note Important features or instructions.
Caution Risk of unintended consequences or loss of data.
Warning Risk of permanent loss of data.
.
Table 2 : Text C o nve n tions
Convention Description
Screen displays This typeface represents information as it appears on the screen.
Screen displays bold This typeface indicates how you would type a particular command.
The words “enter”
and “type”
[Key] names Key names appear in text in one of two ways. They may be
Words in bold type Bold text indicates a button or field name.
Words in italicized type Italics emphasize a point or denote new terms at the place where they are defined in
When you see the word “enter” in this guide, you must type something, and then
press the Return or Enter key. Do not press the Return or Enter key when an
instruction simply says “type.”
• referred to by their labels, such as “the Return key” or “the Escape key.”
• written with brackets, such as [Return] or [Esc].
If you must press two or more keys simultaneously, the key names are linked with a
plus sign (+). For example:
Press [Ctrl]+[Alt]+[Del].
the text.
10
Ridgeline Concepts and Solutions Guide

Related Publications
The Ridgeline documentation set includes the following:
● Ridgeline Reference Guide
● Ridgeline Concepts and Solutions Guide (this guide)
● Ridgeline Installation and Upgrade Guide
● Ridgeline Release Notes
● Ridgeline License Agreement
Both the Ridgeline Reference Guide and the Ridgeline Concepts and Solutions Guide can be found online in
Adobe Acrobat PDF format in the
docs subdirectory of the Ridgeline installation directory.
You must have Adobe Acrobat Reader version 5.0 or later (available from
http://www.adobe.com free of
charge) to view these manuals.
The Ridgeline software also includes context-sensitive online Help, available from the Help menu in
each Ridgeline window.
Other manuals that you will find useful are:
● ExtremeWare Software User Guide
● ExtremeWare Command Reference Guide
● ExtremeXOS Concepts Guide
● ExtremeXOS Command Reference Guide
For documentation on Extreme Networks products, and for general information about Extreme
Networks, see the Extreme Networks home page:
● http://www.extremenetworks.com
Customers with a support contract can access the Technical Support pages at:
● http://www.extremenetworks.com/services/eSupport.asp
The technical support pages provide the latest information on Extreme Networks software products,
including the latest Release Notes, information on known problems, downloadable updates or
patches as appropriate, and other useful information and resources.
Customers without contracts can access manuals at:
● http://www.extremenetworks.com/services/documentation/
Ridgeline Concepts and Solutions Guide
11

Related Publications
12
Ridgeline Concepts and Solutions Guide

Ridgeline Overview
1
CHAPTER
This chapter describes:
● The features of the Ridgeline
● The Ridgeline software architecture and components
● Overview of Ridgeline switch management
™
software
Introduction
Today's corporate networks commonly encompass hundreds or thousands of systems, including
individual end user systems, servers, network devices such as printers, and internetworking systems.
Extreme Networks
management tools to meet those needs.
The Ridgeline (Ridgeline) Management Suite is a scalable full-featured network management tool that
simplifies configuration, troubleshooting, and status monitoring of IP-based networks. Offering a
comprehensive set of network management applications providing the ability to configure, monitor,
troubleshoot, and manage the network and its elements, Ridgeline delivers on both the basic
requirements of network management while adding valuable and intuitive features that help save time
by streamlining common tasks.
Ridgeline offers a comprehensive set of network management applications that are easy to use from a
workstation configured with a web browser and the Java plug-in. The Ridgeline application and
database support three of the most popular operating environments in the marketplace, Microsoft
Windows, Red Hat Enterprise Linux, and Sun Microsystems’ Solaris.
™
recognizes that network managers have different needs, and delivers a suite of
Ridgeline Features
In large corporate networks, network managers need to manage systems “end to end.”
Ridgeline is a powerful, flexible and easy-to-use application for centralizing configuration,
troubleshooting, and status monitoring of IP-based networks of Extreme Networks switches and
selected third-party devices, regardless of the network size.
Ridgeline establishes a new benchmark for accommodating convergence applications by offering
intuitive user interfaces and by reducing the complexity of managing converged networking
Ridgeline Concepts and Solutions Guide
13

Ridgeline Overview
environments. Ridgeline’s open architecture accommodates a multi-vendor, service-rich environment
that enables voice-class availability and the enforcement of robust security policies.
● Operational Simplicity. Simplicity begins with a detailed real-time view of the entire network.
Ridgeline’s maps provide users with an overview of every element of the network and how they all
connect at Layer 2 and Layer 3. Centralized configuration management and firmware management
simplifies the configuration and maintenance of your network elements. These functions can be
performed simultaneously on groups of devices anywhere on the network as well as on devices
individually.
● Voice-Class Availability. Ridgeline’s availability is greatly enhanced by granular health and status
monitoring of the network. Ethernet Automatic Protection Switching (EAPS) protocol support within
Ridgeline enhances a highly available Extreme Networks switching environment. The Real Time
Statistics feature provides a graphical representation of utilization and error statistics for multiple
ports on a device, device slot, or within a port group.
● Point-and-click network provisioning. Ridgeline’s provisioning features simplify network
configuration tasks with selectable options in dialog boxes. Ridgeline automatically validates the
options you’ve selected prior to deploying the configuration to managed devices, ensuring that the
configuration is correct before it goes into production.
● Comprehensive Security. Ridgeline provides multiple features that control and monitor the security
features on Extreme Networks’ products, including creation and management of VLANs easily
throughout the network. The IP/MAC Address Finder tool can locate any MAC address on your
network.
● Hierarchical grouping for devices and ports. Ridgeline allows you to assemble the devices and
ports in your network into groups and subgroups, and view information about them or manage
them at a group level. You can organize your network into a hierarchy of groups, with subgroups
for campuses, buildings, and individual rooms.
● Integrated network topology maps. Ridgeline’s network topology map feature is integrated with the
device group functionality, so that when you create a device group, you have the option of selecting
the Map view of the group, which causes Ridgeline to generate a network topology map, populated
with the devices in the group. Ridgeline automatically adds any links that exist between the device
nodes, and organizes them into submaps as appropriate. You can further customize your maps with
background images, decorative nodes and clouds, and user-specified links.
● Overlay views of VLANs in network maps. Information about the VLANs configured on the
devices in your network is readily accessible from Network View windows. VLAN services
information (VMAN, VLAN aggregation, VLAN translation, and Private VLAN) is incorporated into
network topology maps.
● Advanced scripting capabilities. Ridgeline includes an interface for creating and executing scripts
on your managed devices. Scripts created in Ridgeline can include ExtremeXOS CLI commands, as
well as commands and constructs in the Tcl scripting language. Scripts bundled with Ridgeline ease
common network configuration tasks. Ridgeline scripts can also be configured as script tasks, which
can run automatically at designated times.
● Multi-platform capability. The Ridgeline server supports Sun SPARC and Intel platforms, and the
Microsoft Windows, Red Hat Enterprise Linux and Solaris operating environments. Clients on any of
these platforms can connect to servers on any platform.
● Support for multiple users with security. Users must log in to the Ridgeline application, and can be
granted different levels of access to the application features based on their assigned role. Three basic
predefined roles are provided, and additional user roles can be created. Telnet and SSH access to
Extreme switches can also be controlled based on the user identity. To protect sensitive data from
being intercepted or altered by unauthorized access, Secure Shell 2 (SSHv2) protocol and HTTPS
protocols are provided. These protocols encrypt traffic between the switch management port and the
Ridgeline.
14
Ridgeline Concepts and Solutions Guide

● Support for third-party devices. Any device running a MIB-2 compatible SNMP agent can be
discovered by Ridgeline and monitored at a basic level. These devices can appear on a topology
map, with basic status and alarm handling based on MIB-2 functionality. Based on Ridgeline’s Third
Party Integration Framework, selected appliances from Extreme Networks partners can be integrated
into Ridgeline in a robust fashion that allows reporting, alarm management, and monitoring with
graphical front and back panel views.
1
Ridgeline Concepts and Solutions Guide
15

Ridgeline Overview
● Manage large numbers of devices. Ridgeline server can manage up to 2000 devices with a single
installation of the Ridgeline software. For even larger networks, you can split the management task
among several Ridgeline servers in a distributed server mode that lets you monitor the status of
those servers from a single client.
● VPLS discovery and visualization. Ridgeline can discover the Virtual Private LAN Service (VPLS)
configuration on the managed devices in your network, and display an overlay view of selected
VPLS instances, including information about specific pseudo wires. Ridgeline scripts can create
VPLS instances and configure devices as VPLS peers.
● PBB discovery, visualization, and provisioning. Ridgeline identifies the Service VLANs (SVLANs),
Backbone VLANs (BVLANs), Customer VLANs (CVLANs), and Extended Service ID (ISID)
instances in your Provider Backbone Bridge (PBB) networks. You can display an overlay view of a
selected PBB network, along with detailed information about PBB components in Ridgeline tables.
Ridgeline’s PBB provisioning feature allows you to create BVLANs on selected devices, ports, or
links, as well as modify and delete existing BVLANs.
● Ethernet service provisioning. Using the service provisioning wizard, you can create E-Line (point-
to-point) and E-LAN (multipoint-to-multipoint) services. You can select the devices and ports that
make up the service, specify the transport method (VLAN, VMAN, or PBB), create and apply
bandwidth profiles, then validate the configuration and deploy it on your network.
The Ridgeline features are described in more detail in the following sections. The rest of this manual
describes how to best use these features to manage various aspects of your network. For detailed
instructions on using specific features of Ridgeline see the context-sensitive online Help available from
the Help menu at the top of Ridgeline windows. The Ridgeline Reference Guide also provides a detailed
description of the functionality of each Ridgeline feature.
Inventory Management
Ridgeline keeps a database of all devices managed by the software. Any Ridgeline user with read-only
access to this feature can view status information about the switches currently known to Ridgeline.
Ridgeline provides a discovery function to discover the components of your network. Users with the
appropriate access (roles with read/write access) can use this feature to discover Extreme devices as
well as any third-party devices running a MIB-2 compatible SNMP agent. Devices may be discovered
by specific IP address or within a range of IP addresses. Third-party devices that support SNMP version
3 (SNMPv3) are discovered as SNMP version 1 (SNMPv1) and are added to the Ridgeline database as
SNMPv1 devices. Network devices can also be added to the Ridgeline database manually.
Once a network device is known to the Ridgeline database, you can copy it to a specific device group,
and configure it using a Device Manager (ExtremeWare Vista for Extreme devices). Ridgeline also
allows you to set a device to unmanaged status so that Ridgeline will not poll and can ignore traps
when a device is scheduled for maintenance.
Ridgeline also provides a command-line utility that lets you create device groups and import large
numbers of devices into the database through scripts, to streamline the process of adding and
organizing devices for management purposes. These utilities are described in Appendix E “Ridgeline
Utilities”.
Ridgeline displays detailed information about individual devices through a front panel image that
provides a visual device representation, with associated detailed configuration and status information.
Any Ridgeline user can view status information about the network devices known to Ridgeline. Users
with the appropriate access permissions can also view and modify configuration information for those
switches.
16
Ridgeline Concepts and Solutions Guide

Network Views
Ridgeline’s Network Views provide at-a-glance information about the devices, device groups, and port
groups in your network. You can display summary information about the devices or ports, links
between devices, VLANs, and EAPS domains, and you can select individual devices in tables or maps
to view detailed information about them.
Device Groups and Port Groups
Ridgeline has a powerful grouping feature that allows you to assemble groups of devices and ports, and
view information about them or manage them at a group level. You can organize your devices and
ports in a logical group structure, and administer and view status of components within the individual
groups. Graphical representations of device groups can appear in Network Views
Map Views
Ridgeline’s maps allow you to view Ridgeline-managed devices and the links between devices
graphically, as a set of maps. These maps can be organized into sets of submaps that allow you to
represent your network as a hierarchical system of campuses, buildings, floors, closets, or whatever
logical groupings you want.
1
A Ridgeline map is a graphical representation of a device group. When you create a device group, you
have the option of selecting the Map view of the group, which causes Ridgeline to generate a network
topology map, populated with the devices in the group.
Ridgeline also adds any links that exist between the device nodes. You can customize the resulting
maps by moving elements, adding new elements, such as links, “decorative” (non-managed) nodes, and
text, and customizing the device nodes themselves. Information about the links and devices in maps is
displayed graphically, with colored icons indicating device alarm level and state of the links between
devices.
Ridgeline Scripts
Ridgeline scripts are files containing CLI commands, control structures, and data manipulation
functions that can be executed on managed devices. Ridgeline scripts support syntax and constructs
from ExtremeXOS 12.1 (and higher) CLI scripts and the Tcl scripting language. Ridgeline includes a
number of bundled scripts that can perform such tasks as downloading firmware, uploading/
downloading configuration files, and configuring VLANs.
Ridgeline scripts can be run manually from the Ridgeline client, or you can configure them as script
tasks, which can run automatically at designated times.
The Alarm Manager
The Ridgeline Alarm System provides fault detection and alarm handling for the network devices
monitored by the Ridgeline software. This includes Extreme devices and some third-party devices—
those that the Ridgeline software can include in its database. The Alarm Manager also lets you define
your own alarms that will report errors under conditions you specify, such as repeated occurrences or
exceeding threshold values. You can specify the actions that should be taken when an alarm occurs, and
you can enable and disable individual alarms.
Ridgeline Concepts and Solutions Guide
17

Ridgeline Overview
Fault detection is based on SNMP traps, RMON traps, Syslog messages, and some limited polling. The
Alarm Manager supports SNMP MIB-2 and the Extreme Networks private MIB. You can also configure
alarms based on certain event thresholds, or on the content of Syslog messages. When an alarm occurs
you can specify actions such as sending e-mail, forwarding a trap, running a program, running a script,
sending a page, or sounding an audible alert.
The Configuration Manager and the Firmware Manager
The Ridgeline Configuration Manager provides a mechanism and a graphical interface for uploading
and downloading configuration files to and from managed devices. The Ridgeline Firmware Manager
can download ExtremeWare software images and BootROM images to Extreme Networks devices, or to
Extreme modules that include software.
The Configuration Manager provides a framework for storing the configuration files, to allow tracking
of multiple versions. Configuration file uploads can be performed on demand, or can be scheduled to
occur at regular times—once a day, once a week, or at whatever interval is appropriate.
The Configuration Manager also includes a facility to create and edit ExtremeXOS scripts, then deploy
them to managed devices.
The Firmware Manger can be configured to automatically track the firmware versions in Extreme
devices, will indicate whether newer versions are available, and can automatically retrieve those
versions from Extreme if desired.
The IP/MAC Address Finder
The IP/MAC Address Finder lets you search for specific network addresses (MAC or IP addresses) and
identify the Extreme Networks switch and port on which the address resides. You can also use the IP/
MAC Finder to find all addresses on a specific port or set of ports. If you have enabled Ridgeline’s
periodic MAC Address polling, which does polls for edge port address information, you can perform a
fast address search by just searching the Ridgeline database for this information. Alternatively you can
direct Ridgeline to search the FDBs of specific Extreme switches. You can export the results of your
search to a file, either on the server or on your local (client) system.
Real-Time Statistics
The Statistics feature of the Ridgeline software provides a graphical presentation of utilization and error
statistics for Extreme switches in real time. The data is taken from Management Information Base (MIB)
objects in the etherHistory table of the Remote Monitoring (RMON) MIB. You can choose from a variety
of styles of charts and graphs as well as a tabular display.
You can view data for multiple ports on a device, device slot, or within a port group, optionally
limiting the display to the “top N” ports (where N is a number you can configure). You can also view
limited historical statistics for an individual port. If you choose to view a single port, the display shows
the value of the selected variable(s) over time, and can show utilization history, total errors history, or a
breakdown of individual errors.
In addition, the Statistics feature lets you “snapshot” a graph or table as a separate browser page. You
can then save, print, or e-mail the page.
18
Ridgeline Concepts and Solutions Guide

Ridgeline Reports
Ridgeline Reports are HTML pages that can be accessed separately from the main Ridgeline user
interface, without logging on to Ridgeline. Ridgeline reports do not require Java, so reports can be
loaded quickly, even over a dial-up connection, and can be viewed on systems that cannot run the
Ridgeline client. Reports can be printed using your browser’s Print function.
The Reports capability provides a large number of predefined HTML reports that present a variety of
types of information from the Ridgeline database. You can also create your own reports by writing Tcl
scripts. Further, within the Reports Module are several useful tools such as a MIB Browser and other
tools that can provide Ridgeline system information.
Reports can also be accessed from within Ridgeline. A Summary report is displayed on the Ridgeline
Home page, which provides basic information on the status of Ridgeline devices and alarms. From this
report you can access other more detailed reports.
Role-based Access Management
All Ridgeline users must log on with a user name and password in order to access Ridgeline features.
Ridgeline initially provides four user roles:
● Monitor role: users who can view status information only.
● Manager role: users who can modify device parameters as well as view status information.
● Administrator role: users who can create, modify and delete Ridgeline user accounts as well as
perform all the functions of a user with Manager access.
● Disabled role: users whose account information is maintained, but who have no access to any
features of the product.
1
An Administrator user can create additional roles, can modify the capabilities available under each role,
and can add and delete Ridgeline users, as well as enable or disable access for individual users.
By default, Ridgeline provides its own authentication and authorization for Ridgeline users. However,
through Ridgeline Administration, Ridgeline can be configured to act as a Remote Authentication Dial
In User Service (RADIUS) client, allowing it to use an external RADIUS server to authenticate Ridgeline
users. As an option, the external RADIUS server can be configured to return user role information as
well as the user authentication.
As an alternative, Ridgeline can be configured to act as a RADIUS server, providing authentication for
Ridgeline users as well as for other devices such as Extreme switches. However, the RADIUS server
built into Ridgeline should only be used for demonstration or testing purposes, and should not be used
to provide primary authentication services in a production environment. The Ridgeline RADIUS server
is not sufficiently robust to perform as the authentication server in a production environment.
Distributed Server Mode
To manage very large numbers of network devices, or devices that are geographically distributed, the
management task can be divided up between multiple Ridgeline servers. Each server in the server
group is updated at regular intervals with network summary and status information from the other
servers in the group. From the Ridgeline home page, a client attached to any one of the servers in the
server group can view summary status information from the other servers in the group in addition to
the standard Network Summary report. The Ridgeline client also lets the user easily navigate between
the different servers in the group to see detailed management information about the devices managed
by those servers.
Ridgeline Concepts and Solutions Guide
19

Ridgeline Overview
EAPS Monitoring and Configuration Verification
Ethernet Automatic Protection Switching (EAPS) provides “carrier-class” network resiliency and
availability for enterprise networks. Ridgeline monitors EAPS rings from Network Views. You can
identify and display the status of EAPS rings, including Master and Transit nodes, link status, and a
variety of status information. Detailed status information is provided in multiple tables for domains,
devices and links.
You can also run a configuration verification which produces a report that details any configuration
errors detected among your EAPS nodes or domains.
Ridgeline Software Architecture
The Ridgeline software is made up of three major functional components:
● The Ridgeline Server. The server is responsible for managing security and communicating with the
managed objects, database, and client systems.
● The Ridgeline Database. The database is a Relational Database Management System (RDBMS),
which is used as both a persistent data store and a data cache.
● The Ridgeline Client. The client is a Java application downloaded on demand from the server to a
workstation running a supported browser and the Java plug-in. To start the client, a user points his
or her browser to the Ridgeline server and clicks the Log on to Ridgeline link. The client application
is then automatically downloaded to the user’s workstation and started.
20
Ridgeline Concepts and Solutions Guide
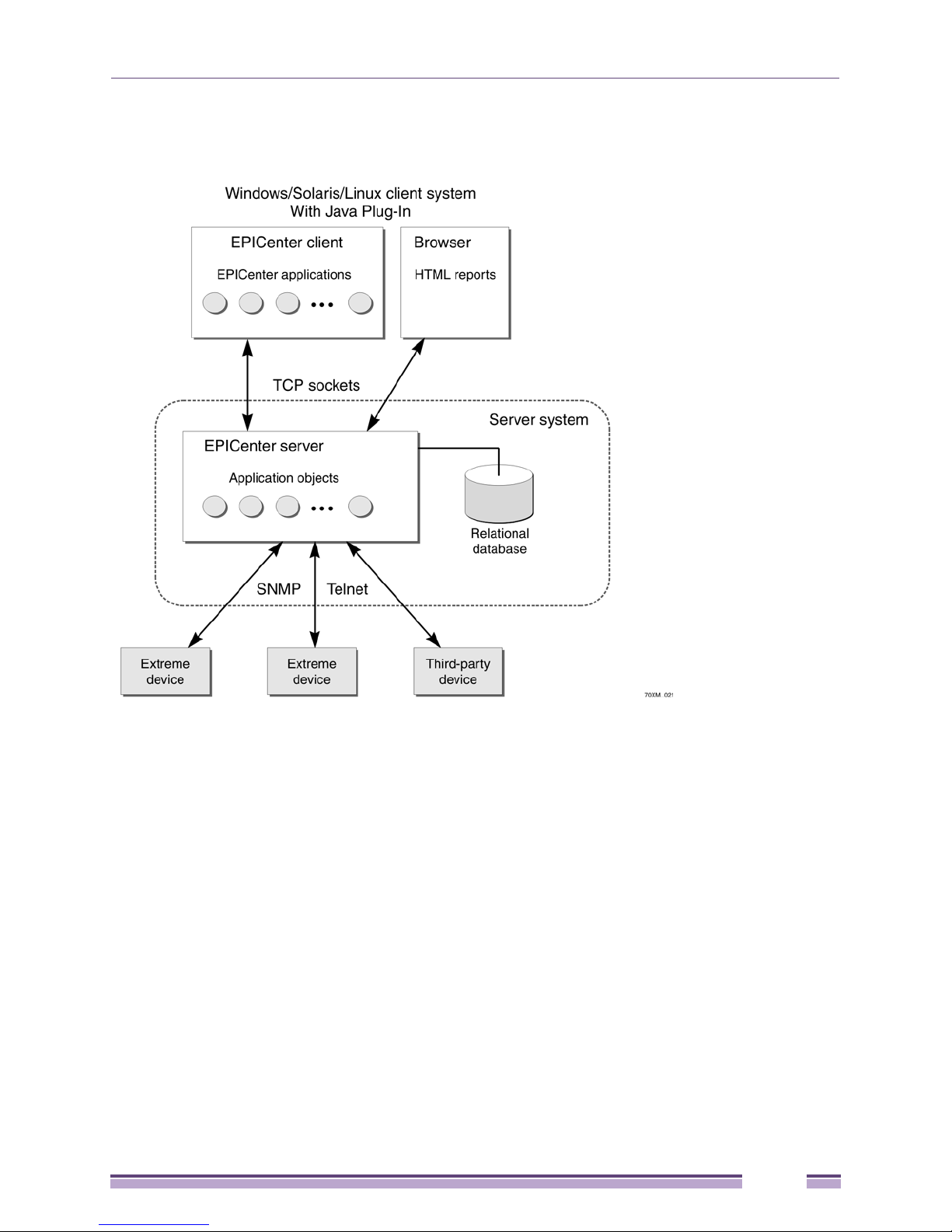
Figure 1 illustrates the architecture of the Ridgeline software.
Figure 1: Ridgeline Software Architecture
1
Extreme Networks Switch Management
Ridgeline primarily uses the Simple Network Management Protocol (SNMP) to monitor and manage the
devices in the network. The Ridgeline server periodically does a status poll of the devices it is managing
to determine if the devices are still accessible. It also does a full detailed poll of each device at longer
intervals. This interval for this less frequent detailed polling can be adjusted on each individual device.
The Ridgeline software also gives you the ability to gather device status at any time using the Update
devices option under the View menu.
To avoid the overhead of frequent device polling, the Ridgeline software also uses a mechanism called
SmartTraps to identify changes in Extreme device configuration. In addition, standard SNMP MIB-2
traps can be used to define alarms for a large variety of other conditions.
SNMP and MIBs
Ridgeline uses SNMP whenever possible to obtain information about the devices it is managing, and to
implement the configuration changes made through Ridgeline.
Ridgeline Concepts and Solutions Guide
21

Ridgeline Overview
The Remote Monitoring (RMON) MIB
Ridgeline can use statistics gathered from the Remote Monitoring (RMON) MIB to provide utilization
statistics on a port-by-port basis, if RMON is supported and enabled on the Extreme devices Ridgeline
is managing. Utilization and error statistics can be displayed within the Real-Time Statistics application,
which provides a number of chart, graph, and tabular display formats. The Ridgeline Alarm Manager
also provides the ability to define threshold-based RMON rules for generating trap events that can be
used in Ridgeline alarm definitions.
Traps and Smart Traps
Fault detection is based on Simple Network Management Protocol (SNMP) traps, syslog messages, and
some limited polling. The Alarm System supports SNMP Management Information Base-2 (MIB-2), the
Extreme Networks private MIB, Remote Monitoring (RMON) traps, and selected traps from other MIBs.
The Ridgeline software uses a mechanism called SmartTraps to identify changes in Extreme device
configuration.
When an Extreme switch is added to the Ridgeline database, the Ridgeline software creates a set of
SmartTraps rules that define the configuration change events that the Ridgeline server needs to know
about. These rules are downloaded into the Extreme switch, and the Ridgeline server is automatically
registered as a trap receiver on the switch. Subsequently, whenever a status or configuration change
takes place, the ExtremeWare software on the switch uses the SmartTraps rules to determine if the
Ridgeline server should be notified. These changes can be changes in device status, such as fan failure
or overheating, or configuration changes made on the switch through the ExtremeWare CLI or
ExtremeWare Vista.
For non-Extreme devices, Ridgeline does not automatically register itself as a trap receiver; you must
manually configure those devices to send traps to Ridgeline. See “Configuring Devices for Use With
Ridgeline” on page 309 for information on configuring devices to send traps to Ridgeline.
Device Status Polling
Ridgeline uses several types of polling to monitor the status of the devices it manages. Since device
polling adds a certain amount of traffic load to the network, Ridgeline tries to minimize the amount of
polling that it does, and many aspects of its polling algorithms are configurable.
Ridgeline polls for basic device status approximately every five minutes using SNMP. This poll interval
can be changed in Ridgeline Administration under the Server Properties for SNMP. Ridgeline also polls
periodically for detailed device status information. By default, this interval is 30 minutes for Extreme
modular chassis switches, and 90 minutes for Extreme stackable chassis switches. The detailed polling
interval can be set for individual devices. The detailed polling gets more complete information, still
only polls for information that has changed; a manual Update Devices action is required to retrieve all
information about the device. An Update Devices action is performed automatically whenever the
Ridgeline client application is started.
Telnet Polling
When it is not possible to use SNMP to obtain information from Extreme devices, Ridgeline uses Telnet
polling instead. Ridgeline uses Telnet polling to obtain MAC address information for edge ports from a
device Forwarding Database (FDB) and to obtain netlogin information. Telnet polling is also used to
obtain power supply IDs for Alpine devices.
22
Ridgeline Concepts and Solutions Guide

Optionally, you can use SSH2 instead of Telnet to communicate with Extreme Networks devices. This
requires that you run a version of ExtremeWare or ExtremeXOS that supports SSH.
You can disable Telnet polling if necessary through the Server Properties for Devices in Ridgeline
Administration. However, you will lose the ability to collect edge port information via FDB polling, as
well as netlogin information.
Edge Port Polling Using the MAC Address Poller
Ridgeline can maintain information about the MAC and IP addresses detected on Extreme switch edge
ports by polling the FDB tables of the Extreme switches it is managing. If MAC address polling is
enabled, Ridgeline uses Telnet polling to retrieve FDB information at regular intervals based on the
settings of server properties in the Ridgeline Administration.
MAC address polling can be enabled or disabled globally. If enabled, it can then be disabled for
individual devices or for specific ports on devices.
Ridgeline distinguishes edge ports from trunk ports based on whether the port is running the Extreme
Discovery Protocol (EDP) or the Link layer Discovery Protocol (LLDP). Ridgeline assumes that ports
that run EDP or LLDP are trunk ports, and ports that do not run EDP or LLDP are edge ports.
However, trunk ports on non-Extreme devices that do not support EDP or LLDP may be identified
incorrectly as edge ports. You can disable MAC address polling on individual ports to prevent Ridgeline
from polling these trunk ports for MAC addresses.
1
Updating Device Status with the Ridgeline Database
A user with an appropriate role (a role with read/write access) can use the Update devices option
under the View menu to update the device status in the Ridgeline database when the user believes that
the device configuration or status is not correctly reported by Ridgeline. The Update Devices action
causes Ridgeline to poll the switch and update all configuration and status information except for
uploaded configuration files. The SmartTraps rules are also reset in case the user has accidentally
deleted the trap receiver or any SmartTrap rules.
Extreme Networks Device Support
Extreme Networks devices running the ExtremeXOS or ExtremeWare software (version 6.2 or later) are
supported by most features in Ridgeline. Some features, such as the EAPS monitoring function, require
more recent versions of the software. See the Ridgeline Release Notes for specific information about the
hardware and software versions supported by this release of the Ridgeline software.
Third-Party Device Support
Any device running a MIB-2 compatible SNMP agent can be discovered by Ridgeline, and saved in the
database. All devices in the database can also appear on a topology map. The Alarm Manager can
handle basic MIB-2 SNMP traps from any device in the database, including RMON traps from devices
with RMON enabled. The Statistics feature can display statistics for any device with RMON enabled.
Ridgeline’s third-party integration framework allows selected devices to be integrated into Ridgeline
with a higher level of functionality. Devices integrated through this framework may include devicespecific front and rear panel views, additional SNMP trap support, and the ability to launch external
applications from within Ridgeline, if appropriate.
Ridgeline Concepts and Solutions Guide
23

Ridgeline Overview
24
Ridgeline Concepts and Solutions Guide

Getting Started with Ridgeline
2
CHAPTER
This chapter covers how to use some of the basic features of the Ridgeline system:
● Starting Ridgeline
● How to get help
● Working with Ridgeline windows
● Ridgeline user roles
● Adding devices to Ridgeline
● Using Network Views
● Displaying device inventory information
● Viewing device properties
● Opening a Telnet session to a device from Ridgeline
● Managing device configurations and firmware
● Using the Ridgeline Alarm Manager
● Using Basic Reports
Starting Ridgeline
The Ridgeline software consists of a server component that runs on a Windows, Solaris or Red Hat
Enterprise Linux server, and a client component, which can be launched from a Web browser.
Once the Ridgeline server is running, multiple clients can connect to it. The Ridgeline software supports
multiple administrator users, with different roles that determine the Ridgeline functions each user can
perform.
This chapter assumes you have successfully installed (or upgraded to) the current Ridgeline software
version—version 3.0 or later—and that the Ridgeline server is running.
If you have not yet installed version 3.0, see the Ridgeline Installation and Upgrade Guide for instructions.
The Ridgeline Installation and Upgrade Guide is included in the Ridgeline product package along with the
Ridgeline software CD, and is also available in Adobe PDF format on the CD, and from the Extreme
Networks web site.
Ridgeline Concepts and Solutions Guide
25

Getting Started with Ridgeline
Starting the Ridgeline Server
The Ridgeline Server consists of two components:
● The Ridgeline Database Server
● The Ridgeline Server
Both components must be running in order to run the Ridgeline client.
In a Windows environment, the Ridgeline server components are installed as services. By default, the
two Ridgeline Server components will start automatically when you boot the server. At installation, you
can optionally specify that the components be started manually. If you chose this option, see the
Ridgeline Installation and Upgrade Guide for to instructions for starting the Ridgeline server components
manually.
Starting the Ridgeline Server in a Linux or Solaris Environment
To start the Ridgeline server, enter the following commands in the order shown:
/etc/init.d/RidgelineDB20 start
/etc/init.d/RidgelineServer20 start
You must have administrative rights to access init.d files.
Launching the Ridgeline Client
The Ridgeline Client initialization process makes use of Java Web Start technology. Java Web Start allows
you to obtain files necessary to run the Ridgeline Client directly from the Ridgeline Server by pointing a
browser to the Ridgeline Server and clicking on a hyperlink. The download and installation of the
Ridgeline software on the client system takes place automatically.
Each time you launch the Client, Ridgeline checks whether you have the most current version. If you do
not, Ridgeline automatically updates the client files on your system.
Client initialization using Java Web Start requires that the client system have a certain version of the
Java plug-in installed. If the client system does not have this required Java version, then you are
directed to a location where you can download the correct version.
The Ridgeline Client application can be launched on systems running one of the following operating
environments:
● Microsoft Windows Vista, Windows XP Professional with SP1 or later, or Windows 2003/2008
Server running on an Intel Pentium-compatible CPU
or
● Solaris 10
or
● Red Hat Enterprise Linux Version 5
A Ridgeline Client requires a monitor that supports 1024 x 768 resolution, and at least 16-bit color. Your
system display settings must be set for at least 65536 colors. See the Ridgeline Installation and Upgrade
Guide for memory, CPU, disk and other requirements.
26
Ridgeline Concepts and Solutions Guide
To launch the Ridgeline Client, you need to have the following information:
● The name or IP address of the Ridgeline Server to which the Client should connect
● The HTTP port that the Client uses to communicate with the server (the default is 8080). This is the
HTTP port you entered when you installed the Ridgeline Server.
To launch the Ridgeline Client, do the following:
1 Launch your web browser.
2 Enter the URL for your Ridgeline Server, in the form:
http://<host>:<port>/
Replace <host> with the name or IP address of the system where the Ridgeline Server is running.
Do not use
Replace
localhost as the host.
<port> with the TCP port number that you assigned to the Ridgeline web server during
installation.
NOTE
If you configured your Ridgeline Server to use the default web server port 80, you do not need to
include the port number. However, the port used by Ridgeline is 8080 by default, so in most cases you do need
to include the port.
2
3 The Ridgeline Welcome page appears.
Figure 2: Ridgeline Welcome Page
4 Click the Log on to Ridgeline link.
Ridgeline Concepts and Solutions Guide
27
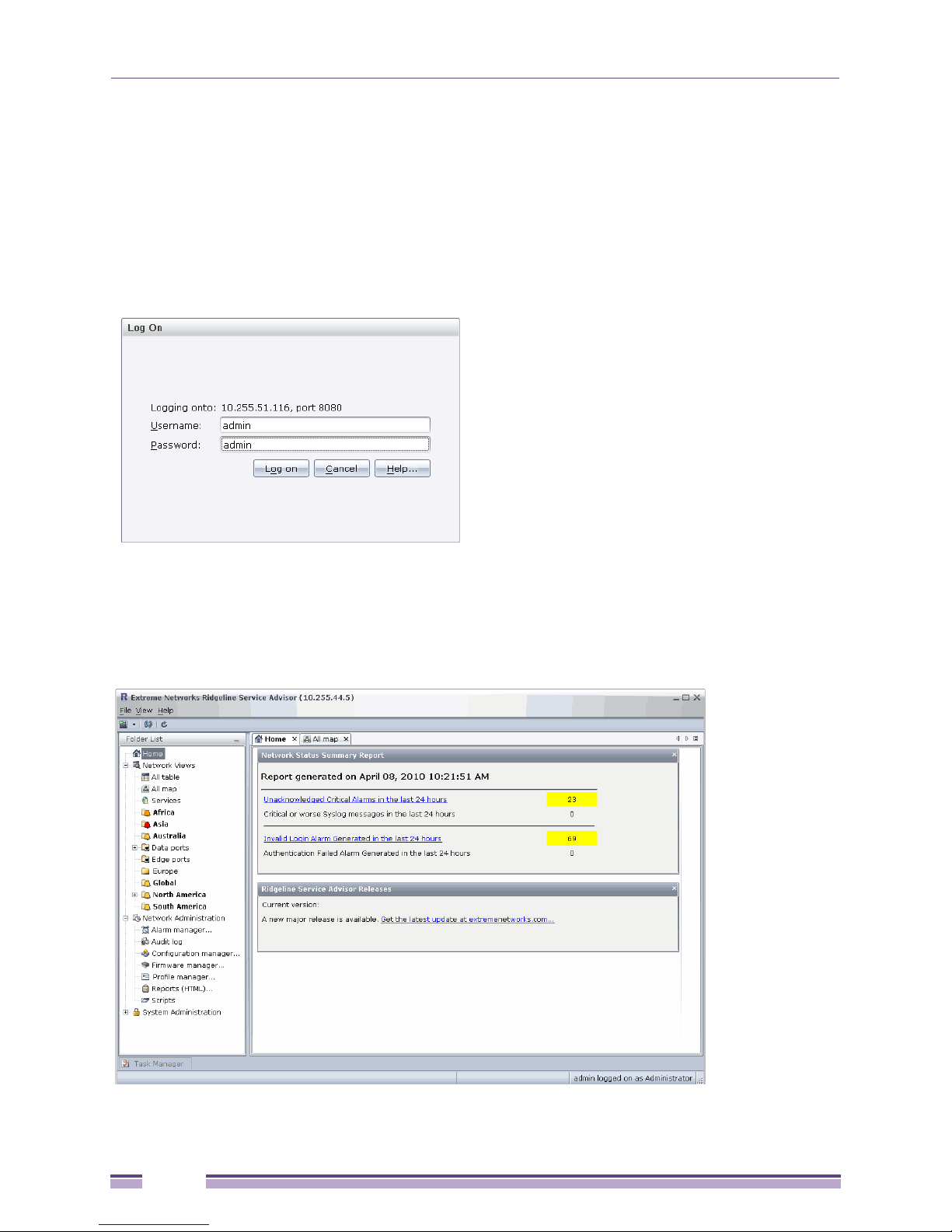
Getting Started with Ridgeline
5 Ridgeline checks if your system is running the correct version of the Java plug-in. If you are not
running the correct version, you are directed to a page where you can download the correct version.
If you are running the correct version of the Java plug-in, the Ridgeline Client software is
downloaded from the Ridgeline Server and installed on the local system.
6 After the software is downloaded, you are prompted whether you want to run the application. Click
Run to continue.
7 The Ridgeline Log On screen appears, and you are prompted for a username and password.
Figure 3: Ridgeline Log On Screen
8 If this is the first time you are logging in to Ridgeline, enter admin in both the Username field and
the Password field. Click Log on to connect to the Ridgeline server.
9 After a successful login, the Ridgeline 3.0 Home screen appears displaying the Network Summary
Report, as shown in Figure 4.
Figure 4: Ridgeline Home Screen
See “Ridgeline Reports” in the Ridgeline Reference Guide for an explanation of this report.
28
Ridgeline Concepts and Solutions Guide

Getting Help
This guide provides an overview of the Ridgeline software features with the goal of showing how you
can use Ridgeline to simplify your network management tasks and help you solve problems with your
network or its devices. It does not provide a detailed explanation of how to use the features of the
software.
For detailed help on specific features, Ridgeline provides context-sensitive online Help, accessible
through the Help menu located in the Ridgeline menu bar. From the Help menu, you can view HTMLbased help on the feature you are using, presented in a browser window.
In the Reports feature, there is a Help link in the introductory paragraph on the Main reports page.
From the Help menu, the Ridgeline Help selection displays the table of contents for the complete Help
system.
Ridgeline also provides the Ridgeline Reference Guide, which also describes how to use the Ridgeline
features. This guide can be accessed from the
directory. In the Windows environment this is
3.0\extreme.war\helptext\docs
Ridgeline3.0/extreme.war/helptext/docs
http://www.extremenetworks.com, under the Support area.
. In a Linux or Solaris environment this is /opt/ExtremeNetworks/
doc subdirectory under the Ridgeline installation
\Program Files\Extreme Networks\Ridgeline
. It can also be downloaded from the Extreme web site at
2
You must have a version of Adobe Acrobat Reader installed (version 4 or later) to view the PDF file.
(Acrobat Reader is available for download from Adobe Systems at
http://www.adobe.com.
Working with Ridgeline Windows
Windows in the Ridgeline user interface are made up of a number of frames. Figure 5 shows the
components that comprise a typical window in Ridgeline.
Ridgeline Concepts and Solutions Guide
29

Getting Started with Ridgeline
Figure 5: Components of the Ridgeline User Interface (Network Views Window)
Menu Bar Icon Bar
Folders
Navigation
Frame
Device Details FrameMap ViewTabbed Windows
Navigation Table
The main components of the Ridgeline user interface are the following:
Menu Bar Options and commands available in Ridgeline. The items shown in the menu bar vary
Icon Bar Icons for functions available in Ridgeline, based on the selected item. You can move
Navigation Frame Tree view of the of folders and subfolders in Ridgeline. You can click on items in the
Tabbed Windows When you click one of the main folders or a device group folder, it opens a tabbed
Navigation Table Table of information about the objects displayed in the selected folder. Selecting a
Details Frame Detailed information about the object selected in the Navigation Table.
Map View For a selected device group, the graphical representation of the devices and links in
based on the folder that is selected in the Navigation Frame.
your mouse over an icon to view text describing what the icon does.
Navigation Frame to show items lower in the hierarchy.
Ridgeline has four main folders: Home, Network Views, Network Administration, and
Administering Ridgeline. Clicking on a main folder reveals the subfolders below it. The
subfolders contain links to device groups and Ridgeline applications.
window for that folder above the Navigation Table. Tabbed windows are dockable,
meaning that they can be moved around in the main Ridgeline window. See “Moving
Tabbed Windows in Ridgeline” on page 32 for more information.
device in the Navigation Table displays detailed information about the selected device
in the Device Details Frame.
the group. Selecting a device in the Map View causes the corresponding row in the
Navigation Table to be selected.
30
Ridgeline Concepts and Solutions Guide

Modifying Table Views
Much of the information displayed in Ridgeline is in tabular format. You can sort the rows in a table,
modify the table column size, move columns around in a table, and remove columns from a table.
Sorting Table Rows
You can sort the rows of a columnar display according to the contents of any individual column. To
sort the rows, click on the column heading you want to use as the sort criteria. Click once to sort in
ascending order; click a second time to reverse the sort order.
The column that is currently being used as the sort criteria is indicated with a small triangle in the
column heading cell. The direction of the triangle (facing up or facing down) indicates whether the sort
is ascending or descending.
Resizing Table Columns
You can resize the widths of each column. To do this, follow these steps:
2
1 Place the cursor over the line separating the column you want to resize from the column to its right.
2 Click and hold the left mouse button to “grab” the column separator.
3 Drag the separator until the column is are the desired width.
Moving Table Columns
To move a column in a table, click and hold the left mouse button to “grab” the column heading, then
drag the column to where you want it to be in the table.
Removing Columns From a Table
To remove one or more columns from a table, follow these steps:
1 Click on the icon in the upper right corner of the table you want to modify. A window such as
the following appears:
Figure 6: Selecting Columns to Display in a Table
2 Uncheck the columns you want to remove from the table and click OK. Columns that cannot be
removed from the table are greyed out.
Ridgeline Concepts and Solutions Guide
31

Getting Started with Ridgeline
Moving Tabbed Windows in Ridgeline
Tabbed windows in Ridgeline are dockable, which means that you can move them to new locations in the
main Ridgeline window. To move a window to a new location, do the following:
1 Place the cursor over the tab of the window you want to move.
2 Click and hold the left mouse button to “grab” the window.
3 Drag the window to a new location.
4 Release the left mouse button.
5 At the prompt, indicate whether you want the window to be displayed horizontally or vertically.
Ridgeline User Roles
Ridgeline provides four pre-defined roles for levels of user access to the features of the product:
● The Administrator role provides full read/write access to all features of the product, including to
Ridgeline Administration, where the features of Ridgeline itself can be configured, and where users
can be added or deleted, and their roles modified.
● The Manager role provides full read/write access to all features of the product except for Ridgeline
Administration.
● The Monitor role provides read-only access to the features of the product—a user with a Monitor role
can view status and configuration information, but cannot do any configuration tasks.
● The Disabled role provides no access to any features of the product.
Every user created in Ridgeline is assigned a role which determines the access that user has to the
features of the product.
In Ridgeline, the administrator can also create additional roles with any combination of read-only, readwrite, or disabled access to different Ridgeline product features. In addition, for the Administrator,
Manager, and Monitor roles, access can be disabled on a feature-by-feature basis (except that access to
Ridgeline Administration is never disabled for the Administrator role).
A user’s role determines which features the user can access. A user whose role provides read-write
access to a feature can perform all the functions within that feature–both those that show status
information, and those that perform configuration operations, for example. A user whose role provides
read-only access will be able to view status and configuration information, but will not be able to
perform configuration operations or store information in the Ridgeline database.
Creating the Device Inventory
The first step in using Ridgeline is to collect information about the devices in the network to populate
the Ridgeline database. Ridgeline provides a discovery function that can automatically find and retrieve
information about the devices on your network. You can also add devices individually.
32
Ridgeline Concepts and Solutions Guide

Using Discovery
When you first install Ridgeline, the device inventory is empty. The easiest way to populate the
inventory database is to use the Discovery feature (select New > Discover device from the File menu)
to automatically detect the devices on your network. With Discovery you can:
● Search for devices by specific IP addresses or ranges of IP address, including using wildcard search
parameters to specify the IP address sets you want to query.
● Limit your search to Extreme devices only, or include all discovered MIB-2 devices regardless of
manufacturer
● Specify a search range using CIDR format
● Enable the discovery to use SNMPv3 in its search
Figure 7 shows an example of a discovery specification. You can add multiple address range
specifications to be executed in a single discovery operation.
Figure 7: Discovering devices to add to the Ridgeline inventory database
2
Note that you must provide the SNMP read community string to enable Ridgeline to get information
from the devices it finds. If your devices do not all use the same read community string, you will need
to add each set of devices as a separate specification, as shown in the example.
When you run the discovery, Ridgeline returns a list of all the devices it has found within the
parameters you provided, as shown in Figure 8.
It does not automatically add these devices to the Ridgeline inventory; you must select and add the
devices either individually or in groups.
Ridgeline Concepts and Solutions Guide
33

Getting Started with Ridgeline
Figure 8: Results of a discovery
To add devices to the database, select the set of devices you want to add and click the Add button.
For each device or set of devices you add to the inventory database, Ridgeline first asks you to provide
contact information for those devices:
● The device login name and password
● The SNMP write community string (for SNMP v1 devices)
● The protocol used for communicating with the device (HTTP or HTTPS)
● The User Name, Privacy and Authentication protocols and passwords for SNMP V3 devices
Ridgeline pops up a dialog box where you can provide this information. It pre-fills the fields with a
default set of communication information that you can change as appropriate to the specific devices you
are adding.
The information you provide in the pop-up dialog is used for all the devices in the set you have selected
to add. Therefore, if you have devices that use different passwords, protocols, or community strings,
you must add them to the database in separate Add operations.
Adding Devices Individually
There may be a number of situations in which you want to add an individual device to Ridgeline
without doing a discovery. In this case you can use the Add Device function to add a device to the
inventory. Select New > Device from the File menu.
Figure 7 shows an example of adding individual devices to Ridgeline. For each device you want to add,
enter the device’s IP address and click New.
34
Ridgeline Concepts and Solutions Guide

Figure 9: Adding Devices to Ridgeline Individually
2
Ridgeline pre-fills the fields in the window with the default communication information—you can
change it as appropriate.
Setting Up Default Device Contact Information
For simplicity in managing multiple devices in large networks, administrators typically use the same
logins, passwords, community strings and so on, for multiple devices. Therefore, to save time when
adding new devices, Ridgeline provides default values for these communication parameters.
To save time when you add your own network devices to the Ridgeline inventory, you can configure
the default values to those used in your own network.
To change the default communication values, select Default communications settings from the To o l s
menu.
Ridgeline uses the Extreme default values for its switches as the defaults in Ridgeline:
● Login as admin with no password
● SSH2 disabled
● For Cisco devices only, the default Cisco enable password (none)
● Default SNMP v1 community strings public (for read) and private (for write)
● SNMP V3 user initialmd5
● SNMP V3 privacy set to No Privacy, with no password
● SNMP V3 authentication set to MD5 Authentication, with password initialmd5
You can change any of these as appropriate for your network installation. You can also override the
defaults for any individual device or set of devices when you initially add the devices to Ridgeline, or
by selecting the device in Network Views and selecting Modify communications settings from the
Device menu.
Ridgeline Concepts and Solutions Guide
35

Getting Started with Ridgeline
Using Network Views
After you add devices to Ridgeline, they appear in Ridgeline Network Views. Network Views provide at-
a-glance displays of the devices, device groups, ports, and port groups in your network. You can view
summary information about the devices or ports, links between devices, VLANs, and EAPS domains,
and you can select individual devices in tables or maps to view detailed information about them.
Figure 10 shows an example of a Ridgeline Network Views display. Click the tabs to show separate
tables of information about devices, links, VLANs, and EAPS domains.
Figure 10: Displaying Information in Network Views
Click a row in the Navigation Table Information about the selected object
appears in the Details window
The table in a Network View window lists information about the device, port, or group selected in the
navigation frame. You can select one or more objects within the table to display additional information
about the selected object(s) in the details frame. If you double-click on the object in the table, Ridgeline
displays the details in a new window.
36
The devices where the object is
configured are highlighted on the map
Ridgeline Concepts and Solutions Guide

The table has the following tabs:
Devices Displays information about the devices in the device group. Clicking on a device in the
table displays additional information about the selected device in the details window,
and also highlights the device’s icon in the Map View.
Links Displays information about all of the links between the devices in the device group,
including automatically detected and user-defined links. Clicking on a link highlights the
link in the Map View.
VLANs Displays information about the VLANs configured on the devices in the device group.
Clicking on a VLAN in the table displays additional information about the selected
VLAN in the details window, and also displays in the Map View an overlay highlighting
all of the devices and links where the selected VLAN is configured.
Enable the “Show Full Path” checkbox to display the path a packet would take across
the various VLANs in the network, taking into consideration VLAN services configured
on the managed devices, such as subscriber VLANs, Private VLANs, and VMANs.
EAPS Displays information about all of the EAPS domains configured on the devices in the
device group. Clicking on a row in the table displays additional information about the
selected EAPS domain in the details window, and in the Map View provides an overlay
of the status of the devices and links in the EAPS domain.
In the Map View for a selected device group, the devices relevant to the object selected in the table are
highlighted in the map. For example, if you select a VLAN in the navigation table, all of the devices
where that VLAN is configured are highlighted in the Map View.
2
Figure 11: Viewing VLAN Information in Network Views
Ridgeline Concepts and Solutions Guide
37

Getting Started with Ridgeline
The status of items in Network Views is displayed graphically, with icons indicating the operational
condition of devices or ports, and lines indicating the state and traffic level of links between devices. A
bell icon shows the level of the highest alarm level for devices or groups.
Device Groups and Port Groups
Ridgeline’s grouping feature allows you to assemble your devices and ports into groups and subgroups
and view information about them or manage them at a group level.
For example, you can create a device group, “Main Campus”, consisting of devices in that location.
Within the “Main Campus” device group, you can create subgroups such as “Building 1”, “Building 2”,
and so on, and administer and view status of devices within the individual groups. You can create a
port group consisting of the voice-over-IP (VoIP) ports on all switches in your network, and monitor
status of the ports in the group.
In Network Views, device groups and port groups are represented with folder icons. If a group has
subgroups below it, you can click on the plus sign next to the group in the navigation frame to show
the group hierarchy, as shown in Figure 12.
Figure 12: Expanding a Device Group to Show the Hierarchy
The severity of highest level alarm for a group and its subgroups is indicated by the color of the bell on
the group’s folder icon.
See Chapter 3, “Organizing Devices and Ports Into Groups” for more information.
Map Views
Ridgeline’s network topology map feature allows you to view your network (Ridgeline-managed
devices and the links between devices) graphically, as a set of maps. These maps can be organized into
sets of submaps that allow you to represent your network as a hierarchical system of campuses,
buildings, floors, closets, or whatever logical groupings you want.
38
Ridgeline Concepts and Solutions Guide

Figure 13: Network Topology Map View
2
A network topology map is a graphical representation of a device group. In Network Views, you have
the option of selecting the Map View of the device group, which causes Ridgeline to generate a network
topology map, populated with the devices in the group. Ridgeline also adds any links that exist
between the device nodes, and organizes them into submaps as appropriate. You can customize the
resulting maps by moving elements, adding new elements, such as links, “decorative” (non-managed)
nodes, and text, and customizing the device nodes themselves.
You can customize the layouts of your maps into hierarchical views using copy and paste, or by
deleting devices from one map and then adding them to a different map. You can also add and remove
user-defined links between devices, as well as decorative nodes (nodes that aren’t discovered or
managed by Ridgeline). See Chapter 4, “Using Map Views” for more information
Displaying Device Inventory Information
The Device Inventory window shows an active graphical display of a device’s front panel, as well as a
panel of status information. For some devices, a back panel view may also be provided.
Ridgeline Concepts and Solutions Guide
39

Getting Started with Ridgeline
To display the Device Inventory for a device, click on the device’s row in the Devices table, then select
Inventory from the Device menu. This display shows additional information that Ridgeline has
gathered from the switch agent.
Figure 14: Device Inventory Window
You can click on the slots and ports in the Panel View to display additional information about the
selected item.
Viewing Device Properties
You can view the properties of a device in Ridgeline. The Device Properties window shows several tabs
of information about the selected device (see Figure 15). To display this window, select a device, then
select Properties from the File menu, or from the right-click pop-up menu.
40
Ridgeline Concepts and Solutions Guide

Figure 15: Device Properties window
2
The Device Properties window displays a set of tabs at the top of the window, depending on the type
and configuration of the device. The following tabs may appear:
● Device
● Network Clients
● Syslog Messages
Each tab displays the name of the device and a status “light” which shows the status of the device as
detected by the Ridgeline software. For details about the information displayed on these tabs, see the
Ridgeline Reference Guide or the online Help.
Opening a Telnet Session to a Device
You can open a Telnet session on an individual device, and execute commands just as you would from a
standard Telnet interface. You can optionally record the commands and output from a Telnet session
and save the results to a file.
For Extreme Networks devices, Ridgeline will automatically log into the switch based on the device
login name and contact password configured for the device in the Add Device window. For third-party
devices, you will need to provide the login and password interactively.
To open a Telnet session to a device, click on the device’s row in the Devices table (or select it in the
Map View, if available), then select Tel ne t i nt o from the Device menu. A Ridgeline Telnet window is
opened, and a Telnet session to the device is started, as shown in Figure 16.
Ridgeline Concepts and Solutions Guide
41

Getting Started with Ridgeline
Figure 16: Ridgeline Telnet Window
The Ridgeline Telnet window is a two-tone window—the bottom of the window is white, the top is
gray. The last 25 lines of Telnet commands and responses always appear in the white portion of the
window. As output grows, the older lines scroll up into the gray portion of the screen. This makes it
easy to tell whether you are viewing the most recent Telnet output.
To copy text in a Ridgeline Telnet window, select the text, then right-click and select Copy from the popup menu.
To paste text from the clipboard to the command prompt in the Ridgeline Telnet window, right-click
and select Paste from the pop-up menu.
To record the commands and output from a Telnet session, select Start Recording from the To ol s menu
in the Ridgeline Telnet window. You can also start recording by clicking the icon, or by right-clicking
and selecting Start Record from the pop-up menu.
To stop the recording, select Stop Recording from the To ol s menu in the Ridgeline Telnet window. You
can also start recording by clicking the icon, or by right-clicking and selecting Stop Record from the
pop-up menu. The recorded commands and output from the Telnet session are saved to a file on your
local system.
On Windows systems, the file saved in the following directory:
C:\Documents and Settings\<user>\.ridgeline\3.0\<server_ipaddr>\data\admin\telnet
On Solaris/Linux systems, the file saved in the following directory:
~<user>/.ridgeline/3.0/<server_ipaddr>/data/admin/telnet
42
Ridgeline Concepts and Solutions Guide

2
The file name is in the format
10_210_12_4-20090113-120302.txt
<device_ipaddr>-<date>-<time>.txt; for example:
Collecting Device Information for Extreme Support
You can log into a device from the server and run ExtremeXOS commands that collect information
about the device, save it to an archive and send it to the server’s TFTP directory. You can then log into
the server and get the archive.
To collect information about a device and copy it to the server TFTP directory, do the following:
1 From the Devices tab, select the device from which you want to collect data.
2 From the Device menu, select Telnet into. This option is also available from the right-click context
menu. A Telnet window into the device opens (Figure 16).
3 In the Telnet window, enter the show tech all logto file command. The following example shows the
command and the command messages:
BD-12804.1 # show tech all logto file
show tech command output is logging into internal-memory
...................................................
show tech command output file show_tech.log.gz is saved into internal-memory
BD-12804.2 #
4 Enter the command upload debug <IP_address> where <IP_address> is the address of the server.
When prompted to run the show tech logto file command, enter N. The following example shows
the command and command messages.
BD-12804.2 # upload debug 10.210.16.74
Do you want to run show tech logto file first? (y/N) No
..........................
The following files on the MASTER have been uploaded:
Tarball Name: BD-12804_AI_09081505.tgz
./show_tech.log.gz
./trace.devmgr.27844
./trace.nodemgr.27845
Tarball Name: BD-12804_AC_09081505.tgz
./epicenter.cfg
./mullai_torino.cfg
./primary.cfg
./secondary.cfg
./snapshot.cfg
./torino-0404.cfg
BD-12804.3 #
In this example, two .tgz archives are created: BD-12804_AI_09081505.tgz and BD12804_AC_09081505.tgz
5 On the server, verify the location of the TFTP folder by clicking To o l s > TFTP server configuration.
The Configure TFTP Server dialog (Figure 17) displays the path to the TFTP folder in the Set TFTP
Root field.
Ridgeline Concepts and Solutions Guide
43

Getting Started with Ridgeline
Figure 17: Configure TFTP Server
Use the cursor to scan the entire path to the TFTP directory. If the server uses the default system
TFTP server, the path is
/opt/ExtremeNetworks/RidgelineServiceAdvisor2.0EPICenter7.1_web/user.war/tftp.
Log into the server to retrieve the .tgz files using the protocol that the server requires, Telnet or SSH.
Managing Device Configurations and Firmware
Ridgeline provides two features that can help you manage the configuration files and the firmware
versions on your devices.
● The Configuration Manager provides an interface for uploading and saving backup configurations
from your devices. You can upload configuration files from your devices on an “as needed” basis, or
on a regular schedule. You can also save configuration files as “baseline” files for your devices, and
then compare those baselines against newly uploaded configuration files to determine if changes
have been made. The Configuration Manager also provides an interface you can use to download a
saved configuration to a device.
● The Firmware Manager helps you manage the versions of firmware installed on your devices.
Ridgeline will check the Extreme web site to find the most current versions of the device, slot and
bootROM software, and will download it to the Ridgeline server if you so choose. It can tell you if
the software on your devices is the most current versions, and can also manage the process of the
upgrading the images on your devices. Since there are multiple versions of software for different
device and module types, and the software images and BootROM versions must also be compatible,
the Firmware Manager can warn you if you attempt a download that may not be compatible with
the device you have selected.
Once you have added your devices to Ridgeline, it is a good idea to save a set of baseline configuration
files to use as a reference for identifying configuration changes to your devices. It is also a good idea to
set up a regular schedule for uploading configuration files for archiving.
Periodically it is also a good idea to check for newer releases of the software and BootROM images for
your Extreme devices. You can then download them to the Ridgeline server, where they will be
available for download to your devices when you decide to upgrade those devices.
See Chapter 18, “Managing Network Device Configurations and Updates” for more information.
44
Ridgeline Concepts and Solutions Guide

Using the Ridgeline Alarm Manager
The Ridgeline Alarm Manager provides fault detection and alarm handling for the network devices
monitored by Ridgeline. This includes Extreme devices as well as some third-party devices—those that
Ridgeline can include in its database.
The Alarm Manager provides a set of predefined, enabled alarms that will immediately report
conditions such as authentication or login failures, device problems such as power supply or fan
failures, reachability problems, or device reboots. You can also define your own alarms that will report
errors under conditions you specify, such as repeated occurrences or exceeding threshold values. You
can specify the actions that should be taken when an alarm occurs, and you can enable and disable
individual alarms.
Fault detection is based on SNMP traps, syslog messages, and some limited polling. The Alarm
Manager supports SNMP MIB-2, the Extreme Networks private MIBs, RMON traps, and selected traps
from other MIBs. When an alarm occurs you can specify actions such as sending e-mail, running a
program, running a script, sending a page or sounding an audible alert. You can also forward the trap
to another trap receiver.
To view alarms in Ridgeline, expand the list of folders under Network Administration, and click Alarm
Manager.
2
Predefined Alarms
For convenience, the Ridgeline Alarm Manager provides a number of predefined alarms. These alarms
are enabled by default and are active as soon as the Ridgeline server starts up. These include the
following alarms:
● Authentication failure (SNMP MIB-2 trap)
● Config Upload Failed (Ridgeline event, indicates failure in an upload initiated by Ridgeline)
● Device reboot (Ridgeline event)
● Device Warning from Ridgeline (Ridgeline event)
● ESRP State Changed (Extreme proprietary trap)
● Fan failure (Ridgeline event)
● Health Check Failed (Extreme proprietary trap)
● Invalid login (Extreme proprietary trap)
● Overheat (Ridgeline event)
● Power Supply Failed (Ridgeline event)
● Rogue Access Point Found (Ridgeline event)
● Redundant Power Supply (RPS) alarm condition (Extreme proprietary trap)
● SNMP unreachable (Ridgeline event)
NOTE
When Extreme Networks devices are added to the Ridgeline, they are automatically configured to send
traps to the Ridgeline server (unless you are running in non-intrusive Mode). To receive traps from non-Extreme
devices, you must manually configure those devices to send traps to the Ridgeline server. See “Configuring Devices
Ridgeline Concepts and Solutions Guide
45

Getting Started with Ridgeline
for Use With Ridgeline” on page 309 for information on registering Ridgeline as a trap receiver on non-Extreme
devices.
The Alarm Log Browser
You use the Alarm Log Browser to view a summary of the alarms that have occurred among the devices
you are managing. An alarm can be generated due to an SNMP or RMON trap, a syslog message, or
based on the results of a poll. By default, all the predefined alarms are enabled; therefore, you may see
alarm log entries the first time you display the Alarm Browser, even if you have not defined any alarms
of your own.
Figure 18: The Alarm Log Browser window
For more information on using the Ridgeline Alarm Manager, see the Ridgeline Reference Guide or the
online Help.
Using Basic Ridgeline Reports
Ridgeline provides a large number of reports based on the data in the Ridgeline database. The Network
Status Summary Report that appears when you first log into the Ridgeline client is one example of these
reports.
Ridgeline reports are displayed in HTML in a browser window, even if you are running the Ridgeline
client. You must have a browser installed on your system to be able to view reports. You can also view
46
Ridgeline Concepts and Solutions Guide

reports by logging directly into the Reports feature from a browser, without running the Ridgeline
client: just select the Log on to Reports only link from the Ridgeline Welcome page.
Figure 19 shows a few of the reports you can view through the Reports feature.
Figure 19: Examples of Ridgeline reports
2
Most reports can be sorted in a number of ways, and many reports can be filtered to display only the
data of interest, based on the types of information shown in the report. In addition, from some reports
the displayed data can be exported to files in formats (
applications for analysis or display.
Ridgeline Concepts and Solutions Guide
csv or xml) that can be imported into other
47

Getting Started with Ridgeline
In addition to the Network Summary Report, Ridgeline provides the following reports and tools:
Table 3: Ridgeline Reports
Report
Category
Main • Extreme eSupport Export Exports Ridgeline data for use by Extreme
Network
Summary
Report
Devices • Device Inventory Report
Slots, Stacks
and Ports
Report Name Description
technical support. Accessible from the Main reports
page.
• Network Summary Report Summary status of the network, as well as version
by Device Group and Device Type
By Device
Device Details
Power Over Ethernet
Power Over Ethernet Details
Wireless Ports
• ReachNXT Devices Status of ReachNXT devices connected to
• Device Status Report
by Device Group
By Device
Alarm Details
• Slot Inventory, by Card Type
Card Summary (by Card or All
Cards)
Device Details
Slot Details
Empty Slots Report
• Stack Inventory
Stack Summary
Device Details
Stack Details
and patch information about the Ridgeline server.
Shows status of distributed servers if Gold upgrade
is installed.
Overview of devices known to Ridgeline, by Device
Group. From this report you can access the Device
Details report, and additional subreports such as
PoE information and Wireless port information for
devices that support those features.
switches known to Ridgeline.
Status of devices by device group. From here you
can access status of individual devices (alarms, not
responding, for example) and can drill down to
Alarm Details
Inventory of cards (by type) installed in devices in
the Ridgeline database. The Card Summary Report
shows details about cards of a given type. From
there you can view details about the device hosting
the card. The Empty Slots report shows empty
slots by device.
Inventory of stacking devices. From this report you
can access Device Details for the stacking device,
or Stack Details.
• Interface Report Inventory of all ports on devices in the database
• Unused Port Report
By Device
EAPS • EAPS Summary Summary of EAPS domains known to Ridgeline
• EAPS Log EAPS-related Trap and Syslog entries for devices
Logs • Alarm Ridgeline alarm log (more information available
• Event Ridgeline event log entries
• Syslog Syslog entries
• Config Mgmt Log of configuration management actions (config
Summary of inactive ports by device including
location, with subreports (by device) showing
length of inactivity, VLAN membership etc.
configured for EAPS
through Alarm Log Browser feature)
file uploads/downloads) and results
Ridgeline Concepts and Solutions Guide
48

Table 3: Ridgeline Reports (continued)
2
Report
Category
Client
Reports
MIB Poller
Tools
Ridgeline
Server
Report Name Description
• Network Login List of network login activity by device
• Current Clients
Wireless Client History Report
• Client History Historical presentation of activity by wireless client
• Spoofed Clients
Device Details
Wireless Port Details
• Unconnected Clients List of wireless clients not in the data forwarding
• MIB Poller Summary Displays data in a MIB collection. Users with an
• MIB Query Provides an interface to query for the value of
• Server State Summary Shows a variety of status information about the
• Debug Ridgeline Tools to aid in analyzing Ridgeline performance.
List of all current wireless clients detected,
regardless of client state.
List of clients with the same MAC address detected
on different wireless interfaces. From here you can
view details on the device or interface reporting the
client.
state
Administrator role can start or stop a collection.
specific MIB variables. This is available only to
users with an Administrator role.
See “Tuning and Debugging Ridgeline” on
page 215 for more information.
Ridgeline server.
These are available only to users with an
Administrator role.
See “Tuning and Debugging Ridgeline” on
page 215 for more information.
See the Ridgeline online Help or the “Ridgeline Reports” chapter of the Ridgeline Reference Guide for
detailed information on what each of these reports shows.
Ridgeline Concepts and Solutions Guide
49

Getting Started with Ridgeline
50
Ridgeline Concepts and Solutions Guide

Organizing Devices and Ports
Into Groups
3
CHAPTER
This chapter describes how you can use the Ridgeline grouping feature to place devices and ports into
hierarchical groups.
About Ridgeline Groups
Ridgeline has a powerful grouping feature that allows you to assemble groups of devices and ports, and
view information about them or manage them at a group level.
The Ridgeline grouping feature allows you to do the following:
● Organize your devices and ports in a logical group structure
For example, you can create a device group, “Main Campus”, consisting of devices in that location.
Within the “Main Campus” device group, you can create subgroups such as “Building 1”, “Building
2”, and so on, and administer and view status of devices within the individual groups.
You can create a port group consisting of the voice-over-IP (VoIP) ports on all switches in your
network, and monitor status of the ports in the group.
● Establish the scope for performing operations in Ridgeline
Device and port groups are used in conjunction with other Ridgeline features, such as the Firmware
Manager and Profile Manager, to limit the display to just those devices in a specific group. For
example, if you want to use the Firmware Manager to upgrade the software images for just the
devices in the “Building 1” device group, you can display the contents of the Building 1 device
group in the Firmware Manager window, and select only the devices in the group for upgrade.
● View graphical representations of device groups
Ridgeline’s topology maps allow you to create diagrams of device groups in your network and
display information about them graphically.
See Chapter , “Using Map Views” for more information.
Displaying Groups in the Network Views Folder
To display the device groups and port groups in Ridgeline, expand the list of items in the Network
Views folder. Figure 20 shows the display for a device group.
Ridgeline Concepts and Solutions Guide
51

Organizing Devices and Ports Into Groups
Figure 20: Displaying a Device Group
Network Views Folder
“All” Device Group
Top-level Group
Subgroup
Group
Alarm
Status
Port
Group
Map
View of
Group
Table
View of
Group
The Network Views folder in the Ridgeline Navigation frame lists the device groups and port groups
defined in Ridgeline. By default, a single device group, All, contains all of the devices known to
Ridgeline.
Within the Network Views folder, you can create groups and subgroups and populate them with
devices from the All group. A top-level group can have multiple subgroups below it. The alarm status
for the group is indicated on the folder icon next to the group name.
Clicking a group in the Network Views folder shows information about the devices in the table view. In
the table view are tabs for displaying information about links between the devices, VLANs, and EAPS
configuration. Information in the table view can be exported to a Microsoft Excel spreadsheet.
The map view allows you to view a graphical representation of the devices in a top-level device group
and its subgroups, as well as the status of links between the devices. See Chapter , “Using Map Views”
for information about creating and using maps.
52
Ridgeline Concepts and Solutions Guide

Group Membership Guidelines
Groups can contain only one kind of object: ports cannot be members of device groups, and devices
cannot be members of port groups.
A given device or port can reside in multiple groups in the Network Views folder, but not within the
same top-level group hierarchy.
For example, you can create a top-level device group called “North America,” with a subgroup “Bay
Area” that has a subgroup “Santa Clara Campus”. If you place a given switch in the “Santa Clara
Campus” subgroup, you cannot also place the same switch in either of the “North America” or “Bay
Area” groups.
However, if you create a second top-level group called “EXOS Switches”, which is not a subgroup of
the “North America” group, you can place the switch in the “EXOS Switches” group, even though the
switch also resides in the “Santa Clara Campus” subgroup of the “North America” group.
Managing Device Groups and Port Groups
3
This section describes how to perform the following tasks:
● Create a group
● Add a device to a device group
● Add a port to a port group
● Copy or move groups
● Remove devices or ports from groups
● Modify the properties of a group
● Display detailed group information
● Export group information to a Microsoft Excel spreadsheet
Creating a Group
To create a group, do the following:
1 From the Ridgeline File menu, select New > Group. The New Group window is displayed, as
shown in Figure 21.
Ridgeline Concepts and Solutions Guide
53

Organizing Devices and Ports Into Groups
Figure 21: New Group Window
2 Enter the name and optional description for the new group
3 Click the appropriate radio button to specify whether this is a device or port group
4 Select the location in the Network Views hierarchy where the new group should be placed.
Highlight Network Views to make this a top-level group. If other top-level groups exist, highlight
one of them to make the new group a subgroup of the highlighted group. To make the new group a
subgroup of an existing subgroup, expand the list of groups and select a subgroup from the list.
5 Click OK to create the new group.
Adding a Device to a Device Group
To add a device to a device group, do the following:
1 Display the device in a table of devices.
One way to do this is to select the All view, then click the All devices button to show all devices.
2 Click the device to select it in the table
3 From the File menu, select Group > Copy to Group.
The Copy to group window is displayed, as shown in Figure 22. This window lists the device
groups that have been created in Ridgeline. By default, just the top-level groups are displayed. To
display the subgroups within a top-level group, click the plus sign next to the group name.
54
Ridgeline Concepts and Solutions Guide

Figure 22: Copy to Device Group Window
4 Select the group in which you want to place the device. Note that a device can be placed in a top-
level group hierarchy only once. See “Group Membership Guidelines” on page 53 for more
information.
5 Click OK to place the device in the selected group.
3
Adding Ports to a Port Group
The ports that make up a port group can be either from a single device or from multiple devices.
Adding Ports from a Single Device to a Port Group
If the port group will contain ports from a single device, do the following:
1 Display the device in a table of devices.
One way to do this is to select the All view, then click the All devices button to show all devices.
2 Right-click the device and select Open from the pop-up menu to display the device details window
for the selected device, as shown in Figure 23.
Ridgeline Concepts and Solutions Guide
55

Organizing Devices and Ports Into Groups
Figure 23: Device Details Window
3 The Device Details window lists all of the ports on the selected device. Select the ports you want to
add to the port group. Use Shift-Click to select a group of ports or Ctrl-Click to select individual
ports.
4 After selecting the ports, right-click and select Copy to group from the pop-up menu.
The Copy to group window is displayed, as shown in Figure 24. This window lists the port groups
that have been created in Ridgeline. By default, just the top-level groups are displayed. To display
the subgroups within a top-level group, click the plus sign next to the group name.
Figure 24: Copy to Port Group Window
5 Select the group in which you want to place the port(s). Note that a port can be placed in a top-level
group hierarchy only once. See “Group Membership Guidelines” on page 53 for more information.
6 Click OK to place the port(s) in the selected group.
56
Ridgeline Concepts and Solutions Guide

Adding Ports from Multiple Devices to a Port Group
If the port group will contain ports from multiple devices, do the following:
1 From the File menu, select Group > Add Ports to Port Group
The Add to Port Group window is displayed, as shown in Figure 25.
Figure 25: Add to Port Group Window
3
2 The Add to Port Group window lists the devices in the Ridgeline inventory. Click the All Devices
button to display all of the devices in inventory, or click the Device group button and specify one or
more device groups from the drop-down list.
3 Devices in the selected group (either all devices, or one or more device groups) are displayed in the
left column of the window. From the left column, select the devices that contain the ports that you
want to add to the port group, then double-click the device, or click the Right Arrow button, to
move the device to the right column
4 When all of the devices with ports you want to add to the port group are in the right column, click
the Next button to display the port selection window, as shown in Figure 26.
Ridgeline Concepts and Solutions Guide
57

Organizing Devices and Ports Into Groups
Figure 26: Port Selection Window
5 The port selection window lists all of the ports on all of the devices you selected in the Add to port
group window. Select the ports you want to add to the port group. You can use the Filter and Quick
Filter boxes to limit the number of ports displayed in the table. Use Shift-Click to select a group of
ports or Ctrl-Click to select individual ports.
6 After selecting the ports, click the Add Selected Port(s) to Group button.
The Copy to group window is displayed. This window lists the port groups that have been created
in Ridgeline. By default, just the top-level groups are displayed. To display the subgroups within a
top-level group, click the plus sign next to the group name.
7 Select the group in which you want to place the port(s). Note that a port can be placed in a top-level
group hierarchy only once. See “Group Membership Guidelines” on page 53 for more information.
8 Click OK to place the port(s) in the selected group.
Copying or Moving Groups
You can copy or move a device group into another device group, and copy or move a port group into
another port group. Note that device groups cannot be moved or copied into port groups, and port
groups cannot be moved or copied into device groups. Groups cannot be copied or moved to the root
(Network Views) group.
58
Ridgeline Concepts and Solutions Guide

To copy or move a group to another group, do the following:
1 In the Network Views folder, select the group you want to copy or move.
2 Right-click and select either Copy to group or Move to group from the pop-up menu.
A window is displayed listing the groups that have been created in Ridgeline. By default, just the
top-level groups are displayed. To display the subgroups within a top-level group, click the plus sign
next to the group name.
3 Highlight the destination group in which you want to copy or move the selected group, then click
the OK button.
The selected group is moved or copied to the destination group. If the copy or move operation
would result in a device or port being placed in a top-level group hierarchy more than once,
Ridgeline displays an error message, and the operation is cancelled.
Removing Devices or Ports from Groups
To remove a device or port from a group, do the following:
1 In the Network Views folder, select the group that contains the device or port you want to remove.
2 Select the device or port in the table.
3 From the Edit menu, select Delete.
Ridgeline prompts you for confirmation to delete the selected devices or ports. For a device, you can
elect to delete it from just the selected group or from all groups. If you delete a device from all
groups, it is removed from the Ridgeline inventory database.
3
Modifying the Properties of a Group
You can change the properties for a device group or port group, including the group name or
description.
To change the properties for a group, do the following:
1 In the Network Views folder, select the group whose properties you want to modify.
2 From the File menu, select Group > Properties to display the Properties window for the group, as
shown in Figure 27.
Ridgeline Concepts and Solutions Guide
59

Organizing Devices and Ports Into Groups
Figure 27: Properties Window for a Device Group
3 Add or change information in the Name or Description fields, and click OK to save the changes.
Displaying Group Details
To display details about a group, click on the group’s row in the Table View. Information about the
selected group appears in the details frame. If you double-click on the row, the device details are
displayed in a separate window, as shown in Figure 28.
60
Ridgeline Concepts and Solutions Guide

Figure 28: Group Details Window
3
Groups and subgroups within the hierarchy are indicated by a vertical bar (|) character between device
group names. For example, “North America | Bay Area” indicates a top-level group “North America”
with a subgroup “Bay Area”.
In addition, the display lists information the contents of the group, either ports or devices. You can use
the Filter and Quick Filter boxes to limit the contents of the table.
Exporting Group Information
You can export a Microsoft Excel spreadsheet containing information about the contents of a device
group or port group.
1 In the Network Views folder, select the group you want to export.
If necessary, use the Filter box to filter the list of devices or ports in the table.
2 Select Save as from the File menu.
Ridgeline Concepts and Solutions Guide
61

Organizing Devices and Ports Into Groups
Figure 29: Save As Window
3 Select whether to save the only the viewable data (that is, just the filtered data currently shown in
the table), or all data for all devices/ports in the group.
4 Click Browse and specify the location and name for the exported file.
5 Click Save to export the group information to the specified location.
62
Ridgeline Concepts and Solutions Guide

Using Map Views
4
CHAPTER
This chapter describes Ridgeline’s Map View feature and how you can use it to create graphical
representations of device groups in your network. It contains the following sections:
● “About Network Topology Maps” on page 63
● “Creating Maps” on page 69
About Network Topology Maps
In Ridgeline, a map view is a graphical representation of a specific device group or the All group. When
you create a device group, you have the option of selecting the Map view of the group, which causes
Ridgeline to generate a network topology map, populated with the devices in the group. Ridgeline also
adds any links that exist between the device nodes, and organizes them into submaps as appropriate.
You can customize the resulting maps by moving elements, adding new elements, such as links,
“decorative” (non-managed) nodes, and text, and customizing the device nodes themselves.
NOTE
Links can only be discovered and auto-populated between Extreme Networks devices that have the
Extreme Discovery Protocol (EDP) or the Link Layer Discovery Protocol (LLDP) enabled, or on third-party devices
with LLDP enabled. Links cannot be discovered on non-Extreme Networks devices that do not run LLDP, or on
Extreme Networks devices with EDP and LLDP disabled.
In addition, from a managed device node on a map, you can invoke other Ridgeline functions such as
the alarm browser, Telnet, real-time statistics, or view the device details window.
You can customize the layouts of your maps into hierarchical views using copy and paste, or by
deleting devices from one map and then adding them to a different map. You can also add and remove
user-defined links between devices, as well as decorative nodes (nodes that aren’t discovered or
managed by Ridgeline).
To display the topology map for a device group, select the device group in the Network Views folder
and click the Map tab. (Topology maps are not available for port groups.) If a topology map exists for
the group, then it appears in the Map view, as shown in Figure 30.
Ridgeline Concepts and Solutions Guide
63

Using Map Views
Figure 30: Map View of a Device Group
Network Views Folder
Device Group Map View
Group
Alarm
Status
Device
Node
Zoom Bar
Device Details
Link
Submap
Node
Navigation
Table
Navigation Box
The main components of an Ridgeline Map View are the following:
Device Group A set of devices that have been placed in an Ridgeline group hierarchy
In Ridgeline, you can create groups of ports and devices, although topology maps are
supported for device groups only. See Chapter 3, “Organizing Devices and Ports Into
Groups” for information about creating device groups.
A device group hierarchy has one top-level group and can have multiple levels of
subgroups below it. When a map is created, Ridgeline creates separate maps for the
top-level group, as well as for any subgroups.
Map View The graphical representation of the devices and links in the currently selected device
Navigation Table Table of information about the objects displayed in the Map View. Selecting a device in
group or subgroup. Selecting a device in the Map View causes the corresponding row
in the Navigation Table to be selected.
the Navigation Table causes the corresponding icon in the Map View to be selected,
and detailed information about the selected device to be displayed in the device details
window.
You can click on the tabs in the Navigation Table to display information about the
devices, links, VLANs, and EAPS rings in the device group.
64
Ridgeline Concepts and Solutions Guide

4
Alarm Status The highest level alarm currently unacknowledged among the devices in the current
Device Node Within the map view, an icon that represents a managed device in the device group.
Subgroup Node Within the map view, an icon that represents a subgroup of the currently displayed
Links Colored lines that represent connectivity between nodes in the map.
Navigation Box A box in the lower corner of the Map View that provides a thumbnail view of the
Zoom Bar Specifies the magnification level for the map. You can move the slider to zoom to one
Device Details Detailed information about the selected object.
map or any of its submaps. Devices and submaps within this map that have alarm
propagation disabled do not contribute to this status.
If the alarm icon has an “X” through it, this means alarm propagation has been
disabled for this map, and will not contribute to the alarm status of the next higher-level
map.
group.
topology map. Use the smaller box within the Navigation Box to move around a large
map. Click the arrow icon to display or hide the Navigation Box in the Map View.
of six magnification levels.
You can click on the tabs to display information about the ports, operational status,
links, VLANs, and EAPS rings for the selected device.
Map Elements
The following elements can appear on a map:
Device Nodes. Device nodes represent the managed devices found in the device group.
A device node shows the following information:
● The name of the device as it is kept in the Inventory database.
● An optional, user-supplied annotation for the node.
● A small icon representing the specific device or device product line. If the device is of an
“unknown” type, an unknown device icon (a circle with a question mark) is displayed.
● The device’s IP address.
● The device alarm status, indicated by the presence of an alarm icon (small bell). The alarm status
shows the highest level alarm currently unacknowledged for the device. The color of the bell
indicates the severity of the alarm.
If no icon appears, then either there are no unacknowledged alarms for the device, or the alarm
status is below the alarm status threshold for the view. The alarm status threshold is set in the
properties window for the map, and specifies the lowest severity level at which an alarm status icon
should be displayed for a device node on the map.
If the alarm icon has an “X” through it, this means alarm propagation has been disabled for this
device; the alarm status of this device does not influence the aggregate alarm status displayed for the
map in which this node is located.
● The device status, indicated by the icon.
- A red slash through the icon indicates that the device is down.
- A gray icon indicates that the device is offline.
- An icon without a red slash or gray color indicates that the device is up.
Ridgeline Concepts and Solutions Guide
65

Using Map Views
Subgroup Nodes. A subgroup node represents a child map of the current map. It resembles a folder
icon.
The subgroup node icon shows the following information:
● The name of the node (submap), which can be edited.
● The subgroup alarm status, indicated by the presence of an alarm icon (small bell). The alarm status
shows the highest level alarm currently unacknowledged for any device within the subgroup. If
multiple devices within the subgroup have unacknowledged alarms, the icon indicates the most
severe alarm among all those devices. The color of the bell indicates the severity of the alarm.
If the alarm icon has an “X” through it, this means alarm propagation has been disabled for this
subgroup; the alarm status of this subgroup does not influence the aggregate alarm status displayed
for higher level maps.
A subgroup node does not provide any additional status information.
Hyper Nodes. A hyper node represents a link termination where the terminating node is present in a
higher-level map or device group. A hyper node shows the same information as the device group it
represents. A hyper node can have links only between itself and other devices on the displayed map. A
hyper node does not link to other hyper nodes.
You can double-click on a hyper node icon to navigate directly to the map and the device group
represented by the hyper node.
A hyper node icon shows the following information:
● The name of the device group that this hyper node represents.
● An optional, user-supplied annotation for the hyper node.
● The alarm status, indicated by the presence of an alarm icon (small bell). The alarm status shows the
highest level alarm currently unacknowledged for the devices in the group. The color of the bell
indicates the severity of the alarm.
If no icon appears, then either there are no unacknowledged alarms for the device group, or the
alarm status is below the alarm status threshold for the view.
NOTE
You cannot add, cut, or delete hyper nodes; they are placed and removed automatically by Ridgeline as
required by device connectivity.
Decorative Nodes. A decorative map node can be created by the user to represent any other type of
node that is not discovered or managed by Ridgeline, such as a server or workstation. A decorative
node shows the name, description, and optional annotation of the node, which can be edited.
Text Nodes. A text map node is a single-line text field that can be placed anywhere in a network map.
It can be used to create a title for the map, additional annotations for other map elements, comments,
and so on.
Clouds. A cloud can be added to a map to represent a network. As with decorative nodes, you can
add name, description, and optional annotation to a cloud.
Links. A link represents connectivity between nodes in the map. Links are automatically detected on
Extreme Networks devices when EDP or LLDP is enabled on either device. Links can also be detected
on third-party devices that support LLDP. Links can also be user-created.
66
Ridgeline Concepts and Solutions Guide

NOTE
For devices with EDP and/or LLDP disabled or not supported, you can manually add user-defined links to
the map to represent connectivity between devices. They are not updated when the map topology changes. The
behavior of the system-discovered links described in the following paragraphs does not apply to user-defined links.
When a discovered link connects two devices on the same map, the link will be annotated with the port
number, or slot and port number for each of the endpoints.
When one of the endpoints is within a higher-level device group, a hyper node is used to represent the
higher-level device group that contains the endpoint.
If there are multiple links running between two devices, each link is shown individually as long as
there are 24 links or fewer. If 25 or more links connect two devices, they are represented as a composite
link. For a composite link, the link annotation provides the total number of links in the composite and
the number of links in each applicable status category (up, down, partially up, or unknown).
The appearance of a link shows a variety of information about the link.
The width of the link line indicates the link type:
● A thin line indicates a 10/100 link.
● A medium line indicates a gigabit link.
● A thick line indicates a 10 gigabit link.
● A very thick line indicates a composite link.
4
The color of the link line indicates the link status:
● A green line indicates that the link is up (both device ports are up).
● A red line indicates that the link is down (both device ports are down).
● A yellow line may be displayed for composite or load-shared links:
- For a composite link, yellow indicates that some of the links in the composite are up, and some
are down or unknown.
- For links that are members of a load shared group, yellow indicates that one or more load-shared
links are down. All links in the group will be displayed as yellow if one or more of the links in
the group is down.
● A blue line indicates a user-created link.
● A broken line indicates a down link.
The format of the link annotation indicates whether the link was created (discovered) automatically by
Ridgeline, or is a user-created link:
● If the endpoints in the link annotation are separated by a dash (p1:2 - p24) the link was created
automatically.
● If the endpoints in the annotation are separated by an “x” (p1:2 x p24) the link is a user-created
link. A user-created link may also have a “?” as the port, indicating an unknown port.
● If the ports on a device running ExtremeWare are load-shared, the endpoint is followed by an “s”
(
p17s - p24s) in the annotation.
● The management port is indicated by an “m” (p17 - p2m).
Ridgeline Concepts and Solutions Guide
67

Using Map Views
NOTE
Ridgeline does not support load sharing on devices running ExtremeXOS.
Navigating Maps
To move around in the map, you can do the following:
● Use the Zoom bar to zoom in or out of an area of the map
● Use the Navigation box to move to a section of a map
● Click in the Map view and drag so that the section appears in the display
Zooming In and Out on a Map
To zoom in the current map, do one of the following:
● Select Zoom in from the Map menu.
● Click the icon at the top of the zoom bar.
● Move the slider on the zoom bar upward.
To zoom out the current map, do one of the following:
● Select Zoom out from the Map menu.
● Click the icon at the bottom of the zoom bar.
● Move the slider on the zoom bar downward.
Using the Navigation Box
The navigation box is in the lower corner of the Map View, and provides a thumbnail view of the entire
map.
68
Ridgeline Concepts and Solutions Guide

Figure 31: Navigation Box in a Map View
Arrow Icon
Navigation
Box
4
Drag the smaller
box to move around
the map
Use the smaller box within the Navigation Box to move around a large map. Click the arrow icon to
display or hide the Navigation Box in the Map View.
Creating Maps
This section describes how to perform the following tasks:
● Creating a topology map for a device group
● Specifying properties for the topology map
● Laying out the topology map
● Creating user-defined links between devices
● Removing inactive links
● Adding graphic elements, such as decorative nodes, network clouds, and text boxes
● Adding an annotation to a device icon in a map
● Exporting a map to an SVG file
● Deleting the maps for a device group and subgroups
Ridgeline Concepts and Solutions Guide
69

Using Map Views
Creating a Map for a Device Group
Since a map is a graphical representation of a device group, the first step in creating a topology map is
to create a device group. See Chapter 3, “Organizing Devices and Ports Into Groups” for information
about creating device groups.
To create a topology map for a device group, do the following:
1 In the Network Views folder, select a device group. (Topology maps are not available for port
groups or the All group.)
2 Click the Map tab below the Table View of the device group. Ridgeline displays a blank map with a
prompt asking whether to create a map for the group.
3 Click Ye s to create the map. Depending on the number of devices and links in the device group, it
may take a few minutes for Ridgeline to generate the map.
When generating the map, Ridgeline creates an icon for each device, and automatically detects links
between Extreme Networks devices when EDP or LLDP is enabled on either device. Links can also
be detected on third-party devices that support LLDP.
Specifying Map Properties
Map properties include the alarm status that is displayed on the map, background image, the content of
the labels describing links, and the sizing of objects on the map.
● To specify properties for the currently displayed map, select Properties from the Map menu.
● To specify global properties for all maps, select Options from the To o l s menu.
The following window is displayed:
Figure 32: Map Properties Window
In the Information section of the window, you can specify the lowest severity level at which an alarm
status icon is displayed for a device node. In the map, the device’s alarm status is represented by an
70
Ridgeline Concepts and Solutions Guide

alarm icon (small bell). The alarm status shows the highest level alarm currently unacknowledged for
the device. The color of the bell indicates the severity of the alarm.
You can also specify how information is displayed for the devices on the map. Each kind of device
information (alarm status, device name, IP address, device annotation) can be shown with the device
icon at all zoom levels, not at all, or at relevant zoom levels. Showing the information at relevant zoom
levels (the default) means that each type of device information is shown at some zoom levels of the
map, and not at others. For example, by default a device’s IP address or alarm status is shown at zoom
level 4 and below; a device’s name and annotation is shown at zoom level 3 or below.
In the Background Image section, you can specify the filename of a graphic to be used as a background
image on the map. Ridgeline includes a number of sample background images, and you can add your
own. To add an image to the list of available background images, place it in the
<Ridgeline_install_dir>/extreme.war/gifs/topologyBackgroundImages directory.
In the Link Label section, you can indicate the text caption that appears on links. This can be either the
port numbers (for example, p1-p2), or the port number with the port name in parentheses.
In the Appearance section, you can specify the size of the text used in the captions for the map title,
objects, and links, as well as the background color of the map.
4
After specifying properties for the map, click Save changes to apply the new properties and close the
window. Click Restore global map settings to reset the map properties to the globally set values.
Laying Out the Map
You can drag map nodes around on the map yourself, or you can have Ridgeline lay out the map nodes
for you. To have Ridgeline do the map layout, select Auto layout from the Map menu.
The Auto layout function calculates a default map layout, optimizing for node and link placement to
minimize overlap. If necessary, Ridgeline may create a layout that is larger than the visible window
area. In this case, scroll bars allow you to view different parts of the map.
Creating User-Defined Links
Links represent connectivity between nodes in the map. When a map is created, links are automatically
detected on Extreme Networks devices when EDP or LLDP is enabled on either device. Links can also
be detected on third-party devices that support LLDP.
In addition to the automatically detected links, you can manually define your own links. This can be
useful in situations where you want to represent a link between devices when a “real” link cannot be
detected by Ridgeline. This may be the case if EDP and LLDP are disabled on an Extreme Networks
device, if a non-Extreme Networks device does not support LLDP, or if neither EDP or LLDP are
supported by the version of software running on the device.
On the map display, the endpoints of a user-defined link are separated by an “x” rather than by a dash
“-”. For example, the link annotation “p1:1 - p24“indicates an automatically detected link; the
annotation “p1:1 x p24” indicates a user-defined link.
Ridgeline Concepts and Solutions Guide
71

Using Map Views
To create a user-defined link, do the following:
1 Display the map for the device group by clicking on the Map tab at the bottom of the Ridgeline
window.
2 From the File or the Map menu, select New > Link, or select two devices and right-click in the map
view and select New > Link from the pop-up menu. The New Link window is displayed, as shown
in Figure 33.
Figure 33: New Link Window
3 The New Link window is divided into two sections, Side A and Side B, representing a device on
either end of the link. For each side of the link, do the following:
a From the Name list, select the device for this side of the link. The Name list contains the name
and IP address of each object in the device group.
b Optionally, from the Port number list, select a port on the device for the endpoint of the link. If
you enable the Show VLANs box, the VLANs that the selected port is a member of are displayed.
c As an alternative to selecting a port, you can specify a text annotation to describe this side of the
link on the map. To do this, click the Annotation button, and enter the text in the box.
4 When you have finished specifying both ends of the link, click OK to create the link on the map.
Removing Inactive Links from the Map
On a topology map, the color of the link line indicates the link status. A red line indicates that the link
is inactive (at least one of the ports that make up the link is down). You can remove the inactive links
from the map.
To remove the inactive links between two devices:
1 Select the two devices in the map view.
2 From the Map menu, select Clear inactive links from > Selected two devices.
Removing inactive links clears links that exist between the selected two devices in the currently
displayed map, as well as in any other device maps with inactive links between the two devices.
To remove the inactive links in the top-level group and subgroups of a device group:
1 Display the map view of the device group.
2 From the Map menu, select Clear inactive links from > Selected primary group and its subgroups.
72
Ridgeline Concepts and Solutions Guide

To remove the inactive links for all the devices in all device groups:
● From the Map menu, select Clear inactive links from > All devices.
Adding Graphic Elements to the Map
In addition to devices, links, and background images, you can add other graphic elements to the map to
represent objects not managed by Ridgeline. These elements include:
● Decorative Nodes. Decorative nodes represent any type of node that is not discovered or managed
by Ridgeline, such as a server or workstation.
To add a decorative node to your map, select New > Node from the File or the Map menu. The
following window is displayed:
Figure 34: New Node Window
4
In the New Node window, enter the name and optional description and annotation for the node,
and click Create node.
● Tex t B o x e s . Text boxes can be used to create a title for the map, additional annotations for other
map elements, comments, and so on.
To add a text box to your map, select New > Text box from the File or the Map menu. A new text
box with the words “Type here” is placed on the map. Double-click the text box and replace the
“Type here” text with your own text.
● Clouds. Clouds can be added to a map to represent a network.
To add a cloud to your map, select New > Cloud from the File or the Map menu. The following
window is displayed:
Figure 35: New Cloud Window
In the New Cloud window, enter the name and optional description and annotation for the cloud,
and click Create cloud.
To delete any of these graphic elements, select the object you want to delete, then select Delete from the
Edit menu, or right-click in the map view and select Delete from the pop-up menu.
Ridgeline Concepts and Solutions Guide
73

Using Map Views
Adding a Device Annotation
A device annotation is a single line of text that can be placed with a device icon enhance its description.
The device annotation, if configured, appears only with the device icon on the map; it does not appear
in any other view.
To add a device annotation, do the following:
1 Select the device in the map view.
2 From the Map menu, select Device annotation, or right-click the device in the map view and select
Device annotation from the pop-up menu. The Device annotation window is displayed, as shown in
Figure 33.
Figure 36: Device Annotation Window
3 In the text box, enter the annotation for the device.
4 Click Save changes to apply the annotation to the device and close the window.
Exporting Maps
You can export a Map view to a Scalable Vector Graphics (SVG) file that can be opened in a browser or
other application that supports the SVG format. Note that Microsoft Internet Explorer requires
installation of a plug-in to display SVG files.
To export a map to SVG format, do the following:
1 Display the map view that you want to export.
2 On the Ridgeline icon bar, click the Save as icon.
3 In the Save map as window, specify a name and location for the SVG file, then click Save.
74
Ridgeline Concepts and Solutions Guide

Deleting Maps
To delete the maps for a device group, do the following:
1 In the Ridgeline Administration folder, click Optimization. Ridgeline displays a table of the top-level
device groups that have topology maps defined, as shown in Figure 37.
Figure 37: Selecting Maps to Delete from the Optimization Folder
4
The table displays the name of each top-level group, the description (if one is configured), and the
number of maps in the group and subgroups.
2 Select a top-level group from the list and select Delete from the Edit menu.
Ridgeline prompts you for confirmation to delete the map.
3 Click Ye s to delete the map. When you do this, all of the maps for the selected top-level groups and
subgroups are deleted.
Ridgeline Concepts and Solutions Guide
75

Using Map Views
76
Ridgeline Concepts and Solutions Guide

Provisioning Network
Resources
5
CHAPTER
Ridgeline’s network resource provisioning feature simplifies network configuration tasks by allowing
you to specify devices, ports, and parameters using options in lists in dialog boxes. Ridgeline
automatically validates the options you’ve selected prior to deploying the configuration to managed
devices, ensuring that the configuration is correct before it goes into production.
Using Ridgeline provisioning windows, you can create a VLAN simply by selecting the devices, ports,
and tagging options you want, then validate and deploy the VLAN configuration by clicking a button.
You can provision the following kinds of network resources in Ridgeline:
● VLANs and vMANs. Using Ridgeline provisioning windows, you can create a VLAN or vMAN
simply by selecting the devices, ports, and tagging options you want, then validate and deploy the
VLAN or vMAN configuration by clicking a button.
● Backbone VLANs (BVLANs) for Provider Backbone Bridge (PBB) networks. Ridgeline’s
provisioning interface helps you configure a PBB network by facilitating the creation of BVLANs on
selected devices, ports, or links.
● E-Line and E-LAN services. Using the service provisioning wizard, you can create and modify E-
Line (point-to-point) and E-LAN (multipoint-to-multipoint) services. You can select the devices and
ports that make up the service, specify traffic mapping options, create and apply bandwidth profiles,
then validate the configuration and deploy it on your network.
● EAPS domains. You can use the EAPS provisioning feature to configure EAPS domains, including
specifying member links, the EAPS master node, primary and secondary ports, control VLAN, hello
timer, and fail timer parameters. Your configuration is validated by the software before it is
deployed to managed devices.
Provisioning Example
The following section illustrates how to use network resource provisioning to create a VLAN on devices
managed by Ridgeline. The procedure is generally similar for the other kinds of resources that Ridgeline
can provision. See the links above for specific information about provisioning each type of resource.
Creating a VLAN
To create a VLAN, do the following:
Ridgeline Concepts and Solutions Guide
77

Provisioning Network Resources
1 Under Network Views, select the folder containing the devices you want to configure.
2 In the Navigation Table, or the Map View (if displayed), click on the devices to select them. For a
VLAN, you can select one or more switches, links, or ports.
Figure 38: Selecting Devices to Provision
78
Ridgeline Concepts and Solutions Guide

3 From the Services menu, select New > VLAN, or right-click in the Navigation Table and select
VLAN from the pop-up menu. The VLAN Provisioning window is displayed, as shown in Figure 39.
Figure 39: VLAN Provisioning Window
5
In the VLAN provisioning window, the selected devices automatically appear in the Available
devices table. If the switch software running on a device does not support the feature you are
configuring, it is greyed-out in the Available devices table.
4 Click one of the devices to view the Available ports table for the device.
5 For each port you want to add to the VLAN, select the port and click the Add tagged or Add
untagged button.
6 Edit the values in the Tag and Name fields for the new VLAN.
7 When you have finished configuring the VLAN, click the Create VLAN button to start the validation
and deployment process. The Progress and Results window is displayed, as shown in Figure 40.
Ridgeline Concepts and Solutions Guide
79

Provisioning Network Resources
Figure 40: Progress and Results Window for VLAN Provisioning Tasks
Validating command syntax and
checking software compatibility
Verifying connectivity to the
selected devices
Deploying the commands on
the devices
Updating the device information
in the database
The validation rules or commands
entered on the device for the
selected task
8 Ridgeline validates the options you selected against a set of predefined configuration rules, and
ensures that the target switches are running a version of software that supports the features you are
provisioning.
If Ridgeline successfully validates the selected options, it verifies network connectivity to the target
switches. If a connection can be established to all of the target switches, Ridgeline deploys the
configuration commands, then saves the configuration file on each switch. Finally, Ridgeline updates
its own database with information about the configuration changes on the switches.
Modifying a VLAN
For existing VLANs, you can edit settings and deploy the changes to the devices where the VLAN is
configured.
To modify a VLAN, do the following:
1 Under Network Views, select the folder containing the devices you want to configure.
2 In the Navigation Table, click the VLAN tab, and select the VLAN you want to modify.
80
Ridgeline Concepts and Solutions Guide

3 Right-click in the Navigation Table and select the setting you want to modify from the pop-up
menu.
For a VLAN, you can edit the list of ports or links in the VLAN, as well as the name and network
name of the VLAN. You can also delete the VLAN from the devices where it is configured.
Figure 41: Selecting a VLAN to Modify
5
4 If you select Properties from the pop-up menu, the Properties window for the VLAN is displayed,
which provides a list of settings you can modify.
Ridgeline Concepts and Solutions Guide
81

Provisioning Network Resources
Figure 42: VLAN Properties Window
5 Click the setting you want to modify to bring up the provisioning window for that setting. For
example, Figure 43 shows the provisioning window for a VLAN port list.
Figure 43: Provisioning Window for a VLAN Port List
6 Make any necessary changes to the VLAN configuration.
7 When you have finished modifying the VLAN, click the Save changes button to validate and deploy
the changes to the VLAN.
82
Ridgeline Concepts and Solutions Guide

Troubleshooting for Provisioning Tasks
Ridgeline’s provisioning interface makes it easy to identify errors in network configuration and correct
them. You can click on any of the tasks in the Progress and Results window and display additional
information about the validation rules or CLI commands executed for the selected task.
If a validation task is unsuccessful, Ridgeline flags the task in the Progress and Results window. You can
click on the task to display additional information about why it was unsuccessful, as shown in
Figure 44. Click the Back button to return to the provisioning window and make any necessary
corrections, then re-deploy the configuration.
Figure 44: Unsuccessful Input Validation
5
Ridgeline handles errors encountered during the provisioning process in the following ways:
● If Ridgeline is not able to establish connectivity to one of the target switches, then it does not
proceed with the provisioning tasks on any of them.
● If commands that were validated by Ridgeline turn out not to be valid when actually deployed on
the switch, such as if the switch responds to a command with an error message, then Ridgeline rolls
back the commands that it had entered prior to the error, and halts the provisioning process.
● Any commands entered on the other target switches are automatically rolled back to what was in
the previous configuration.
● While the commands are being rolled back, if the switch goes offline (that is, becomes no longer
managed by Ridgeline), the commands continue to be rolled back until they have all been removed.
● If the device becomes unreachable, or it is not possible to log into the device to roll back the
commands, then the rollback process for the device fails, and Ridgeline displays an error message.
Ridgeline Concepts and Solutions Guide
83

Provisioning Network Resources
NOTE
Only one provisioning request can be processed on the Ridgeline server at a time. If you attempt to make
multiple provisioning requests at the same time, such as simultaneously from two different Ridgeline clients, an
error message is displayed.
Viewing Logged Information about Provisioning
Tasks
Ridgeline logs information about the provisioning tasks it has performed on managed devices. You can
view this information in the Ridgeline Audit Log.
To display the Audit Log, click on Audit Log under the Network Administration folder. The Audit Log
view is displayed, as shown in Figure 45. Click the Provisioning tab to view a table of the provisioning
tasks that have been run on the Ridgeline server.
In the Filters box, you can limit the display to the provisioning tasks that were run over a specified time
period, or that contain specified text in the table or the progress and results details window. Click a row
in the table to display the progress and results details for the selected provisioning task.
Figure 45: Ridgeline Audit Log for Provisioning Tasks
84
Ridgeline Concepts and Solutions Guide

You can double-click a row in the table to display the progress and results details in a separate window.
Figure 46: Audit Log Details Window for a Provisioning Task
5
See the Ridgeline Reference Guide for more information about the features of the Audit Log.
Ridgeline Concepts and Solutions Guide
85

Provisioning Network Resources
86
Ridgeline Concepts and Solutions Guide

Managing Ethernet Services
6
CHAPTER
An Ethernet service is a method for provisioning Ethernet connectivity over a wide-area or Metro
Ethernet network. Ethernet services can provide customers point-to-point or multipoint-to-multipoint
Ethernet connectivity across a service provider’s network.
Service providers set up Ethernet services for their customers at User Network Interface (UNI) ports
connecting customer equipment to their network. The actual means of transporting the customer traffic
across the service provider’s network is at the discretion of the service provider. A service provider can
configure an Ethernet service to use a specified VLAN, VMAN, or PBB BVLAN as the transport method
between the UNI ports to the customer network.
Using Ridgeline, you can create E-Line (point-to-point) and E-LAN (multipoint-to-multipoint) Ethernet
services. You can select the devices and ports that make up the service, specify traffic mapping options,
create and apply bandwidth profiles, then validate the configuration and deploy it on your network.
For Ethernet services using VLAN or VMAN transport methods, Ridgeline adds the UNI ports to the
transport VLAN/VMAN on the devices where it is configured. For Ethernet services using a PBB
BVLAN as the transport method, Ridgeline creates the SVLANs or CVLANs, maps an ISID to an
SVLAN, adds the UNI ports to the SVLAN, then adds the ISID to the BVLAN. Bandwidth profiles, if
specified in the Ethernet service configuration, are applied to the UNI ports.
Information about the Ethernet services known to Ridgeline is available in Network Views displays. The
Services view provides at-a-glance information about the Ethernet services, the devices and ports where
they are configured, and details about the transport method specified for each service.
E-Line Service
An E-Line service is a point-to-point Ethernet Virtual Connection (EVC) that can be implemented in a
service provider network, as illustrated in Figure 47. E-Line services can be created to support Ethernet
Private Line (EPL) and Ethernet Virtual Private Line (EVPL) services.
In an E-Line service, two UNI ports connected to customer equipment (CE) devices form the endpoints
for the service. Customer traffic entering the service provider network at one UNI port is associated
with the EVC. The UNI ports are associated with each other so that customer traffic in the E-Line
service is exchanged only between the two UNI ports.
Ridgeline Concepts and Solutions Guide
87

Managing Ethernet Services
Figure 47: E-Line Service
UNI Port UNI Port
E-Line Service
(Point-to-Point)
Customer
Equipment
Transport Method
Can be VLAN / VMAN / BVLAN
Service Provider Network
Customer
Equipment
When Ridgeline provisions an E-Line service, it also adds the VLAN, VMAN, or PBB BVLAN to an
EAPS domain on the devices where the VLAN/VMAN/BVLAN is configured.
E-LAN Service
An E-LAN service is a multipoint-to-multipoint EVC, as illustrated in Figure 48. An E-LAN service can
have two or more UNI ports connected to CE devices. E-LAN services can be created to support
Ethernet Private LAN (EP-LAN) and Ethernet Virtual Private LAN (EVP-LAN) services.
Figure 48: E-LAN Service
E-LAN Service
(Multipoint-to-Multipoint)
UNI Port
Customer
Equipment
UNI Port
88
UNI Port
Transport Method
Can be VLAN / VMAN / BVLAN
Service Provider Network
Ridgeline Concepts and Solutions Guide
Customer
Equipment
UNI Port

Bandwidth Profiles
By default, an E-Line or E-LAN service provides best-effort service for customer traffic on the UNI
ports. In some cases, such as when the UNI ports in an Ethernet service have different line rates, you
can specify bandwidth profiles and apply them to the UNI ports.
A bandwidth profile can specify values for Committed Information Rate (CIR), Committed Burst Size
(CBS), Excess Information Rate (EIR), Excess Burst Size (EBS), and single/dual-rate profile settings. You
can apply bandwidth profiles to all UNI ports in the service, or to selected UNI ports.
Configuring Ethernet Services
Using Ridgeline, you can perform the following Ethernet service configuration tasks:
● Create an Ethernet service
● Modify settings for Ethernet services
● Create and assign customer names to services
● Create and apply bandwidth profiles
6
For more information on Ridgeline’s network resource provisioning feature, see “Provisioning Network
Resources” on page 77.
Creating an Ethernet Service
To create an Ethernet service, do the following:
1 Under Network Views, from the Services menu, select New > E-Line service or E-LAN service. This
starts the Service Provisioning wizard. The window in Figure 49 displays.
Ridgeline Concepts and Solutions Guide
89

Managing Ethernet Services
Figure 49: E-Line Service Provisioning Window
2 Enter a name for the new E-Line or E-LAN service.
3 Optionally, enter a description for the service.
4 Select the customer who will be using this service. See “Creating a Customer Profile” on page 95 for
information about adding a customer to this list.
5 Select the transport type to be used with this service: 802.1Q (VLAN), 802.1ad (PB/VMAN), or
802.1ah (PBB).
6 Select the UNI ports for this service. An E-Line service must consist of 2 UNI ports. An E-LAN
service can have 2 or more UNI ports.
Devices that do not support Ethernet services are greyed-out in the service provisioning window.
You can expand the list of items in the Available devices table by selecting a group from the Show
devices in box.
7 Click Next to display the traffic mapping options for the service.
90
Ridgeline Concepts and Solutions Guide

Figure 50: Traffic Mapping Options for an Ethernet service (VLAN or VMAN Transport Type)
6
Ridgeline Concepts and Solutions Guide
91

Managing Ethernet Services
Figure 51: Traffic Mapping Options for an Ethernet service (PBB BVLAN Transport Type)
8 In the Traffic Mapping box, select the VLAN, VMAN, or BVLAN that will be used as the transport
method for the service. Ridgeline automatically populates the list box with the available VLANs,
VMANs, or BVLANs.
● For VLANs, specify whether traffic is tagged or untagged for both UNI ports, or for a selected
UNI port.
● For BVLANs, specify the ISID and ISID name, and the name and tag of the VLAN (for port-based
services), SVLAN, or CVLAN.
9 Optionally specify a bandwidth profile to use one or more ports in the service. See “Creating a
Bandwidth Profile” on page 96 for information on setting up bandwidth profiles. (If the transport
method is a BVLAN, bandwidth profile selection is on the following screen.)
10 Indicate whether to enable the service after it has been provisioned on the target devices.
11 By default, Ridgeline validates the settings you selected for the Ethernet service, then gives you the
option to deploy the service on the target devices.
If you want to deploy the service immediately after successful validation, without a separate
deployment step, check the box next to “If validation has no errors, continue automatically to
creating the new service.”
12 When you have finished configuring the Ethernet service, click the Validate button to start the
validation process. (If the transport method is a BVLAN, click Next to specify bandwidth profile
settings, then click Val i d a te .)
92
Ridgeline Concepts and Solutions Guide

Figure 52: Validation Window for an Ethernet Service
6
13 If the validation is successful, click Create Ethernet Service to deploy the service to the target
devices. Otherwise, click Back to go back to the previous screen and modify the settings.
Ridgeline Concepts and Solutions Guide
93

Managing Ethernet Services
Figure 53: Provisioning Window for an Ethernet Service
14 After Ridgeline successfully validates the selected options, it verifies network connectivity to the
target switches. If a connection can be established to all of the target switches, Ridgeline deploys the
configuration commands, then saves the configuration file on each switch. Finally, Ridgeline updates
its own database with information about the configuration changes on the switches.
The information in the Provisioning window is logged in the Ridgeline Audit Log. See “Viewing
Logged Information about Provisioning Tasks” on page 84 for more information.
Modifying an Ethernet Service
For existing E-Line and E-LAN services, you can edit settings and deploy the changes to the devices
where the service is configured.
To modify an Ethernet service, do the following:
1 Under Network Views, select the Services view.
2 In the Services table, select the Ethernet service you want to modify, right-click, and select the setting
you want to modify from the pop-up menu.
For an Ethernet service, you can edit the name and description of the service, the customer the
service is assigned to, bandwidth profile settings, and the UNI ports specified for the service.
Ridgeline Concepts and Solutions Guide
94

3 If you select Properties from the pop-up menu, the Properties window for the Ethernet service is
displayed, which provides a list of settings you can modify.
Figure 54: Ethernet Service Properties Window
6
4 Click the setting you want to modify to bring up the provisioning box for that setting. For example,
Figure 55 shows the provisioning box for the Ethernet service name and description.
Figure 55: Provisioning Window for Ethernet Service Name and Description
5 Make any necessary changes to the settings, then click the Save button to validate and deploy the
changes.
Creating a Customer Profile
When configuring an Ethernet service in Ridgeline, you can associate the service with a specific
customer profile. The name of the customer associated with an Ethernet service appears in Network
Views tables and in the Services view.
To create a customer profile and associate it with an Ethernet service, do the following:
1 Open the Customer Profile configuration window. You can do this when creating the service by
selecting New Customer from the Customer list in the Ethernet service provisioning window.
You can also right-click an existing service in a Network Views table, and select Edit customer from
the pop-up menu, or open the Properties page for a service and click the Edit customer button, or
select Customer Name from the To o ls menu.
Ridgeline Concepts and Solutions Guide
95

Managing Ethernet Services
Figure 56: Customer Profile Configuration Window
2 Click New to create a new customer profile, or select an existing profile and click Edit.
Figure 57: Customer Settings Window
3 In the Customer Settings window, enter a name for the customer, and optionally specify a
description, address, contact, and fax number. When you are done, click Add (for a new customer
profile) or Modify (for an existing customer profile).
4 After you create a customer profile, you can apply it to an Ethernet service. See “Modifying an
Ethernet Service” on page 94.
Creating a Bandwidth Profile
A bandwidth profile compares traffic received on a UNI port with a series of thresholds, and specifies
how the traffic should be forwarded based on those thresholds. A bandwidth profile can specify perport thresholds for Committed Information Rate (CIR), Committed Burst Size (CBS), Excess Information
Rate (EIR), and Excess Burst Size (EBS), as well as single/dual-rate profile settings. You can apply
bandwidth profiles to all UNI ports in an Ethernet service, or to selected UNI ports.
To create a bandwidth profile, do the following:
1 Open the Bandwidth Profile configuration window. You can do this when creating the service by
selecting New profile from the Bandwidth profile list in the Traffic mapping options window.
You can also right-click an existing service in a Network Views table, and select Edit bandwidth
profile from the pop-up menu, or open the Properties page for a service and click the Edit customer
button, then select New profile from the Bandwidth profile list, or select Bandwidth Profile from
the To o l s menu.
96
Ridgeline Concepts and Solutions Guide

Figure 58: Bandwidth Profile Configuration Window
2 Click New to create a new bandwidth profile, or select an existing profile and click Edit.
6
Figure 59: Bandwidth Profile Settings Window
3 In the Bandwidth Profile Settings window, enter a name for the bandwidth profile, and specify
settings for the following parameters:
Quality Profile (QP)
Single/Dual Rate
Committed Information Rate (CIR) The average rate for service traffic up to which the network delivers the
service traffic and is committed to meeting the performance objectives
defined by the CoS Service Attribute.
You can specify the CIR in Kbps, Mbps, or Gbps.
Committed Burst Size (CBS) The maximum allowed size for a burst of service traffic sent at the UNI
Excess Information Rate (EIR) The average rate of service traffic up to which the network may deliver
Excess Burst Size (EBS) The maximum size of a burst of service traffic sent at the UNI speed to
speed to remain CIR-conformant.
You can specify the CBS in Kb, Mb, or Gb.
service traffic but without any performance objectives.
You can specify the EIR in Kbps, Mbps, or Gbps.
remain EIR-conformant.
You can specify the EBS in Kb, Mb, or Gb.
Ridgeline Concepts and Solutions Guide
97

Managing Ethernet Services
4 When you are done, click Add (for a new bandwidth profile) or Modify (for an existing bandwidth
profile).
5 After you create a bandwidth profile, you can apply it to the UNI ports in Ethernet services. See
“Modifying an Ethernet Service” on page 94.
Viewing Ethernet Services Information
You can display information about E-Line and E-LAN services from the All map or All table, or from the
Services view under Network Views.
Using the All Table and All Map View
To view information about the E-Line and E-LAN services known to Ridgeline, click a device group or
the All map or All table group under the Network Views folder, then click the Services tab. A table listing
the E-Line and E-LAN services in the group is displayed, as shown in Figure 60.
Figure 60: Services Table in Network Views
If you also have enabled the map view of a device group, you can select a row in the table and display
an overlay view highlighting all of the devices and UNI ports in the map where the selected E-Line or
E-LAN service is configured, as shown in Figure 60.
98
Ridgeline Concepts and Solutions Guide
 Loading...
Loading...