Extreme Networks Policy, Policy Manager Supervisor Edition 1.2 Manager User Manual

Extreme Networks Policy Manager (EPM)
Supervisor Edition - User Guide
Version 1.2
Extreme Networks, Inc.
3585 Monroe Street
Santa Clara, California 95051
(888) 257-3000
(408) 579-2800
http://www.extremenetworks.com
Published: November 2007
Part number: 100260-00 Rev 04

AccessAdapt, Alpine, BlackDiamond, EPICenter, ESRP, Ethernet Everywhere, Extreme Enabled, Extreme Ethernet
Everywhere, Extreme Networks, Extreme Standby Router Protocol, Extreme Turbodrive, Extreme Velocity,
ExtremeWare, ExtremeWorks, ExtremeXOS, the Go Purple Extreme Solution, ScreenPlay, Sentriant, ServiceWatch,
Summit, SummitStack, Unified Access Architecture, Unified Access RF Manager, UniStack, UniStack Stacking, the
Extreme Networks logo, the Alpine logo, the BlackDiamond logo, the Extreme Turbodrive logo, the Summit logos,
the Powered by ExtremeXOS logo, and the Color Purple, among others, are trademarks or registered trademarks of
Extreme Networks, Inc. or its subsidiaries in the United States and/or other countries.
Adobe, Flash, and Macromedia are registered trademarks of Adobe Systems Incorporated in the U.S. and/or other
countries. AutoCell is a trademark of AutoCell. Avaya is a trademark of Avaya, Inc. Merit is a registered trademark
of Merit Network, Inc. Internet Explorer is a registered trademark of Microsoft Corporation. Mozilla Firefox is a
registered trademark of the Mozilla Foundation. sFlow is a registered trademark of sFlow.org. Solaris and Java are
trademarks of Sun Microsystems, Inc. in the U.S. and other countries.
Specifications are subject to change without notice.
All other registered trademarks, trademarks, and service marks are property of their respective owners.
© 2007 Extreme Networks, Inc. All Rights Reserved.
2
Extreme Networks Policy Manager (EPM)

Table of Contents
Preface........................................................................................................................................... 7
Introduction ...............................................................................................................................7
Conventions................................................................................................................................7
Related Publications ...................................................................................................................8
Chapter 1: Overview ........................................................................................................................ 9
Introduction ...............................................................................................................................9
Description of the Extreme Networks Policy Manager ......................................................................9
About This Manual ....................................................................................................................10
Editions of the EPM ..................................................................................................................10
Chapter 2: Installing The Extreme Networks Policy Manager............................................................ 11
Introduction .............................................................................................................................11
Hardware and Software Requirements .........................................................................................11
Switch Requirements ................................................................................................................11
EPM Installation .......................................................................................................................13
Chapter 3: Viewing Policies and Rules ...........................................................................................15
Introduction .............................................................................................................................15
Opening the EPM......................................................................................................................15
Configuring the EPM for use on a Switch.....................................................................................18
Description of the Windows and Menus .......................................................................................20
The EPM Desktop................................................................................................................20
Menu Bar .....................................................................................................................21
Toolbar.........................................................................................................................23
Status Panel .................................................................................................................23
Status Bar ....................................................................................................................25
Rule Editor Window.............................................................................................................26
Hide and Show the Panels .............................................................................................26
Tree Structure Panel......................................................................................................27
Rule Editing and Viewing Panel ......................................................................................27
Rule Properties Panel ....................................................................................................28
Rule Parameters Tab ...............................................................................................28
Rule Information Tab...............................................................................................28
Rule Navigator Window ........................................................................................................29
Opening an Existing Policy.........................................................................................................30
Opening a Policy File Locally................................................................................................30
Opening a Policy File from a Switch ......................................................................................31
Policy Parsing .....................................................................................................................32
Searching for Rules in a Policy ...................................................................................................33
Search by Name............................................................................................................33
Search by Parameter .....................................................................................................34
Working Among the Windows and Panels.....................................................................................36
Extreme Networks Policy Manager (EPM) 1.2 User Guide
3
3

Table of Contents
Chapter 4: Creating Policies and Rules........................................................................................... 37
Introduction .............................................................................................................................37
Creating a New Policy................................................................................................................37
Creating a New Rule for a Policy.................................................................................................37
Saving a Policy .........................................................................................................................39
Validating and Checking a Policy ................................................................................................40
Importing and Exporting Rules into a Policy.................................................................................41
Importing Rules ..................................................................................................................41
Exporting Rules...................................................................................................................42
Chapter 5: Modifying Policies and Rules ........................................................................................ 43
Introduction .............................................................................................................................43
Marking Rules ..........................................................................................................................44
Adding and Deleting Rules in a Policy .........................................................................................44
Adding Rules ......................................................................................................................44
Deleting Rules ....................................................................................................................44
Modifying Rules ........................................................................................................................45
Renaming a Rule ................................................................................................................45
Reclassifying a Rule ............................................................................................................45
Changing Rule Parameters ...................................................................................................46
Applying Changes to an Activated Policy..........................................................................47
Managing Global and Policy Variables .........................................................................................48
Organizing Rules.......................................................................................................................49
Deleting Policies .......................................................................................................................49
Managing Policy Activity ............................................................................................................50
Activating and Deactivating a Policy......................................................................................50
Disabling a Rule..................................................................................................................52
Chapter 6: Running Extreme Networks Policy Manager Examples..................................................... 53
Introduction .............................................................................................................................53
Example 1—Example_TCP_Threshold.pol....................................................................................53
Open and View the Policy.....................................................................................................53
Save to a Switch .................................................................................................................54
Activate the Policy on a Port.................................................................................................55
Modify Rule Parameters.......................................................................................................57
Example 2—Example_TCP_UDP_Balance.pol ..............................................................................58
Open and View the Policy.....................................................................................................58
Search for a Rule ................................................................................................................59
Incorporate into a Policy ......................................................................................................61
Appendix A: Help Messages.......................................................................................................... 63
Introduction .............................................................................................................................63
Predefined CLEAR-Flow System Counters ....................................................................................63
Synonyms used for Rule Constants ............................................................................................65
Type Selection Panel .................................................................................................................68
Match Condition Selection Panel ................................................................................................69
Action Modifier Selection Panel..................................................................................................70
True Action Selection Panel .......................................................................................................75
4
Extreme Networks Policy Manager (EPM) 1.2 User Guide

Table of Contents
Match Condition Selection Panel ................................................................................................75
Appendix B: Troubleshooting ......................................................................................................... 77
Introduction .............................................................................................................................77
Connectivity Problems ...............................................................................................................77
EXOS Compatibility Problems.....................................................................................................77
Local Client Runtime Problems ..................................................................................................78
Rule and Policy Version Problems...............................................................................................78
SSH Problems ..........................................................................................................................78
Index ............................................................................................................................................ 79
Extreme Networks Policy Manager (EPM) 1.2 User Guide
5Extreme Networks Policy Manager (EPM) 1.2 User Guide
5

Table of Contents
6
Extreme Networks Policy Manager (EPM) 1.2 User Guide
Preface
This preface introduces this user guide, describes guide conventions, and lists other useful publications.
Introduction
This guide provides the required information to use the Extreme Networks Policy Manager (EPM) Supervisor Edition software. It is intended for use by network administrators who are responsible for
monitoring and managing Local Area Networks and assumes a basic working knowledge of:
● Local Area Networks (LANs)
● Ethernet concepts
● Ethernet switching and bridging concepts
● Routing concepts
● Access Control Lists (ACLs)
● CLEAR-Flow
NOTE
If the information in a Release Note differs from the information in this User Guide, the Release Note takes
precedence.
Conventions
Tab le 1 and Ta bl e 2 list conventions that are used throughout this guide.
Table 1: Notice Icons
Icon Notice Type Alerts you to...
Note Important features or instructions.
Caution Risk of unintended consequences or loss of data.
Warning Risk of permanent loss of data.
Extreme Networks Policy Manager (EPM) 1.2 User Guide
7
Preface
.
Table 2: Text Conventions
Convention Description
Screen displays This typeface represents information as it appears on the screen.
Screen displays bold This typeface indicates how you would type a particular command.
The words “enter”
and “type”
[Key] names Key names appear in text in one of two ways. They may be
Words in bold type Bold text indicates a button or field name.
Words in italicized type Italics emphasize a point or denote new terms at the place where they are defined in
When you see the word “enter” in this guide, you must type something, and then
press the Return or Enter key. Do not press the Return or Enter key when an
instruction simply says “type.”
• referred to by their labels, such as “the Return key” or “the Escape key.”
• written with brackets, such as [Return] or [Esc].
If you must press two or more keys simultaneously, the key names are linked with a
plus sign (+). For example:
Press [Ctrl]+[Alt]+[Del].
the text.
Related Publications
Other manuals that you will find useful are:
● ExtremeXOS Concepts Guide
● ExtremeXOS Command Reference Guide
For documentation on Extreme Networks
Networks, see the Extreme Networks home page:
http://www.extremenetworks.com
Customers with a support contract can access the Technical Support pages at:
http://www.extremenetworks.com/services/eSupport.asp
The technical support pages provide the latest information on Extreme Networks software products,
including the latest Release Notes, information on known problems, downloadable updates or
patches as appropriate, and other useful information and resources.
Customers without contracts can access manuals at:
http://www.extremenetworks.com/services/documentation/
®
products, and for general information about Extreme
8
Extreme Networks Policy Manager (EPM) 1.2 User Guide

1 Overview
Introduction
This chapter describes the following sections:
● Description of the Extreme Networks Policy Manager on page 9
● About This Manual on page 10
● Editions of the EPM on page 10
Description of the Extreme Networks Policy Manager
The Extreme Networks Policy Manager (EPM) is a client application for the configuration and
management of Access Control Lists (ACLs) and Continuous Learning, Examination, Action and
Reporting of Flows (CLEAR-Flow or CF) on EXOS-based Extreme Networks switches. It is a GUI-based
software download designed to simplify the management process.
ACLs are used to perform packet filtering and forwarding decisions on traffic traversing the switch.
Each packet arriving on an ingress port and/or VLAN is compared to the access list applied to that
interface and is either permitted or denied. ACLs are typically applied to traffic that crosses Layer 3
router boundaries, but is possible to use access lists within a Layer 2 virtual LAN (VLAN).
CLEAR-Flow is an extension to ACLs that implements security, monitoring, and anomaly detection in
Extreme XOS software. ACL policy rules are created to count packets of interest. CLEAR-Flow rules are
added to the policy to monitor the ACL counter statistics for situations of interest in the individual
network. Such situations can include: the cumulative value of a counter; the change to a counter over a
sampling interval; the ratio of two counters; or even the ratio of the changes of two counters over an
interval. For example, monitoring the ratio between TCP SYN and TCP packets might show an
abnormally large ratio which may indicate a SYN attack.
The counters used in CLEAR-Flow are either defined by the user in an ACL entry, or can be a
predefined counter. Refer to a list and description of these counters in Appendix A on page 63.
If the rule conditions are met, the CLEAR-Flow actions configured in the rule are executed. The switch
can respond by modifying an ACL that will block, prioritize, or mirror the traffic, executing a set of CLI
commands, or sending a report using a SNMP trap or EMS log message.
For additional information about ACLs or CLEAR-Flow refer to the ExtremeXOS Concepts Guide.
Extreme Networks Policy Manager (EPM) 1.2 User Guide
9
Overview
About This Manual
This manual consists of six chapters, two appendixes and an index, arranged as shown in Tab le 3 .
Table 3: List of Chapters
Chapter Description
1 - Overview Describes the Extreme Networks Policy Manager and the User Guide
2 - Installing EPM Describes the hardware, software and switch requirements, and explains the
3 - Viewing Policies and Rules Describes procedures for viewing policies and rules locally and through a
4 - Creating Policies and Rules Describes procedures for creating policies and rules
5 - Modifying Policies and Rules Describes procedures to modify existing policies and rules
6 - Running EPM Examples Provides two examples to demonstrate capabilities and procedures
Appendix A Contains help messages and other reference material that appear in the EPM
Appendix B Contains suggestions for dealing with problems that may occur when running
Index Contains a keyword index to the User Guide
contents.
installation process
switch
program
the EPM
Editions of the EPM
Currently, one edition of the EPM is available—the Supervisor Edition. The Supervisor Edition allows
the user the capability to create, modify and save policies either locally or when connected to a switch.
In this User Guide, the terms EPM and Extreme Networks Policy Manager always refer to the
Supervisor Edition.
10
Extreme Networks Policy Manager (EPM) 1.2 User Guide
2 Installing The Extreme Networks Policy
Manager
Introduction
This chapter describes the following sections:
● Hardware and Software Requirements on page 11
● Switch Requirements on page 11
● EPM Installation on page 13
Hardware and Software Requirements
The EPM is a software application that is installed on a customer’s PC. Ta bl e 4 displays the minimum
requirements for a single user.
Table 4: Minimum Hardware and Software Requirements
Item Windows Linux
Processor Pentium 4 or AMD Athlon Pentium 4 or AMD Athlon
Operating System Windows XP (Home or Professional) Fedora Core 5
Memory 512 MB (1 GB is recommended for
better performance.)
Storage 10 GB 10 GB
CD-ROM Drive Not required. The EPM is installed
from a network download.
X-windows
512 MB (1 GB is recommended for
better performance.)
Not required. The EPM is installed
from a network download.
Switch Requirements
The following apply to the switch used with the EPM.
● The EPM can be run on the following Extreme Networks switches:
■ BlackDiamond
■ Summit
■ BlackDiamond 10808
■ BlackDiamond 12800 series
Although the BlackDiamond 8800 and Summit switches listed above support the EPM, they do not support
CLEAR-Flow rules. Therefore, when the EPM is used with these switches, CLEAR-Flow rules and their raw rule
text are displayed but the rules themselves are disabled
Extreme Networks Policy Manager (EPM) 1.2 User Guide
®
NOTE
®
8800 series
family of switches (Summit X150, X250e, X450, X450a and X450e series)
11

Installing The Extreme Networks Policy Manager
● The switch must be running ExtremeXOS
● The EPM requires a Secure Shell (SSH) module installed and running on the switch to manage policy
™
11.4 or later.
file transfer. The default state of SSH is “disabled”, so ensure that this application has been enabled
using the
enable ssh2 command.
To load and run the SSH module on a switch, use the following commands:
a Download image
<ip> <yy>-xxx-ssh.xmod primary
where “yy” is the switch type and “xxx” is the release number
For example,
download image 10.1.1.1 bd10k-11.4.4.7-ssh.xmod primary
b run update
c enable ssh2
d enable clear-flow (for CLEAR-Flow supported switches)
For additional information, refer to the ExtremeXOS Command Reference Guide and the ExtremeXOS
Concepts Guide.
● A Trivial File Transfer Protocol (TFTP) server must be installed and running prior to loading or
saving policy files using the EPM. The server is required to transfer policy files to and from switches.
Install an external TFTP server on port 69 and set the EPM’s policy staging directory to the TFTP
server’s root. Set the staging directory after the EPM is installed. (Refer to “Configuring the EPM for
use on a Switch” on page 18 for information on setting the staging directory and other configuration
procedures.)
● Ensure that the EPM user has read/write permission to the installation directory and the TFTP
directory.
12
Extreme Networks Policy Manager (EPM) 1.2 User Guide
EPM Installation
EPM Installation
The EPM is installed from a network download and utilizes a user interface installation Wizard. Use the
following procedure:
1 Download the EPM program files from Extreme Networks’ Software Downloads web page.
2 On Windows, double click the installation bundle executable icon.
On Linux, run the installation script (.sh file) from an xterm window.
The Setup Wizard window is launched as shown below.
NOTE
Installation on Linux uses the Installation Wizard with similar panels and properties.
and is followed by
3 Continue progressing through the screens that ask you to:
a Accept the license agreement,
b Select the destination directory,
c Select the start menu folder, and
d Select additional tasks (Create a desktop icon, Create a Quick Launch icon).
Extreme Networks Policy Manager (EPM) 1.2 User Guide
13
Installing The Extreme Networks Policy Manager
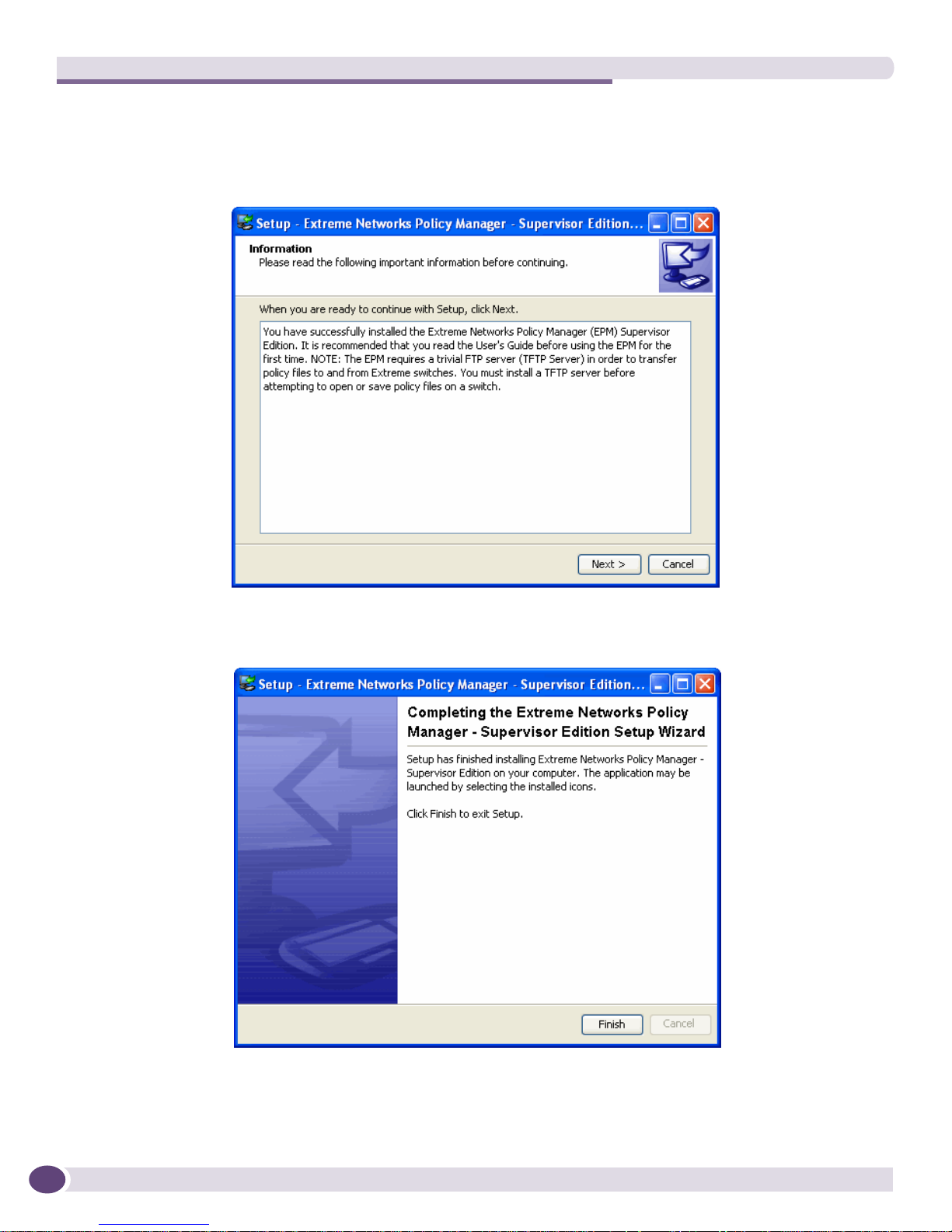
The Wizard then extracts and installs the files, and displays
e Notification of the file installation,
f The following Information window, and
g The following finishing window.
4 Click Finish. The EPM is installed.
14
Extreme Networks Policy Manager (EPM) 1.2 User Guide

3 Viewing Policies and Rules
Introduction
This chapter provides a brief description of the different ways to view policies and rules in the Extreme
Networks Policy Manager (EPM).
The EPM functions in two modes—local and switch. In local mode, the user can work independently
within an offline set of files to create, modify and verify policies and rules. The local files can also be
used as a backup system for files running on a switch. When working locally, certain elements of the
application are hidden and can be seen only when connected to a switch. In switch mode, the user can
utilize all the functions of the EPM.
Each policy is viewed and edited individually and only one policy can be open at a time. If one policy
is open in the program and the user attempts to open or create another, the EPM prompts with a save
command before closing the currently open policy.
This chapter describes the following sections:
● Opening the EPM on page 15
● Configuring the EPM for use on a Switch on page 18
● Description of the Windows and Menus on page 20
● Opening an Existing Policy on page 30
● Searching for Rules in a Policy on page 33
● Working Among the Windows and Panels on page 36
Opening the EPM
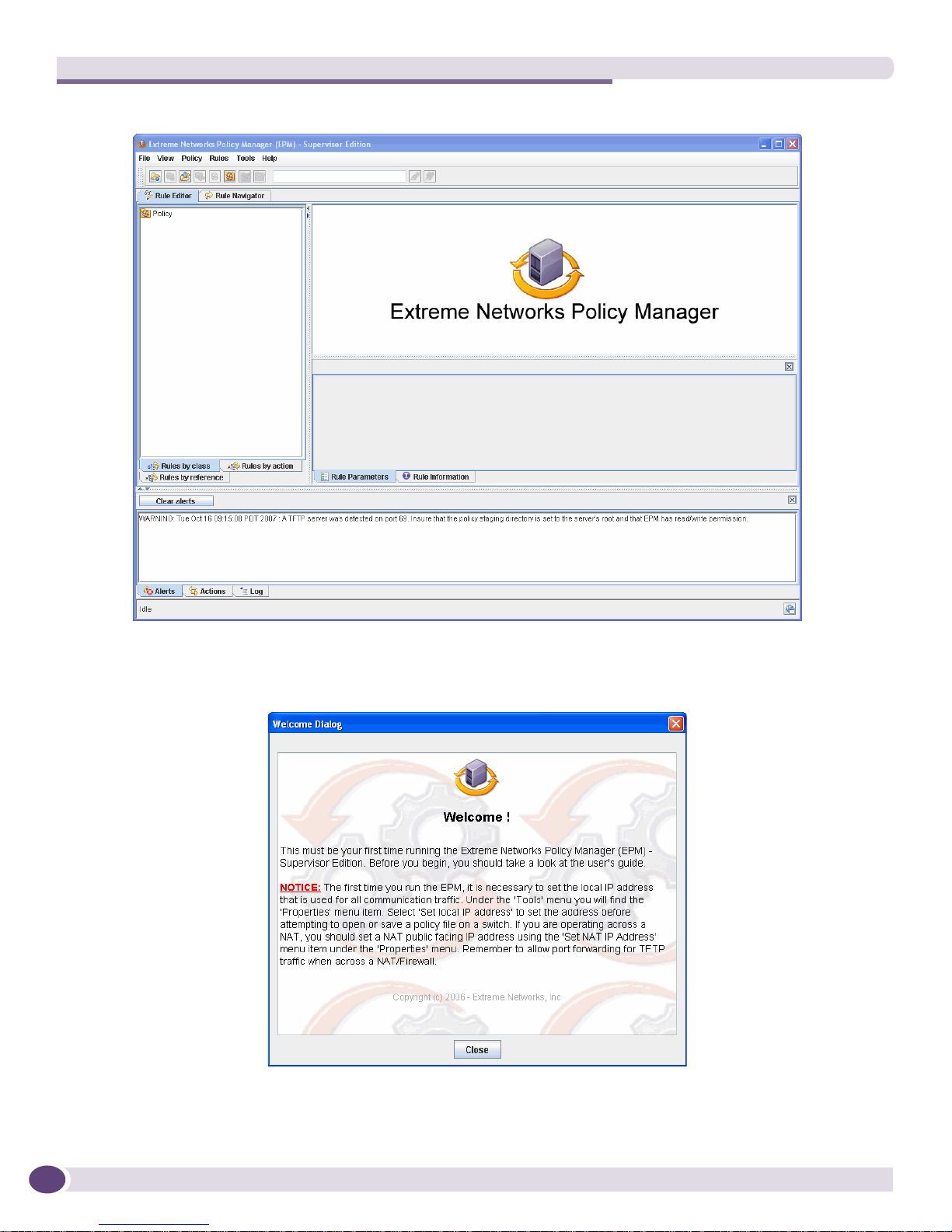
1 Launch the EPM through Start > Programs > Extreme Networks Policy Manager > epm_supervisor
or by using a desktop icon if one was selected during the installation process. The EPM opens to the
Rule Editor window as shown below.
NOTE
Only one instance of the EPM can be executed on the desktop at a time.
Extreme Networks Policy Manager (EPM) 1.2 User Guide
15
Viewing Policies and Rules
The first time the EPM program is launched, the following message is displayed
.
16
Extreme Networks Policy Manager (EPM) 1.2 User Guide
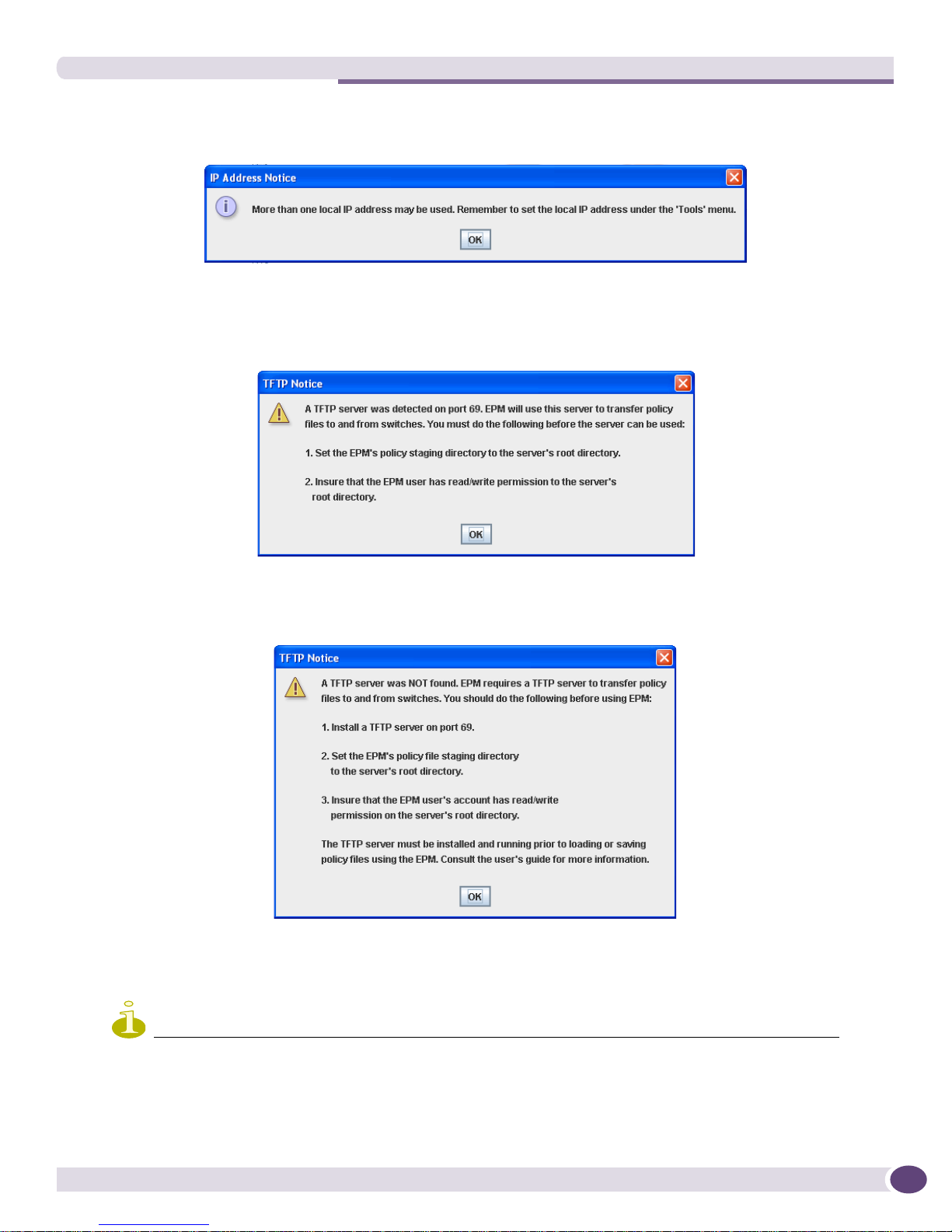
Opening the EPM
2 After reading, Close the box. The following IP Address Notice is displayed. This notice is displayed
every time the EPM is opened until an IP address has been set.
3 Click OK. The EPM then notifies the user if it has found a TFTP server. Without one, the EPM can
open and save local policies only.
a If it finds a TFTP server, the following notice is displayed.
Refer to “Configuring the EPM for use on a Switch” on page 18 to set the policy staging directory.
b If it does not find a TFTP server, the following notice is displayed.
If necessary, take the appropriate action to enable a TFTP server.
4 Click OK to close the box. The EPM Rule Editor window remains.
NOTE
A notice regarding TFTP server availability is also displayed in the Status Panel under the Alerts tab. (Refer to
“Status Panel” on page 23.)
Extreme Networks Policy Manager (EPM) 1.2 User Guide
17
Viewing Policies and Rules
Configuring the EPM for use on a Switch
Before attempting to open a policy from a switch or save a policy to a switch, be certain that the
following steps have been completed.
● The EPM has found a TFTP server. Check that the TFTP server is running on client and is listening
on port 69.
● The user running the EPM has read/write/create permission to the TFTP server’s root directory.
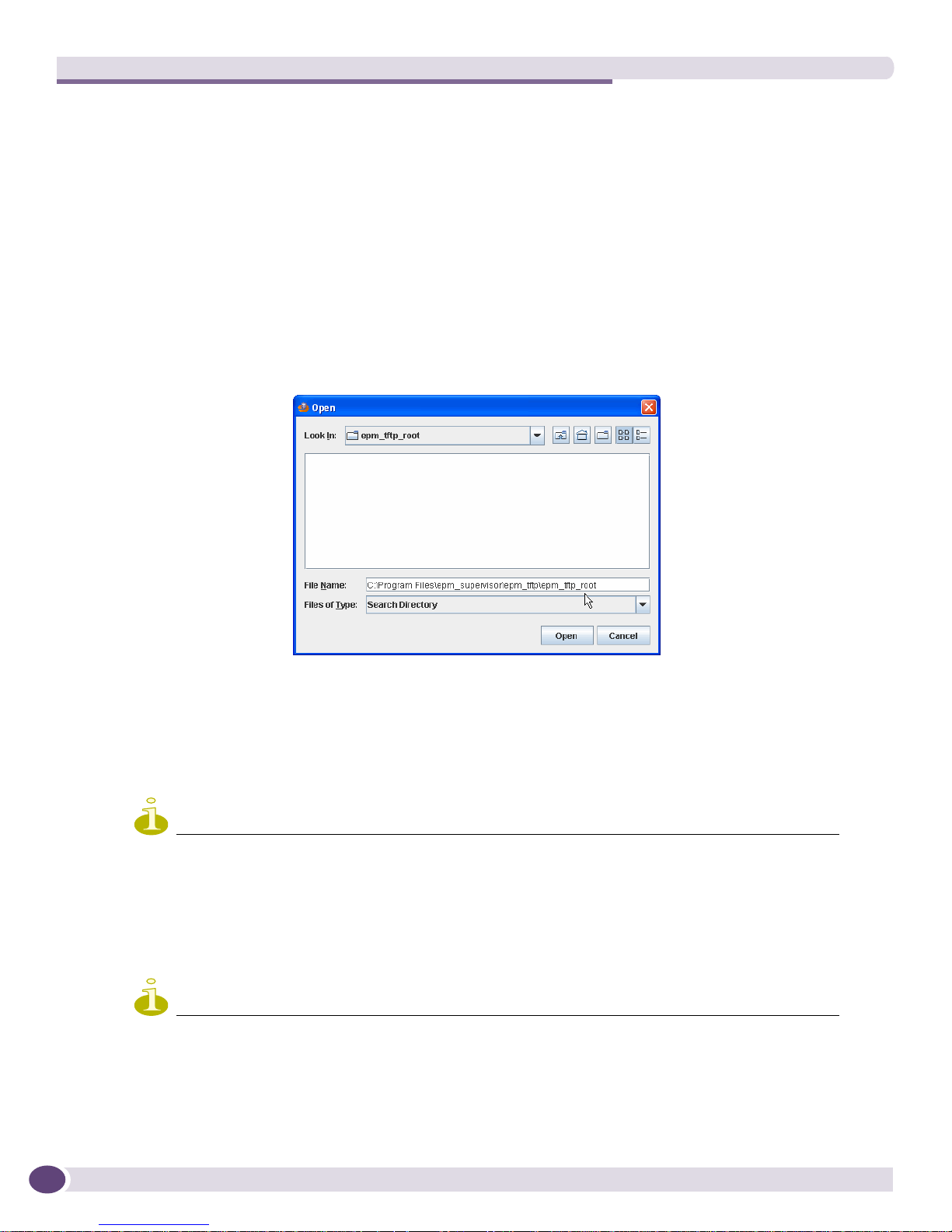
● The file staging directory is pointing towards the TFTP server’s root directory. To set the directory:
a Choose Tools > Properties > Set file staging directory from the menu. A file Open box is
displayed.
b Point to the TFTP server’s root directory as shown below.
c Click Open. The box closes and the file staging directory is set.
● The local IP address is set. To set the address:
a Choose Tools > Properties > Set Local IP Address from the menu. A Local IP Selection box
opens.
b From the dropdown menu, select an available IP address and click OK. The IP address is set.
NOTE
If the network configuration is changed, the local IP address must be reset.
● If applicable, set the public side address of NAT. If not applicable, leave blank. To set the address:
a Choose Tools > Properties > Set NAT IP address from the menu. An Input dialog box is
displayed.
b Enter the address and click OK.
NOTE
Network Address Translation (NAT) is a method used by networking equipment such as routers to share an IP
address.
18
Extreme Networks Policy Manager (EPM) 1.2 User Guide
Configuring the EPM for use on a Switch
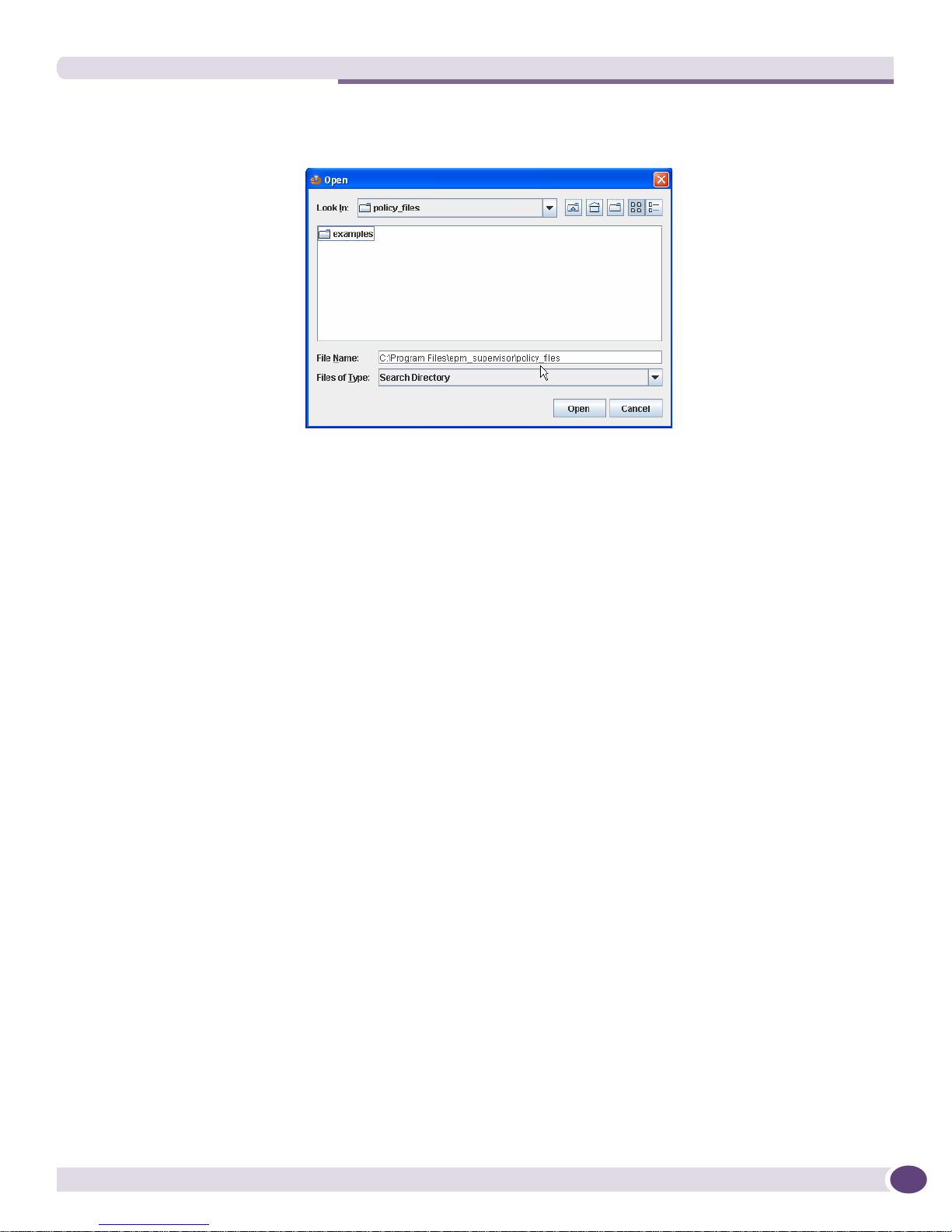
● The file search directory is pointing towards the policy files as shown below. This is the default.
Choose Tools > Properties > Set file search directory to check the file name in the file Open box.
Extreme Networks Policy Manager (EPM) 1.2 User Guide
19
Viewing Policies and Rules
Description of the Windows and Menus
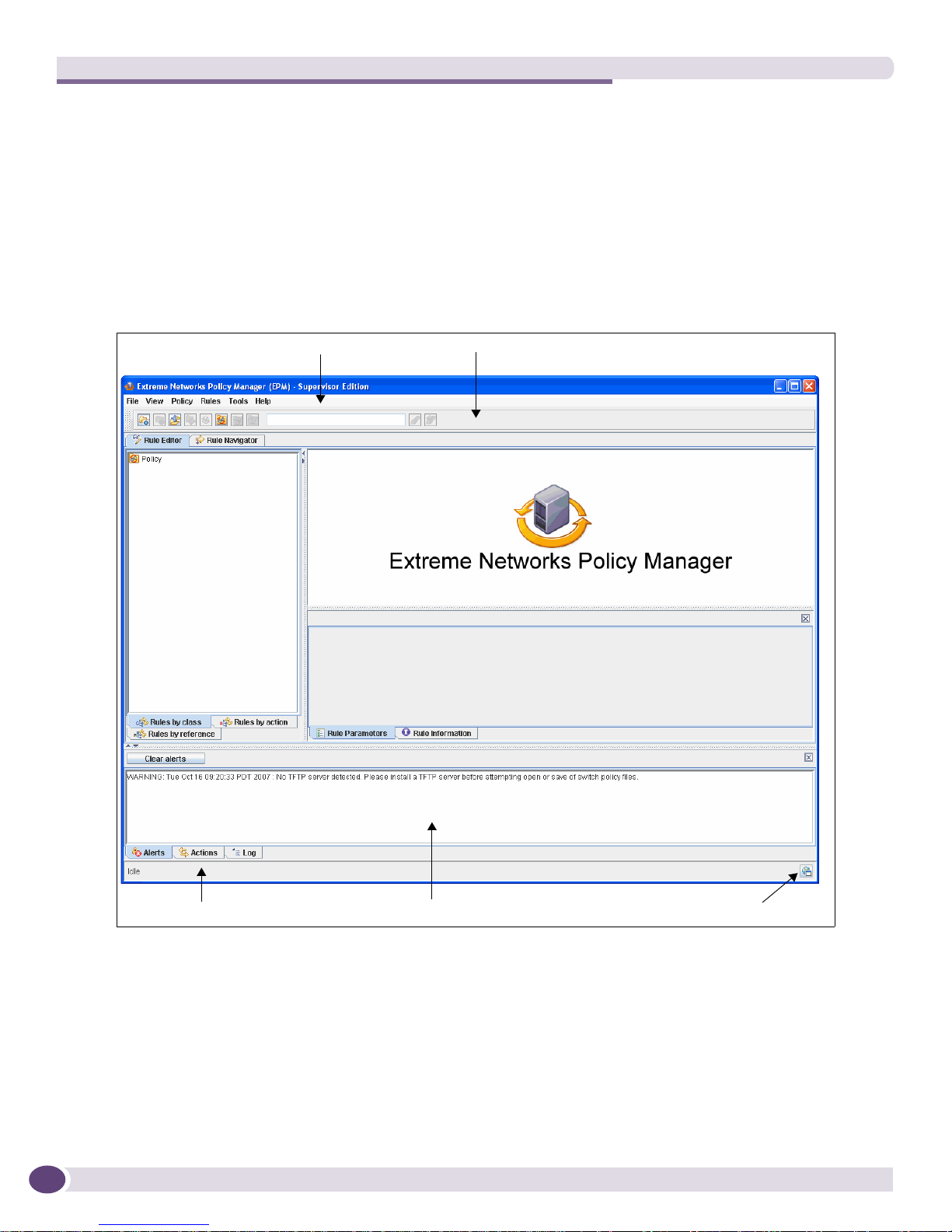
The EPM Desktop
The program opens to the Rule Editor window. The two primary working windows are the Rule Editor
window which is described on page 26 and the Rule Navigator window which is described on page 29.
Some window elements are common to both the Rule Editor and the Rule Navigator windows. The
following screen identifies those common elements.
Menu Bar
Toolbar
Status Bar
These include:
● A standard Menu Bar, discussed on page 21
● A To ol b ar, discussed on page 23
● A Status Panel, discussed on page 23
● A Status Bar, discussed on page 25
● A link icon to access the eSupport Website
20
Status Panel
“Go to the eSupport Website”
Extreme Networks Policy Manager (EPM) 1.2 User Guide
Description of the Windows and Menus
Menu Bar
The Menu Bar consists of six standard menus—File, View, Policy, Rules, To o l s and Help. Ta bl e 5
describes the elements of these menus.
Table 5: EPM Standard Menus
Menu Components Description
File
New Begins the process to create a new policy. Refer to “Creating a New Policy”
on page 37.
Open Opens an existing policy file.
Switch Opens an existing policy file from a switch. Refer to “Opening a Policy File
from a Switch” on page 31.
Local Opens an existing policy file from a local file. Refer to “Opening a Policy File
Save Saves changes to an existing policy in the location (switch or local) in which
Save As Saves a new policy or saves changes to an existing policy to a different
Switch Saves to a switch.
Local Saves locally.
Import From Imports all rules from one policy into the current policy. Refer to “Importing
Export To Exports all rules from the current policy to populate a new policy or to
Exit Closes the EPM.
View Shows and hides certain panels in the window. When one or more is hidden,
Status Panel Shows and hides the Status Panel.
Rule Properties Panel Shows and hides the Rule Properties Panel.
Tool Bar Shows and hides the Tool Bar.
Policy Includes functions to create, modify and check a policy.
New Policy Begins the process to create a new policy. Refer to “Creating a New Policy”
Search Searches the current policy for specific rules. Refer to “Searching for Rules
Validate & Check Validates and checks a new or modified policy. Refer to “Validating and
Refresh Refreshes the currently loaded policy when it is activated on a switch after it
Activity Activates a policy stored on the switch, allowing control of the active VLANs
Recalculate rule ranks Recalculates the rule ranks when ACL and/or CLEAR-Flow rules have been
Reorder rules by rank Places rules in order by rule rank when they have been recalculated. Refer to
Locally” on page 30.
it was opened.
location. Refer to “Creating a New Policy” on page 37.
Rules” on page 41.
replace the existing rules in another policy. Refer to “Exporting Rules” on
page 42.
the shown panels expand to fill the window.
on page 37.
in a Policy” on page 33.
Checking a Policy” on page 40.
has been modified. Refer to “Applying Changes to an Activated Policy” on
page 47.
and active ports of the current policy. Refer to “Managing Policy Activity” on
page 50.
added to or deleted from the policy. Refer to “Organizing Rules” on page 49.
“Organizing Rules” on page 49.
Extreme Networks Policy Manager (EPM) 1.2 User Guide
21
Viewing Policies and Rules
Table 5: EPM Standard Menus (Continued)
Menu Components Description
Reorder rules by initial
position
Rules Begins the process to create a new rule.
New Rule Opens the Rule Wizard to create a new rule. Refer to “Creating a New Rule
Tools
Global Variables... Opens a dialog box in which global variables can be set. Refer to “Managing
Policy Variables... Opens a dialog box in which policy variables can be set. Refer to “Managing
Synonyms... Displays a list of synonyms. Refer to “Synonyms used for Rule Constants” on
System Counters... Displays a list of predefined CLEAR-Flow system counters. Refer to
Properties Refer to “Configuring the EPM for use on a Switch” on page 18 for the
Set local IP address Opens a box to choose from available IP addresses or enter a new address.
Set NAT IP address Opens a box to set the public side address of your NAT (Network Address
Set files search directory Sets the default directory for finding policy files when a policy is opened
Set file staging directory Sets the location of the tftp server’s root directory. Files are 'staged' or
Message Capture Captures data to be used to diagnose problems.
Tracing Turns tracing log on and off.
Debug Turns debug log on and off. When on, a message is written to a debug text
Set Capture Size Sets the maximum number of lines of data to be captured. The allowed range
Policy Parsing
Ignore Unknown
Keywords
Sentriant Actions
Reset XML to factory When the Sentriant XML code has been rewritten, replaces it with the
Write XML Allows you to write specialized code to replace or supplement factory code.
Help
About Extreme Networks
Policy Manager
Places rules in their original position regardless of rank. Refer to “Organizing
Rules” on page 49.
for a Policy” on page 37.
Global and Policy Variables” on page 48.
Global and Policy Variables” on page 48.
page 65.
“Predefined CLEAR-Flow System Counters” on page 63.
following properties.
Translation), if appropriate.
locally. The Open > File function will set itself to this location.
copied to and from the root directory when a policy is opened and saved on a
remote switch. Refer to “Configuring the EPM for use on a Switch” on
page 18.
file and is not displayed in an EPM window.
is between 1 and 100,000.
Turns Ignore Unknown Keywords on and off. When on (the default), a policy
with terms that the EPM does not understand, is loaded but with
qualifications. When off, a policy that the EPM does not understand is not
loaded. Refer to “Policy Parsing” on page 32.
original factory code.
Lists: Application Name, Edition, Version and Build number.
In the Rule Editing and Viewing Panel and the Rule Navigator window, another menu is displayed
when you right-click any rule in the list. For details about the functions of this menu, refer to the
chapter, “Modifying Policies and Rules” on page 43.
22
Extreme Networks Policy Manager (EPM) 1.2 User Guide
Description of the Windows and Menus
Toolbar
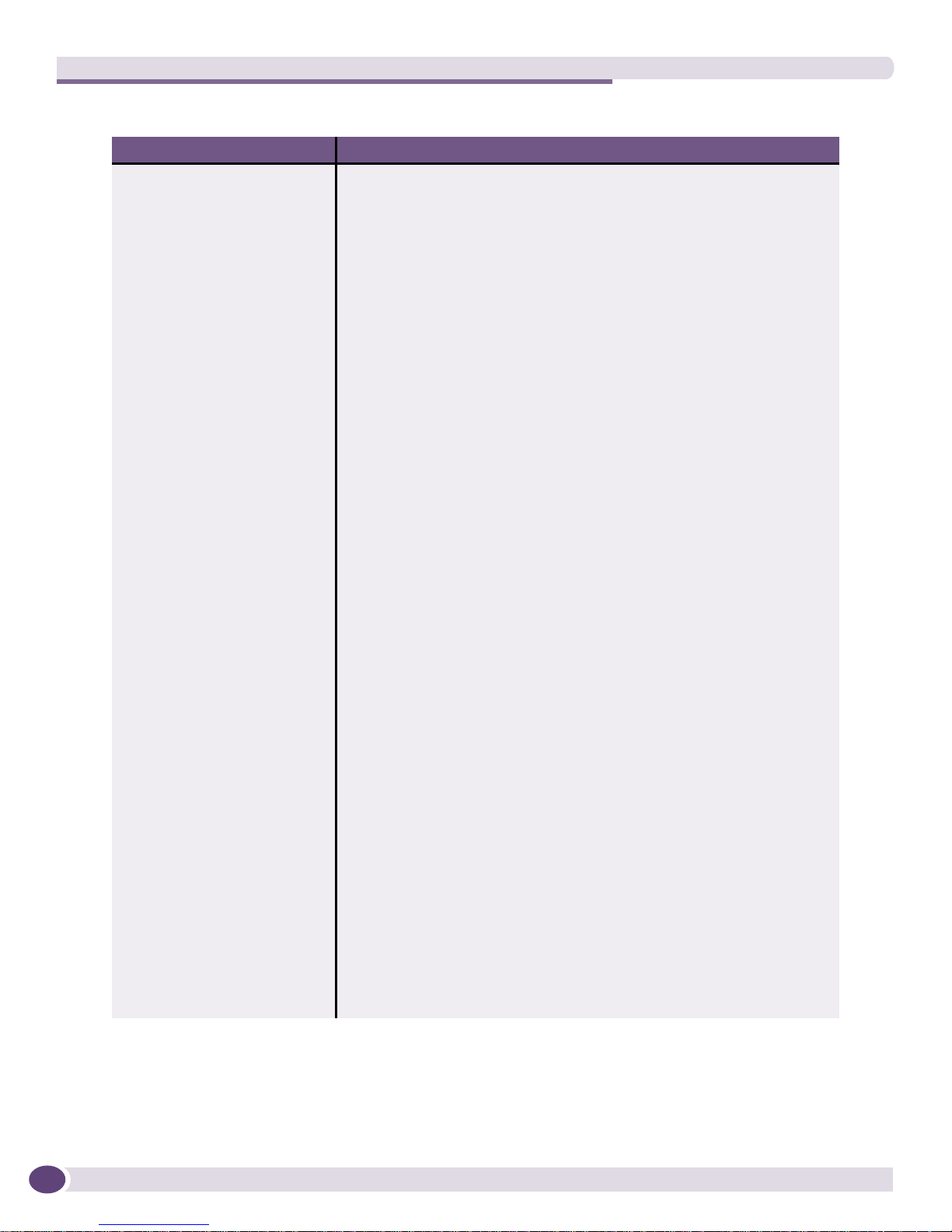
The Toolbar contains icons for the most common menu operations and are shown in Ta b le 6 .
Table 6: Toolbar Icons
Icon Description
Opens a local policy
Saves changes to a local policy
Opens a policy from a switch
Saves changes to a policy on switch
Creates a new rule
Creates a new policy
Validates and checks a policy
Searches a policy for particular rule
elements
Searches for a particular rule
Repeats the search for a particular rule
Status Panel
The Status Panel displays data from different log files—Alert, Actions, Log, Policy Information and
Rule Activity. A log is selected by clicking its panel tab. These logs are described below with examples
of the screens.
● The Alerts tab displays the alerts log messages. Alerts are warnings or notices about an
action or error that may or may not have inhibited EPM functions.
Extreme Networks Policy Manager (EPM) 1.2 User Guide
23
Viewing Policies and Rules
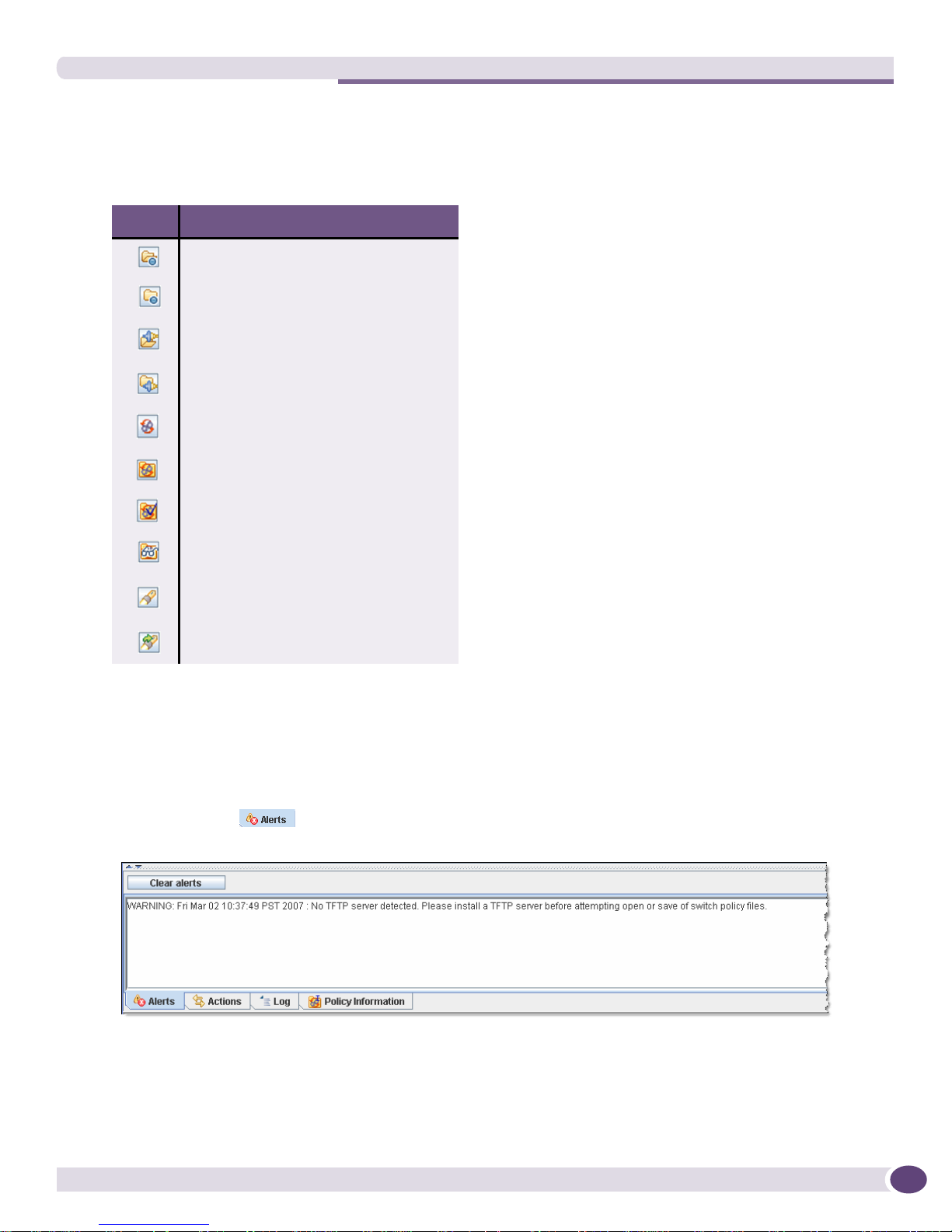
● The Actions tab displays the actions log messages. All user actions are recorded for audit
purposes. (The replay of actions is planned for a future release.)
● The Log tab displays common log messages. The common log contains any trace or error
messages that inhibit or cause failure of EPM functions.
For each of these three logs (Alerts, Actions and Log), there is a “Clear” button that removes the entries
currently appearing on the screen. These entries are then stored in the program’s log files
(\Program Files\epm_supervisor\log). To set the maximum number of status capture lines for a log,
choose Tools > Properties > Message Capture > Set Capture Size from the menu.
● The Policy Information tab is displayed when a policy is opened and shows
Information and Notes about that currently open policy. Information shows basic data including
when and by whom the policy was created and last modified as well as the number and type of
rules. Notes might include the purpose of the policy or other user defined identifiers. This is a read/
write text box.
To add to the Notes field:
a In the field, begin typing the desired text. The Apply Notes button is enabled.
b When the text is entered, click the Apply Notes button. The text is added.
To rem o ve not es :
a Highlight the text to be removed then press the keyboard’s Delete or Backspace key. The Apply
Notes button is enabled.
b Click the Apply Notes button. The text is removed.
24
Extreme Networks Policy Manager (EPM) 1.2 User Guide
Description of the Windows and Menus
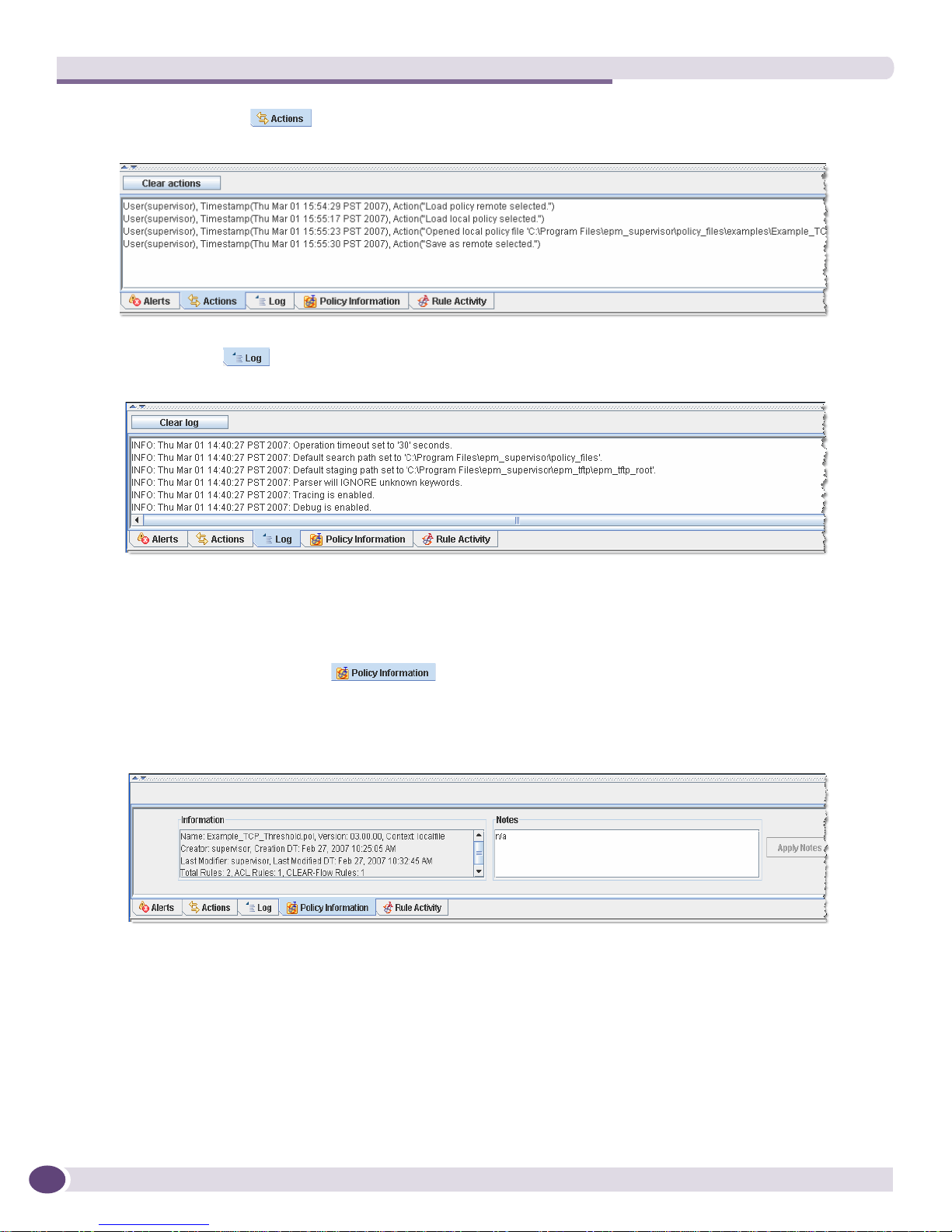
● The Rule Activity tab displays activity data for a policy running on a switch. The EPM
updates the data every 15 to 30 seconds. This log is shown only when the EPM is connected to a
switch.
For the Rule Activity log, there is a Refresh button that manually updates any modified activity.
Status Bar
The Status Bar displays the current activity of the EPM. When it is not executing a function it reads
“Idle.” Otherwise, it shows an explanation of the function that is running. For example:
● When opening a file locally, the status bar reads “Operation 'OpenLocal' is in progress. (The
operation should complete within '30' seconds.)” or
● When exiting the EPM, the status bar reads “Operation 'FlushLogsAndExit' is in progress (The
operation should complete within '30' seconds.)”
Extreme Networks Policy Manager (EPM) 1.2 User Guide
25
 Loading...
Loading...