Page 1

Volume
1
User Manual
EFC301FR
EFC301FM
ID/Mifare IP@DOOR TCP/IP
Network Access Control System
Page 2

EVERFOCUS ELECTRONICS CORPORATION
EFC301FR
EFC301FM
Instruction Guide
2014 EverFocus Electronics Corp
All rights reserved. No part of the contents of this manual may be reproduced or transmitted in any form or
by any means without written permission of the EverFocus Electronics Corporation.
Page 3

TCP/IP Network Access Controller
TABLE OF CONTENTS
1 Introduction ............................................................................................................ 1
1.1 Features .................................................................................................................... 2
1.2 Specification ............................................................................................................. 2
1.3 Packing List ............................................................................................................... 3
1.4 Optional Device ........................................................................................................ 3
1.5 Installation Procedures ............................................................................................ 4
1.6 Installation Preparation ............................................................................................ 4
1.6.1 Obtain a Floor Plan ....................................................................................... 4
1.6.2 Determine the Hardware and Location ....................................................... 5
1.6.3 Determine the Number of Controllers According to System Structure ....... 6
2 Hardware Installation .............................................................................................. 7
2.1 Installing the Controller ............................................................................................ 7
2.2 Definitions of Terminal Block and LEDs .................................................................... 8
2.3 Installing and Connecting the Readers ................................................................... 10
2.3.1 RS232 .......................................................................................................... 11
2.3.2 Wiegand (Self-adaptive) ............................................................................. 11
2.4 Connecting to the Door Lock .................................................................................. 12
2.4.1 Connecting to an Electric Strike ................................................................. 12
2.4.2 Connecting to a Magnetic Lock .................................................................. 12
2.5 Connecting to the Door Sensor .............................................................................. 13
2.6 Connecting to the Door Button .............................................................................. 13
2.7 Connecting to the Fire Alarm ................................................................................. 13
2.8 Connecting to the Alarm Input ............................................................................... 13
2.9 Connecting to the Alarm Output ............................................................................ 14
3 Connection ............................................................................................................. 15
3.1 Connecting to the Computer through the TCP/IP .................................................. 15
3.2 Connecting to Power .............................................................................................. 15
3.3 Restoring the Controller ......................................................................................... 16
3.4 Before First Use ...................................................................................................... 16
4 Operation Instructions of Hardware........................................................................ 17
4.1 Operation Instructions of Keystrokes on the Reader ............................................. 17
4.2 Operation of Home Page ........................................................................................ 18
4.3 Main Menu of System Setting ................................................................................ 20
4.4 System Setting ........................................................................................................ 20
4.4.1 Set Language .............................................................................................. 21
4.4.2 Set Date Format ......................................................................................... 21
I
Page 4

TCP/IP Network Access Controller
4.4.3 Set Date ...................................................................................................... 22
4.4.4 Set Time ...................................................................................................... 22
4.4.5 Set Summer Time (Daylight Savings) .......................................................... 23
4.4.6 Set SYS Password ........................................................................................ 23
4.4.7 Set ARM Password ..................................................................................... 24
4.4.8 Set Backlight ............................................................................................... 25
4.4.9 Restore Expired Event ................................................................................ 25
4.4.10 Erase All Events .......................................................................................... 25
4.4.11 Restore Factory Setting .............................................................................. 26
4.5 Card Setting ............................................................................................................ 27
4.5.1 Add Card ..................................................................................................... 27
4.5.2 Delete Card ................................................................................................. 28
4.5.3 Set Card Properties ..................................................................................... 29
4.6 Reader Setting ........................................................................................................ 33
4.6.1 Enter Reader Setting Menu ........................................................................ 33
4.6.2 Set SYS Reader ............................................................................................ 33
4.6.3 Set AUS Reader ........................................................................................... 34
4.7 Door Setting ............................................................................................................ 34
4.7.1 Set Open Time ............................................................................................ 35
4.7.2 Set Over Time ............................................................................................. 35
4.7.3 Door Access Mode ...................................................................................... 36
4.8 Alarm Setting .......................................................................................................... 36
4.8.1 Composition of Alarm ................................................................................ 36
4.8.2 Basic Configuration of the Alarm ............................................................... 36
4.8.3 Enter Alarm Setting Menu .......................................................................... 37
4.8.4 AlarmIN Setting .......................................................................................... 37
4.9 Address Setting ....................................................................................................... 39
4.10 Set Network ............................................................................................................ 40
4.10.1 DHCP Setting .............................................................................................. 40
4.10.2 Set IP Address ............................................................................................. 40
4.10.3 Reset Network Setting ................................................................................ 41
4.11 System Info ............................................................................................................. 41
4.12 Introduction of System Operation ......................................................................... 41
4.12.1 Door Open by Swiping Card ....................................................................... 41
4.12.2 Door Open with Single Password ............................................................... 42
4.12.3 Door Open with Both Card and Password ................................................. 42
4.12.4 Door Open with Multiple Cards ................................................................. 42
4.12.5 Specific Door Control Mode ....................................................................... 43
5 Software Introduction ............................................................................................ 44
II
Page 5

TCP/IP Network Access Controller
5.1 Main Functions ....................................................................................................... 44
5.2 Profiles of Highlighted Features ............................................................................. 44
5.3 TCP/IP-based Architecture of Access Control System............................................ 45
6 Getting Started ....................................................................................................... 46
6.1 Quick Start .............................................................................................................. 46
6.1.1 Set Access Rule ........................................................................................... 46
6.1.2 Multiple Card Addition Methods ............................................................... 47
6.1.3 Set Department and Cardholder ................................................................ 48
6.1.4 Configure and Manage Attendance ........................................................... 49
6.1.5 Real-time Monitoring ................................................................................. 50
6.1.6 Export Function .......................................................................................... 50
6.1.7 Print Function ............................................................................................. 51
6.2 First Use .................................................................................................................. 52
6.2.1 Login Page................................................................................................... 52
6.3 Get Familiar with the Browser Page ....................................................................... 53
6.3.1 Introduction of the Main Page ................................................................... 53
6.3.2 Menu .......................................................................................................... 53
6.3.3 Control Panel .............................................................................................. 54
6.3.4 System Event Record .................................................................................. 55
7 Basic Setting ........................................................................................................... 57
7.1 Change Password ................................................................................................... 57
7.2 Set User and Authority ........................................................................................... 58
7.3 User Group ............................................................................................................. 60
7.3.1 Add User Group .......................................................................................... 60
7.3.2 Change User Group .................................................................................... 60
7.3.3 Delete User Group ...................................................................................... 60
7.4 User Setting ............................................................................................................ 61
7.4.1 Add User ..................................................................................................... 61
7.4.2 Edit User ..................................................................................................... 62
7.4.3 Delete User ................................................................................................. 62
7.4.4 Export User Information ............................................................................. 62
7.4.5 Print User Information ............................................................................... 63
7.4.6 Search User ................................................................................................. 63
7.5 Local Server ............................................................................................................ 63
7.6 System Upgrade ..................................................................................................... 64
7.6.1 Online Upgrade .......................................................................................... 64
7.6.2 Local Upgrade ............................................................................................. 64
8 Cardholder ............................................................................................................. 66
8.1 Department Setting ................................................................................................ 66
III
Page 6

TCP/IP Network Access Controller
8.1.1 Add Department ......................................................................................... 66
8.1.2 Edit Department ......................................................................................... 67
8.1.3 Delete Department..................................................................................... 67
8.2 Cardholder Setting ................................................................................................. 68
8.2.1 Add Cardholder .......................................................................................... 68
8.2.2 Change Cardholder ..................................................................................... 71
8.2.3 Delete Cardholder ...................................................................................... 72
8.2.4 Export Cardholder Information .................................................................. 73
8.2.5 Print Cardholder Information ..................................................................... 73
8.2.6 Query Cardholder ....................................................................................... 73
8.3 Import Cardholders ................................................................................................ 73
9 Real-time Monitoring ............................................................................................. 75
9.1 Real-time Event ...................................................................................................... 75
9.2 Report ..................................................................................................................... 76
9.2.1 Query Cardholder Information ................................................................... 76
9.2.2 Export Cardholder Information .................................................................. 76
9.2.3 Print Cardholder Information ..................................................................... 76
10 Maintenance .......................................................................................................... 77
10.1 Data Backup ............................................................................................................ 77
10.1.1 Manual Backup ........................................................................................... 77
10.1.2 Automatic Backup ...................................................................................... 78
10.2 Restore ................................................................................................................... 78
10.2.1 Restore from FTP ........................................................................................ 78
10.2.2 Restore from Local ..................................................................................... 79
10.3 Purge Out-of-date Data .......................................................................................... 79
11 Controller Management ......................................................................................... 80
11.1 Controller Setting ................................................................................................... 80
11.1.1 Change Controller Information .................................................................. 80
12 Access Rule............................................................................................................. 83
12.1 Date Type ............................................................................................................... 83
12.1.1 Add Date ..................................................................................................... 83
12.1.2 Delete Date ................................................................................................. 84
12.2 Door Schedule ........................................................................................................ 85
12.3 Group Schedule ...................................................................................................... 86
12.3.1 Add Group Schedule ................................................................................... 86
12.3.2 Delete Group Schedule .............................................................................. 87
12.3.3 Set Group Schedule .................................................................................... 87
12.4 Access Group .......................................................................................................... 88
12.4.1 Add Access Group ....................................................................................... 88
IV
Page 7

TCP/IP Network Access Controller
12.4.2 Delete Access Group .................................................................................. 89
13 Card Management .................................................................................................. 90
13.1 Card Setting ............................................................................................................ 90
13.1.1 Add (Register) Card .................................................................................... 91
13.1.2 Edit/Change Card........................................................................................ 92
13.1.3 Change Cards in Batch ................................................................................ 93
13.1.4 Delete Card ................................................................................................. 93
13.1.5 Delete All Cards .......................................................................................... 93
13.1.6 Export Card Information ............................................................................. 93
13.1.7 Print Card Information ............................................................................... 93
13.1.8 Query Card.................................................................................................. 93
13.2 Card Import ............................................................................................................ 94
14 Report .................................................................................................................... 96
14.1 Card Report ............................................................................................................ 96
14.1.1 Query Card Information ............................................................................. 96
14.1.2 Export Card Information ............................................................................. 96
14.1.3 Print Card Information ............................................................................... 96
14.2 Card-dependent Event ........................................................................................... 97
14.2.1 Query Card-Related Events ........................................................................ 97
14.2.2 Import Card-Related Events ....................................................................... 97
14.2.3 Print Card-Related Events .......................................................................... 97
14.3 Card-independent Event ........................................................................................ 97
14.3.1 Query Card-Irrelevant Events ..................................................................... 98
14.3.2 Import Card-Irrelevant Events .................................................................... 98
14.3.3 Print Card-Irrelevant Events ....................................................................... 98
15 Basic Attendance Management .............................................................................. 99
15.1 Attendence Time Setting ........................................................................................ 99
15.2 Edit Attendence Time ............................................................................................. 99
15.2.1 Query Attendance Time ........................................................................... 100
15.2.2 Export Attendance Information ............................................................... 100
15.2.3 Print Attendance Information .................................................................. 100
15.3 Week Holiday Setting ........................................................................................... 100
15.3.1 Edit Weekend ........................................................................................... 101
15.3.2 Query Weekend........................................................................................ 101
15.3.3 Export Weekend ....................................................................................... 101
15.3.4 Print Weekend .......................................................................................... 102
15.4 Special Holiday Setting ......................................................................................... 102
15.4.1 Add Special Date ....................................................................................... 102
15.4.2 Query Special Holiday Setting .................................................................. 103
V
Page 8

TCP/IP Network Access Controller
15.4.3 Edit Special Date ....................................................................................... 103
15.4.4 Delete Special Date .................................................................................. 103
15.4.5 Export Special Date .................................................................................. 104
15.4.6 Print Special Date ..................................................................................... 104
16 Attendance Exception ........................................................................................... 105
16.1 No-Access-Attendance ......................................................................................... 105
16.1.1 Add No-Access-Attendance ...................................................................... 105
16.1.2 Query of Registration of Not Swiping a Card ........................................... 106
16.1.3 Edit Record of Not Swiping a Card ........................................................... 106
16.1.4 Delete Registration of Not Swiping a card ............................................... 107
16.1.5 Export Registration of Not Swiping a card ............................................... 107
16.1.6 Print Registration of Not Swiping a card .................................................. 107
16.2 Time-off Enroll ...................................................................................................... 107
16.2.1 Add Time-off Enroll .................................................................................. 107
16.2.2 Query Time-off Enroll ............................................................................... 108
16.2.3 Edit Time-off Enroll ................................................................................... 108
16.2.4 Delete Leave Record ................................................................................. 109
16.2.5 Export Time-off Enroll .............................................................................. 109
16.2.6 Print Time-off Enroll ................................................................................. 109
16.3 Overtime Enroll .................................................................................................... 109
16.3.1 Add Overtime Enroll ................................................................................. 110
16.3.2 Query Overtime Enroll ............................................................................. 110
16.3.3 Edit Overtime Enroll ................................................................................. 111
16.3.4 Delete Overtime Enroll Records ............................................................... 112
16.3.5 Export Overtime Enroll Records. .............................................................. 112
16.3.6 Print Overtime Enroll Record. .................................................................. 112
17 Attendance Report ............................................................................................... 113
17.1 Original Access Record ......................................................................................... 113
17.1.1 Query Original Access Record .................................................................. 113
17.1.2 Export Original Access Record .................................................................. 113
17.1.3 Print Original Access Record .................................................................... 113
17.2 Report by Cardholder ........................................................................................... 114
17.2.1 Generate Report by Cardholder ............................................................... 114
17.2.2 Export Report by Cardholder ................................................................... 114
17.2.3 Print Report by Cardholder ...................................................................... 114
17.3 Statistics by Cardholder ........................................................................................ 115
17.3.1 Generate Statistics by Cardholders .......................................................... 115
17.3.2 Export Statistics by Cardholders............................................................... 115
17.3.3 Print Statistics by Cardholder ................................................................... 115
VI
Page 9

TCP/IP Network Access Controller
17.4 Statistics by Department ...................................................................................... 115
17.4.1 Generate Statistics by Department .......................................................... 116
17.4.2 Export Statistics by Department .............................................................. 116
17.4.3 Print Statistics by Department ................................................................. 116
VII
Page 10

Chapter
1
1 Introduction
The EFC301F is a Linux-based IP access control system combined with a card reader and a
door controller. The series comes in two models, EFC301FR and EFC301FM, supporting ID
card and MIFARE card respectively.
The EFC301F system is designed to control single door, and connect up to two readers. You
can simply connect the system to the network using a Cat 5 cable or through the PoE and to
power through the PoE port. Built-in with an RFID module, the controller can manage more
than 100,000 cards and 1,000,000 event records, and support 2,048 management groups.
The user-friendly electronic map management function makes it easy to manage the access
or events through the Web browser. You can also easily configure the operation using the
keypad on the reader.
• EFC301FR: Supports ID card
• EFC301FM: Supports MIFARE card
Figure 1-1
1
Page 11
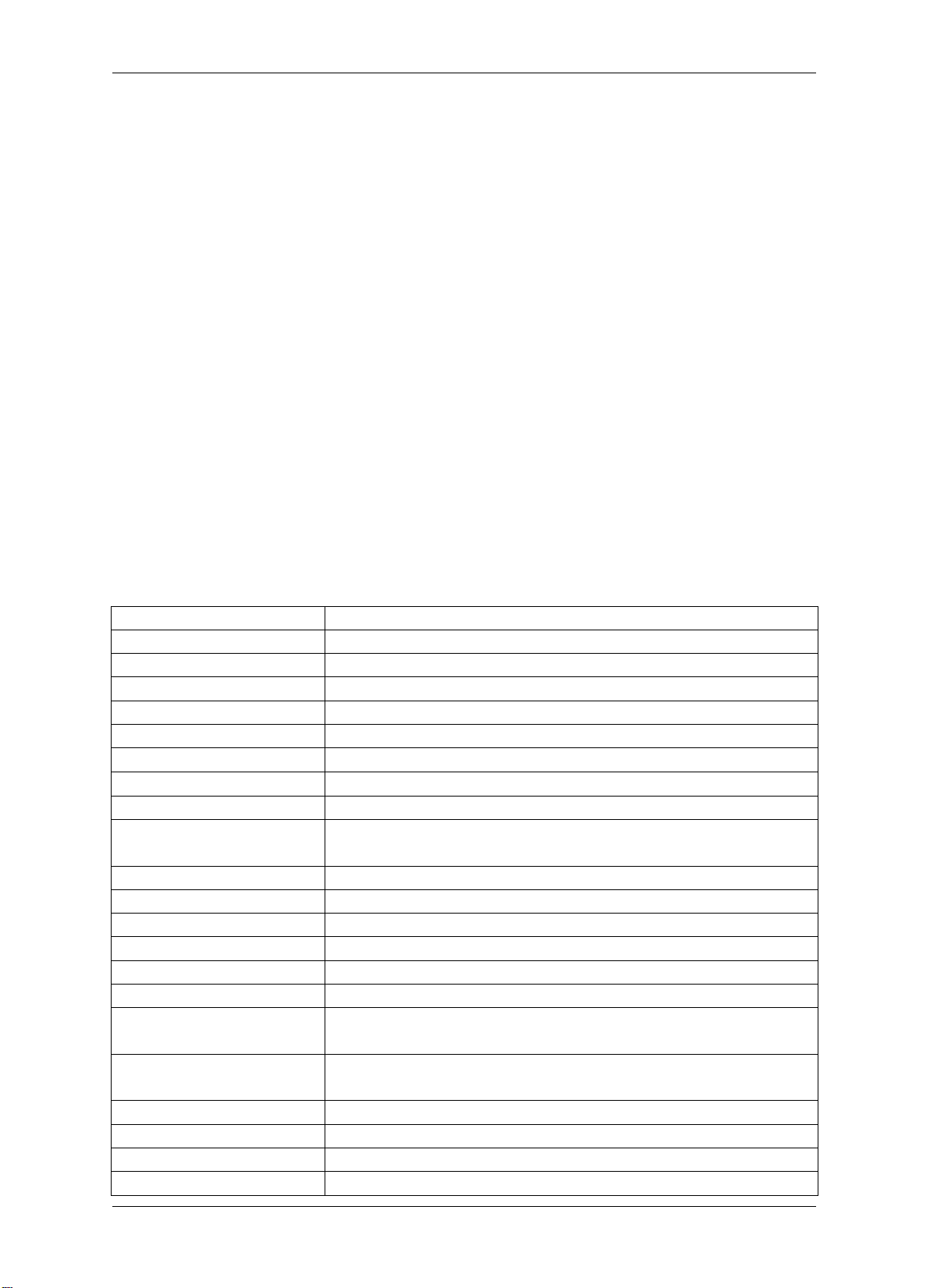
TCP/IP Network Access Controller
Operating System
Linux embedded
Database
Built-in
Memory
512 M
Web Setting Page
Support setting, monitoring and management
Maximum Card Amount
100,000
Maximum Even Records
1,000,000
Door Control
Single door
Card password
8 digits
System password
8 digits
Protection Setting /
Alarm Input
5 inputs (1 fire alarm; 4 common alarms)
Alarm Output
2 outputs
Network Interface
100M ethernet interface
Baud Rate
9600 bps
Card Reading Distance
5 ~ 10 cm
Card Reading Time
200 ms
Programmable Time
Each day can be divided into 10 time-period with a
Each door supports independent 10 date settings (from
Management Group
2,048
Management Plans
2,048
Daylight Saving Time
Yes
Card Expiration
Yes
1.1 Features
Network access through CAT 5 cable (10M / 100M Ethernet) or PoE
Remote setting, control and management; no software needed to be installed
Secure access through the Web browser is guaranteed by SSL (Secure Socket Layer)
Plug-and-play through DHCP or static IP
Multiple languages support and multilingual Web pages: English, Simplified Chinese
and Russian
On-line system update support
Control multiple controllers through central management software
Manage up to 100,000 cards and 1,000,000 event records
2,048 management groups support
Manage 10 time periods every day, with a minimum interval of 1 min
3 data types setting, up to 255 date settings support
Real-time electronic map display and edit support
Real-time event records support
Powerful management function: Access management according to time, date,
location, authority of card holder, etc.
Powerful alarm access function and protection setting / withdrawal function in the
protection area
1.2 Specification
Withdrawal Password
Periods
8 digits
minimum time interval of 1 min.
Programmable Date
Sunday to Monday, and 3 customized dates)
2
Page 12
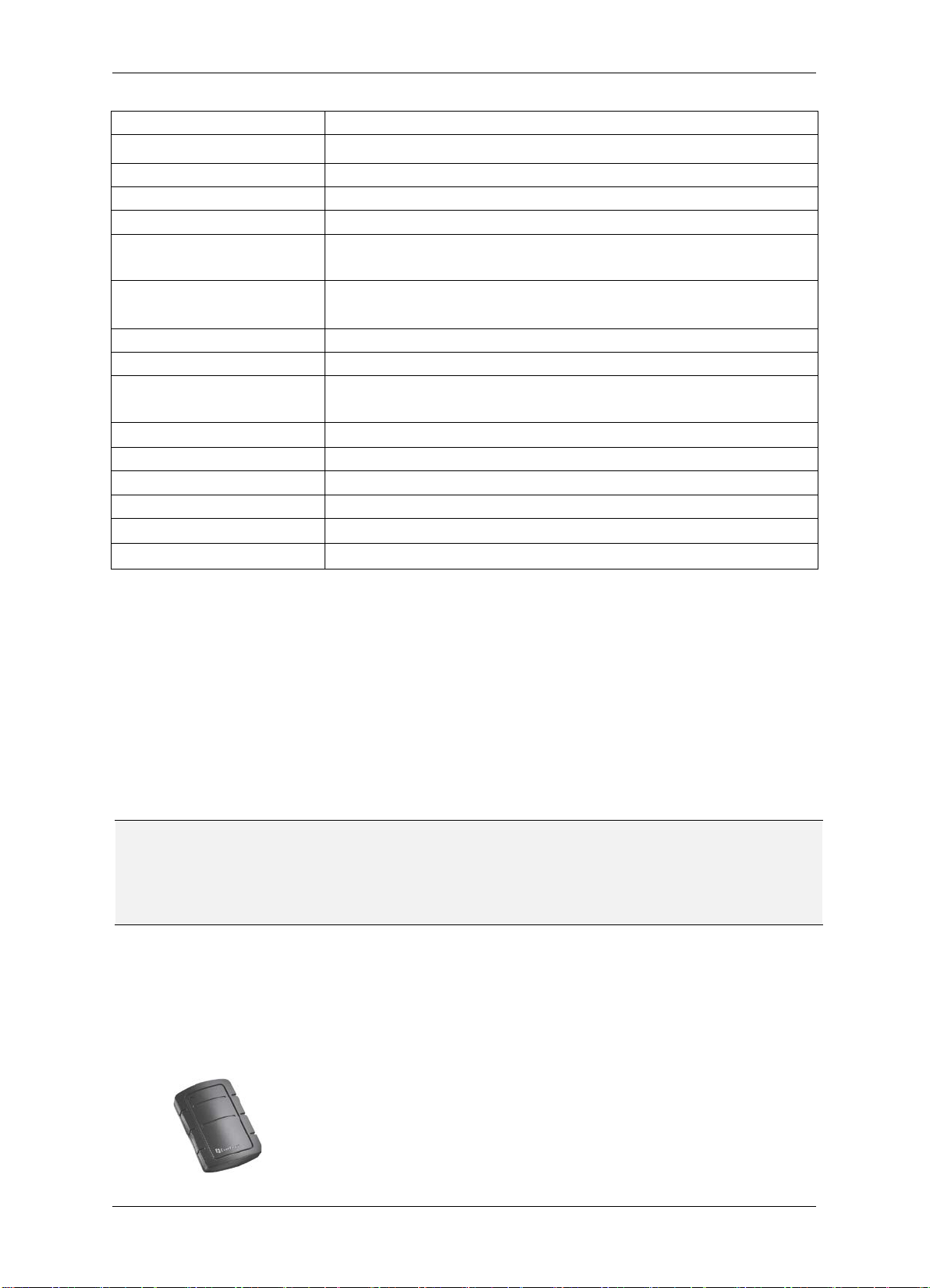
Power-Fail Protection
Yes
Real-Time Clock Yes
Anti-Dismantle Switch
Yes, N C
Keypad
3×4
Access Control Mode
13 modes
Multi-Card Door Open
supports 4 × 4 locking class, and allows 4-shift × 4-card
With Backlight,4×9 for Simplified Chinese,4×18 for English
Buzzer
Built-in
Driving Current of Door
4A (Max.)
Driving Current of
POE,12 VDC±15%,1A
Power Consumption
< 10W
Maximum Current
600mA
Dimension (L x W x H)
123mm×77mm×27mm
Operating Temperature
0
5%~95% (no condensation)
process. If any items are missing, notify your EverFocus Electronics Corp. Sales
Representative or Customer Service Branch. Please also keep the shipping carton for
TCP/IP Network Access Controller
Mode
LCD Display
Alarm Relay
(max.) multi-card door open setting
and Russian
4A (Max.)
Power Supply
℃~40℃
Operating Humidity
1.3 Packing List
Please check that there is no missing item in the package before installing.
EFC301F IP Access Control System x 1 (1 controller + 1 reader)
User’s Manual x 1
Mounting Kit for installing the reader:
- M3 mm *6 mm Screw x 2 sets
- ST2.9 mm *6 mm Screw x 2
- L-Type Spanner
Note: Contact the shipper if any items appear to have been damaged in the shipping
possible future use.
1.4 Optional Device
Optional device can expand your controller’s capabilities and versatility. Please contact your
dealer for more information.
EverFocus USB desktop card reader (ERU171/181)
3
Page 13
TCP/IP Network Access Controller
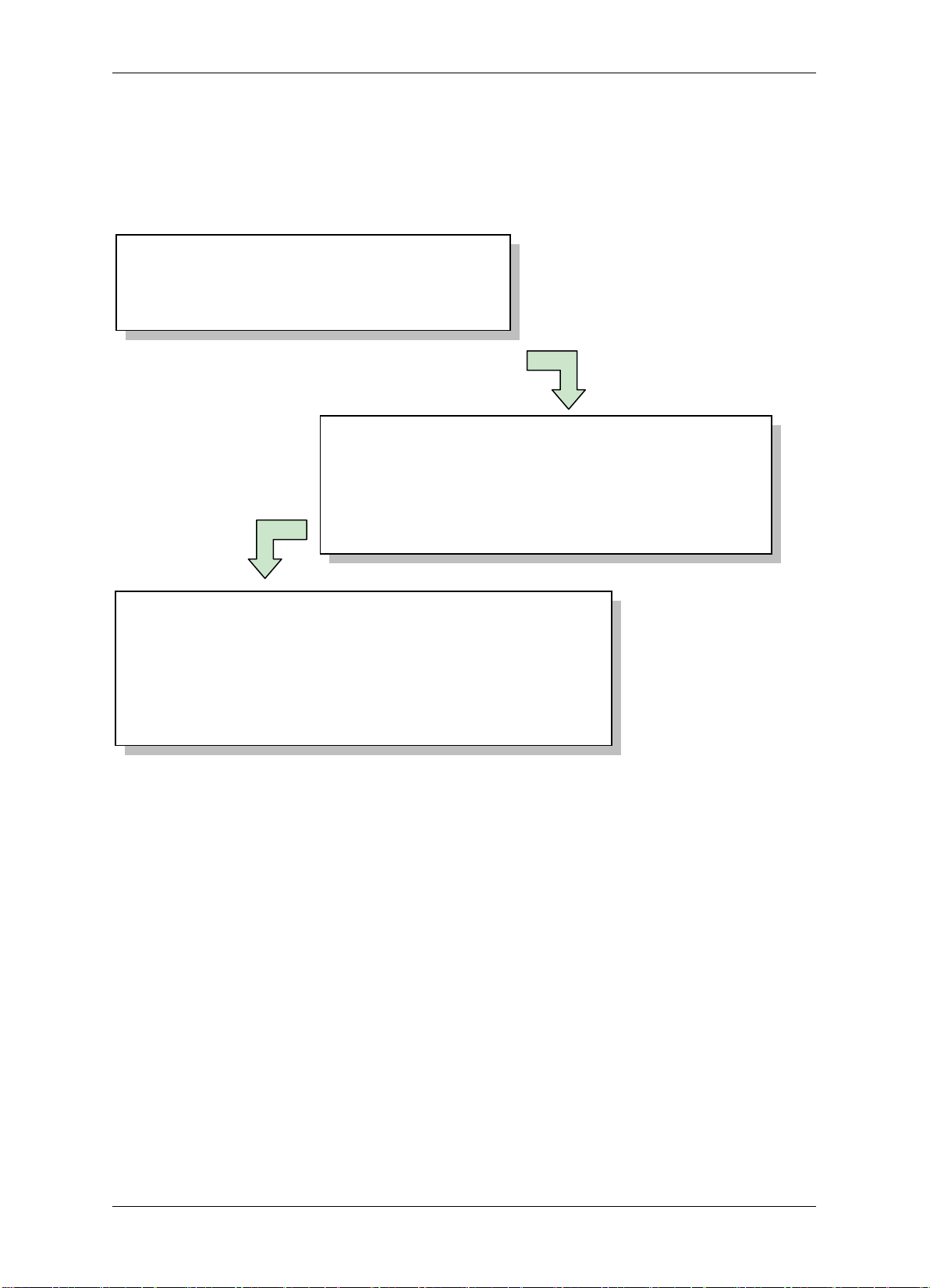
Step 1: Installation Preparation
Step 2: Hardware Installation
Step 3: Software Setup / Configuration
1.5 Installation Procedures
The Installation has three procedures described as below. Each procedure will be
introduced in the following sections in detail.
• Obtain a floor plan
• Determine the hardware and location
• Installing the controller
• Connecting to the door lock / open button / sensor / bell
• Connecting the controller to the network
• Connecting to the alarm input / output
• Log in controller built-in software through IE on computer
• Set up user account for user software
• Set up controller and other equipment
• Set holidays, shifts and door access rule
• Log in card and set up card attributes
1.6 Installation Preparation
Before installation, users are advised to collect information properly which will make the
installation more smoothly and helps to reduce time and energy cost. For professional
constructors, the information below will be of great use.
1.6.1 Obtain a Floor Plan
Obtain a floor plan of the building in which the access control system is to be installed.
Obtaining a floor plan helps the installer determine what components need to be installed,
and where. It also is essential in determining the length of cable needed to connect readers
to the controller. A floor plan can be a blue print of the building, a design, or simply a
drawing of the facility. Any document showing the footprint of the building can be used.
The dimensions are important to note, especially when determining cable lengths. A floor
plan may be obtained from your local city hall.
4
Page 14
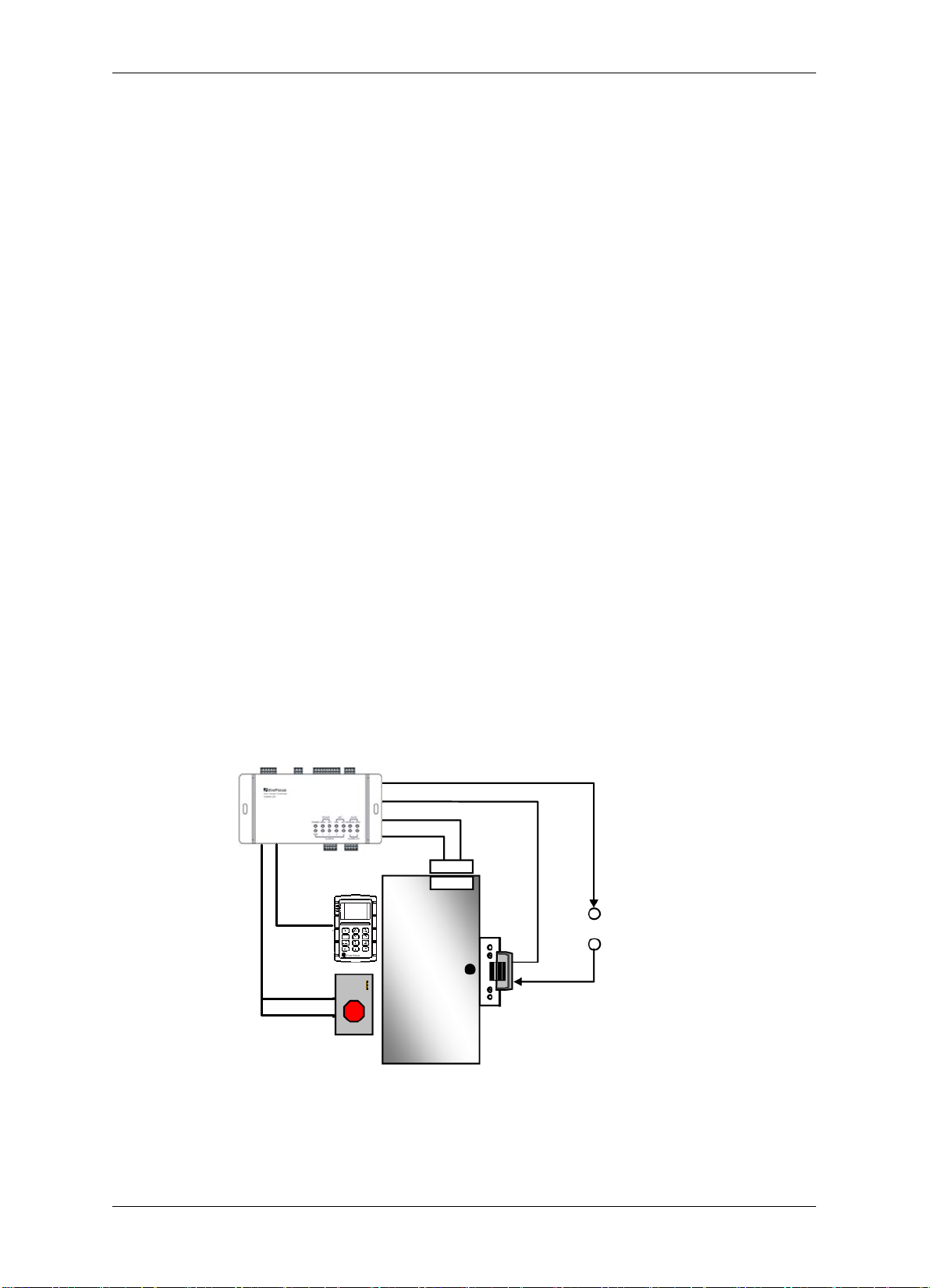
TCP/IP Network Access Controller
Additional
Power Supply
V-
V+
Door Lock
Door
Sensor
EFC301F
Reader
EFC301F Controller
Door Open Button
1.6.2 Determine the Hardware and Location
Determine which hardware to use and where it will be installed. This is the most crucial step
in the preparation stage. First, determine how many access points, or doors, need to be
managed by the access control system. These access points will control the security of the
facility, and can limit the entry and exit to and from any given area of the building. After
deciding which doors need to be controlled, the user must also determine the level of
security needed at each door. There are many ways to manage each door, using different
resources. These resources include, but are not limited to: proximity readers, mag strip
readers, relays, and request to exits. A few common door configurations are described
below:
1.6.2.1 One Set of EFC301F (One Reader) – The Basic Door Entry Control
The most basic configuration involves one EFC301F (controller + reader) and an electric
strike. In this configuration, a person presents a card to the reader, and is either granted
or denied access. The electric strike unlocks if the system grants access. Another
variation of this scenario involves setting the system up to monitor whether the door is
open, which allows the system to protect against propped open doors, or doors being
held open for too long.
1.6.2.2 One Set of EFC301F (One Reader) + One Door Open Button – Control of Exit
Adding a door open button to the above scenario allows the system to control when to
allow people to exit through a door. The door open button equipment includes a
button which has to be pressed when a card holder exits, or a door sensor. The
equipment should be arranged on the secure side of the door.
Figure 1-2
5
Page 15

TCP/IP Network Access Controller
1.6.2.3 One Set of EFC301F (Two Readers) – Control of both Entry and Exit
When the security grade is relatively high or the administrator requires the card holders
to get in or out at fixed time or date through specific door, one controller and two
readers are needed. Additional installation of one reader on the side of the door
requires the card holders to swipe the card when exiting and entering. This rule has
more reliable security regarding who can enter and who can exit and the administrator
can also master the entry and exit time of card holders.
1.6.3 Determine the Number of Controllers According to System Structure
Determine how many controllers and network interfaces are required.
Each EFC301F Controller can connect up to two readers. If the system requests installation
of more than two readers, the number of the controller will be increased. You can refer to
Chapter 3 for more details.
6
Page 16
TCP/IP Network Access Controller
Screws
Wall
Chapter
2
2 Hardware Installation
After the preparation work is finished, user can start installation. This chapter mainly
introduces how to install the hardware part, which is divided into four steps:
1. Install the controller.
2. Install the reader and connect the reader to the controller.
3. Connect the electric strikes or magnetic locks.
4. Connect the controller to the system computer and reader (optional).
2.1 Installing the Controller
The controller should be installed in an easily-accessible position. However, it should be
noticed that the controller is the core part of the entire system and can be used to change
database. After the installation site is selected, a relative secure clean position in which the
administrator is easy to operate should be selected. In order to facilitate power supply and
communication, a prepared wire chase must be arranged on the periphery of the controller
before installing the controller.
For installing the controller to the desired location, two screws or anchors have to be
prepared.
7
Page 17
TCP/IP Network Access Controller
POW
ER SENSOR1LOCK
3
AL
ARM IN
2 4
MA
IN A
UX
1 2FIRE
ALA
RM OU
T
DOORREADER
EverFocus
ControlUnit
RE
SET MAINREADER AUXREADERDCIN
CT
T
R
G
DCO
DAT
CT
DCO
G
DAT
NAV Access Controller
LNK ACT
NET
LAN
A
LA
RM
I
N D
OOR LOCKBUTTON&SENSOR ALARM OUT
OOMCOOM
C
M
E
D
D
D
D
D
TTON
D
NSOR
D
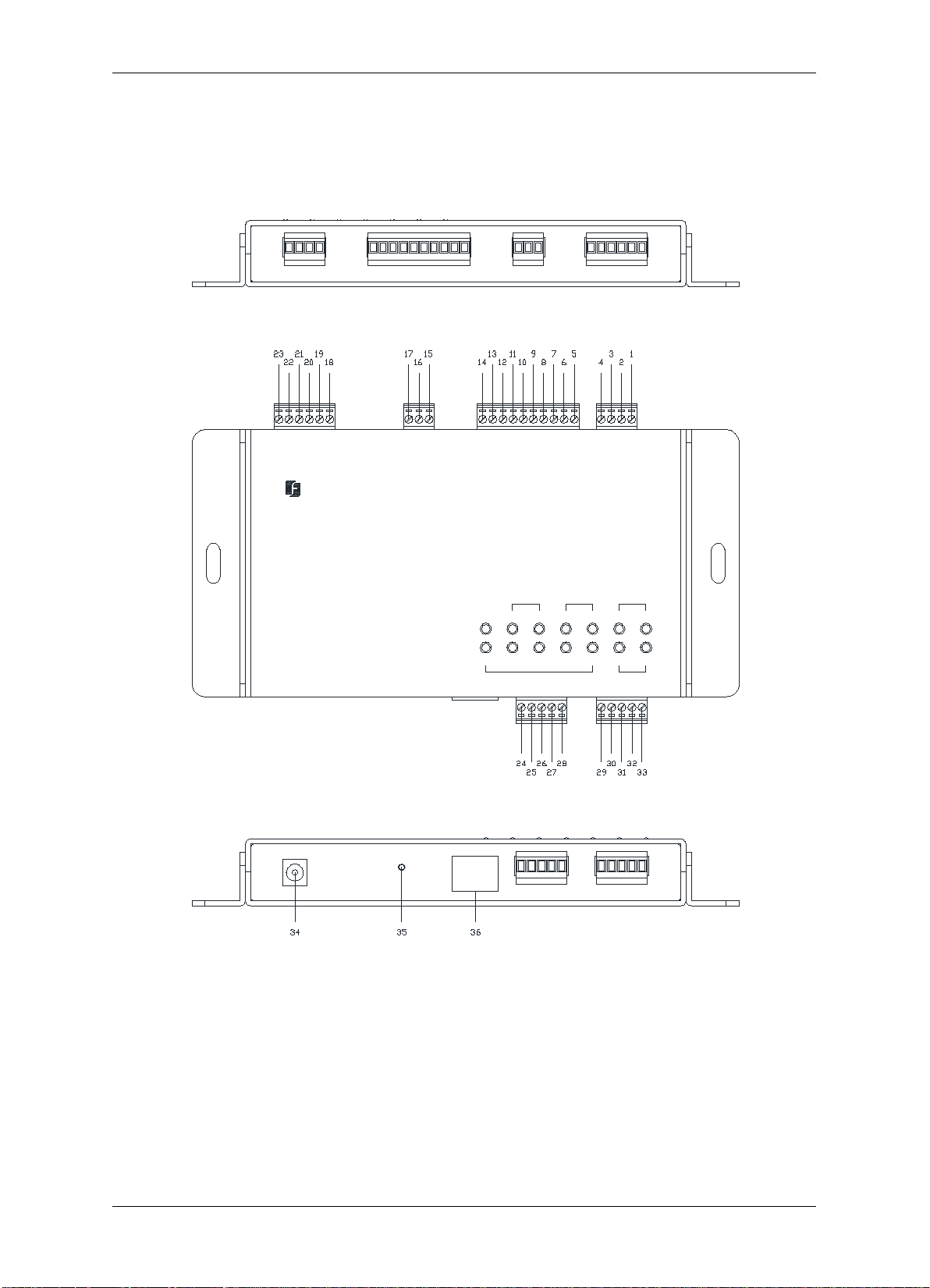
2.2 Definitions of Terminal Block and LEDs
You can connect up to two readers to the EFC301F controller. The images and tables below
show the information about the terminal block and LEDs.
8
Page 18
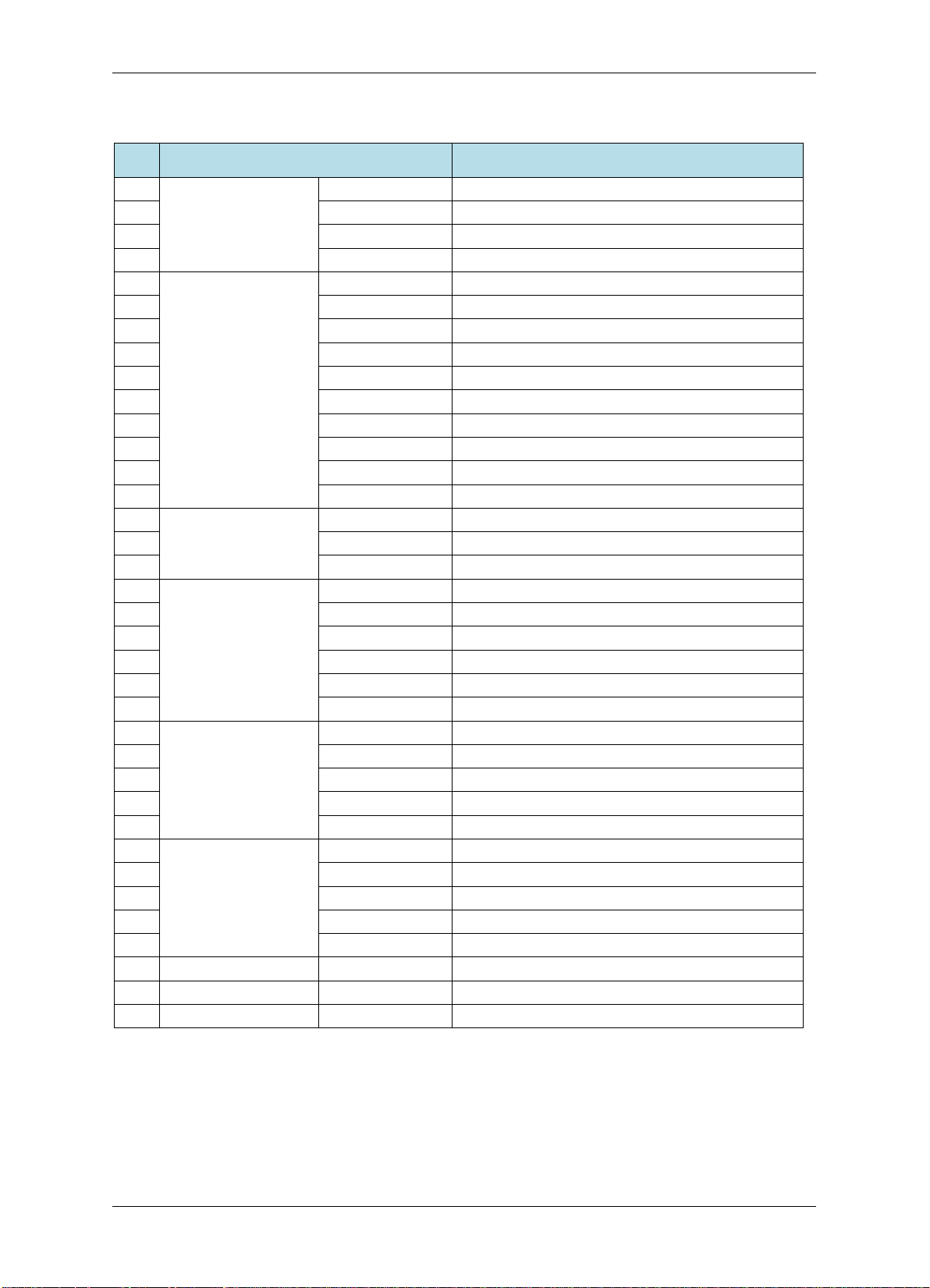
Tabl e 2-1 Terminal Block on the Controller
1
Button &Sensor
GND
Ground
2
SENSOR
Door sensor input
3
GND
Ground
4
BUTTON
Door button input
5
Alarm IN
GND
Ground for alarm input
6
IN 4
Alarm input 4
7
GND
Ground for alarm input
8
IN 3
Alarm input 3
9
GND
Ground for alarm input
10
IN 2
Alarm input 2
11
GND
Ground for alarm input
12
IN 1
Alarm input 1
13
GND
Ground for alarm input
14
FIRE
Fire alarm input
15
Door Lock
NC
Normally closed end of door lock
16
COM
Common terminal of door lock output
17
NO
Normally opened end of door lock
18
Alarm OUT
2NC
Normally closed end of alarm output 2
19
2COM
Common terminal of alarm output 2
20
2NO
Normally opened end of alarm output 2
21
1NC
Normally closed end of alarm output 1
22
1COM
Common terminal of alarm output 1
23
1NO
Normally opened end of alarm output 1
24
Main Reader
DCOUT
12 VDC power output for reader
25
GND
Ground
26
RXD
RS232-TXD (transfer)
27
TXD
RS232-RXD (receive)
28
CTRL
Controller output
29
Aux Reader
DCOUT
12 VDC power output for reader
30
GND
Ground
31
DATA0
Wiegand DATA0
32
DATA1
Wiegand DATA1
33
CTRL
Controller output
34
DC IN
12 VDC power input
35
RESET
Reset button
36
LAN
LAN port (network / PoE)
TCP/IP Network Access Controller
No.
Terminal Name Function
9
Page 19
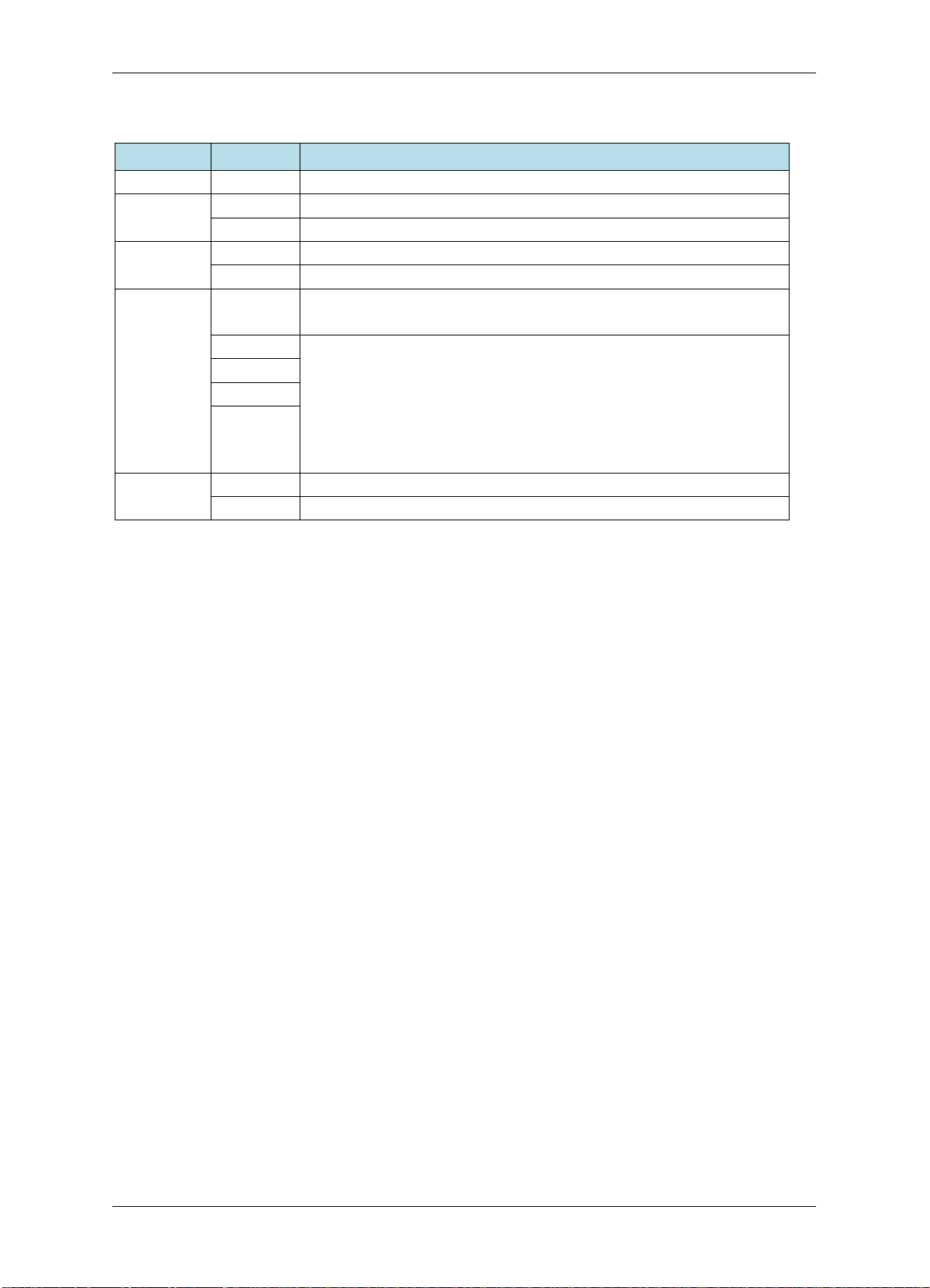
POWER
Light up to indicate the power is on.
MAIN
Light up to indicate the main reader is ready to use.
AUX
Light up to indicate the secondary reader is ready to use.
SENSOR
Light up to indicate the door is opened.
LOCK
Light up to indicate the door is closed.
Blink to indicate the fire alarm is triggered.
1
Continuously light up to indicate the protection setup success
input setup.
2
3
ALARM
1
Continuously light up to indicate the alarm output 1 is active.
2
Continuously light up to indicate the alarm output 2 is active.
Tabl e 2-2 Definition of LEDs on the Controller
LED Definitions
READER
DOOR
TCP/IP Network Access Controller
FIRE
ALARM IN
Continuously light up to indicate its in the protection status.
(in the protection setup statue).
Blink slowly to indicate the protection setup is progressing.
Blink quickly to indicate the alarm is triggered.
4
No light to indicate no protection setup or failure of alarm
OUT
2.3 Installing and Connecting the Readers
The reader has to be installed nearby the door and connected to the controller directly. You
can connect up to two readers to the EFC301F controller. The general procedure is
described below:
1. Mount each reader, following the instructions included with the reader. Typically, this
will include drilling two holes in the mounting wall, and then using the reader
mounting hardware to secure the reader to the mounting wall.
2. Once the readers are mounted, connect them to the door module. For wiring
definitions, please see previous sections in this manual.
The EFC301F controller can control up to two readers. The supported reader formats are
EverAccess RS232 and Wiegand format. For instructions on connecting each type, please
refer to Figure 2-1 for the RS232 reader connection and Figure 2-2 for the Wiegand reader
connection.
10
Page 20
2.3.1 RS232
controller to display the
connect an EverFocus RS232 reader with LCD display to the Main Reader terminal. The
for indicating the door
1
2
A B C
D E F
3
G H I4J K L
5 6
M N O
7
PQRS
T U V WXYZ
*
0 #
Red
Black
Yellow
Gray
Blue
Reader Ctrl
RX
TX
GND
+ 12V
98
32
33
30
31
29
Y
el
low
GND
+ 1
2V
37
38
35
36
3
4
Read
er
Ct
r
l
Black
R
ed
1
2
A B
C
D E F
3
G
H I
4
J K
L
5 6
M
N O
7
PQRS
T U V WXYZ
*
0 #
98
Re
ad
e
r_
Dat
a0
Re
a
de
r_D
ata
1
Bro
wn
Green
24
29
33
Terminal 29-33 signifies RS232 reader.
Figure 2-1 Connecting to the reader using RS232 format
TCP/IP Network Access Controller
25
26
27
28
2.3.2 Wiegand (Self-adaptive)
Terminal 34-38 signifies Wiegand reader. The controller will automatically adjust to the
Wiegand format of the card reader.
30
31
32
Figure 2-2 Connecting to the reader using Wiegand format
The EFC301F controller can provide 12 VDC voltage for two card readers. Twisted cable is
recommended to connect the controller and card readers.
Note: The EFC301F controller can connect up to two readers. The Main Reader terminal,
designed for connecting to the RS232 reader, allows the
management user interface on the LCD display of the reader. Therefore, it is required to
AUX Reader terminal is only for connecting to the Wiegand reader
status and alarm signals.
11
Page 21
TCP/IP Network Access Controller
V+
V-
N.C.
COM
16
17
15
COM
N.O.
V-
V+
16
17
15
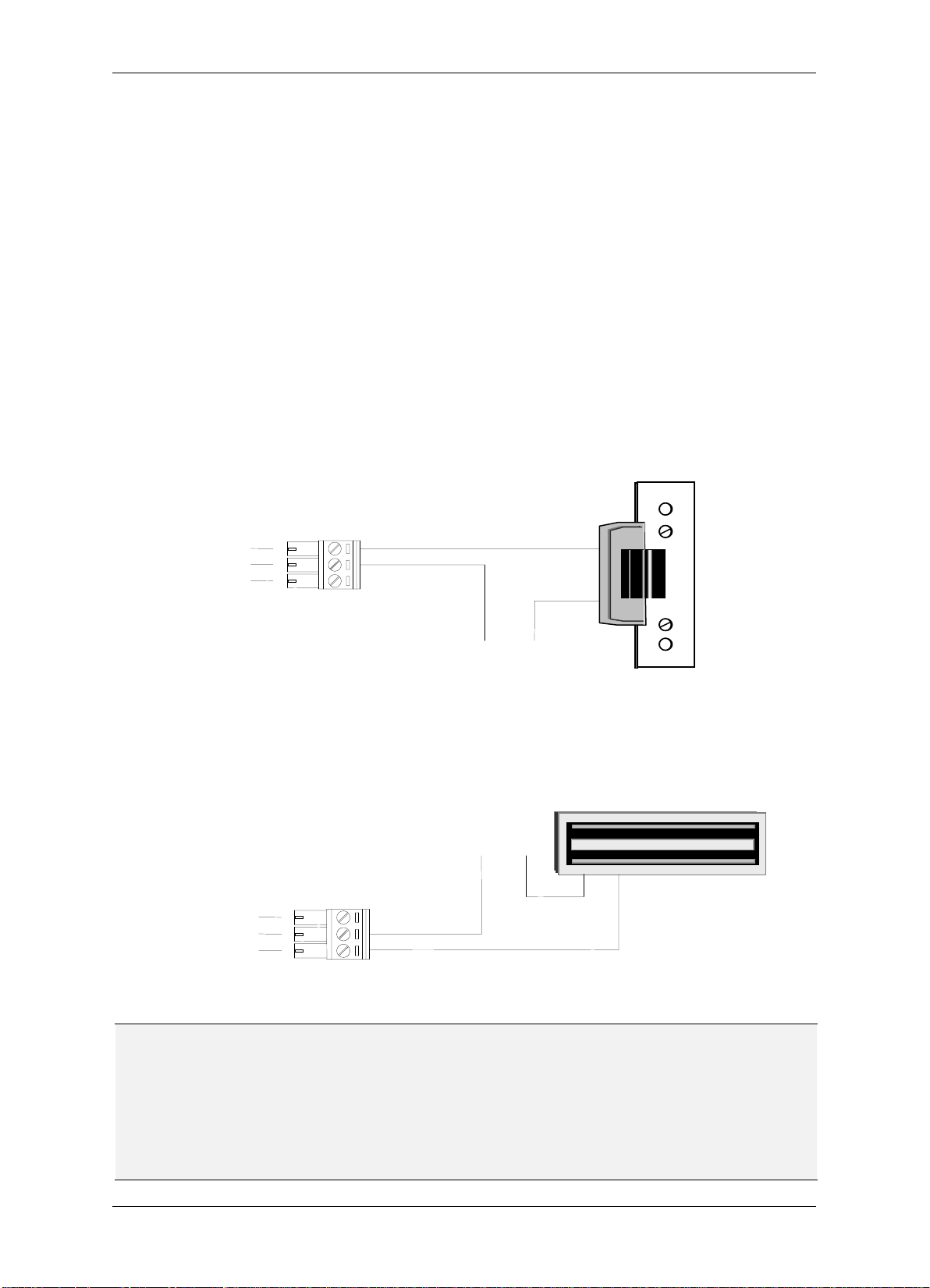
2.4 Connecting to the Door Lock
The controller provides one Door Lock terminal for locking / unlocking the door. You can
connect either an electric strikes or magnetic locks to the reader. Terminal 15 is used for
normally opened terminal (N.O.). Terminal 16 is used for common terminal (COM). Terminal
17 is used for normally closed terminal (N.C.).
The electrical door lock must have a separate power supply. The power supply for the
electrical door lock depends on the specification of the lock. Carefully choose the cable
connecting the door locks to fit the current draw. Two common types of electrical door
locks in the market are electric strike locks and magnetic locks. The connection methods for
these examples are shown in Figure 2-3 and Figure 2-4 respectively.
2.4.1 Connecting to an Electric Strike
Connect the Electric Strike to terminals 15-17 on the reader.
Figure 2-3 Example for connecting to an electric strike
2.4.2 Connecting to a Magnetic Lock
Connect the Magnetic Lock to terminals 15-17 on the reader.
Figure 2-4 Example for connecting to a Magnetic Lock
Note:
1. The maximum current outputted by the Door Lock relay on the controller is less than
5A. If the current of the door lock exceeds the capacity, an external power relay is
required.
2. V+ in the figures represents one lead of an external power source. When using DC
voltage, put the positive lead here. When using AC, the leads are interchangeable.
12
Page 22
TCP/IP Network Access Controller
Alarm sensor
for alarm in 1
Alarm input
GND
8
7
9
10
12
11
13
14
5
6
3 4 2 1 3 4 2
1
Door Sensor
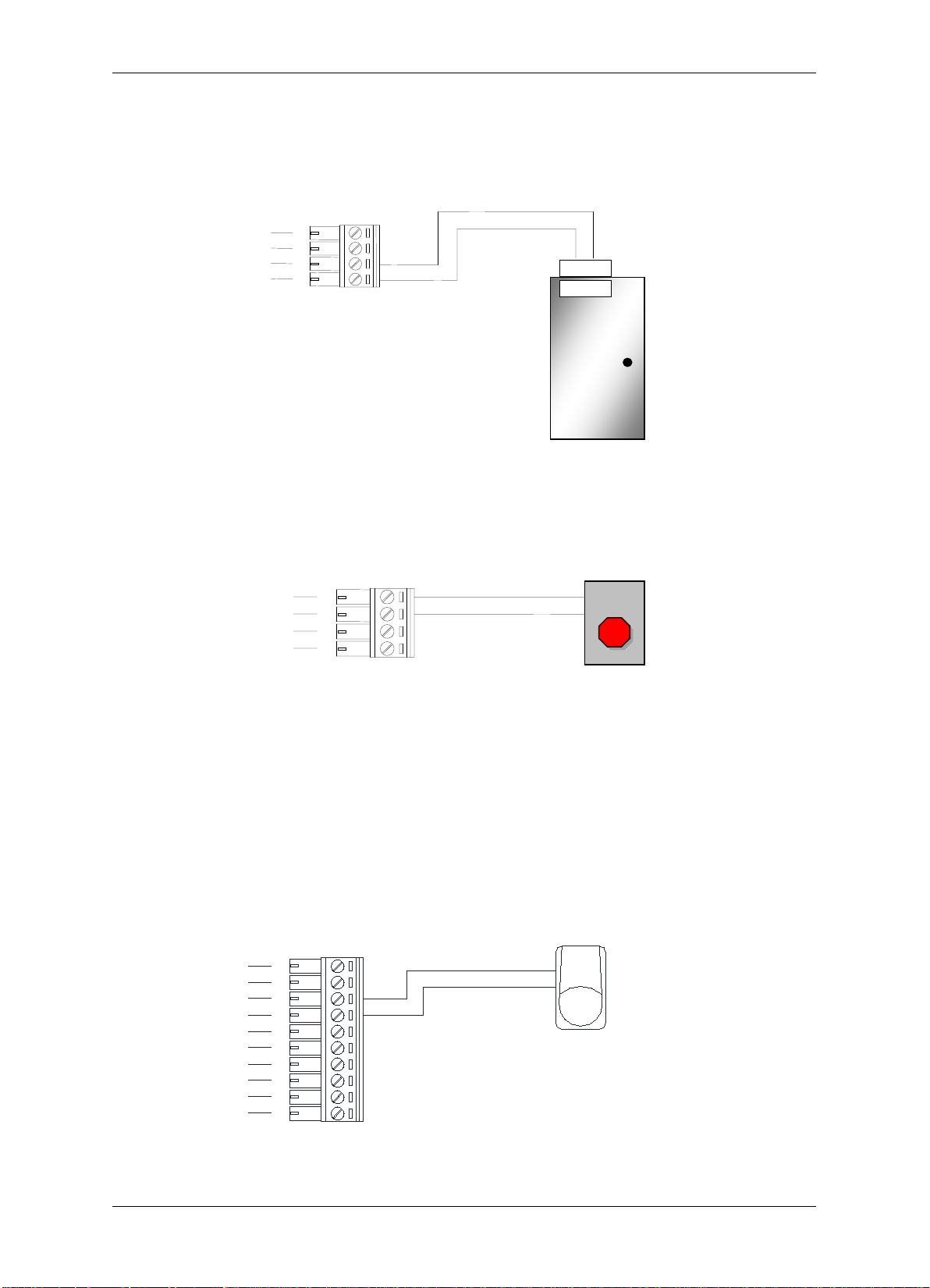
2.5 Connecting to the Door Sensor
The interface to the door sensor is also provided by the controller. Connect the door sensor
to terminals 1 and 2.
Figure 2-5 Example for connecting to the Door Sensor
2.6 Connecting to the Door Button
The interface to the door sensor is also provided by the controller. Connect the door sensor
to terminals 3 and 4.
Figure 2-6 Example for connecting to the Door Button
2.7 Connecting to the Fire Alarm
One fire alarm input is provided. The corresponding terminals are 13 and 14.
2.8 Connecting to the Alarm Input
Other than the fire alarm, 4 alarm inputs are provided. Using the alarm input 1 as an
example, the method to connect the alarm sensor to the alarm input 1 is shown in Figure
2-7:
Figure 2-7 Connecting the alarm sensor to the controller
13
Page 23
TCP/IP Network Access Controller
Exteral
Alarming
Device
C.terminal
N.O. terminal
COM
N.O.
21
20
22
23
18
19
N.C.
COM
N.C. terminal
C.terminal
Exteral
Alarming
Device
21
20
22
23
18
19
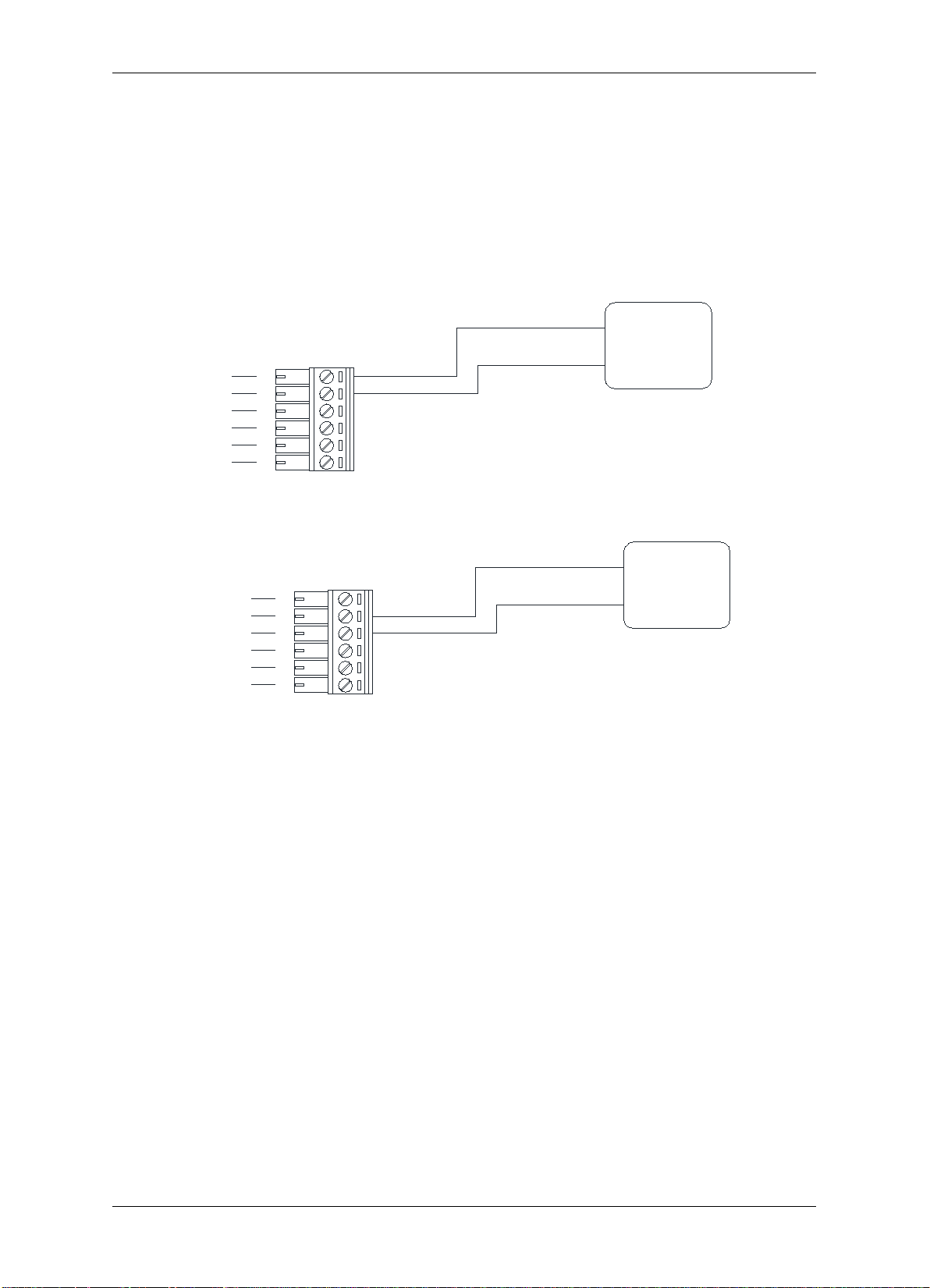
2.9 Connecting to the Alarm Output
Two alarm outputs are provided. Users can assign the corresponding relay status to the
different events. There are three terminals: COM, N.O. and N.C. The wiring depends on the
alarm device. Please read the user manual of the external alarm devices before wiring.
Using the alarm output 1 as an example, the method to connect the alarm device to the
alarm output 1 is shown in figures below:
Figure 2-8 Connecting to the N.O. alarm device
Figure 2-9 Connecting to the N.C. alarm device
14
Page 24
TCP/IP Network Access Controller
DAT
CT
DCO
G
DAT
RESET
MAINREADER AUXREADER
DC IN LAN
CT
T
R
G
DCO
Chapter
3
TCP/IP
POWER
SENSOR1LOCK
3
ALARMIN
2 4
MAIN AUX
1 2FIRE
ALARMOUT
DOORREADER
EverFocus
ControlUnit
NAVAccessController
LNK ACT
NET
P
OW
ER
SENSOR1LOCK
3
ALARMIN
2 4
M
AI
N AUX
1 2FIRE
ALARMOUT
DOORREADER
EverFocus
ControlUnit
NAVAccessController
LNK ACT
NET
Controller Controller
3 Connection
3.1 Connecting to the Computer through the TCP/IP
User can carry out basic setting through the keypad on the EFC301F reader or connection
with the computer via TCP/IP. User can carry complicated system administration by
accessing the embedded system in the controller through various browsers.
3.2 Connecting to Power
You can power the controller through a specific PoE network switch by connecting a
network cable to the LAN port on the controller, or by connecting a 12 VDC power source to
the power port on the controller.
Note:
1. The voltage range of power source for EFC301F controller is 12 VDC±15%. The
2. The distance from the power supply to the controller should be within 2 meters. In
Figure 3-1 Connecting to power
maximum current of the controller is 600mA.
addition, the electromagnetic lock and alarm equipment must be powered separately
from the controller. The controller can only supply power for controller and readers.
15
Page 25
TCP/IP Network Access Controller
RESET
RESET
3.3 Restoring the Controller
To restore the controller to the factory default settings, press the Reset button on the
controller using a paperclip.
Figure 3-2 Reset button on the controller
3.4 Before First Use
Before first use, please follow the instructions below:
1. Set up the IP address, date and time of the controller.
2. Set up the card properties.
3. Set up the alarm signals.
4. Set up the door settings.
5. Set up the date and time period.
16
Page 26
TCP/IP Network Access Controller
Chapter
4
4 Operation Instructions of Hardware
EFC301F integrates the card reader function, keystroke operation function, LCD display
function and control function. This chapter mainly introduces the functions of the system
and the relevant operating procedures. The simple settings of the controller can be
conducted through the keyboard and LCD display on the reader, and the operations of other
complex functions need to be controlled through the WEB browser. For details, please refer
to the description in the software chapter.
4.1 Operation Instructions of Keystrokes on the Reader
The 3×4 keyboard on the main card reader is shown in the figure above.
Main Interface
#: System function key
*: Protection setup / withdrawal key
Enter System Menu
#: OK
*: Cancel
“2”、“8”: Up and down movement
“4”: Enter previous menu. If no previous menu is available, return to main interface
“6”: Enter next menu
“5”: Select
1 2 3
4 5 6
7 8 9
* 0 #
17
Page 27

TCP/IP Network Access Controller
Input ARM PIN
2013-01-04
Input SYS PIN
2013-01-04
4.2 Operation of Home Page
After the system is installed, the LCD screen of the reader will display the date, day of the
week and time. This page is called the Home Page and various operations of the controller
will be correspondingly displayed here. After entering the system menu, each time “*” key
is pressed, it will return to the previous menu. In addition, not performing any operation for
1 min or continuously pressed “*”, will make the system automatically return to the Home
Page.
MON 09:38
Welcome
Press system key “#” on the Home Page and the system will request the user to input the
system administration password. See the figure below:
_ _ _ _ _ _ _ _
Cancel OK
After inputting the system password, press the confirmation key “#” to enter the “System
Setting” menu. The default password of the system is 00000000. For security purposes,
after entering the system for the first time, please change the password as soon as possible
and properly maintain the password. If an incorrect password is entered three consecutive
times, the system will automatically sound the alarm and lock the keyboard for 1 min. Then,
after pressing any key, the following screen will show up:
MON 09:38
Keyboard Locked!
Welcome!
Press “*” on the main interface of the system and the protection setup / withdrawal
administration. Interface will show up. First, the system requests that the user input the
alarm administration password.
_ _ _ _ _ _ _ _
Cancel OK
18
Page 28
TCP/IP Network Access Controller
The default password of the system is 00000000. After entering the alarm administration
password, press “#.” If an incorrect password is entered three consecutive times, the system
will automatically sound the alarm and lock the keyboard for 1 min. For security purposes, it
is suggested that the user change the password after entering the system for the first time
and properly secure the password.
After the protection setup administration authority is successfully verified, enter the
protection setup administration system. If there currently is an alarm input or latched alarm
input, the system will request to reset the alarm. The system will prompt the user to press
“#” to reset the alarm system, carry out protection setup or withdrawal
operation, press “#” to toggle between protection setup and protection
withdrawal and press “*” to exit and save the settings on exit. If carrying out protection
setup operation of the system, after exit, the system will enter protection setup delaying
state.
Alarm Reset?
[#] To Reset
System disarmed
[#] to Arm
System Armed
[#] To Disarm
Under the protection setup operation mode, the Alarm In LED lamp 1-4 on the casing of the
controller will indicate four different states, see Table 4-1:
Yell ow LED System Protection State
Off
On In protection setup state
Slowly blink
Rapidly blink
Table 4-1 States of Indicator Lamp
In protection withdrawal state
In protection setup delaying state
In protection setup state, and alarm triggered.
19
Page 29
TCP/IP Network Access Controller
Restore Expired Event
Auto Daylight
Set Language
Alarm Setting
System Setting
4.3 Main Menu of System Setting
After entering the System Setting menu, the numerical keys 2 and 8 have up and down
scrolling functions, respectively, the “*” key has the function of returning to the previous
menu or exiting the menu system and the “#” key has the function of confirming entry of
the current highlight menu. The main menu of the System Setting has eight submenu items.
After scrolling to the last menu item, continue rolling downward, it will return to the first
menu item.
Card Setting
Reader Setting
Door Setting
Address Setting
Set Network
System Info
4.4 System Setting
In the System Setting main menu, scroll to “System Setting” menu item and press “#” to
enter the “System Setting” menu. In the System Setting menu, there are 11 submenu items
in all. Users can carry out basic setup by selecting the corresponding menu items, such as
date, time, password, etc. After entering the “System Setting” menu, the following screen
will show up:
Set Date Format
Set Date
Set Time
Set SYS Password
Set ARM Password
Set Backlight
Roll up and down with the numerical keys 2 and 8 to select the menu items and press “#” to
enter the corresponding setup.
Erase All Events
Restore Factory Setting
20
Page 30

TCP/IP Network Access Controller
Set Language
*English
Set Language
4.4.1 Set Language
In the “System Setting” menu, scroll to “Set Language” menu item and press “#” to enter
the “Set Language” interfaces.
Set Date Format
Set Date
Set Time
Scroll to select Chinese, English or Russian, press “5” to select, press “#” to save setting and
exit and press “*” to cancel the setting.
简体中文
pyccknň
4.4.2 Set Date Format
In the “System Setting” menu, scroll to “Set Date Format” menu item and press “#” to enter
the “Set Date Format” interface.
Set Date Format
Set Date
Set Time
Users can select two date formats: “MM-DD-YY” or “YY-MM-DD.” The current date format is
displayed on LCD. Press “#” to toggle between the two formats. Press “*” to exit the data
display format setup interface. And return to the “System Setting” menu.
YYYY-MM-DD
[#]to toggle
MM-DD-YYYY
[#]to toggle
21
Page 31

TCP/IP Network Access Controller
Set Time
Set Language
Set Date (YYMMDD)
Set Language
4.4.3 Set Date
In the “System Setting” menu, scroll to “Set Date” menu item and press “#” to enter the
“Set Date” interface.
Set Date Format
Set Date
Set Time
Use the numerical keys to input the current date with 6 digits (YY: MM: DD).The year is set
in the range of 2000-2038. Press “#” to confirm the change to the new date.
20__-__-__
Cancel OK
4.4.4 Set Time
In the “System Setting” menu, scroll to the “Set Time” menu item and press “#” to enter the
“Set Time” interface.
Set Date Format
Set Date
Set Time
Use the numerical keys to input the current time with 6 digits (HH:MM:SS). The time is set
in the range of 00:00:00--23:59:59. After input is finished, press “#” to confirm.
__:__:__
Cancel OK
22
Page 32

TCP/IP Network Access Controller
Set Date
Auto Daylight
Auto Daylight
Set Date Format
4.4.5 Set Summer Time (Daylight Savings)
In the “System Setting” menu, scroll to “Auto Daylight” menu item and press “#” to enter
the “Auto Daylight” interface.
Set Date
Set Time
Auto Daylight
Press “#” to toggle between summer time on/off and press “*” to exit. The setting is
finalized upon exit.
saving:
OFF
[#]to toggle
saving:
On
[#]to toggle
When the summer time setting is enabled, the controller will automatically adjust to the
summer time, i.e. the a.m. 1:59:59 of the first Sunday in April is adjusted to a.m. 3:00, and
the a.m. 1:59:59 of the first Sunday in October is adjusted to a.m. 1:00:00.
4.4.6 Set SYS Password
The user is requested to input the system administration password before setting the
controller. The default password of the system is 00000000. For security purposes, it is
suggested that the user changes the password before using the controller and properly
secure the password. Once the password is lost, the system administration password has to
be reset after general reset, meanwhile, the data in the system will be deleted.
In the “System Setting” menu, scroll to the “Set SYS Password” menu and press “#” to enter
the “Set SYS Password” interface.
After inputting a new system administration password, press “#”twice to confirm. The
system will display whether the new password takes effect. If the two passwords entered
are different, the system will prompt to reset.
Set Time
Auto Daylight
Set SYS Password
23
Page 33

TCP/IP Network Access Controller
Passwords mismatch
Setting updated
Repeat:
Input ARM PIN
Set Time
Passwords mismatch
Setting updated
Repeat:
Input SYS PIN
_ _ _ _ _ _
Cancel OK
_ _ _ _ _ _
Cancel OK
successfully
Please retry
Pressing “*” before pressing “#” for confirmation, the new password will not take effect and
the system will return to the previous menu.
4.4.7 Set ARM Password
Before protection setup and withdrawal of the controller, the alarm administration
password must be input through the keyboard. The default alarm administration password
is 00000000.
In the “System Setting” menu, scroll to “Set ARM Password” menu item and press “#” to
enter the “Set ARM Password” interface.
After inputting a new system administration password twice, press “#” to confirm and the
system will display whether the new password takes effect. If the passwords entered are
different, the system will prompt to reset.
Auto Daylight
Set SYS Password
Set ARM Password
_ _ _ _ _ _
Cancel OK
successfully
_ _ _ _ _ _
Cancel OK
Please retry
24
Page 34

TCP/IP Network Access Controller
Restored events
Restorable event
Set SYS Password
System Backlight
System Backlight
Set ARM Password
Set Backlight
4.4.8 Set Backlight
In the “System Setting” menu, scroll to the “Set Backlight” menu item and press “#” to
enter the “Set Backlight” interface.
Erase All Events
Timeout Time
Press “#” to toggle between the “Normal Open” state and the “Automatic Control” state of
the backlight. Automatic control refers to the backlight that will be on for every keystroke
operation or card swiping. If there is no subsequent operation, the backlight will turn off
after 1 min. Press “*” to exit. The setting will be finalized on exit.
Self-motion
[#]to toggle
normal open
[#]to toggle
4.4.9 Restore Expired Event
This function is designed for restoring all the expired events to the system. In the “System
Setting” menu, scroll to the “Restore Expired Event” menu item and press “#” to enter the
interface.
Set ARM Password
Set Backlight
Restore Expired Event
Press “#” to restore the events.
4.4.10 Erase All Events
The controller can record all events occurring after being powered. When the event records
are full (the maximum number of event records is 1,000,000 events), the new event records
will overwrite the earliest event records.
09025
09025
25
Page 35

TCP/IP Network Access Controller
Are you sure back
Set Backlight
Restore Factory Setting
Are you sure to
Set ARM Password
All event records can be cleared through the following instructions. In the System Setting
menu, scroll to the “Erase All Events” menu item and press “#” to enter the “Erase All
Events” interface.
Set Backlight
Restored Expired Event
Erase All Events
The system will prompt the user to re-confirm that all the event records will be deleted and
will be unrecoverable after pressing “#.”
erase all eve-nts
Device is oper
-ating OK
record?
Cancel OK
4.4.11 Restore Factory Setting
This function can restore the controller to the default setup.
In the “System Setting” menu, scroll to the “Restore Factory Setting” menu item and press
“#” to enter the “Restore Factory Setting” interface.
Restored Expired Event
Erase All Events
The system will prompt the user to re-confirm that the general reset operation will be
carried out after pressing “#.”
to Restore Factory?
Cancel OK
Device is oper
-ating…
26
Page 36

TCP/IP Network Access Controller
Index #.: 00001
Index #.: 00001
Add Card
System Setting
Card Setting
Loading…
4.5 Card Setting
In the “System Setting” main menu, scroll to “Card Setting” menu item and press “#” to
enter the “Card Setting” submenu.
Reader Setting
Door Setting
All function setups under the Card Setting menu will be introduced below.
4.5.1 Add Card
In the “Card Setting” submenu, scroll to “Add Card” menu item and press “#” to enter the
“Add Card” interface.
Delete Card
Set Card Properties
When adding a card, the controller will generate a serial number for each newly added card.
User can swipe the card or manually input the card number and then press “#” to confirm.
Then the system will add this card to the controller. If the card already exists in the system,
the system will show: Card Already Exists.
Card ID:
_ _ _ _ _ _ _ _ _ _ _
Card ID:
000009251887
Cancel OK
Cancel OK
27
Page 37

TCP/IP Network Access Controller
Are you sure to
Please card or input
Please card or input
Delete One Card
Delete All Cards
Add Card
Delete Card
Card already existed
Added Card
successfully
4.5.2 Delete Card
The user can directly delete the card from the controller through the card number or delete
all cards at one time. In the “Card Setting” submenu, scroll to the “Delete Card” menu item
and press “#” to enter the “Delete Card” submenu. Users can choose between the two card
deletion methods.
Set Card Properties
4.5.2.1 Delete One Card
The controller can delete one card through its card number. The card number
corresponding to the card to be deleted has to be inputted manually or by swiping the card.
In the “Delete Card” submenu, scroll to the “Delete One Card” menu item and press “#” to
enter the “Delete One Card” interface. The system will request the user to input the card
number.
After inputting the card number, press “#” and the system will prompt: “Delete Card?” Press
“#” to delete. If the card does not exist in the system, the system will show: “Unknown
Card .”
card ID…
_ _ _ _ _ _ _ _ _ _ _
delete Card?
000009251887
Cancel OK
card ID…
000009251887
28
Page 38

TCP/IP Network Access Controller
Unknown Card
Please card or input
Please card or input
Add Card
Delete Card
Set Card Properties
Are you sure to
Unknown Card
Deleted Card
successfully
4.5.2.2 Delete All Cards
In the “Delete Card” submenu, scroll to the “Delete All Cards” menu item and press “#” to
enter the “Delete All Cards” interface. The system will request the user to reconfirm
whether to delete all cards. Press “#” to delete all cards.
delete all Card?
Cancel OK
Device is oper
–ating OK
Caution: This operation will delete all card information from the controller.
4.5.3 Set Card Properties
In the “Card Setting” menu, scroll to “Set Card Properties” menu item and press “#” to
enter the “Set Card Properties” interface. The system will prompt the user to input the card
number. If the card does not exist in the system, the system will prompt “Unknown Card.”
card ID..
_ _ _ _ _ _ _ _ _ _ _
card ID..
000009251887
After inputting the card number, press “#” to enter the card attribute setup menu. Each
card has seven attributes that can be changed. Scroll to select the menu item to be set. And
press #” to enter the setup interface of the corresponding item.
29
Page 39

TCP/IP Network Access Controller
Please place admin
PIN Setting
Status setting
Administrator Setting
ARM Setting
First Card
Modify ID
Modify PIN
4.5.3.1 Status setting
Scroll to the “Status setting” menu item and press “#” to enter the “Status setting” interface.
Press “#” to toggle between two statuses. The system displays the current status of the card.
Press “*” to exit and the setting is finalized on exit.
Card enabled
[#]to toggle
Card disabled
[#]to toggle
4.5.3.2 Administrator Setting
Scroll to the “Set Administrator” menu item and press “#” to enter the “Set Administrator”
interface. Press “#” to toggle between two statuses. The system displays the current status
of the card administrator function. Press “*” to exit and the setting is finalized upon exit.
Admin enabled
[#]to toggle
Admin disabled
[#]to toggle
If a card is set to open the administrator function, the card holder will be assigned as the
system administrator. If there are one or more cards with administrator authority in the
system, the interface will request to verify the administrator card when logging into the
controller. Then, please swipe the administrator card or manually input the card number of
the administrator card.
Card...
_ _ _ _ _ _ _ _ _ _ _
30
Page 40

TCP/IP Network Access Controller
Please place arm
4.5.3.3 ARM Setting
Scroll to the “ARM Setting” menu item and press “#” to enter its interface. Press “#” to
toggle between two statuses. The system displays the current status of the protection setup
function. Press “*” to exit and the setting is finalized upon exit.
ARM disabled
[#]to toggle
ARM enabled
[#]to toggle
If a card is set to be valid for the protection setup function, the card holder will be assigned
as the protection setup administrator. If there are one or more cards with the protection
setup administrator authority in the system, the interface will request to verify the
administrator card when logging into the controller. Then swipe the administrator card or
manually input the card number of the administrator card.
admin Card...
_ _ _ _ _ _ _ _ _ _ _
4.5.3.4 First Card
Scroll to the “First Card” menu item and press “#” to enter its interface. Press “#” to toggle
between the two statuses. The system displays the current status of the first card function.
Press “*” to exit, and the setting is finalized upon exit.
Swiping the card with the first card function at the controller terminal will trigger the door
normal open setting in the Access Access Rule (this setting is involved in the Access Control
regulation rules in the embedded software of the controller – door region scheme setting).
4.5.3.5 PIN Setting
Each card has an 8-digit password and the password status can be set to be valid or invalid.
If the door entry/exit rule is set to be using card or password, the door can only be opened
using the independent password of the card whose password is set to valid, i.e. if user
wants to open the door with the independent password, the password in the card has to be
set to valid. Scroll to “PIN Setting" menu item and press “#” to enter its interface. Press “#”
to toggle between the two statuses. The system displays the current status of the card
password function. Press “*” to exit, and the setting is finalized upon exit.
First Card:
disabled
[#]to toggle
First Card:
enabled
[#]to toggle
31
Page 41

TCP/IP Network Access Controller
Passwords mismatch
Setting updated
Repeat New PIN:
Input New PIN:
Card already existed
Setting updated
Input New ID:
Input New ID:
PIN disabled
[#]to toggle
PIN enabled
[#]to toggle
4.5.3.6 Modify ID
Each card has a unique card number and the card number can be changed.
Scroll to the “Modify ID” menu item and press “#” to enter its interface. Input a new card
number and press “#” to change. Then the system will show: “Change successful.” If the
same card already exists in the system, the system will show: “Card Already Exists.”
_ _ _ _ _ _ _ _ _ _ _
000009251887
successfully
4.5.3.7 Modify PIN
Each card has an 8-digit password and the password can be changed.
Scroll to the “Modify PIN” menu item and press “#” to enter its interface. The system will
prompt the user to input a new card password. After inputting, press “#” to confirm, then
the system will prompt the user to input it again. If the passwords input are identical, the
system will successfully change the password. Otherwise, the system will not change the
password.
_ _ _ _ _ _ _ _
Cancer OK
_ _ _ _ _ _ _ _
Cancer OK
successfully
Please retry
32
Page 42

TCP/IP Network Access Controller
Timeout Time
Timeout Time
Set SYS Reader
System Setting
4.6 Reader Setting
Card reader properties can be directly set up on the controller, including system reader, aux
reader and the allocation of readers to doors.
Card Setting
Reader Setting
4.6.1 Enter Reader Setting Menu
In the “System Setting” main menu, scroll to “Reader Setting” menu item and press “#” to
enter the “Reader Setting” submenu.
Set AUX Reader
4.6.2 Set SYS Reader
The Set SYS Reader menu includes Timeout Time and Direction settings. You can set up the
timeout time for PIN input. When users input wrong password or no operation is activated
within the setup time, the system will return to the main menu automatically. The Direction
setting is used to control the entry/exit direction and indicate the allocation of readers to
door.
4.6.2.1 Timeout Time
In the “Reader Setting” menu, select “Set SYS Reader” menu item and press “#” to enter its
interface.
Direction
Select “Timeout Time” menu item, press “#” to enter the interface below. Use the numeric
buttons to input time. The time range limit is between 000 Min 03 Sec and 999 Min 59 Sec.
Press “#” to confirm and the setting will take effect. Press “*” to erase the input time and
re-input the time.
000 Min 10 Sec
Cancel OK
33
Page 43

TCP/IP Network Access Controller
AUX Reader Keypad:
AUX Reader Keypad:
Timeout Time
Set SYS Reader
Direction
Direction
4.6.2.2 Direction
In the “Reader Setting” menu, select “Set SYS Reader” menu item and press “#” to enter its
interface. Select “Direction” menu item, press “#” to enter the interface below. The LCD will
display the status of the direction. Press “#” to toggle between Entry and Exit status. Press
“*” to exit and the setting will take effect.
Entry
[#]to toggle
Exit
[#]to toggle
4.6.3 Set AUS Reader
The settings for AUS reader are similar to the SYS reader except the Keypad setting. In the
“Reader Setting” menu, select “Set AUS Reader” menu item and press “#” to enter its
interface.
Note that the AUS reader only supports Wiegand format. There is only Wiegand signal input,
no Wiegand signal output.
Set AUS Reader
The setup procedures of Timeout Time and Direction of AUS reader are the same with SYS
re a der. To enable / disable the Keypad function of the AUX reader, press “#” to toggle
between disabled and enabled. Press “*” to exit and the setting will take effect.
4.7 Door Setting
EFC301F controls a single door. The user can set the door open time, door over time and
door open mode.
In the “System Setting” main menu, scroll to the “Door Setting” menu item and press “#” to
enter the “Door Setting” submenu. Scroll to select different menu items.
[#]to toggle
Direction
Keypad Setting
disabled
34
enabled
[#]to toggle
Page 44

TCP/IP Network Access Controller
Door Over Time
Door Open Time
Set Open Time
Set Over Time
Door Access Mode
4.7.1 Set Open Time
The door open time is the door open time after the valid card is swiped or the door open
button is pressed and the default value is 3 seconds. The maximum time set on the
controller is 999 min 59s. if the door open button is pressed, the door will open. The door
open time is started after the door open button is released. Scroll to the “Set Open Time ”
menu item and press “#” to enter its interface.
000 Min 03 Sec
Cancel OK
For setting the minutes, input three digits in the range of 0-999, and for setting seconds,
input two digits in the range of 0-59. Press “#” to confirm and the setting will take effect.
Press “*” to exit and the setting will not take effect.
4.7.2 Set Over Time
The door status switch is used to detect the open/closed status of the door. In general cases,
the door is closed. In case of door opening, the door should be closed after being opened
for a period of time, during which the controller may not receive the signal from the door
status switch. At the end of the door open time, if a door which should be closed is not
closed, timing will start and the recorded time is the Door Over Time. When the time has
exceeded, the controller will generate an alarm. The default Door Over Time is 10s.The
maximum Door Over Time set on the controller is 999 min 59s.
Scroll to “Set Over Time” menu item and press “#” to enter its interface.
For setting “minutes,” input three digits in the range of 0-999 and for setting “seconds,”
input two digits in the range of 0-59. Press “#” to confirm and the setting will take effect.
Press “*” to exit and the setting will not take effect.
000 Min 10 Sec
Cancel OK
35
Page 45

TCP/IP Network Access Controller
Normal Close
ormal Open
Follow schedule
Door Entry Mode
4.7.3 Door Access Mode
Select “Door Entry Mode” or “Door Exit Mode” menu item and press “#” to enter the
submenu. Select the desired mode and press the numerical key “5” to select. The selected
item is marked with a “*”. Then, press“*” or“#” to exit the current interface.
Door Exit Mode
*Card Only
Card + PIN
Card or PIN
N
4.8 Alarm Setting
The EFC301F controller provides 1 fire alarm input, 4 alarm inputs and 2 alarm outputs.
Users can carry out detailed configurations through the user interface. Details will be
introduced below.
4.8.1 Composition of Alarm
The alarm input of the EFC301F controller can be connected with external alarm equipment
such as a PIR sensor, glass breakage sensor, etc and the alarm output can drive a 4A alarm
relay.
4.8.2 Basic Configuration of the Alarm
The EFC301F controller will record all events such as entry permit, entry prohibition, etc.
Some dangerous events are required to trigger alarm output, such as fire alarm input,
protection area alarm input, etc. Some events do not need alarm output, such as card
swiping operations at invalid times. Whether the alarm is required to be triggered will be
set according to the user’s requirement. EFC301F collects all the event records that may
trigger alarm output and makes effective or ineffective alarm choices of these events.
All major events can be set to trigger alarms, such as alarm input signals, unknown cards,
expired cards, invalid cards, invalid door regions, invalid times, anti-passback failure, wrong
password, wrong system password, wrong protection setup/withdrawal password, forced
door open, Door Over Time and remote alarm. The detailed setup method will be
introduced below.
36
Page 46

TCP/IP Network Access Controller
Door Action on
Door Action on
Input mode:*NO
AlarmIN Type:2
AlarmIN Type:
AlarmIN Type:
AlarmIN Setting
4.8.3 Enter Alarm Setting Menu
In the “System Setting” main menu, select “Alarm Setting” menu item and press “#” to
enter the submenu. The submenu of the “Alarm Setting” has “AlarmIN Setting” and “Alarm
Action Setting” submenu items for setting physical alarm input and alarm output time of
alarm events, respectively.
Alarm Action Setting
4.8.4 AlarmIN Setting
Select the “AlarmIN Setting” menu item and press “#” to enter its interface. Because the
controller only has one alarm input circuit, the system will display the alarm type of the
current alarm input. The default alarm type of the alarm input port of the system is a fire
alarm. The user can scroll to the alarm type to be set and press the numerical key “5” to
select. Press “#” to save the current setting and enter the next step.
Cancel Next
4.8.4.1 Fire Alarm Setting
There are two fire alarm input modes: Normally Opened and Normally Closed. Normally
Opened means the circuit disconnects in the normal condition (i.e. without input) and
connects with activated inputs. Normally Closed is the opposite: the circuit connects in the
normal condition (i.e. without input) and disconnects with activated inputs.
Cancel Next
Alarming:
Open
* Other
Fire
Others
*Fire
[#]to toggle
Others
*Fire
Cancel Next
NC
Alarm Port:1 2
N N
Alarming:
Close
[#]to toggle
37
Page 47

TCP/IP Network Access Controller
Alarm Time
Delay Timeout
Input mode: *NC
Input mode: *NO
AlarmIN Type:
Scroll to the preset input mode, press “5” to select. After finishing the setup, press “#” to
save the current setting and enter the door and fire alarm linkage setup interface. In case of
a fire alarm, the door may have two actions: open and close. Press “#” to toggle between
open and close.
The system displays the current door action when a fire alarm sounds. Press “*” to exit, and
the setting is finalized upon exit.
4.8.4.2 Other Alarm Setting
If the set alarm is another type, the general Alarm Setting interface will show up. The
general Alarm Setting has three steps: First, set input mode; then set protection setup delay
time; and finally set the alarm time.
*Other
Fire
Cancel Next
NO
* Latch
Output mode:
* Latch
NC
Output Mode:
Step 1: Select the input mode to be set and press “5” to confirm. There are three input
modes: Off, normally opened and normally closed. Select Off will invalid the alarm input.
The NO and NC mode settings are the same as those in Chapter 4.8.4.1 Fire Alarm Setting.
After selecting the input mode, input the focus to transfer to the output mode check box,
select the output mode to be set and press “5” to confirm. There are two output modes:
latch and transparent. If a latch mode is selected, when the alarm output is withdrawn, the
system will keep the alarm output until the end of the alarm time; and if transparent output
mode is selected, the alarm output and alarm input will occur and be withdrawn
simultaneously. After selecting the input and output modes, press “#” to save the current
settings and enter the protection setup delay time setting interface.
Step 2: After protection setup of the system is conducted, the system requires a period of
time to respond to the alarm input from the protection area, which is called the alarm delay
time. The default alarm delay time is 30s. After inputting the protection setup delay time,
press “#” to save the current setting and enter the alarm time setting interface.
000 Min 30 Sec
Cancel OK
001 Min 00 Sec
Cancel OK
38
Page 48

TCP/IP Network Access Controller
Alarm Time
SYS PIN Fail
Cancel Next
Panic Open Alarm
Card Pin Fail
Expire Card Alarm
SYS PIN Fail
Step 3: In case of an alarm, the alarm output will last for a period of time, which is called
the alarm time. When the alarm exceeds this period of time, the alarm will be automatically
cleared (except for fire alarm, which can only be manually reset).The default alarm time is 1
min. After inputting the alarm time, press “#” to save the current setting. The system will
return to the submenu of the “Alarm Setting.”
4.8.4.3 Alarm Action Setting
The Alarm Setting can set the alarm with physical input, as well as the alarm output time of
illegal events, such as the unknown card, invalid card, expired card, invalid time, invalid door
region, etc.
In the submenu of the “Alarm Setting,” select the “Alarm Action Setting” menu item and
press “#” to enter the submenu to set the alarm output time. The submenu has 13 menu
items. Select the corresponding alarm events and Alarm Action Setting for the
corresponding events.
ARM PIN Fail
Remote Alarm Out
Unknown Card
Invalid Card Alarm
Invalid Time Alarm
ABP Fail Alarm
Forced Open Alarm
Held Open Alarm
Panic Open Alarm
Reader Lost Alarm
For example, in case of setting the SYS PIN Fail, in the submenu, select “SYS PIN Fail” menu
item and press “#” to enter the alarm time setting interface. All the outputs of alarm events
are latched modes and their settings are similar to the physical alarm input time setting.
The setting steps of other alarm events are the same as those of the SYS PIN Fail Setting.
Alarm Port: 1 2
Y N
000 Min 10 Sec
Cancel OK
4.9 Address Setting
Each device connected to the same RS485 bus must have a unique address for the purpose
of communications and control. When multiple controllers connect to PC via an RS485 bus,
each controller must be assigned a distinct address.
39
Page 49

TCP/IP Network Access Controller
DHCP Setting:
DHCP Setting:
DHCP Setting
Address:
Press the numerical keys to input the address. The range is between 0000~9999. “#” to
confirm and the setting will take effect. Press “*” to exit and the setting will not take effect.
The default address is 0000.
0000
Cancel OK
4.10 Set Network
In the system main menu, select the “Set Network” menu item with numerical key “2” or “8”
and press “#” to enter this menu item. In the submenu items, select DHCP Setting, Set IP
Address or Reset Network Setting.
Set IP Address
Reset Network Setting
4.10.1 DHCP Setting
Select the “DHCP Setting” menu item and press function key “#” or numerical keys “5” or “6”
to enter the setting menu.
On
[#]to toggle
Press “#” key to switch between “ON” and “OFF”. Press “*” to confirm the DHCP status
setting and exit.
If DHCP is ON, it will get an IP address after controller connected to internet.
Off
[#]to toggle
4.10.2 Set IP Address
Select the “Set IP Address” item and press the function key “#” or numerical keys “5” or “6”
to enter the interface.
40
Page 50

TCP/IP Network Access Controller
2012-01-04
2012-01-04 09 :25
Ver: 1.0.0-2
IP Address:
___.___.___.___
Cancel OK
Input the IP address to be set and press “#” to confirm. Press “ * ” to exit. Factory default IP
address: 192.168.1.200.
4.10.3 Reset Network Setting
Select the “Reset Network Setting” item and press the function key “#” or numerical keys “5”
or “6” to enter the setting menu.
Are you sure?
Press “#” to confirm “Reset Network Setting”, and press “*” to exit.
4.11 System Info
In the main menu of the System Setting, select the “System Info” menu item and press “#”
to enter the System Info display interface. Display the hardware version of the current
controller, amount of stored user cards and total amount of recorded events.
MAC: _ _:08:43:22
Cards: 00100
Events: 0003098
4.12 Introduction of System Operation
4.12.1 Door Open by Swiping Card
0009251826
Access granted
Welcome to EverFocus
MON 09:25
Access denied
Welcome to EverFocus
41
Page 51

TCP/IP Network Access Controller
2010-01-04 089:25
2010-01-04
Input Card PIN
If the swiped card has the corresponding user name, after successful authentication, the
user name information of the card holder and “Auth Successful” will be displayed. If the
user name information is not set, the card number of the swiped card will be displayed. If
the card is not available in the system or the card has no door open function, “Auth Fails”
will be displayed.
4.12.2 Door Open with Single Password
In the main interface, press any numerical key and the password input interface will show
up.
_ _ _ _ _ _ _ _
Cancel OK
The user has three chances to enter the correct password. If all the three inputs are wrong,
“Auth Fails” will display. If the password is correct, “Auth Successes” will display. If the card
number is not displayed and “********” is shown on the screen, the door open when
single password is successful.
4.12.3 Door Open with Both Card and Password
If the authentication is passed after swiping the card, a password window will show up to
request input of the password of the corresponding card.
4.12.4 Door Open with Multiple Cards
In the event that the door is opened only when several card holders swipe the cards at the
same time, after receiving the first card with door opening authority, the controller will
display prompting messages for user information and successful authentication and this will
last 3 seconds. Then a message will prompt for the user to swipe the next card and the
remaining time. If the system receives the next legal card before the end of the time, the
system will display a message of user information and successful authentication and last 3
seconds and then open the door. If the door is still not opened, the system will reset the
remaining waiting time and continue waiting for more cards until the door is opened and
the state before swiping cards is restored. In the above process, the system will not
repeatedly accept the same card. If during the process of waiting for the next card, the
MON 09:25
Access denied
Welcome to EverFocus
********
Access granted
Welcome to EverFocus
42
Page 52

TCP/IP Network Access Controller
2013-01-04 09:35
2013-01-04 09:25
system receives an illegal card, the system will be restored to the state before swiping the
card.
Name
Access granted
Welcome to EverFocus
Wait
Next Card…
4.12.5 Specific Door Control Mode
Normally Closed Mode: If the current door mode is normally closed, the system will regard
any card as an illegal card and prohibit entry and exit.
Normally Opened Mode: If the current door mode is normally opened and the door is in the
opened state, the system will not automatically lock. If the normally opened mode is newly
set, the system will judge whether the door needs to be opened with the first card
according to the configuration. In the event that the door needs to be opened with the first
card, the system will open the door after verifying a card with the first card authority and
keep the door lock in the unlocked state. In the event that the door is opened without the
first card, the system will directly unlock and open the door.
Service Time Period Mode: In this mode, the system will automatically switch the door open
mode according to the preset control strategy and the unlocking and door open manner in
the specific time period will be determined by the specific control strategy. The time period
mode is set in the embedded software of the controller.
43
Page 53

TCP/IP Network Access Controller
Chapter
5
5 Software Introduction
5.1 Main Functions
Not only can the EFC301F controller be conducted basic settings on the controller but also
advanced system setting by a browser logging in the embedded software (hereinafter
referred to as Software). The EFC301F controller can store and maintain related data and
provide basic attendance-checking functions according to the data.
The software has a concise page layout and clear classification of functional modules. The
windowing structure design facilitates convenient and effective system management, the
convenient home page layout enables users to understand the operating content at a
glance and the graphical toolbars enables users to operate in a more visual way.
The software carries out hierarchical authorization management and can be logged in to
only by inputting a username and password for identity authorization, so as to protect the
system from being illegally accessed. The database is encrypted to avoid illegal access to the
database. Users can be granted with authority capable of distinguishing the Cardholder
logged in and the users divided into different User Groups use different system functions.
The settings of a duress password and multi-card door open through the system can
manage the entry/exit of the Access Control system in a more safe and effective way, so as
to enhance the security of the Access Control system.
5.2 Profiles of Highlighted Features
Supports various auxiliary hardware
Supports multiple operating system platforms
Good user page layout design and convenient operation
Database management
Supports multiple language patterns
Special features
The software supports a desktop card reader, USB card reader, etc.
Applicable to Windows 2000 and the later versions of Windows Operating System
User page layout with Vista style
Adopt fire-new icon design
Supports FTP, local database backup/restore
Supports Simplified Chinese, English and Russian
User-friendly interface for door region, protection region, alarm input/output, fire
alarm and other real-time statuses.
Supports remote operation of the controller, door region, protection region, alarm,
and remote control.
Supports duress password door open and multi-card door open
Optionally adjust the size of the operating window and the operating region
Practical attendance management function with convenient operation
44
Page 54

TCP/IP Network Access Controller
5.3 TCP/IP-based Architecture of Access Control System
Figure 5-1 Diagram of system architecture
45
Page 55

6 Getting Started
Chapter
6
This chapter will instruct how to rapidly set the EFC301F TCP/IP-based Access Control
integrated device through the browser using the identity of a super administrator and how
to realize door open by swiping a card and Attendance functions.
6.1 Quick Start
6.1.1 Set Access Rule
6.1.1.1 Set Date
Click the menu bar “Access Control” “Access Rule” “Date Type” to enter the interface
of data settings. Following are instructions for how to add a date (for detailed settings,
please refer to 12.1 Date Type).
Operation Procedures:
1) Select date cycling type.
2) Select date in the calendar.
3) Select date type.
4) Input remarks.
5) Click the “Save” button.
6.1.1.2 Set Door Schedule
Click the menu bar “Access Control” “Access Rule” “Door Schedule” to enter the
interface. Following are instructions for how to add a door schedule (for detailed settings,
please refer to 12.2 Door Schedule).
Operation Procedures:
1) Input the name of a new schedule in the textbox.
2) Click the time period of “Daysetting,” set time period and entry/exit mode in the
3) Click the “Save” button to save the settings.
6.1.1.3 Set Group Schedule
Click the menu bar “Access Control” “Access Rule” “Group Schedule” to enter the
interface. Following are instructions for how to add a group schedule (for detailed settings,
please refer to 12.3.1 Add Group Schedule).
Operation Procedures:
1) Click the “Add” button to enter the adding page.
2) Input the name of a new schedule in the textbox of “Schedule Name.”
3) Click the time period of “Daysetting,” a dialog box will pop up, in which the time period
TCP/IP Network Access Controller
pop-up dialog box, save and close the dialog box.
46
Page 56

TCP/IP Network Access Controller
and the door entry/exit mode can be set.
4) After settings the mode of various date types, click the “Save” button, then the new
schedule is added into the Group Schedule list.
6.1.1.4 Set Access Group
Click the menu bar “Access Control” “Access Rule” “Access Group” to enter the
interface. Following are instructions for how to add an access group (for detailed settings,
please refer to 12.4.1 Add Access Group).
Operation Procedures:
1) Input the name of a new access group in the “access group name“ textbox.
2) Select the unlocking levels corresponding to the locks.
3) Select a schedule name.
4) Click the “Save” button to finish the settings.
6.1.2 Multiple Card Addition Methods
The software provides multiple methods to add cards into the system. Any method can be
selected to realize this function. Following are instructions for how to add a card and
allocate it into the corresponding control group.
The default control group is “Full Granted” and the default password is “000000.” First,
select the format of the card to be added.
6.1.2.1 Rapid Card Addition
When a user logs in to the software and swipes a card on the controller, the card swiping
record will be displayed in the system event records and can be copied (for details, please
refer to 6.3.4.2 Illegal Card Swiping Records).
Operation Procedures:
1) Swipe the card to be added to the card reader connected with the controller in which
the card is added.
2) Log in to the software, then the card swiping record will appear in the system event
records (entry/exit card swiping records or illegal card swiping records). Copy the card
number.
3) Select the correct card format.
4) Add one new card in the card page, paste the card number in and click the “Save”
button to finish addition.
6.1.2.2 Card Page
Click the menu bar “Access Control” “Card” “Card Settings” to enter the page of card
settings. Following are instructions for how to add a card and allocate it into the access
group (for detailed settings, please refer to 4.5 Card Setting).
Operation Procedures:
1) Click the “Add” button to enter the card adding page.
2) Fill in card attributes.
3) If the Cardholder member is already in the system, allocate the card to one employee.
47
Page 57

TCP/IP Network Access Controller
4) Select the access group to which the card belongs in the pull-down menu of the “Access
Group.”
5) Or click the “Private Schedule” to allocate a special control scheme for the card. When
the card has a “Private Schedule” applied, the design is used for authentication in case
of door entry/exit and it has the highest control priority.
6) Click the “Save” button to finish addition.
6.1.2.3 Import into Card with Excel File
Edit card data in Excel (no limit to card quantity), save as csv. file and register the card to the
controller through the card import function of the software (whether the card is required to
be register to the controller depends on the control group settings of the card; if no control
group option is selected, the default control group “Full Granted” will be granted.)
Click the menu bar “Access Control” “Card” “Import Cards”.
Operation Procedures:
1) Click the “Browse” button, select the Excel file to be imported and click “Next.”
2) Select the corresponding value of the related column name.
3) Click the “Import” button to finish the addition.
6.1.3 Set Department and Cardholder
6.1.3.1 Set Department
Click the menu bar “System” “Cardholder” “Department Setting” to enter the page of
department setting. Following are instructions for how to add a new department (for
detailed settings, please refer to 8.1.1 Add Department).
Operation Procedures:
1) Click the “Add” button
2) Fill in the name of the department
3) Select the superior department
4) Click the “Save” button to finish addition.
6.1.3.2 Set Cardholder
Click the menu bar “System” “Cardholder” “Cardholder Setting” to enter the page of
Cardholder setting. Following are instructions for how to add new Cardholder (for detailed
settings, please refer to 8.2.1 Add Cardholder).
Operation Procedures:
1) Click the “Add” button, then a Cardholder adding dialog box will pop up.
2) Fill in employee number, name, department and other information of the Cardholder
member and upload his/her photo.
3) A new card can be added to the Cardholder therein.
4) Click the “Save” button to finish addition.
48
Page 58

TCP/IP Network Access Controller
6.1.4 Configure and Manage Attendance
6.1.4.1 Set Date
Click the menu bar “Access Control” “Access Rule” “Date Type” to enter the interface
of data settings. Following are instructions for how to add a Weekend (for detailed settings,
please refer to 12.1.1 Add Date).
Operation Procedures:
1) Select date Rectype.
2) Select date in the calendar.
3) Select date type.
4) Input remarks (optional).
5) Click the “Save” button to add a new date in the list.
6.1.4.2 No-Access-Attendance
Click the menu bar “Attendance” “Attendance Exception” “No-Access_Attendance” to
enter the page. Following are instructions for how to register a record of not swiping a card
(for detailed settings, please refer to 16.1.1 Add No-Access-Attendance).
Operation Procedures:
1) Click the “Add” button.
2) Select one record in the Cardholder list and set card swiping time and comment
information.
3) Click the “Save” button.
6.1.4.3 Overtime Enroll
Click the menu bar “Attendance” “Attendance Exception” “Overtime Enroll” to enter
the page. Following are instructions for how to register overtime (for detailed settings,
please refer to 16.3.1 Add Overtime Enroll).
Operation Procedures:
1) Click the “Add” button.
2) Select one record in the Cardholder list and set the card swiping time, working hours
and comment information.
3) Click the “Save” button.
6.1.4.4 Time-off Enroll
Click the menu bar “Attendance” “Attendance Exception” “Time-off Enroll” to enter
the page. Following are instructions for how to register a leave record (for detailed settings,
please refer to 16.2.1 Add Time-off Enroll).
Operation Procedures:
1) Click the “Add” button.
2) Select one record in the Cardholder list and set card swiping time and comment
information.
3) Click the “Save” button.
49
Page 59

TCP/IP Network Access Controller
6.1.5 Real-time Monitoring
Click the menu bar “System” “Real-time Monitoring” “Real-time Event.” The display in
the middle part of the page is the real-time entry/exit status of Cardholder in the system.
The display on the right side of the page is the detailed information of the Cardholder in
and out.
6.1.6 Export Function
Most functional modules in the system provide an “Export” function. Click the “Export”
button in the page to export the information in this page in the csv format, then the file
save dialog box will pop up. See the figure below:
Figure 6-1 Export
Click the “Save” button and select the path to save the file. See the figure below:
Figure 6-2 Save
After selecting the path, click the “Save” button to finish the operation. Csv file exported
successfully
!Note: If Chinese characters are included in the content, file conversion will be required. If
the file is directly opened with Excel, the part containing Chinese characters will be
displayed as Wingdings. For the file conversion operation on the import/export part in the
system, please refer to the following procedures which will not be repeatedly described.
50
Page 60

TCP/IP Network Access Controller
Operation Procedures:
Right click the saved csv file and select “Edit” in the pull-down menu.
By default, the file is opened with notepad. Select “File” in the menu bar “Save as,” then
the dialog box will pop up. See the figure below:
Figure 6-3 Convert exported file
1) In the dialog box, select “All Files” as Save type, and select “UTF-8” as code.
2) Click the “Save” button to finish conversion.
3) Open the converted file with Excel and check whether the Chinese characters are
normally displayed.
6.1.7 Print Function
Most functional modules in the system provide “Print” functions. Click the “Print” button in
the page to enter the print page (see Figure 6-4). The menu bar includes an Export Report,
Print Report, Refresh, Switch Tree, Go to First Page, Go to Previous Page, Go to Next Page,
Go to Last Page, Go to Page, Close Current View, Search Text, Zoom, and other functional
operations. The operations of printing in the system are all the same and will not be
repeatedly described.
Figure 6-4 Print user information
51
Page 61

TCP/IP Network Access Controller
6.2 First Use
6.2.1 Login Page
Open browser and input the IP address of the controller in the address bar. If the user does
not carry out any settings for the IP address, the default IP address of the controller will be
192.168.1.200. Following the prompts on the page, input login name, password and
identifying code and Click the “Login” button. See Figure 6-5:
Figure 6-5 Login
Select the language of the operation page at the right upper corner of the page. The
EFC301F controller supports Chinese, English and Russian languages.
The factory defaults for logging in to the EFC301F controller are:
Login name: Admin
Password: Admin
!Note: Admin is a special “super administrator” which is mainly designed for system
installation and restoration. The “super administrator” has all authority for operating the
software and is unchangeable. The user itself can not be deleted and only the password can
be changed. Please change and remember well the password after the first login to ensure
the security of the software.
The password of the super administrator is carried out through “System” “Basic Setting”
“Change Password.” The super administrator can create users and change the authority
of the user through “Basic Setting” “User Group” “Add.” If all other users are deleted
and the password of the super administrator is lost, then the software cannot be accessed.
After inputting a username and password in the login page, select whether “login with the
identity of central server user,” and then click the “Login” button to enter the browser page
of the EFC301F controller.
If the username or password is wrong, a dialog box indicating illegal login will pop up. See
Figure 6-6:
52
Page 62

TCP/IP Network Access Controller
Control
Menu Bar
Login
Information
Real-time Electronic Map
System Event
Detailed
Information
Figure 6-6 Illegal login
6.3 Get Familiar with the Browser Page
6.3.1 Introduction of the Main Page
The page adopts a humanized design concept to ensure users get familiar with it as soon as
possible. After logging in to the system, the user will enter the main page of the program.
See the figure below:
Panel
Cardholder
Cardholder
Status Display Region
Record Display
Region
Figure 6-7 Main page
6.3.2 Menu
The menu is composed of the System, Access Control and Attendance (see Figure 6-8). Click
each main menu item to expand its submenu options and click each option of the submenu
to start the corresponding function. The specific functions will be introduced in detail in the
latter chapters.
Figure 6-8 Menu bar
If a login user has no access authority to a certain module function, the function will not be
displayed on the menu bar.
53
Page 63

TCP/IP Network Access Controller
Click this button to
6.3.3 Control Panel
Click below the menu, then the “Control Panel” on the left side of
the main page will be hidden (see Figure 6-9). When user clicks the button or double clicks
the hidden bar, the list will be displayed and the main page is restored to the original.
display list
Figure 6-9 Hiding the control panel on the left side
6.3.3.1 Control Panel
The control panel features various buttons including Open Door, Lock and Freeze, Frozen
Door Release, Arm, Disarm, Alarm and Reset Alarm.
Figure 6-10 Equipment list
54
Page 64

TCP/IP Network Access Controller
6.3.4 System Event Record
The region displays all the event records of the system, including normal card swiping
records, illegal card swiping records, operation control records, alarm records, etc.
6.3.4.1 Entry/Exit Card Swiping Records
This type of record includes normal card swiping records and password door open records.
The content of the entry/exit card swiping records includes event time, cardholder name,
entry or exit and card number. Select a certain event record and then the information of the
cardholder can be seen on the right-side panel.
Figure 6-11 Entry/exit card swiping records
6.3.4.2 Illegal Card Swiping Records
This type of record includes unknown cards, expired cards, invalid cards, wrong card
passwords, invalid door regions, invalid time periods and duress entry.
The content of the illegal card swiping records includes event time, cardholder name, entry
or exit, card number and event.
Figure 6-12 Illegal card swiping records
6.3.4.3 Operation Control Records
This type of record includes the records of the remote operation of the controller in the
software, the records of protection setup/withdrawal on the controller, the records of
restore alarm, the records of door open with the door open button, etc. (For details, please
refer to 9.1 Real-time Event).
The content of operation control records includes event time and event.
55
Page 65

TCP/IP Network Access Controller
Figure 6-13 Operation control records
6.3.4.4 Alarm Event Records
This type of record includes protection region alarm, fire alarm, wrong system password,
wrong protection region password, anti-dismantle alarm, forced door open, duress door
open and door open timeout (For details, please refer to 11.1 Controller Setting).
The content of alarm event records includes event time and event.
Figure 6-14 Alarm event records
6.3.4.5 Other Records
The other records related to the controller in the system include events lost.
The content of system settings records includes event time and event.
Figure 6-15 System settings records
56
Page 66

TCP/IP Network Access Controller
Chapter
7
7 Basic Setting
This chapter will introduce the Basic Setting of the EFC301F controller in detail, which
includes changing passwords, User Group, User Setting, Local Server, system upgrade and
central server configuration.
Change password: Change login password.
User Group: Add, delete and change the User Groups in the software. The quality of the
User Groups has no limit and the user can add the User Group(s) as required.
User Setting: Add, delete and change the user who can log in to and use the software. By
default, the software generates admin as a super user who has all the operation authorities
of the software. The user can only change the password of the super user.
Local Server: Set the IP type, address, gateway, date, time, etc. of NAV controller.
System upgrade: Support online upgrade and local upgrade.
Central server configuration: Configure the system settings.
7.1 Change Password
The changed password is the login password by which the user logs in to the embedded
software of EFC301F through the browser and only the current login password can be
changed.
First, input the old password, then input the new password and input the new password
again and then click the “Save” button. The contents of the new password and repeat
password must be the same. If the input content has an error, click the “Reset” button to fill
it in again.
Figure 7-1 Change login password
57
Page 67

TCP/IP Network Access Controller
Function
system
manager
common user
Change password
√ √ √
User Group
√
User Setting
√
Local Server
√ √
System upgrade
√
Central server
√
Department settings
√ √
Cardholder Setting
√ √
Import Cardholders
√ √
Real-time event
√ √ √
Cardholder
√ √ √
Data backup
√ √
Data restoration
√ √
Expired data clear
√ √
7.2 Set User and Authority
In the system, one user means one person who operates the software. Due to different
authorities, the used pages may be different. Each user is defined by four attributes: Name,
login name, password and authority.
“Name” should be the true name of the user. “Login Name” is the identity to be input when
the user accesses the login dialog box of the system. “Password” is the password to be input
when the user accesses the login dialog box of the system. “Authority” will be introduced in
detail below.
Note: “User” and “Cardholder” are different. A cardholder is a person who goes in or out of
the Access Control system (such as a common employee of a company), while the user is
the person who monitors or configures the Access Control system through the software.
Authority defines the limited level of the user operating the software. Different authorities
have different software operation limits.
Click the menu bar “System” “Basic Setting” “User Group” to enter the User Group
page. For detailed settings, please refer to 7.3 User Group. When entering the “User Group”
in case of first use of the software, the system will automatically initialize the User Group.
The software has three default authorities: System administrator, manager, common user.
Each authority has no limit on the user quantity.
System administrator: The user can use all functions of the software system, including Basic
Setting, Cardholder, Access Control, attendance management, database management, etc.
Manager: The user can use all functions of the software system except Basic Setting.
Common user: The user can use all functions of the software system except Basic Setting
and database management.
The table below lists the specific functions of each authority, and “√” indicates if the
function is available in the corresponding authority.
System
administrator
configuration
information
58
Page 68

Controller settings
√ √
Date settings
√ √
Door region scheme
settings
√ √
Control group settings
√ √
Control group scheme
√ √
Card number type
√ √
Card settings
√ √
Card import
√ √ √
Card information
√ √ √
Card-relevant event
√ √ √
Card-irrelevant event
√ √ √
Basic Settings
√ √
Week Holiday Settings
√ √
Special Holiday
√ √
No-Access-Attendance
√ √
Time-off Enroll
√ √
Overtime Enroll
√ √
Original Access Record
√ √ √
Report by Cardholder
√ √ √
Statistics by
√ √ √
Statistics by
√ √
TCP/IP Network Access Controller
Access
Control
Attendance
settings
settings
Settings
Cardholder
Department
Table 7-1 Function list of authorities
The User Group of the system administrator cannot be changed or deleted and the other
two User Groups can both be changed or deleted.
59
Page 69

TCP/IP Network Access Controller
7.3 User Group
In the User Group page, the current User Group list in the system is displayed on the left
side. The user who has the authority of User Group can carry out User Group creation,
change and deletion operations in this page.
Figure 7-2 User Group
7.3.1 Add User Group
Click the “New” button on the upper side of the page, input the name of the new User
Group in the box of “Name of User Group,” tick off the detailed operation authorities of the
User Group, edit and click the “Save” button to finish the operations.
7.3.2 Change User Group
Select the name of the User Group to be changed in the left-side User Group list, change
the name and detailed operation authorities of the User Group, edit and click the “Save”
button to finish the operation.
7.3.3 Delete User Group
Select the name of the User Group to be deleted in the left-side User Group list, click the
“Delete” button, then the confirmation dialog box “Confirm Delete?” pops up. If it is
confirmed to delete the User Group, click the “OK” button, then the system displays a dialog
box reading, “Deleted Successfully.”
!Note: The User Group which is being used by the user cannot be deleted.
Figure 7-3 Delete current record
60
Page 70

TCP/IP Network Access Controller
User Query Region
Function Editing
User Information
7.4 User Setting
User Setting are used to create, change and delete users and define the authority types of
these users. The user herein actually refers to the account which can log in to and use the
software. Please distinguish with “Employer.” The user includes login name, password, User
Group, username, etc. The software has a default super user, “admin,” which belongs to the
User Group of system administrator and cannot be deleted.
Click the menu “System” “Basic Setting” “User Setting” to open the User Setting page.
See Figure 7-4.
Region
Figure 7-4 User Setting
Region
7.4.1 Add User
In the page, click the “Add” button in “Function Editing Region,” then the user addition page
pops up (see Figure 7-5). Input the login name, username, password and User Group name
and click the “Save” button to add a new user to the user list in the page.
Figure 7-5 Add user
Login name: The name for the user to log in and use the software, which can be any
combination of figures, letters, spaces, Chinese characters and other displayable characters.
The longest login name is 20 bits and any character occupies 1 bit. The letters of the login
name are case sensitive. The login name cannot be the same as an existing user login name
and cannot be empty. If the user inputs an existing login name, the system will prompt that
the login name has already been used when saving it.
Username: The true name of user. This item is for facilitating system management and must
be filled in.
61
Page 71

TCP/IP Network Access Controller
Password: Any combination of figures, letters, spaces, Chinese characters and other
displayable characters. The longest login name is 20 bits and any character occupies 1 bit.
The letters of the login name are case sensitive.
Confirm password: Must be the same as the input content of the password. If the two
passwords input are not consistent with each other, the system will prompt that “Input
Password Do Not Match.”
Name of User Group: Name of the User Group to which the user belongs. The
administrator can allocate the new user to any User Group and the User Group of the
system administrator can operate all functional modules.
7.4.2 Edit User
Select the column in which the user to be changed is located and click the “Edit” button,
then the user edition dialog box pops up (see Figure 7-6).The login name, username,
password and User Group of the user can all be changed. In case of resetting the login
password of the user, check “Reset Password,” edit, and click the “Save” button, then the
system displays a dialog box reading, “Deleted Successfully.” In case of not changing, click
the “Cancel” button to return to the “User Setting” page.
Figure 7-6 Change user
7.4.3 Delete User
Select the column in which the user to be deleted is located, click the “Delete” button and
the dialog box “Confirm Delete?” pops up. If it is confirmed to delete the user, click the “OK”
button to finish the operation.
!Note: The default user “admin” cannot be deleted.
7.4.4 Export User Information
Click the “Export” button to export all user information in the system in the csv format, then
the file save dialog box pops up. Select the path to save the file and click “OK.” For detailed
operation procedures, please refer to 6.1.6 Export Function.
62
Page 72

TCP/IP Network Access Controller
7.4.5 Print User Information
Click the “Print” button to enter the user information printing page. For detailed operation
procedures, please refer to 6.1.7 Print Function.
7.4.6 Search User
Select login name or username in the pull-down menu of “Search” in “Search Editing
Region,” input the content to be searched for and then click the “Search” button. If there is
information meeting the conditions in the system, the information will be displayed in the
user information list region below (see Figure 7-7). If you want to look over all the users in
the current controller after searching, click the “All” button.
!Note: “Search” herein refers to a precise search.
Figure 7-7 Search user
7.5 Local Server
The Local Server can set the IP, time, data and time zone of the currently logged-in
controller. Click the system main menu “System” “Basic Setting” “Local Server” to
enter the Local Server page. See Figure 7-8.
Figure 7-8 Local Server
Click the IP type as in the above figure, select static or dynamic type, input IP, subnet mask
and gateway in the textbox, confirm and click the “OK” button. The page will display this
prompt dialog box:
63
Page 73

TCP/IP Network Access Controller
Click “OK” again and re-log in to the controller using the changed IP address.
Click the “Reset” button to read and display the network settings in the current controller in
the page input box.
Click the “Synchronize with Local Time” button and the time of the controller will
synchronize with the local time. The required time can also be set by the user. Click the “Set”
button to save the time settings.
Select the required time zone or the time zone where the location is located, click the “Set”
button to complete the controller time zone settings.
7.6 System Upgrade
The embedded software in the controller can be upgraded to the latest version through
system upgrade.
The system upgrade is divided into online upgrades and local upgrades.
Click the system main menu “System” “Basic Setting” “System Upgrade” to enter the
system upgrade page. See Figure 7-9. By default, the online upgrade page will show up.
Figure 7-9 Online upgrade
7.6.1 Online Upgrade
The upgrade is carried out through the FTP or HTTP address and account provided by the
service provider. As in the above figure, after inputting the accurate address and account,
click the “Update” button, then online upgrade starts. After the online upgrade is finished,
please re-log in.
7.6.2 Local Upgrade
The upgrade is carried out locally through the upgrade package provided by the service
provider. Click the “Browse” button as in the above figure, select the upgrade package, click
the “Upload” button, then the local upgrade starts. After the local upgrade is finished,
please re-log in.
64
Page 74

TCP/IP Network Access Controller
Figure 7-10 Local upgrade
65
Page 75

TCP/IP Network Access Controller
Chapter
8
8 Cardholder
This chapter will introduce the Cardholder of the EFC301F in detail, including department
setting, Cardholder Setting and Import Cardholders.
Department setting: Set the parameter information related to departments and groups of
the company.
Cardholder Setting: Set employee number, name, department and other information of
Cardholder, and allocate one or more card for Cardholder and set the attributes thereof.
Import Cardholders: Import the edited file in the form of CSV (Excel) into the controller.
8.1 Department Setting
Select the menu bar “System” “Cardholder” “Department Setting” to enter the page
of department setting; see the figure below:
Figure 8-1 Department setting
The left side of the page is the tree structure of the organization structure and the right side
of the page is the list of the nodes directly belonging to the node selected from the left-side
tree structure. The addition, change and deletion operations can be carried out in the page
on the right side and the system will automatically save it after finishing the operation.
Set the parameter information related to departments and groups of the company. The
organization structure has three layers in all: The first layer is company information, the
second layer is department information and the third layer is group information.
8.1.1 Add Department
Click the “Add” button. The department addition page will pop up; see the figure below:
66
Page 76

TCP/IP Network Access Controller
Figure 8-2 Add department
Input the name of the department in the input box of “Department Name,” click the input
box of “Superior Department,” select the superior department to which the added new
department belongs and click the “Save” button, then the system returns to the
department setting page.
The names of the departments belonging to the same hierarchy can be the same.
The name of the newly added department should not be the same as the name of the
previously added department.
8.1.2 Edit Department
Select one department item, click the “Edit” button to enter the department edition page;
see the figure below:
Figure 8-3 Change department
Input the name of the department in the input box of “Department Name,” click the input
box of “Superior Department,” select the superior department to which the currently edited
department belongs, change the hierarchy to which the department belongs to by changing
the superior department, and click the “Save” button, then the system returns to the
department setting page.
8.1.3 Delete Department
Select one department in the list and click the “Delete” button, then a dialog box pops up;
see the figure below:
Figure 8-4 Confirm deletion
67
Page 77

TCP/IP Network Access Controller
If it is confirmed to delete, please click “OK” button to delete the department and delete
the corresponding node in the tree structure at the same time. If some parent node has
subsectors, the department cannot be deleted. A dialog box pops up; see the figure below:
Figure 8-5 Department in use cannot be deleted.
8.2 Cardholder Setting
Select the system menu bar “System” “Cardholder” “Cardholder Setting” to enter the
Cardholder Setting page; see the figure below:
Figure 8-6 Cardholder Setting
As in the above figure, the upper part of the page is the query region, the middle line is the
operation region and the lower part is the Cardholder information list.
In the operation region on the right upper corner of the page, the number of Cardholder
information items displayed per page can be set. By default of the system, 20 records are
displayed per page. In addition, the page turn button and jump button are helpful for users
to rapidly access the desired page. See the figure below:
Figure 8-7 Operation region
8.2.1 Add Cardholder
Click the “Add” button and the Cardholder Setting registration page pops up; see the figure
below:
68
Page 78

TCP/IP Network Access Controller
Figure 8-8 Add Cardholder
a) Cardholder Information Region: The items in this region are used to set the basic
information of Cardholder.
Employee number: Any printable character. The employee number is the unique ID of
Cardholder in the system. If the employee number already exists in the system when newly
adding Cardholder, the system will display a dialog box reading, “Failed to save Cardholder
information.”
Figure 8-9 Failed to save Cardholder information
Name: True name of Cardholder.
Gender: The gender is male by default.
Department: Click the department to which the new Cardholder member belongs.
Employment/Resignation date: When clicking the input box with mouse, a time selection
box pops up, in which the employment date of Cardholder is selected; year and month are
selected in the upper part and the day is selected in the middle part.
Figure 8-10 Calendar
Photo: Click the “Browse” button, then the selection page for uploading photo pops up.
Select photo and the click the “Upload” button.
69
Page 79

TCP/IP Network Access Controller
Operation Procedures:
1) Select the photo to be uploaded: Click the “Browse” button and find the photo to be
uploaded. The file size must not be larger than 2M.
2) Upload file: After selecting the photo, click the “Upload File” button.
3) Photo name: After the photo is uploaded, the file name is listed therein.
!Note: The employee number and name of Cardholder must be filled in; other parameters
are optional. However, we recommend that you fill in all information so as to display more
visual information in case of querying.
b) Card Information Region: The items in this region can rapidly add one or more cards for
the currently added Cardholder and can set the related attributes of the card(s).
The card information is mainly to correlate the Cardholder and the card. You can directly
input the internal code (in most cards, a string of figures or symbols printed on the back of
the card) of the card to be correlated, or connect with the ERU Series USB desktop card
reader (please refer to the operating instruction manual for ERU Series hardware) and read
the internal code of the card by swiping the card.
Card Format: The system has three card formats: Decimal, hexadecimal and nnn-nnnnn.
Before adding a card, select correct card format and set through the path: “Access Control”
“Card” “Card Setting.”
Add Card: Input card number, click the “Save Card Number” button to save the card number.
If the card to be registered is the same as the card in the system, the system will display a
dialog box reading, “Card already allocated to others, reallocate the card?” One user can
hold one or more cards.
Figure 8-11 Card repeat
Delete Card: Select the tab of the card to be deleted, click the “Delete Card” button to
delete the card.!Note: This operation is real-time processing.
Card Validity: Indicates whether the registered card is activated. Check this item to activate
the card. The other attributes of the card may not act until the card is activated. The card
will be invalid in case of not checking.
First Card Door Open: It indicates that the card held by the Cardholder is the first card and
is used for opening the door when setting normally opened function of the door region. If
the controller 0001 sets the door to be normally opened at a.m. 9:00-11:00, during this
period of time, the Cardholder holding the card with the first card attribute swipes the card
on the card reader under the controller to activate the normally opened state of the door in
the corresponding door region.
Arm/Disarm: It indicates whether the cardholder has the authority to set up/withdraw
protection and reset alarms on the selected controller. Checking this item will activate the
protection setup function of the card, and the cardholder will has the authority of
protection setup.
70
Page 80

TCP/IP Network Access Controller
Check APB: It indicates whether anti-passback (anti-follow) of the cardholder is activated. If
this item is checked and the controller activates the overall anti-passback function, the
anti-passback setting of the card will be valid.
Administrator: Indicates the cardholder has the administrator authority for system
configuration.
PIN Enabled: It indicates whether the personal password is activated. If the check box for
using password is checked, the password setting of the cardholder will be activated. The
cardholder can set an eight-digit door open password.
Force PIN: The duress password is used for raising an alarm when the cardholder opens the
door under duress and is only valid when the door is set to open with a password. The
duress password has 2 digits. In case of using the duress password, first input the first 6
digits of the normal password and then input the duress password and confirm, then the
alarm is generated and the door is opened.
Check Expire: If the card validity period is checked, it indicates that the card can be used
only in the validity period and cannot be used to enter any door region out of the validity
period. Click the input box with the mouse, then a time selection dialog box pops up. The
time of the validity period is in increments of minutes.
Private Schedule: Two management modes are provided: Control group and card scheme
setting. The card design refers to the priority entry/exit rules of the current card in the door
region controlled by the controller. Among all of the three rules of the card, the order of
priority is: Card design > Control group scheme > door design, with the priority from high to
low. The design selected from the pull-down menu of the card design is the control group
scheme (non-control group).
Access Group: The setting of the Access Control authority. The system allocates 2048 Access
Control authority for all the cardholders and sets different Access Access Rule for different
User Groups.
When all the information is filled in and the card setting is finished, click “OK” button, then
the system will display a dialog box reading, “Added successfully.”
8.2.2 Change Cardholder
If the information of one Cardholder member needs to be changed, select the name column
of the Cardholder member and click the “Edit” button in the operation bar to enter the
change page; see the figure below:
71
Page 81

TCP/IP Network Access Controller
Figure 8-12 Change Cardholder
The change of the Cardholder information is similar to the addition of the Cardholder
information. After the Cardholder information is changed as required, click the “Save”
button to finish the operation.
8.2.3 Delete Cardholder
If the information of one Cardholder member needs to be deleted, select the name column
of the Cardholder, and click the “Delete” button, then the page displays a confirmation
dialog box:
Figure 8-13 Confirm deletion
If it is confirmed, click “OK” button to delete the information of the Cardholder.
In case of deleting the information of several Cardholder members, press “Shift” on the
keyboard while selecting the columns of the Cardholder to be deleted and click the “Delete”
button, then the confirmation box “Confirm delete?” pops up. Click “OK” to delete the
information of all of the selected Cardholder.
72
Page 82

TCP/IP Network Access Controller
8.2.4 Export Cardholder Information
Click the “Export” button to export all user information in the system in the csv format, then
the file save dialog box pops up. Select the path to save the file and click “OK.” For detailed
operation procedures, please refer to 6.1.6 Export Function.
8.2.5 Print Cardholder Information
Click the “Print” button to enter the user information printing page. For detailed operation
procedures, please refer to 6.1.7 Print Function.
8.2.6 Query Cardholder
The “Query” condition includes employee number and name. First select query condition,
and input the keyword related to the character field in the textbox after “Keyword.” After
inputting the query condition, click the “Search” button, then the system will list the results
meeting the condition. Click the “All” button, then the system will list all Cardholder
information in the system. The query herein is a precise query and the result will not be
listed unless the query condition and the keyword are completely met.
8.3 Import Cardholders
Select the system menu bar “System” “Cardholder” “Import Cardholders” to enter the
Import Cardholders page; see the figure below:
Figure 8-14 Import Cardholders
Operation Procedures:
1) Upload Excel file: Click the “Browse” button and find the file to be uploaded. The
imported file must be in the form of CSV (Excel 97-2003) and be smaller than 1M.
2) Click the “Next” button to enter the import operation page; see the figure below:
73
Page 83

TCP/IP Network Access Controller
Figure 8-15 Import Cardholder information
3) Click the drop-down box of each attribute, select the corresponding attribute category
and check the radio button at the top of the column.
4) Click the “Import” button on the lower side of the page to start importing Cardholder
information.
5) After the import is finished, the system will display “XXX records imported.”
!Note: All of the user information in the system is imported in the form of csv. Select the
path to save the file and click “OK.” For detailed operation procedures, please refer to
6.1.6 Export Function.
74
Page 84

TCP/IP Network Access Controller
Chapter
9
9 Real-time Monitoring
9.1 Real-time Event
Select the system menu bar “System” “Real-time Monitoring” “Real-time Event” to
enter the real-time monitoring page; see the figure below:
As shown in the above figure, the real-time event monitoring page is divided into three
basic regions.
The control panel is positioned in the column on the leftmost side and has door status
indication icons for Door Open and Door Close and alarm indication icons for Protection
Setup, Protection Withdrawal, Alarm and Alarm Reset as well as a Logoff button.
The electronic map is positioned in the middle upper part and the real-time status icon of
the device displays the different status of the device, such as whether the door is open or
closed, if there is an alarm or not, etc.
The real-time event records of the controller are positioned in the middle part. It
automatically receives the event information of the controller and scrolls the event
information to display in real time. In case of accessing the page for the first time, the
events of the controller are sequentially listed according to the sequence of being received.
When receiving a new event, it automatically lists the latest event in the first line.
The cardholder information is positioned on the right side of the page and are used to
display the information of the cardholder who triggers the event of the controller. When
clicking to select the middle real-time event record, if the selected event contains the
cardholder information, the related information of the cardholder, such as photo, name,
gender, department, etc., will be displayed in the cardholder information column on the
rightmost side; if there is no information for the cardholder, the related contents in this
column are blank.
Figure 9-1 Real-time event
75
Page 85

TCP/IP Network Access Controller
9.2 Report
9.2.1 Query Cardholder Information
Select the system menu bar “System” “Report” “Cardholder Report” to enter the
Cardholder information query page; see the figure below:
Figure 9-2 Query Cardholder information
The Cardholder information query is a precise query achieved through inputting the
employee number or name of the Cardholder.
The “Query” condition includes an employee number and name. First select query
condition and input the keyword related to the character field in the textbox after
“Keyword.” After inputting the query condition, click the “Search” button, then the system
will list the results meeting the condition. Click the “All” button and the system will list all
Cardholder information in the system.
For example, employee numbers “ef-001” and “ef-002” are available in the system. If you
want to query “ef-001,” select “employee number” as a query condition, input “ef-001” in
the keyword input box and Click the “Search” button. In case any character is missing, the
user cannot be found.
9.2.2 Export Cardholder Information
Click the “Export” button to export all Cardholder information in the system in the csv
format, then the file save dialog box pops up. Select the path in which to save the file and
Click “OK.” For detailed operation procedures, please refer to 6.1.6 Export Function.
9.2.3 Print Cardholder Information
Click the “Print” button to enter the Cardholder information printing page. For detailed
operation procedures, please refer to 6.1.7 Print Function.
76
Page 86

TCP/IP Network Access Controller
Chapter
10
10 Maintenance
10.1 Data Backup
Click the “System” “Maintenance,” and select “Backup” to enter the data backup page;
see the figure below:
10.1.1 Manual Backup
Manual backup refers to backup of system data in the local server through the operation of
the administrator. Select the “Manual Backup” item and Click the “Backup” button, then the
backup file will be saved in the local computer.
Figure 10-1 Data backup
Figure 10-2 Manual backup
77
Page 87

TCP/IP Network Access Controller
10.1.2 Automatic Backup
Data backup can be carried out by manual backup or automatic backup. The automatic
backup page is shown in the figure below.
Figure 10-3 Automatic backup
Operation Procedures:
1) Check to enable automatic backup.
2) Select the date and start time of automatic backup.
3) Set the username, password, URL, port and file save path of the backup file in the FTP
server. (FTP server refers to remote server)
4) Select whether the expired backup file is cleared during automatic backup.
5) Click the “Save” button to finish operation.
10.2 Restore
Click the “System” “Maintenance” “Restore” to enter the data restoration page. The
system provides two data restoration manners: Database restoration from FTP and
database restoration from local.
10.2.1 Restore from FTP
Figure 10-4 Restore from FTP
78
Page 88

TCP/IP Network Access Controller
Operation Procedures:
1) Fill in the username and password to log in to the FTP server.
2) Fill in the URL, port and file save path (e.g. abcd/nav_090818183801) of the FTP server.
3) Click the “Save” button.
10.2.2 Restore from Local
Figure 10-5 Restore from Local
Operation Procedures:
1) Click the “Browse” button and select the site for saving the restored file locally.
2) Select the file to be restored and Click the “Restore” button to start to restore data.
3) The system displays a prompt dialog box reading, “Database restored successfully.”
10.3 Purge Out-of-date Data
Click the “System” “Maintenance,” select “Purge Out-of-date Data” to enter the expired
data clear page; see the figure below:
Figure 10-6 Purge Out-of-date Data
Select the event type and cut-off date of data and Click the “Clear” button, then the system
will completely clear all the events with the selected event type category according to the
selection time.
For example, select the “Remote Door Open” events occurring 3 months ago and Click the
“Clear” button, then the system will delete all the “Remote Door Open” events occurring 3
months ago.
!Note: Expired data clear only clears the event records, operation control records, etc. in
the software system and may not clear the configuration information of the system
software; the cut-off time can be any time and the current selection time is exclude.
79
Page 89

TCP/IP Network Access Controller
Chapter
11
11 Controller Management
This chapter will introduce how to set the controller. Through this chapter, you can learn:
How to add, delete and configure the controller in the system software.
How to download data into the controller.
11.1 Controller Setting
Click the “Access Control” “Controller,” select “Controller Setting” to enter the controller
setting page; see the figure below:
The related configurations of one controller are provided in this operation page of the
controller (see Figure 11-1), card reader, alarm, alarm time or other settings. Next, the
operations will be introduced in detail.
11.1.1 Change Controller Information
Figure 11-1 Controller setting
80
Page 90

TCP/IP Network Access Controller
Unlock Duration: Set up the duration time for the door to be opened when an open door
request is permitted.
Held Open Duration: The delay time (unit: S) for triggering a door open timeout alarm
event when the actual door open time exceeds the set time.
Area Name: The location name of the controller.
APB Enable: Check to enable the APB function.
When APB Check Fail: Choose to open the door or close the door.
System Reader Input Time: The time allowed for inputting a password when opening the
door or carrying out other operations with passwords. If the time is longer than the waiting
time, the input menu will be canceled and return to the main setup menu.
Reader Input Time: Set up the waiting time of inputting the card number of password of
the aux. reader.
Outcome: Indicates if the card reader is in door entry position or door exit position. If the
item is checked, it indicates that the card reader is in the door exit position.
Keypad: Indicates the reader features a keypad.
Greeting in Screen: Input the greeting text for the screen on the reader. Up to 40 characters
can be inputted.
Card Switch: After opening the door using the first card, the status of the door is normal or
normally opened. The checked box indicates to trigger.
Date Format: Select a date format.
Daylight Saving: Check to enable the Daylight Saving function. You can further set up the
start or end time of the daylight saving time.
Click the “Save” button to finish the operation.
11.1.1.1 Alarm Input
Figure 11-3 Alarm Input
Name: Input a name for the alarm input.
81
Page 91

TCP/IP Network Access Controller
Fire Alarm: Indicates this is a fire alarm input.
Input Mode: Select from Disabled, Normal Open or Normal Close.
Output Mode: Select from Launch mode 1, Launch mode 2, Launch mode 1.2 or No output.
Alarm Duration: Set up the duration time when an alarm has been triggered. Minimum
time is 5 sec.
Arm Delay: The controller will be in the arm status after the setup time. Minimum time is 5
sec.
Action Doors: This function will be enabled when the Fire Alarm is selected. Select Open
Door or Close Door.
Click the “Save” button to finish the operation.
11.1.1.2 Alarm Setting
In the alarm setting page, the user can configure whether the controller alarm output is
triggered in case of an event alarm of the controller and configure the alarm output time.
Figure 11-4 Alarm time
Select an Output Port and set up the alarm duration time. Click the “Save” button to finish
the operation.
82
Page 92

TCP/IP Network Access Controller
Chapter
12
12 Access Rule
12.1 Date Type
Click the “Access Control” “Access Rule,” select “Date Type” to enter the date setting
page; see the figure below:
Figure 12-1 Date setting
12.1.1 Add Date
In the operating button region, click the “Add” button, then the dialog box reading “Add
Date” pops up.
Figure 12-2 Add date
The controller supports the setting of 10 date types, including from Sunday to Saturday (7
types), user-defined 1, user-defined 2, and user-defined 3, of which Sunday to Saturday are
automatically set according to the calendar and user can define the user-defined 1,
user-defined 2 and user-defined 3 as required.
In this manual, the user-defined 1, user-defined 2 and user-defined 3 are all regarded as
holidays. Holiday setting refers to the three date types. The EverFocus controller supports
255 holiday settings.
83
Page 93

TCP/IP Network Access Controller
Cycling Type
The software allows flexible holiday settings according to three different standards. The
three cycling types are as follows:
1) One-time Holiday
One-time holiday refers to a holiday only occurs once and will not occur in the future
years, for example, an unfixed holiday.
2) Month Holiday
Month holiday refers to the holiday which occurs on a certain day in a certain month
every year. For example: New Year’s day, Jan 1 every year.
3) Week Holiday
Week holiday is another periodic holiday and refers to a certain day in a certain week of
a certain month. This holiday is common in western countries. For example,
Thanksgiving Day is the fourth Thursday of December every year. The user need not
change the week holiday every year.
!Note: These holidays should be allocated during system initialization and re-checked at the
beginning of every year.
Operation Procedures:
1) Select date cycling type.
2) Select date in the calendar.
3) Select date type.
4) Input remarks (optional).
5) Click the “Save” button to add a new date in the list.
12.1.2 Delete Date
Operation Procedures:
1) Check the date(s) (one, part or all) to be deleted in the date list.
2) Click “Delete,” then the prompt dialog box “Confirm delete?” pops up.
3) Click “OK,” then the selected control date is deleted.
!Note: After addition or deletion of a date, the system will automatically “Save” the
changed information.
84
Page 94

TCP/IP Network Access Controller
12.2 Door Schedule
Click “Access Control” “Access Rule,” select “Door Schedule” to enter the door region
scheme setting page; see the figure below:
Figure 12-3 Delete control group
Left click the “Datesetting” in the selected date type, then the following time period setting
page pops up.
Figure 12-4 Time period setting
Input time in the start time and end time, select the door entry/exit mode during the time
period and then click the “Apply” button.
!If the authority of multi-card door open is required, please check “Multi-card Door Open”
and select the respective locking level of the four locks in the lock level column. In the
control group setting page, the corresponding unlocking level of the card can be set.
After setting and changing all the entry/exit modes, click the “Save” button and click the
“Return” button to return to the scheme setting page.
After setting the date time period of door region design, click the “Save” button to save the
setting. See the figure below.
85
Page 95

TCP/IP Network Access Controller
Figure 12-5 Update data
After the setting of a certain date is finished, the setting of another date is the same. Select
the set date in the door region scheme setting page, click the “Copy” button to copy the set
date rules, click to select the date on which the rules are applied, and click the “Paste”
button in the operation bar, then the rules copy is finished.
12.3 Group Schedule
Click “Access Control” “Access Rule,” select “Group Schedule” to enter the control group
scheme setting page; see the figure below:
Figure 12-6 Group schedule
12.3.1 Add Group Schedule
In the control group scheme setting page, click the “Add” button to enter the scheme
setting page.
Figure 12-7 Add control group scheme
86
Page 96

TCP/IP Network Access Controller
Operation Procedures:
1) Input the name of a new design in the textbox of “Schedule Name.”
2) Click the time period of “Datesetting,” a dialog box will pop up, in which the time
period and the door entry/exit authentication authority can be set; see Figure 12-9.
3) After setting the authentication mode of various date types, click the “Save” button,
then the new design is added into the control group scheme list.
12.3.2 Delete Group Schedule
Operation Procedures:
1) In the Group Schedule setting page, check the items to be deleted.
2) Click the “Delete” button.
3) The confirmation box “Confirm delete?” pops up.
4) Click “OK,” then the selected control group is deleted.
12.3.3 Set Group Schedule
Click one group schedule in the group schedule list and click the “Edit” button to enter the
group schedule setting page; see the figure below:
Figure 12-8 Edit control group scheme
By default, the date time periods allow free entry/exit. In case it is required to respectively
set the date time periods in the schemes, in the control scheme setting page, left click
“Datesetting” in the selected date type, then the following time period setting page pops
up:
Figure 12-9 Set time period and authentication mode
87
Page 97

TCP/IP Network Access Controller
Input times in the start time and end time, select the door entry/exit mode during the time
period and then click the “Apply” button to finish the setting. After setting and changing all
the entry/exit modes, click the “Save” button and click the “Return” button to return the
scheme setting page.
After setting the date time period of the control scheme, click the “Save” button to save the
setting. See the figure below:
Figure 12-10 Update data
After the setting of a certain date is finished, the setting of another date is the same. Select
the set date in the control group scheme setting page, click the “Copy” button to copy the
set date rules, click to select the date on which the rules are applied and click the “Paste”
button in its operation bar, then the rules copy is finished.
12.4 Access Group
Click the “Access Control” “Access Rule,” select “Access Group” to enter the control group
setting page; see the figure below:
Figure 12-11 Access group
12.4.1 Add Access Group
In the “Access Group Setting” page, click the “Add” button, then the control group addition
interface pops up.
Figure 12-12 Add control group
88
Page 98

TCP/IP Network Access Controller
Operation Procedures:
5) Input the name of a new control group in the textbox after the name of the control
group.
6) Select the unlocking levels corresponding to the locks.
7) Select the name of the control group scheme or the door scheme.
8) Click the “Save” button to finish control group adding.
Click the “Scheme” button, then the page will switch to the control group scheme page.
12.4.2 Delete Access Group
Operation Procedures:
1) In the access group setting page, check the access group to be deleted.
2) Click the “Delete” button;
3) The confirmation box “Confirm delete?” pops up;
4) Click “OK,” then the selected control group is deleted.
89
Page 99

TCP/IP Network Access Controller
Chapter
13
Card list column
Operating button region
Card no. type
Query operation region
13 Card Management
This chapter will introduce how to add and edit cards. Through this chapter, you can
understand:
Setting of card number types.
How to add, delete and edit one or more cards in the system software.
How to import cards to the controller.
13.1 Card Setting
Click the “Access Control” “Card,” select and click “Card Setting” to enter the card setting
page; see the figure below:
As shown in the figure, the card setting page is comprised of the upper query operation
region, the operating button region and the lower card list column.
Query operation region:
Select query conditions and keywords to conduct a precise search. The user can
conveniently and rapidly search for the card.
Card type:
Select the card no. type from the drop-down list.
Figure 13-1 Card setting
90
Page 100

TCP/IP Network Access Controller
Operating button region:
The operating button region includes Add, Edit, Delete, Export and Print buttons for
corresponding operations.
Card list column:
The card list column displays all the information of the card, including the card number,
employee number, cardholder name, card validity, first card door open, protection setup
validity, password status, anti-passback validity, card validity period, card use scheme and
control group.
13.1.1 Add (Register) Card
In the card setting page, click the “Add” button, then the card adding dialog box pops up;
see the figure below:
Figure 13-2 Add card
Operation Procedures:
1) Input the card number in the textbox. In case of adding multiple cards with consecutive
numbers, check “Mass Cards,” and then input the quantity of cards added in batch. The
input card number is the initial card number.
2) Set the attributes of the card, including card validity, first card door open, protection
setup validity, anti-passback validity, card validity period, password status, card scheme
selection and control group. Check the first card door open, protection setup validity,
password status and other attributes of the card; input password and duress password;
select card validity period; select the control group; and select the card scheme.
3) Allocate the card or multiple cards to one Cardholder. After inputting the employee
number, the name column will automatically display the Cardholder number; click to
select. In a similar way, the Cardholder number can be input first.
4) After selecting the attributes of the card, click the “Save” button, then the card will be
91
 Loading...
Loading...