Page 1

User’s Guide
FastFind Links
Unpacking and Installation
Computer Setup
Setting the initial IP address
EtherWAN ED3575 – V1.94.3.4
EtherWAN ED3575 Users Guide
1
Page 2

All Rights Reserved
Dissemination or reproduction of this document, or its contents, is not authorized except
where expressly permitted. Violators are liable for damages. All rights reserved, for the
purposes of patent application or trademark registration.
Disclaimer of Liability
The information contained in this document is subject to change without notice. EtherWAN is
not liable for any errors or omissions contained herein or for resulting damage in connection
with the information provided in this manual.
Registered Trademarks
The following words and phrases are registered Trademarks of EtherWAN Systems Inc.
EtherOS™
Ethernet to the World™
All other Trademarks are the property of their respective owners.
Warranty
For details on the EtherWAN warranty replacement policy, please visit our website at:
https://kb.etherwan.com/index.php?CategoryID=13
Products Supported by this Manual:
V1.94.3.4 EtherWAN ED3575
Contact EtherWAN Systems
Corporate Headquarters
EtherWAN Systems Inc.
2301 E Winston Rd Anaheim
Anaheim, CA 92806
Tel: (714) 779 3800
Fax: (714) 779 3806
Email: support@etherwan.com
EtherWAN ED3575 Users Guide
ii
Page 3

Preface
TABLE OF CONTENTS
Table of Contents ................................................................................................... iii
Table of Figures ...................................................................................................... xi
Preface .................................................................................................................... xv
Changes in this Revision ......................................................................................... xv
Document Conventions .......................................................................................... xvi
Safety and Warnings .............................................................................................. xvi
Typographic Conventions ....................................................................................... xvi
Unpacking and Installation ................................................................................... 17
Package Contents ................................................................................................... 17
Unpacking ............................................................................................................... 17
Required Equipment and Software .......................................................................... 18
Computer Setup ..................................................................................................... 19
Management Methods and Protocols ...................................................................... 19
Default IP ................................................................................................................. 20
Login Process and Default Credentials .................................................................... 20
Setting the initial IP address ................................................................................. 21
Simple IP Addressing .............................................................................................. 21
CLI Command Usage ............................................................................................. 22
Navigating the CLI Hierarchy ................................................................................... 22
CLI Keyboard Shortcuts ........................................................................................... 22
CLI Command modes .............................................................................................. 23
General Configuration Mode .............................................................................. 23
MSTP Configuration Mode ................................................................................. 23
Interface Configuration Mode ............................................................................. 24
VLAN Database Configuration Mode ................................................................. 24
Saving a Configuration from the CLI .................................................................. 24
System Menu ......................................................................................................... 25
System Information .................................................................................................. 25
System Name/Password.......................................................................................... 27
System Name/Password using the CLI .................................................................... 28
IP Address ............................................................................................................... 29
EtherWAN ED3575 Users Guide
iii
Page 4

Preface
Static IP ............................................................................................................. 29
DHCP Client ...................................................................................................... 29
Default Gateway ................................................................................................ 29
DNS Server ........................................................................................................ 29
IP Address - Configuration using the CLI ................................................................. 31
IP Address ......................................................................................................... 31
Default Gateway ................................................................................................ 32
Domain Name Server (DNS) .............................................................................. 33
Enable/Disable DHCP Client on a VLAN ............................................................ 34
Enable/Disable Static IP on a VLAN................................................................... 34
Management Interface ............................................................................................. 36
HTTPS ............................................................................................................... 36
Telnet. ................................................................................................................ 36
SSH (Secure Shell) ............................................................................................ 37
Management Interface Configuration using the CLI ................................................. 38
Enabling/Disabling Telnet .................................................................................. 38
Enabling/Disabling SSH ..................................................................................... 39
Enabling/Disabling HTTP and/or HTTPS ........................................................... 40
Save Configuration Page ......................................................................................... 42
Save Configuration ............................................................................................ 42
Load Configuration ............................................................................................. 42
Backup Configuration ......................................................................................... 42
Restore Default .................................................................................................. 43
Auto Save .......................................................................................................... 43
Save Configuration Page using the CLI ................................................................... 44
Saving a Configuration ....................................................................................... 44
Restore Default Settings .................................................................................... 44
Load Configuration from a TFTP Server ............................................................ 45
Save Configuration to a TFTP Server ................................................................ 45
Auto Save Configuration .................................................................................... 46
Firmware Upgrade ................................................................................................... 47
Firmware Update using the CLI ............................................................................... 48
Reboot ..................................................................................................................... 49
Reboot using the CLI ............................................................................................... 49
Logout ..................................................................................................................... 49
Logout from the CLI ................................................................................................. 49
User Account Page .................................................................................................. 50
Changing the User Mode ................................................................................... 50
Creating a New User .......................................................................................... 51
Changing an Existing User Account ................................................................... 52
User Privilege Configuration .................................................................................... 53
User Account Settings using the CLI........................................................................ 55
Multi-User Mode................................................................................................. 55
EtherWAN ED3575 Users Guide
iv
Page 5

Preface
Single User Mode .............................................................................................. 55
Radius User Mode ............................................................................................. 56
Creating a New User .......................................................................................... 57
Permissions ....................................................................................................... 57
Diagnostics ............................................................................................................ 58
Utilization ................................................................................................................. 58
System Log.............................................................................................................. 59
System log using CLI command .............................................................................. 59
Remote Logging ...................................................................................................... 60
Remote Logging using CLI commands .................................................................... 62
ARP Table ............................................................................................................... 63
ARP Table using CLI Commands ............................................................................ 64
Route Table ............................................................................................................. 65
Route Table Using CLI Commands ......................................................................... 65
Alarm Setting ........................................................................................................... 66
Port ......................................................................................................................... 67
Configuration ........................................................................................................... 67
Port Status ............................................................................................................... 69
Rate Control ............................................................................................................ 70
RMON Statistics ...................................................................................................... 71
Per Port VLAN Activities .......................................................................................... 72
Port Security ............................................................................................................ 73
Setting the Port Description ............................................................................... 74
Enable or Disable a Port .................................................................................... 74
Setting the Port Speed ....................................................................................... 75
Setting Port Duplex ............................................................................................ 75
Enable or Disable Port FlowControl ................................................................... 76
Display Port Status ............................................................................................ 76
Setting a Ports Rate Control .............................................................................. 76
Display a Ports RMON Statistics ........................................................................ 77
Display a Ports VLAN Activities .......................................................................... 77
Setting MAC Port Security ................................................................................. 77
Switching ................................................................................................................ 79
Bridging ................................................................................................................... 79
Aging Time......................................................................................................... 80
Threshold Level ................................................................................................. 80
Storm Control Type ............................................................................................ 80
Port Isolation ...................................................................................................... 81
Block Multicast ................................................................................................... 81
Loopback Detect ...................................................................................................... 83
EtherWAN ED3575 Users Guide
v
Page 6

Preface
Loopback Detection (Global) .............................................................................. 83
Loopback Detect Action ..................................................................................... 83
Loopback Detect Recovery Time ....................................................................... 83
Polling Interval ................................................................................................... 84
Loopback Detection (Per Port) ........................................................................... 85
Storm Detect ............................................................................................................ 86
Enable/Disable Storm Detection ........................................................................ 86
Static MAC Entry ..................................................................................................... 88
Adding a Static MAC Address to a Port .............................................................. 88
Removing a Static MAC Address from a Port ..................................................... 89
Adding a MAC to the Static-MAC-Entry Discard Table ....................................... 89
Removing a MAC address from the Static-MAC-Entry Discard Table ................ 90
Port Mirroring ........................................................................................................... 91
Link State Tracking .................................................................................................. 93
Enable/Disable Link State Tracking ................................................................... 93
Port Settings ...................................................................................................... 94
Switch Configuration Examples Using CLI Commands ............................................ 95
Setting the Aging Time Value ............................................................................. 95
Enabling Port Isolation ....................................................................................... 95
Enabling Block Multicast .................................................................................... 96
Setting Storm Control ......................................................................................... 96
Enabling Loopback Detect (Global) .................................................................... 97
Setting the Loopback Detect Action ................................................................... 97
Setting the Loopback Detect Recovery Time ..................................................... 97
Setting the Loopback Detect Polling Interval ...................................................... 98
Enabling Loopback Detect (Port) ....................................................................... 98
Configuring Storm-Detect ................................................................................... 99
Adding a MAC Address for Static-MAC-Entry Forwarding ................................ 103
Adding a MAC Address for Static-MAC-Entry Discarding ................................. 103
Configuring Port Mirroring ................................................................................ 104
Enabling a Link State Tracking Group .............................................................. 104
Assigning a Port to a Link State Tracking Group .............................................. 105
Trunking ............................................................................................................... 106
Overview ............................................................................................................... 106
Static Channel Trunking ................................................................................... 106
Link Aggregation Control Protocol .................................................................... 106
Port Trunking ......................................................................................................... 107
LACP Trunking ...................................................................................................... 109
Trunking Configuration Examples Using CLI Commands ....................................... 111
Adding an Interface to a Static Trunk ............................................................... 111
Adding an Interface to an LACP Trunk ............................................................. 111
Setting the LACP Port Priority .......................................................................... 112
EtherWAN ED3575 Users Guide
vi
Page 7

Preface
Setting the LACP Timeout ................................................................................ 112
STP/Ring Page – Overview ................................................................................. 113
Choosing the Spanning Tree Protocols .................................................................. 113
Spanning Tree Protocol (STP) ......................................................................... 113
Rapid Spanning Tree protocol (RSTP) ............................................................. 113
Multiple Spanning Tree Protocol (MSTP) ......................................................... 113
STP/Ring Page - Configuring RSTP ................................................................... 114
Global Configuration Page ..................................................................................... 114
Enabling the RSTP Protocol ............................................................................ 114
Additional Global Configuration page settings .................................................. 114
The Root Bridge & Backup Root Bridge ........................................................... 116
Setting the MAX Age, Forward Delay and Hello Timer ..................................... 118
RSTP Port Setting Page ........................................................................................ 120
Spanning Tree Port Roles ................................................................................ 120
Path Cost & Port Priority .................................................................................. 121
Point to Point Link ............................................................................................ 123
Edge Port ......................................................................................................... 123
RSTP Configuration Examples Using CLI Commands ........................................... 124
Enabling the Spanning Tree Protocol ............................................................... 124
Bridge Priority, Max Age, Forward Delay, and Hello Time ................................ 124
Modifying the Port Priority and Path Cost ......................................................... 125
Manually Setting a Port to be a Shared or Point to Point Link .......................... 125
Enabling/Disabling a port to be an Edge Port ................................................... 126
STP/Ring Page - Configuring MSTP ................................................................ ... 127
Global Configuration Page ..................................................................................... 127
Enabling the MSTP Protocol ............................................................................ 127
The CIST Root Bridge & Backup CIST Root Bridge ......................................... 129
Setting Bridge Priority ...................................................................................... 129
Configuring the CST Network Diameter ........................................................... 131
MSTP Properties Page .......................................................................................... 132
Configuring an MSTP Region........................................................................... 132
Configuring the IST Network Diameter ............................................................. 134
MSTP Instance Setting Page ................................................................................. 135
Setting an MSTP Instance ............................................................................... 135
Modifying MSTP parameters for load balancing ............................................... 136
MSTP Port Setting page ........................................................................................ 138
Adjusting the blocking port in an MSTP network .............................................. 138
MSTI Instance Port Membership ...................................................................... 140
MSTP Configuration Examples Using CLI Commands .......................................... 141
Enabling Spanning Tree for MSTP ................................................................... 141
vii
EtherWAN ED3575 Users Guide
Page 8

Preface
Bridge Priority, Max Age, Forward Delay, and Hello Time ................................ 142
IST MAX Hops ................................................................................................. 142
MSTP Regional Configuration Name and the Revision Level ........................... 143
Creating an MSTI Instance .............................................................................. 143
Setting MSTI Priority ........................................................................................ 144
Modifying CIST Port Priority and Port Path Cost .............................................. 144
Adding a Port to an MSTI Instance .................................................................. 145
STP/Ring Page - Alpha Ring ............................................................................... 146
Alpha Ring Setting Page ........................................................................................ 146
EtherWAN α-Ring Technology ......................................................................... 146
Implementing a Simple α-Ring ......................................................................... 146
Connecting two α-Ring Networks together ....................................................... 148
STP/Ring Page – Alpha Chain ............................................................................ 149
The Alpha Chain Protocol ...................................................................................... 149
General Overview .................................................................................................. 149
Alpha Chain Settings ............................................................................................. 150
Global Settings ................................................................................................ 150
Configuring the Alpha Chain Ports ................................................................... 151
Alpha Chain Pass-Through Ports ........................................................................... 153
Configuring Alpha Chain using CLI commands ...................................................... 154
Storm Control ................................................................................................... 154
Configuring Chain Ports ................................................................................... 154
Configuring Chain Pass-Through Ports ............................................................ 155
STP/Ring Page - Advanced Setting .................................................................... 156
Advanced Bridge Configuration ............................................................................. 156
Advanced Per Port Configuration ........................................................................... 157
Configuring Spanning Tree Advanced Settings using CLI commands.................... 158
Enabling BPDU Guard Globally ....................................................................... 158
Enabling BPDU Guard on a Port ...................................................................... 158
Enabling BPDU Guard Error Disable-timeout ................................................... 159
VLAN ..................................................................................................................... 160
Port Based VLAN vs. Tagged Based VLAN ........................................................... 160
Configuring VLANs in Port Based VLAN Mode ...................................................... 160
Enabling Port Based VLAN .............................................................................. 160
Port Based VLAN Configuration Examples ...................................................... 161
Port Based VLAN Configuration Examples using CLI Commands ................... 163
VLAN Configuration in 802.1Q Tag Based VLAN Mode ......................................... 164
General Overview ............................................................................................ 164
Enabling 802.1Q Tagged Based VLAN ............................................................ 165
viii
EtherWAN ED3575 Users Guide
Page 9

Preface
Configuring 802.1Q VLAN Database................................................................ 166
802.1Q Tag Based VLAN Configuration Examples Using CLI Commands ............ 167
Configuring a 802.1Q VLAN ............................................................................. 167
Configuring an IP Address for a Management VLAN ....................................... 167
Removing an IP Address from a Management VLAN ....................................... 168
Configuring an Access Port .............................................................................. 168
Configuring a Trunk Port .................................................................................. 169
Add an IP to the Management VLAN ..................................................................... 170
Configuring the Port Type and the PVID setting ..................................................... 171
Configuring the VLAN Egress (outgoing) Member Ports .................................. 172
QoS ....................................................................................................................... 174
Global Configuration Page ..................................................................................... 175
Web GUI Interface ........................................................................................... 175
QoS Global Configuration using the CLI Interface ................................................. 177
Enable/Disable QoS Trust ................................................................................ 178
Configuring the Egress Expedite Queue .......................................................... 178
802.1p Priority Page .............................................................................................. 180
Web GUI Interface ........................................................................................... 180
802.1p Priority Submenu – CLI Interface ............................................................... 181
DSCP Page – HTTP Interface ............................................................................... 182
DSCP Submenu – CLI Interface ............................................................................ 183
QoS Interface Commands – CLI Interface ............................................................. 184
SNMP .................................................................................................................... 185
SNMP General Settings ......................................................................................... 185
Configuring SNMP v1 & v2 Community Groups ..................................................... 188
Configuring SNMP v3 Users .................................................................................. 189
Adding SNMP v3 Users to the switch ............................................................... 189
Deleting SNMP v3 Users from the switch ......................................................... 192
SNMP Configuration Examples Using CLI Commands .......................................... 193
Enabling SNMP and configuring general settings............................................. 193
Configuring SNMP Traps ................................................................................. 194
Configuring SNMP v1 & v2 Community Groups ............................................... 196
Adding SNMP v3 Users ................................................................................... 196
IEEE 802.1X .......................................................................................................... 197
Configuring 802.1X from the GUI system ............................................................... 197
Enabling Radius ............................................................................................... 197
Adding a Radius Server ................................................................................... 198
Enabling 802.1X on a Port ............................................................................... 200
EtherWAN ED3575 Users Guide
ix
Page 10

Preface
LLDP ..................................................................................................................... 202
LLDP General Settings .......................................................................................... 203
Enable/Disable LLDP ....................................................................................... 203
Holdtime Multiplier ........................................................................................... 203
Global TLV Setting ........................................................................................... 204
LLDP Ports Settings .............................................................................................. 205
Enabling LLDP transmission for a specific Port ................................................ 205
Enabling LLDP Reception for a specific Port .................................................... 205
Enabling Notifications ...................................................................................... 205
LLDP Neighbors .................................................................................................... 207
LLDP Statistics ...................................................................................................... 208
LLDP Configuration Examples Using CLI Commands ........................................... 209
Enable/Disable LLDP ....................................................................................... 209
LLDP Holdtime Multiplier .................................................................................. 210
LLDP Transmit Interval .................................................................................... 210
Enable/Disable Global LLDP TLVs .................................................................. 211
Enabling LLDP Transmit on a Port ................................................................... 212
Enabling LLDP Receive on a Port .................................................................... 212
Enabling LLDP Notify ....................................................................................... 213
Enabling Transmission of the Management IP ................................................. 213
Enabling Specific TLV’s on a Port .................................................................... 214
VDSL ..................................................................................................................... 215
VDSL Status .......................................................................................................... 215
Other Protocols.................................................................................................... 216
GVRP .................................................................................................................... 216
General Overview ............................................................................................ 217
Enabling the GVRP Protocol at the Global Level ............................................. 218
Enabling the GVRP Protocol at the Port Level ................................................. 219
GVRP Configuration Examples Using CLI Commands .................................... 220
IGMP Snooping ..................................................................................................... 223
General Overview ............................................................................................ 223
Enabling the IGMP Snooping Modes ............................................................... 224
Configuring IGMP Snooping General properties .............................................. 225
Configuring IGMP Passive Mode Specific properties ....................................... 226
Configuring IGMP Querier Mode Specific properties ........................................ 227
Configuring IGMP Unknown Multicast Forwarding ........................................... 228
Monitoring Registered Multicast Groups .......................................................... 232
IGMP Configuration Examples Using CLI Commands ..................................... 233
Network Time Protocol .......................................................................................... 241
Enabling NTP ................................................................................................... 241
Setting the NTP Server IP Address .................................................................. 241
EtherWAN ED3575 Users Guide
x
Page 11

Preface
Setting the Timezone ....................................................................................... 241
Setting the Polling Period ................................................................................. 241
Manually Syncing Time .................................................................................... 242
Daylight Savings Time - Weekday Mode .......................................................... 242
Daylight Savings Time – Date Mode ................................................................ 243
Network Time Protocol Configuration Examples Using CLI Commands ........... 245
GMRP .................................................................................................................... 248
General Overview ............................................................................................ 248
GMRP Normal mode ........................................................................................ 248
GMRP Fixed mode .......................................................................................... 248
GMRP Forbidden mode ................................................................................... 249
GMRP Forward All mode ................................................................................. 249
GMRP Disabled mode ..................................................................................... 249
Enabling the GMRP Feature Globally on the Switch ........................................ 249
Configuring the GMRP Feature Per Port .......................................................... 250
GMRP Configuration Examples Using CLI Commands .................................... 253
DHCP Server ......................................................................................................... 255
General Overview ............................................................................................ 255
Configuring the DHCP Server .......................................................................... 255
DHCP Configuration Examples Using CLI Commands .................................... 258
DHCP Relay .......................................................................................................... 259
General Overview ............................................................................................ 259
Configuring the DHCP Relay ........................................................................... 259
DHCP Relay Configuration Examples Using CLI Commands........................... 261
TABLE OF FIGURES
Figure 1: Login screen ......................................................................................................... 20
Figure 2: Assigning an IP address ....................................................................................... 21
Figure 3: System Information .............................................................................................. 26
Figure 4: System Name/Password ...................................................................................... 27
Figure 5: IP Address............................................................................................................ 30
Figure 6: Management Interface.......................................................................................... 37
Figure 7: Save Configuration Page ...................................................................................... 43
Figure 8: Firmware Upgrade Page ...................................................................................... 48
Figure 9: User Mode............................................................................................................ 51
Figure 10: Creating Users ................................................................................................... 52
Figure 11: Selecting an Existing User Account .................................................................... 53
Figure 12: Deleting a User Account ..................................................................................... 53
EtherWAN ED3575 Users Guide
xi
Page 12

Preface
Figure 13: User Privilege Page ............................................................................................ 54
Figure 14: Utilization Page .................................................................................................. 58
Figure 15: System Log ........................................................................................................ 59
Figure 16: Remote Logging Page ........................................................................................ 61
Figure 17: ARP Table .......................................................................................................... 63
Figure 18: Route Table ........................................................................................................ 65
Figure 19: Alarm Trigger ..................................................................................................... 66
Figure 20: Trigger Enable .................................................................................................... 66
Figure 21: Port Configuration .............................................................................................. 68
Figure 22: Port Status ......................................................................................................... 69
Figure 23: Rate Control ....................................................................................................... 70
Figure 24: RMON Page ....................................................................................................... 71
Figure 25: Port VLAN Activities ........................................................................................... 72
Figure 26: Port Security ....................................................................................................... 73
Figure 27: Bridging .............................................................................................................. 82
Figure 28: Loopback Detection ............................................................................................ 84
Figure 29:Loopback Detection (port) ................................................................................... 85
Figure 30: Storm Detect – Global ........................................................................................ 86
Figure 31: Storm Detect – Per Port ..................................................................................... 87
Figure 32: MAC Static Entry ................................................................................................ 88
Figure 33: Removing a Static MAC ..................................................................................... 89
Figure 34: Adding a MAC – Static-MAC-Entry Table ........................................................... 89
Figure 35: Deleting a MAC – Static-MAC-Entry Table ......................................................... 90
Figure 36: Port Mirroring ..................................................................................................... 92
Figure 37: Disabling Port Mirroring ...................................................................................... 92
Figure 38: Link State Tracking ............................................................................................. 93
Figure 39: Link State Tracking – Port Settings..................................................................... 94
Figure 40: Port Trunking – Version 1 ................................................................................. 108
Figure 41: LACP Trunking Version 1 ................................................................................. 110
Figure 42: STP/Ring Global Configuration ......................................................................... 115
Figure 43: Bridge ID .......................................................................................................... 116
Figure 44: Bridge ID Display .............................................................................................. 117
Figure 45: Max Age, Hello Timer & Forward Delay ............................................................ 119
Figure 46: Spanning Tree Port Roles ................................................................................ 120
Figure 47: Port ID .............................................................................................................. 121
Figure 48: Port Priority and Path Cost ............................................................................... 122
Figure 49: Enabling MSTP ................................................................................................ 128
Figure 50: Bridge ID .......................................................................................................... 129
Figure 51: Bridge ID Display .............................................................................................. 130
Figure 52: Max Age, Hello Timer & Forward Delay ............................................................ 132
Figure 53: MSTP Region and Revision Level .................................................................... 133
Figure 54: MSTP Properties – Max Hops .......................................................................... 134
Figure 55: VLAN Instance Configuration ........................................................................... 135
EtherWAN ED3575 Users Guide
xii
Page 13

Preface
Figure 56: VLAN Instance ID ............................................................................................. 136
Figure 57: Setting the MSTI Regional Root Bridge ............................................................ 137
Figure 58: Port Cost & Priority ........................................................................................... 139
Figure 59: Port Instance Configuration .............................................................................. 140
Figure 60: Port Instance - Adding Ports ............................................................................. 141
Figure 61: α-Ring Settings ................................................................................................. 147
Figure 62: Ring Coupling ................................................................................................... 148
Figure 63: Alpha Chain Setting .......................................................................................... 151
Figure 64: Chain Ports – Master and Slave on one Switch ................................................ 151
Figure 65: Chain Ports – Master Chain Port ...................................................................... 152
Figure 66: Advanced Bridge Configuration ........................................................................ 156
Figure 67: Advanced Per Port Configuration ..................................................................... 157
Figure 68: Port Based VLAN ............................................................................................. 160
Figure 69: Port Based VLAN – Example 1 ......................................................................... 161
Figure 70: Port Based VLAN – Example 2 ......................................................................... 162
Figure 71: Tag-based VLAN .............................................................................................. 165
Figure 72: Add VLAN ........................................................................................................ 166
Figure 73: Add VLAN Page ............................................................................................... 166
Figure 74: Management VLAN IP Address ........................................................................ 170
Figure 75: VLAN Port Setting ............................................................................................ 171
Figure 76: VLAN Links ...................................................................................................... 172
Figure 77: VLAN Ports ...................................................................................................... 173
Figure 78: Tag or Untag ports ........................................................................................... 173
Figure 79: Global Configuration ......................................................................................... 175
Figure 80: 802.1p Priority .................................................................................................. 180
Figure 81: DSCP ............................................................................................................... 182
Figure 82: SNMP General Settings ................................................................................... 187
Figure 83: Community Name V1/V2c ................................................................................ 188
Figure 84: Add User .......................................................................................................... 189
Figure 85: SNMP v3 Settings ............................................................................................ 190
Figure 86: User name & Access Mode .............................................................................. 190
Figure 87: Auth Password ................................................................................................. 191
Figure 88: Privacy PassPhrase ......................................................................................... 191
Figure 89: Delete User ...................................................................................................... 192
Figure 90: Select User ....................................................................................................... 192
Figure 91: Enable Radius .................................................................................................. 198
Figure 92: Radius Setup .................................................................................................... 199
Figure 93: Resulting Radius Server Setup ......................................................................... 199
Figure 94: Enabling 802.1X on a Port ................................................................................ 201
Figure 95: LLDP Global Settings ....................................................................................... 204
Figure 96: LLDP Ports Settings ......................................................................................... 206
Figure 97: LLDP Neighbors ............................................................................................... 207
Figure 98: LLDP Statistics ................................................................................................. 208
EtherWAN ED3575 Users Guide
xiii
Page 14

Preface
Figure 99: VDSL Status Page ........................................................................................... 215
Figure 100: GVRP ............................................................................................................. 216
Figure 101: GVRP Configuration Distribution Switch ......................................................... 218
Figure 102: GVRP Configuration Access Switch ............................................................... 218
Figure 103: GVRP Per Port Settings ................................................................................. 219
Figure 104: IGMP Mode .................................................................................................... 224
Figure 105: IGMP General Properties ............................................................................... 225
Figure 106: IGMP Passive Mode ....................................................................................... 226
Figure 107: Querier Mode Properties ................................................................................ 227
Figure 108: Disabled Mode Forwarding Port ..................................................................... 228
Figure 109: PassiveForwardMode ..................................................................................... 229
Figure 110: ForceForwardMode ........................................................................................ 230
Figure 111: IGMP Querier Mode Forwarding ..................................................................... 231
Figure 112: Current Multicast Groups ................................................................................ 232
Figure 113: NTP Settings .................................................................................................. 242
Figure 114: Daylight Savings – Weekday Mode ................................................................ 243
Figure 115: Daylight Savings – Date Mode ....................................................................... 244
Figure 116: GMRP Global Setting ..................................................................................... 250
Figure 117: GMRP Per Port Setting .................................................................................. 252
Figure 118: DHCP Server ................................................................................................. 256
Figure 119: DHCP Bindings .............................................................................................. 257
Figure 120: DHCP Binding Table ...................................................................................... 257
EtherWAN ED3575 Users Guide
xiv
Page 15
Preface
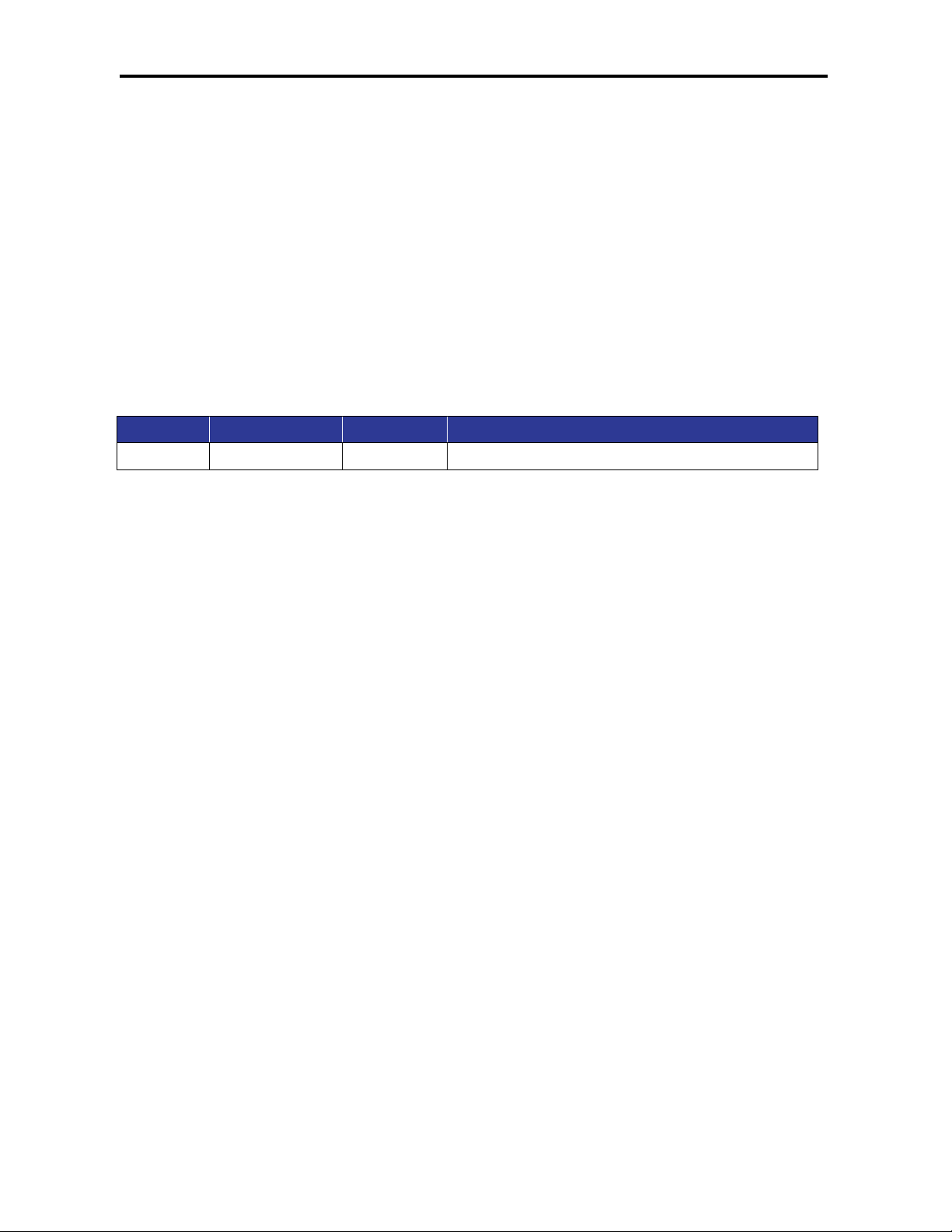
Revision
Document Version
Date
Description
A
Version 1
04/02/2015
Initial release for Firmware version 1.94.3.4
PREFACE
Audience
This guide is designed for the person who installs, configures, deploys, and maintains the
Ethernet network. This document assumes the reader has moderate hardware, computer,
and Internet skills.
Document Revision Level
This section provides a history of the revision changes to this document.
Changes in this Revision
N/A
xv
EtherWAN ED3575 Users Guide
Page 16

Preface
Symbol
Meaning
Description
Note
Notes emphasize or supplement important points of the main text.
Tip
Tips provide helpful information, guidelines, or suggestions for performing tasks more
effectively.
Warning
Warnings indicate that failure to take a specified action could result in damage to the
device, or could result in serious bodily injury.
Electric Shock Hazard
This symbol warns users of electric shock hazard. Failure to take appropriate
precautions such as not opening or touching hazardous areas of the equipment could
result in injury or death.
Convention
Description
Bold
Indicates text on a window, other than the window title, including menus, menu options, buttons, fields, and labels.
Italic
Indicates a variable, which is a placeholder for actual text provided by the user or system. Angled brackets (< >)
are also used to indicate variables.
screen/code
Indicates text that is displayed on screen or entered by the user.
< > angled
brackets
Indicates a variable, which is a placeholder for actual text provided by the user or system. Italic font is also used to
indicate variables.
[ ] square
brackets
Indicates optional values.
{ } braces
Indicates required or expected values.
| vertical bar
Indicates that you have a choice between two or more options or arguments.
Document Conventions
This guide uses the following conventions to draw your attention to certain information.
Safety and Warnings
This guide uses the following symbols to draw your attention to certain information.
Typographic Conventions
This guide also uses the following typographic conventions.
EtherWAN ED3575 Users Guide
xvi
Page 17

UNPACKING AND INSTALLATION
This chapter describes how to unpack and install the EtherWAN ED3575
The topics covered in this chapter are:
Package Contents (Page 17)
Unpacking (Page 17)
Required Equipment and Software (Page 18)
Computer Setup (Page 19)
Management Methods and Protocols (Page 19)
Default IP (Page 20)
Login Process and Default Credentials (Page 20)
Setting the initial IP address (Page 21)
Package Contents
When you unpack the product package, you will find the items listed below. Please inspect
the contents, and report any apparent damage or missing items immediately to your
authorized reseller.
The EtherWAN ED3575
Product CD
Quick Installation Guide
Unpacking
Follow these steps to unpack the EtherWAN ED3575 and prepare it for operation:
1. Open the shipping container and carefully remove the contents.
2. Return all packing materials to the shipping container and save it.
3. Confirm that all items listed in the "Package Contents" section are included in the
shipment. Check each item for damage. If any item is damaged or missing, notify your
authorized EtherWAN representative.
EtherWAN ED3575 Users Guide
17
Page 18

Required Equipment and Software
The following hardware and software are needed in order to manage the switch from the
web interface:
Computer with an Ethernet Interface (RJ-45)
Managing the switch requires a personal computer (PC) or notebook computer
equipped with a 10/100base-TX Ethernet interface and a physical RJ-45
connection. The preferred operating system for the computer is Microsoft Windows
XP/Vista/7. It is possible to use Apple OSX or Linux systems as well, but, for the
sake of brevity, all web configurations in this manual will be shown using Windows
7 as the underlying operating system.
Cat 5+ Ethernet Cables
An Ethernet cable of at least Category 5 rating is required to connect your
computer to the switch. The cable can be configured as “straight-through” or
crossover.
TFTP Server Software
Trivial file transfer protocol (TFTP) server software is needed to update the switch
firmware and to upload/download configuration files to the switch. Users not
performing these tasks do not need TFTP software installed. Several good TFTP
servers are available for free online. The server that will be used in this manual is
TFTPD32 by Philippe Jounin.
Web Browser Software
The end user can employ any of the following web browsers during switch
configuration: Internet Explorer, Firefox, or Chrome. Internet Explorer is the
preferred browser for EtherWAN switch configuration. If there is trouble with other
browsers while attempting to program the switch, Internet Explorer should be used.
EtherWAN ED3575 Users Guide
18
Page 19

COMPUTER SETUP
The end user’s management computer may need to be reconfigured prior to connecting to
the switch in order to access the switch’s web interface through its default IP address (See
Default IP).
Management Methods and Protocols
There are several methods that can be used to manage the switch. This manual
will show the details of configuring the switch using a web browser. Each section
will be followed by the CLI (Command Line Interface) commands needed to
achieve the same results as described in that section.
The methods available to manage the EtherWAN ED3575 include:
SSH - Secure Shell CLI that is accessible over TCP/IP networks which and
is generally regarded as the most secure method of remotely accessing a
device.
Telnet - is like SSH in that it allows a CLI to be established across a
TCP/IP network, but it does not encrypt the data stream.
HTTP (Hypertext Transfer Protocol) is the most popular switch
management protocol involving the use of a web browser.
RS232 – The EtherWAN ED3575 is equipped with an RS232 serial port
that can be used to access the switches CLI. The Serial port is DCE DB9F.
A straight through serial cable is used to connect to a typical computer
serial port.
EtherWAN ED3575 Users Guide
19
Page 20

Default IP
The switch’s default IP address is 192.168.1.10. The user will need to modify the
management computer so that it is on the same network as the switch. For
example, the user could change the IP address of the management computer to
192.168.1.100 with a subnet mask of 255.255.255.0.
Login Process and Default Credentials
Once a compatible IP address has been assigned to the management computer,
the user is ready to log into the switch. To log in, type the URL http://192.168.1.10/
into the address field of the browser and hit return. The following will appear in the
browser window (See Figure 1)
The Default Login is root (case sensitive)
There is no password by default
Enter the login name and click the Login button
Figure 1: Login screen
20
EtherWAN ED3575 Users Guide
Page 21
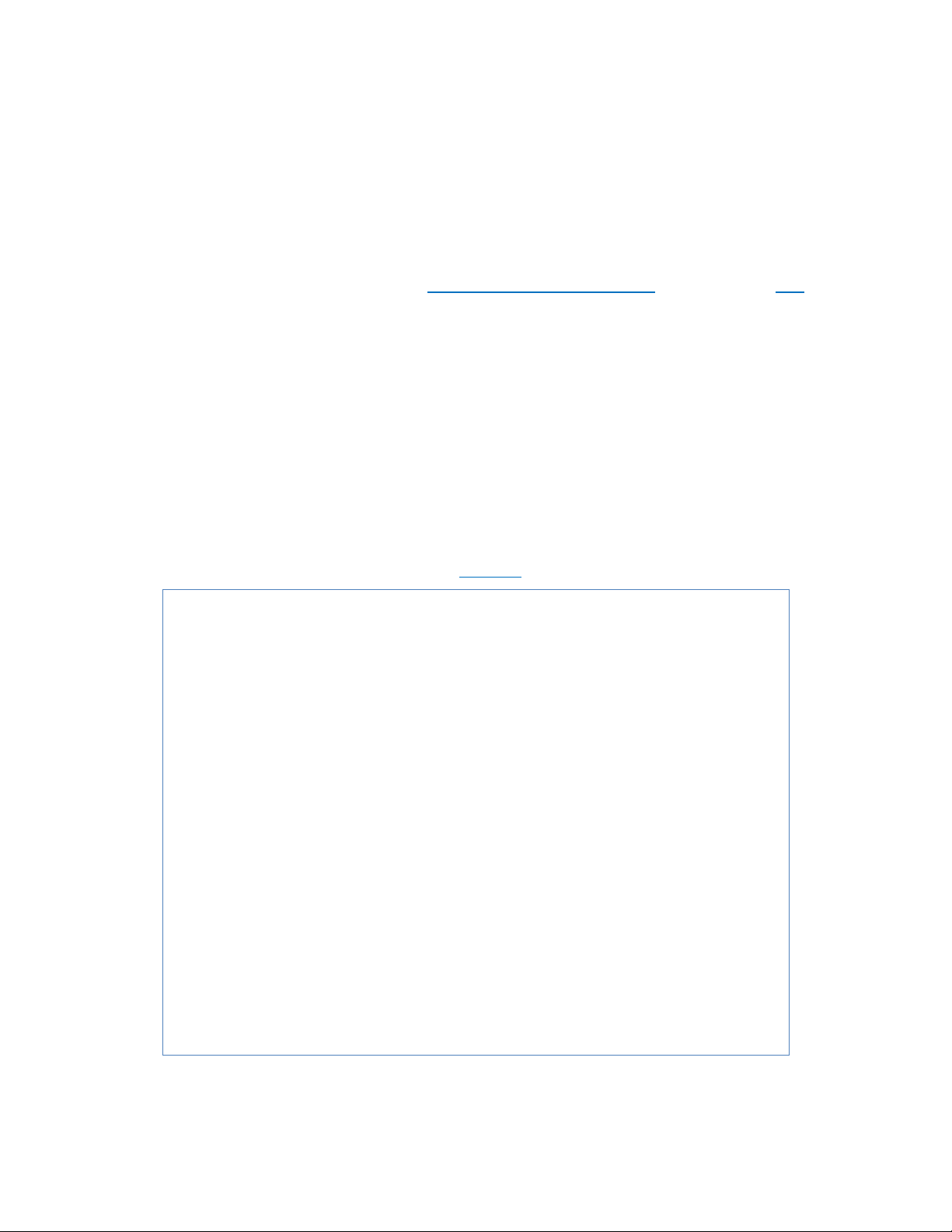
SETTING THE INITIAL IP ADDRESS
Once logged in the user can now configure the extender per the network requirements. The
two major addressing options are:
Simple IP addressing
Multiple VLAN addressing (See Add an IP to the Management VLAN on page 170).
Simple IP Addressing
A new IP address can now be assigned to the switch. From the System Information screen,
go to the left-hand navigation menu.
1. Click on the + next to System
2. Click on IP address
3. Enter the desired IP address and subnet mask in the IP Address/Subnet Mask
fields associated with VLAN 1
4. Click the Apply & Save button (See Figure 2)
Figure 2: Assigning an IP address
EtherWAN ED3575 Users Guide
21
Page 22

CLI COMMAND USAGE
This chapter describes accessing the EtherWAN ED3575 by using Telnet, SSH, or serial
ports to configure the Switch, navigating the Command Line Interface (CLI), typing keyboard
shortcuts, and moving between the levels. This chapter assumes the user has a working
understanding of Telnet, SSH, and Terminal emulation applications.
Note: For a serial port connection use a standard DB9F to DB9M Modem Cable. The
default Serial port parameters are 115200, 8 None 1, No Flow Control.
Navigating the CLI Hierarchy
The CLI is organized into a hierarchy of levels. Each level has a group of commands for a
specific purpose. For example, to configure a setting for the VLAN server, one would
navigate to the VLAN level, which is under the config level.
CLI Keyboard Shortcuts
Ctrl + a: place cursor at the beginning of a line
Ctrl + b: backspace one character
Ctrl + d: delete one character
Ctrl + e: place cursor at the end of the line
Ctrl + f: move cursor forward one character
Ctrl + k: delete from the current position to the end of the line
Ctrl + l: redraw the command line
Ctrl + n: display the next line in the history
Ctrl + p: display the previous line in the history
Ctrl + u: delete entire line and place cursor at start of prompt
Ctrl + w: delete one word back
EtherWAN ED3575 Users Guide
22
Page 23

CLI Command modes
Throughout this manual, each section that has CLI commands relevant to that section
requires that the CLI be in a specific configuration mode. This section shows the main CLI
commands to needed to enter a specific mode.
General Configuration Mode
To set the EtherWAN ED3575 to General configuration mode, run the following
commands from the CLI:
1. enable
2. configure terminal
Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#
MSTP Configuration Mode
To set the EtherWAN ED3575 to General MSTP configuration mode, run the
following commands from the CLI:
1. enable
2. configure terminal
3. spanning-tree mst configuration
Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#spanning-tree mst configuration
switch_a(config-mst)#
23
EtherWAN ED3575 Users Guide
Page 24

Interface Configuration Mode
Interface mode on the EtherWAN ED3575 is used to configure the Ethernet ports and VLAN
information. Valid interfaces are:
fe<port #> - 100mb ports use fe followed by the port number. Example: fe1
ge<port #> - Gigabit ports use ge followed by the port number. Example: ge1
vlan1.<vlan#> - VLAN’s use vlan. Followed by the VLAN ID. Example: vlan1.10
Example 1 configures 100mb port 1
switch_a>enable
switch_a#configure terminal
switch_a(config)#interface fe1
switch_a(config-if)
Example 2 configures VLAN ID 9
switch_a>enable
switch_a#configure terminal
switch_a(config)#interface vlan1.9
switch_a(config-if)
VLAN Database Configuration Mode
VLAN Database Configuration Mode on the EtherWAN ED3575 is used to configure the
VLAN settings.
Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#vlan database
switch_a(config-vlan)#
Saving a Configuration from the CLI
Example:
switch_a>enable
switch_a#write memory
Building configuration.....
[OK]
switch_a#>
EtherWAN ED3575 Users Guide
24
Page 25

SYSTEM MENU
System Information
The System information link on the Left menu of the Web Configuration page takes you to a
page that shows the following (see Figure 3):
System Name
o The System name is typically used by network administrators. If SNMP is
enabled on the Switch, the system name can be found using MIB II
(RFC1213) in the sysName property.
Firmware Version
o If SNMP is enabled on the Switch, the Firmware version can be found using
MIB II in the sysDesc property
System Time
o System time can be change using NTP
MAC Address
o The hardware (MAC) address of the Management interface
Default Gateway
o The IP address of your networks Gateway (Typically a Router on your
network)
DNS Server
o The Dynamic Name Server (DNS) for your network
VLAN ID
o One or more listings depending on the number of VLANs defined on the
Switch
o Lists VLAN ID, IP address, and subnet mask of the VLAN Interface(s)
Current User Information
o Lists the current the currently logged in user and their user privileges
25
EtherWAN ED3575 Users Guide
Page 26

Figure 3: System Information
EtherWAN ED3575 Users Guide
26
Page 27
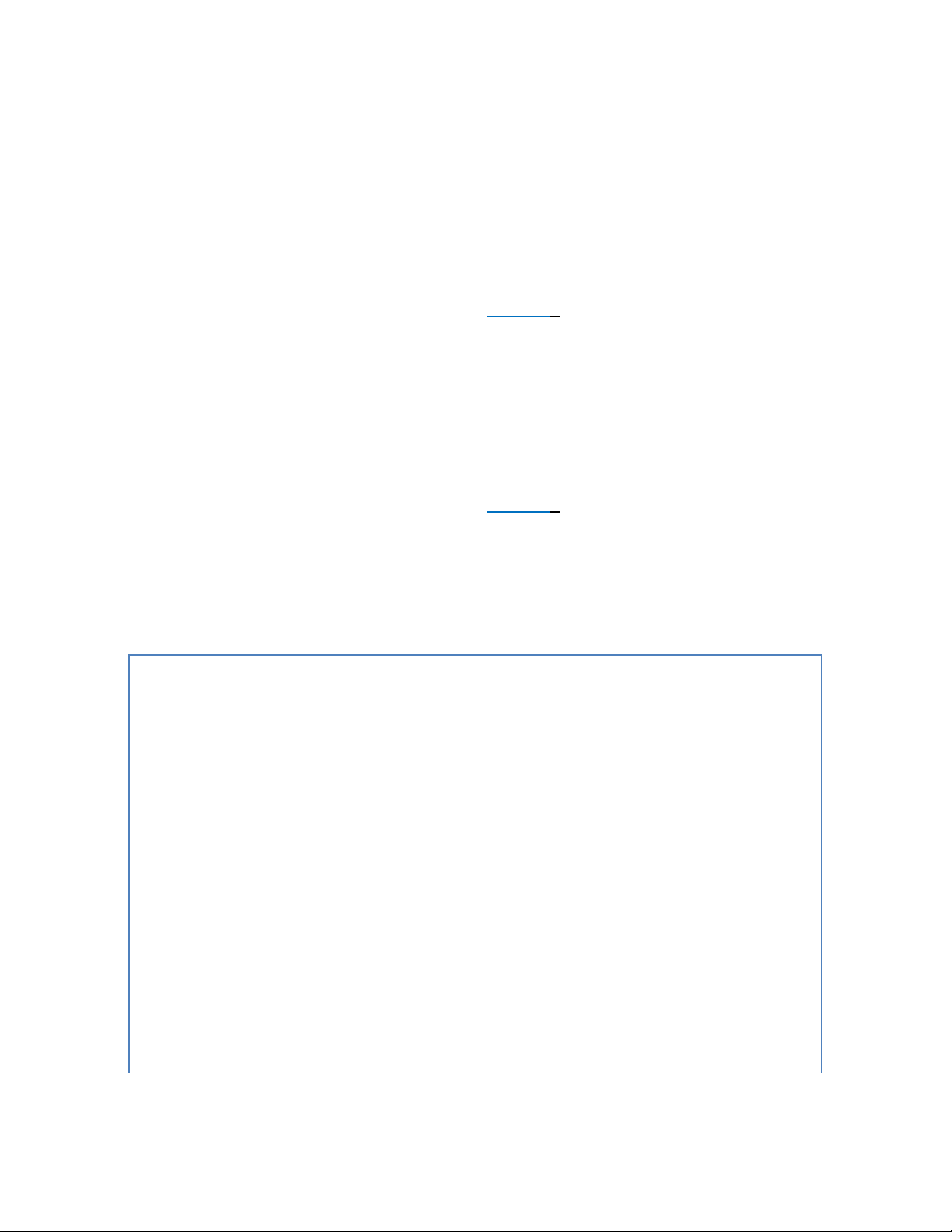
System Name/Password
The System name is typically used by network administrators to make it easier to document
a networks infrastructure and locate equipment on large networks. If SNMP is enabled on
the Switch, the system name can be found using MIB II (RFC1213) in the sysName
property. To change the system name:
1. Click on the + next to System.
2. Click on System Name/Password (see Figure 4).
3. Use your mouse to place the cursor in the System Name text box.
4. Replace the existing name with the name you want to assign to the Switch.
5. Click on the Update Setting button.
By default, there is no password assigned to the Switch. To add or change a password:
1. Click on the + next to System.
2. Click on System Name/Password (see Figure 4).
3. Use your mouse to place the cursor in the Password text box.
4. Enter the new password.
5. Retype the password in the Retype Password text box.
6. Click on the Update Setting button below the Retype Password text box.
Figure 4: System Name/Password
EtherWAN ED3575 Users Guide
27
Page 28

System Name/Password using the CLI
For more information on CLI command usage see CLI Command Usage.
System Name
To set the system name on a Switch, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
hostname <name>
no hostname
Usage Example 1: Setting a Hostname
switch_a>enable
switch_a#configure terminal
switch_a(config)#hostname switch_a
switch_a(config)#q
switch_a#
Usage Example 2: Removing a Hostname
switch_a>enable
switch_a#configure terminal
switch_a(config)#no hostname
switch_a(config)#q
switch_a#
Password
To enable a password on a Switch, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
enable password <password>
Usage Example
switch_a>enable
switch_a#configure terminal
switch_a(config)#enable password mypassword
switch_a(config)#q
switch_a#
28
EtherWAN ED3575 Users Guide
Page 29

IP Address
To navigate to the IP Address page:
1. Click on the + next to System
2. Click on IP Address (see Figure 5)
There are 4 settings on this page:
Static IP (see Simple IP Addressing)
DHCP Client
Use this to enable or disable DHCP on a VLAN.
To enable the DHCP Client:
1. Use the drop down box to enable the DHCP client on a particular VLAN
2. Click the Submit Button
Default Gateway
If DHCP is enabled, the gateway setting is controlled by the DHCP server. The
setting will be grayed out and the gateway supplied by the DHCP server will be
displayed. The default gateway setting can be used when using a Static IP address.
To enable the default gateway:
1. Use the drop-down box to enable the default gateway.
2. Type in the default gateway in the Default Gateway text box.
3. Click on the Apply & Save button.
DNS Server
If DHCP is enabled, the DNS Server setting is controlled by the DHCP server. The
setting will be grayed out and the DNS Server supplied by the DHCP server will be
displayed. The DNS Server setting can be used when using a Static IP address. To
enable the DNS Server:
1. Use the drop-down box to enable the DNS Server.
2. Type in the default gateway in the Default Gateway text box.
3. Click on the Submit button.
Note: After making changes to settings in the IP address section, the
configuration needs to be saved using the System/Save configuration page
(See Save Configuration)
29
EtherWAN ED3575 Users Guide
Page 30
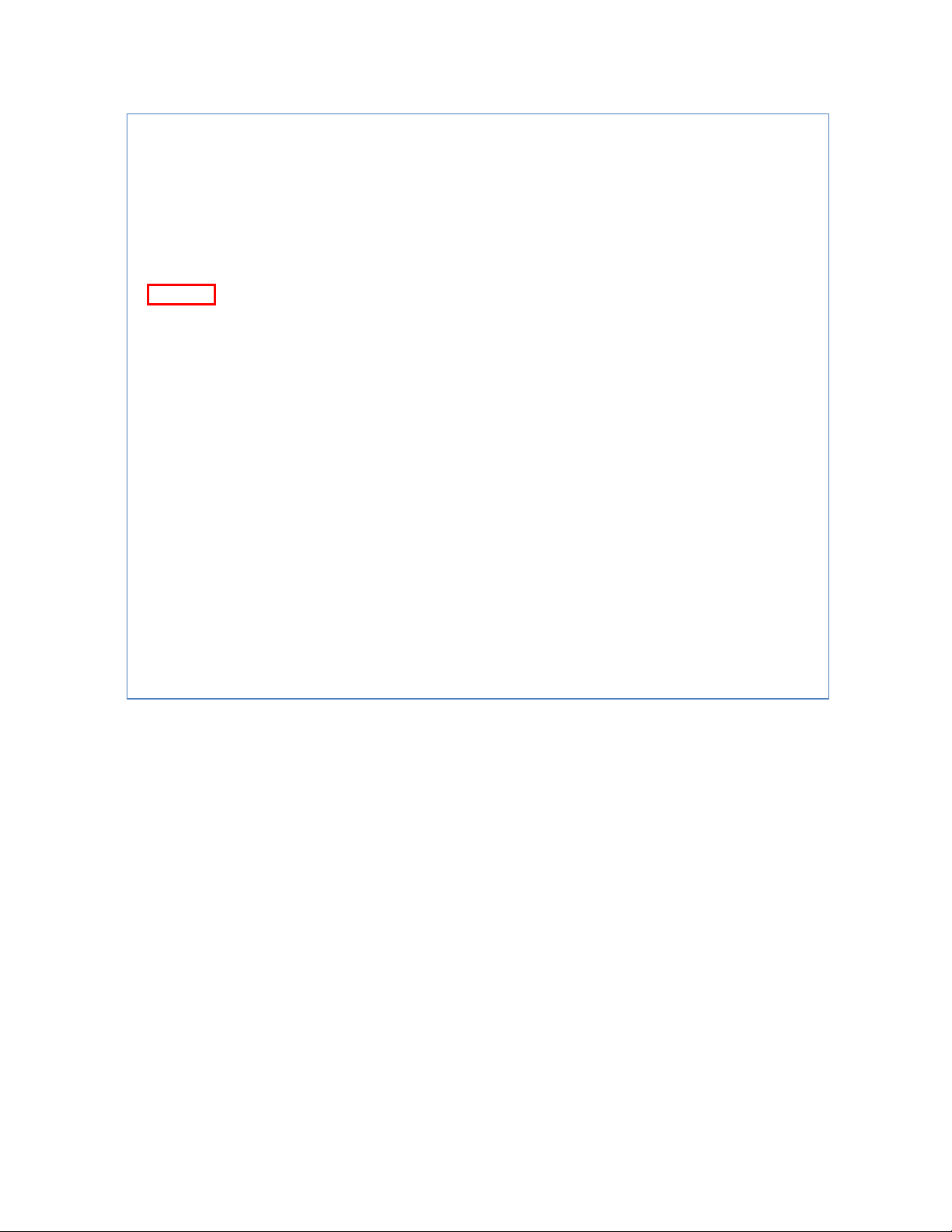
Figure 5: IP Address
EtherWAN ED3575 Users Guide
30
Page 31

IP Address - Configuration using the CLI
For more information on CLI command usage see CLI Command Usage.
IP Address
To set the IP address, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
ip address <A.B.C.D/M> (IP Address/Mask e.g. 10.0.0.1/8)
no ip address
Note: The Subnet Mask is defined as a Network Prefix instead of the common dotted
decimal (ex. 255.255.255.0).
The most commonly used Network Prefixes are:
/8 – Known as Class A. Also known in dotted decimal as 255.0.0.0
/16– Known as Class B. Also known in dotted decimal as 255.255.0.0
/24– Known as Class C. Also known in dotted decimal as 255.255.255.0
Usage Example 1: Assigning an IP address
switch_a>enable
switch_a#configure terminal
switch_a(config)#ip address 192.168.1.1/24
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
Usage Example 2: Removing an IP address
switch_a>enable
switch_a#configure terminal
switch_a(config)#no ip address
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
EtherWAN ED3575 Users Guide
31
Page 32

Default Gateway
To set the Default Gateway, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
ip default-gateway <A.B.C.D>
no ip default gateway
Usage Example 1: Setting the Gateway
switch_a>enable
switch_a#configure terminal
switch_a(config)#ip default-gateway 192.168.1.254
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
Usage Example 2: Removing the Gateway
switch_a>enable
switch_a#configure terminal
switch_a(config)#no ip default-gateway
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
32
EtherWAN ED3575 Users Guide
Page 33

Domain Name Server (DNS)
To set the DNS, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
ip dns <A.B.C.D>
no ip dns
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#ip dns 192.168.1.253
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
Usage Example 2: Remove a DNS IP Address
switch_a>enable
switch_a#configure terminal
switch_a(config)#no ip dns
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
EtherWAN ED3575 Users Guide
33
Page 34

Enable/Disable DHCP Client on a VLAN
To enable the DHCP client on a VLAN, use the following CLI commands:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax:
get ip dhcp enable
no get ip dhcp enable
Usage Example – Enable DHCP Client on VLAN2:
switch_a>enable
switch_a#configure terminal
switch_a(config)#interface vlan1.2
switch_a(config-if)#get ip dhcp enable
switch_a(config-if)#q
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
Enable/Disable Static IP on a VLAN
To set the IP address, use the following CLI commands:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax:
ip address <A.B.C.D>
no ip address <A.B.C.D>
Usage Example 1 – Enable Static IP on VLAN2:
switch_a>enable
switch_a#configure terminal
switch_a(config)#interface vlan1.2
switch_a(config-if)#ip address 192.168.1.11
switch_a(config-if)#q
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
34
EtherWAN ED3575 Users Guide
Page 35

Usage Example 2 – Enable DHCP Client on VLAN2:
switch_a>enable
switch_a#configure terminal
switch_a(config)#interface vlan1.2
switch_a(config-if)#no ip address 192.168.1.11
switch_a(config-if)#q
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
EtherWAN ED3575 Users Guide
35
Page 36

Management Interface
To navigate to the Management Interface page:
1. Click on the + next to System
2. Click on Management Interface
The Management Interface configuration page has three settings that allow the user to
configure the methods available to manage the EtherWAN ED3575.
HTTPS
HTTPS (Hypertext Transfer Protocol Secure) allows the user to determine what
method, if any, is used to configure the EtherWAN ED3575. The default is
unencrypted HTTP (see Figure 6).
To disable the Web interface:
1. Uncheck Http and Https.
2. Click on the Update setting button.
Warning! Once the Submit button is pressed, the Web console will no longer
function. As a safety precaution, the configuration is not saved by default. Rebooting
the EtherWAN ED3575 will restore the Web Console. To save the configuration,
connect using the new IP address.
To enable the Web Interface:
1. Check HTTP, HTTPS or both
2. Click on the Update Setting button.
3. Save the Configuration (see Save Configuration)
Telnet.
Telnet is a network protocol that allows a remote computer to log into the EtherWAN
ED3575 to access its CLI (Command Line Interface). The CLI can be accessed using
Telnet, SSH and the serial port on the EtherWAN ED3575. The secure method of
accessing the CLI over a network is SSH.
To enable or disable Telnet:
1. Click the Enable or Disable radio button in the Telnet section on the
Management Interface page (see Figure 6 below)
2. Click on the Update Setting button
3. Save the Configuration (see Save Configuration)
EtherWAN ED3575 Users Guide
36
Page 37

SSH (Secure Shell)
Secure Shell or SSH is a network protocol that allows data to be exchanged using a
secure channel between two networked devices such as a computer and the
EtherWAN ED3575. SSH is disabled by default on the V1.94.3.4 EtherWAN ED3575.
To enable or disable SSH:
1. Click the Enable or Disable radio button in the SSH section on the
Management Interface page (see Figure 6)
2. Click on the Update Setting button
3. Save the Configuration (see Save Configuration)
Figure 6: Management Interface
37
EtherWAN ED3575 Users Guide
Page 38

Management Interface Configuration using the CLI
For more information on CLI command usage see CLI Command Usage.
Enabling/Disabling Telnet
To enable or disable telnet, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
ip telnet
no ip telnet
Usage Example 1: Enabling Telnet:
switch_a>enable
switch_a#configure terminal
switch_a(config)#ip telnet
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
Usage Example 2: Disabling Telnet:
switch_a>enable
switch_a#configure terminal
switch_a(config)#no ip telnet
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
Note: If using Telnet to run the CLI Commands that disable telnet you will lose your
connection. To Disable Telnet using the CLI, use SSH or the RS232 Console port on
the Switch.
EtherWAN ED3575 Users Guide
38
Page 39

Enabling/Disabling SSH
To enable or disable SSH, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
ip ssh
no ip ssh
Usage Example 1: Enabling SSH:
switch_a>enable
switch_a#configure terminal
switch_a(config)#ip ssh
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
Usage Example 2: Disabling SSH:
switch_a>enable
switch_a#configure terminal
switch_a(config)#no ip ssh
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
Note: If using SSH to run the CLI Commands that disable SSH you will lose your
connection. To Disable SSH using the CLI, use Telnet or the RS232 Console port on
the Switch.
EtherWAN ED3575 Users Guide
39
Page 40

Enabling/Disabling HTTP and/or HTTPS
To enable or disable telnet, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
ip http server
ip http secure-server
no ip http server
no ip http secure-server
Usage Example 1: Enabling HTTP:
switch_a>enable
switch_a#configure terminal
switch_a(config)#ip http server
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
Usage Example 2: Disabling HTTP:
switch_a>enable
switch_a#configure terminal
switch_a(config)#no ip http server
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
40
EtherWAN ED3575 Users Guide
Page 41

Usage Example 3: Enabling HTTPS:
switch_a>enable
switch_a#configure terminal
switch_a(config)#ip http secure-server
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
Usage Example 4: Disabling HTTPS:
switch_a>enable
switch_a#configure terminal
switch_a(config)#no ip http secure-server
switch_a(config)#q
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
EtherWAN ED3575 Users Guide
41
Page 42

Save Configuration Page
To navigate to the Save Configuration page:
1. Click on the + next to System
2. Click on Save Configuration
The Save Configuration page contains the following configuration functions (see Figure 7):
Save Configuration
To save the currently running configuration to the flash memory on the EtherWAN
ED3575:
1. Click the Save Configuration button
2. If the save is successful you will see the message:
Building configuration….. [OK]
Load Configuration
This function is used to load a previously saved configuration. Backing up and
loading a configuration is achieved using a TFTP server.
To load a configuration:
1. Enter the IP address of your TFTP server in the TFTP Server text box
2. Enter the name of the configuration file in the FILE text box
3. Click on the Backup button
4. If the file is successfully loaded the following message will be shown:
Success! System reboot is required!
Backup Configuration
This function is used to backup the current configuration of the EtherWAN ED3575.
Backing up the configuration is achieved using a TFTP server such as TFTPD32.
To backup a configuration:
1. Enter the IP address of your TFTP server in the TFTP Server text box
2. Enter the name of the configuration file in the FILE text box
3. Click on the Backup button
4. If the backup is successful the following message will be shown:
tftp <filename> to ip <ip address> success!!
EtherWAN ED3575 Users Guide
42
Page 43

Restore Default
To restore the V1.94.3.4 EtherWAN ED3575 to factory defaults:
1. Click on the Restore Default button.
Auto Save
The Auto Save function is used to set the switch to automatically save the
configuration to flash. If the saved configuration is the same as the running
configuration then a save is not made. The Auto Save interval is used to determine
how often the running configuration is checked for changes.
To set the Auto Save function:
1. Click the drop-down box next to Auto Save.
2. Set the Auto Save interval (5~65535 sec)
Note: If a Firewall is running on the PC that is running the TFTP server it may need
to be temporarily disabled.
Figure 7: Save Configuration Page
EtherWAN ED3575 Users Guide
43
Page 44

Save Configuration Page using the CLI
For more information on CLI command usage see CLI Command Usage.
Saving a Configuration
To save a running configuration, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
write memory
Usage Example 1: Saving a Configuration
switch_a>enable
switch_a#write memory
Building configuration.....
[OK]
switch_a#q
switch_a#
Restore Default Settings
To restore the Switch to its default settings, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
restore default
Usage Example 1: Restoring Defaults
switch_a>enable
switch_a#restore default
switch_a#q
switch_a#
44
EtherWAN ED3575 Users Guide
Page 45

Load Configuration from a TFTP Server
To Load a Configuration from a TFTP server, use the following CLI commands:
CLI Command Mode: Privileged Exec Mode
CLI Command Syntax:
install config-file <tftpserver_ipaddress> <filename>
Usage Example: Loading a Configuration
switch_a>enable
switch_a#install config-file 192.168.1.100 file_name.txt
switch_a#q
switch_a#
Save Configuration to a TFTP Server
To Save a Configuration to a TFTP server, use the following CLI commands:
CLI Command Mode: Privileged Exec Mode
CLI Command Syntax:
write confige-file <tftpserver_ipaddress> <filename>
Usage Example: Saving a Configuration
switch_a>enable
switch_a#write config-file 192.168.1.100 flash.tgz
switch_a#q
switch_a>
45
EtherWAN ED3575 Users Guide
Page 46

Auto Save Configuration
To set the Auto Save Configuration, use the following CLI commands:
CLI Command Mode: Privileged Exec Mode
CLI Command Syntax:
service auto-config enable
no service auto-config enable
service auto-config interval <number>
Usage Example 1: Enabling Auto Save and setting the interval
switch_a>enable
switch_a#service auto-config enable
switch_a#service auto-config interval 10
switch_a#q
switch_a>
Usage Example 2: Disabling Auto Save
switch_a>enable
switch_a#no service auto-config enable
switch_a#q
switch_a>
EtherWAN ED3575 Users Guide
46
Page 47

Firmware Upgrade
To navigate to the Firmware Upgrade page:
1. Click on the + next to System
2. Click on Firmware Upgrade
To upgrade the firmware on the EtherWAN ED3575, a TFTP server is required. The
firmware file for the V1.94.3.4 EtherWAN ED3575 is in a .TGZ or .IMG format. This is a
compressed file; however, it should not be decompressed before updating the V1.94.3.4
EtherWAN ED3575.
To update the firmware on the EtherWAN ED3575 (see Figure 8):
1. Copy the firmware file to the correct directory for your TFTP server. The correct
directory depends on your TFTP server settings
2. Enter the filename of the firmware in the Filename text box.
3. Enter the IP Address of your TFTP server in the TFTP Server IP text box.
4. Click on the Upgrade button.
5. During the firmware upgrade, you will see the following messages. Do not reboot or
unplug the Switch until the final message is received.
a. Downloading now, please wait...
b. tftp <filename>.img from ip <ip address> success!!
Install now. This may take several minutes, please
wait...
c. Firmware upgrade success!
Note: If a Firewall is running on the PC that is running the TFTP server it may need to
be temporarily disabled.
EtherWAN ED3575 Users Guide
47
Page 48

Figure 8: Firmware Upgrade Page
Firmware Update using the CLI
For more information on CLI command usage see CLI Command Usage.
CLI Command Mode: Privileged Exec Mode
CLI Command Syntax:
install image <tftpserver_ipaddress> <filename>
Usage Example:
switch_a>enable
switch_a#install image 192.168.1.100 flash.tgz
switch_a#q
switch_a#
Note: Depending on the firmware being loaded, the extension may not be .tgz. The
Switch does not use the extension to validate firmware.
48
EtherWAN ED3575 Users Guide
Page 49

Reboot
To navigate to the Reboot page:
1. Click on the + next to System
2. Click on Reboot
To reboot the EtherWAN ED3575:
1. Click on the Reboot button.
2. Click OK on the popup message.
Reboot using the CLI
For more information on CLI command usage see CLI Command Usage.
CLI Command Mode: Privileged Exec Mode
CLI Command Syntax:
reload
Usage Example:
switch_a>enable
switch_a#reload
switch_a#q
switch_a#
Logout
To logout of the Web Configuration Console:
1. Click on the + next to System
2. Click on Logout
Logout from the CLI
CLI Command Mode: Exec mode or Privileged Exec Mode
CLI Command Syntax:
logout
49
EtherWAN ED3575 Users Guide
Page 50

User Account Page
To navigate to the User Account page:
1. Click on the + next to System
2. Click on User Account
From the User Account page, multiple users can be setup with different access privileges to
the switch. There are two modes that can be used, Single-User or Multi-User.
Changing the User Mode
To set the user mode (see Figure 9):
1. Select Single-User, Multi-User or Radius-User in the drop-down box in the Multi-
User Mode section. See IEEE 802.1X for more information on setting up Radius
Authentication.
2. Click on the Update Setting button.
3. Click OK on the Popup message that appears.
Note: Changing the user mode saves the configuration and reboots the Switch
EtherWAN ED3575 Users Guide
50
Page 51

Figure 9: User Mode
Creating a New User
To create a new user (see Figure 10):
1. Choose the Create option from the drop-down list next to the User Account row
heading.
2. Enter a User Name (case sensitive) for the new user in the User Name text box.
3. Enter a Password for the new user in the Password text box.
4. Re-enter the Password in the Confirm Password text box.
5. Select a Privilege Level from the drop-down list next to the Privilege Level row
heading. For more information on Privilege levels see the User Privilege
Configuration.
6. Click on the Update button.
7. Save the configuration (See the Save Configuration Page)
51
EtherWAN ED3575 Users Guide
Page 52

Figure 10: Creating Users
Changing an Existing User Account
To make modifications to an existing user account:
1. Choose an existing user from the drop-down list next to the User Account row
heading (see Figure 11).
2. Change the password and/or access level following the steps in Creating a New
User.
3. To delete an existing user, select the user as in step 1 and then click on the Delete
button (see Figure 12).
EtherWAN ED3575 Users Guide
52
Page 53

Figure 11: Selecting an Existing User Account
Figure 12: Deleting a User Account
User Privilege Configuration
To navigate to the User Privilege page:
1. Click on the + next to System.
2. Click on User Privilege.
There are 3 different Privilege levels on the EtherWAN ED3575.
Admin – Has access to all configuration and administration of the Switch.
Technician – Configurable by Admin – By default no configuration ability is given.
Operator – Configurable by Admin – By default no configuration ability is given.
EtherWAN ED3575 Users Guide
53
Page 54

The User Privilege Configuration page allows specific configuration and/or administration
levels to be assigned or removed from the Technician and Operator user roles.
Note: For each function, an operator’s privilege cannot be higher than a technician's
To configure the privileges for each user access level, follow the below steps:
1. For each of the configuration options listed under Web function \ User Privilege
(see Figure 13), select the proper privilege from the drop-down list under the
appropriate user access level (Technician or Operator). The valid options are:
a. Show, Hidden, Read-Only, Read-Write
2. Click on the Update button at the bottom of the page.
3. Save the configuration (see Save Configuration)
Figure 13: User Privilege Page
54
EtherWAN ED3575 Users Guide
Page 55

User Account Settings using the CLI
For more information on CLI command usage see CLI Command Usage.
Multi-User Mode
To enable the multi-user feature, use the following CLI commands:
CLI Command Mode: Line Configuration Mode
CLI Command Syntax: login local
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#line console 0
switch_a(config-line)#login local
% Switching Single/Multi/Radius-User mode need to reboot the
switch to take effect!
switch_a(config-line)#q
switch_a(config)#q
switch_a#
Single User Mode
To enable the single-user feature, use the following CLI commands:
CLI Command Mode: Line Configuration Mode
CLI Command Syntax: login
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#line console 0
switch_a(config-line)#login
% Switching Single/Multi/Radius-User mode need to reboot the
switch to take effect!
switch_a(config-line)#q
switch_a(config)#q
switch_a#
EtherWAN ED3575 Users Guide
55
Page 56

Radius User Mode
To enable the radius-user feature, use the following CLI commands:
CLI Command Mode: Line Configuration Mode
CLI Command Syntax: login radius
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#line console 0
switch_a(config-line)#login radius
% Switching Single/Multi/Radius-User mode need to reboot the
switch to take effect!
switch_a(config-line)#q
switch_a(config)#q
switch_a#
EtherWAN ED3575 Users Guide
56
Page 57

Creating a New User
To create a new user, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
username <user name-4 to 16 characters> privilege
<admin|operator|technician> password < 8|blank> <password-1 to 35
characters>
Note: The optional <8> CLI command after the CLI command password is
used to specify that the password should be displayed in encrypted form in the
configuration file.
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#username user1 privilege operator password 1234
switch_a(config)#username user1 privilege operator password 8 1234
switch_a(config)#username user2 privilege technician password 4321
switch_a(config)#username user2 privilege technician password 8 4321
switch_a(config)#username user3 privilege admin password 5678
switch_a(config)#username user3 privilege admin password 8 5678
switch_a(config)#q
switch_a#
Permissions
Permissions must be set using the Web GUI. See User Privilege Configuration.
EtherWAN ED3575 Users Guide
57
Page 58

DIAGNOSTICS
Utilization
To navigate to the Utilization page:
1. Click on the + next to Diagnostics.
2. Click on Utilization.
The Utilization page shows (see Figure 14):
CPU Utilization – Current and Max Utilization
Memory Utilization – Total, Used and Free Memory
Figure 14: Utilization Page
58
EtherWAN ED3575 Users Guide
Page 59

System Log
To navigate to the System Log page:
1. Click on the + next to Diagnostics.
2. Click on System Log.
The System Log shows the date and time of port links going up or down (see Figure 15)
Figure 15: System Log
System log using CLI command
For more information on CLI command usage see CLI Command Usage.
CLI Command Mode: Exec Mode or Privileged Exec Mode
CLI Command Syntax:
show system-log
Usage Example:
switch_a#show system-log
switch_a#q
switch_a#
EtherWAN ED3575 Users Guide
59
Page 60

Remote Logging
To navigate to the Remote Logging page:
1. Click on the + next to Diagnostics.
2. Click on Remote Logging.
Remote Logging to a Syslog server allows administrators to log important system and
debugging information. The Remote Logging configuration page allows reporting to a Syslog
server to be enabled or disabled as well as management of a list of Syslog servers to report
to (see Figure 16).
To configure the Remote Logging on the EtherWAN ED3575:
1. Click on the Enable or Disable radio button under Remote Logging.
2. Click on the Update Setting button.
To add a Syslog server:
1. Enter the IP Address of the Syslog Server in the Syslog Server IP text box.
2. Click on the Add Syslog Server button.
To delete a Syslog server from the list of servers currently on the switch:
1. Select the Syslog server from the Drop down box
2. Click on the Delete Syslog Server button
EtherWAN ED3575 Users Guide
60
Page 61

Figure 16: Remote Logging Page
EtherWAN ED3575 Users Guide
61
Page 62

Remote Logging using CLI commands
For more information on CLI command usage see CLI Command Usage.
Enable/Disable Remote Logging
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
remote-log enable
no remote-log enable
Usage Example 1: Enable Remote Logging
switch_a>enable
switch_a#remote-log enable
switch_a#q
switch_a#
Usage Example 2: Disable Remote Logging
switch_a>enable
switch_a#no remote-log enable
switch_a#q
switch_a#
Add/Delete a Remote Logging Host
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
remote-log add <ip_address>
remote-log del <ip_address>
remote-log del all
Usage Example 1: Add a Remote Logging Host
switch_a>enable
switch_a#remote-log add 192.168.1.100
switch_a#q
switch_a#
Usage Example 2: Delete a Remote Logging Host
switch_a>enable
switch_a#remote-log del 192.168.1.100
switch_a#q
switch_a#
EtherWAN ED3575 Users Guide
62
Page 63

ARP Table
To navigate to the ARP Table page:
1. Click on the + next to Diagnostics.
2. Click on ARP Table.
The ARP Table page shows ARP (Address Resolution Protocol) entries that are stored in
the Switches ARP Table. This is useful for System Administrators for troubleshooting
purposes. The information shown is:
IP Address of the listed device
Hardware Address – For Ethernet devices this will always be 1.
Flags
o 2 = Device responded to ARP Request
o 0 = No response to ARP Request
Hardware Address – MAC Address of the listed device
VLAN – The VLAN that the listed device is on
Figure 17: ARP Table
63
EtherWAN ED3575 Users Guide
Page 64

ARP Table using CLI Commands
For more information on CLI command usage see CLI Command Usage.
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
show arp-table
Usage Example:
switch_a>enable
switch_a#show arp-table
IP address HW type Flags HW address Mask VLAN
10.58.7.130 1 2 00:50:B6:65:2A:22 * 1
switch_a#q
switch_a#
EtherWAN ED3575 Users Guide
64
Page 65

Route Table
To navigate to the Route Table page:
1. Click on the + next to Diagnostics.
2. Click on Route Table.
The Route Table lists the routes to network destinations and metrics (distances) that are
associated with those routes. The Route Table contains information about the topology of
the network around it.
Figure 18: Route Table
Route Table Using CLI Commands
For more information on CLI command usage see CLI Command Usage.
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
show route-table
Usage Example:
switch_a>enable
switch_a#show route-table
Destination Gateway Genmask Flags Metric Ref Use VLAN
10.58.7.0 0.0.0.0 255.255.255.0 U 0 0 0 1
switch_a#q
switch_a#
EtherWAN ED3575 Users Guide
65
Page 66

Alarm Setting
This setting applies only to Switch models that have a hardware relay.
To navigate to the Alarm Setting page:
1. Click on the + next to Diagnostics.
2. Click on Alarm Setting.
The Alarm Setting page allows users to define Ethernet port Link-down and Power failure
alarms for triggering an alarm using the relay on the switch.
To configure an Ethernet port or Power input:
1. Select an Ethernet port or Power input from the drop-down box (see Figure 19).
Figure 19: Alarm Trigger
3. Select YES or NO from the drop-down box next to Trigger Enabled (see Figure 20).
4. Click Update Setting to save any changes made.
Figure 20: Trigger Enable
EtherWAN ED3575 Users Guide
66
Page 67

PORT
Configuration
To navigate to the Configuration page:
1. Click on the + next to Port.
2. Click on Configuration.
Port configuration contains such useful features as flow control, port speed, and duplex
settings. Some users will find these settings very valuable such as when the switch is
connecting to a latency-critical device such as a VOIP phone or IP camera or video
multiplexor. In these cases, and others, the ability to alter the port settings can make the
difference between a poorly responding device and one that functions without loss of data or
clarity.
The Configuration page shows (see Figure 21):
Port Number – fe(n) for 100mb ports and ge(n) for Gigabit ports
Link Status – Operational State of the Port’s Link (Read-Only)
Port Description – User-supplied Port Description
Admin Setting – Administratively Enable or Disable the Port.
Speed – Speed and Duplex Settings for Port.
Flow Control – State of Flow Control for the Port.
To provide a description to a port on the EtherWAN ED3575:
1. Click in the Description text box for the appropriate port.
2. Type in the description of the port.
3. Click on the Submit button.
To enable or disable a port on the EtherWAN ED3575:
1. Click on the drop-down box under Admin Setting and select either Link Up or Link
Down.
2. Click on the Submit button.
67
EtherWAN ED3575 Users Guide
Page 68

To set the Port Speed and/or Port Duplex Settings on the EtherWAN ED3575:
1. Click on the drop-down box under Speed and select the desired port speed / duplex
settings for that port. Please note, not all port types will have the same options. For
example, 100Mb fiber ports will typically be limited to a single option of 100M/FD
(100Mbps and Full Duplex) while running 1Gb UTP ports will have six options for
speed/duplex.
2. Click on the Submit button.
To enable or disable a port’s Flow Control settings on the EtherWAN ED3575:
1. Click on the drop-down box under Flow Control and select either Enable or Disable.
2. Click on the Submit button.
Figure 21: Port Configuration
68
EtherWAN ED3575 Users Guide
Page 69

Port Status
To navigate to the Port Status page:
1. Click on the + next to Port.
2. Click on Port Status.
This page is a read-only page that lists the settings described in the previous section. It is
useful if all the user intends to do is read the values of the port settings, not modify the port
settings. .The Port Status page shows (see Figure 22):
Port Number – fe(n) for 100mb ports and ge(n) for Gigabit ports
Link Status – Operational State of the Port’s Link.
Port Description – User-supplied Port Description
Admin Setting – Administratively State of the Port.
Speed – Speed and Duplex Settings for Port.
Flow Control – State of Flow Control for the Port.
Figure 22: Port Status
EtherWAN ED3575 Users Guide
69
Page 70

Rate Control
To navigate to the Rate Control page:
1. Click on the + next to Port.
2. Click on Rate Control.
The Rate Control page allows the user to set the maximum throughput on a port or ports on
both packets entering the port (from the connected device) or packets leaving the port.
The Ingress text box controls the rate of data traveling into the port while the Egress text
box controls the rate of data leaving the port.
Note: Entries will be rounded down to the nearest acceptable rate value. If the value
entered is below the lowest acceptable value then the lowest acceptable value will be
used.
The Rate Control page is shown below (see Figure 23):
To provide either an ingress or egress rate control for a port on the EtherWAN ED3575:
1. Click in the Ingress or Egress TextBox for the appropriate port.
2. Type in the ingress/egress rate for the port according to the values listed above.
3. Click on the Update Setting button.
Figure 23: Rate Control
EtherWAN ED3575 Users Guide
70
Page 71

RMON Statistics
To navigate to the RMON Statistics page:
1. Click on the + next to Port.
2. Click on RMON Statistics.
RMON Statistics gives a detailed listing of the types and quantity of packets that a particular
port has seen since the last reboot of the Switch (see Figure 24).
To view the RMON statistics for a particular port on the EtherWAN ED3575:
1. Click on the link to the port at the top of the RMON Statistics page.
To clear the RMON statistics for a particular port on the EtherWAN ED3575:
1. Click on the link to the port at the top of the RMON Statistics page.
2. Click on the Clear button at the bottom of the page.
3. The statistics for the port will update every ten seconds.
Pay particular attention to the values for CRC/Alignment errors and collisions. Nonzero
values for these fields can indicate that a port speed or duplex mismatch exists on the port.
Figure 24: RMON Page
EtherWAN ED3575 Users Guide
71
Page 72

Per Port VLAN Activities
To navigate to the Per Port VLAN Activities page:
1. Click on the + next to Port.
2. Click on Per Port VLAN Activities.
This is a read-only page that will allow the user to see what devices are connected to a
particular port and the VLAN associated with that device and port.
To clear the MAC addresses for a particular port on the EtherWAN ED3575 (see Figure 25):
1. Click on the link to the port at the top of the Per Port VLAN Activities page.
2. Click on the Clear MAC button at the bottom of the page.
3. The statistics for the port will update every ten seconds.
Figure 25: Port VLAN Activities
72
EtherWAN ED3575 Users Guide
Page 73

Port Security
This feature is not available on all models.
To navigate to the Port Security page:
1. Click on the + next to Port.
2. Click on Port Security.
The Port Security submenu allows the user to control access to the ports on the Switch
based on the source MAC addresses of the network devices.
To Add a MAC Address to a port:
1. Select the Enable or Disable from the Mode column for the port you want to
configure.
2. Enter the MAC Address of the device you want to connect to the port
3. Click Update Setting.
To remove a MAC Address from a port
1. Select the MAC Address from the Drop-down list next to the port that you want to
configure (see Figure 26)
2. Click on Update Setting.
Figure 26: Port Security
EtherWAN ED3575 Users Guide
73
Page 74

Port Configuration Examples Using CLI Commands
For more information on CLI command usage see CLI Command Usage.
Setting the Port Description
To provide a description of a port use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: description <description text>
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)#description A_Port_Description
switch_a(config)#q
switch_a(config)#q
switch_a#
Enable or Disable a Port
To administratively enable or disable a port use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax:
shutdown
no shutdown
Usage Example 1: Disabling a port:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)#shutdown
switch_a(config)#q
switch_a(config)#q
switch_a#
Usage Example 2: Enabling a port:
EtherWAN ED3575 Users Guide
74
Page 75

switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)#no shutdown
switch_a(config)#q
switch_a(config)#q
switch_a#
Setting the Port Speed
To set the port speed for a port use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: bandwidth <1-10000000000 bits> (usable units : k, m, g)
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)#bandwidth 100m
switch_a(config)#q
switch_a(config)#q
switch_a#
Setting Port Duplex
To set the duplex for a port use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: duplex <full | half | auto>
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)#duplex full
switch_a(config)#q
switch_a(config)#q
switch_a#
EtherWAN ED3575 Users Guide
75
Page 76

Enable or Disable Port FlowControl
To enable or disable flowcontrol for a port use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: flowcontrol on
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)#flowcontrol on
switch_a(config)#q
switch_a(config)#q
switch_a#
Display Port Status
To display the port status for a port use the CLI commands below:
CLI Command Mode: Privileged Exec Mode
CLI Command Syntax: show interface <ifname>
Usage Example:
switch_a>enable
switch_a#show interface fe1
Setting a Ports Rate Control
To set a ports rate control use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: rate-control <ingress | egress> value <value in kbps>
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)#rate-control ingress value 100000
switch_a(config)#q
switch_a(config)#q
switch_a#
76
EtherWAN ED3575 Users Guide
Page 77

Display a Ports RMON Statistics
To display a ports RMON statistics use the CLI commands below:
CLI Command Mode: Privileged Exec Mode
CLI Command Syntax: show interface statistics <interface name>
Usage Example:
switch_a>enable
switch_a#show interface statistics fe1
switch_a#
Display a Ports VLAN Activities
To display a port’s VLAN activities use the CLI commands below:
CLI Command Mode: Privileged Exec Mode
CLI Command Syntax: show bridge interface <interface name>
Usage Example:
switch_a>enable
switch_a#show bridge interface fe1
switch_a#
Setting MAC Port Security
To enable MAC port security use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: port-security enable
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)# port-security enable
switch_a(config)#q
switch_a(config)#q
switch_a#
77
EtherWAN ED3575 Users Guide
Page 78

To disable MAC port security use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: no port-security enable
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)# no port-security enable
switch_a(config)#q
switch_a(config)#q
switch_a#
To set the allowed MAC addresses use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: port-security allowed-address <value>
(in hex format. Ex. 00aa.0062.c609)
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)# port-security allowed-address 00aa.0062.c609
switch_a(config)#q
switch_a(config)#q
switch_a#
To delete an allowed MAC address use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: no port-security allowed-address <value>
(in hex format. Ex. 00aa.0062.c609)
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#int fe1
switch_a(config-if)# no port-security allowed-address 00aa.0062.c609
switch_a(config)#q
switch_a(config)#q
switch_a#
EtherWAN ED3575 Users Guide
78
Page 79

SWITCHING
Bridging
To learn MAC addresses, a Switch reads all packets that it detects on the LAN or on the
local VLAN, looking for MAC addresses of sending nodes. It places these addresses into its
Ethernet Switching table, along with the interface on which the traffic was received and the
time when the address was learned. When the Switch receives traffic on an interface, it
searches the Ethernet switching table for the MAC address of the destination. If the MAC
address is not found, the traffic is flooded out all of the other interfaces associated with the
VLAN. If traffic is received on an interface that is associated with VLAN 1 and there is no
entry in the Ethernet switching table for VLAN 1, then the traffic is flooded to all access and
trunk interfaces that are members of VLAN 1.
Flooding allows the Switch to learn about destinations that are not yet in its Ethernet
switching table. If a certain destination MAC address is not in the Ethernet switching table,
the Switch floods the traffic to all interfaces except the interface on which it was received.
When the destination node receives the flooded traffic, it sends an acknowledgment packet
back to the Switch, allowing the Switch to learn the MAC address of the node and to add the
address to its Ethernet switching table.
The Switch uses a process called aging to keep the Ethernet switching table current. For
each MAC address in the Ethernet switching table, the Switch records a timestamp of when
the information about the network node was learned. Each time the Switch detects traffic
from a MAC address that is in its Ethernet switching table, it updates the timestamp of that
MAC address. A timer on the Switch periodically checks the timestamp, and if it is older than
the value set for mac-table-aging-time, the Switch removes the node's MAC address from
the Ethernet switching table. This aging process ensures that the Switch tracks only active
MAC addresses on the network and that it is able to flush out from the Ethernet switching
table MAC addresses that are no longer available.
The user can configure:
How long MAC addresses remain in the Ethernet switching table
Add a MAC address permanently to the switching table
Prevent a MAC address from ever being registered in the switching table.
To navigate to the Bridging page:
1. Click on the + next to Switching.
2. Click on Bridging.
EtherWAN ED3575 Users Guide
79
Page 80

Aging Time
The Aging Time value is a global value and represents the time that a networked device’s
MAC address will live in the switch’s memory before being removed. The default value is
300s (5 minutes) (see Figure 27).
To update the Aging Time value on the EtherWAN ED3575:
1. Click in the Error Disable Recovery text box at the top of the Port Security DynamicMAC page.
2. Type in the desired value. Values can be from 0 to 65535 seconds. A value of 0
indicates that the port is not to return to normal operating condition until an
administrator resets the port or the Switch is restarted.
3. Click on the Update Setting button.
Threshold Level
The Threshold Level setting is a per port value. A traffic storm occurs when packets flood
the LAN, creating excessive traffic and degrading network performance. The traffic storm
control feature prevents LAN ports from being disrupted by a broadcast or multicast traffic
storm on physical interfaces. A Threshold is set to determine when the Switch will react to
Broadcasts and/or Multicasts.
To set the Threshold level per port:
1. Type in the desired value. Values can be from 0.1 to 100. This value is a percentage
of allowable broadcast traffic for this port. Once this percentage of traffic is
exceeded, all broadcast traffic beyond this percentage is dropped.
2. Click on the Update Setting button.
Storm Control Type
The Storm Control Enabled Type setting is a per port value. The Storm Control Enabled
Type allows users to determine the type of storm control to be used by the Switch.
To set the Storm Control Enabled Type:
1. Select the check box next to Broadcast and/or DFL-Multicast for the port that
needs to be changed
2. Click on the Update Setting button.
EtherWAN ED3575 Users Guide
80
Page 81

Port Isolation
The Port Isolation setting is a per port value. Port Isolation can be used to isolate a port or
ports so that only the isolated ports can communicate with one another (see Figure 27).
To update the Port Isolation value for a port on the EtherWAN ED3575:
1. Click on the Port Isolation drop-down box for the port to be isolated.
2. Select the value enable on the Port Isolation drop-down box.
3. Click on the Update Setting button.
4. Repeat as necessary for all ports that are to be isolated.
Block Multicast
The Block Multicast setting is a per port value. Block Multicast is a straight-forward
description of a feature that is used to block multicast traffic from accessing a port (see
Figure 27).
To update the Block Multicast value for a port on the EtherWAN ED3575:
1. Click on the Block Multicast drop-down box for the port to be isolated.
2. Select the value enable on the Block Multicast drop-down box.
3. Click on the Update Setting button.
4. Repeat as necessary for all ports that are to have multicast traffic blocked.
EtherWAN ED3575 Users Guide
81
Page 82

Figure 27: Bridging
EtherWAN ED3575 Users Guide
82
Page 83

Loopback Detect
Loopback detection is quite simply the ability of the Switch to detect when a port on the
Switch has been connected directly (or “looped back”) to another port on the Switch. This
configuration would likely lead to a broadcast storm on the Switch which would cause
network performance to suffer. Loopback detection offers the ability of the Switch to detect
this condition and shutdown the loop-backed port before any disruption of network traffic
occurs.
To navigate to the Loopback Detect page:
1. Click on the + next to Switching.
2. Click on Loopback Detect.
Loopback Detection (Global)
To globally enable the Loopback Detect feature of the EtherWAN ED3575 (see Figure 28):
1. Click on the Loopback Detect drop-down box.
2. Select Enable from the drop-down list.
3. Click on the Update Setting button.
Loopback Detect Action
To change the action that the Switch takes when a loopback condition is detected (see
Figure 28):
1. Choose an action from the Loopback Detect Action drop-down list. The available
options are None and Error Disable.
2. Click on the Update Setting button.
Loopback Detect Recovery Time
To change the length of time that the Loopback Detect Action will stay in effect (see Figure
28):
1. Enter a value in the text box next to Error Disable Recovery. Valid values range
from 0 to 65535 seconds.
2. Click on the Update Setting button.
EtherWAN ED3575 Users Guide
83
Page 84

Polling Interval
To change the polling interval of the Loopback Detect function (see Figure 28):
1. Enter a value in the text box next to Interval. Valid values range from 1 to 65535
seconds.
2. Click on the Update Setting button.
Figure 28: Loopback Detection
EtherWAN ED3575 Users Guide
84
Page 85

Loopback Detection (Per Port)
To enable Loopback Detection for a particular port or ports on the EtherWAN ED3575 (see
Figure 29):
1. Select the value Enable from the Mode drop-down list for a port on the Loopback
Detect page.
2. Click on the Update Setting button.
Figure 29:Loopback Detection (port)
EtherWAN ED3575 Users Guide
85
Page 86

Storm Detect
The Storm Detect feature allows the Switch to be configured to disable a port that is
receiving a large number of Broadcast and/or Multicast packets. The Switch can monitor for
packets and take action based on percentage of bandwidth utilization or number of packets
per second.
To navigate to the Storm Detect page:
1. Click on the + next to Switching.
2. Click on Storm Detect.
Enable/Disable Storm Detection
1. Enable or Disable Storm Detection by Clicking on the drop down box in the StormDetect Configuration box (see Figure 30).
2. Set the Storm Detect interval to a number between 2 and 65535 seconds. The
Default value is 10 seconds.
3. Set the Storm-Detect errdisable-recovery time to value between 0 and 65535
seconds. The Default is 0 (disabled). This value determines if the Switch should re-
enable the port after the specified value or leave the port disabled.
Figure 30: Storm Detect – Global
4. Set the By Utilization(%) for each port in the Storm-Detect Per Port Configuration
box (see Figure 31). The default is 0 (not limited). Setting this to a value between 1
and 100 will cause the port to be disabled when the defined percentage of bandwidth
is reached.
5. Set the type of packet to be monitored in the Drop-down box under By Broadcast /
Multicast+Broadcast Packets Per Second. Set the value to BC to monitor
Broadcast packets and BC-MC to monitor both Broadcast and Multicast packets.
EtherWAN ED3575 Users Guide
86
Page 87

6. Set the number of packets per second to a value between 0 and 1000000 packets.
The default is 0 (not limited).
Figure 31: Storm Detect – Per Port
EtherWAN ED3575 Users Guide
87
Page 88

Static MAC Entry
Occasionally, it may be useful to specify a MAC address on a particular port and VLAN
rather than adjusting the ageing time for the entire Switch. Alternatively, it is also possible
and even desirable to prevent a MAC address from ever being registered with a Switch.
These features are offered under the Static MAC Entry menu.
To navigate to the Static MAC Entry menu:
1. Click on the + next to Switching.
2. Click on Static MAC Entry.
Adding a Static MAC Address to a Port
To add a static MAC entry for a particular port (see Figure 32):
1. Enter the MAC address for end the corresponding port’s text box. The format of the
MAC address should be in the form aaaa:bbbb:cccc).
2. Select the VLAN that this MAC address is associated with from the VLAN ID drop-
down list for the port.
3. Click on the Submit button.
Figure 32: MAC Static Entry
EtherWAN ED3575 Users Guide
88
Page 89

Removing a Static MAC Address from a Port
To remove a static MAC entry for a particular port (see Figure 33):
1. For a particular port, select the MAC address to be deleted from the Delete MAC
Address drop down box.
2. Click on the Submit button.
Figure 33: Removing a Static MAC
Adding a MAC to the Static-MAC-Entry Discard Table
To add a MAC address to the Static-MAC-Entry Discard table (see Figure 34):
1. Enter a MAC address in the form “0000.1234.abdc” in the Add MAC Address text
box of the Static-MAC-Entry-Discard section.
2. Select the VLAN associated with the MAC address.
3. It should be noted that while static MAC address for forwarding is associated with the
Switch on a per-port basis. Static MAC discards are associated with the Switch for all
ports.
4. Click on the Submit button.
Figure 34: Adding a MAC – Static-MAC-Entry Table
EtherWAN ED3575 Users Guide
89
Page 90

Removing a MAC address from the Static-MAC-Entry Discard Table
To remove a MAC address from the Static-MAC-Entry Discard table (see Figure 35):
1. From the drop-down box underneath Delete MAC Address, select the MAC address
to be deleted.
2. Click on the Submit button.
Figure 35: Deleting a MAC – Static-MAC-Entry Table
EtherWAN ED3575 Users Guide
90
Page 91

Port Mirroring
Port mirroring allows network traffic from one port to be copied or mirrored to another port.
This is a very useful troubleshooting feature in that all data from one port is sent to another
port which is attached to a computer or other network device that is configured to capture
packets. This enables a network administrator or technician to see the traffic that is entering
or leaving a particular port without disrupting normal network operations on the port that is
being mirrored.
To navigate to the Port Mirroring menu:
1. Click on the + next to Switching.
2. Click on Port Mirroring.
To configure port mirroring for a port or ports on the EtherWAN ED3575 (see Figure 36):
1. Select the port or ports that traffic is to be mirrored from under the Mirror From
column.
2. Select the destination port under the Mirror To drop down box.
3. Select the type of traffic that should be mirrored from the Mirror Mode drop down
box. The available options are:
a. TX – transmit only
b. RX – Receive Only
c. TX/RX – Transmit and Receive.
4. Click on the Submit button.
EtherWAN ED3575 Users Guide
91
Page 92

Figure 36: Port Mirroring
To disable port mirroring for a port or ports on the EtherWAN ED3575 (see Figure 37):
1. Under the Current Settings section, the current port mirroring configuration should
be displayed.
2. Click on the Delete button.
.
Figure 37: Disabling Port Mirroring
EtherWAN ED3575 Users Guide
92
Page 93

Link State Tracking
Link-state tracking binds the link state of multiple interfaces. Link-state tracking provides
redundancy in the network when used with server network interface card (NIC) adapter
teaming or bonding. When the server network adapters are configured in a primary or
secondary relationship known as teaming and the link is lost on the primary interface,
connectivity transparently changes to the secondary interface.
To navigate to the Link State Tracking menu:
1. Click on the + next to Switching.
2. Click on Link State Tracking.
Enable/Disable Link State Tracking
To enable Link State Tracking for a particular group on the EtherWAN ED3575 (see Figure
38):
1. Under Group Setting, click the check box of the Link State groups that are to be
enabled (or disabled).
2. Click on Update Setting.
Figure 38: Link State Tracking
EtherWAN ED3575 Users Guide
93
Page 94

Port Settings
To configure individual ports for a Link State group on the EtherWAN ED3575 (see Figure
39):
1. Under Port Setting, select the Link State Group that the port will belong to from the
Group drop-down box
2. Select if the port is upstream or downstream from the Up/Down Stream)drop down
box.
3. Click on Update Setting.
Figure 39: Link State Tracking – Port Settings
EtherWAN ED3575 Users Guide
94
Page 95

Switch Configuration Examples Using CLI Commands
For more information on CLI command usage see CLI Command Usage.
Setting the Aging Time Value
To update the Aging Time value on the EtherWAN ED3575, use the CLI commands below:
CLI Command Mode: General Configuration Mode
CLI Command Syntax: bridge 1 ageing-time (time in ms)
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#bridge 1 ageing time 300
switch_a(config)#q
switch_a#
Enabling Port Isolation
To enable Port Isolation for a port on the EtherWAN ED3575, use the CLI commands
below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: port-isolation enable
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a#configure interface fe1
switch_a(config)#port-isolation enable
switch_a(config)#q
switch_a(config)#q
switch_a#
95
EtherWAN ED3575 Users Guide
Page 96

Enabling Block Multicast
To enable Block Multicast for a port on the EtherWAN ED3575, use the CLI commands
below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: switchport block multicast
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a#configure interface fe1
switch_a(config)#switchport block multicast
switch_a(config)#q
switch_a(config)#q
switch_a#
Setting Storm Control
To set the value for the Broadcast and or DLF-Multicast Storm Control value of a port on
the EtherWAN ED3575, use the CLI commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: stormcontrol <broadcast | dlf-multicast> <level>
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a#configure interface fe1
switch_a(config)#storm-control broadcast 20
switch_a(config)#q
switch_a(config)#q
switch_a#
96
EtherWAN ED3575 Users Guide
Page 97

Enabling Loopback Detect (Global)
To enable Loopback Detect on the EtherWAN ED3575, use the CLI commands below:
CLI Command Mode: General Configuration Mode
CLI Command Syntax: bridge 1 loopback-detect <enable | disable>
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#bridge 1 loopback-detect enable
switch_a(config)#q
switch_a#
Setting the Loopback Detect Action
To set the action for Loopback Detect on the EtherWAN ED3575, use the CLI commands
below:
CLI Command Mode: General Configuration Mode
CLI Command Syntax: bridge 1 loopback-detect action <err-disable | none>
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#bridge 1 loopback-detect action err-disable
switch_a(config)#q
switch_a#
Setting the Loopback Detect Recovery Time
To set the recovery time for Loopback Detect on the EtherWAN ED3575, use the CLI
commands below:
CLI Command Mode: General Configuration Mode
CLI Command Syntax: bridge 1 loopback-detect errdisable-recovery <0-65535>
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#bridge 1 loopback-detect errdisable-recovery 30
switch_a(config)#q
switch_a#
97
EtherWAN ED3575 Users Guide
Page 98

Setting the Loopback Detect Polling Interval
To set the polling interval for Loopback Detect on the EtherWAN ED3575, use the CLI
commands below:
CLI Command Mode: General Configuration Mode
CLI Command Syntax: bridge 1 loopback-detect interval <1-65535>
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)#bridge 1 loopback-detect interval 5
switch_a(config)#q
switch_a#
Enabling Loopback Detect (Port)
To enable Loopback Detection on a port on the EtherWAN ED3575, use the CLI
commands below:
CLI Command Mode: Interface Configuration Mode
CLI Command Syntax: loopback-detect enable
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a#interface fe1
switch_a(config)# loopback-detect enable
switch_a(config)#q
switch_a(config)#q
switch_a#
98
EtherWAN ED3575 Users Guide
Page 99

Configuring Storm-Detect
To Enable or Disable Storm-Detect use the CLI command Below:
CLI Command Mode: General Configuration Mode
CLI Command Syntax:
bridge 1 storm-detect errdisable
no bridge 1 storm-detect errdisable
Default: Disabled
Usage Example – Enabling storm detect:
switch_a>enable
switch_a#configure terminal
switch_a(config)# bridge 1 storm-detect errdisable
switch_a(config)#q
switch_a#
Usage Example – Disabling storm detect:
switch_a>enable
switch_a#configure terminal
switch_a(config)# no bridge 1 storm-detect errdisable
switch_a(config)#q
switch_a#
To set the storm-detect interval, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax: bridge 1 storm-detect interval <2-65535>
Default: 10
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)# bridge 1 storm-detect interval 10
switch_a(config)#q
switch_a#
99
EtherWAN ED3575 Users Guide
Page 100

To set the storm-detect recovery time, use the following CLI commands:
CLI Command Mode: General Configuration Mode
CLI Command Syntax: bridge 1 storm-detect errdisable-recovery <0-65535>
Default: 0 No errdisable recovery.
Usage Example:
switch_a>enable
switch_a#configure terminal
switch_a(config)# bridge 1 storm-detect errdisable-recovery 60
switch_a(config)#q
switch_a#
Storm Detect Packet Type
Enable this port’s storm detect by detect number of broadcast or broadcast plus
multicast packets per second. Unit is packets per second. Set to 0 to disable this feature.
To set the storm-detect packet type use the following CLI commands:
CLI Command Mode: Interface Mode
CLI Command Syntax: storm-detect (bc | mc-bc) pps <0-100000>
bc = broadcast only
mc-bc = count broadcast & multicast packets together.
Default: 0 (Disabled)
Usage Example 1 – Enabling Multicast + Broadcast:
switch_a>enable
switch_a#configure terminal
switch_a(config)# interface fe1
switch_a(config-if)#storm-detect mc-bc pps 50000
switch_a(config-if)#q
switch_a(config)#q
switch_a#
100
EtherWAN ED3575 Users Guide
 Loading...
Loading...