ESET MOBILE SECURITY - ANNEXE 706 SYMBIAN, MOBILE SECURITY Installation Manual

ESET Mobile Security
Symbian
Installation Manual and User Guide

ESET Mobile Security
Copyright ©2011 by ESET, spol. s.r.o.
ESET Mobile Security was developed by ESET, spol. s r.o.
For more information visit www.eset.com.
All rights reserved. No part of this documentation may be
reproduced, stored in a retrieval system or transmitted in any
form or by any means, electronic, mechanical, photocopying,
recording, scanning, or otherwise without permission in
writing from the author.
ESET, spol. s r.o. reserves the right to change any of the
described application software without prior notice.
Customer Care Worldwide: www.eset.eu/support
Customer Care North America: www.eset.com/support
REV. 3.2.2011
Contents
..............................................31.
Installation of ESET Mobile Security
....................................................................3Minimum system requirements1.1
....................................................................3Installation1.2
.......................................................................3Installation on your device1.2.1
.......................................................................3Installation using your computer1.2.2
....................................................................4Uninstallation1.3
..............................................52.
Product activation
....................................................................5Activation using login and password2.1
....................................................................5Activation using registration key2.2
..............................................63.
Update
....................................................................6Settings3.1
..............................................74.
On-access scanner
....................................................................7Settings4.1
..............................................85.
On-demand scanner
....................................................................8Running a whole device scan5.1
....................................................................8Scanning a folder5.2
....................................................................9General settings5.3
....................................................................9Extensions settings5.4
..............................................106.
Threat found
....................................................................10Quarantine6.1
..............................................117.
Anti-Theft
....................................................................11Settings7.1
..............................................138.
Firewall
....................................................................13Settings8.1
..............................................149.
Security audit
....................................................................14Settings9.1
..............................................1610.
Antispam
....................................................................16Settings10.1
....................................................................16Whitelist / Blacklist10.2
....................................................................17Locating spam messages10.3
....................................................................17Deleting spam messages10.4
..............................................1811.
Viewing logs and statistics
..............................................2012.
Troubleshooting and support
....................................................................20Troubleshooting12.1
.......................................................................20Unsuccessful installation12.1.1
.......................................................................20Connection to update server failed12.1.2
.......................................................................20Timeout downloading file12.1.3
....................................................................20Technical support12.2
3
1. Installation of ESET Mobile
Security
1.1 Minimum system requirements
To install ESET Mobile Security for Symbian, your
mobile device must meet following system
requirements:
Minimum system requirements
Operating system
S60 3rd Edition Feature Pack 1 or
2 (Nokia only)
S60 5th Edition (Nokia only)
Symbian 3 (Nokia only)
Available free
space
2 MB
1.2 Installation
Save all open documents and exit all running
applications before installing. You can install ESET
Mobile Security directly on your device or use your
computer to install it.
After successful installation, activate ESET Mobile
Security by following the steps in the Product
activation section.
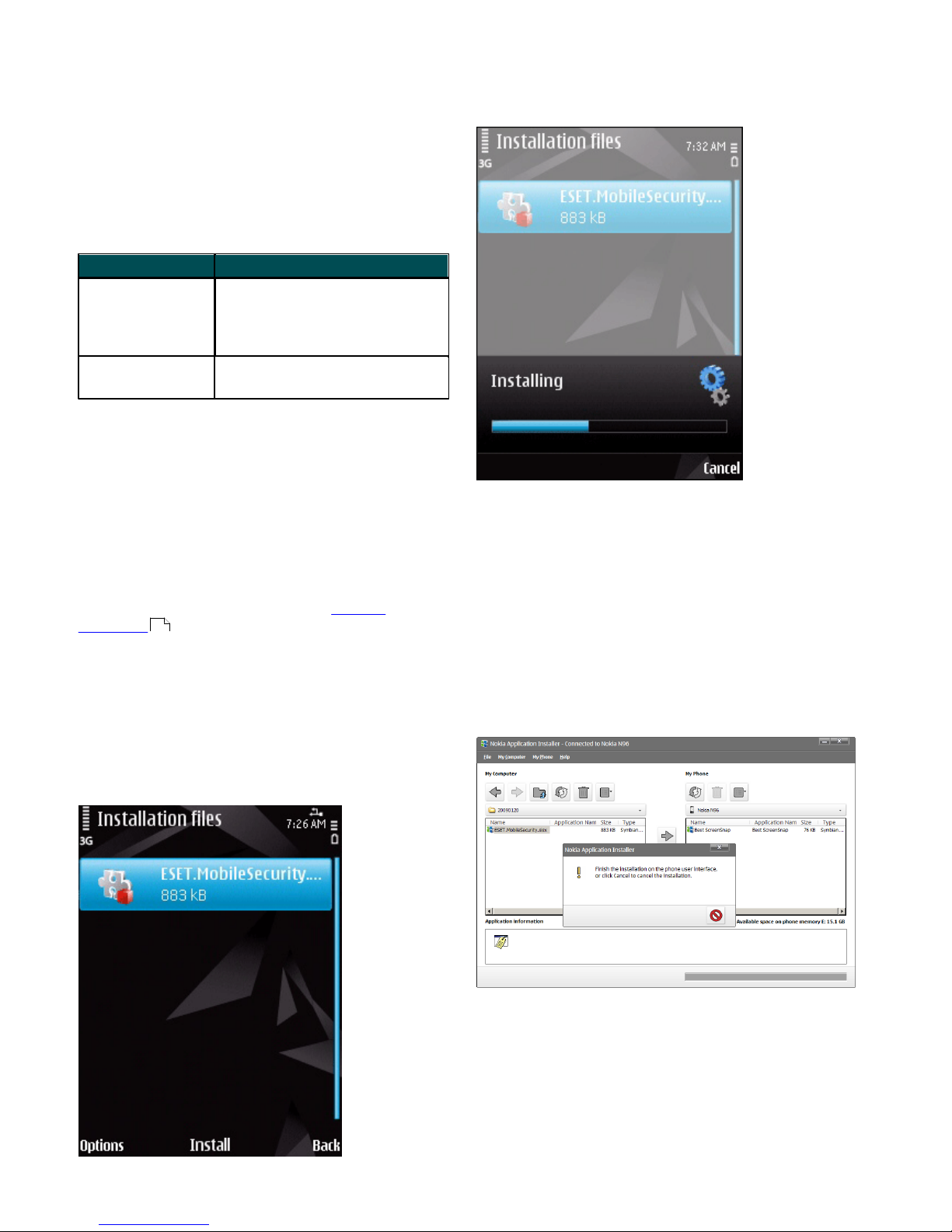
1.2.1 Installation on your device
To install ESET Mobile Security directly on your device,
download the .sis installation file onto your device by
Wi-Fi, Bluetooth, USB file transfer or email attachment.
Locate the file on your device. Tap the file to launch the
installer and then follow the prompts in the installation
wizard.
Installing ESET Mobile Security
NOTE: The Symbian user interface varies by device
model. The installation file may appear in a different
menu or folder on your device.
Installation progress
After installation, you can modify the program settings.
However, the default configuration provides the
maximum level of protection against malicious
programs.
1.2.2 Installation using your computer
To install ESET Mobile Security using your computer,
connect your mobile device to the computer via Nokia
PC Suite. After the device is recognized, run the
downloaded installation package (.sis file) and follow
the instructions in the installation wizard.
Launching the installer on your computer
Then follow the prompts on your mobile device.
5
4
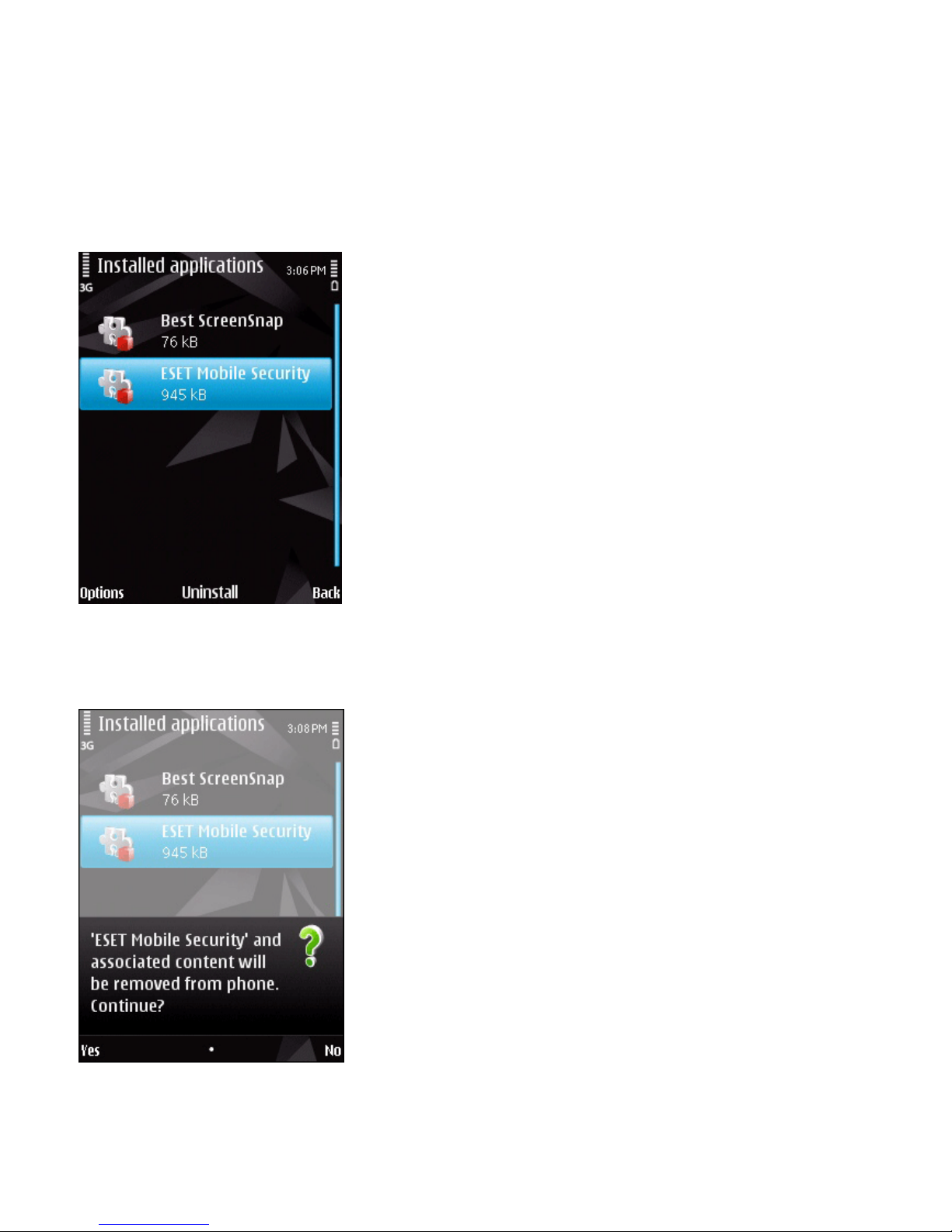
1.3 Uninstallation
To uninstall ESET Mobile Security from your mobile
device, tap My Content > Application manager >
Installed applications.
NOTE: The Symbian user interface varies by device
model. These options may be slightly different on your
device.
Removing ESET Mobile Security
Select ESET Mobile Security and tap Options >
Uninstall. Tap Yes when prompted to confirm the
uninstallation.
Removing ESET Mobile Security
5
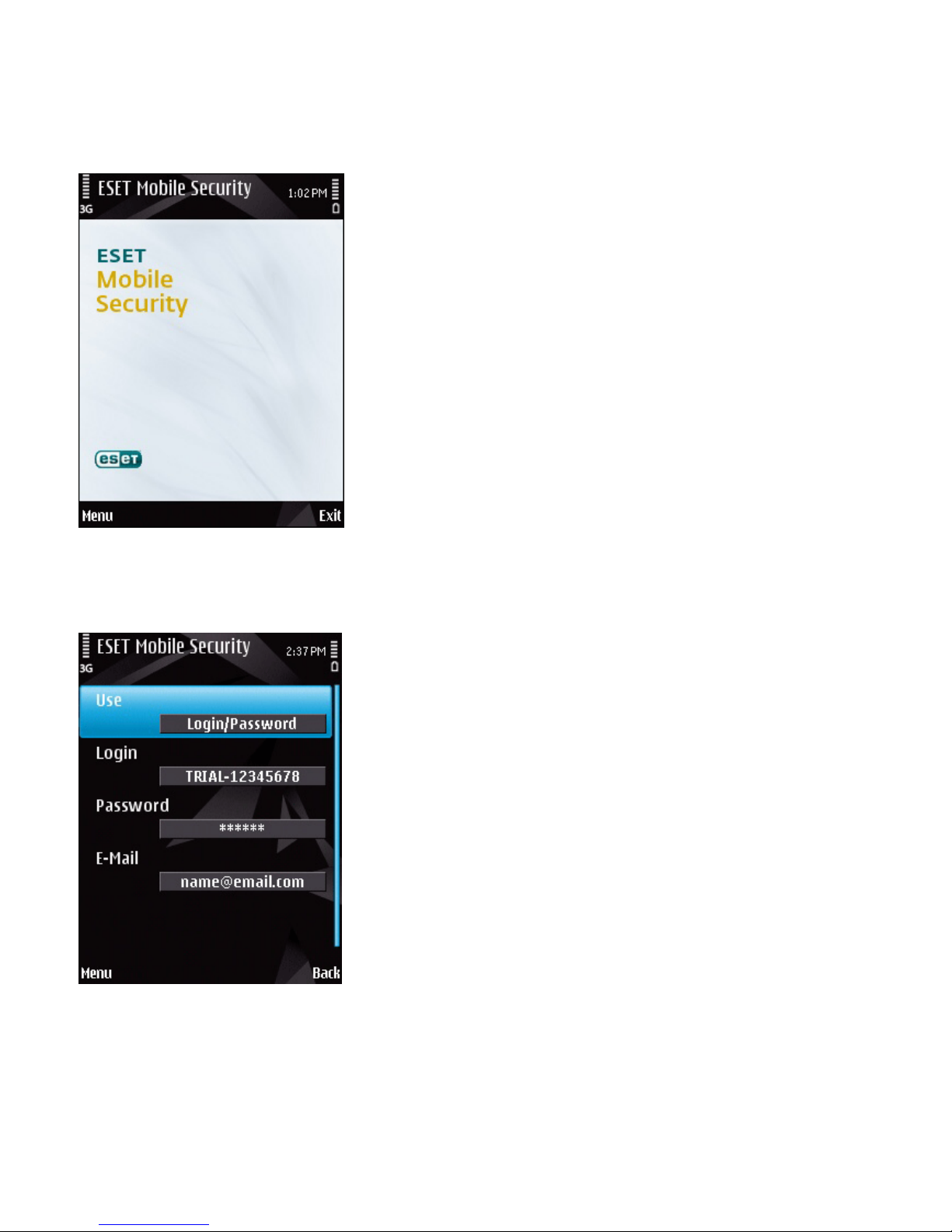
2. Product activation
The main ESET Mobile Security window (Menu >
Applications > ESET Mobile Security) is the starting
point for all instructions in this manual.
The main ESET Mobile Security window
After a successful installation, ESET Mobile Security
must be activated. If you are not prompted to activate
your product, tap Menu > Activate.
Program activation
There are two activation methods; the one that applies
to you will depend on the manner in which you
acquired your ESET Mobile Security product.
2.1 Activation using login and password
If you purchased your product from a distributor, you
received a login and password with your purchase.
Select the Login/Password option and enter the
information you received in the Login and Password
fields. Enter your current contact address in the Email
field. Tap Menu > Activate to complete the activation.
2.2 Activation using registration key
If you acquired ESET Mobile Security with a new device
(or as a boxed product), you received a Registration key
with your purchase. Select the Registration key
option, enter the information you received in the Key
field and your current contact address in the Email
field. Tap Menu > Activate to complete the activation.
Your new authentication data (Login and Password)
will automatically replace the Registration key and will
be sent to the email address you specified.
In both cases you will receive a confirmation email
about a successful product activation.
Each activation is valid for a fixed period of time. After
the activation expires, it will be necessary to renew the
program license (the program will notify you about this
in advance).
NOTE: During activation, the device must be connected
to the Internet. A small amount of data will be
downloaded. These transfers are charged according to
your service agreement with your mobile provider.

6
3. Update
By default, ESET Mobile Security is installed with an
update task to ensure that the program is updated
regularly. You can also perform updates manually.
After installation, we recommend you run the first
update manually. To do so, tap Menu > Action >
Update.
3.1 Settings
To configure update settings, tap Menu > Settings >
Update.
The Internet Update option enables or disables
automatic updates.
You can specify the Update Server from which updates
are downloaded (we recommend leaving the default
setting of updmobile.eset.com).
To set the time interval for the automatic updates, use
the Auto Update option.
In the Default APN Connection option, choose a type
of connection that will be used for downloading
updates.
Update settings
NOTE: To prevent unnecessary bandwidth usage, virus
signature database updates are issued as needed, when
a new threat is added. While virus signature database
updates are free with your active license, you may be
charged by your mobile service provider for data
transfers.
 Loading...
Loading...