Page 1

ESET File Security
Installation Manual and User Guide
Linux, BSD and Solaris
Page 2

ESET File Security
Copyright ©2011 by ESET, spol. s r. o.
ESET File Security was developed by ESET, spol. s r. o.
For more information visit www.es et.com.
All rights res erved. No part of this documentation ma y be reproduce d,
stored in a retri eva l syste m or transmi tte d in any form or by any
mea ns, ele ctronic, mecha nical , photocopying, recording, scanning, or
othe rwis e without permis sion in wri ting from the author.
ESET, spol . s r. o. res erve s the right to cha nge any of the describe d
applic ation software without prior notic e.
Customer Care Worldwide : www.es et.eu/support
Customer Care North America: www.e se t.com/support
REV. 2011-02 -08
Contents
..................................................................3
1. Introduction
.........................................................................................3
Mai n functionali ty1.1
.........................................................................................3
Key features of the sys tem1.2
..................................................................5
2. Terminology and abbreviations
..................................................................7
3. Installation
..................................................................8
4. Architecture Overview
..................................................................10
5. Integration with File System services
.........................................................................................10
On-demand scanner5.1
.........................................................................................10
On-access scanner powered by Dazuko5.2
................................................................................10Opera tion principle5.2.1
................................................................................11Installa tion and configuration5.2.2
................................................................................11Tips5.2.3
.........................................................................................11
On-access scanner us ing prel oad LIBC l ibra ry5.3
................................................................................12Opera tion principle5.3.1
................................................................................12Installa tion and configuration5.3.2
................................................................................12Tips5.3.3
..................................................................13
6. Important ESET File Security mechanisms
.........................................................................................13
Handle Object Pol i cy6.1
.........................................................................................13
User Speci fi c Configura tion6.2
.........................................................................................14
Sampl es Submis sion Sys tem6.3
.........................................................................................14
Web Interface6.4
................................................................................15Licens e ma nagement6.4.1
................................................................................16On-Access scanner (DAC) configuration example6.4.2
................................................................................16On-Dema nd scanner6.4.3
................................................................................17Statis tic s6.4.4
.........................................................................................17
Remote Admini s tration6.5
................................................................................18Remote Admini stration us age example6.5.1
.........................................................................................20
Logging6.6
..................................................................21
7. ESET Security system update
.........................................................................................21
ESETS update utility7.1
.........................................................................................21
ESETS update process description7.2
.........................................................................................21
ESETS mirror http daemon7.3
..................................................................22
8. Let us know
..................................................................23
9. Appendix A. PHP License
Page 3

3
1. Introduction
Dear user, you have acqui red ESET File Security - the premier security sys tem runni ng under the Linux, BSD and Solaris OS. As
you will soon find out, ESET's state-of-the-art scanning engine has unsurpas sed scanning speed and detection ra tes combined
with a very s mal l footprint that makes i t the ideal choi ce for any Linux, BSD and Solaris OS server.
1.1 Main functionality
On-demand scanner
The On-demand sca nner can be invoked by a privileged user (usuall y a system admi ni strator) through either the command
line interface or the web interface; or by the operating s ys tem's automatic schedul ing tool (e.g., cron). Thus, the term
O n -dem an d
refers to fil e system objects being scanned on user or s ys tem demand.
On-access scanner
The On-access s canner is i nvoked whenever a us er a nd/or operating s ys tem attempts to access fil e system objects . This a lso
cl arifies the use of the term
O n -a ccess
; becaus e a s can i s tri ggered by any attempt to access fil e system objects .
1.2 Key features of the system
Advanced engine algorithms
The ESET antivirus scanni ng engine algori thms provi de the highest detection rate and the fas test scanni ng times.
Multi-processing
ESET File Security is developed to run on s i ngle- as well as multi-process or units.
Advanced Heuristics
ESET File Security includes unique adva nced heuristics for Win32 worms, ba ckdoor i nfections and other forms of malware.
Built-In features
Built-in a rchivers unpack a rchived objects without the need for any external progra ms.
Speed and efficiency
To increase the speed and efficiency of the system, its archi tecture is ba sed on the runni ng da emon (resi dent program) where
al l sca nni ng requests a re sent.
Enhanced security
All executive daemons (except esets_dac) run under non-pri vileged user account to enhance security.
Selective configuration
The system supports selective confi guration ba sed on the user or cl i ent/server.
Multiple logging levels
Multipl e logging levels can be confi gured to get information about system acti vi ty and infiltrations .
Web interface
Configura tion, admi ni strati on a nd l i cense management are offered through an i ntui tive and user-friendly Web interface.
Remote administration
The system supports ESET Remote Administrati on for mana gement in la rge computer networks.
No external libraries
The ESET Fil e Securi ty instal lation does not require external li braries or programs except for LIBC.
User-specified notification
The system can be configured to notify speci fi c users i n the event of a detected infiltration or other important events.
Low system requirements
To run effici ently, ESET Fil e Security requires j ust 16MB of hard-disk space and 32MB of RAM. It runs smoothly under the 2.2.x,
2.4.x a nd 2.6.x Linux OS kernel vers ions as well as under 5.x, 6.x FreeBSD OS kernel versions.
Page 4

4
Performance and scalability
From lower-powered, smal l offi ce servers to enterprise-cla ss ISP servers wi th thousands of users, ESET Fil e Securi ty delivers
the performance and s cal ability you expect from a UNIX based s ol ution, in addition to the unequaled security of ESET products.
Page 5

5
2. Terminology and abbreviations
In this section we will review the terms a nd a bbreviations used i n thi s document. Note that a boldface font is reserved for
product component names and al s o for newly defined terms and abbrevi ations. Terms a nd a bbreviations defined i n this chapter
are expanded upon later in this document.
ESETS
ES ET Security
is a standard acronym for all s ecurity products developed by ESET, spol. s r. o. for Linux, BSD and Sol ari s
operating s ystems. It is a lso the name (or i ts part) of the software package containing the products.
RSR
Abbreviation for ‘RedHat/Novell(SuSE) Ready’. Note that we also support RedHat Ready and Novell(SuSE) Ready varia tions of
the product. The RSR package di ffers from the ‘standard’ Linux version in that it meets the FHS (File-system Hierarchy Standard
defined a s a part of Linux Standa rd Bas e) criteri a required by the RedHat Ready and Novell(SuSE) Ready certi fi ca te. This means
that the RSR package is installed as an add-on application - the primary i ns tal l ation directory i s ‘/opt/eset/esets’.
ESETS daemon
The mai n ESETS system control and s ca nni ng da emon:
esets_d a emo n
.
ESETS base directory
The directory where ESETS loada bl e modules contai ni ng the virus signature databa se are stored. The abbreviation
@ BA SE D IR @
wil l be used for future references to this directory. The
@ BA SE D IR @
value for the foll owing Opera ting Systems i s
lis ted below:
Linux: /var/lib/esets
Linux RSR: /var/opt/eset/esets/lib
FreeBSD: /var/lib/esets
NetBSD: /var/lib/esets
Solaris: /var/opt/esets/lib
ESETS configuration directory
The directory where al l files related to the ESET Fil e Security configuration are stored. The abbrevia tion
@ ETCDIR @
wil l be
used for future references to this di rectory. The
@ ETCDIR @
value for the foll owing Opera ting Systems i s listed below:
Linux: /etc/esets
Linux RSR: /etc/opt/eset/esets
FreeBSD: /usr/local/etc/esets
NetBSD: /usr/pkg/etc/esets
Solaris: /etc/opt/esets
ESETS configuration file
Mai n ESET Fil e Security configura tion file. The abs olute path of the file is as foll ows:
@ETCDIR@/esets.cfg
ESETS binary files directory
The directory where the relevant ESET Fil e Securi ty bi na ry fil es are stored. The abbrevia tion
@ BIND IR@
wil l be used for future
references to thi s directory. The
@ BIND IR@
value for the foll owing Opera ting Systems i s listed below:
Linux: /usr/bin
Linux RSR: /opt/eset/esets/bin
FreeBSD: /usr/local/bin
NetBSD: /usr/pkg/bin
Solaris: /opt/esets/bin
ESETS system binary files directory
The directory where the relevant ESET Fil e Securi ty s ystem binary fi les are stored. The abbrevi ation
@ SB IN D IR@
wil l be used
for future references to this directory. The
@ SB IN D IR@
value for the foll owing Opera ting Systems i s listed below:
Linux: /usr/sbin
Linux RSR: /opt/eset/esets/sbin
FreeBSD: /usr/local/sbin
NetBSD: /usr/pkg/sbin
Solaris: /opt/esets/sbin
Page 6

6
ESETS object files directory
The directory where the relevant ESET Fil e Securi ty obj ect files and l ibra ri es are stored. The abbrevia tion
@ LIBD IR @
wil l be
used for future references to this di rectory. The
@ LIBD IR @
value for the foll owing Opera ting Systems i s listed below:
Linux: /usr/lib/esets
Linux RSR: /opt/eset/esets/lib
FreeBSD: /usr/local/lib/esets
NetBSD: /usr/pkg/lib/esets
Solaris: /opt/esets/lib
Page 7

7
3. Installation
After purchasing ESET Fil e Security, you wil l receive your a uthoriza tion data (us ername, pass word and l i cense key). This data
is necessary for both identifyi ng you a s our cus tomer and al lowing you to downl oad upda tes for ESET File Security. The
username/pas s word data is a lso required for downloading the ini tial i nstal lation package from our web si te. ESET Fil e Securi ty
is dis tri buted as a bi nary fi l e:
esets.i386.ext.bin
In the binary fi l e shown above,
‘ex t’
is a Linux, BSD and Sol ari s OS di s tri bution dependent suffi x, i.e., ‘deb’ for Debian, ‘rpm’ for
RedHat and SuSE, ‘tgz’ for other Linux OS distri butions , ‘fbs5.tgz’ for FreeBSD 5.x, ‘fbs6.tgz’ for FreeBSD 6.x, ‘nbs4.tgz’ for NetBSD 4.
xx a nd ‘s ol10.pkg.gz‘ for Sol a ri s 10.
Note that the Linux RSR binary file format is:
esets-rsr.i386.rpm.bin
To install or upgrade the product, use the following command:
sh ./esets.i386.ext.bin
For the Linux RSR vari ation of the product, use the command:
sh ./esets-rsr.i386.rpm.bin
to displa y the product’s User License Acceptance Agreement. Once you have confirmed the Acceptance Agreement, the
installation packa ge is pl aced i nto the current working directory a nd relevant informati on regardi ng the package’s installati on,
un-instal lati on or upgrade is displa yed ons creen.
Once the package is installed, you can verify that the main ESETS servi ce i s running by using the foll owing command:
Linux OS:
ps -C esets_daemon
BSD OS:
ps -ax | grep esets_daemon
Solaris:
ps -A | grep esets_daemon
After pressing ENTER, you should see the foll owing (or si milar) message:
PID TTY TIME CMD
2226 ? 00:00:00 esets_daemon
2229 ? 00:00:00 esets_daemon
At least two ESETS daemon process es a re running in the background. The firs t PID represents the process and threads manager
of the sys tem. The other represents the ESETS sca nni ng process.
Page 8

8
4. Architecture Overview
Once ESET Fil e Securi ty i s successfully installed, you should become familia r wi th its a rchitecture.
Figure 4-1. Structure of ESET File Security.
The structure of ESET File Security is s hown i n Figure 4-1. The sys tem is comprised of the following parts:
CORE
The Core of ESET File Security i s the ESETS daemon (esets_daemon). The daemon uses ESETS API libra ry l i besets.so and ESETS
loadi ng modules em00X_xx.dat to provi de base system tasks such as scanning, maintenance of the agent daemon processes,
maintenance of the sampl es submis sion system, logging, notification, etc. Please refer to the
esets_d a emo n (8 )
man pa ge for
details.
AGENTS
The purpos e of ESETS agent modul es i s to integrate ESETS with the Linux, BSD and Solaris Server environment.
UTILITIES
The utility modules provide si mple and effective management of the system. They are respons i bl e for relevant sys tem tas ks
such as license mana gement, quarantine mana gement, sys tem setup and update.
CONFIGURATION
Proper confi guration i s the most important aspect of a s mooth-running security system - the remai nder of this chapter i s
dedicated to explai ni ng all related components. A thorough understandi ng of the
esets.cfg
file is als o hi ghl y recommended, as
this fi l e contains informati on essential to the confi guration of ESET File Security.
After the product is s uccess ful l y i ns tal l ed, al l its confi gura tion components are stored in the ESETS configuration directory.
The directory consi s ts of the foll owi ng fi les:
@ETCDIR@/esets.cfg
This i s the most important configuration file, as i t controls a l l maj or as pects of the product‘s functional i ty. The esets.cfg file is
made up of s everal s ections, each of which contai ns vari ous parameters. The file contai ns one global and several “agent“
sections , with al l section names enclosed i n s qua re brackets. Parameters i n the global s ection are used to define configuration
options for the ESETS daemon as well as default val ues for the ESETS sca nni ng engine confi guration. Parameters i n agent secti ons
are used to define confi gura tion options of modul es used to i ntercept various data fl ow types i n the computer and/or its
neighborhood, and prepare it for scanning. Note that in additi on to the various parameters us ed for system configura tion, there
are also rul es governing the organiza tion of the fil e. For detai l ed information on the most effective way to organi ze this fi l e,
Page 9

9
please refer to the
esets.cfg (5 )
and
esets_d a emo n (8 )
man pa ges, as well as relevant agents‘ man pages.
@ETCDIR@/certs
This di rectory is used to store the certificates used by the ESETS web interface for authentication. Please see the
esets_ww w i(8 )
man pa ge for detai l s.
@ETCDIR@/license
This di rectory is used to store the product(s) li cense key(s) you have acquired from your vendor. Note that the ESETS daemon
wil l check onl y this directory for a val i d l i cense key, unless the
‘license_dir’
parameter in the ESETS configuration file i s redefined.
@ETCDIR@/scripts/license_warning_script
If enabled by the ESETS confi guration fi le parameter
‘license_wa rn _en a bled’
, this script will be executed 30 days (once per da y)
before product license expi ra tion, sending a n emai l notification about the expiration status to the system administrator.
@ETCDIR@/scripts/daemon_notification_script
If enabled by the ESETS confi guration fi le parameter
‘ex ec_s crip t’
, this script is executed in the event of a detected infi l tration
by the antivirus s ystem. It is used to send email notifi cation about the event to the system administrator.
Page 10

10
5. Integration with File System services
This chapter describes the On-demand and On-access scanner configuration whi ch wil l provide the most effective protection
from vi rus a nd worm fil e system infecti ons . ESET File Securi ty’s s canning power is deri ved from the On-demand scanner
command
‘es ets_sca n’
and the On-access s canner command
‘es ets_d a c’
. The Linux version of ESET Fil e Security offers a n
additi ona l On-a ccess scanner techni que which uses the preloa ded library module
libes ets_ p a c.so
. All of these commands a re
described in the foll owi ng sections.
W arnin g !
Novell Stora ge Services (NSS) break common unix securi ty pri nciples the scanner relies on when limiting pri vi l eges.
This resul ts in no threat detection on NSS mounted volumes. If you have such mounted volume, set the
‘es ets_u ser’
parameter to
‘ro o t’
in ESETS configuration file and restart ESETS daemon.
5.1 On-demand scanner
The On-demand sca nner can be invoked by a privileged user (usuall y a system admi ni strator) through the command line
interface or web interface, or by the operating sys tem’s automatic scheduling tool (e.g., cron). Thus, the term
O n -dem an d
refers to
file system objects whi ch are sca nned on user or system demand.
The On-demand sca nner does not requi re speci al confi guration i n order to run. After the ESETS package has been properly
installed and a valid license has been moved to the license keys di rectory (@ETCDIR@/li cense), the On-demand s ca nner can be
run i mmediately us i ng the command l i ne interface or the Scheduler tool. To run the On-demand scanner from the command l i ne,
use the following s yntax:
@SBINDIR@/esets_scan [option(s)] FILES
where FILES is a lis t of di rectories and/or fil es to be scanned.
Multipl e command line options are avai l able usi ng ESETS On-demand s canner. To s ee the full li s t of options, please see the
esets_sca n(8 )
man pa ge.
5.2 On-access scanner powered by Dazuko
The On-access s canner is i nvoked by user(s) access and/or operating s ys tem access to fil e system objects. This a lso explai ns
the term
O n -a ccess
; the scanner is triggered on any a ttempt to access a selected fil e system object.
The techni que used by ESETS On-access s canner is powered by the Dazuko (da-tzu-ko) kernel modul e and is bas ed on the
interception of kernel cal l s . The Dazuko project is open s ource, which means that its s ource code is freely distri buted. This
al l ows users to compile the kernel modul e for their own custom kernels. Note that the Dazuko kernel modul e is not a part of any
ESETS product and must be compil ed and instal led into the kernel pri or to usi ng the On-access command
esets_d a c
. On the other
hand the Dazuko techni que makes On-a ccess sca nni ng i ndependent from the fil e system type used. It is a lso suitabl e for
scanning of file sys tem objects via Network File Sys tem (NFS), Nettalk and Samba.
Import a nt :
Before we provide detai led information related to On-access s canner confi guration and us e, it s houl d be noted
that the scanner has been pri marily developed and tested to protect external ly mounted file systems. In ca se of multiple fil e
systems that are not externall y mounted, you will need to excl ude them from fil e access control i n order to prevent system hang
ups. An example of a typi ca l di rectory to exclude is the
‘/dev ’
directory and any directori es used by ESETS.
5.2.1 Operation principle
The On-access s canner
esets_d a c
(ESETS Dazuko-powered file Access Control ler) is a resi dent program which provi des
conti nuous moni tori ng a nd control over the file sys tem. Every fil e system object is scanned based on cus tomizable fil e access
event types. The foll owi ng event types are supported by the current versi on:
Open events
To activa te this file access type set the value of the
‘ev ent_m ask ’
parameter to open in the
[d a c]
section of the esets.cfg file.
This will enabl e the ON_OPEN bit of the Dazuko access mask.
Close events
To activa te this file access type set the value of the
‘ev ent_m ask ’
parameter to close in the
[d a c]
section of the esets.cfg file.
This will enabl e the ON_OPEN bit of the Dazuko access mask. This will enabl e the ON_CLOSE and ON_CLOSE_MODIFIED bits of the
Dazuko access mask.
NOTE: Some OS kernel versions do not support the interception of ON_CLOSE events. In these cas es, close events will not be
monitored by
esets_d a c
.
Exec events
To activa te this file access type set the value of the
‘ev ent_m ask ’
parameter to exec i n the
[d a c]
section of the esets.cfg file. This
Page 11

11
wil l enable the ON_EXEC bit of the Dazuko access mas k.
The On-access s canner ensures that all opened, closed and executed files are first scanned by the esets_daemon for viruses.
Depending on the sca n resul ts, access to specific files i s denied or allowed.
5.2.2 Installation and configuration
The Dazuko kernel module must be compiled and install ed within the running kernel before initializi ng
esets_d a c
. For detai l s
on how to compil e and install Dazuko, pl ease see:
http://www.dazuko.org
Once Dazuko i s installed, review and edit the
[g loba l]
and
[d a c]
sections of the ESETS configuration file (esets.cfg). Note that
proper functioni ng of the On-a ccess scanner i s dependent upon confi gurati on of the
‘a gen t_en ab le d ’
option within the
[d a c]
section of this fi le. Additional l y, you mus t define the fil e system objects (i .e. directories and fi les) that are to be monitored by the
On-access scanner. This can be accomplished by defini ng the parameters of the
‘ctl_in cl ’
and
‘ctl_ex cl’
options, which are al so
located within the
[d a c]
section. After making cha nges to the esets.cfg fil e, you can force the newly created confi guration to be re-
read by reloading the ESETS daemon.
5.2.3 Tips
To ensure that the Dazuko modul e loads prior to initia l ization of the
esets_d a c
daemon, follow these steps:
Place a copy of the Dazuko module in either of the foll owi ng di rectories reserved for kernel modul es:
/lib/modules
or
/modules
Use the kernel utilities ‘depmod’ and ‘modprobe’ (For BSD OS, use ‘kldconfig’ and ‘kl dl oad’) to handle dependenci es and
successful initializa tion of the newly added Dazuko module.
In the esets_daemon ini tial i zation scri pt ‘/etc/ini t.d/esets_daemon’, insert the following l i ne before the daemon initializa tion
statement:
/sbin/modprobe dazuko
For BSD OS’s the line
/sbin/kldconfig dazuko
must be inserted into the ‘/usr/local/etc/rc.d/esets_daemon.sh’ scri pt.
W arnin g !
It i s extremely important that these steps are executed in the exact order gi ven. If the kernel module is not loca ted
withi n the kernel modules directory it will not properl y l oa d, caus ing system hang-ups.
5.3 On-access scanner using preload LIBC library
In the previous s ections we descri bed the integration of the On-access s canner powered by Dazuko with Linux/BSD fi l e system
services. If, however, the use of Dazuko i s not feas ible, for exampl e for s ys tem adminis trators who mai ntain criti ca l systems
where:
the source code and/or confi guration fi les related to the runni ng kernel are not avai lable,
the kernel is more monoli thic than modular,
the Dazuko modul e simpl y does not support the given OS.
In any of these cases, the On-access s canni ng techni que based on the preload LIBC li brary shoul d be us ed. See the foll owing
topics in this s ection for detailed i nformation. Please note that this section is relevant only for Linux OS users a nd contai ns
information regarding the operation, ins tall ation and confi gurati on of the On-access s ca nner usi ng the preload library
‘lib esets_p a c.so’
.
Page 12

12
5.3.1 Operation principle
The On-access s canner
libes ets_ p a c.so
(ESETS Preloa d l ibra ry bas ed file Access Control l er) i s a sha red objects library whi ch is
activa ted at system start-up. This l i brary is used for LIBC cal l s by fi le sys tem servers such a s FTP server, Samba server etc. Every
file system object is sca nned based on cus tomiza bl e file access event types. The followi ng event types are supported by the
current versi on:
Open events
This fi l e access type is activa ted if the word
‘o p en ’
is present in the
‘ev ent_m ask ’
parameter in the esest.cfg fil e (
[p a c]
section).
Close events
This fi l e access type is activa ted if the word
‘close’
is present in the
‘ev ent_m ask ’
parameter in the esets.cfg fil e (
[p a c]
section).
In this ca se, all file descriptor and FILE stream close functions of the LIBC are intercepted.
Exec events
This fi l e access type is activa ted if the word
‘ex ec’
is present in the
‘ev ent_m ask ’
parameter in the esets.cfg (
[p a c]
section). In
this cas e, al l exec functions of the LIBC are intercepted.
All opened, cl osed and executed fil es a re sca nned by the ESETS daemon for vi ruses. Based on the resul t of s uch scans, access
to given fi l es i s denied or allowed.
5.3.2 Installation and configuration
The
libes ets_ p a c.so
library modul e is i ns tall ed us ing a standard i ns tal l ation mechani s m of the preloaded l ibra ri es. One has
just to define the environment varia bl e
‘LD _PRELO A D’
with the absol ute path to the
libes ets_ p a c.so
library. For more information,
please refer to the
ld .so (8 )
man pa ge.
NOTE: It is important that the
‘LD _PRELO A D‘
environment vari a bl e is defi ned onl y for the network server daemon processes
(ftp, Samba, etc.) that will be under control of the On-access scanner. Generall y, preloa di ng LIBC cal l s for al l operating sys tem
process es i s not recommended, as this can dramatically sl ow the performance of the sys tem or even cause the sys tem to hang. In
this s ense, the ‘/etc/ld.so.preload’ file shoul d not be used, nor should the ‘LD_PRELOAD‘ environment variabl e be exported
global l y. Both would override all relevant LIBC cal ls, which could lead to system hang-up duri ng i ni tial i zation.
To ensure that only relevant file access cal ls withi n a given fil e system are intercepted, executable statements can be
overri dden us i ng the following l i ne:
LD_PRELOAD=/usr/lib/libesets_pac.so COMMAND COMMAND-ARGUMENTS
where ‘COMMAND COMMAND-ARGUMENTS’ is the original executable statement.
Review and edit the
[g loba l]
and
[p a c]
sections of the ESETS configuration file (esets.cfg). In order for the On-access s canner to
functi on correctly, you must define the file system objects (i .e. directories a nd fi l es) that are required to be under control of the
preload library. This can be achieved by defining the parameters of the
‘ctl_in cl ’
and
‘ctl_ex cl’
options in the
[p a c]
section of the
ESETS configurati on fi l e. After maki ng changes to the esets.cfg file, you can force the newly created confi guration to be re-read by
reloadi ng the ESETS daemon.
5.3.3 Tips
In order to activate the On-access scanner immedia tely a fter file system start-up, the
‘LD _PRELO A D’
environment vari a bl e must
be defined within the appropri ate network file server initia l ization s cript.
Ex a mp le:
Let’s assume we want to have the On-access scanner to monitor al l fi l e sys tem access events immediately after
starting the Samba server. Within the Samba daemon ini tiali zation scri pt (/etc/init.d/smb), we would replace the statement
daemon /usr/sbin/smbd $SMBDOPTIONS
with the following l i ne:
LD_PRELOAD=/usr/lib/libesets_pac.so daemon /usr/sbin/smbd $SMBDOPTIONS
In this way, selected file sys tem objects controlled by Samba wil l be scanned at system start-up.
Page 13
13
6. Important ESET File Security mechanisms
6.1 Handle Object Policy
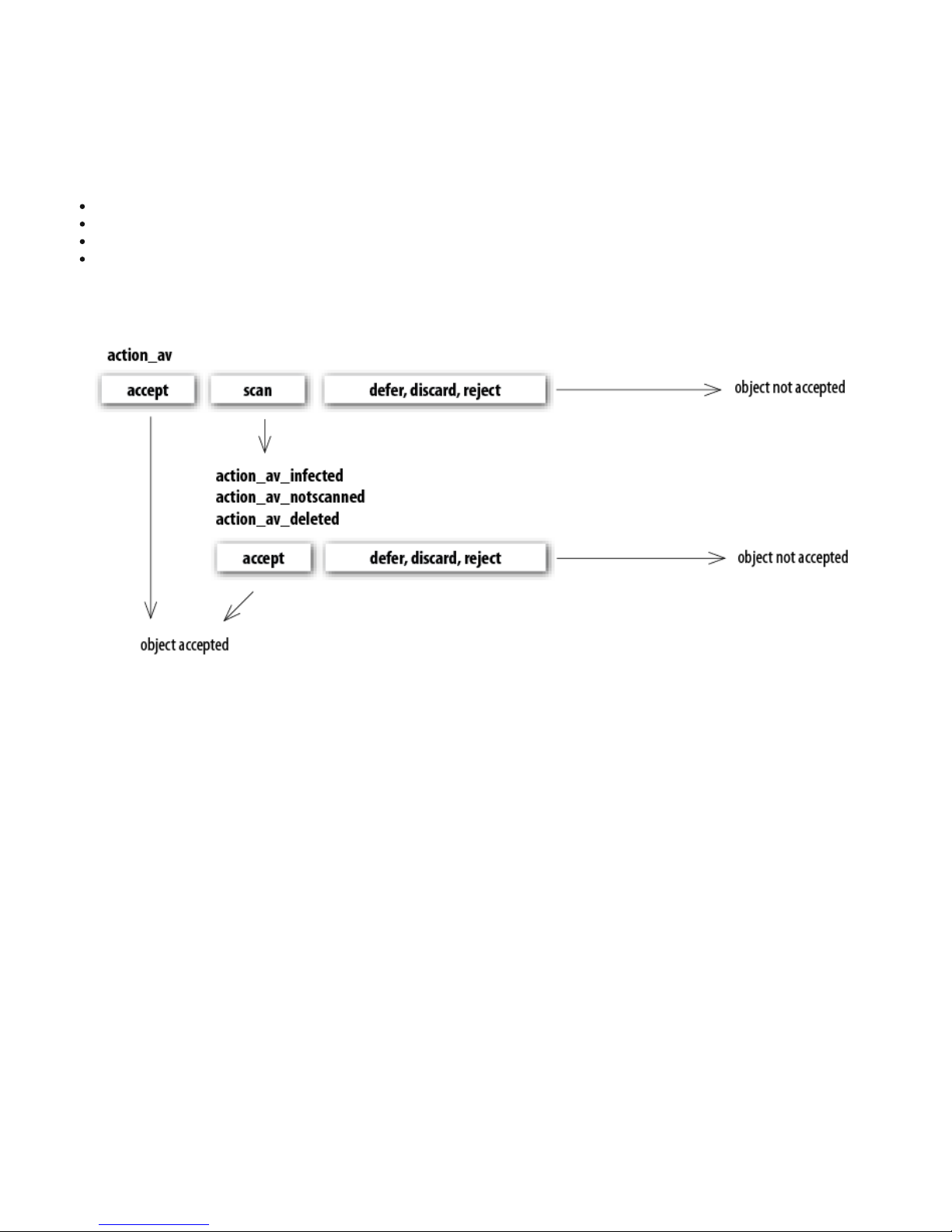
The Handl e Object Policy (s ee figure 6-1) mechanism provides fi l tering of scanned obj ects bas ed on their status. This
functi onality is ba sed on the foll owi ng configuration options:
action_av
action_av_infected
action_av_notscanned
action_av_deleted
For detai l ed information on these options, please refer to the
esets.cfg (5 )
man pa ge.
Figure 6-1. Scheme of Handle Object Policy mechanism.
Every object processed is fi rs t handl ed according to the configuration of the
‘a ctio n _a v ‘
option. If thi s option is set to
‘a ccep t’
(or
‘d efer’, ‘d isca rd ’, ‘reject’
) the object i s accepted (or deferred, di scarded, rejected). If the option i s set to
‘sca n’
the object i s
scanned for vi rus infil tra tions, and i f the
‘a v_clea n_m o d e
’ option is s et to
‘yes
’, the object is also cleaned. In additi on, the
confi gurati on options
‘a ctio n _a v _in fected
’,
‘a ctio n _a v _n o ts ca nn ed
’ and
‘a ctio n _a v _d eleted
’ are taken into a ccount to further
eval uate handl ing of the object. If an
‘a ccep t’
action has been taken as a resul t of these three acti on options , the object is
accepted. Otherwise, the object is bl ocked.
6.2 User Specific Configuration
The purpos e of the User Speci fic Configuration mecha ni sm is to provide a hi gher degree of cus tomiza tion and functiona lity. It
al l ows the sytem administra tor to define ESETS antivi rus s canner parameters ba sed on the user who i s accessing file system
objects.
A detai l ed descri ption of this functi ona lity can be found i n the
esets.cfg (5 )
man pa ge; in thi s section we wil l provide only a
short exampl e of a user-specifi c configurati on.
In this example, the goal is to use the
esets_d a c
module to control the ON_OPEN and ON_EXEC access events for an external
disc mounted under the /home directory. The modul e can be confi gured in the
[d a c]
section of the ESETS configura tion file. See
below:
[dac]
agent_enabled = yes
event_mask = "open"
ctl_incl = "/home"
action_av = "scan"
To specify scan settings for an individual user, the
‘u ser_co nfig ’
parameter must specify the speci al confi guration fi l ename
where the individual s canning rules wi ll be stored. In the example shown here, the speci al confi gurati on fi l e is cal l ed
‘es ets_d a c_s p ec.cf g ’
and is l ocated within the ESETS configura tion directory (This di rectory is bas ed on your opera ting system.
Please see Terminology and abbreviati ons page).
Page 14

14
[dac]
agent_enabled = yes
event_mask = "open"
ctl_incl = "/home"
action_av = "scan"
user_config = "esets_dac_spec.cfg"
Once the
‘u ser_co nfig ’
file para meter is specifi ed within the
[d a c]
section, the
‘es ets_d a c_s p ec.cf g ’
file must be created in the
ESETS configurati on directory. Finall y, add the desi red scanni ng rules.
[username]
action_av = "reject"
At the top of the special s ection, enter the username to which the individual rules will be appl i ed. This configuration wil l
al l ow all other users attempting to access the fil e-sys tem to be process ed normally. i.e., all file system objects accessed by other
users wi ll be scanned for i nfi ltrations , except for the user
‘u sern am e’
, whose access wil l be rejected (blocked).
6.3 Samples Submission System
The Samples submiss i on s ys tem is an intelli gent
Th rea tSen se.Ne t
technology that collects infected objects which have been
detected by advanced heuristics a nd deli vers them to the samples submis s ion system server. All virus sampl es collected by the
sa mple submission system will be processed by the ESET virus laboratory and if necessa ry, a dded to the ESET virus signature
database.
NOTE: According to our li cense agreement, by enabli ng s ample submiss i on s ys tem you are agreeing to allow the computer
and/or pl atform on which the esets_daemon is i nstal l ed to col l ect data (which may incl ude pers onal information about you
and/or the user of the computer) and sa mples of newly detected viruses or other threats and send them to our vi rus la b. This
feature is turned off by default. All i nformation collected will be us ed onl y to anal yze new threats and wil l not be used for any
other purpose.
In order to activate the Samples Submi ssion System, the sa mples s ubmissi on s ys tem cache must be initi alized. This can be
achieved by enabl ing the
‘sa m ples_en a bled ’
option in the
[g loba l]
section of the ESETS configura tion file. To al l ow for the actual
deli very of sa mples to the ESET virus laboratory servers, the para meter
‘sa m ples_s en d_p erio d ’
must also be speci fi ed in the same
section.
In addi tion, users can choose to provide the ESET virus l a boratory team with supplementary informati on usi ng the
‘sa m ples_p rov id er_m a il’
and/or
‘sa m ples_p rov id er_co un try’
confi gurati on options . The informati on collected using these options
wil l assi st in provi di ng the ESET team with an overvi ew about a gi ven infiltration whi ch may be spreading over the Internet.
For more i nformation on the Sampl es Submis sion Sys tem, refer to the
esets_d a emo n (8 )
man pa ge.
6.4 Web Interface
The Web Interface al l ows user-friendly configurati on, adminis tra tion and license management of ESET Security sys tems. This
module is a separate agent and must be expli citly enabled. To quickly confi gure the
W eb In terfa ce
, set the foll owing options in
the ESETS configura tion file and restart the ESETS daemon:
[wwwi]
agent_enabled = yes
listen_addr = address
listen_port = port
username = name
password = pass
Replace the text in italics with your own va l ues and direct your browser to
‘h ttps:// a dd ress :p o rt’
(note the https). Login with
‘u sern am e/ p ass w o rd ’
. Basic us age ins tructions can be found on the help page and techni ca l details about
esets_ww w i
can be
found on the
esets_ww w i(1 )
man pa ge.
The web interface allows you to remotely a ccess the ESETS daemon and deploy it easil y. Thi s powerful utili ty makes it easy to
read and write confi gurati on va lues.
Page 15

15
Figure 6-1. ESET Security for Linux - Home screen.
The web interface window of ESET Fil e Securi ty i s divided into two mai n s ections. The primary wi ndow, that serves to displ ay
the contents of the selected menu option and the main menu. This hori zontal bar on the top lets you na vi gate between the
following main options:
Home
- provides basic system and ESET product information
L icen ses
- is a l i cense management utility, see the following chapter for mode details
Con fig ur a tion
- you can change the ESET File Security system confi gura tion here
Con t r o l
- al l ows you to run simple tas ks and view globa l statistics about obj ects processed by esets_daemon
Help
- provides detai led usage instructions for the ESET Fil e Securi ty web interface
L o g ou t
- use to end your current session
6.4.1 License management
You can upl oad a new li cense using the Web interface, as shown in Figure 6-2.
If you want to di splay li censes in the console, use the foll owing command:
/usr/sbin/esets_lic --list
If you want to import new li cense files, use the following command:
/usr/sbin/esets_lic --import *.lic
Figure 6-2. ESET Licenses.
You can enable the li cense notification option in the
Glo b a l
section options. If enabl ed, this functionali ty will notify you 30
days prior to your license expiration.
Page 16

16
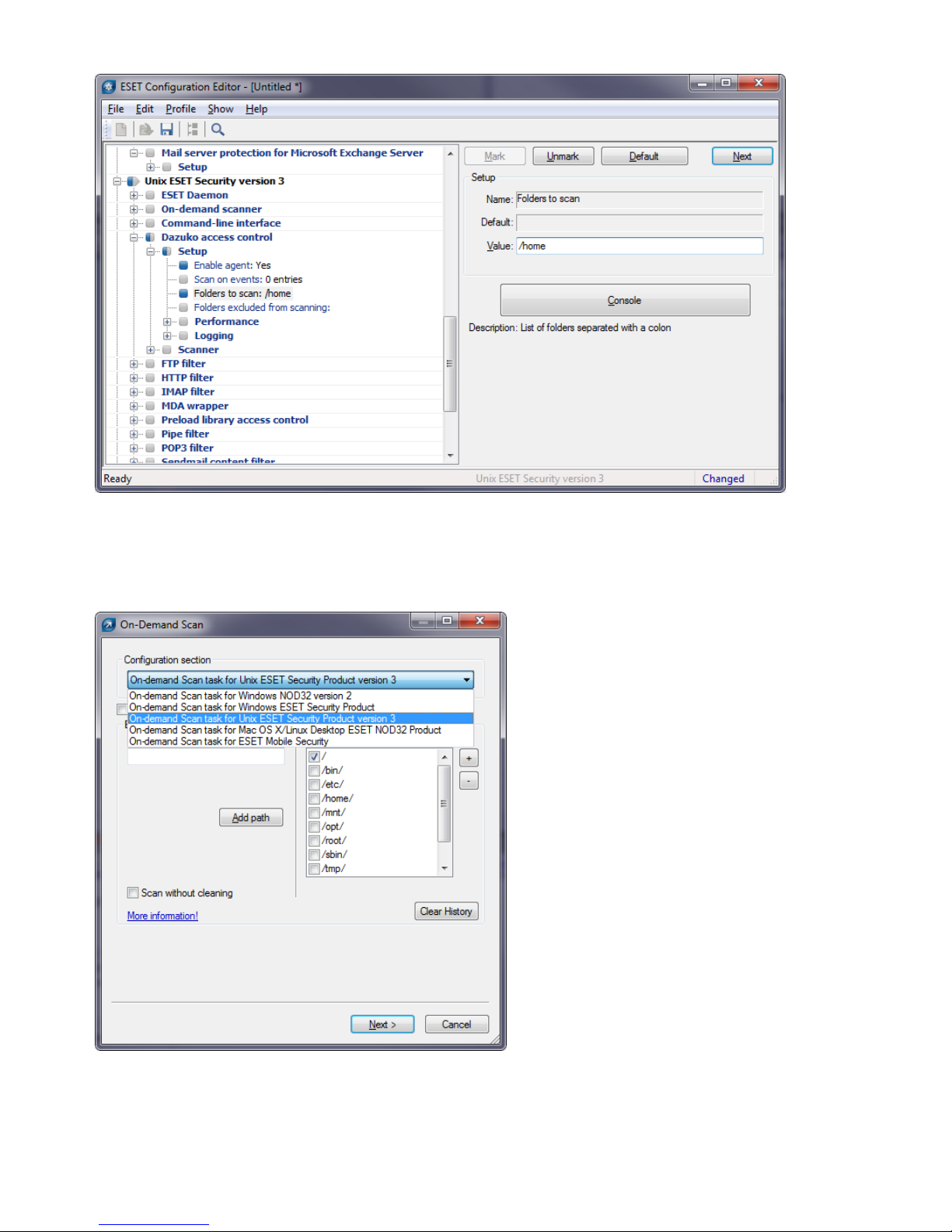
6.4.2 On-Access scanner (DAC) configuration example
There are two ways you can to confi gure ESETS. In our example we wil l demonstrate how to use either of them to setup the DAC
module, descri bed i n section 5.2. You can choos e the option that best suits you.
Usi ng the ESETS confi gurati on fi l e:
[dac]
agent_enabled = yes
event_mask = "open"
ctl_incl = "/home"
action_av_deleted = "reject"
action_av = "scan"
action_av_infected = "reject"
Usi ng the web interface:
Figure 6-3. ESETS - Configuration > On-Access scanner.
When changi ng s ettings in the web interface, al ways remember to save your confi guration by the cl i ck
Sa ve cha n g es
. To appl y
your new changes cl ick the
A p p ly ch a ng es
button in the
Con fig ur a tion
sections pa nel.
6.4.3 On-Demand scanner
This s ection comprises an example on how to run the On-Demand scanner to scan for viruses:
Navi gate to
Con t r o l > O n-Dem a nd Sca n
Enter the path to the directory you want to sca n
Execute the Command-l ine scanner by cli cking the
Sca n
button
Page 17

17
Figure 6-4. ESETS - Control > On-Demand scanner.
ESET Command-l i ne scanner will a utomatically run in the background. To see the scanni ng progress, click the
V iew
link. A new
browser window wil l open.
6.4.4 Statistics
You can vi ew statistics for all of active ESETS agents here.
St atistics
summary refreshes every 10 seconds .
Figure 6-5. ESETS - Control > Statistics.
6.5 Remote Administration
ESETS supports ESET Remote Admini strati on for file security management in l arge computer networks. The ESETS Remote
Admini strati on Cl i ent is pa rt of the mai n ESETS daemon and performs the following functions:
Communicates with ERA Server and provi des you with system information, configuration, protection statuses and several
other features
All ows cl ient configura tions to be viewed/modifi ed using the ESET Configuration Editor and i mpl emented with the help of
confi gurati on tasks
Can perform
Upd a te N o w
tasks
Performs On-demand scans as requested, and submits the resul ting back to ERA Server
Sca n Log
Adds l ogs of notable scans performed by the ESETS daemon to
Th r ea t Log
Sends a l l non-debug mess ages to
Ev ent L og
These functi onalities are not supported:
Firewall Log
Remote Instal l
Page 18

18
Figure 6-6. ERA Console tabs.
For more i nformation, please read the ESET Remote Adminis tra tor manual . This manua l is located on our web si te at the
following l i nk:
http://www.eset.com/documentation
6.5.1 Remote Administration usage example
Before commencing any remote administration process ens ure your system fulfil l s the three following prerequisites:
Runni ng ERA Server
Runni ng ERA Console
Enabl e RA Cli ent in the ESETS daemon. Ensure that firewall settings do not block tra ffic to ERA Server or vi ce versa.
To setup the bas i cs , specify the address of your ERA Server in the
‘ra cl_server_a dd r’
parameter first. If you are using a pas sword
to access the ERA Consol e pass word, you must edit the value of the
‘ra cl_pa ssw o rd’
parameter accordingly. Cha nge the val ue of
the ‘racl _interval ’ parameter to adj us t the frequency of connections to ERA Server (in minutes).
You can either use the web interface (see al so previ ous chapter) to apply the new configuration, or you can adj us t these
parameters i n the
[g loba l]
section of the ESETS configura tion file as follows:
racl_server_addr = "yourServerAddress"
racl_server_port = 2222
racl_password = "yourPassword"
racl_interval = 1
NOTE: All a ppl i ca bl e ESET Remote Adminis tra tion Client vari ables are listed on the
esets_d a emo n (8 )
man pa ge.
The ESETS daemon confi gurati on will be reloa ded and RACL will connect to ERA Server. You will be abl e to see a newly
connected cl i ent in your ERA Console. Press the F5 button (or
M en u > V iew > Refr esh
) to manua lly refresh the li st of connected
cl ients.
Figure 6-7. ERA Console.
By using ERA Console you ca n create a configura tion tas k to ESETS daemon from ERA Consol e:
Right click the connected
Client N a me
Navi gate to
N ew Ta sk > C o n fig ur a tion T a sk > Cr ea te...
Expand
Un ix ES ET Secu r ity tree
For a n example of a configuration task by the DAC agent, see below:
Page 19
19
Figure 6-8. ERA Configuration Editor.
The
N ew Ta sk
context menu contai ns On-demand s ca nni ng options (enabled/dis abled cleani ng).
You can select the desi red product, that you wis h to s et the task for, i n the
O n -Dem a nd Sca n
pop-up window in the
Con fig ur a tion S ectio n
drop-down menu. Make sure that you select the
O n -d em an d Sca n ta sk fo r Unix E SET S ecu r it y P ro d u ct
option
(i.e. the product that is i ns tal l ed on your target works tation).
Figure 6-9. ERA On-demand scan.
Page 20

20
6.6 Logging
ESETS provides system daemon logging via s ys log.
Syslog
is a standard for l oggi ng program mess ages and ca n be us ed to log
system events s uch as network and securi ty events.
Messages refer to a fa cil i ty:
auth, authpriv, daemon, cron, ftp, lpr, kern, mail, ..., local0, ..., local7
Messages are assigned a priority/level by the sender of the message:
Error, Warning, Summall, Summ, Partall, Part, Info, Debug
This s ection descri bes how to confi gure and read the logging output of sysl og. The
‘syslog _fa cility’
option (default value
‘d a em o n ’
) defines the sys l og faci l ity used for logging. To modify s ys log settings edit the ESETS configura tion file or use the web
interface. Modify the val ue of the
‘syslog _cla ss ’
parameter to change the logging clas s. We recommend you modify these settings
only if you a re famil i ar with sys l og. For an example of sys l og configuration see below:
syslog_facility = "daemon"
syslog_class = "error:warning:summall"
The name and l ocati on of the log file depend on your syslog installation and configuration (e.g. rsyslog, sys log-ng, etc.).
Standa rd fil enames for s ys l og output fi les are for example
‘syslog ’, 'd aem o n.lo g '
, etc. To follow sysl og activity, run one of the
following commands from the cons ol e:
tail -f /var/log/syslog
tail -100 /var/log/syslog | less
cat /var/log/syslog | grep esets | less
If you enabl e ESET Remote Administra tion, ERA log entries ol der than given days by the option
‘ra cl_lo g s_lifetim e’
wil l be
automatical l y deleted.
Page 21

21
7. ESET Security system update
7.1 ESETS update utility
To maintai n the effectiveness of ESET File Security, the virus signature databa se must be kept up to date. The esets_update
util i ty has been developed for this purpos e. See the
esets_u p d a te( 8 )
man pa ge for detai l s. To la unch an update, the confi gura tion
options
‘a v_up d a te_usern a me’
and
‘a v_up d a te_pa ssw ord ’
must be defined in the
[g loba l]
section of the ESETS configura tion file.
In the event that your server accesses the Internet via HTTP proxy, the addi tional confi gura tion options
‘p ro xy _a d dr’, ‘p ro xy _po rt’
must be defined. If access to the HTTP proxy requires a us erna me and pa ssword, the
‘p ro xy _usern a me’
and
‘p ro xy _pa ssw ord ’
options must als o be defined in this s ection. To initiate an upda te, enter the foll owing command:
@SBINDIR@/esets_upda te
To provi de the highest possible securi ty for the end us er, the ESET team continuousl y collects vi rus defini tions from all over
the world - new patterns a re added to the virus s i gnature database in very s hort intervals. For this reason, we recommend that
updates be initiated on a regular ba sis. To s peci fy the update frequency, the
‘a v_up d a te_perio d ’
option must be defined in the
[g loba l]
section of the ESETS configura tion file. The ESETS daemon must be up a nd runni ng i n order to successfully update the
virus signature databas e.
7.2 ESETS update process description
The update process consi s ts of two stages: First, the precompiled update modules are downloaded from the ESET server. If the
option
‘a v_mirror_en a bled ’
is s et to ‘yes’ in the
[g loba l]
section of the ESETS configura tion file, copies (or mirror) of these update
modules are created in the fol lowing directory:
@BASEDIR@/mirror
If desired, the Mirror directory pa th ca n be redefined usi ng the
‘a v_mirror_d ir’
option in the
[g loba l]
section of the ESETS
confi gurati on fi l e. The newly created Mirror ca n then serve as a fully functi onal update server and can be used to create lower
(chi l d) Mi rror s ervers . See section 7.3 for detai ls.
The option
‘a v_mirror_p cu’
al l ows you to downl oad Program Component Update (PCU) modules for Windows-bas ed ESET
security products. These modul es can be mirrored from the ESET server.
NOTE: Once you set your username, pas sword a nd l i cens e for ESET Fil e Security to downl oad PCU's for ESET NOD32 Antivirus /
ESET Smart Security, please contact our Technica l Support and request a cha nge, that wil l enable your ESET Fil e Securi ty to
download PCU's for our Wi ndows-based products.
The second stage of the update process i s the compilati on of modules loadabl e by the ESET File Security scanner from those
stored in the loca l mirror. Typicall y, the following ESETS loadi ng modules are created: loader modul e (em000.dat), scanner
module (em001.da t), virus signature databa se module (em002.dat), archi ves support modul e (em003.dat), advanced heuri s tics
module (em004.da t), etc. The modules are created in the following directory:
@BASEDIR@
This i s the directory where the ESETS daemon loads modul es from and thus can be redefined usi ng the
‘b a se_d ir’
option in the
[g loba l]
section of the ESETS configura tion file.
7.3 ESETS mirror http daemon
ESETS mirror http daemon is installed automatically with ESET Fil e Securi ty. The http mirror daemon starts i f the option
‘a v_mirror_h ttpd _en a bled’
in the
[g loba l]
section of the ESETS configura tion file is set to
‘yes ’
and the Mirror i s enabled.
Options
‘a v_mirror_h ttpd _port’
and
‘a v_mirror_h ttpd _a d dr’
define the port (default 2221) and address (default: all l ocal tcp
address es) where the http server l i stens.
The option
‘a v_mirror_h ttpd _a u th_m o d e’
al l ows access authentication (default: none) to be changed to basic. The options
‘a v_mirror_h ttpd _usern a me’
and
‘a v_mirror_h ttpd _pa ssw o rd’
al l ow an admini s trator to define the login and pas sword used to
access the Mirror.
Page 22

22
8. Let us know
Dear user, we hope this Gui de has provi ded you wi th a thorough understandi ng of the requi rements for ESET File Security
installation, configuration a nd maintenance. However, our goal i s to continua lly improve the qual i ty and effectiveness of our
documentation. If you feel that any s ections in this Gui de are uncl ear or i ncomplete, please let us know by contacting Customer
Care:
http://www.eset.com/support
or us e directly the support form:
http://www.eset.eu/support/form
We are dedicated to provi de the highest level of support and look forward to helping you s houl d you experience any probl ems
concerning this product.
Page 23

23
9. Appendix A. PHP License
The PHP License, versi on 3.01 Copyri ght (c) 1999 - 2006 The PHP Group. All rights reserved.
Redis tri bution and us e in source and bi na ry forms, with or without modification, is permitted provided that the foll owing
conditi ons are met:
1. Redis tri butions of source code must retain the above copyri ght notice, this list of condi tions and the foll owing di scl aimer.
2. Redis tri butions in bi nary form must reproduce the above copyri ght notice, this l i st of conditi ons and the followi ng di s cl aimer
in the documentation and/or other materi als provi ded with the distribution.
3. The name “PHP” must not be used to endorse or promote products derived from this s oftware without pri or written
permis s ion. For written permis sion, please contact group@php.net.
4. Products derived from this s oftware may not be called “PHP”, nor may “PHP” appear i n their name, without prior wri tten
permis s ion from group@php.net. You may i ndi cate that your software works in conjunction with PHP by s aying “Foo for PHP”
instead of calling it “PHP Foo” or “phpfoo”
5. The PHP Group may publ i sh revised and/or new versi ons of the license from time to time. Each version will be given a
disti ngui shing version number. Once covered code has been published under a particular version of the li cense, you may
al ways continue to use it under the terms of that versi on. You may al s o choose to use such covered code under the terms of
any subsequent version of the license publ i shed by the PHP Group. No one other than the PHP Group has the right to modify
the terms appl ica bl e to covered code created under thi s License.
6. Redis tri butions of any form whatsoever must retain the followi ng acknowledgment: “This product incl udes PHP software,
freely a vaila bl e from <http://www.php.net/software/>”.
THIS SOFTWARE IS PROVIDED BY THE PHP DEVELOPMENT TEAM "AS IS" AND ANY EXPRESSED OR IMPLIED WARRANTIES,
INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE
DISCLAIMED. IN NO EVENT SHALL THE PHP DEVELOPMENT TEAM OR ITS CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT,
INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE
GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF
LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT
OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBI LITY OF SUCH DAMAGE.
 Loading...
Loading...