Page 1

Quick Start Guide
for Mac
Page 2

ESETCybersecurity provides state-of-the-art protection for your computer against
malicious code. Based on the ThreatSense® scanning engine first introduced in the
award-winning NOD32 antivirus system, ESETCybersecurity continues to deliver
unprecedented protection against zero-day threats, without the need for constant
signature updates to recognize the threats. This manual will guide you step-by-step
through the quick setup and configuration of the product.
Antispyware: Protects you from hidden
backdoors, downloaders, exploits, crackers,
hijackers, password stealers, key loggers
andproxies.
Antivirus: Proactively detects and disables
more known and even unknown new
malware threats than any other security
product.
Page 3
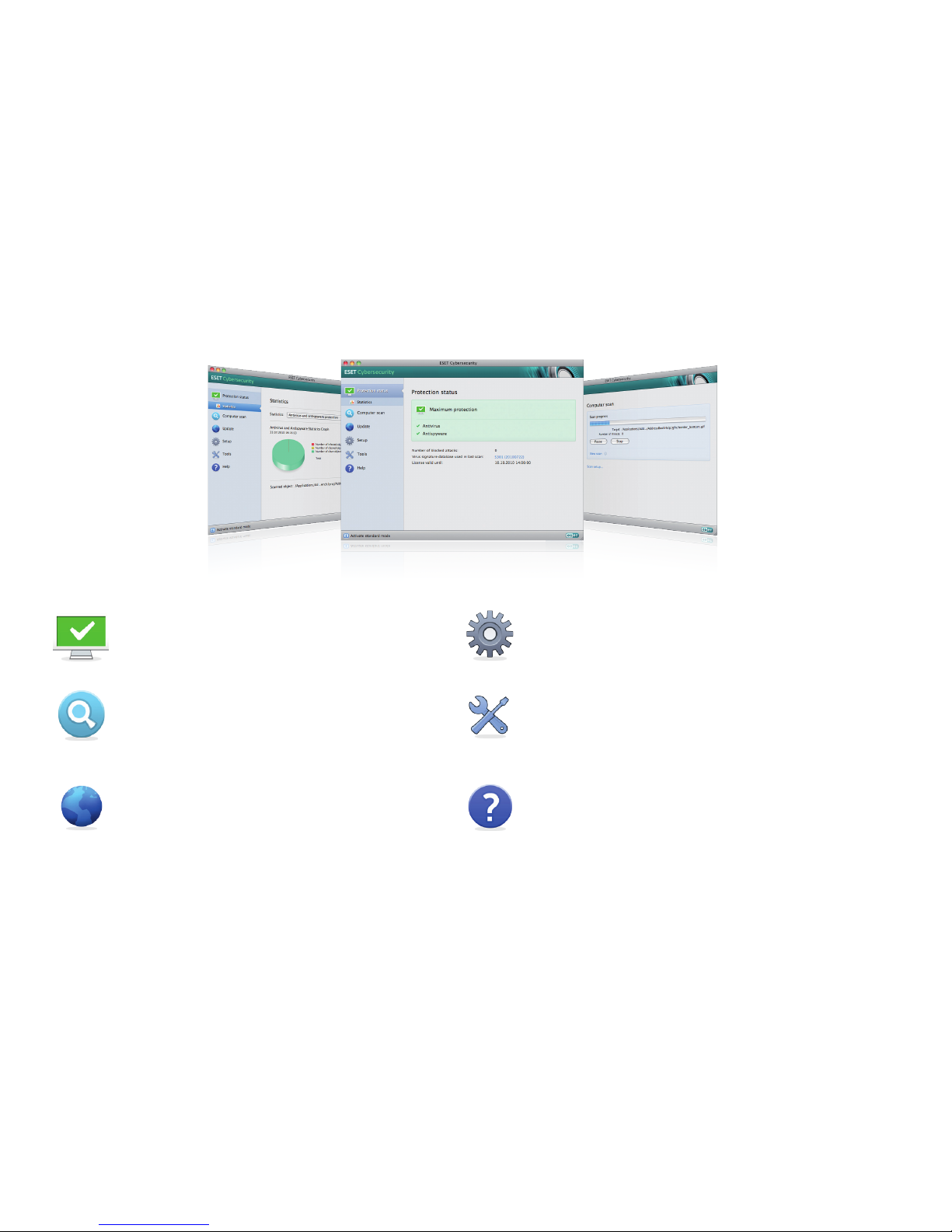
Protection status informs you about the current
protection level of your computer and security.
A computer scan is an important part of each
antivirus solution. It is used to perform ascan of the
files and folders onyour computer’s disk(s).
The Update section contains important information
about the program updates. It is vitally important
for the program toupdate regularly to provide the
maximum level of protection against thelatest
threats.
Setup options allow you to adjust the protection levels
ofyour computer.
The Tools section, available in extended mode, allows
you to enter advanced features: log files, quarantine and
scheduler.
Comprehensive help and support for ESETCybersecurity.
You can also contact ESET technical support directly
from here.
Page 4
Before you begin the installation
process, please close all open programs
on your computer. ESETCybersecurity
contains components that may
conflict with other antivirus programs
that may already be installed on your
computer. ESET strongly recommends
that you remove any other programs
to prevent potential problems. You
can install ESETCybersecurity from an
installation CD or from afile available
on the ESET website.
To launch the installer wizard, do one
of the following:
• If you are instal
ling from the
installation CD, insert the CD into the
CDROM drive and the menu screen
will appear. Doubleclick on the ESET
Cybersecurity Installation icon to
launch the installer.
Installation
• If you are installing from adown
loaded file, doubleclick the file you
downloaded to launch the installer.
•
Additional features including
manuals, training and uninstalling
can be accessed by doubleclicking on
the appropriate icon from the menu
screen
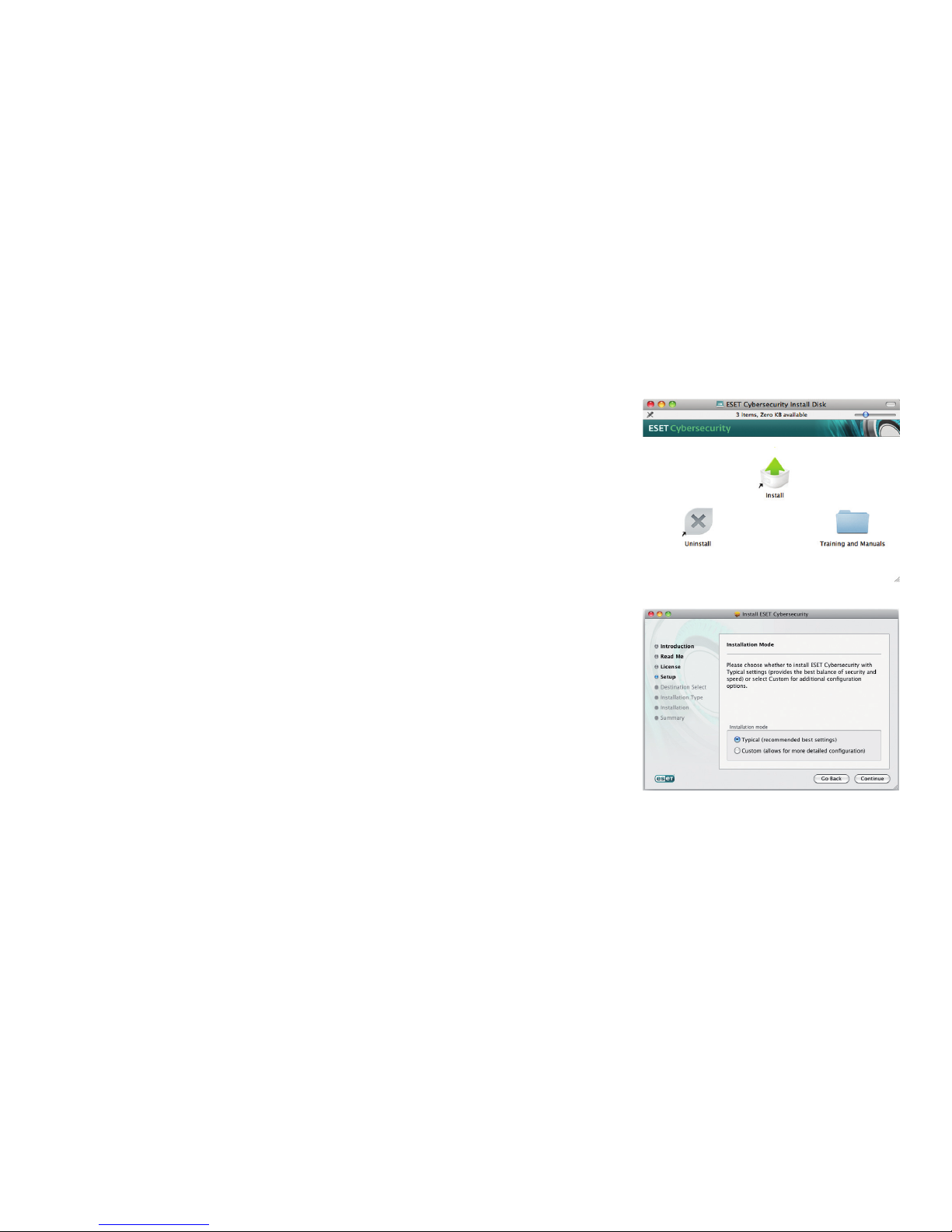
After launching the installer and
accepting the license agreement,
the installer will oer two types of
installation options:
Typical only the most important
parameters will be configured during
installation. Other parameters will be
preset to their recommended settings.
This mode provides our recommended
comprehensive protection and is
suitable for most users.
Custom enables configuration
of all advanced parameters during
installation.
This guide describes typical installation.
Page 5

ThreatSense.Net
ThreatSense.Net plays an important
role in our research regarding new
detection technologies that enable
us to proactively capture malware
and thus provide you with better
protection. We recommend that
you leave the ThreatSense.Net Early
Warning System enabled.
Click Continue to proceed to the next
step.
Detection of potentially
unwanted applications
Since some potentially unwanted
applications are used legitimately and
might not necessarily pose a security
risk, the user‘s consent is required to
enable detection. We recommend
selecting the Enable detection of
potentially unwanted applications
option.
Click Continue to proceed to the next
step.
Installation location
Select a disk where you want to install
ESETCybersecurity and click Continue.
Page 6

Completing the installation
When all necessary parameters
have been configured, start the final
installation by clicking the Install
button. The installation progress will
be indicated by aprogress bar. After
installation is complete, you must
restart your computer. Simply click
the Restart button on the Installation
Completed screen.
Product Activation
When you restart your machine, you
will see the Product Activation Type
window.
If you purchased ESET Cybersecurity
online, you have already received
a username and password. Select
Activate using a Username and
Password and click Next. Enter your
username including the hyphon and
password carefully. Click Activate to
complete the activation process.
If you purchased a retail copy of ESET
Cybersecurity, select Activate using
an Activation Key. The Activation
key is usually supplied on the back of
the product package and inside your
CD case and consists of , or
characters. Ensure that your email
address is entered correctly, as the
username and password required
for updating ESET Cybersecurity
will be sent to this address. After
clicking Activate, your username
and password will be entered for you
automatically. If you choose not to
activate at this time, click Activate
later. If you selected activate later, the
Product Activation window will appear
the next time you start your system.
The method for entering a username
and password manually is described in
the following section.
Page 7

Starting
ESETCybersecurity
Check for new version
ESETCybersecurity starts protecting
your computer immediately after
activation. At any time you may open
ESETCybersecurity to check your
protection status or to perform various
scanning and maintenance tasks.
To start ESETCybersecurity:
• Click on the ESETCybersecurity
icon located in your menu bar
top of the screen and choose
Openwindow.
For maximum protection, it is
important to use the latest build
of ESET Cybersecurity. To check for
anew version, click Update from
the main menu on the left. If a new
build is available, a message that says
“Anew version of ESET Cybersecurity
is available” will be displayed at the
bottom of the window. Click Learn
more… to display a new window
containing the version number of the
new build and the list of changes in the
new version or other important info.
Click Download to download the latest
build. Click OK to close the window and
download the upgrade later.
If you clicked Download, the file will
be downloaded to your downloads
folder or the default folder set by your
browser. When the file has finished
downloading, launch the file and
follow the installation directions.
Your username and password will
be automatically transferred to the
new installation. It is recommended
to check for upgrades regularly, and
especially after a recent installation.
Page 8

Entering Username and Password for update
If you purchased ESET Cybersecurity
online, you must enter the username
and password you received with your
license email. You will also need to
enter the username and password if
you are renewing or reinstalling the
software.
In the left pane of the
ESETCybersecurity screen, select
Update and then click Username and
password setup… on the right.
Enter the username and password to
the appropriate fields and click OK to
confirm. The username and password
are both case sensitive. Enter them
carefully and precisely. Copying and
pasting from the license email is
recommended.
Your username and password must be
correctly entered to receive updates
and ensure that your computer is
continually protected against newly
emerging threats.
Update
By default, ESETCybersecurity is
set to receive regular updates once
every minutes. If you entered
your username and password after
the installation and no update has
been performed yet, we recommend
starting the update manually:
•
Select Update in the left pane of the
main ESETCybersecurity screen
•
Click Update virus signature
database
The update module will connect to the
Internet, contact an available ESET
update server and download digitally
signed update files, which contain the
most recent malware signatures as
well as new definitions for advanced
heuristics and other program modules.
As soon as a newer update has been
installed, ESETCybersecurity displays
the new version of the virus signature
database in the Mac OS menu bar.
Page 9

Computer scanning
After successful installation and
update, we recommend that you
perform a complete computer scan
to check for existing threats. To do
this, click Computer scan in the main
ESETCybersecurity screen and select
Smart scan. ESETCybersecurity will
begin scanning all local hard drives. As
long as the scan continues, the status
window shows the progress bar as
well as the current statistics about
scanned and infected files found. Ifa
threat is detected, ESET Cybersecurity
will quarantine the file and display an
alert. You should be able to continue
working as normal while the scan
takes place.
Page 10

Protection Status indication
ESET Cybersecurity’s current
protection status is indicated in the
following ways:
• The menu bar icon
• A report in the Protection status
window
In the event that any protection
module is disabled, the Protection
status window will show the name of
the disabled module, along with a link
allowing you to reenable it.
The individual protection statuses are
indicated by colors:
green Antivirus protection is
working properly; your computer is
protected against malicious software
and network attacks. This status
indicates that all protection modules
are enabled and the virus signature
database is uptodate.
yellow Realtime file system
protection is enabled, but the
maximum level of protection is not
ensured. The yellow icon is displayed
if ESET Cybersecurity requires your
attention.
red – The Realtime filesystem
protection is disabled. Since the proper
functioning of these modules is vital to
your system’s security, we recommend
enabling the inactive module
immediately.
Page 11

Resolving Issues
ESET’s technical support specialists
are ready to assist you in resolving
potential problems. Before contacting
technical support, we strongly
recommend searching for asolution
on the ESET website first. This will help
you to resolve the problem quickly
within acouple of minutes.
Answers to the most frequently asked
questions can be found at:
http://kb.eset.com/faq
For various problem solutions,
directions and hints, read our
knowledgebase:
http://kb.eset.com
To contact ESET’s technical support,
please fill in the support form:
http://www.eset.com/support/contact
Page 12

www.eset.com
Copyright © 2010 ESET, spol. s r. o. ESET, logo of ESET, NOD, ThreatSense, ThreatSense.Net
and/or other mentioned products of ESET, spol.sr. o., are registered trademarks of ESET, spol.sr. o.
Other companies mentioned here or products, may be registered trademarks of its proprietors.
Produced according to quality standards of ISO :.
 Loading...
Loading...