Equaline N305213A Users Manual

802.11n Modular WLAN
Access Point
User Guide
i

Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against
harmful interference in a residential installation. This equipment generates, uses and can radiated radio frequency energy and, if not installed and used in accordance with the instructions, may cause
harmful interference to radio communications. However, there is no guarantee that interference will
not occur in a particular installation. If this equipment does cause harmful interference to radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one of the following measures:
z Reorient or relocate the receiving antenna.
z Increase the separation between the equipment and receiver.
z Connect the equipment into an outlet on a circuit different from that to which the receiver is
connected.
z Consult the dealer or an experienced radio/TV technician for help.
FCC Caution: To assure continued compliance, (example – use only shielded interface cables when
connecting to computer or peripheral devices). Any changes or modifications not expressly approved
by the party responsible for compliance could void the user’s authority to operate this equipment.
This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter.
FCC Radiation Exposure Statement
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled environment. This equipment should be installed and operated with minimum distance 20 cm between the radiator & your body.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation.
ii

R&TTE Compliance Statement
This equipment complies with all the requirements of DIRECTIVE 1999/5/CE OF THE EUROPEAN
PARLIAMENT AND THE COUNCIL OF 9 March 1999 on radio equipment and telecommunication
terminal equipment and the mutual recognition of their conformity (R&TTE).
The R&TTE Directive repeals and replaces in the directive 98/13/EEC (Telecommunications Terminal Equipment and Satellite Earth Station Equipment) as of April 8,2000.
Safety
This equipment is designed with the utmost care for the safety of those who install and use it. However, special attention must be paid to the dangers of electric shock and static electricity when working with electrical equipment. All guidelines of this and of the computer manufacture must therefore
be allowed at all times to ensure the safe use of the equipment.
EU Countries Intended for Use
The ETSI version of this device is intended for home and office use in Austria, Belgium, Denmark,
Finland, France (with Frequency channel restrictions), Germany, Greece, Ireland, Italy, Luxembourg,
Portugal, Spain, Sweden, The Netherlands, and United Kingdom.
The ETSI version of this device is also authorized for use in EFTA member states Norway and Switzerland.
EU Countries Not Intended for Use
None.
iii

Table of Contents
1. Introduction.........................................................................................................................1
1.1. Overview...................................................................................................................1
1.2. Features.................................................................................................................... 1
1.3. LED Definitions......................................................................................................... 3
2. First-Time Installation and Configuration............................................................................ 4
2.1. Power........................................................................................................................ 4
2.2. Installing the Access Point........................................................................................ 4
2.3. Connecting a Managing Computer...........................................................................5
2.4. Configuring the AP.................................................................................................... 6
2.4.1. Login............................................................................................................... 6
2.4.2. Selecting Mode............................................................................................... 7
2.4.3. Configuring TCP/IP Settings........................................................................... 8
2.4.4. Configure IEEE 802.11 Settings..................................................................... 9
2.4.5. Review and Apply Settings........................................................................... 10
2.5. Setting up Client Computers................................................................................... 11
2.5.1. Configure IEEE 802.11 Settings................................................................... 11
2.5.2. Configure TCP/IP-Related Settings.............................................................. 11
2.6. Confirm Settings of the Access Point and Client Computers.................................. 12
2.6.1. Checking if the IEEE 802.11n-Related Settings Work.................................. 12
2.6.2. Checking if the TCP/IP-Related Settings Work............................................ 12
3. Advanced Network Management...................................................................................... 12
3.1. Overview................................................................................................................. 13
3.1.1. Menu Structure.............................................................................................13
3.1.2. Save, Save & Restart, and Cancel Commands............................................ 14
3.1.3. Home and Refresh Commands....................................................................15
3.2. Viewing Status........................................................................................................ 15
3.2.1. Associated Wireless Clients......................................................................... 15
3.2.2. Current DHCP Mappings.............................................................................. 16
3.2.3. System Log................................................................................................... 16
3.2.4. Link Monitor.................................................................................................. 17
3.3. General Operations ................................................................................................17
3.3.1. Specifying Operational Mode .......................................................................17
3.3.2. Changing Password .....................................................................................18
3.3.3. Managing Firmware...................................................................................... 19
3.3.3.1. Upgrading Firmware by HTTP............................................................ 19
3.3.3.2. Backing up and Restoring Configuration Settings by HTTP............... 19
3.3.3.3. Upgrading Firmware by TFTP............................................................20
3.3.3.4. Backing up and Restoring Configuration Settings by TFTP...............22
3.3.3.5. Resetting Configuration to Factory Defaults....................................... 23
3.4. Configuring TCP/IP Related Settings .....................................................................23
3.4.1. Addressing.................................................................................................... 23
3.4.2. DHCP Server................................................................................................ 24
3.4.2.1. Basic................................................................................................... 24
3.4.2.2. Static DHCP Mappings....................................................................... 24
3.5. Configuring IEEE 802.11 Related Settings............................................................. 25
3.5.1. Communication............................................................................................. 25
3.5.1.1. Basic................................................................................................... 25
3.5.1.2. Link Integrity....................................................................................... 26
3.5.1.3. Association Control ............................................................................26
3.5.1.4. Load Balancing................................................................................... 26
3.5.1.5. Wireless Distribution System.............................................................. 26
3.5.2. Security......................................................................................................... 29
3.5.2.1. Selecting Wireless Security Mode...................................................... 30
iv

3.5.2.2. MAC-Address-Based Access Control ................................................31
3.5.3. IEEE 802.1x/RADIUS...................................................................................33
3.6. Advanced Settings.................................................................................................. 35
3.6.1. Packet Filters................................................................................................ 35
3.6.1.1. Ethernet Type Filters..........................................................................35
3.6.1.2. IP Protocol Filters...............................................................................35
3.6.1.3. TCP/UDP Port Filters ......................................................................... 36
3.6.2. Management................................................................................................. 36
3.6.2.1. UPnP.................................................................................................. 36
3.6.2.2. System Log ........................................................................................37
3.6.2.3. SNMP.................................................................................................37
Appendix A: Default Settings................................................................................................ 39
Appendix B: Troubleshooting................................................................................................ 40
B-1: Wireless Settings Problems................................................................................... 40
B-2: TCP/IP Settings Problems .....................................................................................41
v
1. Introduction
1.1. Overview
The Access Point modular WLAN access point (AP) enables 802.11n or 802.11g client computers to
access the resources on an Ethernet network wirelessly or wired. It conveniently fits into standard
wall outlets and only takes a few minutes to install and configure for use. The Access Poi nt has a
built-in browser-based management application offering an easy to follow setup-wizard for novice
wireless users as well as comprehensive settings for more advanced users and/or network administrators.
1.2. Features
z Access Point Firmware Features
Operational Modes
AP/Bridge. This mode provides both Access Point and Static LAN-to-LAN Bridg-
ing functionality. The static LAN-to-LAN bridging function is supported through
Wireless Distribution System (WDS).
AP Client. This mode is for Dynamic LAN-to-LAN Bridging. The AP Client auto-
matically establishes bridge links with APs from any vendor.
RF Type Selection.
IEEE 802.11n only, IEEE 802.11g only, IEEE 802.11g only, or mixed mode (802.11n,
802.11g and 802.11b simultaneously).
64-bit and 128-bit WEP (Wired Equivalent Privacy).
encryption.
Enabling/Disabling SSID Broadcasts.
the administrator can enable or disable the SSID broadcasts functionality for security reasons. When the SSID broadcast functionality is disabled, a client computer cannot connect
to the Access Point with “blank” network name (SSID, Service Set ID); the correct SSID
has to be specified on client computers.
MAC-address-based Access Control.
it can be configured to block unauthorized wireless client computers based on MAC (Media Access Control) addresses. Additionally, an ACL (Access Control List) can be downloaded from a TFTP server.
The RF type of the WLAN interface can be configured to work in
For authentication and data
When the Access Point is in AP/Bridge mode,
When the Access Point is in AP/Bridge mode,
IEEE 802.1x/RADIUS.
ured to authenticate wireless users and distribute encryption keys dynamically by IEEE
802.1x Port-Based Network Access Control and RADIUS (Remote Authentication Dial-In
User Service).
WPA (Wi-Fi Protected Access).
posed by the Wi-Fi Alliance (http://www.wi-fi.org
mode and full WPA mode are supported. WPA is composed of TKIP (Temporal Key Integrity Protocol) and IEEE 802.1x and serves as a successor to WEP for better WLAN security.
When the Access Point is in AP/Bridge mode, it can be config-
The Access Point supports the WPA standard pro-
). Both WPA-PSK (Pre-Shared Key)
1
Repeater. When the Access Point is in AP/Bridge mode, it can communicate with other
APs or wireless bridges via WDS (Wireless Distribution System). Therefore, a Access
Point can wirelessly forward packets from wireless clients to another Access Point. Then
the second Access Point forwards the packets to the Ethernet network.
Wireless Client Isolation.
When the Access Point is in AP/Bridge mode, wireless-to-wireless traffic can be blocked so that the wireless clients cannot see each other.
This capability can be used in hotspots applications to prevent wireless hackers from attacking other wireless users’ computers.
AP Load Balancing.
Several Access Point’s can form a load-balancing group. Within a
group, wireless client associations and traffic load can be shared among the devices. This
function is available when the Access Point is in AP/Bridge mode.
Transmit Power Control.
Transmit power of the Access Point’s RF module can be ad-
justed to desired RF coverage.
Link Integrity.
When the Access Point is in AP/Bridge mode and its Ethernet LAN inter-
face is detected to be disconnected from the wired network, all currently associated wireless clients are disassociated by the Access Point and no wireless client can associate with
it.
Association Control.
When the Access Point is in AP/Bridge mode, it can be configured to deny association requests when it has served too many wireless clients or traffic
load is too heavy.
Associated Wireless Clients Status.
When the Access Point is in AP/Bridge mode, it
can show the status of all wireless clients that are currently associated or ‘connected’.
Auto Channel Selection.
The auto channel selection feature allows the device to auto-
matically select the channel that will provide optimum performance on powering up the
Access Point.
z DHCP client. The Access Point can automatically obtain an IP address from a DHCP server.
z DHCP server. The Access Point can automatically assign IP addresses to computers or other
devices by DHCP (Dynamic Host Configuration Protocol).
Static DHCP Mappings.
The administrator can specify static IP address to MAC ad-
dress mappings so that IP addresses are always assigned to the hosts with the specified
MAC addresses.
Showing Current DHCP Mappings.
Displays which IP address is assigned to which
host identified by an MAC address.
z Packet Filtering. The Access Point provides Layer 2, Layer 3, and Layer 4 filtering capabili-
ties.
z Firmware Management Tools
Firmware Upgrade.
The firmware of the Access Point can be upgraded in the following
methods:
TFTP-based. Upgrading firmware by TFTP (Trivial File Transfer Protocol).
2
HTTP-based. Upgrading firmware by HTTP (HyperText Transfer Protocol).
Configuration Backup.
to a file via TFTP
Configuration Reset.
tory-default values.
z Management
Browser-based Network Manager
via a Web browser. The management protocol is HTTP (Hyper Text Transfer Protocol)-based.
SNMP.
IEEE 802.1x, and Private Enterprise MIB are supported.
UPnP.
user can locate the Access Point in My Network Places and use a Web browser to configure it.
System Log.
Local log. System events are logged to the on-board RAM of the Access Point and
SNMP (Simple Network Management Protocol) MIB I, MIB II, IEEE 802.1d,
The Access Point responds to UPnP discovery messages so that a Windows XP
can be viewed using a Web browser.
or HTTP for later restoring.
For system operational status monitoring.
The configuration settings of the Access Point can be backed up
Clears current configuration settings and restores to fac-
for configuring and monitoring the Access Point
Remote log by SNMP trap. Systems events are sent in the form of SNMP traps to
a remote SNMP management server.
z Power over Ethernet. Power is supplied to the Access Point via an Ethernet cable using an
802.3af compliant power injector.
z Hardware Watchdog Timer. If the firmware “hangs” in an invalid state, the hardware
watchdog timer will detect this situation and restart the Access Point. This way, the Access Point
can provide continuous services.
1.3. LED Definitions
There are several LED indicators on the front of the Access Point. Please refer to the definitions below:
C
3
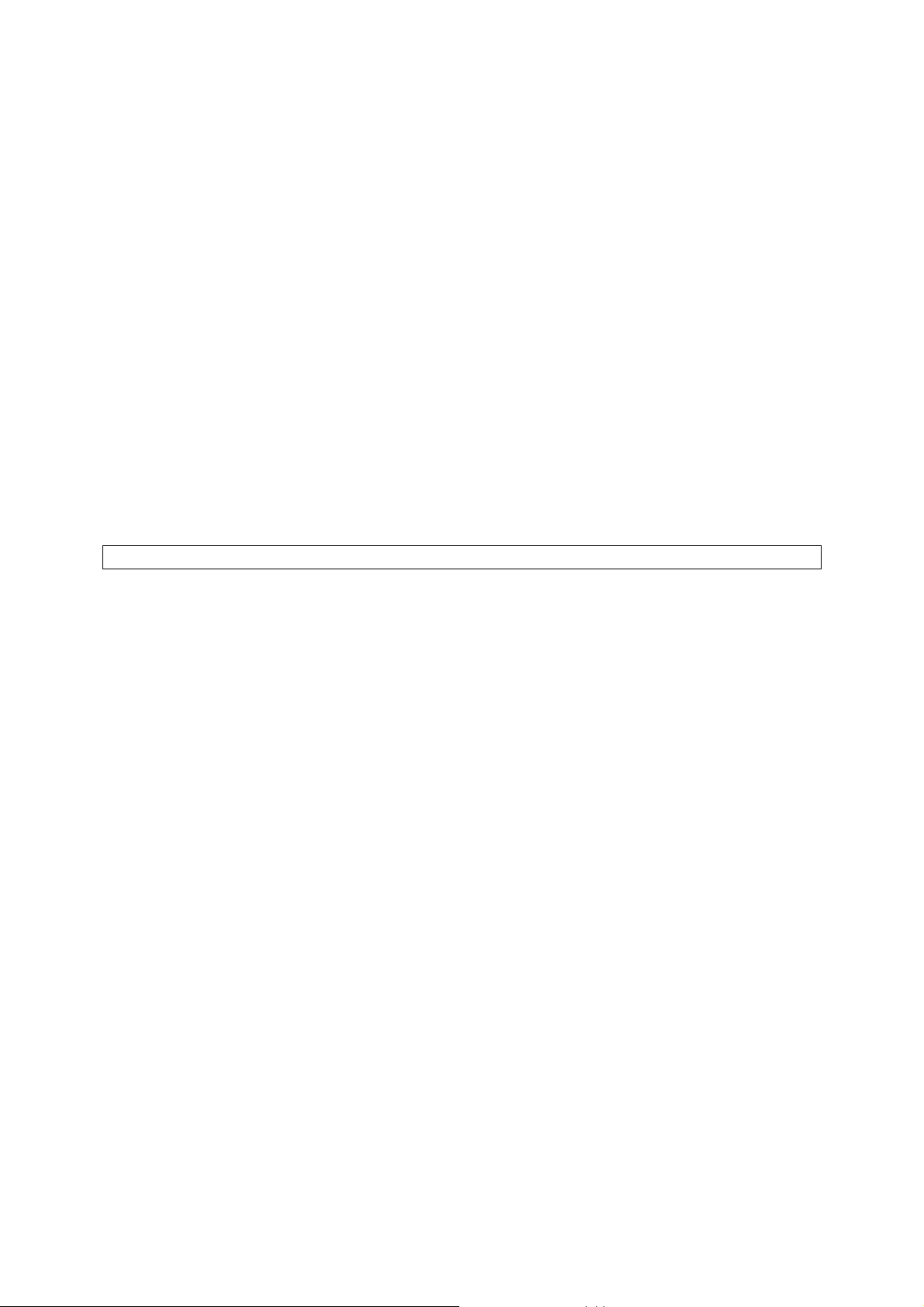
A. WAN: Green, solid when connected, flashing when data activity
B. Wireless: Green, solid when on, flashing when wireless data activity
C. RJ-45 LAN port
Amber, solid when LAN connection
Green, solid when LAN connection, flashing when activity
2. First-Time Installation and Configuration
2.1. Power
The Access Point is powered using PoE (Power over Ethernet). The Access Point automatically selects the suitable power supply.
To power the AP by PoE:
1. Plug one connector of an Ethernet cable to an available port of a PoE injector or switch.
2. Plug the other connector of the Ethernet cable to the WAN port on the rear of the Access Point.
NOTE: The Access Point is 802.3af compatible.
2.2. Installing the Access Point
The Access Point has two options for installation: desktop/flat surface or into a standard Ethernet wall
jack.
Desktop or flat surface:
1. Remove the Access Point from the box and snap apart the two pieces of the screw less faceplate
that are affixed to the Access Point.
2. Place the Access Point in desired location upon the desk or flat surface.
3. Using the single-port PoE Injector, connect one end of an Ethernet LAN cable from a LAN port
on the network router or switch and the opposite end to the port marked “Data In”. Use another
Ethernet LAN cable to connect the port marked “Data Out” to the WAN port (on rear) of the
Access Point.
4. Plug the single-port PoE power cord into an electrical outlet.
5. Check the LED indication lights. Two LEDs (WAN, Wireless) should be properly lit.
Ethernet Wall Jack:
1. Remove the Ethernet wall jack faceplate.
2. Plug the wall jack LAN cable to the WAN port, the rear port, of the main housing of Access Point.
All two green LEDs on the Access Point should be lit if properly connected to a router/switch and
PoE power supply. If “yes”, proceed to step 3.
3. Slowly insert the Access Point into the wall box until the main housing of Access Point is flush to
4
the wall.
4. Fasten the Access Point main housing to the wall box with screws provided.
5. Line-up and push the faceplate cover onto the main housing until it snaps securely into place.
2.3. Connecting a Managing Computer
To configure the Access Point using the Advanced option, a managing computer with a Web browser
is needed.
NOTE: If you are using the browser, Opera, to configure the Access Point, click the menu item File,
click Preferences..., click File types, and edit the MIME type, text/html, to add a file extension
“.sht” so that Opera can work properly with the Web management pages of the AP.
Since the configuration/management protocol is HTTP-based, make sure that the IP address of the
managing computer and the IP address of the managed AP are in the same IP subnet (the default
IP address of the Access Point is Obtain from DHCP Server).
NOTE: When the AP failed to obtain IP from DHCP Server, after 3 attempts, the AP will set the de-
fault IP to 192.168.100.1.
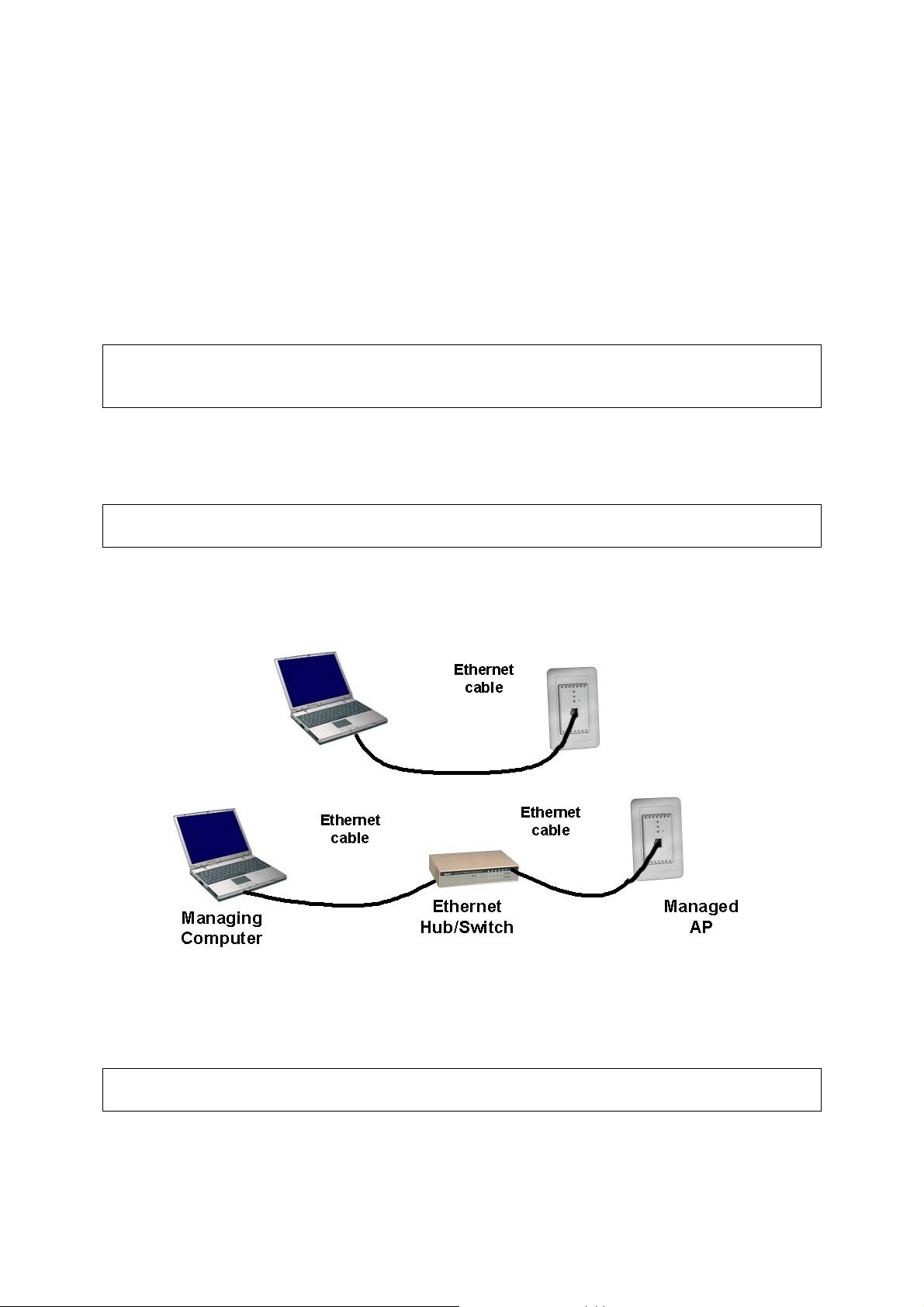
To connect the Ethernet managing computer and the managed Access Point for first-time configuration, you have two choices as illustrated in Fig. 1.
Fig. 1. Connecting a managing computer and the Access Point via Ethernet
You can use either a standard Ethernet cable (included in the package) or a switch/hub with two normal Ethernet cables.
NOTE: One connector of the Ethernet cable must be plugged into the Access Point WAN port for
configuration.
5
2.4. Configuring the AP
After the IP addressing issue is resolved, launch a Web browser on the managing computer. Then, go
to “http://AP IP to access the Web-based Network Manager login page.
TIP: The Access Point can be reached by its host name using a Web browser. For example, if the Ac-
cess Point is named “AP”, you can use the URL “http://AP” to access.
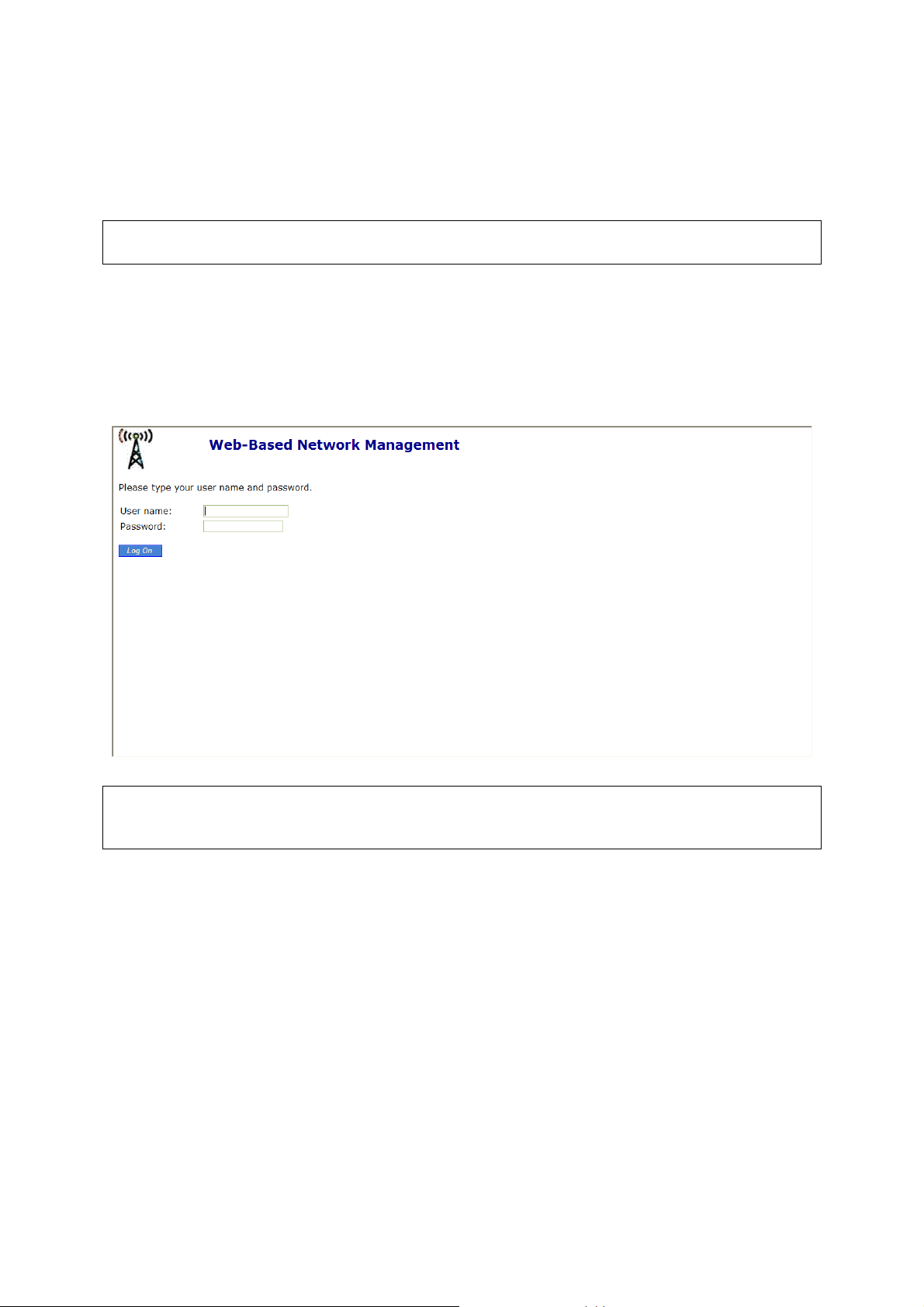
2.4.1. Login
Before the Home page is shown, you will be prompted to enter the user name and password to gain
the right to access the Web-based Network Manager. For first-time configuration, use the default user
name “admin” and default password “admin”, respectively.
Fig. 2. The Login page
NOTE: It is strongly recommended that the password be changed for security reasons. On the start
page, click the General, Password link to change the value of the password (see Section 3.3.1 for
more information).
6
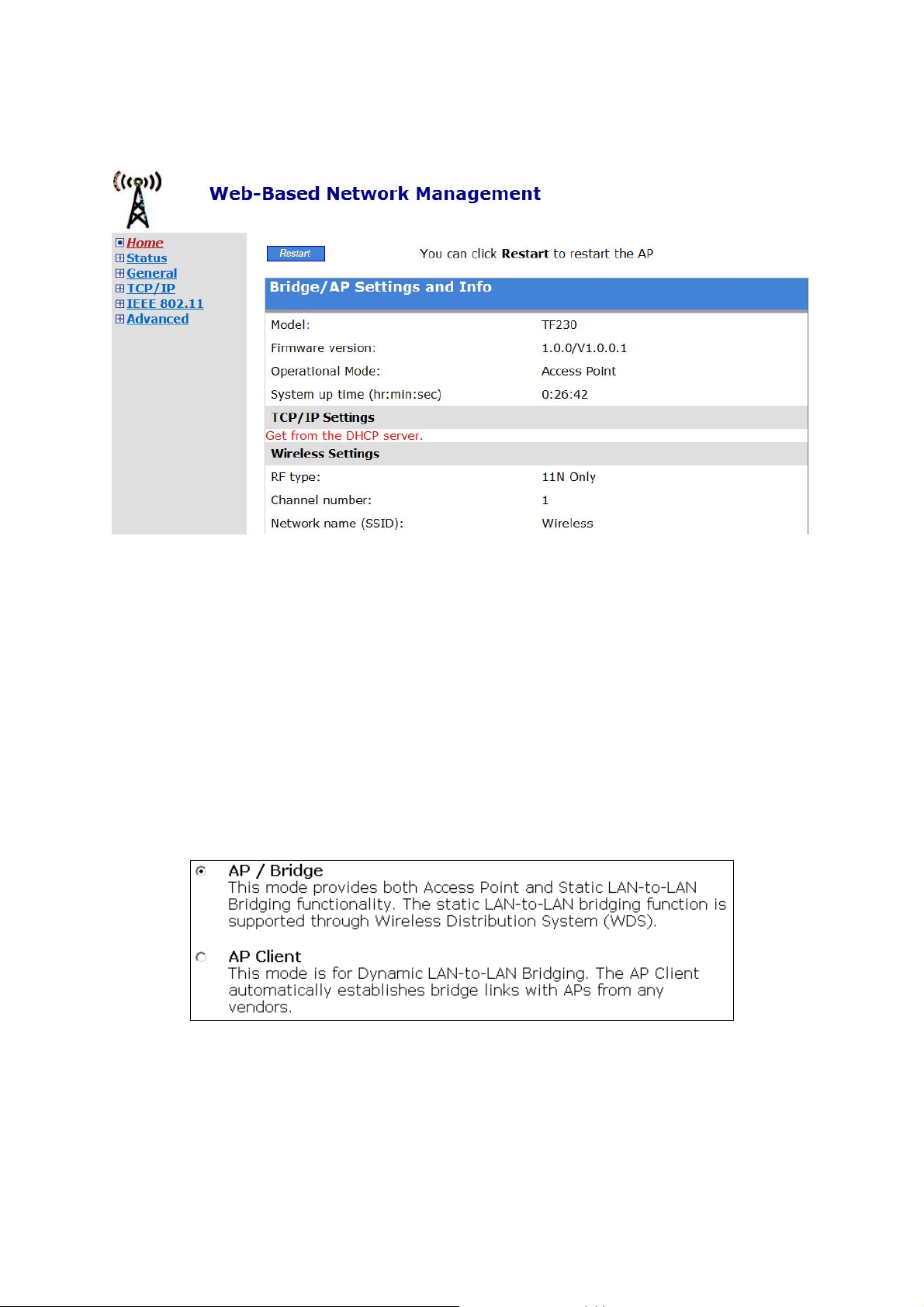
Once you have successfully logged in, the Home page opens. Click on the main manual on left hand
side for Setup.
Fig. 3. The Home page
2.4.2. Selecting Mode
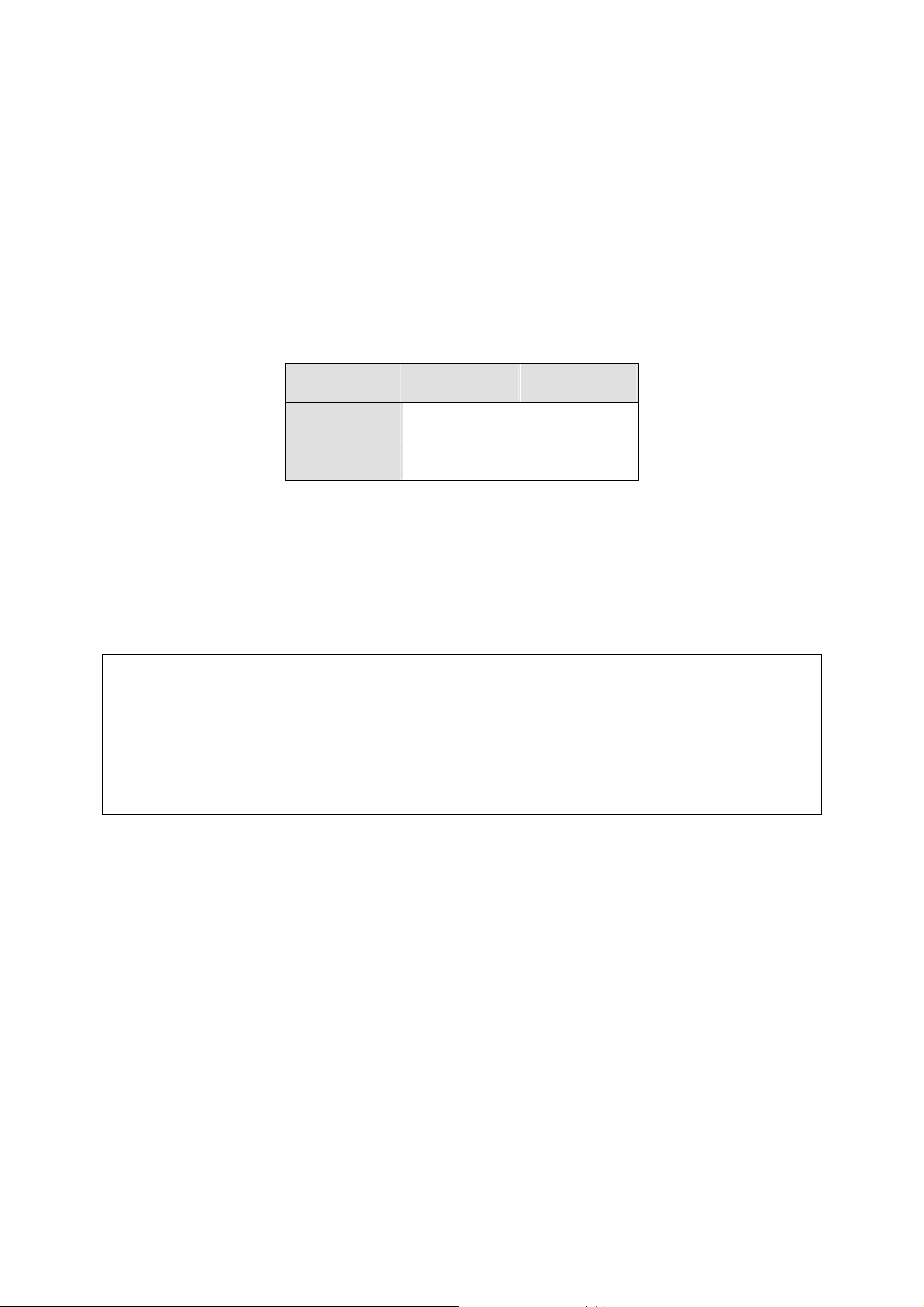
The Access Point supports two operational modes:
AP/Bridge. This mode provides both Access Point and Static LAN-to-LAN Bridging
functionality. The static LAN-to-LAN bridging function is supported through Wireless
Distribution System (WDS).
AP Client. This mode is for Dynamic LAN-to-LAN Bridging. The AP Client automati-
cally establishes bridge links with APs from any vendors.
Fig. 4. Operational mode settings
1. Click on General from the side menu, and then select Operational Mode.
2. Select an operational mode and click Save to apply the setting.
In either mode, the Access Point forwards packets between its Ethernet interface and wireless interface for wired hosts on the Ethernet side and wireless host(s) on the wireless side.
7
There are two types of wireless links as specified by the IEEE 802.11 standard.
STA-AP. This type of wireless link is established between an IEEE 802.11 Station (STA)
and an IEEE 802.11 Access Point (AP). An STA is usually a client computer (PC or PDA)
with a WLAN network interface card (NIC). The AP Client mode is actually an STA.
WDS. This type of wireless link is established between two IEEE 802.11 Access Point’s.
Wireless packets transmitted along the WDS link comply with the IEEE 802.11 WDS
(Wireless Distribution System) format at the link layer.
The relationships among the operational modes and the wireless link types are shown in the following
table:
AP/Bridge AP Client
AP/Bridge
AP Client
Table 1. Operational modes vs. wireless link types.
To establish a static bridge link based on WDS, the AP/bridges at both end of the WDS link must be
manually configured with each other’s MAC addresses (see Section 3.5.1.5 for more information). To
establish a dynamic bridge link between an Access Point and an AP Client, both devices have to be
configured with the same SSID and WEP settings. The AP Client automatically scans for any Access
Point that is using the matched SSID and establishes a bridge link with the scanned Access Point.
NOTE: Although it’s more convenient to use dynamic bridging, it has a limitation—the AP Client
only can forward TCP/IP packets between its wireless interface and Ethernet interface; other type of
traffic (such as IPX and AppleTalk) is not forwarded.
TIP: When the Access Point is configured to be in AP Client, it can be used as an Ether-
net-to-wireless network adapter. For example, a notebook computer equipped with an Ethernet adapter can be connected to this device with a crossover Ethernet cable for wireless connectivity to another
access point.
WDS STA-AP
STA-AP
2.4.3. Configuring TCP/IP Settings
The IP address can be manually set or automatically assigned by a DHCP server on the LAN. If you
are manually setting the IP address, Subnet mask, and Default gateway settings, set them appropri-
ately, so that they comply with your LAN environment. In addition, you can specify the Host name
and Domain (DNS suffix) of the AP.
8
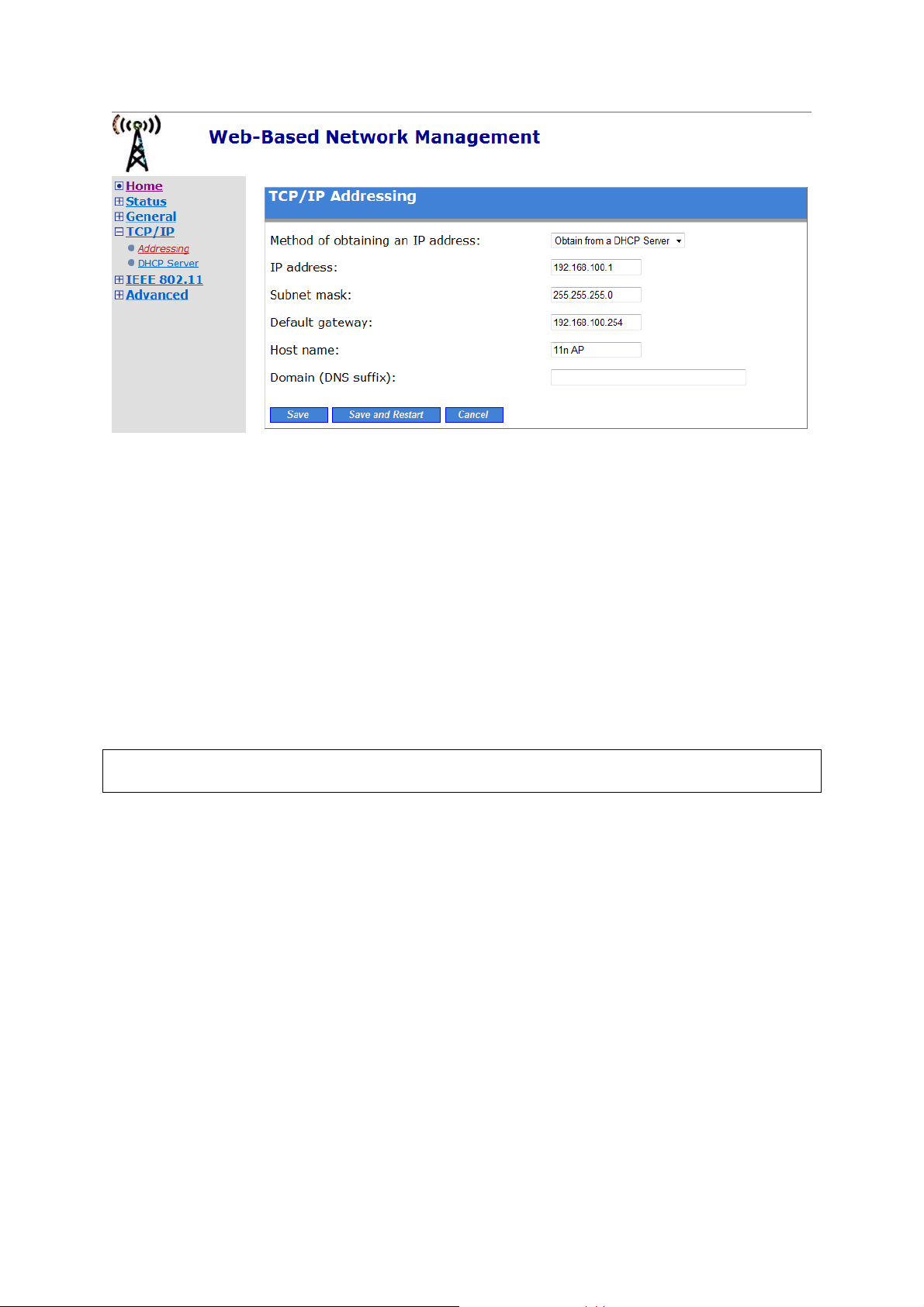
Fig. 5. TCP/IP settings.
1. Click on TCP/IP from the side menu and select Addressing.
2. When you have finished making changes, click Save or Save & Restart.
2.4.4. Configure IEEE 802.11 Settings
The Network Manager utility allows the user to configure IEEE 802.11n-related communication settings, including Regulatory domain, Channel number, and Network name (SSID) of the Access
Point. The number of available RF channels depends on local regulations; therefore you have to
choose an appropriate regulatory domain to comply with local regulations. The SSID of a wireless
client computer and the SSID of the Access Point must be identical for them to communicate
with each other.
NOTE: Put a check in the Auto Channel Selection checkbox to allow the Frequency Channel of
the Access Point to be automatically set.
9
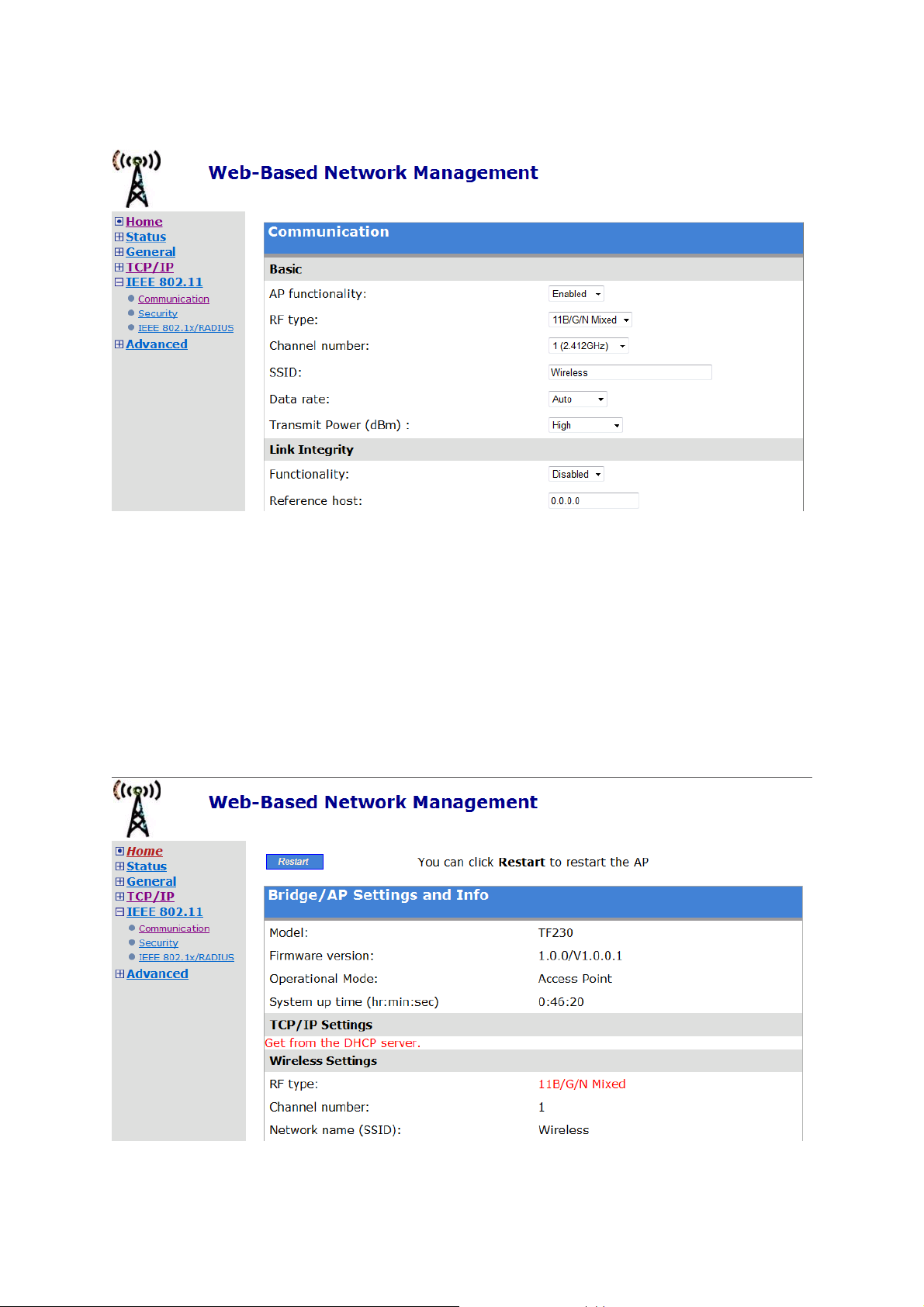
Fig. 6. IEEE 802.11n communication settings
1. Click on IEEE 802.11 from the side menu, and then select Communication.
2. When you have finished, scroll to the bottom of the screen and click either Save or Save &
Restart.
2.4.5. Review and Apply Settings
On the Summary page, you can review all the settings you have made. Changes are highlighted in red.
If they are OK, click Restart to restart the Access Point for the new settings to take effect.
Fig. 7. Settings changes are highlighted in red.
10
 Loading...
Loading...