Ensure Technologies XyLoc Client User Manual

User’s Guide
XyLoc Client
(ver 8.x.x)

Table of Contents
Introduction .................................................................................................................................... 4
Your XyLoc Package ............................................................................................................................... 4
Support Information ................................................................................................................................. 4
XyLoc Core Functionality ........................................................................................................................ 5
XyLoc Solo Overview .................................................................................................................... 6
The XyLoc System ................................................................................................................................... 6
XyLoc Product Architecture .................................................................................................................... 7
How XyLoc Works ........................................................................................................................................... 7
XyLoc Secure Login and Password Overview ......................................................................................... 8
Windows 2000/XP ............................................................................................................................................ 8
XyLoc Password ............................................................................................................................................... 8
Getting Started ............................................................................................................................... 9
Using the XyLoc Lock ............................................................................................................................. 9
Installing the XyLoc Lock (USB) ............................................................................................................ 9
Placement of the XyLoc Lock ........................................................................................................................... 9
The XyLoc Lock Status Light ......................................................................................................................... 11
Using the XyLoc Key ............................................................................................................................. 12
Installing the XyLoc Software ............................................................................................................... 14
Understanding Core Settings .................................................................................................................. 27
Administrative Levels ..................................................................................................................................... 27
Administrator .......................................................................................................................................... 27
User ......................................................................................................................................................... 28
Guest ....................................................................................................................................................... 28
AutoLogon ...................................................................................................................................................... 28
Authentication Methods .................................................................................................................................. 28
Login Authentication ............................................................................................................................... 28
Unlock Authentication ............................................................................................................................ 29
Configuring the XyLoc Software ........................................................................................................... 30
Security Configuration and User Preferences .................................................................................................. 30
User Setup ....................................................................................................................................................... 31
User Name ............................................................................................................................................... 31
Add User… ............................................................................................................................................. 32
What It Does: ......................................................................................................................................... 32
Delete User… .......................................................................................................................................... 32
Key ID ..................................................................................................................................................... 32
Add Key… .............................................................................................................................................. 32
Delete Key… ........................................................................................................................................... 32
Login Authentication ............................................................................................................................... 32
Allow Password Override (No Key) ....................................................................................................... 33
Unlock Authentication ............................................................................................................................ 34
Allow Password Override (No Key) ....................................................................................................... 34
Unlock to Key Only for up to x seconds/minutes .................................................................................... 34
Range ...................................................................................................................................................... 35
Range Refinement ................................................................................................................................... 35
Personal Name ........................................................................................................................................ 35
Advanced Settings ................................................................................................................................... 35
Advanced User Settings .................................................................................................................................. 36
Administrative Level ............................................................................................................................... 36
Auto Logoff Time ................................................................................................................................... 37
User can logoff locked workstation ......................................................................................................... 37
Key ID ..................................................................................................................................................... 37
Pass Key .................................................................................................................................................. 38
Beep When Locking ................................................................................................................................ 38
Lock if the Key is Stationary for ............................................................................................................. 38
Note: Ensure recommends the 1-minute option for demonstration purposes only. ............................... 38
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 2 of 62

XyLoc Password ..................................................................................................................................... 39
What It Does: ......................................................................................................................................... 39
Sets the XyLoc password. ...................................................................................................................... 39
Note: This box will only appear if this key is part of a Kiosk Account. ............................................... 39
Lock in Password Override ..................................................................................................................... 39
Run Application Integration Logoff ........................................................................................................ 39
Setting the Active Zone ........................................................................................................................... 40
Adding New Users .................................................................................................................................. 42
Kiosk Accounts ....................................................................................................................................... 45
Adding New Keys ................................................................................................................................... 46
PC Setup .......................................................................................................................................................... 48
XyLoc Lock Attached To ........................................................................................................................ 48
XyLoc Security Server Search Order ...................................................................................................... 48
Log Records To Upload .......................................................................................................................... 49
Advanced Settings ................................................................................................................................... 49
Advanced PC Settings ..................................................................................................................................... 50
XSS Client Port ....................................................................................................................................... 50
XyLoc Mode ........................................................................................................................................... 50
Min. Password Length ............................................................................................................................. 50
Logging ........................................................................................................................................................... 51
User Activity Log .................................................................................................................................... 51
NOTE: This option will only be available to a XyLoc Administrator. ................................................. 51
Testing XyLoc Keys ....................................................................................................................................... 52
Find Specific Key Mode .......................................................................................................................... 53
Find Strongest Key Mode ........................................................................................................................ 53
Sequence number .................................................................................................................................... 53
Range ...................................................................................................................................................... 54
Key Voltage ............................................................................................................................................ 54
Key Revision ........................................................................................................................................... 54
Overriding the XyLoc System ................................................................................................................ 55
User Forgets Their Key… ............................................................................................................................... 55
User Does Not Have a XyLoc Key… ............................................................................................................. 56
Unlocking using Password Override… ........................................................................................................... 56
Replacing the XyLoc Battery ................................................................................................................. 57
Software Removal .................................................................................................................................. 57
Troubleshooting ..................................................................................................................................... 58
System Functionality ................................................................................................................... 60
Normal Operational Mode ..................................................................................................................... 60
Hardware Architecture ........................................................................................................................... 60
Radio Frequency (RF) System ............................................................................................................... 60
Spectral Reuse ................................................................................................................................................. 61
Time Division Multiple Access (TDMA) ....................................................................................................... 61
Technical Specifications ................................................................................................................................. 61
Revision History ........................................................................................................................... 62
© Ensure Technologies, 1998-2008. All rights reserved. XyLoc and Ensure Technologies are trademarks of Ensure Technologies, Inc.
Other trademarks are the property of their respective owners.
Acrobat® Reader copyright © 1987-2008 Adobe Systems Incorporated. All rights reserved. Adobe and Acrobat are trademarks of
Adobe Systems Incorporated
Technical inform ation contained herein is subject to change without notice.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 3 of 62

Your XyLoc Package
The following is a checklist of all items included in the XyLoc User’s Package:
Software Release Notes
Quick Start Instructions
XyLoc Solo
XyLoc Key
XyLoc USB Lock
USB Extension Cable
XyLoc Lanyard
CD-ROM containing:
XyLoc software installer
Electronic version of XyLoc User’s Guide in Adobe Acrobat format
Introduction
Adobe Acrobat Reader installer
Support Information
We are available to answer any questions or provide any needed assistance. Please contact:
Ensure Technologies
Technical Support
(734) 547-1631
support@ensuretech.com
FCC Compliance
This device complies with Part 15 of the FCC Rules and with RSS-210 of Industry Canada.
Operation of this device is subject to the following two conditions:
1. This device may not cause harmful interference, and
2. This device must accept any interference received, including interference that may cause
undesired operation.
Warning: Changes or modifications not expressly approved by Ensure Technologies for compliance could
void the user’s authority to operate the equipment. The term “IC:” before the radio certification number
only signifies that Industry Canada technical specifications were met.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 4 of 62
XyLoc Core Functionality
The XyLoc Solo is a flexible hardware/software platform with expanding capabilities. Below
is an overview of the core capabilities in the XyLoc Solo and future capabilities.
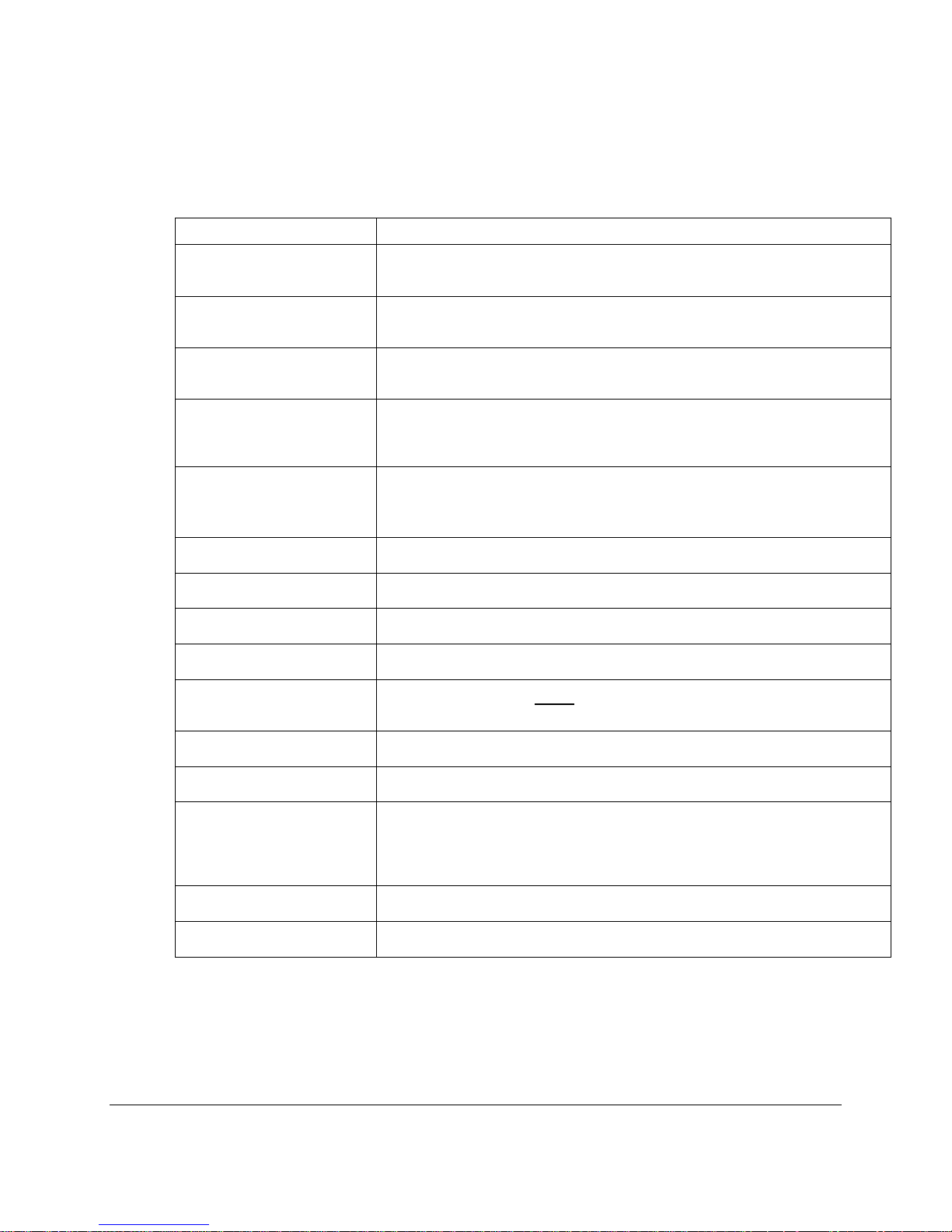
Capability Functionality
Full-Time Access Control
Proximity-Based ID and
Authentication
Automatic Network Logon
Multi-User Support
Access Methods
Transparent Operation
Programmable Range
Management
System Connection
OS Support
Continuously monitors for the presence or absence of authorized users, secures the PC
when user leaves Active Zone, and unlocks when user returns
Confirms the user’s identity and verifies authorized access to the PC based on user’s
proximity to PC
Provides automatic logon to pre-configured network services; maintains network
sessions when the user leaves Active Zone.
One Key can be programmed to unlock hundreds of Locks (for system administrators or
department managers); One Lock can support multiple Keys (for shared PC
environments); Kiosk accounts
Single factor security: Hands-Free, Select User Name
Dual factor security (recommended): Must Enter Password
Protects PC without requiring any action or intervention by the user
User-definable Active Zone for maximum flexibility
User or administrator locally manages and administers XyLoc system
Connects via the USB port
Windows 2000, and XP. NOTE: Windows 95, Windows 98, NT4 and Windows ME
are not supported
Key Type
Installation
Screen Saver Support
Scalable Management
KeyCard
Installs in minutes using only one cable and simple installation Wizard
Any windows screen saver is supported. NOTE: Since XyLoc takes over the security
of the workstation a password protected screen saver in Windows 2000/XP is no longer
available or needed. XyLoc will secure the workstation for the user immediately when
they exit the Active Zone.
XyLoc Security Server for central management and audit log tracking of the users
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 5 of 62

XyLoc Solo delivers desktop security that positively identifies authorized users and permits
access to PCs and portables as appropriate.
The focus of XyLoc Solo is three-fold:
1. Providing full-time access control to PCs and portables
2. Taking the burden of compliance off the end user
3. Making the computer more convenient for the user
XyLoc Solo runs on Windows 2000 and Windows XP. It has been designed with careful
consideration to the varying security dynamics of these operating systems. XyLoc provides
an additional layer of protection to the built-in security capabilities of Windows 2000 and XP.
The XyLoc System
XyLoc Solo Overview
XyLoc KeyCard
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
XyLoc Lock
Page 6 of 62

XyLoc Product Architecture
XyLoc is a microprocessor-based turnkey solution. Its patented technology is based on
wireless radio frequency (RF) technology that continuously monitors authorized users based
on their proximity to the PC and grants access to the PC as appropriate. The XyLoc system
consists of:
• XyLoc Software: authenticates and identifies multiple users and controls the lock and
key;
• XyLoc Lock: a small ultra-low power receiver that plugs into a USB port;
• XyLoc Key: a small, wireless transmitter with unique user ID that can be clipped to a
belt or key ring, worn on a neck lanyard, or attached to an ID badge.
How XyLoc Works
The XyLoc Lock and Key are in constant, encoded two-way wireless communication with
each other. As an authorized user approaches the PC, the XyLoc Key identifies and
authenticates the user, and unlocks the PC when the user enters the pre-set Range. Then,
when the authorized user moves out of the Active Zone, XyLoc automatically secures the
desktop. The PC is instantly secured and remains so until an authorized user returns to within
a user-configured unlock range. Background tasks, such as printing and downloading,
however, may continue while the PC is securely locked.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 7 of 62

XyLoc Secure Login and Password Overview
Windows 2000/XP
The Windows NT based Operating Systems (2000/XP) are designed with more inherent
security. There is already a GINA in place which controls the logins, profiles and security
permissions on the workstation. The XyLoc system also has a GINA, which takes over the
primary windows logon and in turn “calls” the Microsoft GINA. Most of the inherent
Microsoft security is still in place, and XyLoc enhances that security with a proximity based
solution.
The XyLoc Secure Login will be the first screen that is displayed on the PC, and the same
basic login process will be used. The exception is that hitting “CTRL+ALT+DEL” on the
keyboard will allow access to the standard Microsoft/Novell login box and a user can login
with a valid local or domain account and override XyLoc. This is to allow an Administrator
to still gain access to the PC, even if that Administrator does not have a XyLoc account.
There is a registry setting that can be enabled which will block all non-XyLoc accounts from
gaining access to the system, even Administrators, however this setting is disabled on the
default installation.
Also, the F8 keystroke at boot up is not disabled at login. This is due to the security of
Windows itself, and only an Administrator should have access to truly bypass XyLoc in Safe
Mode.
Lastly, in Windows 2000/XP, the password-protected screensaver is no longer password
protected. Because XyLoc takes control of the security of the workstation, XyLoc also
handles the locking action of the PC. Since the system will lock immediately when the user
leaves his/her active range the password protection on the screensaver is no longer needed. It
will still function as a standard screensaver, but will no longer have a password.
XyLoc Password
For flexibility and security, the XyLoc system provides an additional password, the XyLoc
Password (sometimes referred to as a PIN). The XyLoc password is only used in a Kiosk
account and has two possible applications:
1. It is used by the Kiosk Account feature to provide multi-factor authentication in a shared
log-on account. NOTE: Starting in version 8.2.4, this is the only password that is
accepted in conjunction with a user’s XyLoc key.
2. It is used in conjunction with the user’s Personal Name when performing a Password
Override in a Kiosk account to ensure individual security even when a XyLoc Key is not
present.
NOTE: In a XyLoc Solo, when used in a unique account environment, the XyLoc Password
(PIN) will synchronize with the user’s unique account password. The Kiosk account is the
only type that will have a XyLoc password that can differ from the user’s system account
password. If it is desired to use at PIN with a unique account, XyLoc 8.3.6 with
must be used. Earlier version of either will not support this functionality.
XSS 4.2.4
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 8 of 62

Getting Started
Using the XyLoc Lock
The XyLoc Lock included in this package is a low power receiver that is connected to the PC
through a USB interface.
Note: Windows 2000/XP users must have local Administrator privileges to complete the
installation.
Installing the XyLoc Lock (USB)
1. Close all open applications.
2. Please wait to attach USB XyLoc lock until prompted by XyLoc software
install wizard.
3. Insert the XyLoc CD into the CD drive.
4. Install the XyLoc System Software. If the Auto Run does not start the CD,
please go to the CD and click on the “Install.exe” file and follow the instructions.
USB Plug
Placement of the XyLoc Lock
XyLoc uses advanced wireless technology to make PC security more convenient for the user.
The proper placement of the XyLoc Lock will ensure that users get the best performance
from XyLoc. For additional guidelines and suggestions, please view the “XyLoc Positioning
Tutorial” included on the installation CD.
Ideal placement is with the face of the Key parallel to the LED on the front of the Lock. The
best performance of the system will be achieved by trying to maintain this positioning while
you are seated at your PC doing your work.
The primary factor in deciding where to place the XyLoc Lock is to determine where the user
will wear the XyLoc Key the majority of the time. The Key can be clipped to a shirt pocket or
belt or worn on a lanyard around the user’s neck.
Once you’ve identified where the Key will be worn, place the Lock at the same height as
where the Key will be when the user is at the PC. You should also make sure that the path
between the Lock and Key is unobstructed (such as obstruction caused by your arm that
might occur while using your mouse or keyboard).
For example, if the user will wear the Key on the left side of the shirt, use the Velcro strip to
secure the Lock to the left side of the user’s monitor at the same height as the Key will be
when the user is seated.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 9 of 62
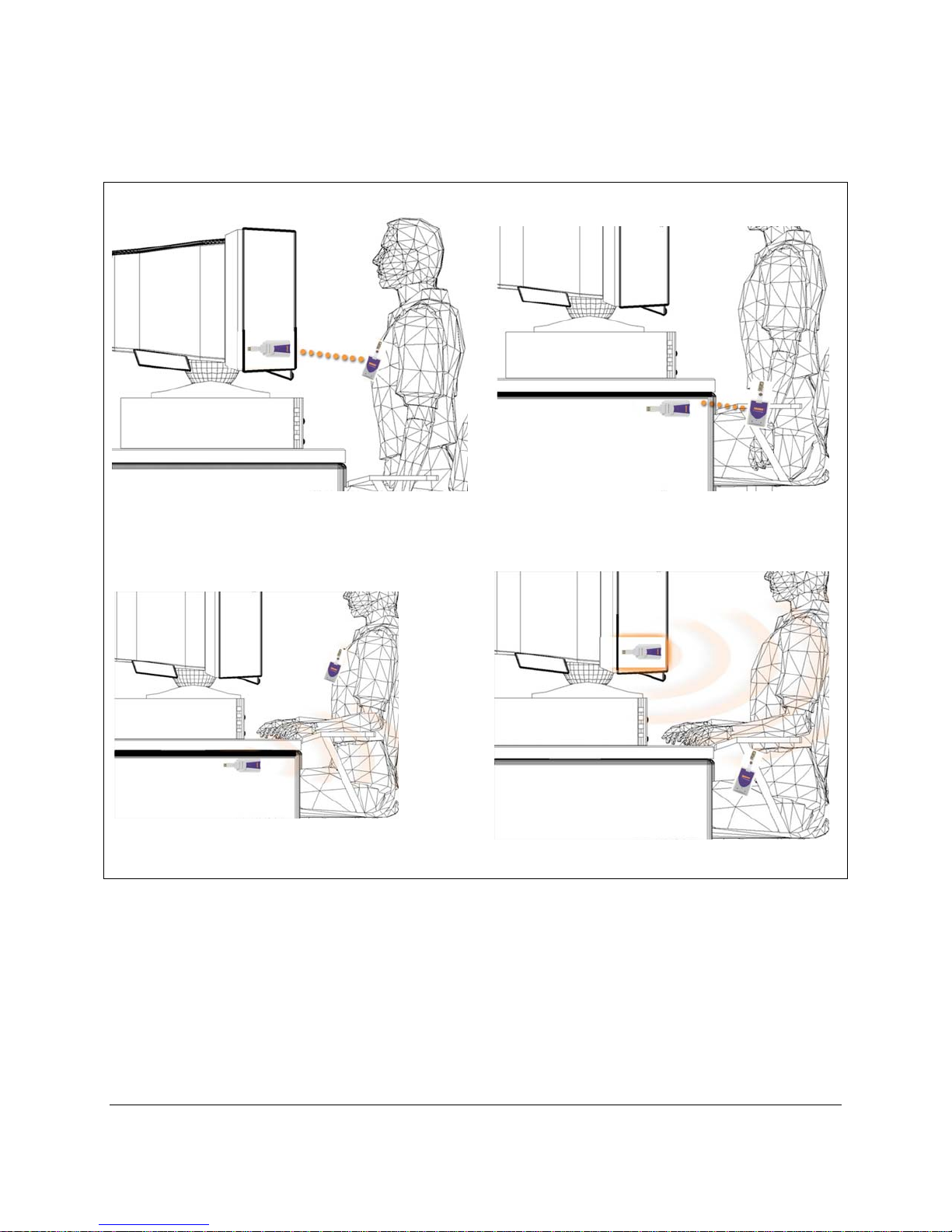
If the user will wear the Key on the right side of the belt, use the Velcro strip to secure the
Lock to the underside of the user’s desk. The Lock should be at the same height as the Key
will be when the user is seated. The user should keep the face of the Key pointing at the LED.
Ideal Lock Placement Acceptable Lock Placement
Less Desirable Lock Placement
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 10 of 62

The XyLoc Lock Status Light
The LED indicator light on the XyLoc Lock has three possible states:
1. Green – The indicator light is green when the computer is unlocked and available for
access.
2. Red – The indicator light is red when the computer is locked or disabled.
3. Off – The indicator light is off if the XyLoc system is not receiving power.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
LED Status Light
Page 11 of 62

Using the XyLoc Key
The XyLoc Key is a low power radio transmitter with a unique non-volatile and noncloneable user identification code.
LED Status Light
ON Button
The KeyCard is powered by single coin cell that last approximately twelve to twenty-four
months. The KeyCard has two switches on its front panel marked “O” and “X”. The “O”
turns the Key ON and “X” manually turns the Key OFF. The Status LED flashes green
when the system is turned ON and red when it is turned OFF. The OFF action requires an
extended depression of the “X” button to turn the Key OFF, but to turn the key ON just press
and release the “O” button.
The KeyCard uses sophisticated power management technology and will automatically turn
OFF approximately 9 hours after it was first turned ON. You may extend this automatic turn
OFF time up to 4 additional hours by pressing the “O” button one time for each additional
hour, any time after the Key has been turned ON.
The Status LED also functions as a battery tester. As long as the LED functions, the
KeyCard has sufficient battery power. The XyLoc software also incorporates a Battery
Voltage Meter with which the user may check the battery life through the XyLoc
configuration software (See the section for Testing the XyLoc Keys). Also, the XyLoc
Security Server (XSS) at any time has a status log that reports when a battery is running low
on battery life. Please review the XSS User Guide for more details.
OFF Button
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 12 of 62

The Key must be in the possession of the user at all ti mes. The XyLoc system provides tools
to help ensure user compliance. XyLoc is capable of identifying a Key that has been left
stationary. The XyLoc system can be configured to automatically secure the workstation,
should a Key be left unattended. This action is also recorded in the Audit Logs.
NOTE: To insert the battery into the KeyCard, place the KeyCard with the XyLoc logo
face down, remove the two retaining screws and slide open the lid. Replace the CR 3032
coin cell with the “+” up.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 13 of 62
Installing the XyLoc Software
The XyLoc software controls the operation of the Lock/Key and their interaction with the
PC’s operating system. The software offers flexible configuration
desktop preferences to meet the users varying needs. Installation is accomplished via a
simple-to-use wizard.
Except where noted, the following instructions apply to all supported Microsoft
Windows systems.
NOTE: Windows 2000/XP users must have local Administrator privileges to complete
the installation.
NOTE: The Windows XPe version of the XyLoc client only supports English. The
other language versions have been removed to keep the install package small enough to
be installed on a Windows XPe Thin Client device.
NOTE: In version 8.2.4 the installation program was changed to an MSI based
installer. This has changed some of the installation process slightly as well as the
screens that are displayed. The instructions below are for this new installer, except
where indicated.
1. Exit any applications that are currently running.
options and selectable
2. Place the XyLoc CD-ROM into the CD-ROM drive. Choose Install XyLoc Software.
3. If the installer does not automatically launch, use either My Computer or Windows
Explorer to select the CD-ROM drive, and run install.exe to execute the Installation
Wizard and then follow the Wizard’s instructions.
4. Select the language for the installation.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 14 of 62
5. Click Next on the welcome screen to continue with installation.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 15 of 62
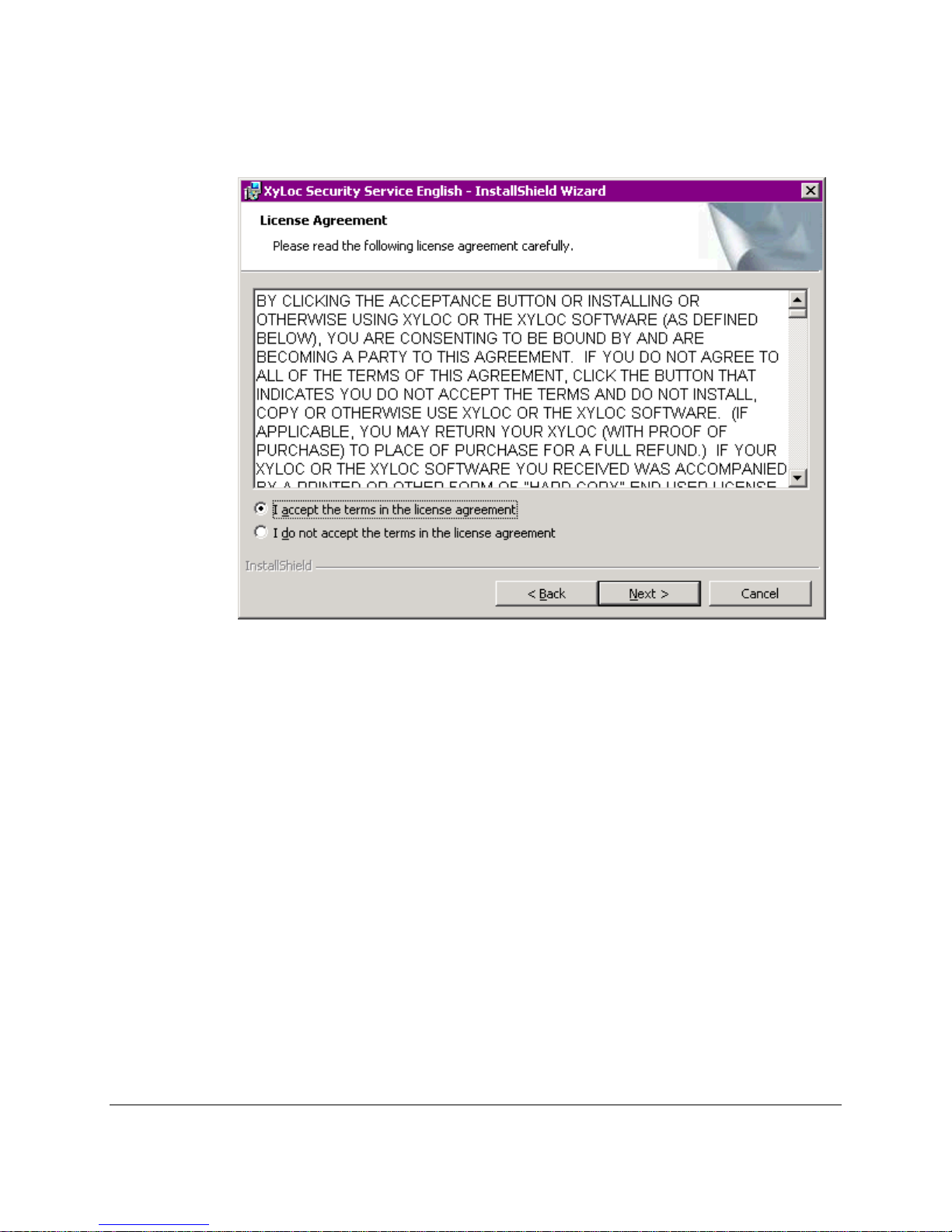
6. Please review the terms of the Software License Agreement. If you accept all of the
terms of the Software License Agreement, click Yes, and the installation will continue.
If you do not accept all of the terms of the Software License Agreement, click No to
cancel the installation process.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 16 of 62
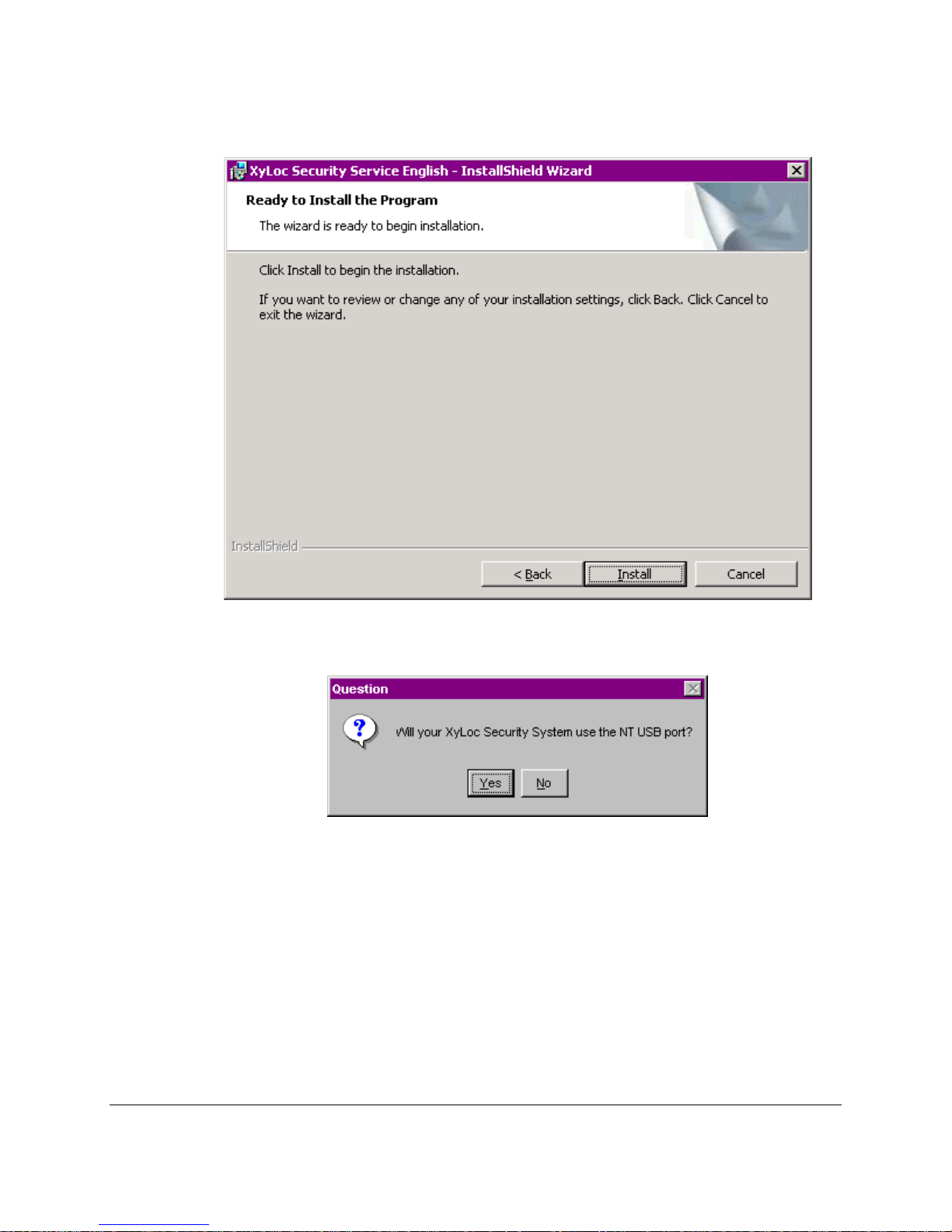
7. Once the program is ready to install the files, the “Ready to Install” window will display.
Click “Install” on this screen when you are ready to install (NOTE: This screen does not
come up in 8.2.3 and earlier)
8. For NT4 users, the Question window will be presented. Select Yes when using the USB
lock.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 17 of 62
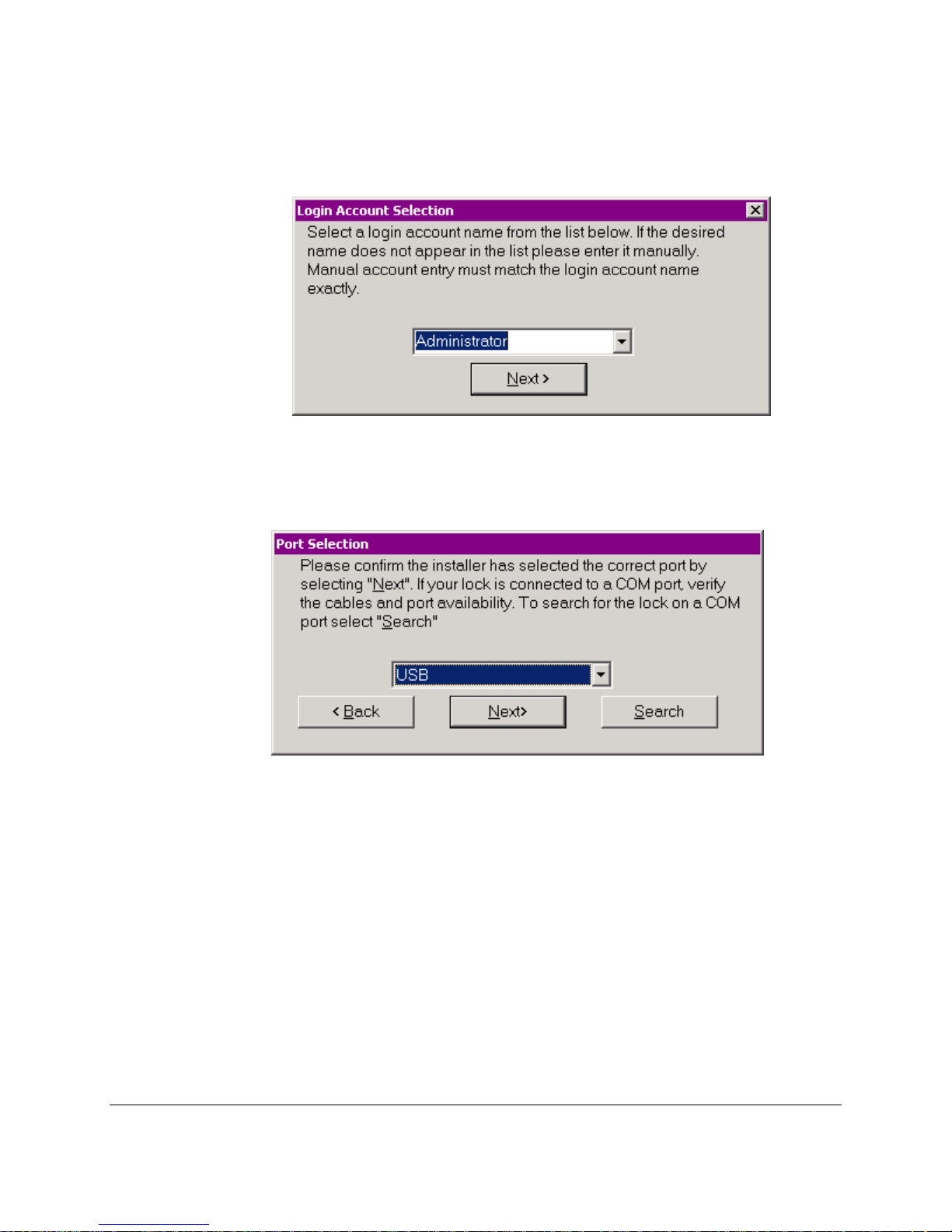
9. Login Account Selection: Select the desired user name from the list. This list is created
by examining the Users database on the PC. If XyLoc is to be configured for a network
logon account, type the account name here, being careful to enter the name exactly as it
appears for your normal logon. Please create a user via the Users control panel in
Windows.
10. Lock Identification: XyLoc will attempt to find the port to which the Lock is attached.
Click OK to continue. On a new installation, the Lock should not be connected yet,
therefore XyLoc will not find the Lock. The Port Selection screen will appear. Please
confirm that the correct port has been selected and correct it if necessary. Click “Next”.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 18 of 62
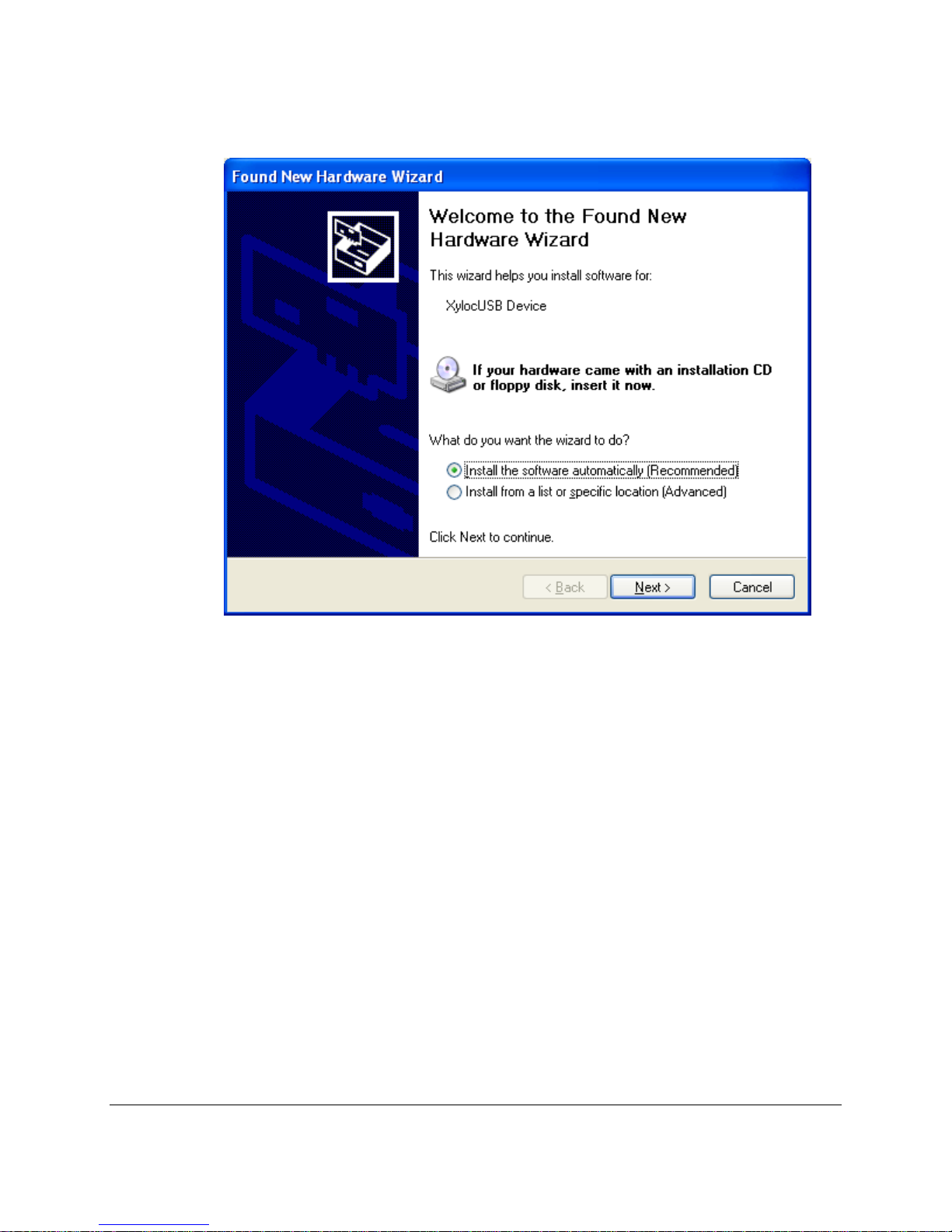
11. If you are using the USB version, connect the lock to the computer at this time. NOTE:
On Windows XP, the Found New Hardware Wizard will appear. Leave the default for
“Install the software automatically (Recommended)” and click Next.
Ensure Technologies – User’s Guide for XyLoc Client ver 8.x.x
Drawing#: 510-0100-003 Drawing Rev: 0.08 Rev Date: 04-25-2006
Page 19 of 62
 Loading...
Loading...