Page 1

ENUWI-XAN3
Wireless – N150 Adapter
User’s Manual
Page 2

Table of Contents
1 INTRODUCTION............................................................................................................................... 3
FEATURES & BENEFITS ............................................................................................................................... 3
PACKAGE CONTENTS .................................................................................................................................. 4
USB ADAPTER DESCRIPTION ..................................................................................................................... 4
SYSTEM REQUIREMENTS ............................................................................................................................ 5
APPLICATIONS ............................................................................................................................................ 5
NETWORK CONFIGURATION ....................................................................................................................... 6
2 ENUWI-XAN3 USB ADAPTER FOR WINDOWS® (XP, 7 & VISTA®)...................................... 7
BEFORE YOU BEGIN ................................................................................................................................... 8
INSTALLING DRIVERS ................................................................................................................................. 8
PROFILES .................................................................................................................................................. 13
INFRASTRUCTURE MODE .......................................................................................................................... 13
AD-HOC MODE ......................................................................................................................................... 14
AUTHENTICATION AND SECURITY ............................................................................................................ 16
WEP Encryption ................................................................................................................................. 16
WPA, WPA2 Authentication & TKIP, AES Encryption ....................................................................... 17
WPA-PSK Authentication & TKIP, AES Encryption .......................................................................... 17
LEAP Authentication .......................................................................................................................... 18
802.1x with PEAP ............................................................................................................................... 19
PEAP Authentication with EAP/TLS Smartcard ................................................................................. 19
802.1x with TTLS with EAP-MD5, MS-CHAP, MS-CHAPv2 ............................................................. 20
802.1x CA Server ................................................................................................................................ 21
NETWORK (SITE SURVEY) ........................................................................................................................ 23
ADVANCED CONFIGURATION ................................................................................................................... 25
WPS™ ..................................................................................................................................................... 25
UNINSTALL THE DRIVERS & CLIENT UTILITY .......................................................................................... 27
3 ENUWI-XAN3 USB ADAPTER FOR MAC™ OS X .................................................................... 31
INSTALLING THE DRIVERS ........................................................................................................................ 31
PROFILES .................................................................................................................................................. 33
INFRASTRUCTURE MODE .......................................................................................................................... 34
AD-HOC MODE ......................................................................................................................................... 36
AUTHENTICATION AND SECURITY ............................................................................................................ 37
WEP Encryption ................................................................................................................................. 37
WPA-PSK Authentication & TKIP, AES Encryption .......................................................................... 38
LINK STATUS ............................................................................................................................................ 39
SITE SURVEY ............................................................................................................................................ 40
STATISTICS ............................................................................................................................................... 41
ADVANCED CONFIGURATION ................................................................................................................... 41
WPS™ ..................................................................................................................................................... 42
ABOUT ...................................................................................................................................................... 46
APPENDIX A – GLOSSARY .................................................................................................................... 47
APPENDIX B – SPECIFICATIONS ........................................................................................................ 59
APPENDIX C – FCC INTERFERENCE STATEMENT ....................................................................... 60
2
Page 3

INTRODUCTION
The ENUWI-XAN3 high-speed wireless USB 2.0 client adapter is the most
convenient way to let you put a desktop or a notebook computer almost anywhere
without the hassle of running network cables. Now there will be no more drilling holes
and eyesore exposed cables. Once you are connected, you can do anything, just like
the wired network. This USB client adapter operates seamlessly in 2.4GHz
frequency spectrum supporting the 802.11b, 802.11g, and 802.11n wireless
standards. It’s the best way to add wireless capability to your existing wired network
or simply surf the web.
To protect your wireless connectivity, the high-speed ENUWI-XAN3 Wireless N-150
USB 2.0 client adapter can encrypt all wireless transmissions through 64 / 128-bit
WEP, WPA, WPA-PSK and WPA-AES encryption and authentication allowing you to
experience the most secured wireless connectivity available.
The Encore’s ENUWI-XAN3 802.11n N-150 Adapter implements a Wireless N-Draft
2.0 technology which extremely improves wireless signal for your computer than the
existing wireless 802.11g technology. The incredible speed of the ENUWI-XAN3
802.11n Wireless USB adapter makes heavy traffic networking activities more
flexible. Enjoy the racing speed of wireless connection.
Adding an Encore’s ENUWI-XAN3 Wireless N-150 Adapter to your Mac or PC
Notebook or Computer, it provides an excellent performance and cost-effective
solution for doing media-centric activities such as streaming video, gaming, and
enhances the QoS (WMM) without any reduction of performance. It extends 3 times
network coverage and boosts 6 times transmission throughput than the existing
802.11g products. Advanced power management and low power consumption are
among the added features of the ENUWI-XAN3.
For more security-sensitive application, the ENUWI-XAN3 supports Hardware-based
IEEE 802.11i encryption/decryption engine, including 64-bit/128-bit WEP, TKIP, and
AES. Also, the ENUWI-XAN3 supports the Wi-Fi alliance WPA and WPA2 encryption
and is Cisco CCX V1.0, V2.0 and V3.0 compliant.
3
Page 4
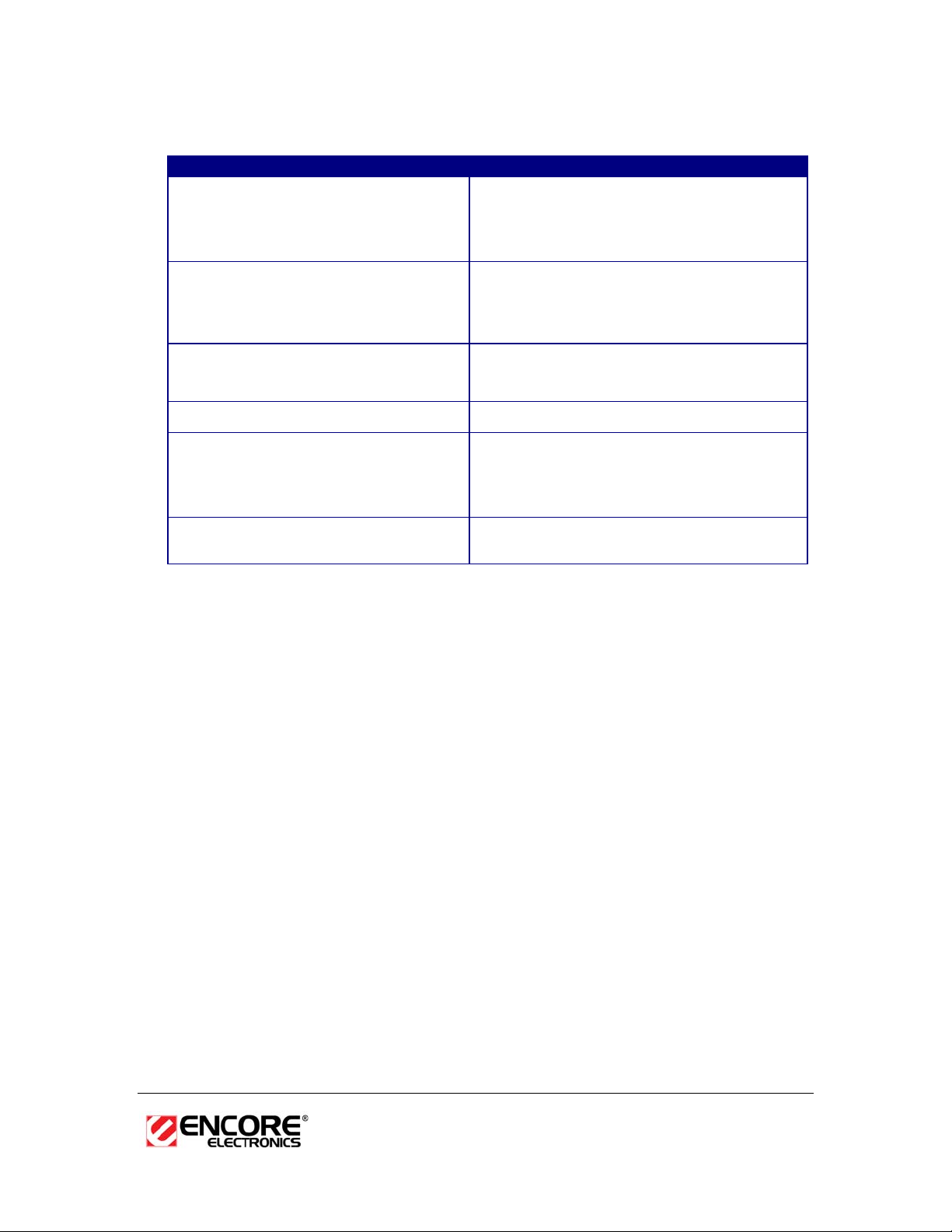
Features & Benefits
Features Benefits
Racing Spee d up to 150Mbps data rate
Enjoy the Internet connection in crazy-fast
(2.4GHz 802.11n technology)
Advanced power management
WPA/WPA2 (IEEE 802.11i), WPA-PSK,
WPA2-AES, WEP 64/128 Supported
Support 1Tx-1Rx Radio
WMM (IEEE 802.11e) standard support
USB 2.0 / 1.1
Package Contents
speed, without the hassles of strangle
wires.
Low power consumption. A useful feature
for notebooks on battery mode that
makes longer battery life and still surf the
internet
Powerful data security.
With Intelligent Antenna enabled
Wireless Multimedia Enhancements Quality
of Service supported (QoS) / enhanced
power saving for Dynamic Networking
USB 2.0 interface and backward
compatible with USB 1.1
Open the package carefully, and make sure that none of the items listed below are
missing. Do not discard the packing materials, in case of return; the unit must be
shipped in its original packaging.
h One ENUWI-XAN3 Wireless N-150 Adapter
h One CD-ROM with Driver, Utility Software and User Manual Included
h One Quick Installation Guide
USB Adapter Description
The USB adapter is a standard USB adapter that fits into any Type A USB interface.
The USB adapter has one LED indicator and one replaceable R-SMA dipole external
Antenna.
4
Page 5
System Requirements
The followings are the minimum system requirements for ENUWI-XAN3
h PC/AT or Mac compatible computer with available USB interface.
h Windows® 2000/XP/Windows Vista® or Mac™ OS X operating system.
h 30 MB of free disk space for installing the USB adapter software driver and
software utility program.
Applications
The wireless LAN products are easy to install and highly efficient. The following list
describes some of the many applications made possible through the power and
flexibility of wireless LANs:
a) Difficult to wire environments
There are many situations where wires cannot be laid easily. Historic
buildings, older buildings, open areas and across busy streets make the
installation of wired LANs either impossible or very expensive.
b) Temporary workgroups
Consider situations in parks, athletic arenas, exhibition centers, disasterrecovery, temporary offices and construction sites where one wants a
temporary WLAN established and removed.
c) The ability to access real-time information
5
Page 6

Doctors/nurses, point-of-sale employees, and warehouse workers can
access real-time information while dealing with patients, serving
customers and processing information.
d) Frequently changed environments
Show rooms, meeting rooms, retail stores, and manufacturing sites where
frequently rearrange the workplace.
e) Small Office and Home Office (SOHO) networks
SOHO users need a cost-effective, easy and quick installation of a small
network.
f) Wireless extensions to Ethernet networks
Network managers in dynamic environments can minimize the overhead
caused by moves, extensions to networks, and other changes with
wireless LANs.
g) Wired LAN backup
Network managers implement wireless LANs to provide backup for
mission-critical applications running on wired networks.
h) Training or Educational facilities
Training sites at corporations and students at universities use wireless
connectivity to ease access to information, information exchanges, and
learning.
Network Configuration
To better understand how the wireless LAN products work together to create a
wireless network, it might be helpful to depict a few of the possible wireless LAN PC
card network configurations. The wireless LAN products can be configured as:
a) Ad-hoc (or peer-to-peer) for departmental or SOHO LANs.
b) Infrastructure for enterprise LANs.
a) Ad-hoc (peer-to-peer) Mode
This is the simplest network configuration with several computers
equipped with the Network Interface Cards that form a wireless network
whenever they are within range of one another. In ad-hoc mode, each
client is peer-to-peer, would only have access to the resources of the
other client and does not require an access point. This is the easiest and
least expensive way for the SOHO to set up a wireless network. The
image below depicts a network in an ad-hoc mode.
6
Page 7
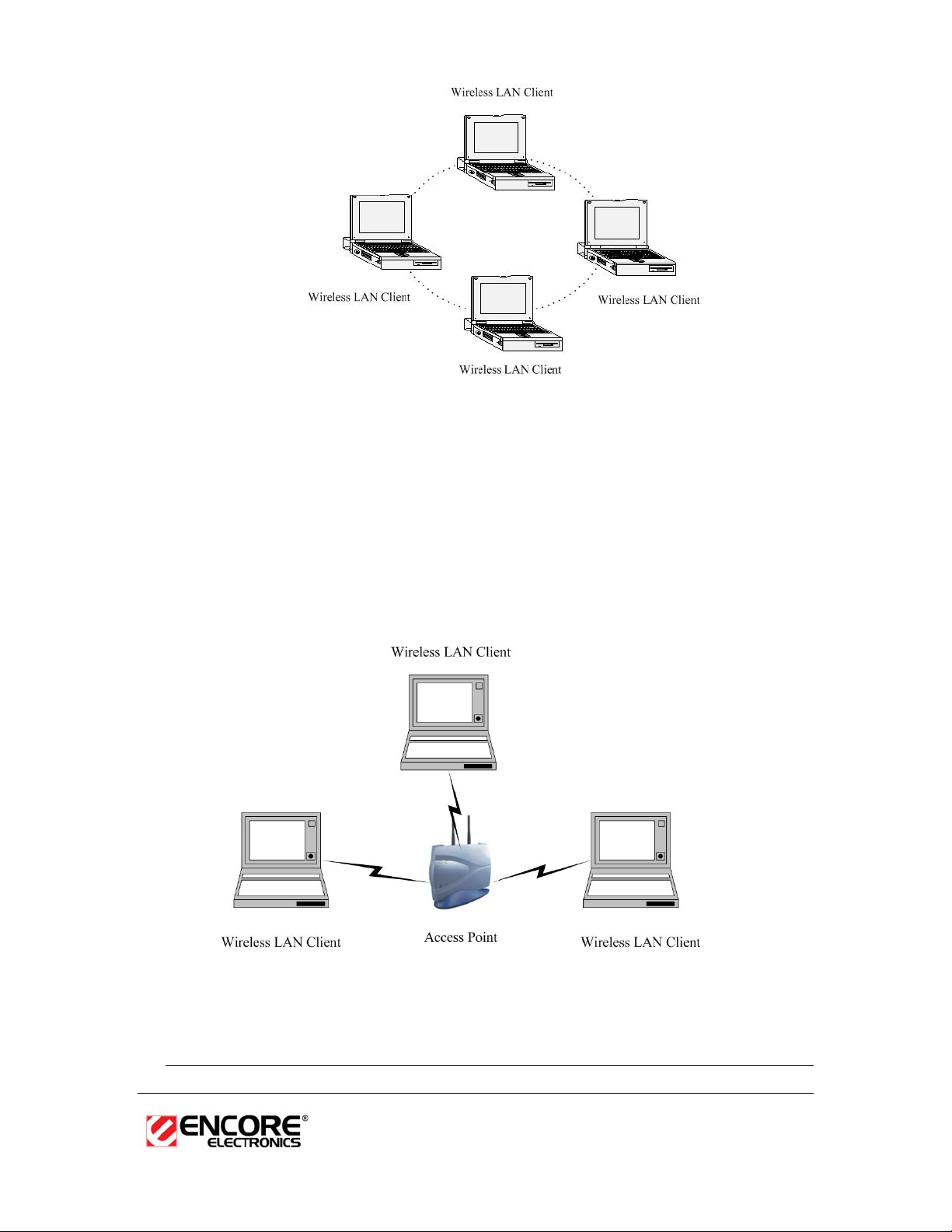
b) Infrastructure Mode
The infrastructure mode requires the use of an Access Point (AP) or a a
router. In this mode, all wireless communication between two computers
has to be via the AP. It doesn’t matter if the AP is stand-alone or wired to
an Ethernet network. If used in stand-alone, the AP can extend the range
of independent wireless LANs by acting as a repeater, which effectively
doubles the distance between wireless stations. The image below
depicts a network in infrastructure mode.
ENUWI-XAN3 for Windows® XP, Windows® 7 &
®
Windows Vista
7
Page 8

Before You Begin
During the installation, the Windows XP setup process may need to copy some
systems files from its original Windows installation CD. It is highly advisable to have
your Windows XP original setup disc handy in case the installation steps would ask
for system files. Some Windows XP computers may have the necessary installation
system files archived on the hard disk located in C:\WINDOWS \OPTIONS\CABS
directory. This archived may be hidden to you. If you are unsure of this, have the
Windows setup disc ready before starting the installation process.
Software Driver Installation
Follow the steps below in order to install the ENUWI-XAN3 software drivers:
1. Insert the ENUWI-XAN3 CD-ROM provided in the package. The setup should
run automatically and you should see a pop up welcome screen in a few
seconds then will disappear and replace with the ENUWI-XAN3 Main Menu
screen. If the setup does not run automatically, you must manually select the
setup.exe file from the CD-ROM drive.
NOTE: Do not insert the ENUWI-XAN3 USB adapter to the USB port at this point. You will
be asked to do so later on in this installation procedure.
NOTE: A Welcome screen will pop up for a few seconds and will disappear and
will be replace with the ENUWI-XAN3 Main menu screen seen below.
8
Page 9

2. Click on Windows Driver icon to start the installation process.
9
Page 10
3. Click on the Install button to begin the installation.
4. Wait for a few seconds until the driver and client utility is installed.
10
Page 11
5. The installation is complete. Click on the Finish button.
11
Page 12
6. Depends on your system. You will be asked to restart your computer. Click to
select “Yes, I want to start my computer now.” Then click the “Finish” button.
7. After the reboot, carefully insert the ENUWI-XAN3 USB adapter into the
available USB port. Windows will automatically detect and install the new
hardware.
8. A new Encore
the picture above. Right click on the
icon is now added to the task bar or system tray similar to
icon and then click on “Launch
Config Utilities”. You can also launch the Encore Wireless Utility software by
going to START, then move your mouse over to “All Programs”, move your
mouse over to “Encore Wireless” then click on “Encore Wireless Utility:”
Note: Click on Use Zero Configuration as Configuration Utility if you would
like to use Windows Zero Configuration (Windows XP only).
12
Page 13
Profiles
The Profile tab is used to store the settings of multiple Access Points such as
home, office, café, etc. When adding a profile you are required to enter a profile
name and SSID as well as configure the power-saving mode, network type,
RTS/fragmentation threshold and encryption/authentication settings. A profile
can be configured as Infrastructure or Ad-hoc mode. The configuration settings
for each mode are described below.
Infrastructure Mode
The infrastructure mode requires the use of an Access Point (AP). In this mode,
all wireless communication between two computers has to be via the AP. It
doesn’t matter if the AP is stand-alone or wired to an Ethernet network. If used in
stand-alone, the AP can extend the range of independent wireless LANs by
acting as a repeater, which effectively doubles the distance between wireless
stations.
13
Page 14
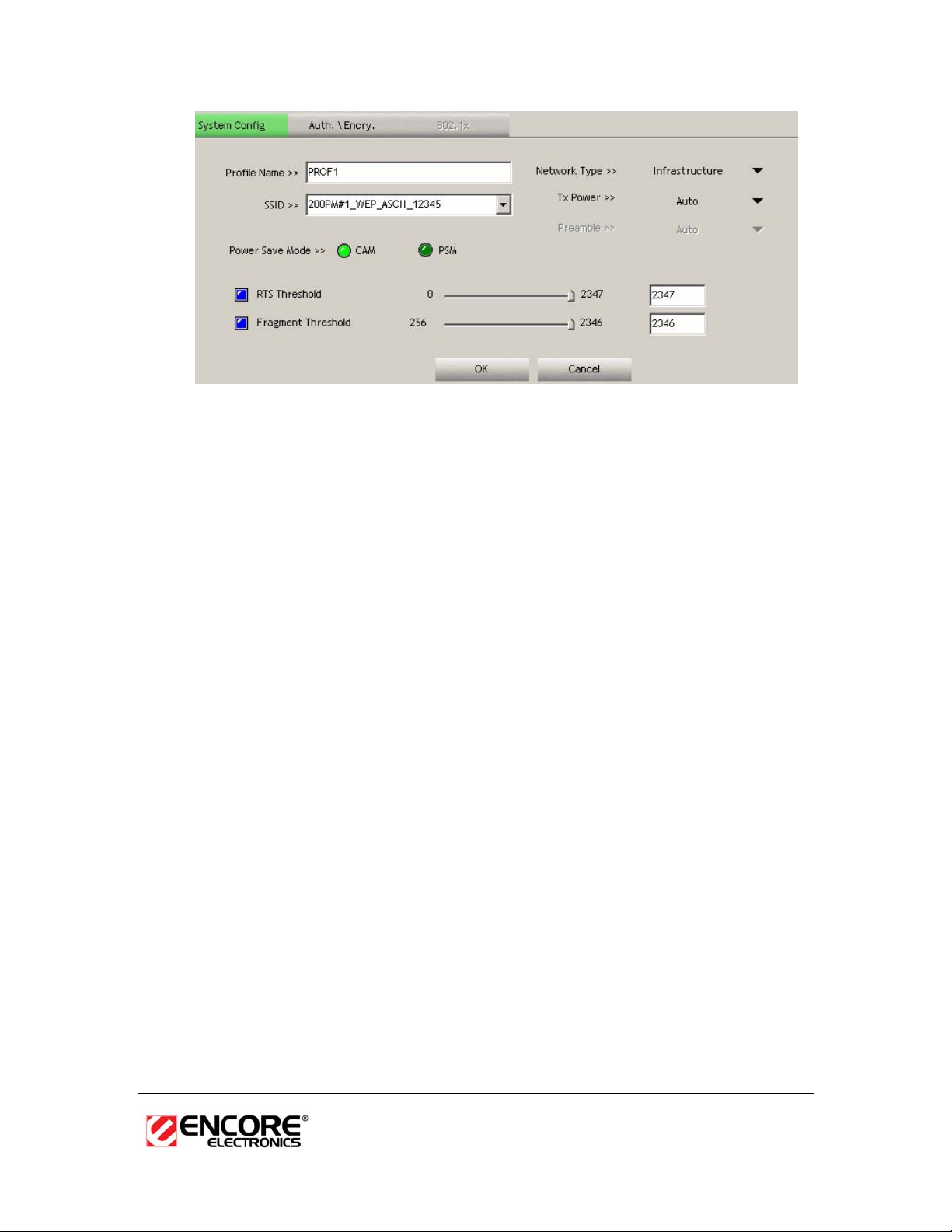
h Profile: Enter a name for the profile; this does not need to be the same
as the SSID.
h SSID: Enter the SSID of the network or select one from the drop-down
list. The SSID is a unique name shared among all points in your wireless
network. The SSID must be identical for all points in the network, and is
case-sensitive.
h PSM: Select a power saving mode (PSM) option.
o CAM (Continuously Active Mode): Select this option if your
notebook is always connected to the power supply.
o PSM (Power Saving Mode): Select this option if your notebook
uses its battery power. This option minimizes the battery usage
while the network is idle.
h Network Type: Select Infrastructure from the drop-down list.
h TX Power: Select a transmit power from the drop-down list. If your
notebook is connected to external power then select 100% or auto, if
not, select one of the lower values for power saving.
h RTS Threshold: Place a check in this box if you would like to enable
RTS Threshold. Any packet in the RTS/CTS handshake larger than the
specified value (bytes) will be discarded.
h Fragment Threshold: Place a check in this box if you would like to
enable Fragment Threshold. Any packet larger than the specified value
(bytes) will be discarded.
h Click on the OK button to save the changes.
Ad-hoc Mode
This is the simplest network configuration with several computers equipped with
the wireless Network Interface Cards that form a wireless network whenever they
are within range of one another. In ad-hoc mode, each client is peer-to-peer,
would only have access to the resources of the other client and does not require
an access point. This is the easiest and least expensive way for the SOHO to set
up a wireless network.
14
Page 15
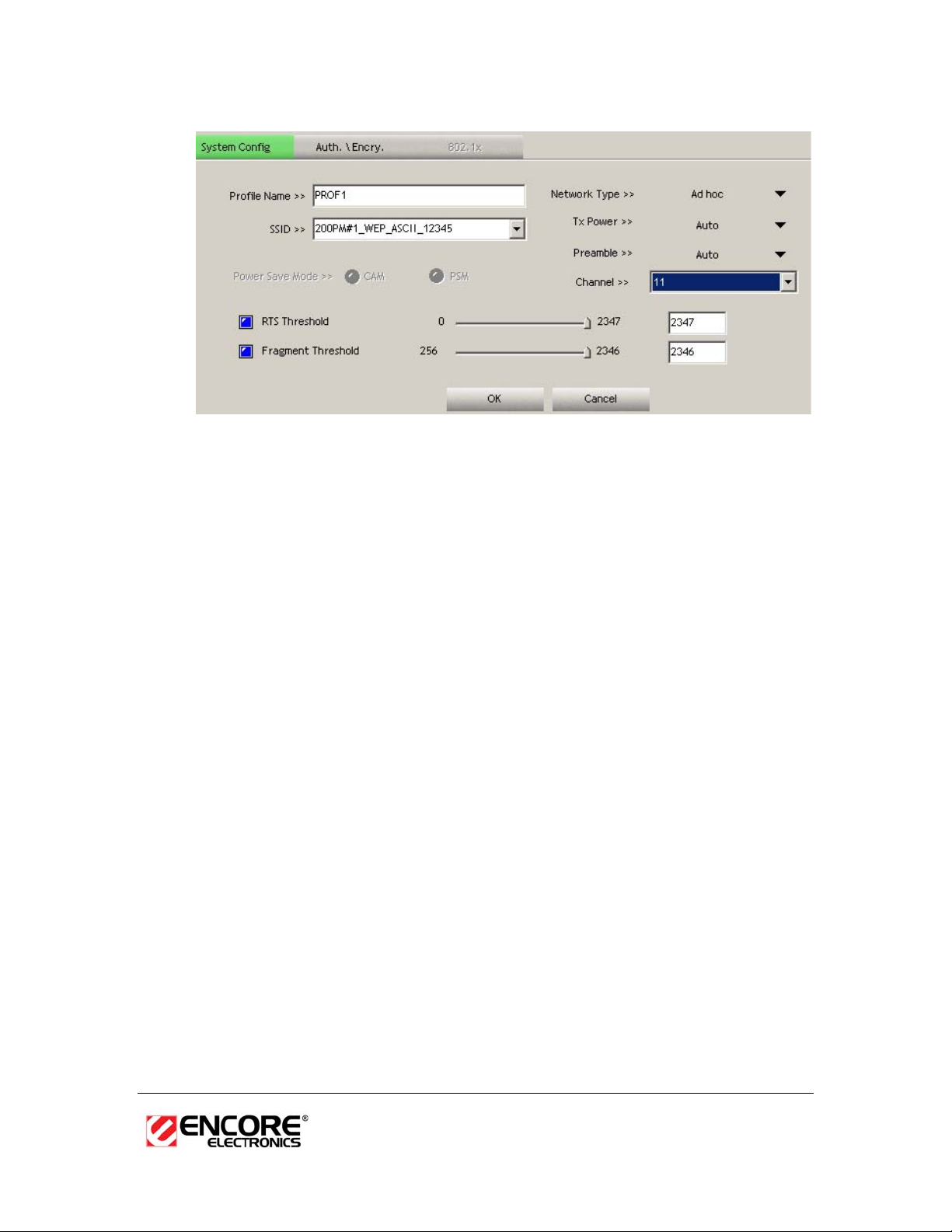
h Profile: Enter a name for the profile; this does not need to be the same
as the SSID.
h SSID: Enter the SSID of the network or select one from the drop-down
list. The SSID is a unique name shared among all points in your wireless
network. The SSID must be identical for all points in the network, and is
case-sensitive.
h Network Type: Select Ad-hoc from the drop-down list.
h Preamble: Select Auto from the drop-down list, unless you are aware of
the preamble type (long or short) used in each station.
h Channel: Displays the channel number of the Access Point.
h TX Power: Select a transmit power from the drop-down list. If your
notebook is connected to external power then select 100% or auto, if
not, select one of the lower values for power saving.
h Click on the OK button to save the changes.
15
Page 16
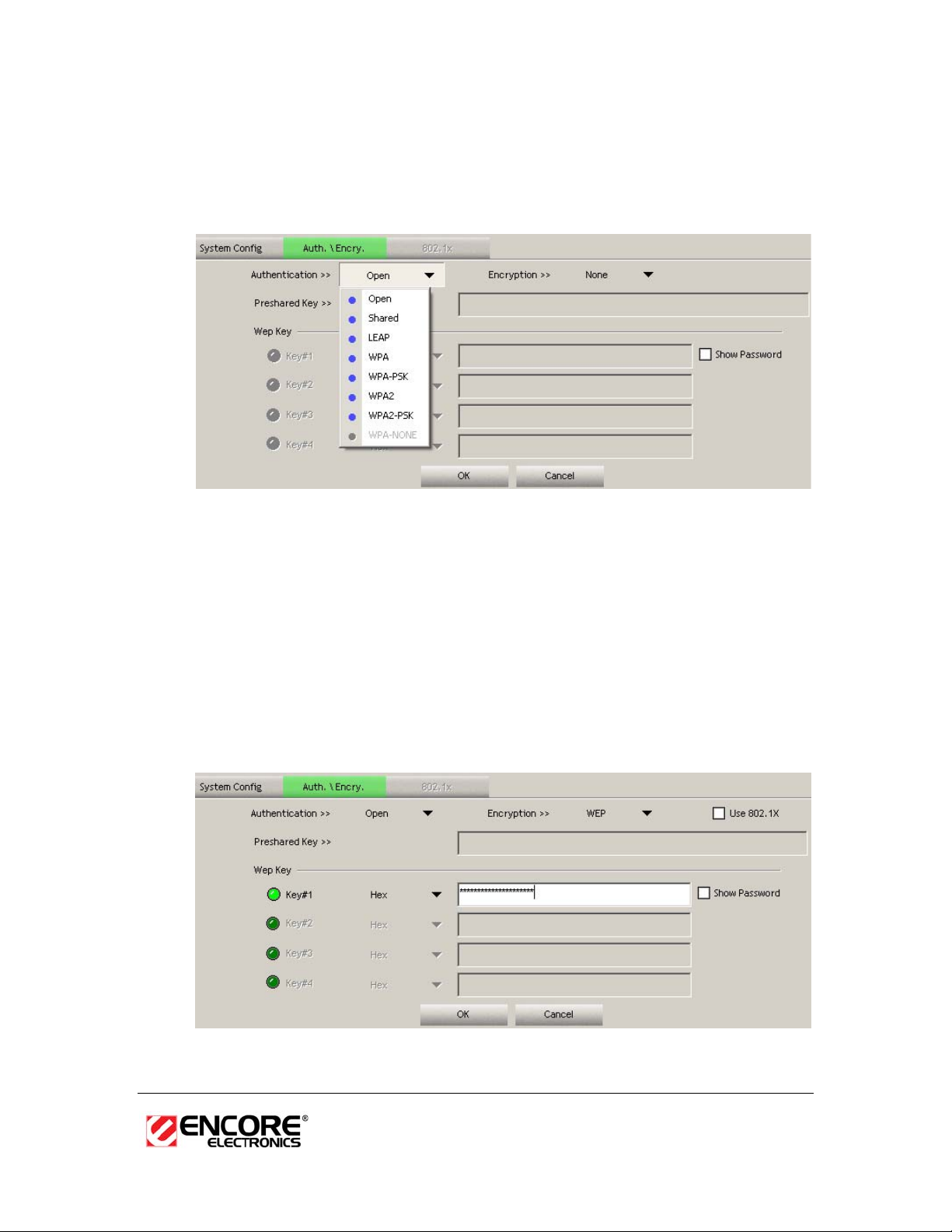
Authentication and Security
The Security tab allows you to configure the authentication and encryption
settings such as: WEP, WPA, WPA-PSK, WPA2, and 802.1x. Each security
option is described in detail below.
WEP Encryption
The WEP tab displays the WEP settings. Encryption is designed to make the
data transmission more secure. You may select 64 or 128-bit WEP (Wired
Equivalent Privacy) key to encrypt data (Default setting is Disable). WEP
encrypts each frame transmitted from the radio using one of the Keys from a
panel. When you use WEP to communicate with the other wireless clients, all the
wireless devices in this network must have the same encryption key or pass
phrase. The following information is included in this tab, as the image depicts
below.
h Authentication Type: Select Open or Shared from the drop-down list.
h Encryption: Select WEP from the drop-down list.
16
Page 17
h WEP Key (Hex or ASCII): Type a character string into the field. For 64-bit
enter 5 alphanumeric or 10 hexadecimal characters. For 128-bit enter 13
alphanumeric or 26 hexadecimal characters.
h Click on the Apply button to save the changes.
h Show Password check box. If you want to make sure the accuracy of
password you type, click the Show Password box to check it.
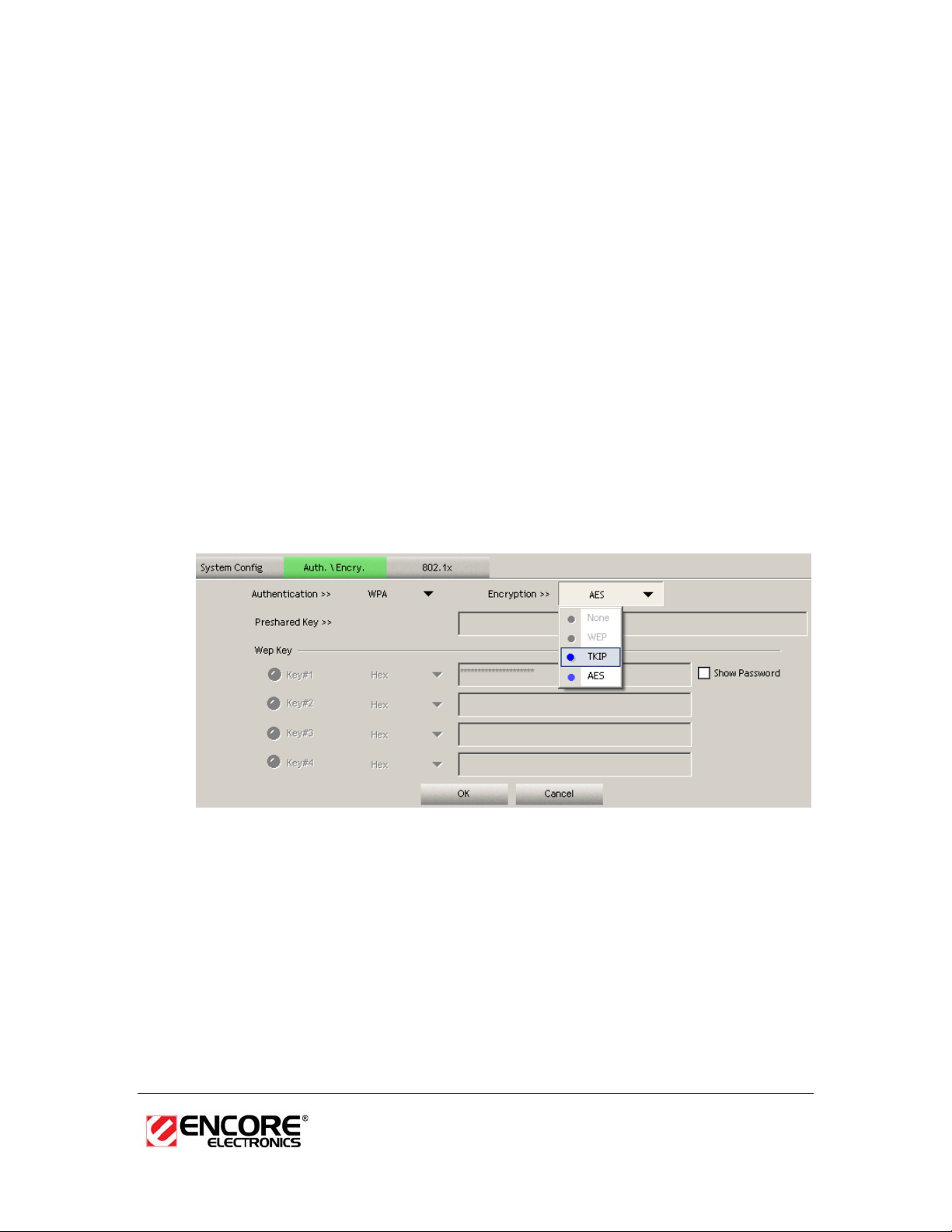
WPA, WPA2 Authentication & TKIP, AES Encryption
WPA (Wi-Fi Protected Access) was designed to improve upon the security
features of WEP (Wired Equivalent Privacy). This is used along with 802.1x
security setting. The technology is designed to work with existing Wi-Fi products
that have been enabled with WEP. WPA provides improved data encryption
through the Temporal Integrity Protocol (TKIP), which scrambles the keys using a
hashing algorithm and by adding an integrity-checking feature which makes sure
that keys haven’t been tampered with. EAP (Extensible Authentication Protocol)
is an extension to the PPP protocol that enables a variety of authentication
protocols to be used. It passes through the exchange of authentication messages,
allowing the authentication software stored in a server to interact with its
counterpart in the client.
h Authentication Type: Select WPA or WPA2 from the drop-down list.
h Encryption: Select TKIP or AES from the drop-down list.
h Click on the Apply button to save the changes.
h Show Password check box. If you want to make sure the accuracy of
password you type, click the Show Password box to check it.
WPA-PSK Authentication & TKIP, AES Encry ption
WPA – PSK (Pre-shared Key) is used in a Pre Shared Key mode that does not
require an authentication server. Access to the Internet and the rest of the
wireless network services is allowed only if the pre-shared key of the computer
matches that of the Access Point. This approach offers the simplicity of the WEP
17
Page 18

key, but uses stronger TKIP encryption. EAP (Extensible Authentication Protocol)
is an extension to the PPP protocol that enables a variety of authentication
protocols to be used. It passes through the exchange of authentication messages,
allowing the authentication software stored in a server to interact with its
counterpart in the client.
h Authentication Type: Select WPA-PSK or WPA2-PSK from the drop-down
list.
h Encryption: Select TKIP or AES from the drop-down list.
h WPA Preshared key: Enter a pass phrase which is between 8 and 32
characters long.
h Click on the Apply button to save the changes.
h Show Password check box. If you want to make sure the accuracy of
password you type, click the Show Password box to check it.
LEAP Authentication
LEAP (Lightweight Extensible Authentication Protocol) also known as CiscoWireless EAP provides username/password-based authentication between a
wireless client and a RADIUS server. LEAP is one of several protocols used with
the IEEE 802.1X standard for LAN port access control. LEAP also delivers a
session key to the authenticated station, so that future frames can be encrypted
with a key that is different than keys used by others sessions. Dynamic key
delivery eliminates one big vulnerability; static encryption keys that are shared by
all stations in the WLAN. EAP (Extensible Authentication Protocol) is an
extension to the PPP protocol that enables a variety of authentication protocols
to be used. It passes through the exchange of authentication messages, allowing
the authentication software stored in a server to interact with its counterpart in the
client
18
Page 19

h Authentication Type: Select LEAP from the drop-down list.
h Identity: Enter the user name.
h Password: Enter the password.
h Domain: Enter a domain name.
h Encryption: Select WEP, WPA-TKIP or WPA2-AES encryption.
h Click on the OK button to save the changes.
802.1x with PEAP
802.1X provides an authentication framework for wireless LANs allowing a user
to be authenticated by a central authority. 802.1X uses an existing protocol called
EAP. EAP (Extensible Authentication Protocol) is an extension to the PPP
protocol that enables a variety of authentication protocols to be used. It passes
through the exchange of authentication messages, allowing the authentication
software stored in a server to interact with its counterpart in the client.
PEAP Authentication with EAP/TLS Smartcard
EAP/TLS Smartcard provides for certificate-based and mutual authentication of
the client and the network. It relies on client-side and server-side certificates to
perform authentication and can be used to dynamically generate user-based and
session-based WEP keys to secure subsequent communications between the
WLAN client and the access point.
19
Page 20

h Authentication Type: Select PEAP from the drop-down list.
h Protocol: If your network uses TLS or Smart Card to authenticate its users,
select TLS/Smartcard from the drop down list. TLS (Transport Layer
Security) is an IETF standardized authentication protocol that uses PKI
(Public Key Infrastructure) certificate-based authentication of both the client
and authentication server.
h Identity: Enter the user name.
h Click on the OK button to save the changes.
802.1x with TTLS with EAP-MD5, MS-CHAP, MS-CHAPv2
802.1X provides an authentication framework for wireless LANs allowing a user
to be authenticated by a central authority. 802.1X uses an existing protocol called
EAP. EAP (Extensible Authentication Protocol) is an extension to the PPP
protocol that enables a variety of authentication protocols to be used. It passes
through the exchange of authentication messages, allowing the authentication
software stored in a server to interact with its counterpart in the client. TLS
(Transport Layer Security) is an IETF standardized authentication protocol that
uses PKI (Public Key Infrastructure) certificate based authentication of both the
client and authentication server.
20
Page 21

h Authentication Type: Select TTLS from the drop-down list.
h Protocol: Select EAP-MSCHAP v2, MS-CHAP, or CHAP from the drop-
down list.
h Identity: Enter the user name.
h Password: Enter the password.
h Click on the OK button to save the changes.
802.1x CA Server
Depending on the EAP in use, only the server or both the server and client may
be authenticated and require a certificate. Server certificates identify a server,
usually an authentication or RADIUS server to clients. Most EAPs require a
certificate issued by a root authority or a trusted commercial Certificate Authority.
h Use certificate chain: Place a check in this to enable the certificate use.
h Certificate issuer: Select the Certification Authority from the drop-down list.
h Allow intermediate certificates: During tunnel creation the client must
verify the server’s certificate. When checking this certificate the signature
is verified against a list of trusted certificate authorities. If this parameter is
true then the client will also accept a signature from a trusted intermediate
21
Page 22

certificate authority, otherwise it will not.
h Server name: Enter the server name if not selected from the existing drop-
down list above.
h Click on the OK button to save the changes.
22
Page 23

Network (Site Survey)
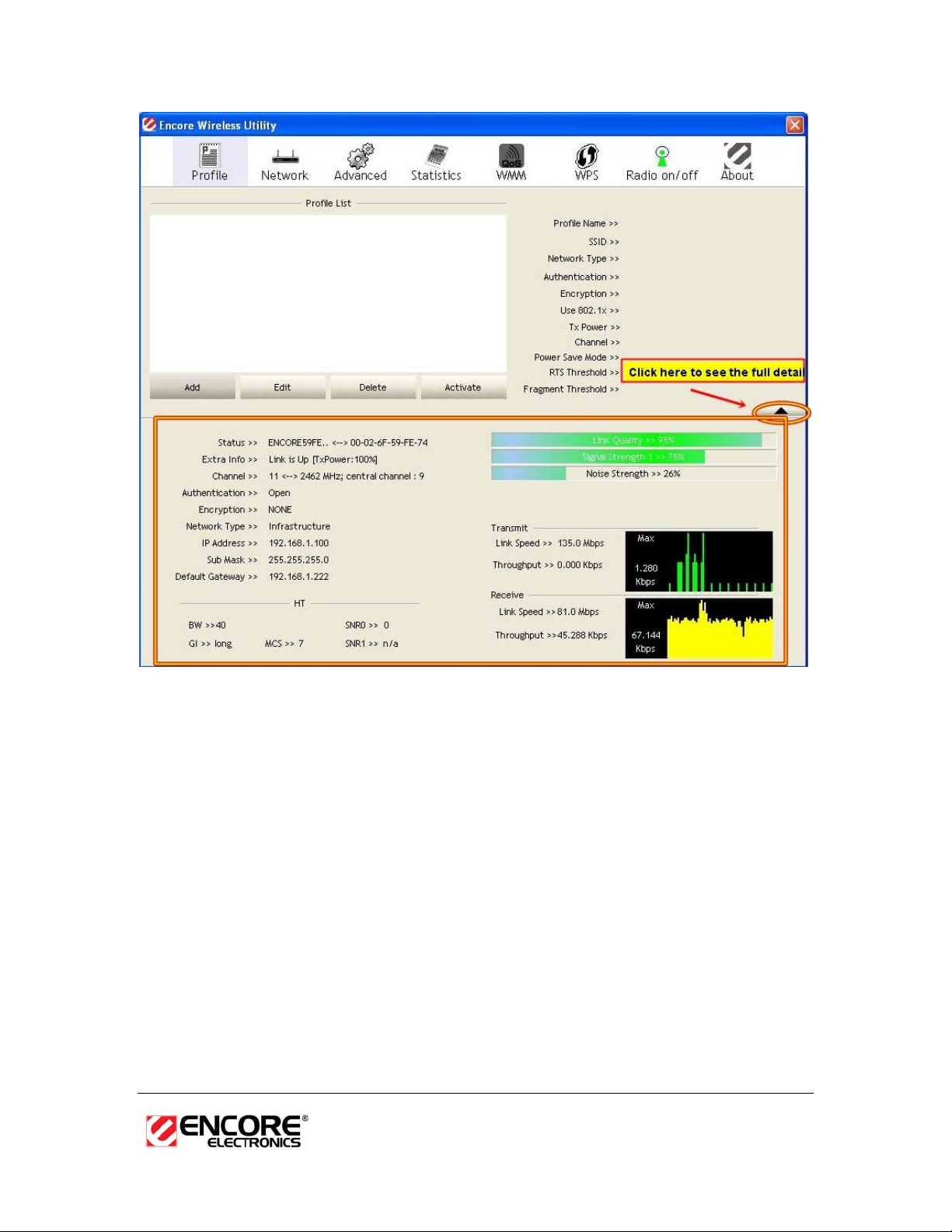
The Network tab displays a list of Access Points and Stations in the area, and
allows you to connect to a specific one. The following information is included in
this tab, as the image depicts below.
The information is displayed in the following order: SSID, MAC, Channel,
Mode, Security, and Signal.
h SSID: Displays the SSID of the Access Point. The SSID is a unique
name shared among all points in your wireless network. The SSID must
be identical for all points in the network, and is case-sensitive.
h MAC: AP MAC address
h Channel: Displays the channel number of the Access Point.
h Mode: Displays the supporting AP mode.
h Signal: Displays the receiving signal strength from the Access Point.
h Rescan: Click on this button to view a list of Access Points in the area.
h Add to Profile: Click on this button to add the SSID and its associated
23
Page 24

settings into a profile.
h Connect: to connect with a specific Access Point, select the SSID from
the list, and then click on the Connect button.
h Activate: set this AP as default AP.
h Status: This indicates the state of the client. There are three options:
o Associated: Indicates that the wireless client is connected to an
Access Point (AP). The BSSID is shown in the form of 12 HEX
digits, which is the MAC address of the AP.
o Scanning: Indicates that the wireless client is searching for an AP
in the area.
o Disconnected: Indicates that there are no APs or clients in the
area.
h Extra Info: Displayed here are information about the link stats and the
percent of output power.
h Channel: The operating frequency channel that the client is using
(infrastructure mode).
h Authentication: Displays the authentication type.
h Encryption: Displays the encryption type.
h Network Type: Displays the network type; infrastructure or ad-hoc.
h IP Address: Displays the IP address.
h Sub Mask: Displays the subnet mask IP address.
h Default Gateway: Displays the IP address of the default gateway.
h Link Speed: The current rate at which the client is transmitting and
receiving.
h Transmit/ReceiveThroughput: Displays the Tx (transmit) and Rx
(receive) kilo-bytes per second.
h Link Quality: In infrastructure mode, this bar displays the transmission
quality between an AP and a client. In Ad-hoc mode, this bar displays
the transmission quality between one client, and another.
h Signal Strength: This bar displays the strength of the signal received
from an AP or client.
h Noise Level: Displays the background noise level; a lower level
indicates less interference.
h HT: High Through-Put / 802.11 n Section
h BW: Channel Bandwidth
h GI:
Guard Interval
h MCS: Modulation Coding Scheme
h SNR: Signal Noise Rate
24
Page 25

Advanced Configuration
The Advanced tab is used to configure Tx burst, WMM, and CCX.
h Wireless mode: Currently supports 2.4G wireless only.
h Enable Tx BURST: Click the check box will enhance the throughput
h Enable TCP Window Size: Enhance the throughput if enable this function.
h WMM Enable: Click the check box to enable WMM QoS capability. (XP only)
h CCX: Enable this option if the network supports Cisco Compatible
Extensions. (XP only)
h Click on the Apply button to close this window.
WPS™
WPS (Wireless Push Button) is for WiFi Protected Setup™. By pressing this
button, the security settings of the device will automatically synchronize with
other wireless devices on your network that support Wi-Fi Protected Setup™.
Connecting to the WPS® Secured Network
Press the WPS® button on your router. Open the ENUWI-AXN3 Wireless
LAN Utility by doing right-click on the
logo located next to the Windows
clock at the bottom right of the screen, click to select “Launch Config
Utility”. Click on the WPS® Tab and wait a few seconds for the router and
your ENUWI-AXN3 to be associated. The WPS Associate IE bar indicates
the progress. Once connections are established, a green bar similar to this
(Image here) will appear at the same place where the Windows clock is
located in the bottom right of the screen.
25
Page 26

h Rescan: Click on this button to view a list of Access Points in the area.
h Connect: Click on the AP to start WPS connection with the AP
h Disconnect: Click to terminate WPS connection
26
Page 27

Uninstall the ENUWI-XAN3 Software Driver & Client Utility
If the ENUWI-XAN3 installation is unsuccessful for any reason, the best way to
solve the problem may be to completely uninstall the software driver and its utility
and repeat the installation procedure again.
Follow these steps below in order to uninstall the client utility:
1. Click on Start > Encore Wireless > Uninstall – Encore ENUWI-XAN3
2. The un-installation process will follow.
27
Page 28

3. Select the “Remove all” button.
28
Page 29

NOTE: The image above may have different title from your screen, ignore it.
4. Click on the Yes button to confirm the un-installation process and then click
on the Next button.
5. Click “Finish” to go to the next screen
6. The un-installation process is complete. For some PC you will be prompted to
restart your PC. If so, select “Yes, I want to restart my computer now”
radio button and then click on the “Finish” button. Then remove the USB
adapter.
29
Page 30

NOTE: The image above may have different title from your screen, ignore it.
30
Page 31

2 ENUWI-XAN3 for MAC™ OS X
Driver Installation
Follow the steps below in order to install the USB adapter drivers:
1. Insert the CD-ROM provided to in this package. The setup should run
automatically. If the setup would not run automatically, then you must manually
select the setup.dmg
file from the CD-ROM drive.
2. Click on the Continue button to configure the next step.
31
Page 32

3. Select the Macintosh HD and then click on the Continue button.
4. Click on the Continue button to configure the next step.
32
Page 33

5. The installation is complete. Click on the Restart button.
6. Carefully insert the USB adapter into the USB port. MAC™ OS X will then detect
and install the new hardware.
7. The Client Utility is installed in the Applications folder.
Profiles
The Profile tab is used to store the settings of multiple Access Points such as
home, office, café, etc. When adding a profile you are required to enter a profile
name and SSID as well as configure the power-saving mode, network type,
RTS/fragmentation threshold and encryption/authentication settings. A profile
can be configured as Infrastructure or Ad-hoc mode. The configuration settings
for each mode are described below.
33
Page 34

Infrastructure Mode
The infrastructure mode requires the use of an Access Point (AP). In this mode,
all wireless communication between two computers has to be via the AP. It
doesn’t matter if the AP is stand-alone or wired to an Ethernet network. If used in
stand-alone, the AP can extend the range of independent wireless LANs by
acting as a repeater, which effectively doubles the distance between wireless
stations.
34
Page 35

h Profile: Enter a name for the profile; this does not need to be the same
as the SSID.
h SSID: Enter the SSID of the network or select one from the drop-down
list. The SSID is a unique name shared among all points in your wireless
network. The SSID must be identical for all points in the network, and is
case-sensitive.
h PSM: Select a power saving mode (PSM) option.
o CAM (Continuously Active Mode): Select this option if your
notebook is always connected to the power supply.
o PSM (Power Saving Mode): Select this option if your notebook
uses its battery power. This option minimizes the battery usage
while the network is idle.
h Network Type: Select Infrastructure from the drop-down list.
h TX Power: Select a transmit power from the drop-down list. If your
notebook is connected to external power then select 100% or auto, if
not, select one of the lower values for power saving.
h RTS Threshold: Place a check in this box if you would like to enable
RTS Threshold. Any packet in the RTS/CTS handshake larger than the
specified value (bytes) will be discarded.
h Fragment Threshold: Place a check in this box if you would like to
enable Fragment Threshold. Any packet larger than the specified value
(bytes) will be discarded.
h Click on the Apply button to save the changes.
35
Page 36

Ad-hoc Mode
This is the simplest network configuration with several computers equipped with
the PC Cards that form a wireless network whenever they are within range of one
another. In ad-hoc mode, each client is peer-to-peer, would only have access to
the resources of the other client and does not require an access point. This is the
easiest and least expensive way for the SOHO to set up a wireless network.
h Profile: Enter a name for the profile; this does not need to be the same
as the SSID.
h SSID: Enter the SSID of the network or select one from the drop-down
list. The SSID is a unique name shared among all points in your wireless
network. The SSID must be identical for all points in the network, and is
case-sensitive.
h Network Type: Select Ad-hoc from the drop-down list.
h TX Power: Select a transmit power from the drop-down list. If your
notebook is connected to external power then select 100% or auto, if
not, select one of the lower values for power saving.
h Preamble: Select Auto from the drop-down list, unless you are aware of
the preamble type (long or short) used in each station.
h Ad-hoc wireless mode: Select a wireless mode from the drop-down list
depending on the type of stations used in the ad-hoc network. Select
B/G Mix if the network consists of 11b and 11g stations. Select B-only or
G-only if the network consists of only one type of wireless mode.
h RTS Threshold: Place a check in this box if you would like to enable
RTS Threshold. Any packet in the RTS/CTS handshake larger than the
specified value (bytes) will be discarded.
36
Page 37

h Fragment Threshold: Place a check in this box if you would like to
enable Fragment Threshold. Any packet larger than the specified value
(bytes) will be discarded.
h Click on the Apply button to save the changes.
Authentication and Security
The Security tab allows you to configure the authentication and encryption
settings such as: WEP, WPA-PSK, WPA2-PSK and 802.1x. Each security option
is described in detail below.
WEP Encryption
The WEP tab displays the WEP settings. Encryption is designed to make the
data transmission more secure. You may select 64 or 128-bit WEP (Wired
Equivalent Privacy) key to encrypt data (Default setting is Disable). WEP
encrypts each frame transmitted from the radio using one of the Keys from a
panel. When you use WEP to communicate with the other wireless clients, all the
wireless devices in this network must have the same encryption key or pass
phrase. The following information is included in this tab, as the image depicts
below.
h Authentication Type: Select Open or Shared from the drop-down list.
h Encryption: Select WEP from the drop-down list.
h WEP Key: Type a character string into the field. For 64-bit enter 5
37
Page 38

alphanumeric or 10 hexadecimal characters. For 128-bit enter 13
alphanumeric or 26 hexadecimal characters.
h Click on the Apply button to save the changes.
h Show Password check box. If you want to make sure the accuracy of
password you type, click the Show Password box to check it.
WPA-PSK Authentication & TKIP, AES Encryption
WPA – PSK (Pre-shared Key) is used in a Pre Shared Key mode that does not
require an authentication server. Access to the Internet and the rest of the
wireless network services is allowed only if the pre-shared key of the computer
matches that of the Access Point. This approach offers the simplicity of the WEP
key, but uses stronger TKIP encryption. EAP (Extensible Authentication Protocol)
is an extension to the PPP protocol that enables a variety of authentication
protocols to be used. It passes through the exchange of authentication messages,
allowing the authentication software stored in a server to interact with its
counterpart in the client.
h Authentication Type: Select WPA or WPA2 from the drop-down list.
h Encryption: Select TKIP or AES from the drop-down list.
h WPA Preshared key: Enter a pass phrase which is between 8 and 32
characters long.
h Click on the Apply button to save the changes.
h Show Password check box. If you want to make sure the accuracy of
password you type, click the Show Password box to check it.
38
Page 39

Link Status
The Link Status tab displays the current status of the wireless radio. The
following information is included in this tab, as the image depicts below.
h Status: This indicates the state of the client. There are three options:
o Associated: Indicates that the wireless client is connected to an
Access Point (AP). The BSSID is shown in the form of 12 HEX
digits, which is the MAC address of the AP.
o Scanning: Indicates that the wireless client is searching for an AP
in the area.
o Disconnected: Indicates that there are no APs or clients in the
area.
h Current Channel: The operating frequency channel that the client is
using (infrastructure mode).
h Link Speed: The current rate at which the client is transmitting and
receiving.
h Throughput (bytes/sec): Displays the Tx (transmit) and Rx (receive)
kilo-bytes per second.
h Link Quality: In infrastructure mode, this bar displays the transmission
quality between an AP and a client. In Ad-hoc mode, this bar displays
the transmission quality between one client, and another.
h Signal Strength: This bar displays the strength of the signal received
from an AP or client.
h Noise Level: Displays the background noise level; a lower level
39
Page 40

indicates less interference.
h HT: High Through-Put / 802.11n Section
h BW: Channel Bandwidth
h GI: Guard Interval
h MCS: Modulation Coding Scheme
h Click on the OK button to close this window.
h dBm Check Box. When you click on the check box as the drawing
below. The signal strength and noise level will be shown as the dBm
measurements.
Site Survey
The Site Survey tab displays a list of Access Points and Stations in the area, and
allows you to connect to a specific one. The following information is included in
this tab, as the image depicts below.
h SSID: Displays the SSID of the Access Point. The SSID is a unique
name shared among all points in your wireless network. The SSID must
be identical for all points in the network, and is case-sensitive.
h BSSID: Displays the MAC address of the Access Point.
h Signal: Displays the receiving signal strength from the Access Point.
h Channel: Displays the channel number of the Access Point.
h Authentication: displays the authentication on the Access Point, this
40
Page 41

includes WPA, WPA-PSK, WPA2, or Unknown.
h Encryption: Displays the encryption on the Access Point, this includes
WEP, TKIP, AES or None.
h Network Type: Indicates whether the SSID is a Station (Ad-hoc) or
Access Point (Infrastructure).
h Rescan: Click on this button to view a list of Access Points in the area.
h Connect: to connect with a specific Access Point, select the SSID from
the list, and then click on the Connect button.
h Add Profile: Click on this button to add the SSID and its associated
settings into a profile.
h Click on the OK button if you have made any changes.
Statistics
The Statistics tab displays transmit and receive packet statistics in real-time.
Information included is frames transmitted/received successfully, transmitted
successfully without and after retry, received with CRC error, duplicate frames
received, etc.
Advanced Configuration
The Advanced tab is used to configure the wireless mode (802.11b-only,
802.11g-only, or 802.11b/g-mixed), B/G protection and country/channel setting.
41
Page 42

h Wireless mode: Select 802.11 B/G/N mixed if the wireless network uses
both 11b, 11g and 11n stations and APs.
h Tx Rate: The transmit rate should be set to auto, however you may
manually select a transmit rate from the drop-down list.
h Tx BURST: Click the check box will enhance the throughput
h Click on the Apply button to save the changes.
WPS™
WPS (Wireless Push Button) is used for WiFi Protected Setup™. By pressing
this button, the security settings of the device will automatically synchronize with
other wireless devices on your network that support Wi-Fi Protected Setup™.
Connecting to the WPS® Secured Network on Mac Computers
1. Press the WPS® button on your router
2. Open the Wireless Utility and then click on the “WPS” from the upper menu bar
42
Page 43

3. Click the “PBC” button and wait a few seconds for the router and your ENUWI-XAN3 to
establish association.
4. When connected, a green check mark is visible and your router’s SSID or wireless ID
name should be listed under the “WPS Profile List”.
43
Page 44

Definitions:
h Rescan: Click on this button to view a list of Access Points in the area.
h Renew: Regenerate a new PIN code
h Config Mode: switch between Enrollee or Registrar
h Profile Detail: show profile of the selected party
44
Page 45

h Connect: Click on the AP to start WPS connection with the AP
h Disconnect: Click to terminate WPS connection
h Import Profile: Load pre-stored profile database
h Delete: Remove the selected item
45
Page 46

About
The About tab displays information about the device, such as: the network driver
version and date, configuration utility version and date, and the NIC (Network
Interface Card) firmware version and date.
46
Page 47

Appendix A – Glossary
8
802.11
A family of specifications for wireless local area networks (WLANs) developed by a
working group of the Institute of Electrical and Electronics Engineers (IEEE).
A
Access Control List
ACL. This is a database of network devices that are allowed to access resources on the
network.
Access Point
AP. Device that allows wireless clients to connect to it and access the network
ActiveX
A Microsoft specification for the interaction of software components.
Address Resolution Protocol
ARP. Used to map MAC addresses to IP addresses so that conversions can be made in
both directions.
Ad-hoc network
Peer-to-Peer network between wireless clients
ADSL
Asymmetric Digital Subscriber Line
Advanced Encryption Standard
AES. Government encryption standard
Alphanumeric
Characters A-Z and 0-9
Antenna
Used to transmit and receive RF signals.
AppleTalk
A set of Local Area Network protocols developed by Apple for their computer systems
AppleTalk Address Resolution Protocol
AARP. Used to map the MAC addresses of Apple computers to their AppleTalk network
addresses, so that conversions can be made in both directions.
Application layer
7th Layer of the OSI model. Provides services to applications to ensure that they can
communicate properly with other applications on a network.
ASCII
American Standard Code for Information Interchange. This system of characters is most
commonly used for text files
Attenuation
The loss in strength of digital and analog signals. The loss is greater when the signal is
being transmitted over long distances.
Authentication
To provide credentials, like a Password, in order to verify that the person or device is
47
Page 48

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
really who they are claiming to be
Automatic Private IP Addressing
APIPA. An IP address that that a Windows computer will assign itself when it is
configured to obtain an IP address automatically but no DHCP server is available on the
network
B
Backward Compatible
The ability for new devices to communicate and interact with older legacy devices to
guarantee interoperability
Bandwidth
The maximum amount of bytes or bits per second that can be transmitted to and from a
network device
Basic Input/Output System
BIOS. A program that the processor of a computer uses to startup the system once it is
turned on
Baud
Data transmission speed
Beacon
A data frame by which one of the stations in a Wi-Fi network periodically broadcasts
network control data to other wireless stations.
Bit rate
The amount of bits that pass in given amount of time
Bit/sec
Bits per second
BOOTP
Bootstrap Protocol. Allows for computers to be booted up and given an IP address with
no user intervention
Bottleneck
A time during processes when something causes the process to slowdown or stop all
together
Broadband
A wide band of frequencies available for transmitting data
Broadcast
Transmitting data in all directions at once
Browser
A program that allows you to access resources on the web and provides them to you
graphically
C
Cable modem
A device that allows you to connect a computer up to a coaxial cable and receive Internet
access from your Cable provider
CardBus
A newer version of the PC Card or PCMCIA interface. It supports a 32-bit data path, DMA,
and consumes less voltage
CAT 5
Category 5. Used for 10/100 Mbps or 1Gbps Ethernet connections
48
Page 49

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
Client
A program or user that requests data from a server
Collision
When do two devices on the same Ethernet network try and transmit data at the exact
same time.
Cookie
Information that is stored on the hard drive of your computer that holds your preferences
to the site that gave your computer the cookie
D
Data
Information that has been translated into binary so that it can be processed or moved to
another device
Data Encryption Standard
Uses a randomly selected 56-bit key that must be known by both the sender and the
receiver when information is exchanged
Database
Organizes information so that it can be managed updated, as well as easily accessed by
users or applications.
Data-Link layer
The second layer of the OSI model. Controls the movement of data on the physical link of
a network
DB-25
A 25 ping male connector for attaching External modems or RS-232 serial devices
DB-9
A 9 pin connector for RS-232 connections
dBd
Decibels related to dipole antenna
dBi
Decibels relative to isotropic radiator
dBm
Decibels relative to one milliwatt
Decrypt
To unscramble an encrypted message back into plain text
Default
A predetermined value or setting that is used by a program when no user input has been
entered for this value or setting
Demilitarized zone
DMZ: A single computer or group of computers that can be accessed by both users on
the Internet as well as users on the Local Network, but that is not protected by the same
security as the Local Network.
DHCP
Dynamic Host Configuration Protocol: Used to automatically assign IP addresses from a
predefined pool of addresses to computers or devices that request them
Digital certificate:
An electronic method of providing credentials to a server in order to have access to it or a
network
49
Page 50

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
Direct Sequence Spread Spectrum
DSSS: Modulation technique used by 802.11b wireless devices
DMZ
"Demilitarized Zone". A computer that logically sits in a "no-mans land" between the LAN
and the WAN. The DMZ computer trades some of the protection of the router's security
mechanisms for the convenience of being directly addressable from the Internet.
DNS
Domain Name System: Translates Domain Names to IP addresses
Domain name
A name that is associated with an IP address
Download
To send a request from one computer to another and have the file transmitted back to the
requesting computer
DSL
Digital Subscriber Line. High bandwidth Internet connection over telephone lines
Duplex
Sending and Receiving data transmissions at the sane time
Dynamic DNS service
Dynamic DNS is provided by companies to allow users with Dynamic IP addresses to
obtain a Domain Name that will always by linked to their changing IP address. The IP
address is updated by either client software running on a computer or by a router that
supports Dynamic DNS, whenever the IP address changes
Dynamic IP address
IP address that is assigned by a DHCP server and that may change. Cable Internet
providers usually use this method to assign IP addresses to their customers.
E
EAP
Extensible Authentication Protocol
Email
Electronic Mail is a computer-stored message that is transmitted over the Internet
Encryption
Converting data into cyphertext so that it cannot be easily read
Ethernet
The most widely used technology for Local Area Networks.
F
Fiber optic
A way of sending data through light impulses over glass or plastic wire or fiber
File server
A computer on a network that stores data so that the other computers on the network can
all access it
File sharing
Allowing data from computers on a network to be accessed by other computers on the
network with different levels of access rights
Firewall
A device that protects resources of the Local Area Network from unauthorized users
outside of the local network
50
Page 51

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
Firmware
Programming that is inserted into a hardware device that tells it how to function
Fragmentation
Breaking up data into smaller pieces to make it easier to store
FTP
File Transfer Protocol. Easiest way to transfer files between computers on the Internet
Full-duplex
Sending and Receiving data at the same time
G
Gain
The amount an amplifier boosts the wireless signal
Gateway
A device that connects your network to another, like the internet
Gbps
Gigabits per second
Gigabit Ethernet
Transmission technology that provides a data rate of 1 billion bits per second
GUI
Graphical user interface
H
H.323
A standard that provides consistency of voice and video transmissions and compatibility
for videoconferencing devices
Half-duplex
Data cannot be transmitted and received at the same time
Hashing
Transforming a string of characters into a shorter string with a predefined length
Hexadecimal
Characters 0-9 and A-F
Hop
The action of data packets being transmitted from one router to another
Host
Computer on a network
HTTP
Hypertext Transfer Protocol is used to transfer files from HTTP servers (web servers) to
HTTP clients (web browsers)
HTTPS
HTTP over SSL is used to encrypt and decrypt HTTP transmissions
Hub
A networking device that connects multiple devices together
I
ICMP
Internet Control Message Protocol
51
Page 52

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
IEEE
Institute of Electrical and Electronics Engineers
IGMP
Internet Group Management Protocol is used to make sure that computers can report
their multicast group membership to adjacent routers
IIS
Internet Information Server is a WEB server and FTP server provided by Microsoft
IKE
Internet Key Exchange is used to ensure security for VPN connections
Infrastructure
In terms of a wireless network, this is when wireless clients use an Access Point to gain
access to the network
Internet
A system of worldwide networks which use TCP/IP to allow for resources to be accessed
from computers around the world
Internet Explorer
A World Wide Web browser created and provided by Microsoft
Internet Protocol
The method of transferring data from one computer to another on the Internet
Internet Protocol Security
IPsec provides security at the packet processing layer of network communication
Internet Service Provider
An ISP provides access to the Internet to individuals or companies
Intranet
A private network
Intrusion Detection
A type of security that scans a network to detect attacks coming from inside and outside
of the network
IP
Internet Protocol
IP address
A 32-bit number, when talking about Internet Protocol Version 4, that identifies each
computer that transmits data on the Internet or on an Intranet
IPsec
Internet Protocol Security
IPX
Internetwork Packet Exchange is a networking protocol developed by Novel to enable
their Netware clients and servers to communicate
ISP
Internet Service Provider
J
Java
K
Kbps
A programming language used to create programs and applets for web pages
52
Page 53

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
Kilobits per second
Kbyte
Kilobyte
L
L2TP
Layer 2 Tunneling Protocol
LAN
Local Area Network
Latency
The amount of time that it takes a packet to get from the one point to another on a
network. Also referred to as delay
LED
Light Emitting Diode
Legacy
Older devices or technology
Local Area Network
A group of computers in a building that usually access files from a server
LPR/LPD
"Line Printer Requestor"/"Line Printer Daemon". A TCP/IP protocol for transmitting
streams of printer data.
M
MAC Address
A unique hardware ID assigned to every Ethernet adapter by the manufacturer.
Mbps
Megabits per second
MDI
Medium Dependent Interface is an Ethernet port for a connection to a straight-through
cable
MDIX
Medium Dependent Interface Crossover, is an Ethernet port for a connection to a
crossover cable
MIB
Management Information Base is a set of objects that can be managed by using SNMP
Modem
A device that Modulates digital signals from a computer to an analog signal in order to
transmit the signal over phone lines. It also Demodulates the analog signals coming from
the phone lines to digital signals for your computer
MPPE
Microsoft Point-to-Point Encryption is used to secure data transmissions over PPTP
connections
MTU
Maximum Transmission Unit is the largest packet that can be transmitted on a packetbased network like the Internet
Multicast
Sending data from one device to many devices on a network
53
Page 54

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
N
NAT
Network Address Translation allows many private IP addresses to connect to the Internet,
or another network, through one IP address
NetBEUI
NetBIOS Extended User Interface is a Local Area Network communication protocol. This
is an updated version of NetBIOS
NetBIOS
Network Basic Input/Output System
Netmask
Determines what portion of an IP address designates the Network and which part
designates the Host
Network Interface Card
A card installed in a computer or built onto the motherboard that allows the computer to
connect to a network
Network Layer
The third layer of the OSI model which handles the routing of traffic on a network
Network Time Protocol
Used to synchronize the time of all the computers in a network
NIC
Network Interface Card
NTP
Network Time Protocol
O
OFDM
Orthogonal Frequency-Division Multiplexing is the modulation technique for both 802.11a
and 802.11g
OSI
Open Systems Interconnection is the reference model for how data should travel between
two devices on a network
OSPF
Open Shortest Path First is a routing protocol that is used more than RIP in larger scale
networks because only changes to the routing table are sent to all the other routers in the
network as opposed to sending the entire routing table at a regular interval, which is how
RIP functions
P
Password
A sequence of characters that is used to authenticate requests to resources on a network
Personal Area Network
The interconnection of networking devices within a range of 10 meters
Physical layer
The first layer of the OSI model. Provides the hardware means of transmitting electrical
signals on a data carrier
Ping
A utility program that verifies that a given Internet address exists and can receive
54
Page 55

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
messages. The utility sends a control packet to the given address and waits for a
response.
PoE
Power over Ethernet is the means of transmitting electricity over the unused pairs in a
category 5 Ethernet cable
POP3
Post Office Protocol 3 is used for receiving email
Port
A logical channel endpoint in a network. A computer might have only one physical
channel (its Ethernet channel) but can have multiple ports (logical channels) each
identified by a number.
PPP
Point-to-Point Protocol is used for two computers to communicate with each over a serial
interface, like a phone line
PPPoE
Point-to-Point Protocol over Ethernet is used to connect multiple computers to a remote
server over Ethernet
PPTP
Point-to-Point Tunneling Protocol is used for creating VPN tunnels over the Internet
between two networks
Preamble
Used to synchronize communication timing between devices on a network
Q
QoS
Quality of Service
R
RADIUS
Remote Authentication Dial-In User Service allows for remote users to dial into a central
server and be authenticated in order to access resources on a network
Reboot
To restart a computer and reload it's operating software or firmware from nonvolatile
storage.
Rendezvous
Apple's version of UPnP, which allows for devices on a network to discover each other
and be connected without the need to configure any settings
Repeater
Retransmits the signal of an Access Point in order to extend it's coverage
RIP
Routing Information Protocol is used to synchronize the routing table of all the routers on
a network
RJ-11
The most commonly used connection method for telephones
RJ-45
The most commonly used connection method for Ethernet
RS-232C
The interface for serial communication between computers and other related devices
55
Page 56

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
RSA
Algorithm used for encryption and authentication
S
Server
A computer on a network that provides services and resources to other computers on the
network
Session key
An encryption and decryption key that is generated for every communication session
between two computers
Session layer
The fifth layer of the OSI model which coordinates the connection and communication
between applications on both ends
Simple Mail Transfer Protocol
Used for sending and receiving email
Simple Network Management Protocol
Governs the management and monitoring of network devices
SIP
Session Initiation Protocol. A standard protocol for initiating a user session that involves
multimedia content, such as voice or chat.
SMTP
Simple Mail Transfer Protocol
SNMP
Simple Network Management Protocol
SOHO
Small Office/Home Office
SPI
Stateful Packet Inspection
SSH
Secure Shell is a command line interface that allows for secure connections to remote
computers
SSID
Service Set Identifier is a name for a wireless network
Stateful inspection
A feature of a firewall that monitors outgoing and incoming traffic to make sure that only
valid responses to outgoing requests are allowed to pass though the firewall
Subnet mask
Determines what portion of an IP address designates the Network and which part
designates the Host
Syslog
System Logger -- a distributed logging interface for collecting in one place the logs from
different sources. Originally written for UNIX, it is now available for other operating
systems, including Windows.
T
TCP
Transmission Control Protocol
56
Page 57

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
TCP Raw
A TCP/IP protocol for transmitting streams of printer data.
TCP/IP
Transmission Control Protocol/Internet Protocol
TFTP
Trivial File Transfer Protocol is a utility used for transferring files that is simpler to use
than FTP but with less features
Throughput
The amount of data that can be transferred in a given time period
Traceroute
A utility displays the routes between you computer and specific destination
U
UDP
User Datagram Protocol
Unicast
Communication between a single sender and receiver
Universal Plug and Play
A standard that allows network devices to discover each other and configure themselves
to be a part of the network
Upgrade
To install a more recent version of a software or firmware product
Upload
To send a request from one computer to another and have a file transmitted from the
requesting computer to the other
UPnP
Universal Plug and Play
URL
Uniform Resource Locator is a unique address for files accessible on the Internet
USB
Universal Serial Bus
UTP
Unshielded Twisted Pair
V
Virtual Private Network
VPN: A secure tunnel over the Internet to connect remote offices or users to their
company's network
VLAN
Virtual LAN
Voice over IP
Sending voice information over the Internet as opposed to the PSTN
VoIP
Voice over IP
W
Wake on LAN
57
Page 58

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
Allows you to power up a computer though it's Network Interface Card
WAN
Wide Area Network
WCN
Windows Connect Now. A Microsoft method for configuring and bootstrapping wireless
networking hardware (access points) and wireless clients, including PCs and other
devices.
WDS
Wireless Distribution System. A system that enables the interconnection of access points
wirelessly.
Web browser
A utility that allows you to view content and interact with all of the information on the
World Wide Web
WEP
Wired Equivalent Privacy is security for wireless networks that is supposed to be
comparable to that of a wired network
Wide Area Network
The larger network that your LAN is connected to, which may be the Internet itself, or a
regional or corporate network
Wi-Fi
Wireless Fidelity
Wi-Fi Protected Access
An updated version of security for wireless networks that provides authentication as well
as encryption
Wireless ISP
A company that provides a broadband Internet connection over a wireless connection
Wireless LAN
Connecting to a Local Area Network over one of the 802.11 wireless standards
WISP
Wireless Internet Service Provider
WLAN
Wireless Local Area Network
WPA
Wi-Fi Protected Access. A Wi-Fi security enhancement that provides improved data
encryption, relative to WEP.
X
xDSL
A generic term for the family of digital subscriber line (DSL) technologies, such as ADSL,
HDSL, RADSL, and SDSL.
Y
Yagi antenna
A directional antenna used to concentrate wireless signals on a specific location
58
Page 59

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
Appendix B – Specifications
ST ANDARD
Data Rates
1, 2, 5.5, 6, 9, 11, 12, 18, 24, 36, 48,
54, 72, 84, 150 (150Mbps Tx PHY
support)
Standards / Compliance
IEEE802.3, IEEE802.3u, IEEE802.11b,
IEEE802.11g, 802.11n (2.0)
Regulation Certifications
FCC Part 15, ETSI 300/328/CE, RoHS
Status LEDs
POWER / LINK
Drivers
Windows 2000/XP/Windows Vista / Mac
OSX
RF Information
Frequency Band
U.S., Europe and Japan product
covering 2.4 to 2.484 GHz,
programmable for different country
regulations
Media Access Protocol
Carrier Sense Multiple Access with
Collision Avoidance (CSMA/CA)
Modulation T ech nology
802.11g: OFDM (64-QAM, 16-QAM,
QPSK, BPSK)
802.11b: DSSS (DBPSK, DQPSK,
CCK)
Operating Channels
11 for North America, 13 for Europe
Receiver Sensitivity
• 135Mbps: Typical - 65dBm @
10% PER
• 54Mbps: Typical - 68dBm @
10% PER
• 11Mbps: Typical - 84dBm @ 8%
PER
Available transmit power
• 2.412~2.472G(IEEE802.11b)
18dBm @1~11Mbps
• 2.412~2.472G(IEEE802.11g)
15 dBm @6Mbps
14 dBm @54Mbps
• 2.412~2.472G(IEEE802.11n)
15dBm
Antenna Configuration
1X 2dBi, 1T1R Mode
Networking
LAN Ports
10/100 Mbps Fast Ethernet RJ-45
Topology
Ad-Hoc, Infrastructure
Wireless Security
• 64/128-bits WEP Encryption
• WPA-PSK, WPA2-PSK, WPA, WPA2
• WPS™ Button
Physical Features
Form Factor
USB 2.0/1.1
Dimensions (L x W x H)
63 x 21 x 10.6 mm
Environmental
Temperature Range
Operating: 0°C to 40°C
Storage: -10°Cto 70°C
Humidity (non-condensing)
10%~95% RH Typical
Package Contents
• One ENUWI-N3 USB Dongle
• One CD-ROM with User’s Manual and
Drivers
• Quick Installation Guide
59
Page 60

ENUWI-N3 USB Wireless Adapter 802.11b/g/n Wireless LAN USB 2.0 Client Adapter
Appendix C – FCC Interference Statement
Federal Communication Commission Interference Statement
This equipment has been tested and found to comply with the limits for a Class B digital device,
pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection
against harmful interference in a residential installation. This equipment generates uses and can
radiate radio frequency energy and, if not installed and us ed in accordance with the instructions, may
cause harmful interference to radio communications. However, there is no guarantee that interference
will not occur in a particular installation. If this equipment does cause harmful interference to radio or
television reception, which can be determined by turning the equipment off and on, the user is
encouraged to try to correct the interference by one of the following measures:
z Reorient or relocate the receiving antenna.
z Increase the separation between the equipment and receiver.
z Connect the equipment into an outlet on a circuit different from that to which the receiver is
connected.
z Consult the dealer or an experienced radio/TV technician for help.
FCC Caution: Any changes or modifications not expressly approved by the party responsible for
compliance could void the user's authority to operate this equipment.
This device complies with Part 15 of the FCC Rules. Operation is subject to the foll owing t wo conditions:
(1) This device may not cause harmful interference, and (2) this device must accept any interference
received, including interference that may cause undesired operation.
IMPORTANT NOTE:
FCC Radiation Exposure Statement:
This equipment complies with FCC radiation exposure limits set forth for an uncontrolled enviro nment.
This device complies with FCC RF Exposure limits set forth for an uncontrolled env ironment, under 47
CFR 2.1093 paragraph (d)(2).
This transmitter must not be co-located or operating in conjunction with any other antenna or transmitter.
60
 Loading...
Loading...