Page 1
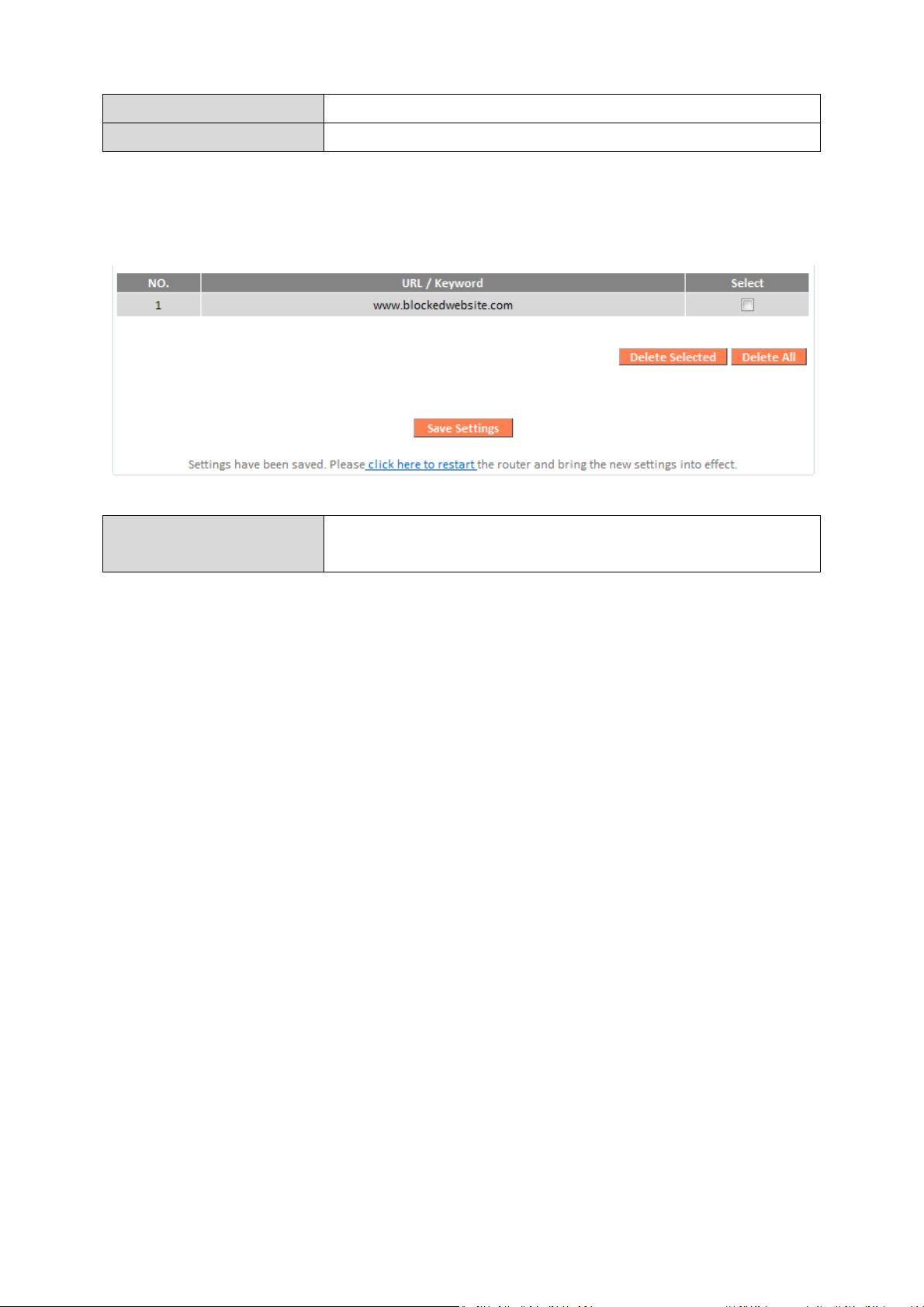
URL/Keyword
Enter the URL or keyword to be blocked.
Add
Add the
URL or keyword to the blocked table.
Delete Selected
/
Delete All
Delete selected or all entries from the table.
Blocked URLs/keywords entries will be listed in the table as shown below.
Select an entry using the “Select” checkbox.
77
Page 2
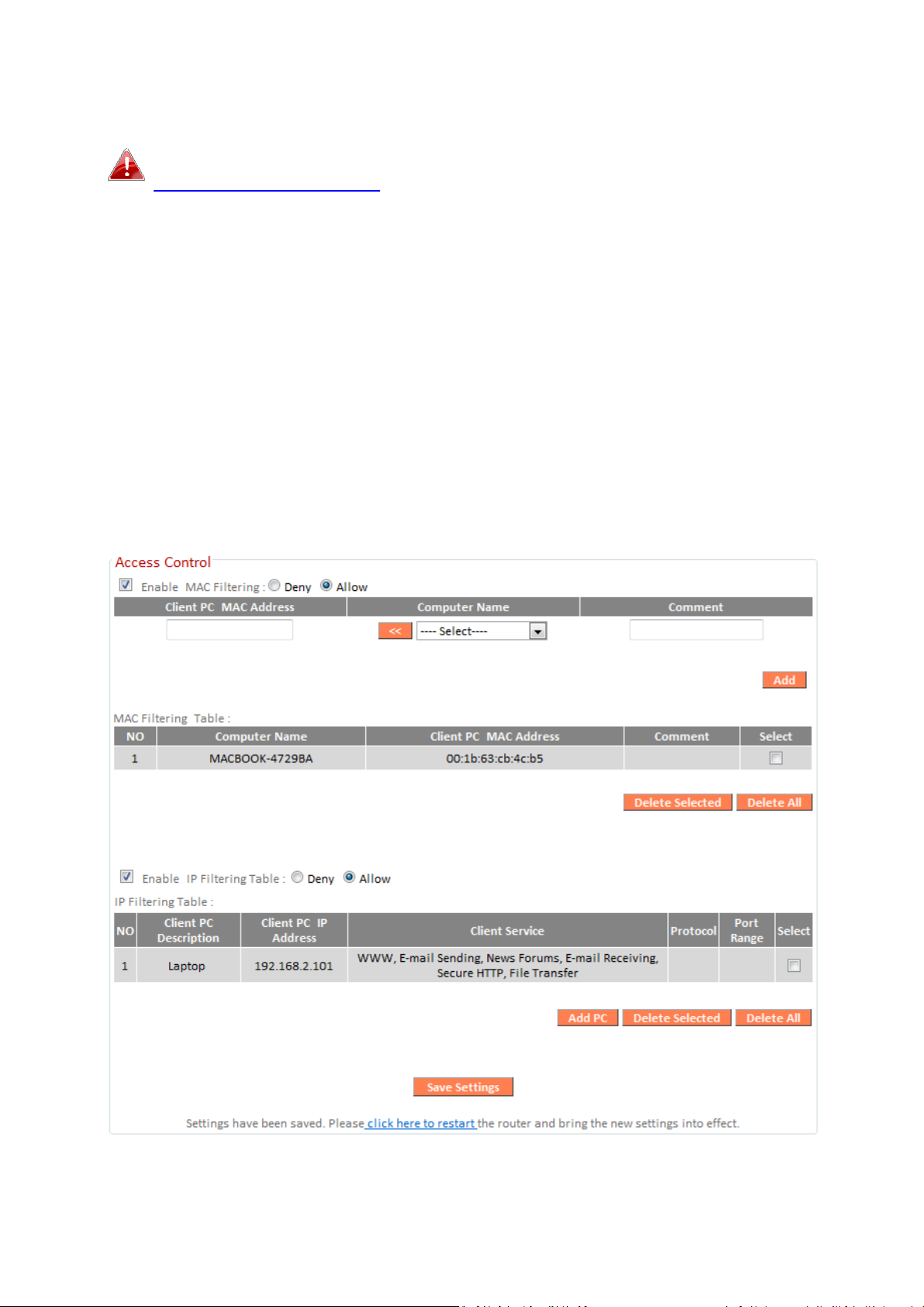
III-3-6-2. Access Control
Access Control (MAC filtering) can also be configured from
III-3-5-4. Access Control.
Access Control is a security feature that can help to prevent unauthorized
users from connecting to your wireless router.
This function allows you to define a list of network devices permitted or
denied to connect to the BR-6428nS V3/BR-6228nS V3. Devices are each
identified by their unique MAC address or IP address. Specific services can
also be allowed/denied for IP addresses.
Check/uncheck the “Enable MAC Filtering” and/or “Enable IP Filtering” box to
enable/disable MAC filtering and/or IP filtering.
78
Page 3

MAC Filtering:
Enable MAC
Check the box to enable MAC filtering and
specified MAC address.
Client PC MAC
Enter
a
MAC address of c
omputer or network
‘
aabbccddeeff
’.
Computer Name
Select a computer name from the drop
-
down
it manually.
Comment
Enter a comment for reference/identification
characters.
Add
Click “Add”
to add the MAC address to the
MAC add
ress filtering table.
Delete Selected
/
Delete All
Delete selected or all entries from the table.
Filtering
Address
select whether to “Deny” or “Allow” access for
device manually without dashes or colons e.g.
for MAC address ‘aa-bb-cc-dd-ee-ff’ enter
list and click “<<” to add its MAC address into
the “Client PC Mac Address” field.
Click “Refresh’ in the drop-down menu to
refresh the list of available MAC addresses. If
the address you wish to add is not listed, enter
consisting of up to 16 alphanumerical
MAC address entries will be listed in the table as shown below. Select an entry
using the “Select” checkbox.
79
Page 4
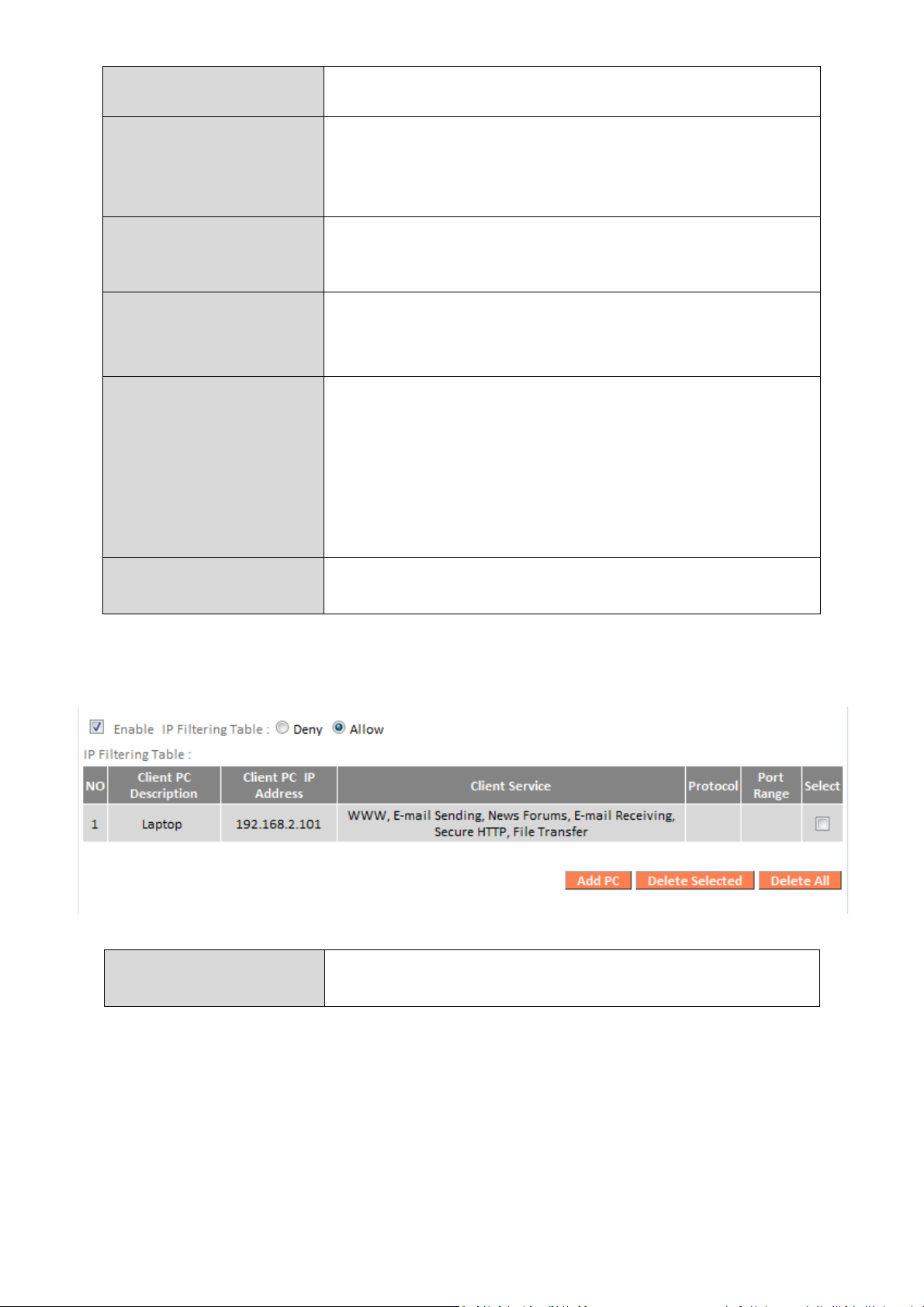
IP Filtering:
Enable IP Filtering
Chec
k the box to enable IP filtering and select
specified IP address.
Add PC
Opens a new window to add a new IP to the
to above.
whether to “Deny” or “Allow” access for
list, to deny or allow access/services according
80
Page 5
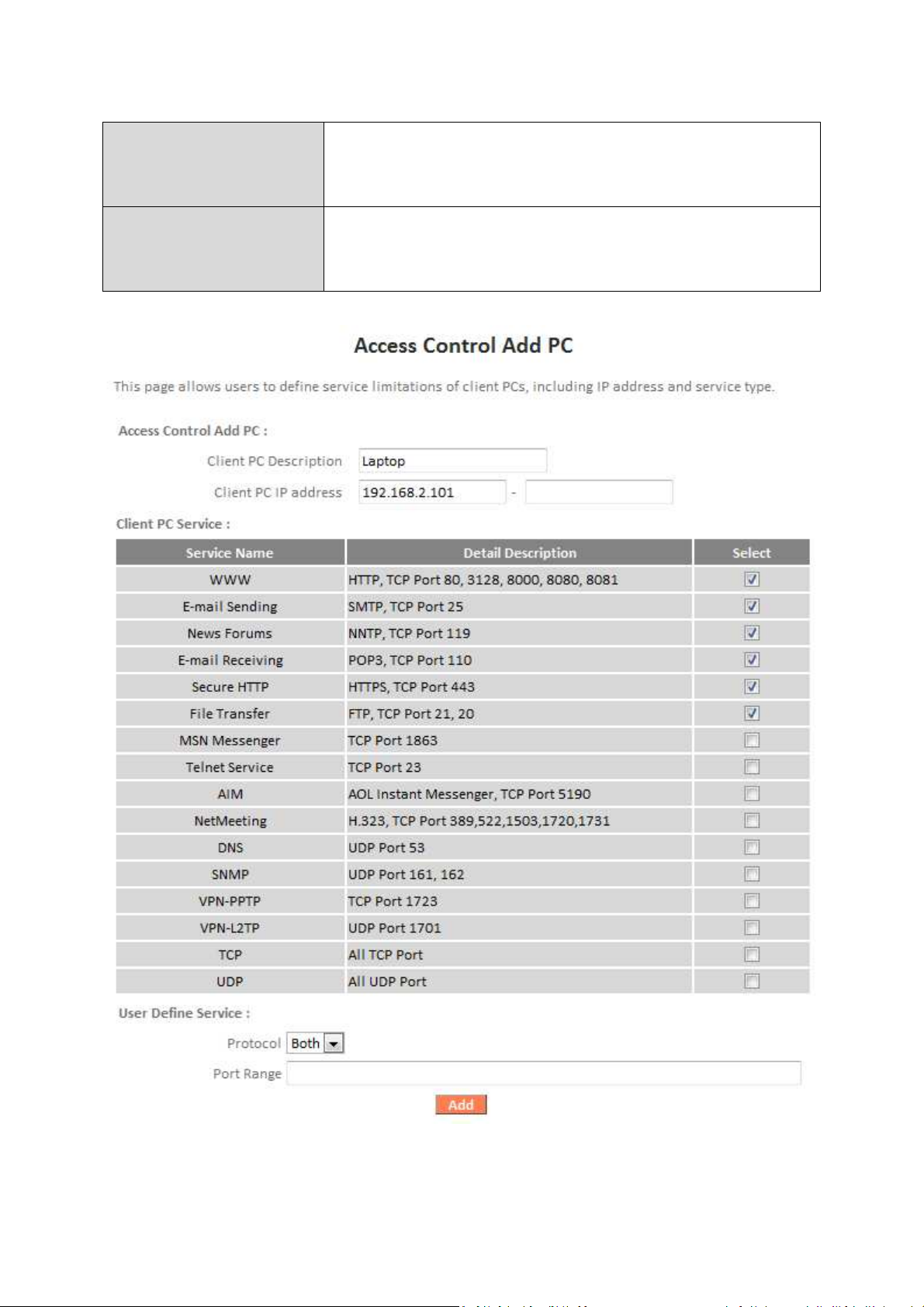
Client PC
Description
Enter a desc
ription for reference/identification
of up to 16 alphanumeric characters.
Client PC IP address
Enter a
startin
g IP address in the left field
and
the end IP address in the right field to define a
the left fi
eld
only
to define a single IP address.
Service Name
Various services are listed here with a short
service you wish to select.
Protocol
Select protocol “TCP” or “UDP” or “Both” for a
list.
Port Range
Enter the port range for the service not
110,115
,120.
Add
Click “Add”
to add
selected services or a user
defined service to the IP filtering table.
Delete Selected/
Delete All
Delete selected or all entries from the table.
range of IP addresses; or enter an IP address in
description. Check/uncheck the box for each
service not included in the “Client PC Service”
included in the “Client PC Service” list.
Enter a single port number e.g. 110, a range of
port numbers e.g. 110-120, or multiple port
numbers separated by a comma e.g.
IP filtering entries will be listed in the IP filtering table shown below.
81
Page 6
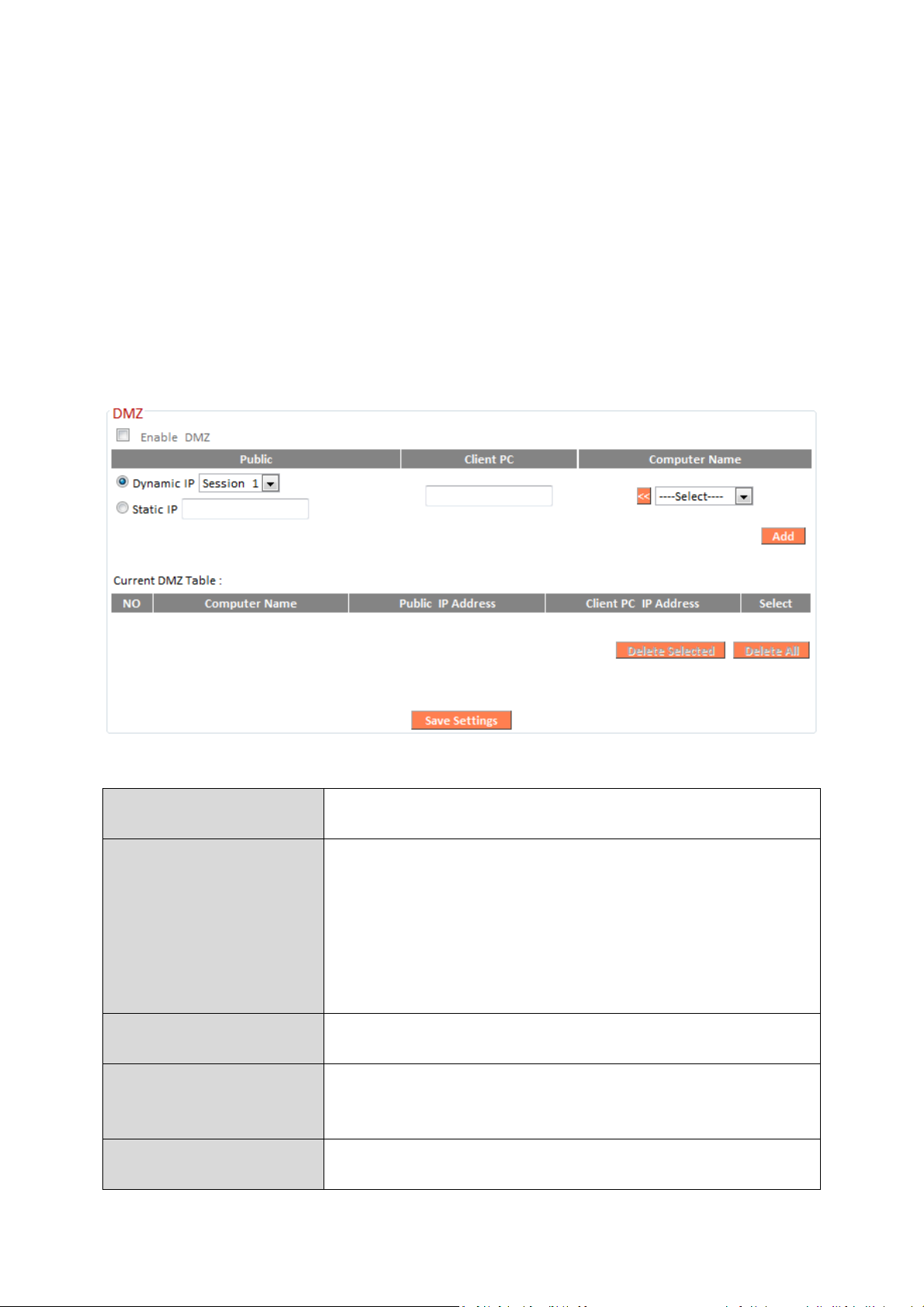
III-3-6-3. DMZ
Enable DMZ
Check/uncheck the box to
enable/disable the
device’s DMZ function.
Public
Select “Dynamic IP” or “Static IP” here.
want to map to a specific private IP addr
ess.
Client PC
Enter the private IP address that the internet IP
address will be mapped to.
Computer Name
Select a computer name from the list and click
field (above).
Add
Click
“
Add
” to add the client t
o the
“
Current
DMZ Table
”.
A Demilitarized Zone (DMZ) is an isolated area in your local network where
private IP addresses are mapped to specified Internet IP addresses, allowing
unrestricted access to the private IP addresses but not to the wider local
network.
You can define a virtual DMZ host here. This is useful for example, if a
network client PC cannot run an application properly from behind an NAT
firewall, since it opens the client up to unrestricted two-way access.
For “Dynamic IP” select an Internet connection
session from dropdown menu.
For “Static IP” enter the IP address that you
“<<” to enter its IP address into the “Client PC”
82
Page 7
DMZ entries will be displayed in the table shown below:
Delete Selected/
Delete All
Delete selected or all entries from the table.
III-3-6-4. DoS
Denial-of-Service (DoS) is a common form of malicious attack against a
network. The router’s firewall can protect against such attacks.
If you are not familiar with these functions, it is recommended you keep the
default settings.
83
Page 8
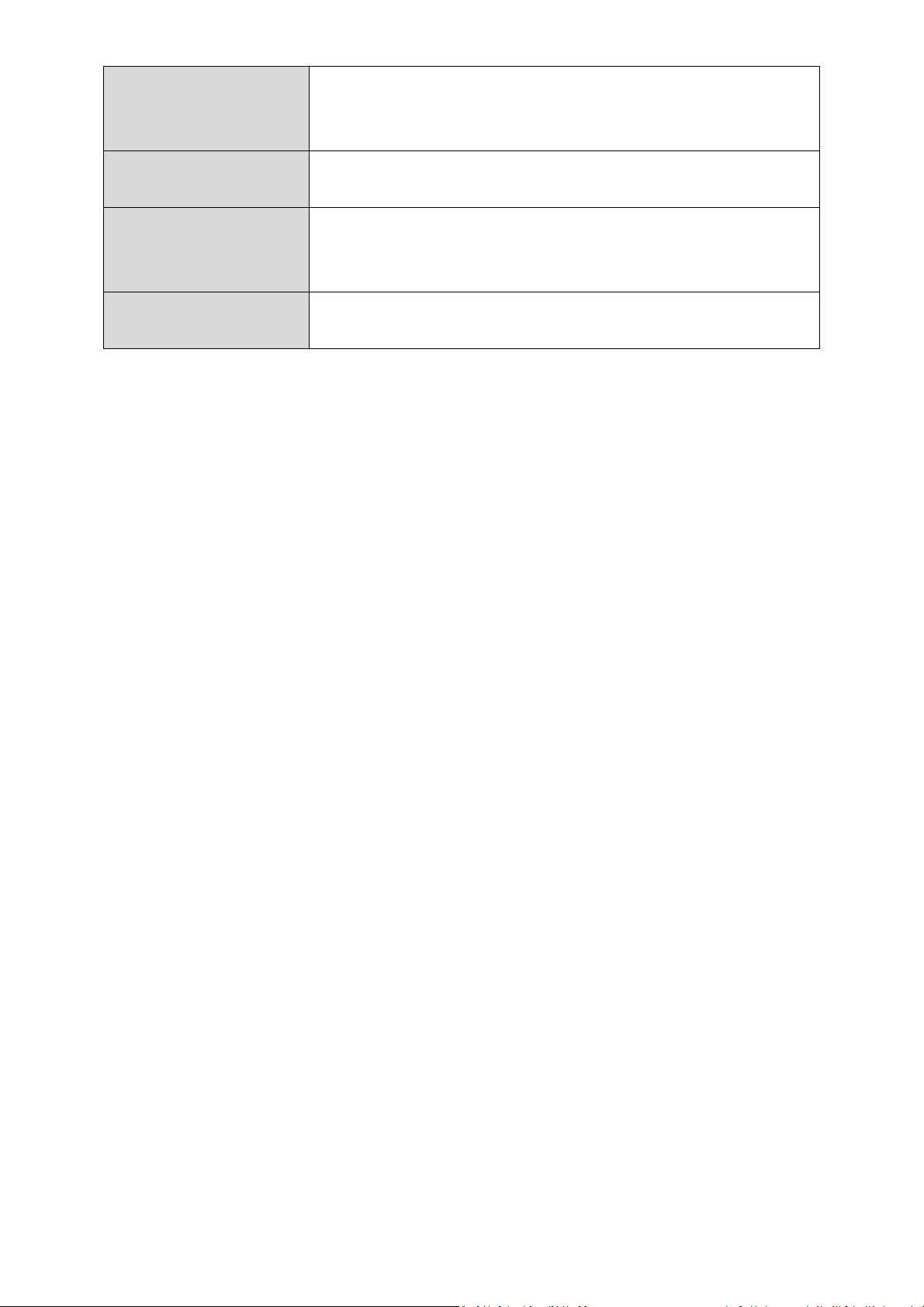
Ping of Death
Specify the frequency of ping of death packets
which will trigger the router’s DoS protection
function.
Discard Ping from
WAN
Check this box and the router will not answer
ping requests from the Internet.
Port Scan
Intruders use “port scanners” to detect open
port scan to prevent.
S
ync Flood
Specify the frequency of sync flood packets
which will trigger the DoS protection function.
Internet IP address ports. Check each type of
84
Page 9
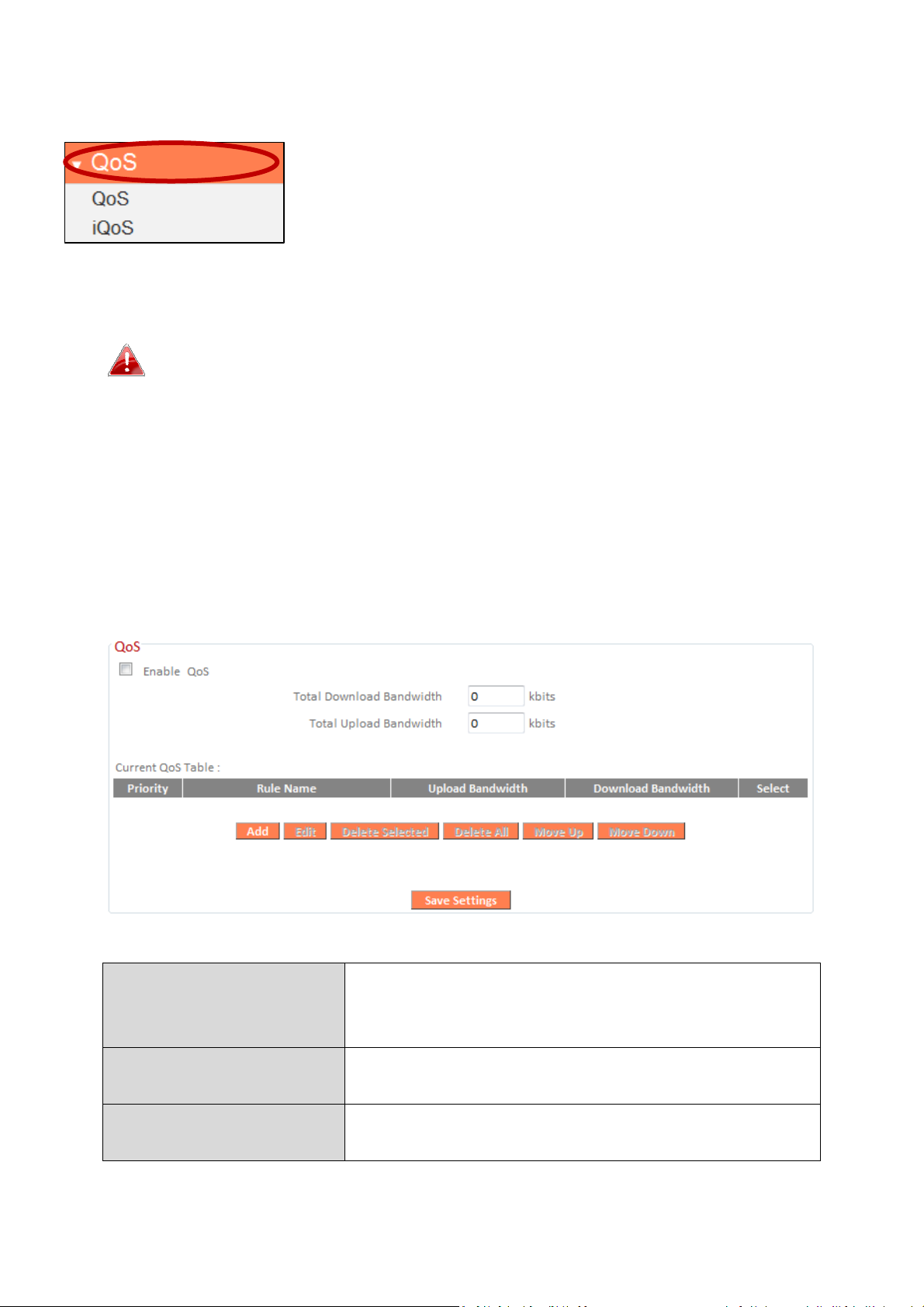
III-3-7. QoS
Total Download
E
nter your total download bandwidth limit
kbits.
Total Upload
Bandwidth
Enter your total upload bandwidth limit from
your Internet service provider (ISP) in kbits.
Add
Opens a new window to add a new QoS rule
t
o the current QoS table.
Quality of Service (QoS) is a feature to manage
Internet bandwidth efficiently. Some applications
require more bandwidth than others to function
properly, and QoS allows you to ensure that sufficient
bandwidth is available. Minimum or maximum bandwidth can be guaranteed
for a specified application.
QoS can improve the
performance. QoS is recommended to optimize performance for
online gaming.
BR-6428nS V3/BR-6228nS V3
’s
III-3-7-1. QoS
Check/uncheck the box “Enable QoS” to enable/disable the QoS function.
Click “Add” to open a new window and setup a QoS rule. The “Current QoS
Table” displays all QoS rules.
Bandwidth
from your Internet service provider (ISP) in
85
Page 10
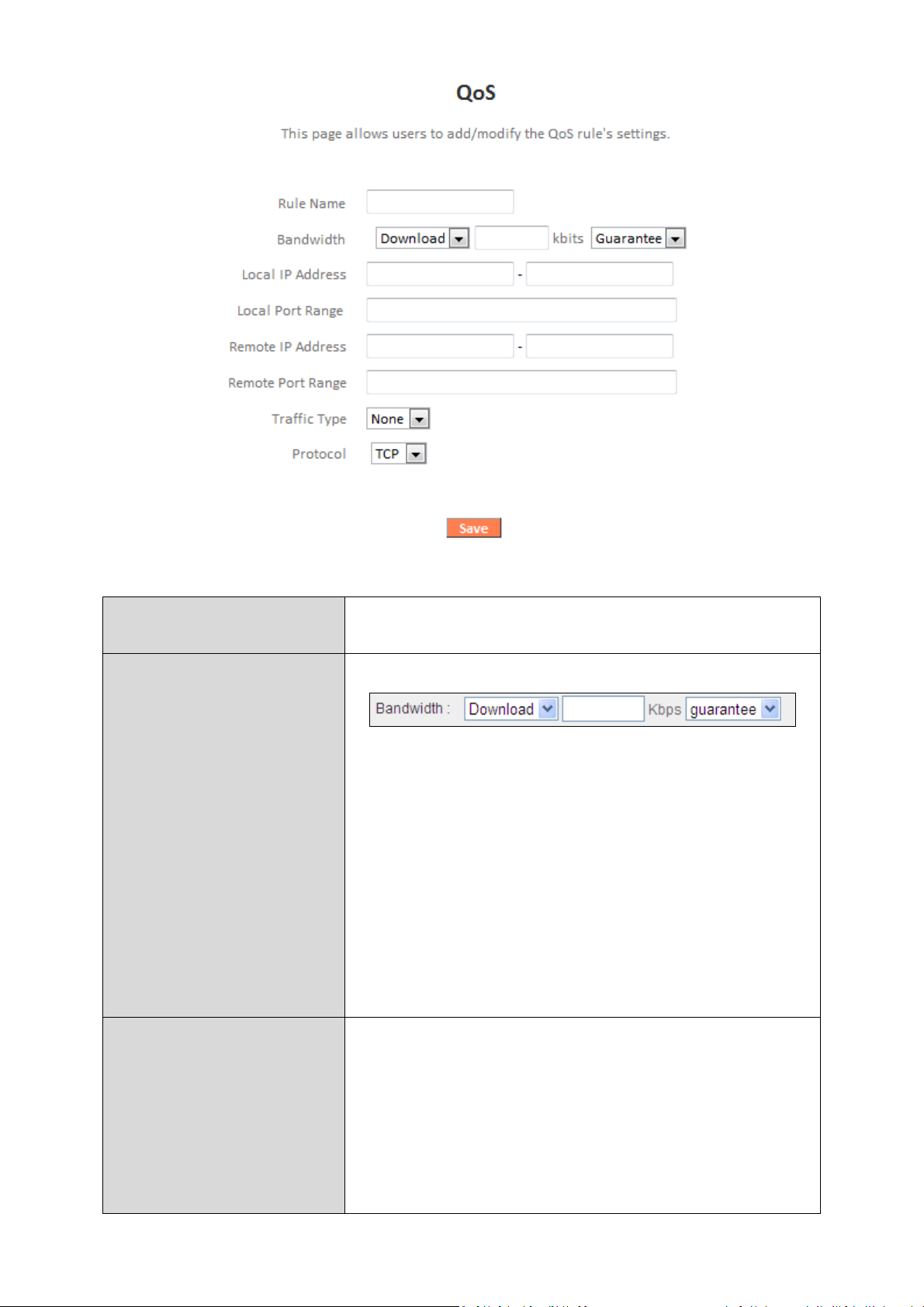
Rule Name
Enter a name for the QoS rule for
reference/identification.
Bandwidth
Set the
bandwidth limits for the
QoS rule:
(maximum).
Local IP Address
Enter
the IP address range
to which the
QoS
IP address.
(1) (2) (3)
1. Select “Download” or “Upload” for the
QoS rule.
2. Enter the bandwidth limit.
3. Select whether the bandwidth is a
“Guarantee” (minimum) or “Max”
rule will be applied.
Enter a starting IP address in the left field
and the end IP address in the right field to
define a range of IP addresses; or enter an IP
address in the left field only to define a single
86
Page 11
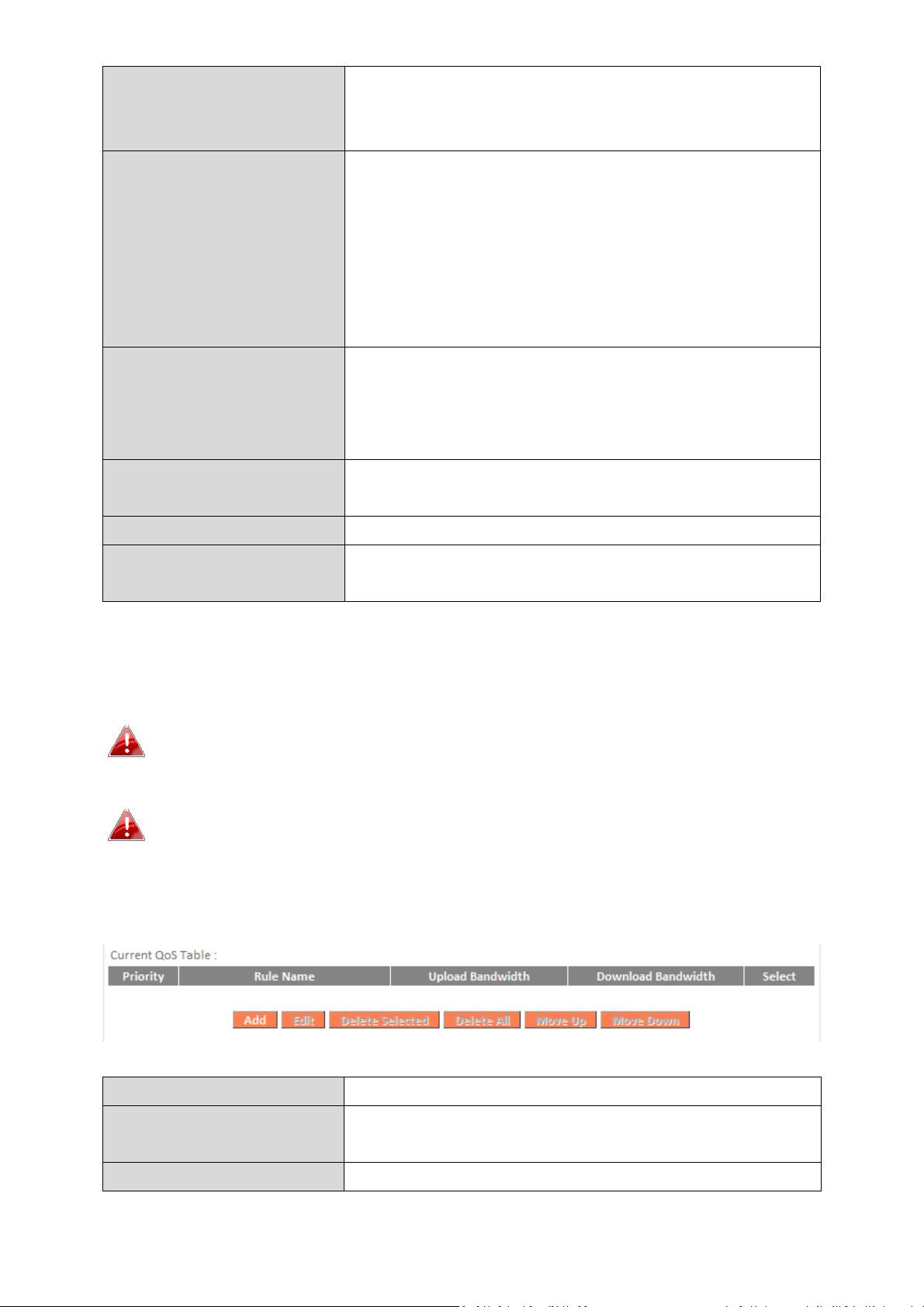
Local Port Range
Enter
the port range
to activate the QoS rule.
Enter a single port number e.g. 110 or a
range of port numbers e.g. 11
0-120
Remote IP Address
Enter
the
remote
IP address range
which will
IP address.
Remote Port Range
Enter
the
remote
port range
to activate the
range of port numbers e.g. 110
-
120
Traffic Type
Select
traffic type as an alternative to
specifying a
po
rt range above.
Protocol
Select a “
TCP
” or “UDP
” protocol type
.
Save
Click ‘add’ button to add a new QoS rule
(detailed instructions will be given below).
Edit
Edit a selected rule.
Delete Selected/
Delete All
Delete selected or all entries from the
table.
Move Up/Down
Move selected rule up
or down the list.
activate the QoS rule.
Enter a starting IP address in the left field
and the end IP address in the right field to
define a range of IP addresses; or enter an IP
address in the left field only to define a single
QoS rule.
Enter a single port number e.g. 110 or a
QoS rule entries will be listed in the “Current QoS Table” as shown below.
Select a rule using the “Select” checkbox.
When using the “Edit” button only one rule can be selected each
time.
QoS rules will be processed in the order that they are listed i.e.
the rule at the top of the list will be applied first, and then the
second rule etc. The order can be adjusted using the “Move
Up/Down” buttons.
87
Page 12
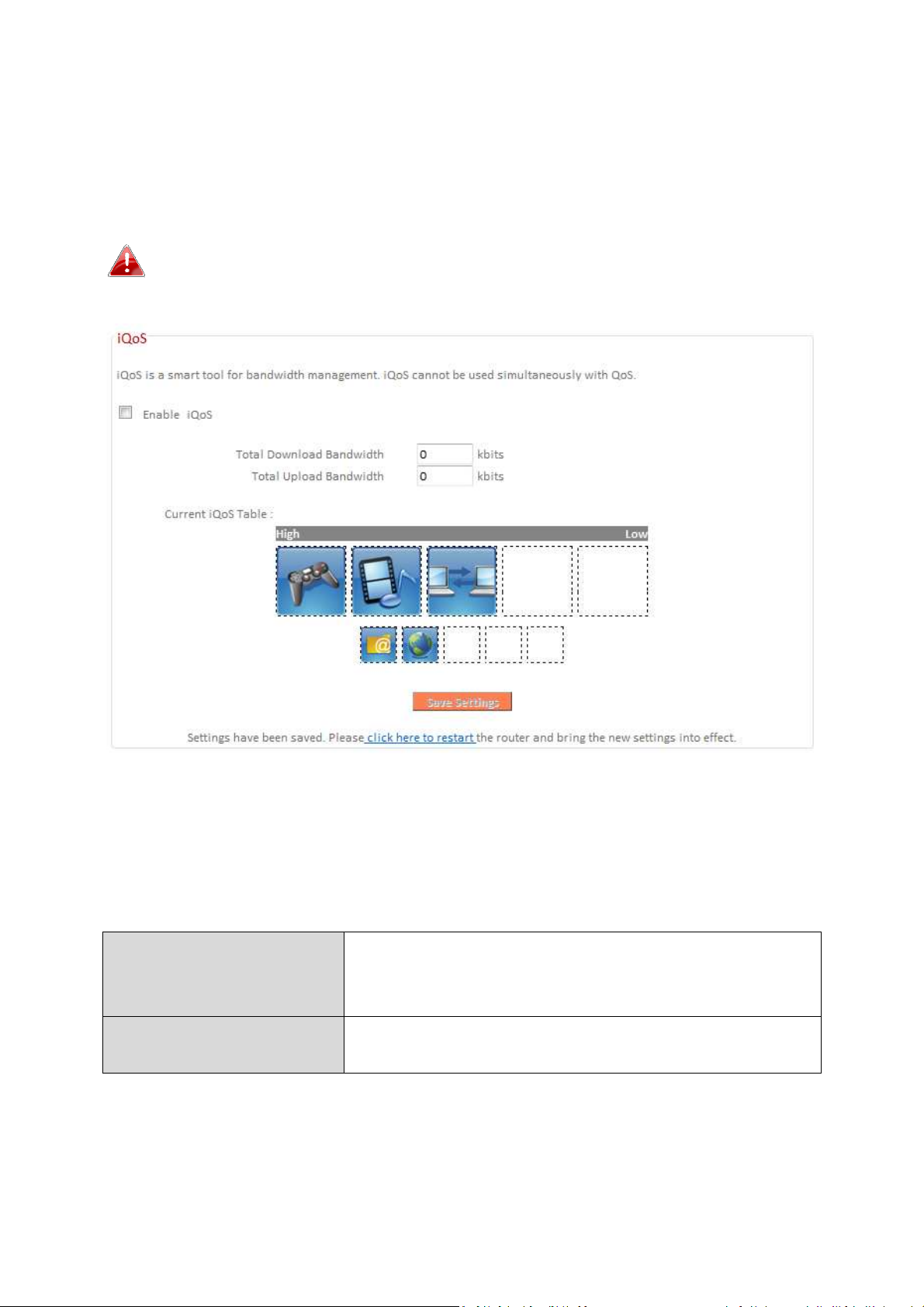
III-3-7-2. iQoS
Total Download
Enter your total download bandwidth limit
kbits.
Total Upload
Bandwidth
Enter you
r total
upload
bandwidth limit from
your Internet service provider (ISP) in kbits.
iQoS is a more intuitive and automated tool to manage internet bandwidth
than manually configuring the settings using QoS. For online gamers or users
with bandwidth requirements for audio/video, iQoS is a useful function.
iQoS cannot be used in conjunction with QoS and vice-versa.
When one is enabled, the other is automatically disabled.
Check/uncheck the box “Enable iQoS” to enable/disable the iQoS function,
and then enter your bandwidth limits and arrange the network application
icons in priority order in the “Current iQoS Table”. Icons with higher priority
will be assigned bandwidth more efficiently for better performance.
Bandwidth
from your Internet service provider (ISP) in
88
Page 13

The icons represent the following categories:
Internet Browsing
P2P/BT Downloads
FTP
Multimedia
Online Gaming
The iQoS table is ordered left to right, high to low priority. Click a small icon
below the table to insert it into the table, and click a large icon in the table to
remove it. All spaces in the priority table must be filled.
89
Page 14
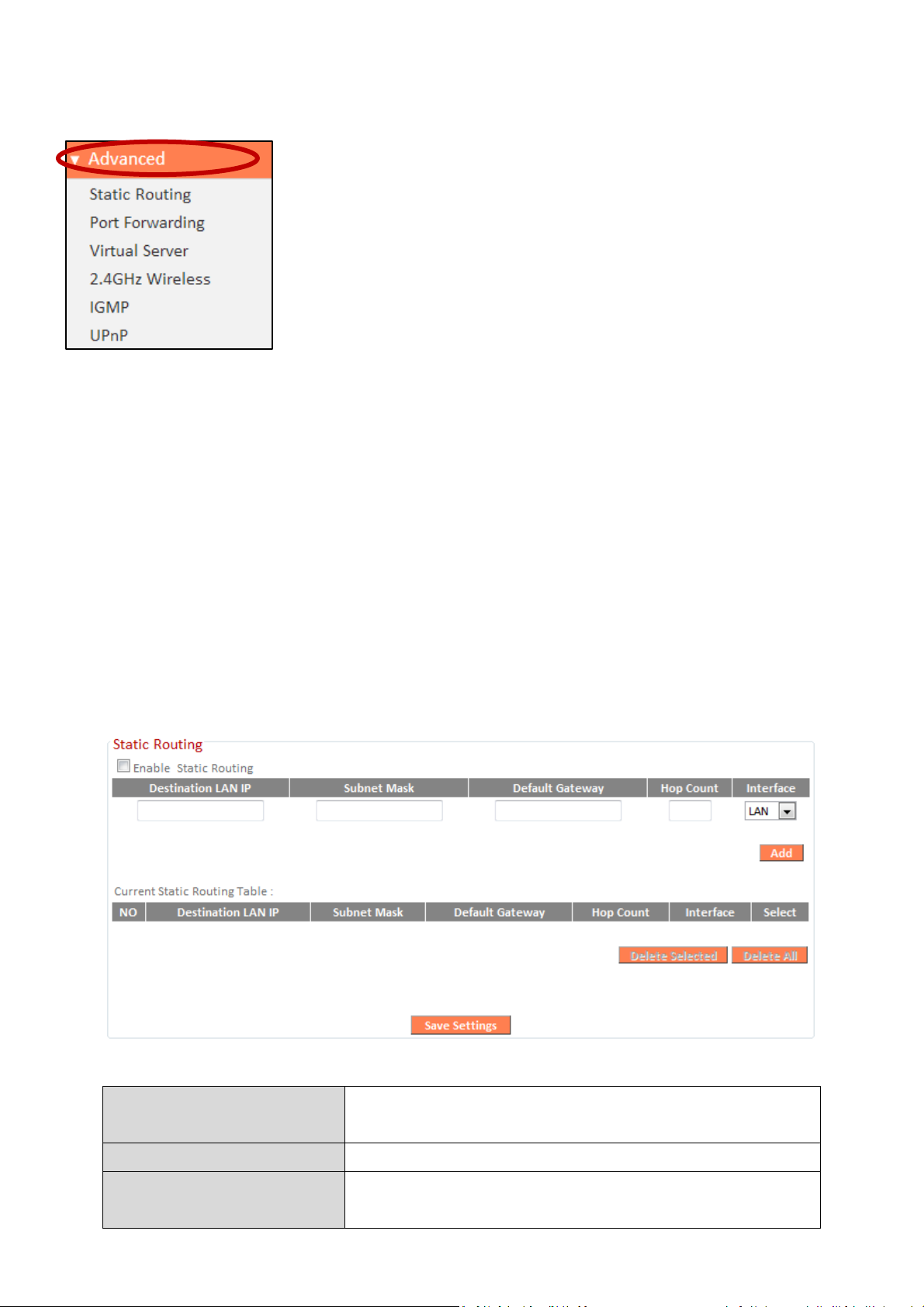
III-3-8. Advanced
Enable Static Routing
Check/uncheck the box to enable/d
isable
static routing.
Destination LAN IP
Enter the destination network’s IP address.
Subnet Mask
Enter the subnet mask of the destination
network.
Advanced features of the BR-6428nS V3/BR-6228nS V3
can be configured from the “Advanced” menu.
III-3-8-1. Static Routing
Static routing is a method of configuring path selection of routers,
characterized by the absence of communication between routers regarding
the current topology of the network. The opposite of static routing is dynamic
routing, sometimes also referred to as adaptive routing.
You can configure static routing and manually add routes to the routing table
shown below.
90
Page 15
Default Gateway
Enter the default gateway of the destination
network.
Hop Count
Enter the hop count (the
distance between
destination network and this broadband
router) here.
Interface
Enter the interface which leads to
destination network.
Add
Add the route to the current static routing
table.
Delete Selected/
Delete All
Delete selected or all entries from the table.
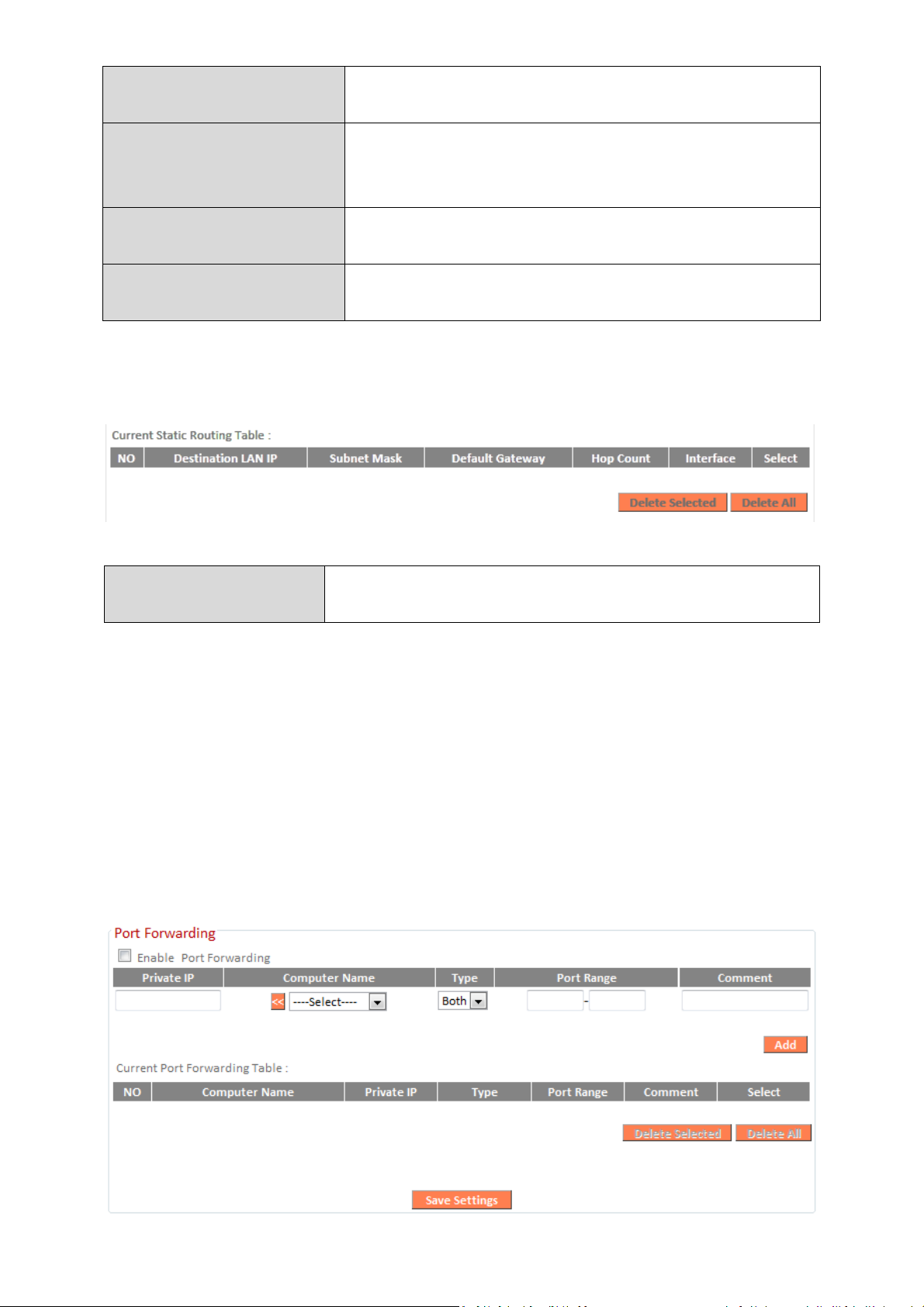
Static Routing Table entries will be displayed in the table shown below:
III-3-8-2. Port Forwarding
This function allows you to redirect a single port or consecutive ports of an
Internet IP address to the same port of a local IP address. The port number(s)
of the Internet IP address and local IP address must be the same.
If the port number of the Internet IP address and local IP address is different,
please use the “Virtual Server” function instead.
91
Page 16

Private IP
Enter the IP address
of the computer on the
local network.
Computer Name
Windows computers on the local network
IP address to the “Private IP” field.
Type
Select the type o
f connect
ion, “
TCP
”, “
UDP
”
or “Both”.
Port Range
Input the starting port number in the left
number in the left field.
Comment
Enter a
comment for reference or
identification.
Delete Selected/
Delete All
Delete selected or all entries from the table.
will be listed here – select a computer from
the list and click << to automatically add the
field, and input the ending port number in
the right field. If you only want to redirect a
single port number, only enter a port
Port Forwarding Table entries will be displayed in the table shown below:
92
Page 17
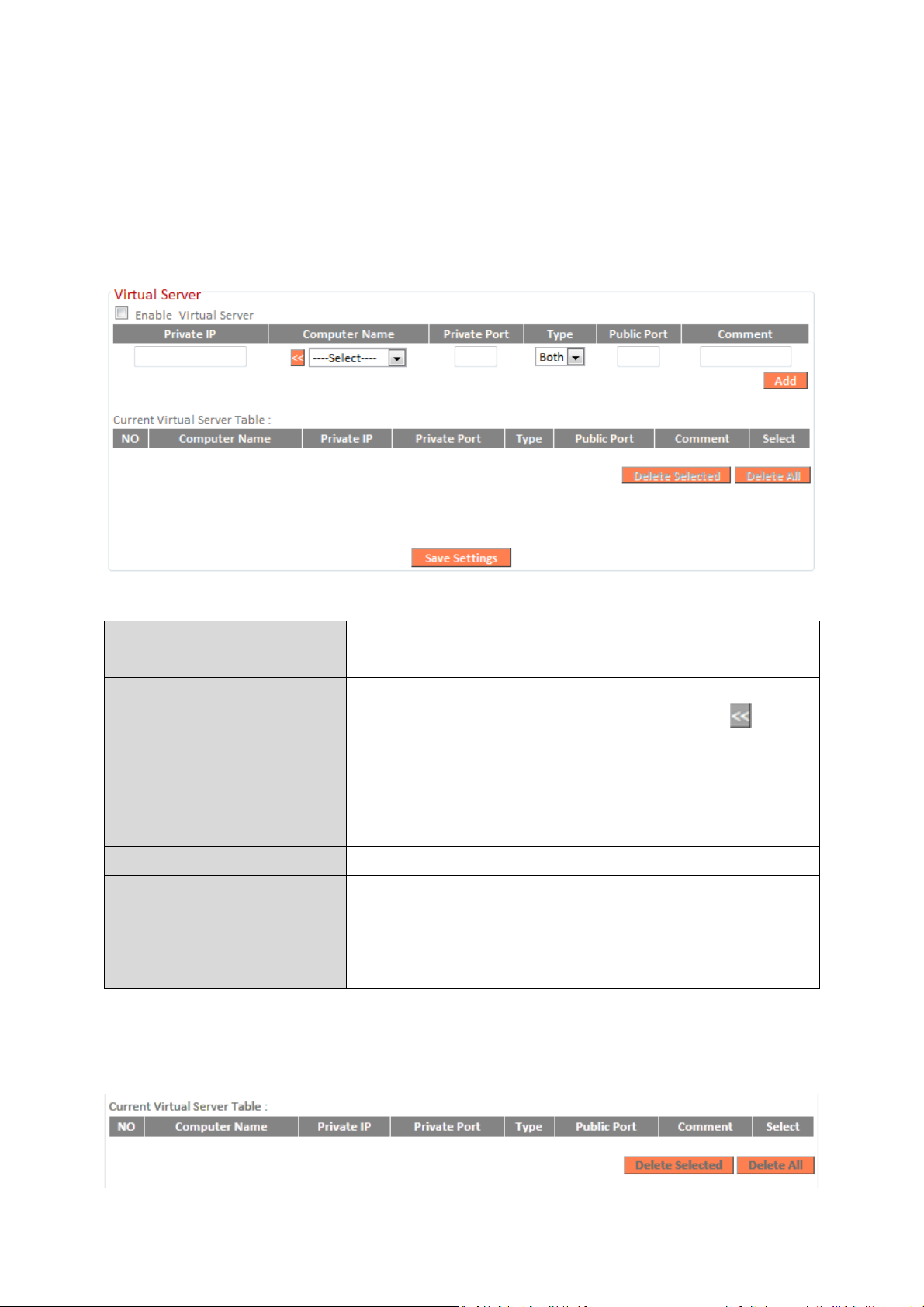
III-3-8-3. Virtual Server
P
rivate IP
Specify the IP address of the computer on
your local network.
Computer Name
Select the name of a Windows computer
field.
Private Port
Specify the private port
you wish to use on
the computer in your local network.
Type
Select the type of Internet Protocol.
Public Port
Specify a public port to access the computer
on your local network.
Comment
Enter a comment for reference or
identification.
This function allows you to set up an internet service on a local computer,
without exposing the local computer to the internet. You can also build
various sets of port redirection, to provide various internet services on
different local computers via a single internet IP address.
from the drop-down menu and click to
auto-input its IP address in the “Private IP”
Current Virtual Table entries will be displayed in the table shown below:
93
Page 18
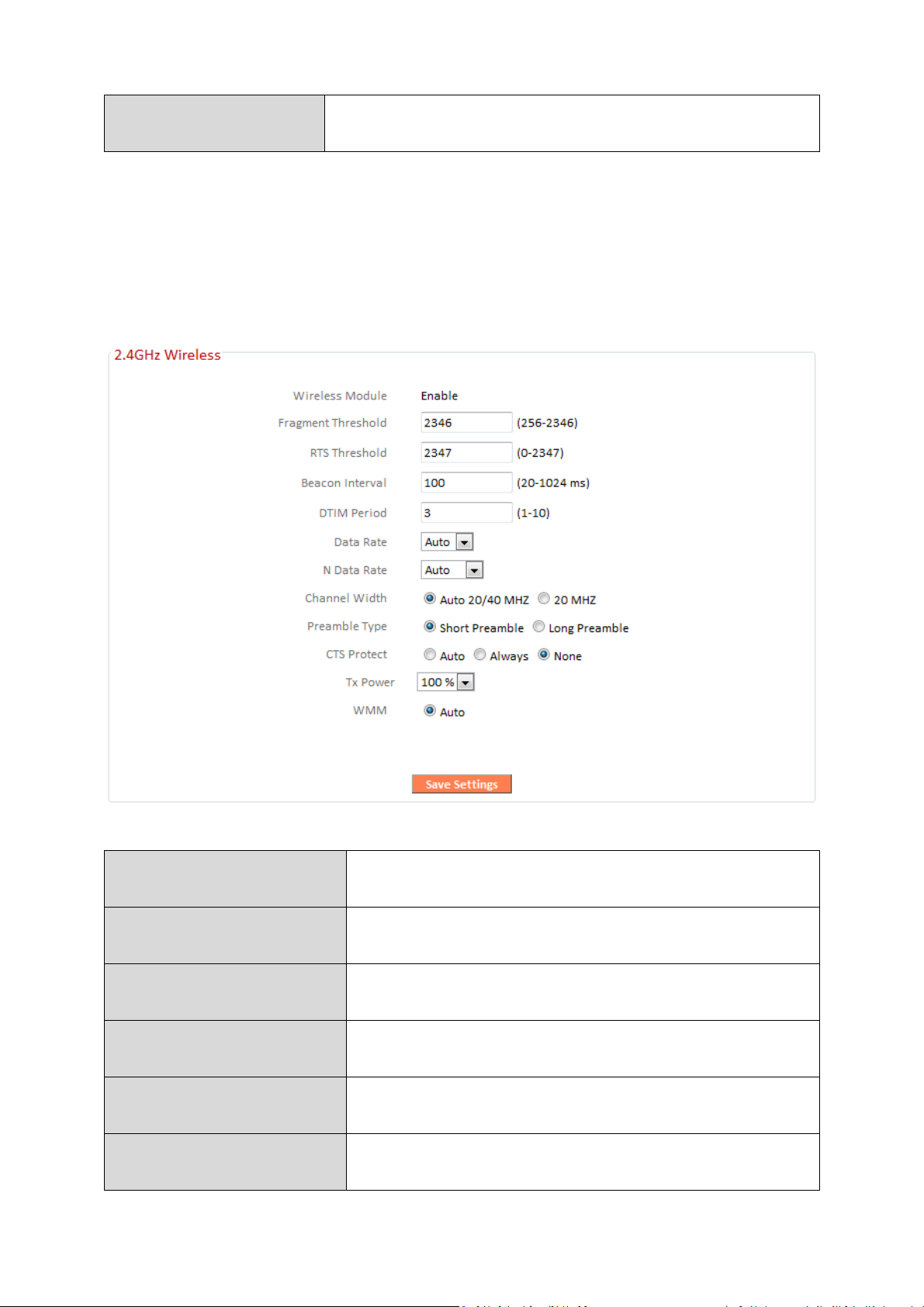
Fragment Threshold
Set the Fragment threshold of
the
wireless
radio. T
he
default value is 2346.
RTS Threshold
Set the RTS threshold of
the
wireless radio.
T
he
default value is 2347.
Beaco
n Interval
Set the beacon interval of
the
wireless radio.
T
he
default value is 100.
DTIM Period
Set the DTIM period of wireless radio. T
he
default value is 3.
Data Rate
Set the wireless data transfer rate. T
he
defau
lt is set to A
uto.
N Data Rate
Set the
data rate of 802.11
n
. T
he
default is
set to Auto
.
Delete Selected/
Delete All
Delete selected or all entries from the table.
III-3-8-4. 2.4GHz Wireless
These settings are for experienced users only. Please do not change any of the
values on this page unless you are already familiar with these functions.
94
Page 19
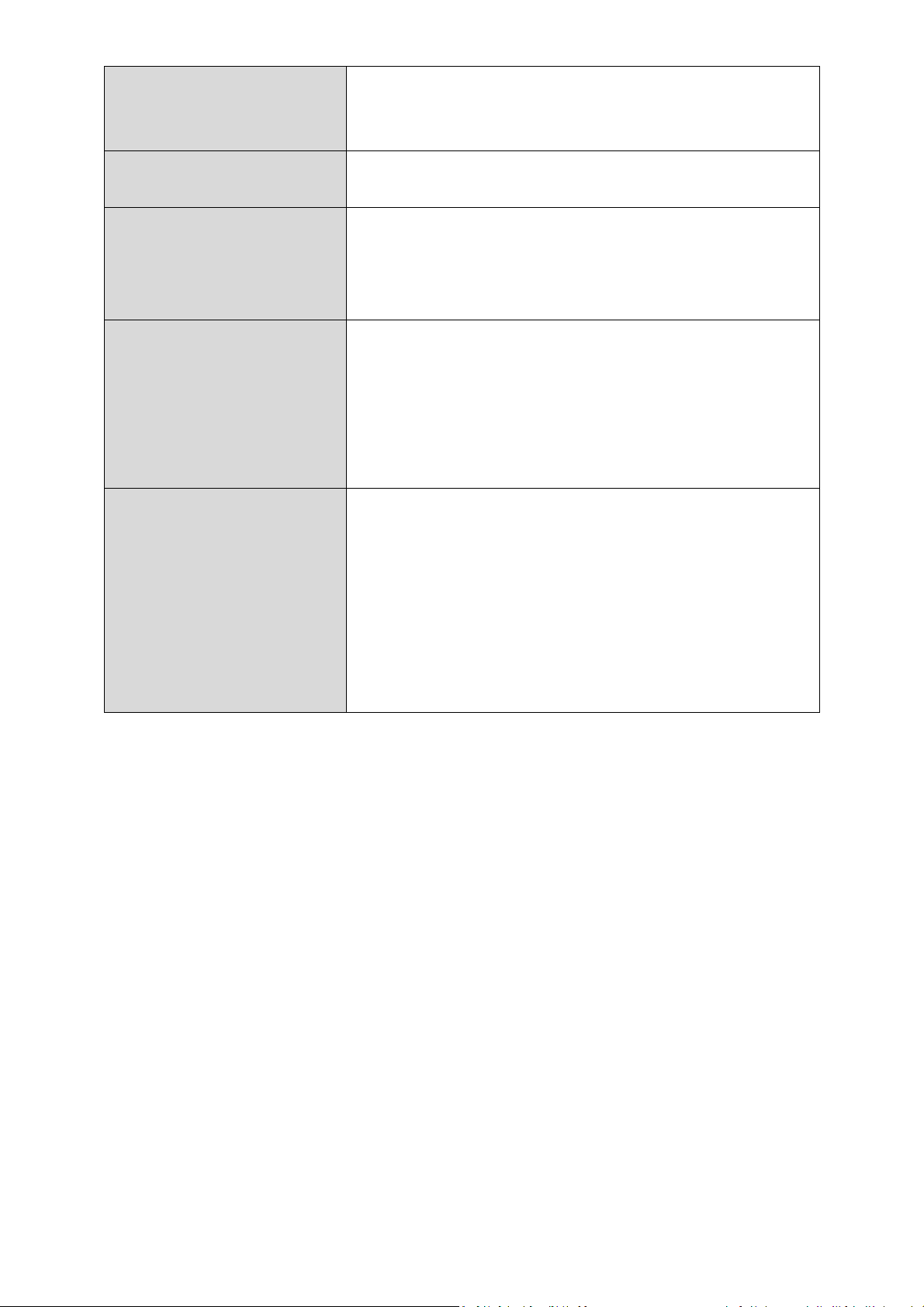
Channel Width
Select wireless channel width (bandwidth
used by wireless signals from the device) –
the recommended value is Auto 20/40MHz.
Preamble Type
Set the wireless radio
preamble type.
The
default
value is “Short Preamble”.
CTS Protect
Enabling
this setting will reduce the chance
recommended to set this option to “Auto”.
Tx Power
Set the power output of
the
wireles
s radio.
access your signal.
WMM
WMM (Wi
-
Fi Multimedia) technology
can
responses
for better performance.
of radio signal collisions between 802.11b
and 802.11g wireless access points. It’s
You may not require 100% output power.
Setting a lower power output can enhance
security since potentially malicious/unknown
users in distant areas will not be able to
improve the performance of certain network
applications, such as audio/video streaming,
network telephony (VoIP) and others. When
WMM is enabled, the device will prioritize
different kinds of data and give higher
priority to applications which require instant
95
Page 20
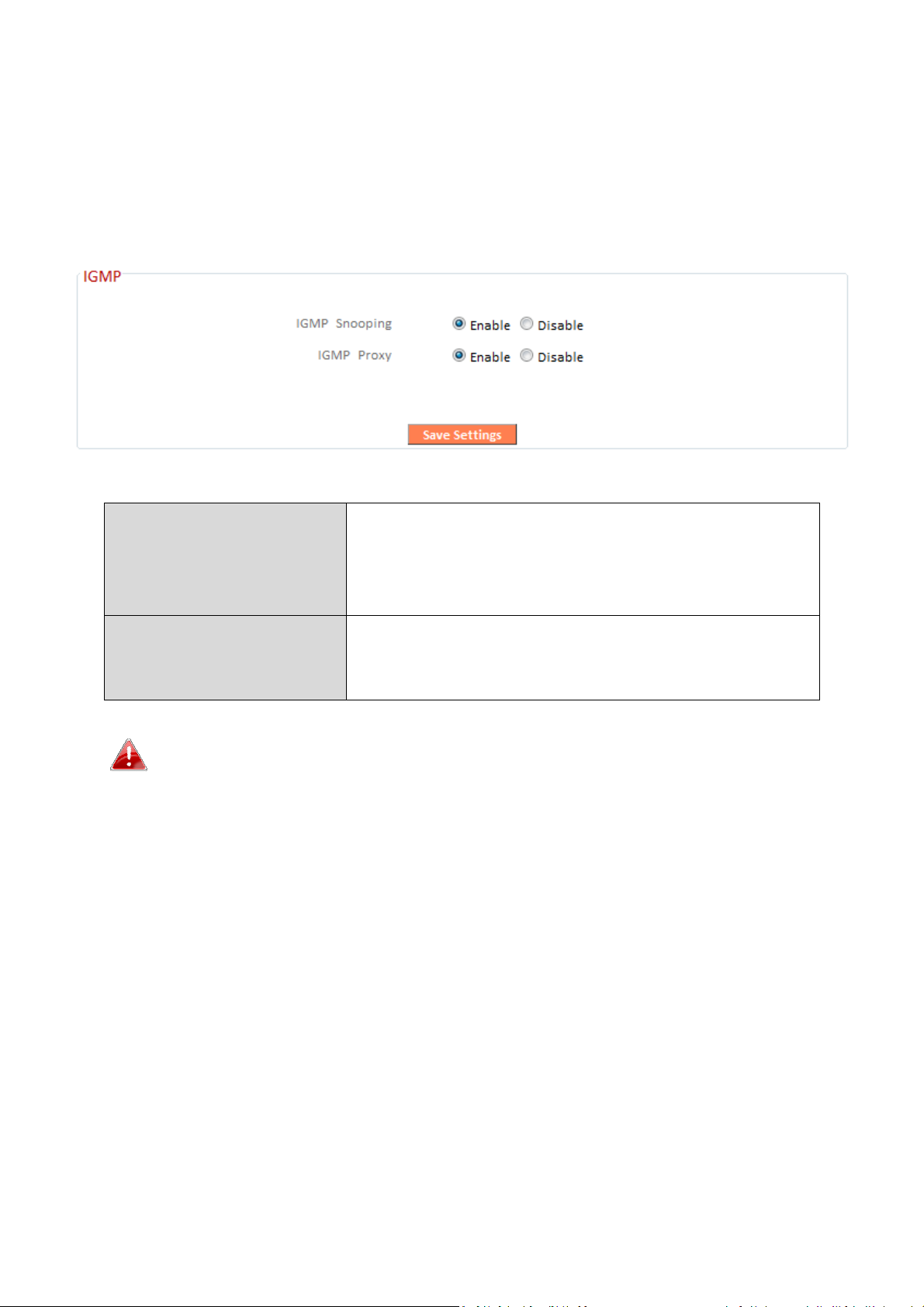
III-3-8-5. IGMP
IGMP Snoop
ing
IGMP snooping monitors traffic between
disable.
IGMP Proxy
IGMP proxy enables intelligent multicast
information. Select enable or disa
ble.
IGMP is a communications protocol used to establish multicast group
memberships. It allows for a more efficient use of resources and better
performance for applications such as IPTV video streaming.
hosts and multicast routers to facilitate
bandwidth conservation. Select enable or
forwarding based on IGMP snooping
It is recommended to set “IGMP Snooping” and “IGMP Proxy” to
“Enable”.
96
Page 21
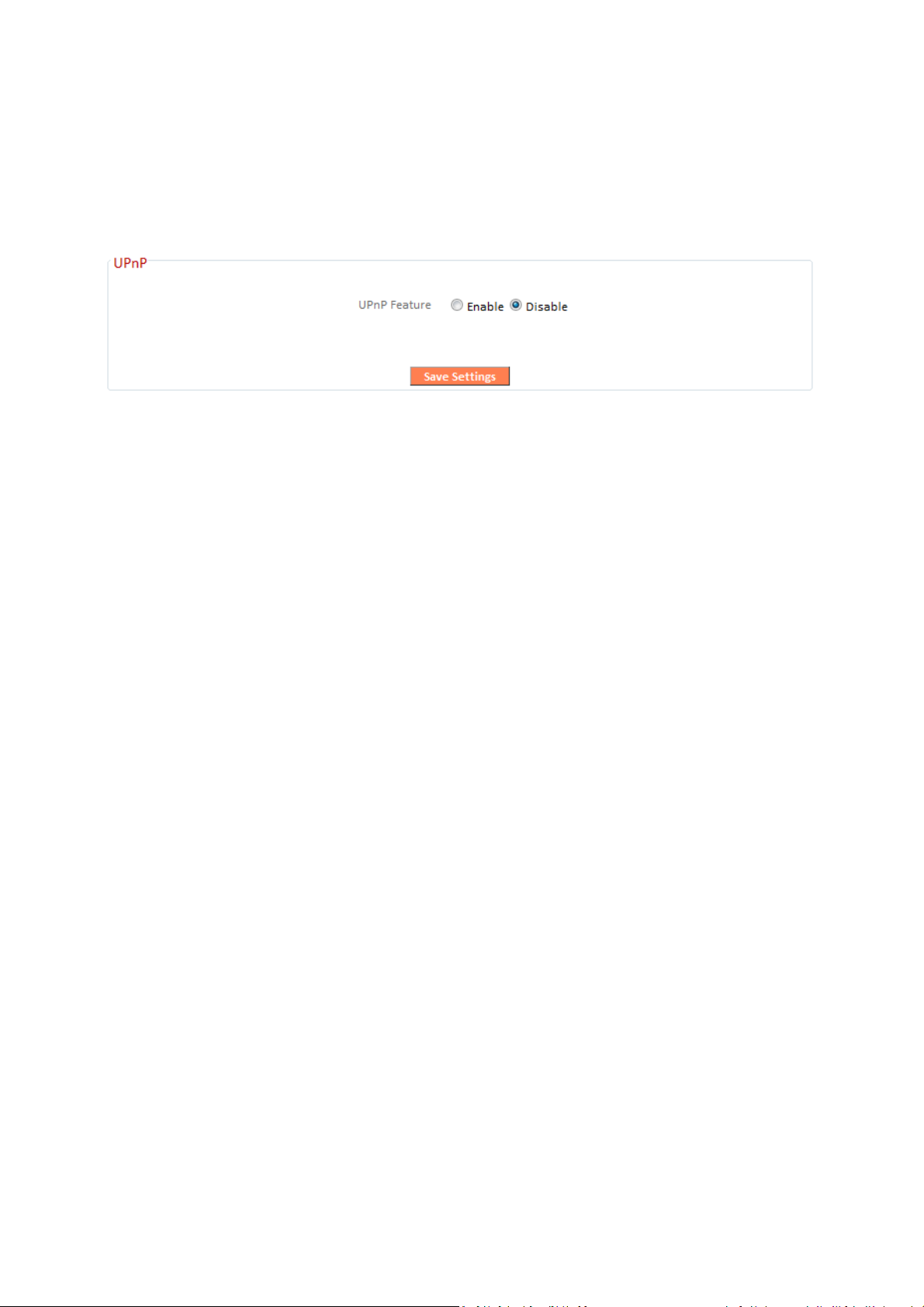
III-3-8-6. UPnP
Universal plug-and-play (UPnP) is a set of networking protocols which enables
network devices to communicate and automatically establish working
configurations with each other. Select “Enable” or “Disable”.
97
Page 22
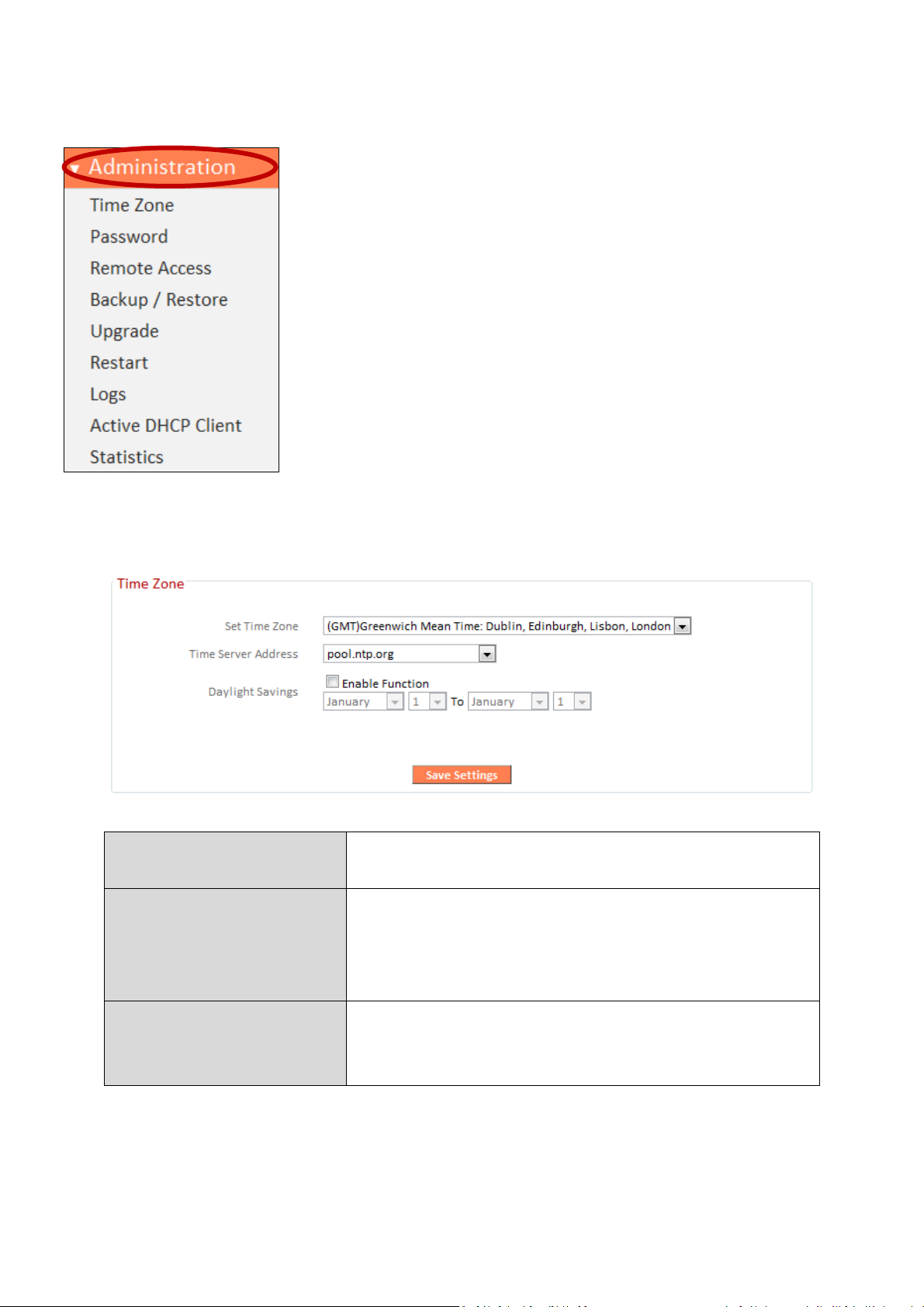
III-3-9. Administration
Set Time Zone
Select the time zone of your country or
reg
ion
.
Time Server Address
The travel router supports NTP (Network
manually.
Daylight Saving
If your country/region uses daylight saving
box, and select the start and end date.
III-3-9-1. Time Zone
Various administrative functions can be accessed from
the “Administration” menu.
Time Protocol) for automatic time and date
setup. Input the host name of the IP server
time, please check the “Enable Function”
98
Page 23
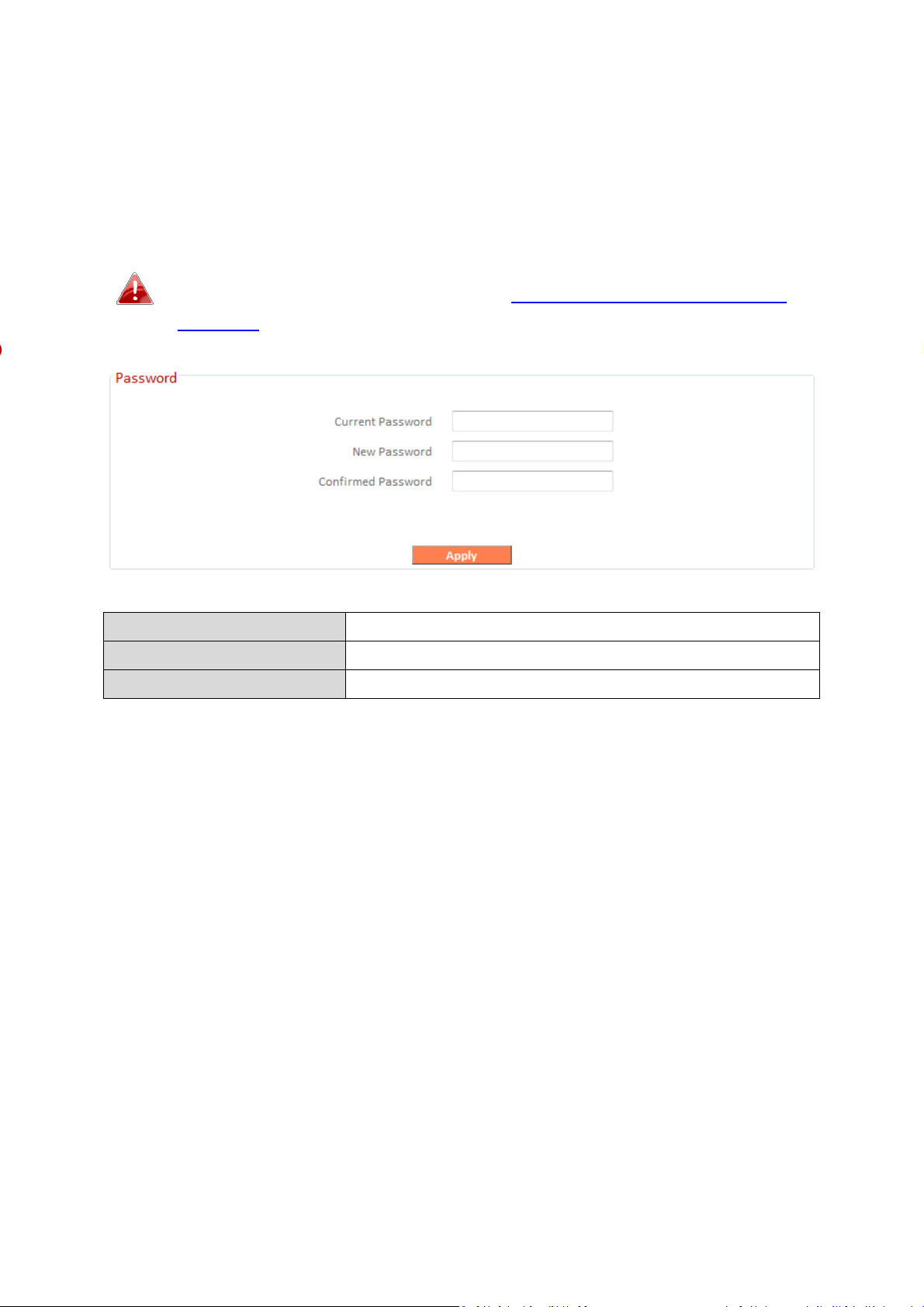
III-3-9-2. Password
Current Password
Enter your cur
rent password.
New Password
Enter your new password.
Confirmed Password
Confirm your new password.
You can change the password used to login to the browser-based
configuration interface here. It is advised to do so for security purposes.
Please make a note of the new password. In the event that you
forget the password and are unable to login to the browser
based configuration interface, see II-7. Reset to factory default
settings for how to reset the device.
99
Page 24
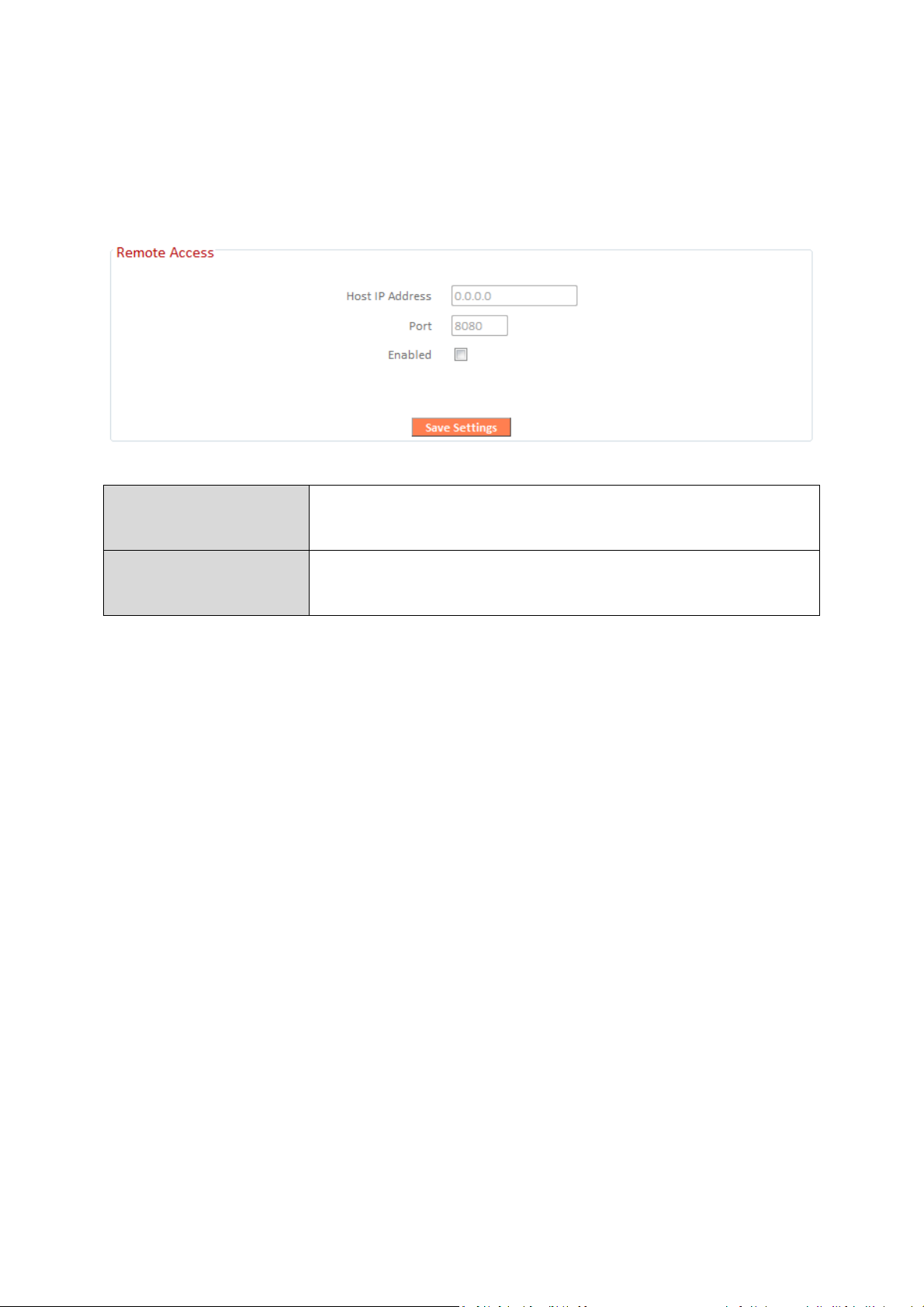
III-3-9-3. Remote Access
Check “Enabled” to enable the remote access feature and then enter the
appropriate values.
Host IP Address
Port
Specify the IP address which is allowed remote
access.
Specify a port number (0–65535) used for
remote access.
100
Page 25

III-3-9-4. Backup/Restore
Backup Settings
Click
“
Save
” to save the current settings on your
computer as config.bin file.
Restore Settings
Click
“Browse
” to find a previously saved
your current settings.
Restore to
Click
“
Reset
” to restore settings to the factory
“Ok”
. See below for more information.
config.bin file and then click “Upload” to replace
Factory Default
default. A pop-up window will appear and ask
you to confirm and enter your log in details.
Enter your username and password and click
III-3-9-5. Upgrade
The upgrade page allows you to upgrade the system firmware to a more
recent version. You can download the latest firmware from the Edimax
website. After the upgrade, the system will restart.
Do not switch off or disconnect the device during a firmware
upgrade, as this could damage the device. It is recommended that
you use a wired Ethernet connection for a firmware upgrade.
101
Page 26

III-3-9-6. Restart
In the event that the router malfunctions or is not responding, then it is
recommended that you restart the device.
III-3-9-7. Logs
You can view the system log and security log here. Use the drop down menu
in the top-right corner to select which log to view.
102
Page 27

Save
Click
“
Save
” to save the
log on your computer
as
.txt
file.
Clear
Click
“Clear” to clear/erase the existing log.
Refresh
Click “Refresh” to refresh the log and update any
activity.
III-3-9-8. Active DHCP Client
Information about active DHCP clients is shown in the table, which displays
the DHCP server assigned IP address, MAC address and time expired for
each computer or device on the local network.
III-3-9-9. Statistics
Displays sent and received packet network statistics.
103
Page 28

IV. Appendix
IV-1. Configuring your IP address
For first time access to the URL http://Edimax.Setup please ensure your
computer is set to use a dynamic IP address. This means your computer can
obtain an IP address automatically from a DHCP server. You can check if your
computer is set to use a dynamic IP address by following IV-1-1. How to check
that your computer uses a dynamic IP address.
Static IP users can also temporarily modify your computer’s IP address to be
in the same IP address subnet e.g. 192.168.2.x (x = 3 – 254) as the BR-6428nS
V3/BR-6228nS V3 in order to access http://Edimax.Setup.
The BR-6428nS V3/BR-6228nS V3’s default IP address is
192.168.2.1.
The procedure for modifying your IP address varies across different operating
systems; please follow the guide appropriate for your operating system in
IV-1-2. How to modify the IP address of your computer.
Static IP users please make a note of your static IP before you
change it.
You can assign a new IP address to the device which is within the subnet of
your network during setup or using the browser based configuration interface
(refer to III-3-4. LAN). Then you can access the URL http://Edimax.Setup in
future without modifying your IP address.
Please remember to change your IP address back to its original
value after the device is properly configured.
104
Page 29

IV-1-1. How to check that your computer uses a dynamic IP address
Please follow the instructions appropriate for your operating system.
IV-1-1-1. Windows XP
1.
Click the “Start” button (it should be located in the lower-left corner of
your computer), then click “Control Panel”. Double-click the “Network and
Internet Connections” icon, click “Network Connections”, and then
double-click “Local Area Connection”. The “Local Area Connection Status”
window will then appear, click “Properties”.
2.
“Obtain an IP address automatically” and “Obtain DNS server address
automatically” should be selected.
105
Page 30

106
Page 31

IV-1-1-2. Windows Vista
1.
Click the “Start” button (it should be located in the lower-left corner of
your computer), then click “Control Panel”. Click “View Network Status and
Tasks”, then click “Manage Network Connections”. Right-click “Local Area
Network”, then select “Properties”. The “Local Area Connection Properties”
window will then appear, select “Internet Protocol Version 4 (TCP / IPv4)”,
and then click “Properties”.
2.
Select “Obtain an IP address automatically” and “Obtain DNS server
address automatically” should be selected.
107
Page 32

108
Page 33

IV-1-1-3. Windows 7
1.
Click the “Start” button (it should be located in the lower-left corner of
your computer), then click “Control Panel”.
2.
Under “Network and Internet” click “View network status and tasks”.
3.
Click “Local Area Connection”.
109
Page 34

4.
Click “Properties”.
5.
Select “Internet Protocol Version 4 (TCP/IPv4) and then click “Properties”.
110
Page 35

6.
Select “Obtain an IP address automatically” and “Obtain DNS server
address automatically” should be selected.
111
Page 36

IV-1-1-4. Windows 8
1.
From the Windows 8 Start screen, you need to switch to desktop mode.
Move your curser to the bottom left of the screen and click.
2.
In desktop mode, click the File Explorer icon in the bottom left of the
screen, as shown below.
3.
Right click “Network” and then select “Properties”.
112
Page 37

4.
In the window that opens, select “Change adapter settings” from the left
side.
5.
Choose your connection and right click, then select “Properties”.
113
Page 38

6.
Select “Internet Protocol Version 4 (TCP/IPv4) and then click “Properties”.
7.
Select “Obtain an IP address automatically” and “Obtain DNS server
address automatically” should be selected.
114
Page 39

115
Page 40

IV-1-1-5. Mac OS
1.
Have your Macintosh computer operate as usual, and click on “System
Preferences”.
2.
In System Preferences, click on “Network”.
3.
Click on “Wi-Fi” in the left panel and then click “Advanced” in the lower
right corner.
4.
Select “TCP/IP” from the top menu and “Using DHCP” in the drop down
menu labeled “Configure IPv4” should be selected.
116
Page 41

117
Page 42

IV-1-2. How to modify the IP address of your computer
Please follow the instructions appropriate for your operating system. In the
following examples we use the IP address 192.168.2.10 though you can use
any IP address in the range 192.168.2.x (x = 3 – 254) in order to access iQ
Setup/browser based configuration interface.
Please make a note of your static IP before you change it.
IV-1-2-1. Windows XP
1.
Click the “Start” button (it should be located in the lower-left corner of
your computer), then click “Control Panel”. Double-click the “Network and
Internet Connections” icon, click “Network Connections”, and then
double-click “Local Area Connection”. The “Local Area Connection Status”
window will then appear, click “Properties”.
2.
Select “Use the following IP address” and “Use the following DNS server
addresses”, then input the following values:
118
Page 43

Your existing static IP address will be displayed in the “IP
address” field before you replace it. Please make a note of this IP
address, subnet mask, default gateway and DNS server
addresses.
IP address: 192.168.2.10
Subnet Mask: 255.255.255.0
Preferred DNS Server: 192.168.2.1
Click ‘OK’ when finished.
119
Page 44

IV-1-2-2. Windows Vista
1.
Click the “Start” button (it should be located in the lower-left corner of
your computer), then click “Control Panel”. Click “View Network Status and
Tasks”, then click “Manage Network Connections”. Right-click “Local Area
Network”, then select “Properties”. The “Local Area Connection Properties”
window will then appear, select “Internet Protocol Version 4 (TCP / IPv4)”,
and then click “Properties”.
2.
Select “Use the following IP address” and “Use the following DNS server
addresses”, then input the following values:
Your existing static IP address will be displayed in the “IP
address” field before you replace it. Please make a note of this IP
address, subnet mask, default gateway and DNS server
addresses.
IP address: 192.168.2.10
Subnet Mask: 255.255.255.0
Preferred DNS Server: 192.168.2.1
Click ‘OK’ when finished.
120
Page 45

IV-1-2-3. Windows 7
1.
Click the “Start” button (it should be located in the lower-left corner of
your computer), then click “Control Panel”.
2.
Under “Network and Internet” click “View network status and tasks”.
3.
Click “Local Area Connection”.
121
Page 46

4.
Click “Properties”.
122
Page 47

5.
Select “Internet Protocol Version 4 (TCP/IPv4) and then click “Properties”.
6.
Select “Use the following IP address” and “Use the following DNS server
addresses”, then input the following values:
Your existing static IP address will be displayed in the “IP
address” field before you replace it. Please make a note of this IP
address, subnet mask, default gateway and DNS server
addresses.
IP address: 192.168.2.10
Subnet Mask: 255.255.255.0
Preferred DNS Server: 192.168.2.1
Click ‘OK’ when finished.
123
Page 48

IV-1-2-4. Windows 8
1.
From the Windows 8 Start screen, you need to switch to desktop mode.
Move your curser to the bottom left of the screen and click.
2.
In desktop mode, click the File Explorer icon in the bottom left of the
screen, as shown below.
124
Page 49

3.
Right click “Network” and then select “Properties”.
4.
In the window that opens, select “Change adapter settings” from the left
side.
125
Page 50

5.
Choose your connection and right click, then select “Properties”.
6.
Select “Internet Protocol Version 4 (TCP/IPv4) and then click “Properties”.
126
Page 51

7.
Select “Use the following IP address” and “Use the following DNS server
addresses”, then input the following values:
Your existing static IP address will be displayed in the “IP
address” field before you replace it. Please make a note of this IP
address, subnet mask, default gateway and DNS server
addresses.
IP address: 192.168.2.10
Subnet Mask: 255.255.255.0
Preferred DNS Server: 192.168.2.1
Click ‘OK’ when finished.
127
Page 52

IV-1-2-5. Mac
1.
Have your Macintosh computer operate as usual, and click on “System
Preferences”
2.
In System Preferences, click on “Network”.
3.
Click on “Wi-Fi” in the left panel and then click “Advanced” in the lower
right corner.
4.
Select “TCP/IP” from the top menu and select “Manually” from the drop
down menu labeled “Configure IPv4”, then click “OK”.
128
Page 53

Your existing static IP address will be displayed in the “IP
address” field before you replace it. Please make a note of this IP
address, subnet mask, default gateway and DNS server
addresses.
5.
In the “IPv4 Address” and “Subnet Mask” field enter IP address
192.168.2.10 and subnet mask 255.255.255.0. Click on “OK”.
129
Page 54

6.
Click “Apply” to save the changes.
130
Page 55

IV-1-3. How to Find Your Network Security Key
To find your network security key, please follow the instructions appropriate
for your operating system.
If you are using Windows XP or earlier, please contact your ISP or
router manufacturer to find your network security key.
IV-1-3-1. Windows 7 & Vista
1.
Open “Control Panel” and click on “Network and Internet” in the top
menu.
2.
Click on “View network status and tasks” which is under the heading
“Network and Sharing Center”.
3.
Click on “Manage wireless networks” in the left menu.
131
Page 56

4.
You should see the profile of your Wi-Fi network in the list. Right click on
your Wi-Fi network and then click on “Properties”.
5.
Click on the “Security” tab, and then check the box labeled “Show
characters”. This will show your network security key. Click the “Cancel”
button to close the window.
132
Page 57

IV-1-3-2. Mac
1.
Open a new Finder window, and select “Applications” from the menu on
the left side. Open the folder labeled “Utilities” and then open the
application “Keychain Access”.
2.
Select “Passwords” from the sub-menu labeled “Category” on the left side,
as shown below. Then search the list in the main panel for the SSID of your
network. In this example, the SSID is “EdimaxWireless” – though your SSID
will be unique to your network.
133
Page 58

3.
Double click the SSID of your network and you will see the following
window.
4.
Check the box labeled “Show password” and you will be asked to enter
your administrative password, which you use to log into your Mac. Enter
your password and click “Allow”.
134
Page 59

Your network security password will now be displayed in the field next to
the box labeled “Show password”. In the example below, the network
security password is “edimax1234”. Please make a note of your network
security password.
135
Page 60

IV-1-4. How to Find Your Router’s IP Address
To find your router’s IP address, please follow the instructions appropriate for
your operating system.
IV-1-4-1. Windows XP, Vista & 7
1.
Go to “Start”, select “Run” and type “cmd”, then press Enter or click “OK”.
2.
A new window will open, type “ipconfig” and press Enter.
136
Page 61

3.
Your router’s IP address will be displayed next to “Default Gateway”.
137
Page 62

IV-1-4-2. Windows 8
1.
From the Windows 8 Start screen, move your curser to the top right
corner of the screen to display the Charms bar.
2.
Click “Search” and enter “cmd” into the search bar. Click the “Command
Prompt” app which be displayed on the left side.
138
Page 63

3.
A new window will open, type “ipconfig” and press Enter.
139
Page 64

4.
Your router’s IP address will be displayed next to “Default Gateway”.
140
Page 65

IV-1-4-3. Mac
1.
Launch “System Preferences” and click on “Network”.
2.
If you are using an Ethernet cable to connect to your network, your
router’s IP address will be displayed next to “Router”.
3.
If you are using Wi-Fi, click “Wi-Fi” in the left panel, and then “Advanced”
in the bottom right corner.
141
Page 66

4.
Click the “TCP/IP” tab and your router’s IP address will be displayed next
to “Router”.
142
Page 67

IV-2. Connecting to a Wi-Fi network
For help connecting to your device’s Edimax.Setup SSID for initial setup, or to
connect to your device’s new Wi-Fi network (SSID) after setup is complete,
follow the guide below:
Below is an example of how to connect using Windows Vista – the
process may vary slightly for other versions of Windows.
1.
Click the network icon ( , or ) in the system tray and select “Connect
to a network”.
2.
Search for the SSID of your BR-6428nS V3/BR-6228nS V3 and then click
“Connect”. If you set a password for your network, you will then be
prompted to enter it.
143
Page 68

3.
After correctly entering your password, you will be successfully connected
to the BR-6428nS V3/BR-6228nS V3’s wireless network.
144
Page 69

IV-3. Troubleshooting
network.
router’s SSID (above) +"_2EX".
network.
If you are experiencing problems with your BR-6428nS V3/BR-6228nS V3,
please check below before contacting your dealer of purchase for help.
If you are experiencing problems immediately after a firmware
upgrade, please contact your dealer of purchase for help.
1. In range extender mode, how do I connect to a network which
has a hidden SSID?
a. During iQ Setup select “Setup extender manually” as shown below. Manually
enter the SSID of the hidden network, an SSID for your device and the
encryption information for the hidden network.
SSID Enter the SSID (network name) of your existing, hidden
Device SSID Enter an SSID for the BR-6428nS V3/BR-6228nS V3 or leave
it blank to use a default which consists of your existing
Encryption Enter the encryption information for your existing, hidden
145
Page 70

2. I can’t access the Internet.
a. Ensure that all cables are connected properly. Try a different Ethernet cable.
b. Switch your BR-6428nS V3/BR-6228nS V3 and network device off and back on
again. Check the LED status of the BR-6428nS V3/BR-6228nS V3.
c. Check if you can access the web based configuration interface. If not, please
ensure your computer is set to use a dynamic IP address.
d. Login to the web based configuration interface and go to Internet > WAN Setup
and check that the connection type is correct. If you are unsure which internet
connection type you have, please contact your Internet Service Provider (ISP).
e. Connect your computer directly to your modem and check if you can access the
internet. If you can’t, please contact your Internet service provider for
assistance.
3. I can’t open the browser based configuration interface.
a. Please ensure your computer is set to use a dynamic IP address. Refer to the
user manual for guidance if you are unsure how to do this.
b. Ensure you enter the correct password. The password is case-sensitive.
4. How do I reset my device to factory default settings?
a. To reset the device back to its factory default settings, press and hold the
WPS/Reset button for over 10 seconds, until the power LED begins to flash.
Please wait a few minutes for the product to restart. When the device restarts,
all settings will be reset. Default settings are displayed on the product label on
the back of the device, as shown below:
146
Page 71

cable.
when
you go to the “Router Login” URL (above).
(above).
device’s unique MAC address is displayed here.
Setup (WPS).
Router Login Enter this URL in a web browser to run iQ Setup or
configure advanced settings. You must be
connected to the device by Wi-Fi or Ethernet
Username/Password This is the default username and password to
access the browser based configuration interface
Wi-Fi Network
Name
MAC A MAC address is unique to every device and is
PIN CODE This is your device’s PIN code for Wi-Fi Protected
5. I forgot my password.
a. Reset the router to its factory default settings and use the default username
admin and default password 1234. Default settings are displayed on the product
label on the back of the device, as shown above.
This is the default Wi-Fi network name for the
device. Search for this name (SSID) and connect to
it in order to access the “Router Login” URL
used for identification within a network. Your
6. My BR-6428nS V3/BR-6228nS V3 has a weak wireless signal in
range extender mode.
a. Weak signals are usually caused by interference from other devices or obstacles
blocking the BR-6428nS V3/BR-6228nS V3’s wireless signal:
b. Keep the device away from other radio devices such as microwaves or wireless
telephones.
c. Do not put the device in the corner of a room or under/nearby metal.
d. Ensure there are as few obstacles as possible between the BR-6428nS
V3/BR-6228nS V3 and your wireless network device.
In range extender mode, the BR-6428nS V3/BR-6228nS V3’S weak wireless signal
may be in turn caused by a weak signal from your existing router. It’s important to
choose a good location for the BR-6428nS V3/BR-6228nS V3 in relation to your
existing wireless router. The best location is roughly in the middle between your
existing wireless router and the area you would like to be covered by the
BR-6428nS V3/BR-6228nS V3. If you are too far away from your existing router,
then it is difficult for the BR-6428nS V3/BR-6228nS V3 to receive a wireless signal.
147
Page 72

7. Do the WAN and LAN ports work the same when the device is in
different modes?
No, the WAN and LAN ports have slightly different functions depending on the
operating mode of the device.
a. In Wi-Fi router mode, the WAN port is for a direct connection to your xDSL
modem. The LAN ports are for wired network clients.
b. In access point mode, the WAN port is not functional. Connect your existing
router to the device’s LAN port, and the other LAN ports can connect wired
network clients.
c. In range extender mode, the WAN port is not functional and the LAN ports are
for wired network clients. Do not connect your existing router to the device’s
WAN or LAN ports, as this can cause the device to malfunction.
8. My network is configured to use static IP addresses. How can I
assign a static IP address to my BR-6428nS V3/BR-6228nS V3?
a. You can modify the device’s IP address using the browser based configuration
interface. Please refer to III-3-4. LAN.
148
Page 73

IV-4. Glossary
Default Gateway (Wireless bridge): Every non-access point IP device needs to
configure a default gateway’s IP address. When the device sends out an IP
packet, if the destination is not on the same network, the device has to send
the packet to its default gateway, which will then send it out towards the
destination.
DHCP: Dynamic Host Configuration Protocol. This protocol automatically gives
every computer on your home network an IP address.
DNS Server IP Address: DNS stands for Domain Name System, which allows
Internet servers to have a domain name (such as www.Broadbandaccess
point.com) and one or more IP addresses (such as 192.34.45.8). A DNS server
keeps a database of Internet servers and their respective domain names and
IP addresses, so that when a domain name is requested (as in typing
"Broadbandaccess point.com" into your Internet browser), the user is sent to
the proper IP address. The DNS server IP address used by the computers on
your home network is the location of the DNS server your ISP has assigned to
you.
DSL Modem: DSL stands for Digital Subscriber Line. A DSL modem uses your
existing phone lines to transmit data at high speeds.
Ethernet: A standard for computer networks. Ethernet networks are
connected by special cables and hubs, and move data around at up to 10/100
million bits per second (Mbps).
IP Address and Network (Subnet) Mask: IP stands for Internet Protocol. An IP
address consists of a series of four numbers separated by periods, that
identifies a single, unique Internet computer host in an IP network. Example:
192.168.2.1. It consists of 2 portions: the IP network address, and the host
identifier.
The IP address is a 32-bit binary pattern, which can be represented as four
cascaded decimal numbers separated by “.”: aaa.aaa.aaa.aaa, where each
“aaa” can be anything from 000 to 255, or as four cascaded binary numbers
separated by “.”: bbbbbbbb.bbbbbbbb.bbbbbbbb.bbbbbbbb, where each “b”
can either be 0 or 1.
149
Page 74

A network mask is also a 32-bit binary pattern, and consists of consecutive
leading 1’s followed by consecutive trailing 0’s, such as
11111111.11111111.11111111.00000000. Therefore sometimes a network
mask can also be described simply as “x” number of leading 1’s.
When both are represented side by side in their binary forms, all bits in the IP
address that correspond to 1’s in the network mask become part of the IP
network address, and the remaining bits correspond to the host ID.
For example, if the IP address for a device is, in its binary form,
11011001.10110000.10010000.00000111, and if its network mask is,
11111111.11111111.11110000.00000000
It means the device’s network address is
11011001.10110000.10010000.00000000, and its host ID is,
00000000.00000000.00000000.00000111. This is a convenient and efficient
method for access points to route IP packets to their destination.
ISP Gateway Address: (see ISP for definition). The ISP Gateway Address is an
IP address for the Internet access point located at the ISP's office.
ISP: Internet Service Provider. An ISP is a business that provides connectivity
to the Internet for individuals and other businesses or organizations.
LAN: Local Area Network. A LAN is a group of computers and devices
connected together in a relatively small area (such as a house or an office).
Your home network is considered a LAN.
MAC Address: MAC stands for Media Access Control. A MAC address is the
hardware address of a device connected to a network. The MAC address is a
unique identifier for a device with an Ethernet interface. It is comprised of
two parts: 3 bytes of data that corresponds to the Manufacturer ID (unique
for each manufacturer), plus 3 bytes that are often used as the product’s
serial number.
NAT: Network Address Translation. This process allows all of the computers
on your home network to use one IP address. Using the broadband access
point’s NAT capability, you can access the Internet from any computer on
your home network without having to purchase more IP addresses from your
ISP.
Port: Network Clients (LAN PC) uses port numbers to distinguish one network
application/protocol over another. Below is a list of common applications and
protocol/port numbers:
150
Page 75

Application
Protocol
Port Number
Telnet
TCP
23
FTP
TCP
21
SMTP
TCP
25
POP3
TCP
110
H.323
TCP
1720
SNMP
UCP
161
SNMP Trap
UDP
162
HTTP
TCP
80
PPTP
TCP
1723
PC Anywhere
TCP
5631
PC Anywhere
UDP
5632
Access point: A access point is an intelligent network device that forwards
packets between different networks based on network layer address
information such as IP addresses.
Subnet Mask: A subnet mask, which may be a part of the TCP/IP information
provided by your ISP, is a set of four numbers (e.g. 255.255.255.0) configured
like an IP address. It is used to create IP address numbers used only within a
particular network (as opposed to valid IP address numbers recognized by the
Internet, which must be assigned by InterNIC).
TCP/IP, UDP: Transmission Control Protocol/Internet Protocol (TCP/IP) and
Unreliable Datagram Protocol (UDP). TCP/IP is the standard protocol for data
transmission over the Internet. Both TCP and UDP are transport layer protocol.
TCP performs proper error detection and error recovery, and thus is reliable.
UDP on the other hand is not reliable. They both run on top of the IP (Internet
Protocol), a network layer protocol.
WAN: Wide Area Network. A network that connects computers located in
geographically separate areas (e.g. different buildings, cities, countries). The
Internet is a wide area network.
Web-based management Graphical User Interface (GUI): Many devices
support a graphical user interface that is based on the web browser. This
means the user can use the familiar Netscape or Microsoft Internet Explorer
to Control/configure or monitor the device being managed.
151
Page 76

COPYRIGHT
Copyright Edimax Technology Co., Ltd. all rights reserved. No part of this publication
may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
into any language or computer language, in any form or by any means, electronic,
mechanical, magnetic, optical, chemical, manual or otherwise, without the prior written
permission from Edimax Technology Co., Ltd.
Edimax Technology Co., Ltd. makes no representations or warranties, either expressed or
implied, with respect to the contents hereof and specifically disclaims any warranties,
merchantability, or fitness for any particular purpose. Any software described in this
manual is sold or licensed as is. Should the programs prove defective following their
purchase, the buyer (and not this company, its distributor, or its dealer) assumes the
entire cost of all necessary servicing, repair, and any incidental or consequential damages
resulting from any defect in the software. Edimax Technology Co., Ltd. reserves the right
to revise this publication and to make changes from time to time in the contents hereof
without the obligation to notify any person of such revision or changes.
The product you have purchased and the setup screen may appear slightly different from
those shown in this QIG. The software and specifications are subject to change without
notice. Please visit our website www.edimax.com for updates. All brand and product
names mentioned in this manual are trademarks and/or registered trademarks of their
respective holders.
152
Page 77

FCC Statement
This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC
rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This
equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the
instructions, may cause harmful interference to radio communications. However, there is no guarantee that interference will not
occur in a particular installation. If this equipment does cause harmful interference
to radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try to
correct the interference by one or more of the following measures:
-Reorient or relocate the receiving antenna.
-Increase the separation between the equipment and receiver.
-Consult the dealer or an experienced radio/TV technician for help.
To assure continued compliance, any changes or modifications not expressly approved by the party responsible for compliance
could void the user’s authority to operate this equipment. (Example- use only shielded interface cables when connecting to
computer or peripheral devices).
FCC Radiation Exposure Statement
This equipment complies with FCC RF radiation exposure limits set forth for an uncontrolled environment. This transmitter must
not be co-located or operating in conjunction with any other antenna or transmitter. This equipment should be installed and
operated with a minimum distance of 20 centimeters between the radiator and your body.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device
may not cause harmful interference, and (2) this device must accept any interference received, including interference that
may cause undesired operation.
Caution!
Any changes or modifications not expressly approved by the party responsible for compliance could void the user's authority to
operate the equipment.
153
Page 78

EU Declaration of Conformity
English: This equipment is in compliance with the essential requirements and other relevant
provisions of Directive 1999/5/EC, 2009/125/EC.
Français:
Čeština:
Polski:
Română:
Русский:
Magyar:
Türkçe:
Українська:
Slovenčina:
Deutsch:
Español:
Italiano:
Nederlands:
Português:
Norsk:
Svenska:
Dansk:
Suomi:
Cet équipement est conforme aux exigences essentielles et autres dispositions de la
directive 1999/5/CE, 2009/125/CE.
Toto zařízení je v souladu se základními požadavky a ostatními příslušnými ustanoveními
směrnic 1999/5/ES, 2009/125/ES.
Urządzenie jest zgodne z ogólnymi wymaganiami oraz szczególnymi warunkami
określonymi Dyrektywą UE 1999/5/EC, 2009/125/EC.
Acest echipament este în conformitate cu cerinţele esenţiale şi alte prevederi relevante ale
Directivei 1999/5/CE, 2009/125/CE.
Это оборудование соответствует основным требованиям и положениям Директивы
1999/5/EC, 2009/125/EC.
Ez a berendezés megfelel az alapvető követelményeknek és más vonatkozó irányelveknek
(1999/5/EK, 2009/125/EC).
Bu cihaz 1999/5/EC, 2009/125/EC direktifleri zorunlu istekler ve diğer hükümlerle ile
uyumludur.
Обладнання відповідає вимогам і умовам директиви 1999/5/EC, 2009/125/EC.
Toto zariadenie spĺňa základné požiadavky a ďalšie príslušné ustanovenia smerníc
1999/5/ES, 2009/125/ES.
Dieses Gerät erfüllt die Voraussetzungen gemäß den Richtlinien 1999/5/EC, 2009/125/EC.
El presente equipo cumple los requisitos esenciales de la Directiva 1999/5/EC,
2009/125/EC.
Questo apparecchio è conforme ai requisiti essenziali e alle altre disposizioni applicabili
della Direttiva 1999/5/CE, 2009/125/CE.
Dit apparaat voldoet aan de essentiële eisen en andere van toepassing zijnde bepalingen
van richtlijn 1999/5/EC, 2009/125/EC.
Este equipamento cumpre os requesitos essênciais da Directiva 1999/5/EC, 2009/125/EC.
Dette utstyret er i samsvar med de viktigste kravene og andre relevante regler i Direktiv
1999/5/EC, 2009/125/EC.
Denna utrustning är i överensstämmelse med de väsentliga kraven och övriga relevanta
bestämmelser i direktiv 1999/5/EG, 2009/125/EG.
Dette udstyr er i overensstemmelse med de væsentligste krav og andre relevante
forordninger i direktiv 1999/5/EC, 2009/125/EC.
Tämä laite täyttää direktiivien 1999/5/EY, 2009/125/EY oleelliset vaatimukset ja muut
asiaankuuluvat määräykset.
-----------------------------------------------------------------------------------------------------------
WEEE Directive & Product Disposal
At the end of its serviceable life, this product should not be treated as household or general waste. It
should be handed over to the applicable collection point for the recycling of electrical and electronic
equipment, or returned to the supplier for disposal.
154
Page 79

Declaration of Conformity
We, Edimax Technology Co., Ltd., declare under our sole responsibility, that the
equipment described below complies with the requirements of the European R&TTE
directives.
Equipment: 5-in-1 N300 Wi-Fi Router, Access Point & Range Extender
Model No.: BR-6428nS V3
Equipment: 5-in-1 N150 Wi-Fi Router, Access Point & Range Extender
Model No.: BR-6228nS V3
The following European standards for essential requirements have been followed:
AN/NZS CISPR 22: 2009+A1:2010
EN 300 328 V1.8.1 (2012-06)
EN 301 489-1 V1.9.2 (2011-09)
EN 301 489-17 V2.2.1 (2012-09)
EN 55022: 2010+AC:2011 Class B
EN 55024: 2010
IEC 60950-1:2005(2nd)+A1:2009/EN 60950-1:2006+A11:2009+A1:2010+A12:2011+A2:2013
EN 61000-3-2: 2006+A1:2009+A2:2009 Class A
EN 61000-3-3: 2013
IEC 61000-4-2: 2008 / EN 61000-4-2:2009
IEC 61000-4-3: 2006+A1: 2008+A2: 2010 / EN 61000-4-3: 2006+A1: 2008+A2: 2010
IEC 61000-4-4: 2012 / EN 61000-4-4: 2012
IEC 61000-4-5: 2005 / EN 61000-4-5: 2006
IEC 61000-4-6: 2008 / EN 61000-4-6: 2009
IEC 61000-4-11: 2004 / EN 61000-4-11: 2004
Edimax Technology Co., Ltd.
No. 3, Wu Chuan 3rd Road,
Wu-Ku Industrial Park,
New Taipei City, Taiwan
Date of Signature: July, 2014
Signature:
Printed Name:
Albert Chang
Title: Director
Edimax Technology Co., Ltd.
155
Page 80

156
 Loading...
Loading...