Page 1

ES3528
ES3528-WDM
Powered by Accton
Layer 2 Metro Access Switch
Management Guide
www.edge-core.com
Page 2

Page 3

Management Guide
ES3528 Fast Ethernet Switch
Layer 2 Ethernet Metro Access Switch
with 24 Fast Ethernet Ports (RJ-45),
2 Gigabit Combination Ports (RJ-45/SFP),
2 Gigabit Extender Module Slots (RJ-45/SFP),
1 Fast Ethernet Management Port (RJ-45)
ES3528-WDM Fast Ethernet Switch
Layer 2 WDM Metro Access Switch
with 24 100BASE-BX Single-Fiber Ports (SC),
2 Gigabit Combination Ports (RJ-45/SFP),
2 Gigabit Extender Module Slots (RJ-45/SFP),
1 Fast Ethernet Management Port (RJ-45)
Page 4

ES3528
ES3528-WDM
F1.0.1.7 E122006/ST-R01
149100033100A
Page 5

Contents
Section I: Getting Started
Chapter 1: Introduction 1-1
Key Features 1-1
Description of Software Features 1-2
System Defaults 1-6
Chapter 2: Initial Configuration 2-1
Connecting to the Switch 2-1
Configuration Options 2-1
Required Connections 2-2
Remote Connections 2-3
Basic Configuration 2-3
Console Connection 2-3
Setting Passwords 2-4
Setting an IP Address 2-4
Manual Configuration 2-4
Dynamic Configuration 2-5
Enabling SNMP Management Access 2-6
Community Strings (for SNMP version 1 and 2c clients) 2-6
Trap Receivers 2-7
Configuring Access for SNMP Version 3 Clients 2-8
Managing System Files 2-8
Saving Configuration Settings 2-9
Section II: Switch Management
Chapter 3: Configuring the Switch 3-1
Using the Web Interface 3-1
Navigating the Web Browser Interface 3-2
Home Page 3-2
Configuration Options 3-3
Panel Display 3-3
Main Menu 3-4
Chapter 4: Basic Management Tasks 4-1
Displaying System Information 4-1
Configuring the Switch for Normal Operation or Tunneling Mode 4-3
Configuring the Maximum Frame Size 4-4
Configuring Support for Jumbo Frames 4-5
Displaying Switch Hardware/Software Versions 4-6
Displaying Bridge Extension Capabilities 4-7
Setting the Switch’s IP Address 4-8
v
Page 6

Contents
Manual Configuration 4-9
Using DHCP/BOOTP 4-10
Managing Firmware 4-11
Downloading System Software from a Server 4-12
Saving or Restoring Configuration Settings 4-14
Downloading Configuration Settings from a Server 4-15
Console Port Settings 4-16
Telnet Settings 4-18
Configuring Event Logging 4-20
System Log Configuration 4-20
Remote Log Configuration 4-21
Displaying Log Messages 4-23
Sending Simple Mail Transfer Protocol Alerts 4-23
Resetting the System 4-25
Setting the System Clock 4-26
Configuring SNTP 4-26
Setting the Time Zone 4-27
Chapter 5: Simple Network Management Protocol 5-1
Enabling the SNMP Agent 5-2
Setting Community Access Strings 5-3
Specifying Trap Managers and Trap Types 5-4
Configuring SNMPv3 Management Access 5-7
Setting a Local Engine ID 5-7
Specifying a Remote Engine ID 5-8
Configuring SNMPv3 Users 5-9
Configuring Remote SNMPv3 Users 5-11
Configuring SNMPv3 Groups 5-13
Setting SNMPv3 Views 5-16
Chapter 6: User Authentication 6-1
Configuring User Accounts 6-1
Configuring Local/Remote Logon Authentication 6-2
Configuring HTTPS 6-5
Replacing the Default Secure-site Certificate 6-6
Configuring the Secure Shell 6-7
Generating the Host Key Pair 6-9
Configuring the SSH Server 6-11
Configuring 802.1X Port Authentication 6-13
Displaying 802.1X Global Settings 6-14
Configuring 802.1X Global Settings 6-15
Configuring Port Settings for 802.1X 6-15
Displaying 802.1X Statistics 6-18
Filtering IP Addresses for Management Access 6-20
vi
Page 7

Contents
Chapter 7: Client Security 7-1
Configuring Port Security 7-1
Chapter 8: Access Control Lists 8-1
Configuring Access Control Lists 8-1
Setting the ACL Name and Type 8-2
Configuring a Standard ACL 8-3
Configuring an Extended ACL 8-4
Configuring a MAC ACL 8-7
Configuring ACL Masks 8-9
Specifying the Mask Type 8-9
Configuring an IP ACL Mask 8-10
Configuring a MAC ACL Mask 8-12
Binding a Port to an Access Control List 8-13
Chapter 9: Port Configuration 9-1
Displaying Connection Status 9-1
Configuring Interface Connections 9-3
Creating Trunk Groups 9-6
Statically Configuring a Trunk 9-7
Enabling LACP on Selected Ports 9-8
Configuring LACP Parameters 9-10
Displaying LACP Port Counters 9-13
Displaying LACP Settings and Status for the Local Side 9-14
Displaying LACP Settings and Status for the Remote Side 9-16
Setting Broadcast Storm Thresholds 9-17
Configuring Port Mirroring 9-19
Configuring Rate Limits 9-20
Showing Port Statistics 9-21
Chapter 10: Address Table Settings 10-1
Setting Static Addresses 10-1
Displaying the Address Table 10-2
Changing the Aging Time 10-4
Chapter 11: Spanning Tree Algorithm 11-1
Displaying Global Settings 11-3
Configuring Global Settings 11-6
Displaying Interface Settings 11-10
Configuring Interface Settings 11-13
Configuring Multiple Spanning Trees 11-16
Displaying Interface Settings for MSTP 11-19
Configuring Interface Settings for MSTP 11-20
Chapter 12: VLAN Configuration 12-1
IEEE 802.1Q VLANs 12-1
Enabling or Disabling GVRP (Global Setting) 12-4
vii
Page 8

Contents
Displaying Basic VLAN Information 12-4
Displaying Current VLANs 12-5
Creating VLANs 12-6
Adding Static Members to VLANs (VLAN Index) 12-7
Adding Static Members to VLANs (Port Index) 12-9
Configuring VLAN Behavior for Interfaces 12-10
Configuring IEEE 802.1Q Tunneling 12-12
Adding an Interface to a QinQ Tunnel 12-16
Configuring Private VLANs 12-17
Enabling Private VLANs 12-17
Configuring Uplink and Downlink Ports 12-18
Configuring Protocol-Based VLANs 12-18
Configuring Protocol Groups 12-19
Mapping Protocols to VLANs 12-20
Chapter 13: Class of Service 13-1
Layer 2 Queue Settings 13-1
Setting the Default Priority for Interfaces 13-1
Mapping CoS Values to Egress Queues 13-3
Selecting the Queue Mode 13-5
Setting the Service Weight for Traffic Classes 13-6
Layer 3/4 Priority Settings 13-7
Mapping Layer 3/4 Priorities to CoS Values 13-7
Selecting IP Precedence/DSCP Priority 13-7
Mapping IP Precedence 13-8
Mapping DSCP Priority 13-10
Mapping IP Port Priority 13-11
Chapter 14: Quality of Service 14-1
Configuring Quality of Service Parameters 14-1
Configuring a Class Map 14-2
Creating QoS Policies 14-5
Attaching a Policy Map to Ingress Queues 14-8
Chapter 15: Multicast Filtering 15-1
Layer 2 IGMP (Snooping and Query) 15-2
Configuring IGMP Snooping and Query Parameters 15-3
Displaying Interfaces Attached to a Multicast Router 15-5
Specifying Static Interfaces for a Multicast Router 15-6
Displaying Port Members of Multicast Services 15-7
Assigning Ports to Multicast Services 15-8
Multicast VLAN Registration 15-9
Configuring Global MVR Settings 15-10
Displaying MVR Interface Status 15-11
Configuring MVR Interface Status 15-12
Displaying Port Members of Multicast Groups 15-14
viii
Page 9

Contents
Assigning Static Multicast Groups to Interfaces 15-15
Chapter 16: Domain Name Service 16-1
Configuring General DNS Service Parameters 16-1
Configuring Static DNS Host to Address Entries 16-3
Displaying the DNS Cache 16-5
Section III: Command Line Interface
Chapter 17: Overview of Command Line Interface 17-1
Using the Command Line Interface 17-1
Accessing the CLI 17-1
Console Connection 17-1
Telnet Connection 17-1
Entering Commands 17-3
Keywords and Arguments 17-3
Minimum Abbreviation 17-3
Command Completion 17-3
Getting Help on Commands 17-3
Showing Commands 17-4
Partial Keyword Lookup 17-5
Negating the Effect of Commands 17-5
Using Command History 17-5
Understanding Command Modes 17-6
Exec Commands 17-6
Configuration Commands 17-7
Command Line Processing 17-9
Command Groups 17-10
Chapter 18: General Commands 18-1
enable 18-1
disable 18-2
configure 18-2
show history 18-3
reload 18-4
prompt 18-4
end 18-4
exit 18-5
quit 18-5
Chapter 19: System Management Commands 19-1
Device Designation Commands 19-1
hostname 19-1
System Status Commands 19-2
show startup-config 19-2
show running-config 19-4
ix
Page 10

Contents
show system 19-6
show users 19-7
show version 19-7
System Mode Commands 19-8
system mode 19-8
show system mode 19-9
System MTU Commands 19-9
jumbo frame 19-10
system mtu 19-11
show system mtu 19-11
File Management Commands 19-12
copy 19-13
delete 19-15
dir 19-16
whichboot 19-17
boot system 19-17
Line Commands 19-19
line 19-19
login 19-20
password 19-21
timeout login response 19-22
exec-timeout 19-22
password-thresh 19-23
silent-time 19-24
databits 19-24
parity 19-25
speed 19-25
stopbits 19-26
disconnect 19-26
show line 19-27
Event Logging Commands 19-28
logging on 19-28
logging history 19-29
logging host 19-30
logging facility 19-30
logging trap 19-31
clear log 19-31
show logging 19-32
show log 19-33
SMTP Alert Commands 19-34
logging sendmail host 19-34
logging sendmail level 19-35
logging sendmail source-email 19-35
logging sendmail destination-email 19-36
logging sendmail 19-36
x
Page 11

Contents
show logging sendmail 19-37
Time Commands 19-37
sntp client 19-38
sntp server 19-39
sntp poll 19-39
show sntp 19-40
clock timezone 19-40
calendar set 19-41
show calendar 19-42
Chapter 20: SNMP Commands 20-1
snmp-server 20-2
show snmp 20-2
snmp-server community 20-3
snmp-server contact 20-4
snmp-server location 20-4
snmp-server host 20-5
snmp-server enable traps 20-7
snmp-server engine-id 20-8
show snmp engine-id 20-9
snmp-server view 20-10
show snmp view 20-11
snmp-server group 20-11
show snmp group 20-12
snmp-server user 20-14
show snmp user 20-15
Chapter 21: User Authentication Commands 21-1
User Account Commands 21-1
username 21-2
enable password 21-3
Authentication Sequence 21-4
authentication login 21-4
authentication enable 21-5
RADIUS Client 21-6
radius-server host 21-6
radius-server port 21-7
radius-server key 21-7
radius-server retransmit 21-8
radius-server timeout 21-8
show radius-server 21-8
TACACS+ Client 21-9
tacacs-server host 21-9
tacacs-server port 21-10
tacacs-server key 21-10
show tacacs-server 21-11
xi
Page 12

Contents
Web Server Commands 21-11
ip http port 21-11
ip http server 21-12
ip http secure-server 21-12
ip http secure-port 21-13
Telnet Server Commands 21-14
ip telnet server 21-14
Secure Shell Commands 21-15
ip ssh server 21-17
ip ssh timeout 21-18
ip ssh authentication-retries 21-19
ip ssh server-key size 21-19
delete public-key 21-20
ip ssh crypto host-key generate 21-20
ip ssh crypto zeroize 21-21
ip ssh save host-key 21-21
show ip ssh 21-22
show ssh 21-22
show public-key 21-23
802.1X Port Authentication 21-24
dot1x system-auth-control 21-25
dot1x default 21-25
dot1x max-req 21-25
dot1x port-control 21-26
dot1x operation-mode 21-26
dot1x re-authenticate 21-27
dot1x re-authentication 21-27
dot1x timeout quiet-period 21-28
dot1x timeout re-authperiod 21-28
dot1x timeout tx-period 21-29
show dot1x 21-29
Management IP Filter Commands 21-33
management 21-33
show management 21-34
Chapter 22: Client Security Commands 22-1
Port Security Commands 22-1
port security 22-2
IP Source Guard Commands 22-3
ip source-guard 22-3
ip source-guard binding 22-5
show ip source-guard 22-6
show ip source-guard binding 22-6
DHCP Snooping Commands 22-7
ip dhcp snooping 22-7
xii
Page 13

Contents
ip dhcp snooping vlan 22-9
ip dhcp snooping binding 22-10
ip dhcp snooping verify mac-address 22-11
ip dhcp snooping database flash 22-12
ip dhcp snooping trust 22-12
show ip dhcp snooping 22-13
show ip dhcp snooping binding 22-13
Chapter 23: Access Control List Commands 23-1
IP ACLs 23-1
access-list ip 23-2
permit, deny (Standard ACL) 23-2
permit, deny (Extended ACL) 23-3
show ip access-list 23-5
access-list ip mask-precedence 23-6
mask (IP ACL) 23-6
show access-list ip mask-precedence 23-10
ip access-group 23-11
show ip access-group 23-11
MAC ACLs 23-12
access-list mac 23-12
permit, deny (MAC ACL) 23-13
show mac access-list 23-14
access-list mac mask-precedence 23-15
mask (MAC ACL) 23-15
show access-list mac mask-precedence 23-17
mac access-group 23-18
show mac access-group 23-18
ACL Information 23-19
show access-list 23-19
show access-group 23-19
Chapter 24: Interface Commands 24-1
interface 24-1
description 24-2
speed-duplex 24-2
negotiation 24-3
capabilities 24-4
flowcontrol 24-5
media-type 24-6
shutdown 24-6
switchport packet-rate 24-7
switchport block 24-8
clear counters 24-8
show interfaces status 24-9
show interfaces counters 24-10
xiii
Page 14

Contents
show interfaces switchport 24-11
Chapter 25: Link Aggregation Commands 25-1
channel-group 25-2
lacp 25-2
lacp system-priority 25-4
lacp admin-key (Ethernet Interface) 25-4
lacp admin-key (Port Channel) 25-5
lacp port-priority 25-6
show lacp 25-7
Chapter 26: Mirror Port Commands 26-1
port monitor 26-1
show port monitor 26-2
Chapter 27: Rate Limit Commands 27-1
rate-limit 27-1
rate-limit cos 27-2
show rate-limit cos 27-3
Chapter 28: Address Table Commands 28-1
mac-address-table static 28-1
clear mac-address-table dynamic 28-2
show mac-address-table 28-3
mac-address-table aging-time 28-4
show mac-address-table aging-time 28-4
Chapter 29: Spanning Tree Commands 29-1
spanning-tree 29-2
spanning-tree mode 29-2
spanning-tree forward-time 29-4
spanning-tree hello-time 29-4
spanning-tree max-age 29-5
spanning-tree priority 29-6
spanning-tree pathcost method 29-6
spanning-tree transmission-limit 29-7
spanning-tree mst-configuration 29-7
mst vlan 29-8
mst priority 29-9
name 29-9
revision 29-10
max-hops 29-11
spanning-tree spanning-disabled 29-11
spanning-tree cost 29-12
spanning-tree port-priority 29-13
spanning-tree edge-port 29-14
spanning-tree portfast 29-14
xiv
Page 15

Contents
spanning-tree link-type 29-15
spanning-tree mst cost 29-16
spanning-tree mst port-priority 29-17
spanning-tree protocol-migration 29-18
show spanning-tree 29-18
show spanning-tree mst configuration 29-20
Chapter 30: VLAN Commands 30-1
GVRP and Bridge Extension Commands 30-1
bridge-ext gvrp 30-2
show bridge-ext 30-2
switchport gvrp 30-3
show gvrp configuration 30-3
garp timer 30-4
show garp timer 30-5
Editing VLAN Groups 30-6
vlan database 30-6
vlan 30-7
Configuring VLAN Interfaces 30-8
interface vlan 30-8
switchport mode 30-9
switchport acceptable-frame-types 30-9
switchport ingress-filtering 30-10
switchport native vlan 30-11
switchport allowed vlan 30-11
switchport forbidden vlan 30-12
Displaying VLAN Information 30-13
show vlan 30-13
Configuring Private VLANs 30-14
pvlan 30-14
show pvlan 30-15
Configuring Protocol-based VLANs 30-16
protocol-vlan protocol-group (Configuring Groups) 30-17
protocol-vlan protocol-group (Configuring Interfaces) 30-17
show protocol-vlan protocol-group 30-18
show interfaces protocol-vlan protocol-group 30-19
Configuring IEEE 802.1Q Tunneling 30-20
switchport mode dot1q-tunnel 30-21
show dot1q-tunnel 30-21
switchport dot1q-ethertype 30-22
Chapter 31: Class of Service Commands 31-1
Priority Commands (Layer 2) 31-1
queue mode 31-2
show queue mode 31-2
switchport priority default 31-3
xv
Page 16

Contents
queue bandwidth 31-4
queue cos-map 31-4
show queue bandwidth 31-5
show queue cos-map 31-6
vlan priority 31-6
show vlan based priority 31-7
Priority Commands (Layer 3 and 4) 31-8
map ip port (Global Configuration) 31-8
map ip port (Interface Configuration) 31-9
map ip precedence (Global Configuration) 31-9
map ip precedence (Interface Configuration) 31-10
map ip dscp (Global Configuration) 31-11
map ip dscp (Interface Configuration) 31-11
show map ip port 31-12
show map ip precedence 31-13
show map ip dscp 31-14
Chapter 32: Quality of Service Commands 32-1
class-map 32-2
match 32-3
policy-map 32-4
class 32-5
set 32-6
police 32-6
service-policy 32-7
show class-map 32-8
show policy-map 32-8
show policy-map interface 32-9
Chapter 33: Multicast Filtering Commands 33-1
IGMP Snooping Commands 33-1
ip igmp snooping 33-2
ip igmp snooping vlan static 33-2
ip igmp snooping version 33-3
ip igmp snooping leave-proxy 33-3
ip igmp snooping immediate-leave 33-4
show ip igmp snooping 33-5
show mac-address-table multicast 33-6
IGMP Query Commands 33-6
ip igmp snooping querier 33-7
ip igmp snooping query-count 33-7
ip igmp snooping query-interval 33-8
ip igmp snooping query-max-response-time 33-8
ip igmp snooping router-port-expire-time 33-9
Static Multicast Routing Commands 33-10
ip igmp snooping vlan mrouter 33-10
xvi
Page 17

Contents
show ip igmp snooping mrouter 33-11
Multicast VLAN Registration Commands 33-11
mvr (Global Configuration) 33-12
mvr (Interface Configuration) 33-13
show mvr 33-14
Chapter 34: Domain Name Service Commands 34-1
ip host 34-1
clear host 34-2
ip domain-name 34-3
ip domain-list 34-3
ip name-server 34-4
ip domain-lookup 34-5
show hosts 34-6
show dns 34-7
show dns cache 34-7
clear dns cache 34-8
Chapter 35: IP Interface Commands 35-1
Basic IP Configuration 35-1
ip address 35-1
ip default-gateway 35-2
ip dhcp restart 35-3
show ip interface 35-4
show ip redirects 35-4
show arp 35-4
ping 35-5
Section IV: Appendices
Appendix A: Software Specifications A-1
Software Features A-1
Management Features A-2
Standards A-2
Management Information Bases A-3
Appendix B: Troubleshooting B-1
Problems Accessing the Management Interface B-1
Using System Logs B-2
Glossary
Index
xvii
Page 18

Contents
xviii
Page 19

Tables
Table 1-1 Key Features 1-1
Table 1-2 System Defaults 1-6
Table 3-1 Web Page Configuration Buttons 3-3
Table 3-2 Switch Main Menu 3-4
Table 4-1 Logging Levels 4-20
Table 5-1 SNMPv3 Security Models and Levels 5-2
Table 5-2 Supported Notification Messages 5-13
Table 6-1 HTTPS System Support 6-6
Table 6-2 802.1X Statistics 6-18
Table 9-1 LACP Port Counters 9-13
Table 9-2 LACP Internal Configuration Information 9-14
Table 9-3 LACP Neighbor Configuration Information 9-16
Table 9-4 Port Statistics 9-21
Table 11-1 Recommended STA Path Cost Range 11-14
Table 11-2 Recommended STA Path Costs 11-14
Table 11-3 Default STA Path Costs 11-14
Table 13-1 Mapping CoS Values to Egress Queues 13-3
Table 13-2 CoS Priority Levels 13-3
Table 13-3 Mapping IP Precedence 13-8
Table 13-4 Mapping DSCP Priority 13-10
Table 17-1 General Command Modes 17-6
Table 17-2 Configuration Command Modes 17-8
Table 17-3 Keystroke Commands 17-9
Table 17-4 Command Group Index 17-10
Table 18-1 General Commands 18-1
Table 19-1 System Management Commands 19-1
Table 19-2 Device Designation Commands 19-1
Table 19-3 System Status Commands 19-2
Table 19-4 System Mode Commands 19-8
Table 19-5 Frame Size Commands 19-9
Table 19-6 Flash/File Commands 19-12
Table 19-7 File Directory Information 19-16
Table 19-8 Line Commands 19-19
Table 19-9 Event Logging Commands 19-28
Table 19-10 Logging Levels 19-29
Table 19-11 show logging flash/ram - display description 19-32
Table 19-12 show logging trap - display description 19-33
Table 19-13 SMTP Alert Commands 19-34
Table 19-14 Time Commands 19-37
Table 20-1 SNMP Commands 20-1
Table 20-2 show snmp engine-id - display description 20-9
Table 20-3 show snmp view - display description 20-11
xix
Page 20

Tables
Table 20-4 show snmp group - display description 20-13
Table 20-5 show snmp user - display description 20-15
Table 21-1 Authentication Commands 21-1
Table 21-2 User Access Commands 21-1
Table 21-3 Default Login Settings 21-2
Table 21-4 Authentication Sequence Commands 21-4
Table 21-5 RADIUS Client Commands 21-6
Table 21-6 TACACS+ Client Commands 21-9
Table 21-7 Web Server Commands 21-11
Table 21-8 HTTPS System Support 21-13
Table 21-9 Telnet Server Commands 21-14
Table 21-10 Secure Shell Commands 21-15
Table 21-11 show ssh - display description 21-22
Table 21-12 802.1X Port Authentication Commands 21-24
Table 21-13 Management IP Filter Commands 21-33
Table 22-1 Client Security Commands 22-1
Table 22-2 Port Security Commands 22-1
Table 22-3 IP Source Guard Commands 22-3
Table 22-4 DHCP Snooping Commands 22-7
Table 23-1 Access Control List Commands 23-1
Table 23-2 IP ACL Commands 23-1
Table 23-3 MAC ACL Commands 23-12
Table 23-4 ACL Information Commands 23-19
Table 24-1 Interface Commands 24-1
Table 24-2 show interfaces switchport - display description 24-12
Table 25-1 Link Aggregation Commands 25-1
Table 25-2 show lacp counters - display description 25-7
Table 25-3 show lacp internal - display description 25-8
Table 25-4 show lacp neighbors - display description 25-9
Table 25-5 show lacp sysid - display description 25-10
Table 26-1 Mirror Port Commands 26-1
Table 27-1 Rate Limit Commands 27-1
Table 27-2 Mapping Default to Per Port CoS Priority Levels 27-2
Table 28-1 Address Table Commands 28-1
Table 29-1 Spanning Tree Commands 29-1
Table 29-2 Recommended STA Path Cost Range 29-12
Table 29-3 Recommended STA Path Cost 29-12
Table 29-4 Default STA Path Costs 29-12
Table 30-1 VLAN Commands 30-1
Table 30-2 GVRP and Bridge Extension Commands 30-1
Table 30-3 Commands for Editing VLAN Groups 30-6
Table 30-4 Commands for Configuring VLAN Interfaces 30-8
Table 30-5 Commands for Displaying VLAN Information 30-13
Table 30-6 Private VLAN Commands 30-14
Table 30-7 Protocol-based VLAN Commands 30-16
xx
Page 21

Tables
Table 30-8 IEEE 802.1Q Tunneling Commands 30-20
Table 31-1 Priority Commands 31-1
Table 31-2 Priority Commands (Layer 2) 31-1
Table 31-3 Default CoS Priority Levels 31-5
Table 31-4 Priority Commands (Layer 3 and 4) 31-8
Table 31-5 Mapping IP Precedence to CoS Values 31-10
Table 31-6 Mapping IP DSCP to CoS Values 31-12
Table 32-1 Quality of Service Commands 32-1
Table 33-1 Multicast Filtering Commands 33-1
Table 33-2 IGMP Snooping Commands 33-1
Table 33-3 IGMP Query Commands 33-6
Table 33-4 Static Multicast Routing Commands 33-10
Table 33-5 Multicast VLAN Registration Commands 33-11
Table 33-6 show mvr - display description 33-15
Table 33-7 show mvr interface - display description 33-15
Table 33-8 show mvr members - display description 33-16
Table 34-1 DNS Commands 34-1
Table 34-2 show dns cache - display description 34-7
Table 35-1 Basic IP Configuration Commands 35-1
Table B-1 Troubleshooting Chart B-1
xxi
Page 22

Tables
xxii
Page 23

Figures
Figure 3-1 Home Page 3-2
Figure 3-2 Front Panel Indicators 3-3
Figure 4-1 System Information 4-2
Figure 4-2 System Mode 4-3
Figure 4-3 System MTU 4-4
Figure 4-4 Configuring Support for Jumbo Frames 4-5
Figure 4-5 Switch Information 4-6
Figure 4-6 Displaying Bridge Extension Configuration 4-8
Figure 4-7 IP Interface Configuration - Manual 4-9
Figure 4-8 IP Interface Configuration - DHCP 4-10
Figure 4-9 Copy Firmware 4-12
Figure 4-10 Setting the Startup Code 4-12
Figure 4-11 Deleting Files 4-13
Figure 4-12 Downloading Configuration Settings for Start-Up 4-15
Figure 4-13 Setting the Startup Configuration Settings 4-15
Figure 4-14 Configuring the Console Port 4-17
Figure 4-15 Configuring the Telnet Interface 4-19
Figure 4-16 System Logs 4-21
Figure 4-17 Remote Logs 4-22
Figure 4-18 Displaying Logs 4-23
Figure 4-19 Enabling and Configuring SMTP Alerts 4-24
Figure 4-20 Resetting the System 4-25
Figure 4-21 SNTP Configuration 4-26
Figure 4-22 Clock Time Zone 4-27
Figure 5-1 Enabling the SNMP Agent 5-2
Figure 5-2 Configuring SNMP Community Strings 5-3
Figure 5-3 Configuring SNMP Trap Managers 5-6
Figure 5-4 Setting the SNMPv3 Engine ID 5-7
Figure 5-5 Setting an Engine ID 5-8
Figure 5-6 Configuring SNMPv3 Users 5-10
Figure 5-7 Configuring Remote SNMPv3 Users 5-12
Figure 5-8 Configuring SNMPv3 Groups 5-15
Figure 5-9 Configuring SNMPv3 Views 5-17
Figure 6-1 User Accounts 6-2
Figure 6-2 Authentication Server Settings 6-4
Figure 6-3 HTTPS Settings 6-6
Figure 6-4 SSH Host-Key Settings 6-10
Figure 6-5 SSH Server Settings 6-12
Figure 6-6 802.1X Global Information 6-14
Figure 6-7 802.1X Global Configuration 6-15
Figure 6-8 802.1X Port Configuration 6-16
Figure 6-9 802.1X Port Statistics 6-19
Figure 6-10 IP Filter 6-21
xxiii
Page 24

Figures
Figure 7-1 Port Security 7-3
Figure 8-1 Selecting ACL Type 8-3
Figure 8-2 ACL Configuration - Standard IPv4 8-4
Figure 8-3 ACL Configuration - Extended IPv4 8-6
Figure 8-4 ACL Configuration - MAC 8-8
Figure 8-5 Selecting ACL Mask Types 8-9
Figure 8-6 ACL Mask Configuration - IP 8-11
Figure 8-7 ACL Mask Configuration - MAC 8-12
Figure 8-8 ACL Port Binding 8-14
Figure 9-1 Port - Port Information 9-1
Figure 9-2 Port - Port Configuration 9-5
Figure 9-3 Static Trunk Configuration 9-7
Figure 9-4 LACP Trunk Configuration 9-9
Figure 9-5 LACP - Aggregation Port 9-11
Figure 9-6 LACP - Port Counters Information 9-13
Figure 9-7 LACP - Port Internal Information 9-15
Figure 9-8 LACP - Port Neighbors Information 9-16
Figure 9-9 Port Broadcast Control 9-18
Figure 9-10 Mirror Port Configuration 9-19
Figure 9-11 Rate Limit Configuration 9-20
Figure 9-12 Port Statistics 9-24
Figure 10-1 Static Addresses 10-1
Figure 10-2 Dynamic Addresses 10-3
Figure 10-3 Address Aging 10-4
Figure 11-1 STA Information 11-4
Figure 11-2 STA Global Configuration 11-9
Figure 11-3 STA Port Information 11-12
Figure 11-4 STA Port Configuration 11-15
Figure 11-5 MSTP VLAN Configuration 11-17
Figure 11-6 MSTP Port Information 11-19
Figure 11-7 MSTP Port Configuration 11-21
Figure 12-1 Globally Enabling GVRP 12-4
Figure 12-2 VLAN Basic Information 12-4
Figure 12-3 VLAN Current Table 12-5
Figure 12-4 VLAN Static List - Creating VLANs 12-7
Figure 12-5 VLAN Static Table - Adding Static Members 12-8
Figure 12-6 VLAN Static Membership by Port 12-9
Figure 12-7 VLAN Port Configuration 12-11
Figure 12-8 Tunnel Port Configuration 12-16
Figure 12-9 Private VLAN Status 12-17
Figure 12-10 Private VLAN Link Status 12-18
Figure 12-11 Protocol VLAN Configuration 12-19
Figure 12-12 Protocol VLAN Port Configuration 12-20
Figure 13-1 Default Port Priority 13-2
Figure 13-2 Traffic Classes 13-4
xxiv
Page 25

Figures
Figure 13-3 Queue Mode 13-5
Figure 13-4 Queue Scheduling 13-6
Figure 13-5 IP Precedence/DSCP Priority Status 13-8
Figure 13-6 IP Precedence Priority 13-9
Figure 13-7 IP DSCP Priority 13-10
Figure 13-8 IP Port Priority Status 13-11
Figure 13-9 IP Port Priority 13-12
Figure 14-1 Configuring Class Maps 14-4
Figure 14-2 Configuring Policy Maps 14-7
Figure 14-3 Service Policy Settings 14-8
Figure 15-1 IGMP Configuration 15-4
Figure 15-2 Multicast Router Port Information 15-5
Figure 15-3 Static Multicast Router Port Configuration 15-6
Figure 15-4 IP Multicast Registration Table 15-7
Figure 15-5 IGMP Member Port Table 15-8
Figure 15-6 MVR Global Configuration 15-10
Figure 15-7 MVR Port Information 15-11
Figure 15-8 MVR Port Configuration 15-13
Figure 15-9 MVR Group IP Information 15-14
Figure 15-10 MVR Group Member Configuration 15-15
Figure 16-1 DNS General Configuration 16-2
Figure 16-2 DNS Static Host Table 16-4
Figure 16-3 DNS Cache 16-5
xxv
Page 26

Figures
xxvi
Page 27

Section I: Getting Started
This section provides an overview of the switch, and introduces some basic
concepts about network switches. It also describes the basic settings required to
access the management interface.
Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1-1
Initial Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 2-1
Page 28

Getting Started
Page 29
Chapter 1: Introduction
This switch provides a broad range of features for Layer 2 switching. It includes a
management agent that allows you to configure the features listed in this manual.
The default configuration can be used for most of the features provided by this
switch. However, there are many options that you should configure to maximize the
switch’s performance for your particular network environment.
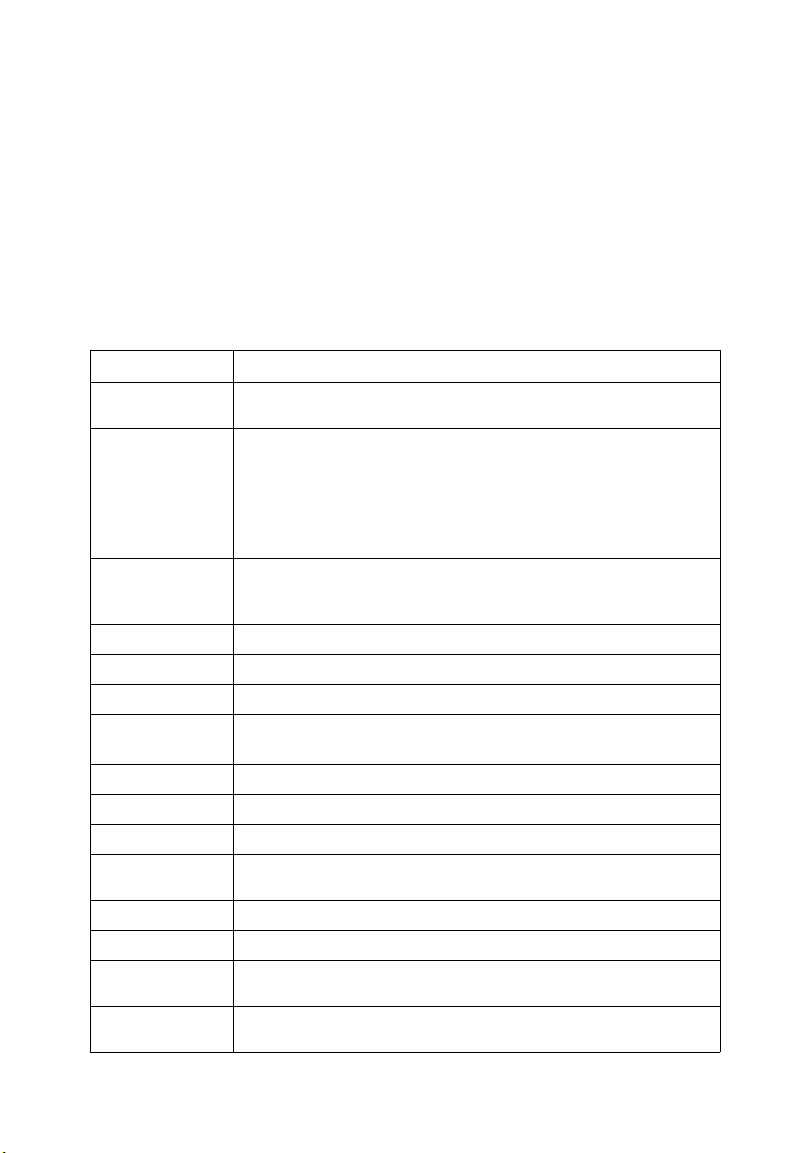
Key Features
Table 1-1 Key Features
Feature Description
Configuration Backup
and Restore
Authentication Console, Telnet, web – User name / password, RADIUS, TACACS+
Access Control Lists Supports IP or MAC ACLs
DHCP Client Supported
DNS Client and proxy service
Port Configuration Speed and duplex mode and flow control
Rate Limiting Input and output rate limiting per port
Port Mirroring Single session, one source port to one analysis port
Port Trunking Supports up to 12 trunks per unit, using either static or dynamic trunking (LACP)
Storm Control Broadcast and multicast storm control
Unknown Packet
Blocking
Address Table Up to 4K MAC addresses in the forwarding table, 1024 static MAC addresses
IEEE 802.1D Bridge Supports dynamic data switching and addresses learning
Store-and-Forward
Switching
Spanning Tree
Algorithm
Backup to TFTP server
Web – HTTPS
Telnet – SSH
SNMP v1/2c - Community strings
SNMP version 3 – MD5 or SHA password
Port – IEEE 802.1X, MAC address filtering
Fast Ethernet ports - 157 rules, 4 masks shared by 8-port groups
Gigabit Ethernet ports - 29 rules, 4 masks
Input rate limiting per port per CoS value
Blocks multicast or unicast packets with unknown MAC address
Supported to ensure wire-speed switching while eliminating bad frames
Supports standard STP, Rapid Spanning Tree Protocol (RSTP), and Multiple
Spanning Trees (MSTP)
1-1
Page 30
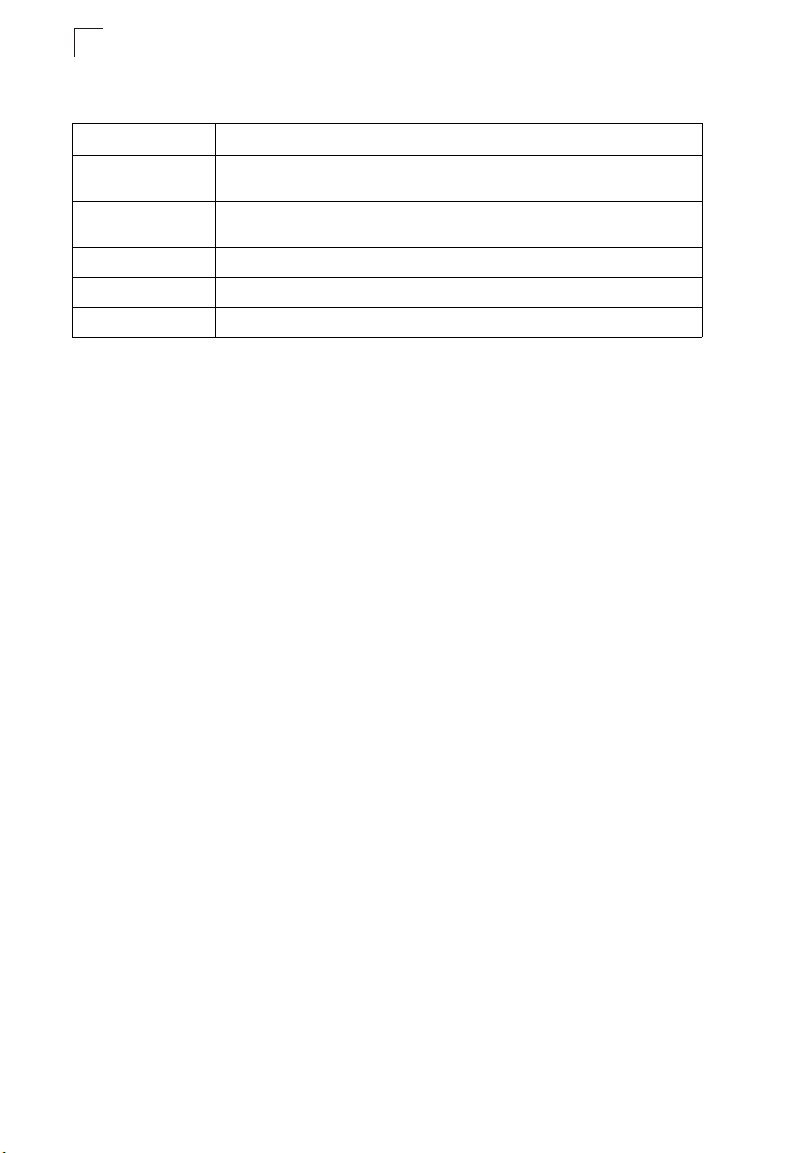
Introduction
1
Table 1-1 Key Features (Continued)
Feature Description
Virtual LANs Up to 255 using IEEE 802.1Q, port-based, protocol-based VLANs, private VLANs,
Traffic Prioritization Default port priority, VLAN priority, traffic class map, queue scheduling, IP
Qualify of Service Supports Differentiated Services (DiffServ)
Multicast Filtering Supports IGMP snooping and query, as well as Multicast VLAN Registration
Tunneling Supports IEEE 802.1Q tunneling (QinQ)
and QinQ tunneling
Precedence, or Differentiated Services Code Point (DSCP), and TCP/UDP Port
Description of Software Features
The switch provides a wide range of advanced performance enhancing features.
Flow control eliminates the loss of packets due to bottlenecks caused by port
saturation. Broadcast storm suppression prevents broadcast traffic storms from
engulfing the network. Untagged (port-based), tagged, and protocol-based VLANs,
plus support for automatic GVRP VLAN registration provide traffic security and
efficient use of network bandwidth. CoS priority queueing ensures the minimum
delay for moving real-time multimedia data across the network. While multicast
filtering provides support for real-time network applications. Some of the
management features are briefly described below.
Configuration Backup and Restore – You can save the current configuration
settings to a file on a TFTP server, and later download this file to restore the switch
configuration settings.
Authentication – This switch authenticates management access via the console
port, Telnet or web browser. User names and passwords can be configured locally or
can be verified via a remote authentication server (i.e., RADIUS or TACACS+).
Port-based authentication is also supported via the IEEE 802.1X protocol. This
protocol uses Extensible Authentication Protocol over LANs (EAPOL) to request
user credentials from the 802.1X client, and then uses the EAP between the switch
and the authentication server to verify the client’s right to access the network via an
authentication server (i.e., RADIUS server).
Other authentication options include HTTPS for secure management access via the
web, SSH for secure management access over a Telnet-equivalent connection,
SNMP Version 3, IP address filtering for SNMP/web/Telnet management access.
MAC address filtering and IP source guard also provide authenticated port access.
While DHCP snooping is provided to prevent malicious attacks from unsecure ports.
1-2
Page 31

Description of Software Features
Access Control Lists – ACLs provide packet filtering for IP frames (based on
address, protocol, TCP/UDP port number or TCP control code) or any frames
(based on MAC address or Ethernet type). ACLs can by used to improve
performance by blocking unnecessary network traffic or to implement security
controls by restricting access to specific network resources or protocols.
Port Configuration – You can manually configure the speed and duplex mode, and
flow control used on specific ports, or use auto-negotiation to detect the connection
settings used by the attached device. Use the full-duplex mode on ports whenever
possible to double the throughput of switch connections. Flow control should also be
enabled to control network traffic during periods of congestion and prevent the loss
of packets when port buffer thresholds are exceeded. The switch supports flow
control based on the IEEE 802.3-2005 standard.
Rate Limiting – This feature controls the maximum rate for traffic transmitted or
received on an interface. Rate limiting is configured on interfaces at the edge of a
network to limit traffic into or out of the network. Traffic that falls within the rate limit is
transmitted, while packets that exceed the acceptable amount of traffic are dropped.
Input rate limits can also be set for traffic based on Class of Service (CoS) values.
Port Mirroring – The switch can unobtrusively mirror traffic from any port to a
monitor port. You can then attach a protocol analyzer or RMON probe to this port to
perform traffic analysis and verify connection integrity.
Port Trunking – Ports can be combined into an aggregate connection. Trunks can
be manually set up or dynamically configured using IEEE 802.3-2005 (formerly
IEEE 802.3ad) Link Aggregation Control Protocol (LACP). The additional ports
dramatically increase the throughput across any connection, and provide
redundancy by taking over the load if a port in the trunk should fail. The switch
supports up to 12 trunks.
Storm Control – Broadcast and multicast storm suppression prevents traffic from
overwhelming the network. When enabled on a port, the level of traffic passing
through the port is restricted. If traffic rises above a pre-defined threshold, it will be
throttled until the level falls back beneath the threshold.
Static MAC Addresses – A static address can be assigned to a specific interface
on this switch. Static addresses are bound to the assigned interface and will not be
moved. When a static address is seen on another interface, the address will be
ignored and will not be written to the address table. Static addresses can be used to
provide network security by restricting access for a known host to a specific port.
IP Address Filtering – Access to unsecure ports can be controlled using DHCP
Snooping, and IP Source Guard which filters ingress traffic based on static IP
addresses and addresses stored in the DHCP Snooping table.
IEEE 802.1D Bridge – The switch supports IEEE 802.1D transparent bridging. The
address table facilitates data switching by learning addresses, and then filtering or
forwarding traffic based on this information. The address table supports up to 16K
addresses.
1
1-3
Page 32

Introduction
1
Store-and-Forward Switching – The switch copies each frame into its memory
before forwarding them to another port. This ensures that all frames are a standard
Ethernet size and have been verified for accuracy with the cyclic redundancy check
(CRC). This prevents bad frames from entering the network and wasting bandwidth.
To avoid dropping frames on congested ports, the switch provides 32 MB for frame
buffering. This buffer can queue packets awaiting transmission on congested
networks.
Spanning Tree Algorithm – The switch supports these spanning tree protocols:
Spanning Tree Protocol (STP, IEEE 802.1D) – This protocol provides loop detection.
When there are multiple physical paths between segments, this protocol will choose
a single path and disable all others to ensure that only one route exists between any
two stations on the network. This prevents the creation of network loops. However, if
the chosen path should fail for any reason, an alternate path will be activated to
maintain the connection.
Rapid Spanning Tree Protocol (RSTP, IEEE 802.1w) – This protocol reduces the
convergence time for network topology changes to about 3 to 5 seconds, compared
to 30 seconds or more for the older IEEE 802.1D STP standard. It is intended as a
complete replacement for STP, but can still interoperate with switches running the
older standard by automatically reconfiguring ports to STP-compliant mode if they
detect STP protocol messages from attached devices.
Multiple Spanning Tree Protocol (MSTP, IEEE 802.1s) – This protocol is a direct
extension of RSTP. It can provide an independent spanning tree for different VLANs.
It simplifies network management, provides for even faster convergence than RSTP
by limiting the size of each region, and prevents VLAN members from being
segmented from the rest of the group (as sometimes occurs with IEEE 802.1D STP).
Virtual LANs – The switch supports up to 255 VLANs. A Virtual LAN is a collection
of network nodes that share the same collision domain regardless of their physical
location or connection point in the network. The switch supports tagged VLANs
based on the IEEE 802.1Q standard. Members of VLAN groups can be dynamically
learned via GVRP, or ports can be manually assigned to a specific set of VLANs.
This allows the switch to restrict traffic to the VLAN groups to which a user has been
assigned. By segmenting your network into VLANs, you can:
• Eliminate broadcast storms which severely degrade performance in a flat network.
• Simplify network management for node changes/moves by remotely configuring
VLAN membership for any port, rather than having to manually change the network
connection.
• Provide data security by restricting all traffic to the originating VLAN.
• Use private VLANs to restrict traffic to pass only between data ports and the uplink
ports, thereby isolating adjacent ports within the same VLAN, and allowing you to
limit the total number of VLANs that need to be configured.
• Use protocol VLANs to restrict traffic to specified interfaces based on protocol type.
Traffic Prioritization – This switch prioritizes each packet based on the required
level of service, using eight priority queues with strict or Weighted Round Robin
1-4
Page 33

Description of Software Features
Queuing. It uses IEEE 802.1p and 802.1Q tags to prioritize incoming traffic based on
input from the end-station application. These functions can
independent priorities for delay-sensitive data and best-effort data.
This switch also supports several common methods of prioritizing layer 3/4 traffic to
meet application requirements. Traffic can be prioritized based on the priority bits in
the IP frame’s Type of Service (ToS) octet or the number of the TCP/UDP port.
When these services are enabled, the priorities are mapped to a Class of Service
value by the switch, and the traffic then sent to the corresponding output queue.
Quality of Service – Differentiated Services (DiffServ) provides policy-based
management mechanisms used for prioritizing network resources to meet the
requirements of specific traffic types on a per-hop basis. Each packet is classified
upon entry into the network based on access lists, IP Precedence or DSCP values,
or VLAN lists. Using access lists allows you select traffic based on Layer 2, Layer 3,
or Layer 4 information contained in each packet. Based on network policies, different
kinds of traffic can be marked for different kinds of forwarding.
Multicast Filtering – Specific multicast traffic can be assigned to its own VLAN to
ensure that it does not interfere with normal network traffic and to guarantee
real-time delivery by setting the required priority level for the designated VLAN. The
switch uses IGMP Snooping and Query to manage multicast group registration. It
also supports Multicast VLAN Registration (MVR) which allows common multicast
traffic, such as television channels, to be transmitted across a single network-wide
multicast VLAN shared by hosts residing in other standard or private VLAN groups,
while preserving security and data isolation for normal traffic.
IEEE 802.1Q Tunneling (QinQ) – This feature is designed for service providers
carrying traffic for multiple customers across their networks. QinQ tunneling is used
to maintain customer-specific VLAN and Layer 2 protocol configurations even when
different customers use the same internal VLAN IDs. This is accomplished by
inserting Service Provider VLAN (SPVLAN) tags into the customer’s frames when
they enter the service provider’s network, and then stripping the tags when the
frames leave the network.
be used to provide
1
1-5
Page 34

Introduction
1
System Defaults
The switch’s system defaults are provided in the configuration file
“Factory_Default_Config.cfg.” To reset the switch defaults, this file should be set as
the startup configuration file (page 4-15).
The following table lists some of the basic system defaults.
Table 1-2 System Defaults
Function Parameter Default
Console Port
Connection
Authentication Privileged Exec Level Username “admin”
Web Management HTTP Server Enabled
Baud Rate auto
Data bits 8
Stop bits 1
Parity none
Local Console Timeout 0 (disabled)
Password “admin”
Normal Exec Level Username “guest”
Enable Privileged Exec from Normal
Exec Level
RADIUS Authentication Disabled
TACACS Authentication Disabled
802.1X Port Authentication Disabled
HTTPS Enabled
SSH Disabled
Port Security Disabled
DHCP Snooping Disabled
IP Source Guard Disabled
IP Filtering Disabled
HTTP Port Number 80
HTTP Secure Server Enabled
HTTP Secure Port Number 443
Password “guest”
Password “super”
1-6
Page 35

System Defaults
Table 1-2 System Defaults (Continued)
Function Parameter Default
SNMP SNMP Agent Enabled
Community Strings “public” (read only)
Traps Authentication traps: enabled
SNMP V3 View: defaultview
Port Configuration Admin Status Enabled
Auto-negotiation Enabled
Flow Control Disabled
Rate Limiting Input and output limits Disabled
Input limit per port per CoS value Disabled
Port Trunking Static Trunks None
LACP (all ports) Disabled
Storm Protection Status Broadcast: enabled (all ports)
Rate Limit Broadcast: 500 packets per second
Unknown Packet
Blocking
Spanning Tree
Algorithm
Address Table Aging Time 300 seconds
Virtual LANs Default VLAN 1
Status Multicast: disabled
Status Enabled, RSTP
Fast Forwarding (Edge Port) Disabled
PVID 1
Acceptable Frame Type All
Ingress Filtering Disabled
Switchport Mode (Egress Mode) Hybrid: tagged/untagged frames
GVRP (global) Disabled
GVRP (port interface) Disabled
“private” (read/write)
Link-up-down events: enabled
Group: public (read only); private (read/write)
Multicast: disabled
Unicast: disabled
(Defaults: All values based on IEEE 802.1w)
1
1-7
Page 36

Introduction
1
Table 1-2 System Defaults (Continued)
Function Parameter Default
Traffic Prioritization Ingress Port Priority 0
Queue Mode WRR
Weighted Round Robin Queue: 0 1 2 3 4 5 6 7
IP Precedence Priority Disabled
IP DSCP Priority Disabled
IP Port Priority Disabled
VLAN-based Priority Disabled
IP Settings Management. VLAN Any VLAN configured with an IP address
IP Address 0.0.0.0
Subnet Mask 255.0.0.0
Default Gateway 0.0.0.0
DHCP Client: Enabled
DNS Service: Disabled
BOOTP Disabled
Multicast Filtering IGMP Snooping Snooping: Enabled
Multicast VLAN Registration Disabled
System Log Status Enabled
Messages Logged Levels 0-7 (all)
Messages Logged to Flash Levels 0-3
SMTP Email Alerts Event Handler Enabled (but no server defined)
SNTP Clock Synchronization Disabled
Weight: 1 2 4 6 8 10 12 14
Querier: Disabled
1-8
Page 37

Chapter 2: Initial Configuration
Connecting to the Switch
Configuration Options
The switch includes a built-in network management agent. The agent offers a variety
of management options, including SNMP, RMON and a web-based interface. A PC
may also be connected directly to the switch for configuration and monitoring via a
command line interface (CLI).
Note: An IP address for this switch is obtained via DHCP by default. To change this
address, see “Setting an IP Address” on page 2-4.
The switch’s HTTP web agent allows you to configure switch parameters, monitor
port connections, and display statistics using a standard web browser such as
Netscape Navigator version 6.2 and higher or Microsoft IE version 5.0 and higher.
The switch’s web management interface can be accessed from any computer
attached to the network.
The CLI program can be accessed by a direct connection to the RS-232 serial
console port on the switch, or remotely by a Telnet or Secure Shell (SSH)
connection over the network.
The switch’s management agent also supports SNMP (Simple Network
Management Protocol). This SNMP agent permits the switch to be managed from
any system in the network using network management software such as
Te ra w av e’ s TM S .
The switch’s web interface, CLI configuration program, and SNMP agent allow you
to perform the following management functions:
• Set user names and passwords
• Set an IP interface for a management VLAN
• Configure SNMP parameters
• Enable/disable any port
• Set the speed/duplex mode for any port
• Configure the bandwidth of any port by limiting input or output rates
• Control port access through IEEE 802.1X security or static address filtering
• Filter packets using Access Control Lists (ACLs)
• Configure up to 255 IEEE 802.1Q VLANs
• Enable GVRP automatic VLAN registration
• Configure IGMP multicast filtering
• Upload and download system firmware via TFTP
• Upload and download switch configuration files via TFTP
• Configure Spanning Tree parameters
• Configure Class of Service (CoS) priority queuing
2-1
Page 38

Initial Configuration
2
• Configure up to 12 static or LACP trunks
• Enable port mirroring
• Set broadcast storm control on any port
• Display system information and statistics
Required Connections
The switch provides an RS-232 serial port that enables a connection to a PC or
terminal for monitoring and configuring the switch. A null-modem console cable is
provided with the switch.
Attach a VT100-compatible terminal, or a PC running a terminal emulation program
to the switch. You can use the console cable provided with this package, or use a
null-modem cable that complies with the wiring assignments shown in the
Installation Guide.
To connect a terminal to the console port, complete the following steps:
1. Connect the console cable to the serial port on a terminal, or a PC running
terminal emulation software, and tighten the captive retaining screws on the
DB-9 connector.
2. Connect the other end of the cable to the RS-232 serial port on the switch.
3. Make sure the terminal emulation software is set as follows:
• Select the appropriate serial port (COM port 1 or COM port 2).
• Set to any of the following baud rates: 9600, 19200, 38400, 57600, 115200
(Note: Set to 9600 baud if want to view all the system initialization messages.).
• Set the data format to 8 data bits, 1 stop bit, and no parity.
• Set flow control to none.
• Set the emulation mode to VT100.
• When using HyperTerminal, select Terminal keys, not Windows keys.
Notes: 1. When using HyperTerminal with Microsoft® Windows® 2000, make sure that
For a description of how to use the CLI, see “Using the Command Line Interface” on
page 17-1. For a list of all the CLI commands and detailed information on using the
CLI, refer to “Command Groups” on page 17-10.
you have Windows 2000 Service Pack 2 or later installed. Windows 2000
Service Pack 2 fixes the problem of arrow keys not functioning in
HyperTerminal’s VT100 emulation. See www.microsoft.com for information
on Windows 2000 service packs.
2. Refer to “Line Commands” on page 19-19 for a complete description of
console configuration options.
3. Once you have set up the terminal correctly, the console login screen will be
displayed.
2-2
Page 39

Basic Configuration
2
Remote Connections
Prior to accessing the switch’s onboard agent via a network connection, you must
first configure it with a valid IP address, subnet mask, and default gateway using a
console connection, DHCP or BOOTP protocol.
An IP address for this switch is obtained via DHCP by default. To manually configure
this address or enable dynamic address assignment via DHCP or BOOTP, see
“Setting an IP Address” on page 2-4.
Note: This switch supports four concurrent Telnet/SSH sessions.
After configuring the switch’s IP parameters, you can access the onboard
configuration program from anywhere within the attached network. The onboard
configuration program can be accessed using Telnet from any computer attached to
the network. The switch can also be managed by any computer using a web
browser (Internet Explorer 5.0 or above, or Netscape Navigator 6.2 or above), or
from a network computer using SNMP network management software.
Note: The onboard program only provides access to basic configuration functions. To
access the full range of SNMP management functions, you must use
SNMP-based network management software.
Basic Configuration
Console Connection
The CLI program provides two different command levels — normal access level
(Normal Exec) and privileged access level (Privileged Exec). The commands
available at the Normal Exec level are a limited subset of those available at the
Privileged Exec level and allow you to only display information and use basic
utilities. To fully configure the switch parameters, you must access the CLI at the
Privileged Exec level.
Access to both CLI levels are controlled by user names and passwords. The switch
has a default user name and password for each level. To log into the CLI at the
Privileged Exec level using the default user name and password, perform these
steps:
1. To initiate your console connection, press <Enter>. The “User Access
Verification” procedure starts.
2. At the Username prompt, enter “admin.”
3. At the Password prompt, also enter “admin.” (The password characters are not
displayed on the console screen.)
4. The session is opened and the CLI displays the “Console#” prompt indicating
you have access at the Privileged Exec level.
2-3
Page 40

Initial Configuration
2
Setting Passwords
Note: If this is your first time to log into the CLI program, you should define new
passwords for both default user names using the “username” command, record
them and put them in a safe place.
Passwords can consist of up to 8 alphanumeric characters and are case sensitive.
To prevent unauthorized access to the switch, set the passwords as follows:
1. Open the console interface with the default user name and password “admin” to
access the Privileged Exec level.
2. Type “configure” and press <Enter>.
3. Type “username guest password 0 password,” for the Normal Exec level, where
password is your new password. Press <Enter>.
4. Type “username admin password 0 password,” for the Privileged Exec level,
where password is your new password. Press <Enter>.
Username: admin
Password:
CLI session with the Layer 2 Ethernet Metro Access Switch
To end the CLI session, enter [Exit].
Console#configure 18-2
Console(config)#username guest password 0 [password] 21-2
Console(config)#username admin password 0 [password]
Console(config)#
*
is opened.
* Most of the interface examples in this manual are based on the ES3528. There is no
significant difference in the interface provided for the ES3528 and ES3528-WDM.
Setting an IP Address
You must establish IP address information for the switch to obtain management
access through the network. This can be done in either of the following ways:
Manual — You have to input the information, including IP address and subnet mask.
If your management station is not in the same IP subnet as the switch, you will also
need to specify the default gateway router.
Dynamic — The switch sends IP configuration requests to BOOTP or DHCP
address allocation servers on the network.
Manual Configuration
You can manually assign an IP address to the switch. You may also need to specify
a default gateway that resides between this device and management stations that
exist on another network segment. Valid IP addresses consist of four decimal
numbers, 0 to 255, separated by periods. Anything outside this format will not be
accepted by the CLI program.
Note: An IP address for this switch is obtained via DHCP by default.
2-4
Page 41

Basic Configuration
Before you can assign an IP address to the switch, you must obtain the following
information from your network administrator:
• IP address for the switch
• Network mask for this network
• Default gateway for the network
To assign an IP address to the switch, complete the following steps:
1. From the Global Configuration mode prompt, type “interface vlan 1” to access
the interface-configuration mode. Press <Enter>.
2. Type “ip address ip-address netmask,” where “ip-address” is the switch IP
address and “netmask” is the network mask for the network. Press <Enter>.
3. Type “exit” to return to the global configuration mode prompt. Press <Enter>.
4. To set the IP address of the default gateway for the network to which the switch
belongs, type “ip default-gateway gateway,” where “gateway” is the IP address
of the default gateway. Press <Enter>.
Console(config)#interface vlan 1 24-1
Console(config-if)#ip address 192.168.1.5 255.255.255.0 35-1
Console(config-if)#exit
Console(config)#ip default-gateway 192.168.1.254 35-2
Console(config)#
2
Dynamic Configuration
If you select the “bootp” or “dhcp” option, IP will be enabled but will not function until
a BOOTP or DHCP reply has been received. You therefore need to use the “ip dhcp
restart” command to start broadcasting service requests. Requests will be sent
periodically in an effort to obtain IP configuration information. (BOOTP and DHCP
values can include the IP address, subnet mask, and default gateway.)
If the “bootp” or “dhcp” option is saved to the startup-config file (step 6), then the
switch will start broadcasting service requests as soon as it is powered on.
To automatically configure the switch by communicating with BOOTP or DHCP
address allocation servers on the network, complete the following steps:
1. From the Global Configuration mode prompt, type “interface vlan 1” to access
the interface-configuration mode. Press <Enter>.
2. At the interface-configuration mode prompt, use one of the following commands:
• To obtain IP settings via DHCP, type “ip address dhcp” and press <Enter>.
• To obtain IP settings via BOOTP, type “ip address bootp” and press <Enter>.
3. Type “end” to return to the Privileged Exec mode. Press <Enter>.
4. Type “ip dhcp restart” to begin broadcasting service requests. Press <Enter>.
2-5
Page 42

Initial Configuration
2
5. Wait a few minutes, and then check the IP configuration settings by typing the
“show ip interface” command. Press <Enter>.
6. Then save your configuration changes by typing “copy running-config
startup-config.” Enter the startup file name and press <Enter>.
Console(config)#interface vlan 1 24-1
Console(config-if)#ip address dhcp 35-1
Console(config-if)#end
Console#ip dhcp restart 35-3
Console#show ip interface 35-4
IP address and netmask: 192.168.1.54 255.255.255.0 on VLAN 1,
and address mode: DHCP
Console#copy running-config startup-config 19-13
Startup configuration file name []: startup
\Write to FLASH Programming.
\Write to FLASH finish.
Success.
Enabling SNMP Management Access
The switch can be configured to accept management commands from Simple
Network Management Protocol (SNMP) applications such as HP OpenView. You
can configure the switch to (1) respond to SNMP requests or (2) generate SNMP
traps.
When SNMP management stations send requests to the switch (either to return
information or to set a parameter), the switch provides the requested data or sets the
specified parameter. The switch can also be configured to send information to
SNMP managers (without being requested by the managers) through trap
messages, which inform the manager that certain events have occurred.
The switch includes an SNMP agent that supports SNMP version 1, 2c, and 3
clients. To provide management access for version 1 or 2c clients, you must specify
a community string. The switch provides a default MIB View (i.e., an SNMPv3
construct) for the default “public” community string that provides read access to the
entire MIB tree, and a default view for the “private” community string that provides
read/write access to the entire MIB tree. However, you may assign new views to
version 1 or 2c community strings that suit your specific security requirements (see
page 5-16).
Community Strings (for SNMP version 1 and 2c clients)
Community strings are used to control management access to SNMP version 1 and
2c stations, as well as to authorize SNMP stations to receive trap messages from
the switch. You therefore need to assign community strings to specified users, and
set the access level.
2-6
Page 43

Basic Configuration
2
The default strings are:
• public - with read-only access. Authorized management stations are only able to
retrieve MIB objects.
• private - with read-write access. Authorized management stations are able to both
retrieve and modify MIB objects.
To prevent unauthorized access to the switch from SNMP version 1 or 2c clients, it is
recommended that you change the default community strings.
To configure a community string, complete the following steps:
1. From the Privileged Exec level global configuration mode prompt, type
“snmp-server community string mode,” where “string” is the community access
string and “mode” is rw (read/write) or ro (read only). Press <Enter>. (Note that
the default mode is read only.)
2. To remove an existing string, simply type “no snmp-server community string,”
where “string” is the community access string to remove. Press <Enter>.
Console(config)#snmp-server community admin rw 20-3
Console(config)#snmp-server community private
Console(config)#
Note: If you do not intend to support access to SNMP version 1 and 2c clients, we
recommend that you delete both of the default community strings. If there are no
community strings, then SNMP management access from SNMP v1 and v2c
clients is disabled.
Trap Receivers
You can also specify SNMP stations that are to receive traps from the switch. To
configure a trap receiver, use the “snmp-server host” command. From the Privileged
Exec level global configuration mode prompt, type:
“snmp-server host host-address community-string
[version {1 | 2c | 3 {auth | noauth | priv}}]”
where “host-address” is the IP address for the trap receiver, “community-string”
specifies access rights for a version 1/2c host, or is the user name of a version 3
host, “version” indicates the SNMP client version, and “auth | noauth | priv” means
that authentication, no authentication, or authentication and privacy is used for v3
clients. Then press <Enter>. For a more detailed description of these parameters,
see “snmp-server host” on page 20-5. The following example creates a trap host for
each type of SNMP client.
Console(config)#snmp-server host 10.1.19.23 batman 20-5
Console(config)#snmp-server host 10.1.19.98 robin version 2c
Console(config)#snmp-server host 10.1.19.34 barbie version 3 auth
Console(config)#
2-7
Page 44

Initial Configuration
2
Configuring Access for SNMP Version 3 Clients
To configure management access for SNMPv3 clients, you need to first create a
view that defines the portions of MIB that the client can read or write, assign the view
to a group, and then assign the user to a group. The following example creates one
view called “mib-2” that includes the entire MIB-2 tree branch, and then another view
that includes the IEEE 802.1d bridge MIB. It assigns these respective read and read/
write views to a group call “r&d” and specifies group authentication via MD5 or SHA.
In the last step, it assigns a v3 user to this group, indicating that MD5 will be used for
authentication, provides the password “greenpeace” for authentication, and the
password “einstien” for encryption.
Console(config)#snmp-server view mib-2 1.3.6.1.2.1 included 20-10
Console(config)#snmp-server view 802.1d 1.3.6.1.2.1.17 included
Console(config)#snmp-server group r&d v3 auth mib-2 802.1d 20-11
Console(config)#snmp-server user steve group r&d v3 auth md5
greenpeace priv des56 einstien 20-14
Console(config)#
For a more detailed explanation on how to configure the switch for access from
SNMP v3 clients, refer to “Simple Network Management Protocol” on page 5-1, or
refer to the specific CLI commands for SNMP starting on page 20-1.
Managing System Files
The switch’s flash memory supports three types of system files that can be managed
by the CLI program, web interface, or SNMP. The switch’s file system allows files to
be uploaded and downloaded, copied, deleted, and set as a start-up file.
The three types of files are:
• Configuration — This file type stores system configuration information and is
created when configuration settings are saved. Saved configuration files can be
selected as a system start-up file or can be uploaded via TFTP to a server for
backup. The file named “Factory_Default_Config.cfg” contains all the system
default settings and cannot be deleted from the system. If the system is booted with
the factory default settings, the master unit will also create a file named
“startup1.cfg” that contains system settings for initialization, including information
about the unit identifier, MAC address, and installed module type. The
configuration settings from the factory defaults configuration file are copied to this
file, which is then used to boot the switch. See “Saving or Restoring Configuration
Settings” on page 4-14 for more information.
• Operation Code — System software that is executed after boot-up, also known as
run-time code. This code runs the switch operations and provides the CLI and web
management interfaces. See “Managing Firmware” on page 4-11 for more
information.
• Diagnostic Code — Software that is run during system boot-up, also known as
POST (Power On Self-Test).
2-8
Page 45

Managing System Files
Due to the size limit of the flash memory, the switch supports only two operation
code files. However, you can have as many diagnostic code files and configuration
files as available flash memory space allows. The switch has a total of 32 Mbytes of
flash memory for system files.
In the system flash memory, one file of each type must be set as the start-up file.
During a system boot, the diagnostic and operation code files set as the start-up file
are run, and then the start-up configuration file is loaded.
Note that configuration files should be downloaded using a file name that reflects the
contents or usage of the file settings. If you download directly to the running-config,
the system will reboot, and the settings will have to be copied from the
running-config to a permanent file.
2
Saving Configuration Settings
Configuration commands only modify the running configuration file and are not
saved when the switch is rebooted. To save all your configuration changes in
nonvolatile storage, you must copy the running configuration file to the start-up
configuration file using the “copy” command.
New startup configuration files must have a name specified. File names on the
switch are case-sensitive, can be from 1 to 31 characters, must not contain slashes
(\ or /), and the leading letter of the file name must not be a period (.). (Valid
characters: A-Z, a-z, 0-9, “.”, “-”, “_”)
There can be more than one user-defined configuration file saved in the switch’s
flash memory, but only one is designated as the “startup” file that is loaded when the
switch boots. The copy running-config startup-config command always sets the
new file as the startup file. To select a previously saved configuration file, use the
boot system config:<filename> command.
The maximum number of saved configuration files depends on available flash
memory, with each configuration file normally requiring less than 20 kbytes. The
amount of available flash memory can be checked by using the dir command.
To save the current configuration settings, enter the following command:
1. From the Privileged Exec mode prompt, type “copy running-config
startup-config” and press <Enter>.
2. Enter the name of the start-up file. Press <Enter>.
Console#copy running-config startup-config 19-13
Startup configuration file name []: startup
\Write to FLASH Programming.
\Write to FLASH finish.
Success.
Console#
2-9
Page 46

Initial Configuration
2
2-10
Page 47

Section II: Switch Management
This section describes the basic switch features, along with a detailed description of
how to configure each feature via a web browser, and a brief example for the
Command Line Interface.
Configuring the Switch . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 3-1
Basic Management Tasks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 4-1
Simple Network Management Protocol . . . . . . . . . . . . . . . . . . . . . . . . . . . . 5-1
User Authentication . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 6-1
Client Security . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 7-1
Access Control Lists . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 8-1
Port Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 9-1
Address Table Settings . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 10-1
Spanning Tree Algorithm . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 11-1
VLAN Configuration . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 12-1
Class of Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 13-1
Quality of Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 14-1
Multicast Filtering . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 15-1
Domain Name Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 16-1
Page 48

Switch Management
Page 49

Chapter 3: Configuring the Switch
Using the Web Interface
This switch provides an embedded HTTP web agent. Using a web browser you can
configure the switch and view statistics to monitor network activity. The web agent
can be accessed by any computer on the network using a standard web browser
(Internet Explorer 5.0 or above, or Netscape Navigator 6.2 or above).
Note: You can also use the Command Line Interface (CLI) to manage the switch over a
serial connection to the console port or via Telnet. For more information on using
the CLI, refer to Chapter 17: “Overview of Command Line Interface.”
Prior to accessing the switch from a web browser, be sure you have first performed
the following tasks:
1. Configure the switch with a valid IP address, subnet mask, and default gateway
using an out-of-band serial connection, BOOTP or DHCP protocol. (See “Setting
an IP Address” on page 2-4.)
2. Set user names and passwords using an out-of-band serial connection. Access
to the web agent is controlled by the same user names and passwords as the
onboard configuration program. (See “Setting Passwords” on page 2-4.)
3. After you enter a user name and password, you will have access to the system
configuration program.
Notes: 1.
You are allowed three attempts to enter the correct password; on the third
failed attempt the current connection is terminated.
2. If you log into the web interface as guest (Normal Exec level), you can view
the configuration settings or change the guest password. If you log in as
“admin” (Privileged Exec level), you can change the settings on any page.
3. If the path between your management station and this switch does not pass
through any device that uses the Spanning Tree Algorithm, then you can set
the switch port attached to your management station to fast forwarding (i.e.,
enable Admin Edge Port) to improve the switch’s response time to
management commands issued through the web interface. See “Configuring
Interface Settings” on page 11-13.
3-1
Page 50

Configuring the Switch
3
Navigating the Web Browser Interface
To access the web-browser interface you must first enter a user name and
password. The administrator has Read/Write access to all configuration parameters
and statistics. The default user name and password “admin” is used for the
administrator.
Home Page
When your web browser connects with the switch’s web agent, the home page is
displayed as shown below. The home page displays the Main Menu on the left side
of the screen and System Information on the right side. The Main Menu links are
used to navigate to other menus, and display configuration parameters and
statistics.
Figure 3-1 Home Page
Note: The examples in this chapter are based on the ES3528B. Other than the
subscriber port type, there are no significant differences between the ES3528 and
ES3528-WDM. The panel graphics for both switch types are shown on the
following page.
3-2
Page 51

Navigating the Web Browser Interface
3
Configuration Options
Configurable parameters have a dialog box or a drop-down list. Once a configuration
change has been made on a page, be sure to click on the Apply button to confirm
the new setting. The following table summarizes the web page configuration
buttons.
Table 3-1 Web Page Configuration Buttons
Button Action
Apply Sets specified values to the system.
Revert Cancels specified values and restores current values prior to
Help Links directly to web help.
pressing “Apply.”
Notes: 1.
To ensure proper screen refresh, be sure that Internet Explorer 5.x is
configured as follows: Under the menu “Tools / Internet Options / General /
Temporary Internet Files / Settings,” the setting for item “Check for newer
versions of stored pages” should be “Every visit to the page.”
2. When using Internet Explorer 5.0, you may have to manually refresh the
screen after making configuration changes by pressing the browser’s refresh
button.
Panel Display
The web agent displays an image of the switch’s ports. The Mode can be set to
display different information for the ports, including Active (i.e., up or down), Duplex
(i.e., half or full duplex), or Flow Control (i.e., with or without flow control). Clicking on
the image of a port opens the Port Configuration page as described on page 9-3.
ES3528
ES3528-WDM
Figure 3-2 Front Panel Indicators
3-3
Page 52

Configuring the Switch
3
Main Menu
Using the onboard web agent, you can define system parameters, manage and
control the switch, and all its ports, or monitor network conditions. The following
table briefly describes the selections available from this program.
Table 3-2 Switch Main Menu
Menu Description Page
System 4-1
System Information Provides basic system description, including contact information 4-1
System Mode Configures the switch to operate in normal mode or QinQ
System MTU Sets the maximum transfer unit for traffic crossing the switch 4-4
Switch Information Shows the number of ports, hardware/firmware version
Bridge Extension Shows the bridge extension parameters 4-7
IP Configuration Sets the IP address for management access 4-8
Jumbo Frames Enables support for jumbo frames 4-5
File Management 4-11
Copy Operation Allows the transfer and copying files 4-12
Delete Allows deletion of files from the flash memory 4-12
Set Startup Sets the startup file 4-12
Line 4-16
Console Sets console port connection parameters 4-16
Telnet Sets Telnet connection parameters 4-18
Log 4-20
Logs Sends error messages to a logging process 4-23
System Logs Stores and displays error messages 4-20
Remote Logs Configures the logging of messages to a remote logging process 4-21
SMTP Sends an SMTP client message to a participating server 4-23
Reset Restarts the switch 4-25
SNTP 4-26
Configuration Configures SNTP client settings, including a specified list of
Clock Time Zone Sets the local time zone for the system clock 4-27
SNMP 5-1
Configuration Configures community strings and related trap functions 5-3
Agent Status Enables or disables SNMP 5-2
tunneling mode
numbers, and power status
servers
4-3
4-6
4-26
3-4
Page 53

Navigating the Web Browser Interface
Table 3-2 Switch Main Menu (Continued)
Menu Description Page
SNMPv3 5-7
Engine ID Sets the SNMP v3 engine ID 5-7
Remote Engine ID Sets the SNMP v3 engine ID on a remote device 5-8
Users Configures SNMP v3 users 5-9
Remote Users Configures SNMP v3 users on a remote device 5-11
Groups Configures SNMP v3 groups 5-13
Views Configures SNMP v3 views 5-16
Security 6-1
User Accounts Configures user names, passwords, and access levels 6-1
Authentication Settings Configures authentication sequence, RADIUS and TACACS 6-2
HTTPS Settings Configures secure HTTP settings 6-5
SSH 6-7
Settings Configures Secure Shell server settings 6-11
Host-Key Settings Generates the host key pair (public and private) 6-9
Port Security Configures per port security, including status, response for
security breach, and maximum allowed MAC addresses
802.1X Port authentication 6-13
Information Displays global configuration settings 6-14
Configuration Configures global configuration parameters 6-15
Port Configuration Sets the authentication mode for individual ports 6-15
Statistics Displays protocol statistics for the selected port 6-18
ACL 8-1
Configuration Configures packet filtering based on IP or MAC addresses 8-1
Mask Configuration Controls the order in which ACL rules are checked 8-9
Port Binding Binds a port to the specified ACL 8-13
IP Filter Configures IP addresses that are allowed management access 6-20
Port 9-1
Port Information Displays port connection status 9-1
Trunk Information Displays trunk connection status 9-1
Port Configuration Configures port connection settings 9-3
Trunk Configuration Configures trunk connection settings 9-3
Trunk Membership Specifies ports to group into static trunks 9-7
3
7-1
3-5
Page 54

Configuring the Switch
3
Table 3-2 Switch Main Menu (Continued)
Menu Description Page
LACP 9-8
Configuration Allows ports to dynamically join trunks 9-8
Aggregation Port Configures parameters for link aggregation group members 9-10
Port Counters Information Displays statistics for LACP protocol messages 9-13
Port Internal Information Displays settings and operational state for the local side 9-14
Port Neighbors Information Displays settings and operational state for the remote side 9-16
Port Broadcast Control Sets the broadcast storm threshold for each port 9-17
Trunk Broadcast Control Sets the broadcast storm threshold for each trunk 9-17
Mirror Port Configuration Sets the source and target ports for mirroring 9-19
Rate Limit 9-20
Input Port Configuration Sets the input rate limit for each port 9-20
Input Trunk Configuration Sets the input rate limit for each trunk 9-20
Output Port Configuration Sets the output rate limit for each port 9-20
Output Trunk Configuration Sets the output rate limit for each trunk 9-20
Port Statistics Lists Ethernet and RMON port statistics 9-21
Address Table 10-1
Static Addresses Displays entries for interface, address or VLAN 10-1
Dynamic Addresses Displays or edits static entries in the Address Table 10-2
Address Aging Sets timeout for dynamically learned entries 10-4
Spanning Tree 11- 1
STA
Information Displays STA values used for the bridge 11-3
Configuration Configures global bridge settings for STP, RSTP and MSTP 11-6
Port Information Displays individual port settings for STA 11-10
Trunk Information Displays individual trunk settings for STA 11-10
Port Configuration Configures individual port settings for STA 11-13
Trunk Configuration Configures individual trunk settings for STA 11-13
MSTP
VLAN Configuration Configures priority and VLANs for a spanning tree instance 11-16
Port Information Displays port settings for a specified MST instance 11-19
Trunk Information Displays trunk settings for a specified MST instance 11-19
Port Configuration Configures port settings for a specified MST instance 11-20
3-6
Page 55

Navigating the Web Browser Interface
Table 3-2 Switch Main Menu (Continued)
Menu Description Page
Trunk Configuration Configures trunk settings for a specified MST instance 11-20
VLAN 12-1
802.1Q VLAN 12-1
GVRP Status Enables GVRP VLAN registration protocol 12-4
Basic Information Displays information on the VLAN type supported by this switch 12-4
Current Table Shows the current port members of each VLAN and whether or
Static List Used to create or remove VLAN groups 12-6
Static Table Modifies the settings for an existing VLAN 12-7
Static Membership by Port Configures membership type for interfaces, including tagged,
Port Configuration Specifies default PVID and VLAN attributes 12-10
Trunk Configuration Specifies default trunk VID and VLAN attributes 12-10
Private VLAN 12-17
Status Enables or disables the private VLAN 12-17
Link Status Configures the private VLAN 12-18
Protocol VLAN 12-18
Configuration Creates a protocol group, specifying the supported protocols 12-19
Port Configuration Maps a protocol group to a VLAN 12-20
Priority 13-1
Default Port Priority Sets the default priority for each port 13-1
Default Trunk Priority Sets the default priority for each trunk 13-1
Traffic Classes Maps IEEE 802.1p priority tags to output queues 13-3
Traffic Classes Status Enables/disables traffic class priorities (not implemented) NA
Queue Mode Sets queue mode to strict priority or Weighted Round-Robin 13-5
Queue Scheduling Configures Weighted Round Robin queueing 13-6
IP Precedence/
DSCP Priority Status
IP Precedence Priority Sets IP Type of Service priority, mapping the precedence tag to
IP DSCP Priority Sets IP Differentiated Services Code Point priority, mapping a
IP Port Priority Status Globally enables or disables IP Port Priority 13-11
IP Port Priority Sets TCP/UDP port priority, defining the socket number and
not the port is tagged or untagged
untagged or forbidden
Globally selects IP Precedence or DSCP Priority, or disables
both.
a class-of-service value
DSCP tag to a class-of-service value
associated class-of-service value
3
12-5
12-9
13-7
13-8
13-10
13-8
3-7
Page 56

Configuring the Switch
3
Table 3-2 Switch Main Menu (Continued)
Menu Description Page
QoS 14-1
DiffServ Configure QoS classification criteria and service policies 14-1
Class Map Creates a class map for a type of traffic 14-2
Policy Map Creates a policy map for multiple interfaces 14-5
Service Policy Applies a policy map defined to an ingress port 14-8
IGMP Snooping 15-2
IGMP Configuration Enables multicast filtering; configures parameters for multicast
Multicast Router
Port Information
Static Multicast Router
Port Configuration
IP Multicast Registration
Table
IGMP Member Port Table Indicates multicast addresses associated with the selected
MVR 15-9
Configuration Globally enables MVR, sets the MVR VLAN, adds multicast
Port Information Displays MVR interface type, MVR operational and activity
Trunk Information Displays MVR interface type, MVR operational and activity
Group IP Information Displays the ports attached to an MVR multicast stream 15-14
Port Configuration Configures MVR interface type and immediate leave status 15-8
Trunk Configuration Configures MVR interface type and immediate leave status 15-8
Group Member Configuration Statically assigns MVR multicast streams to an interface 15-15
DNS 16-1
General Configuration Enables DNS; configures domain name and domain list; and
Static Host Table Configures static entries for domain name to address mapping 16-3
Cache Displays cache entries discovered by designated name servers 16-5
query
Displays the ports that are attached to a neighboring multicast
router for each VLAN ID
Assigns ports that are attached to a neighboring multicast router 15-6
Displays all multicast groups active on this switch, including
multicast IP addresses and VLAN ID
VLAN
stream addresses
status, and immediate leave status
status, and immediate leave status
specifies IP address of name servers for dynamic lookup
15-3
15-5
15-7
15-7
15-10
15-11
15-11
16-1
3-8
Page 57

Chapter 4: Basic Management Tasks
This chapter describes the basic functions required to set up management access to
the switch, display or upgrade operating software, or reset the system.
Displaying System Information
You can easily identify the system by displaying the device name, location and
contact information.
Field Attributes
• System Name – Name assigned to the switch system.
• Object ID – MIB II object ID for switch’s network management subsystem.
• Location – Specifies the system location.
• Contact – Administrator responsible for the system.
• System Up Time – Length of time the management agent has been up.
These additional parameters are displayed for the CLI.
• System Description – Brief description of device type.
• MAC Address – The physical layer address for this switch.
• Web Server – Shows if management access via HTTP is enabled.
• Web Server Port – Shows the TCP port number used by the web interface.
• Web Secure Server – Shows if management access via HTTPS is enabled.
• Web Secure Server Port – Shows the TCP port used by the HTTPS interface.
• Telnet Server – Shows if management access via Telnet is enabled.
• Telnet Server Port – Shows the TCP port used by the Telnet interface.
• Authentication Login – Shows the user login authentication sequence.
• Jumbo Frame – Shows if jumbo frames are enabled.
• Power Module Status – Shows the power module status.
• Power Module Type – Shows the power module type.
• Fan – Shows the power fan status.
• POST Result – Shows results of the power-on self-test
4-1
Page 58

Basic Management Tasks
4
Web – Click System, System Information. Specify the system name, location, and
contact information for the system administrator, then click Apply. (This page also
includes a Telnet button that allows access to the Command Line Interface via Telnet.)
Figure 4-1 System Information
CLI – Specify the hostname, location and contact information.
Console(config)#hostname R&D 5 19-1
Console(config)#snmp-server location WC 9 20-4
Console(config)#snmp-server contact Ted 20-4
Console(config)#exit
Console#show system 19-6
System Description: 24 port Ethernet Metro Access Switch
System OID String: 1.3.6.1.4.1.259.8.2.2
System Information
System Up Time: 0 days, 0 hours, 24 minutes, and 7.84 seconds
System Name: R&D 5
System Location: WC 9
System Contact: Ted
MAC Address (Unit1): 00-12-CF-21-DC-E0
Web Server: Enabled
Web Server Port: 80
Web Secure Server: Enabled
Web Secure Server Port: 443
Telnet Server: Enable
Telnet Server Port: 23
Jumbo Frame: Disabled
Power Module A Status : UP
Power Module B Status : Not present
Power Module A Type :
Power Module B Type : [None]
Fan(1) : OK
Fan(2) : OK
Fan(3) : OK
†
*
4-2
Page 59

Configuring the Switch for Normal Operation or Tunneling Mode
POST Result:
DUMMY Test 1 ................. PASS
UART Loopback Test ........... PASS
DRAM Test .................... PASS
Timer Test ................... PASS
I2C Bus Initialization ....... PASS
Switch Int Loopback Test ..... PASS
Console#
* ES3528-WDM System Description: 24 port WDM Metro Access Switch
† ES3528-WDM System OID String: 1.3.6.1.4.1.259.8.2.3
4
Configuring the Switch for
Normal Operation or Tunneling Mode
The system can be configured to operate in normal mode or IEEE 802.1Q (QinQ)
tunneling mode which is used for passing Layer 2 traffic across a service provider’s
metropolitan area network.
Command Attributes
System Mode – Sets the switch to operate in one of the following modes:
• Normal Mode – The switch functions in normal operating mode. (This is the default
operating mode.)
• QinQ Mode – Sets the switch to QinQ mode, and allows the QinQ tunnel port to
be configured. For an explanation of QinQ see “Configuring IEEE 802.1Q
Tunneling” on page 12-12.
Web – Click System, System Mode. Select the required system mode, and click
Apply.
Figure 4-2 System Mode
CLI – This example sets the switch to operate in QinQ mode.
Console(config)#system mode qinq 19-8
Console(config)#exit
Console#show system mode 19-9
System mode is QinQ mode
Console#
4-3
Page 60

Basic Management Tasks
4
Configuring the Maximum Frame Size
The maximum transfer unit (or frame size) for traffic crossing the switch should be
set to minimize unnecessary fragmentation and maximize the transfer of large
sequential data streams.
Command Usage
• Fast Ethernet ports are only affected by the System MTU setting.
• Gigabit Ethernet ports are only affected by the Jumbo frame size setting.
• The switch provides more efficient throughput for large sequential data transfers
by supporting jumbo frames on Gigabit Ethernet ports of up to 9216 bytes.
Compared to standard Ethernet frames that run only up to 1.5 KB, using jumbo
frames for Gigabit Ethernet significantly reduces the per-packet overhead required
to process protocol encapsulation fields.
• Frame sizes for Fast Ethernet ports can be extended up to 1546 bytes, and are
used primarily to allow for additional header fields – not to significantly increase the
per-packet data size. These Fast Ethernet extended fames and are more often
called “baby jumbo frames.”
• To use jumbo frames, both the source and destination end nodes (such as a
computer or server) must support this feature. Also, when the connection is
operating at full duplex, all switches in the network between the two end nodes
must be able to accept the extended frame size. And for half-duplex connections,
all devices in the collision domain would need to support jumbo frames.
• After setting the jumbo frame size, remember to implement the new setting by
enabling jumbo frames as described in the next section.
Command Attributes
• System MTU (1500-1548) – Specifies the MTU size for Fast Ethernet ports.
(Range: 1500-1548 bytes)
• Jumbo (1500-9216) – Specifies the jumbo frame size (MTU) for Gigabit Ethernet
ports. (Range: 1500-9216 bytes)
Web – Click System, System MTU. Set the maximum frame size for Fast Ethernet
and Gigabit Ethernet ports, then click Apply.
Figure 4-3 System MTU
4-4
Page 61

Configuring Support for Jumbo Frames
CLI – This example sets the MTU for Fast Ethernet ports to 1528 bytes.
Console(config)#system mtu 1528 19-11
Console(config)#exit
Console#show system mtu 19-11
System MTU size is 1528 Bytes
System Jumbo MTU size is 1518 Bytes
Console#
4
Configuring Support for Jumbo Frames
The switch provides more efficient throughput for large sequential data transfers by
supporting jumbo frames up to 9216 bytes for Gigabit Ethernet. Compared to
standard Ethernet frames that run only up to 1.5 KB, using jumbo frames
significantly reduces the per-packet overhead required to process protocol
encapsulation fields. Frame sizes for Fast Ethernet ports can be extended up to
1546 bytes, and are used primarily to allow for additional header fields – not to
significantly increase the per-packet data size.
Command Usage
To use jumbo frames, both the source and destination end nodes (such as a
computer or server) must support this feature. Also, when the connection is
operating at full duplex, all switches in the network between the two end nodes must
be able to accept the extended frame size. And for half-duplex connections, all
devices in the collision domain would need to support jumbo frames.
Command Attributes
Jumbo Packet Status – Configures support for jumbo frames. (Default: Disabled)
Web – Click System, Jumbo Frames. Enable or disable support for jumbo frames,
and click Apply.
Figure 4-4 Configuring Support for Jumbo Frames
CLI – This example enables jumbo frames globally for the switch.
Console(config)#jumbo frame 19-10
Console(config)#
4-5
Page 62

Basic Management Tasks
4
Displaying Switch Hardware/Software Versions
Use the Switch Information page to display hardware/firmware version numbers for
the main board and management software, as well as the power status of the
system.
Field Attributes
Main Board
• Serial Number – The serial number of the switch.
• Hardware Version – Hardware version of the main board.
• EPLD Version – Version number of EEPROM Programmable Logic Device.
• Number of Ports – Number of built-in ports.
• Main Power Status – Displays the status of the primary power supply.
• Redundant Power Status – Displays the status of the redundant power supply.
Management Software
• Unit ID – Unit number in stack.
• Loader Version – Version number of loader code.
• Boot-ROM Version – Version of Power-On Self-Test (POST) and boot code.
• Operation Code Version – Version number of runtime code.
• Role – Shows that this switch is operating as Master.
Web – Click System, Switch Information.
4-6
Figure 4-5 Switch Information
Page 63

Displaying Bridge Extension Capabilities
4
CLI – Use the following command to display version information.
Console#show version 19-7
Unit 1
Serial Number: 0000E8900000
Hardware Version: R01
EPLD Version: 0.01
Number of Ports: 29
Agent (Master)
Unit ID: 1
Loader Version: 1.0.0.1
Boot ROM Version: 1.0.0.7
Operation Code Version: 1.0.1.7
Console#
Displaying Bridge Extension Capabilities
The Bridge MIB includes extensions for managed devices that support Multicast
Filtering, Traffic Classes, and Virtual LANs. You can access these extensions to
display default settings for the key variables.
Field Attributes
• Extended Multicast Filtering Services – This switch does not support the filtering
of individual multicast addresses based on GMRP (GARP Multicast Registration
Protocol).
• Traffic Classes – This switch provides mapping of user priorities to multiple traffic
classes. (Refer to “Class of Service” on page 13-1.)
• Static Entry Individual Port – This switch allows static filtering for unicast and
multicast addresses. (Refer to “Setting Static Addresses” on page 10-1.)
• VLAN Learning – This switch uses Independent VLAN Learning (IVL), where each
port maintains its own filtering database.
• Configurable PVID Tagging – This switch allows you to override the default Port
VLAN ID (PVID used in frame tags) and egress status (VLAN-Tagged or
Untagged) on each port. (Refer to “VLAN Configuration” on page 12-1.)
• Local VLAN Capable – This switch does not support multiple local bridges outside
of the scope of 802.1Q defined VLANs.
• GMRP – GARP Multicast Registration Protocol (GMRP) allows network devices to
register endstations with multicast groups. This switch does not support GMRP; it
uses the Internet Group Management Protocol (IGMP) to provide automatic
multicast filtering.
4-7
Page 64

Basic Management Tasks
4
Web – Click System, Bridge Extension.
Figure 4-6 Displaying Bridge Extension Configuration
CLI – Enter the following command.
Console#show bridge-ext 30-2
Max support VLAN numbers: 256
Max support VLAN ID: 4094
Extended multicast filtering services: No
Static entry individual port: Yes
VLAN learning: IVL
Configurable PVID tagging: Yes
Local VLAN capable: No
Traffic classes: Enabled
Global GVRP status: Disabled
GMRP: Disabled
Console#
Setting the Switch’s IP Address
This section describes how to configure an IP interface for management access
over the network. The IP address for this switch is obtained via DHCP by default. To
manually configure an address, you need to change the switch’s default settings to
values that are compatible with your network. You may also need to a establish a
default gateway between the switch and management stations that exist on another
network segment.
You can manually configure a specific IP address, or direct the device to obtain an
address from a BOOTP or DHCP server. Valid IP addresses consist of four decimal
numbers, 0 to 255, separated by periods. Anything outside this format will not be
accepted by the CLI program.
4-8
Page 65

Setting the Switch’s IP Address
Command Attributes
• Management VLAN – ID of the configured VLAN (1-4093). By default, all ports on
the stack are members of VLAN 1. However, the management station can be
attached to a port belonging to any VLAN, as long as that VLAN has been assigned
an IP address.
• IP Address Mode – Specifies whether IP functionality is enabled via manual
configuration (Static), Dynamic Host Configuration Protocol (DHCP), or Boot
Protocol (BOOTP). If DHCP/BOOTP is enabled, IP will not function until a reply has
been received from the server. Requests will be broadcast periodically by the
switch for an IP address. (DHCP/BOOTP values can include the IP address,
subnet mask, and default gateway.)
• IP Address – Address of the VLAN to which the management station is attached.
Valid IP addresses consist of four numbers, 0 to 255, separated by periods.
(Default: 0.0.0.0)
• Subnet Mask – This mask identifies the host address bits used for routing to
specific subnets. (Default: 255.0.0.0)
• Gateway IP Address – IP address of the gateway router between the stack and
management stations that exist on other network segments. (Default: 0.0.0.0)
• MAC Address – The physical layer address for this switch.
4
Manual Configuration
Web – Click System, System, IP Configuration. Select the VLAN through which the
management station is attached. Enter the IP address, subnet mask and gateway,
then click Apply.
Figure 4-7 IP Interface Configuration - Manual
4-9
Page 66

Basic Management Tasks
4
CLI – Specify the management interface, IP address and default gateway.
Console#config
Console(config)#interface vlan 1 24-1
Console(config-if)#ip address 10.1.0.253 255.255.255.0 35-1
Console(config-if)#exit
Console(config)#ip default-gateway 10.1.0.254 35-2
Console(config)#
Using DHCP/BOOTP
If your network provides DHCP/BOOTP services, you can configure the stack to be
dynamically configured by these services.
Web – Click System, IP Configuration. Specify the VLAN to which the management
station is attached, set the IP Address Mode to DHCP or BOOTP. Click Apply to
save your changes. Then click Restart DHCP to immediately request a new
address. Note that the stack will also broadcast a request for IP configuration
settings on each power reset.
Figure 4-8 IP Interface Configuration - DHCP
Note: If you lose your management connection, make a console connection to the
Master unit and enter “show ip interface” to determine the new stack address.
CLI – Specify the management interface, and set the IP address mode to DHCP or
BOOTP, and then enter the “ip dhcp restart” command.
Console#config
Console(config)#interface vlan 1 24-1
Console(config-if)#ip address dhcp 35-1
Console(config-if)#end
Console#ip dhcp restart 35-3
Console#show ip interface 35-4
IP Address and Netmask: 192.168.0.100 255.255.255.0 on VLAN 1,
Address Mode: DHCP
Console#
4-10
Page 67

Managing Firmware
Renewing DCHP – DHCP may lease addresses to clients indefinitely or for a
specific period of time. If the address expires or the stack is moved to another
network segment, you will lose management access to the stack. In this case, you
can reboot the stack or submit a client request to restart DHCP service via the CLI.
Web – If the address assigned by DHCP is no longer functioning, you will not be
able to renew the IP settings via the web interface. You can only restart DHCP
service via the web interface if the current address is still available.
CLI – Enter the following command to restart DHCP service.
Console#ip dhcp restart 35-3
Console#
4
Managing Firmware
You can upload/download firmware to or from a TFTP server, or copy files to and
from switch units in a stack. By saving runtime code to a file on a TFTP server, that
file can later be downloaded to the switch to restore operation. You can also set the
switch to use new firmware without overwriting the previous version. You must
specify the method of file transfer, along with the file type and file names as required.
Command Attributes
• File Transfer Method – The firmware copy operation includes these options:
- file to file – Copies a file within the switch directory, assigning it a new name.
- file to tftp – Copies a file from the switch to a TFTP server.
- tftp to file – Copies a file from a TFTP server to the switch.
• TFTP Server IP Address – The IP address of a TFTP server.
• File Type – Specify opcode (operational code) to copy firmware.
• File Name –
the file name should not be a period (.), and the maximum length for file names on
the TFTP server is 127 characters or 31 characters for files on the switch.
(Valid characters: A-Z, a-z, 0-9, “.”, “-”, “_”)
Note: Up to two copies of the system software (i.e., the runtime firmware) can be stored
in the file directory on the switch. The currently designated startup version of this
file cannot be deleted.
The file name should not contain slashes (\ or /),
the leading letter of
4-11
Page 68

Basic Management Tasks
4
Downloading System Software from a Server
When downloading runtime code, you can specify the destination file name to
replace the current image, or first download the file using a different name from the
current runtime code file, and then set the new file as the startup file.
Web – Click System, File Management, Copy Operation. Select “tftp to file” as the
file transfer method, enter the IP address of the TFTP server, set the file type to
“opcode,” enter the file name of the software to download, select a file on the switch
to overwrite or specify a new file name, then click Apply. If you replaced the current
firmware used for startup and want to start using the new operation code, reboot the
system via the System/Reset menu.
Figure 4-9 Copy Firmware
If you download to a new destination file, go to the File Management, Set Start-Up
menu, mark the operation code file used at startup, and click Apply. To start the new
firmware, reboot the system via the System/Reset menu.
Figure 4-10 Setting the Startup Code
4-12
Page 69

Managing Firmware
4
To delete a file select System, File Management, Delete. Select the file name from
the given list by checking the tick box and click Apply. Note that the file currently
designated as the startup code cannot be deleted.
Figure 4-11 Deleting Files
CLI – To download new firmware form a TFTP server, enter the IP address of the
TFTP server, select “config” as the file type, then enter the source and destination
file names. When the file has finished downloading, set the new file to start up the
system, and then restart the switch.
To start the new firmware, enter the “reload” command or reboot the system.
Console#copy tftp file 19-13
TFTP server ip address: 10.1.0.19
Choose file type:
1. config: 2. opcode: <1-2>: 2
Source file name: V1.0.0.28.bix
Destination file name: V10028
\Write to FLASH Programming.
-Write to FLASH finish.
Success.
Console#config
Console(config)#boot system opcode:V10028 19-17
Console(config)#exit
Console#reload 18-4
4-13
Page 70

Basic Management Tasks
4
Saving or Restoring Configuration Settings
You can upload/download configuration settings to/from a TFTP server, or copy files
to and from switch units in a stack. The configuration file can be later downloaded to
restore the switch’s settings.
Command Attributes
• File Transfer Method – The configuration copy operation includes these options:
- file to file – Copies a file within the switch directory, assigning it a new name.
- file to running-config – Copies a file in the switch to the running configuration.
- file to startup-config – Copies a file in the switch to the startup configuration.
- file to tftp – Copies a file from the switch to a TFTP server.
- running-config to file – Copies the running configuration to a file.
- running-config to startup-config – Copies the running config to the startup config.
- running-config to tftp – Copies the running configuration to a TFTP server.
- startup-config to file – Copies the startup configuration to a file on the switch.
- startup-config to running-config – Copies the startup config to the running config.
- startup-config to tftp – Copies the startup configuration to a TFTP server.
- tftp to file – Copies a file from a TFTP server to the switch.
- tftp to running-config – Copies a file from a TFTP server to the running config.
- tftp to startup-config – Copies a file from a TFTP server to the startup config.
• TFTP Server IP Address – The IP address of a TFTP server.
• File Type – Specify config (configuration) to copy configuration settings.
File Name
•
leading letter of the file name should not be a period (.), and the maximum length
for file names on the TFTP server is 127 characters or 31 characters for files on
the switch. (Valid characters: A-Z, a-z, 0-9, “.”, “-”, “_”)
Note:
— The configuration file name should not contain slashes (\ or /),
The maximum number of user-defined configuration files is limited only by
available flash memory space.
the
4-14
Page 71

Saving or Restoring Configuration Settings
4
Downloading Configuration Settings from a Server
You can download the configuration file under a new file name and then set it as the
startup file, or you can specify the current startup configuration file as the destination
file to directly replace it. Note that the file “Factory_Default_Config.cfg” can be
copied to the TFTP server, but cannot be used as the destination on the switch.
Web – Click System, File Management, Copy Operation. Choose “tftp to
startup-config” or “tftp to file,” and enter the IP address of the TFTP server. Specify
the name of the file to download, select a file on the switch to overwrite or specify a
new file name, and then click Apply.
Figure 4-12 Downloading Configuration Settings for Start-Up
If you download to a new file name using “tftp to startup-config” or “tftp to file,” the file
is automatically set as the start-up configuration file. To use the new settings, reboot
the system via the System/Reset menu. You can also select any configuration file as
the start-up configuration by using the System/File Management/Set Start-Up page.
Figure 4-13 Setting the Startup Configuration Settings
4-15
Page 72

Basic Management Tasks
4
CLI – Enter the IP address of the TFTP server, specify the source file on the server,
set the startup file name on the switch, and then restart the switch.
Console#copy tftp startup-config 19-13
TFTP server ip address: 192.168.1.19
Source configuration file name: config-1
Startup configuration file name [] : startup
\Write to FLASH Programming.
-Write to FLASH finish.
Success.
Console#reload
To select another configuration file as the start-up configuration, use the boot
system command and then restart the switch.
Console#config
Console(config)#boot system config: startup 19-17
Console(config)#exit
Console#reload 18-4
Console Port Settings
You can access the onboard configuration program by attaching a VT100
compatible device to the switch’s serial console port. Management access through
the console port is controlled by various parameters, including a password, timeouts,
and basic communication settings. These parameters can be configured via the web
or CLI interface.
Command Attributes
• Login Timeout – Sets the interval that the system waits for a user to log into the
CLI. If a login attempt is not detected within the timeout interval, the connection is
terminated for the session. (Range: 0 - 300 seconds; Default: 0)
• Exec Timeout – Sets the interval that the system waits until user input is detected.
If user input is not detected within the timeout interval, the current session is
terminated. (Range: 0 - 65535 seconds; Default: 0 seconds)
• Password Threshold – Sets the password intrusion threshold, which limits the
number of failed logon attempts. When the logon attempt threshold is reached, the
system interface becomes silent for a specified amount of time (set by the Silent
Time parameter) before allowing the next logon attempt. (Range: 0-120; Default: 3
attempts)
• Silent Time – Sets the amount of time the management console is inaccessible
after the number of unsuccessful logon attempts has been exceeded.
(Range: 0-65535; Default: 0)
• Data Bits – Sets the number of data bits per character that are interpreted and
generated by the console port. If parity is being generated, specify 7 data bits per
character. If no parity is required, specify 8 data bits per character. (Default: 8 bits)
4-16
Page 73

Console Port Settings
• Parity – Defines the generation of a parity bit. Communication protocols provided
by some terminals can require a specific parity bit setting. Specify Even, Odd, or
None. (Default: None)
• Speed – Sets the terminal line’s baud rate for transmit (to terminal) and receive
(from terminal). Set the speed to match the baud rate of the device connected to
the serial port. (Range: 9600, 19200, 38400, 57600, or 115200 baud, Auto;
Default: Auto)
• Stop Bits – Sets the number of the stop bits transmitted per byte.
(Range: 1-2; Default: 1 stop bit)
• Password
started on a line with password protection, the system prompts for the password.
If you enter the correct password, the system shows a prompt. (Default: No
password)
• Login
single global password as configured for the Password parameter, or by
passwords set up for specific user-name accounts. (Default: Local)
Web – Click System, Line, Console. Specify the console port connection parameters
as required, then click Apply.
1
– Specifies a password for the line connection. When a connection is
1
– Enables password checking at login. You can select authentication by a
4
1. CLI only.
Figure 4-14 Configuring the Console Port
4-17
Page 74

Basic Management Tasks
4
CLI – Enter Line Configuration mode for the console, then specify the connection
parameters as required. To display the current console port settings, use the show
line command from the Normal Exec level.
Console(config)#line console 19-19
Console(config-line)#login local 19-20
Console(config-line)#password 0 secret 19-21
Console(config-line)#timeout login response 0 19-22
Console(config-line)#exec-timeout 0 19-22
Console(config-line)#password-thresh 5 19-23
Console(config-line)#silent-time 60 19-24
Console(config-line)#databits 8 19-24
Console(config-line)#parity none 19-25
Console(config-line)#speed auto 19-25
Console(config-line)#stopbits 1 19-26
Console(config-line)#end
Console#show line console 19-27
Console configuration:
Password threshold: 5 times
Interactive timeout: Disabled
Login timeout: Disabled
Silent time: 60
Baudrate: auto
Databits: 8
Parity: none
Stopbits: 1
Console#
Telnet Settings
You can access the onboard configuration program over the network using Telnet
(i.e., a virtual terminal). Management access via Telnet can be enabled/disabled and
other various parameters set, including the TCP port number, timeouts, and a
password. These parameters can be configured via the web or CLI interface.
Command Attributes
• Telnet Status – Enables or disables Telnet access to the switch.
(Default: Enabled)
• Telnet Port Number – Sets the TCP port number for Telnet on the switch.
(Range: 1 - 65535; Default: 23)
• Login Timeout – Sets the interval that the system waits for a user to log into the
CLI. If a login attempt is not detected within the timeout interval, the connection is
terminated for the session. (Range: 0 - 300 seconds; Default: 300 seconds)
• Exec Timeout – Sets the interval that the system waits until user input is detected.
If user input is not detected within the timeout interval, the current session is
terminated. (Range: 0 - 65535 seconds; Default: 600 seconds)
• Password Threshold – Sets the password intrusion threshold, which limits the
number of failed logon attempts. When the logon attempt threshold is reached, the
system interface becomes silent for a specified amount of time (set by the Silent
Time parameter) before allowing the next logon attempt.
(Range: 0-120; Default: 3 attempts)
4-18
Page 75

Telnet Settings
4
• Password2 – Specifies a password for the line connection. When a connection is
started on a line with password protection, the system prompts for the password.
If you enter the correct password, the system shows a prompt. (Default: No
password)
• Login
2
– Enables password checking at login. You can select authentication by a
single global password as configured for the Password parameter, or by
passwords set up for specific user-name accounts. (Default: Local)
Web – Click System, Line, Telnet. Specify the connection parameters for Telnet
access, then click Apply.
Figure 4-15 Configuring the Telnet Interface
CLI – Enter Line Configuration mode for a virtual terminal, then specify the
connection parameters as required. To display the current virtual terminal settings,
use the show line command from the Normal Exec level.
Console(config)#line vty 19-19
Console(config-line)#login local 19-20
Console(config-line)#password 0 secret 19-21
Console(config-line)#timeout login response 300 19-22
Console(config-line)#exec-timeout 600 19-22
Console(config-line)#password-thresh 3 19-23
Console(config-line)#end
Console#show line vty 19-27
VTY configuration:
Password threshold: 3 times
Interactive timeout: 600 sec
Login timeout: 300 sec
Console#
2. CLI only.
4-19
Page 76

Basic Management Tasks
4
Configuring Event Logging
The switch allows you to control the logging of error messages, including the type of
events that are recorded in switch memory, logging to a remote System Log (syslog)
server, and displays a list of recent event messages.
System Log Configuration
The system allows you to enable or disable event logging, and specify which levels
are logged to RAM or flash memory.
Severe error messages that are logged to flash memory are permanently stored in
the switch to assist in troubleshooting network problems. Up to 4096 log entries can
be stored in the flash memory, with the oldest entries being overwritten first when the
available log memory (256 kilobytes) has been exceeded.
The System Logs page allows you to configure and limit system messages that are
logged to flash or RAM memory. The default is for event levels 0 to 3 to be logged to
flash and levels 0 to 7 to be logged to RAM.
Command Attributes
• System Log Status – Enables/disables the logging of debug or error messages to
the logging process. (Default: Enabled)
• Flash Level – Limits log messages saved to the switch’s permanent flash memory
for all levels up to the specified level. For example, if level 3 is specified, all
messages from level 0 to level 3 will be logged to flash. (Range: 0-7, Default: 3)
Table 4-1 Logging Levels
Level Severity Name Description
7 Debug Debugging messages
6 Informational Informational messages only
5 Notice Normal but significant condition, such as cold start
4 Warning Warning conditions (e.g., return false, unexpected return)
3 Error Error conditions (e.g., invalid input, default used)
2 Critical Critical conditions (e.g., memory allocation, or free memory
1 Alert Immediate action needed
0 Emergency System unusable
* There are only Level 2, 5 and 6 error messages for the current firmware release.
error - resource exhausted)
• RAM Level – Limits log messages saved to the switch’s temporary RAM memory
for all levels up to the specified level. For example, if level 7 is specified, all
messages from level 0 to level 7 will be logged to RAM. (Range: 0-7, Default: 7)
Note:
The Flash Level must be equal to or less than the RAM Level.
4-20
Page 77

Configuring Event Logging
4
Web – Click System, Logs, System Logs. Specify System Log Status, set
event messages to be logged to RAM and flash memory, then click Apply.
Figure 4-16 System Logs
CLI – Enable system logging and then specify the level of messages to be logged to
RAM and flash memory. Use the show logging command to display the current
settings.
Console(config)#logging on 19-28
Console(config)#logging history ram 0 19-29
Console(config)#
Console#show logging ram 19-32
Syslog logging: Disabled
History logging in RAM: level emergencies
Console#
the level of
Remote Log Configuration
The Remote Logs page allows you to configure the logging of messages that are
sent to syslog servers or other management stations. You can also limit the event
messages sent to only those messages at or above a specified level.
Command Attributes
• Remote Log Status – Enables/disables the logging of debug or error messages
to the remote logging process. (Default: Disabled)
• Logging Facility – Sets the facility type for remote logging of syslog messages.
There are eight facility types specified by values of 16 to 23. The facility type is
used by the syslog server to dispatch log messages to an appropriate service.
The attribute specifies the facility type tag sent in syslog messages. (See RFC
3164.) This type has no effect on the kind of messages reported by the switch.
However, it may be used by the syslog server to process messages, such as sorting
or storing messages in the corresponding database. (Range: 16-23, Default: 23)
• Logging Trap – Limits log messages that are sent to the remote syslog server for
all levels up to the specified level. For example, if level 3 is specified, all messages
from level 0 to level 3 will be sent to the remote server. (Range: 0-7, Default: 7)
• Host IP List – Displays the list of remote server IP addresses that will receive
syslog messages. The maximum number of host IP addresses allowed is five.
• Host IP Address – Specifies a new server IP address to add to the Host IP List.
4-21
Page 78

Basic Management Tasks
4
Web – Click System, Logs, Remote Logs. To add an IP address to the Host IP List,
type the new IP address in the Host IP Address box, and then click Add. To delete
an IP address, click the entry in the Host IP List, and then click Remove.
Figure 4-17 Remote Logs
CLI – Enter the syslog server host IP address, choose the facility type and set the
logging trap.
Console(config)#logging host 10.1.0.9 19-30
Console(config)#logging facility 23 19-30
Console(config)#logging trap 4 19-31
Console(config)#logging trap
Console(config)#exit
Console#show logging trap 19-32
Syslog logging: Enabled
REMOTELOG status: Disabled
REMOTELOG facility type: local use 7
REMOTELOG level type: Warning conditions
REMOTELOG server ip address: 10.1.0.9
REMOTELOG server ip address: 0.0.0.0
REMOTELOG server ip address: 0.0.0.0
REMOTELOG server ip address: 0.0.0.0
REMOTELOG server ip address: 0.0.0.0
Console#
4-22
Page 79

Configuring Event Logging
4
Displaying Log Messages
Use the Logs page to scroll through the logged system and event messages. The
switch can store up to 2048 log entries in temporary random access memory (RAM;
i.e., memory flushed on power reset) and up to 4096 entries in permanent flash
memory.
Web – Click System, Log, Logs.
Figure 4-18 Displaying Logs
CLI – This example shows the event message stored in RAM.
Console#show log ram 19-32
[1] 00:01:30 2001-01-01
"VLAN 1 link-up notification."
level: 6, module: 5, function: 1, and event no.: 1
[0] 00:01:30 2001-01-01
"Unit 1, Port 1 link-up notification."
level: 6, module: 5, function: 1, and event no.: 1
Console#
Sending Simple Mail Transfer Protocol Alerts
To alert system administrators of problems, the switch can use SMTP (Simple Mail
Transfer Protocol) to send email messages when triggered by logging events of a
specified level. The messages are sent to specified SMTP servers on the network
and can be retrieved using POP or IMAP clients.
Command Attributes
• Admin Status – Enables/disables the SMTP function. (Default: Enabled)
• Email Source Address – Sets the email address used for the “From” field in alert
messages. You may use a symbolic email address that identifies the switch, or the
address of an administrator responsible for the switch.
• Severity – Sets the syslog severity threshold level (see table on page 4-20) used
to trigger alert messages. All events at this level or higher will be sent to the
configured email recipients. For example, using Level 7 will report all events from
level 7 to level 0. (Default: Level 7)
4-23
Page 80

Basic Management Tasks
4
• SMTP Server List – Specifies a list of up to three recipient SMTP servers. The
switch attempts to connect to the other listed servers if the first fails. Use the New
SMTP Server text field and the Add/Remove buttons to configure the list.
• Email Destination Address List – Specifies the email recipients of alert
messages. You can specify up to five recipients. Use the New Email Destination
Address text field and the Add/Remove buttons to configure the list.
Web – Click System, Log, SMTP. Enable SMTP, specify a source email address,
and select the minimum severity level. To add an IP address to the SMTP Server
List, type the new IP address in the SMTP Server field and click Add. To delete an IP
address, click the entry in the SMTP Server List and click Remove. Specify up to five
email addresses to receive the alert messages, and click Apply.
4-24
Figure 4-19 Enabling and Configuring SMTP Alerts
Page 81

Resetting the System
4
CLI – Enter the IP address of at least one SMTP server, set the syslog severity level
to trigger an email message, and specify the switch (source) and up to five recipient
(destination) email addresses. Enable SMTP with the logging sendmail command
to complete the configuration. Use the show logging sendmail command to display
the current SMTP configuration.
Console(config)#logging sendmail host 192.168.1.4 19-34
Console(config)#logging sendmail level 3 19-35
Console(config)#logging sendmail source-email
big-wheels@matel.com 19-35
Console(config)#logging sendmail destination-email
chris@matel.com 19-36
Console(config)#logging sendmail 19-36
Console(config)#exit
Console#show logging sendmail 19-37
SMTP servers
-----------------------------------------------
1. 192.168.1.4
SMTP minimum severity level: 4
SMTP destination email addresses
-----------------------------------------------
1. chris@matel.com
SMTP source email address: big-wheels@matel.com
SMTP status: Enabled
Console#
Resetting the System
Web – Click System, Reset. Click the Reset button to restart the switch. When
prompted, confirm that you want reset the switch.
Figure 4-20 Resetting the System
CLI – Use the reload command to restart the switch.
Console#reload 18-4
System will be restarted, continue <y/n>?
When restarting the system, it will always run the Power-On Self-Test.
Note:
4-25
Page 82

Basic Management Tasks
4
Setting the System Clock
Simple Network Time Protocol (SNTP) allows the switch to set its internal clock
based on periodic updates from a time server (SNTP or NTP). Maintaining an
accurate time on the switch enables the system log to record meaningful dates and
times for event entries. You can also manually set the clock using the CLI. (See
“calendar set” on page 19-41.) If the clock is not set, the switch will only record the
time from the factory default set at the last bootup.
When the SNTP client is enabled, the switch periodically sends a request for a time
update to a configured time server. You can configure up to three time server IP
addresses. The switch will attempt to poll each server in the configured sequence.
Configuring SNTP
You can configure the switch to send time synchronization requests to time servers.
Command Attributes
• SNTP Client – Configures the switch to operate as an SNTP client. This requires
at least one time server to be specified in the SNTP Server field. (Default: Disabled)
• SNTP Poll Interval – Sets the interval between sending requests for a time update
from a time server. (Range: 16-16384 seconds; Default: 16 seconds)
• SNTP Server – Sets the IP address for up to three time servers. The switch
attempts to update the time from the first server, if this fails it attempts an update
from the next server in the sequence.
Web – Select SNTP, Configuration. Modify any of the required parameters, and click
Apply.
4-26
Figure 4-21 SNTP Configuration
Page 83

Setting the System Clock
4
CLI – This example configures the switch to operate as an SNTP client and then
displays the current time and settings.
Console(config)#sntp client 19-38
Console(config)#sntp poll 16 19-39
Console(config)#sntp server 10.1.0.19 137.82.140.80 128.250.36.2 19-39
Console(config)#exit
Console#show sntp 19-40
Current time: Jan 6 14:56:05 2004
Poll interval: 60
Current mode: unicast
SNTP status : Enabled
SNTP server 10.1.0.19 137.82.140.80 128.250.36.2
Current server: 128.250.36.2
Console#
Setting the Time Zone
SNTP uses Coordinated Universal Time (or UTC, formerly Greenwich Mean Time,
or GMT) based on the time at the Earth’s prime meridian, zero degrees longitude. To
display a time corresponding to your local time, you must indicate the number of
hours and minutes your time zone is east (before) or west (after) of UTC.
Command Attributes
• Current Time – Displays the current time.
• Name – Assigns a name to the time zone. (Range: 1-29 characters)
• Hours (0-13) – The number of hours before/after UTC.
• Minutes (0-59) – The number of minutes before/after UTC.
• Direction – Configures the time zone to be before (east) or after (west) UTC.
Web – Select SNTP, Clock Time Zone. Set the offset for your time zone relative to
the UTC, and click Apply.
Figure 4-22 Clock Time Zone
CLI - This example shows how to set the time zone for the system clock.
Console(config)#clock timezone Dhaka hours 6 minute 0 after-UTC 19-40
Console#
4-27
Page 84

Basic Management Tasks
4
4-28
Page 85

Chapter 5:
Simple Network Management Protocol (SNMP) is a communication protocol
designed specifically for managing devices on a network. Equipment commonly
managed with SNMP includes switches, routers and host computers. SNMP is
typically used to configure these devices for proper operation in a network
environment, as well as to monitor them to evaluate performance or detect potential
problems.
Managed devices supporting SNMP contain software, which runs locally on the
device and is referred to as an agent. A defined set of variables, known as managed
objects, is maintained by the SNMP agent and used to manage the device. These
objects are defined in a Management Information Base (MIB) that provides a
standard presentation of the information controlled by the agent. SNMP defines both
the format of the MIB specifications and the protocol used to access this information
over the network.
The switch includes an onboard agent that supports SNMP versions 1, 2c, and 3.
This agent continuously monitors the status of the switch hardware, as well as the
traffic passing through its ports. A network management station can access this
information using software such as HP OpenView. Access to the onboard agent
from clients using SNMP v1 and v2c is controlled by community strings. To
communicate with the switch, the management station must first submit a valid
community string for authentication.
Access to the switch using from clients using SNMPv3 provides additional security
features that cover message integrity, authentication, and encryption; as well as
controlling user access to specific areas of the MIB tree.
The SNMPv3 security structure consists of security models, with each model having
it’s own security levels. There are three security models defined, SNMPv1,
SNMPv2c, and SNMPv3. Users are assigned to “groups” that are defined by a
security model and specified security levels. Each group also has a defined security
access to set of MIB objects for reading and writing, which are known as “views.”
The switch has a default view (all MIB objects) and default groups defined for
security models v1 and v2c. The following table shows the security models and
levels available and the system default settings.
Simple Network Management Protocol
5-1
Page 86

Simple Network Management Protocol
5
Table 5-1 SNMPv3 Security Models and Levels
Model Level Group Read View Write View Notify View Security
v1 noAuthNoPriv public
(read only)
v1 noAuthNoPriv private
(read/write)
v1 noAuthNoPriv user defined user defined user defined user defined Community string only
v2c noAuthNoPriv public
(read only)
v2c noAuthNoPriv private
(read/write)
v2c noAuthNoPriv user defined user defined user defined user defined Community string only
v3 noAuthNoPriv user defined user defined user defined user defined A user name match only
v3 AuthNoPriv user defined user defined user defined user defined Provides user
v3 AuthPriv user defined user defined user defined user defined Provides user
defaultview none none Community string only
defaultview defaultview none Community string only
defaultview none none Community string only
defaultview defaultview none Community string only
authentication via MD5 or
SHA algorithms
authentication via MD5 or
SHA algorithms and data
privacy using DES 56-bit
encryption
Note: The predefined default groups and view can be deleted from the system. You can
then define customized groups and views for the SNMP clients that require access.
Enabling the SNMP Agent
Enables SNMPv3 service for all management clients (i.e., versions 1, 2c, 3).
Command Attributes
SNMP Agent Status – Enables SNMP on the switch.
Web – Click SNMP, Agent Status. Enable the SNMP Agent by marking the Enabled
checkbox, and click Apply.
Figure 5-1 Enabling the SNMP Agent
CLI – The following example enables SNMP on the switch.
Console(config)#snmp-server 20-2
Console(config)#
5-2
Page 87

Setting Community Access Strings
5
Setting Community Access Strings
You may configure up to five community strings authorized for management access
by clients using SNMP v1 and v2c. All community strings used for IP Trap Managers
should be listed in this table. For security reasons, you should consider removing the
default strings.
Command Attributes
• SNMP Community Capability – The switch supports up to five community strings.
• Current – Displays a list of the community strings currently configured.
• Community String – A community string that acts like a password and permits
access to the SNMP protocol.
Default strings: “public” (read-only access), “private” (read/write access)
Range: 1-32 characters, case sensitive
• Access Mode – Specifies the access rights for the community string:
- Read-Only – Authorized management stations are only able to retrieve MIB
objects.
- Read/Write – Authorized management stations are able to both retrieve and
modify MIB objects.
Web – Click SNMP, Configuration. Add new community strings as required, select
the access rights from the Access Mode drop-down list, then click Add.
Figure 5-2 Configuring SNMP Community Strings
CLI – The following example adds the string “spiderman” with read/write access.
Console(config)#snmp-server community spiderman rw 20-3
Console(config)#
5-3
Page 88

Simple Network Management Protocol
5
Specifying Trap Managers and Trap Types
Traps indicating status changes are issued by the switch to specified trap managers.
You must specify trap managers so that key events are reported by this switch to
your management station (using network management platforms such as HP
OpenView). You can specify up to five management stations that will receive
authentication failure messages and other trap messages from the switch.
Command Usage
• If you specify an SNMP Version 3 host, then the “Trap Manager Community String”
is interpreted as an SNMP user name. If you use V3 authentication or encryption
options (authNoPriv or authPriv), the user name must first be defined in the
SNMPv3 Users page (page 5-9). Otherwise, the authentication password and/or
privacy password will not exist, and the switch will not authorize SNMP access for
the host. However, if you specify a V3 host with the no authentication (noAuth)
option, an SNMP user account will be automatically generated, and the switch will
authorize SNMP access for the host.
• Notifications are issued by the switch as trap messages by default. The recipient
of a trap message does not send a response to the switch. Traps are therefore not
as reliable as inform messages, which include a request for acknowledgement of
receipt. Informs can be used to ensure that critical information is received by the
host. However, note that informs consume more system resources because they
must be kept in memory until a response is received. Informs also add to network
traffic. You should consider these effects when deciding whether to issue
notifications as traps or informs.
To send an inform to a SNMPv2c host, complete these steps:
1. Enable the SNMP agent (page 5-2).
2. Enable trap informs as described in the following pages.
3. Create a view with the required notification messages (page 5-16).
4. Create a group that includes the required notify view (page 5-13).
To send an inform to a SNMPv3 host, complete these steps:
1. Enable the SNMP agent (page 5-2).
2. Enable trap informs as described in the following pages.
3. Create a view with the required notification messages (page 5-16).
4. Create a group that includes the required notify view (page 5-13).
5. Specify a remote engine ID where the user resides (page 5-8).
6. Then configure a remote user (page 5-11).
Command Attributes
• Trap Manager Capability – This switch supports up to five trap managers.
• Current – Displays a list of the trap managers currently configured.
• Trap Manager IP Address – IP address of a new management station to receive
notification messages.
• Trap Manager Community String – Specifies a valid community string for the
new trap manager entry. Though you can set this string in the Trap Managers table,
we recommend that you define this string in the SNMP Configuration page (for
5-4
Page 89

Specifying Trap Managers and Trap Types
Version 1 or 2c clients), or define a corresponding “User Name” in the SNMPv3
Users page (for Version 3 clients). (Range: 1-32 characters, case sensitive)
• Trap UDP Port – Specifies the UDP port number used by the trap manager.
• Trap Version – Indicates if the user is running SNMP v1, v2c, or v3. (Default: v1)
• Trap Security Level – When trap version 3 is selected, you must specify one of
the following security levels. (Default: noAuthNoPriv)
- noAuthNoPriv – There is no authentication or encryption used in SNMP
communications.
- AuthNoPriv – SNMP communications use authentication, but the data is not
encrypted (only available for the SNMPv3 security model).
- AuthPriv – SNMP communications use both authentication and encryption (only
available for the SNMPv3 security model).
• Trap Inform – Notifications are sent as inform messages. Note that this option is
only available for version 2c and 3 hosts. (Default: traps are used)
- Timeout – The number of seconds to wait for an acknowledgment before
resending an inform message. (Range: 0-2147483647 centiseconds;
Default: 1500 centiseconds)
- Retry times – The maximum number of times to resend an inform message if
the recipient does not acknowledge receipt. (Range: 0-255; Default: 3)
• Enable Authentication Traps
trap managers whenever authentication of an SNMP request fails.
(Default: Enabled)
• Enable Link-up and Link-down Traps
whenever a port link is established or broken. (Default: Enabled)
3
– Issues a notification message to specified IP
3
– Issues a notification message
5
3. These are legacy notifications and therefore when used for SNMP Version 3 hosts, they must
be enabled in conjunction with the corresponding ent ries in the Notification View (page 5-13).
5-5
Page 90

Simple Network Management Protocol
5
Web – Click SNMP, Configuration. Enter the IP address and community string for
each management station that will receive trap messages, specify the UDP port,
SNMP trap version, trap security level (for v3 clients), trap inform settings (for v2c/v3
clients), and then click Add. Select the trap types required using the check boxes for
Authentication and Link-up/down traps, and then click Apply.
Figure 5-3 Configuring SNMP Trap Managers
CLI – This example adds a trap manager and enables authentication traps.
Console(config)#snmp-server host 10.1.19.23 private version 2c
udp-port 162 20-5
Console(config)#snmp-server enable traps authentication 20-7
5-6
Page 91

Configuring SNMPv3 Management Access
5
Configuring SNMPv3 Management Access
To configure SNMPv3 management access to the switch, follow these steps:
1. If you want to change the default engine ID, do so before configuring other
SNMP parameters.
2. Specify read and write access views for the switch MIB tree.
3. Configure SNMP user groups with the required security model (i.e., SNMP v1,
v2c or v3) and security level (i.e., authentication and privacy).
4. Assign SNMP users to groups, along with their specific authentication and
privacy passwords.
Setting a Local Engine ID
An SNMPv3 engine is an independent SNMP agent that resides on the switch. This
engine protects against message replay, delay, and redirection. The engine ID is
also used in combination with user passwords to generate the security keys for
authenticating and encrypting SNMPv3 packets.
A local engine ID is automatically generated that is unique to the switch. This is
referred to as the default engine ID. If the local engineID is deleted or changed, all
SNMP users will be cleared. You will need to reconfigure all existing users.
A new engine ID can be specified by entering 10 to 64 hexadecimal characters. If
less than 64 characters are specified, trailing zeroes are added to the value. For
example, the value “0123456789” is equivalent to “0123456789” followed by 54
zeroes.
Web – Click SNMP, SNMPv3, Engine ID. Enter an ID of up to 64 hexadecimal
characters and then click Save.
Figure 5-4 Setting the SNMPv3 Engine ID
CLI – This example sets an SNMPv3 engine ID.
Console(config)#snmp-server engine-id local 12345abcdef 20-8
Console(config)#exit
Console#show snmp engine-id 20-9
Local SNMP engineID: 8000002a8000000000e8666672
Local SNMP engineBoots: 1
Console#
5-7
Page 92

Simple Network Management Protocol
5
Specifying a Remote Engine ID
To send inform messages to an SNMPv3 user on a remote device, you must first
specify the engine identifier for the SNMP agent on the remote device where the
user resides. The remote engine ID is used to compute the security digest for
authenticating and encrypting packets sent to a user on the remote host.
SNMP passwords are localized using the engine ID of the authoritative agent. For
informs, the authoritative SNMP agent is the remote agent. You therefore need to
configure the remote agent’s SNMP engine ID before you can send proxy requests
or informs to it. (See “Specifying Trap Managers and Trap Types” on page 5-4 and
“Configuring Remote SNMPv3 Users” on page 5-11.)
The engine ID can be specified by entering 10 to 64 hexadecimal characters. If less
than 64 characters are specified, trailing zeroes are added to the value.
the value “0123456789” is equivalent to “0123456789” followed by 54 zeroes.
Web – Click SNMP, SNMPv3, Remote Engine ID. Enter an ID of up to 64
hexadecimal characters and then click Save.
Figure 5-5 Setting an Engine ID
For example,
CLI – This example specifies a remote SNMPv3 engine ID.
Console(config)#snmp-server engine-id remote 54321 192.168.1.19 20-8
Console(config)#exit
Console#show snmp engine-id 20-9
Local SNMP engineID: 8000002a8000000000e8666672
Local SNMP engineBoots: 1
Remote SNMP engineID IP address
80000000030004e2b316c54321 192.168.1.19
Console#
5-8
Page 93

Configuring SNMPv3 Management Access
5
Configuring SNMPv3 Users
Each SNMPv3 user is defined by a unique name. Users must be configured with a
specific security level and assigned to a group. The SNMPv3 group restricts users to
a specific read, write, or notify view.
Command Attributes
• User Name – The name of user connecting to the SNMP agent. (Range: 1-32
characters)
• Group Name – The name of the SNMP group to which the user is assigned.
(Range: 1-32 characters)
• Security Model – The user security model; SNMP v1, v2c or v3.
• Security Level – The security level used for the user:
- noAuthNoPriv – There is no authentication or encryption used in SNMP
communications. (This is the default for SNMPv3.)
- AuthNoPriv – SNMP communications use authentication, but the data is not
encrypted (only available for the SNMPv3 security model).
- AuthPriv – SNMP communications use both authentication and encryption (only
available for the SNMPv3 security model).
• Authentication Protocol – The method used for user authentication. (Options:
MD5, SHA; Default: MD5)
• Authentication Password – A minimum of eight plain text characters is required.
• Privacy Protocol – The encryption algorithm use for data privacy; only 56-bit DES
is currently available.
• Privacy Password – A minimum of eight plain text characters is required.
• Actions – Enables the user to be assigned to another SNMPv3 group.
5-9
Page 94

Simple Network Management Protocol
5
Web – Click SNMP, SNMPv3, Users. Click New to configure a user name. In the
New User page, define a name and assign it to a group, then click Add to save the
configuration and return to the User Name list. To delete a user, check the box next
to the user name, then click Delete. To change the assigned group of a user, click
Change Group in the Actions column of the users table and select the new group.
Figure 5-6 Configuring SNMPv3 Users
CLI – Use the snmp-server user command to configure a new user name and
assign it to a group.
Console(config)#snmp-server user chris group r&d v3 auth md5
greenpeace priv des56 einstien 20-14
Console(config)#exit
Console#show snmp user 20-15
EngineId: 80000034030001f488f5200000
User Name: chris
Authentication Protocol: md5
Privacy Protocol: des56
Storage Type: nonvolatile
Row Status: active
Console#
5-10
Page 95

Configuring SNMPv3 Management Access
5
Configuring Remote SNMPv3 Users
Each SNMPv3 user is defined by a unique name. Users must be configured with a
specific security level and assigned to a group. The SNMPv3 group restricts users to
a specific read and a write view.
To send inform messages to an SNMPv3 user on a remote device, you must first
specify the engine identifier for the SNMP agent on the remote device where the
user resides. The remote engine ID is used to compute the security digest for
authenticating and encrypting packets sent to a user on the remote host. (See
“Specifying Trap Managers and Trap Types” on page 5-4 and “Specifying a Remote
Engine ID” on page 5-8.)
Command Attributes
• User Name – The name of user connecting to the SNMP agent. (Range: 1-32
characters)
• Group Name – The name of the SNMP group to which the user is assigned.
(Range: 1-32 characters)
• Engine ID – The engine identifier for the SNMP agent on the remote device where
the remote user resides. Note that the remote engine identifier must be specified
before you configure a remote user. (See “Specifying a Remote Engine ID” on
page 5-8.)
• Remote IP – The Internet address of the remote device where the user resides.
• Security Model – The user security model; SNMP v1, v2c or v3. (Default: v1)
• Security Level – The security level used for the user:
- noAuthNoPriv – There is no authentication or encryption used in SNMP
communications. (This is the default for SNMPv3.)
- AuthNoPriv – SNMP communications use authentication, but the data is not
encrypted (only available for the SNMPv3 security model).
- AuthPriv – SNMP communications use both authentication and encryption (only
available for the SNMPv3 security model).
• Authentication Protocol – The method used for user authentication.
(Options: MD5, SHA; Default: MD5)
• Authentication Password – A minimum of eight plain text characters is required.
• Privacy Protocol – The encryption algorithm use for data privacy; only 56-bit DES
is currently available.
• Privacy Password – A minimum of eight plain text characters is required.
5-11
Page 96

Simple Network Management Protocol
5
Web – Click SNMP, SNMPv3, Remote Users. Click New to configure a user name.
In the New User page, define a name and assign it to a group, then click Add to save
the configuration and return to the User Name list. To delete a user, check the box
next to the user name, then click Delete.
Figure 5-7 Configuring Remote SNMPv3 Users
CLI – Use the snmp-server user command to configure a new user name and
assign it to a group.
Console(config)#snmp-server user mark group r&d remote 192.168.1.19 v3
auth md5 greenpeace priv des56 einstien 20-14
Console(config)#exit
Console#show snmp user 20-15
No user exist.
SNMP remote user
EngineId: 80000000030004e2b316c54321
User Name: mark
Authentication Protocol: none
Privacy Protocol: none
Storage Type: nonvolatile
Row Status: active
Console#
5-12
Page 97

Configuring SNMPv3 Management Access
5
Configuring SNMPv3 Groups
An SNMPv3 group sets the access policy for its assigned users, restricting them to
specific read, write, and notify views. You can use the pre-defined default groups or
create new groups to map a set of SNMP users to SNMP views.
Command Attributes
• Group Name – The name of the SNMP group. (Range: 1-32 characters)
• Model – The group security model; SNMP v1, v2c or v3.
• Level – The security level used for the group:
- noAuthNoPriv – There is no authentication or encryption used in SNMP
communications.
- AuthNoPriv – SNMP communications use authentication, but the data is not
encrypted (only available for the SNMPv3 security model).
- AuthPriv – SNMP communications use both authentication and encryption (only
available for the SNMPv3 security model).
• Read View – The configured view for read access. (Range: 1-64 characters)
• Write View – The configured view for write access. (Range: 1-64 characters)
• Notify View – The configured view for notifications. (Range: 1-64 characters)
Table 5-2 Supported Notification Messages
Object Label Object ID Description
RFC 1493 Traps
newRoot 1.3.6.1.2.1.17.0.1 The newRoot trap indicates that the sending
topologyChange 1.3.6.1.2.1.17.0.2 A topologyChange trap is sent by a bridge when
SNMPv2 Traps
coldStart 1.3.6.1.6.3.1.1.5.1 A coldStart trap signifies that the SNMPv2 entity,
warmStart 1.3.6.1.6.3.1.1.5.2 A warmStart trap signifies that the SNMPv2
linkDown
*
1.3.6.1.6.3.1.1.5.3 A linkDown trap signifies that the SNMP entity,
agent has become the new root of the Spanning
Tree; the trap is sent by a bridge soon after its
election as the new root, e.g., upon expiration of
the Topology Change Timer immediately
subsequent to its election.
any of its configured ports transitions from the
Learning state to the Forwarding state, or from
the Forwarding state to the Discarding state. The
trap is not sent if a newRoot trap is sent for the
same transition.
acting in an agent role, is reinitializing itself and
that its configuration may have been altered.
entity, acting in an agent role, is reinitializing
itself such that its configuration is unaltered.
acting in an agent role, has detected that the
ifOperStatus object for one of its communication
links is about to enter the down state from some
other state (but not from the notPresent state).
This other state is indicated by the included
value of ifOperStatus.
5-13
Page 98

Simple Network Management Protocol
5
Table 5-2 Supported Notification Messages (Continued)
Object Label Object ID Description
*
linkUp
authenticationFailure
RMON Events (V2)
risingAlarm 1.3.6.1.2.1.16.0.1 The SNMP trap that is generated when an alarm
fallingAlarm 1.3.6.1.2.1.16.0.2 The SNMP trap that is generated when an alarm
Private Traps -
swPowerStatus
ChangeTrap
swFanFailureTrap 1.3.6.1.4.1.259.8.2.2.2.1.0.17 This trap is sent when the fan fails.
swFanRecoverTrap 1.3.6.1.4.1.259.8.2.2.2.1.0.18 This trap is sent when the fan failure has
swIpFilterRejectTrap 1.3.6.1.4.1.259.8.2.2.2.1.0.40 This trap is sent when an incorrect IP address is
swSmtpConnFailure
Trap
swMainBoardVer
MismatchNotificaiton
swModuleVer
MismatchNotificaiton
swThermalRising
Notification
1.3.6.1.6.3.1.1.5.4 A linkUp trap signifies that the SNMP entity,
*
1.3.6.1.6.3.1.1.5.5 An authenticationFailure trap signifies that the
1.3.6.1.4.1.259.8.2.2.2.1.0.1
1.3.6.1.4.1.259.8.2.2.2.1.0.41 This trap is triggered if the SMTP system cannot
1.3.6.1.4.1.259.8.2.2.2.1.0.56 This trap is sent when the slave board version is
1.3.6.1.4.1.259.8.2.2.2.1.0.57 This trap is sent when the slide-in module
1.3.6.1.4.1.259.8.2.2.2.1.0.58 This trap is sent when the temperature exceeds
acting in an agent role, has detected that the
ifOperStatus object for one of its communication
links left the down state and transitioned into
some other state (but not into the notPresent
state). This other state is indicated by the
included value of ifOperStatus.
SNMPv2 entity, acting in an agent role, has
received a protocol message that is not properly
authenticated. While all implementations of the
SNMPv2 must be capable of generating this
trap, the snmpEnableAuthenTraps object
indicates whether this trap will be generated.
entry crosses its rising threshold and generates
an event that is configured for sending SNMP
traps.
entry crosses its falling threshold and generates
an event that is configured for sending SNMP
traps.
†
This trap is sent when the power state changes.
recovered.
rejected by the IP Filter.
open a connection to the mail server
successfully.
mismatched with the master board version. This
trap binds two objects, the first object indicates
the master version, whereas the second
represents the slave version.
version is mismatched with the main board
version.
the switchThermalActionRisingThreshold.
5-14
Page 99

Configuring SNMPv3 Management Access
Table 5-2 Supported Notification Messages (Continued)
Object Label Object ID Description
swThermalFalling
Notification
swModuleInsertion
Notificaiton
swModuleRemoval
Notificaiton
* These are legacy notifications and therefore must be enabled in conjunction with the corresponding traps on the
SNMP Configuration menu (page 5-6).
†The MIB OID for ES3528 is 1.3.6.1.4.1.259.8.2.2, and for ES3528-WDM is 1.3.6.1.4.1.259.8.2.3.
Web – Click SNMP, SNMPv3, Groups. Click New to configure a new group. In the
New Group page, define a name, assign a security model and level, and then select
read, write, and notify views. Click Add to save the new group and return to the
Groups list. To delete a group, check the box next to the group name, then click
Delete.
1.3.6.1.4.1.259.8.2 .2.2.1.0.59 This trap is sent when the temperature falls be low
the switchThermalActionFallingThreshold.
1.3.6.1.4.1.259.8.2.2.2.1.0.60 This trap is sent when a module is inserted.
1.3.6.1.4.1.259.8.2.2.2.1.0.61 This trap is sent when a module is removed.
5
Figure 5-8 Configuring SNMPv3 Groups
5-15
Page 100

Simple Network Management Protocol
5
CLI – Use the snmp-server group command to configure a new group, specifying
the security model and level, and restricting MIB access to defined read and write
views.
Console(config)#snmp-server group secure-users v3 priv read defaultview
write defaultview notify defaultview 20-11
Console(config)#exit
Console#show snmp group 20-12
.
.
.
Group Name: secure-users
Security Model: v3
Read View: defaultview
Write View: defaultview
Notify View: defaultview
Storage Type: nonvolatile
Row Status: active
Console#
Setting SNMPv3 Views
SNMPv3 views are used to restrict user access to specified portions of the MIB tree.
The predefined view “defaultview” includes access to the entire MIB tree.
Command Attributes
• View Name – The name of the SNMP view. (Range: 1-64 characters)
• View OID Subtrees – Shows the currently configured object identifiers of branches
within the MIB tree that define the SNMP view.
• Edit OID Subtrees – Allows you to configure the object identifiers of branches
within the MIB tree. Wild cards can be used to mask a specific portion of the OID
string.
• Type – Indicates if the object identifier of a branch within the MIB tree is included
or excluded from the SNMP view.
5-16
 Loading...
Loading...