Page 1

ConnectPort® X5 Family
User’s Guide
ConnectPort X5 R
ConnectPort X5 Kit
ConnectPort X5 R CDMA
ConnectPort X5 R CDMA Kit
ConnectPort X5 R Iridium
ConnectPort X5 R Iridium Kit
ConnectPort X5 Fleet
®
90001100_H
Page 2

©Digi International Inc. 2013. All Rights Reserved.
The Digi logo, Digi Connect, Device Cloud, ConnectPort, Digi SureLink, Digi Dialserv, Etherios,
the Etherios logo, the Etherios website, Device Cloud by Etherios, Dev ice Manager, DIA,
RealPort, and XBee are trademarks or registered trademarks of Digi International, Inc.
All other trademarks mentioned in this document are the property of their respective owners.
Information in this document is subject to change without notice and does not represent a
commitment on the part of Digi International.
Digi provides this document “as is,” without warranty of any kind, either expressed or implied,
including, but not limited to, the implied warranties of fitness or merchantability for a particular
purpose. Digi may make improvements and/or changes in this manual or in the product(s) and/or
the program(s) described in this manual at any time.
This product could include technical inaccuracies or typographical errors. Changes are periodically
made to the information herein; these changes may be incorporated in new editions of the
publication.
2
Page 3

Contents
Contents
Contents..............................................................................................................................................................................3
About this guide.................................................................................................................................................................7
Purpose.......................................................................................................................................................................7
Audience.....................................................................................................................................................................7
Scope..........................................................................................................................................................................7
Where to find more information.................................................................................................................................7
Digi contact information ............................................................................................................................................8
Chapter 1: Introduction...........................................................................................................................................................9
Important Safety Information . ....................................................................................................................................9
ConnectPort® X5 Family products..........................................................................................................................10
Features ....................................................................................................................................................................12
User interfaces................................................................................................................................................12
Configurable network services.......................................................................................................................12
IP protocol support .........................................................................................................................................13
Mobile/Cellular features and protocol support...............................................................................................17
RealPort software............................................................................................................................................18
Alarms.............................................................................................................................................................19
Modem emulation...........................................................................................................................................19
Security features in Digi devices....................................................................................................................20
Configuration management .......................................................................... ..................................................21
Customization capabilities..............................................................................................................................21
Supported connections and data paths in Digi devices............................................................................................22
Network services ............................................................................................................................................22
Network/serial clients........................ .... ............................................... .... .... ..................................................24
Interfaces for configuring, monitoring, and administering Digi devices.................................................................25
Configuration capabilities...............................................................................................................................25
Configuration interfaces ............................................................... .... ..............................................................26
Device Manager™ interface...........................................................................................................................28
Monitoring capabilities and interfaces............................................................................................................34
Device administration.....................................................................................................................................35
Chapter 2: Hardware .............................................................................................................................................................36
ConnectPort X5 R and ConnectPort X5 Kit hardware summary.............................................................................37
ConnectPort X5 R models............................................ .... ............................................... ...............................38
ConnectPort X5 development kit models.......................................................................................................38
ConnectPort X5 Fleet hardware summary...............................................................................................................39
3
Page 4

Contents
Interfaces and Wiring Harness guidelines................................................................................................................40
ConnectPort X5 Wiring Harness Connector................................................. ..................................................41
Available interfaces on the Wiring Harness...................................................................................................44
Antennas...................................................................................................................................................................47
ConnectPort X5 R antennas..................................................................................... .......................................47
ConnectPort X5 R CDMA antennas...............................................................................................................48
ConnectPort X5 Iridium antennas ..................................................................................................................49
ConnectPort X5 Fleet antennas ......................................................................................................................49
Certified antennas and specifications.............................................................................................................50
SIM card installation................................................................................................................................................53
Mounting the ConnectPort X5 to a vehicle..............................................................................................................54
ConnectPort X5 R and X5 Iridium.................................................................................................................54
ConnectPort X5 Fleet .....................................................................................................................................55
Satellite setup ...........................................................................................................................................................56
ConnectPort X5 R Iridium..............................................................................................................................56
ConnectPort X5 ORBCOMM-equipped models............................................................................................56
Chapter 3: Configuration.......................................................................................................................................................57
IP address assignment ..............................................................................................................................................58
Default IP address and DHCP settings...........................................................................................................58
Alternative methods of assigning IP addresses ..............................................................................................58
Configure an IP address using DHCP ............................................................................................................58
Configure an IP address using Auto-IP..........................................................................................................59
Test the IP address configuration ...................................................................................................................59
Configuration through Device Manager ........................................................................... .... .... ...............................60
Device Cloud device management through Short Message Service (SMS) commands................................60
Configuration through the web interface .................................................................................................................61
Open the web interface...................................................................................................................................61
Organization of the web interface...................................................................................................................63
Change the IP address from the web interface, as needed..............................................................................65
Network configuration settings.......................................................................................................................66
Mobile (cellular) settings..............................................................................................................................112
XBee network settings..................................................................................................................................137
Serial port settings ........................................................................................................................................151
Alarms...........................................................................................................................................................160
System settings .............................................................................................................................................164
Device Cloud settings...................................................................................................................................172
Users settings................................................................................................................................................181
Position - GPS support.................................................. .... ............................................... .... .........................189
Applications..................................................................................................................................................191
Configuration through the command line..............................................................................................................197
4
Page 5

Contents
Access the command line .............................................................................................................................197
Verify device support of commands.............................................................................................................197
Examples of configuration commands .........................................................................................................198
Configuration through Simple Network Management Protocol (SNMP)................................................. .... ... ......200
Batch capabilities for configuring multiple devices...............................................................................................200
Chapter 4: Monitoring and management...........................................................................................................................201
Monitoring capabilities from Device Manager.................. ............................................... .....................................202
Monitoring capabilities in the web interface..........................................................................................................203
Display system information..........................................................................................................................203
Manage connections and services.................................................................................................................221
Monitoring capabilities from the command line....................................................................................................225
Commands for displaying device information and statistics........................................................................225
Commands for managing connections and sessions.....................................................................................227
Commands for managing XBee networks and nodes...................................................................................228
Monitoring Capabilities from SNMP.....................................................................................................................229
Chapter 5: Device administration.......................................................................................................................................230
Administration from the web interface ..................................................................................................................230
File management...........................................................................................................................................231
X.509 Certificate/Key Management.............................................................................................................232
Backup/restore device configurations...........................................................................................................244
Update firmware and Boot/POST Code.......................................................................................................245
Restore a device configuration to factory defaults.......................................................................................246
Display system information..........................................................................................................................247
Reboot the Digi device .................................................................................................................................247
Enable/disable access to network services ...................................................................................................247
Administration from the command-line interface..................................................................................................248
Chapter 6: Programming.....................................................................................................................................................249
General programming tools and resources .............................................................................................................250
Digi Developer Community Wiki ................................................................................................................250
Digi Python Custom Development Environment page ................................................................................250
Digi Python Programmer’s Guide................................................................................................................250
Python Support Forum on digi.com.............................................. .... .... ........................................................250
DIA...............................................................................................................................................................251
Device Manager............................................................................................................................................251
The Digi API for vehicle bus programming...........................................................................................................252
Vehicle bus protocol specifications..............................................................................................................252
Vehicle bus protocols supported in the Digi API..................................... .... ................................................253
Digi built-in modules for vehicle bus programming ....................................................................................254
5
Page 6

Contents
The SAE J1708 bus protocol API.................................................................................................................255
The SAE J1587 bus protocol API.................................................................................................................258
The CAN bus protocol..................................................................................................................................261
The SAE J1939 bus protocol........................................................................................................................265
Additional programming samples and demos ..............................................................................................267
The Digi API for satellite communication via the Iridium® network...................................................................268
Working with the Iridium network: general notes........................................................................................268
Digi built-in modules for Iridium programming ..........................................................................................268
The Iridium network: SBD transmission......................................................................................................269
The Iridium network: SBD reception...........................................................................................................270
Example Python program.............................................................................................................................272
Additional programming examples and information....................................................................................274
Internal sensor programming .................................................................................................................................274
Power consumption and management ...................................................................................................................275
External power control device......................................................................................................................275
Sleep mode and waking................................................................................................................................275
Power control for satellite modems..............................................................................................................276
Reading data from XBee Drop-in Networking Accessories..................................................................................276
Chapter 7: Specifications and certifications.......................................................................................................................277
Hardware specifications.............................. .... .... ............................................... .... ... .............................................277
ConnectPort X5 R and ConnectPort X5 Kit specifications..........................................................................278
ConnectPort X5 Fleet specifications ............................................................................................................279
Wireless networking features.................................................................................................................................280
Regulatory information and certifications..............................................................................................................282
RF exposure statement..................................................................................................................................282
FCC certifications and regulatory information (USA only).........................................................................282
Industry Canada (IC) certifications ..............................................................................................................284
Safety statements..........................................................................................................................................285
International EMC (Electromagnetic Emissions/Immunity/Safety) standards.............................................286
Environmental requirements for ConnectPort X5 Family products.............................................................287
Chapter 8: Troubleshooting.................................................................................................................................................288
Troubleshooting Resources....................................................................................... .............................................288
System status LEDs................................................................................................................................................289
ConnectPort X5 R LEDs ................................................................................. .... .........................................289
ConnectPort X5 R Iridium LEDs .................................................................................................................289
6
Page 7

Purpose
About this guide
Purpose
This guide describes and shows how to install, provision, configure, monitor, and administer Digi devices.
Audience
This guide is intended for those responsible for setting up Digi devices. It assumes some familiarity with networking
concepts and protocols.
Scope
This guide focuses on configuration, monitoring, and administration of Digi devices. It does not cover hardware details
beyond a certain level, application development, or customization of Digi devices.
Where to find more information
In addition to this guide, find additional product and feature information in the these documents:
Online help and tutorials in the web interface for the Digi device
Quick Start Guides
RealPort
Cellular 101 Tutorial
Digi Connect Family Customization and Integration Guide
Device Cloud
Release Notes
Cabling Guides
Product information available on the Digi website, www.digi.com, and Digi's support site at www.digi.com/
support, including, Support Forums, Knowledge Base, Data sheet s /product briefs, application/solution
guides, and carrier-specific documents
®
Installation Guide
®
tutorials and user’s guides
Digi Wiki for Developers
7
Page 8

Digi contact information
Digi contact information
For more information about Digi products, or for customer service and technical support, contact Digi International.
To Contact Digi International by: Use:
Mail Digi International
11001 Bren Road East
Minnetonka, MN 55343
U.S.A.
World Wide Web: http://www.digi.com/support/
email Look for the link Contact Digi Support at this address:
http://www.digi.com/support/
Telephone (U.S.) (952) 912-3444 or (877) 912-3444
Telephone (other locations) +1 (952) 912-3444 or (877) 912-3444
8
Page 9

Introduction
CHAPTER 1
This chapter introduces Digi devices and their product families, types of connections and data
paths in which Digi devices can be used, and the interface options available for configuring,
monitoring, and administering Digi devices.
Important Safety Information
To avoid contact with electrical current:
Important Safety Information
Never install electrical wiring during an electrical storm.
Never install an Ethernet connection in wet locations unless that connec to r is
specifically designed for wet locations.
Use caution when installing or modifying lines.
Use a screwdriver and other tools with insulated handles.
Wear safety glasses or goggles.
Do not place Ethernet wiring or connections in any conduit, outlet or junction box
containing electrical wiring.
Installation of inside wire may bring you close to electrical wire, conduit, terminals and
other electrical facilities. Extreme caution must be used to avoid electrical shock from
such facilities. Avoid contact with all such facilities.
Ethernet wiring must be at least 6 feet from bare power wiring or lightning rods and
associated wires, and at least 6 inches from other wire (antenna wires, doorbell wires,
wires from transformers to neon signs), steam or hot water pipes, and heating ducts.
Do not place an Ethernet connection where it would allow a person to use an Ethernet
device while in a bathtub, shower, swimming pool, or similar hazardous location.
Protectors and grounding wire placed by the service provider must not be connected to,
removed, or modified by the customer.
Do not touch uninsulated Ethernet wiring if lightning is likely!
External W iri ng : Any external communications wiring installed n eeds to b e constructe d
to all relevant electrical codes. In the United States this is the National Electrical Code
Article 800. Contact a licensed electrician for details.
9
Page 10

ConnectPort® X5 Family products
ConnectPort® X5 Family products
The ConnectPort X5 Family offers compact, ruggedized telematics gateways for cost-effective
fleet management and asset tracking solutions. These gateways provide remote connectivity to
mobile assets to monitor operating health, performance, location and driver/operator behavior, as
well as to enable automated event reporting. They aggregate wireless vehicle Personal Area
Network (VPAN) traf fic, such a s ZigBee and 802.15.4 p oint-to-multipoint, fo r IP connectivity over
a secure cellular, Wi-Fi, or satellite connection in harsh environments.
Gateways in the ConnectPort X5 family include the ConnectPort X5 R, ConnectPort X5 Kit, and
ConnectPort X5 Fleet. The ConnectPort X5 Kit was designed as a development kit to be used for
testing and evaluation prior to deployment of the ConnectPort X5 R or ConnectPort X5 Fleet. The
ConnectPort X5 Kit comes with a development cable, antennas, and, for GSM versions, has an
opening in the enclosure to allow users to insert their own SIM card. As such, the
ConnectPort X5 Kit should be used for testing and evaluation only. Customers will be responsible
for procuring antennas and cabling for their specific ConnectPort X5 R and ConnectPort X5 Fleet
installations.
10
Page 11

ConnectPort® X5 Family products
These gateways support vehicle personal area networks with Digi’s industry-leading XBee radio
technology. Vehicle personal area networks (VPANs) allow users to deploy low-power sensor
networks within and around the vehicle or mobile asset to monitor additio nal asset points, for
example, tires, reefer units, door latch, temperature sensors, cargo sensors, RFID readers, etc.
The ConnectPort X5 family provides flexible wide-area networking connectivity supporting
cellular, Wi-Fi, and satellite communications. Cellular connectivity provides instant, always-on
communications, while Wi-Fi provides a cost-effective way to transfer lar ge files, firmware, or logs
across low-cost private Wi-Fi networks. The ConnectPort X5 Wi-Fi feature can also be used to
network in-vehicle or near-vehicle Wi-Fi-enabled devices, such as vehicle displays and handheld
mobile devices.
Features and benefits of the ConnectPort X5 gateway family include:
For units without external SIM card access, factory-sealed IP67 enclosure, ensuring
protection from dust and total water immersion to 1 meter
For units with external SIM card access, factory-sealed IP67 enclosure, ensuring
protection from dust and immersion.
J1708 protocol support, offering serial connectivity to a large installed base of heavy
duty vehicle fleets
Controller Area Network (CAN) interface support for connection to J1939 or
proprietary vehicle bus
Internal temperature sensor and accelerometer
Advanced power management, including sensitivity to ignition status
Location tracking and geofencing with on-board GPS
Global cellular coverage over GSM/GPRS or CDMA networks
Optional satellite on selected ConnectPort X5 R and ConnectPort X5 Fleet models
Programmable for application development through the Python
®
programming
language, Device Cloud Device Integration Application (DIA) framework and the
Device Cloud services platform
Automated event reporting: the gateway can continuou sly transmit v ehicle statu s at user -
defined intervals
Device Manager™ for management and monitoring
11
Page 12

Features
User interfaces
Features
This is an overview of key features in Digi devices. Firmware features are covered in more detail in
the next three chapters. Hardware specifications are covered in Chapter 7, "Specifications and
certifications"
There are several user interfaces for configuring and monitoring Digi devices, including the
following.
Device Manager™
A web-based interface for configuring, monitoring, and administer ing Digi devices.
Plugging the ConnectPort X5 device into a switch or network to which a laptop
computer is connected all o ws direct access to the web interface for configuration.
A command-line interface available via local serial port, telnet or SSH.
Simple Network Management Protocol (SNMP).
Configurable network services
Access to network services can be enabled and di sabled. This mea ns that a dev ice’s use of network
services can be restricted to those strictly needed by the device. To improve device security, nonsecure services can be disabled. Network services that can be enabled or disabled include:
Advanced Digi Discovery Protocol (ADDP): can enable or disable ADDP, but cannot
change its network port number.
RealPort
Encrypted RealPort
HTTP/HTTPS
Remote Login (rlogin)
Remote Shell (rsh)
Simple Network Management Protocol (SNMP)
Telnet
In the web interface, access to network services is enabled and disabled on the Network Services
page of Network Configuration. For more informati on, see "Network services settin gs" on page 78.
In the command-line interface, network services are enabled and disabled through the set service
command. See the Digi Connect Family Command Reference for the set service command
description.
12
Page 13

IP protocol support
All Digi devices include a Robust on-board TCP/IP stack with a built-in web server. Supported
protocols include, unless otherwise noted:
Transmission Control Protocol (TCP)
User Datagram Protocol (UDP)
Dynamic Host Configuration Protocol (DHCP)
Simple Network Management Protocol (SNMP)
Secure Sockets Layer (SSL)/Transport Layer Security (TLS)
Telnet Com Port Control Option (Telnet) including support of RFC 2217 (ability to
Remote Login (rlogin)
Line Printer Daemon (LPD)
HyperText Transfer Protocol (HTTP)/HyperText Transfer Protocol over Secure Socket
Features
control serial port through Telnet). See "Serial data communication over TCP and UDP"
on page 14 for additional information.
Layer (HTTPS)
Simple Mail Transfer Protocol (SMTP)
Internet Control Message Protocol (ICMP)
Internet Group Management Protocol (IGMP)
Address Resolution Protocol (ARP)
Advanced Digi Discovery Protocol (ADDP)
Point to Point Protocol (PPP)
Network Address Translation (NAT)/Port Forwarding
Secure Shell (SSHv2)
Generic Routing Encapsulation (GRE) Passthrough
IPSec Encapsulating Security Payload (ESP) on most models
ESP Passthrough
Following is an overview of some of the services provided by these protocols.
13
Page 14

Serial data communication over TCP and UDP
Digi devices support serial data communication over TCP and UDP. Key features include:
Serial data communication over TCP, also known as autoconnect and tcpserial can
automatically perform the following functions:
– Establish bidirectional TCP connections, known as autoconnections, between the serial
device and a server or other network device. Autoconnections can be made based on
data and or serial hardware signals.
– Control forwarding characteristics based on size, time, and pattern
– Allow incoming raw, Telnet, and SSL/TLS (secure-socket) connections
– Support RFC 2217, an extension of the Telnet protocol
Serial data communication over UDP, also known as udpserial, can automatically
perform the following functions:
– Digi Connect products can automatically send serial data to one or more devices or
systems on the network using UDP sockets. Options for sending data include whether
specific data is on the serial line, a specific t ime period has elapsed, or after the specified
number of bytes has been received on the serial port.
– Control forwarding characteristics based on size, time, and patterns.
Features
– Support incoming datagrams from multiple destinations.
– Support outgoing datagrams sent to multiple dest inations.
TCP/UDP forwarding characteristics.
Extended communication control on TCP/UDP data paths.
–Timeout
–Hangup
– User-configurable Socket ID string (text string identifier on autoconnect only)
Dynamic Host Configuration Protocol (DHCP)
Dynamic Host Configuration Protocol (DHCP) can be used to automatically assign IP addresses,
deliver TCP/IP stack configuration parameters such as the subnet mask and default router, and
provide other configuration information. For further details, see "Configure an IP address using
DHCP" on page 58.
Auto-IP
Auto-IP is a protocol that will automatically assign an IP address from a reserved pool of standard
Auto-IP addresses to the computer on which it is installed. For Digi devices are set to obtain its IP
address automatically from a DHCP server and the DHCP server is unavailable or nonexistent,
Auto-IP will assign the device an IP address. For further details, see "Configure an IP address using
Auto-IP" on page 59.
14
Page 15

Simple Network Management Protocol (SNMP)
Simple Network Management Protocol (SNMP) is a protocol for managing and monitoring
network devices. SNMP architecture enables a network administrator to manage nodes--servers,
workstations, routers, switches, hubs, etc.--on an IP network; manage network performance, find
and solve network problems, and plan for network growth. Digi devices support SNMP Versions 1
and 2. For more information on SNMP as a device-management interface, see "Simple Network
Management Protocol (SNMP)" on page 33. For a list SNMP-related of supp orted Request for
Comments (RFCs) and Management Information Bases (MIBs), see page 168.
Secure Sockets Layer (SSL)/Transport Layer Security (TLS)
Secure Sockets Layer (SSL)/Transport Layer Security (TLS) are used to provide authentication and
encryption for Digi devices. For more information, see "Security features in Digi dev ice s" on page
20.
Telnet
Digi devices support the following types of Telnet connections:
Features
Telnet Client
Telnet Server
Reverse Telnet, often used for console management or device management
Telnet Autoconnect
RFC 2217, Telnet Com Port Control Option, an extension of the Telnet protocol
For more information on these connections, see "Supported connections and data paths in Digi
devices" on page 22. Access to Telnet network services can be enabled or disabled.
Remote Login (rlogin)
Users can perform logins to remote systems (rlogin). Access to rlogin service can be enabled or
disabled.
HyperText Transfer Protocol (HTTP) HyperText Transfer Protocol over Secure Socket Layer (HTTPS)
Digi devices provide web pages for configuration that can be secured by requiring a user login.
Internet Control Message Protocol (ICMP)
ICMP statistics can be displayed, including the number of messages received, bad messages
received, and destination unreachable messages received.
15
Page 16

Point-to-Point Protocol (PPP)
The Point-to-Point Protocol (PPP) transports multi-protocol packets over point-to-point links. PPP
encapsulates the data packet, allows the server to inform the dial-up client of its IP address (or
client to request the IP address), authenticates the exchange, negotiates multiple protocols, and
reassembles the data packet for network communication. ConnectPort X5 Family devices support
PPP as the connection protocol from the Digi device to th e cellular IP network with NAT (Network
Address Technology).
Network Address Translation (NAT)/Port Forwarding
Network Address Translation (NAT) reduces the need for a large amount of publicly known IP
addresses by creating a separation between publicly known and privately known IP addresses.
Advanced Digi Discovery Protocol (ADDP)
The Advanced Digi Discovery Protocol (ADDP) runs on any operating system capable of sending
multicast IP packets on a network. ADDP allows the system to identify all ADDP-enabled Digi
devices attached to a network by sending out a multicast packet. The Digi devices respond to the
multicast packet and identify themselves to the client sending the multicast.
Features
ADDP communicates with the TCP/IP stack using UDP. The TCP/IP stack should be able to
receive multicast packets and transmit datagrams on a network.
Not all Digi devices support ADDP. Access to ADDP service can be enabled or disabled, but the
network port number for ADDP cannot be changed from its default.
Generic Routing Encapsulation (GRE) Passthrough Encapsulating Security Payload (ESP) ESP Passthrough
Generic Routing Encapsulation (GRE) and Encapsulating Security Payload (ESP) are routing
protocols that are used to route (tunnel) various types of informat ion between networks.
GRE applies to the encapsulation of IP datagrams t unnelled through the interne t. The encapsulation
includes security , typically in the form of IPSec (IP security), and is most commonly fo und in VPN
(Virtual Private Network) implementation. RFC (Request For Comment) 1701 and 1702 define
these standards.Similarly, ESP is used in conjunction with IPsec as a possible way of carrying IP
packets for a Virtual Private Network (VPN) setup. ESP is defined in RFC 2406.
In ESP Passthrough and GRE Passthrough, inbound IPsec ESP or GSP prot ocol traffic is
forwarded from to a VPN device connected to the Digi device’s Ethernet port.
Note: If an Auto-key Internet Key Exchange (IKE)-based VPN is used, UDP port 500 must also be
forwarded.
16
Page 17

Mobile/Cellular features and protocol support
Key cellular features in cellular-enabled Digi devices include:
GSM: GPRS, EDGE, SMS
CDMA: 1xRTT, Ev -DO (Revs 0 and A)
IPSec ESP / IKE
IP Pass-through, also known as bridge mode
3-5 Volt SIM card
Signal-strength LEDs
Provisioning wizard
For Digi devices equipped with a Code-Divisi on Multipl e Access (CDMA)-based cellular mode m,
the Mobile Device Provisioning Wizard is available in the web interface to properly configure the
Digi device with the required configuration used to access the mobile network. The wizard allows
for both automatic and manual provisioning for a variety of mobile service providers.
Features
Digi SureLink™
Digi Connect Family, Digi Cellular Family, and ConnectPort X Family products support the Digi
SureLink™ feature. Digi SureLink provides an “always-on” mobile network connect io n t o ensure
that a Digi device is in a state where it can connect to the network. It does this through hardware
reset thresholds and periodic tests of the connection.
Mobile/Cellular protocols
Mobile/cellular protocols supported include, unless otherwise noted:
Global System for Mobile communication (GSM)
General Packet Radio Service (GPRS)
Enhanced Data Rates for GSM Evolution (EDGE)
Universal Mobile Telecommunications Service (UMTS)
High Speed Packet Access (HSPA)
Code-Division Multiple Access (CDMA)
Evolution-Data Optimized (EV-DO, EVDO, or 1xEV-DO)
Short Message Service (SMS), currently for GSM cellular products only. Digi cellular
gateways implement an SMS-based protocol that allows managing devices by sending
SMS commands from anywhere SMS messages can be sent. See "Short Message
Service (SMS) settings" on page 126.
Wi-MAX
17
Page 18

RealPort software
Digi devices use the patented RealPort COM/TTY port redirection for Microso ft Windows.
RealPort software provides a virtual connection to serial devices, no matter where they reside on
the network. The software is installed directly on the host PC and allows applications to talk to
devices across a network as though the devices were directly attached to the host. Actually, the
devices are connected to a Digi device somewhere on the network. RealPort is un ique among COM
port re-directors because it is the only implementation that allo ws multiple co nnectio ns to multiple
ports over a single TCP/IP connection. Other implementations require a separate TCP/IP
connection for each serial port. Unique features also include full hardware and software flow
control, as well as tunable latency and throughput. Access to RealPort services can be enabled or
disabled.
Encrypted RealPort
Digi devices also support RealPort software with encryption. Encrypted RealPort offers a secure
Ethernet connection between the COM or TTY port and a device server or terminal server.
Encryption prevents internal and external snooping of data across the network by encapsulating the
TCP/IP packets in a Secure Sockets Layer (SSL) connection and encrypting the data using
Advanced Encryption Standard (AES), one of the latest, most efficient security algorithms. Access
to Encrypted RealPort services can be enabled or disabled. Digi’s RealPort with encryption driver
has earned Microsoft’s Windows Hardware Quality Lab (WHQL) certification. Drivers are
available for a wide range of operating systems, including Microsoft Windows Server 2003,
Windows XP, Windows 2000, Windows NT, Windows 98, Windows ME; SCO Open Server;
Linux; AIX; Sun Solaris SPARC; Intel; and HP-UX. It is ideal for financial, retail/point-of-sale,
government or any application requiring enhanced security to protect sensitive information.
Features
18
Page 19

Alarms
Digi devices can be configured to issue alarms, in the form of email message or SNMP traps, when
certain device events occur. These events include changes in GPIO signals, certain data patterns
being detected in the data stream, and cellular alarms for signal strength and amount of cellular
traffic for a given period of time. Receiving alarms about these conditions provides the advantage
of notifications being issued when events occur, rather than having to monitor the device on an
ongoing basis to determine whether these events have occurred. Alarms can also be forwarded to
Device Manager for display and management in that platform. For more information on
configuring alarms, see "Alarms" on page 160.
Modem emulation
Digi devices include a configuration profile that allows the device to emulate a modem. Modem
emulation sends and receives modem responses to a serial de vic e o ver TCP/IP (in clu di ng Eth erne t
and Cellular) instead of Public Switched Telephone Network (PSTN). The modem emulation
profile allows maintaining a current software application but using it over the less expensive
Ethernet network. In addition, Telnet processing can be enabled or disabled on the incoming and
outgoing modem-emulation connections.The modem-emulation commands supported in Digi
devices are documented in the Digi Connect Family Command Reference.
Features
19
Page 20

Security features in Digi devices
Secure access and authentication
One password, one permission level.
Passwords can be issued to device users.
Selective enabling/disabling network services such as ADDP, RealPort, Encrypted
RealPort, HTTP/HTTPS, LPD, Remote Login, Remote Shell, SNMP, and Telnet.
Can control access to inbound ports.
Can control access to specific devices, IP addresses, or networks through IP filtering.
Secure sites for configuration: HTML pages for configuration have appropriate security.
Encryption
Encrypted RealPort offers encryption for the Ethernet connection between the COM/
TTY port and the Digi device. Encryption prevents internal and external snooping of
data across the network by encapsulating the TCP/IP packets in a Secure Sockets Layer
(SSL) connection and encrypting the data using the Advanced Encryption Standard
(AES) security algorithm.
Features
Strong Secure Sockets Layer (SSL) V3.0/ Transport Layer Security (TLS) V1.0-based
encryption: DES (64-bit), 3DES (192-bit), AES (128-/192-/256-bit), IPsec ESP: DES,
3DES, AES.
Wireless Digi Connect products provide Wi-Fi Protected Access (WPA/WPA2/802.11i)
and Wired Equivalent Privacy (WEP) encryption (64-/128-bit). Supported WPA/WPA2/
802.11i authentication methods are:
Supported WPA authentication methods
EAP-TLS PEAP EAP/TTLS
LEAP
(WEP only)
EAP-PEAP/MSCHAPv2 (both PEAPv0 and
PEAPv1)
EAP-PEAP/TLS (both PEAPv0 and PEAPv1)
EAP-PEAP/GTC (both PEAPv0 and PEAPv1)
EAP-PEAP/OTP (both PEAPv0 and PEAPv1)
EAP-PEAP/MD5-Challenge (both PEAPv0 and
PEAPv1)
EAP-TTLS/EAP-MD5-Challenge
EAP-TTLS/EAP-GTC
EAP-TTLS/EAP-OTP
EAP-TTLS/EAP-MSCHAPv2
EAP-TTLS/EAP-TLS
EAP-TTLS/MSCHAPv2
EAP-TTLS/MSCHAP
EAP-TTLS/PAP
20
EAP-TTLS/CHAP
Page 21

SNMP security
SNMP “set” commands can be disabled to make use of SNMP read-only. Changing public and
private community names is recommended to prevent unauthorized access to the device.
Configuration management
Once a Digi device is configured and running, configuration-management tasks need to be
periodically performed, such as:
Upgrading firmware
Copying configurations to and from a remote host
Software and factory resets
Rebooting the device
Memory management
File management
For more information on these configuration-management tasks, see Chapter 5, "Device
administration".
Features
Customization capabilities
Several aspects of using Digi devices can be customized. For example:
The look-and-feel of the device interface can be customized , to use a different company
logo or screen colors.
Custom applications written in Python can be executed.
Custom factory defaults to which devices can be reverted can be defined.
The Digi Connect Family Customization and Integration Guide (Part Number 90000734; available
with the Digi Connect Integration Kit) describes customization and integration tools and processes.
Contact Digi International for more informatio n on the Digi Con nect Integratio n Kit customizatio n
tools and resources and for assistance with customization efforts.
21
Page 22

Supported connections and data paths in Digi devices
Supported connections and data paths in Digi devices
Digi devices allow for several kinds of connections and paths for data flow between the Digi device
and other entities. These connections can be grouped into two main categories:
Network services, in which a remote entity initiates a connection to a Digi device.
Network/serial clients, in which a Digi device initiates a network connect ion or opens a
serial port for communication.
This discussion of connections and data paths may be helpful in understanding the effects of
enabling certain features and choosing certain settings when configuring Digi products.
Network services
A network service connection is one in which a remote entity initiates a connection to a Digi
device. There are several categories of network services:
Network services associated with specific serial ports
Network services associated with serial ports in general
Network services associated with the command-line interface (CLI)
Network services associated with specific serial ports
Reverse Telnet: A telnet connection is made to a Digi device, in which data is passed
transparently between the telnet connection and a named serial port.
Reverse raw socket: A raw TCP socket connection is made to a Digi device, in which
data is passed transparently between the socket and a named serial port.
Reverse TLS socket: An encrypted raw TCP socket is made to a Digi device, in which
data is passed transparently to and from a named serial port.
Modem emulation, also known as Pseudo-modem (pmodem): A TCP connection is
made to a named serial port, and the connection will be “interpreted” as an incoming call
to the pseudo-modem.
22
Page 23

Supported connections and data paths in Digi devices
Network services associated with serial ports in general
RealPort: A single TCP connection manages (potentially) multiple serial ports.
Modem emulation, also known as pseudo-modem (pool): A TCP connection to the
“pool” port is interpreted as an incoming call to an available pseudo-modem in the
“pool” of available port numbers.
rsh: Digi devices support a limited imp lementation of t he Remote shell (rsh) protocol, in
that a single service listens to connections and allows a command to be executed. Only
one class of commands is allowed: a single integer that specifies which serial port to
connect to. Otherwise, the resultin g connection is somewhat simi lar to a reverse telne t or
reverse socket connection.
DialServ: Connecting a DialServ device to the serial port. DialServ simulates a public
switched telephone network (PSTN) to a modem and forwards the data to the serial port.
The Digi device sends and receives the data over an IP network.
Network services associated with the command-line interface
Telnet: A user can Telnet directly to a Digi device’s command-line interface.
rlogin: A user can perform a remote login (rlogin) to a Digi device’s command-line
interface.
23
Page 24

Supported connections and data paths in Digi devices
Network/serial clients
A network/serial client connection is one in which a Digi device initiates a network connection or
opens a serial port for communication. There are several cat egories of network/serial client
connections:
Autoconnect behavior client connections
Command-line interface (CLI)-based clients
Modem emulation (pseudo-modem) client connections
Autoconnect behavior client connections
In client connections that involve autoconnect behaviors, a Digi device initiates a network
connection based on timing, serial activity, or serial modem signals. Autoconnect-related client
connections include:
Raw TCP connection: The Digi device initiates a raw TCP socket connection to a
remote entity.
T elnet connection: The Digi device init iates a TCP connecti on using the Telnet protocol
to a remote entity.
Raw TLS encrypted connection: The Digi device initiates an encrypted raw TCP
socket connection to a remote entity.
Rlogin connection: The Digi device initiates a TCP connection using the rlogin
protocol to a remote entity.
Command-line interface (CLI)-based client connections
Command-line interface based client connectio ns are available for use once a user has established a
session with the Digi device’s CLI. CLI-based client connections include:
telnet: A connection is made to a remote entity using the Telnet protocol.
rlogin: A connection is made to a remote entity using the Rlogin protocol.
connect: Begin communicating with a local serial port.
Modem emulation (pseudo-modem) client connections
When a port is in the modem-emulation or pseudo-modem mode, it can initiate network
connections based on AT command strings received on the serial port.The AT commands for
modem emulation are documented in the Digi Connect Family Command Reference.
24
Page 25

Interfaces for configuring, monitoring, and administering Digi devices
Interfaces for configuring, monitoring, and administering Digi devices
There are several interfaces for configuring, monitoring, and administering Digi devices. These
interfaces are covered in more detail later in this guide.
Configuration capabilities
Device configuration involves setting values and enabling features for such areas as:
Network configuration: Specifying the device’s IP address settings, network-service
settings, and advanced network settings.
Mobile (cellular) configuration: Specifying the mobile service provider and mobile
connection settings for the device.
Alarms: Defining whether alarms should be issued, the conditions that trigger alarms,
and how the alarms should be delivered.
Security/Users configuration: Configuring security features, such as whether password
authentication is required for device users.
System configuration: Specifying system-identifying information, such as a device
description, contact person, and physical location.
25
Page 26

Interfaces for configuring, monitoring, and administering Digi devices
Configuration interfaces
Several interfaces are available for configuring Digi devices, including:
The Digi Device Discovery Utility, which locates Digi devices on a network, and allows
opening the web interface for the devices.
Device Manager, a configuration interface to fine-tune or monitor devices. Device
Manager cannot assign an IP address but it can change one.
A web-based interface embedded with the product, providing device configuration
profiles for quick serial-port configuration and other settings.
A command-line interface (CLI).
Remote Command-line Interface (RCI) protocol
Simple Network Management Protocol (SNMP).
26
Page 27
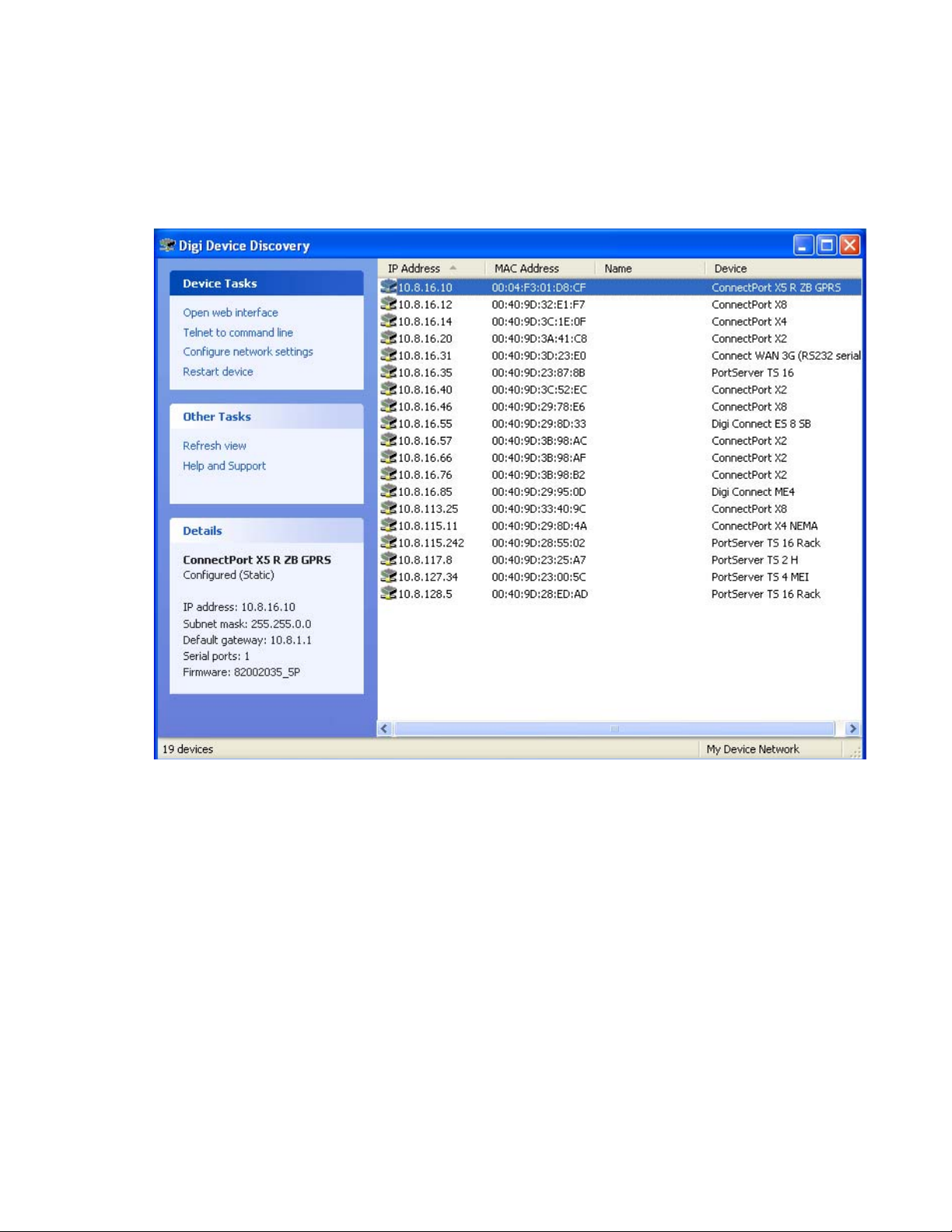
Interfaces for configuring, monitoring, and administering Digi devices
Digi Device Discovery utility
The Digi Device Discovery utility locates Digi devices on a network and allows for opening the
web interface for discovered devices, configuring network settings, and rebooting the device. It
uses a Digi International-proprietary protocol, Advanced Digi Discovery Protocol (ADDP), to
discover the Digi devices on a network, and displays the discovered devices in a list, for example:
Digi Device Discovery quickly locates Digi devices and basic device information, such as the
device’s address, firmware revision, and whether it has been configured. It runs on any operating
system that can send multicast IP packets to a network. It sends out a User Datagram Protocol
(UDP) multicast packet to all devices on the network. Devic es supporting ADDP reply to this UDP
multicast with their configuration information. Even devices that do not yet have an IP address
assigned or are misconfigured for the subnet can reply to the UDP multicast packet and be
displayed in device discovery results.
Not all Digi devices support ADDP. Note that Device discovery responses can be blocked by
personal firewalls, Virtual Private Network (VPN) software, and certain network equipment.
Firewalls will block UDP ports 2362 and 2363 that ADDP uses to discover devices.
Digi Device Discovery is available for downloading from the Digi Support site. After installation,
it is available from the Start menu. Access to the ADDP service can be enabled or disabled, but the
network port number for ADDP cannot be changed from its default. For more information on the
Digi Device Discovery utility, see page 61.
27
Page 28
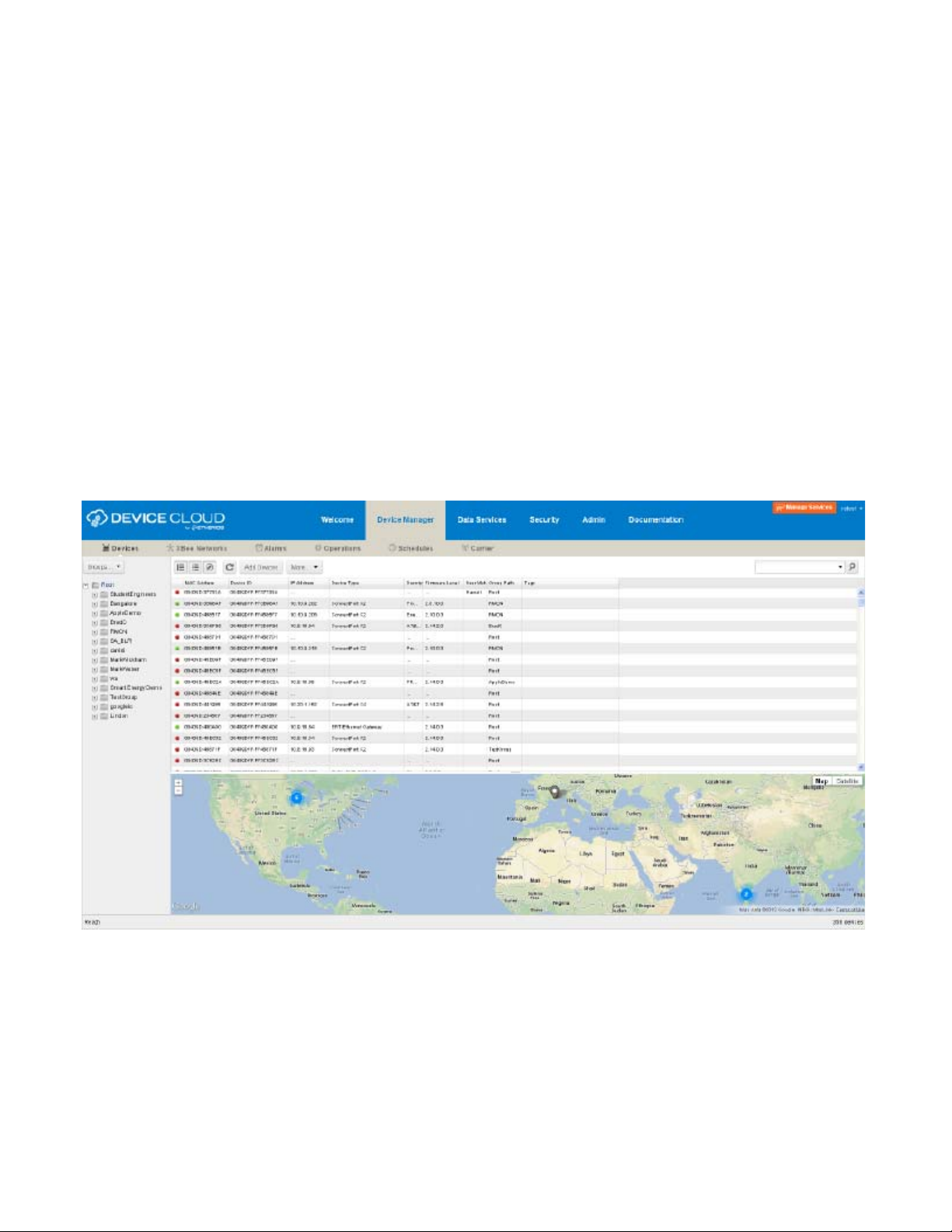
Interfaces for configuring, monitoring, and administering Digi devices
Device Manager™ interface
Device Manager is a software-as-a-service, delivering capabilities that empower IT, network
operations and customer support organizations to conquer the challenges of managing the vast
array of equipment in their device networks. As a network grows, the complexity of effectively
managing the network assets grows exponentially. Hosted on the Device Cloud by Etherios™,
Device Manager directly tackles and conquers the universal problems of a dynamic device
network:
Centralized control over large numbers of devices
Reducing service complexity
Maintaining high levels of security
Provisioning and decommissioning of equipment
Adding functionality to device net wo rk s
A feature of all Digi gateways, routers, devices and components, Device Manager provides a
robust suite of network management tool s with cent ra lized cont rol via t he De vice Man ager serv ice
module.
From the Device Manager interface, you can configure devices, remotely update device firmware,
upload and manage Python/DIA files, remotely reboot devices, reset devices to factory defaults,
backup/restore device configuration properties, import or export the device configuration
properties, track devices, monitor devices and connections.
With Device Manager, management of large populations of devices is made easy. Devices can be
tagged and grouped together enabling management tasks to groups of devices within a network
simultaneously . Furthermore, the Scheduled Operat ions feature allows device management tasks to
28
Page 29

Interfaces for configuring, monitoring, and administering Digi devices
be automated and scheduled to run either on a one -time or a recurring ba sis, against a singl e device
or multiple devices. The Alarms capability of Device Manager facilitates monitoring the health of a
device network. For instance, should a device disconnect or stay connected for longer than a
specified period, an alarm fires and notification of the alarm can be sent via email in real-time.
Some things to note about using Device Manager:
Devices must be registered on Device Manager before they can be accessed via the
Device Cloud platform.
To minimize network traffic, Device Manager uses caching. As a result, device settings
can be out-of-sync between the device and the settings viewed on the Device Manager
console.
Device information can be refreshed on demand when the device is connected, and is
refreshed automatically when a device connects.
For more information on Device Manager as a remote device network management solution, see
these resources:
Device Cloud User’s Guide
Device Cloud Programming Guide
Device Cloud tutorials and other documents available on www.etherios.com/
devicecloud
29
Page 30

We b i n terface
Interfaces for configuring, monitoring, and administering Digi devices
A web interface is provided as an easy way to configure and monitor Digi devices. Configurable
features are grouped into several categories. These categories vary by product ; examples include
Network, Serial Port, Alarms, and System. Most of the configurable features are arranged by most
basic settings on a page, with associated and advanced settings accessi ble from that page . Serial-port
configurations are classified into port profiles, or configuration scenarios that best represents the
environment in which the Digi device will be used. Selecting a particular port profile con figures the
serial port parameters that are needed. To access the web interface, enter the Digi device’s IP
address or host name in a browser’s URL window. The main menu of the web interface is
displayed. For more information, see "Configuration through the web interface" on page 61. The
web interface has a tutorial, accessed from the Home page, and on line help, accessed from the Help
link on each page. Not all settings provided by the command-line interface are displayed in the web
interface. However, the configuration settings in the web interface should be sufficient for most
users. If necessary, settings can be modified later from the command line.
30
Page 31

Interfaces for configuring, monitoring, and administering Digi devices
31
Page 32

Interfaces for configuring, monitoring, and administering Digi devices
Command-line interface
Digi devices can be configured by issuing commands from the command line. The command-line
interface allows communication directly without a graphical interface. To access the command line
from the Digi Device Discovery utility, click Telnet to command line.
For example, here is a command issued from the command line o assign the IP address to the
Ethernet interface:
#> set network ip=192.168.1.1
The command-line interface provides flexibility for making precise changes to device
configuration settings and operation. It does require users to have experience issuing commands,
and access to command documentation.
The command line is available through Telnet or SSH TCP/IP connections, or through serial port
using terminal emulation software such as Hyperterminal. Access to the command line from serial
ports depends on the port profile in use by the port. By default, serial port command-line access is
allowed.
See "Configuration through the command line" on page 197 for more information on this interface.
See the Digi Connect Family Command Refer e nce for command descriptions and examples of
entering configuration commands from the command-line interface. In addition, online help is
available for the commands, through the help and ‘?’ commands.
Remote Command Interface (RCI)
Remote Command Interface (RCI) is a programmatic in terface for configuring and controlling Digi
devices. RCI is an XML-based request/response protocol that allows a caller to query and modify
device configurations, access statistics, reboot the device, and reset the device to factory defaults.
Unlike other configuration interfaces that are desi gned for a user, such as the command-line or web
interfaces, RCI is designed to be used by a program. RCI access consists of program calls. A
typical use of RCI is in a Java applet that can be stored on the Digi device to replace the web
interface with a custom browser interface. Another example is a custom application running on a
PC that monitors and controls an installation of many Digi devices.
As RCI is designed to be used by a program, it is useful for creating a custom configuration user
interface, or utilities that configure or initialize devices through external programs or scripts.
RCI uses HTTP as the underlying transpo rt protoc ol. Depe nding on t he netw ork confi guration , use
of HTTP as a transport protocol could be blocked by some firewalls.
RCI is quite complex to use, requiring users to phrase configu ration request s in Extensible Marku p
Language (XML) format. It is a “power-user” option, intended more for users deve loping their own
user interfaces, or for users implementing embedded control (and thus potentially using RCI over
serial) than for end-users with limited knowledge of device programming.
Not all actions in the web interface have direct equivalents in RCI. Therefore, it may not be easy
for some end-users to determine what needs to be sent through XML for a particular style of
request.
For more details on RCI, see the Digi Co nnect Integration Kit and the Remote Command Interface
(RCI) Specification.
32
Page 33

Interfaces for configuring, monitoring, and administering Digi devices
Simple Network Management Protocol (SNMP)
Simple Network Management Protocol (SNMP) is a protocol for managing and monitoring
network devices. The SNMP architecture enables a network administrator to manage nodes-servers, workstations, routers, switches, hubs, etc.--on an IP network; manage network
performance, find and solve network problems, and plan for network growth. Digi devices support
SNMP Versions 1 and 2.
SNMP is easy to implement in extensive networks. Programming new variables and “dropping in”
new devices in a network are easy. SNMP is widely used. It is a standard interface that integrates
well with network management stations in an enterprise environment. While its capabilities are
limited to device monitoring and display of statistics in Digi devices, read/write capabilities are
expected to be added to Digi devices in future releases.
However, because device communication is UDP-based, the communication is not secure. If more
secure communications with a device are required, use an alt erna te devic e interfac e. SNMP does
not allow for certain task that can be performed from the web interface, such as file management,
uploading firmware, or backing up and restoring configurations. Compared to the web or
command-line interfaces, SNMP is limited in its ability to set specific parameters, such as set port
profile, is not possible.
Accessing the SNMP interface requires a tool, such as a network management station. The
management station relies on an agent at a device to retrieve or update the information at the
device, including Device configuration, status, and statistical information. This information is
viewed as a logical database, called a Management Information Base (MIB). MIB modules
describe MIB variables for a variety of device types and computer hardware and software
components.
A variety of resources about SNMP are available, including reference books, overviews, and other
files on the Internet. For an overview of the SNMP interface and the components of MIB-II, go to
http://www.rfc-editor.org/rfcsearch.html, and search for MIB-II. From the results, locate the text
file describing the SNMP interface, titled Management Information Base for Network
Management of TCP/IP-based internets: MIB-II. The text of the Digi enterprise MIBs can also be
displayed.
For additional discussion of using SNMP as a device monitoring interface, see "Monitoring
Capabilities from SNMP" on page 229.
33
Page 34

Interfaces for configuring, monitoring, and administering Digi devices
Monitoring capabilities and interfaces
Monitoring Digi devices includes such tasks as checking device status, checking runtime state,
viewing serial port operations, and reviewing network stati s tics, and managing their connections.
There are several interfaces for monitoring Digi devices and managing their connections.
As with device configuration, there are several interfaces available for monitoring Digi devices,
including, the web interface embedded with the product, SNMP, command-line interface, and
Device Manager. These interfaces are covered in more detail in Chapter 4, "Monitoring and
management"
Device Manager
In Device Manager, monitoring capabilities can be sorted by the server and the devices managed by
the server. The information is available in logs and can be generated into reports. When available,
the reports post linked totals that can be drilled back to the original devices that make up the
activity of the report.
Device Manager is well-suited to managing ConnectPort X5 Family devices and the networks in
which the devices reside. Advantages include the ability to view an entire network, and multiple
networks, at once, and ease in viewing signal strength, link quality, and alarms
We b i n terface
The web interface has several screens for monitoring Digi devices:
Network Status
Mobile connection status
Serial Port Management: for each port, the port’s description, current profile, and current
serial configuration.
Connections Management: A display of all active system connections.
System Information: general device information; serial port information for each port,
including the port’s description, current profile, and current serial configuration (the
same information displayed by choosing Serial Port Management); and network
statistics.
Command-line interface
Several commands can be issued from the command line to monitor devices. For a review of these
commands and what they can provide from a device-monitoring perspective, see "Monitoring
capabilities from the command line" on page 225.
SNMP
Monitoring capabilities of SNMP include managing network performance, gathering device
statistics, and finding and solving network problems. For more information on using SNMP for
device-monitoring purposes, see "Monitoring Capabili ties from SNMP" on page 229.
34
Page 35

Device administration
Periodically, administrative tasks need to be performed on Digi devices, such as uploading and
managing files, changing the password for logging onto the device, backing up and restoring
device configurations, updating firmware, restoring the configuration to factory defaults, and
rebooting.
As with configuration and monitoring, administration can be done from a number of interfaces,
including the web interface, command line, and Device Manager. See Chapter 5, "Device
administration" for more information and procedures.
Interfaces for configuring, monitoring, and administering Digi devices
35
Page 36

Hardware
CHAPTER 2
This section details requirements and recommendations for installing ConnectPort X5 products,
including the Wiring Harness, mounting requirements, and antennas. See also "Specifications and
certifications" on page 277 and "System status LEDs" on page 289.
36
Page 37

ConnectPort X5 R and ConnectPort X5 Kit hardware summary
(ConnectPort X5 R) (ConnectPort X5 R Iridium)
7
8
7
8
Top View
WIFI CELLULAR GPS SAT
2
3
4
5
1
6
WIFI CELLULAR GPS XBEE
2
3
4
5
1
6
(ConnectPort X5 R) (ConnectPort X5 R Iridium)
Side View
ConnectPort X5 R and ConnectPort X5 Kit hardware summary
1 Wiring Harness Connector. See page 40.
2 Wi-Fi antenna connector. See page 47.
3 Cellular antenna connector. See page 47
4 GPS antenna connector. See page 47
5 XBee antenna connector (ConnectPort X5 R) or Satellite antenna connector
(ConnectPort X5 R Iridium).
See page 47
6 SIM card slot. See page 53.
7 Mounting holes. See page 54.
8 LED status indicators. See page 289.
37
Page 38

ConnectPort X5 R and ConnectPort X5 Kit hardware summary
ConnectPort X5 R models
ConnectPort X5 R is a production unit. Digi installs customer-specific SIM cards into each unit and
ensures that the unit is environmentally sealed. Customer are responsible for providing their own
Wiring Harness and antennas; Wiring Harness guidelines are later in this chapter. All connectors
must be sealed to maintain IP67 and other environmental ratings.
ConnectPort X5 development kit models
The ConnectPort X5 development kit models (C onnectPort X5 Kit, Co nnectPort X5 R CDMA Kit,
and ConnectPort X5 R Iridium Kit are development kits for l ab use only. These development kits
contain:
A ConnectPort X5 R/ConnectPort X5 R CDMA, or Connec tPort X5 R Iridium unit, with
a slot for customers to install their own SIM card. See page 53 for SIM card installation
information.
A Wiring Harness and power cord. The development cables provide access to all
interfaces on your device. See page 40 for more information about the Wiring Harness
and interfaces.
Antennas, which vary by kit version, and may include Wi-Fi, Cellular/GPS, XBee, and
Iridium antennas. See page 47 for antenna connections and specifications.
An Installation Guide and links to all documentation needed to being development on
your unit.
The table shows the part numbers for the development cables and antennas. See page 50
for details on antenna connections and specifications.
Description Digi Part Number
X5 development cable 76000781
Wi-Fi antenna 76000783
Cellular (GSM)/GPS antenna
76000801or
76000782
XBee antenna 76000784
Iridium antenna 76000876
38
Page 39

ConnectPort X5 Fleet hardware summary
1
2
ConnectPort X5 Fleet is a production unit with internal antennas . Digi recommends this version of
the product if using a ConnectPort X5 R would require more than 3 meters of cable length. The
customer is responsible for providing t heir own Wiring Harness.
ConnectPort X5 Fleet hardware summary
1 Wiring Harness Connector. See page 40.
2 Mounting holes (on underside of unit). See page 54.
39
Page 40

Interfaces and Wiring Harness guidelines
WIFI CELLULAR GPS SAT
Wiring Harness
Digi does not provide a Wiring Harness for the ConnectPort X5 R or ConnectPort X5 Fleet.
Instead, you must design and create a Wiring Harness t hat follows the guidelines an d pinouts in this
section. Dig The figure shows a Wiring Harness being connected to a ConnectPort X5 R unit.
Interfaces and Wiring Harness guidelines
40
Page 41

Interfaces and Wiring Harness guidelines
ConnectPort X5 Wiring Harness Connector
The Wiring Harness Connector on all ConnectPort X5 models is a 23-pin IP67 connector from
Tyco. The Wiring Harness must use the mating plug and pins listed in the following table to
connect to the ConnectPort X5 R device.
ConnectPort X5 R 23-pin Connector and Mating Connector Part Numbers
Part Tyco Part Number
Wiring Harness Connector Header 1-776087-1
Wiring Harness Connector Housing 770680-1
Wiring Housing Connector Wire Relief 776464-1
Wiring Housing Connector Pins 770854-3
Wiring Housing Connector Plugs 770678-1
Wiring Housing Connector Crimper 58529-1
The connector pins accept 20-16AWG wire.
If the rubber seal of the mating connector is accidently perforated in an unpopulated location
during cable assembly, the hole can be filled with a plug if the conn ector needs to ma intain an IP67
rating.
The Wiring Harness should be restrained every 7-9” to prevent vibration-related damage.
The recommended minimum cable bend radius is five times the cable diameter.
Use dielectric grease on the main connector contacts when connecting your Wiring Harness to the
ConnectPort X5 R to prevent fretting on the contacts.
41
Page 42

Wiring Harness Connector pins
Pins for the Wiring Harness Connector are arranged as follows. Pin 1 is in the upper-left corner.
Interfaces and Wiring Harness guidelines
42
Page 43

Pinouts
Interfaces and Wiring Harness guidelines
Pinouts for the ConnectPort X5 R and ConnectPort X5 Fleet are as follows.
Pin # Signal Name
1 Digital Ground
2 NC, for internal Digi use
3Serial RXD
4Serial RTS
5 J1708-
6CAN_L
7Ethernet TX-
8Ethernet RX-
9 Chassis Ground
10 Serial TXD
11 Serial CTS
12 J1708+
13 CAN_H
14 Ethernet TX+
15 Ethernet RX+
16 Vin
17 Ignition
18 Reset
19 DIO0
20 DIO1
21 DIO2
22 DIO3
23 NC
43
Page 44

Available interfaces on the Wiring Harness
Serial
Chassis ground
CAN/J1939
J1708
Ignition sense line
Digital I/O lines
Ethernet
Reset
Power/ digital ground
Wiring Harness Connector
The figure shows the interfaces available on the Wiring Harness. Details about each interface
follow.
Interfaces and Wiring Harness guidelines
5-wire RS-232 serial (TXD, RXD, RTS, CTS, GND)
Serial signals TXD, RXD, RTS, CTS, GND are supported. See the pinout on page 43 for the pins
used for these signals. The serial drain wire should be connected to chassis ground.
CAN/J1939
Please refer to the CAN/J1939 specification for proper wiring. The ConnectPort X5 R assumes that
it is plugged into a terminated bus that meets all CAN/J1939 specifications and requirements.
J1708
Please refer to the J1708 specification for proper wiring. The ConnectPort X5 R assumes that it is
plugged into a terminated bus that meets all J1708 specifications and requirements.
Ignition sense line
An ignition sense line, part of the power management strategy, is used to unconditionally wake a
device from a low-power state. To support ignition detect, the ignition pin must be wired into the
vehicle’s ignition detect signal. This pin has a digital input signal for detecting ignition supply
voltage. Voltage range: 0 to +4 8VDC. The pin has protection for short, positive, and negative
overvoltage conditions. VIH = 7V, VIL = 2V.
Power/digital ground
Power and digital ground should be twisted pair and mu st be connected to a fused power supply.
See hardware specs for required voltages and current draw.
44
Page 45

Four digital input/output lines
ConnectPort X5 R has four digital input/output lines. Note that the input and output functions are
shared. The default state of the pins is input.
An external pull-up resistor (~10k) must be used when the sinkin g output drivers are enabled.
The sinking outputs are protected against steady state over-current condi tions by an in-line, self-
resettable fuse.
The table lists specifications for these lines.
Digital mode Specification Value
Digital Input Input type Non-inverting Schmidt trigger
Interfaces and Wiring Harness guidelines
gate
Positive-going switching
~1.6 VDC
threshold
Negative-going switching
~1.0 VDC
threshold
Maximum safe input +30 VDC
Minimum safe input -.5 VDC
Input impedance 1 Megaohm
Default level when no input
Low
applied
Digital Output Output type Open collector sinking driver
Maximum sink current 0.5 ADC
Maximum off voltage +30 VDC
Minimum safe input -.5 VDC
Resistor pull-ups External pull-up required
Note: Exceeding the maximum or minimum safe input values will result in damage to the unit.
45
Page 46

Ethernet
Chassis ground
Reset
Interfaces and Wiring Harness guidelines
The Ethernet cable must conform to networking cable specifications. The Ethernet drain wire
should be connected to chassis ground.
To provide chassis isolation, the metal enc losu r e and di git al ground are not directly tied. The main
reason for this is to avoid potentially large vehicle return currents from flowing through digital
ground, if the product is mounted directly to a vehicle chassis. To prevent static charge build-up,
the two grounds are connected through a high value resistance, to create a discharge path. The
chassis ground should also be connected to the serial and Ethernet drain wires.
A reset pin is available but limited to voltage range 0 to +36VDC. The input structure uses a
Schmitt trigger with VT+ = 1.5V (typ) and VT- = 1V (typ). Digi does not recommend adding this
reset pin to your Wiring Harness. For more information on use of this reset pin and the available
options for performing a reset, see "Restore a device configuration to factory defaults" on page
246.
46
Page 47

Antennas
WIFI CELLULAR GPS SAT
To Cellular
connector
To GPS
connector
Wi-Fi
Antenna
Cellular/GPS
Antenna
XBee
Antenna
ConnectPort X5 R antennas
The ConnectPort X5 R has four antenna options: Wi-Fi, Cellular and GPS, and XBee. The order of
those antennas is shown in the following diagram. The antennas must be mounted at least 8 inches
(20 cm) apart. If your application requires antenna cables longer than 3 meters, Digi recommends
the ConnectPort X5 Fleet product instead. That product has internal antennas so antenna
performance will not be significantly degraded due to long cables.
Antenna locations
Antennas
47
Page 48

ConnectPort X5 R CDMA antennas
WIFI CELLULAR GPS SAT
To Cellular
connector
To GPS
connector
Wi-Fi
Antenna
Cellular/GPS
Antenna
XBee
Antenna
The ConnectPort X5 R CDMA has four antenna options: Wi-Fi, Cellular and GPS, and XBee. The
order of those antennas is shown in the following diagram. The antennas must be mounted at least
8 inches (20 cm) apart. If your application requires antenna cables longer than 3 meters, Digi
recommends the ConnectPort X5 Fleet product instead. That product has inte rnal antennas so
antenna performance will not be significantly degraded due to long cables.
Antenna locations
Antennas
48
Page 49

ConnectPort X5 Iridium antennas
WIFI CELLULAR GPS SAT
To Cellular
connector
To GPS
connector
Wi-Fi
Antenna
Iridium
Antenna
Cellular/GPS
Antenna
The ConnectPort X5 R Iridium has four antenna options: Wi-Fi, Cellular and GPS, and Iridium.
The order of those antennas is shown in the following diagram. The antennas must be mounted at
least 8 inches (20 cm) apart. If your application requires antenna cables longer than 3 meters, Digi
recommends the ConnectPort X5 Fleet product instead. That product has inte rnal antennas so
antenna performance will not be significantly degraded due to long cables.
Antenna locations
Keep Cellular/GPS antenna at least one foot (30.48 cm) away from metal objects.
Cellular/GPS antenna must be mounted on a plastic or glass surface.
Antennas
ConnectPort X5 Fleet antennas
All antennas are built into the product.
49
Page 50

Certified antennas and specifications
The following antennas were used during certification of ConnectPort X5 products and are
included with the ConnectPort X5 development kit products. Y ou must procure your own antennas
for the non-development kit produc ts. If choosing to use othe r antennas than these, ch oose antennas
that conform to these specifications.
Antennas
Antenna Manufacturer Manufacturer
part number
Wi-Fi Taoglas
http://
www.taoglas.com
Cellular /
GPS
Taoglas MA.208.A3011
WS.01.301351 76000783 Frequency range 2400-2500 MHz
11.B30511
Digi part
number
76000801 Frequency range GSM: 880-960 MHz
Specification Value
5150-5350 MHz
Gain 4.1 dB @2400 MHz
4.7 dB @5000 MHz
Antenna size Height: 1.14 in (2.9 cm)
Diameter: 2.05 in (5.21 cm)
Mounting
method
Cable length 9.84 feet (3 meters)
Connector type RP-TNC
Gain Cellular antenna:
18 mm screw mount (.3149 in)
PCS: 1850-1990 MHz
Average: -3.03dBi at 700 –
960MHz
-4.34dBi at 1710 – 2170MHz
Peak: 2.16dBi at 700 – 960MHz
0.42dBi at 1710 – 2170MHz
GPS antenna: 3.5dBic typ @
Zenith
50
Antenna size Length: 7.9 in (20.05 cm)
Width: 2.6 in (6.65 cm)
Height: 0.35 in (0.9 cm)
Mounting
method
Cable length 9.84 feet (3 meters)
Connector type Cellular: TNC (standard polarity
Adhesive mount
TNC)
GPS: RP-TNC (reverse polarity
TNC)
Page 51

Antennas
Antenna Manufacturer Manufacturer
part number
Cellular /
GPS
Taoglas
MA.104.A.A301
351.B301311
Digi part
number
76000782
Specification Value
Frequency range
Quad band;
CDMA: 824-896 MHz
GSM: 880-960 MHz
PCS: 1850-1990 MHz
DCS: 1710-1880 MHz
Gain Cellular antenna:
30 dB typical
Gain at Zenith: 2. dBi min
Gain at 10 degrees elevation:
-4.0 dBi minimum
Axal ratio: 2.0 dB maximum
GPS antenna: 3.5dBic typ @
Zenith
Antenna size
Height: 1.14 in (2.9 cm)
Diameter: 2.05 in (5.21 cm)
Mounting
method
3.149 in (18 mm) screw-in
dipole mount
Cable length 9.84 feet (3 meters)
Connector type
Cellular: TNC (standard
polarity TNC)
GPS: RP-TNC (reverse
polarity TNC)
51
Page 52

Antennas
Antenna Manufacturer Manufacturer
part number
XBee Laird RD2458-5-RA-
TNC
Bobbintron AN2400-
19B01RART
Digi part
Specification Value
number
76000784 Frequency range 2400 - 2483 MHz
Gain 3 dBi @ 2400 MHz
5 dBi @ 5000 MHz
Antenna size 6.8 in (17.27cm)
Mounting
N/A
method
Connector type RP-TNC
76000784 Frequency range 2400-2500 MHz
Gain 3 dBi
Antenna size 6.8 in (17.27cm)
Mounting
method
3.149 in (18 mm) screw-in dipole
mount
Connector type RP-TNC
Iridium Use an Iridium antenna that has been certified for use with the Iridium network to maintain certifications.
52
Page 53

SIM card installation
WIFI CELLULAR GPS SAT
For models without an accessible SIM slot
Models without an accessible SIM slot are sealed during manufacturing to retain their IP67 rating.
Digi installs a customer-provided SIM card prio r to shipping . This SIM card cannot be accessed in
the field. High-temperature SIM cards are recommended to ensure cellular connectivity throughout
the lifetime of the product.
Note: CDMA models do not have a SIM card.
For models with an accessible SIM slot
Several ConnectPort X5 models have a slot to al low p rod uct o wners to insta ll a SIM card . The sl ot
and SIM card orientation are shown below. Remove the rubber plug, if provided, and insert the
SIM card. The metal contacts on the SIM card should be facing down, and the chamfered edge
should be inserted first. High-temperature SIM cards are recommended to ensure cellular
connectivity throughout the lifetime of the product.
SIM card installation
SIM card activation
The SIM card must be activated for cellular service. Contact your mobile service provider and see
"Mobile (cellular) settings" on page 112.
53
Page 54

Mounting the ConnectPort X5 to a vehicle
ConnectPort X5 R and X5 Iridium
The ConnectPort X5 R has flexible mounting holes to allow installation in a variety of locations to
many different surface materials. The illustration shows mounting-hole locations and dimensions.
Mounting the ConnectPort X5 to a vehicle
Use at least four (4) ¼” bolts to mount the ConnectPort X5 R unit. The ConnectPort X5 R unit is
IP67 rated; allowing for it to be mounted inside or outside. The ConnectPort X5 R enclosure is
made of CEP-coated aluminum, and the TNC connectors and nuts are made of nickel-plated brass.
The ConnectPort X5 Main Connector and TNC connectors must be mated to maintain IP67 rating.
The product is not to be installed on a dashboard or on the lower-chassis of a vehicle.
54
Page 55

ConnectPort X5 Fleet
2.71 2.90
11.17
3.20 3.76
2.50
2.40
Thread depth
.375 in (0.952 cm)
Use 1/4-28 stainless steel bolts
Standoff height
0.625 in (1.587 cm)
The ConnectPort X5 Fleet has mounting holes to allow install ation in a variety of locatio ns to many
different surface materials. The illustration shows mounting-hole locations and dimensions.
Mounting the ConnectPort X5 to a vehicle
Use eight 1/4-28 stainless steel bolts to mount the ConnectPort X5 Fleet unit. Use a bolt length
such that the bolt does not penetrate into the Conne ctPort X5 Fleet unit by more than a thread de pth
of .375 in (0.952 cm).
The ConnectPort X5 Fleet unit is IP67 rated; allowing for it to be mounted inside or outside.
55
Page 56

Satellite setup
ConnectPort X5 R Iridium
The Iridium satellite network must be provisioned, or prepared to communicate with the
ConnectPort X5 R Iridium device. To provision your ConnectPort X5 R Iridium device, you will
need to work with your Iridium representative and have the Internati onal Mobile Equipment
Identity or IMEI number for the satellite modem. The IMEI number for the satellite modem is on
the label of the unit with the other identifier numbers for the device.
Management of the Iridium satellite modem is perfo rmed from the command line inte rface by these
commands: iridium, display iridium, and info iridium. See the Digi Connect Family Command
Reference for descriptions of these commands.
ConnectPort X5 ORBCOMM-equipped models
For ConnectPort X5 models equipped with an ORBCOMM satellite modem, there is no web
interface page for configuration. Configuration and ma na geme nt of the OR BCO MM satellite
modem are performed from the command line interface by these commands: set orbcomm,
display orbcomm, info orbcomm, and orbcomm. command. See the Digi Connect Family
Command Reference for descriptions of these commands.
Satellite setup
56
Page 57

Configuration
CHAPTER 3
This chapter describes how to configure a Digi device. It covers these topics:
"IP address assignment" on page 58
"Configuration through Device Manager" on page 60
"Configuration through the web interface" on page 61
"Configuration through the command l ine" on page 197
"Configuration through Simple Network Management Protocol (SNMP)" on page 200
"Batch capabilities for configuring multiple devices" on page 200
57
Page 58

IP address assignment
Default IP address and DHCP settings
All products that have a cellular (WAN) interface ship with static IP address for the Ethernet port
of 192.168.1.1 and DHCP server enabled by default. Plugging the ConnectPort X5 device into a
switch or network to which a laptop computer is connected allows direct access to the web
interface for configuration. The Ethernet port of the laptop should be configured to automatically
receive an IP address and DNS server address.
All products that only have an Ethernet or Wi-Fi (LAN) interface ship with DHCP client enabled
by default. Accessing the web interface on these products is most easily done by connecting it to a
LAN that has a DHCP server.
T o discover which IP address has been assigned to the device, use the Device Discovery Utility for
Windows, available on the Digi Support site. See installation instructions on page 61.
Alternative methods of assigning IP addresses
IP address assignment
There are several methods to assign an IP address to a Digi device, described on the following
pages:
Use Dynamic Host Configuration Protocol (DHCP) from the web interface.
Use Automatic Private IP Addressing (APIPA), also known as Auto-IP.
Configure an IP address using DHCP
An IP address can also be configured using Dynamic Host Configuration Protocol (DHCP). DHCP
is an Internet protocol for automating the configuration of computers that use TCP/IP. DHCP can
be used to automatically assign IP addresses and deliver TCP/IP stack configuration parameters.
As mentioned previously, all products that have a cellular (WAN) interface ship with static IP
address for the Ethernet port of 192.168.1.1 and DHCP server enabled by default . All products that
only have an Ethernet or Wi-Fi (LAN) interface ship with DHCP client enabled by default.
For more information on DHCP server configuration, see "DHCP server settings" on page 74.
58
Page 59

Configure an IP address using Auto-IP
The standard protocol Automatic Private IP Addressing (APIPA or Auto-IP) automatically assigns
the IP address from a group of reserved IP addresses to the device on which Auto-IP is installed.
Use Digi Device Discovery or DHCP to find the Digi device and assign it a new IP address that is
compatible with your network. Once the unit is plugged in, Auto-IP automatically assigns the IP
address. Auto-IP addresses are typically in the 169.254.x.x address range.
Test the IP address configuration
Once the IP address is assigned, make sure it works as configured.
1 Access the command line of a PC or other networked device.
2 Issue the following command:
ping ip-address
where ip-address is the IP address assigned to the Digi device. For example:
ping 192.168.2.2
IP address assignment
59
Page 60

Configuration through Device Manager
Configuration through Device Manager
Device Manager is an on-demand service. After creating a Device Cloud account, you can connect
to Device Manager. There are no infrastructure requirements. Remote devices and enterprise
business applications connect to Device Manager via standards-based Web Services.
For details on using Device Cloud as a management interface, creating a Device Cloud account
and add your ConnectPort X Family device to the Device Manager device list so it can be managed
from that interface, see the Device Cloud User’s Guide.
Device Cloud device management through Short Message Service (SMS) commands
Digi devices can be configured to be managed by Device Cloud through Short Message Service
(SMS) commands. See "Users settings" on page 181.
60
Page 61

Configuration through the web interface
Configuration through the web interface
Open the web interface
To open the web interface, either enter the Digi device’s URL in a web browser and log on to the
device, if required, or use the Digi Device Discovery utility to locate it and open its web interface.
By entering the Digi device’s IP address in a web browser
1 In the URL address bar of a web browser, enter the IP address of the device.
2 If security has not been enabled for the Digi device, the Home page of the web interface is
displayed. If security has been enabled for the Digi device, a login dialog will be displayed.
Enter the user name and password for the device. The default username is root and the
default password is dbps. If these defaults do not work, contact the system administrator
who set up the device. Then the Home page of the web interface is displayed. See
"Organization of the web interface" on page 63 for an overview of using the Home page and
other linked pages.
By using the Digi Device Discovery utility
Alternatively, use the Digi Device Discovery Utility to locate the Digi device and open its web
interface.
Install and run the Digi Device Discovery utility
The Digi Device Discovery Utility is available for downloading from the Digi Support site.
If this utility is not already available on your computer, follow these steps.
1 Fro m a browser, go to www.digi.com.
2 Cl ick th e Support link and select Diagnostics, Utilities and MIBs.
3 Und er Select Your Product for Support, select your Digi device from the product list
and click Submit.
4 Und er Active Products, select your Digi device from the product list.
5 Und er OS Specific Diagnostics, Utilities and MIBs, select the operating system for
your computer from the list.
6 Select either Device Discovery Utility for Windows - Standalone version or
Device Discovery Utility for Windows - Installable version. The standalone version runs
the utility immediately after the download is complete. The installable version installs the
utility on your computer and adds it to a program group named Dig i i n the Start menu.
7 Cl ick Run on the two dialogs. The standalone version of the utility starts immediately.
For the installable version, an installation wizard is displayed. Follow the prompts to
complete the installation. To start the utility, select
Start > Programs > Digi > Digi Device Discovery > Digi Device Discovery
61
Page 62

Discover devices
Configuration through the web interface
From the start menu, select Start > Programs > Digi Connect > Digi Device Disc overy. The Digi
Device Discovery application is displayed.
Locate the device in the list of devices, and double-click it, or select the Digi device from the list
and select Open web interface in the Device Tasks list.
62
Page 63

Organization of the web interface
The Home page
When the web interface is opened, the Home page is displayed. Here is a home page for a
ConnectPort X5 Family product.
Configuration through the web interface
The left side of the Home page has a menu of choices that display pages for configuration,
management, and administration tasks, and to log out of the web interface. This chapter focuses on
the choices under Configuration and Applications. For details on the tasks under
Administration, see Chapter 5, "Device administration".
Clicking Logout logs out of a configuration and management session with a Digi device. It does
not close the browser window, but displays a logout window. To finish logging out of the web
63
Page 64

interface and prevent access by other users, close the browser win dow. Or, log back on to the
device by clicking the link on the screen. After 5 minutes of inactivity, the idle timeout also
automatically performs a user logout.
The Getting Started section has a link to a tutorial on configuring and managing Digi device.
The System Summary section notes all available device-description information.
Configuration pages
The choices under Configuration in the menu display pages for configuring settings for various
features, such as network settings, and serial port settings. Some of the configuration settings are
organized on sets of linked screens. For example, the Network Configuration screen initially
displays the IP Settings, and provides links to Network Services Settings, Advanced Settings, and
other network settings appropriate to the Digi device.
Applications pages
Depending on the Digi device, there may be an Applications menu item for configuring various
applications available for use in the device.
Configuration through the web interface
Python: For loading and running custom programs authored in the Python
programming language onto ConnectPort X Family devices.
RealPort: Configures RealPort settings. See page 195.
Apply and save changes
The web interface runs locally on the device, w hic h means that the inte rface always maintains and
displays the latest settings in the Di gi device. On e ach screen, the Apply button is used to save an y
changes to the configuration settings to the Digi device.
Cancel changes
To cancel changes to configuration settings, click the Refresh or Reload button on the web
browser. This causes the browser to reload the page. Any changes made since the last time the
Apply button was clicked are reset to their original values.
Restore the Digi device to factory defaults
The device configuration can be reset to factory defaults as needed during the configuration
process. See "Restore a device configuration to factory defaults " on pa ge 24 6.
Online help
Online help is available for all screens of the web interface, and for common configuration and
administration tasks. There is also tutorial available on the Home page.
64
Page 65

Configuration through the web interface
Change the IP address from the web interface, as needed
Normally , IP addresses are assigned to Digi devices either through DHCP or the Digi Device Setup
Wizard.
This procedure assumes that the Digi device already has an IP address and you simply want to
change it.
1 Open a web browser and enter the Digi device’s current IP address in the URL address bar.
2 If security is enabled for the Digi device, a login prompt is displayed. Enter the user name
and password for the device. The default username is root and the default password is dbps.
If these defaults do not work, contact the system administrator who set up the device.
3 Cl ick Network to access the Network Configuration page.
4 On th e IP Sett ings page, selec t Use the following IP address.
5 Enter an IP address (and other network settings), then click Apply to save the configuration.
65
Page 66

Network configuration settings
The Network configuration pages include:
Ethernet IP settings: For viewing IP address settings and changing as needed. See
page 69.
WiFi IP settings: For setting the IP address used for wireless LAN communication. See
page 70.
WiFi LAN settings: For setting basic options for wireless LAN devices such as
network name and network connection options. See page 70.
WiFi Security settings: For setting authentication and encryption options for wireless
LAN devices. See page 71.
WiFi 802.1x Authentication setti ngs: Detailed authentication settings for IEEE 802.1x
authentication for wireless LAN devices. See page 73.
DHCP Server settings: For configuring a DHCP server to allow other devices or hosts
on this network to be assigned dynamic IP addresses. See page 74.
Network Services settings: Enable and disables access to variou s netw ork servi ces,
such as ADDP, RealPort and Encrypted RealPort, Telnet, HTTP/HTTPS, and other
services. See page 78.
Configuration through the web interface
Dynamic DNS Update settings: For configuring a Dynamic DNS (DDNS) service that
allows a user whose IP address is dynamically assigned to be located by a host or
domain name. See page 81.
IP Filtering settings: For configuring the Digi Cellular Family device to only accept
connections from specific and known IP addresses or networks. See page 84.
IP Forwarding settings: For configuring the Digi Cellular Family device to forward
certain connections to other devices. This is also known as Network Address
Translation (NAT) or Port Forwarding. See page 85.
IP Network Failover settings: provides a dynamic method for selecting and
configuring the default gateway for the Digi device using a set of rules and link tests to
determine whether a particular network interface can be used to communicate with a
specified destination. See page 88.
Socket Tunnel settings: For configuring a socket tunnel, used to connect two network
devices: one on the Digi Cellular Family device’s local network and the other on the
remote network. See page 92.
Virtual Private Network (VPN) settings: For configuring Virtual Private Networks,
which are used to securely connect two private networks together so that devices may
connect from one network to the other network using secure channels. See page 93.
IP Pass-through settings: Configures a Digi Cellular Family device to pass its mobile
IP address directly through and to the Ethernet device (router or PC) to which it is
connected through the Ethernet port. The Digi Cellular Fam il y device becomes
transparent (similar to the behavior of a cable or DSL modem) to provide a bridge from
the mobile network directly to the end device attached to the Digi Cellular Family
device. See page 102.
66
Page 67

Configuration through the web interface
Host List settings: Adds or removes entries from the host list. For DialServ, the host list
provides a means to map a phone number (in the local name field) to a network
destination, (in the “resolves_to” field). See page 105.
Virtual Router Redundancy Protocol (VRRP) settings: For configuring a number of
routers to represent a virtual router, which simplifies configuration of hosts on a
network.
Advanced Network Settings: Configures the Ethernet Interface speed and mode, TCP/
IP settings, TCP keepalive settings, and DHCP settings. See page 107.
67
Page 68

Configuration through the web interface
Alternatives for configuring network communications
There are three ways a Digi device can be configured on the network.
Using dynamic settings: All network settings will be assigned automatically by the
network, using a protocol called DHCP. Contact your network administrator to find out
if a DHCP server is available.
Using static settings: All network settings are set manually and will not change. The IP
address and subnet mask are mandatory. The rest are not mandatory, but may be needed
for some functions. Contact your network administrator for the required values.
Using Auto-IP: Auto-IP assigns an IP address to the Digi device immediately after it is
plugged in. If running DHCP or ADDP, the Auto-IP address is overridden and a network
compatible IP address is assigned, or a static IP address can be assigned.
Even if a DHCP server is available, the device configuration may work better with static settings.
Once set, static settings will not change, so yo u and other network devices can always find th e Digi
device by its IP address. With dynamic settings, the DHCP server can change the IP address. This
can happen frequently or infrequently depending on how your network administrator has
configured the network.
When the IP address does change, you and other network devices configured to talk to the Digi
device can no longer access the device. In this case, the Digi device must be located the Digi
Device Discovery utility, and other network devices that need to communicate with the Digi device
must be reconfigured.
68
Page 69

Ethernet IP settings
The Ethernet IP Settings page configure how the IP address of the Digi device is obtained, either
by DHCP or by using a static IP address, subnet mask, and default gateway. For more information
about how these settings are assigned and used in your organization, contact your network
administrator.
Obtain an IP address automatically using DHCP: When the Digi device is rebooted,
Use the following IP Address: Choose this option to supply static settings. An IP
IP Address: An IP address is like a telephone number for a computer. Other network
Subnet Mask: The Subnet Mask is combined with the IP address to determine which
Configuration through the web interface
it will obtain new network settings.Use the Digi Device Setup Wizard to find the Digi
device, since it will likely have a new address.
address and Subnet mask must be entered. Other items are not mandatory, but may be
needed for some functions (such as talking to other networks).
devices talk to this Digi device using this ID.
The IP address is a 4-part ID assigned to network devices. IP addresses are in the form
of 192.168.2.2, where each number is between 0 and 255.
network this Digi device is part of. A common subnet mask is 255.255.255.0.
Default Gateway: IP address of the computer that enables this Digi device to access
other networks, such as the Internet.
Enable AutoIP address assignment: With AutoIP enabled, the Digi device will
automatically self-configure an IP address when an address is not available from other
methods, for example, when the Digi device is configured for DHCP and a DHCP
server is not currently available.
69
Page 70

WiFi IP settings
The WiFi IP settings configure how the IP address of a Wi-Fi-enabled Digi device is obtained. It
has the same settings as the Ethernet IP settings page.
WiFi LAN settings
Digi devices with Wi-Fi (wireless LAN) capability contain a wireless network interface that may
be used to communicate to wireless networks using 802.11b/g technology. Contact your
administrator or consult wireless access point documentation for the settings required to setup the
wireless LAN configuration. Settings include:
Network name: The name of the wireless network to which the wireless device should
Connection method: The type of connection method this device uses to communicate
Configuration through the web interface
connect. In situations with multiple wireless networ ks, thi s settin g all ows the dev ice to
connect to and associate with a specific network. Th e network n ame is referred to as the
SSID (service set identifier). If the network name is left blank, the device will search for
wireless networks and connect to the first available network. This is useful if a specific
network name does not need to be used as the device will select the first available
network.
on wireless networks. Choose from:
– Connect to any available wireless network: Use this setting to allow the device to
access any network. The device can either access point networks or peer-to-peer
wireless networks.
– Connect to access point (infrastructure) networks only: Use this setting if the
wireless network that this device needs to connect to is composed of wireless access
points. This is typically the most popular method for connecting to wireless networks.
– Connect to peer-to-peer (ad-hoc) networks only: Use this setting if a ll dev ices on the
wireless network connect to and communicate with each other. This is known as peer-
to-peer in that there is no central server or access point. Each system communicates
directly with each other system.
Country: The country in which this wireless device is being used. The channel settings
are restricted to the legal set for the selected country.
Channel: The frequency channel that the wireless radio will use. Select Auto-Scan to
have the device scan all frequencies until it finds one with an available access point or
wireless network it can join.
Transmit Power: The transmit power level in dBm.
Enable Short Preamble: Enables transmission of wireless frames using short
preambles. If Short Preamble is supported in the wireless network, enabli ng it c an boost
overall throughput.
70
Page 71

WiFi security settings
The WiFi security settings specify the wireless security settings that the wireless network uses.
Multiple security and authentication modes may be chosen depending on the configuration of the
access point or wireless network. The wireless device will automatically select and determine the
authentication and encryption methods to use while associating to the wireless network. If the
wireless network does not use security and uses an Open Network architecture, these settings do
not need to be modified.
Note that WPA settings require that the device communicate to Access Points and is not valid
when the Connection Method is set to Connect to wireless systems using peer-to-peer
(ad-hoc). Also, WPA pre-shared key (WPA-PSK) security is only valid when a specific
Network Name or SSID is being used.
Network Authentication: The authentication method or methods used for wireless
communications.
–
–
Configuration through the web interface
Use any available authentication method: Enables all of the methods. The
actual method used will be determined by the capabilities of the wire less net wo r k.
Use the following selected method(s): Selects one or more authentication
methods for wireless communications.
Open System: IEEE 802.11 open system authentica tion is u sed to estab lish a
connection.
Shared Key: IEEE 802.11 shared key authentication is used to establish a
connection. At least one WEP key must be specified in order to use sh ared key
authentication.
WEP with 802.1x authentication: IEEE 802.1x authentication (EAP) is used to
establish a connection with an authentication server or access point. Wired
Equivalent Privacy (WEP) keys are dynamically generated to encryp t da ta over the
wireless network.
WPA with pre-shared key (WPA-PSK): The Wi-Fi Protected Access (WPA)
protocol is used with a pre-shared key (PSK). The PSK is calculated using a
passphrase and the network SSID.
WPA with 802.1x authentication: The WPA protocol and IEEE 802.1x
authentication (EAP) is used to establish a connection with an authentica tion se rver
or access point. Encryption keys are dynamically generated to encrypt data over the
wireless link.
Cisco LEAP: Lightweight Extensible Authentication Protocol (LEAP) is used to
establish a a connection with an authentication server or access point. Wired
Equivalent Privacy (WEP) keys are dynamically generated to encryp t da ta over the
wireless link. A user name and password must be specified to use LEAP.
71
Page 72

Configuration through the web interface
Data Encryption: Multiple encryption methods can be selected.
Use any available encryption method: enables all of the methods. The actual
–
method used will be determined by the capabilities of the wireless network.
–
Use the following selected method(s): Selects one or more encryption
methods.
Open System: No encryption is used over the wireless link. Open System
encryption is valid only with Open System and Shared Key authentication.
WEP: Wired Equivalent Privacy (WEP) en crypt ion is used ov er the wireless link.
WEP encryption can be used with any of the above authentication methods.
TKIP: Temporal Key Integrity Protocol (TKIP) encryption is used over the
wireless link. TKIP encryption can be used with WPA-PSK and WPA with 80 2.1 x
authentication.
CCMP: CCMP (AES) encryption is used over the wireless link. CCMP can be used
WPA-PSK and WPA with 802.1x authentication.
WEP Keys
– T ransmit Key: Specify the correspond ing key of the encryption key that should be u sed
when communicating with wireless networks using WEP security.
This device allows up to four wireless keys to be set o f either 64-bit or 128-bit
encryption. These keys allow the wireless network to traverse different wireless
networks without having to change the wireless key. Instead, only the transmit key
setting has to be changed to specify which wirele ss k ey t o sen d.
– Encryption Keys: Specify 1 to 4 encryption keys to be used when communicating with
wireless networks using WEP security.
The encryption keys should be a set of 10 (64-bit) or 26 (128-b it) hexadecimal
characters. The encryption key should only contain the characters A-F, a-f, or 0-9.
Optionally, separator characters, such as '-', '_', or '.' may b e used to se parate the set
of characters.
WPA PSK (Pre-Shared Key) Passphrase/Confirm: The passphrase that the Wi-Fi
network uses with WPA pre-shared keys. The pre-shared key is calculated using the
passphrase and the SSID. Therefore, a valid network name must have been previously
specified. In the Confirm field, reenter the passphrase.
Username/Password/Confirm: The username and password combination used to
authenticate on the network when using these authentication methods: WEP with 802.1x
authentication, WPA with 802.1x authentication, or LEAP. In the Confirm field, reenter
the password.
72
Page 73

WiFi 802.1x authentication settings
These settings are not required based on the current Wi-Fi authentication settings. They are only
configurable when WEP with 802.1x authentication or WPA with 802.1x authentication are
enabled on the WiFi Se cu ri ty Settings tab.
EAP Methods: These are the types of Extensible Authentication Protocols (EAP) or
outer protocols that are allowed to establish the in itial connection wit h an authentica tion
server or access point. These are used with WEP with 802.1x authentication and WPA
with 802.1x authentication.
– PEAP: Stands for “Protected Extensible Authentication Protocol.” A username and
password must be specified to use PEAP.
– TLS: Stands for “T ransport Layer Security.” A client certificate and private key must be
installed in order to use TLS.
– TTLS: Stands for “Tunneled Transport Layer Security.” A username and password
must be specified to use TTLS.
PEAP/TTLS Tunneled Authentication Protocols: These are the types of inner
protocols that can be used within the encrypted connection established by PEAP or
TTLS.
These Extensible Authentication Protocols (EAP) can be used with PEAP or TTLS.
Configuration through the web interface
– GTC: Generic Token Card
– MD5: Message Digest Algorithm.
– MSCHAPv2: Microsoft Challenge response Protocol version 2.
– OTP: One Time Password
These non-EAP protocols that can be used with TTLS.
– CHAP: Challenge Response Protocol
– MSCHAP: Microsoft Challenge response Protocol
– TTLS MSCHAPv2: TTLS Microsoft Challenge response Protocol version 2.
– PAP: Password Authentication Protocol
Client Certificate Use: When the TLS is protocol is enabled, a client certificate and
private key must be installed on the Digi device.
– Certificate: Click Browse to select a client certificate file. Then click the next Browse
to select a private key file.
– Private Key File: If the private key file is encrypted, a password must be specified.
Trusted Certificates: Adds and lists trusted certificates.
– Verify server certificates: Enable to verify that certificates received from an
authentication server or access point are signed by a trusted certificate authority (CA).
Standard CAs are built in. Additional trusted certificates may be added.
– T rusted Certificate File: To add add itional trus ted certificates, click Br owse to se lect a
certificate file to upload to the Digi device, then cli ck Upload.
Installed Certificates: Shows which client certificates have been added and are in use.
73
Page 74

DHCP server settings
The DHCP server feature can be enabled in a Digi device to allow other devices or hosts on this
network to be assigned dynamic IP addresses. This DHCP server supports a single subnetwork
scope.
For the DHCP server to operate, the Digi device must be configured to use a static IP address. For
information on how to configure static IP settings, see "Ethernet IP settings" on page 69.
DHCP terminology
Some key DHCP terms involved in configuring a DHCP server include:
scope
A scope is the full consecutive range of possible IP addresses for a network. A scope typically
defines a single physical subnet on your network, to which DHCP services are offered. A scope
is the primary way for the DHCP server to manage distribution and assignment of IP addresses
and related configuration parameters to its clients on the network.
exclusion range
An exclusion range is a limited sequence of IP addresses within a scope, excluded from DHCP
service offerings. Exclusion ranges assure that any addresses in these ranges are not offered by
the server to DHCP clients on your network.
Configuration through the web interface
address pool
After the scope is defined and exclusion ranges are applied, the remaining addresses form the
available address pool within the scope. The addresses in this pool are available for dynamic
assignment by the server to DHCP clients on your network.
lease
A lease is the length of time that the DHCP server specifies, during which a client host can use
an assigned IP address. When the DHCP server grants a lease to a client, the lease is active.
Before the lease expires, the client typic ally needs to renew its address lease assignment with the
DHCP server. A lease becomes inactive when it expires or it is deleted at the server, or if the
client actively releases the lease. The duration of a lease determines when it will expire and how
often the client needs to renew it with the DHCP server in order to retain the lease.
A DHCP server will never grant a lease to its own address. There is no need for its own address
to be in the exclusion range; the DHCP server simply protects its address from bein g offered.
grace period
When a DHCP client actively releases a lease, or when the lease expires without being re newed
by the client, the DHCP server does not immediately delete the lease record and return the
associated IP address to the available address pool. A grace period is the interval of time for
which the lease record is retained before the DHCP server automatically deletes the record from
its lease list, thereby making the IP address available for lease assignment to another client . The
grace period is not a configurable value. See also the discussion of the grace period and what it
means when the DHCP server is running in "View and manage current DHCP leases" on page
223.
74
Page 75

reservation
You may use a reservation to create a permanent address lease assignment by the DHCP server.
Reservations assure that a specified hardware device on the subnet can always use the same IP
address. Address lease reservations associate a specific IP address with a specific client's
Ethernet MAC address.
options
Options are other client configurati on parameters that the DHCP server c an assign when serving
leases to DHCP clients. Most options are defined in RFC 2132. The DHCP server in the Digi
device supports a limited set of options:
– Option 3: Routers on Subnet
– Option 6: DNS Servers
Addresses in the DHCP server settings
The IP address and subnet mask of the DHCP server's scope are the static IP configuration settings
for the Digi device itself.
The default gateway (router) provided to a client with the lease information is the IP address of the
Digi device.
Configuration through the web interface
The DNS servers provided to a client with the lease information are the DNS server addresses
configured in the Digi device. These addresses include any DNS server addresses that the Digi
device acquires when it connects to the mobile network.
75
Page 76

DHCP server configuration settings
Here are the configuration settings for the DHCP server. Typically, these settings can be modified
without having to restart the DHCP server for the changes to become effective in the running
server.
Enable Dynamic Host Configuration Protocol (DHCP) Server: Enables the DHCP
server feature on this Digi device. Note that for the DHCP server to operate, the Digi
device must be configured to use a static IP address. For information on how to
configure static IP settings, see "Ethernet IP settings" on page 69.
– Scope Name: The name of the physical network interface associated with the subnet
being served by the DHCP Server. Most Digi device models have a single network
interface, so there is no choice for the scope name. For models that have multiple
network interfaces, such as an Ethernet interface and a Wi-Fi (802.11) interface, this
DHCP Server may be configured to provide services on either of those interfaces.
– IP Addresses: The starting and ending IP addresses for the scope being served by this
DHCP server. These addresses must be in the same subnet as the Digi device itself.
– Lease Duration: The length of the leases for the scope being served by this DHCP
server. The default lease duration is 24 ho urs. A DH CP clien t ma y request a lease
duration other than this setting, and the DHCP server will grant that request if possible.
Configuration through the web interface
Wait specified delay before sending DHCP offer reply: The interval of time in
milliseconds to delay before offerin g a lease to a new client. The default delay is 500ms,
and the range is 0 to 5000ms. Use of this delay permits this Digi device to reside on a
network with other DHCP servers, yet not offer leases to new clients unless the other
DHCP servers do not make such an offer. This provides a measure of protection against
inadvertently connecting a Digi device to a network that is running its own DHCP
server(s), and offering leases to clients in a manner inconsistent with that network.
Check that an IP address is not in use before offering it: When a DHCP client
requests a new IP address lease, before offering an IP address to that client, use “ping”
to test whether that IP address is already in use by another host on the network but is
unknown to the DHCP server. If an IP address is determined to be i n use, it is marked as
Unavailable for a period of time, and it will not be offered to any client while in this
state. Enabling this test adds approximately one second of del ay before th e IP address is
offered to the client, since the “ping” test must not receive a valid reply for that test to
successfully determine that the IP address is not already in use. This option is off
(disabled) by default. This option does no t a pp ly to Static Lease Reservations, since th e
“ping” test is not used for them.
76
Page 77

Configuration through the web interface
Send the DHCP Server IP address as a DNS Proxy Server: This option configures
the DHCP Server to send its IP address to a DHCP client as the first DNS server in its
lease information. This Digi device supports a DNS Proxy featur e that will relay DNS
requests and responses between DNS clients and servers. The DNS Proxy is not a
feature of the DHCP Server itself, but rather it is managed elsewhere in the
configuration settings for this Digi device. For DNS Pro xy to be used effectively by a
DHCP client, it must be enabled both in the DHCP server configurati on and in the DNS
Proxy settings. For more information, see the description of the Enable DNS Proxy
Service setting in "Advanced network settings" on page 107. This option is on (enabled)
by default.
– Static Lease Reservations: A static lease reservation is a specific IP address paired
with a client's MAC address, which reserves the IP address for that client's use only.
This assures that a client always receives a lease for the same IP address and that no
other client obtains a lease for that address.
To add a reservation, enter the IP address and MAC Address values, check or clear
the Enable checkbox, and then press the Add button.
After adding a reservation, you may click on the IP add ress or MAC address of that
entry in the table, permitting you to specify or modify the lea se du rat ion fo r this
reservation.
The Enable checkbox for the entry permits a reservation to be disabled without
actually removing the entry, then enabled again at a later time.
– Address Exclusions: A specific set of IP addresses to exclude from the scope. The
Apply button: You must click the Apply button to save changes you make to the
DHCP server settings. If you leave this page without applying the changes, those
changes will be discarded.
Manage the DHCP server
The Remove link is used to permanently remove a reservation from the DHCP
server configuration.
The Remove All link is used to permanently remove all reservations from the
DHCP server configuration.
DHCP server will not grant leases to clients for any IP address in the exclusion range.
To add an exclusion, enter the starting and ending IP addresses, check or clear the
Enable checkbox, and then press the Add button.
The Enable checkbox for the entry permits an exclusion to be disabled without
actually removing the entry, then enabled again at a later time.
The Remove link is used to permanently remove an exclusion from the DHCP
server configuration.
The Remove All link is used to permanently remove all exclusions from the DHCP
server configuration.
To manage the DHCP server and view/manage lease status, go to
Management > Network Services. See "Manage DHCP server operation" on page 223.
77
Page 78

Network services settings
The Network Services page shows a set of common network services that are available for Digi
devices, and the network port on which the service is running.
Common network services can be enabled and disabled, and the TCP port on which the network
service listens can be configured. Disabling services may be done for security purposes. That is,
certain services can be disabled so the device ru ns only those services specifically needed. To
improve device security, non-secure services such as Telnet can be disabled.
It is usually best to use the default network port numbers for these services because they are well
known by most applications.
Several services have a setting for whether TCP keep-alives will be sent for the network services.
TCP keep-alives can be configured in more detail on the Advanced Network Settings page.
Configuration through the web interface
Caution
Exercise caution in enabling and disabling network services, particularly
disabling them. Changing certain settings can render a Digi Co nnect device
inaccessible. For example, disabling Advanced Digi Discovery Protocol
(ADDP) prevents the device from being discovered on a network, even if it is
actually connected. Disabling HTTP and HTTPS disables access to the web
interface. Disabling basic servi ces such as Telnet, Rlogin, etc. can make the
Command-Line interface inaccessible.
Supported network services and their default network port numbers
In Digi devices that have multiple serial ports, the network port number defaults for various
services are set based on the following formula:
base network port number + serial port number
For example, the Telnet Passthrough service is set to network port 2001 for serial port 1, 2002 for
serial port 2, 2003 for serial port 3, etc.
If a network port is changed for a particular service, that is the only networ k port number that
changes. That change does not carry over to the other network ports. For example, if the network
port number for Telnet Passthrough is changed from 2001 to 3001, that does not mean that the
other network ports will change to 3002, 3003, etc.
There are two types of network services available:
Basic services, which are accessed by connecting to a particular well-known network
port.
Passthrough services, in which a particular serial port is set up for a particular type of
service. To use the service, users must both use the correct protocol and specify the
correct network port. For example, assuming default service ports and using a Linux
host, here is how a user would access the SSH and Telnet passthrough services:
#> ssh -l fred digi16 -p 2501
#> telnet digi16 2101
The table shows network services, services provided, an d the default netw ork port number for each
service.
78
Page 79

Configuration through the web interface
Service Services provided
Default
network
port
number
Device Discovery, also known as
Advanced Digi Discovery Protocol
(ADDP)
Discovery of Digi devices on a network. Disabling this service
disables use of the Digi Device Discovery utility to locate the
device, either on its own or as part of running the Digi Device
Setup Wizard. The network port number for ADDP cannot be
changed from its default.
Encrypted (Secure) RealPort Secure Ethernet connections between COM or TTY ports and
device servers or terminal servers.
RealPort A virtual connection to serial devices no matter where they
reside on the network.
Modem Emulation Pool (pmodem) Allows the Digi device to emulate a modem. Modem emulation
sends and receives modem responses to the serial device over
the Ethernet instead of Public Switch ed Telephone Network
(PSTN). Telnet processing can be enabled or disabled on the
incoming and outgoing modem-emulation conn ections. The
pmodem service is for connecting to whatever serial port will
answer.
Modem Emulation Passthrough Allows the Digi device to emulate a modem. This service is for
dialing in to a particular serial port that has been set up for
modem emulation.
2362
1027
771
50001
50001
Remote login (Rlogin) Allows users to log in to the Digi device and access the
513
command-line interface through Rlogin.
Remote shell (Rsh) Allows users to log in to the Digi device and access the
514
command-line interface through Rsh.
Secure Shell Server (SSH) Allows users secure access to log in to the Digi device and
22
access the command-line interface.
Secure Shell (SSH) Passthrough Accessing a specific serial port set up for SSH. 2501
Secure Socket Service Authentication and encryption for Digi devices. 2601
Simple Network Management
Protocol (SNMP)
Managing and monitoring the Digi device. To run SNMP in a
more secure manner, SNMP allows for “sets” to be
161
disabled.This securing is done in SNMP itself, not through
Network Services settings. If disabled, SNMP services such as
traps and device information are not used.
79
Page 80

Configuration through the web interface
Service Services provided
Default
network
port
number
Telnet Server Allows users an interactive Telnet session to the Digi device’s
command-line interface. If disabled, users cannot Telnet to the
device.
Telnet Passthrough Allows a Telnet connection directly to the serial port, often
referred to as reverse Telnet.
Transmission Control Protocol
(TCP) Echo
Transmission Control Protocol
(TCP) Passthrough
User Datagram Protocol (UDP)
Echo
User Datagram Protocol (UDP)
Passthrough
Web Server, also known as
HyperText Transfer Protocol
(HTTP)
Used for testing the ability to send and receive over a TCP
connection, similar to a ping.
Allows a raw socket connection directly to the serial port, often
referred to as reverse sockets.
Used for testing the ability to send and receive over a UDP
connection, similar to a ping.
Allows raw data to be passed between the serial port and UDP
datagrams on the network.
Access to web pages for configuration that can be secured by
requiring a user login. HTTP and HTTPS, below, are also
referred to as Web Server or Secure Web Server. These services
control the use of the web interface. If HTTP and HTTPS are
disabled, device users cannot use the w eb interface to configure,
monitor, and administer the device.
23
2001
7
2101
7
2101
80
Secure Web Server, also known as
HyperText Transfer Protocol over
Access to web pages for configuration that can be secured by
requiring a user login with encryption for greater security.
Secure Socket Layer (HTTPS)
Network services and IP pass-through
The IP pass-through feature (Configuration > Network > IP Pass-through) causes the Digi
device to be bridged transparently between Ethernet and mobile data links. Enabling IP Passthrough disables many device features, including man y ne tw ork serv ice s. To provide access to the
device for configuration and management purposes, a subset of network services can be configured
to terminate at the Digi device instead of being passed on to a connected device such as a router. In
the IP pass-through feature, these network services are called pinholes. Services that can be
configured as pinholes include HTTP, HTTPS, Telnet, SSH, and SNMP. See "IP pass-through
settings" on page 102 for more information.
443
80
Page 81

Dynamic DNS update settings
A Dynamic DNS (DDNS) service allows a user whose IP address is dynamically assigned to be
located by a host or domain name. Before a DDNS service may be used, you must create an
account with the DDNS service provider. The provider will give you account information such as
username and password. You will use this account information to register your IP address and
update it as it changes.
A DDNS service provider typically supports the registration of only public IP addresses. When
using such a service provider, if your Digi device has a private IP address (such as 192.168.x.x or
10.x.x.x), your update requests will be rejected.
The Digi device monitors the IP add ress it is assign ed. It will ty pically upda te the DDNS serv ice or
server automatically, but only when its IP address has changed from the IP address it previously
registered with that service.
DDNS service providers may consider frequent updates to be an abuse of their service. In such a
circumstance, the service provider may act by blocking updates from the abusive host for some
period of time, or until the customer contacts the provider. Please observe the requirem ents of the
DDNS service provider to ensure compliance with possible abuse guidelines.
Configuration through the web interface
Settings
The Dynamic DNS Update Settings page includes both settings and status information.
Current IP address: The IP address of the Digi device:
Use the following dynamic DNS service: Disables DDNS updates, or selects the
DDNS service provider to use to register the IP address of this Digi device. When you
select a specific DDNS service provider, you must also provide the related account
information for that service provider.
To force an update request to be sent to a particular DDNS service.
1 Select the None radio button to disable DDNS updates, and then click Apply to
save that change.
2 Select the radio button for the DDNS service you wish to update
3 Click Apply to save that change.
If the settings for the selected DDNS service are all specified a nd valid, an update
request will be sent immediately to that service.
81
Page 82

Configuration through the web interface
DynDNS.org DDNS Service: Y ou must create your account at DynDNS.org before you
can successfully register the IP address of your Digi device with their service. Please
familiarize yourself with their service options and requirements, in order to most
effectively use this feature of your Digi device.
This DDNS service supports only public IP addresses. If you have a private IP address
(such as 192.168.x.x or 10.x.x.x), your update requests will be rejected.
– Host and Domain Name: The fully qualified host and domain name you have
registered with your service provider. An example is: myhost.dyndns.net.
– DynDNS User Name: The user name for the account you have created with your
service provider.
– DynDNS Password: The password for the account you have created with your service
provider.
– DynDNS DDNS System: The system for the account you have created with your
service provider. DynDNS.org supports a number of different services, which vary by
the system you select. The available choices are:
- Dynamic DNS
- Static DNS
- Custom DNS
– Use Wildcards: Enables/disables wildcards for this host. The available choices for this
option are:
- Disable wildcards
- Enable wildcards
- No change to service setting
According to wildcard documentation at DynDNS.org: “The wildcard aliases
*.yourhost.ourdomain.tld to the same address as yourhost.ourdo main.tld.”
Using this option in the settings for your Digi device has the same ef fect as selecting
the wildcard option on the DynDNS.org website. To leave the wildcard option
unchanged from the current selection on their web site, use the “no change” option
in the device settings. Note that DynDNS.org support for this option may vary
according to the DynDNS system you are registered to use.
– Connection Method: The connection method to try when connecting to your service
provider to register your IP address. DynDNS.org supports three methods to connect.
The available choices are:
- Standard HTTP port 80
- Alternate HTTP port 8245
- Secure HTTPS port 443
82
Page 83

Status and history information
The next settings show status and history information for the DDNS service.
Most Recent DDNS Service Update Status: This section provides the status of the
most recent attempt to update a DDNS service or server. The displayed information
confirms the success of an update request, or it may offer information as to the reason an
update request was rejected by the service or server.
A number of status items are shown. Some of them are specific to the DDNS service
being updated. Such information will be helpful when trying to resolve update failures
with the DDNS service provider.
– Service: The name of the DDNS service provider or server being updated.
– Reported: The IP address for your Digi device that is being registered with the DDNS
service provider or server.
– Update Status: A simple indication of success or failure for this last update request.
– Result Information: A DDNS service-specific status message, hel pful when consulting
technical support.
– Raw Result Data: DDNS service-specific update result data returned by the service
provider, helpful when consulting technical support.
Configuration through the web interface
Last Logged Action or Result: The last attempted, logged action or result for the
DDNS feature, helpful for troubleshooting possible problems with DDNS updates. This
information may help identify problems with settings, network conn ect ion failures, and
other issues that prevent a DDNS update from being completed successfully . Successful
results also are reported here.
83
Page 84

IP filtering settings
You can better restrict your device on the network by only allowing certain devices or networks to
connect. This is better known as IP Filtering or Access Con trol Lists (ACL). By enabling IP
filtering, you are telling the device to only accept connections from specific and known IP
addresses or networks. Devices can be filtered on a single IP address or can be restricted as a group
of devices using a subnet mask that only allows specific networks to access to the device.
Configuration through the web interface
Caution
It is important to plan and review your IP filtering settings before applying
them. Incorrect settings can make the Digi device inaccessible from the
network.
IP Filtering Settings settings include:
Only allow access from the following devices and networks: Enables IP filtering so
that only the specified devices or networks are allowed to connect to and access the
device. Note that if you enable this feature and the system from which you are
connecting to the Digi device is not included in the list of allowed devices or networks,
then you will instantly no longer be able to communicate or configure the device from
this system.
– Automatically allow access from all devices on the local subnet: Specifies that all
systems and devices on the same local subnet or network of the device should be
allowed to connect to the device.
Allow access from the following devices: A list of IP addresses of systems or
devices that are allowed to connect to this device.
Allow access from the following networks: A list of networks based on an IP
address and matching subnet mask that are allowed to connec t to this d evi ce. This
option allows grouping several devices that exist on a particular subnet or network
to connect to the device without having to manually specific each individual IP
address.
84
Page 85

IP forwarding settings
When a Digi device acts as a router and communicates on both a private and pu bl ic net wo r k wit h
different interfaces, it is sometime s necessary to fo rward certain c onnections to other devices. Th is
is also known as Network Address Translation (NAT) or Port Forwarding. When an incoming
connection is made to the device on the private network, the IP port is searched for in the table of
port forwarding entries. If the IP port is found, that conn ection is forwarded to another specific
device on the public network.
Port Forwarding/NAT is useful when external devices can not communicate directly to devices on
the public network of the Digi device. For example, this may occur because the device is behind a
firewall. By using port forwarding, the connections can pass through the networks transparently.
Also, Port Forwarding/NAT allows multiple devices on the private network to communicate to
devices on the public network by using a shared private IP address that is controlled by Port
Forwarding/NAT.
Port forwarding can be used to connect from a Digi device to a RealPort device. For this type of
connection to occur, your mobile wireless provider must be mobile-terminated.
IP Forwarding settings include:
Configuration through the web interface
Enable IP Routing: Enables or disables IP forwarding.
Apply the following static routes to the IP routing table: The Digi device can be
configured with permanent static routes. These routes are added to the IP routing table
when this device boots, or afterwa rd wh en netw ork int erfaces become active or ch anges
are made to this list of static routes. The use of static routes provides a means by which
IP datagrams can be routed to a network tha t is not a local network o r accessible through
the default route.
Network Address Translation (NAT) Settings: A list of instances of NAT settings is
displayed. For each instance, the settings are:
– Enable Network Address Translation (NA T): Permit the transl ation and rou ting of IP
packets between private (internal) and public (external) networks. Refer to NAT
configuration options below. Some Digi device models permit the configuration of NAT
instances for more than one network interface.
– NAT Public Interface: The name of the network i nterface for which NAT will perform
address and port translations. The list of interfaces available for NAT configuration
varies according to the capabilities of your Digi device model.
– NAT Table Size Maximum: The maximum nu mber of entries that can be added to the
NAT table. These entries include the configured port and protocol forwarding rules (see
Forward TCP/UDP/FTP Connections and Forward Protocol Connections below), the
DMZ Forwarding rule (see Enable DMZ Forwarding to this IP address below), as well
as dynamic rules for connections that are created and removed during the normal
operation of NAT. The NAT table size maximum value may be configured for any value
in the range 64 through 1024, with the default value being 256 entries. Note that this
setting does not control the maximum number of port or protocol forwarding rules that
can be configured in their respective settings.
85
Page 86

Configuration through the web interface
– Enable DMZ Forwarding to this IP address: DMZ Forwarding allows you t o speci fy
a single host (DMZ Server) on the private (internal) network that is available to anyone
with access to the NAT Public Interface IP address, for any TCP- and UDP-based
services that haven't been configured. Services enabled directly on the Digi device take
precedence over (are not overridden by) DMZ Forwarding. Similarly, TCP and UDP
port forwarding rules take precedence over DMZ Forwarding (please see
Forward TCP/UDP/FTP Connections below). DMZ Forwarding is effectively a
lowest priority default port forwarding rule that doesn't permit the same remapping of
port numbers between the public and private networks, as is possible if you use explicit
port forwarding rules.
If enabled, the DMZ Forwarding rule is used for incomi ng TCP and UDP packets
from the public (external) network, for which there is no other rule. These other
rules include explicit port forwarding rules or existi ng dyn amic rules that were
created for previous communications, be those outbound (private to pu blic) or
inbound (public to private). Also, the DMZ Forwardin g rule is no t used if the re is a
local port on the Digi device to which the packet may be delivered. This includ es
TCP service listener ports as well as UDP ports that are open for various services
and clients. DMZ forwarding does not interfere with established TC P o r UDP
connections, either to local ports or through configured or dy namic NAT rules.
Outbound communications (private to public) from the DMZ Se rve r a re hand led in
the same manner as the outbound communications from other hosts on that same
private network.S
Security Warning: DMZ Forwardi ng pre sents securi ty risks for the DM Z Se rver.
Configure the DMZ Forwarding option only if you un derstan d an d are will ing to
accept the risks associated with providing open access to this server and your
private network.
– Forward protocol connections from external networks to the following internal
devices: Enables protocol forwarding to the specified internal devices. Currently, the
only IP protocols for which protocol forwarding is suppo rted are:
Generic Routing Encapsulation (GRE, IP protocol 47)
Encapsulating Security Payload (ESP, IP protocol 50, tunnel mode only).
These are routing protocols that are used to route (tunnel) various types of
information between networks. If your network needs to use t he GRE or ESP
protocol between the public and private networks, enable this feature accordingly.
86
Page 87

Configuration through the web interface
– Forward TCP/UDP/FTP connections from external networks to the following
internal devices: Specifies a list of connections based on a specific IP port and where
those connections should be forwarded to. Typically the connecting devices come from
the public side of the network and are redirected to a device on the private side of the
network.
It is possible to forward a single port or a range of po rts. To forward a range of
ports, specify the number of ports in the range, in the Range Port Count field for
the port forwarding entry. When a range is configured, the first port in the range is
specified, and the full range is indicated in the displayed en try informatio n.
Note that FTP connections require special handling by NAT. This is because the
FTP commands and replies are character-based, and some of them contain port
numbers in this message text. Those embedded port numbers poten tiall y need to be
translated by NAT as messages pass between the private and public sides of the
network. In consideration of these needs, one should select FTP as the protocol type
when configuring a rule for FTP connection forwarding to an FTP server on th e
private network side. If TCP is used instead, FTP communications may not wo rk
correctly. Note also that TCP port 21 is the standard port number for FTP. Finally,
the use of port ranges for FTP forwarding is not supported; a port count of 1 is
required.
Example
For example, to enable port forwarding of RealPort data (network port 771) on a Digi Connect
WAN VPN to a Digi Connect SP with an IP address of 10.8.128.10, you would do the f ollowing:
Make sure the Enable IP Routing checkbox is checked.
In the Forward TCP/UDP connections from external networks to the following
internal devices section, enter the port forwarding information as follows, and click
Add:
87
Page 88

IP Network Failover settings
The IP Network Failover feature provides a dynamic method for selecting and configuring the
default gateway for the Digi device. Failover uses of a set of rules and link tests to determine
whether a particular network interface can be used to communicate with a specified destination.
The user configures these rules, link tests and the priority order of the interfaces.
Failover maintains a network interface list, ordered by the configured Failover Interface Priority,
and containing information on the state of the network interface and recent success or failure of the
link tests for that interface. The failover status for a network interface is one of the following:
1 - Responding: The interface is Up and configured in the system. It is currently
responding to the link tests. This interface is suitable for use as the default gateway.
2 - Up: The interface is Up and configured in the system. Its status has not been
determined by the link tests, or no link tests are configured. This interface may be
suitable for use as the default gateway.
3 - Not Responding: The interface is Up and configured in the system. However, it is
not currently responding to the link tests, and the number of consecutive test failures has
reached the threshold number configured in the Network Failover sett ing s. T his
interface may be suitable for use as the default gateway.
Configuration through the web interface
4 - Down: The interface is Down or not configured in the system. However, it is not
currently responding to the link tests. This interface is not suitable for use as the default
gateway .
5 - Unknown: The interface is Unknown (does not exist) in the system. This interfa ce is
not suitable for use as the default gateway.
The number shown above for each status value, indicates the priority of that status, used by
failover in selecting the interface to use as the default gate way. Status priority 1 is the most suitable
for use, with lower priorities considered suitable if there are no interfaces at the highest priority.
When any network interface changes status, the interface list is examined for the interface that has
the highest status priority, nearest the start of the list. The highest priority interface with a
Responding status is used as the default gateway. If no interface is marked Responding then the
highest Up interface is used, etc.
When Network Failover performs a link test, it adds a temporary stati c host route to the destination
IP address for the link test, using the network interface that the link test is configured to test. The
static host route is removed when the link test completes. whether successfully or in failure. Users
should be careful to avoid manually configuring static host routes to any of the failover link test
destinations, as such host routes may interfere with failover's link testing. Static IP routes are
configured on the IP Forwarding Settings page. For additional information, see "IP forwarding
settings" on page 85.
In the Advanced Network Settings, the Gateway Priority selection provides a simpler method for
selecting the default gateway. However, if failover is properly configured and enabled, it overrides
the Gateway Priority selection in the Advanced Network Settings. For a description of this nonfailover Gateway Priority selection and information on how to configure it, see "Advanced
network settings" on page 107.
For IP Network Failover status and statistics, see "IP Network Failover statistics" on page 212.
88
Page 89

Network Failover General Settings
Enable IP Network Failover: Enable the Network Failover feature in the Digi device.
Click the checkbox to turn failover on or off.
Enable fallback to the non-failover default gateway priority method: The fallback
option is used if a default gateway cannot be configured by Network Failover. Failure to
configure a default gateway could occur if one or more interfaces are not enabled (On)
for Network Failover use, or if the enabled interfaces are not Up or do not have a
gateway associated with them. Click the checkbox to turn fallback on or off.
Failover Interface Priority: The list of available network interfaces in priority order,
used by failover to determine the default gateway. The default gateway is used to route
IP packets to an outside network, unless controlled by another route.
A network interface may have a static gateway configured for it, or it may obtain a
gateway from DHCP or other means when the interface is configured. The first interface
in this list that supplies a gateway will be used as the default gateway. The default
gateway may change as interfaces connect and disconnect, and as failover link tests
determine that an interface is providing the desired IP packet routing to a remote
network destination.
To change the interface priority order, select an item from the list and click the up or
down arrow.
Configuration through the web interface
89
Page 90

Configuration through the web interface
Link Test Settings for each of the network interfaces: The options tha t follow are
used to configure the link tests for the network in terfaces. Each networ k interface has its
own set of options. Failover can suppor t the use of Ethernet , W i-Fi and Mobile (cellular)
network interfaces. The available interfaces vary among different Digi products.
– Enable IP Network Failover for the XXX Interface: Enable use of the XXX interface
for failover, where XXX is Ethernet, Wi-Fi, or Mobile. Click the checkbox to turn
failover on or off. If a network interface is not enabled for use by failo ver, it will not be
considered by failover for use in selecting the default gateway.
– No Test: Click on the radio button to select no link tests will be used for this interface.
Since no link tests are run, failover will only be awar e of the Up or Down status of the
interface.
– Ping Test: Click on the radio button to select t he Ping Test as the link test to use for this
interface. The Ping Test sends ICMP Echo Request packets to the configured
destination IP address. If an ICMP Echo Reply is received (ping reply), the link test has
successfully demonstrated that the network interface can be used to communicate with
the specified destination.
Primary Destination (Ping Test): The primary, or first, destination to ping. The
destination must be a valid IPv4 address. If the destination is left empty, no Primary
Destination link test will be attempted.
Secondary Destination (Ping Test): The secondary, or second, destination to ping.
The destination must be a valid IPv4 address. If the destinatio n i s left empty, no
Secondary Destination link test will be attemp ted.
Send Count (Ping Test): Th e maxi mu m nu mber of ping requests to send for a ping
link test. When a reply is received, the ping test ends suc cessful ly a nd does not
continue to send ping requests. If no ping reply is received after Send Count ping
requests have been sent, the link test ends in failure.
Send Interval (Ping T e st): The time interval in seconds between sending pin g
requests during a ping link test. The ping tests sends a pin g request. If no pi ng reply
is received before the Send Interval expires, another ping request is sent.
– TCP Connection Test: Click on the radio button to select the TCP Connection Test as
the link test to use for this interface. The TCP Connection Test attempts to establish a
TCP connection to the configured destination IP address and port number. If a
connection is successfully established, or if the remote host actively rejects (resets) the
connection attempt, the link test has successfully demonstrated that the network
interface can be used to communicate with the specified destination. If a TCP
connection is successfully established, it is immediately closed .
Primary TCP Port (TCP Connection Test: The destination TCP port to use to
connect to the Primary Destination address.
Primary Destination (TCP Connection Test): The primary, or first, destination to
which to establish a TCP connection. The Primary TCP Port is us ed as the port to
which the test connects at the Primary Destination. The destination must be a valid
IPv4 address. If the destination is left empty , no Primary Destinati on link test will be
attempted.
Secondary TCP Port (TCP Connection Test): The destination TCP port to use to
connect to the Secondary Destination address.
90
Page 91

Configuration through the web interface
Secondary Destination (TCP Connection Test): The secondary, or second,
destination to which to establish a TCP connection. The Secondary TCP Port is used
as the port to which the test connects at the Secondary Destination. The destination
must be a valid IPv4 address. If the destination is left empty, no Secondary
Destination link test will be attempted.
Connection Timeout (TCP Connection Test): The time in seconds to wait for a
TCP connection to be established or rejected by the destina tion host.
The following four Link Test options are used if the Ping or TCP Connection Link Test is selected.
Repeat the test every: N seconds: The time interval (N) in seconds between the end of
a successful link test and the start of the next link test for the network interface. This
interval is used only after a successful test.
Shorter intervals verify the link more often, but they also inc rease the packet traf fic over
the network interface being tested. The frequency of tests should be considered carefully
for network connections such as Mobile (cellular) connections, which may be
expensive, depending on the service plan in effect with your mobile service provider.
On test failure, retry every: N seconds: The time interval (N) in seconds between the
end of a failed link test and the start of the next link test for the network interface. This
interval is used after a failed test, but only until the “Not Responding” (consecutive
failures) threshold has been reached.
A possible strategy is to configure a shorter Retry interval than the Success interval, to
more quickly test the network connection to determine whether it is truly not working or
there was just a transient test failure. Determining the validity of the link helps failover
determine whether it is necessar y to reconfigure the default gateway.
Report Not Responding after: N consecutive failures: The threshold (N) in
consecutive link test failures at which time the network interface is reported to failover
as “Not Responding”. Upon receiving such a report, failover may determine that the
default gateway should be reconfigured. The count of consecutive failures is reset to
zero when a successful link test completes, or when the network interface is
reconfigured or its connection is restarted (such as a mobile PPP connection).
When Not Responding, retry every: N seconds: The time interval (N) in seconds
between the end of a failed link test and the start of the next link test for the network
interface. This interval is used after a failed test, but only after the “Not Responding”
(consecutive failures) threshold has been reached.
91
Page 92

Socket tunnel settings
A Socket Tunnel can be used to connect two network devices: one on the Digi device’s local
network and the other on the remote network. This is especially useful for providing SSL data
protection when the local devices do not support the SSL protocol.
One of the endpoint devices is configured to ini tiate the soc ket tunn el. The tu nnel is ini tiated when
that device opens a TCP socket to the Digi device device on the configured port number. The Digi
device then opens a separate connection to the specified destination host. Once the tunnel is
established, the Digi device acts as a proxy for the data between the remote network socket and the
local network socket, regardless of which end initiated the tunnel.
Socket Tunnel settings include:
Enable: Enables or disables the configured socket tunnel.
Timeout: The timeout (specified in seconds) controls how long the tunnel will remain
connected when there is no tunnel traffic. If the timeout value is zero, the n no timeout is
in effect and the tunnel will stay up until some other event causes it to close.
Initiating Host: The hostname or IP address of the network device which will initiate
the tunnel. This field is optional.
Configuration through the web interface
Initiating Port: Specify the port number that the Digi devi ce will use to listen for the
initial tunnel connection.
Initiating Protocol: The protocol used between the device that initiates the tunnel and
the Digi device. Currently, TCP and SSL are the two supported protocols.
Destination Host: The hostname or IP address of the destination network device.
Destination Port: Specify the port number that the Digi device will use to make a
connection to the destination device.
Destination Protocol: This is the protocol used between Digi device and t he destination
device. Currently, TCP and SSL are the two supported protocols. This protocol does not
need to be the same for both connections.
Click the Add button to add a socket tunnel. Click the Apply butto n to save the sett ings.
Once the socket tunnel is configured, check the Enable checkbox to enable the socket
tunnel.
92
Page 93

Virtual Private Network (VPN) settings
Virtual Private Networks (VPNs) are used to securely connect two private networks together so
that devices may connect from one network to the other network using secure channels.VPN uses
IP Security (IPSec) technology to protect the transferring of data over the Internet. All Digi
Cellular Family products except Digi Connect WAN support VPNs.
The Digi device is responsible for handling the routing betwee n networks. Devices within the local
private network served by the Digi device can connect to devices on the remote network as if they
are in the local network. The VPN tunnels are configured using various security settings and
methods to ensure the networks are secured.
Uses for VPN-enabled Digi devices
VPN-enabled Digi devices, such as Digi Connect WAN VPN, are cellular-enabled routers that
securely connect remote subnets using IPsec VPN technology . Devices in the Digi device’ s private
network can connect directly to devices on the other private network with which the VPN tunnel is
established. You configure VPN tunnels using security settings and methods to ensure the
networks are secured.
The Digi device is used for primary or backup remote site connectivity. Se cured IPsec VPN t raffic
is typically routed from the Digi device over the cellular IP network and is terminated by a VPN
appliance at the host end.
Configuration through the web interface
A VPN-enabled Digi device can be used in several scenarios; for example:
As the primary remote site router where no other WAN router is used.
As a backup router where the remote site has a primary WAN connection through DSL,
Frame Relay, or other means.
To provide secure access to remote serial and/or Ethernet devices.
This section describes using a Digi device as a primary remote site router using IPsec Encapsulated
Security Payload (ESP) and Internet Key Exchange (IKE)/Internet Security Association and Key
Management Protocol (ISAKMP) pre-shared key methods.
93
Page 94

VPN Global Settings
General Security Settings
Miscellaneous Settings
Configuration through the web interface
– Enable Antireplay: Antireplay allows the IPsec tunnel receiver to detect and reject
packets that have been replayed. Set this field to match that at the remote VPN gateway.
The default is Enabled.
Important: Disable Antireplay if you use manual keyed tunnels.
– Suppress SA lifetime during IKE Phase 1: In most cases, leave this option unchecked.
Some VPN equipment does not negotiate the ISAKMP Phase 1 lifetimes. Such
equipment may refuse to negotiate with the Digi device if it includes lifetime values in
Phase 1 negotiation messages. If the Digi device must communicate with such
equipment, enable this option to prevent the Phase 1 lifetimes from being included in
the ISAKMP Phase 1 messages.
– Suppress Delete Phase 1 SA Message For PFS: In most cases this option should be
unchecked. VPN devices usually send a de let e noti fica tion for a ny phase 2 SAs that are
left over from previous sessions when they start to negoti ate quick mode. However,
some devices do not handle this noti ficatio n correct ly an d wi ll termin ate th e connecti on
when they receive it. If you have trouble connecting to the remote VPN device, you can
try checking this box to suppress sending this message.
– IP addresses of remote VPN peers may change on the fly (Dynamic DNS): Check
this box if you are specifying the address of the remote VPN device with a DNS name,
and that device uses dynamic DNS because its public IP address can change. Checking
this box will cause the Digi device to poll the DNS server once a minute to see if the
remote VPN device’s IP address has changed. The IPSec software will be restarted with
the new IP address if it does change. Checking this option wi ll increase network traffic
since the unit will be polling the DNS server once a minute.
94
Page 95

VPN tunnel configuration settings
Description: Enter a short, one-line description of the VPN tunnel.
VPN Tunnel: Displays settings for encryption and authentication keys. Selecting
ISAKMP is recommended; it is the standard protocol used by almost all VPN devices.
ISAKMP is more secure than manually setting the keys The only time to set the keys
manually is when connecting with an old VPN device that does not support ISAKMP, in
which case you should replace the obsolete box with one that does.
Local Endpoint T ype:
Select Local endpoint is a subnet to allow devices on the remote network to see
devices on the local network. This is the standard way IPsec works and the correct
choice in most cases.
Select Local endpoint is an internal interface to not allow devices on the remote
network to see devices on the local network. This causes the Digi device to create a
virtual endpoint and assign it the IP address specified later in the settings on this page.
Devices on the remote network will only see th e IP address o f this en dpoi nt, an d can not
see the IP addresses of any devices on the local private network. This feature must be
used in combination with NAT. If you select it, then you must update the NAT settings
on the Network >IP Forwarding page. You must enable NAT translation for the VPN
interface that corresponds to the tunnel. Tunnel 1 uses interface vpn0, tunnel 2 uses
vpn1, etc.
Configuration through the web interface
VPN Mode:
If a single remote VPN device will be used for this VPN tunnel, select
Initiate client connections to and accept connections from the remote VPN device
at and enter the remote device’s IP address or DNS name in the field below. If the Digi
device should accept connections from any remote VPN device for this tunnel, select the
Accept connections from any VPN device option.
Identity settings
– Network Interface: mobile|0eth0: Select the network interface used to communicate
with the remote VPN device. The mobile0 device is the one with the cellular modem. In
most cases, this is the correct device to use to communicate with a remote VPN device
on the Internet.
– Negotiate tunnel as soon as interface comes up: Check if the Digi device should
establish the VPN tunnel as soon as the sel ected network interface is re ady to use. Leave
this box unchecked if the Digi device should wait until a device on the local private
network attempts to communicate with a device on the remote network before
establishing the VPN tunnel.
– Use the following as the identity: Use this option to control how the Digi device
identifies itself to the remote VPN device. The Digi device must identify itself to the
remote VPN device when it negotiates the tunnel. You must make sure both devices
agree on what the identification is. Select th e “Use t he following as the identity” option
to enter a string such as a DNS name or an FQDN. Select the “Use the interface IP
address” if the Digi device should send the IP address of the interface you selected
above as its identity. Select Use the identify certificate X.509… to use a PKI
certificate. If using a PKI certificate, remember to load it in the
Administration >X.509 Certificate/Key Management web page.
95
Page 96

Configuration through the web interface
Local Endpoint:
If the Local Endpoint Type is set to Local endpoint is an internal interface, the
following prompts are displayed:
– Host address for tunnel's internal VPN interface: In the IP Address field, enter the
IP address for the virtual network interface in the IP Address. This is the IP address
which will be visible to devices on the remote private network.
– Discard packets sent to the remote subnet unless they come from this local subnet:
Select this option if the Digi device should discard IP packets transmitted from a device
on the local network and addressed to the remote network which do not come from the
subnet you specify below.
IP Address: Enter the IP address of the subnet.
Subnet Mask: Enter the mask for the subnet.
– As indicated on the settings page, having the local endpoint as an internal interface is
used in combination with NAT. Click here to configure the Network Address
Translation (NAT) settings. Select the interface name of vpn0 to configure NAT for this
tunnel.
If the Local Endpoint Type is set to Local endpoint is a subnet, prompts are displayed
for entering the network address and mask for the private network. Both the Digi unit
and the remote VPN device must be configured to use the same values.
– IP Address: Enter the IP address of the local private network.
– Subnet Mask: Enter the mask for the local private network.
Remote Endpoint: Enter the IP address and subnet mask of the remote network. Both
the Digi unit and the remote VPN device must be configured to use the same values.
– Tunnel Network Traffic to the following Remote Network:
IP Address: Enter the IP address of the remote network.
Subnet Mask: Enter the subnet mask of the remote network.
Digi devices support a mode of VPN tunnel operation called VPN tun nel a ll mod e ,
where all traffic that is not directed to the local subnet i s sent across a VPN tunnel to
a remote network. This mode is diff ere nt from the normal mo de o f VPN tu nn el
operation, where the range of the remote subnet is explicitly set VPN tunnel all
mode is supported when the Digi device is the initiator of the VPN connectio n. It is
not supported when the Digi device is the server.
For example, in the normal mode of operation, a user mi ght se t up a VPN tunnel
between the local subnet at 192.168.1.0/24 to a remot e sub net at 172.16.1.0/24. In
this case, the remote subnet range is the subnet at 172.16 .1.x. In VPN tunnel all
mode, the remote subnet is any address that is not on the local subnet, or in this case,
anything not in the subnet 192.16.1.x.
The local subnet must be defined as a specific range, fo r e xampl e 192.168.1.0/24.
This is specified in the VPN settings by setting the IP address of the local subnet to
192.168.1.0, and the subnet mask to 255 .25 5.2 55.0 . VPN tu nnel all mode is
specified by setting the remote IP address to 0.0.0.0, and the remote subn et mask to
0.0.0.0.
96
Page 97

Configuration through the web interface
With the configurat ion described above, any frames sent from the 192.168.1.x
network to any IP address not in the 192.168.1.x subnet will b e set o ver the VPN
tunnel to the remote subnet.
When configuring a Digi device for VPN tunnel all mo de and t he devi ce allows for
setting the gateway priority, set the gateway priority. The gateway priority is set on
the Configuration > Network > Advanced Network Settings page in the
Gateway Priority setting. Set the gateway priority to Ethernet for
Ethernet-enabled Digi devices, or Wifi for a wireless Digi devices. If the Digi
device’s IP address on the Ethernet (or wireless) interface is statically configured,
specify the address for the gateway on that interface. The gateway address is set in
the Configuration > Network > Ethernet IP Settings page.
Pre-Shared Key Settings
If you select the pre-shared key authentication method in o ne or more of your ISAKM P
Phase 1 Policies, then you will be prompted to supply the ID of the VPN device and the
preshared key used for authentication.
– Use the following IP address, FQDN, or username for the remote VPN’s ID: Enter
the remote VPN device’s ID here. Make sure the remote VPN device is configured to
send this ID.
– Use the following pre-shared key to negotiate IKE security settings: Enter the
preshared key here. This must match exactly with the preshared key set on the remote
VPN device.
97
Page 98

ISAKMP Phase 1 Settings
– General Security Settings for Phase 1
Connection Mode: Main|Agg ressive: Set the connection mode to match that
configured on the remote VPN device. If aggressive mode is selected, then the VPN
device will try aggressive mode first, and then try main mode if aggressiv e mod e
fails.
Enable Perfect Forward Secrecy (PFS): Set this option to enable PFS. PFS
guarantees that if one key is broken by an attacker , th at d oes no t h elp h im to break
another key. PFS is more secure, but slows down the negotiatio n p ro cess. Bot h th e
Digi unit and the remote VPN device must be configured the same way.
– NAT-T Settings
Enable NA T Traversal (NAT-T): Set this option if there is a NAT firewall between
the two VPN devices.
Keep Alive Interval: The amount of time in seconds between NAT keep alive
messages. Once a connection is established through a firewall, the VPN devices
have to send keep alive messages to prevent the NAT firewall from timing out the
connection. Set the interval to a value less tha n th e connection timeout of the NAT
firewall.
Configuration through the web interface
– ISAKMP Phase 1 Policies:
Keys are negotiated in two phases. The first phase negotiates the ke ys an d
authentication method to be used to establish the initi al ISAKMP connection.
During this phase, the two VPN devices verify each other’s identity and create a
security association (encrypted connection) which is used during phase 2. The
encryption and authentication settings you specify d etermine the level of security in
the connection the two VPN devices used to communicate with each other.
Select the policies to be used during phase 1 of the ISAKMP negotiation. The most
important thing is to make sure that the Digi unit a nd the remote VPN device use the
same policies. If more than one policy is specified, the VPN d evi ces wi ll u se the
most secure policy that they both have been con fig ured t o sup po rt.
Pre-shared Key: Using DSS a nd RSA signatures is more secure than using a pre-
shared key .
Encryption: The encryption type and the length of the key. The longer the key the
more secure it is.
Integrity: The authentication algorithm. The SHA1 algorithm is more sec ure th an
MD5.
SA Lifetime: The maximum length of the phase 1 security association.
Diffie-Hellman: The Diffie-Hellman group to use for key generation. The larger th e
group the more secure it is.
98
Page 99

Configuration through the web interface
– ISAKMP Phase 2 Settings:
The SAs used for bulk data transfer are created during phase 2. The phase 2 settings
you specify will determine the level of se curity used when devices on the local
private network communicate with devices on the remote private n etwo rk. As with
the other settings, the both the Digi unit and the remote VPN devic e must b e
configured to use the same values. If more than one policy is specified, the VPN
devices will use the most secure policy that they both have been configured to
support.
– General Security Settings for Phase 2
Diffie-Hellman: Select the Diffie-Hellman group used to generate keys. Larger
groups are more secure.
– ISAKMP Phase 2 Policies
Encryption: The encryption algorithm used for encrypting data and the len gt h of
the key. The longer the key the more secure it is. There are three supported
encryption algorithms including DES, 3-DES, and AES. DES encrypti on uses 64-
bit keys, 3-DES encryption uses 192-bit keys, and AES en cryption uses 256-bit
keys.
Authentication: The authentication algorithm used in authenticating clients. There
are two supported authentication algorithms including MD5 and SHA1. MD5
authentication uses 128-bit keys and SHA1 uses 160-bit keys. The SHA1 algorithm
is more secure than MD5.
SA Lifetime: The maximum length of the Phase 2 security association (SA), in
seconds. After the SA has been negotiated, the SA lifetime begins. Once the
lifetime has completed, a new set of SA policies are negotiated with the remote
VPN endpoint.
99
Page 100

Example VPN configuration
Cellular
Data Network
Digi
Connect
VPN
Internet
Remote Site HQ
166.123.99.99
209.123.123.123
PWR
OK
WIC0
ACT/CH0
ACT/CH1
WIC0
ACT/CH0
ACT/CH1
ETH
ACT
COL
VPN
Appliance
17 2.16 .5.0/2 4
17
2.17.1.0
/
24
172.17.1.1
Private IP Tunnel
172.16.5.1
IPSec ESP
WAN
The diagram shows a Digi Connect WAN VPN used as a primary remote site router:
How VPN tunnels work
The Digi device’s Ethernet port usually connects to a switch or hub, which then connects to other
Ethernet devices. The mobile/cellular carrier provides only one IP address to the mobile interface.
The Digi device uses Network Address Translation (NAT), where only the mobile IP address is
visible to the outside. Private IP addresses are typically used on the remote site LAN connected to
the Digi device’s Ethernet port. All outgoing traffic, except the tunneled VPN traffic, uses the
mobile IP address of the Digi device. Using the example network above, the process for initiating
VPN tunnels works like this:
Configuration through the web interface
1 Typically, a host or device on the remote subnet (in this case, 172.17.1.0) requests
information from a host on the main site (HQ) subnet (172.16.5.0). For example, a computer
at 172.17.1.20 needs a file from 172.16.5.100.
2 Th e Digi device sees the reque st as be in g on t he HQ subn et an d ch ec ks wheth er a VPN
tunnel exists between the two sites.
3 If no tunnel exists, the Digi device initiates a VPN tunnel request to its peer — the VPN
concentrator at HQ. The VPN policy settin gs are co mpar ed , and if th ey matc h, an IPsec
tunnel is created between the Digi device and the VPN conc en tra tor. Traffic is encrypted as
defined in the VPN policies.
100
 Loading...
Loading...