Page 1

ST20C2/C4 Core
Instruction Set
Reference Manual
72-TRN-273-01 January 1996
Page 2

2/212
Page 3

3/212
Contents
1 Introduction . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .5
1.1 Instruction name.............................................5
1.2 Code . . . . . . . . . . . . . . . . . . . . . . . . . . . ...........................5
1.3 Description .................................................6
1.4 Definition. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .6
1.5 Error signals . . . . . . ..........................................7
1.6 Comments. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .7
1.7 Notation. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .. . . . . . . . . . . . . . . . . . .8
1.7.1 The processor state....................................8
1.7.2 General . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ..8
1.7.3 Undefined values. . . . . . . . . . . . . . . . . . . . . .................9
1.7.4 Data types . . . . . . . . . . . . . . . .. . . . . . . . . . . . . . . . . . . .. . . . . . .9
1.7.5 Representing memory . . . . . . . . . . . . . . . . . .. . . . . . . . . . . . . . . .9
1.7.6 On-chip peripherals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
1.8 Block move registers. . . . . . . . . . . . . . . . .........................11
1.9 Constants . . . . . . .. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .11
1.10 Operators used in the definitions . . . . . . . . . . . . . . . . . . . . . . . . . .. . . . .13
1.11 Functions . . . . . . . . . . . . . . . . . .. . . . . . . . .. . . . . . . . . . .. . . . . .. .. . .14
1.12 Conditions to instructions . . . . . . . . . . . . . . . . . . . . . . . . . . ...........14
2 Addressing and data representation...............................17
2.1 Word address and byte selector . . . . . .. . . . . . . . . . . . . . . . . . . . . . . . . .17
2.2 Ordering of information. . .. . . . . . . . . . . . . . . . . . . . . . . . . .. . . . . . . . . .17
2.3 Signed integers and sign extension . . . . . . .. . . . . . . . . . . . . . . . . . . . . .18
3 Registers . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .20
3.1 Machine registers . . . . . . . . . . . . . . . . . . . . . . . ....................20
3.1.1 Process state registers.. . . . . . . . . . . .. . . . . . . . . . . . . . . . . . . .20
3.1.2 Other machine registers. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .22
3.2 The process descriptor and its associated register fields. . . . . . . . . . . . .24
4 Instruction representation . . .....................................25
4.1 Instruction encoding . . . . . . . . . . . . . . . . . .. . . . . . . . . . . . . . . . . . . . . . .25
4.1.1 An instruction component.. . . . . . . . . . . . . . . . . . . . . . . . . . . . . .25
4.1.2 The instruction data value and prefixing . . . . . . . . . . . . . . . . . . .25
4.1.3 Primary Instructions. . . . . . . . . . . . . . . . . . . . .. . . . . . . . . . . . . .26
4.1.4 Secondary instructions. . . . . . . . .. . . . .. . . . . . . . . . . . . . . . . . .27
4.1.5 Summary of encoding . .. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .27
4.2 Generating prefix sequences . . . . . . . . . . . . . . . . . . . . . . . . . .. . . . . . . .28
4.2.1 Prefixing a constant . . . . . . . . . .. . . . . . . . . . . . . . . . . . . . . . . . .28
4.2.2 Evaluating minimal symbol offsets. . . . . . . . . . . . . . . . . . . . . . . .29
5 Instruction Set Reference. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .31
Page 4

Contents
4/212
Page 5

5/212
1 Introduction
This manual provides a summary and referenceto the ST20 instruction setfor C2 and
C4 cores. The instructions are listed in alphabetical order, one to a page. Descriptions
are presented in a standard format with the instruction mnemonic and full name of the
instruction at the top of the page,followed by these categories of information:
• Code: the instruction code;
• Description: a brief summary of the purpose and behavior of the instruction;
• Definition: a more complete description of the instruction, using the notation
described below in section 1.7;
• Error signals: a list of errors and other signals which can occur;
• Comments: a list of other important features of the instruction;
• See also: for some instructions, a cross reference is providedto other instruc-
tions with a related function.
These categories are explained in more detail below, using the
add
instruction as an
example.
1.1 Instruction name
The header at the top of each pageshows the instruction mnemonic and, on the right,
the full name of the instruction. For primary instructions the mnemonic is followed by
‘n’ to indicate the operand to the instruction; the same notation is used in the
description to showhow the operand is used.
1.2 Code
For secondary instructions the instruction ‘operation code’ is shown as the memory
code — the actual bytes, including any prefixes, which are stored in memory. The
value is givenas a sequence of bytesin hexadecimal, decoded left to right.The codes
are stored in memory in ‘little-endian’ format — with the first byte at the lowest
address.
For primary instructions the code stored in memory is determined partly by the value
of the operand to the instruction. In this case the op-code is shown as ‘Functionx’
wherexis the function code in the last byte of the instruction. For example,
adc(add
constant
) is shownas ‘Function 8’.
Example
The entry forthe
add
instruction is:
Code:F5
Page 6

6/212
1.3 Description
The description section providesan indication of the purpose of the instruction as well
as a summary of the behavior. This includes details of the use of registers, whose
initial values may be used as parameters and into which results maybe stored.
Example
The
add
instruction contains the followingdescription:
Description: Add Areg and Breg, with checking for overflow.
1.4 Definition
The definitionsection provides a formal description of the behavior of the instruction.
The behavior is defined in terms of its effect on the state of the processor (i.e. the
values in registers and memory before and after the instruction has executed).
The effects of the instruction on registers, etc. are given as relationships of the
following form:
register′←
expression involvingregisters, etc.
Primed names (e.g. Areg′ ) represent values after instruction execution, while
unprimed names represent values when instruction execution starts. For example,
Areg represents the value in Areg before the execution of the instruction while Areg′
represents the value in Areg afterwards. So, the example above states that the
register on the left hand side becomes equal to the value of the expression on the
right hand side after the instruction has been executed.
The description is written with the main function of the instruction stated first(e.g. the
main function of the
add
instruction is to put the sum of Areg and Breg into Areg).
This is followedby the other effectsof the instruction (e.g. popping thestack). There is
no temporal ordering implied by the order in which the statements are written.
The notation is described more fully in section 1.7.
Example
The
add
instruction contains the followingdescription:
Definition:
Areg′←Breg +
checked
Areg
Breg′←Creg
Creg′←
undefined
This says that the integer stack is popped and Areg assigned the sum of the values
that were initially in Breg and Areg. After the instruction has executedBreg contains
the value that wasoriginally in Creg, and Creg is undefined.
Page 7

7/212
1.5 Error signals
This section lists the errors and other exceptional conditions that can be signalled by
the instruction. This only indicates the error signal, not the action that willbe takenby
the processor - this will depend on the trap enable bits which are set, the value in the
trap handler location, etc.
The order of the error signals listed is significantin that if a particular error is signalled
then errors later in the list may not be signalled. The errors that maybe signalled are
as follows:
IntegerError
indicates a variety of general errors such as a valueout of range.
IntegerOverflow
indicates that an overflowoccurred during an integer arithme-
tic operation.
LoadTrap
indicates that an attempt has been madeto loada newtrap handler.
This provides a basic mechanism fora supervisor kernel to manage user processes installing trap handlers.
StoreTrap
, analogous to
LoadTrap
, indicates that an attempt has been made to
store a traphandler so that it can be inspected. Again this allows a supervisor
kernel to manage the trap system used byuser processes.
Example
As an example,the error signals listed forthe
add
instruction are:
Error signals:
IntegerOverflow
can be signalled by +
checked
So,the only error that can be causedby
add
is an integer overflowduring the addition
of Areg and Breg.
1.6 Comments
This section is used for listing other information about the instructions that may be of
interest. Firstly, there is an indication of the type ofthe instruction.These are:
“Primary instruction” — indicates one of the 13 functions which are directly
encoded in a single byte instruction.
“Secondary instruction” — indicates aninstruction which is encoded using
opr
.
Then there is information concerning the scheduling of the process:
“Instruction is a descheduling point” — a process maybe descheduled after
executing this instruction.
“Instruction is a timeslicing point” — a process maybe timesliced after executing this instruction.
“Instruction is interruptible” — the execution of this instruction maybe interrupted bya high priority process.
Page 8

8/212
This section also describes any situations where the operation of the instruction is
undefinedor invalid.
Example
Using the
add
instruction as an example again, the comments listed are:
Comments:
Secondary instruction.
This says that
add
is a secondaryinstruction.
1.7 Notation
The following sections give a full description of the notation used in the ‘definition’
section ofthe instruction descriptions.
1.7.1 The processorstate
The processor state consists of the registers (mainly Areg, Breg, Creg, Iptr, and
Wptr), the contents of memory, and various flags and special registers (such as the
error flags,process queue pointers,clock registers, etc.).
The Wptr register is used for the address of the workspace of the current process.
This address is word aligned and therefore has the two least significant bits set to
zero.Wdesc is used for the ‘process descriptor’— the value that is held in memory as
an identifier of the process when the process is not being executed. This value is
composed of the top 31 bits of the Wptr plus the process priority stored in bit 0 of the
word. Bit 0 is set to 0 for high priority processes and 1 forlow priority processes. Bit 1
of the process descriptor is always 0.
1.7.2 General
The instruction descriptions are not intended to describe the way the instructions are
implemented, but only their effect on the state of the processor.So, for example, the
blockmove instructions are described in terms ofa sequence of
byte
reads and writes
even though the instructions are implemented to perform the minimum number of
word
reads andwrites.
Comments (in
italics
) are used to both clarify the description and to describe actions
or values that cannot easily be represented by the notation used here; e.g.
start next
process
. These actions may be performed in another subsystem in the device, such
as the communications subsystem, and so any changes to machine state are not
necessarily completely synchronized with the execution of the instruction (as the
different subsystems work independently and in parallel).
Ellipses are used to show a range of values; e.g. ‘i = 0..31’ means that i has
values from 0 to 31, inclusive.
Page 9

9/212
Subscripts are used to indicate particular bits in aword; e.g. Aregifor bit i of Areg;and
Areg
0..7
forthe least significantbyte of Areg. Note that bit 0 is the least significantbit in
a word, and bit 31 is the most significantbit.
Generally, if the description does not mention the state of a register or memory
location after the instruction, then the value will not be changed by the instruction.
One exception to this general rule is Iptr, which is assigned the address of the next
instruction in the code
before
every instruction executionstarts. The Iptr is included in
the description only when it is
directly
affected by the instruction (e.g. in the
jump
instruction). In these cases the address of the next instruction is indicated by the
comment “
next instruction
”.
Scheduling operations
Some registers, such as the timer and scheduling list pointers and some special
workspace locations,can be changed at anytime by scheduling operations.Changes
to these are included in the description only when they are
directly
caused by the
instruction, and not just as an effect of any scheduling operation which might take
place.
1.7.3 Undefined values
Many instructions leavethe contents of a register or memory location in an undefined
state. This means that thevalue of the location may be changed by the instruction, but
the new value cannot be easily defined,or isnot a meaningful result of the instruction.
For example, when the integer stackis popped, Creg becomes undefined,i.e. it does
not contain any meaningful data. An undefined value is represented by the name
undefined
. The values of registers which become undefined as a result of executing
an instruction are implementation dependent and are not guaranteed to be the same
on different members of the ST20 familyof processors.
1.7.4 Data types
The instruction set includes operations on four sizes of data: 8, 16, 32 and 64-bit
objects. 8-bit and 16-bit data can represent signed or unsigned integers; 32-bit data
can represent addresses, signed or unsigned integers, or single length floating point
numbers; and 64-bit data can represent signed orunsigned integers,or double length
floating point values. Normally it is clear from the context (e.g. from the operators
used) whether a particular object represents a signed, unsigned or floating point
number.A subscripted label is added (e.g.Areg
unsigned
) to clarify where necessary.
1.7.5 Representing memory
The memory isrepresented by arrays of each data type.These areindexedby a value
representing a byte address. Access to the four data types is represented in the
instruction descriptions in the following way:
byte[
address
]references a byte in memory at the givenaddress
sixteen[
address
]references a 16-bit object in memory
Page 10

10/212
word[
address
]references a 32-bit word in memory
For all of these,the state of the machine referenced is that
before
the instruction if the
function is used without a prime (e.g. word[]), and that
after
the instruction if the
function is used with a prime (e.g.word′[]).
For example, writing a value given by an expression,
expr
, to the word in memory at
address
addr
is represented by:
word′[
addr
] ←
expr
and reading a wordfrom a memory location is achievedby:
Areg′←word[
addr
]
Writing to memory in any of these wayswill updatethe contents of memory,and these
updates will be consistently visible to the other representations of the memory, e.g.
writing a byte at address 0 will modify the least significantbyte of the word at address
0.
Reading and writing in this way cannot be used to access on-chip peripherals.
Reading or writing to memory addresses between
PeripheralStart
and
PeripheralEnd
will have undefinedeffects.
Data alignment
Each of these data items have restrictions on their alignment in memory.Byte values
can be accessed at any byte address, i.e. they are byte aligned. 16-bit objects can
only be accessed at even byte addresses, i.e. the least significant bit of the address
must be 0. 32-bit and 64-bit objects must be word aligned, i.e. the 2 least significant
bits of the address must be zero.
Address calculation
An address identifiesa particular bytein memory.Addresses are frequently calculated
from a baseaddress and an offset. For different instructions the offset maybe givenin
units of bytes, words or double words depending on the data type being accessed. In
order to calculate the address of the data, the offset must be converted to a byte offset
before being added to the base address.This is done by multiplying the offset by the
number of bytes in the particular units being used. So, for example, a word offset is
converted to a byte offset by multiplying it by the number of bytesin a word (4 in the
case of the ST20).
As there are many accesses to memory at wordoffsets, a shorthand notation is used
to represent the calculation of a word address. The notation
register@x
is used to
represent an address which is offset byxwords (4xbytes) from
register
. For example,
in the specification of
load non-local
there is:
Areg′← word[Areg @ n]
Here, Areg is loaded with the contents of the word that is n words from the address
pointed to byAreg (i.e.Areg + 4n).
In all cases, if the givenbase address has the correct alignment then any offset used
will also givea correctly aligned address.
Page 11

11/212
1.7.6 On-chip peripherals
On-chip peripherals may have memory-mapped registers in the address range
PeripheralStart
to
PeripheralEnd
. Access to these registers is represented in the
following way:
PeripheralByte[
address
] references an 8-bit peripheral register
PeripheralSixteen[
address
] references a 16-bit peripheral register
PeripheralWord[
address
] references a 32-bit peripheral register
For all of these, the state of the peripheral referenced is that
before
the instruction if
the function is used without a prime (e.g. PeripheralWord[]), and that
after
the
instruction if the function is used with a prime (e.g. PeripheralWord′[]).
For example, writing a value given by an expression,
expr
, to the register at address
addr
is represented by:
PeripheralWord′[
addr
] ←
expr
and reading a wordfrom a peripheral is achieved by:
Areg′←PeripheralWord[
addr
]
1.8 Block move registers
A group of registers is used in the implementation of blockmoves. These are referred
to as the ‘block move registers’ and include
Move2dBlockLength,Move2dDestStride
,
and
Move2dSourceStride
.
1.9 Constants
A number of data structures have been defined in this book. Each comprises a
number of data slots that are referenced by name in the text and the following
instructions descriptions.
These data structures is listed in Table1.2 to Table1.4.
word offset slot name purpose
0 pw.Temp slot used by some instructions forstoring temporary values
-1 pw.Iptr the instruction pointer ofa descheduled process
-2 pw.Link the address of the workspace of the next process in scheduling list
-3 pw.Pointer saved pointer to communication data area
-3 pw.State savedalternative state
-4 pw.TLink address of the workspace of the next process on the timer list
-5 pw.Time time that a process on a timer list is waiting for
Table1.1 Process workspacedata structure
Page 12
12/212
In addition, a number of constants are used to identify word length related values etc.;
These are listed in Table 1.5 .
A number of values are used bythe ST20 to indicate the state of a process and other
conditions. These are listed in Table 1.6.
word offset slot name purpose
0 le.Index contains the loop control variable
1 le.Count contains number of iterationsleft to perform
Table 1.2 Loop end data structure
word offset slot name purpose
1 pp.Count contains unsigned count of parallel processes
0 pp.IptrSucc contains pointer to firstinstruction of successor process
Table 1.3 Parallelprocess data structure
word offset slot name purpose
2 s.Back back of waiting queue
1 s.Front front of waitingqueue
0 s.Count number of extraprocesses that the semaphore will allow to continue
running on a
wait
request
Table 1.4 Semaphore data structure
Name Value Meaning
BitsPerByte
8 The number of bits in a byte.
BitsPerWord
32 The number of bits in a word.
ByteSelectMask
#00000003 Used to select the byte select bits of an address.
WordSelectMask
#FFFFFFFC Used to select the byte select bits of an address.
BytesPerWord
4 The number of bytes in a word.
MostNeg
#80000000 The most negative integer value.
MostPos
#7FFFFFFF The most positive signed integer value.
MostPosUnsigned
#FFFFFFFF The most positive unsigned integer value.
PeripheralStart
#20000000 The lowest address reserved for memory-mapped on-
chip peripherals.
PeripheralEnd
#3FFFFFFF The highest address reserved for memory-mapped on-
chip peripherals.
Table 1.5 Constants used in the instructiondescriptions
Page 13
13/212
Product identity values
These are values returned by the
lddevid
and
ldprodid
instructions. For specific
product ids in the ST20 family refer to SGS-THOMSON.
1.10 Operators used in the definitions
Modulo operators
Arithmetic on addresses is done using
modulo
arithmetic — i.e. there is no checking
for errors and, if the calculation overflows, the result ‘wraps around’ the range of
values representable in the word length of the processor — e.g. adding 1 to the
address at the top of the address map produces the address of the byte at the bottom
of the address map. There is also a number of instructions for performing modulo
arithmetic, such as
sum,prod
, etc. These operators are represented by the symbols
‘+’, ‘−’, etc.
Name Value Meaning
DeviceId
Depends on processor type. See
below.
A value used to identify the type and revision of processor.
Returned by the
ldprodid
and
lddevid
instructions.
Disabling.p MostNeg
+ #03
#80000003
Stored in the pw.State location while an alternative is being
disabled.
Enabling.p MostNeg
+ #01
#80000001
Stored in the pw.State location while an alternative is being
enabled.
false
0 The boolean value ‘false’.
NoneSelected.o
-1
#FFFFFFFF
Storedinthepw.Tempslot of a process’workspacewhile no
branch of an alternative has yet been selected during the
waiting and disabling phases.
NotProcess.p MostNeg
#80000000
Used,wherevera process descriptor isexpected, to indicate
that there is no process.
Ready.p MostNeg
+ #03
#80000003
Stored inthe pw.Statelocation during the enablingphase of
an alternative,to indicate that a guard is ready.
TimeNotSet.p MostNeg
+ #02
#80000002
Stored in pw.TLink location during enablingof atimer alternative after a time to wait for has been encountered.
TimeSet.p MostNeg
+ #01
#80000001
Stored in pw.TLink location during enablingof atimer alternative after a time to wait for has been encountered.
true
1 The boolean value ‘true’.
Waiting.p MostNeg
+ #02
#80000002
Stored inthepw.Statelocation by
altwt
and
taltwt
toindicate
that the alternative is waiting.
HighPriority
0 High priority
LowPriority
1 Low priority
Table 1.6 Constants used within the ST20
Page 14

14/212
Error conditions
Any errors that can occur in instructions which are defined in terms of the modulo
operators are indicated explicitly in the instruction description. For example the
div
(
divide
) instruction indicates the cases that can cause overflow,independently of the
actual division:
if (Areg = 0) or ((Breg = MostNeg) and (Areg = -1))
{
Areg′←
undefined
IntegerOverflow
}
else
Areg′← Breg /Areg
Breg′← Creg
Creg′←
undefined
Checked operators
To simplify the description of
checked
arithmetic, the operators ‘+
checked
’, ‘−
checked
’,
etc. are used to indicate operations that perform checked arithmetic on signed
integers. These operators signal an
IntegerOverflow
if an overflow,divide by zero, or
other arithmetic error occurs. If no trap is taken, the operators also deliver the modulo
result.
A number of comparison operators are also used and there are versions of some of
these that treat the operands as unsigned integers. A full list of the operators used in
the instruction definitions is given in Table 1.7.
1.11 Functions
Type conversions
The following function is used to indicate a type conversion:
unsign(x) causes the bit-pattern in x to beinterpreted as an unsigned integer.
1.12 Conditions to instructions
In many cases, the action of an instruction depends on the current state of the
processor. In these cases the conditions are shownby an if clause; this can take one
of the following forms:
• if
condition
statement
• if
condition
statement
else
statement
Page 15
15/212
• if
condition
statement
else if
condition
statement
else
statement
These conditions can be nested. Braces, {}, are used to group statements which are
dependent on a condition. For example, thecj(
conditional jump
) instruction contains
the following lines:
if (Areg = 0)
IptrReg′←
next instruction
+ n
Symbol Meaning
Integer arithmetic with overflow checking
+
checked
−
checked
×
checked
Add, subtract, and multiply of signed integers. If the computation overflows an
IntegerOverflow
is signalled and the result of theoperation is truncated to the
word length.
Unchecked (modulo) integer arithmetic
+
−
×
/
rem
Integer add, subtract, multiply, divide and remainder. If the computation overflowsthe result of the operationis truncated to the word length. If a divide or
remainder byzero occurs theresult of the operationis undefined.Noerrorsare
signalled. The operator ‘−’ is also used as a monadicoperator.The sign of the
remainder is the same as the sign of the dividend.
Signed comparison operators
<
>
≤
≥
=
≠
Comparisons of signed integer and floatingpoint values: ‘less than’, ‘greater
than’, ‘less than or equal’, ‘greater than or equal’, ‘equal’ and ‘not equal’.
Unsigned comparison operators
<
unsigned
>
unsigned
≥
unsigned
after
Comparisons ofunsigned integer values:‘less than’,‘greaterthan’, ‘greaterthan
or equal’, and ‘after’ (for comparison of times).
Logical bitwise operations
∼ (or BITNOT)
∧ (or BITAND)
∨ (or BITOR)
⊗ (or BITXOR)
>>
<<
‘Not’ (1’scomplement), ‘and’, ‘or’, ‘exclusive or’, and logical left and right shift
operations on bits in words.
Boolean operators
not
and
or
Boolean combination in conditionals.
Table 1.7 Operators used in the instruction descriptions
Page 16

16/212
else
{
IptrReg′←
next instruction
Areg′← Breg
Breg′← Creg
Creg′←
undefined
}
This says that if the value in Areg is zero, then the jump is taken (the instruction
operand, n, is added to the instruction pointer), otherwise the stack is popped and
execution continues with the next instruction.
Page 17
17/212
2 Addressing and data representation
The ST20 processor is a 32-bit word machine, with byte addressing and a 4 Gbyte
address space. This chapter explains how data is loaded from and stored into that
address space, explains how signed arithmetic is represented, and defines the
arithmetic significance of ordering of data items.
2.1 Word address and byte selector
A machine address is a single word of data which identifies a byte in memory - i.e. a
byte address. It comprises two parts, a word address and a byte selector. The byte
selector occupies the two least significantbits of the word; the wordaddress the thirty
most significant bits. An address is treated as a signed value, the range of which
starts at the most negative integer and continues, through zero, to the most positive
integer. This enables the standard comparison functions to be used on pointer
(address) values in the same waythat theyare used on numerical values.
Certain values can never be used as pointers because they represent reserved
addresses at the bottom of memory space. They are reserved for use by the
processor and initialization. In this text,names are used to represent these and other
values (e.g.
NotProcess.p,Disabling.p
). A full list of names and values of constants
used in this book is given in section1.9.
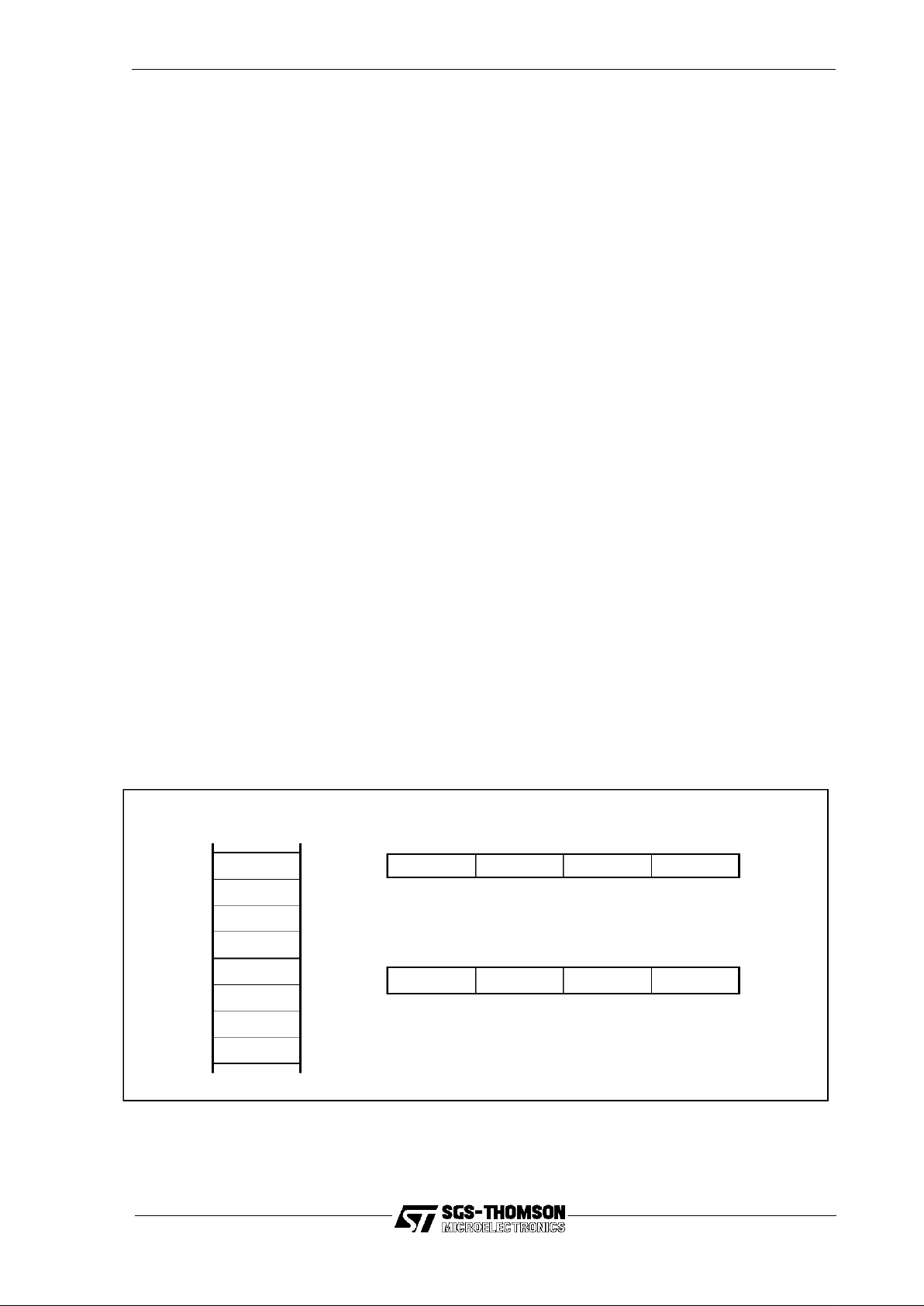
2.2 Ordering of information
The ST20 is ‘little-endian’ — i.e. less significant data is always held in lower
addresses. This applies to bits in bytes,bytes in words and words in memory.Hence,
in a word of data representing an integer, one byte is more significant than another if
its byte selector is the larger of the two. Figure 2.1 shows the ordering of bytes in
words and memory for the ST20. Note that this ordering is compatible with Intel
processors, but not Motorola or SPARC.
Figure 2.1 Bytes in memory and words
words (wordlength is 32 bits)
X
is a word-aligned byte address
X+n
is the bytenbytes past
X
X+7
X+6
X+5
X+4
X+3
X+2
X+1
X+0
Memory
(bytes)
X+3 X+2 X+1 X+0
MSB LSB
31 24 23 16 15 8 7 0
X+7 X+6 X+5 X+4
MSB LSB
31 24 23 16 15 8 7 0
Page 18

18/212
Most instructions that involvefetching data from or storing data into memory,use word
aligned addresses (i.e. bits 1 and 0 are set to 0) and load or store four contiguous
bytes. However,there are some instructions that can manipulate part of the bit pattern
in a word,and a fewthat use doublewords.
A data item that is represented in two contiguous bytes, is referred to as a 16-bit
object. This can be stored, either in the least significant 16-bits of a word location or in
the most significant 16 bits, hence addresses of such locations are 16-bit aligned (i.e.
bit 0 is set to 0).
A data item that is represented in two contiguous words is referred to as a 64-bit
object or a doubleword.
Similarly, a data item represented in a single byte is sometimes referredto as an 8-bit
object.
2.3 Signed integers and sign extension
A signed integer is stored in twos-complement format and may be represented by an
N-bit object. Most commonly a signed integer is represented by a single word (32-bit
object), but as explained, it may be stored, for example, in a 64-bit object, a 16-bit
object, or an8-bit object. In each of theseformats,all the bits within the object contain
useful information.
Consider the example shown in Figure 2.2, which showshowthe value-10 is stored in
a 32-bit register,firstly as an 8-bit object and secondly asa 32-bit object. Observe that
bits 31 to 8 are meaningful for a 32-bit object but not for an 8-bit object. Thesebits are
set to 1 in the 32-bit object to preserve the negative sign of the integer being
represented.
Figure 2.2 Storinga signed integer in different length objects
11110110these bit values not related to integer value
07831bit position
11110110
07831bit position
11 1...
signed integer value (-10) stored as an 8-bit object (byte)
signed integer value (-10) stored as a 32-bit object(word)
Page 19

19/212
The length of the object that stores a signed integer can be increased (i.e. the object
size can be increased). This operation is knownas ‘sign extension’. The extra bits that
are allocated for the larger object, are meaningful to the value of the signed integer.
They must therefore be set to the appropriate value. The value forall these extrabits
is in fact the same as the value of the most significant bit - i.e. the sign bit - of the
smaller object. The ST20 providesinstructions that sign extend byte and half-word to
word, and 32 bits to 64 bits.
Page 20
20/212
3 Registers
3.1 Machine registers
This section introduces the ST20 processor registers that are visible to the
programmer. Firstly the set of registers known as state registers are presented and
discussed. These fully define the state of the executing process. Secondly the other
registers of interest to the programmer,are presented.
3.1.1 Process state registers
The state of a executing process at any instant is defined by the contents of the
machine registers listed in Table 3.1. The ‘register’ column gives the abbreviated
name of the register. The ‘full name / description’ column provides the full textual
name which is usually used when referencing a register in this manual; and where
unclear, a brief description of the information contained in this register.
In addition there is a small number of registers used to implement blockmoves.
Status register
The Status register contains status bits which describe the current state of the
process and any errors which may have occurred. The contents of the Status register
are shown in Table3.2.
‘Shadow’ registers
When a high priority process interruptsa lowpriority process, the state of the currently
executing process needs to be saved. For this purpose, two sets of process state
registers are provided,one each for high and low priority. On interrupt, the processor
switches to using the high priority registers, leaving the low priority registers to
preservethe lowpriority state.
A high priority process may manipulate the low priority ‘shadow’ registers with the
instructions
ldshadow
and
stshadow
. In the definitions of these instructions, the
process state registers havea subscript (e.g. Areg[LowPriority]) indicating the priority.
register full name / description process modes
Status status register
Wptr workspace pointer - contains the address of theworkspace of the currently execut-
ing process
Iptr instruction pointer register - pointer to nextinstruction to be executed
Areg integer stack register A
Breg integer stack register B
Creg integer stack register C
Table 3.1 Process state registers
Page 21

21/212
bit number full name / description
0 breakpoint trap status bit
1 integer error trap status bit
2 integer overflow trap status bit
3 illegal opcode trap status bit
4 load trap trap status bit
5 store trap trap status bit
6 internal channel trap status bit
7 external channel trap status bit
8 timer trap status bit
9 timeslice trap status bit
10 run trap status bit
11 signal trap status bit
12 process interrupt trapstatus bit
13 queue empty trap status bit
14 reserved
15 causeerror status bit
17-16 Scheduler trap return priority status bits:
00 - high priority
01 - lowpriority
19-18 Trap group status bits:
00 - Breakpoint
01 - Error
10 - System
11 - Scheduler
20 timeslice enable bit
25-21 reserved
30-26 Interrupted operation status bits:
00000 - None
00001 -
move
00010 -
devmove
00011 -
move2dall
00100 -
move2dzero
00101 -
move2dnonzero
00110 -
in
00111 -
out
01000 -
tin
01001 -
tin
restart
01010 -
taltwt
01011 -
taltwt
restart
01100 -
dist
01101 -
dist
restart
01110 -
enbc
01111 -
disc
10000 -
resetch
31 status valid
Table 3.2 Status register
Page 22

22/212
If the process state registers are referred to without subscriptsthen the current priority
is implied.
3.1.2 Other machine registers
There are several other registers which the programmershould know about, but which
are not part of the process state. These are presented in Table 3.3.
Enables register
The Enables register contains:
•
TrapEnables
bits (0..15) which can be used to control the taking of traps;
•
GlobalInterruptEnables
bits (16..31) which are used to control timeslicing and
interruptibility. These are normally set to 1.
Bits of
TrapEnables
may be set using the
trapenb
instruction and cleared using
trapdis
. Bits of
GlobalInterruptEnables
may be set using the instruction
gintenb
and
disabled using
gintdis
.
The contents of the Enables register are shown in Table 3.4.
ClockEnables
ClockEnables
is a pair of flags which enable the timers ClockReg to tick. Bit zero of
ClockEnables
controls ClockReg[0] and bit 1 controls ClockReg[1]. In each case,
register full name / description
ProcQueueFPtr[0] high priority front pointer register- contains pointer to first process on the high
priority scheduling list
ProcQueueFPtr[1] low priority front pointer register - contains pointer to firstprocess onthe low
priority scheduling list
ProcQueueBPtr[0] high priority back pointer register - contains pointer to last process on the high
priority scheduling list
ProcQueueBPtr[1] low priority back pointer register - contains pointer to last process on the low
priority scheduling list
ClockReg[0] high priority clock register - contains current value of high priority clock
ClockReg[1] low priority clock register - contains current value of low priority clock
TptrReg[0] high priority timer list pointer register - contains pointer to the firstprocess on
the high priority timer list
TptrReg[1] low priority timerlistpointerregister-contains pointerto the firstprocess on the
low priority timer list
TnextReg[0] high priority alarm register - contains the time of the first process on the high
priority timer queue
TnextReg[1] low priority alarm register - contains the time of the first process on thelow
priority timer queue
Enables trap and globalinterrupt enables register
Table 3.3 Other machine registers
Page 23

23/212
the timer will tick if the
ClockEnables
bit is set to1.
ClockEnables
can be set using the
clockenb
instruction and cleared using
clockdis
.
Error flags
The other machine flags referred to in the instruction definitionsare listed in Table 3.4.
ErrorFlag
is a pair of flags, one for each priority,set by the processor if an integer error
or integer overflow error occurs and the corresponding trap is not enabled. The
processor will immediately halt if the
HaltOnError
flag is also set, or will continue
bit number full name / description
0 breakpoint trap enable bit
1 integer error trap enable bit
2 integer overflow trap enable bit
3 illegal opcode trap enable bit
4 load trap trap enable bit
5 store trap trap enablebit
6 internal channel trap enable bit
7 external channel trap enable bit
8 timer trap enable bit
9 timeslice trap enable bit
10 run trap enable bit
11 signal trap enable bit
12 process interrupt trapenable bit
13 queue empty trap enable bit
15-14 reserved
16 low priority processinterrupt enablebit
17 low priority timesliceenable bit
18 low priority externaleventenable bit
19 low priority timeralarm enable bit
20 high priority process interrupt enable bit
21 high priority timeslice enablebit
22 high priority external event enable bit
23 high priority timer alarm enable bit
31-24 reserved
Table 3.4 Enables register
flag name description
ErrorFlag
Untrapped arithmetic error flags
HaltOnErrorFlag
Halt the processor if the
ErrorFlag
is set
Table 3.5 Error flags
Page 24

24/212
otherwise. The
ErrorFlag
s may also be set by the
seterr
instruction or tested and
cleared by the
testerr
instruction. The
stoperr
instruction stops the current process if
the
ErrorFlag
is set. The low priority
ErrorFlag
is copied to the high priority when the
processor switches from low to high priority. The
HaltOnError
flag may be set by the
sethalterr
instruction, cleared by
clrhalterr
and tested by
testhalterr
.
3.2 The process descriptor and its associated register fields
In order to identify a process completely it is necessary to know: its workspace
address (in which the byte selector is always 0), and its priority (high or low). This
information is contained in the process descriptor. The workspace address of the
currently executing process is held in the workspace pointer register (Wptr) and the
priority is held in the flag Priority.
Wptr points to the current process workspace, which is always word-aligned. Priority
is the priority of the currently executing process where the value 1 indicates low
priority and 0 indicates high priority.
The process descriptor is formed from a pointer to the process workspace or-ed with
the priority flag at bit 0. Bit 1 is always set to 0.
Wdesc is defined so that the following invariants are obeyed:
Wptr = Wdesc ∧
WordSelectMask
Priority = Wdesc ∧ 1
Figure 3.1 Constituents of a process descriptor
Workspace address
21 0
Priority0
31
Page 25

25/212
4 Instruction representation
The instruction encoding is designed so thatthe most commonly executedinstructions
occupy the least number of bytes. This chapter describes the encoding mechanism
and explains how it achievesthis.
A sequence of single byte
instruction components
is used to encode an instruction.
The ST20 interprets this sequence at the instruction fetch stage of execution. Most
users (working at the level of microprocessor assembly language or high-level
languages) need not be aware of the existence of instruction components and do not
need to think about the encoding. The first section (4.1) has been included to provide
a background.The following section (4.2) need only concern the reader that wants to
implement a code generator.
4.1 Instruction encoding
4.1.1 An instruction component
Each instruction component is one byte long, and is divided into two 4-bit parts. The
four most significant bits of the byte are a
function code
, and the four least significant
bits are used to build an
instruction data value
as shown in Figure 4.1.
Figure 4.1 Instruction format
The representation provides for sixteen instruction components (one for each
function), each with a data field ranging from 0 to15.
There are three categories of instruction component. Firstly there are those that
specify the instruction directly in the function field. These are used to implement
primary instructions
. Secondly there are the instruction components that are used to
extend the instruction data value - this process of extension is referred to as
prefixing
.
Thirdly there is the instruction component
operate(opr
) which specifies the instruction
indirectly using the
instruction data value.opr
is used to implement
secondary
instructions
.
4.1.2 The instruction data value and prefixing
The data fieldof an instruction component is used to create an instructiondata value’
Primary instructions interpret the instruction data value as the operand of the
instruction. Secondary instructions interpret it as the operation code forthe instruction
itself.
function code data
0347
Page 26

26/212
The instruction data value is asigned integer that is represented as a 32-bitword. For
each newinstruction sequence, the initial valueof this integer is zero.Since there are
only 4 bits in the data field of a single instruction component, it is only possible for
most instruction components to initially assign an instruction data value in the range 0
to 15. However two instruction components are used to extend the range of the
instruction data value. Hence one or more prefixing components may be needed to
create the correct instruction data value. These are shown in Table 4.1 and explained
below.
All instruction components initially load the four data bits into the least significant four
bits of the instruction data value.
pfix
loads its fourdata bits into the instruction data value,and then shifts this value up
four places.
nfix
is similar, except that it complements the instruction data value
†
before shifting it up. Consequently, a sequence of one or more prefixes can be
included to extend the value.Instruction data values in the range -256 to 255 can be
represented using one prefixinstruction.
When the processor encounters an instruction component other than
pfix
or
nfix
,it
loads the data field into the instruction data value. The instruction encoding is now
complete and the instruction can be executed. When the processor is ready to fetch
the next instruction component, it starts to create a new instruction data value.
4.1.3 Primary Instructions
Research has shown that computers spend most of the time executing instructions
such as: instructions to load and store from a small number of ‘local’ variables,
instructions to add and compare with small constants, and instructions to jump to or
call other parts of the program. For efficiency therefore, these are encoded directly as
primary instructions using the function field of an instruction component.
Thirteen of the instruction components are used to encode the most important
operations performed by any computer executing a high level language. These are
used (in conjunction with zeroor more prefixes) to implement the primary instructions.
Primary instructions interpret the instruction data value as an operand for the
instruction. The mnemonic for a primary instruction will therefore normally include a
this operand - n - when referenced.
The mnemonics and names for the primary instructions are listed in Table4.2.
mnemonic name
pfix
n prefix
nfix
n negative prefix
Table 4.1 Prefixinginstruction components
mnemonic name
adc
n add constant
Table 4.2 Primary instructions
† Note that it inverts
all
32 bits of the instruction data value.
Page 27

27/212
4.1.4 Secondary instructions
The ST20 encodes all other instructions (secondary instructions) indirectly using the
instruction data value.
The instruction component
opr
causes the instruction data value to be interpreted as
the operation code of the instruction to be executed. This selects an operation to be
performed on the valuesheld in the integer stack.This allows a further 16 operations
to be encoded in a singlebyte instruction. Howeverthe prefix instructions can be used
to extend the instruction data value, allowing any number of operations to be
performed.
Secondary instructions do not have an operand specified by the encoding, because
the instruction data value has been used to specify the operation.
To ensure that programs are represented as compactly as possible,the operations are
encoded in such a way that the most frequent secondary instructions are represented
without usingprefix instructions.
4.1.5 Summary of encoding
The encoding mechanism has important consequences.
• Firstly, it simplifies language compilation, by providing a completely uniform
way of allowing a primary instruction to takean operand of anysize up to the
processor word-length.
• Secondly,it allowsthese operands to be represented ina form independent of
ajw
n adjust workspace
call
n call
cj
n conditional jump
eqc
n equals constant
j
n jump
ldc
n load constant
ldl
n load local
ldlp
n load local pointer
ldnl
n load non-local
ldnlp
n load non-local pointer
stl
n store local
stn
l n store non-local
mnemonic name
opr
operate
Table 4.3 Operate instruction
mnemonic name
Table 4.2 Primary instructions
Page 28

28/212
the word-lengthof the processor.
• Thirdly,it enablesany number of secondary instructions to be implemented.
The following provides some simple examples of encoding:
• The instruction
ldc
17 is encoded with the sequence:
pfix1;ldc
1
• The instruction
add
is encoded by:
opr
5
• The instruction
and
is encoded by:
opr 70
which isin turn encoded with the sequence:
pfix4;opr
6
To aid clarity and brevity, prefix sequences and the use of
opr
are not explicitlyshown
in this guide. Each instruction is represented by a mnemonic, and for primary
instructions an item of data, which stands for the appropriate instruction component
sequence. Hence in the above examples, these are just shown as:
ldc 17,add
, and
and
. (Also, where appropriate, an expression may be placed in a code sequence to
represent the code needed toevaluatethat expression.
4.2 Generating prefix sequences
Prefixing is intended to be performed by a compiler or assembler.Prefixing by hand is
not advised.
Normally a value can be loaded into the instruction data valueby a variety of different
prefix sequences . It is important to use the shortest possible sequence as this
enhances both code compaction and executionspeed. The best method of optimizing
object code so as to minimize the number of prefix instructions needed is shown
below.
4.2.1 Prefixinga constant
The algorithm to generate a constant instruction data valueefor a function
op
is
described bythe following recursive function.
prefix(op,e ) = IF
e<16 AND e 0
op( e )
e 16
prefix(pfix, e
>>
4 ); op( e∧#F)
e<0
prefix(nfix, (~e)
>>
4 ); op( e∧#F)
where
( op,e )
is the instruction component with function codeopand data field
e, ~
is a bitwise NOT, and >> is a logical right shift.
Page 29

29/212
4.2.2 Evaluating minimal symbol offsets
Several primary instructions have an operand that is an offset between the current
value of the instruction pointer and some other part of the code. Generating the
optimal prefix sequence to create the instruction data value for one of these
instructions is more complicated. This is because two, or more, instructions with offset
operands can interlock so that the minimal prefix sequences for each instruction is
dependent on the prefixingsequences used for theothers.
For example consider the interlocking jumps below which can be prefixed in two
distinct ways. The instructionsjandcjare respectively
jump
and
conditional jump
.
These are explained in more detail later.The sequence:
cj
+16;j-257
can be coded as
pfix1;cj0;pfix1;nfix0;j
15
but this can be optimizedto be
cj
15;
nfix
15;j1
which is the encoding for the sequence
cj
+15;j-255
This is because when the two offsets are reduced, their prefixing sequences take 1
byte less so that the two interlocking jumps will still transfer control to the same
instructions as before.This compaction of non-optimal prefix sequences is difficult to
perform and a better method is to slowly build up the prefix sequences so that the
optimal solutionis achieved.The following algorithm performs this.
1 Associate with eachjump instruction or offset loadan ‘estimate’ ofthe number
of bytes required to code it and initially set them all to 0.
2 Evaluate all jump and load offsets under the current assumptions of the sizeof
prefixsequences to the jumps and offset loads
3 For each jump or load offset set the number of bytes needed to the numberin
the shortest sequence that will build up the current offset.
†
4 If any change was made to the number of bytesrequired then go backto 2 oth-
erwise the code has reached astable state.
The stable state that is achievedwill be the optimal state.
Steps 2 and 3 can be combined so that the number of bytes required by each jump is
updated as the offset is calculated. This does mean that if an estimate is increased
then some previously calculated offsets may have been invalidated, but step 4 forces
another loop to be performed when those offsets can be corrected.
By initially setting the estimated size of offsets to zero, all jumps whose destination is
the next instruction are optimized out.
† Where thecode being analyzed hasalignment directives, then it ispossible that this algorithm will notreach a stable state. One
solution to this, is to allow the algorithm to increase the instruction size but not allow it to reduce the size. This is achieved by
modifying stage 3 to choose the larger of: the currently calculated length, and the previously calculated length. This approach
does not always lead to minimal sizedcode, but it guarantees termination of the algorithm.
Page 30

30/212
Knowledge of the structure of code generated by the compiler allows this process to
be performed on individual blocks of code rather than on the whole program. For
example it is often possible to optimize the prefixing in the code for the subcomponents ofa programminglanguage constructbefore the code for the construct is
optimized. When optimizing the construct it is known that the sub-components are
already optimal so they can be considered as an unshrinkableblock of code.
This algorithm may not be efficient for long sections of code whose underlying
structure is not known. If no knowledge of the structure is available (e.g. in an
assembler), all the code must be processed at once. In this case a code shrinking
algorithm where in step one the initial number of bytes is set to twice the number of
bytes per wordis used. The prefixsequences then shrink on each iteration of the loop.
1 or 2 iterations produce fairlygood codealthough this method will notalwaysproduce
optimal code as it will not correctly prefix the pathological example givenabove.
Page 31

31/212
5 Instruction Set Reference
Page 32

adc n
32/212
adc
n add constant
Code: Function 8
Description: Add a constant to Areg, with checkingfor overflow.
Definition:
Areg′←Areg +
checked
n
Error signals:
IntegerOverflow
can be signalled by +
checked
Comments:
Primary instruction.
See also:
add ldnlp sum
Page 33

add
33/212
add
add
Code: F5
Description: Add Areg and Breg, with checkingfor overflow.
Definition:
Areg′←Breg +
checked
Areg
Breg′←Creg
Creg′←
undefined
Error signals:
IntegerOverflow
can be signalled by+
checked
Comments:
Secondary instruction.
See also:
adc sum
Page 34

ajw n
34/212
ajw
n adjust workspace
Code: Function B
Description: Move the workspace pointer by the number of words specified in the
operand, in order to allocate orde-allocate the workspace stack.
Definition:
Wptr′←Wptr @ n
Error signals: none
Comments:
Primary instruction.
See also:
call gajw
Page 35

alt
35/212
alt
alt start
Code: 24 F3
Description: Start of a non-timer alternative sequence. The pw.State location of the
workspace isset to
Enabling.p.
Definition:
word′[Wptr @ pw.State] ← Enabling.p
Enter alternativesequence
Error signals: none
Comments:
Secondary instruction.
See also:
altend altwt disc diss dist enbc enbs enbt talt taltwt
Page 36

altend
36/212
altend
alt end
Code: 24 F5
Description: End of alternative sequence. Jump to start of selected process.
Definition:
Terminate alternativesequence
Iptr′←
next instruction
+ word [Wptr @ pw.Temp]
Error signals: none
Comments:
Secondaryinstruction.
Uses the pw.Temp slot in the process workspace.
See also:
alt altwt disc diss dist enbc enbs enbt talt taltwt
Page 37

altwt
37/212
altwt
alt wait
Code: 24 F4
Description: Wait until one of the enabled guards of an alternative has become
ready,and initialize workspace foruse during the disabling sequence.
Definition:
if (word[Wptr @ pw.State]≠ Ready.p)
{
word′[Wptr @ pw.State] ← Waiting.p
Deschedule process and waitfor one of the guards to become ready
}
word′[Wptr @ pw.Temp] ← NoneSelected.o
Areg′←
undefined
Breg′←
undefined
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
Instruction is a descheduling point.
Uses the pw.Temp slot in the process workspace.
See also:
alt altend disc diss dist enbc enbs enbt talt taltwt
Page 38

and
38/212
and
and
Code: 24 F6
Description: Bitwise and of Areg and Breg.
Definition:
Areg′←Breg ∧ Areg
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondaryinstruction.
See also:
not or xor
Page 39

bcnt
39/212
bcnt
byte count
Code: 23 F4
Description: Produce the length, in bytes, of a multiword data object. Converts the
value in Areg, representing a number of words, to the equivalent number of bytes.
Definition:
Areg′←Areg ×BytesPerWord
Error signals: none
Comments:
Secondary instruction.
Page 40

bitcnt
40/212
bitcnt
count bits set in word
Code: 27 F6
Description: Count the number of bits set in Areg and addthis to the value in Breg.
Definition:
Areg′←Breg +
number of bits set to 1 in
Areg
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondaryinstruction.
Page 41

bitrevnbits
41/212
bitrevnbits
reverse bottom n bits in word
Code: 27 F8
Description: Reverse the order of the bottomAreg bits ofBreg.
Definition:
if (0 ≤ Areg) and (Areg ≤ BitsPerWord)
{
Areg′
0..Areg-1
←
reversed
Breg
0..Areg-1
Areg′
Areg..BitsPerWord-1
← 0
}
else
Undefinedeffect
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
The effect of the instruction is undefinedif the number of bits specifiedis more
than the wordlength.
See also:
bitrevword
Page 42

bitrevword
42/212
bitrevword
reversebits in word
Code: 27 F7
Description: Reverse the order of all thebits inAreg.
Definition:
Areg′←
reversed
Areg
Error signals: none
Comments:
Secondaryinstruction.
See also:
bitcnt bitrevnbits
Page 43

bsub
43/212
bsub
byte subscript
Code: F2
Description: Generate the address of the element which is indexedby Breg, in the
byte array pointed to byAreg.
Definition:
Areg′←Areg +Breg
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
See also:
ssub sum wsub wsubdb
Page 44

call n
44/212
call
n call
Code: Function 9
Description: Adjust workspace pointer, saveevaluation stack, and call subroutine at
specifiedbyte offset.
Definition:
Wptr′←Wptr @ -4
word′[Wptr′ @0] ← Iptr
word′[Wptr′ @1] ← Areg
word′[Wptr′ @2] ← Breg
word′[Wptr′ @3] ← Creg
Iptr′←
next instruction
+ n
Areg′←Iptr
Breg′←
undefined
Creg′←
undefined
Error signals: none
Comments:
Primary instruction.
See also:
ajw gcall ret
Page 45

causeerror
45/212
causeerror
cause error
Code: 62 FF
Description: Take a trap with the trap type set to the value in Areg. Only one bit in
Areg should be set; the position of the bit indicates the trap to be signalled. When the
trap is taken the causeerror bit in the status register is set to indicate a user generated
trap.
In the case of a scheduler trap being set then the bottom bit of Breg is used to
determine the priority of the scheduler trap. In addition when the scheduler trap is
trapping a process scheduling operation(e.g. the
run
trap) the Breg is interpreted as
the process descriptor to be scheduled.
Definition:
if (Areg=2i) and (
trap typeiis enabled
)
{
set causeerror bit in Status
cause trap type
i
}
else
Undefinedeffect
Error signals: The causeerror bit is set and the indicated trap signalled if enabled.
Comments:
Secondary instruction.
Sets traps independently of trapenables state.
See also:
tret sttraph ldtrap
Page 46

cb
46/212
cb
check byte
Code: 2B FA
Description: Check that the value in Areg can be represented as an 8-bit signed
integer.
Definition:
if (Areg < -27) or (Areg ≥ 27)
IntegerError
Error signals:
IntegerError
signalled ifAreg is not in range.
Comments:
Secondaryinstruction.
See also:
cbu cir ciru cs csu
Page 47

cbu
47/212
cbu
check byte unsigned
Code: 2B FB
Description: Check that the value in Areg can be represented as an 8-bit unsigned
integer.
Definition:
if (Areg < 0) or (Areg ≥ 28)
IntegerError
Error signals:
IntegerError
signalled if Areg is not in range.
Comments:
Secondary instruction.
See also:
cb cir ciru cs csu
Page 48

ccnt1
48/212
ccnt1
check count from 1
Code: 24 FD
Description: Check that Breg is inthe range1..Areg inclusive,interpreting Areg and
Breg as unsigned numbers.
Definition:
if (Breg = 0) or (Breg
unsigned
> Areg
unsigned
)
IntegerError
Areg′←Breg
Breg′←Creg
Creg′←
undefined
Error signals:
IntegerError
signalled ifAreg is not in range.
Comments:
Secondaryinstruction.
See also:
csub0
Page 49

cflerr
49/212
cflerr
check floatingpoint error
Code: 27 F3
Description: Checks if Areg represents an Inf or NaN.
Definition:
if (Areg ∧ #7F800000 = #7F800000)
IntegerError
Error signals:
IntegerError
signalled if Areg represents an Inf or NaN.
Comments:
Secondary instruction.
See also:
unpacksn roundsn postnormsn ldinf
Page 50

cir
50/212
cir
check in range
Code: 2C F7
Description: Check that Creg is in the range Areg..Breg inclusive.
Definition:
if (Creg < Areg) or (Creg > Breg)
IntegerError
Areg′←Creg
Breg′←
undefined
Creg′←
undefined
Error signals:
IntegerError
signalled ifCreg is not in range.
Comments:
Secondaryinstruction.
See also:
ciru
Page 51

ciru
51/212
ciru
check in range unsigned
Code: 2C FC
Description: Check that Creg is the range Areg..Breg inclusive, treating all as
unsigned values.
Definition:
if (Creg
unsigned
< Areg
unsigned
) or (Creg
unsigned
> Breg
unsigned
)
IntegerError
Areg′←Creg
Breg′←
undefined
Creg′←
undefined
Error signals:
IntegerError
signalled ifCreg is not in range.
Comments:
Secondary instruction.
See also:
cir
Page 52

cj n
52/212
cj
n conditional jump
Code: Function A
Description: Jump if Areg is 0 (i.e. jump if
false
). The destination of the jump is
expressed as a byteoffset from the instruction following.
Definition:
if (Areg = 0)
Iptr′←
next instruction
+ n
else
{
Iptr′←
next instruction
Areg′←Breg
Breg′←Creg
Creg′←
undefined
}
Error signals: none
Comments:
Primary instruction.
See also:
j lend
Page 53

clockdis
53/212
clockdis
clock disable
Code: 64 FE
Description: Stops the clocksspecified in bits 0 and 1 of Areg where bit 0 indicates
the high priority clock and bit 1 the low priority clock. The original values of these two
clock enable bits are returned in Areg.
Definition:
Areg′
1..0
← ClockEnables
Areg′
31..2
← 0
ClockEnables′←ClockEnables ∧ ∼Areg
Error signals: none
Comments:
Secondary instruction.
See also:
clockenb
Page 54

clockenb
54/212
clockenb
clock enable
Code: 64 FF
Description: Starts or restarts the clocks specified in bits 0 and 1 of Areg, where bit
0 indicates the high priority clock and bit 1 indicates the low priority clock. The original
values of these twoclock enable bits are returned in Areg.
Definition:
Areg′
1..0
← ClockEnables
Areg′
31..2
← 0
ClockEnables′←ClockEnables ∨ Areg
Error signals: none
Comments:
Secondaryinstruction.
See also:
clockdis
Page 55

clrhalterr
55/212
clrhalterr
clear halt-on-error
Code: 25 F7
Description: Clear the HaltOnError flag.
Definition:
HaltOnErrorFlag′←
clear
Error signals: none
Comments:
Secondary instruction.
See also:
sethalterr testhalterr
Page 56

crcbyte
56/212
crcbyte
calculate CRC on byte
Code: 27 F5
Description: Generate a CRC (cyclic redundancy check) checksum from the most
significant byte of Areg. Breg contains the previously accumulated checksum and
Creg the polynomial divisor (or ‘generator’). The new CRC checksum, the polynomial
remainder, is calculated by repeatedly (8 times) shifting the accumulated checksum
left, shifting in successivebits from the Areg and if the bit shifted out of the checksum
was a 1,then the generator is exclusive-ored into the checksum.
Definition:
Areg′←temp(8)
Breg′←Creg
Creg′←
undefined
where
temp(0) = Breg
for i = 1..8
temp(i) = (temp(i -1) << 1) + Areg
BitsPerWord-i
)
⊗ (Creg ×temp(i −1)
BitsPerWord-1
)
Error signals: none
Comments:
Secondaryinstruction.
See also:
crcword
Page 57

crcword
57/212
crcword
calculate CRC on word
Code: 27 F4
Description: Generate a CRC (cyclic redundancy check)checksum from Areg. Breg
contains the previously accumulated checksum and Creg the polynomial divisor (or
‘generator’). The new CRC checksum, the polynomial remainder, is calculated by
repeatedly (BitsPerWord times) shifting the accumulated checksum left, shifting in
successive bits from the Areg and if the bit shifted out of the checksumwas a 1, then
the generator is exclusive-ored into the checksum.
Definition:
Areg′←temp(BitsPerWord)
Breg′←Creg
Creg′←
undefined
where
temp(0) = Breg
for i = 1..32
temp(i) = (temp(i -1) << 1) + Areg
BitsPerWord-i
)
⊗ (Creg × temp(i −1)
BitsPerWord-1
)
Error signals: none
Comments:
Secondary instruction.
See also:
crcbyte
Page 58

cs
58/212
cs
check sixteen
Code: 2F FA
Description: Check that the value in Areg can be represented as a 16-bit signed
integer.
Definition:
if (Areg < -215) or (Areg ≥ 215)
IntegerError
Error signals:
IntegerError
signalled ifAreg is not in range.
Comments:
Secondaryinstruction.
See also:
cb cbu cir ciru csngl csucword
Page 59

csngl
59/212
csngl
check single
Code: 24 FC
Description: Check that the two word signed value in Areg and Breg (most
significantword in Breg) can be represented as a single length signed integer.
Definition:
if ((Areg ≥ 0) and (Breg ≠ 0)) or ((Areg < 0) and (Breg ≠ −1))
IntegerError
Error signals:
IntegerError
signalled if Areg is not in range.
Comments:
Secondary instruction.
See also:
cb cbu cir ciru cs csu cword
Page 60

csu
60/212
csu
check sixteen unsigned
Code: 2F FB
Description: Check that the value in Areg can be represented as a 16-bit unsigned
integer.
Definition:
if (Areg < 0) or (Areg ≥ 216)
IntegerError
Error signals:
IntegerError
signalled ifAreg is not in range.
Comments:
Secondaryinstruction.
See also:
cb cbu cir ciru cs csngl cword
Page 61

csub0
61/212
csub0
check subscript from 0
Code: 21 F3
Description: Check that Breg is in therange 0..(Areg-1), interpretingAreg and Breg
as unsigned numbers.
Definition:
if (Breg
unsigned
≥ Areg
unsigned
)
Integer Error
Areg′←Breg
Breg′←Creg
Creg′←
undefined
Error signals:
IntegerError
signalled if Breg is not in range.
Comments:
Secondary instruction.
See also:
ccnt1
Page 62

cword
62/212
cword
check word
Code: 25 F6
Description: Check that the value in Breg can be represented as an N-bit signed
integer. Areg contains 2
(N-1)
to indicate the valueof N (i.e. bit N-1 of Areg is set to 1
and allother bits are set tozero).
Definition:
if (Breg <−Areg) or (Breg ≥ Areg)
IntegerError
Areg′←Breg
Breg′←Creg
Creg′←
undefined
Error signals:
IntegerError
signalled ifBreg is not in range.
Comments:
The result of the instruction is undefinedif Areg is not an integral power of 2.
Undefinedif Areg has more than one bit set.
Secondaryinstruction.
See also:
cb cs csngl xword
Page 63

devlb
63/212
devlb
device load byte
Code: 2F F0
Description: Perform a device read from memory, a memory-mapped device or a
peripheral. The byte addressed by Areg is read into Areg as an unsigned value. The
memoryaccess performed by this instruction is guaranteed to be correctly sequenced
with respect to other device-accessinstructions. Also the instruction is guaranteed to
be executedafter allnormal memory load instructions thatappear beforeit in the code
sequence, and before all normal memory loads that appear later.
Definition:
if (PeripheralStart ≤ Areg ≤ PeripheralEnd)
Areg′
0..7
← PeripheralByte[Areg]
else
Areg′
0..7
← byte[Areg]
Areg′
8..31
← 0
Error signals: none
Comments:
Secondary instruction.
See also:
devls devlw devsb lb
Page 64

devls
64/212
devls
device load sixteen
Code: 2F F2
Description: Perform a device read from memory, a memory-mapped device or a
peripheral. The 16-bit object addressed by Areg is read into Areg as an unsigned
value. The memory access performed by this instruction is guaranteedto be correctly
sequenced with respect to other device-access instructions. Also the instruction is
guaranteed to be executed after all normal memory load instructions that appear
before it in the code sequence,and beforeall normal memory loads that appear after
it.
Definition:
if (PeripheralStart ≤ Areg ≤ PeripheralEnd)
Areg′
0..15
← PeripheralSixteen[Areg]
else
Areg′
0..15
← sixteen[Areg]
Areg′
16..31
← 0
Error signals: none
Comments:
Secondaryinstruction.
See also:
devlb devlw devsbls
Page 65

devlw
65/212
devlw
device load word
Code: 2F F4
Description: Perform a device read from memory, a memory-mapped device or a
peripheral. The word addressed by Areg is read into Areg. The memory access
performed by this instruction is guaranteed to be correctly sequenced with respect to
other device-access instructions. Also the instruction is guaranteed to be executed
after all normal memory load instructions that appear before it in the code sequence,
and before all normal memory loads that appear after it.
Definition:
if (PeripheralStart ≤ Areg ≤ PeripheralEnd)
Areg′←PeripheralWord[Areg]
else
Areg′←word[Areg]
Error signals: none
Comments:
Secondary instruction.
See also:
devlb devls devswldnl
Page 66

devmove
66/212
devmove
device move
Code: 62 F4
Description: Perform a device copy between memory or memory-mapped devices.
Copies Areg bytes to address Breg from address Creg. Onlythe minimumnumber of
reads and writes required to copy the data will be performed. Each read will be to a
strictly higher (more positive) address than the one before and each write will be to a
strictly higher byte address than the one before.There is no guarantee of the relative
ordering of read and write cycles, except that a write cannot occur until the
corresponding read has been performed. The memory accesses performed by this
instruction are guaranteed to be correctly sequenced with respect to other deviceaccess instructions. Also the instruction is guaranteed to be executed after all normal
memoryaccess instructions that appear before it in the code sequence, and before all
normal memory accesses that appear after it.
Definition:
if (
source and destination overlap
)
Undefinedeffect
else for i = 0 .. (Areg
unsigned
− 1)
byte′[Breg + i] ← byte[Creg + i]
Areg′←
undefined
Breg′←
undefined
Creg′←
undefined
Error signals: none
Comments:
Secondaryinstruction.
The effect of the instruction is undefinedif the source and destination overlap.
Instruction is interruptible.
Devmovewill not operate from or to peripheraladdresses.
See also:
move
Page 67

devsb
67/212
devsb
device store byte
Code: 2F F1
Description: Perform a device write from memory, a memory-mapped device or a
peripheral. Store the least significant byte of Breg into the byte addressed by Areg.
The memory access performed by this instruction is guaranteed to be correctly
sequenced with respect to other device-access instructions. Also the instruction is
guaranteed to be executed after all normal memory store instructions that appear
before it in the code sequence,and beforeall normal memory stores that appear after
it.
Definition:
if (PeripheralStart ≤ Areg ≤ PeripheralEnd)
PeripheralByte′[Areg] ← Breg
0..7
else
byte′[Areg] ← Breg
0..7
Areg′←Creg
Breg′←
undefined
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
See also:
devlb devss devswsb
Page 68

devss
68/212
devss
device store sixteen
Code: 2F F3
Description: Perform a device write from memory, a memory-mapped device or a
peripheral. Store bits 0..5 of Breg into the sixteen bits addressed byAreg. A memory
access performed by this instruction is guaranteed to be correctly sequenced with
respect to other device-access instructions. Also the instruction is guaranteed to be
executed after all normal memory store instructions that appear before it in the code
sequence, and before all normal memory stores that appearafter it.
Definition:
if (PeripheralStart ≤ Areg ≤ PeripheralEnd)
PeripheralSixteen′[Areg]← Breg
0..15
else
sixteen′[Areg] ← Breg
0..15
Areg′←Creg
Breg′←
undefined
Creg′←
undefined
Error signals: none
Comments:
Secondaryinstruction.
See also:
devls devsb devsw ss
Page 69

devsw
69/212
devsw
device store word
Code: 2F F5
Description: Perform a device write from memory, a memory-mapped device or a
peripheral. Store Breg into the word of memory addressed by Areg. The memory
access performed by this instruction is guaranteed to be correctly sequenced with
respect to other device-access instructions. Also the instruction is guaranteed to be
executed after all normal memory store instructions that appear before it in the code
sequence, and before all normal memory stores that appear after it.
Definition:
if (PeripheralStart ≤ Areg ≤ PeripheralEnd)
PeripheralWord′[Areg] ← Breg
else
word′[Areg] ← Breg
Areg′←Creg
Breg′←
undefined
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
See also:
devlw devsb devss stnl
Page 70

diff
70/212
diff
difference
Code: F4
Description: Subtract Areg from Breg, without checkingfor overflow.
Definition:
Areg′←Breg − Areg
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondaryinstruction.
See also:
sub
Page 71

disc
71/212
disc
disable channel
Code: 22 FF
Description: Disable a channel guard in an alternative sequence. Areg is the offset
from the byte following the
altend
to the start of the guarded process, Breg is the
boolean guard andCreg is a pointer to the channel. If this is the first ready guard then
the value in Areg is stored in workspace and Areg is set to
true
, otherwise Areg is set
to
false
. Note that this instruction should be used as part of an alternative sequence
following an
altwtortaltwt
instruction.
Definition:
if (Breg =
false
)–
boolean guard is false
Areg′←
false
else if (Creg
is internal channel
)
{
if (word[Creg] = NotProcess.p) –
guard already disabled
Areg′←
false
else if (word[Creg] =Wdesc)
– this guard is not ready
{
word′[Creg] ← NotProcess.p
Areg′←
false
}
else if (word[Wptr @ pw.Temp] = NoneSelected.o)
{
– this is the firstready guard
word′[Wptr @ pw.Temp] ← Areg
Areg′←
true
}
else
– a previousguard selected
Areg′←
false
}
else if (Creg i
s external channel
)
{
Disable comms subsystem and receive status
if (
channel not ready
)
– channel not waiting
Areg′←
false
else if (word[Wptr @ pw.Temp] = NoneSelected.o)
{–
this is the first ready guard
word′[Wptr @ pw.Temp] ← Areg
Areg′←
true
}
else
- a previous guard selected
Areg′←
false
}
Breg′←
undefined
Creg′←
undefined
Page 72

disc
72/212
Error signals: none
Comments:
Secondaryinstruction.
Uses the pw.Temp slot in the process workspace.
See also:
alt altend altwt enbc talt taltwt
Page 73

diss
73/212
diss
disable skip
Code: 23 F0
Description: Disable a ‘skip’ guard in an alternative sequence. Areg is the offset
from the byte following the
altend
to the start of the guarded process and Breg is the
boolean guard. If this is the first ready guard then the value in Areg is stored in
workspace and Areg is set to
true
, otherwise Areg is set to
false
. Note that this
instruction should be used as part of an alternative sequence following an
altwt
or
taltwt
instruction.
Definition:
if (Breg =
false
)–
boolean guard is false
Areg′←
false
else if (word[Wptr @ pw.Temp] = NoneSelected.o)
Areg′←
false – this is the firstready guard
else –
another guard was selected
{
word′[Wptr @ pw.Temp] ← Areg
Areg′←
true
}
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
Uses the pw.Temp slot in the process workspace.
See also:
alt altend altwt enbs talt taltwt
Page 74

dist
74/212
dist
disable timer
Code: 22 FE
Description: Disable a timer guard in an alternative sequence. Areg is the offset
from the byte following the
altend
to the start of the guarded process, Breg is the
boolean guard and Creg is the time after which this guard will be ready. If this is the
first ready guard then the value in Areg is stored in pw.Temp, andAreg is set to
true
.
Note that this instruction should be used as part of an alternativesequence following a
taltwt
instruction.
Definition:
if (Breg =
false
)–
boolean guard is false
Areg′←
false
else if (word[Wptr @ pw.TLink]= TimeNotSet.p)
– no timer is ready
Areg′←
false
else if (word[Wptr @ pw.TLink]= TimeSet.p) –
a timer is ready
{
if not (word[Wptr @ pw.Time] after Creg)
– but not this one
Areg′←
false
else if (word[Wptr @ pw.Temp] = NoneSelected.o)
– this is the firstready guard
{
word′[Wptr @ pw.Temp] ← Areg
Areg′←
true
}
else
– a previousguard selected
Areg′←
false
}
else
Areg′←
false
Remove this process from the timer list
Breg′←
undefined
Creg′←
undefined
Error signals: none
Comments:
Secondaryinstruction.
Instruction is interruptible.
Uses the pw.Temp slot in the process workspace.
See also:
altend enbt talt taltwt
Page 75

div
75/212
div
divide
Code: 22 FC
Description: Divide Breg by Areg, with checking for overflow. The result when not
exact is rounded towardszero.
Definition:
if (Areg = 0) or ((Breg = MostNeg) and (Areg = -1))
{
Areg′←
undefined
IntegerOverflow
}
else
Areg′←Breg / Areg
Breg′←Creg
Creg′←
undefined
Error signals:
IntegerOverflow
can be signalled.
Comments:
Secondary instruction.
See also:
rem
Page 76

dup
76/212
dup
duplicate top of stack
Code: 25 FA
Description: Duplicate the top of the integer stack.
Definition:
Areg′←Areg
Breg′←Areg
Creg′←Breg
Error signals: none
Comments:
Secondaryinstruction.
See also:
pop rev
Page 77

enbc
77/212
enbc
enable channel
Code: 24 F8
Description: Enable a channel guard in an alternative sequence. Areg is the
boolean guard and Breg is a pointer to the channel. Note that this instruction should
only be used as part of an alternative sequence following an
altortalt
instruction.
Definition:
if (Areg ≠
false
)
{
if (Breg
is internal channel
)
{
if (word[Breg] = NotProcess.p) –
not ready
word′[Breg] ← Wdesc
else if (word[Breg] ≠ Wdesc) –
not previously enabled
word′[Wptr @ pw.State] ← Ready.p
}
else if (Breg
is external channel
)
{
Request Comms Subsystem to enableexternal channel
and receivecurrent status of channel
if (
channel ready
)-
word′[Wptr @ pw.State] ← Ready.p
}
}
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
See also:
alt altend altwt disc talt taltwt
Page 78

enbs
78/212
enbs
enable skip
Code: 24 F9
Description: Enable a ‘skip’ guard in an alternative sequence. Areg is the boolean
guard. Note that this instruction should only be used as part of an alternative
sequence following an
altortalt
instruction.
Definition:
if (Areg ≠
false
)
word′[Wptr @ pw.State] ← Ready.p
Error signals: none
Comments:
Secondaryinstruction.
See also:
alt altend altwt diss talt taltwt
Page 79

enbt
79/212
enbt
enable timer
Code: 24 F7
Description: Enable a timer guard in an alternative sequence. Areg is the boolean
guard and Breg is the time after which the guard may be selected. Note that this
instruction should only be used as part of an alternative sequence following a
talt
instruction; in this case the location pw.State will have been initialized to
Enabling.p
and thepw.Tlink slot initialized to
TimeNotSet.p
.
Definition:
if (Areg ≠
false
)
{
if (word[Wptr @ pw.TLink]= TimeNotSet.p) –
this is the first enbt
{
word′[Wptr @ pw.TLink] ← TimeSet.p
word′[Wptr @ pw.Time] ← Breg
}
else if (word[Wptr @ pw.TLink]= TimeSet.p) –
this is not the firstenbt
{
if (word[Wptr @ pw.Time]after Breg) –
this enbt has earlier time
word′[Wptr @ pw.Time] ← Breg
}
}
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
See also:
altend dist talt taltwt
Page 80

endp
80/212
endp
end process
Code: F3
Description: Synchronize the termination of a parallel construct. When all branches
have executed an
endp
instruction a ‘successor’ process then executes. Areg points
to the workspace of this successor process.This workspace contains a data structure
which holds the instruction pointer of the successor process and the number of
processes still active.
Definition:
if (word[Areg @ pp.Count]= 1)
{
Iptr′←word[Areg @ pp.IptrSucc]
Wptr′←Areg
}
else
word′[Areg @ pp.Count] ← word[Areg @ pp.Count]−1
start nextprocess
Areg′←
undefined
Breg′←
undefined
Creg′←
undefined
Error signals: none
Comments:
Secondaryinstruction.
Instruction is a descheduling point.
See also:
startp stopp
Page 81

eqc n
81/212
eqc
n equals constant
Code: Function C
Description: Compare Areg to a constant.
Definition:
if (Areg = n)
Areg′←
true
else
Areg′←
false
Error signals: none
Comments:
Primary instruction.
Page 82

fmul
82/212
fmul
fractional multiply
Code: 27 F2
Description: Multiply Areg by Breg treating the values as fractions, rounding the
result. The values in Areg and Breg are interpreted as fractions in the range greater
than or equal to -1 and less than 1 - i.e. the integer values divided by 2
BitsPerWord-1
.
The result is rounded. The rounding mode used is analogous to IEEE round nearest;
that is the result produced is the fraction which is nearest tothe exactproduct, and, in
the event of the product being equidistant between two factions, the fraction with least
significantbit 0 is produced.
Definition:
if (Areg = MostNeg) and (Breg = MostNeg)
– MostNeg interpreted as -1
{
Areg′←
undefined
IntegerOverflow
}
else
Areg′←(Breg × Areg) /
roundnearest
2
BitsPerWord-1
Breg′←Creg
Creg ←
undefined
Error signals:
IntegerOverflow
can occur.
Comments:
Secondaryinstruction.
Page 83

fptesterr
83/212
fptesterr
test for FPU error
Code: 29 FC
Description: Test for an error in the FPU, if present. This instruction always returns
true
on a processor without an FPU.
Definition:
Areg′←
true
Breg′←Areg
Creg′←Breg
Error signals: none
Comments:
Secondary instruction.
Page 84

gajw
84/212
gajw
general adjust workspace
Code: 23 FC
Description: Set the workspace pointer to the address in Areg, saving the previous
value in Areg.
Definition:
Wptr′←Areg
Areg′←Wptr
Error signals: none
Comments:
Secondaryinstruction.
Areg should be word aligned.
See also:
ajw call gcall
Page 85

gcall
85/212
gcall
general call
Code: F6
Description: Jump to the address in Areg, savingthe previousaddress inAreg.
Definition:
Iptr′←Areg
Areg′←Iptr
Error signals: none
Comments:
Secondary instruction.
See also:
ajw call gajw ret
Page 86

gintdis
86/212
gintdis
global interrupt disable
Code: 2C FD
Description: Disable the global interrupt events specified in the bit mask in Areg.
This allows parts of the built-in scheduler, such as response to external events,
timeslicing etc., to be disabled by software. The original value of the global interrupt
enable register is returned in Areg.
Definition:
GlobalInterruptEnables′← GlobalInterruptEnables ∧ ∼Areg
7..0
Areg′
7..0
← GlobalInterruptEnables
Areg′
31..8
← 0
Error signals: none
Comments:
Secondaryinstruction.
See also:
gintenb
Page 87

gintenb
87/212
gintenb
global interrupt enable
Code: 2C FE
Description: Enable the global interrupt events specified in the bit mask in Areg.
Definition:
GlobalInterruptEnables′← GlobalInterruptEnables ∨ Areg
7..0
Areg′
7..0
← GlobalInterruptEnables
Areg′
8..31
← 0
Error signals: none
Comments:
Secondary instruction.
See also:
gintdis
Page 88

gt
88/212
gt
greater than
Code: F9
Description: Compare the top two elements of the stack, returning
true
if Breg is
greater than Areg.
Definition:
if (Breg > Areg)
Areg′←
true
else
Areg′←
false
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondaryinstruction.
Page 89

gtu
89/212
gtu
greater than unsigned
Code: 25 FF
Description: Compare the top two elements of the stack, treating both as unsigned
integers, returning
true
if Breg is greater than Areg.
Definition:
if (Breg
unsigned
> Areg
unsignded
)
Areg′←
true
else
Areg′←
false
Breg′←Creg
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
Page 90

in
90/212
in
input message
Code: F7
Description: Input a message. The corresponding output is performed by an
out
,
outwordoroutbyte
instruction, and must specify a message of the same length. Areg
is the unsigned length in bytes,Breg is a pointer to the channel and Creg is a pointer
to where the message is to be stored. The process executinginwill be descheduled if
the channel is external or is not ready,and is rescheduled whenthe communicationis
complete.
Definition:
Synchronize, and input
Areg
unsigned
bytes from channel
Breg
to address
Creg
Areg′←
undefined
Breg′←
undefined
Creg′←
undefined
Error signals: Can cause
InternalChannelorExternalChannel
trap to be signalled (if
enabled) when the process is rescheduled after synchronization.
Comments:
Secondaryinstruction.
Instruction is a descheduling point.
Instruction is interruptible.
See also:
out
Page 91

insertqueue
91/212
insertqueue
insert at front of scheduler queue
Code: 60 F2
Description: Insert a list of processes at the front of the scheduling list of priority
indicated by Areg, where 0 indicates high priority and 1 indicates low priority. Breg
and Creg are the front and back, respectively,of thelist to be inserted.
Definition:
if (Breg ≠ NotProcess.p)
{
ProcQueueFPtr′[Areg]←Breg
if (ProcQueueFPtr[Areg] = NotProcess.p)
ProcQueueBPtr′[Areg]←Creg
else
word′[Creg @ pw.Link] ← ProcQueueFPtr[Areg]
}
Areg′←
undefined
Breg′←
undefined
Creg′←
undefined
Error signals: none
Comments:
Secondary instruction.
See also:
swapqueue
Page 92

intdis
92/212
intdis
(localised) interrupt disable
Code: 2C F4
Description: Disable interruption by high priority processes until either an
intenb
instruction is executedor the process deschedules.Timeslicing does not occur while
interrupts are disabled.This instruction is only meaningful forlow priority processes.
Definition:
Disable high priority interrupts
Error signals: none
Comments:
Secondaryinstruction.
See also:
intenb settimeslice
Page 93

intenb
93/212
intenb
(localised) interrupt enable
Code: 2C F5
Description: Enable interruption by high priority processes. This instruction is only
meaningful for low priority processes.
Definition:
Enable high priority interrupts
Error signals: none
Comments:
Secondary instruction.
See also:
intdis settimeslice
Page 94

iret
94/212
iret
interrupt return
Code: 61 FF
Description: Return from external interrupt. Signal
iret
to interrupt handlerand return
to the context of the interrupted process and resume execution. The interrupted high
priority state is recovered from the workspace – if this does not contain a running
process the processor switchesto the interrupted lowpriority state held in the shadow
registers.
Definition:
Status′←word[Wptr]
if (Status
has valid bit set
)
{
Wptr′←word[Wptr + 1]
Iptr′←word[Wptr + 2]
Areg′←word[Wptr + 3]
Breg′←word[Wptr + 4]
Creg′←word[Wptr + 5]
}
else
Return to interrupted low priority state
Error signals: none
Comments:
Secondaryinstruction.
Page 95

jn
95/212
j
n jump
Code: Function 0
Description: Unconditional relative jump. The destinationof thejump is expressedas
a byte offset from the firstbyte after the current instruction.j0 causes a breakpoint.
Definition:
if (n = 0)
Take a
breakpoint
trap
else
Iptr′←
next instruction
+ n
Areg′←
undefined
Breg′←
undefined
Creg′←
undefined
Error signals:j0 can cause a
breakpoint
trap to be signalled.
Comments:
Primary instruction.
Instruction is a descheduling point.
Instruction is a timeslicing point.
See also:
cj lend
Page 96

ladd
96/212
ladd
long add
Code: 21 F6
Description: Add with carry in and check for overflow.The result of the operation is
the sum of Areg, Breg and bit 0 of Creg.
Definition:
if (sum > MostPos)
{
Areg′←sum − 2
BitsPerWord
IntegerOverflow
}
else if (sum < MostNeg)
{
Areg′←sum + 2
BitsPerWord
IntegerOverflow
}
else
Areg′←sum
Breg′←
undefined
Creg′←
undefined
where sum = Areg + Breg + Creg
0
– the value of
sum
is calculated to unlimited precision
Error signals:
IntegerOverflow
can be signalled.
Comments:
Secondaryinstruction.
See also:
lsum
Page 97

lb
97/212
lb
load byte
Code: F1
Description: Load the unsigned byte addressed byAreg into Areg.
Definition:
Areg′
0..7
← byte[Areg]
Areg′
8..BitsPerWord-1
← 0
Error signals: none
Comments:
Secondary instruction.
See also:
bsub devlb lbx ls ldul
Page 98

lbx
98/212
lbx
load byte and sign extend
Code: 2B F9
Description: Load the byte addressed by Areg into Areg and sign extend to a word.
Definition:
Areg′
0..7
← byte[Areg]
Areg′
8..BitsPerWord-1
← Areg′
7
Error signals: none
Comments:
Secondaryinstruction.
See also:
bsub devlb lb xbword lsx ldul
Page 99

ldc n
99/212
ldc
n load constant
Code: Function 4
Description: Load constant into Areg.
Definition:
Areg′←n
Breg′←Areg
Creg′←Breg
Error signals: none
Comments:
Primary instruction.
See also:
adc mint
Page 100

ldclock
100/212
ldclock
load clock
Code: 64 FD
Description: Load into Areg the current value of ClockReg, of the priority selected
by Areg, where 0 indicates high priority and 1 indicates lowpriority.
Definition:
Areg′←ClockReg[Areg]
Error signals: none
Comments:
Secondaryinstruction.
See also:
stclock
 Loading...
Loading...