dallas semiconductor DS1207 service manual

查询DS1207供应商
DS1207
DS1207
TimeKey
FEATURES
• Cannot be deciphered by reverse engineering
• Time allotment from one day to 512 days for trial
periods, rentals, and leasing
• Partitioned memory thwarts pirating
• User-insertable packaging allows personal
possession
• Exclusive blank keys on request
• Appropriate identification can be made with a 64-bit
reprogrammable memory
• Unreadable 64-bit match code virtually prevents
discovery by exhaustive search with over 10
possibilities
• Random data generation on incorrect match codes
obscures real accesses
• 384 bits of secure read/write memory create
additional barriers by permitting data changes as
often as needed
• Rapid erasure of identification, security match code
and secure read/write memory can occur if tampering
is detected
• Durable and rugged
• Applications include software authorization, gray
market software protection, proprietary data, financial
transactions, secure personnel areas, and system
access control
PIN ASSIGNMENT
DALLAS
DS1207
TimeKey
SIDE
19
15
BOTTOM: PIN VIEW
See Mech. Drawings Section
PIN DESCRIPTION
Pin 1 NC No connection
Pin 2 RST Reset
Pin 3 DQ Data input/output
Pin 4 CLK Clock
Pin 5 GND Ground
1.0 IN
DESCRIPTION
The DS1207 TimeKey is a miniature security system
that stores 64 bits of user-definable identification code
and a 64-bit security match code that protects 384 bits of
read/write nonvolatile memory . The 64-bit identification
code and the security match code are programmed into
the TimeKey via a special program mode operation. After programming, the TimeKey follows a procedure with
a serial format to retrieve or update data. The TimeKey
is set to expire from one day to 512 days or infinity, as
specified by the customer. The T imeKey starts its countdown from the first access by the end user.
Interface cost to a microprocessor is minimized by
on-chip circuitry that permits data transfer with only
three signals: Clock (CLK), Reset
Output (DQ). Low pin count and a guided entry for a
mating receptacle overcome mechanical problems normally encountered with conventional integrated circuit
packaging, making the device transportable and
user-insertable.
(RST) and Data Input/
021798 1/17

DS1207
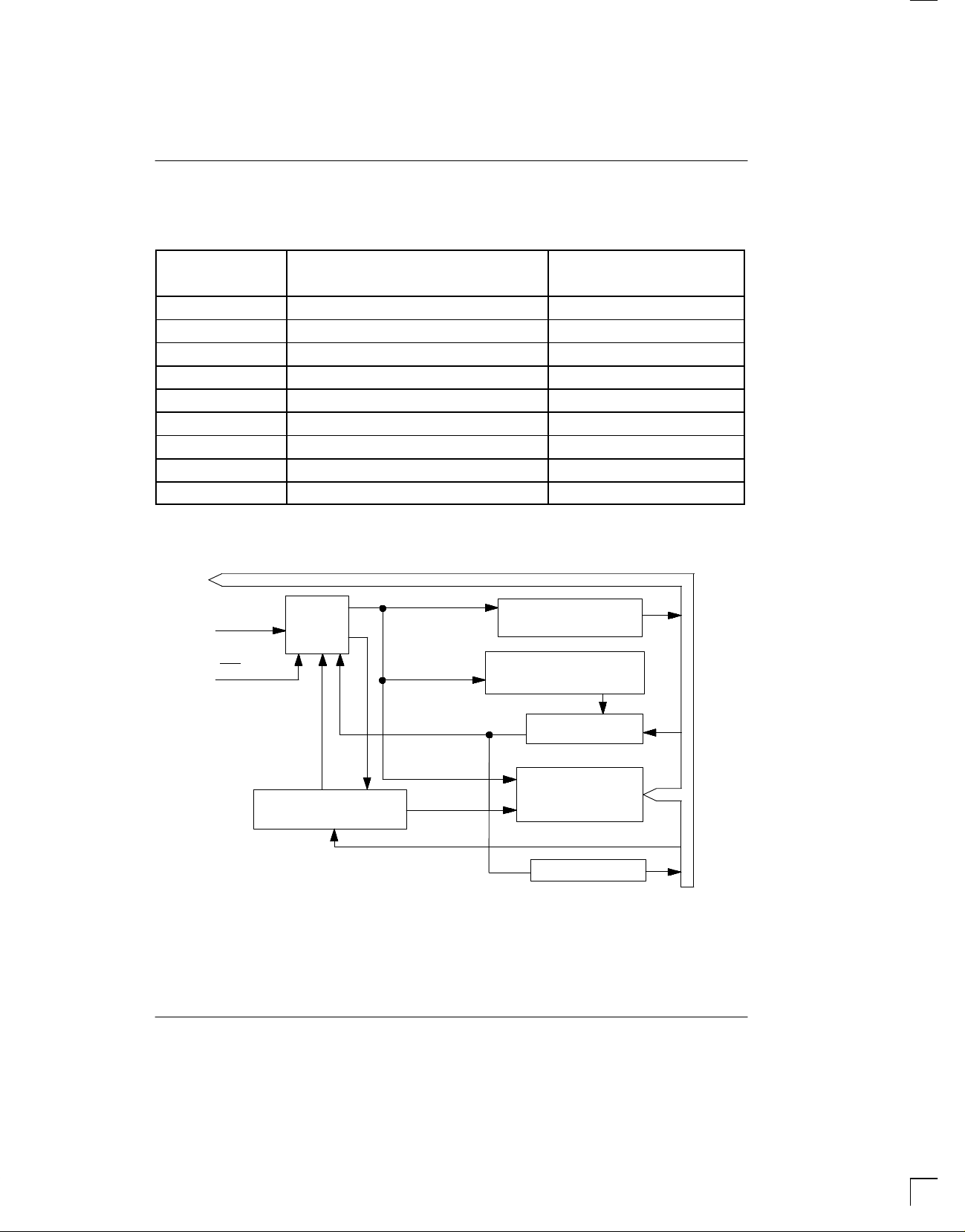
OPERATION – NORMAL MODE
The TimeKey has two modes of operation: normal and
program. The normal mode of operation provides the
functions of reading and writing the 384-bit secure
memory. The block diagram (Figure 1) illustrates the
main elements of the TimeKey when used in the normal
mode. T o initiate data transfer with the T imeKey , RST
taken high and 24 bits are loaded into the command register on each low-to-high transition of the CLK input. The
command register must match the exact bit pattern
which defines normal operations with a function code of
read or write. If one of these patterns is not matched,
communications are ignored. If the command register is
loaded properly , communications are allowed to continue. Data is clocked out of the TimeKey on the
high-to-low transition of the clock. If the pattern matched
in the command register calls for a normal read or write,
the next 64 cycles following the command word are read
and data is clocked out of the identification memory. The
next 64 write cycles are written to the compare register
(Figure 2). These 64 bits must match the exact pattern
stored in the security match memory. If a match is not
found, access to additional information is denied. Instead, if a normal read mode is selected, random
garbled data is output for the next 384 cycles. If a normal
write cycle is selected and a match is not achieved, the
TimeKey will ignore any additional information. However, when a security match is achieved, access is permitted to write the 384-bit secure memory .
OPERATION - PROGRAM MODE
The program mode of operation provides the functions
of programming the identification and security match
memory, and setting and reading the amount of time the
TimeKey can be used. The block diagram in Figure 3 illustrates the main elements of the TimeKey when used
in the program mode. T o initiate the program mode, RST
is driven high and 24 bits are loaded into the command
register on each low-to-high transition of the CLK input.
The command register must match the exact bit pattern
that defines the program mode for the identification and
security match bits or the program mode for setting and
reading the amount of time for which the TimeKey can
be used. If an exact match for one of the seven function
codes of the program mode is not found, the remainder
of the program mode is ignored. When the command
register is properly loaded for programming the identification and security match bits, the next 128 bits are written to the identification and security match memory
(Figure 4). When this mode of operation is invoked, all
memory contents are erased.
SETTING AND READING TIME REMAINING
There are six functions of the program mode which are
used to set or read the amount of time for which the
TimeKey will allow full operation. T o initiate any of the six
functions of the program mode used for setting and
reading time remaining, RST
is
are loaded into the command register on each
low-to-high transition of the CLK input. If the command
register is properly loaded with the function code for
reading the 20-bit day clock counter, the next 20 bits will
be output (LSB first) as a binary count of the amount of
time elapsed in the current day (see Figure 5). The time
can be calculated by dividing this count reading by 2
(20 bits is equal to 1,048,576 counts). One minus this result is the fraction of a day remaining. The 20-bit day
clock counter is driven by an internal oscillator that has a
period of 82.4 ms. If the command register is properly
loaded with the function code for reading the 9-bit number of days counter, the next 9 bits will be output (LSB
first) as a binary count of the days remaining (see
Figure 6). This count is decremented each time the day
clock counter rolls over to zero. When the number of
days remaining counter rolls through zero, normal and
program mode write cycles are inhibited. If the program
mode read cycle to the number of days counter is attempted, the nine bits will be returned as all ones.
If the command register is properly loaded with the function code for writing the 9-bit number of days counter,
the next nine bits will be input (LSB first) as a binary
count of the desired number of days in which the TimeKey will be fully functional (see Figure 7). The number of
days counter can be changed by writing over an entered
value as often as required until the lock command is entered. The lock command is given when the command
register is properly loaded with the function code for
locking up the number of days counter. The lock command consists of the 24-bit command word only (see
Figure 8). Once the lock command is given, all future
write cycles to the number of days register are ignored.
After the correct value has been written and locked into
the number of days counter, the DS1207 will start counting the time from the entered value to zero after the first
access to the TimeKey is executed, provided the arm
oscillator bit is set. The arm oscillator bit is set when the
command register has been properly loaded with the
function code for arming the oscillator. The arm oscillator command consists of the 24-bit command word only
(see Figure 9). One other command is also available for
use in setting and reading time remaining. A stop oscillator command is given when the command register is
is driven high and 24 bits
20
021798 2/17

DS1207
properly loaded with the function code for stopping the
oscillator. The stop oscillator command consists of the
24-bit command word only (see Figure 10). This command will only execute prior to issuing a lock command.
After the lock command is issued, stop oscillator commands are ignored.
A sequence for properly setting the expiration time of
the DS1207 is as follows (see Figure 1 1). First, program
the identification and security match bits to the desired
value. Use normal mode operation to write the appropriate secure data. Second, write the number days remaining register to the desired value. This number can be immediately verified by reading the number of days
remaining. Next, arm the oscillator by writing the appropriate command. Then do a normal mode read. This action will start the internal oscillator. Now read the 20-bit
day clock counter several times to verify that the oscillator is running. After oscillator activity has been verified,
issue the stop oscillator command. The lock command
should be issued, followed by the arm oscillator command. The TimeKey will start the countdown to expiration on the next access. T o guarantee security , a locked
TimeKey cannot be unlocked. The key cannot be reprogrammed after expiration. The oscillator verification
portion of this sequence is not required and can be deleted when speed in setting time remaining is important.
COMMAND WORD
Each data transfer for normal and program mode begins
with a 3-byte command word as shown in Figure 12. As
defined, the first byte of the command word specifies the
function code. Eight function codes are acceptable
(Figure 13). If any one of the bits of the first byte of the
command word fails to meet one of the exact patterns
for function codes, the data transfer will be aborted.
count, lock number of days count, arm oscillator, and
stop oscillator.
The remaining six bits of byte 2 and the first four bits of
byte 3 must be written to match one of the five patterns
as indicated in Figure 12 or data transfer will abort. Under special contract with Dallas Semiconductor, these
bits can be defined by the user as any bit pattern other
than those specified as unavailable. The bit pattern as
defined by the user must be written exactly or data
transfer will abort. The last four bits of byte 3 of the command word must be written 1011 or data transfer will
abort. Table 1 provides a summary of the command
words in hexadecimal as they apply to all function codes
for both program mode and normal mode.
RESET AND CLOCK CONTROL
All data transfers are initiated by driving the RST input
high. The reset input serves three functions. First, it
turns on control logic which allows access to the command register for the command sequence. Second, the
RST signal provides a power source for the cycle to follow. To meet this requirement, a drive source for RST
2 mA at 3.5 volts is required. Third, the RST
signal pro-
vides a method of terminating data transfer.
A clock cycle is a sequence of a falling edge followed by
a rising edge. For data inputs, the data must be valid
during the rising edge of the clock cycle. Command bits
and data bits are input on the rising edge of the clock.
Data bits are output on the falling edge of the clock. The
rising edge of the clock returns the DQ pin to a high impedance state. All data transfer terminates if the RST
pin is low and the DQ pin goes to a high impedance
state. Data transfer is illustrated in Figure 14 for normal
mode and Figure 15 for program mode.
of
The first two bits of the second byte of the command
word specify whether the data transfer to follow is program or normal mode. The bit pattern for program mode
is 0 in bit 0 and 1 in bit 1. The bit pattern for normal mode
is a 1 in bit 0 and a 0 in bit 1. The other two possible combinations for the first two bits of byte 2 will cause the
transfer to abort. The program mode can be invoked
with one of seven function codes: program identification
and security match, read the 20-bit day clock counter,
read the number of days count, write the number of days
TIMEKEY CONNECTIONS
The TimeKey is designed to be plugged into a standard
5-pin 0.1 inch center SIP receptacle. A guide is provided
to prevent the TimeKey from being plugged in backwards and aid in alignment of the receptacle. For portable applications, contact to the TimeKey pins can be determined to ensure connection integrity before data
transfer begins. CLK, RST
pulldown resistors to ground that can be sensed by a
reading device.
, and DQ all have 20K ohm
021798 3/17
DS1207
COMMAND WORDS Table 1
Summary of the command words in hexadecimal as they apply to all function codes for both program mode and normal mode for the DS1207-G01 only.(See Figure 12 and Figure 13 for detailed command words.)
MODE
FUNCTION COMMAND WORDS
MSB LSB
NORMAL READ B0 01 62
NORMAL WRITE B0 01 9D
PROGRAM WRITE B0 02 9D
PROGRAM READ DAY CLOCK COUNTER B0 02 F1
PROGRAM READ DAYS REMAINING B0 02 F3
PROGRAM WRITE DAYS REMAINING B0 02 F2
PROGRAM ARM OSCILLAT OR B0 02 F5
PROGRAM LOCK NUMBER OF DAYS COUNT B0 02 F6
PROGRAM STOP OSCILLATOR B0 02 F4
BLOCK DIAGRAM: NORMAL MODE Figure 1
D/Q
CLK
RST
Control
Logic
64-Bit
Identification
64-Bit
Security Match
021798 4/17
Command Register
Compare Register
384-Bit
Secure Memory
Garbled Data
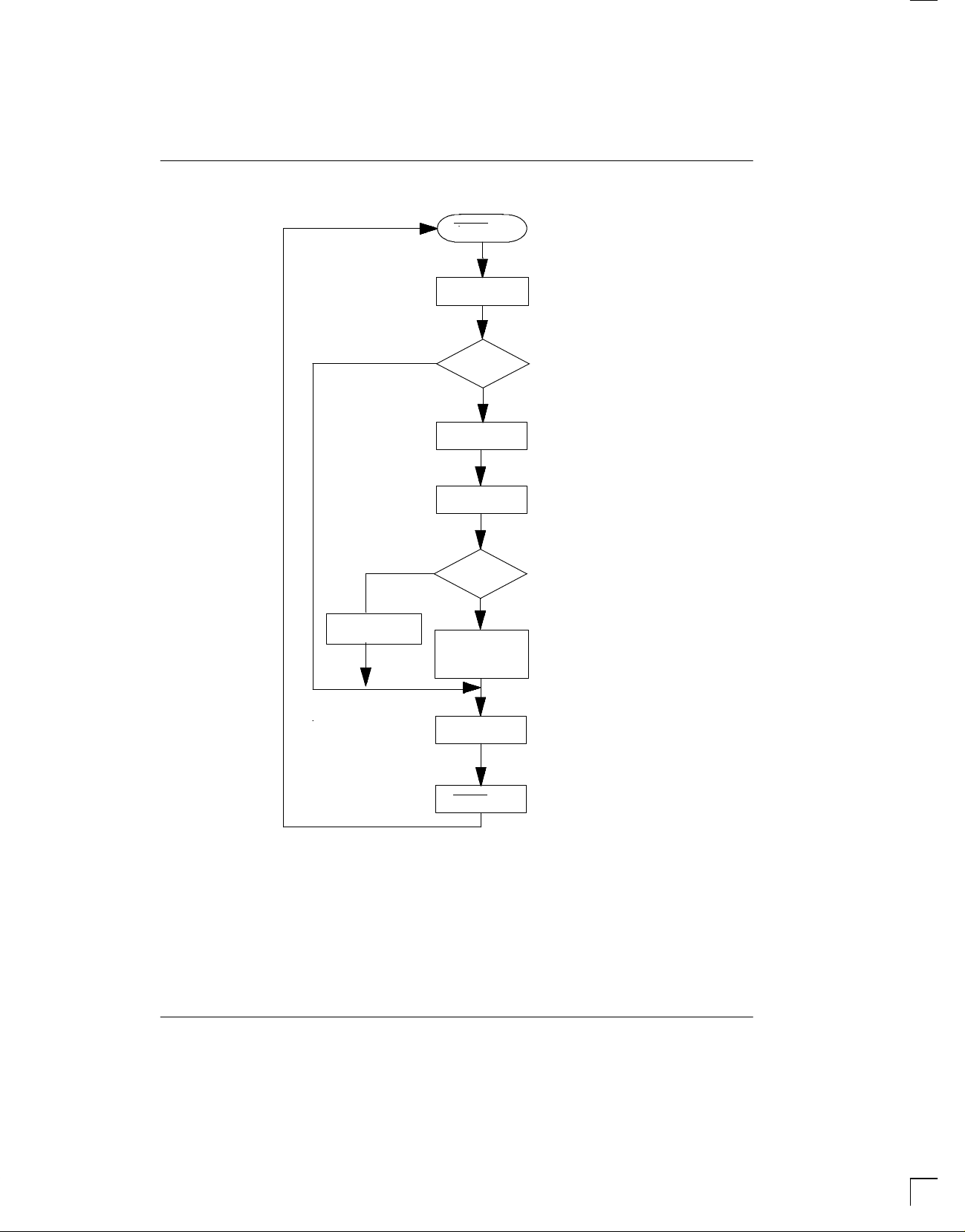
NORMAL MODE: READ OR WRITE SECURE READ/WRITE MEMORY Figure 2A
RESET High
DS1207
NO
NO
Output Garbled
Data
Write Command
Match
for Read or
Write
Read 64 Bits
Write 64 Bits
Match
Read or write
384 bits based on
function code
24 Bits Including
Function Code
Identification
Security Match
Secure Read/Write
Memory
Stop
RESET
Low
Output in High Z
021798 5/17
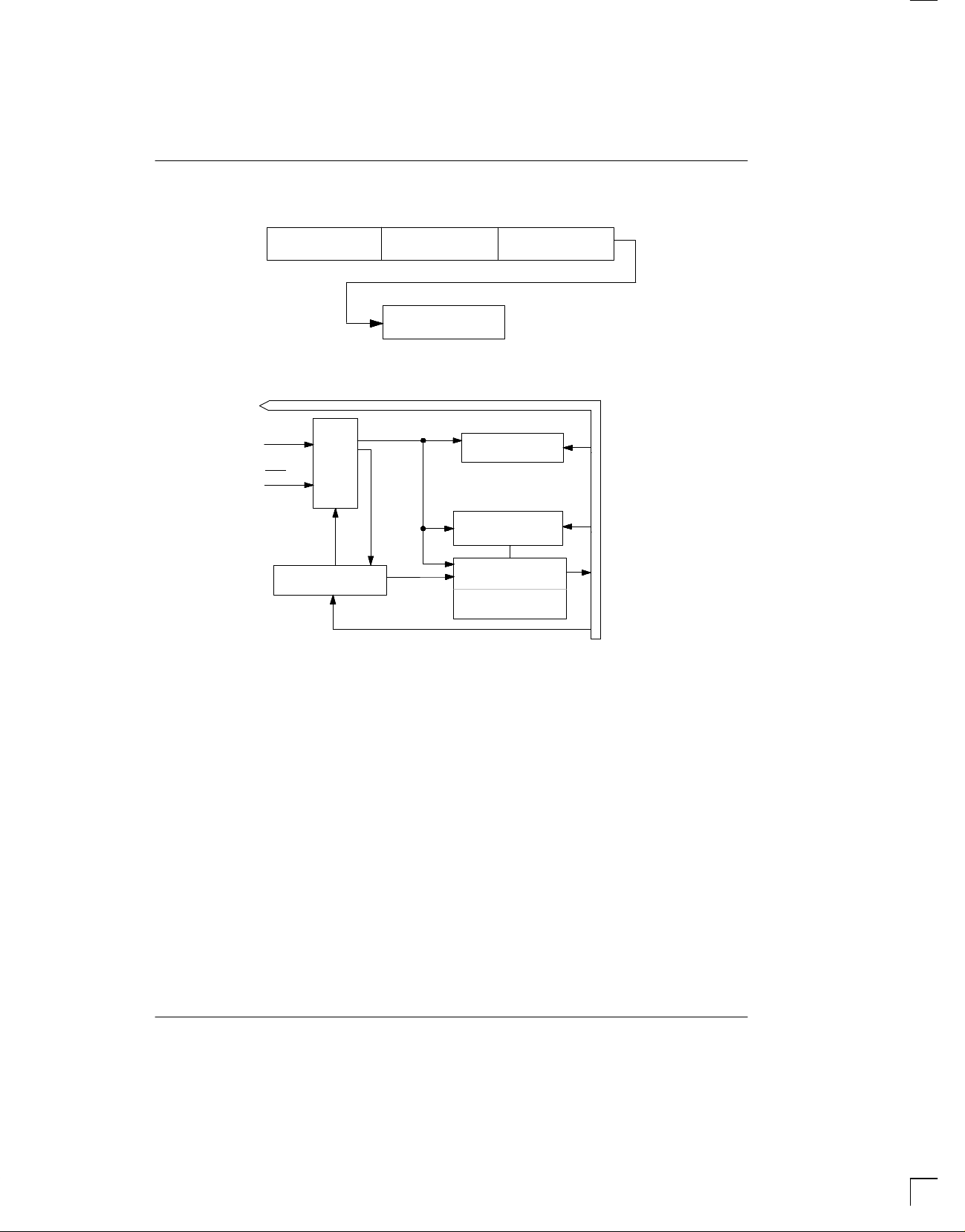
DS1207
SEQUENCE: NORMAL MODE, READ OR WRITE SECURE MEMORY Figure 2B
Function Code
Command Word 64 Read Cycles
Identification Security Match
64 Write Cycles
Match
Secure Memory
384 Reads or Writes
BLOCK DIAGRAM: PROGRAM MODE Figure 3
D/Q
CLK
Control
RST
Logic
Command Register
64–Bit
Identification
64–Bit
Security Match
20-Bit Clock
Counter
9-Bit No. of Days
Remaining Counter
021798 6/17
 Loading...
Loading...